SIEM & Log Management
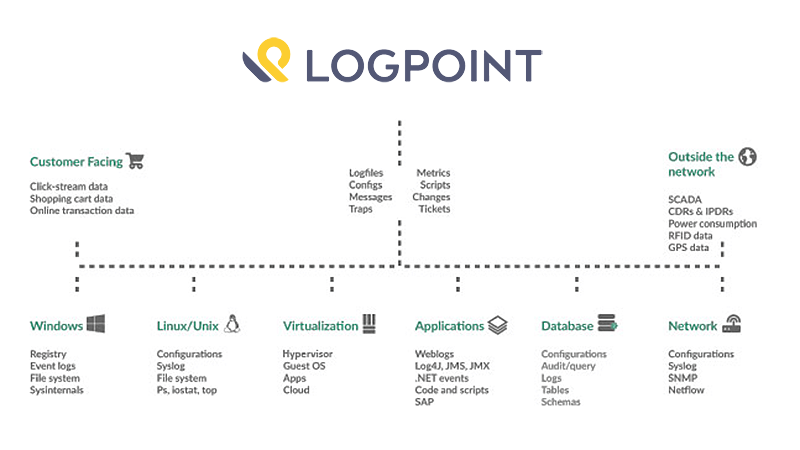
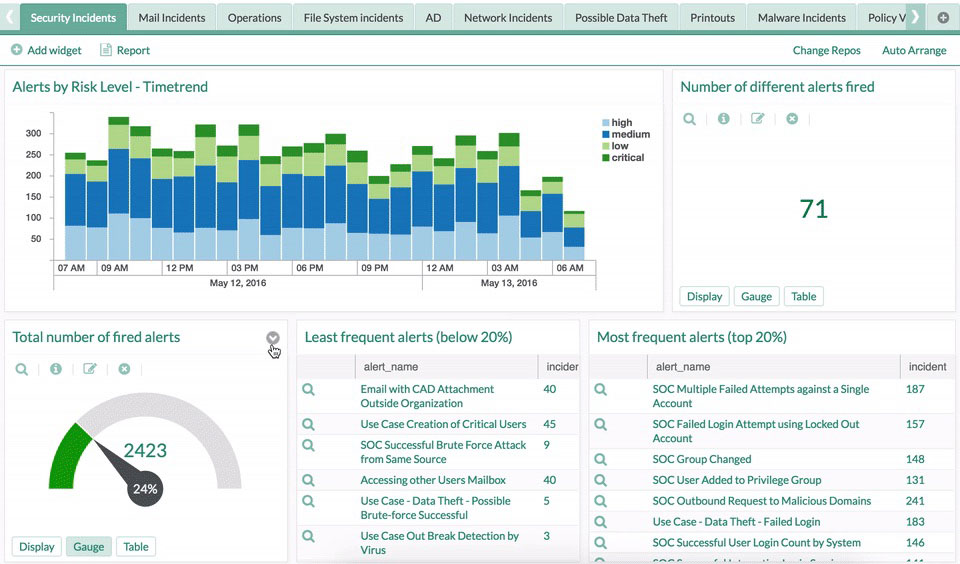
Logpoint is an advanced Security Information and Event Management (SIEM) platform with infinite application & integration possibilities.LogPoint enables the correlation of events and reporting on critical business operation in real-time, allowing enterprises to gather insight and understand the context of the billions of events generated daily by both core business applications as well as the infrastructure supporting and enabling the business.LogPoint provides a rich analysis platform and out-of-the-box dashboarding and reporting for infrastructure and critical business applications, enabling effective management and measurements of the enterprise security.
By leveraging LogPoint, it is possible to provide assurance towards auditors, authorities, and other third-parties that the enterprise is managed and monitored in a convincing, credible and timely fashion.
LogPoint adapts to stay in sync with client needs – from surpassing compliance demands, to seamlessly defending against cybercrime and fraud. LogPoint technology is designed to transform big data into an effortless package. LogPoint doesn't deliver standard results, it is simply delivering what you need, doing the work so you can get the job done.
Videos
-

LogPoint Product Presentation
-

LogPoint. SIEM. But different.
-
LogPoint presentation. SIEM made easy.
-
![How To: Install LogPoint on a virtual machine [step 2]](https://i.ytimg.com/vi/-qHsV7EEhsk/sddefault.jpg)
How To: Install LogPoint on a virtual machine [step 2]
-
![How To: Add devices [step 6]](https://i.ytimg.com/vi/Oi7uyyDxVMM/sddefault.jpg)
How To: Add devices [step 6]
-
![How To: Download and install applications [step 5]](https://i.ytimg.com/vi/WHlKdrApNW0/sddefault.jpg)
How To: Download and install applications [step 5]
-
![How To: Add log collection policies [step 8]](https://i.ytimg.com/vi/iAwLcFRY0Tk/sddefault.jpg)
How To: Add log collection policies [step 8]
-
![How To: Add Normalization policies [step 7]](https://i.ytimg.com/vi/k13Duajv6y0/sddefault.jpg)
How To: Add Normalization policies [step 7]
Information Security
It has never been more lucrative or attractive for abusers to target enterprises than it is now. LogPoint employs proactive monitoring, rapid trouble-shooting, advanced correlation and searches to overlook your enterprise’s security posture.
Across the board, all sectors are experiencing the same shifts, such as increased data-sharing from any location or device including mobile phones. Further, the diversity and accessibility of digital and new media is placing data and other resources at more risk for compromise. LogPoint not only has the ability to handle the mass of Big Data, it can also be leveraged to the diverse infrastructures of any organization.
With the emergence of e.g. Advanced Persistent Threats (APT), the cost of compromise is increasing at a higher rate than many organizations are aware. By definition, detecting APTs before a complete compromise is notoriously difficult. LogPoint offers organizations a qualified toolset that can actually identify APTs.
It has never been more lucrative or attractive for abusers to target enterprises than it is now. LogPoint employs proactive monitoring, rapid trouble-shooting, advanced correlation and searches to overlook your enterprise’s security posture.
Across the board, all sectors are experiencing the same shifts, such as increased data-sharing from any location or device including mobile phones. Further, the diversity and accessibility of digital and new media is placing data and other resources at more risk for compromise. LogPoint not only has the ability to handle the mass of Big Data, it can also be leveraged to the diverse infrastructures of any organization.

Among other things, LogPoint’s extensive reporting and dashboarding capabilities as well as the strong analysis engine enable the IT-responsible and decision makers in the enterprise to
- Perform analysis of security events and APTs.
- Automate and optimize the time spent meeting e.g. compliance and regulatory guidelines.
- Articulate and define the efficiency potential within the enterprise.
- Obtain the data needed for business-process reengineering.
- Identify misconfigurations and errors within the infrastructure.
- Gain substantial time-reduction when conducting root-cause analysis.
In the domain of SIEM, there are many different pillars of security management:
Operational Insight / Intelligence
LogPoint keeps complexities low and efficiencies high – while increasing operational insight.
Many organizations have processes in place to describe how to manage changes in the infrastructure, including handling problems and incidents, as well as measuring capacity and resources. A change in an enterprise’s IT environment is a complex task involving management suites, security updates, or software/hardware errors, as well as system and business owners.
LogPoint’s network and process integration, proactive monitoring and alerting, and tailored reporting can cut through organizational complexities.
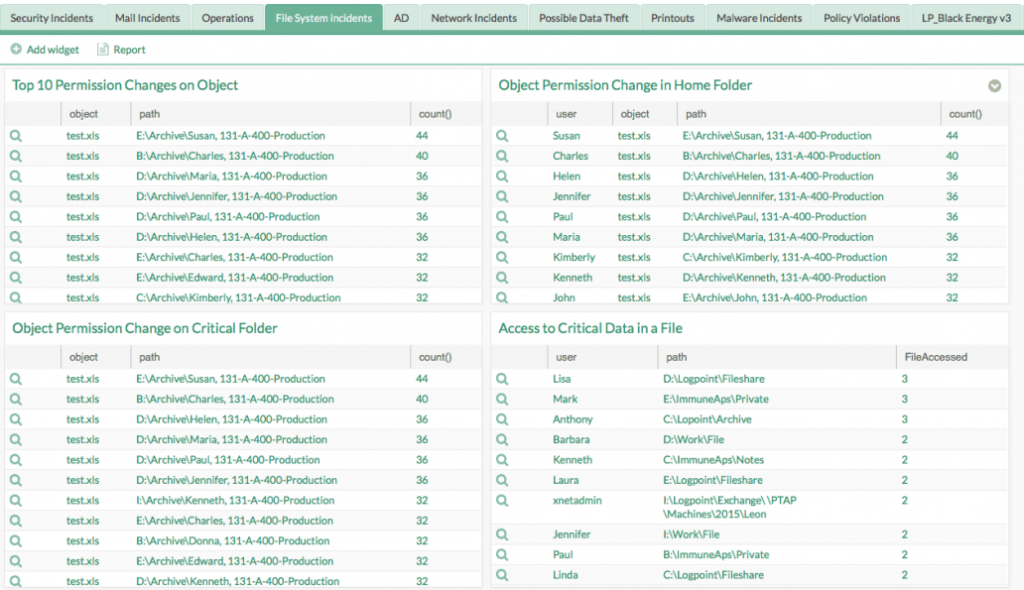
Deploying LogPoint in the network means that devices can send data to the LogPoint system, and actions can then be tracked and compared against registered changes. The same holds true for detecting problems within the infrastructure.
By measuring network traffic, LogPoint can pinpoint when service degradation started, comparing this data to intelligence on changes or modifications. Comparing error messages with incidents in the network greatly reduces the time to resolve and root-cause analysis.
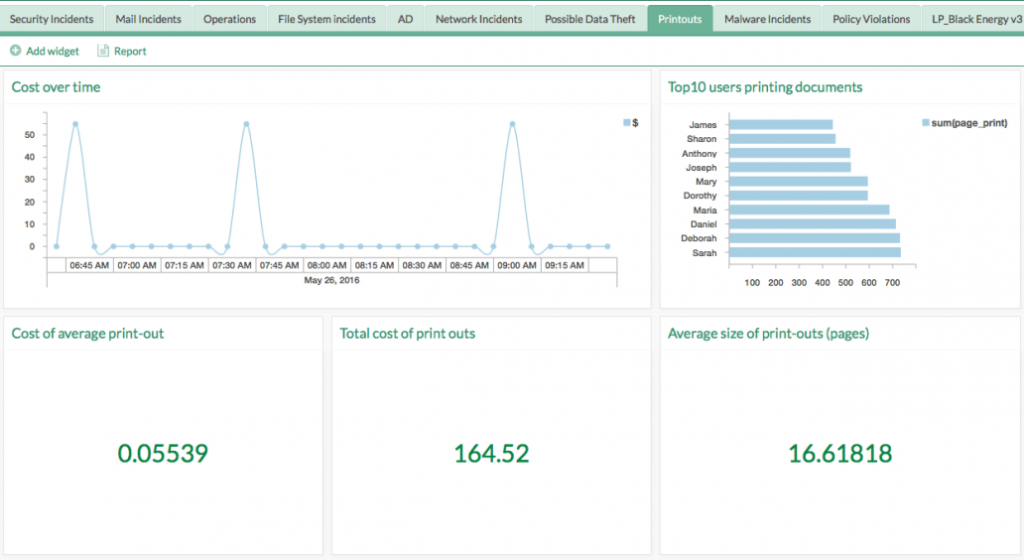
Compliance Management
One of the most common motivators for initiating a SIEM regime is the need to tick all compliance boxes. When the need to meet compliance requires that your organization’s IT team focuses on implementing a SIEM tool, it is clearly crucial that this tool be easy and simple to implement.
LogPoint offers you the highest level of out-of-the-box compliance within the shortest timeframe, delivering a complete set of compliance reporting elements for regulatory domains such as:
PCI-DSS
SOX
ISO27001 and ISO27002<
HIPAA
FISMA
BASEL-II
In addition, LogPoint provides a range of more detailed security monitoring reporting elements.
LogPoint provides a simple, transparent view into business events.
Logpoint provides a complete, transparent overview of the business processes. The analytical engine needed to automatically and manually make sense of an event so that you know exactly who did what, why and when.
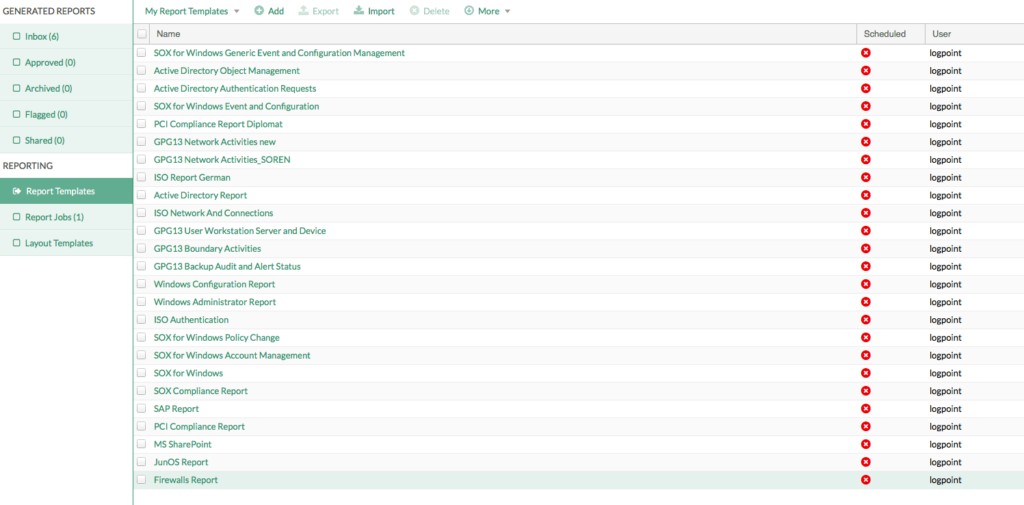
In terms of reporting, LogPoint offers a catalogue of various building blocks for organisations to choose from according to their individual requirements. The reports have been developed to cover the broadest spectrum of regulatory domains.
LogPoint’s flexible architecture and features mean that security resource time can instead be spent on vital daily business operations.
Application Security Monitoring
LogPoint enables you to analyze your critical production applications for optimal performance and maximum availability.
Application monitoring is often forgotten in large enterprises – focus is on servers, firewalls, routers and switches. However, LogPoint allows your applications to be included in the scope of proactive security monitoring and thus, by deploying LogPoint you can make the case for the development of an applications monitoring strategy that is easy to implement and maintain.
Often it is difficult for organizations to prioritize application security over revenue-generating development work and frequently security aspects of an application attack are underestimated. LogPoint delivers a trusted security platform to achieve great insights into any operational application environment such as SAP, Oracle, Microsoft and others.
The challenges with application security monitoring is the amount of information that must be collected, collated, analyzed, and summarized for management and business stakeholders as well as web application developers.
To enable a successful application security strategy, administrators needs visibility into attacks and policies. Understanding what an attack is and how it works is key in order to maximize uptime and performance of the application.
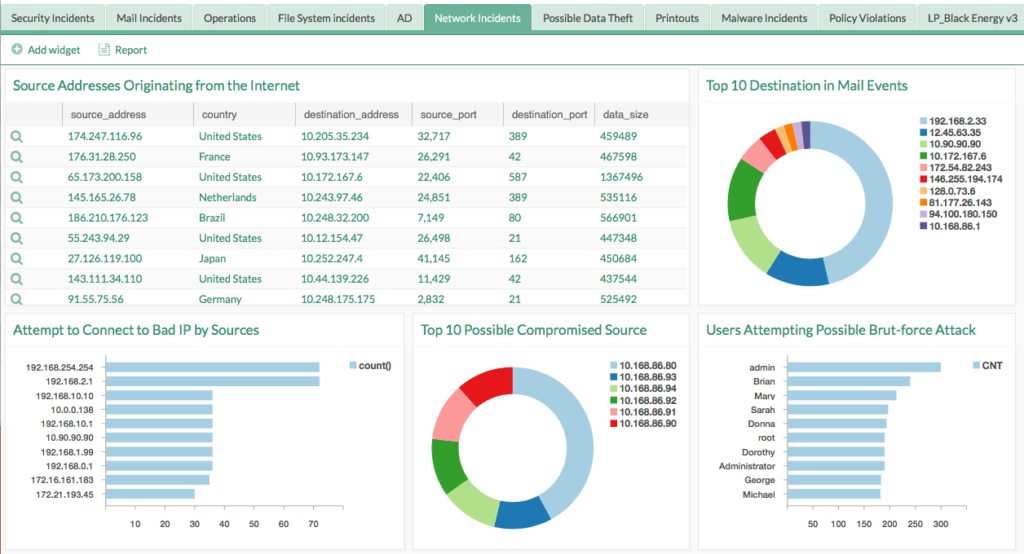
By deploying LogPoint the above is all made available in an easy to use package that integrates with the more traditional IT security facets from the IT operation. LogPoint even correlates data from both logs and structured data sources e.g. CMDBs, Social Security databases, medical records, financial systems and many more.
SAP® Integration
For most SIEM tools, an organization’s SAP® system is a blind spot. SAP® is extremely complex, making it close to impossible to extract logs.
With LogPoint for your organization’s SAP® system, you can achieve full anomaly detection, track critical changes to master data, and view correlations on business violations – out-of-the-box, with easy customization and expansion.
Vulnerable to Sabotage
Given the fact that a company’s SAP® system often stores the key information that attackers are looking for, these systems are especially prone to sabotage, fraud and espionage. There are numerous weaknesses that make your SAP® system vulnerable to sabotage, and along with ordinary threats other common threats include:
- Insecure code
- Missing security patches
- Uncontrolled remote access (RFC, SOAP)
- Active SAP® standard users
- Transports/SW-deployment
- Unauthorised profile changes
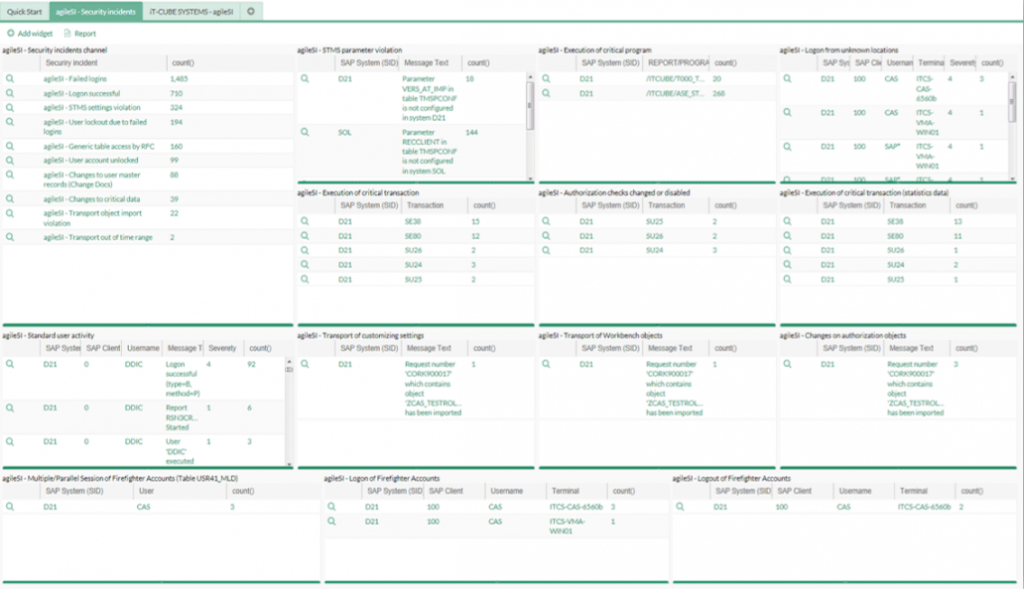
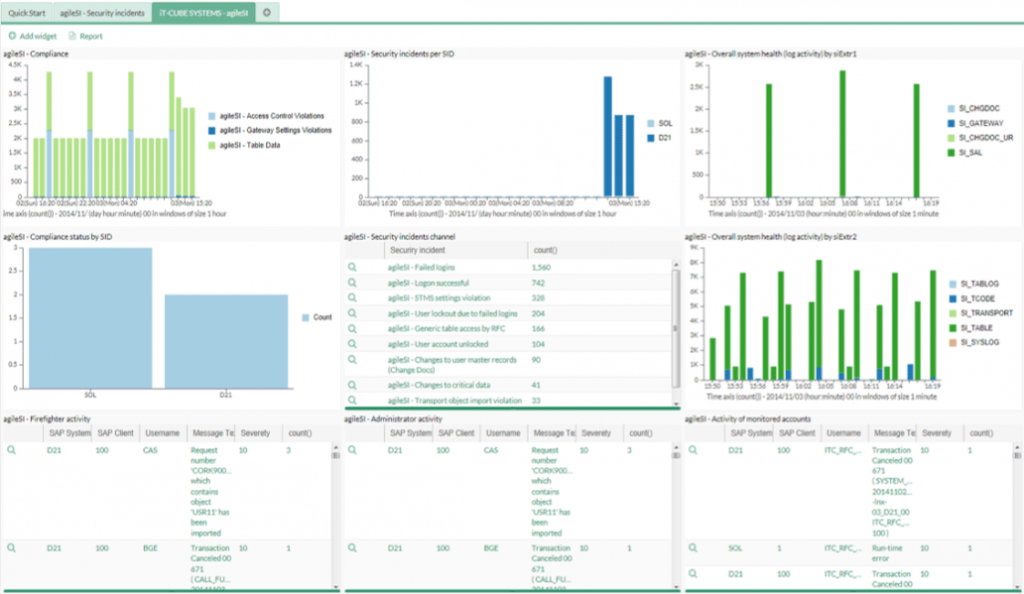
Benefits with LogPoint for SAP®
Proactively monitoring SAP® using LogPoint will result in a variety of benefits, including:
- Improvements to your SAP® Security & Risk Management
- A lowered number and level of criticalness on auditor’s findings
- Transforming risks into remediation
- Fulfilling compliance requirements throughout the SAP® landscape
- Consolidating the labyrinth of the SAP® tool into one, holistic approach
- Protection of essential business processes, sensitive data and intellectual property
Varieties of Implementation
LogPoint offers two varieties of SAP® implementation, the Light version that delivers a system log and an audit log, which can be directly utilized to demonstrate compliance and transparency, reducing costs through complete automation and the Extended version provides you insight beyond what can be derived in the Light version and covers in-depth monitoring of business processes.




