Safeguarding your work environment
Our philosophy is to provide a comprehensive range of solution-based, battle-tested services to improve performance, accelerate growth, reduce risks, and fortify your entire business framework, ensuring peace of mind for secure operations including everything from threat prevention to security infrastructure design to incident detection and response.
NSS technical team works closely with the channel partners to establish project timelines and realistic completion times. For our channel partners we go the extra mile in terms of channel readiness and enablement to ensure that the right product is made available at the right time in the most efficient and cost effective manner.
NSS is aware of the difficulties for both partners and end customers when implementing new information technology systems.
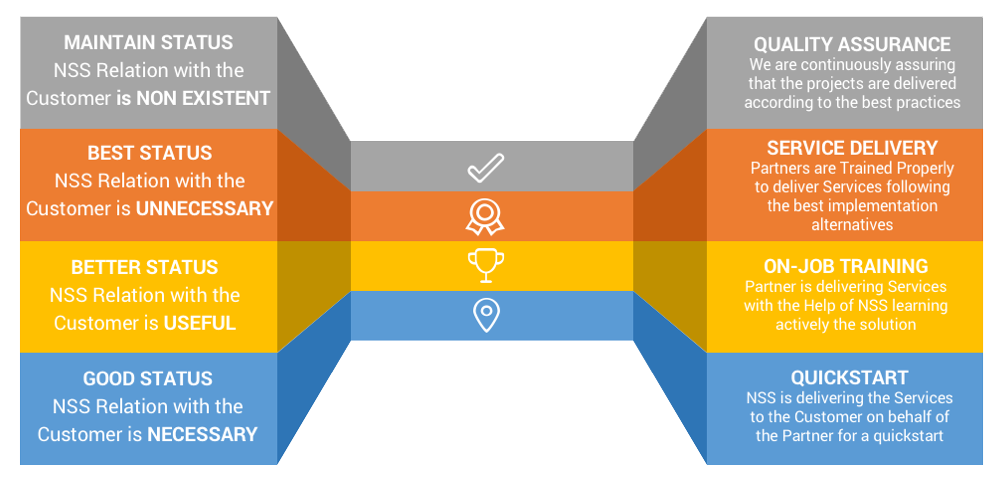
Our highly skilled engineers are certified by vendors official training in all the products that NSS distributes, in order to be able to offer qualified product field special services. NSS is able to offer a service to work with the partner and the customer together for a complete project implementation with the following unique methodology:
In the beggining, NSS is helping the partner to deliver services to the customer as a part of their training. This ensures optimal implementation and good speed of delivery. This is a quick-start method that provides good results for both the partner and the customer.
After one good project implementation, NSS is helping the partner to deliver the project staying behind as a consultant of the partner, safeguarding the project and end-customer investment. This is a necessary stage that provides even better results contributing greatly to the partner morale.
The ideal results are provided when the partner delivers the projects independently from NSS. There is a specific training and enablement plan that NSS has designed that is able to make the partner very strong in project complete delivery, independently of the project complexity. This involves an innovative methodology as NSS is not distributing a single product but a portfolio of solutions that integrate to each other.
NSS offers robust Infrastructure Protection services that cover all of your offensive security needs, aiming to reduce the risk of such attacks through various countermeasures. We help you create a more secure and automated organization by giving you the tools and flexibility you need to keep business running smoothly in an ever-changing threat landscape with security at the forefront. We aim to keep your permissions locked down, your valuable data safe, and your threats minimized, all while maintaining productivity. We focus our solutions on two key areas to help you streamline your security stance.
Our infrastructure protection services allow you to identify and prioritize vulnerabilities in your systems and determine how to best respond to them.
You can’t protect your system if you don’t know what risks you face. Vulnerability management is a long-term security strategy that involves continuously identifying, classifying, prioritizing, remediating, and mitigating vulnerabilities in IT environments.
Having a vulnerability management program is a critical part of maintaining compliance and reducing the risk of both internal and external attacks. Establishing and maintaining a strong program can help you proactively understand potential threats to every asset within your IT infrastructure.
- Vulnerability Scanning & Assessment
- Application Security Testing
- Integrity Monitoring
- Threat Scanning & Monitoring
Reactive solutions and processes like threat detection and patching will always be a vital part of cybersecurity. However, with the threat landscape constantly growing and evolving, it’s become essential to tackle the problem from every angle.
An offensive security approach does just that with proactive solutions and processes that expose and close security gaps before a breach ever occurs. An offensive security strategy identifies weaknesses and uses the same exploitation techniques as threat actors to determine risk. To put it simply, the goal of offensive security is to be a deterrent, providing significant obstacles to ensure that attackers never see your environment as an easy target, but instead one that would be time consuming, labor intensive, and ultimately not worth the hassle.
- Penetration Testing
- Red Team Operations
- Security Testing Services

Chances are, your team is struggling to keep up with the ever-growing workload, increasing security threats, and shifting priorities that have become hallmarks of today’s IT environment. Instead of proactively building your security posture, you’re forced to be reactive, always fighting the biggest fire first.
You need a better way. The NSS way.
NSS is adding value to the ecosystem of clients and channel partners by complementing their skills and knowledge in such a manner that they can enhance their customer base, generate more valuable business opportunities and manage complex business opportunities exceeding their own skill and resource capabilities. NSS value adding is also defined by the official training that can be offered to the channel partners. Learning deeply into a new system can be really difficult. NSS can transform good engineers into solution architects in no time. NSS can teach the partner the best practices and demonstrate all the ways to utilize every bit of value out of the products that NSS distributes.
NSS is an Authorized Training Center for several products of different Vendors. Courses are given in English & Greek language with English documentation. Prices include training materials, vouchers for official vendor certificates when applicable, coffee & lunch during the training procedure. NSS aims to educate and prepare all participants with the skills needed to deploy a solution efficiently and effectively, maximizing the existing investment.

Our technical training team (NSS-TTT) combines a deep knowledge of the products with extensive real world experience of designing, deploying and troubleshooting implementations across the entire range of customer types. All of our courses are taught by systems experts with years of technical support experience and in depth product knowledge so that attendees can not only learn how to configure, but how to avoid common mistakes in system deployments. Most of the training courses include ‘hands on’ exercises. Our training rooms can accommodate up to 6 delegates, allowing for a high level of personalisation and interaction with the trainer bringing the training experience to a really high-level.
By following NSS training courses you can achieve:
Greater efficiency in their IT processes, saving hours of admin time per week.
Improved performance of products, resulting in less internal helpdesk calls.
Reduced need to contact Technical Support with the accompanying time needed for logging and managing cases, conference calls, collecting logs etc.
Improved understanding and adoption, of all modules and technologies used in the products, maximising their organisation’s investment and ensuring organisational security.
Knowledge of the latest industry best practices as well as the latest threats and how to combat them, all ensuring greater protection and improved information security.
NSS offices where training is taking place, is very easily accessible by Metro which is the simplest and quickest way to move around Athens and from the airport to our office, Blue Line, of Keramikos station is merely 70m away from our building.
If you have some spare time, we will be glad to discuss and organize together with you a private tour to Acropolis museum and the ancient Acropolis citadel or any kind of interesting place you like in the center of Athens. Let us know about it !
Our training courses are regularly scheduled onsite, yet hybrid training is also available if requested, as part of a special agreement provided that it meets our high standards. You may contact us at training@nss.gr to discuss your requirements in specific or if you would like to suggest a specific program that is not listed below:

Sophos UTM Certified Engineer Course
Objectives:
This hands-on course is designed to give you a good understanding of Unified Threat Management concept and demonstrate Sophos technology simultaneously. It consists of theory components, demonstrations and practical labs, covering all aspects of the Sophos UTM. It explores best practice for network deployment and configuration, focusing on system administration and troubleshooting. Upon successful completion of this course, students will know how to deploy Sophos UTM in complex environments, Configure Web and SMTP proxies, implement firewall configurations, manage endpoint and e-mail protection using the UTM, set up VPN’s for branch offices and roaming users, integrate the UTM with AD, LDAP and RADIUS, use the UTM as a DNS and DHCP server / forwarder
Overview:
- Unified Threat Management Overview
- Deployment of Sophos UTM in a customer network
- Basic configuration and troubleshooting
- Firewall, network and security settings
- Configuring local user authentication and AD/LDAP integration
- Setting up UTM to manage FTP and HTTP traffic
- Configuring the UTM for e-mail protection
- Setting up site-to-site VPN’s and Remote Access
- Configuring the UTM to protect internal Web Servers
- Architecture, configuration and deployment of Endpoint Protection
- System management and reporting
- Lab Exercises
Duration: 2 Days Hybrid Training
Prerequisites: Good knowledge in Networking
Sophos Endpoint Protection Certified Engineer Course
Objectives:
This hands-on workshop provides high level technical understanding of Sophos Endpoint Security and Control products. Learn about the components, how they are deployed across a network, and focus on system configuration, troubleshooting and best practice. This course equips students with knowledge of all the component parts of Endpoint Security and Control. It presents best practices for network deployment, focusing on system configuration and troubleshooting.
Overview:
- Deployment of Sophos Enterprise Console
- Deployment of Sophos Anti-Virus across a Windows network
- Advanced administration tasks within Sophos Anti-Virus and Enterprise Console
- Application control, device control, and effectively managing threats and potentially unwanted applications (PUAs)
- General troubleshooting
- Dealing with a virus outbreak
- Lab Exercises
Duration: 2 Days Hybrid Training
Prerequisites: Moderate knowledge in Networking, Windows Server Environments, SQL Databases
Sophos Data Protection Certified Engineer Course
Objectives:
This course is designed to provide orientation and training on Sophos Safeguard Enterprise product explaining all the different components, features, and best-practice configurations. Upon Successful completion of this course you will be able to install and implement SafeGuard in an users’ environment, administer SafeGuard via the management Center interface, perform basic troubleshooting, start protecting laptops and desktops from data loss and the resulting fines that can accompany data loss.
Overview:
- SafeGuard components and their inter-communication and configuration
- Policies and basic setup
- Client deployment
- High-level coverage of the modules that are a part of the SafeGuard Client and their usage
- Basic Support of deployed clients
- Lab Exercises
Duration: 2 Days Hybrid Training
Prerequisites: Moderate Knowledge in Networking, PKI & Encryption principles, Windows Server Environments, SQL Databases
Sophos Mobile Control Certified Engineer Course
Objectives:
Upon successful completion of this course you will be able to begin your installation of the Sophos Mobile Control product in a standard environment, identify reasoning behind platform requirements, describe and demonstrate all significant features of the product, including Power User & Admin features, identify how to best capture information on complex problems, communicate effectively for resolution and manage the resolution path.
Overview:
- Live tour of the Sophos Mobile Control web interface
- Overview of prerequisites and installation procedures
- Review of deployment options for Sophos Mobile Control clients
- Review of common administrative tasks within Sophos Mobile Control
- Best-practices for defining polices, deploying apps, and locking/wiping mobile devices
- Lab Exercises
Duration: 1 Day Hybrid Training
Prerequisites: Moderate knowledge in Networking and Mobile Operating Systems handling
Sophos UTM Certified Architect Course
Objectives:
Upon completion of the Sophos UTM Certified Architect training course, students can acquire the skills needed to configure, manage, and update the different features of Sophos UTM solution, even in the most complex network environments. The main focus of this training is based upon the advanced configuration options and more sophisticated scenarios. Typical implementation tasks from practice are provided and analyzed by the participants themselves, configured and tested. With the completion of the advanced lab exercises, participants can achieve very deep product knowledge being able to design solutions of any caliber. This course is designed for anyone who has good exposure to Sophos UTM and wishes to increase their technical understanding of the product to a higher level, particularly in order to pass the Sophos UTM Certified Architect exam.
Overview:
- Advanced Networking and Network Protection
- Advanced User Authentication and Web Protection implementations
- Advanced VPN Connectivity for site-to-site or roadwarrior access
- Multi Domain E-mail Security and Reporting
- Troubleshooting and analysis techniques
- Advanced Lab Exercises completion
Duration: 4 Days Hybrid Training
Prerequisites: Deep knowledge in Networking, Sophos UTM Engineer Certification
Sophos Endpoint Protection Certified Architect Course
Objectives:
Upon Completion of this course students will be able to define the architecture and dimensioning of the solution within the customer site, install and configure the Endpoint Protection solution in a multi-server environment, configure the solution by following the best practices of Sophos. After this course student will be able to perform troubleshooting of all components of the solution, migrate the system to a different server and even have an idea of how Sophos SQL database behind the solution is working. This course is designed for people who had exposure to Sophos Endpoint Security and Control and wish to increase their technical understanding of the product to a superior level.
Overview:
- Install the product in a complex environment
- Prepare recommendations around deployment and best practice in a complex environment
- Resolve issues of high complexity
- Identify reasoning behind platform requirements and how to overcome shortfalls in infrastructure
- Perform detailed ad-hoc customisation to meet requirements
- Identify how to best capture information on complex problems
- Advanced Lab Exercises completion
Duration: 3 Days Hybrid Training
Prerequisites: Good knowledge in Networking, Windows Server Environments, SQL Databases, Sophos Endpoint Protection Engineer Certification
Sophos Data Protection Certified Architect Course
Objectives:
Upon Completion of this course students will be able to define the architecture and dimensioning of the solution within the customer site, deploy and configure the SafeGuard Enterprise solution following the best practices of Sophos. Following that course, students will be able to to perform good troubleshooting of all components of the solution, being able to install the product in a complex environment, describe and demonstrate all significant features of the product, including Power User & Admin features in order to perform the most advanced administrative tasks and control an enterprise diverse environment’s security efficiently and effectively
Overview:
- Architectural Overview of the solution
- Prerequisites of a Succesful Deployment
- Walkthrough of Disk Encryption, Data Exchange, Configuration Protection, File Share and Cloud Storage Configuration
- Advanced Server Configuration & Endpoint Deployment
- Advanced Administration Tasks within Management Console
- Policy configuration and Update
- Reporting and Auditing
- Analysis of the Client Architecture
- Data Recovery Process
- System Updating
- Advanced administration tasks within Sophos Management Center Console
- Tokens and smartcards
- Advanced Lab Exercises completion
Duration: 3 Days Hybrid Training
Prerequisites: Good knowledge in Networking, PKI & Encryption principles, Windows Server Environments, SQL Databases, Sophos Data Protection Engineer Certification
Sophos Mobile Control Certified Architect Course
Objectives:
Upon Completion of this course students will have the opportunity to acquire the skills needed to configure, manage, and update the different features of the solution Sophos Mobile Control on an expert level. Students participating in the course will be able to describe and demonstrate the main features of the solution, define system requirements, designing an architecture for deployment, install and configure Sophos Mobile Control, configure the solution in compliance with the best practices of Sophos and last but not least being able to troubleshooting the individual components of the solution
Overview:
- System Installation
- Customer overview
- Device Management
- Console Management
- Configuring Devices
- Policy configuration
- Sophos Mobile Security
- Upgrade procedures
- Backup and restore procedures
Duration: 3 Days Hybrid Training
Prerequisites: Good knowledge in Networking, Knowledge about Active Directory & Microsoft Exchange or other Email Infrastructure, Knowing how to use a web server with a web interface or similar infrastructure, Know the iOS devices, Android and Windows Mobile, Sophos Mobile Protection Engineer Certification

Array Networks APV Engineer Course
Objectives:
Upon completion of the Array Networks Engineer training, students can acquire a deep understanding of Array Networks application delivery and load balancing solutions and their key competitive advantages, obtain the knowledge to properly install as well as making correct sizing recommendations, troubleshooting problems and out-maneuvering competitors during RFQs.
Overview:
- Introduction of the APV Series
- Installation Basics, Quick Start
- Server Load Balancing, Application Health Checking
- HTTP Caching, SSL Acceleration, HTTP Compression
- URL Filter & Rewrite, Webwall
- Clustering & Config Sync, Link Load Balancing
- Global Server Load Balancing
- Advanced Networking
- Troubleshouting
Duration: 3 Days Hybrid Training
Prerequisites: Good knowledge in Networking
Array Networks AG Engineer Course
Objectives:
Upon completion of the Array Networks Engineer training, students can acquire a deep understanding of Array Networks access gateway solutions and their key competitive advantages, obtain the knowledge to properly install as well as making correct sizing recommendations, troubleshooting problems and out-maneuvering competitors during RFQs.
Overview:
- Introduction of the SPX and AG Series
- Installation Basics, Networking Possibilities
- Access Methods, Client Security
- Virtual Site configuration, Clustering
- Portal Installation & Customization
- DesktopDirect
- Advanced Features
- Troubleshouting
Duration: 3 Days Hybrid Training
Prerequisites: Good knowledge in Networking

PePLink Certified Engineer Course
Objectives:
Upon completion of the Peplink Certified Engineer (PCE) training, students can acquire a deep understanding of Peplink products and their key competitive advantages, obtain the knowledge to properly install and maintain Peplink products as well as making correct product recommendations, troubleshooting problems and out-maneuvering competitors during RFQs.
Overview:
- PePLink VPN Concept, Unbreakable VPN, SpeedFusion Hot-Failover, SpeedFusion Bonding & Applications
- Peplink and Pepwave Product Suite Overview & Configuration
- Balance and MAX Router Overview & Configuration, Web Admin, Standard WAN Load Balancer Deployment, Drop-in Mode, Inbound Load Balancing, Control Outgoing Traffic, High Availability, WLAN Controller, QoS Bandwidth Control, Service Forwarding & Passthrough
- Wireless AP Overview and Configuration, Network Configuration, Secure Access Configurations, WDS Configuration, Wireless Network Discovery
- Surf Series Overview and Configuration, Cellular Mode, WiFi Mode, Wired Mode, WAN Failover
Duration: 1 Day Classroom Training
Prerequisites:Moderate knowledge in Networking




