Cybersecurity Solutions
Fortra offers a comprehensive suite of cybersecurity and automation solutions to protect organizations from modern threats. Its portfolio includes tools for data security, email security, identity and access management, network defense, and vulnerability management. Additionally, it provides automation solutions that enhance efficiency and compliance. With a strong focus on threat management, Fortra helps businesses detect, prevent, and respond to cyber risks, earning the trust of organizations worldwide. By offering multi-layered protection, it ensures resilience against cyberattacks. Fortra empowers businesses to safeguard critical data, optimize operations, and stay ahead in the face of digital challenges.
Security teams don’t care about tools; they seek business results. Every day, Fortra detects and mitigates cyber threats, aiming for successful "protected outcomes." These are one of the ways Fortra is shaping a stronger and simpler future for cybersecurity.
Videos
-

HelpSystems Data Security Suite Demonstration
-

Boldon James - Data Classification Overview
-

Boldon James | File Classifier
-

Boldon James | SharePoint Classifier
-

GoAnywhere File Transfer App
-

What Are the Top File Transfer Protocols?
-
Vulnerability & Threat Management Webinar - HelpSystems (now Fortra) - Digital Defense
-

Penetration Testing: Enabling security teams to conduct advanced testing with ease - HelpSystems
Data Security Management
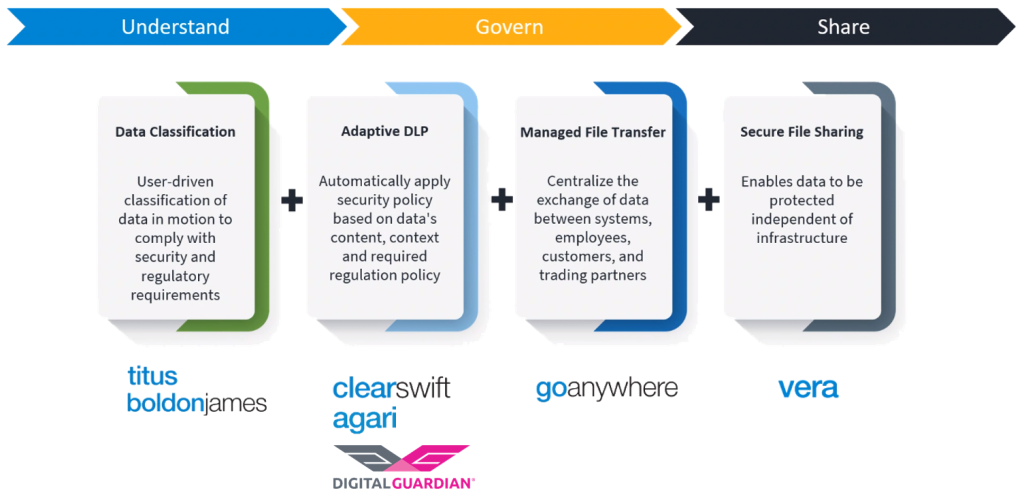
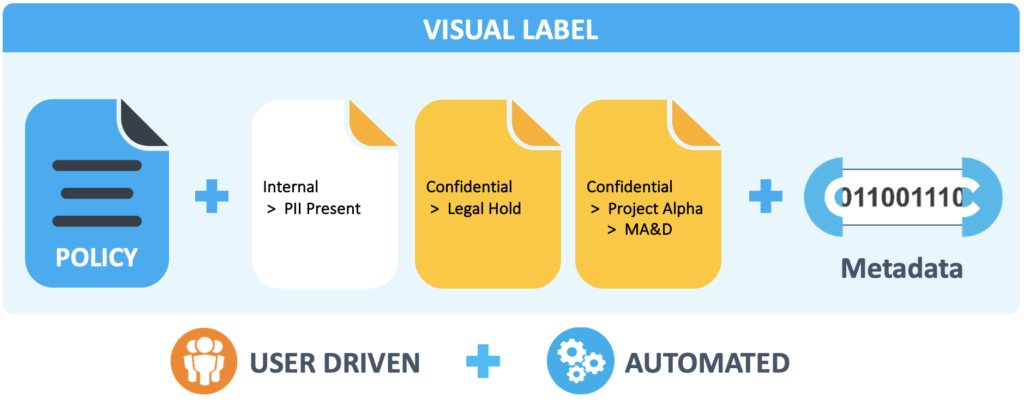
Data Classification
Boldon James
Boldon James is an industry specialist in data classification and secure messaging for military, delivering globally-recognized innovation, service excellence and best-of-breed technology solutions, by integrating with powerful data security and governance ecosystems to enable customers to effectively manage data, streamline operations and proactively respond to regulatory change.
Boldon James is proud to be part of Fortra’s comprehensive cybersecurity portfolio. Fortra simplifies today’s complex cybersecurity landscape by bringing complementary products together to solve problems in innovative ways. These integrated, scalable solutions address the fast-changing challenges you face in safeguarding your organization. With the help of the powerful protection from Boldon James and others, Fortra is your relentless ally, here for you every step of the way throughout your cybersecurity journey.
Key features:
- Improves policy enforcement, delivering compliance, driving business performance
- Automates classification and ensures compatibility
- Simple, unobtrusive and building a culture of security awareness
- Raises user awareness of security responsibilities
Titus
Titus is synonymous with world-class data classification and are trusted by millions of users around the world, including top military, government and Fortune 100 organizations. With the addition of data identification and advanced machine learning technologies, Titus has evolved into a global leader in enterprise-grade data protection solutions, achieving compliance across a wealth of new international data privacy laws and regulations is the benchmark for effective cybersecurity. Experts in data classification, data identification, and security automation.
Fortra’s Titus solutions are trusted by millions of users around the world, including top military, government, and Fortune 100 organizations. With the addition of data identification and advanced machine learning technologies, Titus has evolved into a global leader in enterprise-grade data protection solutions.
Key features:
- Leverages multiple data detection methodologies, including machine learning to best understand data.
- Provides the industry’s most flexible and customizable classification metadata schema.
- Creates metadata that enables DLP and other solutions to make informed decisions around how to handle data, leading to a more efficient data security ecosystem.
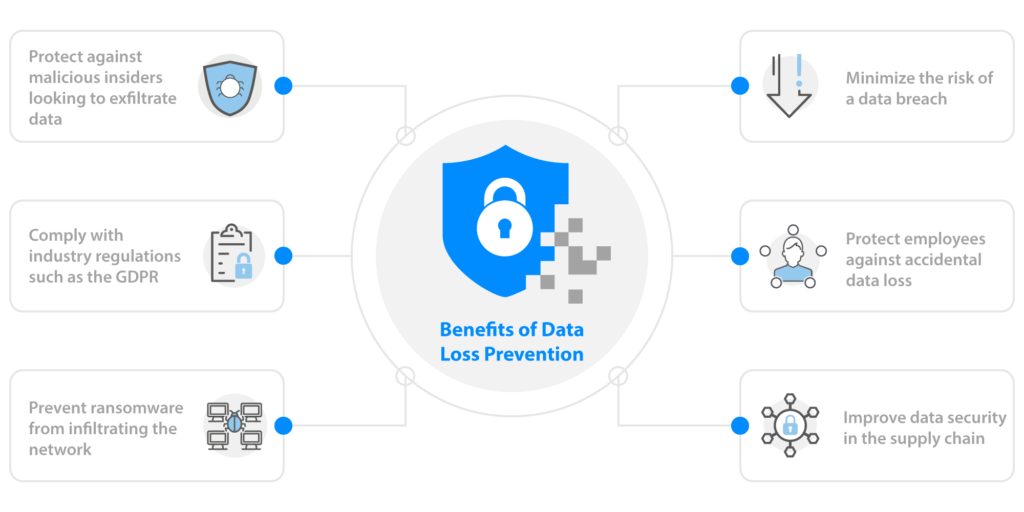
Adaptive Data Loss Prevention (DLP)
Clearswift Endpoint
Data loss prevention (DLP) is a key concern for organizations who need to comply with regulatory requirements such as GDPR or HIPAA. Organizations in industries such as defense, government, healthcare and financial services rely on Clearswift to provide the highest level of cybersecurity protection for email, web and endpoints.
All Clearswift products are based on a deep content inspection engine that detects, analyzes and modifies content in real time. Unique redaction and sanitization features remove only the elements that can potentially cause an unwanted data breach or disruptive cyber-attack, keeping communications flowing and risk-free.
Key features:
- Rules, such as redact, sanitize, delete, encrypt, block, or monitor, are applied based on content and context provided by Data Classification.
- Automatic detection and removal of sensitive and hidden data, and active security threats as data enters an organization.
- Avoid unnecessary disruption and lower IT overhead costs by working jointly with Data Classification and other security solutions.
Clearswift Secure Email Gateway (SEG) provides uniquely powerful protection of an organization’s email data against inbound cyber-attacks and outbound data loss prevention. With deep content inspection capability and powerful adaptive redaction features, it removes evasive cyber-threats and prevents unwanted data breaches in real-time. Working alone or alongside cloud-based email applications such as Office 365 and G Suite, the Secure Email Gateway is an essential security layer to maximize cybersecurity defenses.
Key features:
- Multi-layer anti-virus protection (Sophos, Avira and Kaspersky)
- Zero-hour anti-malware detection and 99.9% spam detection with dual engines
- Deep Content Inspection Engine detecting and analyzing the content of incoming and outgoing emails down to 50 levels
- Message and Structural Sanitization by rewriting URLs before they cause harm and active code (macros, scripts and Active/X) is removed from Microsoft Office, Open Office and PDF files
Clearswift Secure Web Gateway (SWG) gives organizations the ability to enforce consistent internet security through flexible and granular policy management across web traffic, web-based applications, and cloud collaboration platforms. It enables complete granular control over the information that is accessed or shared online, whether it’s limiting or monitoring recreational browsing or preventing the inappropriate leak of critical information.
Key features:
- Multi-layer anti-virus protection (Sophos, Avira and Kaspersky)
- Sophisticated deep content inspection engine that can recognize the difference between an innocent Tweet and a potentially damaging one.
- Clearswift URL database contains 84 categories and is updated daily. It covers millions of sites, and represents billions of web pages.
- Predefined regular expressions for PII Personally Identifiable Information) and PCI (Payment Card Industry)
Secure Managed File Transfer (MFT)
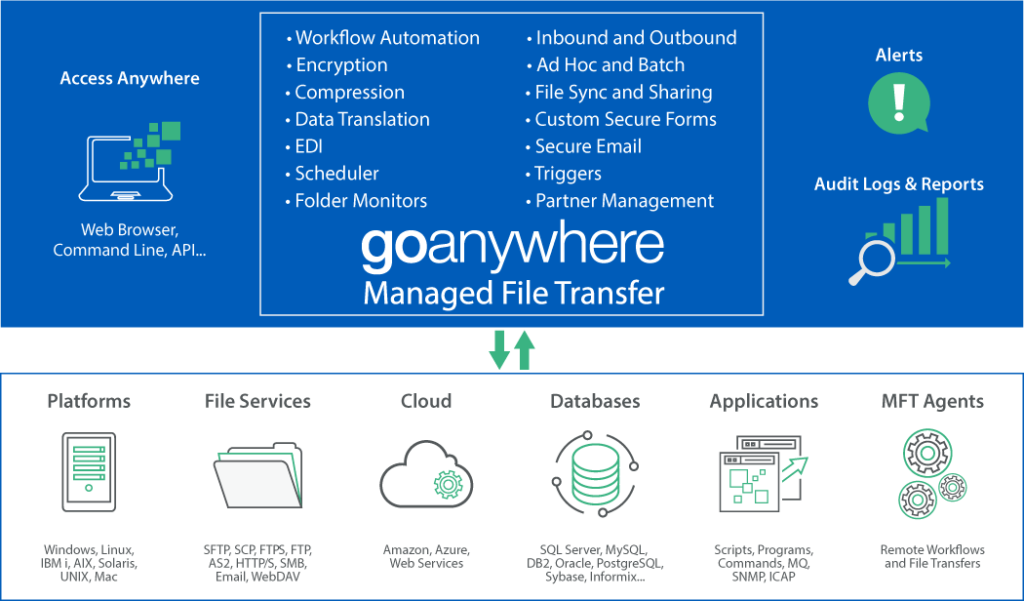
GoAnywhere
With GoAnywhere, IT and cybersecurity professionals can rest easy knowing sensitive files are secure in transit and at rest. GoAnywhere automates and encrypts data between an organization and its trading partners, protecting it from unnecessary vulnerabilities while improving overall file transfer quality and reducing costs.
Key features:
- With MFT workflow automation eliminates the need to use multiple products and scripts to handle your business processes.
- GoAnywhere’s secure collaboration features make connecting with your trading partners, clients, vendors, contractors, employees, and coworkers much easier and faster, especially when you’re on the go.
- The system streamlines the exchange of data between systems, employees, customers, and trading partners.
- GoAnywhere provides centralized control with extensive security settings, detailed audit trails, and helps process information from files into XML, EDI, CSV, and JSON databases.
Secure File Sharing
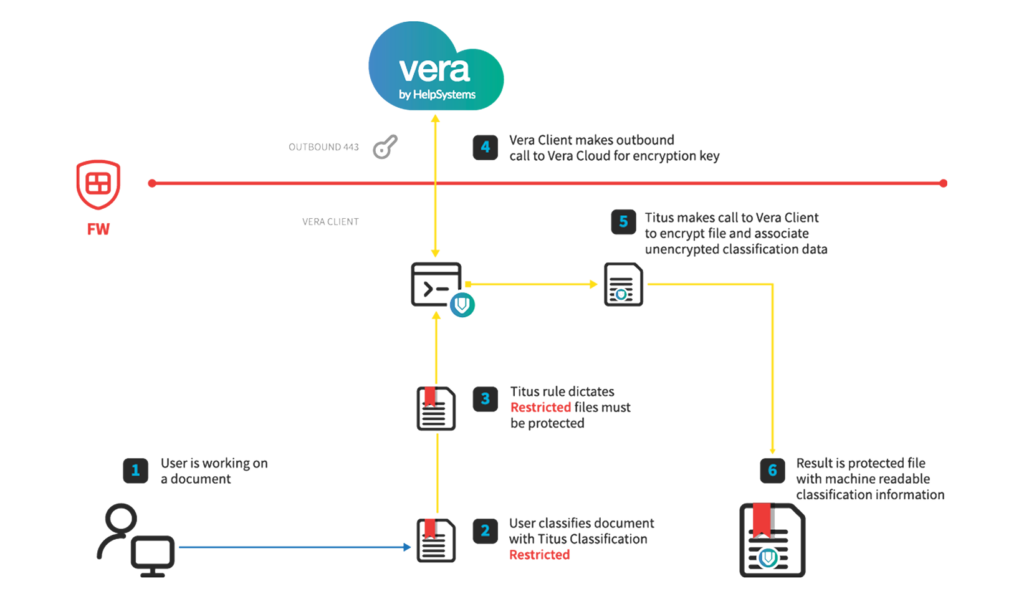
Vera
Secure Sensitive Data Everywhere it Goes
Fortra’s Vera is the security platform chosen by the Fortune 500 to secure, track, and control sensitive information that needs to be shared externally. With a keen focus on the user experience for employees and security pros alike, Fortra’s Vera can protect any kind of information, no matter how it’s stored or shared, anywhere it travels – without affecting how work gets done.
With robust policy enforcement, strong encryption, and strict access controls, Fortra’s data-centric security solution enables teams to collaborate freely while ensuring the highest levels of security, visibility, and control.
Key features:
- SECURE: Automatically secure your sensitive data when it’s shared internally and externally.
- TRACK: Track every time data is accessed throughout it’s lifecycle.
- AUDIT: Mitigate compliance risk with full audit trail.
- REVOKE: Revoke access to sensitive data and files shared with departing employees and 3rd party providers.
Vulnerability Management
Digital Defense
The highest performing vulnerability management software; Protect networks and applications with ease and accuracy.
Vulnerability management is an ongoing process. In addition to regular updates, as an organization evolves, new users, applications, and other changes can create new vulnerabilities that threat actors can exploit. With new vulnerabilities frequently being discovered, following the following steps can be the difference between staying protected and suffering a devastating breach. Digital Defense is the best-in-class vulnerability management and threat assessment platform: cloud-native, built for ease of use, committed to the highest level of performance and accuracy.
Key features:
- High performance and high returns for MSPs
- Rapid monetization and ROI
- Comprehensive support
- Low initial costs
- User-friendly operation
Key Differentiators:
TOTAL SAAS PLATFORM. Powerful and flexible cloud-native vulnerability management and threat assessment platform.
SOFTWARE AND SERVICE. Vulnerability management and penetration testing together.
DEDICATED SUPPORT EXPERTS. Client advocates are dedicated to supporting, training, and helping configure your account.
Penetration Testing
Core Impact
Proactive cyber threat prevention. Simplified identity & access management. Intelligent security.
Core Impact is designed to enable security teams to conduct advanced penetration tests with ease. With guided automation and certified exploits, the powerful penetration testing software enables you to safely test your environment using the same techniques as today’s adversaries. Core Impact’s Rapid Penetration Tests (RPTs) are accessible automations designed to automate common and repetitive tasks.
Core Security delivers market-leading, threat-aware, vulnerability, identity and access management solutions that provide the actionable intelligence and context needed to manage security risks across the enterprise. Uncover the many ways in which your organization can benefit from our analytics-based approach to security.
Key features:
- Automate the routine testing, including proving PCI compliance, to maximize your resources, reserving third-party testing for most robust and complex requests.
- Validate vulnerabilities identified through more than 20 popular scanners, helping to prioritize remediation
- Measure Security Awareness by simulating a phishing campaign using Core Impact’s dynamic tools to find out who is vulnerable to social engineering attacks.
- Validate Remediation Effectiveness by re-testing exploited systems after a penetration test to verify that remediation measures or compensating controls are effective and still working.
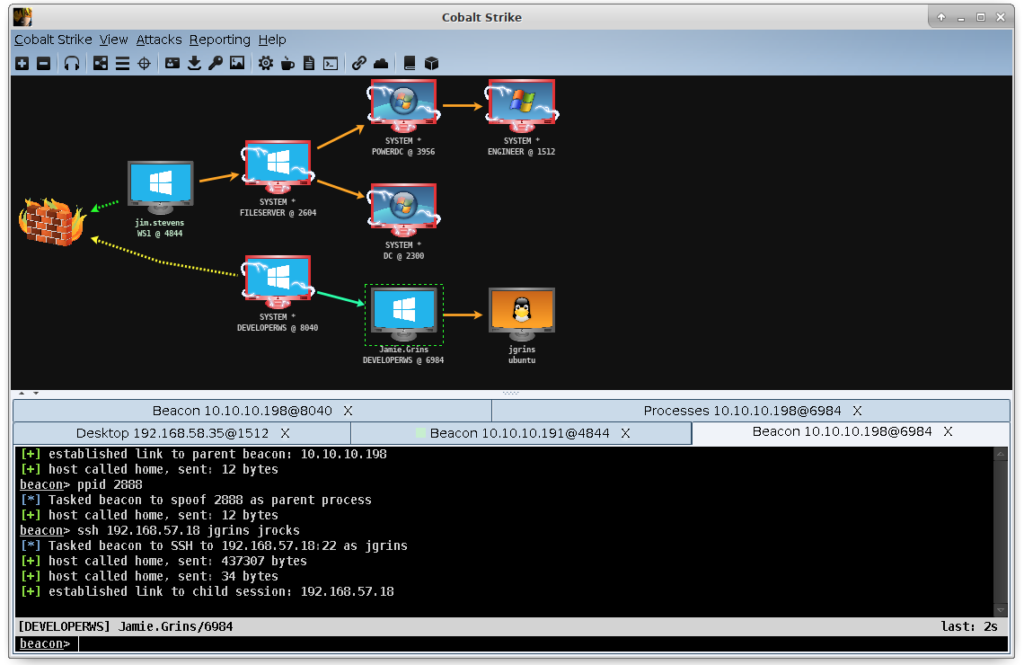
Cobalt Strike
Threat Emulation Software for Adversary Simulations and Red Team Operations
Cobalt Strike gives you a post-exploitation agent and covert channels to emulate a quiet long-term embedded actor in your customer’s network. Malleable C2 lets you change your network indicators to look like different malware each time. These tools complement Cobalt Strike’s solid social engineering process, its robust collaboration capability, and unique reports designed to aid blue team training.
Cobalt Strike is a threat emulation tool, ideal for mimicking an advanced, stealthy threat actor that’s been embedded in an IT environment long-term. Cobalt Strike’s post-exploitation agents and collaboration capabilities ensure effective Adversary Simulations and Red Team operations. Challenge Blue Teams and measure incident response with malleable C2, which allow network indicators to imitate different malware and social engineering processes to strengthen security operations for measuring your security program and incident response capabilities.
Key features:
- Cobalt Strike’s system profiler discovers which client-side applications your target uses, with version information
- Validate vulnerabilities identified through more than 20 popular scanners, helping to prioritize remediation
- Measure Security Awareness by simulating a phishing campaign using Core Impact’s dynamic tools to find out who is vulnerable to social engineering attacks.
- Validate Remediation Effectiveness by re-testing exploited systems after a penetration test to verify that remediation measures or compensating controls are effective and still working.
IBM i Software Solutions
Fortra is your headquarters for leading software, unparalleled IBM i expertise, and IT insights.
Secure. Automate. Inform.
Fortra aligns IT and business goals to help IBM i organizations build a competitive edge. Our software secures IT environments, monitors and automates processes, and provides easy access to the information people need. More than 15,000 organizations in 100+ countries rely on Fortra to make IT lives easier and keep business running smoothly.
We know that modern IT teams need modern IBM i tools. Fortra Insite is your IT operations center. It elevates IBM i visibility into a single pane of glass where key metrics and data insights come together, helping you manage your IBM i estate. With Insite’s unified web interface, it’s easy to update to the latest product versions, create operational dashboards, and manage work from any device.
Underpinning Fortra Insite is powerful, trusted software engineered to solve IT concerns on IBM i. From cybersecurity to systems management to business intelligence, Fortra has you covered.
Unparalleled IBM i and AS/400 Expertise
Fortra is home to the world’s top IBM i experts. From cybersecurity to operations to analytics, our team understands the full potential of this powerful operating system. It shows in our tools, developed and designed with your needs in mind. It shows in our world-class, friendly technical support. And it shows in our highly respected IBM i advocates. We put our knowledge to work for you. We listen to the IBM i community and we know time, resources, and expertise are in short supply. That’s why we can help configure and implement your solutions, so there’s no waiting on your side. If you have IT staff who are new to IBM i, our solutions shorten the learning curve. Our global team of IBM i experts share their knowledge online through webinars and at events around the world. Whether you’re in Argentina or Italy, Sweden or Singapore, you won’t find a bigger advocate for IBM i than Fortra.Explore Our IBM i Software Solutions
Robot
IBM i automation
The Robot product line provides automation solutions for all IBM i environments. Robot offers native IBM i solutions for all critical areas of system management, including job scheduling and batch process management, data replication and high availability, performance and application monitoring, and more.
Powertech
IBM i security
Powertech is the leading source of automated security and compliance solutions for the IBM i as well as AIX and Linux. Our solutions are designed to help you simplify cybersecurity, so you can easily meet auditor demands and harden your system to protect your organization’s most valuable asset: your business-critical data.
Sequel
IBM i business intelligence
Sequel delivers business intelligence solutions for Power Systems™ running on IBM i. With powerful query and reporting capabilities, Sequel makes it easy to access, analyze, and distribute data exactly how you want it.
Valued IBM i and AS/400 Insights
Smart. Trusted. Dynamic.
IBM i is the best-kept secret in IT. This OS is so important to organizations around the world, but finding out how IBM i is used in modern data centers isn’t always easy. Fortra is plugged into the IBM i community at all levels. Our relationships with IBM, technology partners, and our own diverse customer base help us understand what users need—and we deliver.
Through first-of-its-kind research like the annual IBM i Marketplace Survey and the State of IBM i Security Study, IBM i users are better able to see how their peers are using the platform, leveraging modern technology, and driving business forward.
As a respected thought leader in the IBM i space, our research is often cited by IBM and other IBM i advocates. Our goals are to educate the market, keep the platform vibrant, and contribute to the IBM i community.







