The security concept known as “Privilege Creep” occurs when an individual accumulates access rights over time, retaining entry to systems and data beyond the completion of a specific task or the need for such access. This gradual accumulation of unnecessary privileges within an organization not only complicates the management of access rights but also magnifies the potential for security breaches, data theft and misuse of information. As privileges amass unchecked, the attack surface widens, offering malicious actors more opportunities to exploit vulnerabilities that could lead to a breach. Addressing this issue requires diligent access management and adherence to the principle of least privilege, ensuring individuals have access only to the resources necessary for their current roles and responsibilities.
Mitigating Privilege Creep is critical to enhancing an organization’s cyber security posture, but it’s historically been difficult to quickly and securely revoke access rights once they have been granted… until now.
Keeper is excited to announce Time-Limited Access and Self-Destructing Records for encrypted, time-bound access and credential sharing in the Keeper platform.
Time-Limited Access
Time-Limited Access enables users to share a record or folder with another Keeper user for a designated period of time. Upon expiration, the recipient will have their access automatically revoked without requiring the sending party to take any action. Time-Limited Access can be applied to thousands of common scenarios from sharing the WiFi password with a visiting guest to admins sharing the login details for a database.
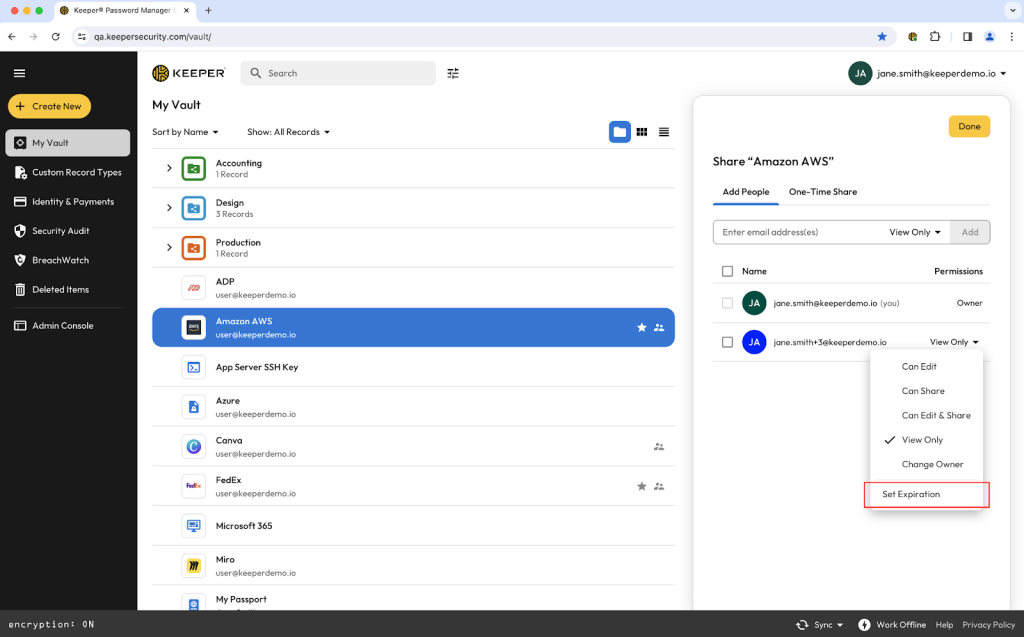
Time-Limited Access solves the long-term struggle many organizations have around elevated access. Users often need to be granted temporary or short-term privileges that go beyond their standard access levels. Organizations can maintain least privilege by only allowing elevated access for the set duration of time and only to perform the tasks required, eliminating the need to create power users with access outside of the scope of their projects.
Combining Time-Limited Access with Keeper Secrets Manager (KSM) provides privileged users with powerful sharing functionality. When paired with KSM’s automatic service account rotation capabilities, users can schedule rotation of the shared credential upon the expiration of access, ensuring the recipient never has standing privilege.
Self-Destructing Records
Self-Destructing Records take this concept one step further by allowing users to create a record and send a one-time share that will delete itself from the sender’s vault after the recipient opens the shared record.
This happens after a designated period of time or once the recipient has viewed the record for five minutes, whichever comes first.
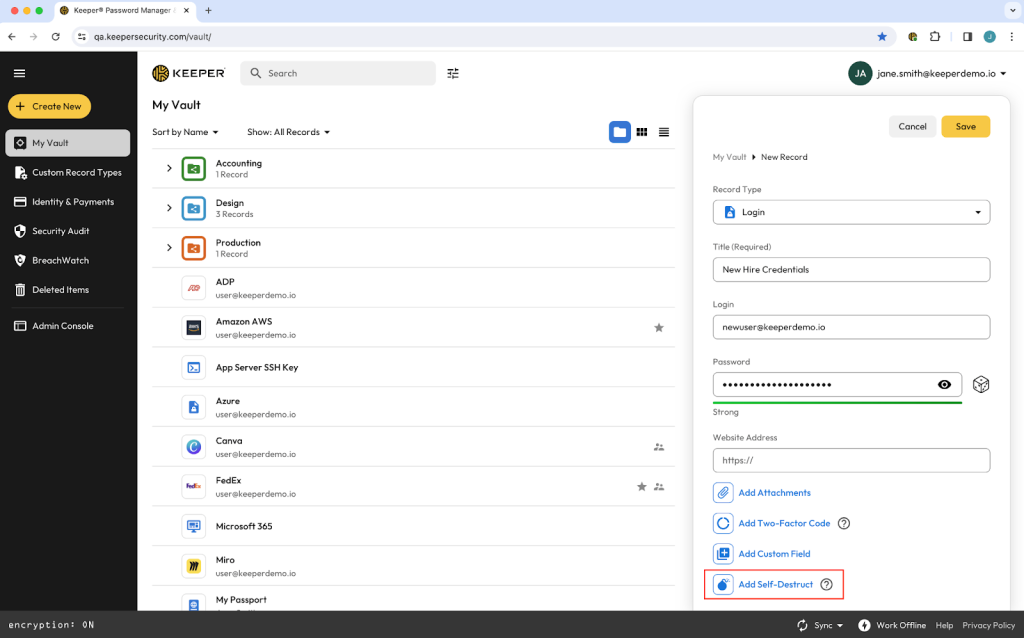
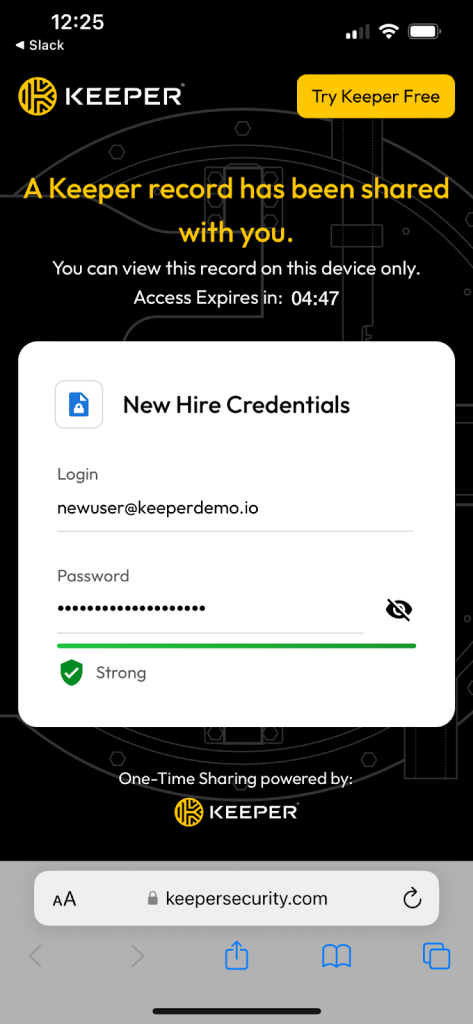
A typical scenario is employee onboarding, when IT needs to share login credentials with a new staff member. IT can share the record containing those credentials and upon receipt, the original record will self-destruct, eliminating the risk associated with long standing access to the employee’s login information.
With Self-Destructing Records, the information can be accessed securely and is automatically deleted, ensuring it doesn’t linger or become accessible beyond its intended purpose. This record’s unique trait of being viewable on only one device further tightens security, preventing unauthorized distribution or viewing on multiple devices.
These access and sharing updates are available for both consumer and business users. Administrators can enable or disable these features in the ‘Creating and Sharing’ section of role settings in the Admin Console for business and enterprise organizations. Administrators with Keeper Advanced Reporting and Alerts Module (ARAM) are also able to receive ARAM events for when a timer is added to a record, and when the timer and share expire.
Easy-to-Use, Encrypted Access for All
Time-Limited Access brings several key benefits to users and administrators:
-
- Revoked access at a time decided by the record owner, eliminating chasing down who has access and removing it at a later time
- Enhances security as traditional short term sharing has been done in insecure ways like writing down passwords or sending them via email and messaging
- Simplified compliance with event recordings and assurance that least privilege access is maintained
Self-Destructing Records enables its own set of benefits including:
-
- Ensuring encryption and security, without filling the sender’s vault with credentials they don’t need to retain
- Assurance that the recipient is the only receiver of the shared credential
Secure and Streamline Credential Sharing with Keeper
Time-Limited Access and Self-Destructing Records are just the latest in Keeper’s ongoing efforts to enhance Privileged Access Management (PAM) capabilities for all users. By limiting the amount of time users have access to records, organizations simplify compliance and end-users can rest easy knowing their records are shared securely.
Using Time-Limited Access and Self-Destructing Records is very simple. To learn how, please refer to the product release notes.
To see Time-Limited Access and Self-Destructing Records in action, schedule a demo today.
Source: Keeper





