Sophos XDR: Expanding our defense against active adversaries
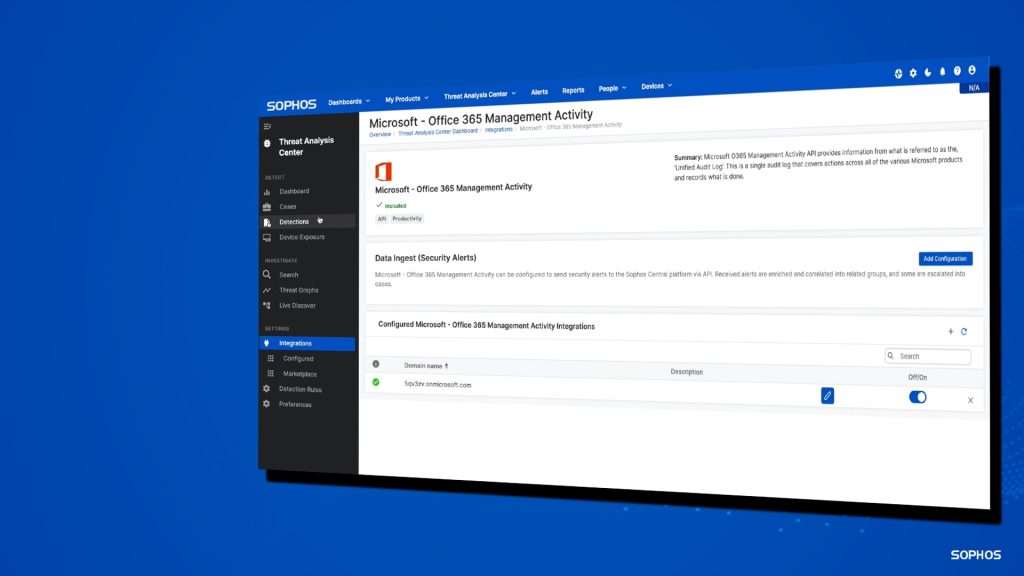
Active adversaries are highly skilled cybercriminals. They use hands-on-keyboard and AI-assisted methods to circumvent preventative security controls and execute advanced multi-stage attacks. Organizations need adaptive security controls designed to detect, investigate, and respond to the approaches commonly used by these sophisticated threat actors. Effective response to advanced threats requires a toolset that enables security operators […]
Sophos XDR: Expanding our defense against active adversaries Read More »