News
There’s definitely an update coming next Tuesday, 18 June 2013, and you might as well get ready for it now if you haven’t already. The details of what will be fixed aren’t a matter of public record yet, so we can’t spell them out for you in detail. Nevertheless, Oracle has published a very brief pre-announcement to remind us of the importance of this month’s fixes. The good news is that lots of security vulnerabilities have been repaired – 40 in total, of which all but three are RCEs, or remote code execution holes.
That’s where untrusted content sent over the network might be able to trick Java into performing operations that really ought to be limited to already-installed, trusted code. In short, an RCE means that you could get infected by malware simply by looking around online, without explicitly downloading, authorising or even noticing the malware being installed.

There are two handy ways to reduce this RCE risk:
· Apply Oracle’s patches as soon as practicable. You can turn on fully-automatic updating if you like.
· Turn off Java in your browser, so that web-based Java applets can’t run at all.
Click here to see the original article.
The research evaluated thousands of website URLs of organizations that utilized the GlobalSign SSL Configuration Checker; many of these organizations were looking to assess the strength and quality of their SSL configurations. Statistics revealed that in the first quarter of 2013 over 6,000 sites used the tool to evaluate the effectiveness of their SSL, and 269 of those sites used the remediation guidance provided by GlobalSign to improve and, in some cases, strengthen the security of their sites within a matter of minutes.
Upon visiting GlobalSign’s SSL Configuration Checker, powered by Qualys SSL Labs, organizations enter their website addresses and instantly receive a letter grade for their configuration. The grading system has three steps. First, the site’s SSL certificate is examined to confirm that it is trusted and valid. If a server fails this step it is automatically given a zero. Next, the server configuration is tested in three categories:
1) protocol support,
2) key exchange support and
3) cipher support.
Finally, a score between 0 and 100 is assigned to the site. The grading scale is as follows:
• score ≥ 80 A
• 65 ≤ score ≤ 79 B
• 50 ≤ score ≤ 64 C
• 35 ≤ score ≤ 49 D
• 20 ≤ score ≤ 34 E
• score
The research revealed that 50 percent of 269 websites that used the GlobalSign SSL Configuration Checker strengthened the effectiveness of their SSL configuration grades in 30 minutes or less. Fifteen percent improved from a B, C, D or F to an A grade in less than two hours.
Notable statistics for the 269 improved websites:
• 172 organizations improved their grade to an A overall – 63%
• 13 organizations improved their F grade to an A, B, or C – 42%
• 95 organizations improved their B grade to an A – 35%
“The improvement in website security is certainly encouraging for us to see, but this is the absolute tip of a very big, fast-moving and dangerous iceberg,” said Ryan Hurst, chief technology officer of GlobalSign. “Administrators can use the SSL Configuration Checker to greatly improve and remediate the security of poorly configured sites, but it is the awareness of this free and easy tool that we are trying to drive. Both small and large organizations with websites must adopt best practices, but first they have to identify the strengths and weaknesses of their sites’ SSL configuration.”
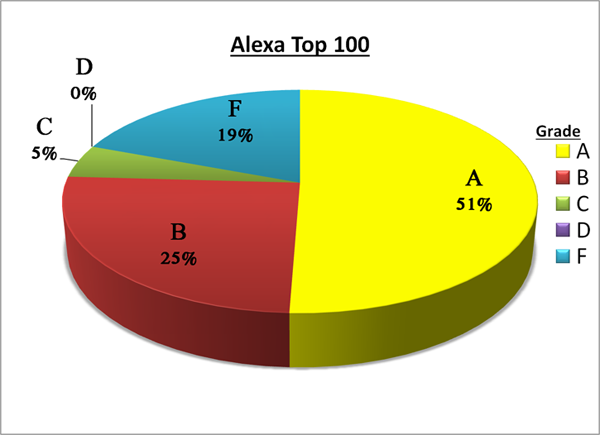
Alexa 100 Sites Evaluated:
In addition to the findings derived from inbound SSL Configuration Checker use, GlobalSign evaluated the SSL effectiveness of the Alexa Top 100 websites. The research revealed the following:
• Over half (51%) of the websites received an A.
• Twenty-five percent received a B and 5 percent scored a C.
These grades are proof that while just over half of the world’s top sites, and the enterprises behind them, are providing effective security, there is ample room for improvement.
Overall SSL Configuration Checker Evaluation results of the Alexa Top 100:
Click here to see the original article.
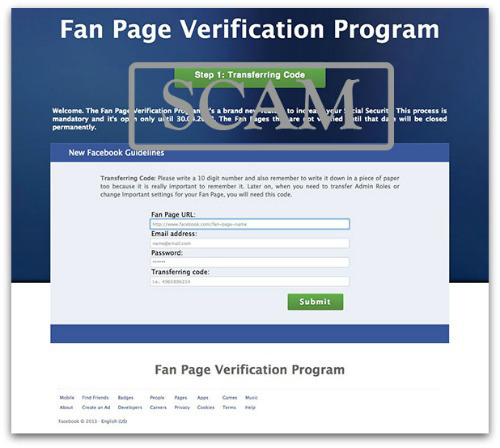
a bogus message supposedly sent from Facebook Security.
According to Hoax-Slayer, the scam claims that Facebook is rolling out a new security feature to protect Page owners.
This supposed new security feature is dubbed the “Fan Page Verification Program”.
It does a nice job of flattering suck-up to entice victims into coughing up their Facebook login details, telling targets that they’ve had ever so many stolen Pages lately, and they simply can’t think of what to do about it except just, well, throw up their hands and Delete them all – yes, Delete those bad, bad Pages, with a capital “D”.
All the stolen Pages, that is, except yours, which, gosh, is so popular with its “High Quality Content”.
The message tells victims that they have to click a link and choose a 10-digit security code to complete the process.
Those who don’t comply will see their Page suspended permanently if the process isn’t completed by May 30, 2013, they go on to say.
Here’s an example of this scammy letter that Hoax Slayer posted on Friday:
Dear Facebook User,
You are receiving this message to notify you about the new security feature from Facebook called “Fan Page Verification Program”.
After many Fan Pages have been stolen lately leaving us no choice but Deleting them forever, we had to come up with an original solution about the Fan Page’s Security.
Luckily, your Fan Page, has a lot of likes and provides High Quality Content, which qualify it for this program.
To complete this process you must choose a 10-digit number (it can be any number) and that number will be assigned as your Security code”. This code will be the new passphrase for changing anything important for your Fan Page, like the Admin roles or other important settings.
Please be aware that this process it’s open only until 30.05.2013 and it’s mandatory to complete it. If you don’t, your Fan Page will be suspended permanently since it is not considered safe for the wide audience.
Please visit the link below to complete the process:
[Malicius Link]
Facebook Security
Anybody who falls for it and clicks on the link will be whisked away to a spot where they’re told to submit Facebook login details and the so-called 10-digit “Transferring Code”.
Click here to see the original article.
Jan

to hack a plane.
That includes potentially gaining information about an aircraft’s onboard computer, changing the intended destination, flashing interior lights, delivering spoofed malicious messages that affect the behavior of the plane, and, just maybe, if pilots don’t manage to turn off autopilot and/or have difficulty with manual flight operation, crashing the plane.
These are theoretical exploits demonstrated by Hugo Teso, a security consultant at n.runs AG in Germany, who gave a talk about his research at the Hack in the Box conference in Amsterdam on Wednesday.
Of course, Teso hasn’t tried any of this out on real planes, given that there aren’t many planes lying around waiting for people/plane/landscape annihilation, which would, at any rate, be illegal and amoral.
Rather, he conducted his research on aircraft hardware and software he acquired from various places.
That includes equipment from vendors offering simulation tools that use actual aircraft code and from eBay, where he found a flight management system (FMS) manufactured by Honeywell and a Teledyne Aircraft Communications Addressing and Reporting System (ACARS) aircraft management unit, according to Network World.
According to Help Net Security’s Zeljka Zorz and Berislav Kucan, Teso’s demonstration shed light on “the sorry state of security of aviation computer systems and communication protocols.”
Teso created these two tools to exploit vulnerabilities in new aircraft management and communication technologies:
An exploit framework named SIMON, and
An Android app named, appropriately enough, PlaneSploit, which delivers attack messages to the airplanes’ FMSes.
The two vulnerable technologies Teso exploited with these tools:
The Automatic Dependent Surveillance-Broadcast (ADS-B) (this surveillance technology, used for tracking aircraft, will be required by the majority of aircraft operating in US airspace by Jan. 1, 2020), and
The Aircraft Communications Addressing and Reporting System (ACARS), a protocol for exchange of short, relatively simple messages between aircraft and ground stations via radio or satellite that also automatically delivers information about each flight phase to air traffic controllers.
According to Help Net Security, Teso abused these “massively insecure” technologies, using the ADS-B to select targets.
He used ACARS to siphon data about the onboard computer and to exploit its weaknesses by delivering spoofed messages that tweak the plane’s behavior.
Using the Flightradar24 flight tracker – a publicly available tool that shows air traffic in real time – Teso’s PlaneSploit Android app allows the user to tap on any plane found within range – range that would be limited, outside of a virtual testing environment, to antenna use, among other things.

The application has four functions: discovery, information gathering, exploitation and post exploitation.
According to Help Net Security, these are some of the functions Teso showed to the conference audience:
Please go here: Allows user to change the targeted plane’s course by tapping locations on the map.
Define area: Set detailed filters related to the airplane, such as activating something when a plane is in the area of X kilometers or when it starts flying on a predefined altitude.
Visit ground: Crash.
Kiss off: Remove plane from the system.
Be puckish: Trigger flashing lights and buzzing alarms to alert the pilots that something is seriously wrong.
Teso has, thankfully, responsibly, refrained from disclosing details about the attack tools, given that the vulnerabilities have yet to be fixed.
In fact, he told his listeners that he’s been pleasantly surprised by the receptivity he’s received by the industry, with companies vowing to aid his research.
Given Teso’s belief in responsible disclosure, the industry can take steps to patch the security holes before someone with more malicious intent has an opportunity to exploit them.
From the sound of things, this researcher has garnered plenty of media attention but still values aircraft and passenger safety well over fame and glory.
Original article can be found here
information security to the status of the most crucial factor that should be taken into account in the adoption of new technologies in the IT environment. The conference aims to present IT professionals with the landscape of new threats and how those threats will be addressed effectively through the implementation of specific policies and the use of modern technology.
Click here to register for the Infocom Security 2013 event
Click here to navigate to Infocom Security 2013 Official Website
Jan
UTM Buyers Guide gives you everything you need to find the best protection that’s also the easiest to manage.
This guide will allow you to:
- Understand what a modern UTM can do for you
- Compare product features, and know what you need to keep your network secure.
- Ask the right questions of vendors as you consider your options
Click here to download the Buyers Guide.
Στο διάγραμμα που δημοσιοποιήθηκε από ανεξάρτητη εταιρεία ερευνών, και περιλαμβάνει τους Δείκτες Υπόσχεσης και Εκπλήρωσης, μπορείτε να δείτε και να συγκρίνετε την αποτελεσματικότητα ορισμένων από τις σπουδαιότερες εταιρείες της βιομηχανίας των υπολογιστών στο marketing αλλά και στην εκτέλεση.
Ένας κατασκευαστής, που βρίσκεται στο πάνω δεξί τεταρτημόριο του διαγράμματος, έχει βαθμολογηθεί με υψηλή βαθμολογία τόσο στο τομέα της υπόσχεσης όσο και στο τομέα της εκπλήρωσης αυτής της υπόσχεσης. Με βάση τα ίδια κριτήρια, μία εταιρεία στο κάτω αριστερό τεταρτημόριο, δεν τα καταφέρνει ούτε στο επίπεδο της υπόσχεσης, ούτε στο επίπεδο εκτέλεσης.
O “Δείκτης Εταιρικής Υπόσχεσης” (Vendor Promise Index) σχεδιάστηκε κατά τέτοιο τρόπο ώστε να μετράει την αποτελεσματικότητα του marketing. Χρησιμοποιεί τέσσερα από τα δεκατέσσερα σημεία αξιολόγησης πελατών (Θέση ανταγωνιστικότητας, Τεχνολογική Καινοτομία, το Στρατηγικό Όραμα του management της εταιρείας καθώς και η Μάρκα/ Φήμη) που σχετίζονται με ιδέες και concepts που μεταφέρονται σε πιθανούς πελάτες σε παγκόσμιο επίπεδο πριν το πραγματικό προϊόν ή κάποια υπηρεσία παραδοθεί προς χρήση.
Ο “Δείκτης Εταιρικής Ικανοποίησης” (Vendor Fulfillment Index) σχεδιάστηκε ως μέτρο για την εκτελεστική αποτελεσματικότητα. Χρησιμοποιούνται και σε αυτή τη περίπτωση τέσσερα από τα δεκατέσσερα κριτήρια βαθμολόγησης πελατών (Απόδοση/ Τιμή, Ποιότητα προϊόντος, Παράδοση σύμφωνα με την Υπόσχεση και Ποιότητα τεχνικής υποστήριξης) τα οποία σχετίζονται με το φυσικό προϊόν και την υπηρεσία που έχει παραδοθεί και την εμπειρία που είχε ο πελάτης από τη χρήση του συγκεκριμένου προϊόντος ή της υπηρεσίας.
Το μέγεθος του κύκλου που βλέπετε στο διάγραμμα επίσης δείχνει τη σχετικότητα μεταξύ των βαθμολογιών που έλαβε κάποια εταιρεία. Οι γραμμές που τέμνονται δείχνουν το μέσο όρο βαθμολογίας που έλαβε κάθε εταιρεία, συμπεριλαμβανομένων και εταιρειών που δεν βρίσκονται στο διάγραμμα. Όπως μπορείτε να δείτε, η Sophos έχει αποσπάσει εξαιρετική βαθμολογία, τόσο στο τομέα του marketing, όσο και στο τομέα του να κάνει πραγματικότητα όλα όσα υπόσχεται για τους πελάτες της.
Jan
But what are the implications of biometric technology as far as enterprise security is concerned? Ryan Hurst, CTO of enterprise SaaS Certificate Authority GlobalSign, has told Softpedia that biometric technology could turn out to be highly beneficial to organizations looking to protect their data, but it depends a great deal on how it’s implemented.
“The recent confirmation of the integration of biometrics in the new iPhone has many asking what the implications are for enterprises. It is too early to tell for sure as the answer will depend on how they have implemented this feature,” said Hurst told us in an emailed statement.
“That said, as mentioned during the Apple keynote, only about half of smartphone users apply a passcode today making mobile devices carrying sensitive corporate data a huge vulnerability for enterprises. If the biometric technology used on the device is applied correctly this could mean more secure enterprise data,” he added.
“More importantly this will force many enterprises to take another look at their own authentication strategy and ask if biometrics is a viable form of authentication for them in comparison to other stronger forms, such as one time passwords and smart cards, and weighing the security benefits and risks of each.”
Hurst highlights the fact that the use of biometric technology could be beneficial in case mobile devices containing enterprise data are stolen or lost. “The first rule of security is if the attacker has physical access to your device then the device is no longer yours. However, the use of biometrics has the potential to make it more difficult for the attacker which can significantly reduce the impact of lost or stolen phones containing enterprise data,” he explained.
You can read the original article, here.
Jan
Steve Gollschewski, Deputy Commissioner, Strategy, Policy and Performance presented the award to Rob Forsyth, Director Sophos Asia Pacific, in recognition the team’s ongoing partnership with the Queensland Police Service, working closely with the community to provide education material for community groups, as well as hosting the Sophos Signature events to explore current and emerging issues, and raising greater awareness in the government and business communities regarding fraud and cybercrime.
According to Detective Superintendent Brian Hay, Head of Fraud Division, Queensland Police Service, the concept of working with the private sector in regard to fraud and cybercrime started 12 years’ ago, and Sophos has supported what is now known as Project Synergy right from the start.
“The Fraud and Cybercrime Partnership Award recognises the Queensland Police Service’s need to partner with industry entities such as Sophos, to better secure and protect the Australian community,” said Detective Superintendent Brian Hay.
“Sophos has shown the courage and character to step forward to participate with the Queensland Police Service since Project Synergy’s inception, and we look forward to continuing our ongoing relationship, to further build and enhance innovative strategies to protect Australia and indeed global communities.”
Sophos has worked closely on many key security projects and initiatives including the Over the Horizon Forum for the Department of Broadband, Communications and the Digital Economy, an event that takes place during National Cybersecurity Awareness Week, where Sophos is an active supporter and committee member.
Sophos also works directly with leading industry associations including the Internet Industry Association (IIA) and Australian Computer Society. Sophos is a member of the Australian Government’s National Standing Committee on Cloud Computing advising on security issues and an Industry Code of Best Practice. The company is also actively supporting the Internet Industry Association’s inaugural National Online Security Council forum being held next month.
Forsyth says the award is an indication of the ongoing work the company invests within the business community to raise greater awareness of security issues.
“It is an absolute honour for Sophos to be recognised by the Queensland Police Service, with this inaugural Partnership Award, and we thank Detective Superintendent Brian Hay and Queensland Police in recognising Sophos’s continued work and education in the community,” Forsyth said.
Sophos will continue its work in driving awareness around security issues, particularly on a local level, rallying the community and business to work together in ensuring Australians understand online safety, fraud and cybercrime.
You can read the original article, here.
The authentication system, based on a new material for the home button and a metal sensor ring around it, has been the subject of numerous rumours and leaked photos and specs already. Speculation about Apple’s interest in fingerprints goes back at least as far as 2009, resurfaces each time a new version of the iPhone is launched, and has grown steadily ever since Apple’s pricey acquisiton of fingerprint tech firm AuthenTec last summer. Today’s confirmation at the iPhone 5s/5c launch ceremony makes it all official at last. According to Apple’s promotional material, the sensor:
“uses advanced capacative touch to take, in essence, a high-resolution image of your fingerprint from the sub-epidermal layers of your skin. It then intelligently analyses this information with a remarkable degree of detail and precision“.
As well as unlocking the phone, the sensor will be able to approve purchases at the Apple store. Fingerprint authentication has been a common sight in laptops for some time, with major vendors including Dell, Lenovo and Toshiba pushing their own built-in variations, usually available as an option alongside more traditional login methods. There are also a range of other implementations available, including many smartphone apps and external readers supported by the Windows Biometric Framework and some leading password managers.

Fingerprints thus probably rank a little above facial recognition as the most widely-deployed biometric authentication technique at the moment. In the past, however, they have proven rather unreliable, plagued with security worries, although suspected flaws are not always proven. Nevertheless, many fingerprint scanners seem to be open to spoofing. Fingerprints are not secret: we leave copies of them wherever we go, even if we’re trying hard not to, as cop show afficionados will be well aware. Once someone devious has got hold of a copy, purely visual sensors can be fooled by photographs, while more sophisticated techniques which measure textures, temperatures and even pulses are still open to cheating using flesh-like materials, or even gelatin snacks. Just how hard it will be to defeat Apple’s recognition system remains to be seen, but as crypto guru Bruce Schneier has pointed out, there’s a big danger in using fingerprints to access online services: the temptation to store the fingerprint info in a central database. Unlike passwords, of course, if your fingerprint data is lifted from a hacked database, you can’t simply change it, short of getting mediaeval on your hands with acid, sandpaper or some other hardened-gangster technique.

So, as expected, Apple has opted to keep all information local to the iPhone – indeed, it is apparently kept in a “secure enclave” on the new A7 chip and can only be accessed by the print sensor itself. Expect this storage area and the connections to it to become the subject of frenzied investigations by hackers of all persuasions. Of course, Apple is not alone in looking into fingerprints, with arch-rivals Samsung also rumoured to be making moves in that direction. (Samsung was a major customer of AuthenTec before it was acquired.) In the long term, how similar their approaches are may be a significant issue for all of us, whatever our smartphone affiliation and whether or not we worry much about privacy, and not just thanks to the inevitable legal rumpus. There are two basic approaches to security: either the way things work is kept proprietary and secret, as far as possible, or it’s made open for general consumption, and more importantly for verification. A cross-vertical group, the FIDO Alliance, was set up earlier this year to develop open specifications for biometric authentication standards, with members including Google, PayPal, hardware makers like Lenovo and LG, and a raft of biometrics and authentication specialists. Beleaguered phonemaker BlackBerry is the latest big-name inductee. The alliance’s aim, to create a universal approach to implementing biometrics in combination with existing passwords and two-factor dongles, is a noble goal. Sadly, given Apple’s history of playing well with others, it’s pretty likely that, as with their connector cables and DRM systems, their fingerprint setup will remain aloof from any attempts to build a truly universal consensus.
Even if a two-culture system prevails, widespread deployment in mass-market handhelds may well be a gamechanger for the adoption of biometric authentication. Touch ID and its inevitable followers could be a major part of all our futures.
You can read the original article, here.
Jan
In addition to delivering iOS 7 support, Sophos announced an update for customers to manage the new business-focused features of Apple’s latest version from the easy-to-use Sophos web-based console, deployed either on-premise or as Software as a Service (SaaS).
According to Gartner, Apple iOS 7 includes more enterprise enhancements than any release since iOS 4.0 introduced mobile device management APIs. Version 3.6 of Sophos Mobile Control enables enterprises of all sizes to protect corporate data, with many new enhancements, including:
- Separation of company and personal data
- Per app VPN
- A new volume purchasing program (VPP)
- Remote configuration of apps
“Sophos Mobile Control allows us to easily manage our existing devices while simultaneously adding new devices safely into our organization,” said Jeri Sample, IT Manager, Meadville Medical Center, an outstanding community medical center in Meadville, Pennsylvania. “It is important for us to keep patient data secure. With accelerated deployment, ease of management, and complete visibility, SMC makes Sophos the right choice on behalf of our staff and our patients.”
“Mobile devices in the workplace are the rule, not the exception,” said John Shaw, Vice President for end user security products at Sophos. “Sophos Mobile Control provides simple to deploy mobile device management and security that will keep employees happy and productive, minimize the workload for IT, and give managers confidence that the company’s data is protected. We think iOS 7 is a huge step forward in enabling personal devices to be used securely at work, and are delighted to be extending the benefits to our partners and customers.”
To learn more about Sophos Mobile Control, please visit http://www.sophos.com/mobile.
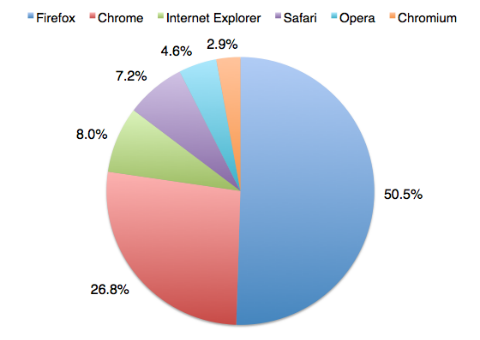
Our poll offered readers the chance to vote for one of the six most popular web browsers – Chrome, Firefox, Internet Explorer, Opera, Safari and Chromium – and asked which you trusted the most. Mozilla’s Firefox, the linear descendant of both Netscape Navigator and the original ‘graphical web browser’ the NCSA Mosaic, was a runaway winner. Firefox accrued almost double the number of votes of its nearest rival, Google Chrome, and more than six times the votes awarded to perennial rival and fellow ‘browser wars’ veteran Internet Explorer.
The results are even more emphatic when you consider how many people actually use each browser. Below is a table that compares the number of votes each browser received in the poll against the number of unique article pageviews from each of those browsers over the same period.
Results are ranked in order of conversion rate – the rate at which page views by a given browser correlate with votes for that browser (Chrome and Chromium identify themselves in the same way and we can’t separate their unique page views so their results are combined in this table).

Top of the table is Opera which was the only browser that scored more votes for trustworthiness than it had users, although it did so with much smaller totals than its competitors. You could probably sum up the entire history of the Opera browser with the phrase “small but loyal following” and despite the regard in which its users hold it Opera seems destined to remain the perennial bridesmaid of the browser world. The poor showing of Internet Explorer is notable but perhaps not surprising given that it is often imposed on users as a matter of corporate policy. What stands out at me is the difference between the Mozilla and Google products. Both browsers are well established and well known open source projects, they both run on Windows, Mac and Linux and unlike Explorer or Safari neither come bundled with an operating system.

Perhaps Chrome users are more cynical or more realistic about where they place their trust. Or perhaps people who choose Chrome are also people who don’t vote in internet polls. We don’t know but I suspect, as the comments on our poll seem to suggest, that the reason for Chrome’s poor showing is that Google’s claim to Do No Evil is simply no longer convincing. The untrustworthiness of Google is a consistent theme across the most highly rated comments on the poll:
“frankly I trust Google the least, as they have too many data points for comparison.
I don’t trust Google as far as I could throw ’em. As a company, it’s entirely uninterested in my security or privacy, especially if it can make money by selling my personal information.
Trusting any software completely is a bit foolish, but anyone who actively trusts Chrome is a good subject for psychological study.”
You get the idea. Of course this is only an online poll and and not a scientific experiment so my conclusions should be taken with a liberal pinch of salt.
You can read the original article, here.
Jan
Recent headlines and mounting evidence suggest that cyberattacks on Critical Infrastructure (CI) systems are increasing as cybercriminals have identified electric utility grids as prime targets for disruption activities. As a result, CI cybersecurity has become a prime concern for governments and citizens alike. The paper focuses on the history of the electric industry, how cybersecurity standards have emerged, what those standards are and how they can be used by other CI sectors to strengthen security and reduce the risk of harmful cyberattacks.
“PKI is a robust technology that provides a secure, scalable and cost-effective method to securely authenticate digital identities on large and complex networks such as those that manage business processes for the wholesale electric market. However, due to the many implementation details involved, if the technology is not executed correctly it can also produce a vulnerable system,” said Kee. “NAESB members have worked together to produce a standard for the Wholesale Energy Sector that is based on best practices, proven management techniques and advanced digital certificate technologies.“
In the wake of increasing attacks, U.S. CIs are stepping up efforts to amplify their cybersecurity and strengthen their defenses. In fact, the white paper notes that in President Obama’s recent Executive Order, the National Institute of Standards and Technology (NIST) was directed to lead the effort to develop a cybersecurity framework that would consist of adopting industry best-practices wherever possible. “As part of NIST’s draft cybersecurity framework of best practices, guidelines and standards, the NAESB standard on PKI stands a good chance of being applied to other CI sectors,” says Lila Kee.
All CIs are managed, controlled and accessible via Internet-connected systems, making them vulnerable to cyberattacks. This white paper details how ISOs in the energy sector have recognized the value of cybersecurity frameworks, have adopted standards developed by NAESB and have demonstrated that standards can be developed using shared expertise from both the public and private sectors – setting a framework for all CI sectors.
“It has become increasingly clear that cybercriminals are targeting the critical infrastructure in an attempt to disrupt our way of life. For this reason, NAESB made it a priority to establish PKI standards in order to fortify our cybersecurity framework,” said Rae McQuade, President of NAESB. “In establishing these standards we hope to provide a strong cybersecurity strategy so that we may best protect the business practices related to the electricity market that are a critical part of the everyday lives of our citizens.”
To read GlobalSign’s white paper visit the page here.
Jan
We began producing antivirus and encryption products nearly 30 years ago. Today our products help secure the networks used by 100 million people in 150 countries and 100,000 businesses. Our products allow you to secure every end point of your network, from laptops to virtual desktops and servers, to web and email traffic and mobile devices.
All devices —managed easily through the cloud. What’s more, securing these devices is made possible through products that fit your precise needs. We ensure your network’s security by providing the one thing no one else can: Simplicity – arching the following three important IT security sections:
Network Protection
Who Needs This
Sophos UTM helps you consolidate your security without compromising its effectiveness. It’s security made simple, protecting your users everywhere while making security easier to deploy and manage.
What’s Protected
- All computers, mobile devices and servers on a network
- Branch offices and remote users connected with VPN
- Email and web servers and even Wi-Fi users
Products
- Unified Threat Management – The ultimate network security package.
- Secure VPN – Turn any location into a secure location.
- Secure Web Gateway – Complete web protection everywhere.
- Web Application Firewall – Uncommon protection from common threats.
- Next-Generation Firewall – This is where network threats go to die.
- Secure Wi-Fi – Super secure, super Wi-Fi.
- Secure Email Gateway – Simple protection for a complex problem.
Enduser Protection
Who Needs This
Our endpoint protection will keep data in and malware out—all within your antivirus budget. And we protect your mobile devices and servers.
What’s Protected
- All computers, mobile devices, and servers on a network.
- Encryption for devices and file shares.
- Mobile devices and laptops on the go.
Products
- Enduser Protection Suites – The all-in-one security suite.
- Mobile Control – Countless devices, one solution.
- Endpoint Antivirus – Essential protection for laptops & desktops.
- SafeGuard Encryption – Encryption everywhere.
Server Protection
Who Needs This
Our antivirus protection delivers more effective, faster protection across your network of physical or virtual servers.
What’s Protected
- Broad platform support for Windows, UNIX and Linux servers.
- Small memory footprint won’t slow you down. Our antivirus agent has low performance impact, and is optimized for virtualization.
- HIPS protection for Windows is easy to deploy and manage.
Products
- Server Security – Pro-server. Anti-virus.
- Network Storage Antivirus – High-tech security for high-tech storage.
- PureMessage – Good news for you. Bad news for spam.
Where are business most likely to be vulnerable and how this can be fixed with Sophos products?
SMB Businesses have a limit of both personnel and financial resources. Security therefore must be simple to setup, configure and administer. Many SMB customers don’t have a security team. So we offer MSP and other methods of delivering simple security to customers at a reasonable cost.
What is the philosophy and the goals to which you aspire?
Sophos believes in keeping things and hence security simple. This starts with our UTM and Endpoint Security Products, making the administration and configuration simple. When security solutions are easy to use, our customers have a higher level of security. This is the vision that drives us as a company: Security made simple. We also don’t believe in scaring our customers, they are smart enough to understand the need for security.
Sophos delivers the vision through dedicated employees that have experience in the global security space and a dedicated channel that is continuously updated via technical and sales staff interested in its success. Our dedicated staff, channel, partners and customers are the key to our success. We are all ultimately on the same team!
How do you know that you have spent enough to make your business secure?
Good and tough question, there is no definitive answer here besides implementing as much as we can in a set budget. The more interesting question is, how do we create the security budget. This is where ISO27001/2 come in, creating a risk process that also looks at assessing what data and informational assets we have.
When a company knows what its assets are, then we can begin to assess the risk, vulnerability, exploits and also damages that could result. After this process, we then start to understand how and with which budget we can mitigate those risks.
What we can expect from Sophos cloud in the near future?
We are driven to adding, new and existing functionality into the Sophos cloud, adding features slowly to make sure we follow our vision of simple security. Every new step and verison brings more of the award winning in premise technology into a new delivery system (the cloud).
This doesn’t mean we will stop selling on premises based solutions. We are really excited about where the cloud is going, with great reports and an overall easy and simple administration console that has all the features a customer or partner could need based on our on-premise know-how.
How do you approach the partner landscape in Greece?
We’ve made it simple to partner with us—with a flexible and generous partner program, delivered by dedicated channel relationship managers. And of course in cooperation with motivated distribution partners like NSS in Greece. Even though we work with more than 12,000 partners you’ll feel supported every step of the way. Because we work hard to get to know you and your organization.
When you partner with us, we help you identify opportunities to retain and grow your customer base and increase profits. You’ll be rewarded with deal registration protection, attractive margins, and joint lead generation programs. We also support you with up-to-date training and certification, so your sales and technical teams are fully qualified in our latest solutions. Our approach is unique—we are 100% channel focused. We continuously invest in our partner relationships. And it’s our mission to help your organization flourish.
Once these are exceeded interSeptor will provide an alert. For other sensors (security, water, power, smoke and dry contact), interSeptor will provide an alert as soon as the sensor switches to an alarm condition.
There are currently five different optional sensors : smoke, water leak, power, security and dry contact sensors.
The interSeptor water detector uses a specially designed cable to detect the presence of moisture at any point along the length of the cable. The water detection unit will sound an audible alarm upon detection and also sends a signal to the interSeptor to start the alarm process. Want an example? You arrive at work on Monday to discover an inch of water across a critical floor space. Of course you are able to quickly install a leak detection system to protect against future instances of this, but what if a system had been in place already? Could you have saved time and money? Could critical equipment be saved? Could staff have spent more time on more important matters?
The answer to these questions is, of course, YES! There is an easy-to -install, leak detection system with:
- Up to 30m leak detection cable
- Hassle-free installation
- Remote Web Access
- Free technical assistance via phone and email
- 60-day money-back guarantee
- 2-year swap out warranty
Jan
According to Gartner, Leaders are at the forefront of making and selling mobile data protection products that are built for enterprise business environments. The requirements necessary for leadership include a long-term road map that follows and/or influence Gartner, Inc’s vision of the developing needs of buyers in the market. Vendors in this quadrant lead the market by making their competitors’ sales staffs nervous and force competitors’ technical staffs to follow their lead. Their MDP products are well-known to clients and are frequently found on RFP shortlists.
“To be positioned as a leader for the past nine years is a testament to our product teams who continue to deliver innovative encryption and data protection products,” said John Shaw, Vice President for enduser security products at Sophos. “An aggressive roadmap, coupled with our plans to make it even simpler for small and medium sized businesses to protect their data by encrypting drives, files, cloud storage and mobile files invisibly, positions us for even more success in the months and years ahead.“
Sophos delivers leading solutions to help organizations protect critical assets. Sophos SafeGuard Enterprise protects data on desktops, laptops, removable media, file shares and to the cloud with proven, standards-based encryption—fully managed from one central console. Sophos also recently announced Sophos Mobile Control 3.5, the latest version of its award-winning mobile device management (MDM) solution, which now also supports iOS 7. Available both on-premise and as-a-service, Sophos Mobile Control 3.5 makes it simple for small and mid-market organizations to secure, monitor and control mobile devices.
Sophos was also positioned as a “Leader” in Gartner, Inc’s “2013 Magic Quadrant for Unified Threat Management.“
Spammers versus spam senders
There’s a big difference, because spammers generally don’t send their own spam in bulk any more. That hasn’t worked for a decade or so, because if you send 10,000,000 unwanted emails as fast as you can from the same server, or even the same data centre, you make an easily-identified target. So 1,000,000 of the messages might get loose before either the data centre (if it cares, and reputable ones most definitely do) or the majority of your recipients, or both, say, “No more!” Not only are you blocked from sending the remaining 9,000,000 emails from your truncated campaign, you probably can’t use those same servers again for days, weeks, months, perhaps ever.
How spam is delivered
Enter the botnet, or robot network. That’s an unwitting collection of surreptitously co-operating zombie computers – in homes, at offices, in coffee shops, at the mall, by the beach – that regularly call home for instructions to servers that the criminals control. The crooks can send each bot in the network a list of email addresses, and then command the entire botnet to start a giant spam campaign. Using bots, those 10,000,000 spams can be sent, say, in 10,000 batches of 1000 emails at a time, presenting a much less obvious pattern to those who defend against spam. (And sticking those 10,000 bot-infected users with the cost of the bandwidth, if you don’t mind.)
Why spam matters
I used the words “unwitting” and “surreptitious” above because, although some users may knowingly participate, the majority of botnet spam senders don’t even realise they’re doing it. That’s why we publish the SPAMPIONSHIP tables: not to lay wholesale accusations of cybercriminality against entire countries, but to raise awareness of something we’ve said a number of times recently, since it’s Cyber Security Awareness Month:
If you don’t make an effort to clean up malware from your own computer, you aren’t part of the solution, you’re part of the problem.
We’re not pointing fingers here at anyone who ever made a mistake and ended up infected by malware, but we do want you to be mindful of the consequences of inaction. For as long as you fail to do anything about spambot malware on your computer, you’re actually helping the crooks to make money, and putting the rest of us, no matter how modestly, in harm’s way.
The SPAMPIONSHIP tables
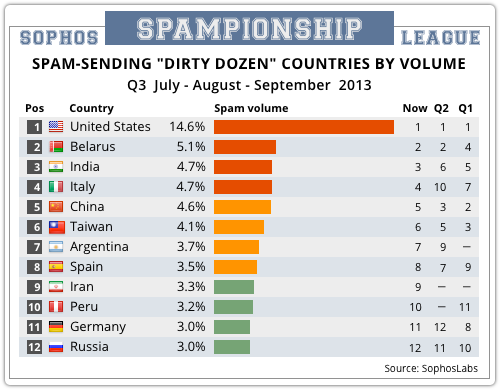
And with those firm-but-fair words behind us, here are the latest figures showing spam by volume on a country-by-country basis:
As you can see, the top of the table is surprisingly consistent, with the countries in the first five places having all been in the Dirty Dozen throughout the year. Of course, you probably expected to see India and China in the list: they each have populations exceeding 1 billion people, so it would be surprising not to see them near the top. Nor is is surprising that the USA is in the Number One spot yet again, this time sending nearly three times as much spam as second-placed Belarus. After all, the US has 30 times the population of Belarus, and internet access is much more strongly established, so you would expect a higher proportion of Americans to have their own computers and to use the internet regularly. It’s when we turn the SPAMPIONSHIP into a per capita comparison that things get interesting:

Here, the numbers next to each country denotes the average spamminess per person compared to the USA. In other words, we divided each country’s spam total by its population, then divided every country’s spam-per-person value by the figure for America. Obviously, that makes US = 1.00, and tells us that the average computer in Belarus was eleven times more likely to send spam than if it were in the USA. Israelis, whose propensity for sending spam sneaks the Middle Eastern country into twelfth place on chart for the first time this year, were 1.8 times as likely as Americans to be spam senders. The per capita chart doesn’t do any favours to small countries, which tend to hide near the bottom of volume-only lists, even if their computers are awash with zombie malware. US neighbour The Bahamas, for example, made it to eighth spot, with double the likelihood of its computers spamming compared to the US. Luxembourg got up to fourth spot, with a spammishness 2.7 times than of the US, up from sixth in Q2 and seventh in Q3.
You can read the original article, here.
The October 2013 CPU covers fixes for: Oracle Database Server, Oracle Enterprise Manager Grid Control, Oracle Supply Chain Products Suite, Oracle Siebel CRM, Oracle Industry Applications, Oracle Primavera Products Suite, Oracle and Sun Systems Products Suite, Oracle MySQL, Oracle Fusion Middleware, Oracle E-Business Suite, Oracle PeopleSoft Products, Oracle iLearning, Oracle Financial Services Software, Oracle Java SE and Oracle Virtualization. All of these updates are important, but arguably Java is the most important of all of them.
51 security vulnerabilities are addressed in Java this quarter, and 50 of them affect Java Applets or Java WebStart, the plugin that runs Java in your web browser. Worse yet, all but one are remotely exploitable without authentication. Some versions of Java update themselves, some rely on the operating system vendor and others are too old to support an auto-update mechanism. This does not make things easy.
Our advice?
1) Determine whether you have Java installed and enabled in your web browser. Visit java.com/en/download/installed.jsp and click “Verify Java version“. If your browser prompts you to install Java, close the tab; you’re Java-free. If it loads the applet, check your version. Be sure you are running Java 7 update 45 (1.7.0_45), Java 6 update 65 (1.6.0_65) or Java 1.5.0_55.
If you must have Java installed you ought to be running Java 7 (1.7). All previous versions are not officially supported and present a greater security risk.
2) If Java is installed and out of date, be sure to update it. Windows users can open the Java Control Panel, select the Update tab and choose Update now. Mac users can check for updates using the integrated Apple updater. Linux users should follow normal procedures for system updates provided by their distribution.

3) Most importantly, if you don’t need Java, get rid of it. Java can be useful for applications (Minecraft, payroll, mortgage calculators) and server-side applications (JBoss and more), but it doesn’t belong in your browser. If you’re not sure, I recommend disabling it. If you run across things that require Java, your browser will alert you with instructions.
You can read the original article, here.
Jan
“Our goal of ‘Security made simple’ can only be fully realized when every interaction Sophos has with customers and partners exceeds their expectations,” said Kris Hagerman, chief executive officer of Sophos. “Mary has an extraordinary track record in building dynamic and high-impact customer care and customer support organizations, and we are thrilled to welcome Mary to our management team.”
With Sophos Winfield will promote and lead a world-class customer support organization that leverages the latest technologies, methodologies and engagement channels to deliver the highest levels of customer satisfaction. Sophos already has one of the industry’s highest reputations for support quality and customer satisfaction. Winfield’s mission will be to enhance that reputation even further; her organization will serve as the focal point for the “voice of the customer” within Sophos and advocate for customers’ needs across all facets of the business.
Mary Winfield said, “I am excited to join the Sophos team. I believe the company is executing a winning strategy, with winning products and a commitment to customer excellence that sets the standard for the security industry. I look forward to helping the company make the most of every engagement with customers in our quest to make security simple“.