News
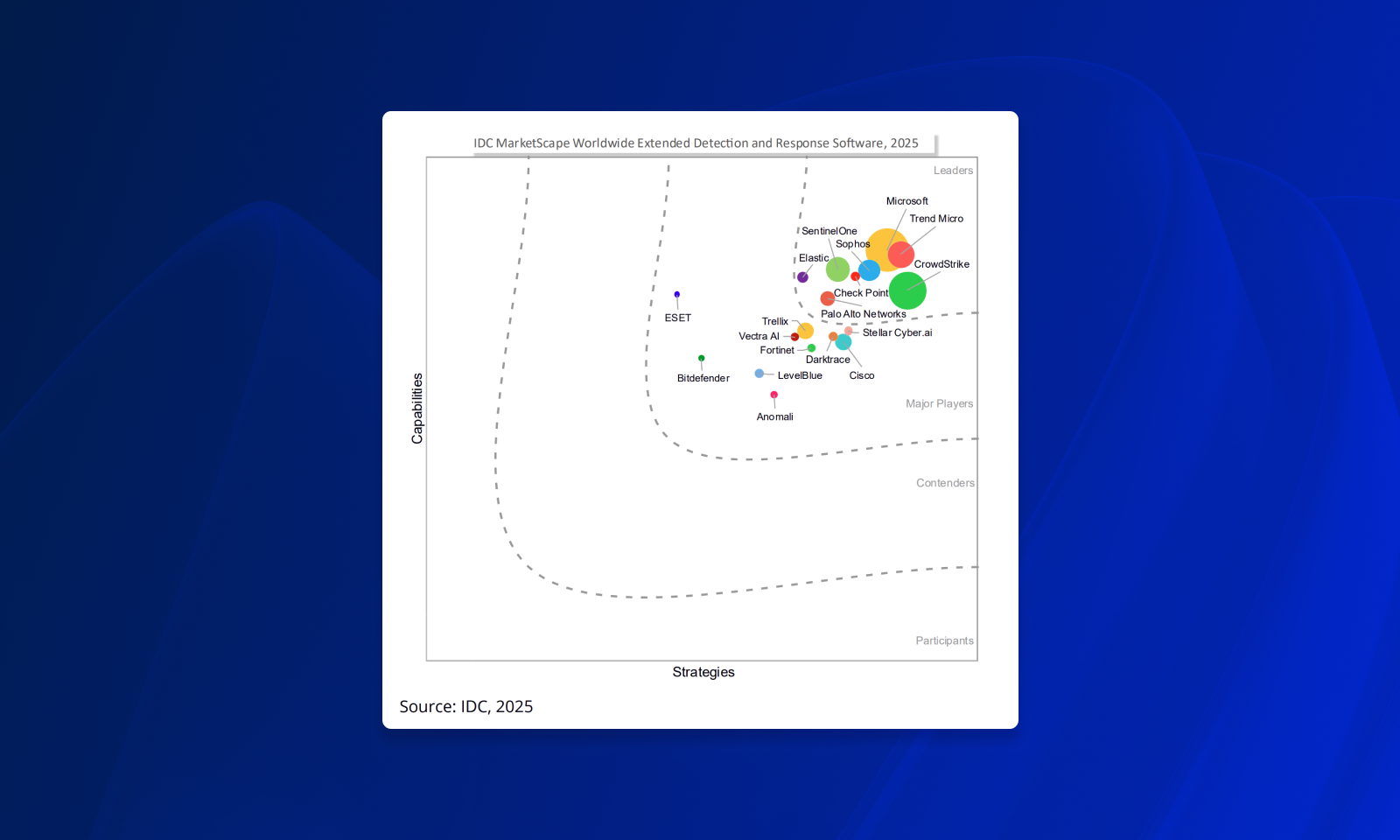
We’re proud to announce that Sophos has been named a Leader in the IDC MarketScape™: Worldwide Extended Detection and Response (XDR) Software 2025.
We believe this recognition reflects our commitment to delivering intelligent, integrated, and scalable security solutions that help organizations stay ahead of threats.
The IDC MarketScape for Extended Detection and Response cites Sophos’ protection capabilities as a strength, noting, “Sophos is viewed favorably in terms of the protections it offers. Key protection technologies included as standard features on the endpoint are host-based firewall and IDS/IPS, device control, DLP, antimalware scans, and encryption.”
The report also highlights Sophos’ proactive defense capabilities, stating, “Colloquially known as ‘Shields Up,’ Sophos’ Adaptive Attack Protection was introduced in 2023. Adaptive attack protection automatically enforces certain protections if there is evidence of a ‘hands-on-keyboard’ attack.”
“While Sophos has been working on many of these technologies internally, the integration of the Taegis XDR platform adds heft to existing capabilities and jumpstarts engineering cycles to newer initiatives.”
— Chris Kissel, IDC
When highlighting when to consider Sophos, the report notes, “Sophos has an international presence, and its ecosystem is designed to empower businesses of all sizes and all types. Cybersecurity novices, intermediate users, and experts will gain value from the Sophos XDR platform.”
Sophos XDR: Innovation that drives results
Sophos Extended Detection and Response (XDR) provides powerful tools and threat intelligence that enable you to detect, investigate, and neutralize threats across your entire IT ecosystem, delivered through Sophos’ adaptive AI-native, open platform.
- Start with the strongest defense: Organizations can focus investigations by stopping more breaches before they start. Sophos XDR includes the unparalleled protection of Sophos Endpoint to stop advanced threats quickly before they escalate.
- Accelerate security operations with AI: AI tools included with Sophos XDR help streamline investigations by providing real-time insights, contextualizing threat data, and offering natural language-driven recommendations. Designed in partnership with our frontline security analysts, the Sophos AI Assistant enables your in-house team to benefit from real-world workflows and the experience of Sophos experts.
- Integrated identity protection: Sophos delivers deep visibility across identity layers and cloud environments. With ITDR, Kubernetes monitoring, and integrations with Microsoft Entra ID and O365, we secure everything from endpoints to cloud workloads.
- Automated and adaptive defenses: Sophos offers a rich set of automated responses—from isolating endpoints to enforcing MFA and rolling back ransomware damage. Our adaptive defenses functionality activates protections during active attacks, minimizing impact and enabling swift recovery.
- Ecosystem flexibility: With an extensive ecosystem of integrations, Sophos XDR fits seamlessly into diverse IT stacks. Whether customers use third-party firewalls, email platforms, or endpoints, Sophos enhances existing investments without disruption.
- An open platform designed to optimize and unify: Benefit from a single view across your entire IT ecosystem in a unified detection and response platform and focus investigation efforts on high-priority items instead of noisy, unactionable alerts. Our open, extensible architecture provides visibility across the entire attack surface by integrating threat information from your existing and future security investments.
Secureworks integration is a game-changer
Following our acquisition of Secureworks in February 2025, Sophos Endpoint is now natively integrated and automatically included with Taegis XDR and MDR subscriptions. This milestone delivers combined prevention, detection, and response in a single platform with lower licensing costs and simplified operations.
This integration strengthens protection, accelerates threat mitigation, and ensures customers maximize ROI while maintaining flexibility.
Industry validation that matters
Sophos XDR isn’t just leading in innovation; it’s earning trust across the board. From analysts to end users, the recognition is clear:
- Sophos is named a Leader in the Gartner® Magic Quadrant™ for Endpoint Protection Platforms for the 16th consecutive report.
- Sophos is named a Leader in the 2025 Frost Radar™ for Managed Detection and Response.
- Sophos is named a Gartner “Customers’ Choice” for EPP for the fourth consecutive year, a “Customers’ Choice” for MDR for the second consecutive year, and a “Customers’ Choice” for XDR in the inaugural version of the report.
- Sophos is the ONLY vendor named a “Customers’ Choice” in both EPP and XDR
- Sophos is named a G2 Leader in Endpoint Protection, EDR, MDR, Firewall, and XDR in its Fall 2025 Grid Reports.
This consistent validation reinforces Sophos as the go-to partner for organizations seeking proven, high-impact security outcomes.
What’s next: Building the future of XDR
We believe being named a Leader in the IDC MarketScape™ is a milestone that reflects our progress. It also marks the beginning of our next chapter: Full integration of Taegis XDR into the Sophos Central platform.
Read an excerpt of the IDC MarketScape™: Worldwide Extended Detection and Response (XDR) Software 2025 here.
Source: Sophos
G2 has published its Fall 2025 Reports, and customers once again put Sophos at the top. Sophos is ranked #1 Overall in Managed Detection and Response (MDR) and #1 Overall in Firewall Software. Speaking to the power of our platform, Sophos is named as a Leader for the 13th consecutive time across every G2 Overall Grid® that defines modern security operations: Endpoint Protection Platforms, Endpoint Detection and Response (EDR), Extended Detection and Response (XDR), Firewall Software, and Managed Detection and Response (MDR).
These recognitions come from verified peer review and reflect what security teams value most: faster time to outcome, simpler operations, and the confidence of a platform that scales from prevention to managed response.
Managed Detection and Response
In addition to the #1 overall ranking among MDR solutions, Sophos MDR is also rated the top solution in five report segments for the category, including the Enterprise and Mid-Market Grids. Sophos MDR also earned the Best Results and Best Usability distinctions among Enterprise customers.
Endpoint
Sophos EDR/XDR was named a Leader across eight different segments in the Fall 2025 Reports, including the Overall, Enterprise, Mid-Market, and Small Business Grids. The Sophos XDR platform earned the Best Usability, Best Results, and Best Relationship distinctions, reinforcing its industry-leading security outcomes.
Firewall
The G2 Fall 2025 Reports marks Sophos Firewall’s 11th consecutive #1 Overall Firewall ranking. But for the first time, Sophos Firewall was also unanimously rated as the #1 firewall solution by all customer segments in the G2 Fall 2025 Reports (Enterprise, Mid-Market and Small Business users). Additionally, Sophos Firewall earned the Overall Best Results, Best Usability, and Best Relationship badges.
What Sophos customers are saying
“The level of comfort and security Sophos MDR has provided to us is immeasurable” said a Lead Infrastructure Engineer in the Mid-Market segment
“[Sophos MDR] is a combination of powerful automation and real human expertise delivered through tightly integrated security ecosystems” said a user in the Enterprise segment
“Sophos Firewall stands out because it combines strong protection with an easy-to-use interface” said a Technical Support Engineer in the Small Business segment
“[Sophos Firewall] offers a robust set of features, including advanced threat protection, user-friendly reporting, and seamless integration with endpoint security” said a Manager in the Mid-Market segment
“What I like best about Sophos Endpoint is its ability to provide powerful protection while remaining simple to manage and almost invisible to end users” said a Technical Engineer in the Small Business segment
“With advanced threat detection powered by deep learning and behavioral analysis, [Sophos Endpoint] swiftly identifies and neutralizes even the most sophisticated threats” said an IT Manager in the Mid-Market segment
For more information on our services and products, speak to your Sophos partner or representative and visit our website.
Source: Sophos
If you’re evaluating endpoint protection, you’ve likely noticed something: Everything starts to sound the same. “AI-powered.” “Next-gen.” “Integrated.”
These claims are everywhere. And with over 90% of organizations now using some form of endpoint protection rather than antivirus, it’s easy to assume all solutions are equal.
They’re not.
That assumption breaks down quickly as organizations mature — moving from basic prevention to detection and response. In this evolution, what once looked like a checkbox exercise becomes a critical architecture decision. What you choose now impacts not just how well you’re protected, but how well you can adapt and reduce overall business risk in the face of evolving threats.
So how do you separate signal from noise?
The power behind the platform
One of the best indicators of what a protection solution can do for you — not just today, but long term — is the platform it’s built on. Not every feature may matter to you on day one, and that’s OK. What matters is whether the foundation gives you room to mature and improve your cyber defense.
This is where platform thinking becomes essential: Are you choosing a product or investing in a strategy?
Modern endpoint protection isn’t just about what’s installed on the device. It’s about the telemetry collected, the integrations supported, the workflows enabled, and the data pipelines behind it all. Especially as AI plays a larger role in threat detection and response, the sophistication of that underlying data infrastructure becomes a force multiplier.
It starts with data
Before AI can assist — let alone automate — you need high-quality, well-structured, and continuously refreshed data. This isn’t new thinking. In fact, data science has long relied on four foundational dimensions: Volume, Variety, Velocity, and Veracity.
Let’s apply those to endpoint protection:
- Volume: How much telemetry is being collected? Are you seeing real-world adversary behaviors at a global scale — not just malware, but hands-on-keyboard attacks, abuse of tools, and stealthy persistence methods?
- Variety: Does the platform only see endpoints, or does it ingest from email, network, cloud, identity, and more? Is the data coming from a diverse customer base across geographies, verticals, and maturity levels? More sources mean better visibility — and more context.
- Velocity: How fast does that telemetry arrive, and how often is it updated? Are your models learning from new threats in hours or days, or are you reliant on weekly signature pushes?
- Veracity: Can you trust the data? Is it enriched with threat intelligence and verified through real-world incident response? Are detections backed by research, not just automation?
The nuance in those answers is what separates one platform from another. And it’s what determines whether a solution can detect emerging threats before they become industry-wide problems, or whether it lags behind the curve.
Start with prevention. Scale to resilience.
The endpoint is often the first — and best — opportunity to stop an attack. But if your architecture allows it, you can extend that prevention to email, network, cloud, and identity. From there, you can build response capabilities across the entire attack surface, strengthening your ability to contain threats quickly and keep core systems operational when something breaks through.
Every step forward compounds your advantage. You reduce business risk, improve time to detect, and accelerate response. And if you don’t have the people to manage it all in-house, you can lean on partners who offer 24/7 managed detection and response services (MDR) that plug directly into your platform.
At Sophos, this isn’t just theory.

We protect over 600,000 organizations worldwide. Our platform, Sophos Central, processes over 223 Terabytes of threat telemetry daily, pulled from every region, sector, and attack surface. We see threats early and often, generating over 34 million detections daily, giving our defenders an edge. And behind that data is Sophos X-Ops, a global team of threat analysts, malware researchers, and response specialists who monitor hundreds of threat groups and thousands of campaigns in real time. Together, the intelligence and expertise built into Sophos Central stop an average of 11 million attacks daily, with 231 advanced threats resolved by our Managed Detection and Response team. Collectively, we keep customers safe and businesses running without disruption.
When people ask us, “Aren’t all endpoint solutions the same these days?” — our answer is simple:
No. They’re not.
Look past the buzzwords. Ask what the platform sees, how fast it learns, and who is validating its insights. The truth is, what powers the protection matters as much as the protection itself. And those with the best data will always be one step ahead. Ultimately, strong cybersecurity isn’t just a technical need. It is a business imperative that defends operations, reputation, and long-term value.
Source: Sophos
BeyondTrust, the global leader in identity security protecting Paths to Privilege™, today announced the availability of new AI security controls in Identity Security Insights®. These capabilities provide unmatched visibility into AI agents, secure orchestration of their actions, and an on-board intelligence layer to help teams make faster, smarter security decisions.
“The rise of AI agents is creating a new and urgent identity security challenge. Agentic AI is not an isolated problem; it’s a subset of the broader non-human identity landscape. To secure it effectively, organizations must think holistically about their entire identity ecosystem, not just one type of identity in a silo. Often built on low-code and no-code platforms, AI agents can be deployed in minutes with privileges that rival human admins” said Marc Maiffret, Chief Technology Officer at BeyondTrust. “BeyondTrust uniquely connects visibility with proactive control across all identities so customers can rein in this new frontier of risk and turn AI into a safe force multiplier that also meets compliance requirements”.
BeyondTrust continues to advance Identity Security Insights with a steady cadence of innovation. In August 2025, we introduced Secrets Insights, a new capability within Identity Security Insights that uncovers and remediates risks tied to secrets and nonhuman identities. Today’s release extends that momentum with AI agent governance, giving customers unified visibility and control, and a future-ready foundation to adopt AI confidently and securely.
Three New Capabilities, Announced Today
1) AI Agent Insights
Expands Identity Security Insights’ market-leading identity capabilities to AI agents. Customers can discover, classify, and risk-score agents across cloud and SaaS platforms (including Salesforce Agentforce and ServiceNow), expose shadow AI, and apply Zero Standing Privilege (ZSP) and Just-In-Time (JIT) access policies to bring agents under full identity governance.
2) MCP Orchestration with BeyondTrust’s Lightweight MCP Server
A secure bridge for brokering agent actions across BeyondTrust products. This enables privilege-safe workflows, such as JIT API requests via Entitle, credential rotations in Password Safe, and future extensibility for both BeyondTrust copilots and customer-deployed LLMs.
3) Omnipresent AI Decision-Support Layer
Embedded directly into the Pathfinder Platform, this ChatGPT-like assistant interacts with customers’ identity security data to deliver real-time insights, guidance, and remediation steps. Powered by BeyondTrust Phantom Labs™ research, it helps teams make better-informed decisions without disrupting existing workflows.
Why It Matters for BeyondTrust Customers
- Move faster with AI, safely – Full visibility into AI, human, and service identities, mapped to privilege escalation paths.
- Increase productivity with integrated intelligence – Automated remediation and real-time insights reduce risk while speeding operations.
- Simplify security with one platform – Consolidated visibility, governance, and enforcement across all identities.
With these advancements, BeyondTrust extends its proven Paths to Privilege and True Privilege™ capabilities to human, machine, secrets, and now AI identities, unifying governance across the entire identity attack surface. Customers can move quickly with AI adoption, without compromise.
Most companies don’t realize how much shadow agentic AI is already operating within their businesses. BeyondTrust has expanded its Identity Security Risk Assessment to provide immediate visibility into these risks as part of the broader identity security picture. Access the complimentary Identity Security Risk Assessment to take action before attackers or compliance auditors do.
For more on BeyondTrust’s approach to securing AI, visit beyondtrust.com/solutions/ai-security.
About BeyondTrust
BeyondTrust is the global identity security leader protecting Paths to Privilege™. Our identity-centric approach goes beyond securing privileges and access, empowering organizations with the most effective solution to manage the entire identity attack surface and neutralize threats, whether from external attacks or insiders.
BeyondTrust is leading the charge in transforming identity security to prevent breaches and limit the blast radius of attacks, while creating a superior customer experience and operational efficiencies. We are trusted by 20,000 customers, including 75 of the Fortune 100, and our global ecosystem of partners.
Source: BeyondTrust
True Privilege™ is BeyondTrust’s industry leading capability for providing a complete view of all the privileges an identity has access to, including both intended and unintended privileges. Made visible by the True Privilege Graph feature in Identity Security Insights™, it goes beyond traditional views of privileges directly assigned to encompass hidden misconfigurations that attackers can exploit to elevate privileges further.
Seeing the True Privilege of an identity means having the ability to understand where privilege and risk truly exist. It’s all about seeing this bigger picture.
In recent years organizations have experienced exponential growth in the number of identities (human, machine, and agentic AI) and the accounts, privileges, and entitlements they can access across cloud, SaaS, and hybrid environments. To secure these identities effectively, you need to be able to cross silos and understand all the Paths to Privilege™ that exist and the True Privilege that this represents.
From Least Privilege to True Privilege: Why Modern Identity Security Demands a New Approach
Privileged Access Management (PAM) is a cornerstone in identity security, designed to reduce risk by enforcing the principle of least privilege. However, in modern environments, a major challenge is that PAM is often thought about in silos. For example, one might focus only on managing highly privileged Windows Domain Administrator accounts with little regard for the plethora of privileged cloud and SaaS roles.
To effectively protect our organizations from modern identity threats, we need consider the bigger picture and understand all the escalation paths across the entire identity attack surface. This is precisely what threat actors do, which is why 90% of organizations experienced an identity-related breach in the past year.
How True Privilege Protects Against Modern Attacks
Meet Amy: a real-world example of hidden risk.
Let’s consider Amy, a developer whose identity has multiple accounts and access to different systems.

Amy has various privileges directly assigned to her accounts, which traditional solutions might have visibility into—but often in a disconnected way. This means one tool might see her AWS privileges, while another sees her Active Directory privileges, making it difficult to get a complete picture of her assigned privilege and access.
But the real risk lies in the indirect or unintended privilege pathways. These can arise from misconfigurations, inherited rights, or hidden connections within the identity infrastructure. In Amy’s case, several apps she manages in Azure have service principals with the ability to assign the Global Administrator role. This means that even though Amy isn’t a Global Administrator herself, a path exists for her to gain that highly privileged role, either for herself or someone else.
Putting True Privilege into Practice
This is all about asking the right questions. Do you know who are the most privileged identities in your organization? How can you be sure a simple misconfiguration won’t allow any user to become a domain administrator? And how do you ensure proper controls, like multi-factor authentication (MFA), are in place for these privileged identities?
For most organizations, these questions are at best difficult but more likely next-to-impossible to answer with existing tools.
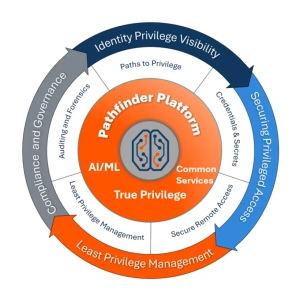
BeyondTrust Pathfinder the Platform with True Privilege Graph
These fundamental identity security questions around sprawling privileges, escalation paths, and solution silos are why we launched our BeyondTrust Pathfinder Platform, a unified and cohesive console. Pathfinder provides organizations with adaptive, intelligent, and risk-aware identity security.
Its deep, cross-domain intelligence capabilities, powered by Identity Security Insights, integrate with your existing solutions to offer context-rich visibility into every identity, going far beyond what traditional tools can offer.
Using AI models, BeyondTrust dynamically maps the True Privilege of identities across all systems and continuously uncovers new Paths to Privilege as your environment changes.
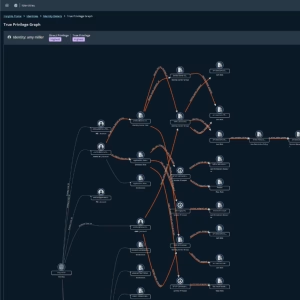
This pragmatic, AI-powered approach provides a level of visibility that previously required a dedicated team of identity security specialists. With Pathfinder, you can remediate risks and reduce your identity attack surface before attackers can exploit them.
Seeing and Addressing True Privilege™, and the Future of PAM
The Modern, Holistic Approach to Identity Security You Need
 No one likes scrolling through endless lists to find an answer. The BeyondTrust True Privilege graph allows you to visually explore the Paths to Privilege for any identity. This makes it easy to see assigned privileges and proactively uncover and fix escalation paths before a threat actor exploits them.
No one likes scrolling through endless lists to find an answer. The BeyondTrust True Privilege graph allows you to visually explore the Paths to Privilege for any identity. This makes it easy to see assigned privileges and proactively uncover and fix escalation paths before a threat actor exploits them.
Pathfinder offers the full suite of BeyondTrust capabilities, allowing you to easily manage privileges and access on-premises, in the cloud, or in OT environments. Whether you want to remove local admin rights, reduce standing privileges with just-in-time (JIT) access, or provide secure remote access without a VPN, Pathfinder is here to help you see, manage, and protect all your Paths to Privilege.
To see the True Privileges in your environment, start our free Identity Security Risk Assessment today.
Source: BeyondTrust
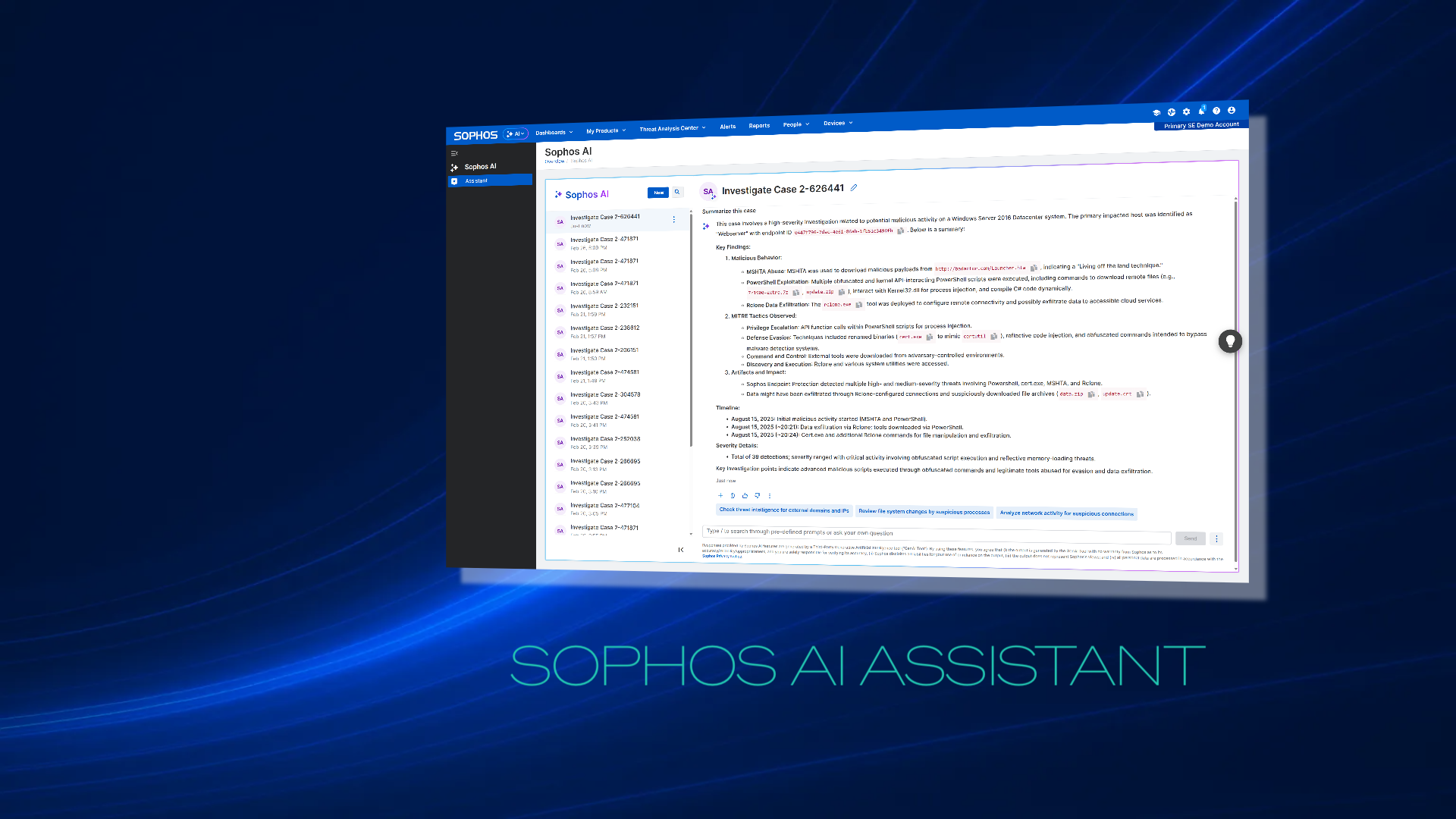
We’re pleased to announce new features to the Sophos AI Assistant, which puts easier case triage and investigation, MDR-grade expertise, guided workflows, and real-time threat hunting directly in the hands of every Sophos XDR and MDR customer.
What is the Sophos AI Assistant?
The Sophos AI Assistant is an integrated feature in Sophos Central that uses large language models (LLMs) and natural language understanding to enable all users — from IT generalists to experienced SOC analysts — to query security telemetry, enrich investigations, and take investigative actions without needing to write SQL-like queries.
It isn’t just another AI tool — it’s expertise from the team behind the world’s leading Managed Detection and Response service, distilled into an intelligent agent. The AI Assistant is included for all Sophos XDR and MDR customers at no additional charge.
With this release, the Sophos AI Assistant has been enhanced to support two key roles:
- Security Analyst – Focused on case investigation and triage.
- Threat Hunter – Focused on proactive, exploratory investigations across the environment.
Getting started with the AI Assistant
Key capabilities in this release
- Updated navigation in Sophos Central
The Sophos AI Assistant is now accessible from a new “AI” menu in the Sophos Central Admin console. This update reflects the increasing importance of AI-powered tools in analyst workflows and ensures easier access to AI-driven insights and actions—whether you’re responding to alerts, investigating incidents, or proactively hunting threats.
- New Security Analyst and Threat Hunter assistants
This release introduces a new AI assistant:
- Security Analyst assistant: Designed for triage, case management, and investigation tasks.
- Threat Hunting assistant: Adds support for proactive hunting workflows, allowing analysts to explore telemetry, craft queries, and investigate suspicious behavior across the estate.
Together, these new context aware assistants unify reactive and proactive capabilities under a single, AI-powered interface.
- Contextual workflows based on analyst role
The AI Assistant now pulls in context based on the function an analyst is performing:
- Security Analysts receive case-aware prompts, enrichment support, and streamlined investigation flows.
- Threat Hunters are provided with advanced search suggestions, guided telemetry pivots, and custom prompt templates.
Whether you’re summarizing case findings or exploring detection anomalies, the AI Assistant ensures a seamless and role-aligned experience.
- Smart prompt starters and in-workflow assistance
To reduce onboarding friction and improve usability, Sophos has introduced intelligent prompt suggestions tailored to common SOC activities. From device analysis to trend reviews, the AI Assistant helps you frame effective queries and make informed decisions—without needing deep familiarity with query languages or telemetry schemas.
Use cases in action
- Alert triage: Quickly summarize the context and related detections
- Investigation: Trace lateral movement using command-line data or user behavior
- Threat hunting: Search for PowerShell execution anomalies over time
- Enrichment: Perform live lookups on hashes, IPs, or domains
You can even add AI Assistant outputs directly into your case notebooks, ensuring that your insights and steps are preserved for auditing or handover.
Sophos Central Documentation – AI Assistant Use Cases
How to write effective prompts
We’ve published a new best practices guide for writing effective AI prompts. This guide helps you frame questions more clearly and precisely to ensure high-quality results from the AI Assistant.
Tips include:
- Be specific: Include device names, time ranges, or detection types
- Give context: Tie the prompt to a case or alert when possible
- Define format: Ask for lists, tables, or summaries if needed
How to craft effective prompts
Ready to try it?
Log in to Sophos Central today and start working with your new AI teammate.
AI Assistant documentation and training resources
Source: Sophos
Despite spending more than $18.5 billion on identity security products in 2024—a 15% increase year over year according to Gartner—identity remains the most common entry point for attackers. It’s the most used vector for initial compromise, and the trend is only expected to continue. This year alone, there have been over 800 million new sets of stolen credentials compromised as a result of the explosion of infostealers.
So, why are we still struggling?
The short answer is that identity security has not evolved fast enough. In contrast to other areas of cybersecurity, identity continues to be stuck in legacy thinking. Traditionally, it has been considered a function of compliance and business enablement, rather than a front-line security function. As a result, most organizations rely on fragmented tools, complex implementations, and reactive controls that are unable to keep up with modern threats.
Account compromise is not an anomaly, but an inevitable consequence of an outdated model.
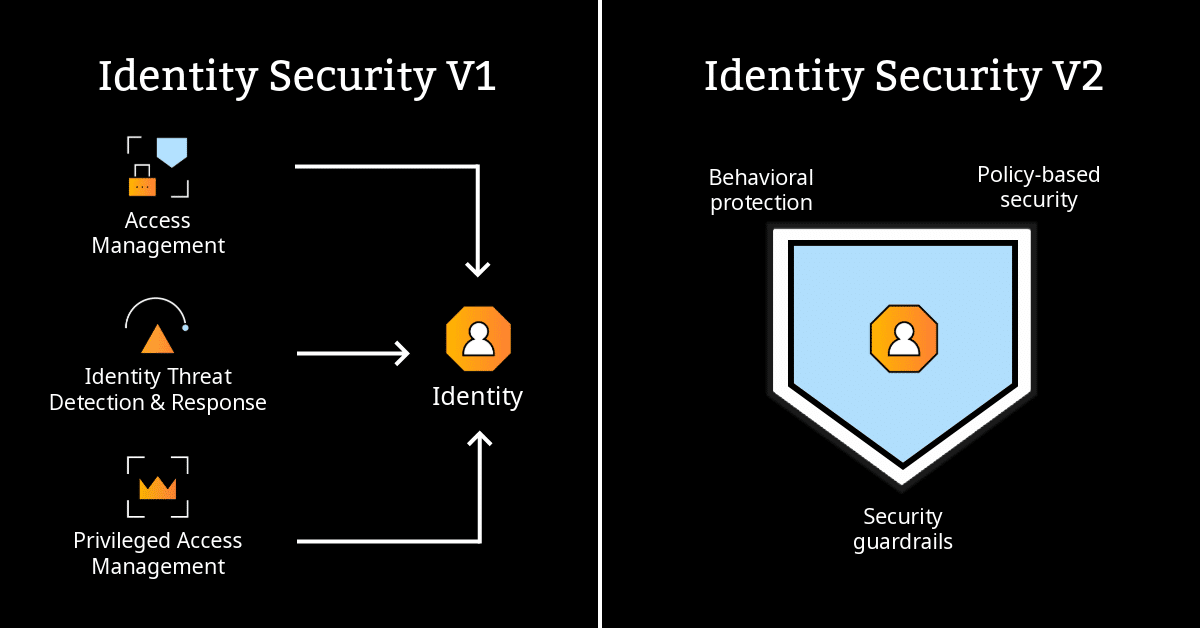
We’re still operating in what can only be called Identity Security v1. This is a first-generation approach that lacks the agility, integration, and focus necessary to combat today’s threats. The strategy is to layer controls over already exposed environments, often through projects that can take many years to complete. But attackers don’t wait—and neither should we.
A clear symptom of this lack of control is the uncomfortable conversations that many security leaders face: What is our residual risk? What does that mean in business terms? When will we be done? These questions are difficult to answer when you’re not fully in control and must constantly react to the environment as it changes beneath you.
Imagine a state where you can clearly define and enforce foundational identity controls: every admin is required to authenticate with MFA, service accounts are restricted to their usual, approved behavior, and all access is denied by default unless explicitly allowed. These controls aren’t aspirational: they’re implementable, enforceable and, most importantly, measurable. Their effectiveness is reflected in the threats that are blocked or contained before they can escalate, providing a direct line between control and risk reduction.
What is needed is a shift in both mindset and technology. Identity Security v2 puts compromise prevention at the centre. It is proactive, universal, and built to manage identity risk without getting in the way of business. As a result, identity is not treated as an afterthought, but as a control point.
There is an urgent need for this change. A perfect storm is brewing around outdated assumptions about identity’s role in security, a lack of modern tools that provide real-time control, and growing complexity across cloud, SaaS, and hybrid environments. Together, these forces call for a new approach, one that allows us to control now, everywhere it matters, and fine-tune later.
We cannot afford to wait. The cost of inaction is written clearly in breach reports and stolen credentials are piling up by the day.
Why identity is different and why that matters
Identity stands apart from other areas of security. Unlike most security domains, identity is fundamentally about people. Even non-human identities, service accounts, APIs, and machine identities ultimately reflect human decisions made by either developers, admins, or platform owners.
Identities are unique in that they are woven tightly into the day-to-day activities of an organization. It affects how people access tools, collaborate, and accomplish tasks—and, crucially, how they feel while doing so.
Identity has historically been funded for two reasons:
- How can we quickly onboard new joiners and make authentication seamless for everyone?
- How can we meet compliance requirements and avoid costly violations?
Now, a third and fundamentally different driver has emerged: how can we defend against identity-based threats? It requires new skills and a new mindset that may not always be aligned with traditional efficiency or compliance objectives.
In many cases, efficiency is associated with an increase in risk and over-provisioned access is a common consequence. The scope of compliance is narrow and deep, whereas security requires broad, real-time visibility and control. Due to these competing priorities, identity teams need to evolve into identity security teams with a new mandate and dedicated tools.
In most areas of security, this evolution is already well established: network, endpoint, and cloud teams all work alongside their specialized security counterparts, supported by purpose-built tools. But in identity, that model is often missing. Teams managing systems like Active Directory, Entra, or Okta are rarely partnered with dedicated security teams, who are themselves enabled by specialized technology. They often lack the tools required to take a truly security-first approach.
To meet today’s threats, that must change.
Why today’s identity security tools are not enough
As identity security has not evolved organizationally, technology has also lagged—especially when compared to other security disciplines.
Let’s take network security as an example. Modern tools don’t just offer visibility; they serve as a universal control plane that enforces guardrails across the entire environment. Security teams can proactively define and apply security policies to control risk and respond in real time to threats. These controls are consistently applied, ensuring no part of the network operates outside the organization’s security framework.
Identity has not had the same evolution.
Today’s identity security tools fall into one of three categories:
- Tools that treat identity as a set of vulnerabilities to be remediated (e.g., weak passwords, excessive privilege, orphaned accounts)
- Tools that isolate risky accounts (e.g., vaulting via PAM)
- Tools that attempt to detect identity-based threats and respond (e.g., ITDR)
The solutions are fragmented, focusing only on cloud, SaaS, or native identity platforms, and are often implemented in silos. As a result, attackers can exploit these gaps easily.
More critically, these tools do not empower identity security teams to take control of risk. They keep teams reactive, forcing them to chase down threats, remediating after the fact, and layering controls in response to what has already happened.
In today’s more complex environments, that model simply does not work. Treating identity as a list of backlog items to fix means exposure persists until everything is perfectly remediated, which is something no organization can realistically achieve.
It is possible to reduce exposure by locking down high-risk accounts; however, this is typically a difficult process, degrades the user experience, and does not scale well. This approach demands perfection: perfect visibility, perfect execution, and complete coverage across every critical system. No company can honestly claim they have achieved that.
Solving account compromises requires more than a patchwork. It requires a new kind of identity security technology—one that gives teams real control, closes gaps proactively, and puts you in the driver’s seat.
How do we take control?
Authentication today is not designed with security as the primary goal. When designing networks, security is front and center. Firewalls, segmentation, and controls are built to limit blast radius and contain threats. You would not accept a network without built-in security controls. Yet authentication is typically designed to ensure uptime and availability. The priority is operational: will users be able to log in when needed? Will the systems stay up and running to support the business? This mindset reflects identity’s legacy as a business enabler, not a security control.
But why is authentication not built security-first?
Why don’t we start from a position of denying by default and applying security controls to enforce security standards in line with our risk appetite? As a result, the blast radius will be narrowed, and the risk of account compromise will be reduced.
Imagine if these were the default policies:
- Require MFA for all access to sensitive infrastructure
- Deny any connection not originating from trusted sources
- Block authentication using legacy or insecure protocols
When we approach identity with this mindset, the game changes. Security risks become less urgent because the environment is controlled by design. It is now easier to explain risk to executives, not because the problems have disappeared, but because we have taken charge of how identity is protected.
This gives you the space and time that you need to modernize your identity landscape while staying in control of risk every step of the way—whether that’s adopting ephemeral credentials, moving toward zero standing privilege, or rethinking how access is granted.
Source: Silverfort
Sophos is delighted to announce that Sophos Endpoint is now natively integrated and automatically included in all Taegis™ Extended Detection and Response (XDR) and Taegis Managed Detection and Response (MDR) subscriptions.
Customers gain immediate access to combined prevention, detection, and response capabilities in a single platform – while lowering costs and simplifying operations. The integration follows Sophos’ acquisition of Secureworks in February 2025 and represents a major milestone in combining the companies’ strengths to help customers defeat cyberattacks with a higher ROI.
Endpoint protection remains one of the most critical layers of defense against today’s cyberthreats, delivering both frontline prevention and vital telemetry for detection and response. With Sophos Endpoint included in all new and existing Taegis XDR and MDR subscriptions, customers can benefit from unmatched ransomware defenses and adversary mitigation capabilities that automatically deploy in the event of an attack. The integration enables organizations to strengthen protection while lowering licensing costs, reduce management overhead through native integration, and accelerate threat mitigation with expanded response actions.
Taegis remains a fully open platform, ensuring customers continue to receive full value from their existing cybersecurity investments and maintain the freedom to use the endpoint protection solution of their choice. This ensures that customers maximize ROI while allowing room in their budget for other cybersecurity priorities.
Watch this 2-minute video to learn more about the integration.
Organizations need superior protection
Too many organizations still treat endpoint protection like a commodity, and that’s exactly the mistake attackers are counting on. The reality is that not all endpoint products are built to stop today’s hands-on-keyboard attacks.
Sophos Endpoint’s prevention-first capabilities, like CryptoGuard anti-ransomware protection and Adaptive Attack Protection, shut down attacks before they can escalate, which is a true game changer for enterprises managing thousands of devices. And by simplifying deployment and policy management, we’re helping organizations stay ahead of threats, lower their total cost of ownership, and maximize the return on their security investments.
Key benefits for Taegis customers
- Lower costs and improved ROI: Sophos Endpoint is now automatically included with all Taegis XDR and Taegis MDR subscriptions, eliminating the need to purchase a separate endpoint security solution.
- Vendor choice preserved: Taegis remains an open platform, allowing organizations to continue using their preferred endpoint solution.
- Industry-leading protection: A 16-time leader in the Gartner® Magic Quadrant™ for Endpoint Protection Platforms, Sophos Endpoint provides unmatched defense against ransomware and other advanced threats, with features such as CryptoGuard and Adaptive Attack Protection, accessible directly from the Taegis console.
- Workflow continuity: Telemetry and detections from Sophos Endpoint are ingested into the Taegis platform, allowing customers to retain existing detection and response workflows.
- Simplified management: Customers can download, install, and manage Sophos Endpoint directly from Taegis.
Meeting customers where they are
To support a range of environments, customers can now choose between three deployment options for endpoint protection:
- Sophos Endpoint: Natively integrated for comprehensive prevention, detection, and response in a single agent.
- Non-Sophos native integrations: Telemetry ingestion ensures full visibility from products such as CrowdStrike, Microsoft Defender, SentinelOne and Carbon Black by Broadcom.
- Other non-Sophos endpoint security solutions: Supported through a detection-only sensor deployment option.
Streamlined Sophos deployment experience for Taegis users
Upgrading to Sophos Endpoint is an easy and frictionless process for Taegis users.
- Customers can download the Sophos Endpoint installers directly from within the Taegis platform – no additional licenses required.
- Documentation and upgrade instructions can be found on the Sophos Endpoint Agent page in the Secureworks documentation.
- Customers can retain their existing detection and response workflows as endpoint telemetry and detections from Sophos Endpoint are now ingested directly into the Taegis platform.
- Additional response capabilities are now available with Live Response functionality for Sophos Endpoint, directly from the Taegis console. This enables security teams to execute commands to terminate suspicious processes, reboot endpoints and servers, delete files, and more, with full, secure shell access. (Note: an endpoint must be running Sophos Endpoint to use Live Response – either the full agent or sensor).
Learn more
Sophos Endpoint is available immediately for all existing and new Taegis XDR and MDR customers. Watch this 2-minute video, explore the Taegis platform, and learn more about Sophos Endpoint. To discuss how Sophos and Taegis can support your cybersecurity goals, speak to your Sophos representative today.
Source: Sophos
The cybersecurity world was jolted by the recent announcement that Palo Alto Networks will acquire CyberArk in a landmark deal valued at approximately $25 billion. Beyond the financial scale of the transaction, this acquisition marks a shift in how the industry views identity security. The recent acquisition validates what we’ve been emphasizing already: identity is both the first and last line of defense, and it demands its own dedicated security layer. Just as we’ve seen in other domains like endpoint and cloud security, protecting identities requires an end-to-end platform—one that offers unified visibility, intelligent insights, and inline protection.
CyberArk, rooted in Privileged Access Management (PAM), has expanded its identity capabilities in response to market needs. But this acquisition surfaces a more critical and timely question:
What is the future of PAM?
We believe we’re witnessing the beginning of a transformation. A future where securing privileged access will no longer revolve around a vault. In fact, vault-based approaches will no longer be the primary method of enforcing privileged access security.
This shift parallels transformations we’ve already seen in other areas of cybersecurity:
- Cloud security has gone agentless, replacing intrusive deployments with lightweight, API-based visibility.
- Multi-Factor Authentication (MFA) does not require code changes or proxies as in the past. Today it is enforced by the identity provider or an extension to the identity provider.
- Identity protection platforms now enforce policies in real time without injecting keys or passwords, reducing the attack surface.
- Network security moved away from physical firewalls and VPNs to Zero Trust Network Access (ZTNA), which grants access dynamically based on identity, context, and posture.
In each of these cases, the core idea was the same: move away from securing secrets or infrastructure, and instead focus on securing the access itself. PAM is now undergoing a similar evolution.
The problem with vault-based PAM
Vaults were introduced as a way to protect the credentials used by privileged accounts—admin usernames and passwords for servers, databases, switches, and more. The premise was sound: don’t let users know or reuse powerful passwords. Instead, let them retrieve credentials from a secure vault when needed, and rotate those passwords after use.
But in practice, vault-based PAM creates several problems:
- It secures the credential, not the access. Once a user retrieves the credential, the vault’s protections end. That password can be stolen from memory, logged by malware, misused by insiders, or intercepted in a man-in-the-middle attack. The access itself isn’t protected—just the storage of the password.
- It’s operationally complex. Vault-based PAM introduces major friction into workflows. Changing how users log into systems—redirecting them through a proxy, forcing them to check out passwords, re-authenticate constantly—often requires training, workarounds, or exceptions. On the NHI front, to rotate service account credentials multiple approvals are typically required and careful work to avoid breaking changes. This change in behavior complicates adoption and makes PAM deployments time-consuming and expensive. Many organizations take years to roll out PAM at scale, especially in hybrid environments where legacy systems, service accounts, and third-party access all require separate configurations.
- It’s not breach-proof. Vaults themselves are high-value targets. Attackers know that compromising a vault can yield credentials for the most sensitive systems in the organization. We’ve seen real-world breaches that prove this. In a high profile 2022 breach, the attacker reportedly gained access to the company’s privileged access vault by harvesting credentials and tricking an employee into approving MFA requests. Once inside, the attacker had access to admin tools, infrastructure, and sensitive data. In other incidents, attackers have exploited vault misconfigurations, API tokens, or integration weaknesses to escalate their access. The idea that vaults are unbreachable is no longer tenable.
- It creates a false sense of security. Security teams often assume that rotating credentials and limiting access to the vault is enough. But if the password is still being handed to the user—even for a short time—it can still be exfiltrated or abused. The security controls (like MFA, session recording, or approval workflows) are tied to the vault, not to the privileged access itself. Once the login is done, there is no additional enforcement point to apply security controls.
Vault-centric PAM worked well in the era of static infrastructure and long-lived accounts. But today’s IT environments are dynamic, distributed, and identity-driven. Simply protecting credentials in a vault is no longer enough.
From privileged account management to privileged access security
The real opportunity—and what defines the vault-free future—is to shift from managing privileged accounts to securing privileged access.
In this model, organizations no longer rely on permanent accounts with vaulted passwords. Instead, privileges are granted dynamically, just-in-time, and removed as soon as they’re no longer needed. Access is brokered and monitored in real time based on user identity, context (device, location, time), and policy.
This eliminates many of the risks associated with vault-based PAM:
- There is no standing credential to steal or reuse.
- The change to user behavior is minimal; no login disruption, and no password checkout process.
- All access is tightly monitored and tied to a verified identity.
- Even if the attacker gains hold of the password, the access is still secured and the attack can be stopped there.
This model also extends seamlessly to non-human identities (NHIs)—like service accounts, scripts, AI agents, and automation tools—which now make up the majority of privileged access in most organizations. Rather than managing thousands of long-lived credentials for these entities, organizations can enforce policies that allow specific systems to initiate privileged access under strict controls, without static secrets. As NHIs become more manageable through identity providers, cloud-native tools, and runtime enforcement, the vault-free approach becomes both more feasible and more secure.
Identity-centric access: A more secure approach
This shift toward privileged access security is made possible by technological advances in identity security. Organizations can now apply strong security controls at the identity layer—enforcing MFA, risk-based policies, session monitoring, and just-in-time elevation—without injecting credentials or modifying infrastructure.
In fact, modern platforms can secure privileged access in a way that’s:
- Proxyless – doesn’t require routing all of the network traffic through a gateway or rewriting apps.
- Credential-free – avoids injecting or exposing privileged credentials.
- Inline & real-time – dynamically responds to access attempts with adaptive policy decisions.
This architectural shift allows organizations to apply Zero Trust principles to privileged access—validating every request continuously, applying least privilege policies, and responding to anomalies instantly.
And it aligns with how security teams want to work: reducing the attack surface, minimizing user disruption, and simplifying operations.
Will vaults disappear?
Vaults will remain part of the privileged access landscape for the foreseeable future. Some systems will continue to require passwords. Some compliance requirements will mandate secure storage of credentials. And in certain break-glass or legacy scenarios, having a vault as a fallback mechanism still makes sense.
But vaults will no longer be the primary way organizations secure privileged access. Instead, the center of gravity will shift to real-time, identity-aware controls—a model that doesn’t rely on handing users credentials, and doesn’t require those credentials to exist in the first place.
We’re already seeing this transition unfold. Modern identity security platforms are being used to enforce granular access controls for privileged sessions across cloud and on-prem environments. These controls—based on who the user is, what resource they’re accessing, and under what context—are more precise, more scalable, and more secure than vault-based approaches.
And importantly, they’re faster to deploy and easier to manage, because they don’t require users to change how they log in or IT teams to redesign their environments.
Looking ahead
The future of privileged access is vault-free. Vaults served a critical function in an earlier era. But as identity becomes the new perimeter, and access becomes the control point, it’s time to move on.
Security leaders who want to reduce risk, accelerate zero trust adoption, and simplify their operational burden should begin by asking: Do I need to protect this password, or can I eliminate it altogether?
By shifting the focus from accounts to access, we can finally secure identities in a way that’s invisible to users, resistant to breaches, and built for the dynamic environments of today—and tomorrow.
Learn more about Privileged Access Security and how it benefits identity and security teams.
Source: Silverfort
Enterprise Strategy Group (ESG) Principal Analyst Todd Thiemann released his latest research on identity security, titled “Identity Security at a Crossroads: Balancing Stability, Agility, and Security.”
The findings make one conclusion clear: with identity security growing more complex, teams believe consolidating capabilities into a single platform is a must to ensure visibility into what employees and non-human identities are accessing, acting on, and connecting to within their environments.
Todd opens the report with the following note to readers: “Workforce identity security is in a state of flux, with changing enterprise infrastructure, an expanding application portfolio to integrate, and sprawling cloud deployments that are exposing unsolved problems, inefficient processes, and fragmented solutions.”
Through the study, ESG surveyed 370 IT and cybersecurity decision-makers across multiple industries, mostly comprising organizations with at least 1,000 or more employees. The goal of this research is to identify and quantify major pain points for leaders managing identity security in their organizations and uncover trends that show how they plan to tackle those concerns.
In this blog, we’ll unpack key findings from the research and explain what it means for organizations’ shifting priorities.
Ready to skip straight to the research? Download the Report here.
70% of teams plan to expand usage of an existing tool to cover a new use case in the next 12-18 months
In addition to organizations expanding usage of existing tools, 62% of organizations plan to implement a net new tool to satisfy a use case, hinting that current solutions may be inadequate to satisfy evolving priorities. We’ll get into what those “evolving priorities” are later, but in the meantime it’s important to unpack the desire to consolidate or adopt new tools.

In the study, participants were asked “What identity solutions are currently in use or expected to be in the next 12-24 months?” Across 18 functional areas including MFA, NHI security, ITDR, and more, nearly half of organizations reported that they use multiple solutions for each. In fact, identity teams “use an average of 11 tools, and the proliferation of tools leads to operational complexity, poor visibility, and identity silos.” If you’re an identity security practitioner looking for an MFA solution (as an example), ESG research shows that 46% of teams aren’t just using one tool for MFA, they’re using multiple. Add in the complexity of 18 functional areas to satisfy? The idea of “tool sprawl” doesn’t even begin to cover what teams have been working with.
What factors drive the tool sprawl?
- 52% report that cloud adoption plays a factor
- 51% cite cyber insurance requirements
- 48% note that they need separate tools for separate environments (like on-prem versus cloud)
- The list continues on page eight of the report
With 46% of organizations managing anywhere from 500-2,499 business applications, consolidation is now a necessity. With a unified identity security platform, teams can gain the comprehensive visibility they need, uncover powerful context across the organization, and make insights-based decisions made possible by having the full picture.
67% of teams are concerned about NHI Security, while 52% believe AI agent adoption raises data privacy issues
Non-human identities include identities like service accounts and API keys. While teams are concerned about securing NHIs, very few have deployed an NHI-specific security tool. Instead, 77% of them are choosing identity security or IAM platforms to tackle NHI security. Again, enterprise identity security teams demonstrate that folding in NHIs into their entire identity security strategy rather than selecting a point solution leads to stronger security outcomes.

Teams report that securing AI agents is now on their radar, too. Data privacy is the top concern, but other sources of uneasiness around AI agents include “Failure of human oversight” and “Control of AI agents falling into adversary hands.”
The truth is, AI agents are not machines, nor are they human. They lie somewhere in between and therefore need to be treated as their own category of identity. An AI Agent security solution needs to address these concerns, so every AI agent is tied to a human and has the proper policies in place to prevent (and detect) improper activity.
Identity Security investment will keep growing—get the research to learn more
91% of organizations surveyed consider identity security one of their top five priorities in the next 12-24 months, with 42% expressing it is the number one priority.
As areas like AI agent security, ITDR, and ISPM become critical to an organization’s overall identity security strategy, teams need to consider how to balance a growing number of focus areas alongside having the right tools to provide the full context needed to make informed decisions for the business.
As ESG’s research uncovers, tool consolidation offers a path to accomplish those goals, with identity security platforms offering the highest chance of meeting the desired outcomes. In fact, a top motivator for many participants (24%) to evolve their existing identity security portfolios was “cost savings because of vendor consolidation,” validating that this approach saves money while optimizing resource utilization.
Download the complete research today to see how your identity security peers are tackling top concerns and where they plan to invest to achieve their goals in 2025 and beyond.
Source: Silverfort
Μάθετε πως η Silverfort μπορεί να δουλέψει για εσάς!
Legacy operating systems that have reached end-of-support often lack security features and updates that are present in newer systems, making them targets for exploitation by adversaries. However, organizations within industries such as manufacturing and healthcare often need to run endpoints with these operating systems for specialized systems, including machinery and medical devices.
Endpoints in operational technology (OT) environments can be difficult and prohibitively expensive to upgrade or replace, resulting in devices being left unsecured or requiring additional security solutions and mitigations.
Comprehensive protection for legacy Windows and Linux endpoints
Introducing Sophos Endpoint for Legacy Platforms — a solution that provides comprehensive next-gen security for a range of Windows and Linux operating systems beyond the standard end-of-support dates provided by platform vendors.
Simplify deployment and management of endpoint security across all devices. Security solutions that limit support to modern operating systems drive organizations to deploy separate solutions for legacy systems, introducing a management burden on IT and security teams. Sophos provides industry-leading endpoint security for both legacy and modern platforms in Sophos Central — a powerful, cloud-based management platform that unifies all Sophos next-gen security solutions.
Protect critical devices beyond operating system vendor support timeframes. Defer difficult and costly upgrades for specialized systems. Sophos Endpoint for Legacy Platforms enables organizations to protect a range of legacy Windows and Linux operating systems beyond standard end-of-support dates offered by platform vendors.
Legacy systems protected by next-gen technologies. Web, application, and peripheral controls reduce the threat surface and block common attack vectors on legacy and out-of-support devices, while deep learning AI models protect against both known and never-before-seen attacks. CryptoGuard anti-ransomware and anti-exploitation technologies stop threats fast, so resource-stretched IT teams have fewer incidents to investigate and resolve.
Neutralize sophisticated attacks that can’t be stopped by technology alone. Legacy devices are attractive targets for exploitation by adversaries. Sophos’ AI-powered EDR and XDR tools enable organizations to detect, investigate, and respond to suspicious activity across all devices, including legacy platforms. Organizations with limited in-house resources can engage industry-leading Sophos MDR services to monitor and respond to threats across the entire IT environment.
Legacy systems deserve industry-leading security
Don’t risk the security of your legacy devices with inferior solutions. Devices running out of support operating systems are often critical to an organization. That’s why at Sophos, we believe these systems deserve the strongest protection, from a proven, market-leading endpoint security vendor.
- Sophos has recently been named a Leader in the 2025 Gartner® Magic Quadrant™ for Endpoint Protection Platforms, marking our 16th consecutive report as a Leader in this category.
- Sophos is named a “Customers’ Choice” vendor in the 2025 Gartner® Peer Insights™ Voice of the Customer Report for Endpoint Protection Platforms for the fourth consecutive year and in the inaugural Voice of the Customer Report for Extended Detection and Response. This makes Sophos the only vendor named a “Customers’ Choice” in both reports.
- Sophos is the only vendor named a Leader across the G2 Spring 2025 Overall Grid® Reports for Endpoint Protection Suites, Endpoint Detection and Response (EDR), Extended Detection and Response (XDR), Firewall Software, and Managed Detection and Response (MDR).
Available today!
Sophos Endpoint for Legacy Platforms is available as an optional add-on for customers with a Sophos Endpoint, Sophos XDR, or Sophos MDR subscription.
It’s ideal for:
- Organizations with critical systems and devices running on legacy or out-of-support operating systems, such as manufacturing, healthcare, and energy.
- Organizations with large endpoint estates that struggle to fully upgrade to newer OS versions before a platform vendor’s end-of-support timeframes.
- Organizations who currently use different endpoint security solutions for legacy vs. modern platforms.
To explore how Sophos Endpoint can help secure your legacy systems, speak to an expert today and download the solution brief.
Source: Sophos
Email remains one of the primary malware delivery methods. With over 90% of successful cyberattacks starting with phishing1 and business email compromise (BEC) attacks accounting for nearly $3 billion in losses per year2, email security has never been more important.
 Furthermore, with the advent of generative AI (GenAI), these phishing and BEC attacks are expected to pose an even greater threat. According to a survey by 451 Research S&P Global Market Intelligence, 83% of security leaders express concern about GenAI enabling more advanced phishing and BEC attacks, up from 21% a year ago.3
Furthermore, with the advent of generative AI (GenAI), these phishing and BEC attacks are expected to pose an even greater threat. According to a survey by 451 Research S&P Global Market Intelligence, 83% of security leaders express concern about GenAI enabling more advanced phishing and BEC attacks, up from 21% a year ago.3
The need for a comprehensive email security solution is clear, but the threat posed by email-based attacks goes deeper. Given email’s prominent role as the starting point of an attack and/or as part of a multi-stage attack, siloed email security proves to be less effective in combating the dynamic threat landscape. An email security solution’s level of integration with a broader MDR service or XDR platform to provide deep visibility and – optimally – control to SecOps teams provides the best outcomes.
Following multiple enhancements to Sophos Email, the only MDR-optimized email security solution, Sophos is introducing two new offerings to boost email security posture. Sophos EMS provides deployment flexibility and integration into Sophos MDR and XDR, while Sophos DMARC Manager ensures DMARC compliance for improved security and brand trust.
Sophos Email
Sophos Email is the only MDR-optimized email security solution, providing comprehensive email security via a single offering.
- Sophos Email delivers protection against phishing and BEC attacks through multi-layered defenses powered by natural language processing (NLP). With NLP-powered message scanning, phishing and BEC attacks are blocked from inboxes before users can interact with them.
- Sophos Email’s native integration with Sophos MDR and Sophos XDR provides truly unmatched threat visibility, response capabilities, and centralized control for security teams. These capabilities enable security teams to have a holistic view of email telemetry and take actions during critical events.
- Sophos Email also seamlessly integrates with M365 and Google Workspace, enhancing the security posture of organizations’ existing investments.
NEW Sophos Email Monitoring System
Sophos Email Monitoring System (EMS) is an easy-to-deploy, powerful sensor that detects threats other email security products miss and provides unrivaled visibility and control to Sophos MDR and XDR. EMS is not an alternative to Sophos Email – it is designed for customers of third-party email security solutions. By providing a second layer of scanning, EMS also helps evaluate the efficacy of an existing third-party solution.
- Sophos EMS easily deploys on top of any existing email security solution to add a layer of threat identification with zero disruption to existing email flow or security policies. Leveraging 20+ AI/ML models, including NLP, Sophos EMS identifies malicious emails otherwise missed.
- Sophos EMS natively integrates email telemetry into Sophos MDR and Sophos XDR. This native integration provides visibility and control to Sophos MDR and XDR that third-party email security solutions can’t.
- Manual clawback functionality in Sophos EMS allows email administrators and security analysts to remove malicious emails from user inboxes that were missed by the existing third-party solution but identified by EMS.
NEW Sophos DMARC Manager – Powered by Sendmarc
Sophos DMARC Manager is the result of a partnership between Sophos and Sendmarc, one of the leading DMARC solution providers. As a protection add-on for Sophos Email and Sophos EMS customers, Sophos DMARC Manager quickly and easily helps organizations ensure and maintain DMARC policy compliance, an increasingly prominent requirement backed by major email providers, governments, and regulators.
- Sophos DMARC Manager protects an organization’s users by verifying a sender’s identity. This protection prevents two increasingly sophisticated types of phishing and BEC attacks: domain spoofing and impersonation attacks.
- By ensuring an organization’s DMARC compliance, Sophos DMARC Manager helps protect an organization’s brand reputation while improving delivery rates for outbound emails.
- DMARC compliance is an ongoing endeavor. Sophos DMARC Manager’s intuitive dashboards, automated monitoring, and comprehensive reporting simplify the otherwise onerous task of maintaining DMARC compliance.
As email continues to be a primary vector for cyberattacks, organizations must evolve their defenses to meet increasingly sophisticated threats, especially those amplified by generative AI. Sophos’ MDR-optimized email security portfolio, now enhanced with EMS and DMARC Manager, reflects the market’s shift toward integrated, visibility-rich solutions. These additions not only enhance email threat detection and response but also support broader security operations through MDR and XDR integration.
– Monika Soltysik, senior research analyst for Security and Trust at IDC
Source: Sophos
Cybersecurity attacks are rising sharply in 2025, and Microsoft has been one among many prominent targets. Research shows that 70 percent of M365 tenants have experienced account takeovers1 and 81 percent have encountered email compromise2.
To mitigate this ongoing risk, Rubrik and Sophos have formed a strategic partnership to help lean IT teams strengthen their cyber resilience and simplify recovery from ransomware, account compromise, insider threats, and data loss in Microsoft 365.
The new joint solution will make Sophos M365 Backup and Recovery powered by Rubrik the only M365 data protection solution that is fully integrated into Sophos’ powerful cybersecurity console. For customers already relying on Sophos for detection and prevention, this integration provides fast and secure recovery of SharePoint, Exchange, OneDrive, and Teams data when it is accidentally or maliciously compromised.
Rubrik’s SaaS-based protection will be available through Sophos Central—the same platform security teams already trust to manage their defenses.
The Need Now is Greater than Ever
In early 2025, Microsoft 365 commercial (paid seats) surpassed 400 million users. If global admin credentials are breached for any of those millions of users, attackers can manipulate retention settings and permanently delete critical business data.
Native tools were not built for cyber resilience at this scale. Litigation Hold is designed for legal search, not to restore massive amounts of enterprise data. The Recycle Bin is limited and short-term and can’t rewind an entire data estate after an incursion. These kinds of native features can serve specific use cases, but are not sufficient to address enterprise-grade needs. At worst, they provide a false sense of security.
Recovery needs to be fast, granular, and reliable at scale. That’s where Rubrik comes in.
Next-level Cyber Recovery & Resilience
According to The State of Ransomware report by Sophos, only 54% of affected companies impacted by ransomware relied on backups for data restoration, while nearly half of organizations chose a far more costly approach by paying the ransom to recover their data, highlighting a continued gap in effective cyber resilience practices.
The Rubrik/Sophos integration is designed to close this gap in several significant ways:
- Immutable, secure backups: Rubrik will isolate backups from the Microsoft 365 tenant and protect them with air gap architecture, WORM-locked immutability, and customer-held encryption keys. Multi-factor authentication and intelligent data lock will help prevent tampering, even if credentials are compromised.
- Fast, flexible recovery: Customers will be able to search and restore emails, files, folders, shared mailboxes, OneDrives, SharePoint sites, and Teams channels to the original location or another user. Rubrik will support both active and inactive accounts, and deliver high-performance restores using containers orchestrated with Azure Kubernetes Service.
- Automated protection and compliance: Rubrik will automatically discover new users, sites, and mailboxes, apply policy-based protection using Entra ID groups, and offer delegated admin controls. Sophos Central makes this automated protection effortless to manage and will eliminate tedious backup tasks for overburdened admins.
This new functionality will be available within Sophos Central. No new interfaces to learn. No extra tooling. Just a unified experience for both security operations and Microsoft 365 data protection.
Building Cyber Resilience, Together
Working with Rubrik, Sophos will be able to give customers the tools they need to detect, protect, and recover with speed and precision if bad agents break into Microsoft systems. For partners, the Rubrik/Sophos integration will unlock new ways to support customers with an offering that directly aligns to the realities of today’s threat landscape.
Rubrik and Sophos share a commitment to helping organizations operate with confidence in the face of risk. Together, we’re raising the bar for Microsoft 365 resilience.
To learn more or activate the integration, contact your Sophos sales team or a representative.
Source: Sophos
Global Artificial Intelligence (AI) infrastructure spending is projected to surpass $200 billion by 2028, according to research from the International Data Corporation (IDC). As organizations rapidly deploy more complex AI systems, the demand for high-performance infrastructure, like Graphics Processing Units (GPUs) and AI accelerators, is surging. This growth exponentially increases computing power, energy consumption and data exchange across hybrid and cloud environments. However, this rapid expansion of AI infrastructure also increases cybersecurity risks.
Traditional security frameworks are falling short in reducing attack surfaces and securing privileged access. The future of AI requires a modern Privileged Access Management (PAM) solution to protect dynamic cloud environments.
The explosive growth of AI infrastructure
Enterprises are rushing to deploy larger and more powerful systems to keep up with the rapid speed of AI breakthroughs. At the center of this growth is a surge in demand for GPUs, which are crucial for training and running modern learning models. Most AI stacks are highly complex and require significant resources, prompting many cloud providers to invest heavily in AI-specific data centers that can process what traditional infrastructure can’t. Since these centers are designed to sustain advanced workloads, organizations require large amounts of computing power, leading to significant increases in energy consumption. Based on a report from the International Energy Agency (IEA), U.S. AI-specific data centers are expected to account for almost half of the country’s electricity demand growth through 2030 – consuming more energy than all energy-focused manufacturing sectors combined.
In addition to the complexity and energy consumption of AI infrastructure, modern AI stacks are deeply integrated into training pipelines, Application Programming Interfaces (APIs) and datasets, which must interact seamlessly across hybrid and cloud environments for optimal performance. As reliance on AI increases, organizations must maintain performance and scalability without jeopardizing their compliance or overall security posture.
Security risks in AI-driven environments
When AI infrastructure expands, so does the attack surface – the total number of entry points where an unauthorized user could access sensitive systems or data. Potential entry points, or attack vectors, include hardware, GPU clusters, software, APIs and endpoints that can be exploited in a cyber attack. One of the most at-risk attack vectors in AI infrastructure is privileged access.
Privileged users, such as engineers, IT administrators and DevOps teams, typically have elevated permissions across infrastructure used for provisioning and accessing data. If just one privileged account is compromised, cybercriminals can use it to access sensitive systems and even corrupt AI outputs.
Traditional perimeter security is no longer sufficient because relying solely on firewalls or network-based defenses cannot provide full visibility and access control. With a modern PAM solution in place, organizations can shift from traditional security methods to identity-centered security models that prioritize enforcing least-privilege access, session monitoring and continuous validation of both human and non-human users through zero trust.
Why modern PAM is critical
As AI environments grow in size and complexity, a modern PAM solution is essential for securing both human and non-human identities. By implementing a PAM solution, organizations can ensure secrets aren’t hardcoded in scripts or exposed in configuration files. Unlike legacy PAM solutions that were built around traditional IT roles and static infrastructure, modern PAM solutions are designed to scale with cloud-native, AI-driven architectures. When a single compromised credential can lead to widespread access across an organization’s infrastructure, deploying a modern PAM solution gives organizations granular control over privileged access, improves visibility and reduces the attack surface.
To secure complex AI environments, modern PAM solutions deliver critical capabilities such as:
- Just-in-Time (JIT) access: Grants privileged access only when necessary and for a limited duration, eliminating standing access.
- Session monitoring and recording: Tracks all privileged sessions in real time and helps detect suspicious activity with detailed audit trails.
- Secrets management: Securely stores, rotates and manages credentials and secrets used in AI pipelines.
- Zero-trust security: Enforces continuous authentication for every user, device and session before granting access.
Securing the future of AI infrastructure with KeeperPAM
As organizations invest in AI, protecting privileged access must remain a top priority. Traditional PAM tools that once protected legacy systems are no longer able to keep up with the demands of AI environments, specifically regarding privileged access. While organizations focus on investing in AI innovation and training Large Language Models (LLMs), they must also invest in cybersecurity, as failure to control privileged access can compromise sensitive data and systems.
Luckily, KeeperPAM is built with the future in mind. Designed for high-performance, resource-intensive environments, KeeperPAM is a modern, cloud-native PAM solution that scales seamlessly alongside AI workloads.
Request a demo of KeeperPAM today to secure your organization and stay ahead of the risks in AI-driven environments.
Source: Keeper Security
Sophos MDR is the world’s most trusted MDR service, with hundreds of cybersecurity experts providing 24-7 monitoring, prevention, detection, and response to more than 30,000 organizations worldwide.
While Sophos MDR leverages telemetry from across our customers’ environments to detect and neutralize threats, one of the most significant advantages – and a key differentiator of the Sophos MDR service – is our deep integration with Microsoft 365 for all customers regardless of the Microsoft license they’re using.
This enables us to see and stop more threats faster, while increasing customers’ return on their Microsoft investments.
A tale of two APIs: Graph Security vs. Management Activity
Many MDR providers heavily rely on Microsoft’s Graph Security API, which provides strong detection value – but only for customers who have invested in a premium E5 license.
For the vast majority of customers using other Microsoft 365 licenses – such as Business Basic, Standard, or even Premium licenses – the Graph Security API provides minimal telemetry.
At Sophos, we take the distinct and highly effective approach of also extensively leveraging Microsoft’s Management Activity API, which provides rich audit logs from Exchange Online, SharePoint, and other Microsoft solutions.
Crucially, this API is available across nearly all Microsoft 365 license tiers, meaning even Business Basic customers benefit.
Better data, better outcomes
Sophos MDR ingests these logs and applies proprietary threat detection rules developed by our threat intelligence and engineering teams.
These aren’t “off the shelf” detections. They’re custom-built to identify high-risk scenarios such as session hijacking, phishing, business email compromise inbox rule creation, and credential-stuffing.
Faster responses, thousands of times over
This approach operates at scale, with several thousand confirmed threats surfaced each month from Microsoft data – threats that would otherwise go undetected without an E5 license.
Consider a typical scenario: a user clicks a phishing link, completes multi-factor authentication, and an attacker hijacks the session.
The attacker then creates hidden inbox rules to delete or redirect emails that would otherwise alert the user to suspicious activity such as invoice fraud.
Because the Microsoft Management Activity API sends all the Microsoft 365 audit logs to the Sophos data lake, Sophos detections are able to flag this behavior based on patterns learned from the audit logs – patterns such as multiple operating systems using the same session or known phishing kit indicators of compromise.
More than just detection
While our deep Microsoft integration is a prime example of how Sophos extends protective capabilities, we don’t stop at detection: Sophos MDR can respond natively within the Microsoft environment.
With the customer’s permission, Sophos MDR analysts can take immediate action to remediate threats in Microsoft 365.
Revoking sessions, blocking user sign-ins, and disabling malicious inbox rules – all without requiring customer interaction.
We conduct many hundreds of these automated response actions every month, with hundreds more executed manually when needed.
Learn more
Sophos brings unique, impactful, and rapid response capabilities to Microsoft environments, even for customers on Microsoft 365 basic license plans.
It’s better cybersecurity and a better return on investment.
Visit Sophos.com/MDR-Microsoft for more information.
Πηγή: Sophos
Sophos is proud to announce that we have been named a Leader in the 2025 Frost Radar™: Managed Detection and Response. This recognition is a testament to our relentless focus on innovation, stopping threats cold, and helping customers stay ahead in an ever-changing threat landscape.
 Published by Frost & Sullivan, the Frost Radar is an industry benchmark that evaluates vendors on two dimensions: Innovation and Growth. This year’s report recognizes Sophos for its open-platform approach to MDR, unmatched incident response capabilities, and strong market momentum.
Published by Frost & Sullivan, the Frost Radar is an industry benchmark that evaluates vendors on two dimensions: Innovation and Growth. This year’s report recognizes Sophos for its open-platform approach to MDR, unmatched incident response capabilities, and strong market momentum.
Supercharging this momentum is our acquisition of Secureworks and a sharp focus on AI, threat intelligence, and customer-driven innovation.
“Sophos’ acquisition of Secureworks represents one of the most important mergers in the history of MDR.”
— Frost & Sullivan, Frost Radar™: Managed Detection and Response, 2025
What makes Sophos a Leader?
Sophos MDR protects more than 30,000 organizations around the world, from lean IT teams to global enterprises. It’s a fully managed service that pairs powerful detection technologies with a world-class team of threat analysts and incident responders across seven global security operations centers. With 24/7 monitoring, threat hunting, and response across endpoint, network, cloud, and identity layers, Sophos MDR is built to adapt to what you need, regardless of whether you’re looking to fully outsource your SOC or strengthen your internal team with expert support.
There were several key factors that Frost noted which elevated Sophos into the top right of this year’s Radar:
Innovation that drives results
- Open-platform visibility: Sophos MDR integrates natively with our own portfolio and with over 350 third-party tools, covering Microsoft 365, Google Workspace, and more.
- Unlimited expert-led incident response: Included with the Sophos MDR Complete service tier, this provides peace of mind without caps or hidden fees.
- AI-powered investigations: Our natural language AI assistant streamlines triage, case summaries, and provides recommendations.
- CTEM-aligned services: Built-in capabilities for exposure management, threat intelligence, and proactive risk mitigation.
- Secureworks opportunity: The acquisition brings in OT visibility, dark web monitoring, and threat intelligence from the Counter Threat Unit (CTU), all integrated into a unified platform.
Recent enhancements to Sophos MDR have sharpened our edge even further. In May 2025, we introduced expanded response actions for Microsoft 365 attacks, enabling MDR analysts to directly contain and remediate threats inside customer M365 environments. We also launched a strategic partnership with Capsule to help customers lower cyber insurance barriers by demonstrating observable MDR controls. Most recently, in July 2025, we unveiled Internal Attack Surface Management (IASM) as part of Sophos Managed Risk, giving organizations unprecedented visibility into vulnerable assets and misconfigurations inside their environment, and further aligning MDR with proactive security principles like CTEM.
Sophos MDR has also been recognized by those who matter most – our customers.
Sophos was recently named a “Customers’ Choice” vendor in the second Gartner® Peer Insights™ Voice of the Customer for Managed Detection and Response (MDR). G2, a major technology user review platform, also released its Summer 2025 Reports, and Sophos ranks as the No. 1 overall MDR solution.
Looking ahead
Being named a Leader in the Frost Radar™ validates the strength of our strategy, the depth of our capabilities, and the value we deliver to customers, but we won’t stop there.
We are committed to continuing our momentum and building the most intelligent, flexible, and integrated MDR platform on the market. Our goal remains the same: helping customers stay ahead of threats and build resilient, proactive security operations.
To learn more about Sophos’ recognition in the 2025 Frost Radar™ for Managed Detection and Response, read the full report here.
Source: Sophos
SE Labs has published its Q2 2025 Endpoint Protection report, and we’re delighted to share that Sophos Endpoint has once again received AAA ratings in the SE Labs Small Business and Enterprise protection tests.
We’ve consistently received AAA SE Labs test awards for the past three years by detecting and stopping real-world cyberattacks and simulated targeted attacks.
Here are the links to the latest reports: Endpoint Security: Small Business | Endpoint Security: Enterprise
The industry’s most sophisticated endpoint security solution
Sophos Endpoint, powered by Intercept X, takes a comprehensive, prevention-first approach to security, blocking threats without relying on any single technique. Multiple deep learning AI models secure against known and never-before-seen attacks.
Web, application, and peripheral controls reduce the customer’s threat surface and block common attack vectors. Behavioral analysis, anti-ransomware, anti-exploitation, and other advanced technologies stop threats fast before they escalate, so resource-stretched IT teams have fewer incidents to investigate and resolve.
Why testing matters
Reputable third-party testing is a crucial tool that enables organizations to make informed decisions about their technology stacks and security investments. However, as attacks increase in volume and complexity, meaningful results can only be achieved when the tests reflect organizations’ real-world realities.
SE Labs is one of the few security testers in the industry that simulates modern-day attack tools, tactics, techniques, and procedures (TTPs) currently used by cybercriminals and pen testers.
Sophos has been participating in their evaluations for many years, consistently receiving top scores in SE Lab’s endpoint security tests in both Enterprise and SMB categories.
SE Labs Awards
This award comes on the heels of winning four awards in this year’s SE LABS ® Awards 2025. The accolades – presented July 2nd in London – validate our commitment to protecting organizations of all sizes by delivering superior cybersecurity outcomes to our customers amid constantly evolving threats.

More accolades for Sophos Endpoint
Consistency is important! When helping an organization choose a security provider, it’s helpful to provide them with multiple viewpoints to help them make an informed decision. To see why customers choose Sophos, visit www.sophos.com/why for a summary of analysts’ views and reports, reputable third-party testing, and the opinions of customers and partners who use our products daily.
- 16x a Leader: For the 16th consecutive time, Sophos has been recognized as a Leader in the 2025 Gartner Magic Quadrant for Endpoint Protection Platforms (EPP).
- Sophos has also been named a “Customers’ Choice” vendor in the 2025 Gartner® Peer Insights™ Voice of the Customer Report for Endpoint Protection Platforms for the fourth consecutive year and in the inaugural Voice of the Customer Report for Extended Detection and Response.
- Sophos is – once again – the only vendor named a Leader across the G2 Overall Grid® Reports for Endpoint Protection Suites, Endpoint Detection and Response (EDR), Extended Detection and Response (XDR), Firewall Software, and Managed Detection and Response (MDR). Based on user feedback, Sophos was ranked the #1 solution in 36 individual reports spanning the Antivirus, EDR, Endpoint Protection Suites, XDR, Firewall, and MDR markets.
Source: Sophos
In 2024, we became one of the first organizations to commit to CISA’s Secure by Design initiative. Aligned with our core organizational values around transparency, Secure by Design has been a guiding force as we continually evaluate and improve our security practices.
We recently passed the one-year anniversary of publishing our pledges for improvement and would like to publicly share the progress we have made against the seven core pillars of the Secure by Design framework.
I’m proud of the progress we’ve made this year but, of course, plans change and we haven’t fully-realized every goal yet. So expect further updates and, very soon, a fresh set of additional commits for the year ahead.
Our pledges: A year in review
Multi-factor authentication (MFA)
Our 2024 pledge:
We pledge to release passkey support in Sophos Central and publish adoption statistics for this stronger MFA mechanism.
How did we do?
In November 2024, we launched passkey support to all customers using Sophos Central. This strategic step was aimed at enhancing authentication security through a phishing-resistant, passwordless login experience. Since its launch in December 2024, we’ve seen strong adoption, with over 20% of all authentications to Central now utilizing passkeys.
In addition to launching passkey support, we went a step further and now prevent the use of legacy MFA mechanisms such as SMS. Users of Central who rely on these legacy mechanisms are required to enrol in either a Time-based One-Time Password (TOTP) or passkey-based MFA during their next login.
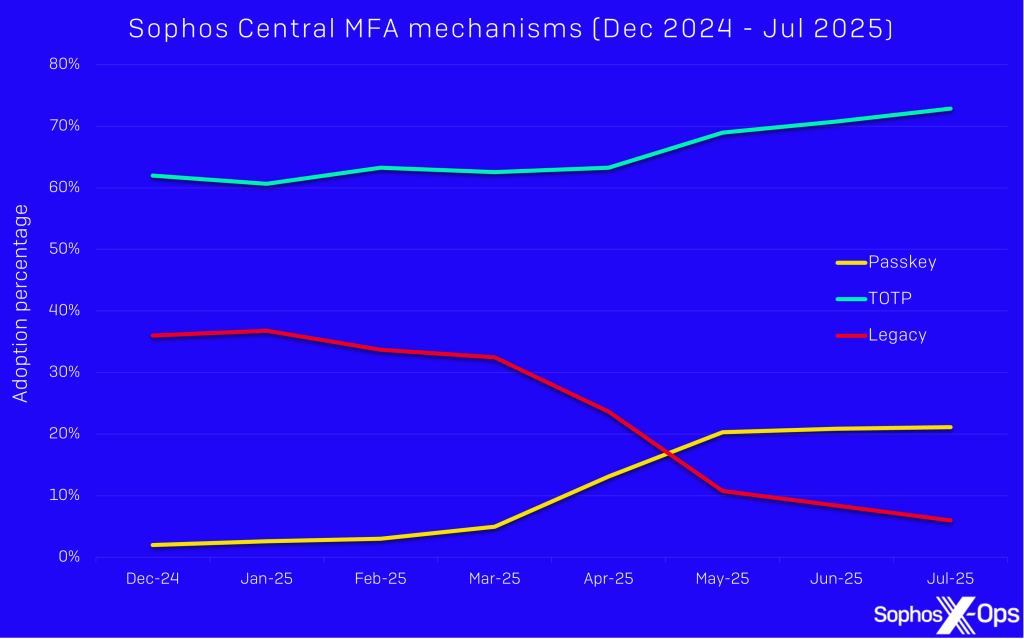
Figure 1: Adoption of Sophos Central MFA mechanisms between December 2024 and July 2025
Default passwords
Our 2024 pledge:
We pledge to continue to disallow default credentials in all current and future products and services.
How did we do?
We have maintained this design principle and will continue to do so in our product development. Sophos products generate strong unique credentials, or require users to provide complex passwords upon setup, to help reduce the likelihood of unauthorized access.
Reducing entire classes of vulnerability
Our 2024 pledge:
In Sophos Firewall v21 (SFOS v21), we pledge to containerize key services related to Central management to add additional trust boundaries and workload isolation. Additionally, SFOS v22 will include an extensive architecture redesign, which will better containerize the Sophos Firewall control plane, further reducing the likelihood and impact of RCE vulnerabilities.
How did we do?
We are taking a risk-based prioritized approach to containerized workloads and have provided better workload isolation in the Sophos Firewall. Starting with the most important and exposed services, the releases of SFOS v21 and SFOS v21.5 included the first of these improvements . We will share details of the progress we are making with the Sophos Firewall control plane rearchitecture for SFOS v22 in a follow-up article, since it won’t be released until later in 2025.
Security patches
Our 2024 pledge:
Running the latest firewall firmware version offers additional security benefits beyond receiving security hotfixes by default. With this in mind, we pledge to release a feature by September 2025 that enables customers to automatically schedule Sophos Firewall (SFOS) firmware updates.
How did we do?
Sophos plans to include the ability to automatically schedule firmware updates with the release of SFOS v22 when it’s released later in 2025. Helping our customers keep their Sophos Firewall firmware up to date is a priority to us to help keep them secure. Currently, 99.41% of our customers’ firewalls benefit from automatically receiving OS-level hotfixes as they are released, thanks to the wide adoption of our automatic hotfix deployment feature.
Vulnerability disclosure policy
Our 2024 pledges:
-
Increase transparency and add to collective industry knowledge by publishing blog posts that review findings and lessons learned from our vulnerability disclosure program
-
Increase the maximum reward available to security researchers.
How did we do?
Since our last post in June 2024, we have continued to invest in our public bug bounty program and the great work that researchers share with us. This year alone we have reviewed more than 800 bug bounty submissions for Sophos products. We have rewarded over $500,000 USD to the researcher community since we started the program back in December 2017 . Today, Sophos ranks among the top Bugcrowd vendors offering the highest rewards per valid finding.
To help incentivize and increase the likelihood of finding critical vulnerabilities which could impact Sophos products, we have made a few key improvements this year which align to our pledges:
- We increased the maximum reward possible for our Windows Intercept X product by $20,000 USD; researchers can now earn $80,000 USD for a P1 submission
- We added a new reward which pays up to $50,000 USD for a P1 finding in Central
- We extended our premium bug bounty scope to include monetary rewards for valid vulnerabilities identified in Taegis and Redcloak, following Sophos’ acquisition of Secureworks earlier in 2025.
We have launched a new dedicated Root Cause Analysis (RCA) section on our Sophos Trust Center, where we have published RCAs from recent incidents. Additionally, we plan to share insights and lessons learned from our bug bounty program in a follow-up post later this year.
CVEs
Our 2024 pledge:
We pledge to extend our internal processes to consistently publish external CVEs for all identified internal vulnerabilities of a severity of high or critical in our products.
How did we do?
We have met this pledge by expanding our internal processes to ensure that any vulnerability identified internally and assessed as high or critical severity is prepared for external CVE publication. Although no vulnerabilities have yet been identified which meet this threshold for publication, the updated processes are fully in place and ready to support consistent and transparent disclosure going forward.
Transparently publishing CVEs for internally discovered issues helps our customers better understand the security posture of our products, supports informed decision-making, and reflects our commitment to industry best practices.
Evidence of intrusions
Our 2024 pledge:
We pledge to provide additional integration capabilities in Sophos Central to simplify the ingestion of audit logs into third parties, with target implementation prior to July 2025.
How did we do?
While we have made foundational progress toward this goal, we’ve had to adjust the timeline to reflect the significant organizational changes and new product opportunities resulting from our acquisition of Secureworks earlier in 2025.
We remain fully committed to this pledge and will continue to provide updates as we roll out improvements.
Next steps
Having reviewed our progress against the commitments we made last year, we’re now focused on the road ahead. In the near future, we’ll share the updated pledges we’re making for the coming year— building on what we’ve learned, where we’ve advanced, and where we still have work to do. Our mission remains the same: to continuously strengthen the security, transparency, and trustworthiness of our products, in alignment with the Secure by Design principles.
Source: Sophos
Sophos has been recognized for defending customers of all sizes against today’s complex cyberattacks, achieving four prestigious awards at the SE Labs Awards 2025.
We’re thrilled to announce that Sophos won four awards in this year’s SE LABS ® Awards 2025. The accolades – presented July 2nd in London – validate our commitment to protecting organizations of all sizes by delivering superior cybersecurity outcomes to our customers amid constantly evolving threats.
 SE Labs Award for Enterprise Endpoint (Windows)
SE Labs Award for Enterprise Endpoint (Windows)
This award recognizes the most effective and reliable endpoint protection solution for enterprise environments running Microsoft Windows. Recipients have demonstrated superior threat detection, operational stability, and resilience against targeted attacks, verified through SE Labs’ independent testing framework.
 SE Labs Award for Small Business Endpoint (Windows)
SE Labs Award for Small Business Endpoint (Windows)
Tailored for the needs of smaller organizations, this award celebrates endpoint security products that provide strong out-of-the-box protection, ease of management, and robust real-world defense for Windows-based networks, without requiring enterprise-level resources to operate effectively.
 SE Labs Award for Small Business Managed Service Provider Solution
SE Labs Award for Small Business Managed Service Provider Solution
With many small businesses relying on external partners to deliver cyber security expertise, this award highlights the top-performing products that are available to MSPs – products that deliver managed endpoint protection with clarity, efficiency, and measurable results. Winners have proven their capability to scale security services and respond rapidly to threats.
 SE Labs Award for Small Business Security Innovator
SE Labs Award for Small Business Security Innovator
Innovation is critical in an evolving threat landscape. This award recognizes a standout vendor or service provider pushing the boundaries of small business cyber security. Whether through breakthrough technology, creative service models, or agile threat response strategies, this honor is reserved for those reshaping the future of SME security.

The awards are judged based on a combination of continual public testing, private assessments, and feedback from SE Labs’ corporate clients.
“Behind every high performing security product is a team committed to excellence”, says Simon Edwards, Founder and CEO of SE Labs.”We believe that we should celebrate the technologies and teams pushing the boundaries in protection and resilience against cyber attacks. The standard of competition for the top place in each category has been very high this year and all of our winners are to be congratulated.”
Sophos is now the largest pure-play Managed Detection and Response (MDR) provider, supporting more than 28,000 organizations. Sophos Endpoint defends more than 300,000 organizations worldwide against advanced attacks, with an AI-powered prevention-first approach, airtight ransomware protection against local and remote ransomware, adaptive defenses, and other innovative technologies. The solutions are powered by historical and real-time threat intelligence from Sophos X-Ops, protecting over 600,000 Sophos customers worldwide.
Why testing matters
Reputable third-party testing is an important tool to help organizations make informed decisions about their technology stack and security investments. However, as attacks increase in volume and complexity, meaningful results can only be achieved when the tests reflect organizations’ real-world realities.
SE Labs is one of the few security testers in the industry that simulates modern-day attack tools and tactics, techniques, and procedures (TTPs) that cybercriminals and penetration testers are currently using.
Sophos has been participating in their evaluations for many years, consistently receiving top scores in SE Labs’ endpoint security tests for enterprise and SMB.
It’s awards season
These awards follow Sophos’s recognition as a Customers’ Choice vendor in the 2025 Gartner® Peer Insights™ Voice of the Customer Reports for Endpoint Protection Platforms and Extended Detection and Response. This makes Sophos the only vendor to be named a Customers’ Choice in both reports, highlighting the comprehensive, robust protection of the Sophos platform.
Sophos has been named a Leader in the 2025 Gartner Magic Quadrant for Endpoint Protection Platforms (EPP) for the 16th consecutive time.
When helping an organization choose a security provider, it is helpful to provide them with multiple viewpoints to assist them in forming an opinion. To see why customers choose Sophos, navigate to www.sophos.com/why for a summary of analysts’ views and reports, reputable third-party testing, and the opinions of customers and partners who use our products daily.
Source: Sophos
Cybercriminals are getting faster at exploiting security gaps. The median dwell time observed by Sophos in the past year was a short two days.
Keeping pace with these agile threat actors leaves little room for forward thinking, but decisions made today will shape your organization’s ability to respond to tomorrow’s threats. The strategies below will help your organization build the right foundations for a cybersecurity program that stands the test of time.
1. Understand the threat landscape
From organized crime to hacktivists and state-sponsored actors, today’s threat landscape is complex and fast-moving. The starting point of a successful cybersecurity strategy is a deep understanding of this shifting threat landscape.
It’s only from here that you can appreciate your organization’s unique security gaps and take the right actions to bolster your defenses. But how do you stay up to date with an ever-changing threat landscape?
Ongoing vigilance
Understanding the threat landscape is a 24/7 endeavor, involving continuous monitoring and analysis of threat actor activity. Thankfully, organizations don’t have to go it alone. A trusted security partner can provide the expertise, processes, and technology to help organizations gain a better understanding of common attack vectors, techniques, and tactics, and how these are evolving in relation to your business.
Comprehensive visibility
To understand your risks in context and address them as they evolve, you need broad visibility across the attack surface. An open extended detection and response (XDR) platform will help you gain a holistic view of your systems, data, and processes and minimize the risk of threats slipping through the cracks.
Threat intelligence
Comprehensive intelligence is critical to a dynamic and resilient security posture, helping organizations anticipate and mitigate emerging threats. Effective threat intelligence systems leverage human expertise, AI, and analytics to analyze attack patterns and refine strategies continuously. Armed with actionable insights, forecasts, and recommendations, organizations can prepare for the worst — in the best way possible.
Sophos’ Active Adversary report shows the kind of intelligence that empowers our customers to continuously outpace and outmaneuver adversaries.
2. Look at threats in context
Context is key to understanding and applying what you learn from threat intelligence. Insights from intelligence, combined with relevant business information, provide the context you need to make informed decisions. After all, threats don’t happen in isolation.
They impact, and are influenced by, the unique environment in which your organization operates. This includes everything from business priorities, supply chain dependencies, and IT systems to regulatory challenges and socioeconomic issues. Contextualizing threats with insights on internal and external factors enhance your organization’s ability to anticipate and mitigate attacks.
Why context matters
- Prioritize what matters most: Not all assets are created equal. Context is key to cutting through the noise and focusing time and resources where they’re needed most.
- Develop targeted strategies: Deeper contextual understanding helps you identify high-risk areas and develop more precise mitigation strategies.
- Apply technology wisely: Applying technology in context enhances efficiency and effectiveness. By tailoring tools and protocols to your specific needs and business conditions, it’s easier to prioritize threats and develop mitigation strategies.
3. Leave room for change
Cybercriminals are masters of reinvention, continuously changing tack to survive and thrive in hostile surroundings. Keeping pace — and getting ahead — means beating them at their own game with a cybersecurity strategy that’s as agile and adaptive as the threats you’re counteracting.
A security program with built-in flexibility and scalability will grow seamlessly with your business and stay constantly aligned with evolving conditions.
How to foster adaptability
- Adopt agile technology and practices: Implement scalable solutions and agile methodologies to enhance responsiveness and drive continuous improvement in dynamic threat environments. Invest in training and resources that foster employee adaptability.
- Use intelligence to get ahead: Leverage real-time intelligence to make more proactive and informed decisions. Adapt your policies, tools, and protocols based on data-driven insights so you can seamlessly pivot your defenses as new threats arise.
- Share real-time insights for real-time adaptability: Keep employees continuously updated on emerging threats and tactics, so they’re able to better anticipate and adapt to risks. Share insights and best practices with partners and industry groups to gain a broader view of the threat landscape and proactively modify your defenses.
4. Don’t underestimate the human factor
Cybersecurity is as much about people as technology. Managing the risks and rewards of what makes us human is critical to cyber resilience.
On the one hand, human expertise adds a vital layer of security to your tech-based defenses. Conversely, when training and awareness are lacking, employees can quickly become a gateway to cyberattacks: 63% of organizations fell victim to ransomware due to lack of expertise/people according to Sophos’ State of Ransomware Report 2025.
Mitigating risk is essential, but not at the expense of human skills like problem-solving, collaboration, and resilience — all indispensable in a robust cybersecurity strategy.
How to manage human strengths and vulnerabilities
- Mitigate human error: “To err is human” but the responsibility for mitigating this risk lies with organizations. Establish clear policies, multi-factor authentication (MFA), and consistent training to help reduce the risk of accidental missteps.
- Nurture “people power”: Cultivate the uniquely human skills that help your people find creative solutions to complex problems. Empower employees with tools and resources that enhance their natural abilities. Organizations that invest in nurturing human talent will be better equipped to adapt to an evolving threat landscape.
- Build a positive cybersecurity culture: Reinforce the importance of cybersecurity through peer influence and leadership buy-in. Reward positive outcomes and create a safe space where employees can report incidents without fear of reprisal.
5. Work on your speed and agility
Speed and agility are non-negotiable in today’s threat landscape as dwell times shorten and cybercriminals get increasingly creative.
Threat actors now have AI on their side, helping them to scale and strike faster — and they have the technology, infrastructure, and resources to continuously adapt and pivot. All of this increases pressure on organizations to detect and respond to threats with greater speed and agility.
How to stay ahead
- Accelerate response times: Reduce the time it takes to detect and respond to a threat to minutes, not hours or days. Take advantage of industry-leading tools and expertise to automate workflows, speed analysis, and accelerate responses. Deploy technologies such as extended detection and response (XDR), endpoint detection and response (EDR), next-gen security information and event management (SIEM), and security orchestration, automation, and response (SOAR) tools. You can also extend your SOC team by partnering with a managed detection and response (MDR) provider that ensures 24/7 coverage.
- Use AI and automation: Beat adversaries at their own game with AI-driven tools and automated systems. Spot anomalies faster and swiftly manage intrusions, automating routine tasks and using predefined playbooks.
- Build flexible security frameworks: Use adaptive security tools with integrated real-time intelligence to quickly anticipate threats and modify strategies and protocols. Deploy solutions that integrate seamlessly with your existing systems to create a security framework that’s as proactive and dynamic as the threats you face.
As the threat landscape evolves with increasing speed and sophistication, so too must the strategies that secure your long-term mission. At Sophos, we help organizations future-proof their defenses with:
- 24/7 security monitoring, detection, and response
- Access to threat experts who can help respond to an active incident
- Industry-leading threat intelligence
- Flexible and scalable solutions
- An open platform that integrates with your existing IT tech stack
With the right mix of technology, intelligence, and expertise, an uncertain future doesn’t have to be an unsafe one. Talk to our experts today to find out how we can help you build a resilient and adaptive cybersecurity strategy.
Source Sophos