News
In the rapidly evolving landscape of cyber threats, artificial intelligence is no longer a luxury: it’s a necessity. At Sophos, we recognized this reality early: we’ve been integrating sophisticated AI capabilities across our product portfolio since 2017.
This deep, practical expertise has allowed us to build the industry’s largest AI-native security platform, combining both predictive machine learning (ML) and revolutionary generative AI (GenAI) to deliver faster detection and smarter, more automated responses.
However, power requires principle. Our long-standing commitment to leveraging AI for defense is governed by a framework designed to ensure that our technologies are not only effective but are also developed and deployed with the highest standards of safety, ethics, and trust.
The six pillars of our responsible AI framework
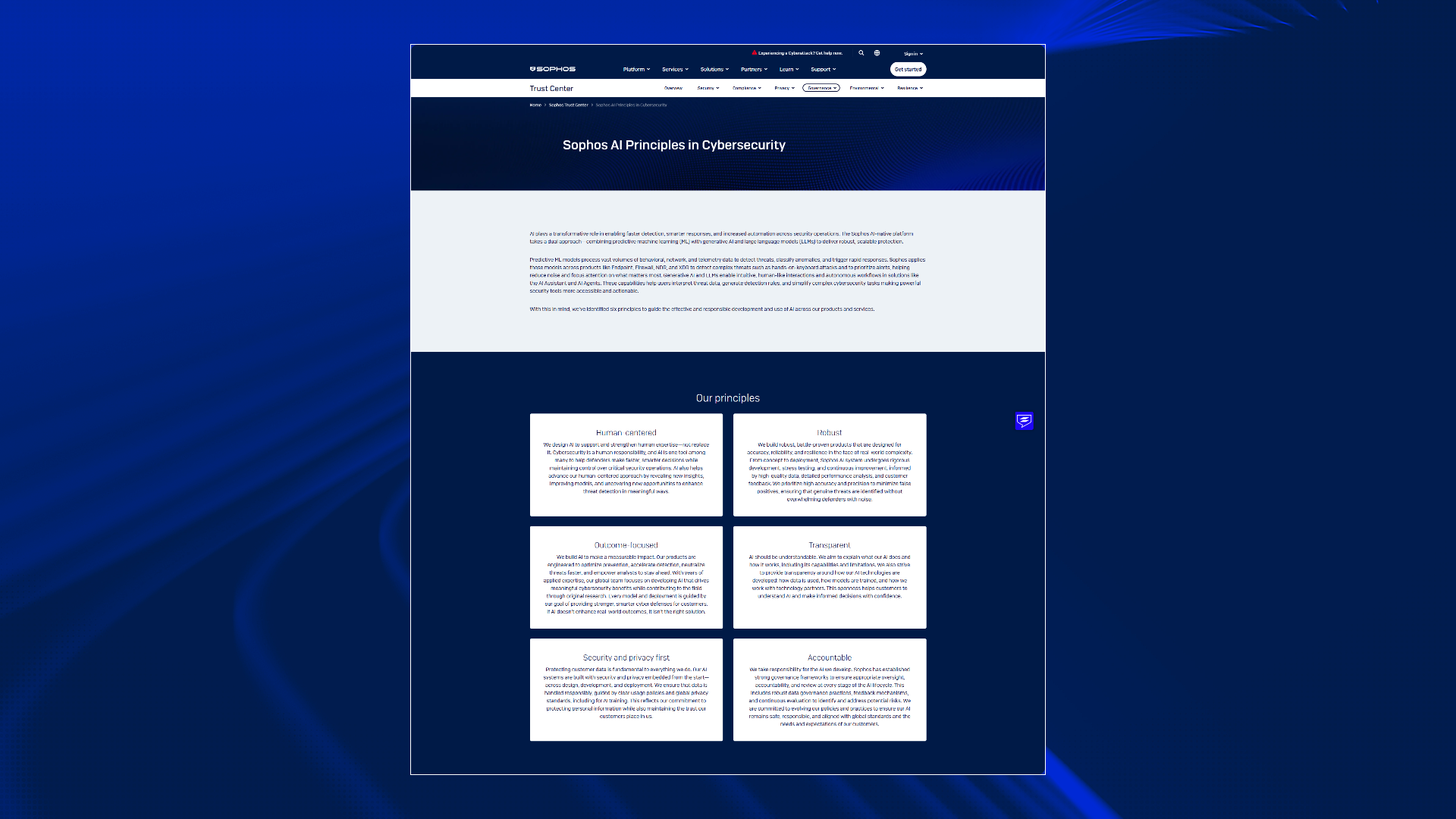
Our approach to responsible AI in cybersecurity is built on six core principles, which guide every phase of development, deployment, and monitoring:
- Human-centered: We design AI to enhance human expertise, not replace it. Our tools are built to support security analysts, allowing them to make faster, smarter decisions while maintaining full control over critical security operations.
- Robust: Our models undergo rigorous development, stress testing, and continuous improvement, ensuring high accuracy and precision to minimize false positives and maintain resilience against real-world complexity and adversarial attacks.
- Outcome-focused: We measure success by real-world impact. Our AI is engineered to optimize prevention, accelerate detection, and neutralize threats faster, focusing on measurable cybersecurity benefits for our customers.
- Security and privacy first: Protecting customer data is paramount. Our systems are built with security and privacy embedded from the start, guided by clear usage policies and global standards. Crucially, we do not share customer data to train third-party large language models (LLMs).
- Accountable: We have established strong governance frameworks with clear roles and oversight to manage risk and review our AI systems at every stage, ensuring we take full responsibility for the technology we develop.
- Transparent: Effective security partnership requires understanding the tools you rely on. We strive to explain what our AI does and how it works, including its capabilities and, importantly, its limitations. We provide clarity around how our AI technologies are developed, including how data is utilized for training our proprietary models, and how we work with technology partners.
Sophos continues to leverage the transformative power of AI to defeat cyberattacks. By anchoring our innovation in a steadfast commitment to human oversight, robust engineering, and complete transparency, we ensure our technologies remain a trustworthy and powerful asset in the global fight against cybercrime.
This openness, through product documentation and governance practices, empowers our customers to make informed decisions and assess the suitability of our AI solutions for their unique needs.
In that spirit, we invite you to further review our AI Principles in Cybersecurity and Responsible AI FAQs web pages, both located in the Sophos Trust Center.
Source: Sophos
Ransomware attacks are evolving faster than ever. For already stretched IT and security teams, staying ahead can feel impossible, but it doesn’t have to be.
The right combination of firewall and endpoint security can stop ransomware before it spreads and restore confidence at the edge of your network.
To help organizations navigate this shifting threat landscape, Chris McCormack, Sophos Network Security Specialist, presented how integrated defenses built on Sophos Firewall and Sophos Endpoint can reduce risk and rebuild trust. Here are five key takeaways from our recent webinar, “Rebuilding Trust at the Edge: A Smarter Approach to Firewall Security.”
Reduce your attack surface
Every exposed system is a potential entry point. Consolidating and securing infrastructure limits opportunities for attackers — and makes your defenses simpler and more effective.
“The best practices to prevent being attacked or targeted in the first place are perhaps most important,” McCormack said during the webinar. “These reduce your surface area of attack or risk of being attacked, which is largely focused on things like minimizing exposed infrastructure and ensuring that what you do have that’s exposed is hardened so it’s not an attractive target — or at least not as attractive as the next vendor.”
Start by identifying everything that is exposed to the internet and removing what’s unnecessary, and hardening what must remain. The fewer targets you present, the harder it is for attackers to get in, and the easier it is for your team to defend.
Design systems to be secure from the start
Security shouldn’t be bolted on — it should be built in. Systems exposed to the internet must be configured correctly, continuously updated, and hardened against attacks.
“Make sure you look for a vendor that can provide automatic over-the-air updates or critical patches that don’t require you to lift a finger,” McCormack said. “You shouldn’t have to schedule a firmware upgrade or reboot your network every time there’s a new vulnerability discovered.”
Sophos Firewall’s automated patching, strong default policies, and cloud-managed configuration through Sophos Central simplify security operations for even small IT teams. Enforcing strong passwords, enabling multi-factor authentication, and applying zero-trust principles are baseline controls that keep intruders out.
Adopt Zero Trust Network Access (ZTNA)
Traditional VPNs assume trust once a connection is made. ZTNA flips that model — no user or device is trusted by default.
Sophos ZTNA verifies identity and device health before granting access, dramatically reducing the risk of lateral movement if an attacker gets ahold of credentials.
“I can’t stress enough the importance of utilizing [ZTNA], which is all about trusting nothing and verifying everything,” McCormack said. “Credential theft [is] a key root cause of ransomware attacks. That’s because many firewalls, many organizations, and network security are trusting that if you have those credentials, we trust you. ZTNA solves this problem.”
Integrated through the Sophos Central platform, Sophos Zero Trust Network Access (ZTNA) offers unified visibility and control over users, devices, and applications — from a single pane of glass. It is a smarter, more secure way to connect remote users and ensure every interaction with your network is legitimate.
Don’t let encrypted traffic hide threats
With most internet traffic now encrypted, attackers use it to mask their movements.
Sophos Firewall uses intelligent TLS inspection and AI-powered analysts to reveal hidden threats — without compromising performance.
“There are technologies out there now that you can use that leverage AI to discover encrypted threat communications and network traffic without you actually having to do the heavy lifting of decrypting that traffic,” he said.
By combining deep packet inspection with insight from Sophos X-ops threat intelligence, Sophos Firewall detects and blocks malware, command and control traffic, and exploits within encrypted sessions — ensuring attackers cannot hide in plain sight.
Detect and respond to active threats — Fast
Even with strong defenses, incidents can still happen — and speed is everything.
Segment your network to contain threats, monitor east-west traffic with Sophos Network Detection and Response (NDR), and unify response through Sophos Extended Detection and Response (XDR).
“Technologies like NDR are typically something you would only find in large enterprise networks, but we’re making it available to everyone and for free,” McCormack said. “So, if a threat is detected by any of our products or an analyst, that information is shared immediately with all other software, and the response kicks off automatically.”
Sophos XDR and NDR work together to give complete visibility across endpoints, firewalls, and email by correlating data to spot suspicious behavior, isolating compromised devices, and stopping attackers in their tracks. This synchronized defense, powered by real-time intelligence, gives security teams enterprise-grade speed and confidence.
Source: Sophos
SealPath, a leading provider of data-focused security and digital rights management, announces the launch of its new product “SealPath Data Classification powered by Getvisibility”.
By utilizing the latest in Artificial Intelligence and Machine Learning technology, it provides its customers with advanced data visibility, protection, control, and dynamic understanding solutions as they are created.
This innovative tool, enhanced with AI for data classification and automatic protection of labeled information, provides the technology that corporate clients need to classify data securely and accurately throughout its lifecycle. This way, organizations from any sector gain the ability to prevent data leaks and comply with the strictest data protection regulations.
With SealPath’s classification, the user receives suggestions on the classification level when creating and editing a document. The software learns and adapts to different types of documents, continuously improving its accuracy through AI, and allows organizations to classify unstructured information with unprecedented confidence.
SealPath information protection is 100% integrated with the new intelligent data classification system, so those files labeled with a specific classification level or subject to specific regulation can be protected automatically and without user intervention.
“SealPath Data Classification powered by GetVisibility was born in response to the obsolete technologies that many companies are currently using to classify and manage their data. The solution’s machine learning models have been previously trained for years through data containing a wide range of document types, from personal, medical, and financial information, and different market verticals. These meticulously trained models, combined with robust software specialized in data classification, minimize human error, costs, and time in labeling corporate information. We hope that this new solution completely transforms the way organizations classify and protect their information,” says Luis Ángel del Valle, CEO of SealPath.
SealPath Data Classification employs a flexible approach, considering different dimensions like data sensitivity, associated regulations (PCI, GDPR, CMMC, etc.), data types, and distribution scope. In this way, the system can adapt the classification to the organization based on the aforementioned dimensions.
SealPath’s protection, along with the AI and Machine Learning classification system, streamlines an organization’s efforts to prevent data classification errors quickly and cost-effectively.
Learn more about SealPath Data Classification here.
Source: Sealpath
We’re excited to share that Silverfort is named as an Example Vendor in the 2025 Gartner A Well-Run Active Directory Requires Strong Identity Controls, authored by Paul Rabinovich, May 2025.
Silverfort is proud to be recognized as an Example Vendor in three key areas of the report:
- Implement MFA to Resources Integrated with AD
- Implement Identity Posture Management and Identity Threat Detection and Response (ITDR)
- MFA Integration Options for AD-Bound Legacy Applications (Authentication Forwarding Solutions)
As organizations race toward the future of the cloud, Active Directory remains one of the most challenging assets to protect. It’s deeply embedded in enterprise infrastructure, and while companies modernize, securing AD and other legacy systems can’t be an afterthought. They still hold the keys to critical access and remain prime targets for attackers.
Silverfort helps organizations secure every identity—human, machine and AI—from legacy to cloud, including the systems that traditional tools can’t cover.
Active Directory security demands strong identity controls
AD has long been the backbone of enterprise identity—and a prime target for attackers.
While AD remains critical, too many organizations are leaving it exposed to credential compromise, lateral movement and privilege escalation.
How Silverfort puts Gartner’s framework into action
Silverfort helps organizations put these best practices into action. Our identity security platform extends modern identity security to AD authentication paths, including systems and protocols traditional identity and access management (IAM) tools can’t reach.
Silverfort delivers MFA protection to every resource and access path, including homegrown applications, command-line tools, legacy systems, and OT environments, while continuously analyzing every authentication across AD and Entra ID for risky behavior.
With Silverfort’s Non-Human Identity (NHI) Security, organizations can discover all NHIs across AD and cloud, map their behavior and risk, and enforce real-time protection for AD service accounts through virtual fencing policies. By combining adaptive MFA, identity security posture management (ISPM), and real-time identity threat detection and response (ITDR), Silverfort helps secure the heart of enterprise identity from the attacks that target it most—all without any infrastructure changes.
Leading the next era of Identity Security
Identity is the new security perimeter, and AD remains central. As environments become more hybrid and threats more sophisticated, organizations need visibility into every authentication, real-time threat detection, and inline, risk-based enforcement for both human and non-human identities.
That’s the evolution Silverfort leads. By integrating seamlessly with both AD and cloud identity providers, Silverfort delivers the most compete security across all types of identities (including human, machine, and AI agents), systems, and applications.
With Silverfort, identity and security teams can work together to enforce MFA protection, continuous risk assessments, ISPM, and ITDR from a unified platform, securing every authentication without disrupting users or infrastructure. This approach embodies the same principles Gartner outlines in its framework: building strong, layered identity controls that protect AD today while preparing for the future of hybrid identity.
Source: Silverfort
In the last few articles on the topic of our latest Sophos Firewall release, we’ve discussed the importance of Secure by Design and covered one of the highlights of this release: the new Health Check feature. There are also a number of other important enhancements to Secure by Design in Sophos Firewall v22. Let’s take a look.
Next-Gen Xstream Architecture
 Sophos Firewall introduced the Xstream Architecture as a key component of v18, enabling XGS Series appliances to take full advantage of the added processing power and capabilities it provided. Since then, Sophos Firewall’s Xstream Architecture has been constantly scaling and adapting to bring additional performance to customer networks.
Sophos Firewall introduced the Xstream Architecture as a key component of v18, enabling XGS Series appliances to take full advantage of the added processing power and capabilities it provided. Since then, Sophos Firewall’s Xstream Architecture has been constantly scaling and adapting to bring additional performance to customer networks.
This is all thanks to the programmable nature of Sophos Firewall’s Xstream Architecture that is NOT dependent on custom silicon ASICs – and in fact works equally well on general-purpose CPUs, virtual CPUs, and our XGS Series models that have dedicated flow processors.
Sophos Firewall v22 introduces our next-generation Xstream Architecture, which has an all-new control plane re-architected for maximum security and scalability to take us into the future. The new control plane enables modularization, isolation, and containerization of services like IPS for example, to run like “apps” on the firewall platform. It also enables complete separation of privileges for added security.
The net result is an ultra-secure, scalable, and streamlined architecture built for the future. This next-gen Xstream Architecture lays a foundation for highly secure, scalable, and modular containerized services, n-node clustering, and full RESTful APIs for high-performance remote management and automation.
High-availability self-healing
In addition, this Next-Gen Xstream Architecture adds a new self-healing capability to high-availability deployments that is continuously monitoring system state and fixes deviations between devices automatically.
Hardened kernel
 The next-gen Xstream Architecture in Sophos Firewall OS is built upon a new hardened kernel (v6.6+) that provides enhanced security, performance, and scalability to maximize current and future hardware. The new kernel offers tighter process isolation and better mitigation for side-channel attacks as well as mitigations for CPU vulnerabilities (Spectre, Meltdown, L1TF, MDS, Retbleed, ZenBleed, Downfall). It also offers hardened usercopy, stack canaries, and Kernel Address Space Layout Randomization (KASLR).
The next-gen Xstream Architecture in Sophos Firewall OS is built upon a new hardened kernel (v6.6+) that provides enhanced security, performance, and scalability to maximize current and future hardware. The new kernel offers tighter process isolation and better mitigation for side-channel attacks as well as mitigations for CPU vulnerabilities (Spectre, Meltdown, L1TF, MDS, Retbleed, ZenBleed, Downfall). It also offers hardened usercopy, stack canaries, and Kernel Address Space Layout Randomization (KASLR).
Remote integrity monitoring
Sophos Firewall OS v22 now integrates our Sophos XDR Linux Sensor that enables real-time monitoring of system integrity, including unauthorized configuration, rule exports, malicious program execution attempts, file tampering, and more.
This helps our security teams who are constantly monitoring our entire Sophos Firewall customer base to better identify, investigate, and respond more quickly to any attack. This is an added security capability that no other firewall vendor provides.
New anti-malware engine
Sophos Firewall OS v22 integrates the latest Sophos anti-malware engine with enhanced zero-day, real-time detection of emerging threats using global reputation lookups. This is possible thanks to a massive cloud database of known malicious files, which is updated every 5 mins or less.
It also introduces AI and ML model detections and delivers enhanced telemetry to SophosLabs for accelerating their emerging threat detection analysis.
Get started today
Be sure to get involved in the Sophos Firewall v22 Early Access Program to better secure your and your customers’ networks and help make this release the best it can be. Also be sure to review the What’s New Guide for a full list of all the new capabilities in Sophos Firewall v22.
Source: Sophos
Keeper Security, the leading cybersecurity provider of zero-trust and zero-knowledge Privileged Access Management (PAM) software protecting passwords, passkeys, privileged accounts, secrets and remote connections, today announces Keeper Forcefield™, the first-of-its kind protection against memory-based attacks on Windows devices. Forcefield is a groundbreaking kernel-level endpoint security product that proactively defends against memory-based attacks, including credential theft from infostealers and runtime memory-scraping malware. Keeper® is the first cybersecurity software company to deliver real-time memory protection at both the user and kernel levels, raising the standard for endpoint security in enterprise environments.
Attackers are increasingly bypassing traditional cybersecurity defenses by targeting unprotected memory rather than exploiting vulnerabilities. Malicious software delivered through phishing attacks or other methods can access application memory to extract passwords, session tokens and other sensitive data – circumventing traditional encryption methods. Keeper Forcefield closes this dangerous gap by locking down memory access at the kernel level. Unlike conventional antivirus or Endpoint Detection and Response (EDR) tools, it enforces real-time memory protection capable of blocking non-privileged, fileless and zero-day attacks without degrading system performance.
“Forcefield closes one of the most dangerous blind spots in endpoint security,” said Craig Lurey, CTO and Co-founder of Keeper Security. “Malware can extract sensitive information directly from a device’s memory, even at the user level where administrative privilege isn’t required. Forcefield prevents this type of exploit entirely without disrupting trusted applications or everyday workflows.”
Forcefield provides peace of mind by actively safeguarding sensitive data from unauthorized access while operating silently in the background. It installs a lightweight, kernel-level driver that shields protected application memory from unauthorized access. Users can easily toggle Forcefield on or off within the Keeper Desktop application or deploy it via Group Policy. The solution continuously differentiates between trusted and untrusted processes in real-time, ensuring legitimate activity continues uninterrupted while malicious or unknown processes are blocked from scraping sensitive data.
How Keeper Forcefield works:
- Kernel-level protection – Actively monitors and restricts memory access to protected applications.
- Selective memory restriction – Blocks unauthorized processes from reading protected application memory.
- Smart process validation – Differentiates between trusted and untrusted processes in real time.
- Uninterrupted system performance – Runs quietly without impacting system or application performance.
Windows applications protected by Forcefield include:
- Web browsers – Chrome, Firefox, Edge, Brave, Opera and Vivaldi
- Keeper software – Desktop App, Web Vault, Browser Extensions, Gateway, Bridge, Commander and KeeperChat
- Operating systems – Windows 11 x64 and ARM64
Forcefield is available for both individual users and enterprise environments. Organizations can deploy protection across fleets of Windows devices in minutes using existing management tools, ensuring scalable and consistent endpoint defense without added friction.
For more information or to download Keeper Forcefield, visit www.keepersecurity.com/forcefield-endpoint-protection.
Source: Keeper Security and PR Newswire
Keeper Security, the leading cybersecurity provider of zero-trust and zero-knowledge Privileged Access Management (PAM) software, today announces that it has been recognized among leading vendors in the 2025 Gartner® Magic Quadrant™ for Privileged Access Management report.
The Gartner Magic Quadrant is widely considered one of the most influential evaluations in enterprise technology, providing security leaders with insights in selecting trusted solutions in today’s rapidly evolving technological landscape. KeeperPAM delivers a modern, cloud-native solution that unifies password and passkey management, secrets and connection management with zero-trust network access, remote browser isolation, privileged session management and endpoint privilege management in a single, easy-to-deploy platform. Designed for today’s hybrid IT environments, KeeperPAM leverages agentic AI and native integrations to provide organizations with complete visibility, control and compliance across every user, device and system.
Keeper differentiates itself in the PAM market with comprehensive enterprise-wide coverage and seamless integration with your technology stack. The next-gen PAM platform centralizes access to systems and data with zero-trust security, enforcing role-based policies and MFA across all assets.
- Password management: Protect and securely share passwords, passkeys and confidential data in a zero-knowledge vault with role-based access control, auditing and reporting.
- Secrets management: Integrate CI/CD pipelines, DevOps tools, custom software and multi-cloud environments into a fully-managed, zero-knowledge platform to secure infrastructure secrets and reduce secrets sprawl.
- Session management: Provide secure, credential-free access to sensitive systems while maintaining full visibility and control over privileged sessions.
- Remote browser isolation: Secure internal web-based applications, cloud apps and BYOD devices from malware, prevent data exfiltration and control browsing sessions with full auditing, session recording and password autofill.
- Endpoint privilege management: An advanced Privileged Elevation and Delegation Management (PEDM) solution that provides secure, Just-in-Time (JIT) privileged access across all Windows, Linux and macOS endpoints, with optional approval workflows and MFA enforcement.
- Admin console and control plane: Streamline deployment, user provisioning and policy enforcement through a centralized admin interface that seamlessly integrates with your existing identity stack.
- AI-powered session analysis that replaces manual log reviews with automated insights, giving organizations the speed and accuracy needed to stay ahead of modern cyber threats.
“KeeperPAM was engineered from the ground up to meet the realities of modern IT environments – cloud-first and hybrid, distributed and highly dynamic,” said Craig Lurey, CTO and Co-founder of Keeper Security. “Our platform eliminates the complexity of legacy PAM tools by delivering a unified, zero-knowledge solution that deploys in minutes and scales effortlessly. By integrating credential and privileged access management with advanced capabilities like AI-powered session analysis and remote browser isolation, we’re empowering security and DevOps teams with tools that are both powerful and intuitive. We believe this recognition from Gartner affirms our commitment to redefining PAM through innovation, simplicity and uncompromising security.”
In 2025, Enterprise Management Associates (EMA) identified Keeper as a Value Leader in the PAM Radar Report, while GigaOm ranked Keeper the Overall Leader in its Password Management Report for the fourth consecutive year. Newsweek also highlighted Keeper among America’s Best Online Platforms, where it achieved the highest ranking of any cybersecurity vendor in the Business Solutions category.
Keeper’s innovation leadership has been further validated with multiple award wins in 2025, including being recognized as the Most Innovative Cybersecurity Company and earning top honors in both Privileged Access Management and Zero-Trust Security in the Cybersecurity Excellence Awards. The Globee Awards selected Keeper as the Cybersecurity Company of the Year, and the Global Infosec Awards honored the company in nine categories, including wins for privileged access management and zero trust.
“We believe Keeper’s recognition in the Gartner Magic Quadrant underscores the momentum we’ve built by challenging legacy approaches to privileged access management,” said Darren Guccione, CEO and Co-founder of Keeper Security. “KeeperPAM reimagines PAM for the modern enterprise, making it simple and scalable, while preserving the foundation of zero-trust and zero-knowledge security. Our vision is to empower organizations everywhere with a platform that is more secure, more intuitive and more accessible, enabling them to stay ahead of today’s rapidly evolving cyber threats.”
With FedRAMP and GovRAMP Authorization; SOC 2 Type II attestation; ISO 27001, 27017 and 27018 certifications and FIPS 140-3 validation; KeeperPAM meets the highest standards of compliance. These achievements provide customers with assurance that Keeper’s platform not only strengthens security but also simplifies audit and regulatory requirements.
Access the full Gartner Magic Quadrant Report for Privileged Access Management to learn more. To learn more about Keeper’s enterprise, business and government solutions, visit KeeperSecurity.com.
Source: Keeper Security and PR newswire
Sophos Firewall v22 is now in early access and the participation has been outstanding.
One of the highlights of this release is the new Health Check feature. This is just one of the many Secure by Design elements in this release, but it’s an important one.
A critical part of keeping your network secure is ensuring your firewall is optimally configured to prevent attackers from exploiting any openings or weak points in your security posture. Sophos Firewall v22 makes your job of optimally securing your firewall much easier with the new Health Check feature.
This new feature evaluates dozens of different configuration settings on your firewall and compares them with CIS (Center for Internet Security) benchmarks and our own recommended best practices, providing immediate insights into areas that may be at risk. It will identify all high-risk settings and provide recommendations with easy drill-down to the areas of concern so you can easily address them.
Watch this short video to see how to take advantage of this new feature:
As shown in the video, there’s a new Control Center dashboard widget with click-through drill-down to the new feature:
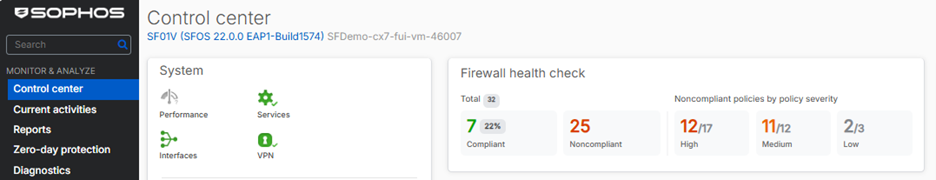
The new Health Check feature has a dedicated main menu item on the left side to access the full detailed report on the compliance of your device:
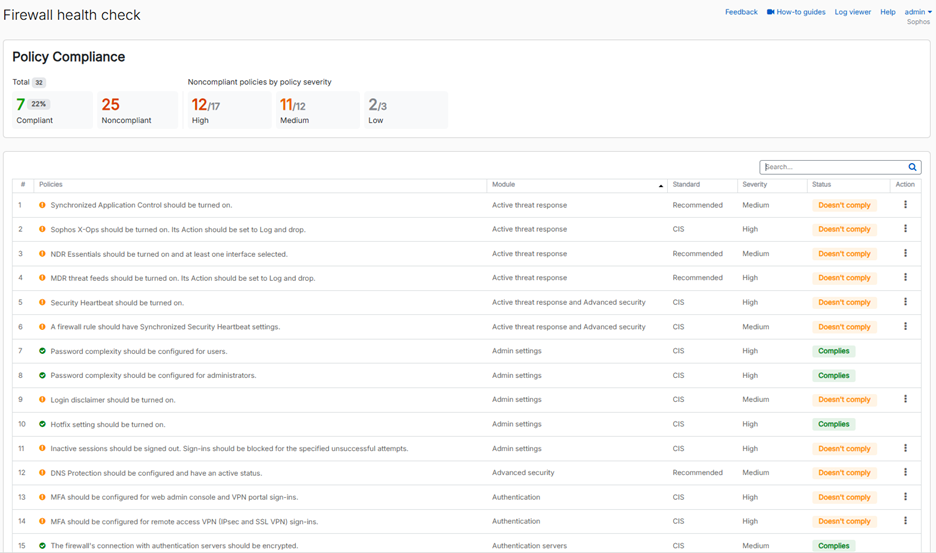
You might be wondering about CIS. The Center for Internet Security (CIS) is a nonprofit community of IT professionals dedicated to evolving standards and best practices for securing IT systems and data.
 You can get more insights into our partnership by visiting the Sophos page on the CIS Benchmarks website. You can also download the benchmark PDF from their website for deeper insights into why these configuration changes are considered a best practice.
You can get more insights into our partnership by visiting the Sophos page on the CIS Benchmarks website. You can also download the benchmark PDF from their website for deeper insights into why these configuration changes are considered a best practice.
The current version on the website was developed based on SFOS v21, but of course also applies just as well to v22. We will be updating the document in partnership with CIS going forward.
Be sure to get involved in the Sophos Firewall v22 Early Access Program to better secure your network and help make this release the best it can be. Also be sure to review the What’s New Guide for a full list of all the new capabilities in Sophos Firewall v22.
Source: Sophos
Recent events with F5 and SonicWall underline a continuing issue: network infrastructure is constantly under attack, and the cybersecurity industry continues to grapple with deep product security challenges.
Our adversaries are targeting the very tools designed to defend us. These are not opportunistic attacks: they’re a long-term strategy requiring years of research and are increasingly involving direct breaches of vendors’ own engineering and product environments.
As disclosed in our Pacific Rim research from last year, Sophos has direct experience with this. We discovered an internal breach of our firewall division in 2018, followed by attacks against customer devices that demonstrated an uncanny knowledge of our product architecture. A handful of other vendors have disclosed similar internal intrusions but this likely only scratches the surface of a wider issue.
What can we do? As Ollie Whitehouse at the National Cyber Security Centre has pointed out, this is ultimately a market incentives problem. Buyers need to demand better. Not by punishing vendors who disclose breaches, but by rewarding vendors who embrace transparency and demonstrate a real commitment to Secure by Design principles.
Over the last several releases, we have continued to invest in implementing Secure by Design principles into all our products, including Sophos Firewall. Sophos Firewall has had numerous updates in the last few years to aggressively harden the product, make it easier to patch vulnerabilities, and to identify when a customer is under attack.
As you probably know, Sophos Firewall is unique in offering zero-touch over-the-air hotfixes that can be used to patch new vulnerabilities without scheduling downtime. Sophos is also the only vendor that is actively monitoring our install base to help identify signs of an attack early.
Sophos Firewall v22 takes Secure by Design to a new level with several important enhancements:
Improved workload isolation – With our next-gen Xstream Architecture, SFOS v22 introduces an all-new control plane re-architected for increased defense-in-depth and scalability. The new control plane enables deeper modularization, isolation, and containerization of services.
Hardened kernel – The next-gen Xstream Architecture in Sophos Firewall OS is built upon a new hardened kernel (v6.6+) that provides enhanced security, performance, and scalability to maximize current and future hardware. This new kernel offers tighter process isolation and better mitigation for side-channel attacks as well as mitigations for CPU vulnerabilities. It also offers hardened usercopy, stack canaries, and Kernel Address Space Layout Randomization (KASLR).
Remote integrity monitoring – Sophos Firewall OS v22 now integrates our Sophos XDR Linux Sensor that enables real-time monitoring of system integrity, including unauthorized configuration, rule exports, malicious program execution attempts, file tampering, and more. This helps our security teams – who are proactively monitoring our entire Sophos Firewall install base – to better identify, investigate, and respond more quickly to any attack. This is an added security capability that no other firewall vendor provides.
Sophos Firewall Health Check – A strong security posture depends on ensuring your firewall and other network infrastructure is optimally configured. Sophos Firewall v22 makes it much easier to evaluate and address the configuration of your firewall with the new Health Check feature, which checks dozens of different configuration settings on your firewall and compares them with CIS benchmarks and other best practices, providing immediate insights into areas that may be at risk.
Be sure to get involved in the Sophos Firewall v22 Early Access Program to better secure your network and help make this release the best it can be.
If you’re a researcher, we welcome security research on our products so please do participate in our bug bounty program. You can receive up to $50K for findings on our firewall platform.
Source: Sophos
Ransomware remains one of today’s most disruptive cyber threats, but it is far from the only one.
Attackers are also exploiting unpatched systems, launching AI-driven phishing campaigns, and using stolen credentials to infiltrate systems and steal sensitive data. These tactics are evolving fast, and IT and security teams are feeling the pressure.
According to Sophos’ 2025 State of Ransomware report:
- 32% of attacks began with unpatched vulnerabilities.
- 28% of victims experienced both encryption and data theft.
- 49% paid the ransom to recover their data.
- 41% of IT teams reported increased anxiety or stress post-attack.
These numbers make one thing clear: organizations need to shift from reacting to preventing.
“Security isn’t just about stopping attacks — it’s about taking back control,” says Joe Levy, Sophos CEO. “That starts with prevention. The earlier you act, the more control you have over your outcomes.”
Inside the toolkit
The Sophos free Cybersecurity Best Practices Toolkit brings together practical, prevention-first resources for organizations of every size. Each one is designed to help you prepare, protect, and practice your response before attackers strike.
Plan Your Response: Incident Response Planning Guide
Build a clear incident response playbook. Learn how to document actions, communicate with stakeholders, and capture lessons from post-incident reviews – get legal documentation tips, communication templates, and guidance on forensic analysis.
Protect your network: Network security best practices for preventing ransomware
Apply proven best practices to harden your network against ransomware and other threats. Learn how to reduce your attack surface, inspect encrypted traffic, and implement zero-trust network access (ZTNA) to block lateral movement.
Practice Readiness: Tabletop Exercise Guide
This guide walks you through how to run realistic tabletop exercises that simulate attacks like insider threats, ransomware, and supply chain compromises, helping to find gaps before attackers do and improve cross-functional communication.
As the guide notes, “Walking through responses in a simulated incident enables participants to develop fluency with the actions needed in a real attack, accelerating execution.”
Why prevention must come first
Every hour saved in detection or response reduces cost, risk, and stress for your team. Prevention isn’t a philosophy — it’s a measurable advantage.
The toolkit outlines how to:
- Run tabletop exercises regularly to test readiness.
- Patch vulnerabilities quickly — addressing the top cause of ransomware in 2025.
- Segment networks to limit attacker movement.
- Replace VPNs with ZTNA to eliminate implicit trust.
- Inspect encrypted traffic to reveal hidden threats
Take control of your defenses today.
Whether you’re a small business, a school district, or a global enterprise, the Sophos Cybersecurity Toolkit gives you a clear path to stronger defenses and greater control, before attackers make their move.
Explore the Cybersecurity toolkit and start building your prevention-first strategy today.
Source: Sophos
Adversaries exploit compromised identities, infrastructure weaknesses, and misconfigurations to gain unauthorized access to sensitive data and systems, putting user-based access and controls at the frontline of modern IT and cybersecurity.
However, with identities no longer confined to the network perimeter, and the widespread shift to cloud and remote work, monitoring and securing identity systems has become increasingly complex. Indicating the scale of the issue, Sophos Incident Response analysis shows that 95% of Microsoft Entra ID environments are misconfigured, creating an open door for threat actors to escalate privileges and launch identity-based attacks.
Protect against identity-based attacks
Introducing Sophos Identity Threat Detection and Response (ITDR) — a powerful new solution that prevents identity-based attacks by continuously monitoring your environment for identity risks and misconfigurations and providing dark web intelligence on compromised credentials.
Built on the proven Secureworks Taegis IDR product, Sophos ITDR is fully integrated into Sophos’ open, AI-native platform, Sophos Central, enabling new and existing customers to deploy with speed and confidence.
Sophos ITDR automatically runs more than 80 advanced identity posture checks, going far beyond basic hygiene to uncover risks in minutes. The solution includes full coverage of MITRE ATT&CK Credential Access techniques, alerts you when credentials are exposed in data breaches, and flags anomalous user activity.
Sophos ITDR helps you:
- Reduce your identity attack surface: Sophos ITDR continuously scans your Microsoft Entra ID environment to uncover misconfigurations, identify security gaps, and provides clear, actionable recommendations.
- Monitor for leaked or stolen credentials: In the past year, the number of stolen credentials offered for sale on one of the dark web’s largest marketplaces has more than doubled*. Sophos ITDR protects user accounts from unauthorized access by monitoring the dark web and breach databases and alerting you when credentials have been exposed.
- Identify risky user behavior: Sophos ITDR detects abnormal activity associated with stolen credentials or insider threats, such as unusual login patterns.
- Protect against identity-based threats: Sophos ITDR enables analysts to respond quickly and effectively with built-in actions such as forcing password resets and locking down suspicious accounts.
A critical part of a complete security solution
Identity is a vital component of any modern security strategy. Sophos provides unmatched cyber defenses through an open, AI-native platform spanning identity, endpoints, network, firewall, cloud, email, and productivity tools. Sophos ITDR strengthens your defenses and is available as an add-on for Sophos Extended Detection and Response (XDR) and Sophos Managed Detection and Response (MDR):
- Sophos XDR + Sophos ITDR: Equip your in-house security teams with advanced tools to detect and stop active adversaries and identity-based threats.
- Sophos MDR + Sophos ITDR: Offload investigations and response activities for identity-based threats to our expert analysts, freeing your IT and security staff to focus on core business priorities.
Learn how Sophos ITDR can elevate your identity security — speak to an expert or visit Sophos.com/ITDR to start a free, no-obligation trial today.
Source: Sophos
We’re pleased to announce that the early access program (EAP) is now underway for the latest Sophos Firewall release. This update brings several Secure by Design enhancements and many of your top requested features.
Secure By Design
Internet facing infrastructure has recently come under increasing attacks to exploit vulnerabilities and other weaknesses to gain a foothold on networks.
As you know, at Sophos, we take security very seriously and over the last several releases we have invested in implementing many Secure By Design principles to harden the product and make it a much more difficult target. This release takes Secure by Design to a whole new level.
Sophos Firewall Health Check
A strong security posture depends on keeping your firmware up to date and ensuring your firewall is optimally configured. Sophos Firewall v22 makes it much easier to evaluate and address the configuration of your firewall with the new Health Check feature.
This new feature evaluates dozens of different configuration settings on your firewall and compares them with CIS benchmarks and other best practices, providing immediate insights to areas that may be at risk. It will identify all high-risk settings and provide recommendations with quick drill-down to the areas of concern so you can easily address them.
The health check status is displayed on a new Control Center widget and a full report is available under the “Firewall health check” main menu item.
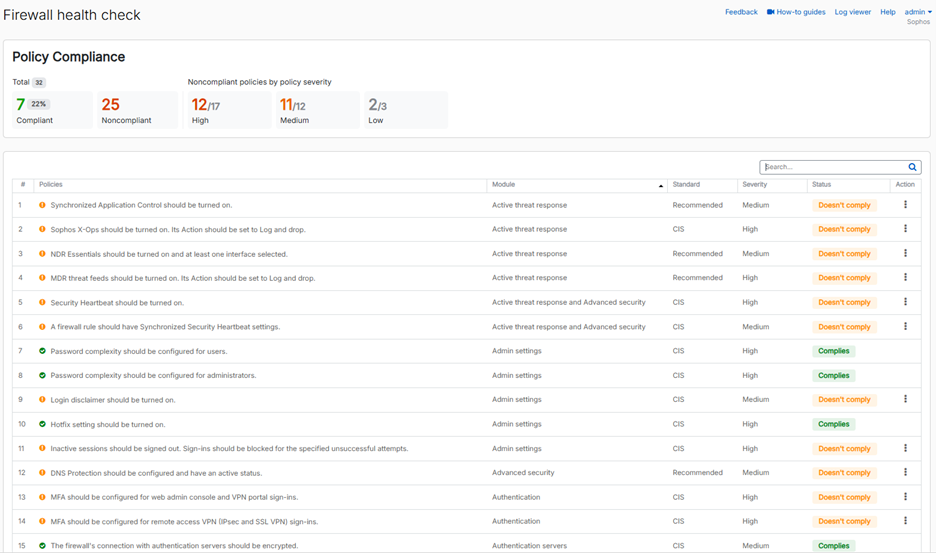
Other Secure By Design enhancements:
- Next-gen Xstream Architecture – introduces an all-new control plane re-architected for maximum security and scalability to take us into the future. The new control plane enables modularization, isolation, and containerization of services like IPS for example, to run like “apps” on the firewall platform. It also enables complete separation of privileges for added security. In addition, high-availability deployments now benefit from a self-healing capability that is continuously monitoring system state and fixes deviations between devices automatically.
- Hardened kernel – The next-gen Xstream Architecture in Sophos Firewall OS is built upon a new hardened kernel (v6.6+) that provides enhanced security, performance, and scalability to maximize current and future hardware. This new kernel offers tighter process isolation and better mitigation for side-channel attacks as well as mitigations for CPU vulnerabilities (Spectre, Meltdown, L1TF, MDS, Retbleed, ZenBleed, Downfall). It also offers hardened usercopy, stack canaries, and Kernel Address Space Layout Randomization (KASLR).
- Remote integrity monitoring – Sophos Firewall OS v22 now integrates our Sophos XDR Linux Sensor that enables real-time monitoring of system integrity, including unauthorized configuration, rule exports, malicious program execution attempts, file tampering, and more. This helps our security teams, who are proactively monitoring our entire Sophos Firewall install base to better identify, investigate, and respond more quickly to any attack. This is an added security capability that no other firewall vendor provides.
- New anti-malware engine – Sophos Firewall OS v22 integrates the latest Sophos anti-malware engine with enhanced zero-day real-time detection of emerging threats using global reputation lookups. It takes full advantage of SophosLabs’ massive cloud database of known malicious files, updated every five minutes or less. It also introduces AI and ML model detections and delivers enhanced telemetry to SophosLabs for accelerating their emerging threat detection analysis.
Other security and scalability enhancements:
- Firmware updates via SSL and certificate pinning ensures authenticity
- Active Threat Response logging improvements enhanced visibility
- NDR Essentials threat score is included in Logs for added insights
- NDR Essentials data center selection for data residency requirements
- Instant web category alerts for education institutions
- XML API access control enhancements with added granularity
- TLS 1.3 support for device access for the WebAdmin console and portals
Streamlined management and quality of life enhancements:
- Enhanced navigation performance
- Hardware monitoring for SNMP with a downloadable MIB
- sFlow Monitoring for real-time visibility
- NTP server settings defaults to “Use pre-defined NTP server”
- UI enhancements for XFRM interfaces with pagination and search/filter options
SG UTM features:
With Sophos UTM heading toward end-of-life soon (July 30, 2026), some migrating customers will appreciate these added features:
- SHA 256 and 512 support for OTP tokens
- MFA support for WAF form-based authentication
- Audit trail logs with before and after tracking to meet the latest NIST standards
Get the full details
Download the full What’s New Guide for a complete overview of all the great new features and enhancements in v22.
Get started today
You can download the upgrade package or installer for v22 from the Sophos Firewall v22 EAP Registration Page. Simply submit your details and the download links will be emailed to you straight away.
All support during the EAP will be through our forums on the Sophos Firewall Community.
Please provide feedback using the option at the top of every screen in your Sophos Firewall as highlighted below in red or via the Community Forums.
Source: Sophos
Just under a year ago, we announced the acquisition of the cloud-forward identity security company, Rezonate. A very exciting milestone for our company. As the product leader, I was excited by the challenge: integrating an entire company, with its own products and capabilities, into our platform.
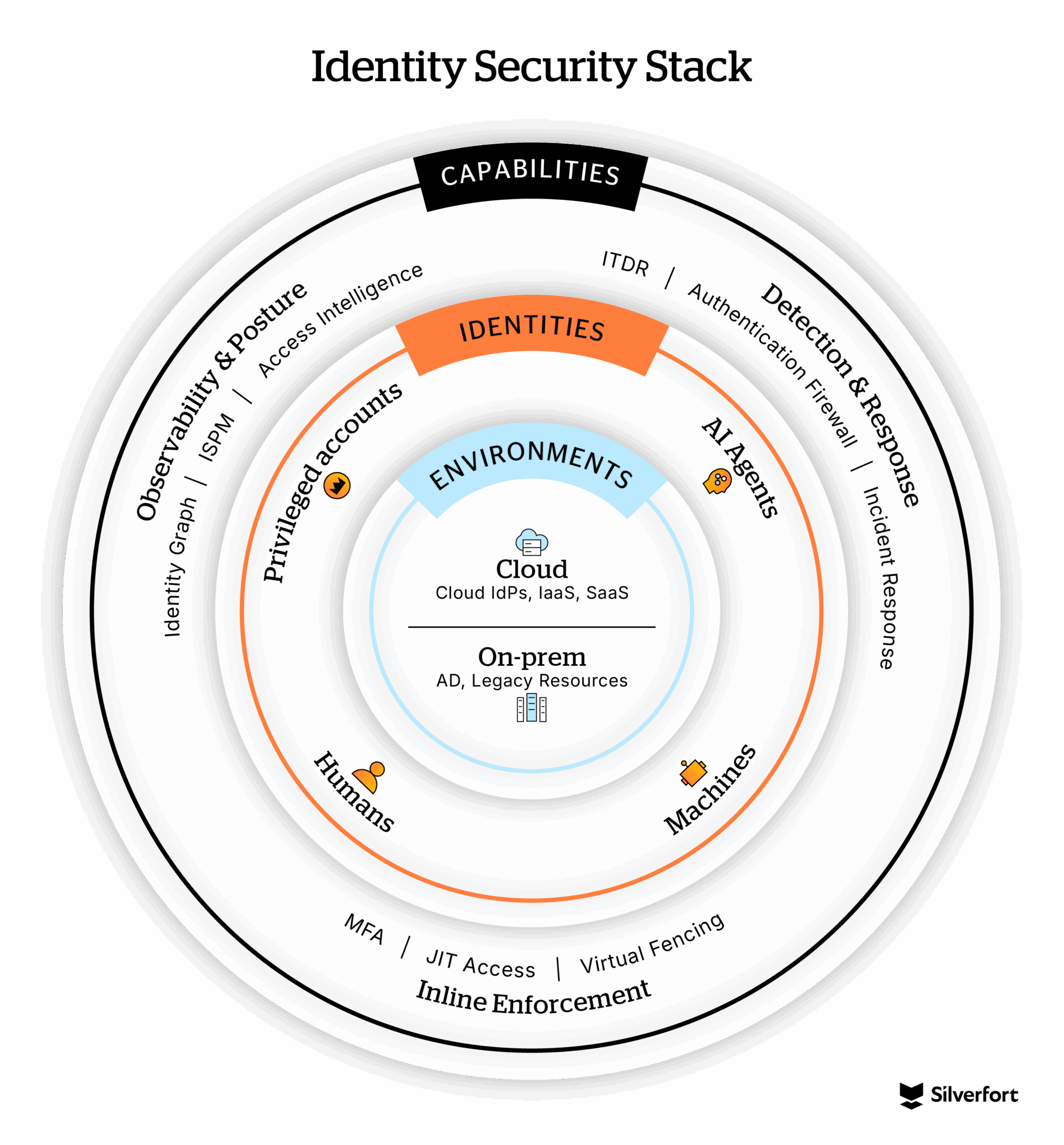
Speed mattered, but this milestone wasn’t just about how fast we could move; it was about redefining what identity security could actually be. Our vision has always been to deliver the most complete identity security platform: protecting every environment and every type of identity with the broadest set of capabilities. And today, I can say we’re continuing to deliver that vision with the latest expansion of the Silverfort Identity Security Platform.
Enterprises are drowning in identity complexity that spans hybrid environments—legacy Active Directory setups, cloud IAMs, SaaS sprawl, machine identities, and AI agents. Everyone’s asking the same questions: Who has access to what? How’s that access being used? And how can I control access?
Until now, the answer has usually been, “We can’t.” Point solutions offer partial visibility leading to gaps and blind spots regularly abused by attackers. The problem only grows as enterprises run parts of their business in the cloud.
We knew we had to meet our customers where they are.
Earlier this year, we announced our expansion to secure cloud-based non-human identities (NHIs). Today, I’m excited to announce the complete expansion of all our products to the cloud and unveil two new capabilities: Identity Graph & Inventory and Access Intelligence. These two innovations deliver the unified visibility and context customers need to take action and secure identities everywhere. They also solidify our leadership in the emerging Identity Visibility and Intelligence Platform (IVIP) space—giving enterprises both observability and insights to stay ahead of identity threats while driving operational efficiency.
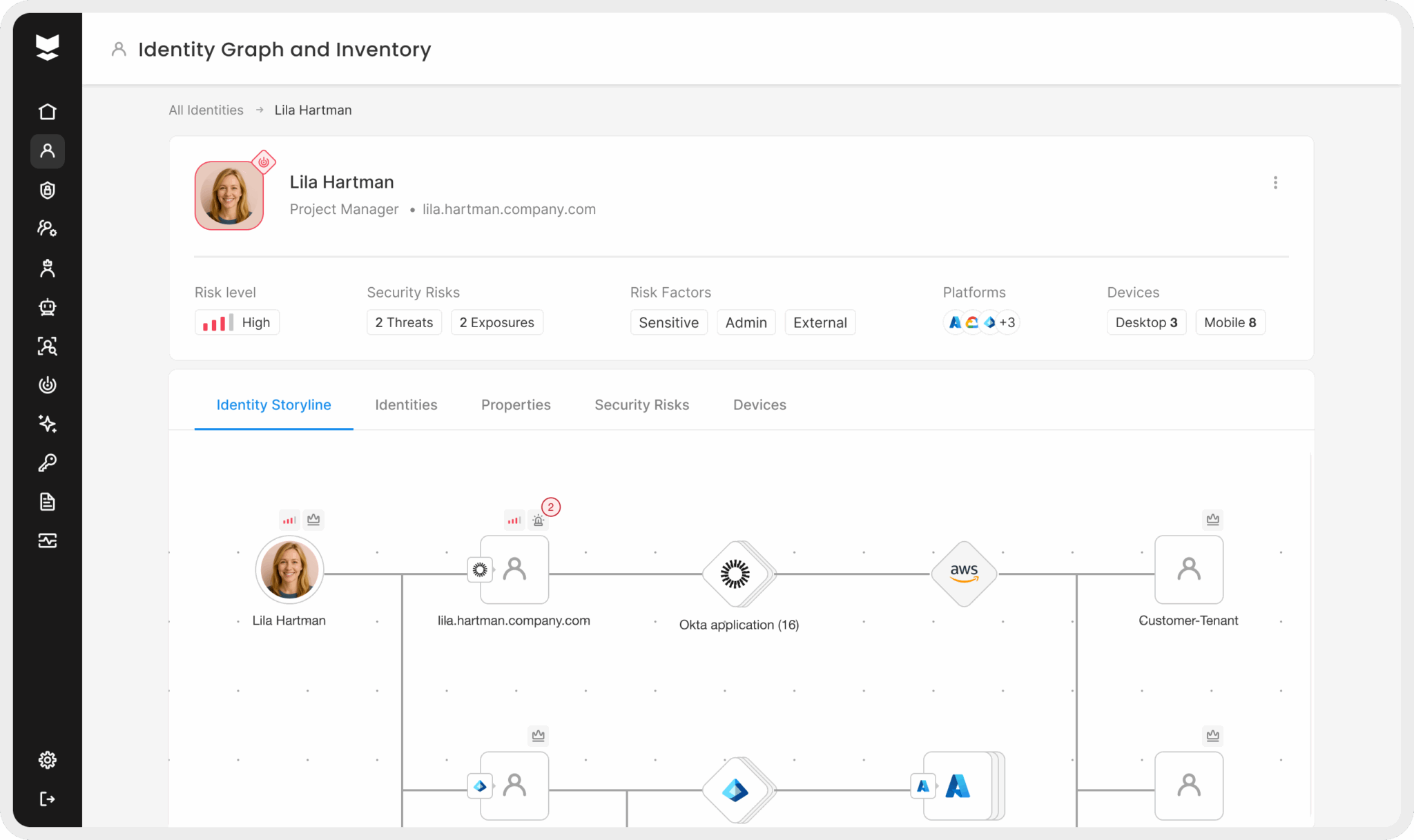
Identity Graph & Inventory: See Everything, Miss Nothing
With Identity Graph & Inventory, we’ve made every identity across your entire identity fabric visible—every user, machine, entitlement, and relationship mapped dynamically across cloud and on-prem systems. It’s a single source of truth that helps teams surfaces hidden access paths and over-privileged accounts, investigate faster, simplify audits, and eliminate blind spots. Instead of static spreadsheets or fragmented reports, you get living intelligence that reflects your real environment.
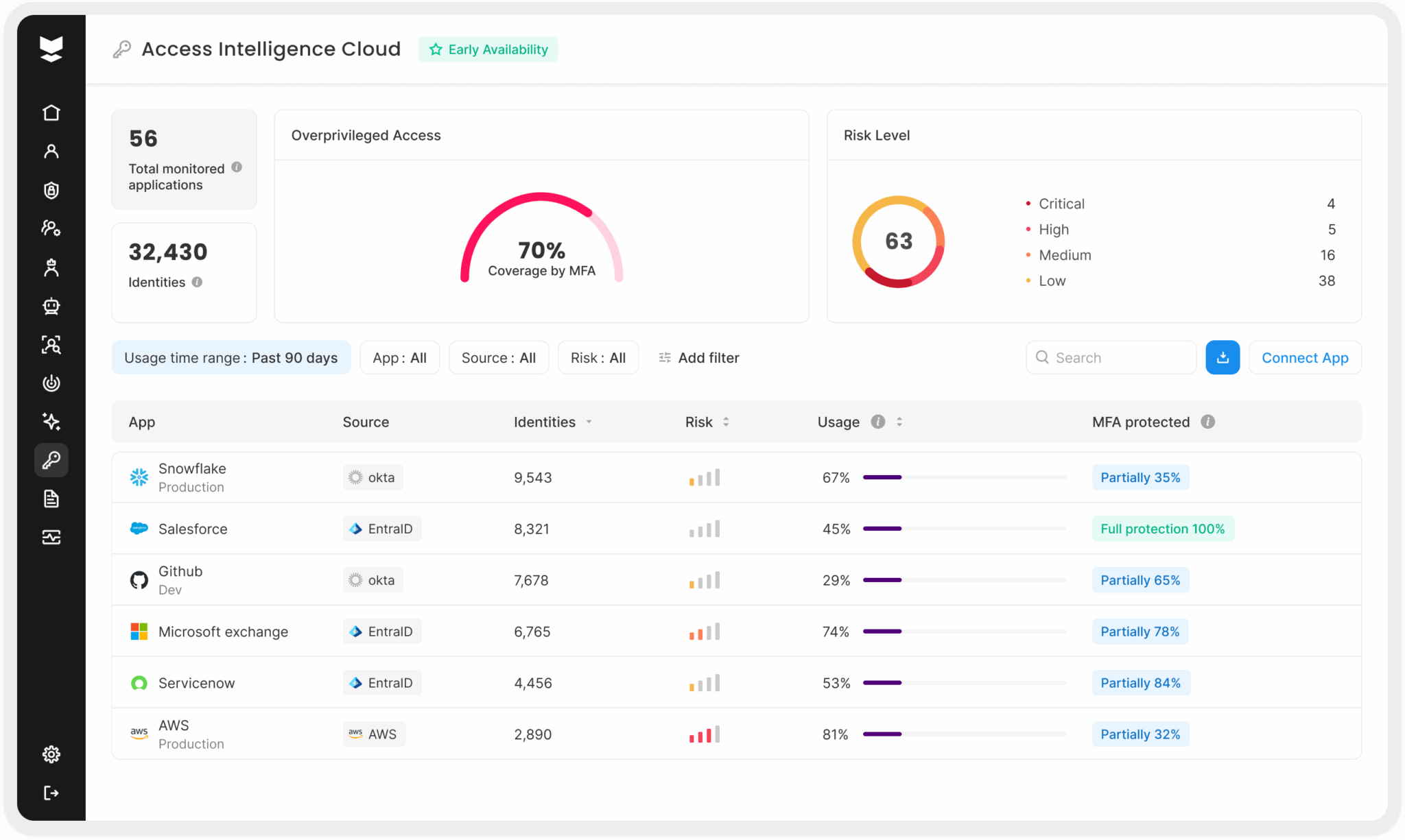
Access Intelligence: See what’s really happening and get to Least Privilege faster
Silverfort Access Intelligence gives teams something they’ve never had before—a clear, resource-centric view of how access is actually being used. It goes beyond permissions to show which users are really connecting to which resources, and how often. This visibility helps organizations enforce least privilege, uncover unused accounts and licenses, and stop threats before they spread.
Identity security done right
Silverfort is known for its unmatched protection for legacy environments. Customers use our platform to extend MFA to critical systems like VPNs, servers, file systems, databases, homegrown apps that were once beyond reach. With unique inline enforcement across every authentication in Active Directory, teams get context and control to protect service accounts, human users, and privileged access—in a single control plane. Teams can strengthen protection and uncover operational efficiencies.
With our latest release, we’re extending the core principles of identity security to the cloud. Customers now have complete visibility across their hybrid IAM stack and can take security-first approach to identity. They are up and running, avoiding the painful “security versus productivity” tradeoffs, and maturing their identity security programs faster than ever.
Now, our platform secures every type of identity—human, machine, and AI—across every environment. It gives organizations the complete picture and the ability to act on it, in real time.
If you’d like to see what’s new, take a moment to check out a demo of Identity Graph & Inventory and Access Intelligence. We think you’ll like what you see.
Source: Silverfort
As cyber threats evolve, organizations must constantly adapt their identity security strategies to stay protected. One of the most significant elements of modern security strategies is network segmentation, which involves the division of a network into smaller, isolated segments to limit unauthorized access to sensitive resources.
As network segmentation is well-known and implemented by most organizations, the rise of identity threats presents a more modern approach to segmentation from the identity control plane.
A further extension of this concept is identity segmentation, which focuses on the identity and attributes of the users, devices, and applications. This approach enables organizations to apply granular access controls to specific identities, improving their overall security posture and protection against unauthorized access.
In this blog, we will explore the difference between network segmentation and identity segmentation. We will also explore how identity segmentation is the key to implementing a true Zero Trust strategy.
The Evolution of Network Segmentation
Network segmentation is a security approach that isolates segments in the enterprise network to reduce the attack surface. Network segmentation works best in the “castle and moat” enterprise environment, securing all exposure points in the environment. This approach has been heavily implemented since the early 2000s by security and IT teams.
While this approach has proven effective in most network security strategies, the evolving nature of cyber threats highlights gaps in network segmentation.
Network segmentation access policies are typically defined by firewall rules or VLANs, which tend to be static and dependent on network traffic. These static policies are dependent on the device and not the user’s access requirements, often granting broad access to users based on their location within the network. Attackers increasingly target user identities, exploiting compromised credentials to gain unauthorized access.
The approach does not adapt to the dynamic nature of modern work environments, where users access resources from a variety of devices and locations. Network segmentation fails to provide the granular control required to secure identities effectively.
Identity Segmentation Boosts Identity Security Posture
Identity segmentation is the approach to security that involves managing and controlling access based on user identities, roles, and attributes. Instead of relying on rigid network boundaries such as IP access lists and firewall rules, identity segmentation divides the network not just from a physical or geographical standpoint, but also from the perspective of the identity control plane.
This is done by segmenting an environment based on the identity and attributes of users, devices, and applications. By doing so, organizations can implement granular access controls, ensuring users only have access to the resources necessary for their roles.
Network Segmentation vs Identity Segmentation
Network segmentation involves dividing a network into different segments to enhance security and control. Traditional network segmentation relies on factors like IP addresses, VLANs, and physical separation to create these segments. While effective at limiting the impact of a breach within the network, network segmentation often falls short in addressing the dynamic and evolving nature of user identities.
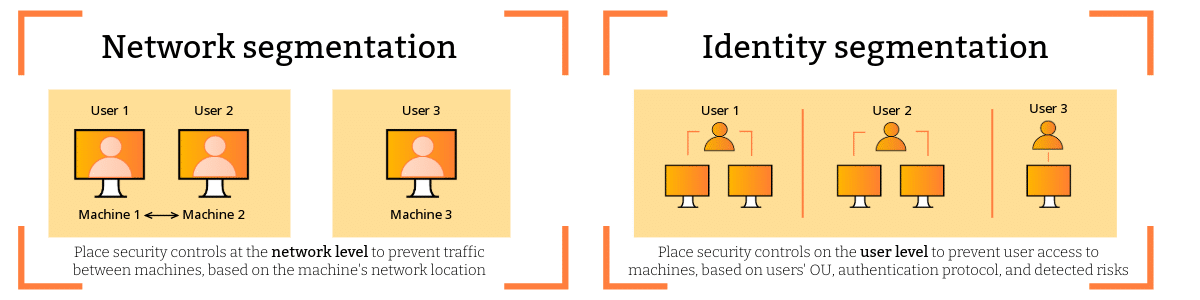
On the other hand, identity segmentation shifts the focus to user identities. This approach aligns with modern security threats where users are the primary targets and threats often exploit compromised credentials. Identity segmentation involves creating access controls based on user attributes, roles, and behavior, so users can only access the resources necessary for their roles, irrespective of their network location.
The primary difference lies in their focus: network segmentation emphasizes securing pathways and infrastructure, while identity segmentation centers on safeguarding individual user identities. Network segmentation tends to rely on static policies based on network structure, whereas identity segmentation involves dynamic and context-aware access controls based on user attributes. Identity segmentation is particularly effective in countering identity-based threats, which have become increasingly prevalent in the cybersecurity landscape.
Adapting to the Zero Trust Architecture
To implement a Zero Trust architecture, all organizations must protect their identities, devices, networks, applications, and workloads, as well as data. It is important to note that while many organizations have successfully implemented a few principles of the Zero Trust model, most still need to strengthen their identity security posture management.
Strong identity management and protection enables organizations to respond more rapidly and precisely when a potential threat arises. IT teams can better track and alert on any identity threats that come up, prompting proactive measures to stop potential unauthorized access attempts.
To construct a complete Zero Trust architecture across your environments, identity management and identity protection must be the core components. This will enable you to manage and protect all aspects of identity effectively, which is essential for safeguarding all types of assets, including those that are on-prem.
Source: Silverfort
You face no shortage of challenges in securing your organization from cyberattacks. The threat landscape continues to evolve, attack surfaces are expanding with the advent of new technologies, new adversary tactics and techniques keep emerging, and there’s more scrutiny than ever about what you’re doing to safeguard your environment.
Accurately assessing where you’re vulnerable to threats isn’t easy. Testing your defenses is an effective, proactive way to measure the strength of your security and set a course for lowering your risk before a threat actor strikes.
Put your defenses to the test and determine your risk
Introducing Sophos Advisory Services – proactive security testing services that provide expert, independent assessment of your cyber defenses and recommendations for improvement. These services support a more strategic approach to cybersecurity by identifying weak spots in your environment, allowing you to fortify your resiliency against potential attacks.
We’re delighted to announce general availability of four security testing services: External Penetration Testing, Internal Penetration Testing, Wireless Network Penetration Testing, and Web Application Security Assessment.
These services…
- Discover weak spots in your defenses. Uncover vulnerabilities in your environment that adversaries could exploit, based on the powerful combination of our experience from performing thousands of engagements and the latest threat intelligence from Sophos X-Ops.
- Assess your risk of being breached. Understand your real-world risk of being impacted by a cyber incident before an attack hits your business.
- Demonstrate your sound security practices to business partners. Show your organization’s commitment to cybersecurity to your customers, partners, stakeholders, regulators, and cyber insurance provider.
- Fortify your cyber resiliency. Make your security programs more resilient against threats. Testing is infused with current and relevant threat information from our research and testing teams.
Available today!
Sophos now offers the following security testing and assessment services:
- External Penetration Testing: Assesses your defenses against an adversary trying to exploit your environment from outside the perimeter.
- Internal Penetration Testing: Evaluates controls inside your perimeter to gauge interior defenses and guard against insider threats.
- Wireless Network Penetration Testing: Assesses your wireless network security networks and how attackers may attempt to gain access.
- Web Application Security Assessment: Tests your web applications for known vulnerabilities.
Sophos Advisory Services are delivered by our world-class team of cross-discipline security testers, backed by hundreds of security analysts and threat research experts.
Our services aren’t check-the-box, generic pass/fail tests. Our security experts meet with you before testing begins to understand your challenges and objectives. When testing concludes, we provide you with a detailed report for technical and non-technical audiences, featuring all steps taken during the engagement, our findings, and actionable recommendations you can use to elevate your organization’s security posture.
Learn more about how Sophos Advisory Services can uncover weak spots in your defenses and fortify your cyber resiliency. Speak to an expert today or visit Sophos.com/Advisory-Services.
Source: Sophos
In today’s fast-paced digital world, the relentless nature of cyber threats is taking a significant toll on the very people charged with defending our businesses: cybersecurity professionals.
 Our latest report, “The Human Cost of Vigilance: Addressing Cybersecurity Burnout in 2025,” sheds light on this growing crisis.
Our latest report, “The Human Cost of Vigilance: Addressing Cybersecurity Burnout in 2025,” sheds light on this growing crisis.
The report examines the direct human impact of these pressures, drawing on new research data to reveal the prevalence, key drivers, and consequences of burnout, ultimately underscoring how strategic solutions can mitigate this critical issue.
In the first quarter of 2025, data was collected via a vendor-agnostic survey of 5,000 IT and cybersecurity professionals across 17 countries, with the survey asking respondents about their experiences with burnout during 2024.
Pervasive strain and extensive repercussions
When asked about personal experiences of cyber fatigue or burnout, 76% of respondents reported experiencing it either constantly, frequently, or occasionally themselves over the last year.
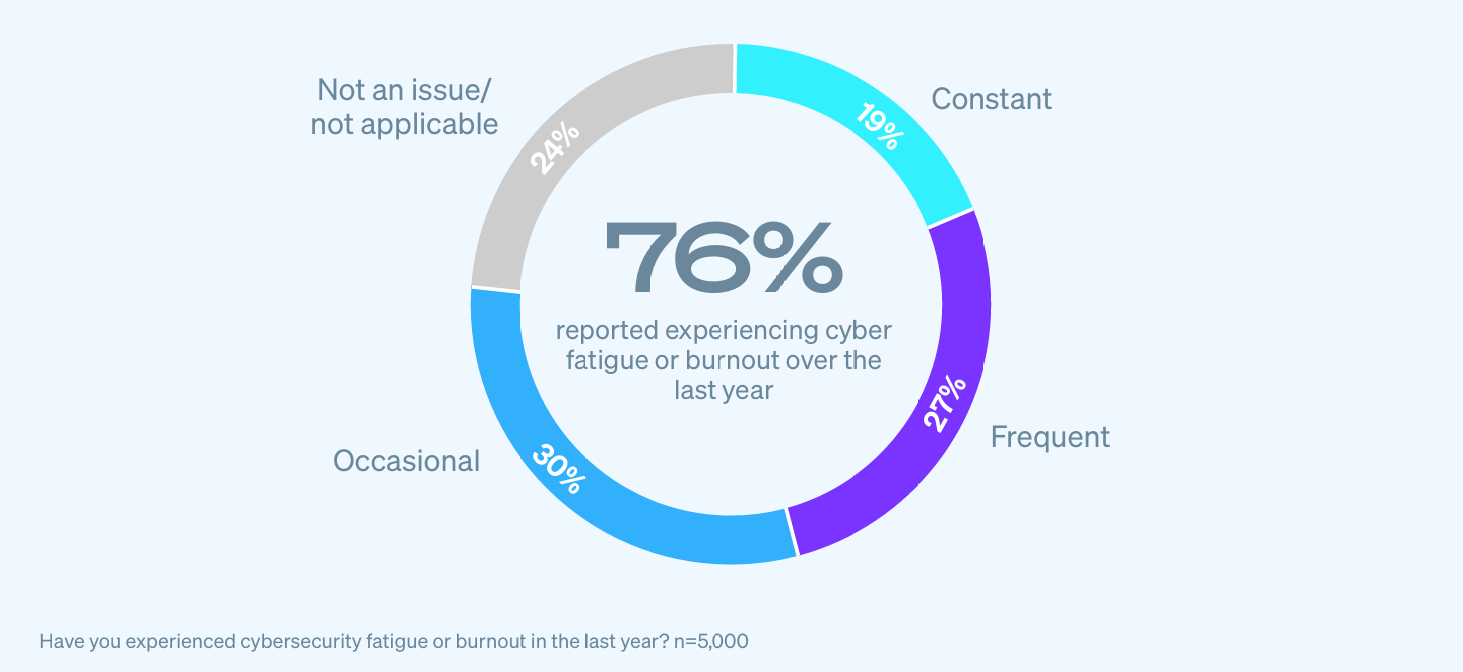
What’s more: the problem is getting worse, with 69% of respondents reporting that cybersecurity fatigue and burnout increased from 2023 to 2024.
The consequences of burnout
Unsurprisingly, burnout has significant negative impacts on the individuals that experience it, with almost half (46%) reporting heightened anxiety about cyberattacks or breaches, 39% admitting to reduced productivity at work, and a third saying they have had a reduced level of engagement at work.
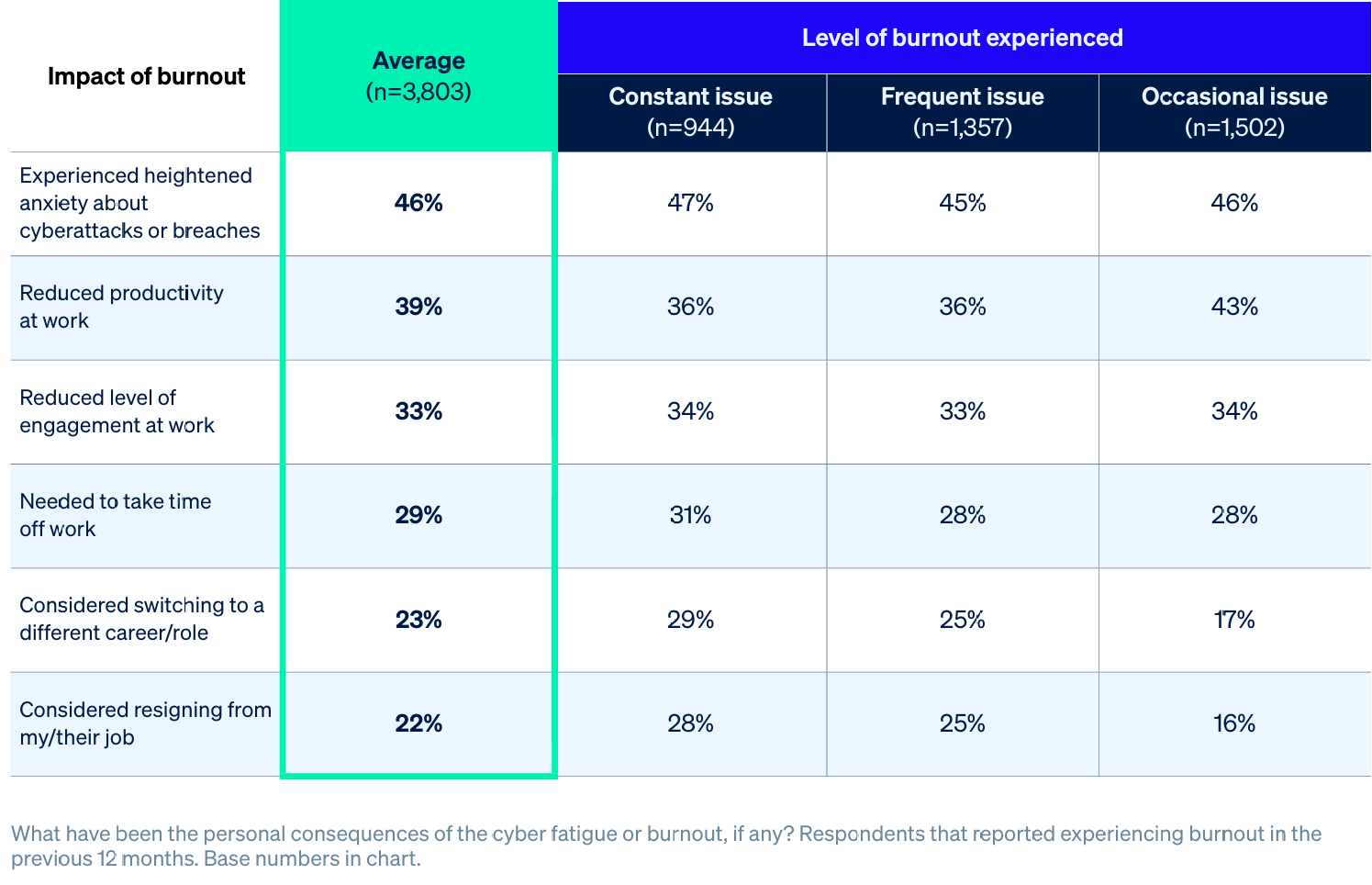
These figures highlight a pervasive challenge that directly undermines the effectiveness and sustainability of cybersecurity defenses.
Core causes of strain
The results reveal that cybersecurity stress is not just a technical issue: it’s a business one as well.
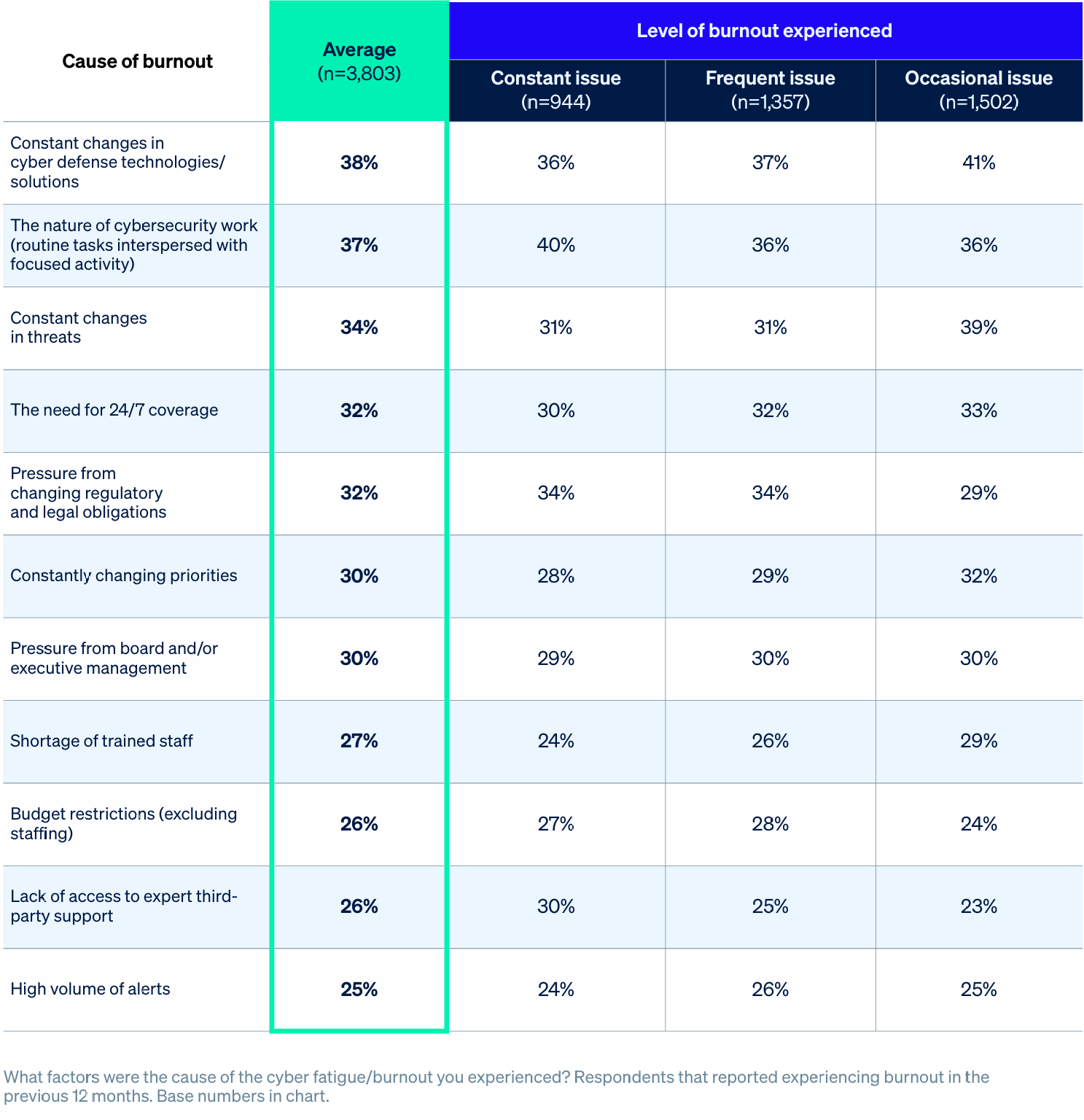
On average, respondents cited three separate factors that contributed to them experiencing burnout, highlighting the multiple pressures that IT teams face.
Learn more
It’s not all bad news, fortunately. For more details on these findings and to learn about potential solutions, we invite you to download the full report.
Source: Sophos
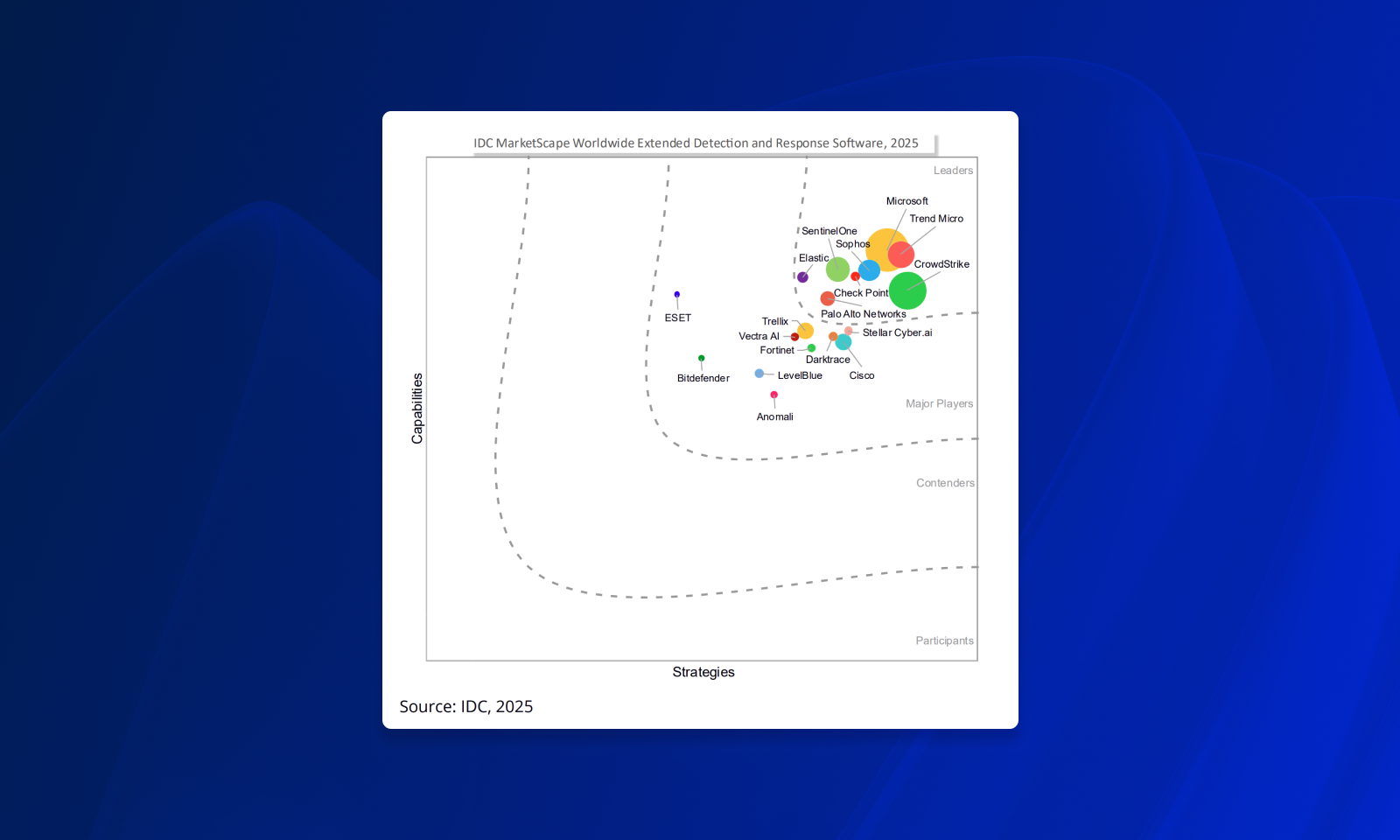
We’re proud to announce that Sophos has been named a Leader in the IDC MarketScape™: Worldwide Extended Detection and Response (XDR) Software 2025.
We believe this recognition reflects our commitment to delivering intelligent, integrated, and scalable security solutions that help organizations stay ahead of threats.
The IDC MarketScape for Extended Detection and Response cites Sophos’ protection capabilities as a strength, noting, “Sophos is viewed favorably in terms of the protections it offers. Key protection technologies included as standard features on the endpoint are host-based firewall and IDS/IPS, device control, DLP, antimalware scans, and encryption.”
The report also highlights Sophos’ proactive defense capabilities, stating, “Colloquially known as ‘Shields Up,’ Sophos’ Adaptive Attack Protection was introduced in 2023. Adaptive attack protection automatically enforces certain protections if there is evidence of a ‘hands-on-keyboard’ attack.”
“While Sophos has been working on many of these technologies internally, the integration of the Taegis XDR platform adds heft to existing capabilities and jumpstarts engineering cycles to newer initiatives.”
— Chris Kissel, IDC
When highlighting when to consider Sophos, the report notes, “Sophos has an international presence, and its ecosystem is designed to empower businesses of all sizes and all types. Cybersecurity novices, intermediate users, and experts will gain value from the Sophos XDR platform.”
Sophos XDR: Innovation that drives results
Sophos Extended Detection and Response (XDR) provides powerful tools and threat intelligence that enable you to detect, investigate, and neutralize threats across your entire IT ecosystem, delivered through Sophos’ adaptive AI-native, open platform.
- Start with the strongest defense: Organizations can focus investigations by stopping more breaches before they start. Sophos XDR includes the unparalleled protection of Sophos Endpoint to stop advanced threats quickly before they escalate.
- Accelerate security operations with AI: AI tools included with Sophos XDR help streamline investigations by providing real-time insights, contextualizing threat data, and offering natural language-driven recommendations. Designed in partnership with our frontline security analysts, the Sophos AI Assistant enables your in-house team to benefit from real-world workflows and the experience of Sophos experts.
- Integrated identity protection: Sophos delivers deep visibility across identity layers and cloud environments. With ITDR, Kubernetes monitoring, and integrations with Microsoft Entra ID and O365, we secure everything from endpoints to cloud workloads.
- Automated and adaptive defenses: Sophos offers a rich set of automated responses—from isolating endpoints to enforcing MFA and rolling back ransomware damage. Our adaptive defenses functionality activates protections during active attacks, minimizing impact and enabling swift recovery.
- Ecosystem flexibility: With an extensive ecosystem of integrations, Sophos XDR fits seamlessly into diverse IT stacks. Whether customers use third-party firewalls, email platforms, or endpoints, Sophos enhances existing investments without disruption.
- An open platform designed to optimize and unify: Benefit from a single view across your entire IT ecosystem in a unified detection and response platform and focus investigation efforts on high-priority items instead of noisy, unactionable alerts. Our open, extensible architecture provides visibility across the entire attack surface by integrating threat information from your existing and future security investments.
Secureworks integration is a game-changer
Following our acquisition of Secureworks in February 2025, Sophos Endpoint is now natively integrated and automatically included with Taegis XDR and MDR subscriptions. This milestone delivers combined prevention, detection, and response in a single platform with lower licensing costs and simplified operations.
This integration strengthens protection, accelerates threat mitigation, and ensures customers maximize ROI while maintaining flexibility.
Industry validation that matters
Sophos XDR isn’t just leading in innovation; it’s earning trust across the board. From analysts to end users, the recognition is clear:
- Sophos is named a Leader in the Gartner® Magic Quadrant™ for Endpoint Protection Platforms for the 16th consecutive report.
- Sophos is named a Leader in the 2025 Frost Radar™ for Managed Detection and Response.
- Sophos is named a Gartner “Customers’ Choice” for EPP for the fourth consecutive year, a “Customers’ Choice” for MDR for the second consecutive year, and a “Customers’ Choice” for XDR in the inaugural version of the report.
- Sophos is the ONLY vendor named a “Customers’ Choice” in both EPP and XDR
- Sophos is named a G2 Leader in Endpoint Protection, EDR, MDR, Firewall, and XDR in its Fall 2025 Grid Reports.
This consistent validation reinforces Sophos as the go-to partner for organizations seeking proven, high-impact security outcomes.
What’s next: Building the future of XDR
We believe being named a Leader in the IDC MarketScape™ is a milestone that reflects our progress. It also marks the beginning of our next chapter: Full integration of Taegis XDR into the Sophos Central platform.
Read an excerpt of the IDC MarketScape™: Worldwide Extended Detection and Response (XDR) Software 2025 here.
Source: Sophos
G2 has published its Fall 2025 Reports, and customers once again put Sophos at the top. Sophos is ranked #1 Overall in Managed Detection and Response (MDR) and #1 Overall in Firewall Software. Speaking to the power of our platform, Sophos is named as a Leader for the 13th consecutive time across every G2 Overall Grid® that defines modern security operations: Endpoint Protection Platforms, Endpoint Detection and Response (EDR), Extended Detection and Response (XDR), Firewall Software, and Managed Detection and Response (MDR).
These recognitions come from verified peer review and reflect what security teams value most: faster time to outcome, simpler operations, and the confidence of a platform that scales from prevention to managed response.
Managed Detection and Response
In addition to the #1 overall ranking among MDR solutions, Sophos MDR is also rated the top solution in five report segments for the category, including the Enterprise and Mid-Market Grids. Sophos MDR also earned the Best Results and Best Usability distinctions among Enterprise customers.
Endpoint
Sophos EDR/XDR was named a Leader across eight different segments in the Fall 2025 Reports, including the Overall, Enterprise, Mid-Market, and Small Business Grids. The Sophos XDR platform earned the Best Usability, Best Results, and Best Relationship distinctions, reinforcing its industry-leading security outcomes.
Firewall
The G2 Fall 2025 Reports marks Sophos Firewall’s 11th consecutive #1 Overall Firewall ranking. But for the first time, Sophos Firewall was also unanimously rated as the #1 firewall solution by all customer segments in the G2 Fall 2025 Reports (Enterprise, Mid-Market and Small Business users). Additionally, Sophos Firewall earned the Overall Best Results, Best Usability, and Best Relationship badges.
What Sophos customers are saying
“The level of comfort and security Sophos MDR has provided to us is immeasurable” said a Lead Infrastructure Engineer in the Mid-Market segment
“[Sophos MDR] is a combination of powerful automation and real human expertise delivered through tightly integrated security ecosystems” said a user in the Enterprise segment
“Sophos Firewall stands out because it combines strong protection with an easy-to-use interface” said a Technical Support Engineer in the Small Business segment
“[Sophos Firewall] offers a robust set of features, including advanced threat protection, user-friendly reporting, and seamless integration with endpoint security” said a Manager in the Mid-Market segment
“What I like best about Sophos Endpoint is its ability to provide powerful protection while remaining simple to manage and almost invisible to end users” said a Technical Engineer in the Small Business segment
“With advanced threat detection powered by deep learning and behavioral analysis, [Sophos Endpoint] swiftly identifies and neutralizes even the most sophisticated threats” said an IT Manager in the Mid-Market segment
For more information on our services and products, speak to your Sophos partner or representative and visit our website.
Source: Sophos
If you’re evaluating endpoint protection, you’ve likely noticed something: Everything starts to sound the same. “AI-powered.” “Next-gen.” “Integrated.”
These claims are everywhere. And with over 90% of organizations now using some form of endpoint protection rather than antivirus, it’s easy to assume all solutions are equal.
They’re not.
That assumption breaks down quickly as organizations mature — moving from basic prevention to detection and response. In this evolution, what once looked like a checkbox exercise becomes a critical architecture decision. What you choose now impacts not just how well you’re protected, but how well you can adapt and reduce overall business risk in the face of evolving threats.
So how do you separate signal from noise?
The power behind the platform
One of the best indicators of what a protection solution can do for you — not just today, but long term — is the platform it’s built on. Not every feature may matter to you on day one, and that’s OK. What matters is whether the foundation gives you room to mature and improve your cyber defense.
This is where platform thinking becomes essential: Are you choosing a product or investing in a strategy?
Modern endpoint protection isn’t just about what’s installed on the device. It’s about the telemetry collected, the integrations supported, the workflows enabled, and the data pipelines behind it all. Especially as AI plays a larger role in threat detection and response, the sophistication of that underlying data infrastructure becomes a force multiplier.
It starts with data
Before AI can assist — let alone automate — you need high-quality, well-structured, and continuously refreshed data. This isn’t new thinking. In fact, data science has long relied on four foundational dimensions: Volume, Variety, Velocity, and Veracity.
Let’s apply those to endpoint protection:
- Volume: How much telemetry is being collected? Are you seeing real-world adversary behaviors at a global scale — not just malware, but hands-on-keyboard attacks, abuse of tools, and stealthy persistence methods?
- Variety: Does the platform only see endpoints, or does it ingest from email, network, cloud, identity, and more? Is the data coming from a diverse customer base across geographies, verticals, and maturity levels? More sources mean better visibility — and more context.
- Velocity: How fast does that telemetry arrive, and how often is it updated? Are your models learning from new threats in hours or days, or are you reliant on weekly signature pushes?
- Veracity: Can you trust the data? Is it enriched with threat intelligence and verified through real-world incident response? Are detections backed by research, not just automation?
The nuance in those answers is what separates one platform from another. And it’s what determines whether a solution can detect emerging threats before they become industry-wide problems, or whether it lags behind the curve.
Start with prevention. Scale to resilience.
The endpoint is often the first — and best — opportunity to stop an attack. But if your architecture allows it, you can extend that prevention to email, network, cloud, and identity. From there, you can build response capabilities across the entire attack surface, strengthening your ability to contain threats quickly and keep core systems operational when something breaks through.
Every step forward compounds your advantage. You reduce business risk, improve time to detect, and accelerate response. And if you don’t have the people to manage it all in-house, you can lean on partners who offer 24/7 managed detection and response services (MDR) that plug directly into your platform.
At Sophos, this isn’t just theory.

We protect over 600,000 organizations worldwide. Our platform, Sophos Central, processes over 223 Terabytes of threat telemetry daily, pulled from every region, sector, and attack surface. We see threats early and often, generating over 34 million detections daily, giving our defenders an edge. And behind that data is Sophos X-Ops, a global team of threat analysts, malware researchers, and response specialists who monitor hundreds of threat groups and thousands of campaigns in real time. Together, the intelligence and expertise built into Sophos Central stop an average of 11 million attacks daily, with 231 advanced threats resolved by our Managed Detection and Response team. Collectively, we keep customers safe and businesses running without disruption.
When people ask us, “Aren’t all endpoint solutions the same these days?” — our answer is simple:
No. They’re not.
Look past the buzzwords. Ask what the platform sees, how fast it learns, and who is validating its insights. The truth is, what powers the protection matters as much as the protection itself. And those with the best data will always be one step ahead. Ultimately, strong cybersecurity isn’t just a technical need. It is a business imperative that defends operations, reputation, and long-term value.
Source: Sophos
BeyondTrust, the global leader in identity security protecting Paths to Privilege™, today announced the availability of new AI security controls in Identity Security Insights®. These capabilities provide unmatched visibility into AI agents, secure orchestration of their actions, and an on-board intelligence layer to help teams make faster, smarter security decisions.
“The rise of AI agents is creating a new and urgent identity security challenge. Agentic AI is not an isolated problem; it’s a subset of the broader non-human identity landscape. To secure it effectively, organizations must think holistically about their entire identity ecosystem, not just one type of identity in a silo. Often built on low-code and no-code platforms, AI agents can be deployed in minutes with privileges that rival human admins” said Marc Maiffret, Chief Technology Officer at BeyondTrust. “BeyondTrust uniquely connects visibility with proactive control across all identities so customers can rein in this new frontier of risk and turn AI into a safe force multiplier that also meets compliance requirements”.
BeyondTrust continues to advance Identity Security Insights with a steady cadence of innovation. In August 2025, we introduced Secrets Insights, a new capability within Identity Security Insights that uncovers and remediates risks tied to secrets and nonhuman identities. Today’s release extends that momentum with AI agent governance, giving customers unified visibility and control, and a future-ready foundation to adopt AI confidently and securely.
Three New Capabilities, Announced Today
1) AI Agent Insights
Expands Identity Security Insights’ market-leading identity capabilities to AI agents. Customers can discover, classify, and risk-score agents across cloud and SaaS platforms (including Salesforce Agentforce and ServiceNow), expose shadow AI, and apply Zero Standing Privilege (ZSP) and Just-In-Time (JIT) access policies to bring agents under full identity governance.
2) MCP Orchestration with BeyondTrust’s Lightweight MCP Server
A secure bridge for brokering agent actions across BeyondTrust products. This enables privilege-safe workflows, such as JIT API requests via Entitle, credential rotations in Password Safe, and future extensibility for both BeyondTrust copilots and customer-deployed LLMs.
3) Omnipresent AI Decision-Support Layer
Embedded directly into the Pathfinder Platform, this ChatGPT-like assistant interacts with customers’ identity security data to deliver real-time insights, guidance, and remediation steps. Powered by BeyondTrust Phantom Labs™ research, it helps teams make better-informed decisions without disrupting existing workflows.
Why It Matters for BeyondTrust Customers
- Move faster with AI, safely – Full visibility into AI, human, and service identities, mapped to privilege escalation paths.
- Increase productivity with integrated intelligence – Automated remediation and real-time insights reduce risk while speeding operations.
- Simplify security with one platform – Consolidated visibility, governance, and enforcement across all identities.
With these advancements, BeyondTrust extends its proven Paths to Privilege and True Privilege™ capabilities to human, machine, secrets, and now AI identities, unifying governance across the entire identity attack surface. Customers can move quickly with AI adoption, without compromise.
Most companies don’t realize how much shadow agentic AI is already operating within their businesses. BeyondTrust has expanded its Identity Security Risk Assessment to provide immediate visibility into these risks as part of the broader identity security picture. Access the complimentary Identity Security Risk Assessment to take action before attackers or compliance auditors do.
For more on BeyondTrust’s approach to securing AI, visit beyondtrust.com/solutions/ai-security.
About BeyondTrust
BeyondTrust is the global identity security leader protecting Paths to Privilege™. Our identity-centric approach goes beyond securing privileges and access, empowering organizations with the most effective solution to manage the entire identity attack surface and neutralize threats, whether from external attacks or insiders.
BeyondTrust is leading the charge in transforming identity security to prevent breaches and limit the blast radius of attacks, while creating a superior customer experience and operational efficiencies. We are trusted by 20,000 customers, including 75 of the Fortune 100, and our global ecosystem of partners.
Source: BeyondTrust