Keeper. How to implement the principle of least privilege
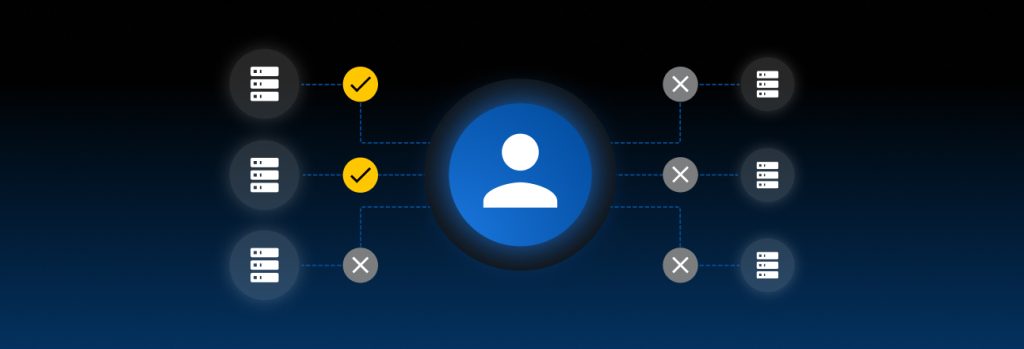
Organizations should implement the principle of least privilege to protect their sensitive data from unauthorized access. To implement the principle of least privilege, organizations need to define roles and permissions, invest in a Privileged Access Management (PAM) solution, enforce MFA, automatically rotate credentials for privileged accounts, segment networks and regularly audit network privileges. Continue reading […]
Keeper. How to implement the principle of least privilege Read More »