News
MITRE ATT&CK® stands for MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK). The MITRE ATT&CK framework is a curated knowledge base and model for cyber adversary behavior, reflecting the various phases of an adversary’s attack lifecycle and the platforms they are known to target.
MITRE Engenuity™ has released the results from the latest round of ATT&CK® Evaluations for Managed Services, assessing the abilities of 11 vendors to detect, analyze, and accurately describe real-world adversary behavior.
This was the second round of ATT&CK Evaluations for Managed Services, initially launched in 2022, to help organizations better understand how offerings like Sophos MDR can help protect them against sophisticated, multi-stage attacks.
Watch this short video for an overview of the evaluation:
What was the scope of the ATT&CK Evaluations?
MITRE Engenuity ATT&CK Evaluations are designed to simulate a representative example of how organizations should expect a managed service provider to engage with them during a sophisticated attack.
The MITRE Engenuity team emulates the behaviors of known threat actors during the evaluation. A ‘black box’ approach was used in this round, whereby MITRE did not disclose the simulated threat actor(s) or the technique scope until the assessment was complete.
This evaluation emulated tactics and techniques used by two known threat groups – menuPass and ALPHV/BlackCat – and assessed each vendor’s abilities to detect and report specific adversary activities.
In total, the evaluation comprised 172 adversary activities (sub-steps) across 15 overall steps. Note, however, that only 43 of the sub-steps – those that MITRE Engenuity considered critical for attack sequence success – were included in the results.
The evaluation focused entirely on detection and reporting. The ability to block, respond to, or remediate threats was not assessed. It’s essential, therefore, to keep in mind that adversary behaviors emulated in this evaluation may have been blocked by protection technologies (e.g., next-gen endpoint tools), which vendors needed to deactivate during the evaluation.
Evaluation participants
Eleven managed security service providers participated in this evaluation round:
| Bitdefender | BlackBerry | CrowdStrike | Field Effect |
| Microsoft | Palo Alto Networks | SecurityHQ | Secureworks |
| SentinelOne | Sophos | Trend Micro |
Sophos’ results
The results of MITRE ATT&CK Evaluations can be interpreted in multiple ways and MITRE Engenuity does not rank or declare any vendor a “winner” or a “leader”. Each vendor’s managed service reports information differently and each organization’s needs and preferences are just as important as the results themselves.
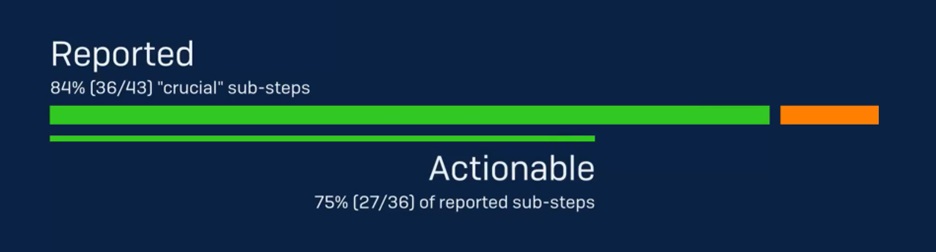
Sophos successfully “Reported” and accurately described 84% of the 43 adversary activities (sub-steps) selected by MITRE Engenuity – higher than the average among participating vendors. The majority (75%) of Sophos’ detections were also categorized as “Actionable”. “Reported” means the adversary activity was successfully identified, and sufficient context was provided. And, where the reported information also successfully addresses the “5 W’s” (Who, What, When, Where, and Why), the activity was further categorized as “Actionable”.
The results also include the number of alert emails sent by each vendor.
To ensure an effective, understandable, and actionable response, Sophos MDR focuses on providing high-value, human-written notifications containing the critical information and context that customers need to know.
During the 5-day MITRE ATT&CK Evaluation for Managed Services, Sophos MDR sent 24 emails. The average among other participants was over 120 emails, with some vendors sending more than 300 emails. Alert fatigue, caused by an overwhelming number of notifications from security solutions, is a major problem in cybersecurity. Sophos understands that your organization’s time is valuable, and when resources are limited, quality is typically better than quantity.
How to use results of MITRE Engenuity ATT&CK Evaluations
ATT&CK Evaluations are among the world’s most respected independent security tests, due in large part to the thoughtful construction and emulation of real-world attack scenarios, transparency of results, and richness of participant information.
When considering a Managed Detection and Response (MDR) service, be sure to review the results from MITRE Engenuity ATT&CK Evaluations alongside other reputable third-party proof points, including verified customer reviews, and analyst evaluations.
As you review the data available in MITRE Engenuity’s evaluation portal, look beyond the numbers and consider the following, keeping in mind that there are some questions about managed security services that the ATT&CK Evaluations cannot help you answer. For example:
- Does the service present information to you the way you want it, with high-value communications containing the critical information you need to know?
- Does the service assume you have an in-house security operations team, or can they provide a full ‘instant SOC’ with the ability to take action to eliminate threats on your behalf?
- Who will be engaging the managed service provider on a day-to-day basis? IT Administrators, experienced security analysts, or perhaps both?
- Can the service integrate with other technologies in your environment to detect and respond to multi-stage threats that extend beyond endpoints (e.g., firewall, email, cloud, identity, network, backup and recovery, etc.)?
- Does the service include full remote incident response, and are the included IR services limited to a fixed number of hours, or uncapped?
Why we participate
Sophos is committed to participating in MITRE Engenuity ATT&CK Evaluations alongside some of the best security vendors in the industry. As a community, we are united against a common enemy. These evaluations help make us better, individually and collectively, for the benefit of the organizations we defend.
Our participation in the latest evaluation further validates Sophos’ position as an industry-leading Managed Detection and Response (MDR) provider and trusted cybersecurity partner to over 22,000 customers.
To learn more about Sophos MDR and how it can support you, visit our website or speak with a security expert today.
Source: Sophos
Remote network monitoring allows IT to stay connected and monitor their organization’s network infrastructure from anywhere in the world. Remote network monitoring offers convenience and flexibility for network engineers managing off-site networks, IT consultants monitoring traffic for clients, managed service providers, or network administrators who simply couldn’t be on-prem on a given day.
By enabling IT to check the performance, security, and health of critical network devices at anytime and from anywhere, organizations can significantly minimize downtime. Instead of discovering issues upon returning to work, requiring the assistance of a local technician, or dispatching someone to the facilities, RMON allows IT to rapidly respond to network issues instantly from anywhere in the world.
What’s the Purpose of Remote Network Monitoring (RMON)?
Many modern organizations have network equipment located in multiple locations that they need to manage. Making sure routers, switches, servers, and other network equipment is up and running everywhere is critical to smooth business operations. But geographically-dispersed networks can make ensuring constant uptime a challenge for IT departments.
Also, in a mobile age, you and your staff are not always in a physical office. Sometimes you’re in the field. Sometimes you work from home. Maybe you have IT staff who work remotely and want remote network monitoring access. Can you give key IT personnel access to your network management tools from anywhere, without risking security breaches? Your organization needs the benefits of remote monitoring.
Remote network management allows IT to use tools to manage network performance no matter where your network devices (or you) are located. Think your company could benefit from remote network management and monitoring? Here are five ways remote access benefits you and your IT team.
Top 5 Benefits of Remote Network Monitoring
1. You can monitor remote offices wherever they’re located.
If your network spans multiple locations, a remote network monitoring software allows you to manage devices in every location. For instance, let’s say you manage the network for a school district with various campuses, or are monitoring local and regional branches of a financial institution. Remote monitoring tools give you visibility into how devices in your central location, as well as all the remote locations, are performing. You can also get alerts wherever and whenever performance falters. To easily distinguish office or branch locations, you can set up location-specific network maps tracking device statuses for that particular location.
Remote network management capabilities are especially helpful for companies who have a small team stationed in one spot but are responsible for managing the entire network. With remote network access, if a device goes down, you don’t have to travel to that location to troubleshoot. This saves IT administrators time, increases your productivity, and enables you to rest easy knowing the whole network is under your surveillance.
Consultants responsible for monitoring client networks and managed service providers (MSPs) also benefit from the ability to monitor a remote location without being on site.
2. IT staff in other offices can monitor the network in real time.
If you have IT team members spread out across locations who are responsible for monitoring network performance, remote access enables those IT staff in other offices, cities, branches, or even countries to view network performance in real-time—even if the software server is installed at headquarters.
This means if a device goes down at a remote location, a network guy located there can troubleshoot without necessarily getting you involved. He also doesn’t have to bother you to ask what you’re seeing on your end—he can see up-to-date network maps and metrics for himself.
3. You and your IT staff can be mobile without risking network neglect.
Having remote access to the network means your IT team doesn’t have to be on-site constantly. If you need to work from the coffee shop or at home, with remote access to the network you can still see the status of network devices on your laptop or mobile device. Mobile network monitoring keeps network data at your fingertips so you never risk outages from lack of access.
4. Access levels can be managed to ensure security.
Some network administrators may balk at the idea of remote access because of potential security threats to the network. One way to secure the network is to require encrypted authentication and make sure that every user has to log in the same way.
Another safeguard against security issues is the ability to customize user access. Most remote network monitoring tools allow you to give access at the admin or user level to certain maps or dashboards. Managing access for your users helps tremendously to keep the connection secure.
Also, find a tool that will update and provide patches whenever security holes surface. Although security threats are a fact of life, good tools will quickly notify users when a patch has been released so you can take advantage of increased security measures as soon as possible.
5. With proper connectivity, you’ll always have access.
To get remote access benefits, it simply requires… access. As long as you have direct access to the network via VPN connectivity or point to point, you’ll be able to manage and monitor all the critical devices within your network. Regardless of where you or they are located.
By allowing remote monitoring capabilities for you and your other IT network staff, you give yourself the kind of flexibility that the modern work world requires. You also gain peace of mind that no matter where you are, you can see the whole network at a glance, whether it spans a city, country, or the world.
What Does Remote Network Monitoring Software Help With?
If you’re managing the network across locations or on the go, it’s clear that remote monitoring is essential. Do you have the right tools? Remote network monitoring software can give you the visibility you need to monitor a widespread network.
Create a Dynamic Network Map
Remote network monitoring software like Intermapper allows you to create a dynamic network map, offering a real-time view of your network’s status. With color-coded indicators, you can easily see which devices are functioning and which are experiencing issues. Various map layouts and icon options let you customize the view to reflect your unique IT environment.
Minimize Impact on Users
Remote network monitoring software keeps you informed by sending real-time alerts via text, email, sound, and more whenever there’s a problem. This enables you to address and resolve technology issues swiftly, minimizing impact on users or customers.
Troubleshoot Problems Quicker
Quickly identify and resolve problems across your distributed network in seconds rather than hours. This efficiency saves you and your IT team time, reduces frustration, and ensures customer and user satisfaction.
Source: Fortra
The main difference between passkeys and 2FA is that passkeys completely remove the need for individuals to enter a password, whereas 2FA enhances the security of an account by requiring an additional method of authentication in addition to a traditional username and password.
Continue reading to learn more about the differences and similarities between passkeys and 2FA, and which is more secure.
What are passkeys?
Passkeys are a type of passwordless authentication that enables users to log in to accounts and applications without entering a password. Instead, passkeys leverage how you unlock your devices such as by entering a passcode, using your biometrics (e.g. Face ID, fingerprint) or using a swipe pattern.
What is 2FA?
Two-Factor Authentication (2FA) is a second form of authentication that is used to verify your identity after you’ve already entered your username and password correctly. When 2FA is enabled on an account, it adds an extra layer of security to ensure that only you have the means to access your account. Some examples of 2FA include the following:
- Time-based One-Time Password (TOTP) codes
- Biometric authentication
- Hardware security keys
- Security questions
- Passkeys used as a second factor
Key differences between passkeys and 2FA
Here are some of the key differences between passkeys and 2FA.
Passkeys completely remove the need to enter a password, 2FA doesn’t
When you enable passkeys on your account, you no longer need to enter a password. Since passwords are removed from the login process, your account is no longer susceptible to password-related attacks, phishing and data breaches. This differentiates from 2FA which enhances the security of your password-protected account by requiring an additional verification method, meaning your password is still vulnerable to compromise. However, this is what makes 2FA important to enable on your accounts since it greatly reduces the risk of your account becoming breached due to a compromised password.
Passkeys aren’t vulnerable to being intercepted, some 2FA methods are
Another key difference between passkeys and 2FA is that because passkeys are automatic (they don’t require the user to manually type anything), they’re not vulnerable to being intercepted, whereas some 2FA methods are vulnerable. Some of the most commonly used 2FA methods are 2FA codes sent through text message and email. While these 2FA methods are convenient, they’re also the least secure since they can be easily intercepted by cybercriminals, which increases the likelihood of your account being compromised. Cybercriminals can also use phishing tactics to get victims to reveal their 2FA codes.
While passkeys and 2FA have some differences, they share the similarity of being used to make accounts more secure by eliminating one-factor authentication, which refers to only signing in with a username and password.
Are passkeys more secure than traditional 2FA methods?
Yes, passkeys are more secure than traditional 2FA methods because they remove passwords, which are susceptible to password-related attacks, are phishing-resistant and support 2FA by design. Many people fail to enable 2FA because they find it difficult to use or don’t like the additional time it takes to log in with it. This often leads to people only securing their accounts with passwords and nothing else, making it much easier for cybercriminals to gain access to them.
With passkeys, users no longer need to worry about their accounts being less secure because they don’t want to enable 2FA. After all, passkeys require authentication before being used so 2FA is a part of the passkey login process.
Use passkeys to keep your online accounts secure
Passkeys should be set up on every website and app they’re available on. To see which apps and websites currently support the use of passkeys as a sign-in or Multi-Factor Authentication (MFA) method, check out our Passkeys Directory.
For websites and apps that don’t currently support passkeys, you’ll have to ensure your passwords are strong and have 2FA enabled. A password manager like Keeper® can aid you with creating and managing all of your passwords, passkeys and 2FA codes. By storing your passwords, passkeys and 2FA codes in Keeper, you’ll be able to access them from anywhere, no matter what device you’re using, making the login process more secure and convenient.
To see how Keeper Password Manager can aid you with securely managing your passwords, passkeys and 2FA codes, start a free 30-day trial today.
Source: Keeper
Network monitoring involves the continuous surveilling of computer networks to detect issues like slow traffic or component failure as well as alerting administrators to these issues to prevent disruptions and prolonged downtime.
What Are the Benefits of Network Monitoring?
Implementing network monitoring offers several benefits to organizations. Firstly, it allows them to stay ahead of outages by providing visibility into network performance, helping to identify potential issues before they impact end users. Organizations like this medical device company rely heavily on network monitoring to alert them to potential upcoming outages and assist them with troubleshooting how to resolve them so that operations are not interrupted.
Secondly, network monitoring enables faster issue resolution. In network emergency situations where time is of the essence, it’s important for IT to be able to quickly pinpoint the source of a problem. The live network maps and performance metric analysis that network monitoring tools are often quipped with provide the visibility necessary to quickly locate the root of an issue and resolve it. Organizations like Vasttrafik – a Swedish transportation service – leverage the visibility that network monitoring provides them to keep their services up and running 24/7.
Moreover, network monitoring delivers immediate return on investment (ROI) by alleviating the burden of manually mapping and monitoring networks for IT teams and reducing the costs associated with outages. Greater Media Detroit’s use of network monitoring exemplifies how it enhances end-user experiences and minimizes disruptions, translating into tangible benefits for organizations.
Additionally, as IT environments evolve with technological advancements and increased connectivity, network monitoring has become indispensable in managing growing and changing networks. Take the education sector for example: As educators use mobile devices, online applications, and other EdTech to create innovative learning experiences, network uptime has never been more important. That’s why institutions like Decatur City Schools are turning to network monitoring to effectively manage the proliferation of connected devices and ensure smooth network performance amidst complexities and transitions.
Why Do You Need Network Monitoring?
Network monitoring is proactive by nature, meaning its primary use is for pointing out potential performance issues and bottlenecks before they happen. Without network monitoring, organizations are opening themselves up to a world of dangerous and damaging possibilities.
Human error and configuration issues typically go hand in hand, and commonly result in minor performance issues that snowball and result in network outages and disruptions. Even the best network professionals don’t always get it right, which is why its important to support them with network monitoring technology.
A lack of network visibility is another dangerous side effect that comes with an absence of network monitoring. A survey by Forrester indicated that 81% of IT leaders believe network visibility is essential for strong network security and response. In other words, organizations cannot afford lengthy fixes of critical IT issues and could save a fortune by investing in network visibility technology.
How Does Network Monitoring Work?
The first phase of network monitoring involves the discovery of devices and the mapping of their connections. Depending on your monitoring needs, you can customize you map to show your entire distributed network, just an IP address range, or even a single subnet. After this step, you should have a clear picture of your entire network and how your devices relate to one another.
Next, you must define performance benchmarks for your network devices so that a polling engine has a point of comparison to base alerting decisions off of. At this stage, you can also define the cadence in which you prefer to monitor, or poll, your devices based on their priority level. For example, laptops may require less frequent monitoring than network infrastructure components like routers and servers.
After you’ve gained visibility into your network and you’ve added your parameters and specifications for how you would like to monitor your devices, your network will then rely on network monitoring protocols used in conjunction with a network monitoring tool to execute the actual monitoring and alerting functions.
How Many Types of Network Monitoring Are There?
SNMP
The Simple Network Management Protocol (SNMP) is an application layer protocol that is used to collect data related to network changes or statuses of network-connected devices.
ICMP
The Internet Control Message Protocol (ICMP) is used by network devices such as routers to communicate error information and other updates to other network devices.
CDP
The Cisco Discovery Protocol (CDP) is a link layer device protocol used to share information with other Cisco equipment.
LLDP
The Link Layer Discovery Protocol (LLDP) is another Layer 2 protocol used in non-cisco related environments such as Netgear.
What Is the Most Common Tool Used for Network Monitoring?
A Network Monitoring System (NMS) is the most common tool used for network monitoring. They offer robust network monitoring capabilities including monitoring and recording network performance, forecasting and detecting issues or bottlenecks, and alerting network administrators to urgent events.
NMS tools most frequently utilize application layer protocols like SNMP to collect change data or statuses from network-connected devices like routers, switches, servers, laptops, and more. Some of the most popular examples of NMS tools include:
- Nagios is one of the favorites in the open-source community for network monitoring. If you have a strong development skillset, this tool could be a great fit for you. Otherwise, open-source network monitoring tools like Nagios and Zabbix can be time consuming and expensive to set up.
- SolarWinds is an enterprise-level NMS that could also be considered a Network Management Software because it performs configuration management, application management, and server management. Network Performance Monitor is the specialized NMS component of SolarWinds. SolarWinds is great for large organizations with dedicated network administrators. For those with a smaller budget and less staff, SolarWinds may not be the right choice.
- PRTG Network Monitor is an enterprise network monitoring solution that runs exclusively on Windows. It performs the critical functions of an NMS – such as helping stay ahead of outages and providing network visibility – while also offering Layer 3 mapping and automatic device discovery.
- Intermapper is an enterprise NMS that is much easier to implement and operate than larger, more robust NMS tools. Intermapper offers real-time monitoring and alerting as well as customizable mapping and probing – so that you can track the status of anything that’s connected to your network.
These tools vary in features, scalability, and pricing, allowing organizations to choose the one that best fits their needs and budget.
Source: Fortra
Sophos’ latest annual study of the real-world ransomware experiences of retail organizations explores the full victim journey, from attack rate and root cause to operational impact and business outcomes.
This year’s report sheds light on new areas of study, including an exploration of ransom demands vs. ransom payments and how often retail organizations receive support from law enforcement bodies to remediate attacks.
Download the report to explore the full findings.
Attack rates have dropped, but recovery is more expensive
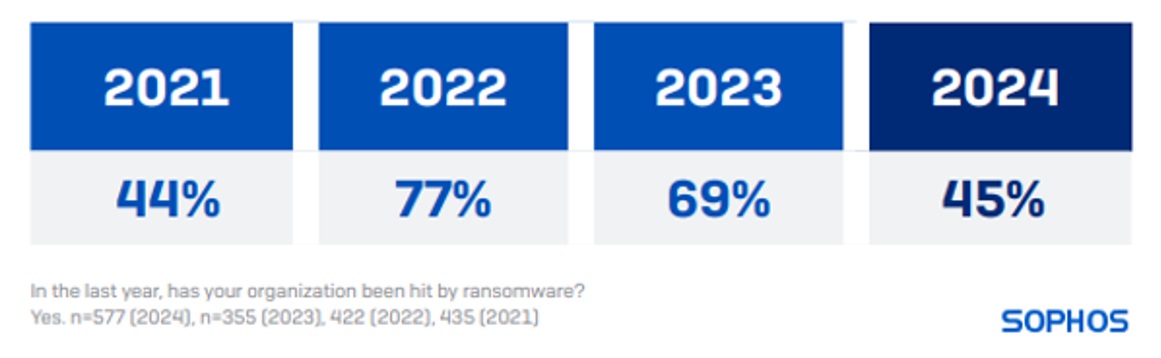
45% of retail organizations reported they were hit by ransomware last year. This is a notable and welcome drop from the 69% and 77% ransomware rates reported in 2023 and 2022, respectively.
92% of retail organizations hit by ransomware in the past year said that the cybercriminals attempted to compromise their backups during the attack. Of the attempts, 47% were successful.
56% of ransomware attacks on retail organizations resulted in data encryption, a considerable drop from the 71% reported in 2023 and 68% in 2022. The data encryption rate in retail was notably lower than the global cross-sector average of 70% and the lowest across all sectors other than financial services (49%).
Retail reported the second-highest data extortion rate (5%) jointly with financial services, where the data was not encrypted but they were held for ransom.
The mean cost for retail organizations to recover from a ransomware attack was $2.73M in 2024, an increase from the $1.85M reported in 2023.
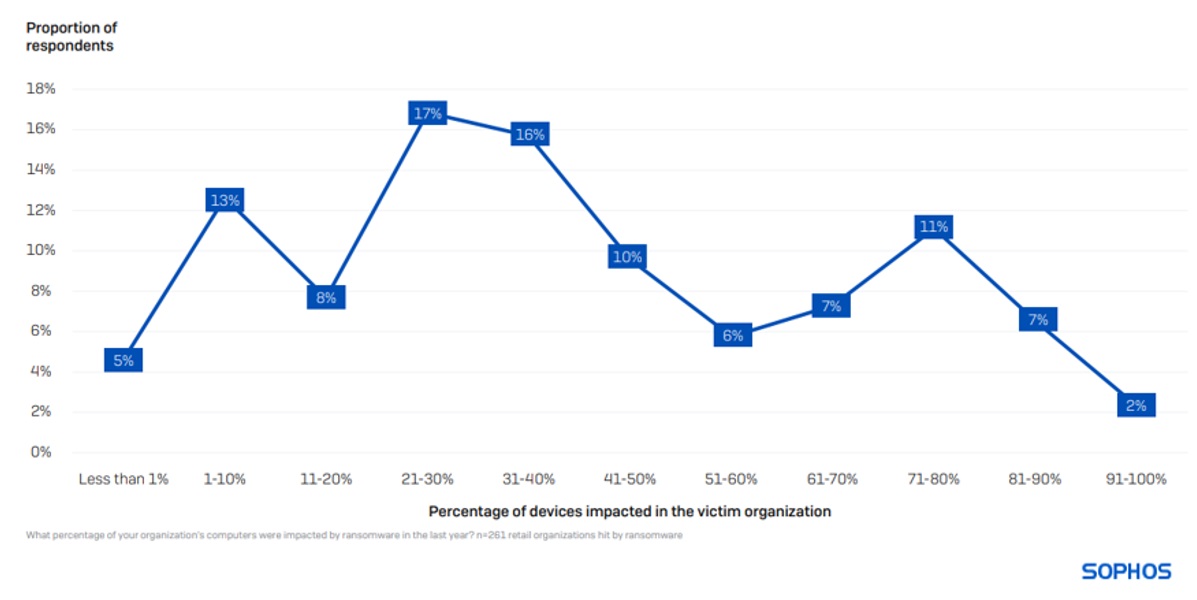
Devices impacted in a ransomware attack
On average, 40% of computers in retail are impacted by a ransomware attack. Having your full environment encrypted is extremely rare, with only 2% of organizations reporting that 91% or more of their devices were impacted.
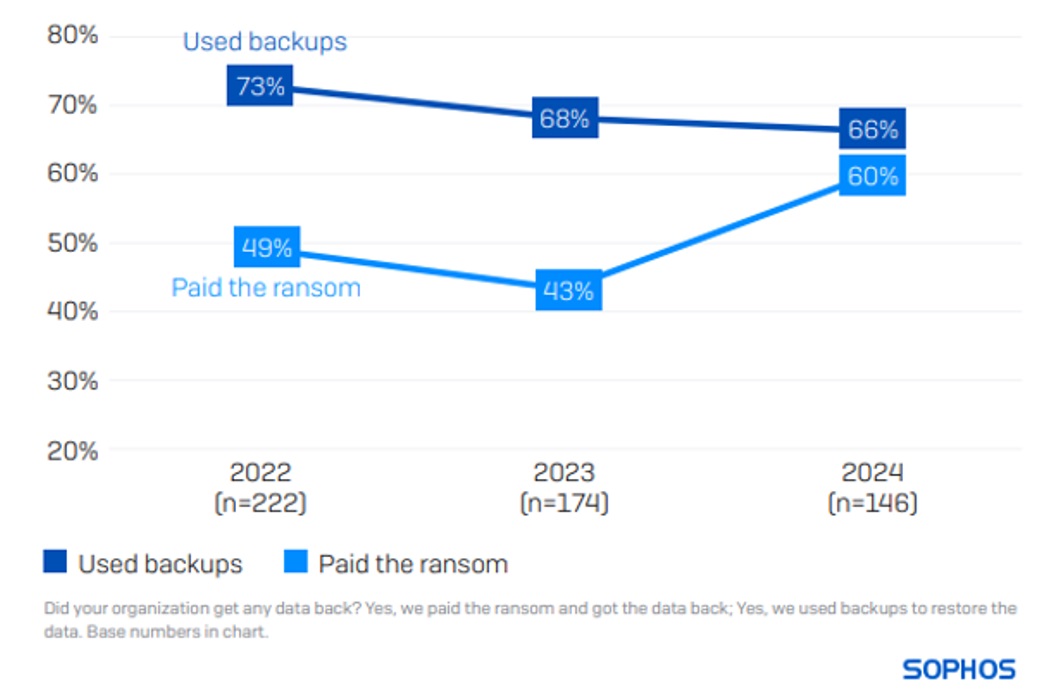
Retail’s propensity to pay the ransom has increased
66% of retail organizations restored encrypted data using backups, while 60% paid the ransom to get data back. The use of backups in retail organizations has fallen slightly for the second consecutive year, but what is more concerning is the sector’s propensity to pay the ransom, which has increased considerably over the last year.
A notable change over the last year is the increase in the propensity for victims to use multiple approaches to recover encrypted data (e.g., paying the ransom and using backups). In this year’s study, over one-third of retail organizations (39%) that had data encrypted reported using more than one method, more than double the rate reported in 2023 (16%).
Retail victims rarely pay the initial ransom sum demanded
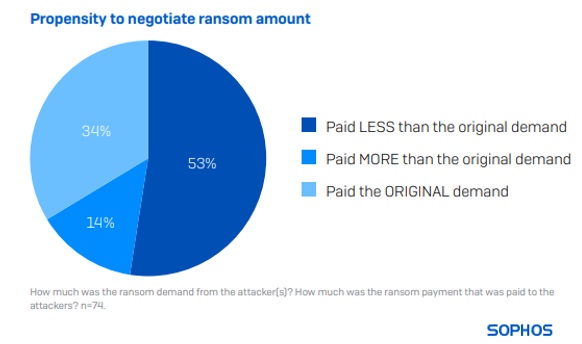 78 retail respondents whose organizations paid the ransom shared the actual sum paid, revealing that the average (median) payment has decreased by 68% over the last year, from $3M to $950K.
78 retail respondents whose organizations paid the ransom shared the actual sum paid, revealing that the average (median) payment has decreased by 68% over the last year, from $3M to $950K.
Only one-third (34%) of respondents said that their payment matched the original request. 53% paid less than the original demand, while only 14% paid more.
Download the full report for more insights into ransom payments and many other areas.
About the survey
The report is based on the findings of an independent, vendor-agnostic survey commissioned by Sophos of 5,000 IT/cybersecurity leaders across 14 countries in the Americas, EMEA, and Asia Pacific, including 577 from the retail sector. All respondents represent organizations with between 100 and 5,000 employees. The survey was conducted by research specialist Vanson Bourne between January and February 2024, and participants were asked to respond based on their experiences over the previous year.
Source: Sophos
We’re pleased to announce the general availability of Sophos DNS Protection. This cloud-based service, managed via Sophos Central, provides an added layer of network protection and is available at no extra charge to all Xstream Protection licensed Sophos Firewall customers.
Great value for Sophos Firewall customers
Sophos DNS Protection adds tremendous new value for our Sophos Firewall customers, who can take advantage of this protection at no extra charge as it’s part of our Xstream Protection Bundle. It enables you to potentially consolidate and save from using another third-party DNS provider or start using a great DNS protection solution without having to pay extra.
What you get: enhanced internet and web security
Sophos DNS Protection adds another layer of security to every network. It works to instantly block access to unsafe and unwanted domains across all ports, protocols, and applications at the earliest opportunity – from both managed and unmanaged devices. DNS protection perfectly complements and augments your existing network security and policy enforcement tools. Sophos DNS Protection can be deployed in just a few minutes.
Sophos DNS Protection is a globally accessible domain name resolution service with integrated policy controls and reporting in Sophos Central. Sophos DNS Protection is backed by SophosLabs’ AI-powered threat intelligence, providing real-time world-wide protection from high-risk domains. As soon as a malicious domain is discovered, it is shared across customers instantly, providing immediate protection for all. By using Sophos DNS Protection in place of your existing public DNS resolver, you can prevent any devices on your network from accessing domains associated with security threats and other unwanted websites controlled through policy.
Protection for networks
Access to the Sophos DNS Resolver is based on the originating public IPv4 address of the DNS queries. Hence, protecting individual devices for remote workers that move from network to network (or site to site) is not viable at this time.
Dynamic IP addresses are supported when used with a dynamic DNS provider.
Integrated dashboarding and reporting
Sophos DNS Protection also provides in-depth visibility into the domains visited from your network, with comprehensive dashboarding and reporting.
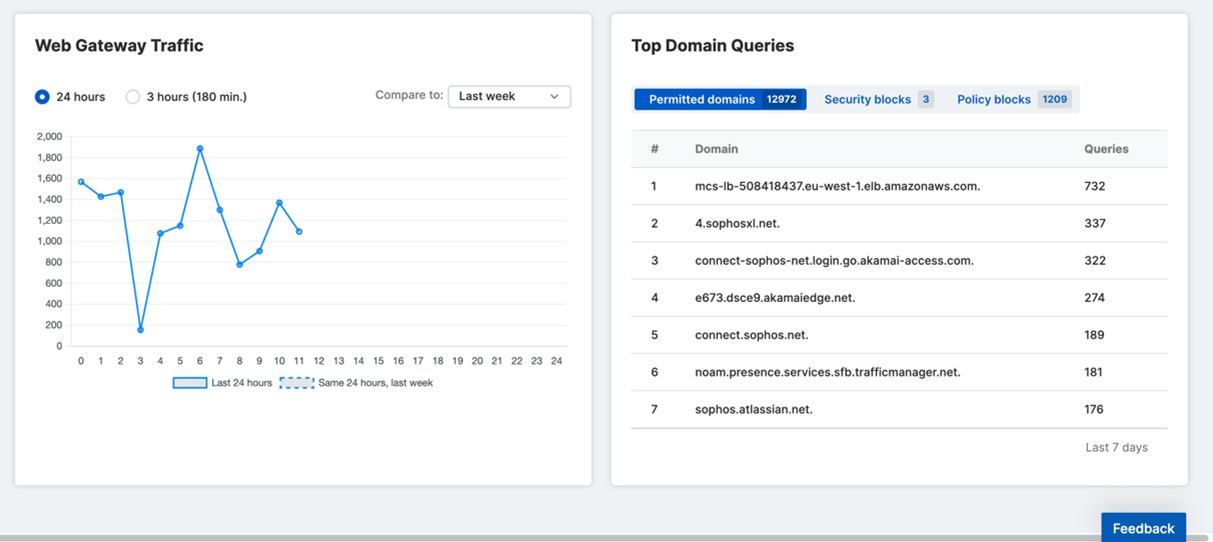
Full reporting with all the same options as Central Firewall Reporting Advanced is also included:
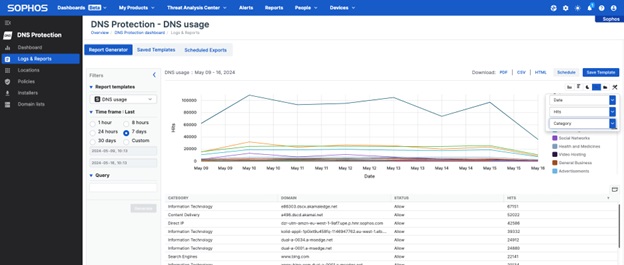
Cross-product integration
Sophos DNS Protection’s log data and intelligence are also shared with the Sophos data lake for Sophos XDR and MDR threat-hunting analysts to help detect active adversaries and threats operating on the network.
Getting started
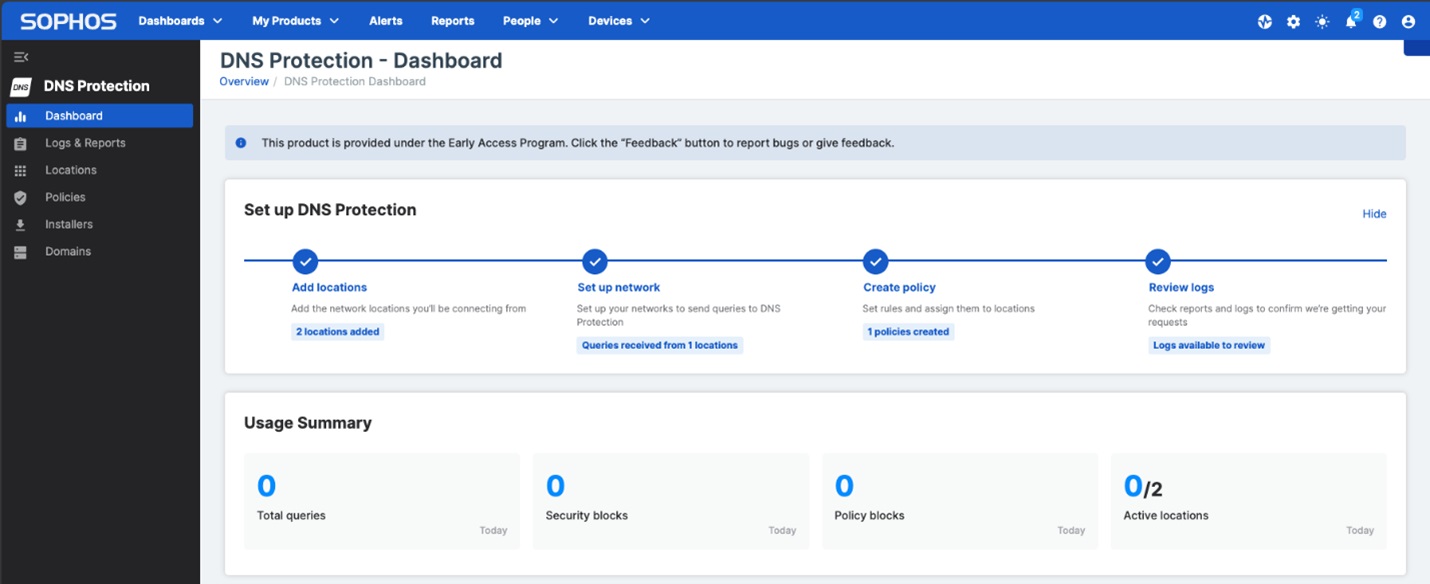
Sophos DNS Protection is available at no additional charge to all licensed Sophos Firewall customers who have the Xstream Protection bundle. If you need to upgrade your license, speak to your Sophos partner or representative.
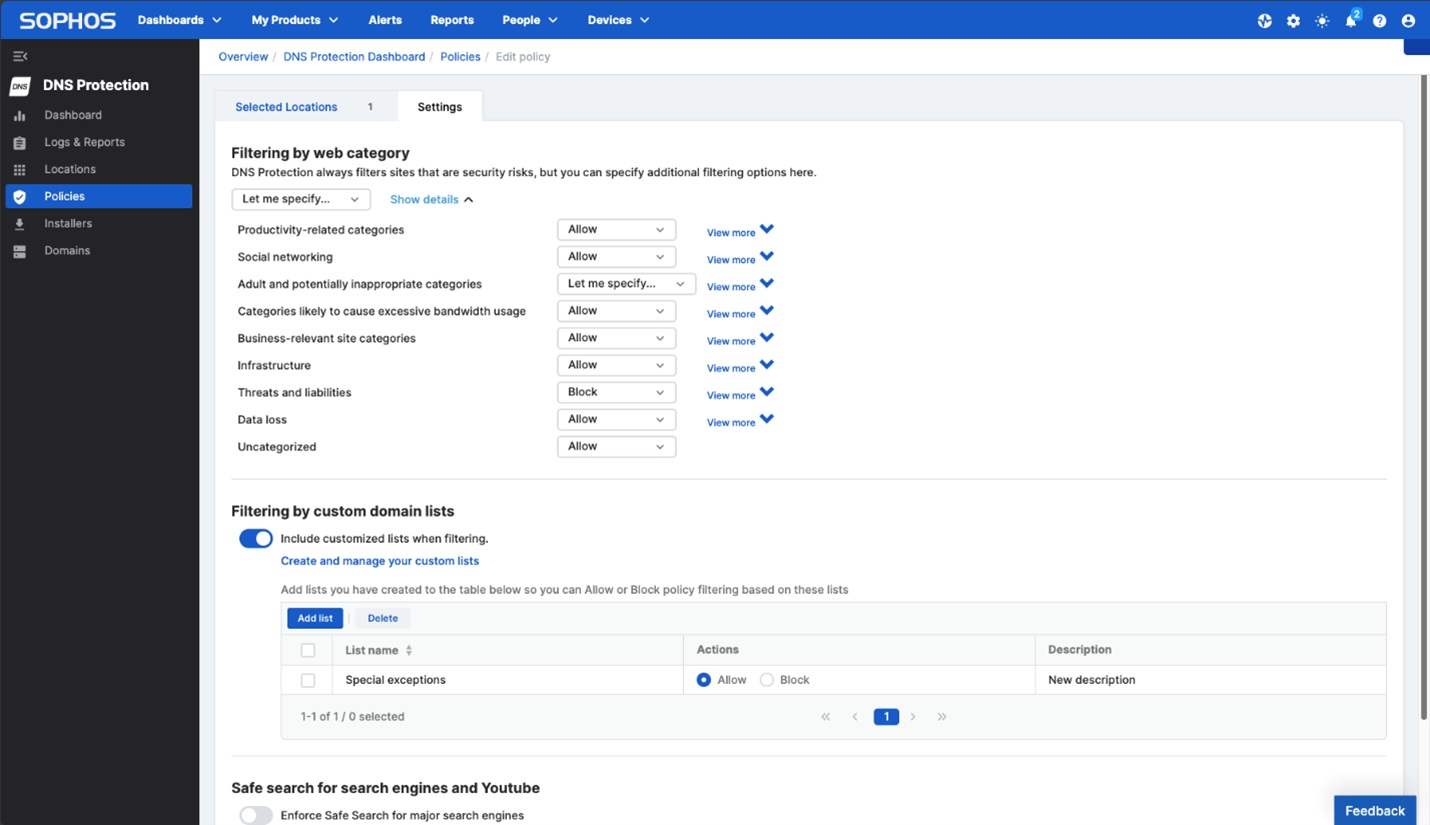
Getting started with Sophos DNS Protection is easy: simply add locations, set DNS settings, create a policy, and go! Watch this video to see the steps for yourself:
To ensure a great customer experience, DNS Protection will be made available in stages over the coming weeks. If you have a Sophos Firewall with Xstream protection and don’t yet see it in Sophos Central right away, please be patient while we ramp up availability.
Consult the full documentation for additional information. And if you don’t yet have a Sophos Firewall, get started today with a free trial!
Source: Sophos
Businesses are increasingly turning to Managed Service Providers (MSPs) for the expert support needed to secure their organization in the face of inevitable cyberattacks. Illustrating the accelerating demand, Canalys predicts that managed services revenue will grow at least 14% in 2024*.
In this fast-growing market, the growth opportunities for MSPs are considerable. Our inaugural MSP Perspectives 2024 report identifies the biggest challenges facing MSPs together with openings to accelerate business and profitability.
From reducing day-to-day overheads through management platform consolidation, to optimizing engagement with MDR vendors, and leveraging the interplay between cyber defenses and cyber insurance, the report highlights opportunities for MSPs to advance their businesses while elevating their clients’ protection against ransomware and breaches.
Insights from 350 MSPs across four countries
MSP Perspectives 2024 shares the outcomes of an independent survey of 350 MSPs in the U.S., UK, Germany and Australia, conducted in March 2024.
The report provides fresh insights into the reality of MSP operations today, focusing on five key areas of MSP business: RMM and PSA tools; cybersecurity management; MDR services; challenges and perceived risks; and impact of cyber insurance.
Read the report to explore the full findings and check out some of the key learnings below.
Biggest MSP challenges and risks
The survey revealed that the biggest day-to-day challenge facing MSPs is keeping up with the latest cybersecurity solutions/technologies, cited by 39% of those surveyed. MSPs also indicated that hiring new cybersecurity analysts to keep up with customer growth and keeping pace with the latest cyberthreats are among their top challenges.
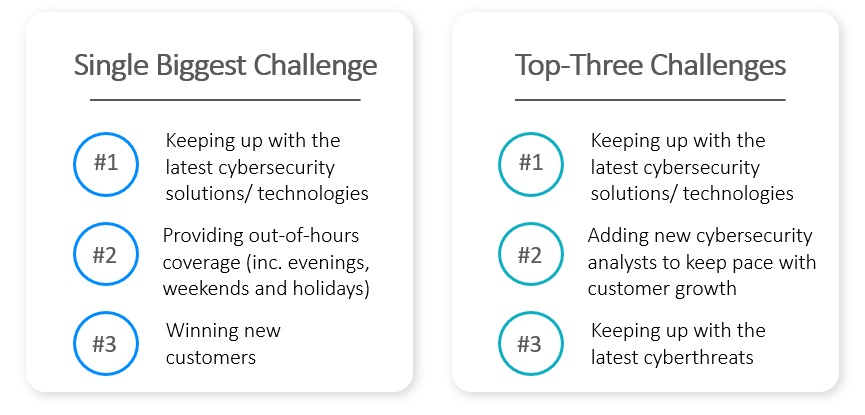
The data also shows that shortage of in-house cybersecurity skills is perceived by MSPs to be the single biggest cybersecurity risk to both their own business and their clients’ organizations. They also consider stolen access data and credentials and unpatched vulnerabilities to be top-three risks for their customers.
As Scott Barlow vice president of MSP at Sophos, comments
“The speed of innovation across the cybersecurity battleground means it’s harder than ever for MSPs to keep up with threats and the cyber controls designed to stop them. When you couple this with a global skills shortage, which has made it infinitely more difficult for many MSPs to attract and retain cybersecurity analyst resources, its unsurprising that MSPs feel unable to keep pace with the changing threat landscape.”
Streamlining partnerships
MSPs are streamlining their cybersecurity partnerships, typically working with a small number of vendors to secure their clients. The study revealed that over half (53%) of MSPs work with just one or two cybersecurity vendors, rising to 83% that use between one and five.
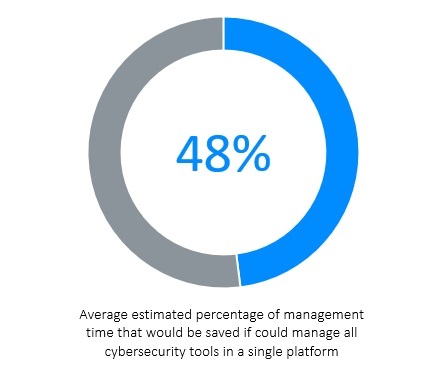
Reflecting the effort and overhead of running multiple platforms, MSPs estimate that they could cut their day-to-day management time by 48% if they could manage all their cybersecurity tools from a single platform.
Delivery of MDR services
In response to today’s complex threat landscape, there is growing demand for managed detection and response (MDR) services to provide always-on coverage. Currently 81% of MSPs offer an MDR service, and almost all (97%) MSPs that do not currently offer MDR plan to add it to their portfolio in the coming years.
66% of MSPs use a third-party vendor to deliver the MDR service and a further 15% deliver jointly through their own SOC and a third-party vendor. Topping the list of essential capabilities in a third-party MDR provider is the ability to provide a 24/7 incident response service.
Accelerating MSP growth with the Sophos MSP program
The data shows that MSPs are strengthening their proposition and reducing overheads by amalgamating the platforms they use and engaging with third-party MDR vendors to expand their service offerings.
Sophos gives MSPs a complete portfolio of industry-best, fully managed security services and solutions, all managed through the Sophos Central security platform. Innovative, adaptive defenses and a complete MSP cybersecurity system deliver cyber confidence that empowers success.
To learn more visit www.sophos.com/msp or request an MSP Experience demo.
Source: Sophos
Many organizations are planning to adopt passwordless authentication or are already in the process of doing so. Passwordless authentication has many benefits such as being more secure than traditional passwords, providing a better user experience, reducing helpdesk costs and enhancing productivity.
Continue reading to learn more about the benefits of implementing passwordless authentication in your organization and how Keeper® helps with its implementation.
What is passwordless authentication?
Passwordless authentication verifies your identity to gain access to an account or system without entering a password. Passwordless authentication allows users to securely log in by verifying that an account belongs to them through other means such as their biometrics (fingerprints and facial recognition), one-time codes sent to a trusted device or hardware tokens. Since passwordless authentication eliminates having to enter a password, it’s considered a better and more secure authentication method.
Top 4 benefits of passwordless authentication
These are the top four benefits of adopting passwordless authentication.
1. More secure than traditional passwords
Passwordless authentication is more secure than using traditional passwords because it removes the risks associated with passwords. When using passwords to log in to accounts and systems, people tend to use weak passwords and reuse passwords across multiple accounts. This places those accounts at a greater risk of becoming compromised, which can lead to account takeovers and data breaches. By removing passwords from the login process, accounts are no longer susceptible to being compromised through password-related attacks such as password cracking and phishing.
2. Better user experience
Passwordless authentication also provides a better user experience since it takes away the pain of people having to remember multiple passwords. Passwords often cause individuals to experience password fatigue, which is a term used to describe the overwhelming stress people feel due to having to remember passwords on their own. Since passwordless authentication doesn’t require people to create or remember passwords, it provides a better user experience.
3. Reduces helpdesk costs
A study by Yubico found that organizations spend an average of $5.2 million per year on password resets. However, this only considers the hard costs of password resets, not the soft costs, which take into account the wide-reaching effects of password resets like the loss in productivity. Since passwordless authentication removes passwords from the login process, password resets become non-existent, significantly reducing the helpdesk costs related to them.
4. Enhances productivity
As mentioned above, one of the soft costs associated with password resets is the loss in productivity for both users and IT administrators. Instead of helping users reset their passwords because they’ve forgotten them, IT teams can spend their time improving their organization’s infrastructure. Additionally, instead of users waiting for their password to be reset, they can continue performing their regular job duties. Adopting passwordless authentication in your organization can remove these roadblocks by eliminating the root of the problem – passwords. By doing this, every employee can focus their time and energy on profitable projects.
Go fully passwordless with the help of Keeper
It can be challenging for organizations to go passwordless because some websites and applications don’t support passwordless authentication methods. However, this doesn’t mean organizations shouldn’t go passwordless; instead, they should look into solutions like Keeper that make going passwordless seamless and secure.
With Keeper, organizations can achieve full coverage, security and access control across every application and website without end-users ever needing to enter a password. Keeper connects Single Sign-On (SSO), IdP and passwordless solutions with passkey management, providing users with a seamless and secure login experience. Even for websites that don’t support passwordless login, Keeper’s autofill feature will log users in automatically.
To learn more about how Keeper can enable your organization to go passwordless, schedule a demo today.
Source: Keeper
In the early years of ransomware, many (if not, most) victims were reluctant to admit publicly that they had been hit for fear of exacerbating the business impact of the attack. Concerns about negative press and customer attrition led many organizations to keep quiet.
More recently, the situation has changed, with ransomware victims increasingly willing to acknowledge an attack. This development is likely driven in part by the normalization of ransomware – our (wholly anonymous) State of Ransomware reports have revealed attack rates above 50% for the last three years and public acknowledgement of an attack by well-known brands is commonplace. In short, being hit by ransomware is no longer perceived to be an automatic badge of shame.
The increase in mandatory reporting of attacks in many jurisdictions is also likely driving greater disclosure, particularly in the public sector which is most impacted by these regulations and requirements.
Although there has been a general sense that reporting has increased, detailed insights and regional comparisons have been hard to come by – until now. This year’s Sophos State of Ransomware survey shines light into this area, revealing for the first time how reporting levels and official responses vary across the 14 countries studied.
Reporting a ransomware attack is a win-win
The nature and availability of official support when dealing with a ransomware attack vary on a country-by-country basis, as do the tools to report a cyberattack. U.S. victims can leverage the Cybersecurity and Infrastructure Security Agency (CISA); those in the UK can get advice from the National Cyber Security Centre (NCSC); and Australian organizations can call on the Australian Cyber Security Center (ACSC), to name but a few.
Reporting an attack has benefits for both the victim and the official bodies that look to support them:
- Immediate remediation support: Governments and other official bodies are often able to provide expertise and guidance to help victims remediate the attack and minimize its impact
- Policy guidance insights: Protecting businesses from cybercrime, including ransomware, is a major focus for many governments around the globe. The more insights officials have into attacks and their impact, the better they can guide policies and initiatives
- Attacker takedown enablement: Timely sharing of attack details assists national and pan-national efforts to takedown criminal gangs, such the Lockbit operation in February 2024
With these benefits in mind, the insights from the survey make encouraging reading.
Insight 1: Most ransomware attacks are reported
Globally, 97% of ransomware victims in the last year reported the attack to law enforcement and/or official bodies. Reporting rates are high across all countries surveyed with just ten percentage points between the lowest rate (90% – Australia) and the highest (100% – Switzerland).

The findings reveal that, while annual revenue and employee count have minimal impact on propensity to report an attack, there are some variations by industry. In sectors with high percentages of public sector organizations, almost all attacks are reported:
- 100% state and local government (n=93)
- 6% healthcare (n=271)
- 5% education (n=387)
- 4% central/federal government (n=175)
Distribution and transport has the lowest reporting rate (85%, n=149), followed by IT, technology and telecoms (92%, n=143).
Insight 2: Law enforcement almost always assists in some way
For the organizations that do report the attack, the good news is that law enforcement and/or official bodies almost always get involved. Overall, just 1% of the 2,974 victims surveyed said that they did not receive support despite reporting the attack.
Insight 3: Support for ransomware victims varies by country
Respondents that reported the attack received support in three main ways:
- Advice on dealing with the attack (61%)
- Help investigating the attack (60%)
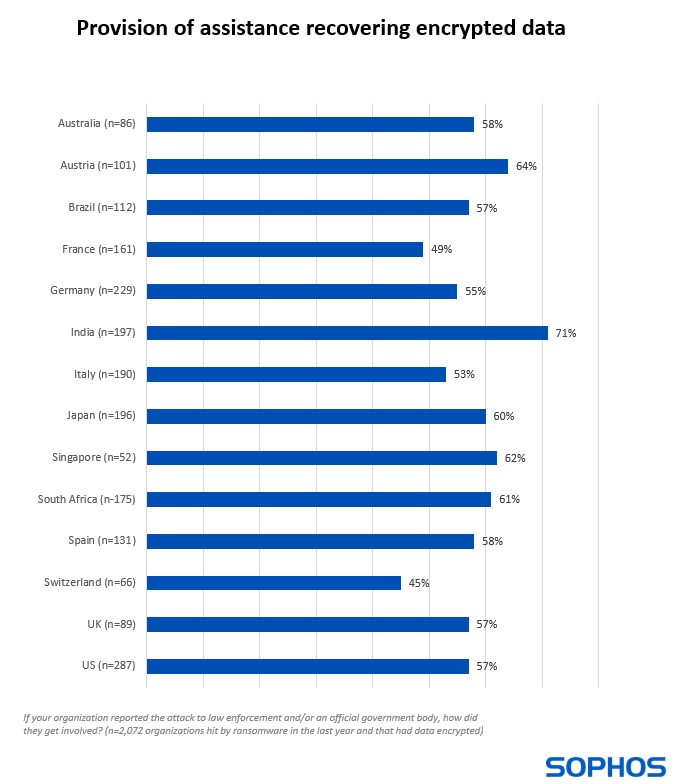
- Help recovering data encrypted in the attack (40% of all victims and 58% of those that had data encrypted)
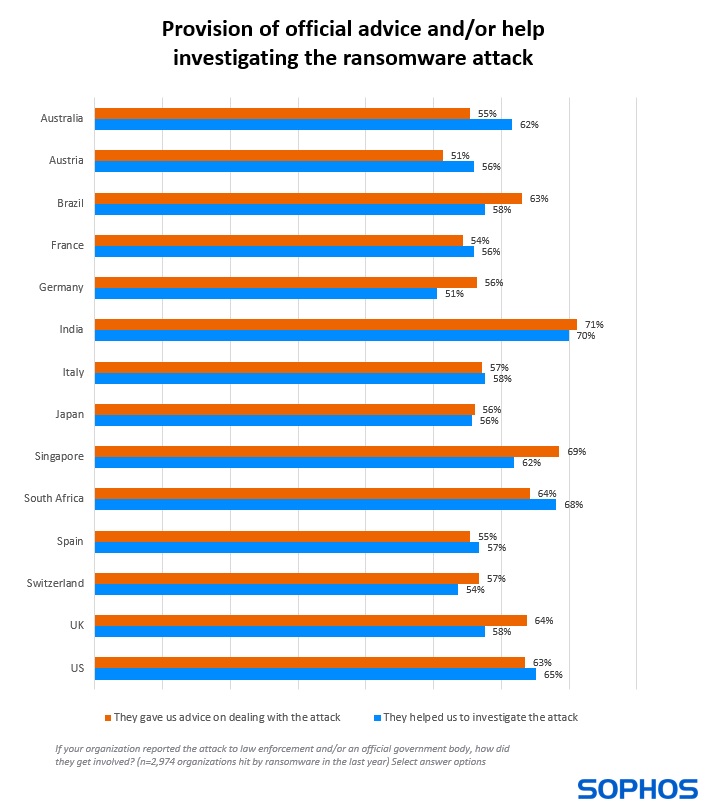
Diving deeper, we see that the exact nature of law enforcement and/or official body involvement varies according to where the organization is based. While more than half of victims received advice on dealing with the attack across all countries surveyed, organizations in India (71%) and Singapore (69%) reported the highest level of support in this area.
Indian respondents also reported the highest level of support in investigating the attack (70%) followed by those in South Africa (68%), while the lowest rate was reported in Germany (51%).
Among those that had data encrypted, more than half globally (58%) received support in recovering their encrypted data. India continues to top the chart, with 71% of those that had data encrypted receiving assistance in recovering it. Notably the countries with the lowest propensity for victims to receive help recovering encrypted data are all in Europe: Switzerland (45%), France (49%), Italy (53%) and Germany (55%).
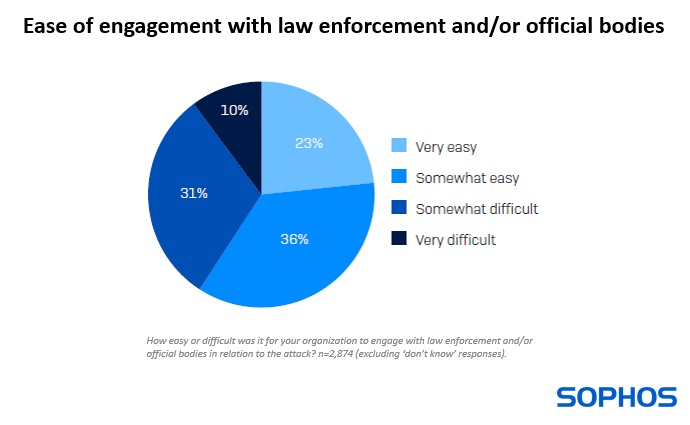
Insight 4: Engaging with law enforcement is generally easy
Encouragingly, more than half (59%) of those that engaged with law enforcement and/or official bodies in relation to the attack said the process was easy (23% very easy, 36% somewhat easy). Only 10% said the process was very difficult, while 31% described it as somewhat difficult.
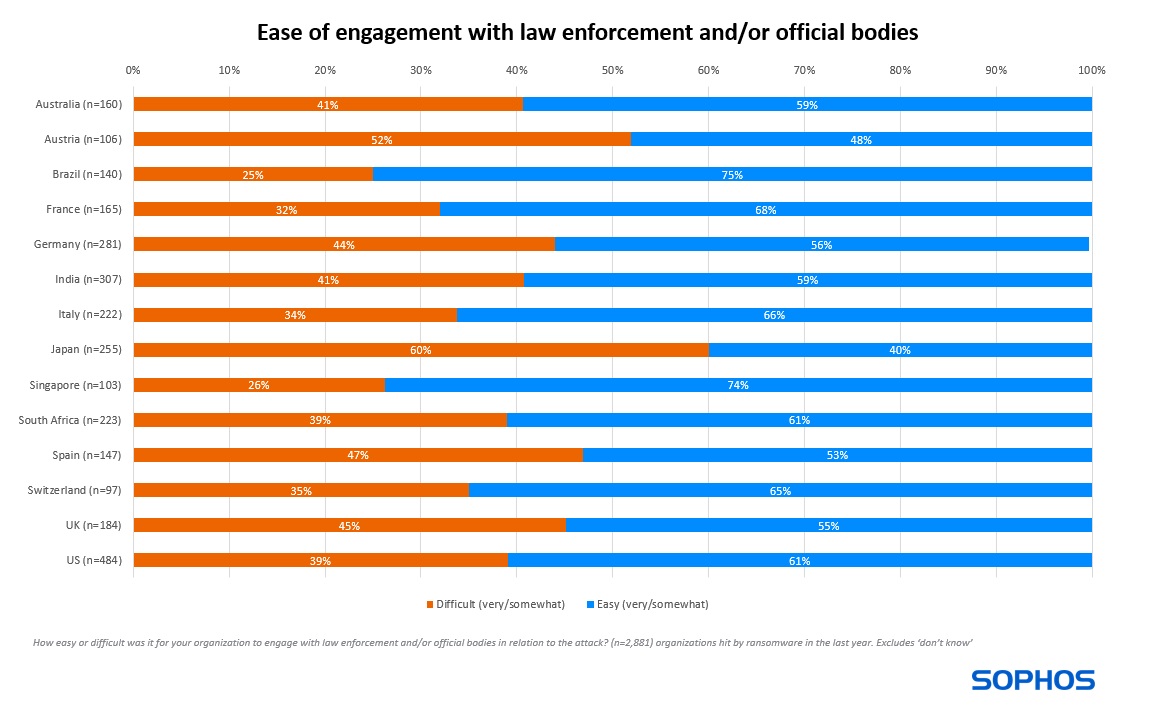
Ease of engagement also varies by country. Those in Japan were most likely to find reporting difficult (60%), followed by those in Austria (52%). Japanese respondents also had the highest propensity to find it “very difficult” to report the attack (23%). Conversely, respondents in Brazil (75%) and Singapore (74%) were most likely to find it easy to engage, while Italian organizations had the highest percentage that found it “very easy” (32%).
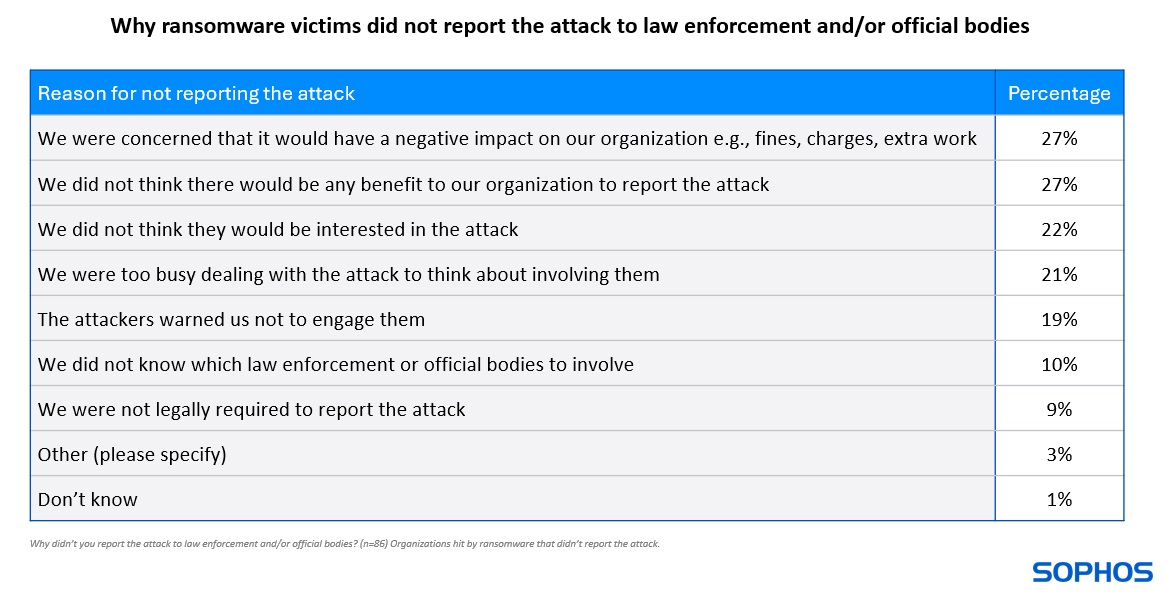
Insight 5: There are myriad reasons attacks are not reported
There were a range of reasons why 3% (86 respondents) did not report the attack, with the two most common being concern that it would have a negative impact on their organization, such as fines, charges, or extra work (27%), and because they did not think there would be any benefit to them (also 27%). Several respondents provided verbatim feedback that they did not engage official bodies as they were able to resolve the issue in-house.
Conclusion
The survey findings have revealed that reporting of ransomware attacks is very common, and victims almost always receive support as a result. Hopefully, these findings will encourage any organization that does fall victim in the future to notify their relevant body/ies. While it is generally easy for organizations to report an attack, there are also opportunities to facilitate the process at what is, inevitably, a very stressful time. As Chester Wisniewski, director, Global Field CTO, Sophos, comments, “Criminals are successful in part due to the scale and efficiency with which they operate. To beat them back, we need to match them in both these areas. That means that, going forward, we need even greater collaboration, both within the private and public sector—and we need it at a global level.”
Source: Sophos
The ISO accommodates up to 40Gbps and 120K connections/second.
We’re thrilled to share a major update for our NDR (Network Detection and Response) product: customers can now deploy NDR on certified hardware to support high traffic volume environments.
Key benefits
When deployed on supported virtual appliances (VMWare ESXi, MS HyperV, and AWS AMI), Sophos NDR is currently limited to 1GBS of network traffic. This limitation poses a challenge for customers with higher traffic and/or distributed branch offices.
This new ISO image deployment for certified hardware will support small, medium, and large network environments, accommodating up to 40Gbps and 120K connections/second.
License information
There is no change to licensing: Sophos NDR product licenses are determined by the number of users and servers in the environment and customers can deploy as many Sophos NDR sensors as needed.
How to get it
Customers and partners can select the new certified hardware ISO during the appliance setup in Sophos Central and follow the provided instructions for deployment on certified hardware.
Certified hardware requirements
- To utilize the ISO image, customers must acquire certified hardware from vendors such as Dell.
- Deploy the ISO only on certified hardware. While the image may work on other hardware, it cannot be supported, and functionality issues may arise.
- The hardware purchase and any associated warranties are the customer’s responsibility. Sophos does not have a reseller agreement with the certified hardware providers, and the hardware cannot be purchased through Sophos.
- Consult the Detailed Certified Hardware Specifications for more information
Source: Sophos
The concept of zero trust is not new. In fact, the primary characteristics have been cybersecurity best practices for decades. And more importantly, zero trust is not a product or something you can buy, but rather a strategy, policy, and workflow for implementing access from assets to data that encapsulates the best security traits possible.
The concept of zero trust has surged in popularity due to the evolving threat landscape that targets vulnerabilities, exploits, misconfigurations, and identity security. It has become mainstream since traditional security measures prove inadequate, and a better method was needed to mitigate the risks every organization faces today.
Zero trust isn’t merely a buzzword; it’s a fundamental shift in how we approach cybersecurity for the long haul. This blog aims to clarify what zero trust is by defining its core components: Zero Trust (ZT), Zero Trust Architecture (ZTA), and Zero Trust Network Access (ZTNA). In addition, it will delve into the nuances of each concept, highlighting their differences and significance in securing modern networks regardless of whether they are used on-premises or for remote access.
What is zero trust?
At its core, zero trust is a security model that operates on the principle of “Never trust, always verify” and provides a measure of confidence in doing so. Unlike traditional security paradigms that rely on network and perimeter-based defenses and access control lists (ACLs), zero trust postulates that threats can exist both outside and inside the network perimeter, and nothing is safe without verification. Simply stated, it treats every access attempt as potentially malicious until proven otherwise, regardless of the user’s location, asset, or workflow.
Zero trust advocates for granular access controls and strict enforcement of least privilege principles to minimize the attack surface and mitigate risks while continuously monitoring all aspects for anomalous communications and user behavior. The primary goal, bluntly stated, is that, if any security incident does occur after all of these principles are applied, it can be contained, managed, and will prevent a beachhead or lateral movement.
A Zero Trust Architecture encompasses the framework, principles, and technologies that enable organizations to implement the zero trust model effectively. It essentially applies products, solutions, policies, and workflows in a cohesive architecture to attain the goals of zero trust. Therefore, in today’s world, a single product from a single vendor does not represent zero trust, but rather just one component of the ultimate goal. Zero trust architectures extend beyond traditional security controls to embody a holistic security strategy that encompasses users, devices, applications, and data. Key components of any zero-trust architecture include:
- Micro-segmentation: Dividing the network, access, data, and running processes into smaller segments and enforcing strict, localized access controls (privileges, permissions, entitlements, and rights) between them to contain breaches and limit lateral movement by attackers.
- Identity and Access Management (IAM): Implementing robust authentication mechanisms, such as multi-factor authentication (MFA), and centralized identity governance and privileged management to provide a high level of continuous confidence in a users’ identities.
- Continuous Monitoring: Leveraging real-time analytics and behavioral analysis to detect anomalies, suspicious activities, and potential threats across the network from inappropriate behavior.
- Encryption: Encrypting data both at rest and in transit to ensure confidentiality and integrity, especially in multi-cloud, hybrid environments, or during remote access when traditional network security controls cannot be adequately enforced.
- Policy Orchestration: Automating the enforcement of security policies based on dynamic factors, such as user roles, device posture, and contextual information, across all layers of an entire workflow.
Zero Trust Network Access is commonly referred to as “perimeter-less security” and is a specific implementation of the zero-trust model focused on securing remote access to an organization’s assets. Zero trust network access has the dubious honor of being branded a product, but as previously discussed, is another component of a true zero trust environment governing network access.
These solutions leverage identity-centric access controls and least privilege principles to authenticate users and grant them access to specific applications or services, regardless of their location or network environment. They alone contain only a partial list of all the traits needed to be a complete zero trust ecosystem, despite vendors marketing them as such. As a reference for their capabilities, traditional Virtual Private Networks (VPNs) typically provide blanket access to the entire network, while zero trust network access solutions offer more granular control, reducing the risk of unauthorized access and lateral movement by threat actors.
At the network layer, they cannot monitor session-based user behavior, continuously monitor identity confidence, nor prevent lateral movement downstream. Therefore, solutions marketed today are only part of the problem.
While zero trust network access represents just one potential implementation of zero trust and zero trust architectures, security professionals should be aware that other implementations could include zero trust application access, zero trust session management, etc. Each one follows a percentage of the required guidelines to be labeled zero trust and solves a unique use case for access and authentication-based technologies.
While zero trust, zero trust architectures, and zero trust network access share the overarching goal of enhancing cybersecurity posture, they differ in scope, emphasis, and implementation:
1. Scope:
- Zero Trust is a security model based on the principle of “never trust, always verify,” applicable to all aspects of cybersecurity.
- Zero Trust Architectures provide a comprehensive framework encompassing network segmentation, identity management, encryption, and policy orchestration to operationalize the zero trust model.
- Zero Trust Network Access is just one of many potential zero trust implementations that focuses on securing remote access to corporate resources, emphasizing identity-centric access controls and least privilege principles. The concept is one of the first zero trust architectures to be partially commercialized in products.
2. Emphasis:
- Zero Trust centers on redefining the traditional perimeter-based security model, emphasizing continuous verification, and enforcing strict access controls regardless of where assets and data, and sources and destinations reside.
- Zero Trust Architectures emphasizes the design and implementing of a holistic security framework that aligns with zero trust principles, encompassing network, identity, data, and application security.
- Zero Trust Network Access is the first major practical implementation that emphasizes the need to secure remote access to organizational resources for all identities, along with the principle of “verify first, access later,” irrespective of the user’s location or trusted device.
3. Implementation:
- Zero Trust can be implemented through a combination of policy changes, technology deployments, and workflow changes within an organization.
- Zero Trust Architectures can be implemented through a structured approach involving network, data, and application segmentation; identity management; encryption; continuous monitoring; and continuous policy enforcement controls.
- Zero Trust Network Access can be implemented through specialized solutions that authenticate users, authorize access based on identity and context, and enforce least privilege principles for remote access. And as a reminder, this is only a partial list of true characteristics to achieve zero trust end to end for any given workflow.
Operationalizing Zero Trust, ZTA, & ZTNA
Zero trust represents a paradigm shift in cybersecurity, advocating for a proactive, identity-centric approach to security through new access controls and continuous monitoring of access and identity behavior. Zero trust Architectures provide the framework and principles necessary to operationalize zero trust effectively through any workflow from remote access to cloud access and beyond. Essentially any access workflow can be envisioned in a zero-trust paradigm.
And finally, while zero trust network access offers a specialized solution for securing remote access in an increasingly decentralized environment by using strict point-to-point encrypted access. By understanding the nuances and differences between zero trust, zero trust architectures, and zero trust network access, organizations can embark on the journey towards a more resilient and adaptive security posture in the face of evolving cyber threats.
Source: BeyondTrust
When we think about storing sensitive information, two types of information come to mind: digital data and physical data. While physical data can be securely stored in a physical vault, digital data should be stored in an encrypted cloud storage solution to protect it from common cyber threats.
Continue reading to learn the best ways to store your sensitive physical and digital information, plus the storage methods to avoid.
The risks of insecurely storing sensitive information
Insecurely storing sensitive information such as your login credentials, credit card details, Social Security card and passport can place you at a greater risk of having your online accounts compromised and your identity stolen. This is why it’s important to securely store your information both physically and digitally so unauthorized individuals aren’t able to access it.
The storage methods you should avoid for your sensitive information include the following.
- Storing physical documents in places where anyone can access them (e.g. under your mattress or in an unlocked drawer at home)
- Storing digital sensitive information in unencrypted cloud storage (e.g. on your device’s notes app or spreadsheets)
The best way to store your digital sensitive information
The best way to store your digital sensitive information is in an encrypted cloud storage solution like a password manager. A password manager is essential for cybersecurity because it aids in generating, storing, managing and sharing passwords. Some password managers can also store passkeys, files, documents and images. Password managers were designed to keep your digital data protected from unauthorized access so cybercriminals aren’t able to use your data maliciously to hack your accounts or steal your identity.
When choosing a password management solution, it’s important to take into account the solution’s security architecture. The password manager you choose should provide you with the highest level of encryption and have a history of being secure and reliable. Some features to look for in a password manager include the following.
- Zero-trust, zero-knowledge security
- 256-bit AES encryption
- Secure password and file sharing
- Passkey and 2FA code storage
- Multi-device compatibility
- Multi-Factor Authentication (MFA) support
The best way to store your physical sensitive information
The best way to store your physical sensitive information is in a safety box. This ensures that no one but you will be able to access it without providing a code, biometric authentication or key. There are many safety boxes to choose from, but we recommend looking at reviews and doing research before investing in one so you choose the best and most secure option.
Here are some best practices to keep in mind when using a safety box.
- If your safety box has a key, make sure no one can easily gain access to it
- If your safety box requires a code, don’t use numbers that are significant to you such as your birthdate or the birthdate of loved ones
How Keeper® helps you securely store your sensitive information
Keeper is a zero-trust and zero-knowledge password manager. Keeper uses 256-bit AES record-level keys and folder-level keys which are generated on your device to encrypt each stored record in your password vault. All contents of your vault are encrypted, including logins, file attachments, 2FA codes, payment information, URLs and custom fields.
Additionally, Keeper’s advanced cloud authentication and network communications model is built for the highest levels of privacy, security and trust, so there’s no need to worry about your stored data falling into the hands of cybercriminals.
Ready to start securely storing your digital data? Start a free 30-day trial of Keeper Password Manager today.
Source: Keeper
We are delighted to announce that Sophos has been named a Leader in the IDC MarketScape: Worldwide Managed Detection and Response (MDR) 2024 Vendor Assessment (doc #US49006922, April 2024).
The IDC MarketScape study evaluates the capabilities and business strategies of 19 managed detection and response service vendors, and positions Sophos in the Leaders Category. We believe this recognition demonstrates that Sophos is an ideal choice for organizations looking to elevate their defenses with a tried-and-true 24/7 expert-led managed detection and response.
Sophos was also recently named a Leader in the IDC MarketScape: Worldwide Modern Endpoint Security for Midsize Businesses 2024 Vendor Assessment (doc #US50521323, February 2024) and in the IDC MarketScape: Worldwide Modern Endpoint Security for Small Businesses 2024 Vendor Assessment (doc #US50521424, March 2024).
Following the assessment, Craig Robinson, Research Vice President of Security Services, IDC, said: “Organizations looking for cost certainty, whether that is through their simplified predictable pricing method, or looking for unlimited incident response services paired with a $1M warranty, should consider utilizing Sophos for their MDR needs.”
Simplicity and flexibility
“With simple pricing and flexible service models, Sophos is named a Leader in the IDC MarketScape: Worldwide Managed Detection and Response (MDR) 2024 Vendor Assessment for providing an easy-to-understand option for companies looking to strengthen their cybersecurity defenses and address complex security needs,” said Craig Robinson, Research Vice President of Security Services, IDC. “The recent introduction of Sophos Managed Risk also demonstrates their commitment to addressing the evolving challenges of their customers in an ever-changing cybersecurity landscape.”
The IDC MarketScape evaluation refers to the flexibility and compatibility offered by Sophos Managed Detection and Response, noting that:
“Sophos MDR has expanded its detection capabilities beyond its Sophos products. Data is collected from third-party alert sources across multiple domains, which include but are not limited to endpoint, firewall, cloud, and identity. IDC recognizes that getting a complete view of attacks often requires the collection, analysis, and correlation of relevant network data along with other telemetry.”
Unlimited full-scale incident response
Sophos MDR Complete and Sophos MDR Essentials service tiers are designed to align to the customer maturity journey. With both service tiers including 24/7 expert-led investigation and response and threat hunting, the IDC MarketScape notes:
“The core differentiator of MDR Complete is that it includes a unique unmetered, full-scale incident response offering at no additional charge. The Sophos Breach Protection Warranty covers up to $1 million in response expenses for qualifying customers.”
Get the excerpt
To learn more about why Sophos was named a Leader in the 2024 IDC MarketScape for Worldwide Managed Detection and Response, read the excerpt here.
Source: Sophos
Virtual Private Networks (VPNs) are used by businesses to secure remote access to systems and encrypt employees’ internet traffic. However, while VPNs add some level of protection for distributed workforces, they aren’t enough to keep your business and employees safe from common cyber threats since they make internal tracking of users complex, lack adequate protection and don’t scale in a remote work environment.
Rather than relying on VPNs, businesses should switch to a secure VPN alternative like Keeper Connection Manager® (KCM) – a zero-trust, agentless remote desktop gateway. Continue reading to learn more about what makes Keeper Connection Manager the best VPN alternative for businesses.
Why businesses need a VPN alternative
Here are some reasons your business should consider a secure VPN alternative.
VPNs make tracking users complex
One of the biggest challenges when using VPNs for remote access is they make tracking users complex. With VPNs, IT teams have to rely on confusing dashboards to attempt to understand what employees are accessing, when and why. This can cause IT admins to overlook tasks and make mistakes that open security gaps.
VPNs lack adequate protection
Some VPNs use less secure protocol standards or low-level encryption, making it easier for threat actors to steal business data even when employees are connected. Additionally, even some of the best VPNs regularly discover new vulnerabilities that cybercriminals can easily exploit. While VPN providers issue software patches for these vulnerabilities, it still leaves your business open to some risk.
VPNs don’t scale in a remote work environment
While VPNs can be effective for infrequent remote access for a limited number of employees, they don’t work well when scaled up. VPNs were not designed to accommodate multiple people to connect to them all day long, which can lead to poor reliability. This can cause many employees to not connect to VPNs, even when they’re supposed to, placing your business at risk of suffering a cyber attack.
Why Keeper Connection Manager is the best VPN alternative
Keeper Connection Manager is the best VPN alternative because it provides users with a zero-trust remote desktop solution that reduces administrative overhead and improves performance, reliability and employee productivity.
With KCM, administrators can provide access to an entire system or just one machine through RDP, SSH, VNC, MySQL and other common protocols without having to share credentials with end users. Access can be revoked at any time and an audit trail helps IT admins understand when and how the system is being used, making it easy to keep track of users so they can better protect their organization.
To access internal resources using KCM, remote teams log in through a web browser – no endpoint clients need to be installed, configured or maintained.
Secure your infrastructure with Keeper Connection Manager
Simply relying on a VPN to secure remote access could do more harm than good for organizations, making it important to consider other more secure solutions. Luckily, Keeper Connection Manager is the perfect solution for organizations that want to provide their IT and DevOps teams with secure and easy access to RDP, SSH, database and K8s endpoints.
Curious to learn more about how Keeper Connection Manager can help you secure your organization’s infrastructure? Start a free 14-day trial today.
Source: Keeper
Our fifth annual report reveals how ransomware experiences have changed over the last year, plus brand-new insights into the business impact of an attack.
The fifth Sophos State of Ransomware Report reveals the real-world ransomware experiences of 5,000 organizations around the globe, from root cause through to severity of attack, financial impact, and recovery time.
Based on the findings of a survey of IT/cybersecurity leaders across 14 countries, this year’s report combines year-on-year insights with brand new areas of study. It includes a deep dive into ransom demands and ransom payments, and shines new light on the role of law enforcement in ransomware remediation.
Download the report to get the full findings and read on for a taster of some of the topics covered.
Attack rates have dropped, but recovery costs have increased
59% of organizations were hit by ransomware last year, a small but welcome drop from the 66% reported in both the previous two years. While any reduction is encouraging, with more than half of organizations experiencing an attack, this is no time to lower your guard.

While the attack rate has dropped over the last year, overall recovery costs (excluding any ransom payment) have soared to $2.73M, a 50% from the $1.82M reported in 2023.
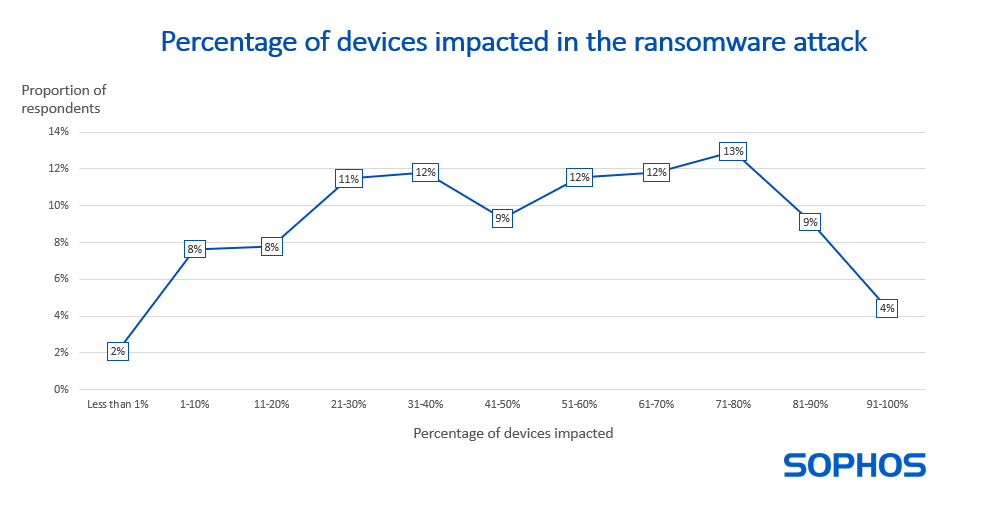
Having your full estate encrypted is rare
On average, just under half (49%) of an organization’s computers are impacted by a ransomware attack. Having your full environment encrypted is extremely rare, with only 4% of organizations reporting that 91% or more of their devices were impacted.
More than half of victims now pay the ransom
For the first time, more than half (56%) of the organizations that had data encrypted admit to paying the ransom to recover data. The use of backups has dropped slightly from last year (68% vs. 70%) while 26% used “other means” to get data back which include working with law enforcement or using decryption keys that had already been made public.
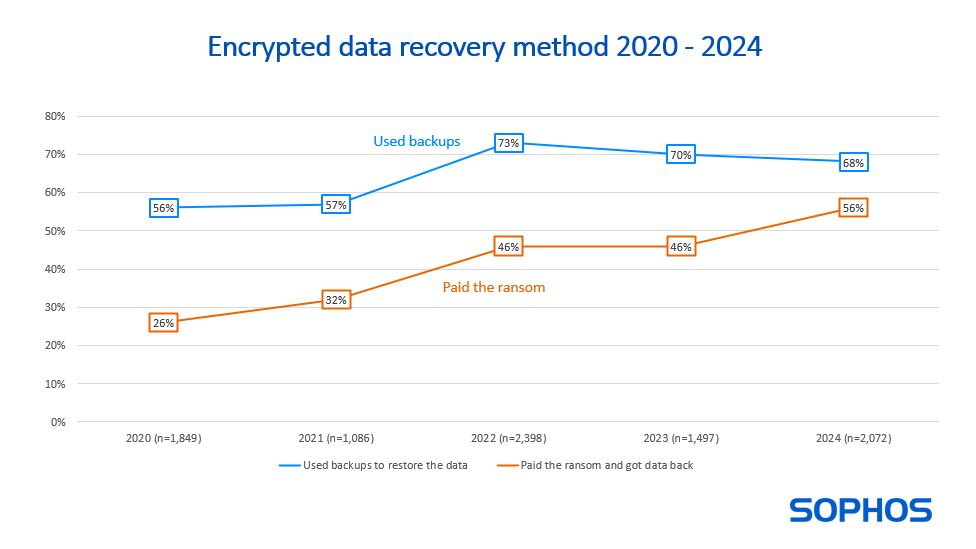
A notable change over the last year is the increase in propensity for victims to use multiple approaches to recover encrypted data (e.g., paying the ransom and using backups). Almost half of organizations that had data encrypted reported using more than one method (47%) this time around, more than double the rate reported in 2023 (21%).
Ransom payments have soared – but victims rarely pay the initial sum demanded
1,097 respondents whose organization paid the ransom shared the actual sum paid, revealing that the average (median) payment has increased 5-fold over the last year, from $400,000 to $2 million.
While the ransom payment rate has increased, only 24% of respondents saying that their payment matched the original request. 44% paid less than the original demand, while 31% paid more.
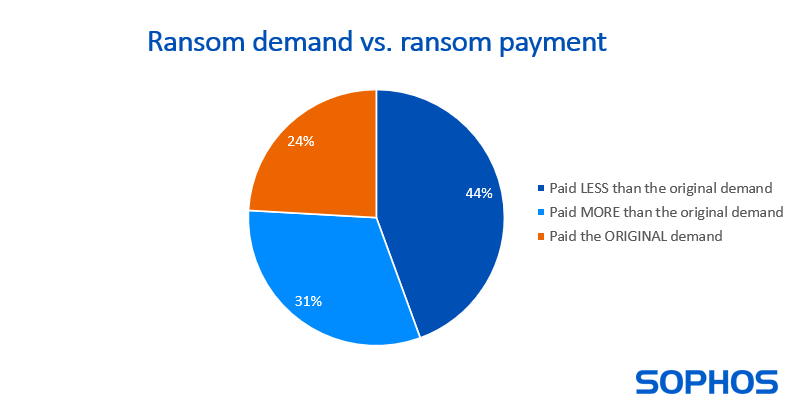
How much was the ransom demand from the attacker(s)? How much was the ransom payment that was paid to the attackers? n=1,097.
For more insights into ransom payments, and many other areas, download the full report.
About the survey
The report is based on the findings of an independent, vendor-agnostic survey commissioned by Sophos of 5,000 IT/cybersecurity leaders across 14 countries in the Americas, EMEA, and Asia Pacific. All respondents represent organizations with between 100 and 5,000 employees. The survey was conducted by research specialist Vanson Bourne between January and February 2024, and participants were asked to respond based on their experiences over the previous year. Within the education sector, respondents were split into lower education (catering to students up to 18 years) and higher education (for students over 18 years).
Source: Sophos
Sophos continues to deliver the strongest endpoint protection in the industry.
Adaptive Attack Protection is a powerful and unique differentiator in Sophos Endpoint. It dynamically enables heightened defenses when a “hands-on-keyboard” attack is detected. In this elevated mode of protection, actions that are usually benign but commonly abused by attackers are blocked outright by Sophos Endpoint – dramatically reducing the likelihood of the attack’s success and giving you more time to neutralize the threat.
As attackers continue to innovate in their approaches, we have extended this unique protection with additional capabilities that further protect Sophos Endpoint customers against active adversaries.
Greater Protection, More Control, Increased Visibility
This Sophos-exclusive protection capability is now even stronger. All Sophos Endpoint customers now benefit from a number of significant enhancements:
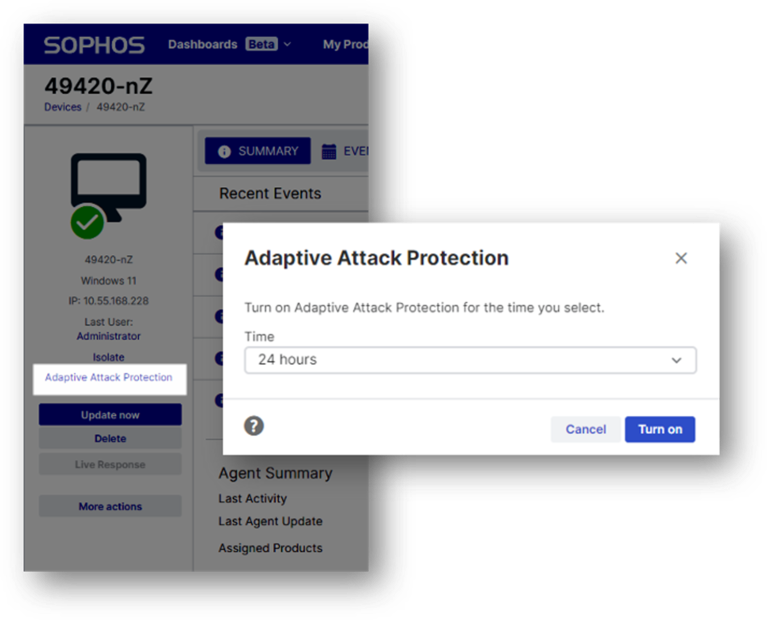
- Greater protection. Customers now have the option to apply specific Adaptive Attack Protection blocking rules persistently via new policy settings in their Sophos Central cloud-based management console.
- More control. Customers can now manually activate (and deactivate) Adaptive Attack Protection on a device to apply more aggressive protection while investigating suspicious activity – ideal for scenarios where fully isolating the device from the network may cause significant operational disruption to the organization. You can also extend the time that Adaptive Attack Protection is activated on a device to give more time to complete an investigation.
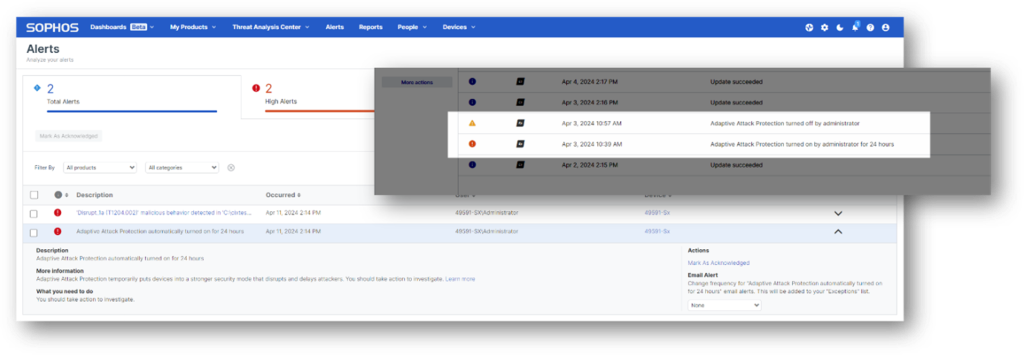
- Increased visibility. New Adaptive Attack Protection events and alerts notify you when a device is under attack and urge responders to take action to neutralize the threat.
New manual controls for Adaptive Attack Protection.
New alerts notify customers when Adaptive Attack Protection is activated on a device.
New Safe Mode Protection
When adversaries fail to break through runtime protection layers on an endpoint, they often attempt to restart the device into Safe Mode, where security software is not present or minimal. Sophos Endpoint now protects against adversary abuse of Safe Mode with two new capabilities:
- Block safe mode abuse: A new Adaptive Attack Protection persistent policy rule is now available that prevents adversaries from programmatically restarting devices into Safe Mode.
- Enable protection in safe mode: Sophos Endpoint protection capabilities, including our unrivaled CryptoGuard anti-ransomware technology and AI-powered malware protection, can now be enabled on devices running in Safe Mode.
New safe mode protection policy settings.
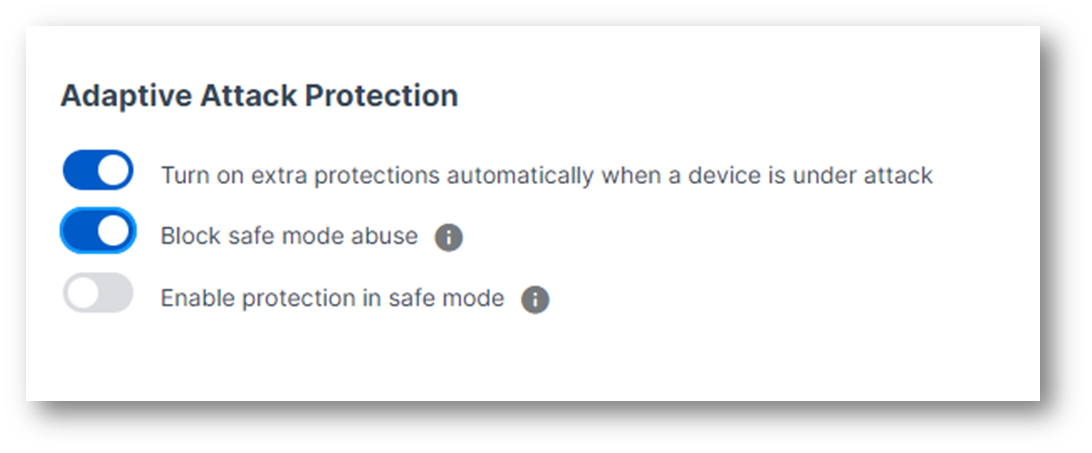
Adaptive Attack Protection is available to all Sophos Endpoint customers today.
To learn more about Sophos Endpoint and how it can help your organization better defend against today’s advanced attacks, speak with a Sophos adviser or your Sophos partner today.
Source: Sophos
The Digital Operational Resilience Act (Regulation (EU) 2022/2554) (“DORA” or the “Act”) is a European Union regulation intended to ensure the digital resilience of financial entities1 in the EU against Information Communication Technologies (ICT) – related incidents and operational disruptions. The European Commission completed DORA on January 16, 2023. Its requirements become effective and apply on January 17, 2025.
Scope of DORA
DORA applies to all EU “financial entities,” including banks, investment firms, credit institutions, insurance companies, crowdfunding platforms, as well as critical third parties offering ICT-related services to financial institutions such as software vendors, cloud service providers and data centers, data analytics providers, and more. Article 2 of (EU) 2022/2554 identifies the following financial entities covered by the Act.
List of financial entities covered by the regulation:
- Credit institutions
- Payment institutions
- Account information service providers
- Electronic money institutions
- Investment firms
- Crypto-asset service providers and issuers of asset-referenced tokens
- Central securities depositories
- Central counterparties
- Trading venues
- Trade repositories
- Management companies
- Managers of alternative investment funds
- Data reporting service providers
- Insurance and reinsurance undertakings
- Insurance intermediaries, reinsurance intermediaries and ancillary insurance intermediaries
- Institutions for occupational retirement provision
- Credit rating agencies
- Administrators of critical benchmarks
- Crowdfunding service providers
Why DORA?
DORA “acknowledges that ICT incidents and a lack of operational resilience have the possibility to jeopardise the soundness of the entire financial system, even if there is “adequate” capital for the traditional risk categories.” The DORA regulatory framework lays out requirements that address the security of financial entities’ networks and information systems to enhance cybersecurity across the EU’s financial sector. This helps financial entities reduce the potential impact of digital threats on their business continuity, legal liability, and financial and reputational loss.
Requirements of DORA
In order to achieve a high common level of digital operational resilience, this Regulation lays down uniform requirements concerning the security of network and information systems supporting the business processes of financial entities as follows:
- ICT Risk Management: Financial entities shall have a sound, comprehensive and well-documented ICT risk management framework as part of their overall risk management system, which enables them to address ICT risk quickly, efficiently and comprehensively and to ensure a high level of digital operational resilience.
- ICT-Related Incident Management Process: Financial entities shall record all ICT-related incidents and significant cyber threats. Financial entities shall establish appropriate procedures and processes to ensure a consistent and integrated monitoring, handling and follow-up of ICT-related incidents, to ensure that root causes are identified, documented and addressed in order to prevent the occurrence of such incidents.
- Digital Operational Resilience Testing: To ensure that financial entities are prepared to tackle ICT-related incidents, DORA defines common standards with a focus on resilience testing by these entities, “such as vulnerability assessments and scans, open source analyses, network security assessments, gap analyses, physical security reviews, questionnaires and scanning software solutions, source code reviews where feasible, scenario-based tests, compatibility testing, performance testing, end-to-end testing and penetration testing.”
- ICT Third-Party Risk Management (TPRM): Recognizing the increasing importance of third-party ICT service providers, DORA requires financial entities to “manage ICT third-party risk as an integral component of ICT risk within their ICT risk management framework” through contractual agreements like accessibility, availability, integrity, security, and protection of personal data; clear termination rights; and more.
- Information and Intelligence Sharing: With the aim of boosting the collective ability of financial institutions to identify and combat ICT risks, DORA encourages them to “exchange amongst themselves cyber threat information and intelligence, including indicators of compromise, tactics, techniques, and procedures, cyber security alerts and configuration tools, to the extent that such information and intelligence sharing:
- aims to enhance the digital operational resilience of financial entities, in particular through raising awareness in relation to cyber threats, limiting or impeding the cyber threats’ ability to spread, supporting defence capabilities, threat detection techniques, mitigation strategies or response and recovery stages;
- takes place within trusted communities of financial entities;
- is implemented through information-sharing arrangements that protect the potentially sensitive nature of the information shared, and that are governed by rules of conduct in full respect of business confidentiality, protection of personal data in accordance with Regulation (EU) 2016/679 and guidelines on competition policy.”
- Oversight Framework of Critical ICT Third-Party Providers: The Joint Committee, in accordance with Article 57(1) of Regulations (EU) No 1093/2010, (EU) No 1094/2010 and (EU) No 1095/2010, shall establish the Oversight Forum as a sub-committee for the purposes of supporting the work of the Joint Committee and of the Lead Overseer referred to in Article 31(1), point (b), in the area of ICT third-party risk across financial sectors. The Oversight Forum shall prepare the draft joint positions and the draft common acts of the Joint Committee in that area.
The Oversight Forum shall regularly discuss relevant developments on ICT risk and vulnerabilities and promote a consistent approach in the monitoring of ICT third-party risk at Union level.
DORA and NIS 2
DORA and NIS 2 are two critical pieces of EU cybersecurity legislation. The NIS 2 Directive (Directive (EU) 2022/2555) is a legislative act that aims to achieve a high common level of cybersecurity across the European Union.
The relationship between DORA and NIS 2 is that NIS 2 aims to improve cybersecurity and protect critical infrastructure in the EU, whereas DORA addresses the EU financial sector’s increasing reliance on digital technologies and aims to ensure that the financial system remains functional even in the event of a cyberattack.
What is significant to note is that NIS 2 is a European directive. By October 17, 2024, Member States must adopt and publish the measures necessary to comply with the NIS 2 Directive. DORA is a European regulation that will be applicable as it stands in all EU countries from January 17, 2025.
Article 1(2) of DORA provides that, in relation to financial entities covered by the NIS 2 Directive and its corresponding national transposition rules, DORA shall be considered a sector-specific Union legal act for the purposes of Article 4 of the NIS 2 Directive.12 DORA is “lex specialis” to NIS 213,14 for the financial sector, a principle that states that a specific law takes precedence over a general one. So, for financial entities covered under DORA, this text prevails over NIS 2. However, this does not mean that NIS 2 obligations are no longer applicable to entities affected by both texts.
Penalties for DORA non-compliance
The potential penalties associated with DORA can be significant and, differently to GDPR and/or NIS 2, encourage the firm to comply by imposing fines on a daily basis. Those organizations deemed noncompliant by the relevant supervisory body may find themselves subject to a periodic penalty payment of 1% of the average daily global turnover in the preceding year, for up to six months, until compliance is achieved. The supervisory body may also issue cease-and-desist orders, termination notices, additional pecuniary measures, and public notices.
DORA timelines
DORA was first proposed by the European Commission in September 2020. It came into force on January 16, 2023. Financial entities and third-party ICT service providers have until January 17, 2025 to prepare for DORA and implement it. Batch 1 of the Regulatory Technical Standards, or RTS, and the Implementing Technical Standards (ITS) were published on January 17, 2024. Batch 2 of these standards is under consultation.
Source: Sophos
NIS2, the reformed edition of the 2016 Network and Information Security (NIS) directive, was entered into force at the start of 2023, following multi-year European Parliament negotiations. Member states have until 17th October 2024 to adopt and publish measures complying with NIS2.
With a little less than a year left for affected organizations to comply with the new requirements, we sat down with Lee Elliott, Director of Solutions Engineering at BeyondTrust, to learn more about NIS2 and its impact on national security. This blog will provide answers to the leading questions about NIS2 to help you prepare your organization to meet the coming deadline.
Q1: What is NIS2?
The Network and Information Security 2 (NIS2) Directive is a landmark piece of European cybersecurity legislation that provides legal measures to boost the overall level of cybersecurity in the European Union (EU). It does so by setting a common, high standard for companies and organizations to comply with in terms of their cybersecurity posture and obligations.
Q2: Who does NIS2 apply to?
Businesses identified by the Member States as operators of “important” or “essential” services. Most of the organisations held accountable by NIS2 are Critical National Infrastructure (CNI) and run Operational Technology (OT) and industrial systems networks.
NIS2 regulations not only cover important or essential services, but also any breach in their supply chain. This means that their subcontractors and suppliers, wherever they are based, need to be as secure as the NIS2 requirements.
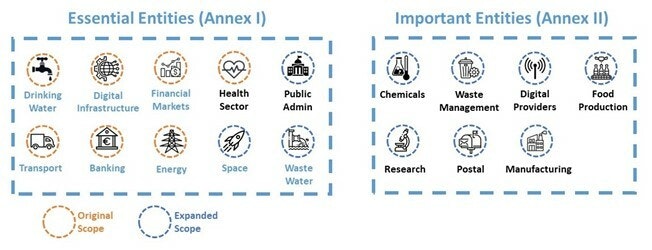
Q3: NIS vs NIS2 – What’s the difference?
NIS2 introduces updates to the EU cybersecurity rules that were originally introduced in 2016 in order to modernise the existing legal framework and keep up with increased digitisation and an evolving cybersecurity threat landscape.
Some key differences include:
- More industry sectors included – the scope of cybersecurity rules has expanded to new sectors and entities, particularly incorporating manufacturing and other OT industries. Company criticality and size is also taken into account.
- New incident response and crisis management reporting requirements – NIS2 requires improvement of the incident response capacities, including strengthened incident reporting obligations, more precise reporting processes, and timeline provisions.
- Enhanced security requirements and controls – Security requirements are strengthened, with focused vulnerability handling and disclosure, policies and procedures to assess the effectiveness of cybersecurity risk management measures, basic computer hygiene practices and cybersecurity training, the effective use of cryptography, human resources security, access control policies, and asset management.
- Bigger penalties – NIS2 introduces more severe penalties for compliance failures. Administrative fines vary based on entity status:
- Essential entity fines can be up to €10,000,000 or 2% of the total annual worldwide turnover in the previous fiscal year (whichever is higher);
- Important entity fines can be as much as €7,000,000 or 1.4% of the total annual worldwide turnover in the previous fiscal year of the company (whichever is higher).
- Increased liability – C-level executives who are responsible for the Risk and Governance of their infrastructure will be held personally liable for a breach and could be removed from their post.
Q4: When does NIS2 come into effect?
The deadline for Member States to transpose the NIS2 Directive into applicable, national law is 17 October 2024. Companies need to be fully compliant with the directive’s updated requirements before this date or they may face severe consequences, including financial penalties and damage to reputation.
Q5: Why is there a focus on operational technology (OT) within NIS2?
OT security has become much more critical because of the recent spate of high-profile attacks. It has also become the focus of increasing compliance frameworks. In terms of security, OT is playing catchup with IT. In IT networks, most security fundamentals have been put in place, but in OT, controls like change management, access control, and vulnerability management are still not being applied.
Q6: What are the challenges of managing and securing OT Environments?
I think it boils down to the focus of an OT environment. For the most part, these environments are manufacturing plants—factories that are producing an output. Availability is paramount. Any downtime will cost a measurable amount based on loss of output. Of course, with CNI, availability becomes even more important as any downtime may have a detrimental effect on the nation! And if you think that IT is more data-centric and so integrity is more of a focus, remember: you can back up data, but it’s not so easy to do with the flow of gas or oil!
Also, OT environments are full of legacy, and sometimes unsupported, equipment. Refresh cycles could be in the decades rather than the 3-to-6-year range that is typically seen in IT. There is an element of technical debt with systems that were never designed to operate with new cyberthreats in mind.
Lastly, there is a temptation for companies to use the authentication and security services they have in IT for their OT environment. For example, using the corporate Active Directory to manage the account authentication and authorisation for OT users. This is a really bad idea. The two areas should be segmented to prevent a breach from crossing from one environment to the other, resulting in a much larger impact.
Q7: What are the next steps for organizations? Should they start mapping NIS2 to more familiar frameworks? What will a gap analysis likely show against the new regulations?
This really depends on the Governance, Risk & Compliance (GRC) team within the company. They should be able to digest the new requirements and see where their existing controls are sufficient and where there are gaps. You must consider also that independent auditors will ensure that all controls are in place and satisfy the requirements. If not, they will enforce plans and penalty-driven timelines to ensure compliance.
To assist with this, NIS2 encourages “the use of European and international standards and technical specifications relevant to the security of network and information systems”, for example ISO27001.
The basics (endpoint security, EDR, antivirus etc.) should already have been covered for NIS or other required security frameworks, but the biggest gap is still phishing. Enforcing least privilege and better identity management will be a key area of focus for most organizations.
Q8: If least privilege is the answer, why has it not been adopted more widely?
Least privilege has been around for a long time. The problem people find is that it’s easy to say, but difficult to do—especially on endpoints, servers, and desktops—because people sometimes do need a certain amount of privilege to do their job. By taking that away, you’re preventing them from actually being productive.
When companies are measured in response times, SLAs, and how quickly get things fixed, and when having applications go down can cost the company millions per day, security sometimes takes a backseat. Then it’s only when they’ve had a breach, or when they think they’re going to have a breach, that they start thinking about it. So, least privilege is difficult from that standpoint. It should be as simple as having the tools in place that allow people to still do their work, with policies that allow them to do what they need to do, but securely.
Q9: What are the specific challenges of incorporating third parties into your security strategy?
Third parties can be seen as the weakest link in the cyber defence chain. Every company relies on third parties to support their Tier 1 business services, but the security of the company as a whole is only as good as the security of the worst third-party company.
This threat is old: one of the first documented cyberattacks occurred on the US hypermarket, Target, in 2013. The attack was caused by a breached third party when the heating and air conditioning support company Target used was breached. The company had VPN access into Target’s stores to monitor and patch the air conditioning systems, but during the recon phase, the threat actors also gained access to Point-of-Sale registers. They installed credit card skimming software and stole credit card details from approximately 40 million customers, eventually costing Target USD420 million.
With the updates in NIS2, incorporating third parties into your security strategy is now paramount. Companies must impose a minimal cybersecurity maturity level on their suppliers and will be responsible for assessing that supplier, not the National Authorities.
Q10: How does technology add to the vendor privileged access management (VPAM) challenge?
Controlling third party access to internal systems is a critical function of supply chain security. However, current technology used by many companies for providing remote access is outdated and doesn’t provide the necessary controls for giving third parties access securely.
VPNs are susceptible to vulnerabilities – just search any CVE database to see. Travelex forgot to patch its VPN in 2020 and was hacked via CVE -2019-11510. The attack cost the company $2.3 million in ransom paid to the hackers, and eventually the company was forced into administration.
As another example of where VPAM is needed, in February of 2022, Toyota shut down 14 manufacturing plants at a cost of about $375 million because of a cyberattack on Kojima Industries, a key supplier. Kojima Industries is a small company and is little-known outside Japan, where it produces cup holders, USB sockets, and door pockets for car interiors. However, its modest role in the automotive supply chain is a critical one, and when the company was hacked, it brought Toyota’s entire production line to a stop. Even after the initial crisis was over, it took months for Kojima to get operations back to normal.
Q11: What’s the best solution for managing vendors and third-party users?
Managing third-party vendors is a combination of policy, process, and technology. Providing any one without the others is pointless.
Managing vendor users is always a difficult problem. Where do you create their accounts? How do you know if someone who left has passed their credentials off to their replacement, or even to several people who are now accessing your infrastructure? Modern solutions allow vendors to manage their own remote access account with the necessary controls in place.
Modern administrative and third-party vendor access solutions should provide clientless access with flexible authentication methods, approval workflows, just-in-time access windows, and visibility and auditing. The latter is important not only for security, but also to ensure vendors are adhering to the agreed contract and process. Additionally, integrating with change procedures and using the change number as an additional verification would be useful.
Q12: There is an argument for accepting legal risk when the cost of compliance exceeds the cost of the fines—why should people spend money on NIS2 compliance instead of just accepting the gaps?
Optimism bias is a tendency to overestimate the likelihood that good things will happen to us while underestimating the probability that negative events will impact our lives. This can affect businesses when company leaders believe they will never be targeted by threat actors.
Mitigating a risk to a lower level of risk so that it can be accepted is good risk management—as long as the mitigation isn’t a temporary fix. But this is an old argument that predates some of the significant attacks on OT/IT environments, and regulatory fines are only part of the cost.
For example, the 2021 Colonial Pipeline ransomware attack cost the company $4.4 billion to pay the threat actors, Darkside. But it also caused a six-day shutdown of fuel supply, which affected airports and fuel stations to such a degree that a State of Emergency was declared. The interesting fact about this attack is that it didn’t directly affect the OT equipment. It shut down the billing infrastructure of the company, but because the extent of the breach was unknown, production was shut down as a precaution.
While this attack is undeniably focused on the US, it serves as an illustration that a breach can result in financial expenses in paying hackers. Moreover, the reputational harm inflicted on both the company and individuals involved can be equally expensive. If this had happened in the EU, there would have been the additional expense of the fines imposed by NIS2.
In addition to financial and reputational risks, under NIS2, individual C-Level executives responsible for the Risk and Governance of their infrastructure face accountability and potential removal from their positions—a risk they might not be willing to accept.
Next steps: achieve NIS2 compliance and secure your identity perimeter with BeyondTrust
BeyondTrust’s innovative solutions are tailored specifically to meet the challenges of securing OT environments and to help organizations secure their identity perimeters. Contact us today to learn more from an expert, and click here to download our whitepaper on how to address the NIS2 directive with Privileged Access Management.
Source: BeyondTrust
The security concept known as “Privilege Creep” occurs when an individual accumulates access rights over time, retaining entry to systems and data beyond the completion of a specific task or the need for such access. This gradual accumulation of unnecessary privileges within an organization not only complicates the management of access rights but also magnifies the potential for security breaches, data theft and misuse of information. As privileges amass unchecked, the attack surface widens, offering malicious actors more opportunities to exploit vulnerabilities that could lead to a breach. Addressing this issue requires diligent access management and adherence to the principle of least privilege, ensuring individuals have access only to the resources necessary for their current roles and responsibilities.
Mitigating Privilege Creep is critical to enhancing an organization’s cyber security posture, but it’s historically been difficult to quickly and securely revoke access rights once they have been granted… until now.
Keeper is excited to announce Time-Limited Access and Self-Destructing Records for encrypted, time-bound access and credential sharing in the Keeper platform.
Time-Limited Access
Time-Limited Access enables users to share a record or folder with another Keeper user for a designated period of time. Upon expiration, the recipient will have their access automatically revoked without requiring the sending party to take any action. Time-Limited Access can be applied to thousands of common scenarios from sharing the WiFi password with a visiting guest to admins sharing the login details for a database.
Time-Limited Access solves the long-term struggle many organizations have around elevated access. Users often need to be granted temporary or short-term privileges that go beyond their standard access levels. Organizations can maintain least privilege by only allowing elevated access for the set duration of time and only to perform the tasks required, eliminating the need to create power users with access outside of the scope of their projects.
Combining Time-Limited Access with Keeper Secrets Manager (KSM) provides privileged users with powerful sharing functionality. When paired with KSM’s automatic service account rotation capabilities, users can schedule rotation of the shared credential upon the expiration of access, ensuring the recipient never has standing privilege.
Self-Destructing Records
Self-Destructing Records take this concept one step further by allowing users to create a record and send a one-time share that will delete itself from the sender’s vault after the recipient opens the shared record.
This happens after a designated period of time or once the recipient has viewed the record for five minutes, whichever comes first.
A typical scenario is employee onboarding, when IT needs to share login credentials with a new staff member. IT can share the record containing those credentials and upon receipt, the original record will self-destruct, eliminating the risk associated with long standing access to the employee’s login information.
With Self-Destructing Records, the information can be accessed securely and is automatically deleted, ensuring it doesn’t linger or become accessible beyond its intended purpose. This record’s unique trait of being viewable on only one device further tightens security, preventing unauthorized distribution or viewing on multiple devices.
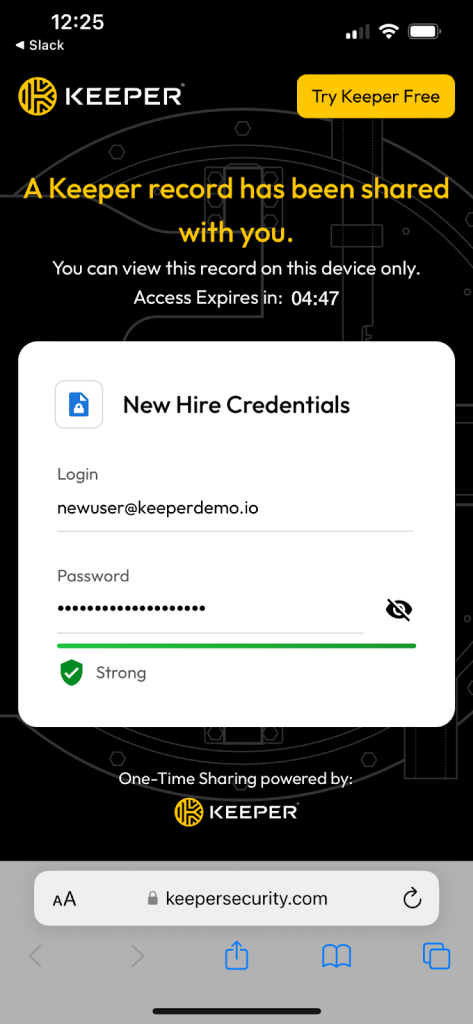
These access and sharing updates are available for both consumer and business users. Administrators can enable or disable these features in the ‘Creating and Sharing’ section of role settings in the Admin Console for business and enterprise organizations. Administrators with Keeper Advanced Reporting and Alerts Module (ARAM) are also able to receive ARAM events for when a timer is added to a record, and when the timer and share expire.
Easy-to-Use, Encrypted Access for All
Time-Limited Access brings several key benefits to users and administrators:
-
- Revoked access at a time decided by the record owner, eliminating chasing down who has access and removing it at a later time
- Enhances security as traditional short term sharing has been done in insecure ways like writing down passwords or sending them via email and messaging
- Simplified compliance with event recordings and assurance that least privilege access is maintained
Self-Destructing Records enables its own set of benefits including:
-
- Ensuring encryption and security, without filling the sender’s vault with credentials they don’t need to retain
- Assurance that the recipient is the only receiver of the shared credential
Secure and Streamline Credential Sharing with Keeper
Time-Limited Access and Self-Destructing Records are just the latest in Keeper’s ongoing efforts to enhance Privileged Access Management (PAM) capabilities for all users. By limiting the amount of time users have access to records, organizations simplify compliance and end-users can rest easy knowing their records are shared securely.
Using Time-Limited Access and Self-Destructing Records is very simple. To learn how, please refer to the product release notes.
To see Time-Limited Access and Self-Destructing Records in action, schedule a demo today.
Source: Keeper
Keeper Security is pleased to announce that passphrases are now supported in the Keeper Vault. Passphrases provide a highly secure yet easy-to-remember approach to logins for all users, and can be both generated and stored with Keeper.
Keeper’s passphrase generator is a new option within its existing password generator. Users and admins will have the choice of which generator they would like to use or enforce for their organization. Keeper’s passphrase generator leverages Electronic Frontier Foundation’s recommended wordlist but has been sanitized to remove any offensive words. Currently, only English words are used by the passphrase generator.
In addition to passphrases, character-specific policies for symbols are now included with Keeper’s existing password generator. For example, users generating a password for a site that doesn’t include certain characters such as ^, ? or + can choose to remove those symbols from their passwords.
How to Use Passphrases in Keeper
The experience of generating and saving a passphrase is nearly identical to the current way to generate and save a password in Keeper, ensuring the same ease of use.
From the Keeper Vault, select Create New and select Record.
Users are prompted to choose their record type and title the record, then select Next. This brings up the record detail menu. To generate a passphrase, click on the dice icon.
This opens the Password Generator where users will see a new drop-down menu option. Click on the drop-down menu and select Passphrase.
Once opened, users can customize their passphrase complexity. Just like passwords, the more complex a passphrase is, the more secure it is. Passphrases in Keeper support up to 20 words.
Selecting Capitals, will capitalize the first letter of each word, while choosing Numbers adds a single digit (0-9) to the beginning or the end of some of the words.
Each word requires a separator. By default, Keeper uses “–” but users can change their default to any of the other options that include “.”, “_”, “!”, “?” or a space by toggling the “Use as default settings” box. Users have the option to include multiple different separators.
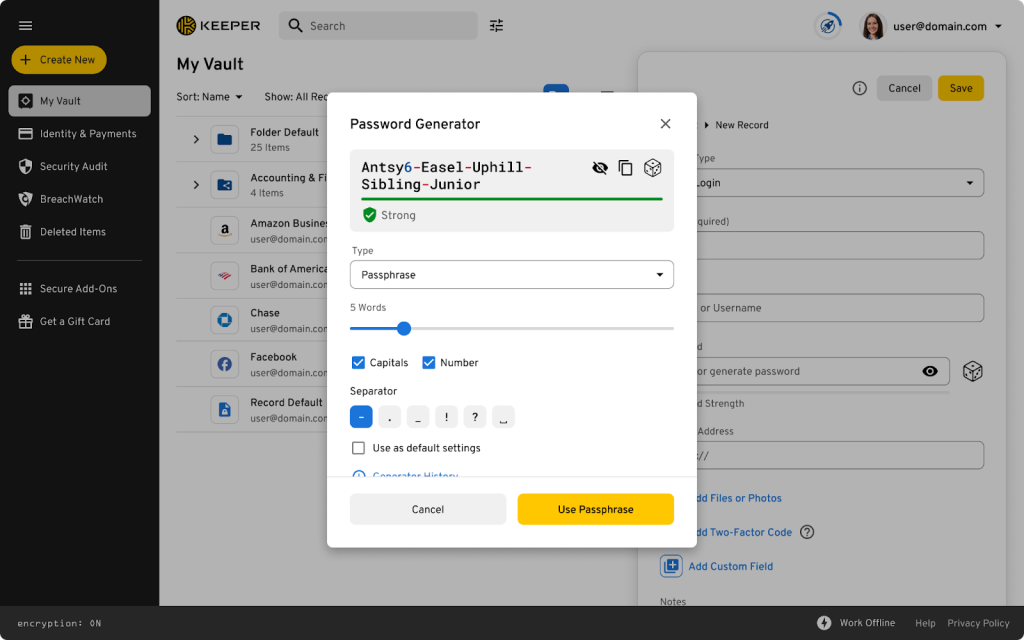
After generating a passphrase, the user will select Use Passphrase and be returned to the record detail menu to save the record.
Click Save and the record with the randomized passphrase will be added to your Keeper Vault.
How to Enable the Passphrase Generator for Administrators
Keeper Administrators looking to enable passphrases for their organization can toggle the ability to leverage passphrases on or off.
Administrators will need to navigate to Record Passwords in the Roles section of the Admin Console and select Passphrase Generator. From this screen, simply toggle Allow Passphrase Generator on or off to select your preferred role policy. Administrators looking to enable passphrases must select at least one of the available separators.
If the Passphrase Generator is disabled, the section will not be interactive in the Admin Console and end users will not have the Passphrase Generator option in their Keeper Vault.
If Keeper Administrators want to only allow passphrases on specific domains, select Domain-Specific Generator. From this tab, click on Add Domain and add the URL of the preferred domains where passphrases will be available for use. After selecting the security rules desired, click Add.
The list of allowed domains will be displayed and administrators can edit them at any point.
Simplify Logins with Keeper
Keeper is driven to continue making its platform easier to use than ever before. Enhancing login types and streamlining the generation of those is key to that approach for both consumers and organizations alike.
To learn more about passphrases and how Keeper is the most secure and easy-to-use password management platform, schedule a demo today.
Source: Keeper