News
James Lyne, Global Head of Security Research, Sophos, said: “Sophos has partnered with Government to support Cyber Streetwise because we believe it’s imperative for both consumers and small businesses to take action to protect themselves online.”
“Consumers and SMEs alike are finding new ways to interact online, including via a greater range of devices, but with this enhanced technology comes risk. SophosLabs finds over 30,000 new infected websites distributing malware every day and, contrary to popular belief, the majority – around 80% – are legitimate small business websites that have been hacked. It’s therefore vital that small businesses in particular get the basics of security right – from installing antivirus to regularly updating and patching software, using complex passwords and protecting data.”
The Cyber Streetwise website – www.cyberstreetwise.com – offers a range of interactive resources for SMEs and consumers to gain impartial advice on how to protect themselves online. Sophos, which has provided security expertise and content for the Cyberstreetwise site, is also pushing visitors from its own dedicated web page – www.sophos.com/cyber-street – to the Cyber Streetwise website.

James Lyne continued: “Those who don’t put basic security measures in place are leaving themselves exposed to attackers capable of silently installing malicious code on their systems without permission. We are proud to have been asked to support and to provide content for Cyber Streetwise, which will play a vital role in encouraging businesses and consumers to adopt safer behaviours online and to take the fight to cyber criminals by improving their online security.”
Cyber Streetwise is urging people to take five actions in order to protect themselves and others from cyber crime:
1. use strong, memorable passwords
2. install anti-virus software on new devices
3. check privacy settings on social media
4. shop safely online – always ensuring to check online retail sites are secure
5. download software and application patches when prompted
You can read the original article at here.
Sophos President and CEO Kris Hagerman said, “Sophos is thrilled to join the many other technology leaders that call Silicon Valley home. A meaningful presence in Silicon Valley gives us a golden opportunity to capitalize on the technology trends and partnership opportunities that are so abundant in this area. Silicon Valley is a renowned global center for the disruptive innovation, top talent and strategic relationships that will help propel Sophos to the next level.”
Mike Valentine, senior vice president of worldwide sales and channel, said, “Sophos is a global company with global reach. Given our ‘Channel First’ sales strategy, it’s important that we have a strong physical presence in the areas that will drive the greatest opportunities. This is why we’ve expanded to the Bay Area, adding it to the other 40 offices we maintain around the world. Sophos is building a market-leading channel program, constantly recruiting and enabling top-notch partners to join our team. This new office provides more evidence of our growing investment in the North America IT security market.”
Meanwhile, the Sophos product development engine continues to hum. The company recently announced Sophos Cloud, an easy to deploy and simple to manage cloud-based service for endpoint protection. The latest version of Sophos Mobile Control delivers best-in-class mobile device management (MDM), enabling organizations of all sizes to use mobile devices such as iPhone, iPad, Android and Windows Phones, to get work done – simply, securely and reliably.
The company also continues to attract top industry talent, including John Keenan as vice president of North America Sales, Mary Winfield as senior vice president of Support, and Dan Schiappa as senior vice president and general manager of the Sophos End User Security Group.
You can read the original article here.
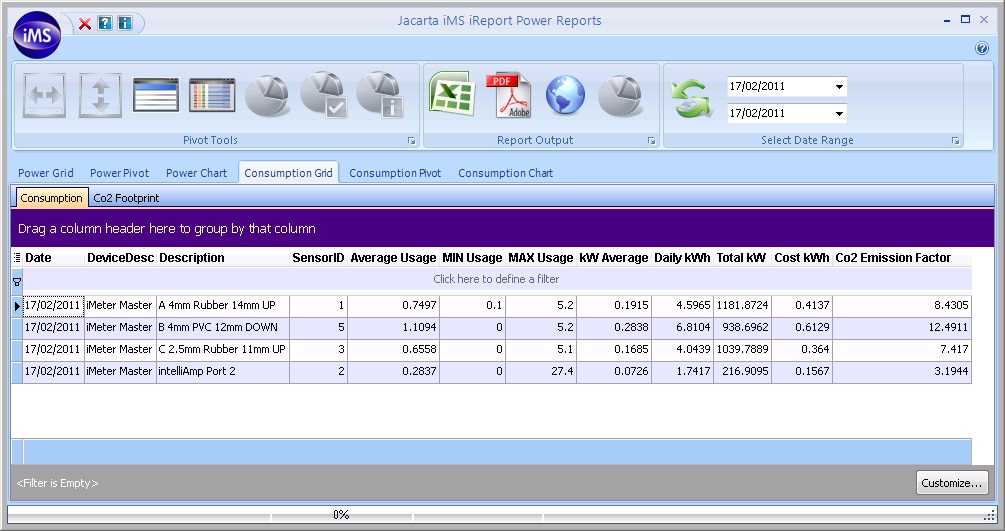
iMeter can monitor up to 496 of the following sensors from a single IP address:
- Current (Amps) using our unique intelliAmp® current sensor (pictured above)
- Voltage
- Temperature
- Humidity
- Airflow
- Water Leak
- Security (door contact or motion)
- Smoke
The unique combination of the sensors on offer means that IT and Facilities personnel can analyse the relationships between power usage, airflow and temperature to help assist data centre management decisions relating to cost control and reduction. The design of the Jacarta Go-Probe sensors enables the complete system to be implemented with zero downtime. The intelliAmp® current sensor can be clipped to the outside of 16 and 32 Amp power cables to monitor the True RMS current draw of single phase racks without any need to disrupt the power flowing into those racks.

interSeptor iMeter® can either be integrated into SNMP network management systems or, alternatively, Jacarta’s powerful iMS software can be used to monitor, log and report on iMeter sensor activity. The overall iMeter package offers a no-fuss, non-disruptive way of implementing an effective power monitoring solution that can influence and assist data centre efficiency decisions for years to come.
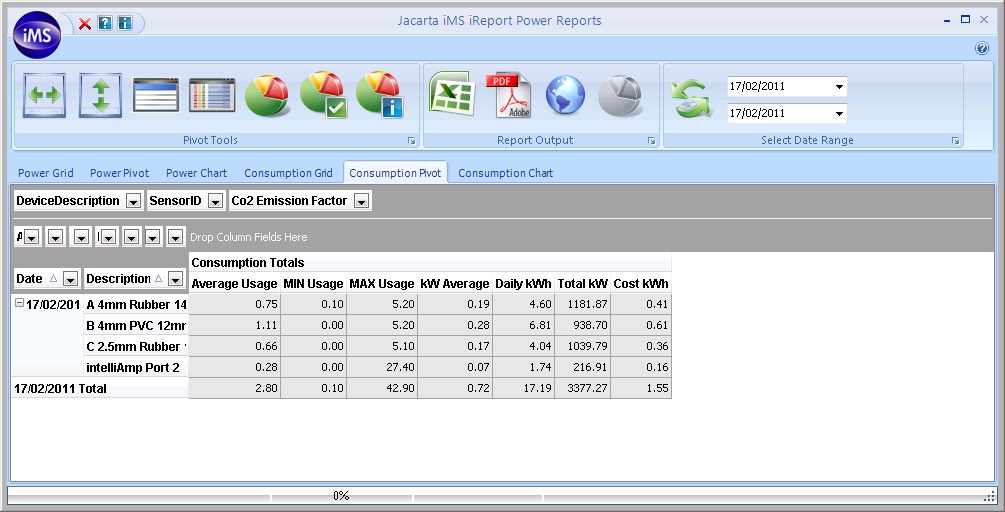
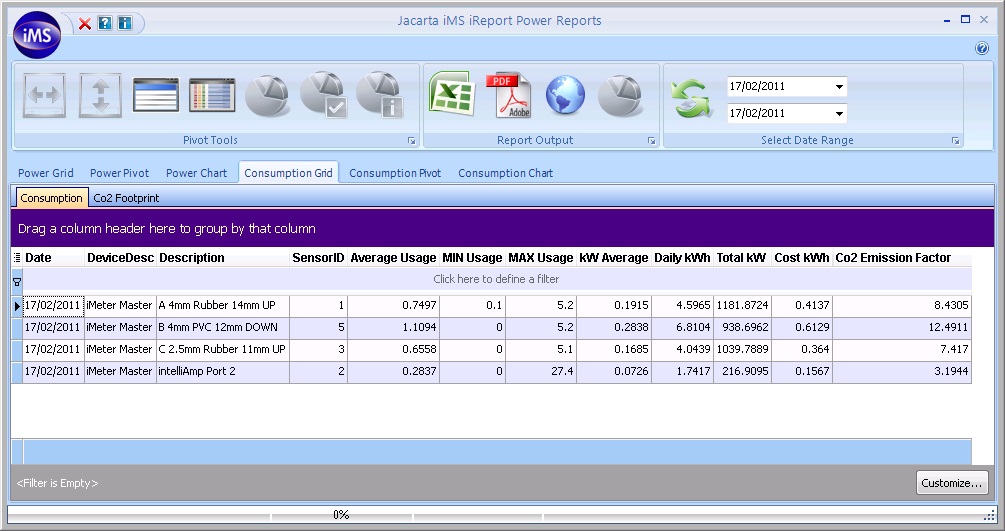
interSeptor iMeter Key Benefits:
- Modular system for easy implementation and budget-matching
- Zero downtime required for installation
- Quickly and easily compare power usage between data centre racks
- Track power efficiency improvements over time
- Use iMeter on-board logs or iMS software to identify where power savings can be made
- Monitor and assess the relationships between temperature, airflow and power usage to improve data centre efficiency
- Solution ensures that, in the unlikely event of sensor failure, there is no disruption to the power supply into your racks
- Integrated environmental and power monitoring ensures alerts can be received quickly to help prevent data centre catastrophe
- An array of additional features such as virtual sensor integration, modbus, SMS and voice alerts (with optional modem), etc. help to ensure that the iMeter can accommodate a broad variety of power and environmental monitoring requirements

You can read the original article here.
Jan
Info-Tech examined ADC vendors that are solving the problems of server downtime due to increased web traffic and preventing malicious attacks against corporate systems. Array Networks’ APV line of application delivery controllers deliver a seamless end-user experience while simultaneously preventing attacks and data leakage.
Array’s feature-rich ADC products, industry-leading price and performance and unmatched reputation for customer service and support make them an unbeatable value to businesses.
Array Networks helps enterprises meet the challenges of delivering applications in the dynamic network environments of modern enterprises. Array has over 5,000 worldwide customers including enterprises, service providers, government and vertical organizations in healthcare, finance, insurance and education. Organizations look to Array to cost-effectively scale the performance, availability and security of applications and data in dynamic network, cloud and mobile environments.
“It’s an honor to be recognized as an Innovator in the ADC market,” said Michael Zhao, President and CEO of Array Networks. “Array is improving enterprise security and traffic management and we will continue to develop application delivery networking solutions that meet customer requirements.
You can read the original article here.
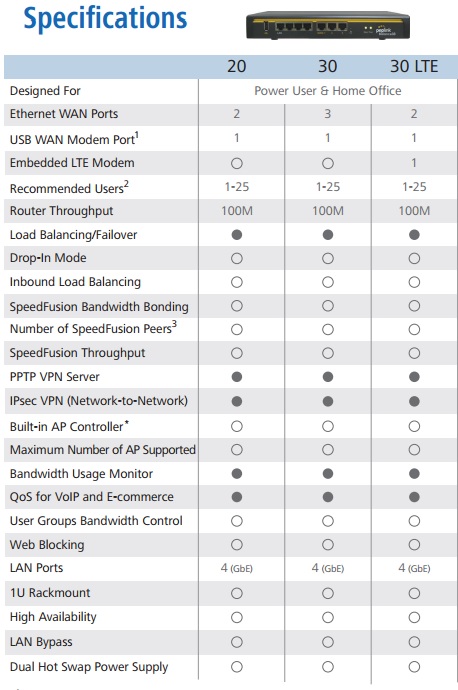
Embedded 4G model supporting 4G LTE for EU and worldwide GSM carriers and providing automatic fallback to 3G as needed. Technologies and frequency bands supported: 4G LTE (Band 1/3/7/8/20); WCDMA/HSDPA/HSUPA/HSPA+/DC-HSPA+ (900/2100 MHz).

You can read the original article here.
Once Microsoft officially ends support for XP on Patch Tuesday in April (the last security update for XP), there will be no new security updates, non-security fixes, assisted support options, or online technical content updates from Microsoft.
That means that XP users, even those with anti-malware protection from Microsoft or security vendors, will face significantly higher security risks after the end of support. As Microsoft said in its announcement, “Our research shows that the effectiveness of anti-malware solutions on out-of-support operating systems is limited.”
To ease the burden of upgrading, Sophos will officially support Windows XP Service Packs 2 and 3 until at least September 30, 2015; and Windows Server 2003 until at least January 31, 2017. See our support knowledgebase for a complete platform support list.
Upgrading to newer Windows operating systems is causing plenty of problems for specialized systems, including for point-of-sale (POS) registers, medical devices, and even ATMs. For those using “embedded” versions of XP on specialized equipment, we recommend isolating these machines and restricting access to non-essential functions using application control available in next-gen firewalls.
In most cases, however, it’s time to upgrade. As Naked Security expert Paul Ducklin writes, Microsoft’s extended anti-malware support doesn’t really change much. “Windows XP will still officially fall off the edge of the world in April 2014 when Microsoft ends support,” Paul writes.
You can read the original article here.
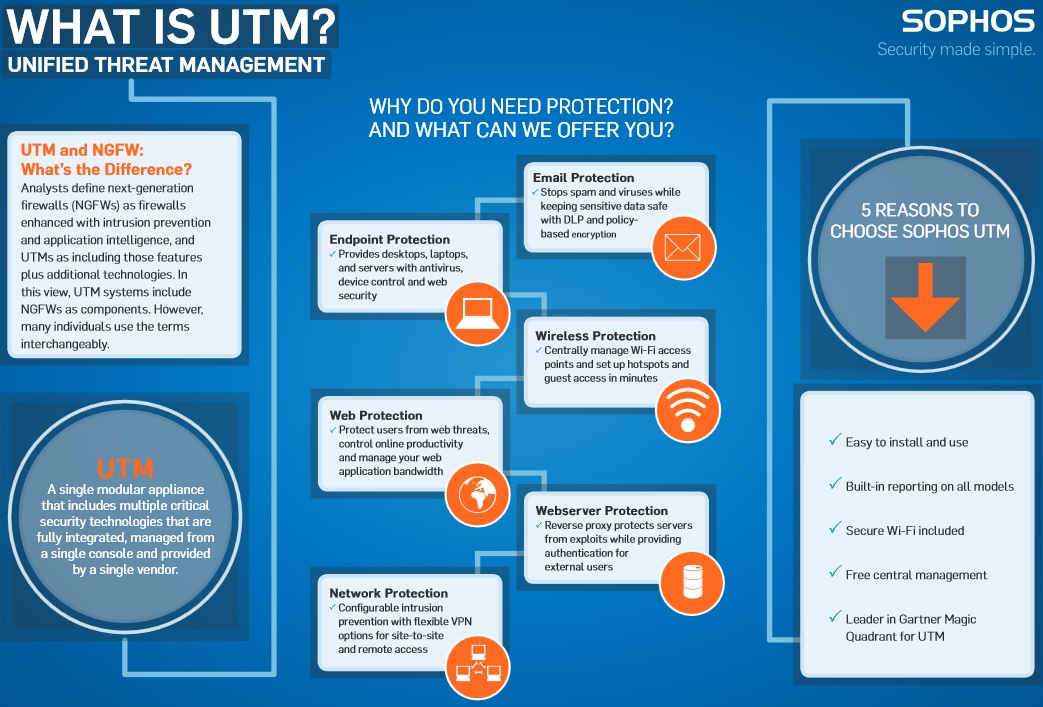
As we explain below, next-generation firewalls are typically defined as firewalls enhanced with intrusion prevention and application intelligence. On the other hand, UTM systems include those features—plus additional technologies such as email security, URL filtering, wireless security, web application firewalls and virtual private networks (VPNs). In this view, UTM systems include NGFWs as components.
Manager’s guide to UTM and next-gen firewalls
UTM systems are among the most widely used tools in the information security arsenal. The concept of unified threat management is very appealing: multiple critical security technologies, integrated on a single platform, provided by a single vendor.
IT managers evaluating UTMs need clearly defined criteria to choose the right protection.
You may wonder: Is a UTM solution right for my organization? What security features are most important? What other issues need to be considered, such as ease of management and support for remote users?
Download our free guide to get the answers to these questions: A Manager’s Guide to Unified Threat Management and Next-Gen Firewalls. (Registration required).
You can read the original article here.
One of our SophosLabs researchers, Anna Szalay, made an interesting discovery recently: a new type of Android malware that slips in through a security hole in the USB debugging feature that allows developers to modify their Android devices. Naked Security expert Paul “Duck” Ducklin reports that this malware can intercept your SMS text messages to steal bank transaction details.
Duck explains in his post that intercepting SMSes from your Android phone allows the attackers to steal information they can use to access, for example, your email accounts or bank accounts:
The crooks want to infect you with malware that knows how to intercept incoming SMSes and redirect their content elsewhere. You can see where this is going: mobile malware that reads your SMSes before you do can steal important data such as the two-factor authentication (2FA) codes sent by your email provider or your bank, giving cybercriminals a way into your account despite the extra layer of protection in place.
SophosLabs detects this SMS-stealing malware as Andr/FakeKRB-H. As Duck explains, this malware gets onto your Android in a multi-step process that starts with your device getting infected by a crafty piece of Windows malware that sneaks in through the USB connection between your Android and a PC. This “helper” malware is a downloader detected by SophosLabs as Troj/DwnlAPK-A.

If you connect your Android to a PC infected by Troj/DwnlAPK-A, the malware sneaks in under the guise of files that “appear to be regular, clean files that enable full USB-to-phone connectivity on Samsung and LG devices,” Duck writes.
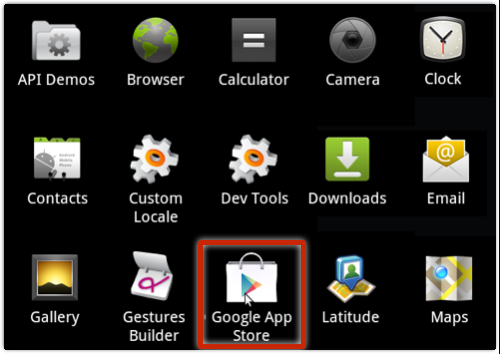
Then, once the downloader is installed, it loads the Android malware onto your device in what appears to be an app disguised as a Google-imitating “Google App Store” (the real Google store is simply called “Play Store”).
This is a good reminder that the bad guys continue to develop inventive ways of compromising our security to get at our most valuable data. Read the article at Naked Security to learn more about this malware and how to block it with security settings on your Android.
Jan
“Sophos and Cyberoam create a winning combination at the right time, in the right product markets and in all the right geographies,” said Kris Hagerman, Chief Executive Officer for Sophos. “Cyberoam has built a strong reputation as an aggressive and nimble innovator in the network security market, and like Sophos, has a ‘channel-first’ approach and reputation for delivering top-notch service and support. The acquisition expands and accelerates our network security roadmap to grow our presence in UTM, advanced threat protection, wireless and next generation firewall – some of the fastest growing markets in all of IT. This also continues our focus of providing exciting opportunities to grow our channel partners and customers.”
For more information, visit the Sophos corporate blog.
Founded in 1999 and headquartered in Ahmedabad, India, Cyberoam is highly regarded for its product innovation, quality, and world-class customer support. The company has more than 65,000 customers, more than 550 employees, and a strong channel focus with a network of 5,500 partners, with particular strength in India, the Middle East, and Africa. Cyberoam’s high performance UTM and Next Generation Firewall appliances, built on a similar Intel-based architecture as Sophos’ UTM solutions, deliver advanced technologies that will complement and expand the entire Sophos network security portfolio. Some of these technologies include the iView reporting engine, application control, user-based network policies, sophisticated next-generation firewall capabilities and advanced threat protection.
Hemal Patel, CEO of Cyberoam said, “Together Sophos and Cyberoam form a powerhouse in network security. We are growing our network security businesses substantially faster than the market, and joining forces allows us to drive even greater innovation and value. Our global footprint, commitment to the channel and complete security portfolio are clear competitive differentiators. We’re pleased to join the Sophos team.”
The acquisition advances Sophos’ position in network security, a strategic growth area for the company and a pivotal element of the company’s complete security strategy. Sophos combines leading security technologies in endpoint, mobile, encryption and data protection, e-mail, web, server, and network – all focused on small and midmarket enterprises and pragmatic enterprises of any size – and delivered entirely through the channel. Combined, Sophos and Cyberoam will have more than 2,200 employees, with more than 600 focused on network security, including more than 350 in R&D.
According to IDC Research, the network security market reached $7.9 billion in 2012; UTM comprised $2.7 billion of the market and was cited as the fastest growing segment at 21% growth. In the recent Gartner Magic Quadrant for Unified Threat Management, Sophos was again named a “Leader” and Cyberoam a “Visionary.”
You can read the original article here.
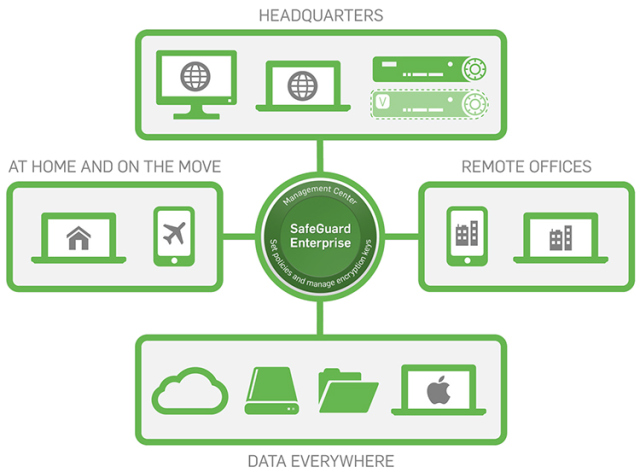
With version 6.1 we’re addressing the two biggest issues in encryption – performance and usability – by leveraging native operating system (OS) encryption for better performance; and delivering multi-platform management across all devices and cloud environments.
SafeGuard Enterprise also solves the major challenge of managing encryption across multiple platforms, devices, and cloud environments. Users and IT staff are now able to share data safely between Windows, Mac and mobile devices – securing data wherever it lives and wherever it is sent.
Managing multiple devices no longer means managing multiple consoles, so IT can fully embrace encryption to support their users. The Sophos encryption approach enables users to safely work the way they need to – sharing files between users, partners and customers via the cloud and the devices they use.
Sophos is the only vendor to offer native device encryption, cloud, mobile, removable and file share encryption in one centrally managed solution, providing unmatched security, performance, and an intuitive user experience.
What’s New in SafeGuard Enterprise 6.1
- With SafeGuard Enterprise you can manage Microsoft BitLocker for Windows or Mac FileVault 2.
- Now with support for Windows 8, and file and disk encryption on Macs, SafeGuard covers more operating systems and platforms.
- Simplified keyring creation grants you seamless, centralized management. With this newest release, you can save time with our keyring creation that requires no repeat login.
- Use a single console to manage full-disk, removable media, file-share, and cloud storage encryption
- Get up-to-date security status for all your devices with reporting and auditing that lets you monitor and enforce compliance with internal policies and external regulations.
You can sign-up for a free 30-day trial here.
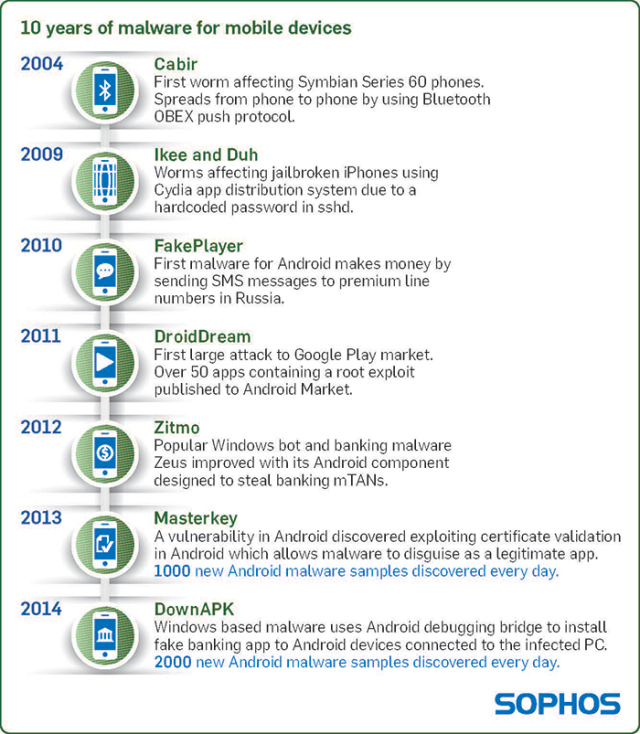
The current total of 650,000+ pieces of Android malware is up by approximately 600% from last January. Check out our mobile malware timeline below for our picks for the most important developments of the past decade, from the birth of mobile malware to today.
Mobile Security Threat Report
It’s been 10 years since the first mobile malware appeared. To mark this dubious anniversary, we’ve produced our first Mobile Security Threat Report. Download the report at sophos.com/mobilethreatreport to see how mobile threats have evolved, and to learn how best to protect yourself and your organization.
Get the free app: Sophos Mobile Security for Android
Sophos Mobile Security is a robust yet lightweight app that protects your Android devices without compromising performance or battery life. Using up-to-the-minute intelligence from SophosLabs, it automatically scans apps as you install them. Other features include a privacy advisor, encryption, and per-app password protection that you can set up for sensitive apps like your email. We’ve received several awards and many great reviews for Sophos Mobile Security, which has been downloaded more than 100,000 times from Google Play.
You can read the original article here.
Jan
Sophos Mobile Control
Protecting millions of mobile devices across tens of thousands of customer accounts, the latest release of Sophos Mobile Control (SMC) features an easy-to-use web-based console—deployed either on-premise or as a Service—to manage, protect and secure data. It delivers effective mobile device management to control the devices that access corporate systems. Using Sophos Mobile Control, IT teams can equally enforce regulatory compliance as well as corporate-mandated policies for complete data and device security without complexity. SMC supports Windows Phone 8, Android, and iOS 7, Apple’s latest mobile operating system.
In a recent research note by IDC, 24% of SMB organizations currently utilize an MDM solution to govern and manage their mobile devices. The study identified Sophos Mobile Control as the most-deployed MDM product among all survey respondents at 25%. In addition, last month, Sophos was named a leader in the Gartner Magic Quadrant for Endpoint Protection Platforms, and recently received a positive review from the 451 Group.
“We’re thrilled by the continued adoption of our MDM solutions. As the IDC report confirms, the market opportunity is huge, and Sophos Mobile Control is already at the head of the pack,” said Dan Schiappa, Senior Vice President and General Manager, Enduser Protection Group, Sophos. “As organizations look to define and refine BYOD policies and comply with regulations and compliance issues, Sophos continues to be a trusted provider for endpoint, network and server protection solutions.”
You can read the original article here.
One area that is becoming increasingly popular with many users is Security. The equipment in Data Centres and Server Rooms is extremely valuable, and that information stored within those environments is often priceless. Jacarta’s solutions can monitor security in a number of ways using various sensors and products:
Security Sensor – The standard Security Sensor is a magnetic reed type sensor that can be used to send an alarm in the event of a door or window being opened.
Vibration Sensor – The Vibration Sensor is often fitted to glass panels and doors where forced entry is possible. As soon as vibration is detected – the sensor will trigger an alert.
PIR Sensor – Using Infra-Red technology, the PIR sensor will alert users to movement within the monitored environment.
The security sensor, vibration sensor and PIR sensor are all part of Jacarta’s Go-Probe sensor range and are therefore compatible with all of the company’s monitoring devices. To view the Go-Probe Sensor literature click here.
JCAM IR IP Camera – Installing a surveillance system can be beneficial in a number of ways. As well as providing a visual deterrent Jacarta’s IP Camera can also be used to monitor staff activity and provide evidence in the case of criminal activity. JCAM IR has a range of key features including night vision and motion sensing. View the product literature here.
The survey was organised by the University of Kent’s Interdisciplinary Research Centre in Cyber Security, by a team composed of both computer scientists and psychologists, and conducted using Google’s Consumer Surveys platform. As the authors of the report caution their readers, the survey covered a relatively small number of people – just over 1,500 UK adults. That leaves it open to inaccuracies for all sorts of reasons, including sampling bias due to the kinds of people drawn to responding to online surveys, but the results seem dramatic enough to be more than just an anomaly. Other data picked up by the survey seems fairly predictable. Around two-thirds of us feel at risk from cybercrime, just over 1 in 4 have been the victim of some sort of “cyber-dependent crime” in the last year, with malware (11.9%) and phishing (7.3%) the main culprits. 1 in 10 has been exposed to online bullying, harassment or stalking.
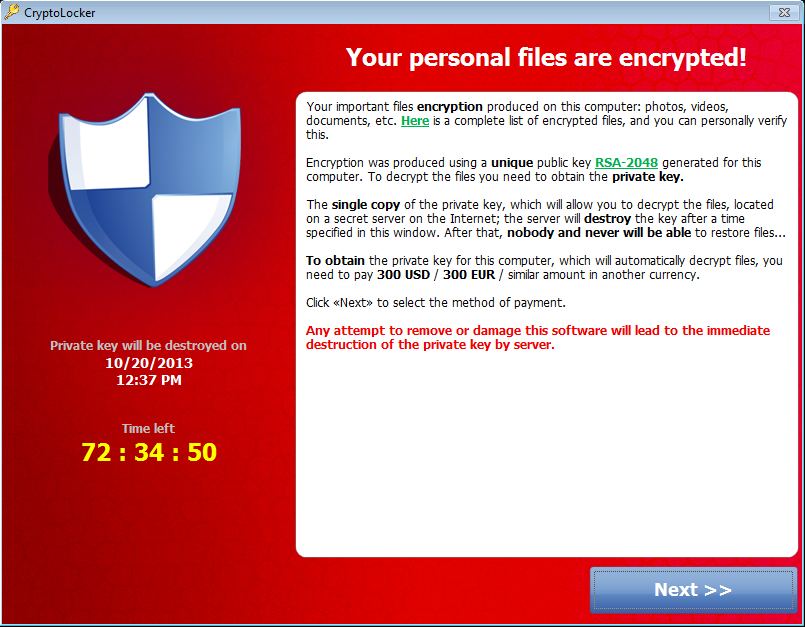
If the rate of malware infections seems a little higher than we normally see in surveys of this nature, that could well be down to the high levels of CryptoLocker and other ransomware included in those figures. 9.7% of people claimed they had been infected by ransomware of some kind, with CryptoLocker specifically named in the survey question and making up around a third of all reported infections.
Survey data always has a problem in that it’s only as accurate as the knowledge (and honesty) of the people being surveyed. Malware, for the most part, aims to avoid revealing its presence to its victims, sometimes going to great lengths to do so. So when you ask someone if they have ever been hit by malware, and their response is a strong and definite “no”, that answer should always be viewed sceptically. How can they possibly know? Proving a negative is not easy in the best of circumstances, and being certain something hasn’t happened simply because you haven’t noticed it happen is particularly difficult when the thing you haven’t noticed is specifically designed to be secretive and stealthy. Have you ever been spied on from a distant rooftop? No? Can you really be sure of that?
Unlike most malware though, CryptoLocker and other ransomware attacks make no secret of their presence, indeed their main intention is to make it very plain to their victims that they have been infected. So it could be that what we’re seeing here is not a change in the total level of malware going around, simply a change in the visibility of it to the general public.
Only a third have firewalls, and perhaps that is no bad thing. Other details emerging from this same survey include less than half of respondents using up-to-date anti-malware, just over a third implementing firewalls, and a little less than that exercising sensible password hygiene. Maybe a little more visibility will finally make the general public start sitting up and paying more attention to the risks of malware and other online threats. At the moment, it seems like we’re still mostly either ignorant or in denial, right up until something nasty infects our machine and nabs our data, or encrypts it and demands a ransom. That so many people pay up is not much of a surprise either. Like other security basics, it looks like proper backing up of sensitive or precious files is a rare thing.
Victims forced to pay up include police departments and law firms, with ransomware threats clearly targeting small businesses where proper security practices such as backups are more likely to be lacking. These shortcomings may have been hidden in the past, but now they are being forced into the spotlight, and the shock may just jolt people into giving the right priority to their security needs.
Here are five “top tips” for keeping safe against malware in general, and cyberblackmailers in particular:
- Keep regular backups of your important files.
- Use an anti-virus, and keep it up to date.
- Keep your operating system and software up to date with patches.
- Review the access control settings on any network shares you have.
- Don’t give administrative privileges to your user accounts.
You can read the original article here. More information about CryptoLocker here.
Jan
The new version includes the following improvements.
- New wizards for step-by-step installation and uninstallation of one or multiple centralized scanners. The install wizard also supports assigning static IP addresses to the scanners.
- The ability for the centralized scanners to receive product upgrades automatically from Sophos, eliminating the need to manually install new product versions.
- More selective email alerts, so administrators can focus on the most critical information.
- A new command-line tool to generate compliance reports showing which virtual guests are protected by which centralized scanners.
If you are currently using Sophos Antivirus for vShield, you may download the new version from the MySophos download page. If you haven’t yet experienced the speed and convenience of agentless scanning for your VMware environment, download the free 30 day trial today.
You can read the original article here.
Jan
Unfortunately, these companies don’t provide complete end-to-end encryption, and there are many loopholes the NSA, or cybercriminals, can slip through.
That’s why an encryption solution that protects data everywhere — in emails, on disk, or in the cloud — is essential. In this short video, we explain how you can get security and performance; plus how you can manage native encryption on Macs and Windows PCs, while also protecting data everywhere it resides.
James Lyne, global head of security research at Sophos, explains that many companies aren’t using encryption for fear of slowing users down. With Sophos, you don’t have to worry about encryption impacting performance, James says.
The new SafeGuard Enterprise solves the major challenge of managing encryption across multiple platforms, devices, and cloud environments. Users and IT staff can easily share data safely between Windows, Mac and mobile devices – securing data wherever it lives and wherever it is sent.
For more information about how to manage native encryption on Windows PCs with SafeGuard Enterprise, you can download our free whitepaper – Managing BitLocker With SafeGuard Enterprise (registration required).
What’s New in SafeGuard Enterprise 6.1
- With SafeGuard Enterprise you can manage Microsoft BitLocker for Windows or Apple FileVault 2 for Mac from a single console.
- Now with support for Windows 8, and file and disk encryption on Macs, SafeGuard covers more operating systems and platforms.
- Simplified keyring creation grants you seamless, centralized management. With this newest release, you can save time with our key ring creation that requires no repeat login.
- Centrally manage full-disk encryption and file encryption, wherever data is stored: removable media, network file shares and even in the cloud.
- Get up-to-date security status for all your devices with reporting and auditing that lets you monitor and enforce compliance with internal policies and external regulations.
You can read the original article here.
Jan
Developed by SophosLabs, this new Sophos UTM approach brings together multiple technologies to rapidly identify and isolate infected clients and prevent communication with malicious command and control hosts. This latest version introduces botnet protection and cloud-based sandboxing to expand on the Sophos UTM’s existing multi-layer Firewall, Web, Email and Endpoint protection. This extends the Sophos commitment to small and mid-market companies, delivering access to advanced protection without the complexity and cost normally associated with such functionality.
“The initial stages of targeted attacks can often go unnoticed by security systems that don’t control incoming and outgoing traffic. For organizations with limited IT resources, investing time and money in a dedicated ATP solution to detect these early signs is simply not realistic, given how tricky, complex and fast moving this type of traffic is,” says Chris Kraft, vice president, product management, Sophos. “That’s what we wanted to change. Today, with a few simple clicks, users get advanced protection without needing to be full-time security experts themselves.”
This new release also significantly enhances the speed of security scanning, with initial data showing the new performance optimized IPS doubling throughput speed in test environments. The Email, Web, and Network Protection modules all experience significant enhancements, including:
- Simplified Email Encryption and DLP – Sophos SPX technology eliminates need for a separate Public Key Infrastructure and policy-based DLP can trigger automatic encryption
- Smarter Web Control – streamlined policy setup enables granular user control and transparent web filtering of https traffic provides seamless protection
- Mobile Access Control – enhances Wi-Fi and VPN security by combining Sophos UTM with Mobile Device Management functionality in Sophos Mobile Control
- Performance Optimized IPS – intelligent processes and pattern management deliver enhanced scanning speeds to rapidly block network attacks and prevent breaches
- Botnet/Command and Control Protection – Sophos Advanced Threat Protection identifies and blocks infected machines communicating with malware command and control servers
“The UTM market is one of the most competitive in security. Numerous features and applications have been added over the past few years, and we’re increasingly seeing solutions are providing more effective security and better performance,” said John Grady, Research Manager, Security Products and Services, IDC. “This latest release from Sophos continues to simplify complex technologies. SPX email encryption is an example of that and is a differentiated approach among other UTM vendors.”
“Students are smart and always find ways to circumvent security, so schools are always in need of better ways to manage their web access and block inappropriate content,” says Bart Wilson, systems support manager, from Twotrees Technologies LLC, a Sophos partner. “UTM 9.2 is a huge step forward in solving this problem. By adding https traffic to web filtering in transparent mode, Sophos will help our customers to take back control – especially with so many students browsing on mobile devices.”
For additional information on all of the features in Sophos UTM 9.2 and extra information on Sophos’ network security solutions, please visit our Network Security area, watch the UTM videos, or check out the dedicated Sophos UTM blogs.
You can read the original article here.
Jan
A ‘channel-first, channel-focused’ company, Sophos continues to receive impressive recognition from CRN/The Channel Company, mostly recently with Michael Valentine, senior vice president, worldwide sales, and Kendra Krause, vice president of channel sales, North America, being named Channel Chiefs just last month. Late last year, Michael Valentine was also named a top IT executive for the mid-market.
Sophos enables partners to sell, market, distribute and implement its award-winning cloud, network, server and enduser protection solutions to organizations of all sizes. The company recently announced a new partner program for North America which includes a simplified deal registration and discount structure, full access to the Sophos product and solution portfolio, sales and marketing tools, training and technical enablement, and significant investments in local channel sales and SE resources.
To determine the 2014 5-Star recipients, The Channel Company’s Research team assessed each vendor’s application based on investments in program offerings, partner profitability, partner training, education and support, marketing programs and resources, sales support and communication.
“Solution providers have a lot of choices when it comes to selecting vendor partners. Identifying the right vendor, with the right technologies, and the right approach can make all the difference,” said Robert Faletra, CEO, The Channel Company. “Our annual Partner Program Guide and 5-Star rating recognizes the very best channel programs available in the market today to help solution providers determine which vendor delivers the best partner elements for their individual business goals.”
John Keenan, vice president of sales for North America, Sophos, said, “Receiving 5-Star recognition from CRN is validation that our strategy is working. From the highest levels, the Sophos team works hard to demonstrate our commitment to the channel in everything we do. We believe investing in those partners who commit to growing their business with us is a smart, simple approach to building lasting relationships and growing revenue. We’re honored to receive positive accolades that come as a result of that approach.”
For more information on the Sophos Partner Program, visit the Sophos website or to learn more about becoming a Sophos partner. The 2014 Partner Program Guide will be featured on CRN.com and the 5-Star Partners listing will be highlighted in the April issue of CRN.
You can read the original article here.
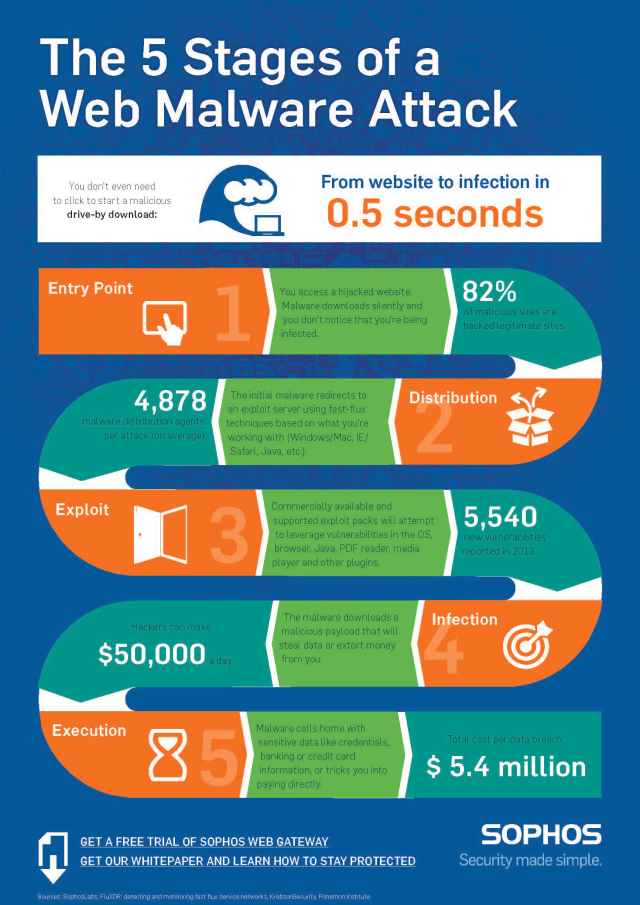
In the spirit of sharing our knowledge, we’d like to show you a pretty great infographic that explains in visual format how a web attack works. As you can see in the infographic below, a web attack happens in five stages, and this whole process takes less than a second. The web is the number one source of malware (a term that combines “malicious” and “software”), and the majority of these malware threats come from what is called a drive-by download.
5 Stages of a Web Attack
The term drive-by download describes how malware can infect your computer simply by visiting a website that is running malicious code (Stage 1: entry point).
Most of the time, these are legitimate websites that have been compromised to redirect you to another site controlled by the hackers (Stage 2: distribution).
Today’s cybercriminals use sophisticated malware packaged in an “exploit kit” that can find a vulnerability in your software among thousands of possibilities.
When your browser is redirected to the site hosting an exploit kit, it probes your operating system, web browser and other software (such as your PDF reader or video player) to find a security vulnerability that it can attack (Stage 3: exploit).
Remember — if you are not applying security updates to your operating system and software, you are unprotected against these exploits.
Once the exploit kit has identified a vulnerability, that is where Stage 4: infection begins. In the infection phase of an attack, the exploit kit downloads what is known as a “payload,” which is the malware that installs itself on your computer.
Finally, in Stage 5: execution, the malware does what it was designed to do, which is mainly to make money for its masters.
The malware known as Zbot can access your email or bank accounts. Another type of payload called ransomware can hold your files hostage until you pay to have them released.
This kind of attack happens all the time. But you don’t have to be a victim. Download our checklist of technology, tools and tactics for effective web protection to find out how you can protect your organization from malware attacks at every step of the way. You should also check out our free whitepaper explaining how malware works and offering tips to help you stop it: Five Stages of a Web Malware Attack. (Registration required).
You can read the original article here.
Jan
In particular, the overhead of running multiple concurrent antivirus scanners on a single host can affect performance and scalability. Meanwhile, the constant starting, stopping, and cloning of virtual machines can leave systems unprotected.
A new Sophos whitepaper explores these challenges and presents two effective approaches to securing your virtual machines without sacrificing performance: agentless antivirus and virtualization-optimized endpoint security. Simultaneous scheduled or on-demand scans can lead to a “scan storm,” increasing resource use and decreasing system performance.
“Scan storms occur when a host’s resources are overwhelmed by many virtual machines (VM) running antivirus scans at the same time. Because each VM is engaged in nearly identical behavior requiring multiple input/output (I/O) operations and substantial CPU processing, data throughput and system response time can slow noticeably. Even an otherwise speedy SAN or local storage array can be affected by the sheer volume of simultaneous read requests.”
The paper also covers how to choose the best approach and the right Sophos product (Sophos Antivirus for vShield, Sophos Server Protection, or Sophos Endpoint Antivirus) for your needs.
Download “Two Great Ways to Protect Your Virtual Machines From Malware” to learn more about how to deliver performance and security in your virtual data center (registration required).
You can read the original article here.