News
Jan
The firmware can be downloaded now from our Downloads page.
Jan
A new program, dubbed PIN Skimmer by its University of Cambridge creators, can correctly guess a high proportion of PINs using the device’s camera and microphone. When selecting from a test set of 50 4-digit PINs, PIN Skimmer correctly infers more than 30% of PINs after 2 attempts, and more than 50% of PINs after 5 attempts on android-powered Nexus S and Galaxy S3 phones. When selecting from a set of 200 8-digit PINs, PIN Skimmer correctly infers about 45% of the PINs after 5 attempts and 60% after 10 attempts. The university team discovered that PIN Skimmer could identify PIN codes entered on number-only softpads by using the camera on the device to monitor the user’s eye movements as they enter their code. Also, the microphone could be used to detect “touch events” – the clicking sound made as the user enters their PIN on the touch screen.
The paper, written in order to raise awareness of side-channel attacks on smartphones, took the approach that the device had already been infected with malware that was then attempting to snaffle the PIN. The university team then set out to see how effective an attack could be and, also, how PIN length may affect the likelihood that the code could be correctly guessed. Mimicking a typical piece of malware, stealth was a key feature in the design. The researchers ran image processing algorithms remotely to minimise battery drain, something that could alert the user that an unauthorised program was running.
An API exposed by the Android operating system was used to disable the LED that switches on in some handsets when the camera is in use. Photos and video taken by PIN Skimmer were saved to the phone but the file sizes were limited to 2.5MB to reduce detection. A real piece of malware could likely hide such files from view completely. Likewise, the research team hypothesised that the sending of data back to the remote server could also be hidden from the user.
Additional network charges is another problem connected with transmitting data. Many smartphone users are on tariffs that charge them additional fees should they use more than a pre-determined amount of data within any monthly period. To that end the report suggested that a real-life Trojan would probably report back to its control centre only when it detected a free WiFi connection within range. The researchers discovered that, contrary to what you may have expected, longer PINs were actually easier to crack than shorter ones. This unexpected result was put down to the fact that longer PINs actually gave the program more information to work with which increased its accuracy.
One of the co-authors of the report, Professor Ross Anderson wrote: Our work shows it’s not enough for your electronic wallet software to grab hold of the screen, the accelerometers and the gyro; you’d better lock down the video camera, and the still camera too while you’re at it. (Our attack can use the still camera in burst mode.)
As for mitigating the risks posed by such an attack, Anderson suggested that questions need to be asked as to which resources should remain accessible during PIN entry, though he did note how disabling some functions, i.e. the speakers, could cause extreme problems to the usability of the device: For instance when a call comes in, the user needs to hear the ring tone while unlocking his phone; otherwise he may assume the caller has hung up.
Instead, he suggests that whitelists may be the answer – denying use of all resources during PIN entry, unless explicitly authorised. Another option, according to Anderson, would be a more widespread adoption of biometrics in smartphones but that is not without its own issues.
You can read the original article here.
Jan
“This certification is a critical step toward the future development of LogPoint. It will enable us to pursue significant opportunities with government authorities, in the security and intelligence sector as well as with major corporations globally,” says Jesper Zerlang, CEO of LogPoint. “We are extremely excited about the partnership with Boeing that will elevate the LogPoint platform to the Tier 1 in the market and place us among the best enterprise SIEM security solutions”
Boeing will assist LogPoint prepare the SIEM platform for the Common Criteria for Information Technology Security Evaluation, with the goal of obtaining Evaluation Assurance Level 3 certification before mid-2014. This certification is often a requirement for cybersecurity contracts in NATO countries and throughout the world. Obtaining it will make LogPoint the only Danish cybersecurity company to meet the standard – and one of few globally.
“We are experiencing a dramatically increasing demand for improved network security as the number of successful network attacks globally are sadly rising. An effective SIEM-solution is one of the cornerstones of efficient enterprise network security, not only to improve security monitoring and early breach detection, but also to answer an increasing demand for regulatory compliance in many countries around the world”, says Jesper Zerlang.
The LogPoint SIEM-platform are currently deployed with more than 250 organizations in Europe, including large- and midsized enterprises in all industry sectors as well as public authorities ranging from municipalities to government authorities. LogPoint is present with offices in the Scandinavian countries as well as Germany and the UK and are currently expanding to a number of other European markets. LogPoint is partner centric and deploy its solution through a network of certified partners, ISP’s and system integrators throughout Europe.
LogPoint is a European, Copenhagen-based IT security company that delivers IT security SIEM solutions for enterprise networks. The LogPoint technology is an advanced Security Information and Event Management (SIEM) platform that provides real-time monitoring and incident management for security-related events from network, security devices, systems and applications as well as log management, analytics and compliance reporting.
You can read the original article here.
Jan
Of 2,000 respondents surveyed globally, 58 percent confirmed that management does not see cyber attacks as a significant risk to their business. Despite this, IT infrastructure and asset security incidences, as well as wider security related disruptions, were found to have cost these SMBs a combined average of $1,608,111 over the past 12 months.
The research, sponsored by Sophos, also identified that the more senior the position of the decision maker in the business, the more uncertainty there was surrounding the seriousness of the potential threat.
“The scale of cyber attack threats is growing every single day,“ said Gerhard Eschelbeck, Chief Technology Officer for Sophos, “yet this research shows that many SMBs are failing to appreciate the dangers and potential losses they face from not adopting a suitably robust IT security posture.”
According to the research, there are three main challenges preventing the adoption of a strong security posture: failure to prioritize security (44 percent); insufficient budget (42 percent); and a lack of in-house expertise (33 percent). In many SMBs there is also no clear owner responsible for cyber security, which often means it falls into the purview of the CIO.
“Today in SMBs, the CIO is often the “only information officer”, managing multiple and increasingly complex responsibilities within the business,” said Eschelbeck. “However, these “OIOs” can’t do everything on their own and as employees are demanding access to critical apps, systems and documents from a diverse range of mobile devices, it would appear security is often taking a back seat.”
The study also reveals uncertainty around whether ‘Bring Your Own Device’ policies (BYOD) and the use of the cloud are likely to contribute to the possibility of cyber attacks. Seventy-seven percent of respondents said the use of cloud applications and IT infrastructure services will increase or stay the same over the next year, yet a quarter of those surveyed indicated they did not know if this was likely to impact security.
Similarly, 69 percent said that mobile access to business critical applications would increase in the next year, despite the fact that half believe this will diminish security postures.
“Small and midsize organizations simply cannot afford to disregard security,” said Larry Ponemon, president of the Ponemon Institute. “Without it there’s more chance that new technology will face cyber attacks, which is likely to cost the business substantial amounts. CIOs are under pressure to implement new technology that informs agile and efficient ways of working, but this should not take precedence over security. The industry needs to recognize the potential dangers of not taking cyber security seriously and create support systems to improve SMB security postures.”
The study targeted SMBs in the United States, United Kingdom, Germany and Asia-Pacific (Australia, India, China and Singapore) to better understand how such organizations are managing security risks and threats. Key findings of the study include:
- Fifty-eight percent of respondents say management does not see cyber attacks as a significant risk.
- One-third of respondents admit they are not certain if a cyber attack has occurred in the past 12 months. Forty-two percent of respondents said their organization had experienced a cyber attack in the past 12 months
- Respondents in more senior positions have the most uncertainty about the threats to their organizations, indicating that the more removed the individual is from dealing on a daily basis with security threats, the less informed they are about the seriousness of the situation and the need to make it a priority.
- CISOs and senior management are rarely involved in decisions regarding IT security priorities. While 32 percent say the CIO is responsible for setting priorities, 31 percent say no one function is responsible.
- Forty-four percent of respondents report IT security is not a priority. As evidence, 42 percent say their budget is not adequate for achieving an effective security posture. Compounding the problem, only 26 percent of respondents say their IT staff has sufficient expertise.
- Respondents estimate that the cost of disruption to normal operations is much higher than the cost of damages or theft of IT assets and infrastructure.
- Mobile devices and BYOD are much more of a security concern than the use of cloud applications and IT infrastructure services. However, these concerns are not preventing extensive use and adoption of mobile devices, especially personal devices.
Uncertainty about their organization’s security strategy and the threats they face varies by industry:
- Respondents in financial services have more confidence, which can probably be attributed to the numerous data protection regulations.
- The technology sector is also more security aware, which is probably due to the IT expertise that exists in these organizations.
- Retailing; education and research; and entertainment and media have the highest level of uncertainty about their organization’s security strategy and the threats they face.
Recommendations:
- Organizations need to concentrate resources on monitoring their security situation in order to make intelligent decisions. While assessing where they stand on the security continuum, organizations need to focus on monitoring, reporting and proactively detecting threats.
- Establish mobile and BYOD security best practices. Carefully plan and implement a mobile strategy so that it doesn’t have an impact on the overall security posture.
- Organizations should look for ways to bridge the gap created by a shortage of information security professionals. Consider ways to free-up time for in-house resources, including a move to cloud technologies, security consulting and easy-to-manage solutions.
- Measure the cost of cyber attacks, including lost productivity caused by downtime. Work with senior management to make cyber security a priority and invest in solutions that restore normal business activity more quickly for a high return on investment.
- Organizations in all sectors are regularly breached and regulations are often simply the beginning of properly securing a network. Consider consolidated security management to gain a more accurate picture of threats that will help focus on problem areas.
A full copy of the Ponemon Institute study: The Risk of an Uncertain Security Strategy, is available here.
Jan
In an increasingly complex security environment Sophos works with partners to make security simple to deliver, implement and manage. Over the last 12 months Sophos has created a more flexible and generous partner programme, providing partners with protection for deal registrations, attractive margins and joint lead generation initiatives. The programme also provides up-to-date certification, to ensure partner sales and technical teams are fully trained across Sophos’s latest solutions to help drive partner businesses forward. Delivered by dedicated channel relationship managers, Sophos gets to know partner businesses to ensure they feel supported every step of the way.
James Vyvyan, Regional Vice President, UKI, Sophos said: “We’re delighted to have won ‘Security Vendor of the Year’. Sophos is committed to a ‘channel first’ strategy and we believe that by taking the time to understand our partners’ business model, we can work together to provide the solutions that best suit their customers’ IT security needs.”
Sophos also won two awards in CRN’s DACH awards on 13 November: Security Vendor of the Year and Channel Champion of the Year 2013.
Commentary from the Sophos Channel
“Many of the innovations Sophos has introduced are unique to the market. These unique solutions make it possible for us to differentiate ourselves from other security consultants and better meet our clients’ needs,” said Mark Robinson, Director, Globelink Infrastructure & Network Security.
“The Sophos Partner Programme empowers proactive and enthusiastic partners like ourselves to achieve the levels of technical and sales accreditation required to represent Sophos at the highest level,” said Paul Cox, Managing Director, Quadsys.
“We’ve worked closely with Sophos for more than 12 years and feel the relationship is stronger now than it has ever been. The sales, technical, financial and management teams at Sophos and Foursys are all working really closely together, which means we get it right and we both put customer service at the top of the agenda,” said Paul Prior, Managing Director, Foursys.
“WD is using enterprise-class components to build a new family of network appliances for small businesses,” said Bill Evans, general manager of WD’s business storage solutions group. “The WD Sentinel S-series network appliances are engineered with Intel Xeon processors, pre-populated with WD Se datacenter 3.5-inch hard drives for rapid deployment, and feature dedicated 2.5-inch boot drives for maximum reliability. No other vendor offers a comparable network storage plus server in an equally small form factor. With a small footprint and quiet fan, an S-series appliance can be deployed anywhere.”
Proven Components from Intel, Microsoft, and WD
Built by WD, powered by an Intel Xeon processor and running Windows Server 2012 R2 Essentials, the WD Sentinel S-series is based on proven technologies from industry leaders. Unlike competitors’ proprietary operating systems, the S-series is a fully configured native Windows Server on which customers can deploy thousands of Windows applications.
“Windows Server 2012 R2 Essentials gives customers the benefit of built-in, groundbreaking, low-cost storage technologies, and WD’s Sentinel S-series hardware helps small businesses take advantage of these technologies,” said Jamie Hamilton, Director of Marketing, OEM Division at Microsoft Corp. “We are pleased to work with WD to tackle the small business, first-server opportunity. WD’s hardware engineering expertise, previous success with network storage products based on Windows Storage Server, and leadership in offering an R2 version of Windows Server 2012 Essentials puts WD in a good position to serve this industry.”
Reliable Enterprise Grade Components
The WD Sentinel S-series include WD 3.5-inch datacenter-class hard drives for enhanced data security. Businesses gain enterprise-class reliability with dual dedicated boot drives (optional on WD Sentinel DS5100), dual gigabit Ethernet ports, and dual external DC-in power adapter ports. This engineered redundancy, along with a bezel lock for physical security, all add to the reliability of this ultra-compact network storage plus server that can be deployed virtually anywhere.
Affordable First Server for Any Small Business
The WD Sentinel S-series is a complete, fully-configured solution with automatic backup and restore software for up to 25 users and 50 computers, all at a very affordable price that starts at $2,560 U.S. MSRP. By combining a single solution for both storage and server requirements, the S-series appliances are a great solution for any small business looking for their first server.
“Finally, a network storage vendor has delivered a low-cost, turn-key solution that meets my customers’ requirements—with no assembly required,” said Kevin Royalty, Microsoft MVP and Managing Partner of Total Care Computer Consulting in Centerville, Ohio. “Small business customers want a packaged solution with balanced disk, processor, memory, and operating system that is engineered and tested as a unit. The DS5100 and DS6100 appliances are ideal as a ‘first server’ due to the high-performance Intel Xeon processor, Windows Server, high-capacity enterprise-class disk storage, and tiny footprint.”
Availability
WD Sentinel S-series appliances are available today at CDW, PC Connection, and Insight, and through select VARs, resellers, and distributors worldwide. The WD Sentinel DS5100 is pre-populated in capacities of 4 or 8 TB. The WD Sentinel DS6100 is available with capacities of 8, 12, or 16 TB.

Jan
WD’s My Cloud personal cloud drives, available now in China in capacities of 2 TB, 3 TB and 4 TB, enable consumers to organize, centralize and secure the digital content from all of their computers and mobile devices and access those files from any device and from anywhere in the world. WD’s My Cloud EX4 high-performance four-bay network attached storage (NAS) solution, available now in China in 0 TB, 8 TB, 12 TB or 16 TB1 capacities, provides creative professionals, prosumers and workgroups a reliable way to save, share, back up, stream and manage massive amounts of digital data. The Baidu Yun service is a leading public cloud storage service provider with more than 100 million users. Consumers and businesses store content on Baidu Yun for easy access and sharing from any computer or mobile device.
The collaboration between WD and Baidu will enable Chinese customers to manage their Baidu Yun account and easily transfer files between their My Cloud or My Cloud EX4 device and Baidu Yun using WD’s My Cloud mobile apps for iOS and Android operating systems. Baidu and WD customers will also be able to back up their local content to Baidu Yun, as well as backup their Baidu Yun account to their local storage using WD SmartWare™ Pro software.
“The growth of Baidu and its public cloud storage and services in China has been spectacular; it’s a pleasure to collaborate with them,” said Jim Welsh, executive vice president, Branded Products and worldwide sales. ”The integration of Baidu Yun with our personal cloud and external storage platforms gives our mutual customers the best of all worlds – the ability to keep content safe at home, while backing up and sharing with friends on Baidu Yun.”
“Baidu aims to provide the best way for people to access their valuable content, regardless of their location,” said Hou Zhenyu, chief architect of Baidu Yun. “WD is a leader in high-capacity local storage, and integrating our public cloud storage service with WD’s platform gives our customers a compelling hybrid cloud storage solution – the best of both public cloud storage and personal cloud storage.”
You can read the original article here.
Jan
In comments that support Array’s ranking in the new report, IDC analysts note that the company’s WAN optimization solution has “increased its chances of cracking bigger deals and positioning themselves as an end-to-end solution provider in the ADC space.”
According to IDC, drivers of Array’s leading position in the India market include the ability to close deals in the lucrative government and banking and financial services industry (BFSI) markets, as well as the ability to offer holistic ADC and WAN solutions with custom costing to potential customers. Although Cisco still leads – due to volume WAN optimization sales – Array is mounting a challenge by way of continued growth in the WAN optimization space.
Mr. Shibu Paul, Country Manager at Array Networks said, “IDC is a respected authority tracking the markets Array serves, and the local IDC team in India has a superior understanding of vendors, partners and customers in the application delivery networking space. The Array team has been working tirelessly to serve our customers, assist our partners and enhance our offerings, and I am extremely pleased to see our efforts paying off as reflected in the new IDC market report.”
“In addition to growing traction in the enterprise based on its suite of application delivery networking solutions, Array is also opening up new opportunities with its line of software appliances which can be hosted on any virtualized server to break price barriers and make solutions more affordable to SMBs,” said Manoj Iyer, IDC’s market analyst for enterprise networking in India. “With the ability to support a broad range of customers and a go-to-market strategy focused on educating partners its load balancing, WAN optimization, enterprise mobility, high availability, BYOD and application acceleration solutions, Array is well positioned to further increase their market share in the application delivery networking market.”
You can read the original article here.
Learn How Balance and MAX Routers Team Up for Unbreakable VPNs
The Balance lineup uses Peplink SpeedFusion technology to integrate seamlessly with MAX cellular routers and deliver unstoppable VPNs in a wide variety of applications. To see how, visit our updated Balance and Unbreakable VPN pages. Filled with helpful deployment diagrams and technology highlights, they’re a great way to learn more about fast, reliable, and affordable Peplink solutions for retail, enterprise, public safety, and much more.

You can read more here.
Jan
1. Always secure your smartphone with a password
One of the most basic security tips, but one which is sometimes completely overlooked! Having no access protection at all is just foolish. Swipe patterns are ok, but greasy finger-trails could reveal too much. A four-digit PIN is an improvement but using a strong passcode is the ideal phone protection.
2. Ensure that your device locks itself automatically
If you set up password-protection on your phone but then leave it unlocked on your desk for 15 minutes, you won’t have achieved very much. Most smartphones allow you to set them up to automatically lock themselves after a period of inactivity. Make sure you choose the shortest timeout you are comfortable with. Two to five minutes is better than ten to thirty, even if it does feel slightly inconvenient.
3. Install security software
Your smartphone is a computing device and should be protected accordingly. Look for an app like Sophos Mobile Security that includes malware prevention, remote data wipe, privacy review of apps and an automatic security advisor to alert you to potential risks when you change a device setting. If you’re in charge of securing your organisation’s phones and tablets, then choose a mobile device management solution like Sophos Mobile Control.
4. Only download apps from approved sources
The Google Play Store and Apple’s App Store take security pretty seriously. They are very careful about what apps they make available and will withdraw apps that raise concerns after release. Read user reviews of apps before installing them – if there are any security concerns then someone else may well have mentioned them.
5. Check your apps’ permissions
Apps. Image courtesy of Shutterstock.Many apps require more than the basic default permissions. For instance, you can reasonably expect an SMS app to send and receive text messages just as a mapping app will request your GPS location. But something like a calculator that needs network access or an alarm clock that wants to read your contact database should be treated with extreme caution!
6. Don’t miss operating system updates
Updates to your OS often include system vulnerability patches, so it’s important to install them. You might want to be advised of updates rather than having them automatically installed, as early adopters sometimes experience teething problems – but the forgetful among you may prefer that to missing updates altogether.
7. Be wary of any links you receive via email or text message
Now you can pick up email on your phone, exercise caution when clicking on links. And phishing scams are not limited to email – a text message can incite you to click on a dodgy link or ask for personal information. Even simply replying to unknown SMS or email senders can raise the crooks’ interest in you, leading to more pressure to respond.
8. Encrypt your smartphone
Even if you’ve secured your smartphone with a password, a thief could still plug your device into a computer and gain access to all of your personal information. Using encryption on your smartphone can help to prevent such data theft.
9. Turn off automatic Wi-Fi connection
WiFi. Image courtesy of ShutterstockOne of the great things about modern mobile phones is their ability to connect to the internet in many ways, but continually probing for wireless networks gives away information about your identity and location, and blindly connecting to unencrypted access points can let your phone leak all sorts of useful things for malicious actors to intercept and act upon. So tell your phone to forget networks you no longer use, so as to minimise the amount of data leakage and configure your phone to automatically turn on/off wireless in certain places using a location-aware smartphone app.
10. Turn off Bluetooth and NFC when not in use
Bluetooth and NFC (near field communication) are great in terms of connectivity, allowing you to use accessories such as wireless keyboards and headsets or make payments with a wave of your smartphone. But it does open a door for the bad guys to gain access to your device and access your data, so you should either switch these features off or put your device into “not discoverable” mode whenever possible. Also, be careful when pairing devices – never accept requests from unknown devices.
You can read more here.
Jan
“While many security experts are aware of the high level trends, few have recognized their significance,” said James Lyne, global head of security research at Sophos. “If 2013 has taught us anything, it is that traditional security controls are struggling. These new behaviors are forcing the industry to adapt and change, and widely held best practices must be reconsidered.”
The threat report highlights new security concerns ranging from stealthy malware tools that offer dynamic camouflage and provide attackers with long-term persistent access to users’ data, to the proliferation of connected devices that represent new and often ill-protected targets. Many new “Internet of Things” devices are becoming commonplace in our homes and everyday infrastructure, offering shadier cybercriminals the potential to impact our daily lives, rather than just the traditional theft of financial information.
“These trends are set to continue in 2014 as threats become even smarter, shadier and stealthier,” said Lyne.
In 2014 Sophos predicts greater focus from cybercriminals on high quality and convincing phishing and social engineering to compensate for harder-to-exploit operating systems like Windows 8.1; embedded devices (such as POS systems, medical systems and new “smart” infrastructure) will open old wounds as security mistakes eliminated in the modern PC environment are carelessly re-implemented; attacks on corporate and personal data in the cloud will continue to grow as providers struggle to refine the security strategy in this new computing platform; and malware for mobile is set to become as sophisticated as its PC relatives.
“It is clear in 2014 we need to be watching not just the evolution of existing attacks, but be prepared for dangerous new threats emerging that we haven’t previously dealt with,” said Gerhard Eschelbeck, CTO at Sophos. “As the industry adapts and enhances protection mechanisms to cover new devices and threats, this is increasingly becoming an issue for every member of society, not just for government and business.”
A full copy of the Security Threat Report 2014 containing more information and statistics on cybercrime in 2013, as well as top tips and predictions on emerging trends, can be downloaded here.
You can read the original article here.
As well as providing excellent daylight surveillance coverage, JCAM-IR also has infra-red capability to enable a comprehensive 24-hour surveillance operation to be implemented.
JCAM-IR Image Quality
Crucial to the successful implementation of any security surveillance strategy is the image quality of the cameras being used. JCAM-IR is an HD 2MP fixed lens camera that can stream video with a resolution of up to HD1080p at up to 30fps. Facial recognition can be achieved in normal light conditions up to a distance of 10m. JCAM-IR has a darkness/low light range of 10m.
JCAM-IR Alerts
When motion is detected by JCAM-IR, videos can be recorded and snapshots (of before and during the event) sent by email. Videos can be saved to the camera’s on-board Micro SD card (user supplied) or, alternatively, to a networked PC. Camera recording and snapshots can also be activated manually or by an event triggered by an optional attached Jacarta Go-Probe sensor (water leak, door open, smoke, etc.).


You can download the brochure here.
We all believe (and hope) that ‘it won’t happen to us’ but how many horror stories of you heard where an unnoticed leak has turned into a flood, a briefly un-manned room has resulted in theft, or a faulty piece of equipment has led to ruined stock, lost data or hardware? SMS Alarm General is an extremely cost-effective way of helping to prevent these initially minor events becoming catastrophic for you or your business.
Up to 2 x Go-Probe sensors and 1 x Temperature sensor can be monitored by the Alarm General and it is also possible to link the Alarm General to alarm panels such as fire, security, generator, UPS, fire suppression, air-conditioning, etc. SMS Alarm General can be used to help protect all types of premises: Offices, data centres, shops, warehouses, industrial units, homes, holiday villas – the list is endless!
How Does SMS Alarm General Work?
The SMS Alarm General solution consists of a quad-band modem, integrated Jacarta configuration and alerting software module, and the capacity to connect up to 2 x Go-Probe sensors and 1 x Temperature sensor. Once a user-supplied SIM card is inserted and the sensors connected, configuration of alarm messages and contact telephone numbers can be carried out by sending text messages to the Alarm General. The Alarm General will reply to acknowledge each of the messages, confirming that the required instruction has been carried out.
Once configured, SMS Alarm General will continually monitor the condition of the sensors and alert the configured mobile phone numbers when an alarm condition is detected. Up to 5 numbers can be alerted. In addition to the alerts, Alarm General can send you a daily status text, and you can remotely check the status of your sensors at any time by sending a text message to the Alarm General.

You can download the brochure here.
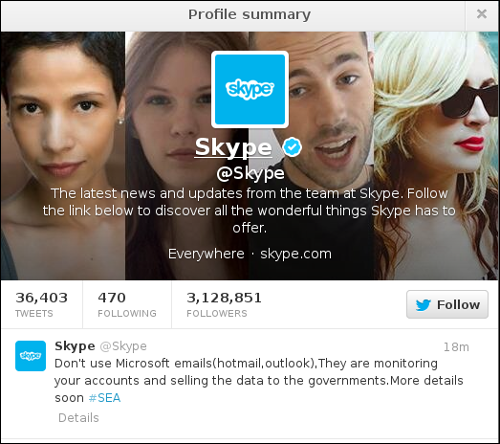
This isn’t entirely surprising as the FBI had issued a warning on Christmas Eve to media organizations about a new wave of phishing attacks associated with the infamous SEA. Skype has more than three million followers on Twitter, which indicates that, had the attackers wanted to send out malicious links or other dangerous content, this could have been a whole lot worse.
What I would like to know is why on earth a company social media profile with over three million followers would not be using two-factor authentication. Earlier this year Twitter rolled out an improved two-factor solution seemingly in response to previous attacks by the SEA. WordPress offers two-factor authentication and Facebook has supported two-factor authentication for a couple of years now, all in an attempt to prevent this exact type of attack.

Microsoft, would you care to explain why you apparently are not using it? We believe it is the responsibility of organizations with a large number of followers to do whatever they can to secure their profiles. We suppose this can be a lesson to the rest of us. Take advantage of the safety net of two-factor authentication whenever possible. While it may be less than perfect, so are you.
You can read the original article here.
The Federal Communications Commission reports that mobile phone theft constitutes 30-40% of all robberies across the United States, a crime that cost US citizens $30 billion in 2012. In the Senator’s own state of California such thefts are even more prevalent, accounting for over 50% of street robberies, Los Angeles alone has seen a 12% increase in smartphone thefts over the last year. If the kill switch legislation is passed, carriers will be able to remotely send a message to any device that has been reported as either lost or stolen. That message would trigger the device to ‘brick’ itself, effectively making it useless, and a far less appealing option for would-be thieves. With a few exceptions, most phones do not offer any form of remote deactivation at this time which makes them especially appealing to thieves who can snatch and sell them on in a very short period of time.
One manufacturer that does offer deactivation is Apple, though Gascón would like to see such a feature become the default rather than an option: “Apple should be commended for leading the way and making efforts to safeguard their customers, but it is still too early to tell how effective their solution will be. Until Activation Lock is fully opt-out, it appears many iPhone owners will not have the solution enabled. This leaves iPhone users at risk as thieves cannot distinguish between those devices that have the feature enabled and those that do not”.

Gascón, along with New York Attorney General Eric Schneiderman, have asked mobile phone manufacturers to propose methods of curtailing the theft of smartphones. Having presented the tech companies with a June 2014 deadline, Gascón said: “I appreciate the efforts that many of the manufacturers are making, but the deadline we agreed upon is rapidly approaching and most do not have a technological solution in place. Californians continue to be victimized at an alarming rate, and this legislation will compel the industry to make the safety of their customers a priority”.
The bill will be formally introduced in January 2014.
The readers who wish to protect their Android devices in case of loss or theft can install Sophos’s free Antivirus and Security app which includes the following features:
- Supports remote commands for Wipe, Lock, Alarm, Locate, Reset passcode and Message to finder
- Reporting of the device location before the battery runs out
- Notification if the SIM card is replaced
You can read the original article here.
Service providers need higher level of encryption support
“If you look at one of our typical deployments, yes, they want security, they want SSL, but the numbers they support are in the thousands,” he said. “It’s nothing compared to a business model that is supporting millions of users. When we are talking to these SaaS providers, it’s a whole new level of value proposition” and a market segment that Array wants to target.
With the new encryption standard requiring almost five times the computational power as 1,024-bit encryption, more robust ADCs are a necessity, he said. SaaS provider YourMembership.com is using Array’s 5600 platform to beef up its capacity and throughput, said Chief Technology Officer Hutch Craig. The St. Petersburg, Fla.-based SaaS provider serves more than 2,300 associations with its menu of back-office services, reaching more than 20 million users. A lot of the provider’s traffic requires secure processing, Craig said; everything from e-commerce to dues information and other sensitive data.
YourMembership.com deployed a pair of ADCs for failover protection at a data center in Orlando, Fla. They replaced two older Array ADCs that were running at more than 50% utilization each because of the volume of transactions they had to process. “Things were getting really tough on them; the 5600s are unbelievable,” Craig said. “Everything is funneled through the ADC, from the API to the actual front-end offering. We have millions of [end users] and tens of thousands of administrators that go into the box.”
-
Craig said the 5600’s SSL acceleration capabilities were a key attribute. In YourMembership.com’s case, the processor-intensive steps needed to handle public-key encryption algorithms are handed off to a hardware accelerator, although the ADC has the ability to process SSL transactions without the use of separate servers.
- More traffic headed in 2014
-
YourMembership.com will increase the amount of traffic routed through the Array ADCs next year as part of a plan to consolidate all of its data center operations in Orlando, Craig said. Right now, the provider has a data center in Austin, Texas, that serves clients YourMembership.com inherited as part of its 2012 acquisition of rival Affiniscape.
-
Craig said YourMembership.com will phase out the Austin data center and route all traffic to Orlando and the 5600s by next spring. Andersen said SaaS providers are a logical target for his company’s ADCs, which are priced from 30% to 40% below competitors’ similarly equipped models.
-
“They have to support a lot more customers and they also have to be on a higher standard of SSL. At the same time, they can’t afford to pay through the nose for ADC hardware,” Andersen said.
The 5600 is priced beginning at $28,995; models that support hardware SSL acceleration begin at $37,995. -
In addition to the 5600, Array beefed up two other models to handle the new encryption standards. The 2600 can process up to 5,000 SSL transactions per second, while the high-end 10650 can handle up to 70,000 transactions per second. All of the devices are engineered with 10 Gigabit Ethernet connectivity and multicore processing with throughput ranging from 10 Gbps to 120 Gbps, depending on the model.
You can read the original article here.
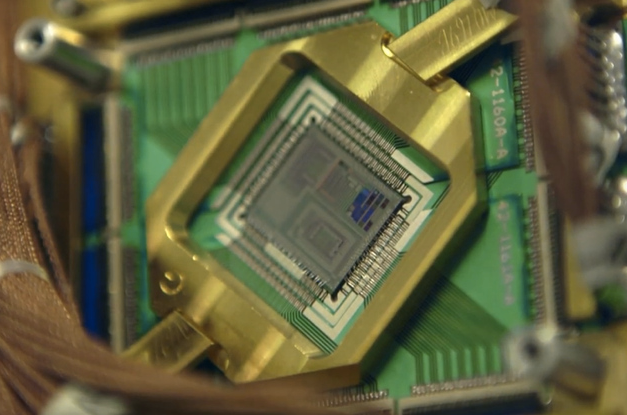
Quantum computing hinges, very broadly, on allowing individual bits (called qubits) to contain superimposed values of zero and one, vastly increasing computing power. Its implications for cryptography, medicine, and research have made it a major goal for public services and private industry alike: DARPA has devoted years of funding to quantum computing research, and Google launched its own “Quantum Artificial Intelligence Lab” last year.
But while qubits have been stored for a limited period of time under certain conditions, and specialized machines have been built using quantum technology, that’s not enough for practical code-breaking applications. Last year, for example,The Economist all but ruled out the possibility that the NSA had a crypto-ready quantum computer.
The NSA’s program, part of the larger intelligence community “Black Budget,” doesn’t actually task anybody with building a quantum computer. According to the memo, it asks researchers to “conduct basic research in quantum physics and architecture/engineering studies to determine if, and how, a cryptographically useful quantum computer can be built.” So while the grant fits with the NSA’s general mission — and quantum computing could one day pose a real threat to present-day encryption methods — it’s a lot more theoretical than the agency’s ability to, say, seed malware to computers from miles away.

You can read the original article here.
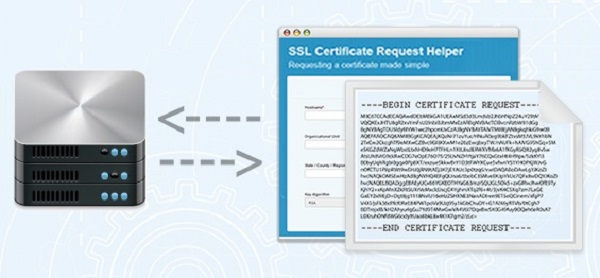
What’s a CSR?
If you have ordered an SSL Certificate before, you were most likely asked to provide a CSR. The CSR is used to deliver the public key that your server will use to identify itself. Generating a CSR can be a hurdle for non-technical staff that aren’t always familiar with the command lines that need to be created and today still remains a time-consuming process even for more experienced users.
CSR Creation Made Easy
Our new CSR creation tool makes it easy to generate the CSR for your server by simply inputting your certificate information (e.g. domain name, organization details, etc.) in the fields provided. The tool will automatically generate the command lines required to create the CSR on your webserver, so you don’t need to write them yourself.

The CSR tool provides command lines for most popular webservers, including OpenSSL, Exchange 2007, IIS and F5 Big-IP.

Bonus Features: Advice on Best Practices
To ensure your SSL Certificates are compliant with the latest security best practices, the CSR tool automatically defaults to the most secure algorithm (RSA) and only offers key length options in line with the latest CA/B Forum guidelines (2048 bit minimum).
Use The Tool
The CSR tool is available in multiple languages at https://csrhelp.globalsign.com and includes support information and FAQs for additional help with the CSR generation process. Secure you website today with SSL the easy way.
You can read the original article here.
The infected ads were served to visitors of the Yahoo homepage over a four-day period last week. Some of the malware that was served up could turn the infected computers into Bitcoin miners. The malware that Yahoo unknowingly served up attacked flaws in Java on the victim machines. Yahoo says that the malware was served up from December 31 to January 3 on its European sites.
Yahoo is being criticized for not doing anything to help the owners of computers infected with malware served from its site.
The web company has promised to monitor and block any ads being used for serving malware. Estimates are that around 27000 infections resulted every hour the ads containing the malware were served. Some malware installed by the rogue ads also installed ZeuS, which tries to steal banking information.

You can read the original article at SlashGear.
Syrian Eagle told Mashable that Microsoft deserves what it got because it’s hawking data to US snoops and multiple governments. The SEA will publish proof of the allegations, Syrian Eagle said: “Microsoft is monitoring emails accounts and selling the data for the American intelligence and other governments. And we will publish more details and documents that prove it. Microsoft is not our enemy but what they are doing affected the SEA.”
On Saturday, the pro-Assad group took over the @MSFTnews and @XboxSupport Twitter accounts and posted various messages hashtagged “SEA”, according to Mashable. One read: “Don’t use Microsoft emails (Hotmail, outlook), They are monitoring your accounts and selling the data to the governments.” The takeovers appear to have been brief: the messages are no longer live, and a Microsoft spokesperson sent this statement to The Register: “Microsoft is aware of targeted cyberattacks that temporarily affected the Xbox Support and Microsoft News Twitter accounts. The accounts were quickly reset and we can confirm that no customer information was compromised.”

The attackers also Tweeted a screenshot of what appears to be a takeover of The Official Microsoft Blog at blogs.technet.com. Microsoft didn’t put out a statement about the alleged attack, but Mashable says its reporters saw it in action and confirmed that it lasted about an hour. Mashable also posted a screenshot showing multiple “Syrian Army Was Here” messages on the defaced site.

Others reported that the blog was either forcing a redirect to the SEA’s site or displaying the defaced blog. At any rate, the blog is now under the company’s control. Microsoft responded to the SEA charges about monitoring email by sending this statement to Mashable: “We’re actively investigating issues and are focused on protecting our employees and corporate network. Microsoft is sometimes obligated to comply with legal orders from governments around the world and provides customer data only in response to specific, targeted, legal demands”.
You can read the original article here.