News
Distributed denial of service (DDoS) attacks have been around since the early 2000’s, and the technology solutions for mitigating such attacks have evolved dramatically over the past few years. Hackers are more sophisticated, and the attacks are increasing, so the old solutions— which never worked perfectly—are even less effective in today’s cyber threat landscape.
Therefore, it’s surprising to see occasional articles that still recommend outdated approaches, such as remote black holing (also called null routing) to stop unwanted traffic. Hosting service providers sometimes try to block bad traffic by injecting a null route with the IP address of the original DDoS victim into their routing infrastructure, to block all DDoS traffic to the victim.
The problem with this approach is that it cannot tell the difference between bad traffic and good traffic; so it not only blocks all DDoS traffic, but it also blocks all good traffic, so it actually supports the DDoS attack against the original victim. If the upstream ISP null routes all good traffic-and-DDoS traffic into the ‘black hole’ it effectively takes the victim offline. This method of defense is simply not acceptable. Furthermore, because most DDoS attacks are highly spoofed, trying to null route on the source IP addresses is nearly impossible.
Modern DDoS mitigation technology effectively detects and blocks DDoS attacks at a granular level, even the low-threshold, sub-saturating attacks that escape human detention. Why block all traffic, when you can simply block the bad traffic, in real time? You can deploy an automated DDoS protection appliance at the network perimeter, and have always on, automatic detection and blocking of DDoS attacks so they never enter your network.
You can read the original article, here.
When most people hear about an “insider threat,” they often assume it’s a malicious employee who is either out to prove a point or trying to selfishly make a buck. Yet, as one startup learned last week, the real “insider threat” is often a well-intentioned person who, in the course of simply trying to do his or her job, accidentally causes something to go wrong.
Human error is a prevalent cause of accidents, which means IT and security teams should prepare accordingly to limit the resulting damage. Here are a few steps organizations can take to limit the impact of accidental insider damage:
Control executables. Even the most security-aware users fall victim to spear-phishing attacks. By controlling what’s allowed to execute on your systems, you can block attackers’ malware from taking over devices and unknowingly exploiting legitimate user privileges.
Get rid of unnecessary privileges. In the case of GitLab, the team member who accidentally deleted a production database was, in fact, authorized to do so. Yet, too often that’s not the case. According to one recent survey, 91 percent of insiders have access to systems that they shouldn’t. If you can’t access it, you can’t break it.
Monitor user activity. Something about being watched by an authority figure encourages people to think twice about their actions. By recording all activity as users access sensitive IT systems, you can encourage your most privileged users to double check their work and discourage any foul play. This means fewer mistakes, fewer malicious actions and less damage to clean up.
Backup. Then backup some more. If IT teams learned one thing in 2016 (or “The Year of Ransomware” if you read the news), it’s that backing up sensitive data is an imperative. Whether an IT admin accidentally deletes an entire database or a cybercrime ring takes your servers hostage, backups are extremely handy. Just ask any of the companies who learned this lesson the hard way.
You can’t predict which users are accidentally going to damage your systems or fall victim to well- disguised attackers, but you can predict that these things will happen – and more than once. However, with some preparation, you can make sure that when these incidents occur the repercussions are minimal.
You can read the original article, here.
After posting an unprecedented and unbroken streak of perfect test scores in AV-TEST’s comparative test of Android security apps, Sophos Mobile Security added the AV-TEST Best Android Security Award 2016 to the AV-TEST Best Protection Award 2015 from last year.
For 14 consecutive tests, spanning all the way back to September 2014, Sophos Mobile Security has achieved a perfect 100% av-test-best-android-security-award-2016-sophosprotection score in AV-TEST’s comprehensive comparison of the top Android security and antivirus apps. To put this into perspective: Sophos Mobile Security has detected and blocked every single piece of malware that AV-TEST has attempted to throw at it, for more than two years.
In addition to getting a perfect protection score, the app also impressed AV-TEST with its features and usability: “The Android protection from Sophos offers superb malware detection, combined with well-devised security features,” said Andreas Marx, CEO of AV-TEST GmbH.
“Top scores, not only in the test category of protection, but also in terms of usability and a good selection of useful security functions, are among the impressive features offered by Sophos,” commented AV-TEST. The award validates SophosLabs’ efforts to increase testing accuracy this past year. Accuracy was already sharp, but the lab thought it could do better, said Onur Komili, third-party testing manager for infrastructure at Sophos.
“After falling just short of winning the top award in 2015 we knew we could do better, which is exactly what we did,” he said. “It’s been over two years since we last registered a false negative in the AV-Test Android Protection tests and we’re the only vendor who can make that claim. Through a lot of hard work and dedication across all of the team in SophosLabs we managed to close the gap and earned the Best Android Security Award in 2016. We’re very proud to have won this award for the first time and hope to earn many more in the years to come”.
Visit the AV-TEST website to read more about the award and check out the most recent test results. Learn more about the best mobile security product in 2016 and download Sophos Mobile Security for free here.

You can read the original article, here.
We’re excited to share that Sophos has been named a leader in the 2017 Gartner Magic Quadrant for Endpoint Protection Platforms.
We believe our leader placement confirms the quality of Sophos endpoint products and recognizes our ongoing technology innovation, exemplified by Sophos Intercept X.
Intercept X delivers powerful anti-exploit and anti-ransomware capabilities, together with advanced clean-up and root cause analysis tools.
It works both with Sophos Central-managed endpoint protection and also antivirus solutions from other vendors, enhancing protection against advanced, zero-day attacks.
Download the report today to learn more and see why Sophos is positioned as a leader.
Not long ago, and after being recognized by Gartner as a leader in seven consecutive Magic Quadrants for Mobile Data Protection, continued the success by being one of the vendors with the most comprehensive solution in the Gartner report, Market Guide for Information-Centric Endpoint and Mobile Protection.
You can read the original article, here.
Our mission at Sophos is to provide the best security solutions on the market and to make them easier to understand, deploy and manage than any of our competitors’ offerings.
From our continuous assessment of the threat landscape, two things are abundantly clear: first, that email is one of the most problematic sources of infection; and second, it’s the ordinary, well-meaning people who often let poisonous emails into their organizations.
It’s easy to be tricked into clicking on a malicious email. So wouldn’t it be great to create a culture where the first instinct of each user was to think twice — even if just for a moment — before clicking on links, downloading attachments or running software that arrived via email? Think of how many threats could be neutralized before they even have a chance to make their way on to corporate networks.
So we’re excited to be able to help create that culture by announcing Sophos Phish Threat, a phishing attack simulator that’s powerful, thoughtful and very easy to use. You’ll be up and running in minutes, with campaigns to help your users learn to spot phishing links, dangerous attachments, and bogus scripts meant to cripple your organization before they have a chance to do harm.
Simply choose a campaign type, select one or more training modules, pick a simulated phishing message, and decide which users to test. Then sit back as the results roll in: top-notch reporting tells you how many messages have been sent out, who’s clicked, and, of those, who’s gone through the required modules. It couldn’t be easier.
Sophos Phish Threat is the outcome of our worldwide hunt for the right technology to offer. That hunt led us to Silent Break Security and its Phish Threat application.
The simulator was developed by Brady Bloxham, the founder of the company, whose pedigree as a former National Security Agency analyst helped convince us that it’s a perfect fit alongside our other best-of-breed solutions in the Sophos Central Admin management console. Brady’s product and team are the perfect addition to the Sophos family and we’re delighted to have them join us.
Sophos Phish Threat is available today in North America and will be available soon in other regions. Give it a try for free and let us know what you think!
You can read the original article, here.
In recent weeks, the UK retail bank Lloyds was hit with a denial of service attack, which reportedly lasted for two days and attempted to block access to 20 million accounts. The attack was part of a broader DDoS campaign against an unspecified number of UK banks that only affected services at Lloyds, Halifax and Bank of Scotland. Availability of services was affected but no customers suffered any financial loss. The attack has attracted significant media attention, being such a high-profile attack with far-reaching potential consequences.
Motive Behind DDoS Attacks on UK Banks
It has also now emerged that the attack was launched as part of a DDoS extortion strategy, which involved a hacker demanding around £75,000 ransom from the bank. An anonymous hacker reportedly told Motherboard that they contacted Lloyds on 11 January by email, informing the bank about security vulnerabilities, and demanded that they pay a ‘consultation fee’ in bitcoins to avoid being attacked. This element of the attack highlights important concerns regarding the evolution of ransom-related DDoS attacks and the threat they pose to businesses.
Increase in DDoS Attacks for Ransom
For some time now, attackers have been using DDoS attacks as part of a wider campaign of cyber threats and techniques, and the trend of ransom-related DDoS has been growing. In a 2016 study, we found that 80 percent of European IT security professionals expect their business to be threatened with a DDoS ransom attack during the next 12 months.
DDoS extortion campaigns are a common tool in the cyber-threat arsenal, and one of the easiest ways for an attacker to turn a quick profit. When service availability is threatened, the victim company needs to consider the potential loss in downtime, revenues and brand damage. When faced with these costly implications, you can understand why some organizations choose to pay the ransom in hopes of circumventing the attack. But in most cases, this is futile: the promise of withholding attacks after the payout is empty.
Corero’s research, which polled over 100 security professionals at the Infosecurity Europe conference in London, highlights the growing threat of cyber extortion attempts targeting businesses in the United Kingdom and continental Europe. In May 2016, the City of London Police warned of a new wave of ransom driven DDoS attacks orchestrated by Lizard Squad, in which UK businesses were told that they would be targeted by a DDoS attack if they refused to pay five bitcoins, equivalent to just over £1,500. Corero’s Security Operations Center also recorded a sharp increase in hackers targeting their customers with such demands at the end of 2015.
Even more concerning was the finding in the study that almost half of these IT security professionals (43%) thought that it was possible that their organization might pay such a ransom demand.
Effective DDoS Defense Methods
The only way for an organization to defend themselves against the DDoS threat, whether ransom-related or other, is to have an always-on, automated DDoS mitigation solution that detects and mitigates DDoS attack attempts instantaneously, even the low-threshold, short duration attacks—and stops them in their tracks. These low-level, sub-saturating DDoS attacks are often used as a precursor to ransom demands, because they are typically not detected by security teams and allow hackers to find pathways and test for vulnerabilities within a network which can later be exploited through other techniques. For this reason, full visibility across all potential network incursions is an essential part of any defense solution, as is the capability to respond in real-time in the event of an attack.
You can read the original article, here.
The Internet of Things (IoT) has been in the news lately for facilitating numerous DDoS exploits across the planet. A global non-profit think tank called the Online Trust Alliance (OTA) has published a paper entitled IoT, a vision for the future. It outlines how the IoT can grow and thrive, especially given that “users’ confidence that their data is secure and private is at an all-time low.” The paper lays out some of the unique challenges posed by securing the IoT and how the network of things can become more sustainable and protect users’ privacy.It is based on an OTA framework of interlocking trust relationships that was released earlier this year.
Securing the IoT is more complex than securing ordinary endpoints. The IoT has a collection of smart devices, such as webcams and Internet-connected printers, which run internal apps (such as web and FTP servers) and cloud services, all of which have their own vulnerabilities.
As the OTA report says, “Every facet and data layer is a potential risk and each data flow must be secured.” Second, building in security for IoT is not usually first and foremost in the minds of every app developer. This is what happened with the Chinese webcam vendor that was part of the botnet exploit mentioned at the beginning of this post. These vendors are usually more interested in having an app that could easily manage the numerous cameras around the world. Not to pick on this vendor, but this is the typical scenario. Most IoT devices are designed without security or privacy needs up front.
Finally, many IoT devices aren’t easily updated when it comes to operating systems or firmware or both. Some of these devices have been in use for more than a decade without any updates. Witness how many IoT devices make use of outdated Windows XP embedded OS, or run on XP hosts. As the OTA report states, “Unfortunately, while such solutions may ship secure, no degree of patching can address design limitations against unforeseen threats decades later.” OTA convened a cross industry working group with the vision to create an IoT Trust Framework, a voluntary self-regulatory model. (You need to be an OTA member in order to download the framework.) They worked with over 100 stakeholders and focused on 31 criteria covering the connected home, office and wearable technologies.
The framework looks at device security, using privacy by design principles, including transparency and device controls, adding lifecycle support and having data portability and transferability. The framework also includes such things as readily available and clearly stated privacy policies, disclosure by the device makers about personally identifiable data collected by each device, descriptions of what data is shared by the device and with whom, and the term and duration of data retention policies.
There are other matters such as forcing default passwords to be changed on first use and using SSL and HTTPS protocols by default. All of these are worthy practices for non-IoT devices too. The OTA framework is a good start at trying to stem the tide of potential IoT security weaknesses. Hopefully it will catch on and prevent future botnet-like exploits from happening.
You can read the original article, here.
According to official data, in 2016 alone, hackers have taken over $1 Billion in the form of ransoms from users trying to retrieve their files after being infected with ransomware.
Ransomware is the most successful malware attack today. It works by locking up your files and crippling your systems until you’ve handed over money. And, one of the biggest problems in the fight against ransomware is the constantly reinvented attacks.
Cybercriminals are finding new methods of spreading the malware, evading detection and even developing ransomware that deletes itself as soon as files are encrypted so that even IT security teams are unable to uncover what variant is on the system.
Ransomware has the potential to cause massive disruption to an organization’s productivity. So it’s vital to understand how to build the best possible defense against it.
The producers of ransomware aren’t just idly waiting for their bit of malware to hit its target. They work in professional teams, constantly updating and enhancing new variants of ransomware – and if you’re caught, the consequences can be severe.
So, with ransomware making headlines for all of the wrong reasons, the pressure is on to put together a top of the line defense. Starting from scratch can be very tough and time consuming. Sophos can make it easier for you. What you can do? Head over to the Sophos Anti-Ransomware Hub and grab your free anti-ransomware toolkit.
Put together by security experts, the kit gives you great resources to help you better understand the ransomware threat, choose the best possible protection for your organization, and get your users up to speed on best security practices.
It includes:
- Anti-ransomware IT security checklist
- Whitepaper on how to stay protected against ransomware
- Posters for your workplace
- On-demand webinar and PowerPoint deck to help educate your users
You will find more information here.
Small- and medium-sized businesses (SMBs) are the backbone of the U.S. economy. According to data available in the U.S. Small Business Administration’s Small Business Profile for 2016, SMBs with fewer than 500 employees make up 99.7 percent of all U.S. companies and employ 56.8 million workers—48 percent of the U.S. workforce.
Cyber security is as important for these companies as it is for large multinationals. SMBs also have sensitive information from employees and customers, proprietary information about products, and they often are part of a global supply chain for other companies. Every business is a target, regardless of size, and none can afford to ignore the security of its IT infrastructure.
The SMB: lots of assets, limited resources
SMBs may assume they have little to interest hackers and therefore put cyber security on the back burner. We know this isn’t true. Hospitals, for example, hold sensitive health information and have networked medical devices at risk. Unfortunately, some learned the hard way with episodes of ransomware disrupting business and damaging reputations.
It is not just a company’s own information and systems that are at risk. SMBs have been the channel in high-profile breaches that compromised millions of records. The 2015 breach of a retail company in which data from 40 million customer credit card accounts were stolen and the U.S. Office of Personnel Management breach that exposed more than 20 million employee records are believed to have originated with credentials from third-party vendors. Attackers use a weak link in the supply chain to breach a larger target; they use the compromised credentials to escalate IT privileges and use privileged accounts to compromise critical systems.
Businesses today run on IT. This makes cyber security a business necessity as well as a technology requirement. A strong security program can not only protect a business’s assets, it can also give it a competitive advantage.
Although SMBs face the same cyber security challenges as large businesses, they often have fewer resources and little in-house expertise to address these challenges. This makes it important that they get the best return on their security investments by prioritizing the right things in their security programs.
The need to know
Cloud computing and hosted services can make advanced technology affordable, and SMBs often find it cost-effective to outsource many IT functions, including security. But at the end of the day, each business is still responsible for its own security. Owners and executives need to understand the basics of cyber security, know what their service providers are doing and what questions to ask of them.
Security needs will vary depending on circumstances. Each company must understand its attack surface—vulnerable areas in the IT environment that could breached to compromise systems—and the impact of each potential breach. By assessing the impact, vulnerabilities can be prioritized, so that the cyber security program focuses on the areas needed to manage risks.
The key to protecting an IT infrastructure is privileged accounts. These accounts, if compromised, can effectively turn an intruder into an insider, giving the attacker rights to move throughout the network, escalate privileges, change settings and configurations and access data. When allocating scarce cyber security resources, privileged accounts must be identified, assessed and prioritized.
A single standard for security
An SMB IT infrastructure may not be as complex as a global enterprise, but the benefits of a layered approach to cyber security applies to all. Additionally, there are documented best practices and basic cyber hygiene practices that should be followed.
Learn more about how CyberArk can help your organization protect privileged accounts.
You can read the original article, here.
SE Labs has just released its Q4 2016 testing results, and we’re pleased to report that Sophos Endpoint Protection scored high.
The results are a testament to Sophos Lab’s diligence in protecting customers against real-time malware threats that are constantly evolving.
The charts below, taken from the report, show how Sophos fared in the various SMB and Enterprise categories.
SMB category:

Enterprise category:

You can read the original article, here.
Sophos Home is a ‘lean, mean, virus-killing machine’ – that’s the verdict of Which?, and who are we to argue?
Which?, the highly regarded UK product testing magazine, placed Sophos Home in the #1 spot, ahead of Panda, Avast, and AVG. The publication gave Sophos Home 5 stars for performance, 5 stars for phishing, and 4 stars for ease-of-use. Which? had this to say about Sophos Home:
“Sophos Home is a lean, mean, virus-killing machine. For fuss-free peace of mind that doesn’t cost a thing, then definitely download it”.
“Sophos keeps things very simple. It’s a no-frills package that doesn’t cluster its interface with lots of details or complex options. Installation and setup is very easy. The software uses nice, clear messaging if it spots something suspicious”.
“The full function is very thorough. It found and destroyed pretty much every single virus we planted on our test PC…And if you’re concerned about getting taken in by online phishing scams, Sophos’s protection will give you peace of mind. Scam websites are flagged the moment you land on them”.
See how we compare to the other programs that were tested (paywall; account required). And, don’t forget, ensure your Windows PC is protected against the threats — download Sophos Home for FREE today!

You can read the original article, here.
Mac malware is on the rise. While Apple does provide system protection for MacOS Sierra, dangerous infections that can wreak havoc are consistently being developed and deployed by cybercriminals.
That’s why we created Sophos Home to protect every Mac in your home with business-grade security. To show you just what Sophos Home is made of independent testing lab AV-Test put it to the test, along with 11 other MacOS security tools.
Our free commercial-grade home security was able to detect 100 percent of the Mac malware the testing lab threw at it, placing us at the top of the pack! Plus, it fully removed all the malware samples.
Read the full report to find out how we did in all areas of the testing. And, most importantly, ensure your Mac stays ahead of the threats – download Sophos Home for FREE today!
You can read the original article, here.
We are excited to announce that we are introducing a new way of experiencing LogPoint! LogPoint Free is a completely free version of LogPoint, which lets you ingest up to 350 events per second (eps), from up to 10 nodes.
LogPoint Free provides full LogPoint functionality, access to support, Help Center and Community.
Free Extension
The LogPoint Free license runs for 90 days but can be extended for free upon request. You can also easily upgrade to a LogPoint license if needed.
Is LogPoint Free for you?
LogPoint Free is designed for you to get full access to the functionality of our proven LogPoint technology and the entire LogPoint and ecosystem. Whether you are testing the solution for your business, or simply have personal, ad hoc needs for search, analytics and visualization of data – LogPoint Free is for you.
What is included in LogPoint Free?
We like to keep things simple and transparent: Full functionality!
Some highlights of what’s included:
- Easily upgrade the license and keep all configured intelligence if you decide to upgrade
- Your favorite analytics tools: Search, Alerting, Reporting, Dashboards
- Unlimited number of users
- Access to the knowledgebase and selected applications
- Full access to our awesome community
What happens if…
350 eps refer to the amount of data you can add per second. If you go above the 350 eps, the events exceeding the limit will simply be dropped without any penalty to functionality. There is no limit on storage, which is only constrained by the supporting hardware. If you need more than 350 eps or 10 nodes, easily upgrade to a LogPoint license suited to your needs. Support is included with LogPoint Free, but please note that response time is “best effort.”
You can download LogPoint Free completely for free HERE – get running in less than 5 minutes!
You can read the original article, here.
Information security professionals recognize that cyber attackers will exploit endpoint vulnerabilities and then make a beeline for privileged credentials. As a result, organizations are evaluating how they can take steps to secure privilege on the endpoint as a fundamental part of their security program.
CyberArk Viewfinity has enabled organizations to reduce both the attack surface and the risk of information stolen or encrypted and held for ransom—all while achieving the right balance between productivity and security. To keep pace with the ever-evolving threat landscape, we unveiled new threat protection features this week: CyberArk Viewfinity is now available as CyberArk Endpoint Privilege Manager.
By interlocking three core capabilities: privilege management, application control and new credential theft detection and blocking, CyberArk Endpoint Privilege Manager represents a combination of powerful technology, deep research and best practices to stop attackers from advancing beyond the endpoint and doing damage.
Key enhancements include:
- The ability to detect and block credential theft attempts by malicious users and applications, including Windows credentials, remote access application credentials and those credentials stored by popular web browsers for use with, for example, corporate network and cloud applications.
- New behavioral analytics to block and contain advanced threats targeting credential theft at the endpoint.
- The ability to block hash harvesting at the endpoint to prevent Pass-the-Hash, an attack leveraging stolen credentials.
The introduction of CyberArk Endpoint Privilege Manager comes on the heels of an FBI flash alert that recommends prioritizing credential protection, including implementing least privilege and restricting local accounts, to limit a threat actor’s ability to gain highly privileged account access and move throughout a network.
CyberArk Endpoint Privilege Manager is available now. For additional resources on detecting and containing cyber attacks while effectively balancing security and productivity, visit this page.
You can read the original article, here.
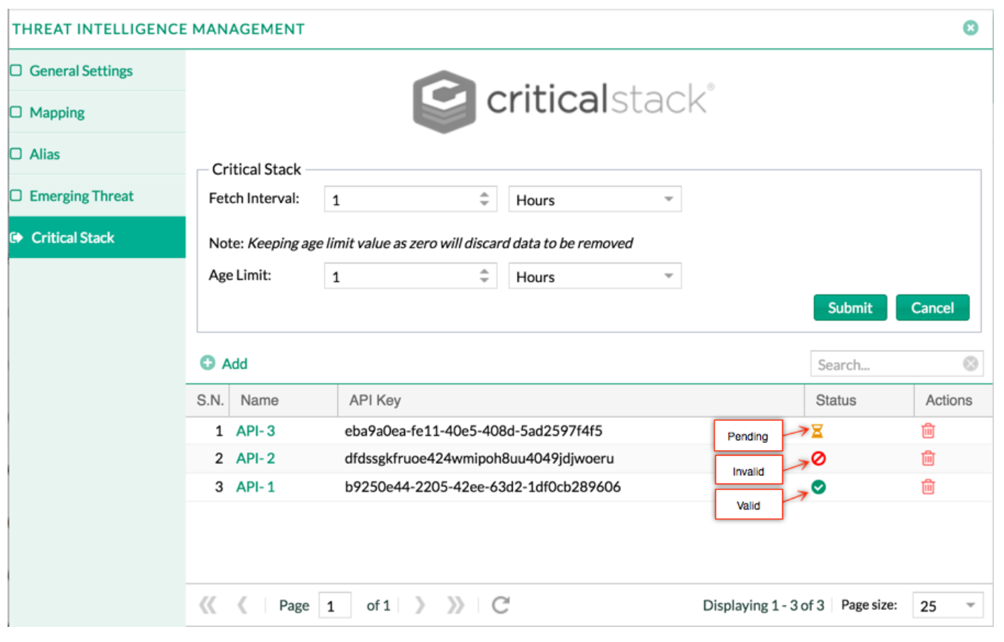
It is with pride and great pleasure that we have the opportunity today to launch our Threat Intelligence application!
With this application, we provide a simple and efficient module for providing contextual attack information to observations from sensor data in your network.
Context
The Threat Intelligence application sources data from best-in-class ProofPoint and the large collection of indicators from Critical Stack. With these sources ingested, LogPoint can analyse structured and unstructed data, alerting if any match between the known-bad indicators and collected enterprise data is identified.
The LogPoint taxonomy and technology stack allows for inspecting any type of collected data, regardless if it comes from your ERP platform, online collaboration platform, hosted Office365 or firewall/antivirus platform. If the data is in LogPoint – it can be correlated with the indicators of compromise.
Reduce Time to Detection
Enterprise log-data is valuable when analysed in and of itself. By correlating your internal data with indicators of compromise, seemingly innocent data can hint at a potential issue. With pre-canned analytics in the form of alert-rules, dashboards and data mappings running out of the box, the Threat Intelligence application is a turn-key application.
Want to Know More?
You can read more about how to get started and set up Threat Intelligence in this blog post.
We also suggest you sign up for our webinar on Threat Intelligence! It takes place December 1st, 2016. Read more about it here.
You can read the original article, here.
If you read the Sophos Blog, you will undoubtedly be aware of how our next-gen endpoint solution can protect you and your business. Sophos is really proud of Intercept X and genuinely believes it’s the best product of its kind out there.
However, we realise that you may want to hear independent opinions as well, which is why we’re pleased to share ESGs Lab’s report with you.
When carrying out the testing, Enterprise Strategy Group (ESG) observed Sophos Intercept X’s performance as well as its agility, usability and reliability in detecting and preventing genuine advanced threats and signatureless exploits.
The tests involved:
- Emailing a Word document containing real ransomware code from, what appeared to be, that user’s manager
- Launching a stack pivoting attack that employed an exploit in a PDF file
- Downloading a free report file from the Web, which also downloaded a second file that attempted to zip up the contents of ‘My Documents’ and upload them to a command and control site

And the verdict?
Sophos Intercept X has made excellent progress closing many of the endpoint security gaps that still exist for organizations worldwide.
But, don’t just take their word for it. Try Sophos Intercept X for free!
You can read the original article, here.
In 2016 alone, hackers have taken over $1 Billion in the form of ransoms from users trying to retrieve their files after being infected with ransomware.
Ransomware is the most successful malware attack today. It works by locking up your files and crippling your systems until you’ve handed over money.
And, one of the biggest problems in the fight against ransomware is the constantly reinvented attacks.
Cybercriminals are finding new methods of spreading the malware, evading detection and even developing ransomware that deletes itself as soon as files are encrypted so that even IT security teams are unable to uncover what variant is on the system.
This video digs deeper into the inner workings of ransomware, techniques employed by crooks to evade traditional technologies and how it malware can be stopped:
You can read the original article, here.
With Version 4.4.3, SEP sesam can now be considered one of the leading data backup solutions for VMware environments. With SEP sesam, the data of organizations and enterprises is protected 24/7 and always available. The new SEP sesam version 4.4.3 is one of the leading data protection solutions for VMware environments.
The new release supports:
1. The start of VMs directly from backup storage
2. VMs can be used immediately because no time is lost performing restores. VMware vMotion automatically moves productive VMs from backup storage to productive VMware storage during operations.
3. Backed-up VMDKs can be attached to productive VMs with Linux, Windows and Open Enterprise Server operating systems regardless of the platform.
4. Single file restore from CBT Full, Inc, and Diff backups
5. Instant recovery from CBT Full, Inc, and Diff backups
6. Single file restores and instant recoveries from deduplicated Si3 backups are also possible
7. SATA disks in addition to SCSI disks during backup and restore via the transport mode Hot-Add.
8. Full functionality is ensured for Linux backup servers and remote device servers.
9. We are looking forward to your participation.
SEP sesam supports a wide range of databases having some very important benefits:

The inaugural 2016 Security Excellence Awards by UK magazine Computing saw Sophos collect two industry prizes last night: SafeGuard 8 took the Data Encryption Award and Sophos XG Firewall won the Firewall Solution and UTM Award.
The ceremony was held in London in the shadow of the Shard, where the Sophos representatives enjoyed the somewhat surprising, albeit entertaining, performance of the skinny public-schoolboy-looking freestyle-rapping presenter, Chris Turner.
Out of the hundreds of companies shortlisted for the 21 awards, Sophos was one of very few companies to collect more than one prize on the night.
Sophos SafeGuard 8, its revolutionary next-gen Synchronized Encryption technology, was up against strong competition from companies including Covata, Vormetric and Cloudview. Sophos XG Firewall, with its ultimate firewall performance, security and control, faced heavy rivals including Barracuda and Panda.
Thanks to the solid efforts of the SafeGuard and XG Firewall product teams, once the dust settled and the freestyle rap had died down, there was only one winner in two of the top categories: Sophos.
All in all, we’re very pleased with our results in this first ever year of the Computing Security Excellence Awards, and we are looking forward to collecting many more prizes in years to come.

You can read the original article, here.
After being recognized by Gartner as a leader in seven consecutive Magic Quadrants for Mobile Data Protection, we continue our success by being one of the vendors with the most comprehensive solution in the new Gartner report, Market Guide for Information-Centric Endpoint and Mobile Protection.
This new report by John Girard of Gartner is the replacement for the now retired Gartner Magic Quadrant for Mobile Data Protection. It defines nine different methods for information-centric endpoint protection, ranging from basic device protection to comprehensive file-based protection methods.
Of the 18 representative companies discussed in the report, Sophos is one of only two companies that can provide a solution for every single method with Sophos SafeGuard and Sophos Mobile Control.
Sophos SafeGuard, with its always-on file-based Synchronized Encryption, will protect your files wherever they go, for example when shared across platforms, emailed, or uploaded to cloud-based storage. The secure container technology and personal information management (PIM) capabilities in Sophos Mobile Control provide secure collaboration everywhere, working across mobile devices without compromising security and preventing accidental data leakage.
We agree with Gartner that, considering that information is highly mobile in today’s world, data protection solutions can no longer be centered around full disk encryption but should instead account for the many ways that business information needs protection as it moves.
To find out what Gartner says about the Information-Centric Endpoint and Mobile Protection marketplace, download the complete Market Guide here.
You can read the original article, here.