News
The team is hard at work putting the finishing touches on our next major release of XG Firewall, and it is a huge release! XG Firewall v17.5 brings some amazing new Synchronized Security features as well as many of your most-requested features.
The best part is you can start taking advantage of many of these new capabilities today, as part of the Early Access Program.
What’s new in XG Firewall v17.5
Here’s a quick overview of the key new features in v17.5:
- Synchronized Security – lateral movement protection – extends our Security Heartbeat™ automated threat isolation to prevent any threat from moving laterally or spreading across the network, even on the same subnet. The firewall instructs all healthy endpoints to completely isolate any unhealthy endpoints.
- Synchronized User ID – utilizes Security Heartbeat™ to greatly streamline authentication for user-based policy enforcement and reporting in any Active Domain network by eliminating the need for any kind of server or client agent.
- Education features – such as per-user policy-based control over SafeSearch and YouTube restrictions, teacher enabled block-page overrides, and Chromebook authentication support.
- Email features – adds Sender Policy Framework (SPF) anti-spoofing protection and a new MTA based on Exim, which closes a couple of top requested feature differences with SG Firewall.
- IPS protection – is enhanced with greatly expanded categories enabling you to better optimize your performance and protection.
- Management enhancements – including enhanced firewall rule grouping with automatic group assignment, and a custom column selection for the log viewer.
- VPN and SD-WAN failover and failback – including new IPSec failover and failback controls and SD-WAN link failback options.
- Client authentication – gets a major update with a variety of new enhancements such as per-machine deployment, a logout option, support for wake from sleep, and MAC address sharing.
- Sophos Connect – is our new IPSec VPN Client, free for all XG Firewall customers, that makes remote VPN connections easy for users, and supports Synchronized Security.
In addition, coming in a following maintenance release we have:
- Wireless APX access point support – provides support for the new Wave 2 access points providing faster connectivity and added scalability.
- Airgap support – for deployments where XG Firewall can’t get updates automatically via an internet connection (due to an “airgap” or physical isolation) – XG Firewall can now be updated via USB.
Sophos Central management of XG Firewall
With v17.5, XG Firewall is also joining Sophos Central. The Early Access Program for Sophos Central Management of XG Firewall is expected to start soon.
You will be able to manage XG Firewall from within Sophos Central along with all your other Sophos Central products. And there’s a few great new features coming along with Sophos Central Management of XG Firewall:
- Secure access and management with single-sign-on through Sophos Central from anywhere.
- Backup management and storage for your regularly scheduled firewall backups.
- Firmware update management to make multiple firewall updates easy.
- Light-touch deployment to enable easy remote setup of a new firewall.
Get early access now!
Head on over to the XG Firewall Community Forums to get the v17.5 EAP firmware update, additional information on what’s new, and to share your feedback with the Sophos Product Team and the rest of the community.
You can read the original article, here.
Who’s responsible for cybersecurity at work? Is it the security team, the employees or a mix of both?
And, perhaps most importantly of all, does everyone in your organization agree?
A recent study commissioned by Sophos revealed that six out of ten employees feel more relaxed about IT security at work than at home, with 45% of people admitting that they don’t feel responsible for IT security at work.
Company security policies are designed to create a safe workplace for all employees. Those policies are often developed by a security team with years of experience, but policies only work if they’re adhered to. No matter how good your security team is, it’s relying on everyone else to make it their responsibility to maintain a safe workplace by following its policies. Helping employees to learn and understand those policies is vitally important.
The workplace isn’t a homogeneous whole though, it’s a collection of individuals with different personalities and learning styles. If everyone receives the same training content, don’t be surprised if the message doesn’t sink in everywhere.
New award-winning security training
Sophos Phish Threat is here to make security awareness training stick.
Phish Threat covers a wide range of topics from general or role-based security awareness to regulatory compliance, in a variety of engaging formats. It makes use of videos, interactive modules and gamification in a mix of visual styles to ensure that everyone gets the message.
Today, we’re excited to announce that our range of training has grown. Thanks to our latest Phish Threat learning partnership with Ninjio, we’ve added over 30 new training modules, plus we’re growing Phish Threat by one new module every month!
Ninjio shares our approach of short, engaging training, and its unique style recently scooped it the Gartner Customer Choice award for Computer Based Training 2018. By dramatizing real-life cyber threat headlines, with Hollywood script writers and great animations, Ninjio brings stories to life.
The freshest content
With all that training at your fingertips, your employees should be cybersecurity ninjas in no time. But to truly test their new-found skills, Phish Threat also provides more than 500 customizable attack email templates in nine languages. And new templates are being added every week, so to help we’ve made it easier to find the latest content fast.
Featured templates
The latest phishing attacks and seasonal campaigns train users to identify real-world attacks hitting their inboxes today, as well as the seasonal campaigns they need to know about.

New templates
New templates are automatically applied to every Phish Threat account. The New flag allows you to quickly find the most recently added templates, to help keep things interesting for your employees.

Five stars from customers
Our latest independent customer reviews show how easy it is to get started, and the almost immediate impact that Phish Threat is having on reducing risk.
“The cloud offering was extremely easy to deploy. The training exercises and videos were extremely relevant, engaging and just the right length”.
You can start educating your employees today with our free anti-phishing toolkit.
Sophos has already been recognized by Gartner as a leader in seven consecutive Magic Quadrants for Mobile Data protection (2009-2015). And now we’re proud to announce that we’ve been named one of the vendors with the most comprehensive solutions in Gartner’s 2018 Market Guide for Information-Centric Endpoint and Mobile Protection for the third year in a row.
This guide replaces the now-retired Gartner Magic Quadrant for Mobile Data Protection. We believe the new guide is intended to help better secure information at rest in a world that has become infinitely mobile – a powerful challenge for today’s cybersecurity professionals.
Gartner details eight protection methods to meet these challenges. According to Gartner, “companies are suffering from gaps in their information-centric protection, and vendors are beginning to fill those gaps, in order to stay competitive, by adopting more of the eight protection methods described.”
Sophos provides a solution in all eight methods of information-centric endpoint protection, with powerful orchestration across multiple layers of security with Synchronized Security.
You can read more about these eight methods in the latest market guide.
The testing of cybersecurity products is a contentious subject, with vendors and test organizations striving to deliver an objective evaluation despite very different ideas of what that looks like. The threat landscape is constantly evolving, and this makes evaluating a single product’s effectiveness at a single point in time problematic. Yet however imperfect and difficult it might be, Sophos is committed to improving every customer’s ability to make informed decisions about security solutions.
For a long time, we have encouraged organizations to seek independent validation of vendor-claimed product effectiveness, ideally from multiple sources. That’s why you’ll find detection performance, analyst reviews, and test results from independent vendors such as NSS Labs, SE Labs, MRG Effitas, and AV-Test on our website and in our marketing materials. Sophos proactively engages in public and commissioned tests and uses the results to improve product effectiveness.
Testing security products isn’t easy. There are few objective resources that can help to establish the connections between how attacks are performed in the real world and the capabilities of security products to prevent or detect them. Designing and executing a statistically relevant and objectively valuable test is extraordinarily difficult. There are many tools, frameworks, and sample sources available, but they require intensive curation, orchestration, and auditing to be used effectively in measurement. These challenges often lead to tests that measure security effectiveness across only a single threat vector, such as static file detections in isolation without consideration for methods of delivery. As a result, published independent tests are not holistic and disproportionately focus on a single dimension, such as file-based portable execution detection.
In 2008, Sophos became a founding member of AMTSO, as we believe that the way to improve testing experiences is to get all stakeholders — vendors, independent test organizations, customers, and analysts — to adopt working practices and test standards that better serve all our customers. In addition to our work with AMTSO, we are committing to uphold certain best practice principles whenever we engage in product testing.
Testing of security products should be fair, rigorous, transparent, and collaborative. Read the Sophos Third-Party Testing Principles here: www.sophos.com/bestpracticetesting
We understand the value of independent evaluations, yet sometimes tests do not provide a clear methodology or enable vendors to comment on results before they are published, which is disadvantageous for customers. With a commitment to transparency and a focus on the customer need, we can find the right path forward.
Sophos believes that customers and the industry will benefit if all security vendors and testing organizations:
- Embrace and contribute to the ongoing review and improvement of such projects as the AMTSO Testing Protocol Standard and MITRE’s ATT&CK Framework;
- Remove arbitrary or excessive restrictions on the use of security products for the purposes of comparative testing and publication of factual results;
- Actively participate in high quality independent tests, especially those that are aligned with the Sophos principles and AMTSO standards;
- Advocate for fair, rigorous, transparent, and collaborative testing that provides the answers prospective customers need to make better informed decisions about security products.
We are proud of the quality and effectiveness of our products – and you can put them to the test. We’ll be sharing more about how we intend to further improve everyone’s ability to test our security products shortly, so watch this space!
You can read the original article, here.
Netwrix conducted a study of the major IT risks that are significant for most organizations and assessed respondents’ readiness to withstand cyber threats.
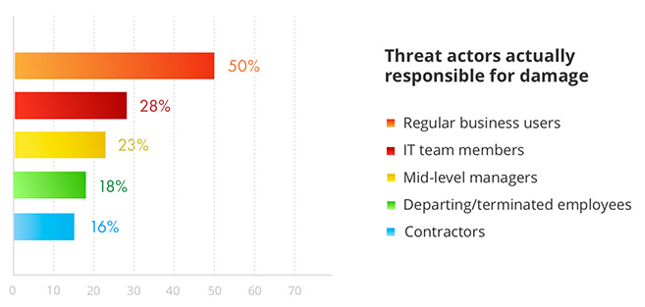
The report is based on the feedback of 1,558 organizations of various sizes from many different regions and industries. It summarizes the experiences and plans the organizations have in regard to addressing six IT risks: physical damage, intellectual property theft, data loss, data breach, system disruption and compliance penalties.
The report reveals the following key findings:
- Most companies consider hacker attacks to be the most dangerous threat, but in fact, insiders cause the majority of security incidents by either malicious or accidental actions.
- Not all critical security controls are reviewed regularly as required by best practices. The most neglected controls include getting rid of stale and unnecessary data and conducting data classification. These controls are exercised rarely or never by 20% and 14% of organizations, respectively.
- Although 70% of companies have done IT risk assessment at least once, only 33% re-evaluate their IT risks regularly.
- 44% of respondents either do not know or are unsure of what their employees are doing with sensitive data.
- Nonetheless, over 60% of respondents think that their level of visibility is high enough, which lulls them into a false sense of security.
- Only 17% of organizations have an actionable incident response plan; 42% have only a draft or have no plan at all.
“Our report illustrates that the foremost reason why the organizations fail to address major IT risks lies in a lax approach to security basics. They are giving priority to some controls and are leaving the most important ones out of scope. Haphazard approach to security basics and poor visibility into sensitive data gives IT pros a false sense of security. However, paying more attention to all security basics can help organizations manage IT risks with more success,” said Steve Dickson, CEO of Netwrix.

You can read the original article, here.
Defence organisations encompass two very different communication environments. Military messaging takes place within live operational environments, and might involve messages passing between different operations and forces, for example, over closed systems and networks. This type of communication must follow strict security procedures and protocols, and conform to stringent standards, as must the classification of the emails and data being shared both internally and with other nations’ defence organisations.
Alongside this, staff across the organisation are sending messages and creating data as part of the day-to-day ‘business as usual’. This could be anything from emailing a supplier to order more stationery for head office, to a sales representative adding new details to a customer record. Information that falls into this category also needs to be classified, controlled and protected.
Many defence organisations are currently reviewing the messaging tools they use, as they transition from existing X.400 systems to a more modern communications infrastructure, and there’s an increasing appetite for moving to commercial, proven off-the-shelf SMTP-based solutions and adhering to the new NATO standards.
‘Integration’ may be the current buzzword in the IT world, but we believe that the best approach is to deploy two separate but complementary solutions that each address a specific environment, application and user base.
Boldon James’ SAFEmail solution, for instance, is well-suited to military and intelligence applications, and has been used by customers in the defence market for 25 years. It’s a robust and tried and tested tool, but one that’s also at the forefront of messaging technology. In addition to current international standards and protocols, the latest version has been future-proofed to comply with the new data protection and labelling standards being introduced by NATO, which we were involved in a consultation on. SAFEmail is able to support both legacy X.400 and new systems, and can be customised to meet requirements.
An enterprise solution such as Classifier can then be deployed alongside a military messaging tool such as SAFEmail®, as a common platform to be used by the entire organisation for classifying ‘everyday’ emails and data. Classifier is structured for secure environments, and complies with industry standards and protocols, but is suited to non-operational activities with a more flexible labelling functionality that can be aligned to how the organisation works, and is currently deployed in live Top Secret level systems.
Procuring both systems from the same vendor has its advantages. The organisation will be assured the same high level of performance across all communication environments, with every message sent protected to military standards. There are also benefits to dealing with a single company, including smoother deployment, consistent support and lower cost of ownership.
Most important of all is that the vendor has a long history of service in military environments, and a profound understanding of both military and enterprise infrastructures.
You can read the original article, here.
Onboarding new devices to management policy controls includes the important step of user authentication. That’s why we’re excited to be one of the launch partners for Google Cloud’s new secure LDAP feature, launched today at Google Next London.
Sophos Mobile customers now have the option to validate their users’ identities with G Suite and Google Cloud Identity.
For organisations using G Suite or Google Cloud Identity, this will dramatically simplify the enrolment process for new devices. Sophos Mobile will use Google’s new secure LDAP implementation to validate users dynamically, during enrolment.
Google will be rolling out secure LDAP to Cloud Identity and G Suite customers in the coming weeks. Sophos customers running their own Sophos Mobile management server can take advantage of it with the release of Sophos Mobile 8.6 later this month.
If you aren’t already a Sophos Mobile customer and you’re wondering how best to secure and manage your mobile fleet, check out Sophos Mobile.
You can read the original article, here.
We are very excited to announce the launch of Sophos Intercept X Advanced with EDR, a new Intercept X offering that integrates intelligent endpoint detection and response (EDR) with the industry’s top-rated malware and exploit protection.
With Intercept X Advanced with EDR, IT and security teams can now better navigate the challenges of today’s most complex threats, such as:
- Understanding the scope and impact of security incidents
- Detecting attacks that may have gone unnoticed
- Searching for indicators of compromise across the network
- Prioritizing events for further investigation
- Analyzing files to determine if they’re potentially unwanted or true threats
- Confidently reporting on the organization’s security posture at any given moment
- Answering tough compliance questions in the event of a breach
Consider the old “needle in a haystack” figure of speech: Most EDR solutions on the market today attempt to collect as much hay as possible to ensure the needles are eventually found.
It’s a complicated, tedious, and manual process. The Sophos approach is different: thanks to industry-leading deep learning technology and unequivocally strong up-front protection, we exponentially shrink the haystack to make the needles much, much easier to find.
Endpoint Detection and Response (EDR) tools give security teams the ability to detect, investigate, and respond to suspicious activity. The best EDR solutions start with the strongest protection, and no other solution offers stronger protection than Intercept X.
Because Intercept X technology is so effective at stopping breaches before they start, the EDR workload is significantly lighter. This means that IT organizations of all sizes can optimize key resources, enabling them to focus on the business of IT rather than chasing false positives and dealing with overwhelming volumes of alerts.
The intelligent EDR built into the new Intercept X Advanced with EDR replicates the capabilities of highly-skilled analysts, allowing organizations to add expertise without having to add headcount. The product leverages deep learning, SophosLabs threat intelligence, and more to mimic the roles of a malware analyst, security analyst, and threat intelligence analyst all in one, without having to pay human salaries for those key skillsets.
Even for larger organizations with a security operations center (SOC), Intercept X Advanced with EDR provides a valuable first tier of detection, freeing up human analysts to focus on what’s most important. Guided investigation allows security teams of all skill levels to quickly understand their security postures thanks to context-sensitive guidance, which offers suggested next steps, clear visual attack representations, and built-in expertise. When an investigation is concluded, analysts can respond with a click of a button.
To learn more, download the Intercept X Advanced with EDR datasheet.
You can read the original article, here.
Data breaches are up 75% in two years, finds a report from the Information Commissioner (ICO). The study, carried out by Kroll, took into account an array of personal data, including health, financial and employment details.
Access to this data was made possible under the Freedom of Information Act, in addition to some ICO data being publicly available.
Incorrect Recipients
Kroll found that over 2,000 reports received by the ICO within the last year could be attributed to human error, compared to just 292 that were deliberate cyber incidents.
Of the reports that were possibly caused by human error, the most common breach types were identified as emails to incorrect recipients (447), data posted or faxed to incorrect recipients (441), and loss or theft of paperwork (438).
As for purely cyber-related attacks without human involvement, the most frequent type within the last year was unauthorised access (102).
Additionally, the health sector was revealed to be the most common source of data breach reports, yielding a total of 1,214, with general business (362), which yielded the highest increase percentage over the past two years (215%), following behind.
GDPR an Important Factor
Kroll said that the increase in reports indicates a correlating increase in transparency on the part of companies as a result of the EU General Data Protection Regulation (GDPR)’s introduction back in May.
“Reporting data breaches wasn’t mandatory for most organisations before the GDPR came into force,” explained Andrew Beckett, Managing Director and EMEA Leader for Kroll’s Cyber Risk Practice, “so while the data is revealing, it only gives a snapshot into the true picture of breaches suffered by organisations in the UK.
“The recent rise in the number of reports is probably due to organisations’ gearing up for the GDPR as much as an increase in incidents. Now that the regulation is in force, we would expect to see a significant surge in the number of incidents reported as the GDPR imposes a duty on all organisations to report certain types of personal data breach.
“We would also expect to see an increase in the value of penalties issued as the maximum possible fine has risen from £500,000 to €20 million or 4 per cent of annual turnover, whichever is higher. The ultimate impact is that businesses face not only a much greater financial risk around personal data, but also a heightened reputational risk.”

The Importance of Automation
Commenting on the finds from Kroll, Sarah Armstrong-Smith, Head Continuity & Resilience at Fujitsu UK & Ireland, said that companies need to support users, helping them become “the strongest link, not the weakest.”
She said: “This needs to go beyond just providing users with security and privacy training and awareness. There also needs to be mechanisms in place to identify and prevent internal data leakages from occurring.”
Ms Armstrong-Smith went on to explain the role of automation in possibly improving data security.
“Automation is helping organisations to detect and respond to changes and adapt policies to protect people and to enable them to be compliant. Not only this, but automation can help organisations react quicker and respond to a breach should it happen.
“They can do it proactively, report it in a timely and compliant way, and ensure they take control of events, rather than the other way around.
“To be truly effective when it comes to protecting personal data requires a mix of people, processes and technologies: all of which have to be carefully aligned so that everything fits together properly.
“At the end of the day, security alone cannot stop a breach, it requires a cultural shift to embed data governance throughout an organisation.”
You can read the original article, here.
We are thrilled to announced that we’ve won the award for Best Anti-Ransomware Solution and have been highly commended in the Best Security Partner Program category at the first Channelnomics Security Awards.
As Channelnomics explains, these awards have been “designed to recognize the trailblazers in the security industry – those players who are embracing the ever-changing face of the market and making it possible for the channel to forge ahead in this challenging landscape.”
The 30-category awards are completely independent and given based on innovation and achievement in the North American market over the year.
With the emergence of Intercept X, our next-gen, anti-ransomware solution, Sophos has led the way in fighting the rise of ransomware. We remain poised to meet new or evolving challenges that ransomware has in store for the industry, which is why we are proud to receive the Best Anti-Ransomware Solution accolade.

And, our customers and partners can attest to it:
“We have deployed Intercept X to more than 10,000 endpoints. Since deployment, it has stopped upwards of 2,500 endpoint ransomware attacks and we’ve had zero ransomware infections across all protected devices“.
– Emily Vandewater, Lead Security Engineer, Flexible Business Systems
As a channel first company, we are constantly working toward the continued success of our partners. Being recognized as having the Best Security Partner Program (Highly Recommended) is a powerful statement that we continue to find success building an optimal, beneficial relationship with our partners, ensuring not just financial growth but continued cybersecurity and safety for their customers.
Stop by the Channelnomics site for more on the awards ceremony and to view a full list of winners.
You can read the original article, here.
We’re very pleased to announce that for the 7th consecutive year, Gartner has named Sophos a Leader in the Magic Quadrant for Unified Threat Management (SMB Multifunction Firewalls) for 2018. We continue to be one of only three vendors in the Leader’s Quadrant which we firmly believe is a testimony to the strength of our product and strategy in the eyes of customers, partners and industry analysts.
The Magic Quadrant is based on an assessment of a company’s completeness of vision and ability to execute which includes a vendor’s understanding of important industry needs and trends and its ability to address them in an effective way.
Sophos continually leads innovation in solving today’s top problems with network protection. We were the first vendor to meaningfully integrate next-gen endpoint and firewall technology together to Synchronize Security – enabling health status monitoring, instant threat identification, and automatic isolation of infected systems. With every release we continue to push the possibilities of Synchronized Security further – with our most recent releases providing breakthroughs in application visibility. Synchronized Application Control, introduced in v17, elegantly solves an enormous industry-wide problem with signature-based application identification and control. Now, with the introduction of Cloud Application Visibility in XG Firewall v17.1, we now have the most comprehensive application coverage – for both desktop and browser-based applications – available anywhere.
As the only IT security company to be positioned as a Leader across both Unified Threat Management and Endpoint Protection Platforms – we believe we are uniquely positioned to continue to lead on this next generation of Synchronized Security.
Sophos also continues to push the envelope in zero-day threat detection by bringing the latest advanced technology from our next-generation endpoint to the firewall such as exploit detection, CryptoGuard and deep learning. Whether it’s our sandboxing, IPS, SSL inspection or web protection, we’re continually investing in innovative protection technologies to ensure your network is protected from the latest threats and potentially unwanted applications.
Although we’ve been a long-running leader in network protection, we’re just getting started. We’ve got a rich roadmap of innovation ahead that will provide tremendous value and solve more of your daily challenges with your network, further distancing us from the rest of the field. It’s a great time to be a Sophos customer or partner, but it’s never too late to join in on the excitement.
Find out what Gartner has written about us in the full Magic Quadrant for Unified Threat Management report (registration required).
You can read the original article, here.
Vulnerability Assessment Builds Security Continuous Improvement Into your Enterprise SDLC
Vulnerability assessments are a highly systemised way for established organisations to gain a comprehensive picture of their security posture, and then maintain and continuously improve on it. When new devices, ports, websites, web applications, or services are added, they are included in regular scans. A vulnerability assessment is a great way to identify, and eventually fix, common vulnerabilities in your applications and servers.
Most security professionals recommend that vulnerability testing is conducted at least quarterly. Our recommendation, however, given that Netsparker allows you to configure scheduled scans, is to scan much more frequently. In any case, you should conduct vulnerability tests following any significant change or addition to your web applications or web APIs. With Netsparker, if you want to, you can run scans daily, with notifications drawing your attention to detected vulnerabilities as they arise. Resources can then be deployed rapidly to deal with critical and important threats.
Penetration Testing Exposes Fragile Cracks In Your Security Architecture
Since penetration testing is so specific, it is best suited to environments where an organisation’s web and network security is considered to be already robust. Organisations may ask a tester to attempt to do something specific, such as gain access to a transactions or bank details database, or alter or delete a single record. The purpose is to reduce exposure to certain risks. Penetration testers check for weak points in the architecture. While vulnerability assessments mostly take care of software vulnerabilities, penetration testers may often use phishing, social engineering and onsite engagements in order to reach their goal. Therefore they can give a much more accurate depiction of a company’s security level. They act exactly as malicious hackers, without producing any devastating loss or alteration of data, of course! For example, a penetration tester might try to establish a connection to a remote server without being detected, in order to exfiltrate sensible data from a system. It is a useful way to demonstrate if attackers with particular objectives in mind stand a healthy chance of success. Ostensibly, though, a pen tester would conduct an endless series of attempted hacks.
The recommendation is that penetration testing is conducted at least once per year.

What Scenarios Can Help Determine the Choice of Approach?
Both vulnerability assessments and penetration tests should be run against network devices, and internal and external servers. It’s crucial to determine whether an attack is possible from the outside (for example, by a malicious attacker targeting publicly-available target surfaces on the internet) or the inside (for example, by a disgruntled employee or contractor, a user with permissions they should not have, or a compromised machine within the internal network).
Vulnerability Assessments Help Enterprises Maintain Consistent Compliance With Standards
Sometimes organisations need to work within certain parameters: they have PCI DSS or other forms of compliance to adhere to and want to test if the current architecture, systems and devices would pass the test. They may want to run a port scan or check against everything on the OWASP Top 10 List. In such scenarios, a vulnerability assessment will provide a more realistic and systematic approach. Even a very large team of developers could never comprehensively reach the end of such tests.
Penetration Testing Helps All Organisations Keep Ahead of the Hackers
Penetration testing comes at security from a different angle. Testers will uncover security risks in the same way that hackers do – by conducting attacks with a single purpose in mind, to gain access to certain data or to change something on an organisation’s website, for example. Pen testers are best commissioned with an open mind, leaving them free to conduct both requested attacks and anything else that occurs to them, depending on their professional experience.
What About the Testers?
One of the most important questions to consider, to help distinguish between vulnerability assessment and pen testing, is: Who’s conducting the testing?
Information Security Professionals Establish Internal Procedures for Continuous Improvement
Contrary to some articles on the subject, vulnerability testing is not a fully-automated process in the sense that all it takes is to push a button. The person who manages regular, automated vulnerability assessments must be already skilled and experienced in information security procedures. They must know what environments and attack surfaces to assess and what to assess them for, as automated security scanners will still require some configuration. And they must be able to interpret the resulting reports and make recommendations on what needs to be done next.
In-house security professionals responsible for vulnerability assessment continuously add value to the security status of organisations and their resources. First, they can establish a baseline. They are likely to want to establish some systems, particularly an assessment schedule and reporting. They can help raise awareness within, while facilitating a continuous reduction in security risks. Meanwhile, they will most certainly expand their own knowledge and skills. Arguably, they are much more likely to feel loyal to an organisation in which they already work.
Penetration Testers Tell It Like It Is
Penetration testers, likewise, must also be knowledgeable professionals who are confident in their abilities.
Most professionals in the field recommend that penetration testers should be independent, external professionals. They must maintain enough distance from your company or systems that they are not hampered by concerns about personal financial security, loyalty or politics. This enables then to state the blunt truth about your security status, however much it hurts!
What About Cost?
How much vulnerability testing costs depends on the scope of the engagement. For small organizations the price will be significantly lower than for a big corporation with thousands of potentially vulnerable machines, IPs and internet facing hosts.
Regardless of the cost, vulnerability assessments produce a better yield on investment. While a pen test may be a deep slice of how secure your system is, it only reveals one thing in one direction. Vulnerability assessments take the long view, investing time and resources in developing systems and procedures that will yield a solid level of security on which to further develop your systems and integrate new components.
So, Which Approach Do We Select?
Simply put, do both. Both approaches have the capability to uncover gaping holes in your security and reveal other less obvious vulnerabilities, ones you weren’t even looking for. One thing is certain, if you’re not scanning or testing, you will encounter a loss of data. The only question is when. Whether it’s a known vulnerability that you’ve not addressed, or the result of a bored hacker’s Sunday afternoon adventures (yes, it’s true, they’re not all malicious!), the result is the same.
The mature, preventative approach is to establish vulnerability testing and scanning as part of your regular SDLC, and additionally employ some unusual types to do what a hacker might do, but on friendly terms (‘white box’ pen testing). Then you can read all the reports and results, examine the recommendations and make smart decisions on how to keep your organisation’s security posture ahead of the bad guys.
You can read the original article, here.
Sophos is committed to providing you with the best protection, performance and value in the industry and the latest NSS Labs retest of XG Firewall validates that we are delivering on that commitment. As expected, XG Firewall has performed extremely well blocking 100% of all evasions with excellent results across all other areas tested by NSS Labs. The results for both security effectiveness and total cost of ownership (TCO) per protected Mbps are outstanding.
Here’s a summary of the results:
- 100% Evasion Resistance
- 94.82% Exploit Block Rate
- 100% Resiliency Coverage
- 100% Stability and Reliability
- 6,194 Mbps tested throughput
- TCO per protected Mbps of $5.47
We encourage you to explore the full test results which are available for download.
You can also see how XG Firewall places on the NSS Labs Security Value Map (SVM) Chart (click to enlarge).
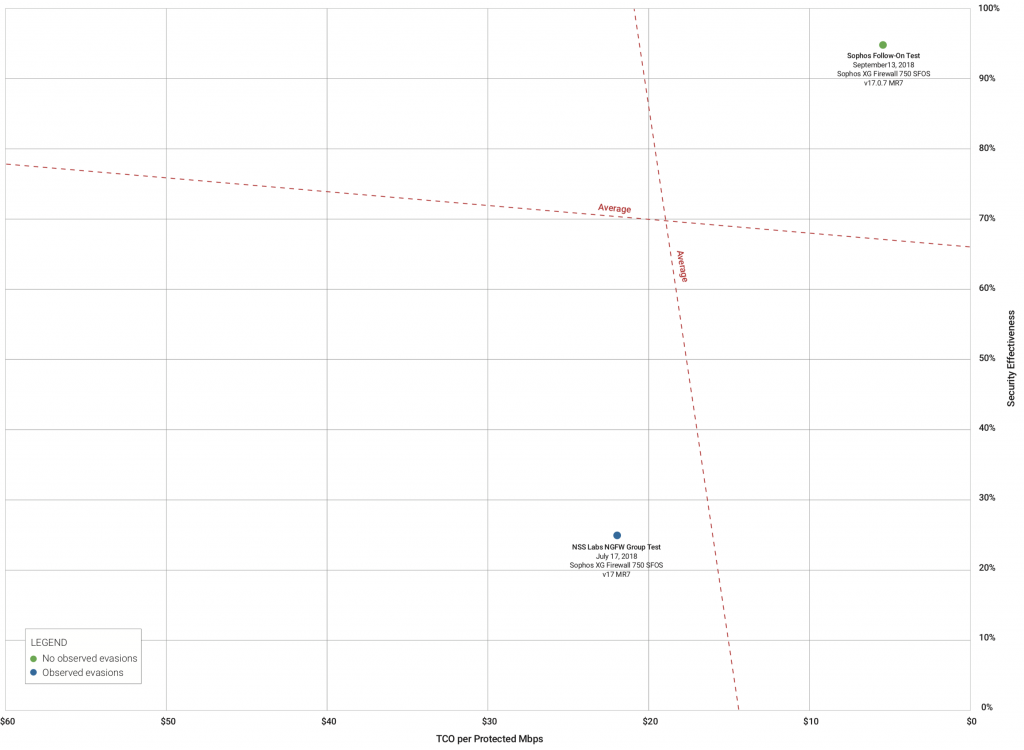
Sophos XG Firewall customers and partners don’t need to take any action as your firewall is providing optimal protection and performance. For those wondering about the HTML padded evasion techniques missed in the June 2018 NSS Labs Next Generation Firewall (NGFW) public test, those were addressed through adjusting the AV engine file size scanning parameters. No action is required as your firewall device comes with optimized default settings based on careful analysis of the current threat landscape. You can learn more about this setting in the XG Firewall Knowledge Base.
As you know, we never rest, and are relentlessly improving and innovating our products. In fact, we have a substantial new release of XG Firewall coming soon – watch this space for more details in the days ahead.
You can read the original article, here.
Apple’s iOS 12 is being released to the public today, and the great news is that Sophos Mobile already supports it. As soon as your users upgrade to the latest versions of the operating system we will be protecting them.
For more information about the features of iOS 12, take a look at Apple’s iOS product page.
If you’re managing Sophos Mobile via Sophos Central you can now control when iOS updates are installed, with the option to delay updates for up to 90 days should any custom application testing be required before roll out. If you’re running your own Sophos Mobile server you can also use the same controls once you’ve upgraded to Sophos Mobile 8.5.
Whenever you’re ready to update to iOS 12, Sophos Mobile is ready for you.
You can read the original article, here.
We’ve watched plenty of software demos over the years, be they with or without the thrill of live attacks involving things appearing on your screen, but there really is nothing quite like getting hands-on with a piece of hardware.
So, with our new APX Series access points, we thought we’d try our hand at one online phenomenon – the unboxing video.
If you haven’t got around to ordering your APX Series just yet, here’s a taste of what you can expect. We’ve gone for the subtle unboxing approach and in the interest of good taste – we’re a British company after all – have refrained from throwing any packaging on the floor.
What is an APX?
The APX Series is a new generation of 802.11ac Wave 2 access points, which can be managed through our Sophos Central platform and so alongside your Sophos Endpoint, Intercept X, Mobile, Server, Email and Encryption.
The first three models are already available in most regions:

The APX 120, an entry-level 2×2 model, will be introduced in late 2018 and further models are in planning for 2019.
The very observant amongst you may have noticed that the second digit in the model number correlates with the MIMO capability, which is fully intentional.
Management support in XG Firewall is planned for late 2018.
To find out more visit the APX Series and Sophos Wireless pages or take a look at the Sophos Central demo, which includes Wireless.
You can read the original article, here.
The latest enhancements for Sophos Email Standard and Advanced customers make the management and reporting of email security even simpler. Here’s what’s changed:
New reporting
You can now view detailed summary information for every inbound and outbound message processed by Sophos Email.
Starting from the ‘Message History’ report in Sophos Central, simply select the new, clickable email subject line of the message you’d like to inspect to see a breakdown of helpful information, including:
- Details of the sender, recipient, date and time
- Full message header information and any attachments
- Details of the steps the message has passed through in our scanning infrastructure
- More visibility into the current status of the message within the scanning process, from sending receipt to the delivery to your inbox
Whether it’s responding to user requests on email delivery status or understanding reasons for a quarantined message, being able to quickly access details related to your organization’s emails is really useful for busy admins.
The Allow and Block Senders policy restricts messages to or from specific email addresses or domains, and it can apply to inbound or outbound messages. In this latest update you have the freedom to create IP address entries here, plus wildcards including country level domains such as .co.
Finding specific user mailboxes is also a simple task with the new Mailbox Search feature within the ‘Mailboxes’ menu option.
Want to find out more?
Check out the Sophos Email Security page for more information, and to sign up for a free 30 day free trial.
Confusion between the terms ‘penetration testing’ and ‘vulnerability assessments’ often begins at the level of language. Those who are not full-time professionals in web security, such as journalists reporting on a big story that affects consumers, use the terms interchangeably, as if referring to the same process.
Experienced professionals in the industry know the difference, but those new to it can be easily confused. Why? Even professionals sometimes use terms in fuzzy or inexact ways, when they should distinguish between things that differ. Let’s be clear on the difference between the two.

What Are Vulnerability Assessments?
A vulnerability assessment involves running a series of multiple tests, against defined websites, web applications, IP addresses and ranges, using a known list of vulnerabilities, such as the OWASP Top 10 list. Assessors may also run tests against systems they know to be incorrectly configured or unpatched. Often, automated security scanning tools are used. Commercially licensed, subscription-based tools are regarded as coming with less risk – regular updates, release notes bring less chance of the inclusion of malicious code. (Their open source equivalents, however, have the significant advantage of being the exact same tools that malicious hackers prefer.)
Vulnerability assessments tend to include the following stages:
- Identifying all resources, and connected resources, within an organisation’s IT systems
- Assigning a value or priority to each one
- Conducting an assessment of lists of known vulnerabilities across a large number of attack surfaces (from login screens to URL parameters to mail servers)
- Fixing the most critical vulnerabilities and making decisions about how to the deal with the rest
What is Penetration Testing?
Penetration testing (pen testing), on the other hand – while it may be considered to be a type of vulnerability assessment – involves replicating a specific type of attack that might be carried out by a hacker. A pen tester will often explore the systems until they find a vulnerability. They may even employ a vulnerability assessment tool to uncover a vulnerability. Once they find something, they will then try to exploit it, to determine whether it would be possible for a hacker to achieve a certain objective (access, change or delete data, for example). Often, while doing this, they may accidentally encounter other vulnerabilities, and follow where they lead. The pen tester may use an automated tool at this point to run a series of exploits against the vulnerability.
Some penetration tests are referred to as ‘white box’ to indicate that the penetration tester has been given detailed information about the environment, such as a list of assets belonging to the organization, source codes, employee names and email addresses etc. When they are referred to as ‘black box’, this indicates tests that are conducted without any prior information about the internal structure, access to source code etc. This kind of pen test of course, can more closely resemble the activities of a malicious hacker, but may also lead to less thorough coverage of the companies potentially vulnerable assets.
What Results Can I Expect From Each Approach?
The answer to this question might best be asked by thinking backwards: What results do you want?
Vulnerability Assessments Report Across All Vulnerabilities
The results are collated in an automated, lengthy report, with a comprehensive list of detected vulnerabilities arranged by priority, determined by how by severe and business-critical they are. As time goes on, this list can reveal changes since the last report. One of the criticisms of the results achieved is that, unlike in penetration testing, they can contain false positives or false negatives. Naturally, this is not the case if you use Netsparker web application vulnerability scanner to conduct your vulnerability testing. It is one of our key features – automatically verifying identified vulnerabilities with Proof-Based Scanning.
Reports should include guidance on how to remediate the detected vulnerabilities, and tools sometimes come with patches subscribers can use. In most cases, results are then allocated to dedicated development teams who conduct fixes, remove the most serious vulnerabilities, and otherwise address the less serious ones. In an ideal world, this activity is ongoing, scheduled regularly, and built into the organisation’s SDLC.
Penetration Testing Reports Deep Into Each Vulnerability
With pen testing, there is no lengthy public report, though some record and publish their actions and anonymized findings, blog about their experiments, or live hack at conferences. If you hire a pen tester, however, they should deliver a (pen test) report, but it tends to be focused on the attack method or exploit, and exactly what data can be compromised. It will generally be accompanied by suggestions on what a hacker might be able to do to, or with, it. This helps business analysts and non-technical professionals, who may not understand all of the technology behind such tests, grasp business process impacts quickly.
Sometimes reports also incorporate remediation advice. However, not all pen tests incorporate exploitation of vulnerabilities in the way that Netsparker does. It may be sufficient simply to illustrate that an attack is possible. In some cases the pen test report may simply report theoretical vulnerabilities because attempting to exploit them may result in a catastrophic denial of service (DoS). And, finally, there is no assessment of vulnerabilities, since the goal is simply to do one thing, or least to determine whether it can be done.
Which Approach Should My Organisation Adopt?
The main question to ask is: What is your current security posture?
To be continued…
With the introduction of Sophos Wireless v2.0 and the new APX Series Access Points, we’re continuing the evolution of our security in order to connect multiple products via our Sophos Central security management platform.
When connected through our new APX Series access points, Sophos Wireless can not only talk to your endpoints but also your mobile devices and even your servers – as long as they’re connected via Wi-Fi.
What does synchronized security with Wireless do?
In this first phase, Wireless receives the Security Heartbeat of any Wi-Fi connected device, which is managed through the same Sophos Central account.
The heartbeat communicates the health state – green, yellow or red – and should a red heartbeat be detected, which can indicate anything from a minor compliance violation for a mobile device, to a ransomware attack on an endpoint or server – the device is automatically put into a ‘walled garden’.
As pleasant an image as that may conjure up in the horticultural sense, here it means that internet access is restricted to a list of pre-defined URLs – a safe environment – thus potentially preventing call-home attempts and further propagation of threats.
So generally speaking, walled gardens are much less fun in the world of Wi-Fi.
Take a look at this short video to see how it works.
Find out more at the Sophos Wireless page or take a look at the Sophos Central demo.
You can read the original article, here.
Cryptocurrencies like Bitcoin have been a source of worry since their creation. Fans of the technology say it’s the future of money in terms of privacy, and the verifiability of complex transactions; but there has always been a great debate that the real ‘value’ of cryptocurrency is in the application and use of the currency such as tax avoidance and for purchases of illicit items and services.
While governments, various financial institutes and law enforcement have begun to crackdown on those concerns by attempts to regulate the market place, cryptocurrencies remain as an attractive form of income when linked to malicious activities such as malware infections, increasing the popularity of these strains.
Because they are valuable, digital, anonymous, and work across borders—anyone can send cryptocurrencies to anyone else, anytime or anywhere – they have become an irresistible target for cybercriminals. It’s no accident that the increasing popularity of cryptocurrencies has seen a parallel rise in malware infections that turn laptops and servers into zombie machines, quietly doing the bidding of a distant and remote bitcoin ‘mining’ operation.
Bitcoin mining or Crypto-jacking takes place when someone else uses your computer to ‘mine’ a cryptocurrency like Bitcoin or Ethereum. Rather than benefit yourself, however, any mined (collected) coins go into the attacker’s (or their client’s) account. By crypto-jacking your machine the crypto-jacker steals and utilizes your resources, in the form of your machine processing power and electricity, and converts them into capital for themselves.
Those computing resources include taking over your graphics processing unit (GPU) and central processing unit (CPU). Bitcoin mining is an exceptionally power and resource-intensive task, pushing those processors into overdrive and requiring large amounts of energy to complete the complex calculations necessary to generate a virtual coin. Pushing your machinery to these levels without the correct cooling and provisions in place can easily cost you your pride and joy or witness a loss of productivity in a workplace environment due to hardware failing from overheating challenges.
That’s what motivated a team of Russian scientists to use the supercomputer at a nuclear research facility to run an unsanctioned bitcoin mining operation. It’s also what motivates crypto-jacking. By creating a distributed computing network compromised of hundreds or thousands zombie/compromised machines, they sidestep the upfront costs of a single, expensive super-powered computer, and then pass on the ongoing costs of powering it.
Those costs are passed on to us
The UK and Australian governments recently suffered website outages thanks to a crypto-jacking malware that infected thousands of government machines. The source of infection was a compromised browser plug-in made by a third-party. Thousands of websites in and outside of Australia, including the UK’s National Health Service, and the UK’s own data protection watchdog, were affected.
Windows machines tend to be the target of crypto-jacking malware, but other devices and operating systems can also be turned into bitcoin mining bots:
- Mac OS and iOS device, including iPhones
- Gaming consoles
- Environment-monitoring devices, used in data centers
- IoT devices within a Smart Home instance
- Home WIFI routers
- Android-run smart TVs and mobile devices
A compromised device is often forced by the malware to run at the maximum of what its components can handle. Mining can slow other processes, overwork cards and processors, or even brick the machine. With degraded capabilities and the connection between the infected host and the command and control server for the crypto mining software being unsecured, the machine can also be vulnerable to infection from other kinds of malware.
While an end user or network admin might realize that a machine is running more slowly than normal, or that CPU usage on the network is high, determining the source of the issue can be difficult. The fact that a crypto-jacked machine is running slowly also makes it harder to investigate. The mining processes initiated by the malware can also mask themselves as normal system tasks.
To stop crypto-jacking, cross correlate network anomalies
Unfortunately, there is no blanket protection against crypto-jacking. As with any malware there are multiple vectors of infection and keeping them out of connected machines is part of the long-term battle against malware.
Security teams should of course, follow standard mitigation techniques – updating antivirus and firewall settings, ensuring all devices are updated with the latest patches, changing or strengthening default credentials, application whitelisting and so on.
But the biggest challenge to stopping crypto-jacking is detection. Proactively monitoring network traffic and machine status can help spot the indicators of infection – spikes in CPU usage, excessive memory usage, network congestion, or servers inexplicably slowing down. However, when seen in isolation, these red flags may not be enough to raise the alarm.
The key is to have network monitoring systems capable of cross-correlating the anomalies. Only then can a system administrator or SOC team can identify the behavioral patterns that point to bitcoin or another cryptocurrency mining. They can then decide on the best approach to stopping it, mitigating the damage, and limiting the size of the energy bill created by the infection.
Securing email gateways, developing countermeasures against web injections, implementing best practice for mobile devices, BYOD (Bring your own device), and promoting a security-aware business culture can all form part of a defense-in-depth against crypto-jacking and other breaches.
Ultimately, however, the security of internet-connected devices against cryptocurrency-mining malware is going to be a top item on the cybersecurity agenda for some time to come.
You can read the original article, here.
This three-day training program was designed and intended for experienced technical professionals who want to install, configure and support the XG Firewall in production environments and is the result of an in-depth study on the next generation firewall of Sophos.
The program consists of presentations and practical workshops for the enhancement of teaching content. Due to the nature of the traditions and the varied experience of the trainees, open discussion is encouraged during the training.
Prerequisites
Participants should have attended the XG Engineer Course.
Recommended Knowledge
- Knowledge of networking to a CompTIA N+ level
- Knowledge of IT security to a CompTIA S+ level
- Experience configuring network security devices
- Be able to troubleshoot and resolve issues in Windows networked environments
- Experience configuring and administering Linux/UNIX systems
Contents
- Module 1: Enterprise Deployment Scenarios
- Module 2: Advanced Firewall
- Module 3: Authentication
- Module 4: Webserver Protection
- Module 5: RED Management
- Module 6: Wireless Protection
- Module 7: Enterprise VPN
- Module 8: High Availability
- Module 9: Troubleshooting
- Module 10: Sizing
Certification
+ exam: Sophos XG Architect
Duration
3 days

Agenda
Trainer: Michalis Eleftheroglou
Day 1 Monday, October 29th, 2018
9:30-10:15 Module 1: Enterprise Deployment Scenarios Part I
- Bridge mode
- Gateway mode
- Mixed mode
10:15-10:30 Break
10:30-12:00 Enterprise Deployment Scenarios Part I
- VLAN
- Link Aggregation
- Routing protocols
12:00-12:15 Break
12:15-13:45 Advanced Firewall Part I
- Stateful inspection
- Strict policy
- Fast path
- Intrusion prevention
- Anti Dos/floofing
- Advanced Threat Protection
13:45-14:45 Break – Lunch
14:45-16:15 Advanced Firewall Part II
- Asymmetric routing
- Local NAT policy
- DHCP options
- Bind to existing DHCP scope
- Country list
- Drop packet capture
- IPS tuning
16:15-16:30 Break
16:30-17:15 Webserver Protection
- Overview
- Web Servers
- Application Protection policies
- Path specific routing
- Authentication policies
- Certificates

Day 2 Tuesday, October 30th, 2018
9:30-10:15 Module 4: Authentication
- Single sign-on (SSO)
- LDAP integration
- Secure LDAP
- STAS (Sophos Transparent Authentication Suite
- Troubleshooting STAS
10:15-10:30 Break
10:30-12:00 Authentication part II
- Sophos Authentication for Thin clients (SATC)
- Troubleshooting SATC
- NTLM
- Troubleshooting NTLM
12:00-12:15 Break
12:15-13:45 Module 5: Red Management
- Overview
- RED Models
- Deployment
- Adding a RED interface
- Balancing and failover
- VLAN port configuration
13:45-14:45 Break – Lunch
14:45-15:30 Module 6: Wireless Protection
- Overview
- Access Points
- Wireless networks
- Security modes
- Deployment
- Built-in wireless
- Mesh networks
- Radius authentication
- Class Activity
15:30-15:45 Break
15:45-17:15 Module 7: Enterprise VPN
- Huge and spoke topology
- Ipsec VPN configuration
- Ipsec VPN policies
- NAT overlap
- Route precedence
- VPN failover
- Logs
- Troubleshooting

Day 3, Wednesday, October 31st, 2018
9:30-11:00 Module 8: High Availability
- Overview
- Prerequisites
- HA packet flow
- Configuration
- HA status
- Console commands
- Logs
- General Administration
11:00-11:15 Break
11:15-12:00 Module 9: Troubleshooting
- Consolidated Troubleshooting Report
- SF loader
- Tcpdump
12:00-12:15 Break
12:15-13:45 Module 10: Sizing
- Hardware appliance models
- Hardware appliance sizing
- Software and virtual devices
- Sizing scenarios
- Class activity
13:45-14:45 Break – Lunch
14:45-17-15 Labs and Exams