News
The term sensitive data exposure means letting unauthorized parties access stored or transmitted sensitive information such as credit card numbers or passwords. Most major security breaches worldwide result in some kind of sensitive data exposure.
Exploiting an attack vector such as a web vulnerability is just the first step that the attacker takes. Further steps usually involve one of three goals: stealing sensitive information, planting malicious software (for example, to attack other targets or enable permanent control/spying), or escalating to other systems (where this choice repeats). Obviously, stealing sensitive information such as credit card data is the most profitable goal for the attacker and most cyberattacks are driven by money, hence sensitive data exposure is the most common attack goal.
Just like it is possible to create software with next to no vulnerabilities, it is also possible to create software that prevents the attacker from accessing sensitive information. Sensitive data exposure is caused by bad design or implementation of computer systems and software as well as misconfiguration of such systems and software.
Defining sensitive data
When you build a web application, you must clearly define what you consider to be sensitive data. While some examples are obvious, like credit card numbers, authentication credentials, or health records, others may not seem so straightforward. Even if a piece of information is to be displayed onscreen by the application, it may still be considered sensitive in transit and storage.
Any type of data that can be considered personal data or private data should be considered sensitive. This means even data such as first and last name, date of birth, or even an email address. Criminals are after such data because they can correlate personal information stolen from other sources to create profiles for identity theft.
Any data related to financials should also be considered sensitive and this does not mean just credit card numbers. For example, bank account numbers, both internal and IBAN, should also be considered sensitive as well as any transaction amounts.
Depending on the industry that your business deals in, some data may be not only considered sensitive but also covered by compliance regulations. Make sure that all that data is secured, both in transit and in storage, otherwise you will lose your compliance.
Sensitive data exposure vulnerabilities in transit
Most websites and web applications nowadays are accessible via secure SSL/TLS connections. Many go as far as enforcing such connections using HTTP strict transport security (HSTS). As a result of this, many web application designers think that it’s safe to transmit sensitive information between the client and the server using clear text.
This mindset is the primary cause of sensitive data exposure in transit. Unfortunately, despite the fact that SSL/TLS provides a high degree of protection, there are cases when a man-in-the-middle attack (MITM) on network traffic is possible. If the attacker somehow manages to access data transmitted between the web application and the user, and this data includes, for example, credit card numbers or clear text passwords, the attack ends up in sensitive data exposure.
Therefore, the best way to protect your web application against sensitive data exposure is never to transmit any sensitive data using clear text and always use cryptographic algorithms to secure them. Note that these should not be weak crypto algorithms because the attacker may store the intercepted data and later attempt to break the encryption using powerful GPUs.
Sensitive data exposure vulnerabilities in storage
Storing sensitive data securely is just as important as transmitting it securely, if not more. If an attacker exploits a vulnerability and gains access to your website or web application, for example, using an SQL injection, they may be able to access the content of your entire database. If any sensitive information is stored in the database without encryption, it’s a guaranteed leak.
When storing sensitive information, using renowned, secure, and strong encryption algorithms is even more important than in the case of transit. A weak algorithm will let the attacker quickly run brute force attacks on the stolen encrypted data and decode the original information.
In addition to strong database encryption, some types of sensitive data need extra protection. For example, passwords that are encrypted or hashed using even the strongest algorithms can be easily broken if the password itself is a weak password. Therefore, avoiding common password vulnerabilities is just as important as encryption or hashing.
Sensitive data exposure vulnerabilities in email
It is shocking to see how many businesses and institutions forget that email is not a secure channel and sensitive data should never be transmitted using this medium. Email connections between the client and the server may be encrypted but the connections between servers are usually done using plain text. The email body is not encrypted, either. And the recipient of the email has no control over how securely their email content is stored or whether it is actually destroyed when the email is deleted client-side.
If your web application sends emails, you should never send any sensitive data in emails and, instead, use the web application itself to present or accept sensitive information. For example, you should never ever send a new password via an email and instead display it for the user on a web page. An institution should also never send any personal and sensitive data in clear text over emails, which is, unfortunately, the way that many government institutions do it in many countries.
Protecting sensitive data
Sensitive data is considered important enough by OWASP (the Open Web Application Security Project) to feature it in the OWASP Top 10 as a separate category. In the 2017 edition, this category was considered the third most important common flaw. We also believe that in the upcoming 2021 OWASP Top 10 this category will only gain in importance. Therefore, you should take great care to protect your sensitive information and avoid sensitive data exposure.
Protecting your sensitive data is really easy as long as you use cryptographic algorithms in transit and in storage along with any side-measures such as, for example, proper key management (so that your keys are as safe as the data itself). In some cases, you don’t even need to transmit or store encrypted data, you can use hash algorithms. Password hashing is the most efficient way to make sure that passwords are never stolen, both in transit and in storage.
Source: Acunetix
Read our new report The IT Security Team: 2021 and Beyond to ascertain the full impact of the pandemic on the IT security teams around the globe.
Based on findings of an individual survey of 5,400 professionals across 30 countries, the report reveals how IT security teams’ cybersecurity experiences changed over the course of 2020 and what this means for the future delivery of IT security.
More work, more learning
With technology a key enabler for dispersed and digital organizations, IT professionals played a vital role in helping organizations to keep going despite the restrictions and limitations necessitated by COVID-19.
At the same time, adversaries were quick to take advantage of the opportunities presented by the pandemic: 61% of IT teams overall reported an increase in the number of cyberattacks targeting their organization over the course of 2020.
It’s therefore not surprising that demand on IT teams grew over the course of 2020. 63% of respondents said their team saw an increase in non-security workload, while 69% experienced an increase in IT security workload.
However, the vast majority of IT teams that faced a rise in cyberattacks (82%) and a heavier security workload (84%) over the course of 2020 also strengthened their security skills and knowledge.
Adversity brought teams together
Despite the challenges created by the pandemic, 52% of the IT teams surveyed said team morale increased during 2020, with those facing the greatest challenges often reporting the greatest increase. For instance, ransomware victims were considerably more likely to have experienced an increase in team morale than those that weren’t hit (60% versus 47%.)
While morale is also likely influenced by external and personal circumstances during the pandemic, these findings suggest that a shared purpose, a sense of value and facing adversity together helped to bond and lift the spirits of IT teams.

The experiences of 2020 have fuelled ambitions for bigger IT teams
Many teams have entered 2021 with plans to increase the size of both in-house and outsourced IT teams, and to embrace the potential of advanced tools and technologies.
The survey found that 68% of IT teams anticipate an increase in in-house IT security staff by 2023, and 56% expect the number of outsourced IT security staff to grow up over the same time frame.
An overwhelming majority (92%) expect Al to help deal with the growing number and/or complexity of threats.
Read the full survey findings
To learn more, including a deep dive into the experiences of different countries and sectors over 2020 and their future IT security delivery plans, read The IT Security Team: 2021 and Beyond survey report.
Source: Sophos
There are many different technologies that drive business for managed service providers (MSPs), but few are more important than professional services automation (PSA) and remote monitoring and management (RMM) tools used to run their core business of delivering IT managed services.
MSPs have a lot on their plate, from managing client relationships, growing sales pipeline, keeping endpoints up to date and secure, and resolving tickets quickly. To grow their business, it’s critical to effectively utilize business management tools like PSA and RMM to drive efficiency, insight, client satisfaction–and ultimately, profitability. So for MSPs, selecting the right vendor for these tools is an important decision.
Canalys MSP Tech Stack Report
Canalys, a third-party analyst firm focused on the MSP channel, recently debuted their annual MSP Tech Stack Report assessing the performance and momentum of global PSA and RMM vendors. Of the 17 vendors analyzed in the report, Datto was given the highest combined Momentum and Performance score, along with placement in the ‘Strategic’ category, indicating a dedication to the development of our solutions and technological capability.
In order to be recognized as a strategic vendor for RMM and PSA, vendors needed to demonstrate strong technological capabilities and illustrate investment and ambition for continued growth. Vendors in this category also needed to display solid work in product development and technological capability, acquisitions to broaden their portfolio, and deliver training to provide MSPs with the skills necessary to help customers with their IT assets.
Driving efficiency and insight through integrated, MSP-centric solutions
Datto has a unique combination of demonstrated performance based on key metrics and strong future opportunities as defined by our technological capabilities, strategy, and open ecosystem. This enables Autotask PSA and Datto RMM to help MSPs deliver efficient, high-quality managed services for the IT environments of today, and prepare for those of tomorrow.
Datto Autotask PSA and RMM are secure, reliable, and intuitive cloud-based platforms designed to help MSPs run their IT managed services business more efficiently. The seamless integration between the two platforms can help elevate MSPs to higher levels of insight, productivity, and profitability with easy navigation between platforms and relevant real-time asset data and actions providing clear insight into your managed estate. This integration enables MSPs to mitigate issues before they occur, shave minutes off each ticket, and unlock new business opportunities.
 “We are excited about being ranked as the highest combined scoring vendor in the RMM and PSA space by Canalys,” said Radhesh Menon, Chief Product Officer at Datto. “Being recognized as a ‘strategic’ vendor validates our focus on innovating to help our partners grow their business with secure and easy-to-use platforms that help drive efficiency, actionable insights, and profitability.”
“We are excited about being ranked as the highest combined scoring vendor in the RMM and PSA space by Canalys,” said Radhesh Menon, Chief Product Officer at Datto. “Being recognized as a ‘strategic’ vendor validates our focus on innovating to help our partners grow their business with secure and easy-to-use platforms that help drive efficiency, actionable insights, and profitability.”
To learn more about the PSA and RMM vendor landscape, download the report today.
Source: Datto
NSS, an international value-added distributor of leading cutting-edge IT solutions, announced its partnership with Password Boss.
Password Boss is an award winning, complete end-to-end, multi-tenant password management solution for MSPs that securely stores their business’s and their clients’ passwords. The features of this amazing password management solution include multi-layered security, role-based access, secure password sharing, remote control tool integration, multi-devices access with mobile synchronization, centralized management portal and dashboard, built-in Dark Web scanning and monitoring and much more. This strategic distribution agreement brings Password Boss technology to MSPs in Southeast Europe by NSS.
Founded in 2014, Password Boss was designed and developed to meet the needs and ways that MSPs work and support their customers and it is built to complement all the tools and applications that MSPs use most.
“We are thrilled to add Password Boss to our product portfolio and distribute this amazing password management solution to our partners MSPs” said George F. Kapaniris, Executive Director, NSS. “We look forward to helping MSPs securely store their businesses’ and clients’ passwords. After all, Password Boss is a password management solution that was built by an MSP for MSPs”.
NSS will distribute Password Boss in the markets of Greece, Cyprus, Malta, and Bulgaria. NSS continues to expand its product portfolio to meet the increasing IT requirements and security needs of businesses and MSPs during this age of digital transformation.
To find out more please visit: https://www.nss.gr/en/products/security/password-boss/
About NSS
NSS is an international Value Added Distributor of Affordable Cutting Edge IT solutions, covering technology areas that include information security, network optimization, communications, and infrastructure systems. NSS has strategic partnerships with superior vendors offering products & services with leading technologies that place the company ahead of the competition in today’s crowded market. NSS products can be acquired through a selected channel of resellers in Greece, Cyprus, Malta, the Balkan and Adriatic Countries.
We are pleased to announce that on May 19, 2021 we have released some exciting updates for all customers using Sophos EDR (Endpoint Detection and Response) with Intercept X Advanced with EDR and Intercept X Advanced for Server with EDR.
What’s new?
Introducing the Sophos Data Lake
The Sophos Data Lake stores critical information from your EDR-enabled endpoints and servers, which means you get access to that data even if those devices are currently offline.
In addition to being able to get key data from devices even when they are not online (for example if knocked offline during an attack, or a misplaced laptop) the Sophos Data Lake also enables event correlation on a much broader scale. For instance, being able to quickly identify that a suspicious account is logged in across multiple devices.
Then when you have identified an area of interest you can query the device with Live Discover and get incredibly rich, live data and remotely access the device via Live Response to take appropriate action. It’s the best of both worlds.
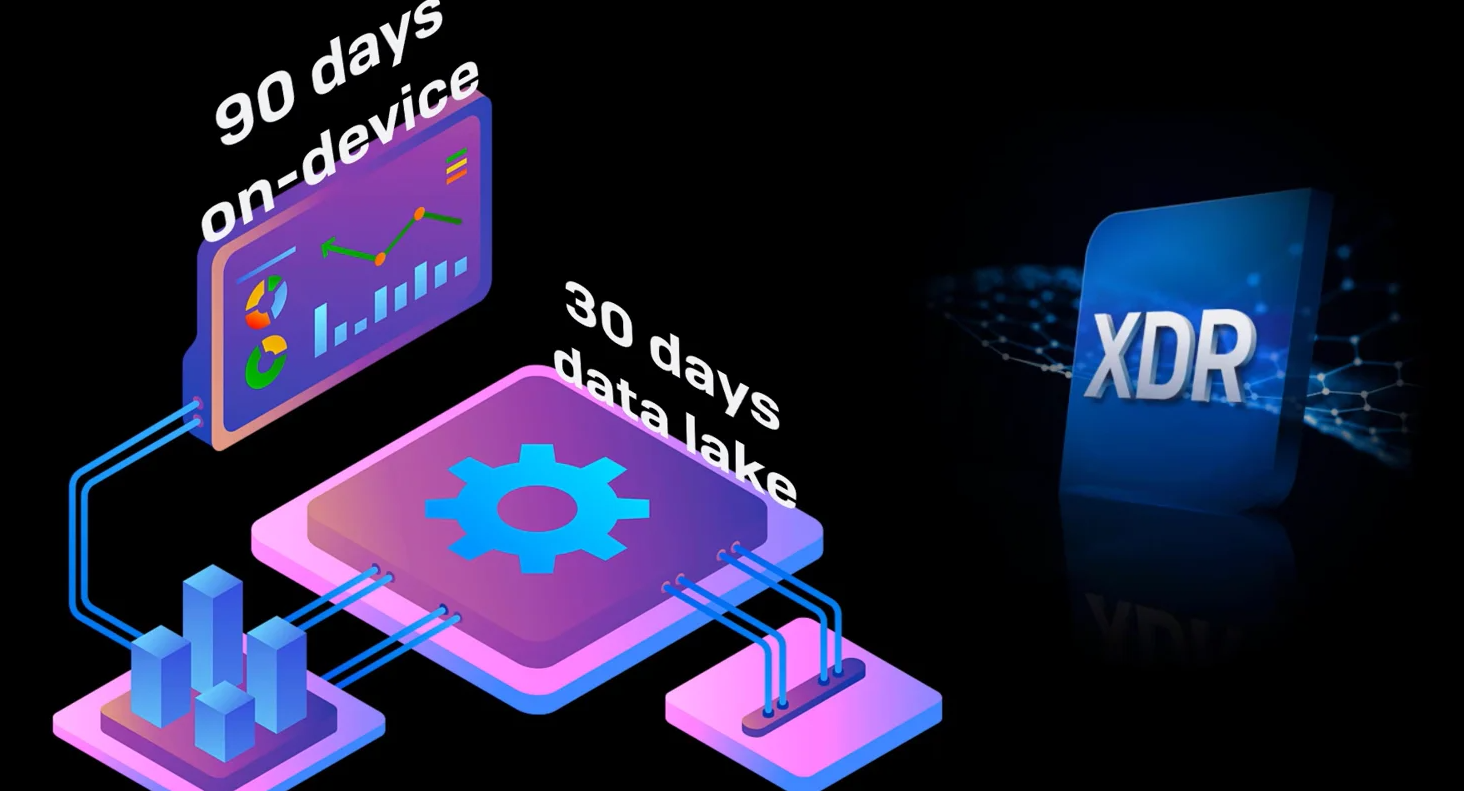
You get 7 days of retention in the data lake as standard (30 days with Sophos XDR) which is in addition to the existing up to 90 days of data stored directly on devices.
Please note that you need to enable the Sophos Data Lake. In your Sophos Central console select ‘Global Settings’ then under Endpoint or Server Protection (or both) select the ‘Data Lake uploads’ setting and turn on the ‘Upload to the Data Lake’ toggle. From the same window you can also select which devices send data to the Sophos Data Lake.
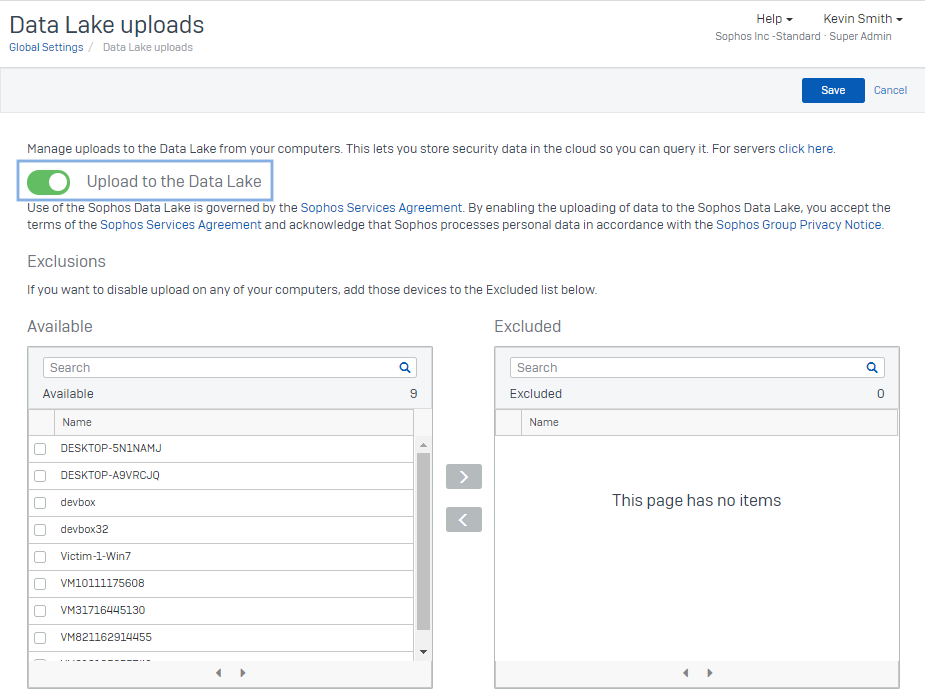
Τhe Sophos Data Lake is available now for Windows and Linux devices. Mac support will come later this year.
Scheduled queries
One of the top requested features, this release introduces scheduled queries so you can have critical information ready and waiting for you. Queries can be scheduled to run overnight so key data is ready for assessment the next day.
To set up a scheduled query you first need to choose a query by going to the ‘Threat Analysis Center’ and then ‘Live Discover’. When you have selected the query you want to run you will see a new option to schedule the query instead of running it immediately.
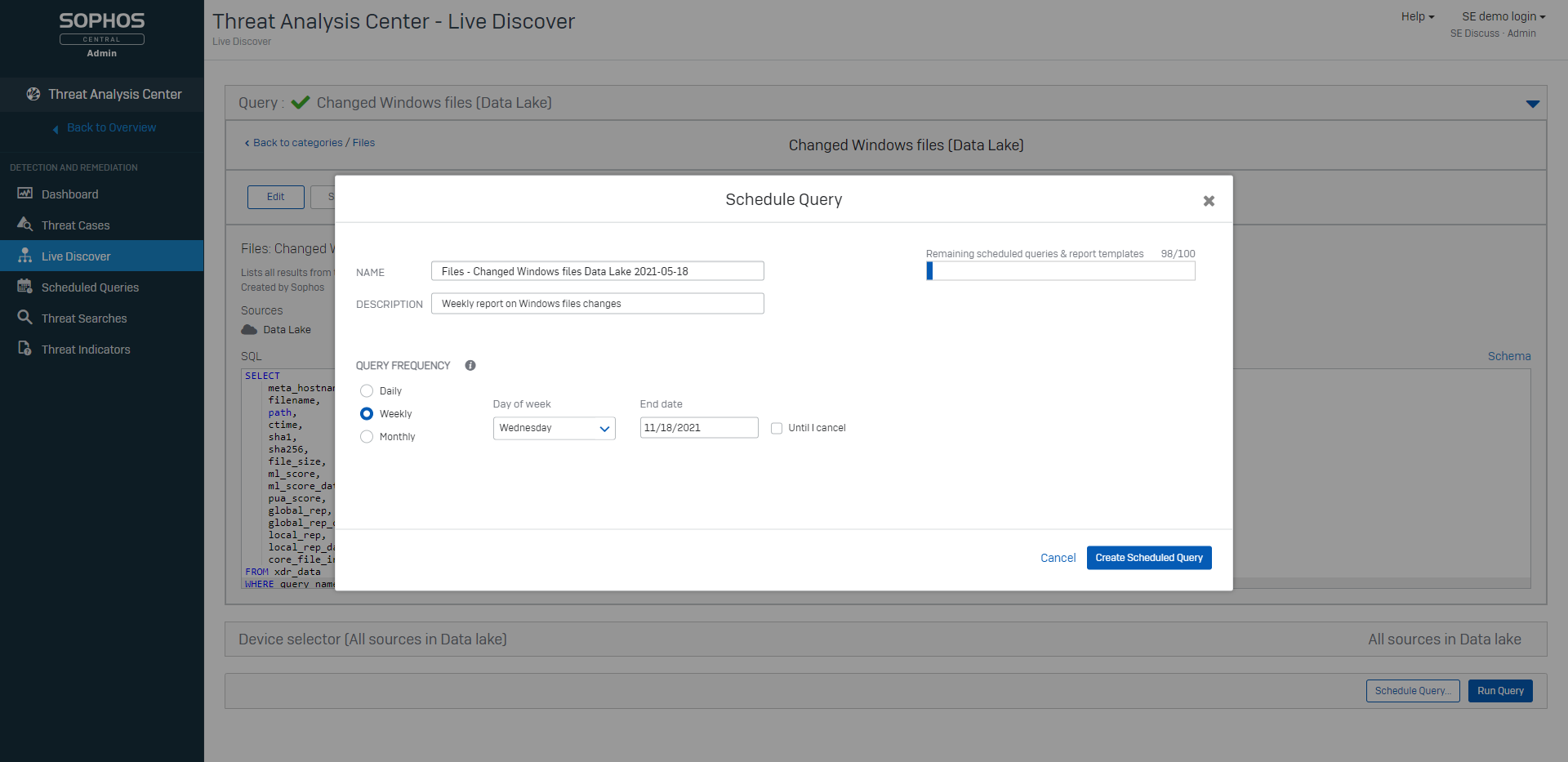
When the query has been successfully scheduled it will appear in your ‘Scheduled Queries’ list.
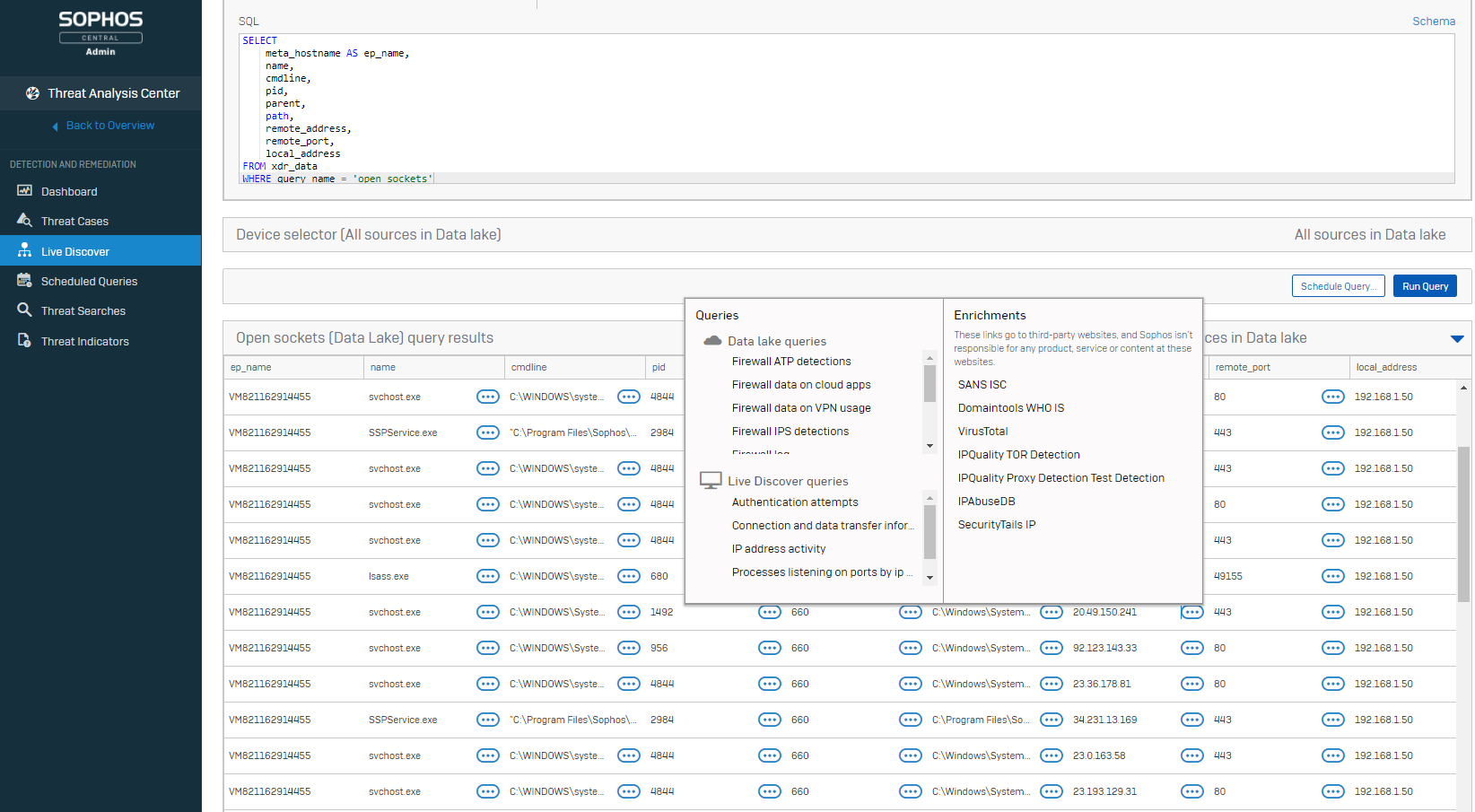
Enhanced usability
Work even faster with enhancements to workflows and pivoting. You’ll get to key information faster and be able to take actions and respond even more quickly.
Sophos XDR
We have also released Sophos XDR (Extended Detection and Response). Sophos XDR goes beyond endpoints and servers, pulling in rich Sophos Firewall and Sophos Email data with more XDR-enabled products coming soon.
Here are just a few Sophos XDR use cases:
| IT Operations | Threat Hunting |
| Identify unmanaged, guest, and IoT devices | Extend investigations to 30 days without bringing a device back online |
| Why is the office network connection slow? Which application is causing it? | Use ATP and IPS detections from the firewall to investigate suspect hosts |
| Look back 30 days for unusual activity on a missing or destroyed device | Compare email header information, SHAs, and other IoCs to identify malicious traffic to a domain |
To learn more about Sophos XDR please see this article.
Source: Sophos
[vc_row][vc_column width=”1/6″][/vc_column][vc_column column_width_percent=”100″ align_horizontal=”align_center” gutter_size=”3″ overlay_alpha=”50″ shift_x=”0″ shift_y=”0″ shift_y_down=”0″ z_index=”0″ medium_width=”0″ mobile_width=”0″ width=”2/3″][vc_custom_heading heading_semantic=”h1″ text_size=”h1″ text_height=”fontheight-578034″ text_color=”color-210407″]
Watch the complete online event BEYOND PRODUCTIVITY
[/vc_custom_heading][/vc_column][vc_column width=”1/6″][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_column_text]
A 90 minutes crash webinar where you will be presented with the Next Generation RMM, how to Unify People, Processes and Data in a Single Pane of Glass, and how to Protect Data and Keep your Business Running along with a complete end-to-end, multi-tenant password management solution for MSPs
[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_single_image media=”100922″ media_width_percent=”100″ alignment=”center” css_animation=”zoom-in” media_link=”url:http%3A%2F%2Fbit.ly%2FNSS-BEYOND-PRODUCTIVITY||target:%20_blank|”][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_separator sep_color=”color-150912″][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_custom_heading text_color=”color-122459″]
One Datto: Drive Revenue With Integrated Solutions
[/vc_custom_heading][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_column_text]
One Datto illustrates how integrated solutions increase efficiency and build MRR. In this video, we show how a fully integrated platform of best-in-class Continuity, SaaS protection, networking, RMM, and PSA solutions combine to streamline a response to a ransomware attack. The integrated platform reduces the number of steps to complete tasks, enabling you to quickly and efficiently return clients to production, grow your MRR with value added managed services, improve the efficiency of your service delivery, and protect your clients from data loss.
[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_single_image media=”100927″ media_width_percent=”100″ alignment=”center” css_animation=”zoom-in”][/vc_column][/vc_row][vc_row][vc_column width=”1/2″][vc_single_image media=”99810″ media_width_percent=”60″ alignment=”center”][vc_column_text]
Protect Data and Keep Business Running. Datto Unified Continuity covers all of your business continuity & disaster recovery needs. Protect servers, files, PCs, and SaaS applications. Datto works with MSPs to customize a solution tailored to you and your clients.
Datto enables you to be prosperous and secure with products designed specifically for MSPs. Datto is more than just a technology provider. Datto empowers you to implement and sell solutions that help you grow.[/vc_column_text][/vc_column][vc_column width=”1/2″][vc_single_image media=”100760″ media_width_percent=”60″ alignment=”center”][vc_column_text]
A complete end-to-end password management solution designed and developed by an MSP specifically for the needs and the ways that today’s MSPs work and support their customers.
The Password Boss password management solution brings industry leading password protection to MSPs for the first time. A perfect fit in your MSP service profile.[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_single_image media=”100828″ media_width_percent=”75″ alignment=”center” media_link=”|||”][/vc_column][/vc_row]
[vc_row][vc_column width=”1/6″][/vc_column][vc_column column_width_percent=”100″ align_horizontal=”align_center” gutter_size=”3″ overlay_alpha=”50″ shift_x=”0″ shift_y=”0″ shift_y_down=”0″ z_index=”0″ medium_width=”0″ mobile_width=”0″ width=”2/3″][vc_custom_heading heading_semantic=”h1″ text_size=”h1″ text_height=”fontheight-578034″ text_color=”color-210407″]
Watch the complete online event BEYOND PRODUCTIVITY
[/vc_custom_heading][/vc_column][vc_column width=”1/6″][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_column_text]
A 90 minutes crash webinar where you will be presented with the Next Generation RMM, how to Unify People, Processes and Data in a Single Pane of Glass, and how to Protect Data and Keep your Business Running along with a complete end-to-end, multi-tenant password management solution for MSPs
[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_single_image media=”100922″ media_width_percent=”100″ alignment=”center” css_animation=”zoom-in” media_link=”url:http%3A%2F%2Fbit.ly%2FNSS-BEYOND-PRODUCTIVITY||target:%20_blank|”][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_single_image media=”100828″ media_width_percent=”75″ alignment=”center” media_link=”url:http%3A%2F%2Fbit.ly%2FNSS-BEYOND-PRODUCTIVITY||target:%20_blank|”][/vc_column][/vc_row][vc_row][vc_column width=”1/2″][vc_single_image media=”99810″ media_width_percent=”60″ alignment=”center”][vc_column_text]
Protect Data and Keep Business Running. Datto Unified Continuity covers all of your business continuity & disaster recovery needs. Protect servers, files, PCs, and SaaS applications. Datto works with MSPs to customize a solution tailored to you and your clients.
Datto enables you to be prosperous and secure with products designed specifically for MSPs. Datto is more than just a technology provider. Datto empowers you to implement and sell solutions that help you grow.[/vc_column_text][/vc_column][vc_column width=”1/2″][vc_single_image media=”100760″ media_width_percent=”60″ alignment=”center”][vc_column_text]
A complete end-to-end password management solution designed and developed by an MSP specifically for the needs and the ways that today’s MSPs work and support their customers.
The Password Boss password management solution brings industry leading password protection to MSPs for the first time. A perfect fit in your MSP service profile.[/vc_column_text][/vc_column][/vc_row]
Autotask PSA is designed to drive efficiency, accountability, and the intelligence of managed service providers (MSPs) by unifying people, processes, and data to provide a singular view across their IT managed services business. The latest enhancements to Autotask PSA improve usability and add Document Manager and Knowledgebase features that increase technician accountability.
Additionally, MSPs who have integrated their Autotask PSA with Datto RMM now have the ability to click into their Datto RMM system directly into remote takeover of managed devices that need additional support.
Document Manager and Knowledgebase Enhancements
The past two releases added Document Manager capabilities within Autotask PSA to improve efficiency by providing quick and easy access to standardized documentation so technicians spend less time searching for answers. SSL Certificate and Domain Tracking capabilities were enabled to provide a single location for MSPs to manage and track expiring assets to help ensure they never miss a renewal.
Additionally, the latest Autotask release increases accountability of Document Manager and Knowledgebase users with revision, rollback, and approval features. Quickly identify when updates were made, and quickly select and restore to the desired version. Those with proper credentials can approve documents and Knowledgebase articles prior to publishing.
Account Management Module Modernized
Autotask PSA’s Account Management module, which provides a real-time view of the health of each account and allows sales teams to manage their sales pipeline by creating and tracking opportunities, has been revamped to reflect our new user experience. The intuitive Company pages now feature a configurable and tab-based UI to help improve account manager and sales rep efficiency and will provide a more cohesive experience with the other Autotask PSA modules.
 Project Task, Time, and Note Entry Usability Enhancements
Project Task, Time, and Note Entry Usability Enhancements
In addition to the Account Management pages getting a major facelift, Project Task, Time, and Note Entry have been updated significantly to improve user experience and efficiency. The integrated Time Entry enables users to quickly and accurately enter or edit time with an intuitive timeline view. The new rich text editor for Note Entry improves context, and enhances understanding of problems by providing a convenient way to stylize text with bold, italicize, underline choices, bulletize and number lists, and embed images.
 Autotask LiveMobile App Improvements
Autotask LiveMobile App Improvements
The Autotask LiveMobile App, which enables remote workers to access the Autotask PSA system even when they are away from their desks, has been enhanced, as well. Beyond just updating the look and feel, the latest updates to the native iOS and Android apps bring the full PSA ticket experience onto a mobile device for improved tech efficiency.
Looking for a PSA platform that helps grow your business by unifying Document Management, Service Desk, CRM, Procurement, Billing, and Reporting behind a single pane of glass? Learn more about Autotask PSA today.
Source: Datto
RMM stands for “remote monitoring and management.” Remote monitoring and management tools are a foundational technology for managed service providers (MSPs). Managing client endpoints and devices is a key tenant in a managed services business, and these tools give MSPs the ability to do so remotely.
What are the benefits of RMM tools?
RMM solutions are used by IT professionals to remotely monitor system status and manage processes without the requirement to physically be on site. With the right RMM tool, MSPs can do more with less–simplifying operations for the MSP while providing efficient service for the client.
Drive Efficiency and Automation into Service Delivery
By centralizing the management of client endpoints, MSPs can reduce costs and increase service delivery efficiency. From installing software to patch management remote monitoring and management software is designed to drive efficiency, scalability, usability, and affordability.
Scale the Business
For maximum uptime, consider a 100% cloud platform with no hardware to maintain. With a cloud-based RMM solution, MSPs can scale their endpoints with ease, whereas an on-premises solution may require upgrades and manual maintenance to grow with your business.
Build Value and Trust with Clients
With a robust remote monitoring and management solution, MSPs can remotely and proactively monitor and support clients with one-click access to endpoints, mitigating risk and anticipating issues before they occur. MSPs can also use their RMM tool to provide clients with valuable insights and reporting.
Unify With Your Operations Engine
MSPs live and breathe in a professional services automation (PSA) tool to deliver service to clients, manage tickets, and organize business operations. To run an efficient and effective managed services business, PSA and RMM tools are essential. So, it only makes sense that integrating them will save MSPs time from not having to switch from platform to platform to complete a task.
Datto RMM: Built for MSPs
Datto RMM is the platform of choice for thousands of MSPs around the world looking to reduce the operational overhead of delivering managed services.
- Comprehensive auditing: Get complete visibility of every device and pinpoint areas for action.
- Real-time monitoring: Implement system-wide monitoring with intelligent alerting, auto-response, and auto-resolution.
- Flexible reporting: Prove your value and help your customers make decisions with a wide array of reports.
- Built-in patch management: Automatically maintain every device with flexible, native OS and application patch update policies.
- Remote control and takeover: Provide instant support with one-click access to any of your managed devices.
What Makes Datto RMM Different
- Rapid pace of innovation: The Datto RMM product team pushes updates to once a month to improve user experience.
- Onboarding and ongoing optimization: Our implementation team is full of pros that specialize in helping MSPs adopt Datto RMM by providing ongoing support that’s unique to their business needs and use cases.
- One price, simple, and affordable: An affordable flat fee per device gives MSPs full visibility, management, and monitoring of every device under contract.
- Performance and security: Datto is 100% cloud-based and built to scale.
- Datto RMM integrations and open ecosystem: Native integrations with Autotask PSA, Datto Networking, and Unified Continuity solutions drive operational efficiency and greater profits for our MSP partners. We’re also committed to an open ecosystem for other MSP tools and technologies.
How to choose the right solution for your MSP business?
Take a look at our eBook, RMM Made MSPeasy, where we’re diving into what you should consider when selecting a solution. Plus, you’ll find advice from industry-leading MSPs on using RMM to increase operational efficiency and drive revenue.
Whether you are just getting started with managed services or are currently evaluating new software, this eBook is for you.
Source: Datto
[vc_row][vc_column][vc_column_text]
After the 2020 pandemic tipped our traditional way of work on its head, companies scrambled to support fully remote workers. But as the vaccine roll-out continues, many organizations are welcoming workers back to the office. However, that doesn’t mean all companies are planning to go back to exactly the same way things were before. BeyondTrust covers three focuses for SecOps in the era of remote / hybrid work…
[/vc_column_text][vc_button button_color=”color-210407″ size=”btn-lg” radius=”btn-round” border_width=”0″ link=”url:https%3A%2F%2Fwww.beyondtrust.com%2Fblog%2Fentry%2Fdispatches-from-anywhere-securing-the-next-wave-of-work%3Futm_source%3DNSS-NewsBlog%26utm_id%3DNSS-Greece||target:%20_blank|”]Read more here…[/vc_button][/vc_column][/vc_row]
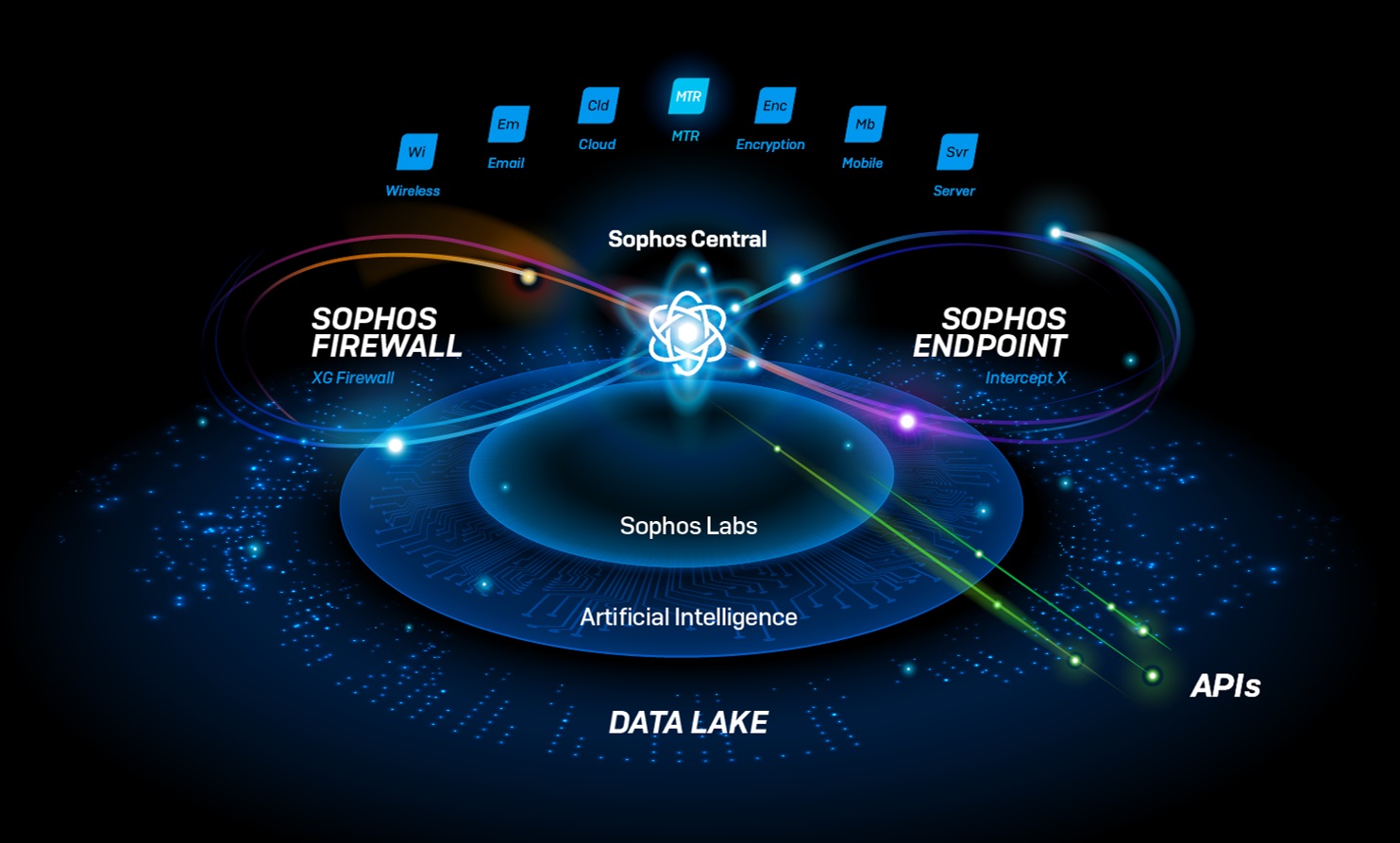
When we set out to build our extended detection and response (XDR) solution, we focused on a key mantra: if you want the best XDR, you need the best data.
Sophos XDR is driven by data. It delivers the most comprehensive and precise data across multiple dimensions for the most accurate threat detection, investigation, and response. This is achieved thanks to the scope of data, range of sources, and data quality.
Scope of data
Sophos XDR blends 90 days of rich, on-device endpoint and server data with 30 days of cross-product telemetry in our data lake. This provides the broadest and most in-depth, contextualized insights for both live and offline devices.
Why do you need both on-device data and data stored in a data lake? The two types of data complement each other, which is key to stopping stealthy, high-stakes attacks.
On-device data provides a live view of what’s happening right now on your endpoints and servers, plus an incredibly detailed historical record of activities for the last 90 days – far more detailed than a data lake would typically retain.
All key information and events are logged. This includes process information down to the thread level (starting, stopping, parent, child), changes to the registry, programs running, system events, and much, much more.
The data lake provides its own set of advantages, such as the ability to detect incidents by correlating information across your estate.
Crucially, it also allows users to query both online and offline devices – even those which may have been taken offline during an attack. However, data stored in a cloud repository is always historical and does not provide a real-time view.
The two data types work together. The data lake provides the 10,000-foot view and helps correlate events across your estate from both live and offline devices. From there, you can pivot to live running systems and access the industry’s richest on-device data set to see exactly what’s happening right now, or what happened in the last 90 days.
Blending on-device data with the information stored in the data lake ensures you get the broadest scope of data so you don’t miss a thing.
Data sources
Sophos XDR is the first and only XDR solution that synchronizes native endpoint, server, firewall, and email security – with mobile and cloud integrations coming soon.
This broad set of data sources goes well beyond endpoint and server visibility alone. Instead, you get the full picture when detecting and investigating incidents.
For example, you could use firewall data to identify suspicious traffic coming from an unmanaged endpoint or investigate a suspected phishing attack to see if there has been further traffic to a malicious domain.
All the data sources are integrated out of the box when you have Sophos XDR-enabled components. There’s no need to create your own custom infrastructure.
Quality of data
When conducting threat detection and response, having a lot of data is only part of the equation.
Because huge volumes of data can be overwhelming, you instead need high-quality data.
Sophos XDR has more high-quality data, which means we deliver stronger signals and less noise for better detection. This is because Sophos XDR is built on top of Intercept X, the world’s best endpoint protection.
Intercept X filters out a lot of the noise that ends up causing alert fatigue for analysts, allowing them to help focus on what’s truly important.
To further improve data quality, Sophos XDR provides additional context to put the data into perspective. This includes additional intelligence from SophosLabs and the Sophos AI team.
Source: Sophos
We are pleased to announce some exciting product updates, including the launch of Sophos XDR (Extended Detection and Response) and significant enhancements to Sophos EDR (Endpoint Detection and Response).
Introducing Sophos XDR
Sophos XDR goes beyond endpoints and servers, pulling in rich Sophos Firewall, Sophos Email, and other data sources.
This means you get even more detailed insight when performing threat hunting or IT operations tasks: both a broad, big picture view of your organization’s cybersecurity environment along with the ability to deep dive into areas of interest for granular detail. It’s the best of both worlds.
Here are just a few Sophos XDR use cases:
| IT Operations | Threat Hunting |
| Identify unmanaged, guest, and IoT devices | Extend investigations to 30 days without bringing a device back online |
| Why is the office network connection slow? Which application is causing it? | Use ATP and IPS detections from the firewall to investigate suspect hosts |
| Look back 30 days for unusual activity on a missing or destroyed device | Compare email header information, SHAs, and other IoCs to identify malicious traffic to a domain |
New to Extended Detection and Response (XDR)? We’ve put together a beginner’s guide to get you up to speed. Download your copy.
Offline Access with the Sophos Data Lake
A key component of both XDR and EDR, the Sophos Data Lake stores critical data from XDR- and EDR-enabled devices, including access to that data even when devices are offline.
For example, you can look back for unusual activity on a device that has been destroyed or taken without authorization. It’s an important part of cybersecurity visibility, giving your organization the ability to see the entire environment and quickly drill down to granular areas of interest.
Data retention periods are 7 days for EDR and 30 days for XDR. That’s in addition to the up-to-90 days of on-disk data stored on devices.
Sophos EDR keeps getting better
This release brings some of the most-requested features to Sophos EDR, making it even easier to ask and answer business-critical IT operations and threat hunting questions.
- Scheduled queries Have critical information waiting for you. You can schedule queries to run overnight so key data is ready for assessment. You’ll have the information you need to quickly perform threat hunting and IT operations tasks.
- Enhanced usability Work even faster with enhancements to workflows and pivoting. You’ll get to key information faster and be able to take actions and respond even more quickly.
To learn more about Sophos XDR and EDR please head over to Sophos.com/XDR and Sophos.com/EDR today.
Source: Sophos
[vc_row][vc_column][vc_column_text]
VPNs have their place, but that scope is getting smaller and smaller. Zero trust is more secure, reliable, and flexible, while also providing better performance than VPNs. If privileged users need access to remote systems, zero trust can protect systems better by providing the necessary checks, session monitoring, and analysis of log data at every step…
[/vc_column_text][vc_button button_color=”color-210407″ size=”btn-lg” radius=”btn-round” border_width=”0″ link=”url:https%3A%2F%2Fwww.beyondtrust.com%2Fblog%2Fentry%2Frethinking-remote-access-security-can-zero-trust-replace-vpns%3Futm_source%3DNSS-NewsBlog%26utm_id%3DNSS-Greece||target:%20_blank|”]Learn more on this on BeyondTrust’s blog[/vc_button][/vc_column][/vc_row]
We are thrilled to announce that for the 12th consecutive report, Sophos has been named a “Leader” in the Gartner Magic Quadrant for Endpoint Protection Platforms (EPP).
We are confident our placement is due to the combination of advanced protection, and broad endpoint detection and response (EDR) threat hunting and IT operations capabilities found in Intercept X.
In addition to a proven track record of stopping ransomware attacks and advanced threats, recent enhancements to EDR capabilities in Intercept X mean that organizations can use powerful SQL queries to answer critical IT operations and threat hunting questions. Pre-written queries with full customization and the ability to craft queries from scratch are included to support all use cases.
We continue to invest in both our protection and EDR capabilities, with multiple releases deployed over the past year. We recently announced Sophos XDR, which extends EDR visibility beyond endpoints and servers.
Intercept X Third Party Test Results
SE Labs
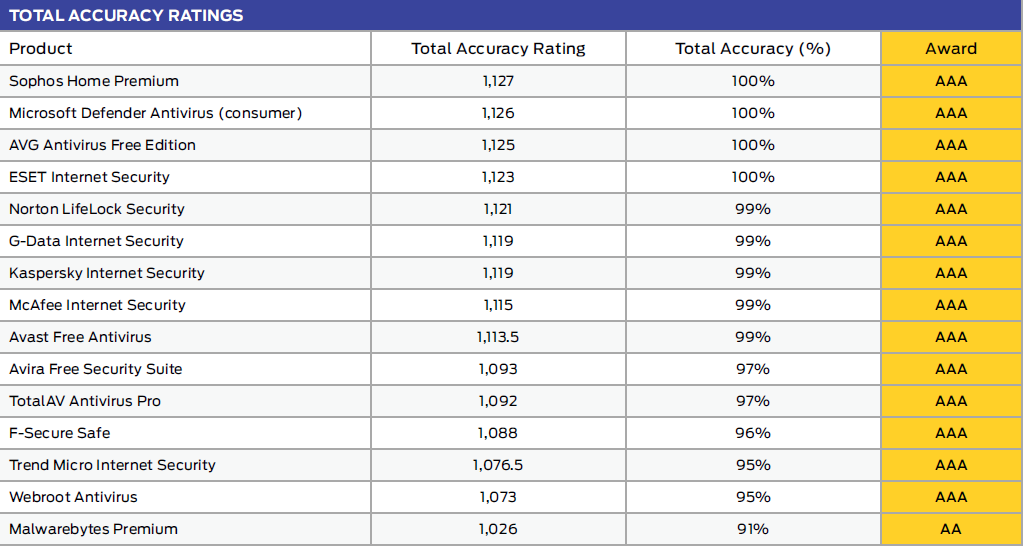
- AAA Rated for Enterprise – 100% total accuracy rating (Jan-Mar 2021)
- AAA Rated for SMB – 100% total accuracy rating (Jan-Mar 2021)
MRG Effitas
PC Magazine
SC Media
CRN 2020 Tech Innovators Awards
Gartner Peer Insights
- Intercept X Advanced with EDR has an average 12-month rating of 4.8 (out of 5.0) on Gartner Peer Insights
- Sophos MTR has an average 12-month rating of 4.8 (out of 5.0) on Gartner Peer Insights
Source: Sophos
With the latest update to Acunetix, we introduced a new feature called the target knowledge base. Every time you scan a target, Acunetix gathers and stores information about it. This information includes paths that make up the site structure, the location of forms and their inputs, parameters used by the web application, any APIs that are used, and the detected vulnerabilities.
Getting Better with Time
The idea behind the target knowledge base is to be able to reuse as much of this information as possible in subsequent scans to empower the Acunetix crawler. You can think of the crawler as an adventurer who is entering a maze and needs to check all available paths to reliably find his way out of the maze. In the same way that the adventurer would be much more efficient at completing his task if he had an updated map of the maze, the crawler becomes more thorough at building the site structure when it can use the target knowledge base.
With the target knowledge base, the scanner does not need to start every scan from zero. Instead, it gets a head start by using the list of URLs from the knowledge base. This is similar to supplying the scanner with an import file, which contains a list of URLs to populate the site structure before the crawler starts to work.
Leave No Spot Behind
While testing the target, Acunetix probes it by submitting various payload data values, formatted in a way that is designed to identify vulnerabilities. The way that the web application responds to the requests made by Acunetix may affect the thoroughness of each scan. Some scans may expose certain URLs while other scans may not, depending on circumstances.
With the target knowledge base, each subsequent scan goes beyond what the crawler discovers during that scan – it uses paths and locations accumulated during previous scans of the same target. This ensures that you can scan URLs that you cannot reach predictably or consistently using the regular crawl function.
In addition, many targets evolve over time as the developers add new features, change existing features, and remove functions. This means that, for example, a function that has been removed may no longer be reachable through any link or web page inside the target, but may still linger on the web server as an orphaned URL. Thanks to the target knowledge base, Acunetix can scan even these orphaned functions.
Reliable Vulnerability Verification and Self-Healing
Acunetix also stores information about all vulnerabilities identified during previous scans of the target and uses this information in subsequent scans of that target. This means that when you want to re-check whether the vulnerabilities are still there, the crawler does not need to identify them again because the scanner is aware of their possible existence.
Another nice feature is that the target knowledge base is self-healing. If you change a part of the site structure and some URLs no longer exist, the crawler will first attempt to reach all the previously stored URLs, and then remove the obsolete ones from the knowledge base. This means that even if you redesign the web application and you know that the previous site structure is no longer valid because of this redesign, a subsequent scan will automatically clean up and correct knowledge base data.
Target Knowledge Base Configuration
If for any reason you wish to temporarily run one or more scans without using the target knowledge base, you can change the settings for the target and disable the use of the knowledge base for any new scans that you launch. Then, you can enable it again to scan the regular version of the target.
You can also permanently delete the contents of the knowledge base and start accumulating new data for the target. To do this, simply expand the Advanced section of the Target Settings page and click the Delete knowledge base button in the Knowledge Base panel.
Source: Acunetix
Intercept X ranked #1 with a 100% total accuracy rating for enterprise, SMB, and consumer protection in three recent SE Labs tests.
Sophos is proud to announce that Sophos Intercept X achieved a 100% Total Accuracy Rating for enterprise, small business, and consumer protection in the SE Labs endpoint protection test report (Jan – Mar 2021). Whether you are protecting your employees at work or their families at home, you can take comfort knowing you are backed by the world’s best endpoint protection.
Intercept X’s unique combination of anti-ransomware technology, deep learning artificial intelligence, exploit prevention, and active adversary mitigations is built to stop the widest range of threats.
Additionally, Sophos Intercept X Advanced with EDR integrates powerful endpoint detection and response (EDR) with the industry’s top-rated endpoint protection. Built for both IT security operations and threat hunting, Intercept X detects and investigates suspicious activity with AI-driven analysis.
For those looking for help with threat detection and response Sophos Managed Threat Response (MTR) provides 24/7 threat hunting, detection, and response capabilities delivered by an expert team as a fully-managed service.
Sophos MTR fuses the protection technology of Intercept X with expert human analysis for improved threat hunting and detection, deeper investigation of alerts, and targeted actions to eliminate threats with speed and precision. Unlike other services, the Sophos MTR team goes beyond simply notifying you of attacks or suspicious behaviors and takes targeted actions on your behalf to neutralize even the most sophisticated and complex threats.
SE Labs is not alone in praising Intercept X. A list of other industry awards can be found here.
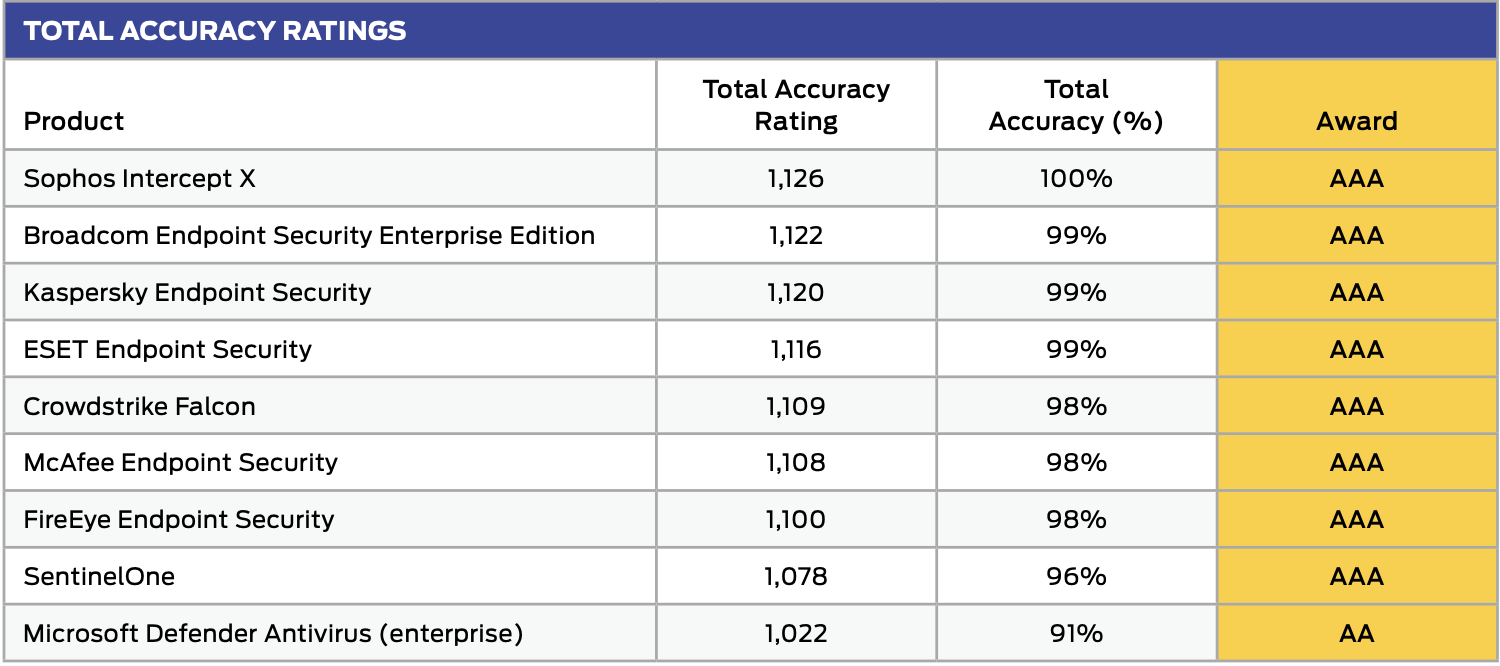
#1 for Enterprise Protection
Sophos Intercept X was the only product tested to achieve a 100% total accuracy rate, once again earning a AAA rating from SE Labs. You can view the full enterprise test results here.
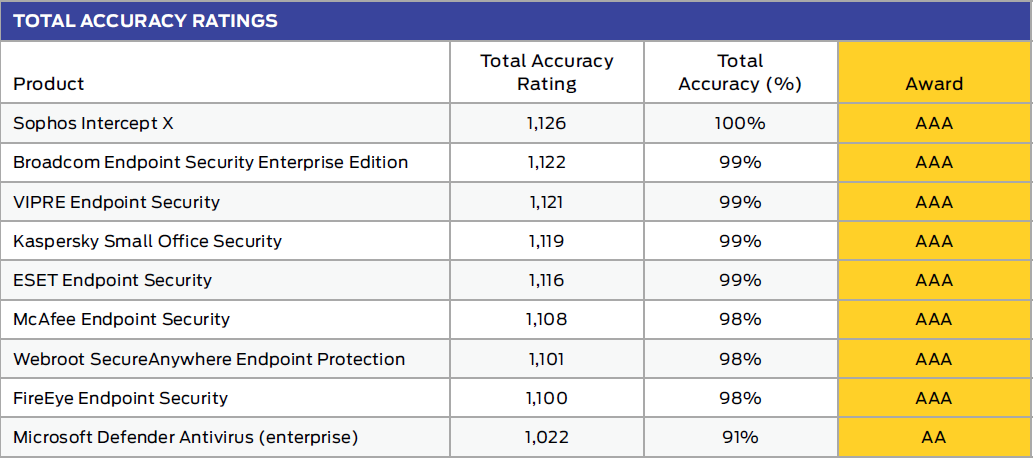
#1 for SMB Protection
In the small business report Intercept X showed why it was the winner of SE Labs’ Small Business Endpoint product of the year in 2020 and 2019. As it did in the enterprise test, Intercept X also ranked first with a 100% total accuracy rate. You can view the full SMB test results here.
#1 for Consumer Protection
The same malware that attacks Fortune 500 companies attacks private users, too. Sophos Home uses the same award-winning security features that keep those companies safe. You can view the full consumer test results here.
Try Intercept X and Sophos Home for free
Testing the powerful features in Intercept X couldn’t be more straightforward. Sign up today for a free 30-day trial of the award-winning protection and EDR functionality, or activate an instant online demo.
Looking for protection for your home devices? Start a free trial of Sophos Home.
Source: Sophos
[vc_row][vc_column][vc_column_text]Ransomware surged in 2020 and shows no signs of relenting thus far in 2021. As an industry, we are failing to keep up with attackers, who are adept at quickly evolving to target vulnerabilities and gaps created by digital transformation, which has quickly accelerated over the last year.[/vc_column_text][vc_button button_color=”color-210407″ size=”btn-lg” radius=”btn-round” border_width=”0″ link=”url:https%3A%2F%2Fwww.beyondtrust.com%2Fblog%2Fentry%2Fransomware-is-increasing-evolving-how-do-we-keep-up%3Futm_source%3DNSS-NewsBlog%26utm_id%3DNSS-Greece||target:%20_blank|”]Get more insights on our partner’s blog[/vc_button][/vc_column][/vc_row]
The State of Ransomware 2021 report provides fresh new insights into the frequency and impact of ransomware.
Based on findings from an independent survey of 5,400 IT managers in mid-sized organizations in 30 countries across the globe, it reveals that 37% of organizations experienced a ransomware attack in the last 12 months – down from 51% in 2020.
Furthermore, fewer organizations suffered data encryption as the result of a significant attack – down from 73% in 2020 to 54% in 2021. So far, so good.
However while the number of organizations being hit by ransomware has dropped since last year, the financial impact of an attack has more than doubled, increasing from US$761,106 in 2020 to US$1.85 million in 2021. This is likely due, in part, to the move by attackers to more advanced and complex targeted attacks that are harder to recover from.
Paying up doesn’t pay off
The number of organizations paying the ransom to get their data back increased over the last year, from 26% of organizations whose data was encrypted in 2020 to 32% in 2021.
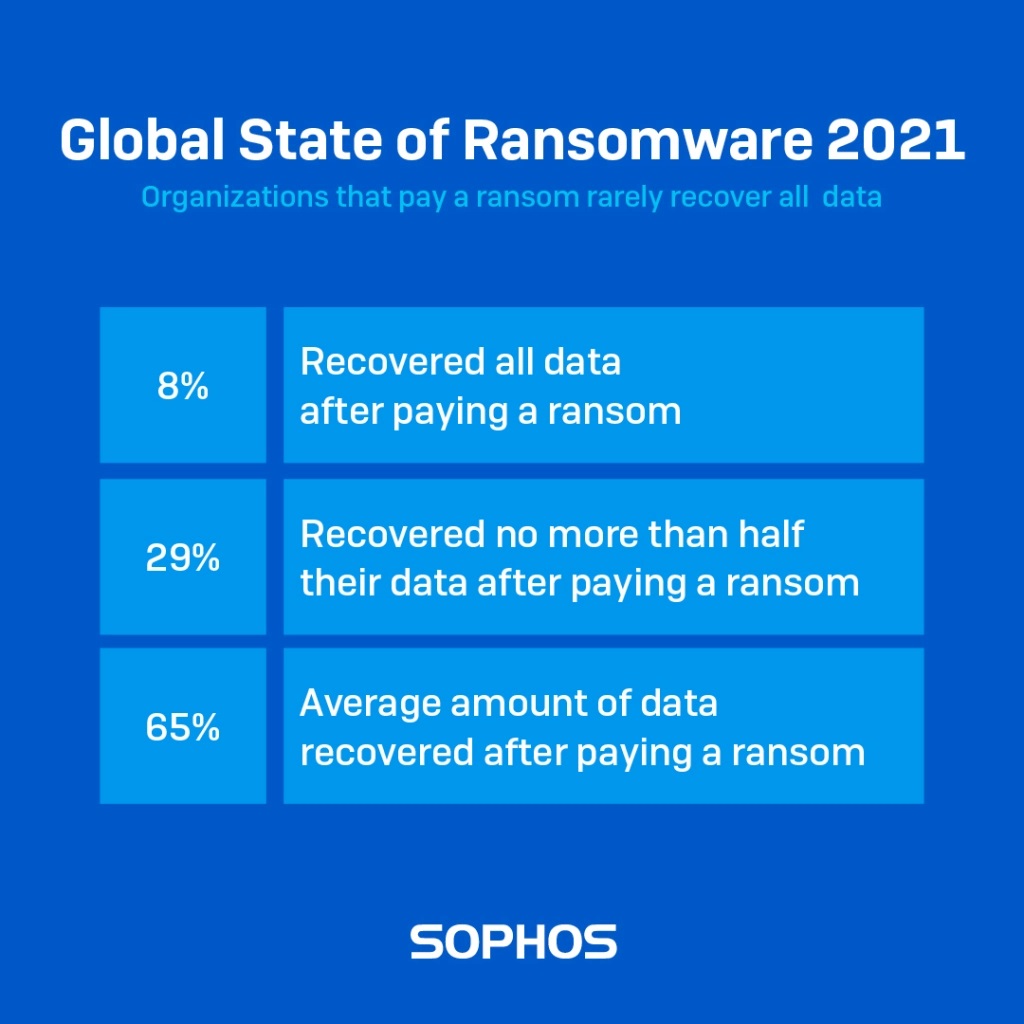
However what adversaries fail to mention in their ransom notes is that your likelihood of getting all your data back after paying up is very slim: fewer than one in ten (8%) got back all their encrypted files.
In fact, on average, organizations that paid the ransom got back only 65% of their data, with 29% getting back no more than half their data. When it comes to ransomware, it doesn’t pay to pay.
The survey also revealed that extortion without encryption is on the rise. 7% of respondents that were hit by ransomware said that their data was not encrypted, but they were held to ransom anyway, possibly because the attackers had managed to steal their information. In 2020, this figure was just 3%.
Winners and losers
The report provides insight into how different countries and sectors have been affected by ransomware over the last year, including:
- India reported the most ransomware attacks with 68% of respondents saying that they were hit last year. Conversely Poland (13%) and Japan (15%) reported the lowest levels of attack.
- Geographical neighbors Austria and the Czech Republic are poles apart when it comes to ransomware recovery costs: Austrian respondents reported the highest recovery cost of all countries surveyed while Czech respondents reported the lowest.
- Retail and education (both 44%) were the sectors that reported the highest levels of attack.
- Local government is the sector most likely to have their data encrypted in a ransomware attack (69%).
Get the full survey findings
Read the State of Ransomware 2021 to get the full findings from the survey. It includes best practice advice from Sophos defenders to help you stay safe from ransomware.
Source: Sophos
Every year, Acunetix brings you an analysis of the most common web security vulnerabilities and network perimeter vulnerabilities. Our annual Web Application Vulnerability Report (now part of the Invicti AppSec Indicator) is based on real data taken from Acunetix Online. We randomly select websites and web applications scanned using our software, anonymize them, and perform statistical analysis. Here are our cybersecurity findings for this year.
The State of Web Application Security
The 2021 report is, unfortunately, quite pessimistic. The slow improvement trend from the previous few years has reversed. Several high and medium severity vulnerabilities are now more common in 2021 than in 2020, including some serious security risks that may lead to the loss of sensitive information.
We believe that this trend reversal is caused by the COVID-19 pandemic. The pandemic has caused most companies to embrace remote work and therefore many security leaders decided to focus on endpoint security, operating system security, and anti-malware efforts to combat the onset of phishing, malicious sites, and malicious code. Therefore, not enough resources were available to improve web security. Instead of investing in thorough processes, businesses went for quick and imperfect solutions, often based on misconfigured web application firewalls (WAF).
In our opinion, such decisions could have severe consequences in the future. As a result of the shift to remote, web application importance increased. To improve the efficiency of remote work, many businesses made their processes available through web browsers, using web applications and APIs. This made it possible for attackers to attempt to gain access to company data through web pages and, as a consequence, could lead to major data breaches.
In a recent study from Forrester Research, The State of Application Security 2021, web applications such as SQL injections, cross-site scripting, or remote file inclusion comprised the most frequently-cited method of attack. The study surveyed 480 global security decision-makers with network, data center, app security, or security ops responsibilities who experienced an external attack in 2020.
The Developer Crisis
With the shift to remote, web software development is also facing more problems, not just the lack of resources. Even before the age of remote work, developers often found it difficult to write secure code, made common functionality mistakes, skipped validation, trusted user input from untrusted sources, passed untrusted data directly to SQL queries, used insecure user session IDs and session management mechanisms, etc.
New remote work environments make it even more difficult for developers to maintain application code security due to communication challenges. If the security focus is shifted away from web application security solutions, developers also lack tools and schooling to improve their security-related skills. If they had access to professional web application security solutions, they would receive information not only about the existence of issues but also guides that would teach them how to avoid such errors in the future. Without such tools, developers are just going to create more and more vulnerabilities.
Vulnerabilities at a Glance
Our report focuses on common vulnerabilities and security misconfigurations – those that you also find in the Open Web Application Security Project – OWASP Top 10 list. We found fewer SQL Injection flaws and directory traversal (path traversal) issues but many other serious issues were more common or just as common as the year before. This includes remote code execution (code injection), cross-site scripting (XSS) issues, vulnerable JavaScript libraries, WordPress vulnerabilities, server-side request forgery (SSRF), host header injection attacks, and more.
The report also contains data on other known vulnerabilities and software security issues including buffer overflow, denial-of-service and DDoS vulnerabilities, issues related to access control and broken authentication such as weak passwords, web server misconfigurations, and more. In the case of all these issues, the trend is similar: you can see a slight increase in numbers.
Beware of the Consequences
In conclusion, the 2021 Web Application Vulnerability Report again emphasizes the importance of web vulnerability scanning, especially in the age of COVID-19 and remote work. Issues discovered by scanners such as Acunetix can have serious consequences and lead to server-side sensitive data exposure including user account compromise, credit card information theft, security breaches of back-end databases, as well as client-side attacks on victims’ browsers.
Read the full report.
Source: Acunetix
Sophos launched the first of the new XGS Series next-gen firewall appliances with Sophos Firewall OS version 18.5.
For network admins, this completely re-engineered hardware platform finally takes a common dilemma off the table: how to scale up protection for today’s highly diverse, distributed, and encrypted networks without throttling network performance.
Coupled with a highly attractive price, the new XGS Series is guaranteed to reshuffle the deck in the network firewall space.
Here are just three key highlights of this new release.
Dual processor architecture – powered by Xstream
Every XGS Series appliance has two hearts beating at its core: a high-performance multi-core x86 CPU, and an Xstream Flow processor to intelligently accelerate applications by offloading security-verified and trusted traffic to the FastPath.
This architecture allows us to retain the same flexibility to extend and scale protection as purely x86-based firewalls while also providing a performance boost that’s unhampered by the limitations of some legacy platform designs.
For example, with the programmable Xstream Flow processors, we can extend the offload capabilities in future software releases, providing additional performance improvements without changing the hardware.
Protection and performance
As much as we like to talk about speeds and feeds in the firewall space, the additional performance headroom in the XGS Series is there for a purpose: protection.
With about 90% of network traffic encrypted (source: Google Transparency Report) and almost 50% of malware using TLS to avoid detection (source: SophosLabs), organizations are leaving huge blind spots in their network visibility by not activating TLS inspection.
Just going by our own telemetry, about 90% of organizations don’t have TLS inspection activated on their firewalls. Even if we take into account that some of those may have separate solutions doing TLS inspection, it’s likely to be the minority rather than the majority. And aside from the security risk that poses, it’s pretty hard to create a policy for traffic that shows as “general” or “unknown”.
Before you all scream, “but TLS inspection breaks the internet,” Sophos Firewall includes native support for TLS 1.3 and provides a user interface which clearly shows if traffic has caused issues and how many users were affected. With just a couple of clicks, you can exclude problematic sites and applications without reverting to a less-than-adequate level of protection.
 We’ve got the edge
We’ve got the edge
The XGS Series includes multiple form factors that beat the all-important price per protected Mbps of many competitive models.
XGS Series appliances are equipped with high-speed interfaces to meet the diverse connectivity requirements of businesses large and small. In addition to the built-in copper, fiber, and a range of other ports on every model, add-on modules provide the flexibility to tailor your device connectivity to your unique environment – both today and in the future.
The XGS Series integrates further with edge infrastructure devices such as APX access points and our SD-RED Remote Ethernet Devices. With cloud-managed Zero-Trust Network Access and access layer network switches coming later this year, we’re bringing your network security to every edge.
Sophos Firewall OS v18.5
The new appliances come with the latest v18.5 software release, which not only provides support for the new hardware but also includes all the 18.x maintenance releases – many new capabilities and security improvements – since the v18 release.
For further information about Sophos Firewall and the XGS Series or to request a quote visit Sophos.com/Firewall or Sophos.com/Compare-XGS.
Source: Sophos