News
Jan
Bolstered Channel Team
Sophos has recently strengthened its channel team with the appointments of Kendra Krause, Americas channel chief and Karen Delaney, Australia & New Zealand channel chief.
Prior to Sophos, Krause served most recently as Fortinet’s Channel Sales and Operations vice president. She previously served in channel sales and marketing roles at SonicWall, WatchGuard and CDW. Delaney spearheaded channel strategies at IBM, Acer and Dell/SonicWALL. Since joining the company, she has played an integral part in bringing Distribution Central and Connector Systems onboard as Sophos’ first distribution partners in Australia and New Zealand.
Channel Honors
Sophos has received considerable recognition for both its channel team and channel program. Included among this year’s honors:
- CRN UK’s Channel Sales & Marketing Award—The Sophos Partner Program was declared “best in the UK”. This award recognizes and rewards the achievements of those individuals and teams responsible for making the UK IT channel so successful.
- CRN’s 2013 Top Women of the Channel—Several Sophos’ channel leaders were among the honorees: Kendra Krause, vice president of Americas channel sales, Amy Gelpey, senior channel marketing manager, and Regina Vignone, director of sales.
- CRN’s Power 100 Most Powerful Women of the Channel—Kendra Krause was among the elite list of executives recognized for their channel achievements.
- CRN’s 2013 5-Star Partner Rating—The 5-Star Partner Program rating recognizes an elite subset of Partner Program Guide vendors that give solution providers the best partnering elements in their channel programs.
- CDW—Sophos was named Sapphire Partner of the Year for 2012; Sophos was one of CDW’s fastest-growing partners of the year.
Key Channel Recognition for Sophos UTM
The company was also highlighted in the 2013 CRN Annual Report Card (ARC). This prestigious study is considered the definitive benchmark for measuring excellence in the IT Channel community and recognizes the top-rated vendor partners in the industry. Sophos was given the highest honors for product innovation in the Network Security Appliances category for its unified threat management (UTM) solution, Sophos UTM. Winners were announced live at an awards reception on Tuesday, August 20, 2013, at the XChange 2013 event in Washington, D.C.
“At Sophos, every year is the year of the partner, but this year in particular has truly demonstrated our ‘channel-first’ commitment—from hosting the largest partner conferences in our history to a game-changing new MSP program, our focus is our channel,” said Mike Valentine, senior vice president, worldwide sales, Sophos. “We offer partners the most complete IT security value proposition—proven and award-winning security solutions that are simple to use, combined with the industry’s most powerful channel program. And with an aggressive roadmap that features an impressive array of offerings, we’re very excited about delivering partners even more value in the coming months to help them grow.”
To learn more about the Sophos Partner Program, please click here or visit http://www.sophos.com/en-us/partners.aspx.
Jan
Increased migration to virtual servers and the ever-growing threat of attack on critical data are presenting new challenges to IT professionals, as they look to maintain high performance and density of servers, without compromising on security. Sophos Server Protection addresses these challenges by integrating agentless antivirus for vShield and full antivirus clients for Windows, Linux, Mac and UNIX into one centrally managed product.
“Servers need the best protection against malware, but managing that protection while maintaining server performance across a diverse environment has inevitably increased complexity and demands on time,” said John Shaw, vice president of product management, Sophos. “We’ve delivered on what matters – server performance and security. Sophos Server Protection provides a single, easy to use management console to assign policies, view alerts and generate reports across platforms. Even licensing, often the bane of IT professionals, is straightforward: one server, one license, any platform.”
Standalone and virtual systems use fewer resources with Sophos Server Protection than with conventional antivirus products. Agentless scanning via vShield Endpoint prevents scan and update storms, automatically protecting every Windows virtual machine on the host through a centralized virtual security appliance. Systems without vShield benefit from a full featured client optimized for performance. Advanced features, including HIPS, application control, and device control, are also included for select platforms.
Sophos Server Protection supports a broad range of server and virtualization platforms, including Windows, Linux, UNIX, Mac, Hyper-V, vSphere/ESX/ESXi and XenServer. It provides proven protection against known and unknown threats, supported by real-time communication with SophosLabs. The Windows client offers additional layers of security, including HIPS, application control and patch assessment.
“Sophos Server Protection is server security made simple, because at Sophos we believe good security shouldn’t have to require the undivided attention of the IT team to make it work. Sophos Server Protection secures your business’s critical assets, without sacrificing performance or adding unnecessary complexity,” concluded Shaw.
Sophos Server Protection will be showcased at VMworld, which takes place in San Francisco between August 25 and 29. Sophos is a VMware Elite Technology Alliance Partner.
Υou can read the original article here.
Jan
One risk is that attackers will have the advantage over defenders who choose to run Windows XP because attackers will likely have more information about vulnerabilities in Windows XP than defenders. The problem is, of course, that once patches stop being provided for newly-discovered vulnerabilities, any problems that are found for more recent versions may well be backwards-compatible with XP. As details of these issues will be widely publicised, for very good reasons, there’s bound to be plenty of research going on into which ones can be used to penetrate the systems of anyone still clinging on to XP. Indeed, some people have already speculated that the bad guys will soon be stockpiling newly-found bugs until after the patch deadline, building up an arsenal of woes to unleash on those too lazy, poor, or stuck in their ways to upgrade.
Once the April 2014 deadline has passed, the world of Windows XP will be a perpetual zero-day, with no hope of relief from danger. It’s clearly in Microsoft’s interest to spread maximum fear, to squeeze as much revenue as they can out of Windows users who will have to pay to step up to Windows 7 or 8. But their warnings do carry considerable weight. In operating system terms, XP is pretty ancient, having been released in 2001 and reaching the end of its standard back in 2009. When the five-year extended support phase ends the platform will have very nearly reached its teens. It remains remarkably popular though, with the best available stats putting it on anywhere from 13 to 30% of systems browsing the web – well overtaken by Windows 7 nowadays, but still streets ahead of Windows 8. Its stability, simplicity and familiarity will make it hard to dislodge from a huge residual user base.
This has led to some speculation that Microsoft might relent and extend the support period further, but this seems unlikely. As Rains also points out in his blog piece, even with regular patching, the security provisions in XP just don’t cut it any more, leaving its users open to all sorts of dangers they would be immune from out-of-the-box with less creaky platforms.
You can read the original article here.
Jan
An equally alarming industry statistic, users not running the most recent version of Android (comprising more than 90 percent of active users) are vulnerable to known exploits, resulting in a more than 600 percent increase in Android malware infections.
In order to keep up with and prevent these risks, Sophos has introduced the latest version of its free Android security app, Sophos Mobile Security 3.0, its full-featured mobile securityand anti-virus application.
What’s New in Sophos Mobile Security 3.0
- Application protection: Protects the start of selected applications with a password, meaning you can let others use your phone without risking your corporate data security. You can protect your settings or Google Play app and any other mobile application.
- Faster Scanning: Significantly improves scan speed by leveraging the power of multi- core phones
- Web Protection (now included in free version): Blocks access to malicious or phishing websites, so you can access the Internet worry-free
“If Android malware risks weren’t enough, Android device loss and theft are an enormous issue, especially considering that more than 100 cell phones are lost or stolen every minute just in the US alone,” said Thomas Lippert, senior product manager, mobile, Sophos. “Mobile malware leads to data loss and unexpected cost issues, while actual device loss and theft leads to potentially much worse. Either way, it’s imperative for users to ensure their devices are protected. And we’re providing this protection—for free.”
Sophos Mobile Security is offered for free in Google Play: https://play.google.com/store/apps/details?id=com.sophos.smsec. Optionally, Sophos Mobile Security can integrate into the company’s flagship mobile device management and security solution, Sophos Mobile Control, providing full central management and integration into the compliance enforcement engine. For more information about Sophos’ mobile offerings, please visit:http://www.sophos.com/en-us/products/mobile.aspx.
Jan
Sophos currently offers an optimized AMI that is compatible with AWS cloud services. With this new hourly-based model, customers are able to take advantage of the many scaling, redundancy and elasticity features offered by AWS. Put simply, this approach lets customers access and securely defend their cloud resources with a solution optimized for the AWS environment.
“With AWS Marketplace, businesses can find, buy and deploy software that is optimized for Amazon EC2, allowing them to focus on delivering business results faster and at a lower cost,” said Sajai Krishnan, GM, AWS Marketplace. “We’re excited to add the Sophos UTM to AWS Marketplace, as we believe its new on-demand hourly pricing allows customers to utilize this advanced network security solution with the elasticity and ease-of-use they want in the cloud.“
“As a long-standing security provider, we know about the many benefits that Amazon Web Services provides, especially to SMBs that have adopted the cloud,” said Angelo Comazzetto, Senior Product Manager, Sophos. “We pride ourselves on developing complete security offerings that are simple to use, and with this offering, companies can better defend their cloud security resources with layers of security provided by Sophos UTM. We are excited to enable this unique offering in the AWS Marketplace.”
For additional information on Sophos’ UTM offerings, please click here.
But those signals were not authentic, and the ship was not on course. The signals were in fact being sent from the White Rose’s upper deck by University of Texas/Cockrell School of Engineering graduate students Jahshan Bhatti and Ken Pesyna. A team from the school had been invited aboard while the White Rose sailed from Monaco to Rhodes, Greece, on the Mediterranean Sea. Using a blue box about the size of a briefcase, the duo spoofed the ship’s GPS signals, sending counterfeit signals that slowly, subtly overpowered the authentic GPS signals until the ship ultimately came under their control.
If this sounds familiar, it’s because students from this engineering school did the same thing to a drone last year. In May 2012, the engineering students tried out their $1,000 spoofer, which they had cobbled together in response to a dare from the US Department of Homeland Security (DHS). Under the direction of Assistant Professor Todd Humphreys, who is now working for the Department of Aerospace Engineering and Engineering Mechanics, the students last spring managed to hack and hijack a drone with what Humphreys at the time said was the most advanced spoofing device ever.

Both the drone and yacht hijackings were designed to shed light on the perils of navigation attacks, serving as evidence that spoofing is a serious threat to marine vessels and other forms of transportation. In plain English, that means that hackers can send drones smashing, say, into our skulls.
After the students had gained control of the ship’s navigation system, the team planned to coerce the ship onto a new course with subtle maneuvers that positioned the yacht a few degrees off its original course. When the ship’s navigation system detected the location discrepancy, the crew corrected the course – at least, they thought they did. In reality, their course corrections were setting the ship slightly off its course line. Watch a video about the attack here.
You can read the original article, here.
Instead of just reinstalling your favourite apps and starting afresh, your new device will know how to get online straight away, how to get into your Twitter account, and how many Angry Birds levels you haven’t conquered yet. Clearly, Google keeps a raft of configuration data on your behalf, because if you have the option enabled and then decide to turn it off you get this dialog: So how risky is this option? It’s not risky in the sense, for example, of the recent flaw in the Tumblr app on iOS. There, Tumblr forgot to secure the actual transmission of personally identifiable information (PII), such as your password.
That meant that crooks at a coffee shop, for example, might easily be able to sniff out and extract your Tumblr password. The Android issue is more subtle: the data is encrypted in transit, and Google (for all we know) probably stores it encrypted at the other end. But it’s not encrypted in the sense of being inaccessible to anyone except you. That’s obvious because, you can recover your data from Google even after you’ve wiped (or lost) your device, or changed your Google account password. In other words, Google can unilaterally recover the plaintext of your Wi-Fi passwords, precisely so it can return those passwords to you quickly and conveniently even if you forget your device password and have to start over. That’s just the sort of convenience which many users will trade against security. So, let’s say some Three Letter Agency were to use some prismatic techqniue to acquire those Wi-Fi passwords from Google. Is that likely? If so, would it be bad? I have to say that it probably would be, if only because the list of Wi-Fi networks and passwords on your device is most likely much more extensive than just your own network in your own home.

You’d effectively be helping to built a list of passwords to go with the already-existing and extensive maps of Wi-Fi access points built up over years, both by Google and others. You probably don’t want to help anyone, friend or foe, to do that. The solution is to encrypt everything “for your eyes only” before you back it up anywhere, especially into the cloud. And the problem with that is it’s not quite as convenient, not least because there’s no password-free way to recover that backed-up data, for example if you forget your password. That’s the dilemma we all face. Are you prepared to accept a digital equivalent of locking your keys in the car forever (for example if you forget your full-disk encryption password and didn’t save the recovery key)? Or would you prefer to have what amounts to a backdoor to your own, or worse still, to other people’s, personal information? What do you think?
You can read the original article, here.
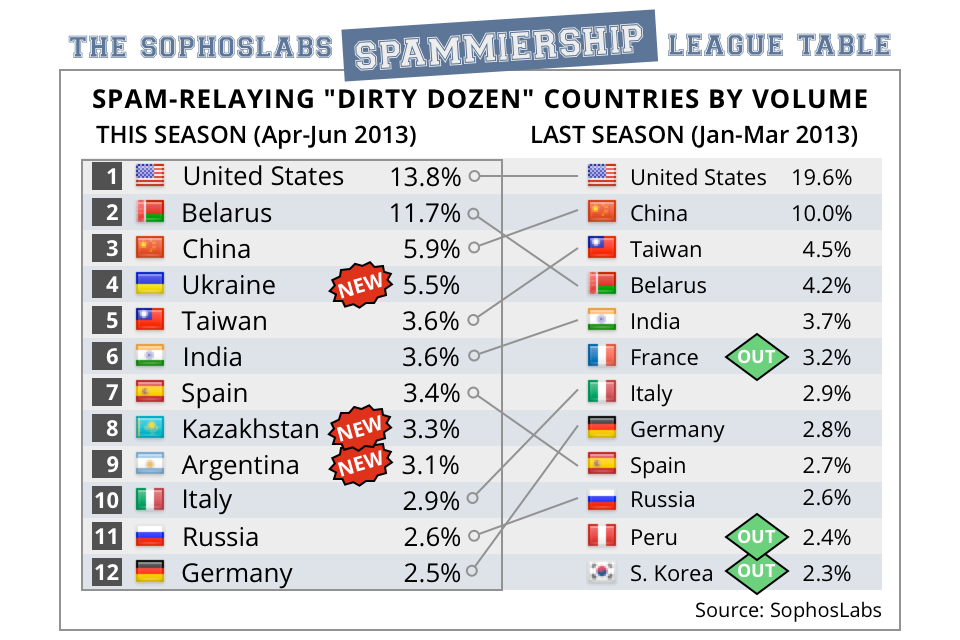
Likewise, the three countries that took their place in the top flight all came up from the 13-24 range. And, just like in your favourite football league, the majority of the high-flyers stayed put at the top. But is it so surprising that the USA is the Man United of the SPAMMIERSHIP, “winning” as often as not, or that China and India are often found near the top? With more than a billion people each and a thirstily-increasing demand for internet access in both countries, where else would you expect to see China and India except in the Dirty Dozen?
Welcome, then, to the SophosLabs SPAMMIERSHIP League Table:
And with more than 300 million people and the lion’s share of the world’s internet connectivity, where else would you expect to see the USA than leading the pack outright? What, then, if we scale the scores up or down in proportion to each country’s population? Now things get interesting, becase a rather different story emerges:

Half of the volume-based culprits are gone, and countries that would usually fly under the radar when measured on spamming volume alone – like Luxembourg and Singapore – suddenly burst onto the scene. Don’t be surprised. This doesn’t mean that usually law-abiding Singapore has turned into a seething swamp of spam-related cybercriminality. Remember that although the Dirty Dozen denotes the extent to which a country’s computers are used for delivering spam, it doesn’t tell us where the spammers themselves are located.
That’s because most spam is sent indirectly these days, especially if it is overtly malevolent, such as:
- Phishing emails. These try to lure you into entering passwords into mock-ups of a real site such as your bank or your webmail account.
- Malware links. These urge you to click links that put you directly in harm’s way by taking your browser to hacked websites.
- Malware deliveries. These use false pretences, such as fake invoices, to trick you into opening infected attachments.
- Identity theft. These invite you to reply with personally identifiable information, often by claiming to offer work from home opportunities.
- Investment scams. These talk up investment plans that are at best unregulated and at worst completely fraudulent.
- Advance fee fraud. These promise wealth or romance, but there are all sorts of fees, bribes and payments to hand over first.
If the crooks behind this sort of cybercrime were to use their own computers, they’d never be able to send the volume of spam they’d like. Also, using their own computers would lead law enforcement to their digital doorsteps. Instead, cybercriminals rely heavily on bots, also known zombies: innocent users’ computers that are infected with malware that regularly calls home to download instructions on what to do next. Those instructions may say something such as “here is a boilerplate email message, and here is a list of email addresses – send a copy to everyone on it.” So, if your country is in the Dirty Dozen, it almost certainly has a much-higher-than-average number of unprotected computers that are actively infected with malware. And if a cybercriminal can secretly tell your computer to send spam to 1000 people you’ve never heard of – leaving you to argue with your ISP why you shouldn’t be thrown off line for antisocial behaviour – then ask yourself this: “What else could he get up to on my account?” In short, the SPAMMIERSHIP League Tables are meant as a light-hearted way of reminding us all of one very serious aspect of computer security: namely that if you put yourself in harm’s way, you’ll probably end up harming lots of other people, too. In other words, getting serious about computer security is the easiest sort of altruism: by protecting yourself, you help to protect everyone else at the same time.
You can read the original article, here.
One of Negobot’s creators, Dr. Carlos Laorden, told the BBC that past chat bots have tended to be too predictable: “Their behaviour and interest in a conversation are flat, which is a problem when attempting to detect untrustworthy targets like paedophiles.” The most innovative aspect of Negobot may be a key differentiator that makes it appear more lifelike: namely, the incorporation of the advanced decision-making strategies used in game theory. In a paper about their creation, the researchers describe how they’ve taught the robot to consider a conversation itself as a game.
For example, the bot identifies the best strategies to achieve its goal in what its programmers have taught it to understand as a competitive game. Negobot’s goal is to collect the information that can help to determine if a subject involved in a conversation has paedophile tendencies, all the while maintaining a convincing, kid-like prattle, sprinkled with slang and misspellings, so the subject doesn’t get suspicious. Negobot keeps track of its conversations with all users, both for future references and to keep a record that could be sent to the authorities if, in fact, the subject is determined to be a paedophile.
The conversation starts out neutral. The bot gives off only brief, trivial information, including name, age, gender and hometown. If the subject wants to keep talking, the bot may talk about favorite films, music, drugs, or family issues, but it doesn’t get explicit until sex comes into the conversation. The bot provides more personal information at higher levels, and it doesn’t shy away from sexual content. The Negobot will try to string along conversationalists who want to leave, with tactics such as asking for help with family, bullying or other typical adolescent problems. If the subject is sick of the conversation and uses less polite language to try to leave, the bot acts like a victim – a youngster nobody pays attention to and who just wants affection from somebody. Robot. Image courtesy of Shutterstock.From there, if the subject has stopped talking to the bot, the bot tries to exchange sex for affection. Is this starting to sound uncomfortably like entrapment?
That’s exactly what gets some experts worried. John Carr, a UK government adviser on child protection, told the BBC that overburdened police could be aided by the technology, but the software could well cross the line and entice people to do things they otherwise might not: “Undercover operations are extremely resource-intensive and delicate things to do. It’s absolutely vital that you don’t cross a line into entrapment which will foil any potential prosecution.” The BBC reports that Negobot has been field-tested on Google chat and could be translated into other languages. Its researchers admit that Negobot has limitations – it doesn’t, for example, understand irony.
Still, it sounds like a promising start to address the alarming rate of child sexual abuse on the internet. Hopefully, the researchers will keep it reined in so as to avoid entrapment – a morally questionable road that could, as Carr pointed out, ruin the chances for prosecutorial success. What do you think? Are you comfortable with the premise, or does the chances of entrapment sour the concept for you?
You can read the original article, here.
Jan
She writes: “I personally notified the very first bounty recipient via email today that his submission for the Internet Explorer 11 Preview Bug Bounty is confirmed and validated. (Translation: He’s getting paid.)“.
She hasn’t yet named names or put a price tag on the first recipient. In fact, there are already multiple researchers who’ll be receiving bounty payouts. MSRC plans to hook up those researchers who want to be publicly recognized for their contributions on an acknowledgement page on its bounty web site. “Stay tuned, as it will come soon“, Moussouris says.
What Microsoft can share at this point are these two key results:
- They’re getting more submissions, earlier. Microsoft has received more vulnerability reports in the first two weeks of its bounty programs than it typically would in an average month. It shows that the strategy for getting more vulnerability reports earlier in the release cycle is working, it says.
- They’re attracting new researchers. Researchers who’ve rarely, or even never, reported directly to Microsoft are now choosing to talk directly to the company. Microsoft interprets that as proof that its strategy to hear from people it usually doesn’t hear from is bearing fruit.
As Moussouris explains it, Microsoft was canny in how it chose to approach the vulnerability market. There’s the black market, where zero-day bugs fetch the highest prices. Then there’s the gray market, where bug-hunting mercenaries make a mint selling information about exploit techniques and unpatched vulnerabilities to corporations and nation states. Microsoft didn’t go there. Instead, it focused on the white market: the place where buyers are after vulnerability information for defensive use, whether it’s vendors themselves (via bounty programs) or a broker who uses the vulnerabilities for their own protection services or threat reports. Moussouris says that three years ago, white-hat bug hunters were passing up cash on the white market and were instead mostly coming to Microsoft directly. That changed over the past few years. Microsoft has witnessed researchers increasingly holding bugs back to see what the going rate might reach on the various markets, typically after Microsoft has released code to manufacturing. The way Microsoft figures it, it’s identified a gap in the market that its new bounty program is filling: namely, in the pre-release, or beta, period.
Moussouris writes: “It’s not about offering the most money, but rather about putting attractive bounties out at times where there are few buyers (if any)… Trying to be the highest bidder is a checkers move, and we’re playing chess“.
There is data out there that bolster Moussouris’ contention that strategically structured, well-timed bounty programs are a good investment. A study recently released by the University of California, Berkeley reports that paying bounties to independent security researchers is a better investment than hiring employees to do it. Piggy and mouse. Image from ShutterstockFor example, Google’s paid out about $580,000 over three years for 501 Chrome bugs, and Firefox has paid out about $570,000 over the same period for 190 bugs. Compare that with just one full-time salaried security researcher digging through code, at, say, $100,000 per year, and the savings can be huge.
You can read the original article, here.
Jan
Some recent industry estimates report that as many as 96 percent of organizations now have employees who use both corporate-managed and personal mobile devices for work purposes, forcing IT to adopt new strategies to protect their data on those devices. Even though huge numbers of smartphones and tablets are lost every day, many users don’t enable even basic password protection.
Mobile malware and hacking is on the rise and many workers are still using unsecured personal mobile devices to access corporate data—a major concern for organizations trying to protect data while letting users work how they want.
Sophos Mobile Control provides the complete security that IT requires to confidently embrace employee device mobility. This latest version delivers Windows Phone 8 support alongside iPhone/iPad and Android, with self-enrollment and self-service capabilities for users, and allows IT to manage the complete device lifecycle as well as loss & theft scenarios.
Also included is an easy-to-use client app, which provides access to compliance status, messages and support information—allowing for comprehensive reporting and giving IT a holistic view of devices. Simpler administration is delivered by an updated menu, dashboard and various other workflow improvements. The SaaS version of Sophos Mobile Control 3.5 delivers better integration into corporate IT with a new remote Exchange ActiveSync (EAS) Proxy that enables organizations to block non-compliant devices from receiving email, and remote LDAP support that allows users to easily connect to Active Directory.
You can read the original article, here.
Jan
By offering this service, GlobalSign hopes to encourage the use of SSL in application development and the growth of security best-practices.
Through GlobalSign’s commitment to the open-source community, projects are eligible to receive one free Wildcard SSL Certificate valid for as long as the project meets minimum requirements. Open-source software projects that allow developers and the general public to freely access the source code have become very popular and are looked upon by many as leaders in the industry, representing an important segment of the technology community. Offering SSL Certificates will allow developers to improve the trust and security of their projects, which people around the world rely on. GlobalSign hopes this partnership can also make a difference by setting an example in how SSL is deployed today.
“We are delighted to show our commitment to the open-source community by offering free SSL Certificates to these projects,” said Ryan Hurst, chief technology officer, GMO GlobalSign, Inc. “We believe this effort will not only help the developers and users of open-source projects but also encourage the adoption of industry best-practices in the use of SSL.”
To qualify for a free Wildcard SSL Certificate from GlobalSign, the software project must use a license approved by the Open Source Initiative. GlobalSign will also require that projects maintain secure SSL configurations. Projects can quickly and easily evaluate their SSL strength by using the GlobalSign SSL Configuration Checker, which currently checks for over 30 common problems relating to configuration and provides recommendations on how to fix them, thus making it easy to achieve a secure configuration.
Those in the open-source software community who are interested in obtaining a free Wildcard SSL Certificate from GlobalSign may enroll for it by visiting https://www.globalsign.com/ssl/ssl-open-source/.
Click here to see the original article.
The new release delivers the first in the industry “IP Centrex for VPS providers“. With this technology, Web Hosting companies can deliver IP PBX services to any size business, all within the Virtualized cPanel management system.
IP Centrex has traditionally been a system for carriers and SIP Trunk solution providers due to the complexity and telecom requirements for setup and delivery of services. “IP Centrex Services” has become a vital part of the evolution to move complex IT services out of the IT closet, to a “centralized” location in the Cloud. VPS hosting providers can now provide valuable services with IP Centrex, in a simple to manage and easy to understand package that runs right inside the Virtualized environment, not requiring any dedicated servers or disruption.
The cPanel Adapter is a totally open source project, managed, maintained, and developed by a community of VPS hosting providers around the globe. The project is hosted at the Google Code site and VPS Hosting companies are encouraged to join and contribute to advance the technology for their own requirements and customer demands.

Features for the IP Centrex system included in the 3.0 release include:
- Setup of phone extensions
- Creation and management of Queues i.e. “support department” or “sales team”
- Certified for SNOM IP Phones with HD Voice
- Encryption for secure calls
- IPv6 support
- Pronto! HTML5 Webmail with WebRTC support for HD Voice calls
- Secure Instant Messaging and Chat rooms
- Email and Calendar services with Encryption features including Certificate Authority
- Pronto! “Native” Mobile Clients available in the Apple App store and Android Store
You can read the original article, here.
Jan
Sophos Complete MSP Security is the first MSP-focused solution to offer complete protection for networks, endpoints, and mobile devices from a single vendor.
Sophos Complete MSP Security makes offering IT security as a service easier and more profitable. MSPs can offer a full range of IT security services that provide instant credibility and proven protection, including centralized management that allows them to easily manage all of their customers’ locations at no extra charge.
With Sophos’ new self-provisioning MSP licensing, this program offers compelling usage-based pricing and pay-as-you-go monthly billing, and it requires no up-front commitments – a business model demanded by today’s MSPs that had gone unmet – until now.
You can read the original article, here.
Jan
Through the partnership, both parties aim to meet the increasing demand for SSL and other digital certificates requirements in the region through a range of dedicated enterprise solutions.
With over 55 percent growth in the SSL market during the last year (source: www.netcraft.com), the requirement for security in the Scandinavian region is at an all-time high. GlobalSign has been working with TrustZone for several years to encourage best practices for website security throughout this territory, issuing over 11,000 SSL Certificates through TrustZone, resulting in a significant acceleration in market growth of over 100 percent (source: www.netcraft.com). The partnership demonstrates both companies’ commitment in working together to enable customers to benefit from industry-leading SSL security solutions and in providing high levels of customer support, delivered directly by TrustZone at the local level.
The two organizations have joined forces to better serve the enterprise market in particular and are introducing GlobalSign’s leading Managed SSL and Enterprise PKI (ePKI) solutions to TrustZone’s customer base, enabling advanced on-demand management of a range of digital certificates. The scalability of both solutions gives large enterprises the ability to streamline workflows, whilst reducing the cost and time resources typically associated with digital certificate management and PKI deployments.
You can read the original article, here.
Jan
“On June 19th we uncovered, halted and contained a targeted attack on our internal network infrastructure. Our systems have been cleaned and there is no evidence of any user data being compromised. We are working with the relevant authorities to investigate its source and any potential further extent. We will let you know if there are any developments. The current evidence suggests a limited impact. The attackers were able to obtain at least one old and expired Opera code signing certificate, which they have used to sign some malware. This has allowed them to distribute malicious software which incorrectly appears to have been published by Opera Software, or appears to be the Opera browser. It is possible that a few thousand Windows users, who were using Opera between 01.00 and 01.36 UTC on June 19th, may automatically have received and installed the malicious software. To be on the safe side, we will roll out a new version of Opera which will use a new code signing certificate“.
The conclusions we reached, based on the announcement above, were:
- The network was breached.
- A code-signing key was stolen.
- Malware has been signed with it and circulated.
- At least one infected file was posted on an Opera server.
- That file may have been downloaded and installed by Opera itself.
- Cleanup and remediation has now been done at Opera.
- That sounds a bit more like Security breach not stopped.
- How else could a signed-and-infected file have been automatically downloaded by an already-installed instance of Opera? Anyway, wouldn’t Opera’s auto-update have failed or produced a warning due to the expired certificate? Until Opera has worked out the answer to these questions, Opera users probably want to assume the worst.
The good news is that the malware involved is widely detected by anti-virus tools, and the period of possible exposure via Opera itself was at most 36 minutes.
→ According to Opera, Sophos products block the offending file as Mal/Zbot-FG.
So, if you are an Opera for Windows user:
- Download a fresh copy of the latest version (since the buggy download appears to be a thing of the past).
- Make sure your anti-virus is up to date.
- If you can spare the time, do an on-demand (“scan now”) check of your computer.
- If we find out more detail about whether malware was distributed by existing Opera installations or not, we’ll let you know.
You can read the original article, here.
This is according to the abstract of a briefing to be given at the upcoming Black Hat USA conference. The attack, dubbed “Mactans“, succeeded in compromising latest generation devices with the latest version of iOS. It led to a persistent infection with software of the attacker’s choice, invisible to the phone’s user thanks to built-in concealment techniques used to hide some of Apple’s own apps.
The researchers, from the Georgia Institute of Technology, say they built their malicious charger in minimal time with little budget, using a credit card-sized BeagleBoard-embedded computer. I’ve always been a little worried when I’ve seen those free charging stations at airports, shopping malls and other public places. OK, so sometimes you just have to get at some power, but the whole idea of plugging my phone into something I have so little reason to trust just seems a little dirty, not to mention unsafe. Now, assuming this is more than the usual pre-conference hype, those fears look more than justified.
Worse, the small scale of this particular device means you wouldn’t even need a big pedestal-sized charging station. While not quite small enough to disguise as a normal Apple USB power converter as it stands, there are still ample opportunities to trick people into trusting a reasonably compact charging device.
With a little more effort and investment, it should be trivial to build a trojanized charger that is almost identical to standard kit. Then we’d really be in trouble. Imagine an eBay shop selling super cheap USB plugs, which could happily take over your phone and make it call premium-rate numbers or harvest passwords from your email or even bank accounts. Not such a bargain all of a sudden. It might be a good time to buy up all the USB chargers you’re going to need – I suspect prices for proven trustworthy hardware might well be going up fairly shortly.
You can read the original article, here.
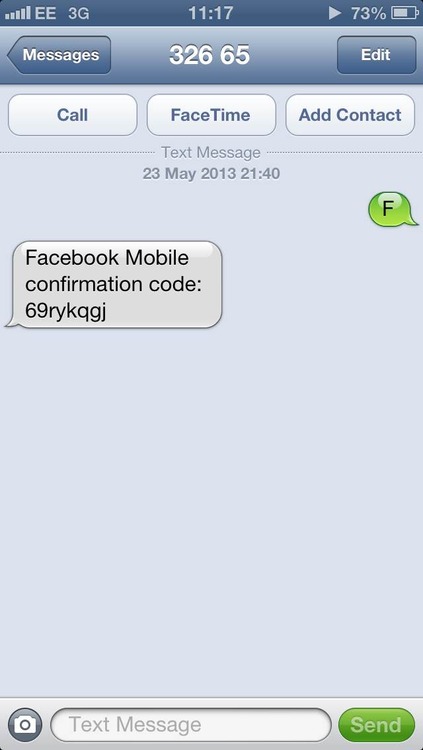
As it is, Whitten explains, Facebook gives users the option of linking their mobile numbers with their accounts. Users then can receive updates via SMS and can also login using their phone number rather than their email address. Whitten found that when sending the letter F to Facebook’s SMS shortcode – which is 32665 in the UK – Facebook returned an 8-character verification code. After submitting the code into the activation box and fiddling with the profile_id form element, Facebook sent Whitten back a _user value that was different from the profile_id that Whitten modified.
Whitten says that trying the exploit might have led to having to reauthorize after submitting the request, but he could do that with his own password instead of trying to guess at his target’s password.

After that point, Facebook was sending an SMS confirmation. From there, Whitten said, an intruder could initiate a password reset request on his targeted user’s account and get the code back, again via SMS. After a reset code is sent via SMS, the account is hijacked, Whitten wrote: We enter this code into the form, choose a new password, and we’re done. The account is ours.

Facebook closed the security hole by no longer accepting the profile_id parameter from users. This could have been a valuable flaw were it to fall into the hands of attackers who might have used it to steal personal data or send out spam. As it is, one commenter on Whitten’s post who obviously didn’t understand the “it’s now fixed” part of the story made the bug’s value clear with his or her eagerness to figure out how to exploit it: ›khalil0777 • a day ago
someone explain me how to exploit it i am realyy need it i wait your helps friends :/
:/ oh well, ›khalil0777, looks like you’re too late for that party.
I’d say better luck next time, but perhaps instead I’ll save my good wishes for Mr. Whitten.
May he enjoy his $20,000.
It was well-earned, and it’s a bargain for Facebook even were the reward to be doubled, considering the grief that could have been caused by such an easy exploit.
Click here to see the original article.
The new line up consists of four rack-mount appliance models with larger internal disk capacities, faster processors, increased memory, and integrated solid state drives (SSDs) to shorten backup time and accelerate data recovery. The bundled WD Arkeia v10.1 software delivers new support for “seed and feed” technology to support hybrid cloud backups. This allows companies to move backups offsite via network replication rather than shipment of tapes.
The new fourth-generation appliances offer:
• Increased Backup and Recovery Speed: New features include integrated LTO5 tape drives, processor upgrades to a maximum of 2 hex-core Intel Xeon, integrated SSDs on select models, and memory up to 96 GB to allow for increased data backup and recovery speeds of both files and disk images. WD Arkeia’s patented Progressive Deduplication™ technology accelerates backups by compressing data at source computers before transfer over local area networks (LANs) or wide area networks (WANs).
• Higher Storage Capacity: Storage capacity doubles from the third generation, with raw capacity now ranging up to 48 TB, configured in RAID-6.
• Improved Ease-of-Use: Version 10.1 of WD Arkeia software, delivered with the new generation, includes an on-boarding wizard to streamline the appliance setup process.
• Storage Reliability: All new WD Arkeia appliances feature WD enterprise-class WD RE™ hard drives for maximum data integrity.
• Simplified Tape-free, Offsite Storage: Version 10.1 of WD Arkeia software extends support for hybrid cloud backup capabilities to the full line of WD Arkeia appliances. “Seed and feed” capabilities allow administrators to supplement network replication of backup sets offsite by using USB-connected hard drives to transfer initial and large backup sets and also to size WAN bandwidth for the replication of nightly incremental backups.
WD Arkeia fourth generation network backup appliances – models RA4300, RA4300T, RA5300, RA6300 – will be available in July 2013 through select DMR’s and WD-authorized value-added resellers (VARs) in the US, Canada, and Europe. Manufacturer’s Suggested Retail Price, including hardware and software, begins at $9,990 USD. WD Arkeia network backup appliances are covered by one year of unlimited access to technical support, one year of software updates, and a one-year limited hardware warranty.
Sophos received top marks in the latest report from AV-Comparatives, a leading international testing lab. The report, titled “Impact of Anti-Virus Software on System Performance,” evaluated twenty one of the world’s leading security products on a PC running under Windows 7.
The testing lab prepared a total of 545 infection scenarios, and Sophos’ antivirus offering tied for the highest score among the products reviewed. It also received an “Advanced +” award, based on the lab’s assessment of the overall results.
“We value the work of independent testing labs like AV-Comparatives, as they help vendors like Sophos to strengthen our offerings, while providing consumers and businesses great insight so that they can make better informed decisions,” said Mark Harris, vice president, engineering, Sophos. “This latest recognition validates the great work of our team, which is committed to developing complete security solutions to combat advanced threats.”
In related testing news, Virus Bulletin, another leading independent lab awarded Sophos with a VBSpam award for its comparative anti-spam testing. This marks the 20th time that Sophos has received this honor for its Sophos Email Appliance. Additionally, Sophos recently received a VB100 award for Sophos Endpoint Security and Control as part of Virus Bulletin’s comparative review on Windows XP Professional SP3.
Click here to see the original article.