News
The UK team were asked recently to provide some comment for a well-known IT Security website around how SIEM can provide a return on investment. It’s an interesting topic, especially since we think that the answer is “Quite easily!”.
But it set us thinking as well because the question was actually phrased thus; “How do you justify the cost of investing in SIEM?” It implies that SIEM is expensive. Justifiably so – because SIEM is perceived as being very expensive, plus difficult to install and a hassle to use. And that is precisely the experience that lots of people have had with this technology.
And there is simply no excuse for it. There’s no reason SIEM can’t be affordable, both for large organisations and smaller enterprises. There’s no reason it has to be complicated to install and a pain in the **** to use.
SIEM is an awesome technology. It can collate the millions and billions of data logs generated by the firewalls, laptops, VOIPs, door entry systems etc etc of even a modest sized organisation. It collates all this disparate data into a single place, extracts the interesting bits and tells you about them.
So if we can design a technology that should make our lives as techies simpler, why is it causing all this pain and knashing of teeth? If we’re clever enough to design something this utterly fabulous at making the complex straightforward, can’t we design it to be easy to use and affordable at point of purchase too?
The answer is of course YES – if we really want to. It’s about customer-centricity, a term that IT professionals sadly aren’t exposed to that often.
So here’s the pitch. LogPoint SIEM is designed to be effortless to install and intuitive to use, because we get that you bought it to make your life simpler (not the other way round). It’s sold on a simple licensing model that means you don’t pay through the nose and keep paying when you don’t have to. It can work with the systems you already have installed so you’re not pushed into new hardware that you neither want nor need.
We at LogPoint are nice people who are truly passionate about the amazing potential of SIEM and what it can do for our customers.
You can read the original article here.
You may be wondering how SG UTM fits in with this new Synchronized Security era we’re entering. The answer is: very well! It’s already got some great Synchronized Security-like integration built-in, and it’s a great platform to start your Synchronized Security journey.
SG UTM, Endpoint and SMC integration
As you probably know, SG UTM has enjoyed tight integration with Sophos Endpoint and Mobile solutions for some time now. Customers have taken advantage of SG UTM’s integration with Sophos Endpoints for off-site web policy enforcement, and with Sophos Mobile Control for NAC-like features to keep non-compliant devices off the network. In fact, it’s these kinds of features which inspired the Synchronized Security strategy. Sophos UTM has been a leader in this area, and still offers some of the best integration between products available.
SG UTM is a great platform to get started with
SG UTM is loved by partners, customers and industry analysts for its simplicity, performance, value and protection. It’s trusted, proven, and feature-rich. It’s also got some great integration with other Sophos products as we’ve already discussed. But it’s also important to keep in mind that SG UTM can be upgraded to enable the next wave of Synchronized Security features, at no charge, at the time of your choosing.
Easily upgrade to XG Firewall when the time is right
Our new XG Firewall is our platform for the future, built on a next-gen foundation that enables a whole new level of integration: Synchronized Security. While it’s still early days for XG Firewall, the great news is that SG and XG hardware appliances are exactly the same, so they can both run the new firmware at the heart of XG Firewall and Synchronized Security – it is 100% compatible with SG-Series hardware appliances.
This means SG UTM appliances can be easily upgraded to the new XG Firewall firmware. There is no upgrade charge whatsoever, so when the time is right for you to migrate you’ll get all the great features you value in the SG UTM and the added bonus of Synchronized Security and other innovative features that are exclusive to XG Firewall.

SG UTM continues to get better and better
While you are still enjoying your SG UTM you’ll be pleased to hear we’re continuing to enhance and update SG UTM with great new features and hardware options as well. Check out all the great stuff in the recent release of UTM Elevated 9.4, if you haven’t already. And be sure to submit your feature requests for upcoming UTM 9 releases too.
More questions?
If you have further questions about the details of how migrating your SG UTM license or configuration to XG will work, we are keeping the Migration FAQ up to date with the latest information.
More Synchronized Security
As you can imagine, we’re rapidly expanding our Synchronized Security plans – it’s about far more than just connecting endpoint and firewall. Continue to monitor this site to find out how we’re connecting more and more security components to Synchronized Security at every point.
You can read the original article here.
The hacktivist collective called Anonymous has brought cybersecurity to the forefront again, as it continues to strike at some of the world’s leading banks and financial organizations with its OpIcarus distributed denial of service (DDoS) attack campaign. Last week Anonymous shut down the London Stock Exchange for two hours.
Coincidentally during the same week, HelpNetSecurity published an article that highlighted a troubling statistic: “1 in 10 banking CEOs don’t know if they’ve been hacked.” The statistic came from a KPMG study of 100 banking executives. The farther down the management chain, the greater the lack of awareness, according to that article: “Approximately 47 percent of banking executive vice presidents and managing directors reported that they didn’t know if their bank had been hacked, and 72 percent of senior vice presidents and directors stated that they didn’t know.”
The statistics above suggest that banking executives are not inclined to share information about cyber incidents with all their senior staff. That may be understandable if not all staff are on a “need to know” basis for security breaches.
Banks Need DDoS Protection
Regardless, banks and other financial institutions can ill-afford to be laggards when it comes to implementing cybersecurity measures. First of all, it’s important for a bank system to maintain uptime, because many bank transactions are time-sensitive. Second, account security is of utmost importance; theft of sensitive data is unacceptable. Third, a cyberattack incurs high IT and legal costs related to damage control after the incident. It’s plain to see that cybersecurity is a bottom-line issue because breaches lead to loss of revenue and customer trust.
DDoS attacks are perhaps the most obvious cyber threats that banks face. People often associate a DDoS attack with a complete network shutdown, but what should scare bank executives even more is the possibility of a low-threshold, Dark DDoS attack. Corero research found that 93% of all DDoS attacks were under 1 Gbps, 95% lasted less than 30 minutes, and 71% of them lasted less than 5 minutes. These statistics indicate that the goal of hackers is not always to cripple a website and make headlines (like Anonymous usually does).
Advanced Persistent Threats (APT)
Cyber criminals increasingly deploy low-threshold attacks because they are small enough to evade the radar of IT staff and traditional DDoS scrubbing solutions. Dark DDoS attacks distract IT staff while the hackers map a network to find its vulnerabilities, and then launch dangerous malware on the network. Corero COO Dave Larson notes, “If you can create a pathway through an enterprise’s network using DDoS — even if it’s a few minutes — that’s enough time, and once they’ve done that, they can embed an advanced persistent threat (APT: essentially the enterprise version of a botnet) that sits there quietly on the server until the bad guys want to use it.”
The hackers can then leak critical information out of a network, such as credit card info or keystrokes, without anyone noticing.
Many companies rely on a firewall or intrusion prevention system (IPS) for protection, but both are rendered useless in the face of a DDoS attack. The only way to stop DDoS attacks is to have an always-on, inline, and automated network threat defense appliance that blocks DDoS traffic at the edge of the network. Without adequate DDoS protection in place, banks could be pouring money down the drain.
You can read the original article here.
For the 11th time in a row, Sophos Mobile Security has received a perfect 100% protection score in the May 2016 edition of AV-TEST’s “The best antivirus software for Android” comparison, after successfully detecting all of the 3,300+ samples used.
We also scored 6.0 out of 6.0 for “usability,” which includes both performance and false positives (of which we had none). You can read the full test results here.
This is the eleventh straight 100% result for Sophos in AV-TEST’s Antivirus for Android shoot-out. While other products put up similar results in the current test, no other vendor comes close to sporting such a long track record of 100% detection scores. AV-TEST recognized this earlier this year by giving its Best Protection 2015 award to Sophos Mobile Security.
Sophos Mobile Security protects your Android devices without compromising performance or battery life. Powered by our award-winning anti-malware technology, Sophos Mobile Security offers a first-class level of anti-malware and antivirus protection. It also provides Potentially Unwanted App detection, privacy and security advisors, loss and theft protection, web protection, and much more.
You can download Sophos Mobile Security for Android free from Google Play.
Sophos Mobile Security is also available as a managed app as part of Sophos Mobile Control or Sophos Central.
You can read the original article here.
Many IT managers have come to regard SSL VPN as a mere commodity technology – needed to provide secure access to network resources for remote and mobile workers, but about as exciting as plain oatmeal. Of course, securing remote access is the primary function of an SSL VPN appliance. However, just as network and security architectures have evolved over the years, SSL VPN technology has continued to evolve as well.
At Array, we’re seeing quite a number of interesting deployment models that go beyond the ‘standard’ use cases for SSL VPN; these real-world installations by Array customers have added simplicity of use and an extra layer of security that bring real value to their respective organizations. In no particular order, here are a few of these innovative uses:
Proxy Microsoft ActiveSync Connections
If your organization has implemented or is planning a Bring Your Own Device (BYOD) initiative, the security of critical servers is an imperative. Rather than opening firewall ports to your Microsoft Exchange CAS servers (typically ports 80 and 443), use an SSL VPN appliance to proxy Microsoft ActiveSync traffic for mobile devices.
Centralize and Simplify Two-Factor/Multifactor Authentication
For geographically dispersed companies, managing across multiple sites can become more than a little painful if two-factor (or multifactor) authentication is deployed at each server that will be accessed remotely. Centralizing authentication at a single SSL VPN appliance allows users to authenticate at one core point – then connections are proxied to the appropriate back-end resource regardless of its physical location. This model dramatically simplifies management of two-factor authentication, while accelerating deployment and reducing complexity for end users. The Array Networks AG Series Secure Access Gateway supports most two-factor (or multifactor) products, and in addition includes an out-of-the-box OTP solution.
Maintain Security of Sensitive Information in the Field
We’ve seen this particular use case most commonly in financial institutions, though it can be useful in any situation where an organization’s staff needs to carry confidential information outside the office. Using Array’s DesktopDirect remote desktop access solution, an add-on for the AG Series SSL VPNs, employees can securely access their work PC from any location and any device, and view applications and data just as if they were in the office.
For example, a bank can provision tablets for employees to use in signing up new accounts at local events, or to meet with customers at their home or office to discuss investment options for their respective portfolios. All customer-confidential information is secured, and does not remain on the tablet – and, as tablets are particularly vulnerable to loss or theft, this last point is quite important.
Central IT Admin Portal
In this example use case, a separate portal is set up specifically for IT staff to securely access and manage internal network resources from a remote location (home, remote office, etc.). Links can be included to proxy Web-based applications, and to proxy RDP connections that are statically assigned based on internal policy. Specific network tools for IT staff that require limited remote access capabilities can also be published to the portal, and two-factor authentication and/or single sign-on can be enforced to meet internal security requirements. Array’s AG Series includes monitoring capabilities that can be used to maintain a log of all remote IT-related tasks as well.
Branding: Maintaining a Consistent Look and Feel
Most companies lack the time or resources required to ‘custom-brand’ Web-based applications such as Outlook, SharePoint and others for a consistent corporate look and feel. Centralizing internal Web-based applications through an SSL VPN simplifies branding by providing a ‘single pane of glass,’ or portal, on the SSL VPN. This portal can be easily customized with the corporate logo, colors and other elements of the brand, and provides an easy-to-use and recognizable point of access to business applications.
These are just a few examples of how Array customers are using SSL VPNs to provide additional security and versatility to their organizations. Join the conversation! We’d love to hear your ideas, questions and comments on ‘outside the box’ uses for SSL VPNs.
You can read the original article here.
Telecoms and Internet Service Providers (ISPs) are constantly making investments to expand or enhance their infrastructure, and to drive customer growth. Their market is structured in a way that forces them to do so, as a means of driving revenues and maintaining their position in the provider food chain. Retaining and growing accounts for existing customers is much easier than gaining new ones, particularly in an industry with such significant turnover. But which technologies offer the greatest opportunities for this kind of advancement?
Many enterprise customers are concerned about security – but this doesn’t mean that telecoms should look solely at security tools when planning the expansion of their service offerings. Instead, they need to look at the much broader picture of risk management. Telecoms can go a step further in their marketplace by offering a DDoS Protection Solution and strategies delivered as a service to their customers.
Why take this approach? The answer is simple. You won’t be able to invest in your infrastructure down the line if you’re losing customers now, or being usurped by those who have a larger, more diverse service offering. Companies are quickly realizing that action is required now, in order to protect future services, and keep up with competitors.
The technology is there, as well as the demand, for telecoms to offer bundled services that can help customers big and small manage the risks facing their networks. Most customers look at security as part of what they need to tackle; encapsulating DDoS mitigation services with other risk management provisions, such as next generation firewalls in tiered bundles, will give customers the flexibility they need and make a huge difference to them in mitigating the cyber threats facing their organizations.
Many ISPs and data center providers are looking at offering DDoS services as part of a bundle this way, with those who have done so seeing massive increases in sign-ups as a direct result of their investment.
So the trick to making those customers stick is to broaden the offering to cover risk management. Studies have shown customers are willing to pay extra. Given their unique positioning within the network infrastructure, ISPs and telecoms are able to harness the latest technology to provide a fantastic service and value for their customers.
You can read the original article here.
Back in March, we wrote about how cybercriminals are using previously-unknown malware to avoid detection from traditional security products.
While conventional anti-malware protection is vital as a first line of defense, organizations need additional ways to combat today’s targeted, unknown malware.
Unfortunately, many next-generation solutions designed to deal with these kinds of threats are too expensive and too complex for many businesses to consider.
Sophos Sandstorm can help
Sophos Sandstorm is an advanced malware defense solution that complements Sophos security products to quickly and accurately detect, block and respond to evasive threats using powerful, cloud-based sandbox technology.
It integrates with Sophos Web Appliance and other Sophos network solutions, such as our Email Appliance and UTM.
Why you should consider Sophos Sandstorm with Sophos Web Appliance
- Advanced protection: it provides an additional layer of protection against fast-moving and targeted threats.
- Accessible: you don’t need to buy or install additional hardware or learn a new system.
- Affordable: It’s the latest enterprise-grade protection without the enterprise price tag.
Try it yourself
If you want an advanced threat solution that’s easy to try and deploy, simple to manage, and uses the best threat intelligence, Sophos Web Appliance with Sophos Sandstorm checks all these boxes.
You can try it yourself on your Sophos Web Appliance. Take a look at the video below to see how:
You can read the original article here.
Everyone knows that traditional antivirus isn’t enough to stop today’s advanced threats, so endpoint security vendors are hoping you’ll consider their “next-gen” solutions. But what exactly does “next-gen” mean, and what capabilities should you expect?
At Sophos, we believe next-gen endpoint protection means an integrated system of technologies that protect against all stages of an attack:
1. Prevention: Stopping malware before it can execute.
2. Detection: Identifying quickly when malware is deployed.
3. Response: Taking action instantly when malware is detected.
Let’s take a quick look at the capabilities your endpoint protection needs to counter threats at each stage.
1. Prevention: The defensive front line
Prevention focuses on stopping malware from ever reaching the device in the first place. Prevention capabilities can be broken down into exposure prevention and pre-execution defense.
Exposure prevention:
– Web protection – can you block malicious webpages?
– Device control – which devices (e.g., USB drives) are allowed to access the endpoint?
– Download reputation – where does the file come from, do other machines in the organization use it?
Pre-execution defense:
– File analytics/HIPS – does a file contain code trying to modify the registry?
– Emulator – can you execute the file in a safe environment to test it?
2. Detection: Catching malware in the act
Detection uses a variety of methods to identify malware that has reached a device. A next-gen endpoint solution should have these run-time detection capabilities.
– Malicious traffic detection – are processes communicating with known threat locations (phoning home)?
– Memory scanning – is a file exhibiting behavior of known malware?
– Exploit detection – is the suspect process cataloging the memory of another process?
3. Response: Clean-up and analysis
Response capabilities should eliminate the malware and perform analysis to identify the entry point of the malware.
– Malware removal – can your endpoint solution remove the executable and other malware components?
– Root cause analysis – can it identify the malware’s origin to understand what was compromised?
Choosing a truly “next-gen” endpoint solution
Sophos experts have written a simple guide to explain why organizations like yours need next-gen endpoint protection. It also explains in straightforward terms the features that a next-gen endpoint solution should have, and how they keep your users and systems secure.
Download the free whitepaper, or sign up for a free 30-day trial of Sophos Next-Gen Endpoint Protection.
You can read the original article here.
We’re pleased that Gartner has named Sophos a visionary in the Gartner 2016 Magic Quadrant for Enterprise Mobility Management Suites*, for the third year in a row. We think this validates Sophos Mobile Control as one of the best mobile management and security products on the market today.
We believe we improved our position in the Magic Quadrant because our enterprise mobility management product, Sophos Mobile Control, offers best-in-class data protection, straightforward management, and comprehensive security. Sophos Mobile Control empowers users to be productive, while keeping business data safe and personal data private.
The fast-moving mobile market is challenging IT departments to react quickly. That’s why it’s important to have an easy-to-use enterprise mobility management (EMM) solution that keeps up with users and their demands for new mobile devices to enhance productivity.
Sophos Mobile Control is the EMM solution for businesses that want to spend less time and effort to manage and secure all those mobile devices. And it now offers new features like managing Windows 10 tablets, notebooks and desktops; powerful encrypted containers; and Apple iOS DEP support.
As the only security company in the Magic Quadrant, we believe Sophos is a Visionary because we make mobile security and data protection a priority, and we keep it simple for IT departments and users alike.
To find out what Gartner says about the dynamic EMM marketplace, and determine what EMM capabilities you need, download the complete Magic Quadrant report here.
You can read the original article here.
Nearly every day there is news about a distributed denial of service (DDoS) attack on some major organization, whether it’s a bank or a government agency. Many other organizations experience DDoS attacks on a daily basis, but those attacks don’t make headline news. It’s an alarming situation, globally. In a recent survey of IT security professionals and network operators at the RSA Conference 2016, 31% of respondents stated that their enterprise experiences DDoS attacks weekly or daily.
The survey also asked participants about their current methods of handling the DDoS threat; nearly one third (30%) of respondents still rely on traditional security infrastructure products (firewall, IPS, load balancers) to protect their businesses from DDoS attacks.
Dave Larson, COO of Corero, states: “Those companies are very vulnerable to DDoS attacks because it’s well-documented that traditional security infrastructure products aren’t sufficient to mitigate DDoS attacks.”
DDoS attack prevention is nearly impossible: it’s difficult to track down hackers, whereas it’s easy and inexpensive to launch a DDoS attack. DDoS attacks are likely to increase rather than go away. However, Corero’s DDoS mitigation appliance can effectively detect and block attacks to prevent network outages and disruptions.
The appliance sits at the network edge, monitoring and mitigating DDoS attack traffic in real time. The solution does not pull attack traffic deeper into the network to a scrubbing center environment, does not rely on human intervention, and does not rely on legacy tools or techniques that some network and security departments use. Rather, it blocks a wide range of DDoS attacks, while maintaining full connectivity and avoiding the disruption of legitimate traffic.
Anti-DDoS technology is more affordable than ever, and easy to implement. In a well known security firm’s report we read: “DDoS attacks cost small-to-medium-sized businesses (SMBs) an average of $52,000 per incident; for larger enterprises, the cost of a DDoS attack is even more significant, resulting in an average of $444,000 in lost business and IT spending.”
Given the costly impacts of a DDoS attack, the question is not whether one should implement a DDoS mitigation appliance, but rather when?
You can read the original article here.
Sophos UTM has added to our collection of industry awards, after being recognized as the Best UTM Solution at the SC Magazine Awards 2016 Europe, held earlier this week in London.
As the editor-in-chief of SC Magazine points out, these awards are designed to recognize the leading players in the industry and to encourage and praise innovation.
It’s an honor to be considered, and the Sophos SG UTM has now swept this award three times in a row, repeating twice in London and also winning in North America recently.
The judges were impressed by Sophos SG UTM, and its many advantages over the other products considered in this category.
As the judges’ full write-up noted, Sophos SG UTM has a full range of features, allowing businesses of any size to reduce the number of solutions they need to manage their security:
“As a fully-featured web security gateway, email gateway, network firewall and wireless management console, Sophos SG Series UTM has enabled its diverse customer base to reduce the number of solutions they need to manage whilst providing enhanced features, such as Advanced Persistent Threat Protection, which even the smallest company, can easily deploy.”
Read the full review (see page 11) to see why we beat the competition once again.

You can read the original article here.
A new version of a deceptive banking malware has been responsible for a series of attacks on financial institutions in many countries around the world in the past year, SophosLabs reports in a new research paper.
Vawtrak (also known as NeverQuest and Snifula) has been around for a few years now, yet it continues to thrive as a popular crimeware-as-a-service kit used by a variety of cybercriminal groups.
SophosLabs analysis of what we are simply calling Vawtrak version 2 shows the malware authors have introduced new innovations, while making frequent updates to meet demand and stay ahead of defenses. SophosLabs has seen Vawtrak version 2 spreading by phony emails claiming to be shipping delivery notices; and Vawtrak being dropped onto computers already infected by the Pony malware.
In the time since our previous research paper on Vawtrak, new banks and countries have been targeted, with several campaigns in countries including the United States, Canada, United Kingdom, Japan, and Israel, with the US being the largest target.
In our earlier analysis of Vawtrak, Germany and Poland were the top-targeted countries, but we did not see significant activity in those countries using version 2. This change in geographic targets could indicate that Vawtrak’s crimeware customers are no longer interested in those countries.
Innovations in Vawtrak version 2
The developers of Vawtrak have invested significant efforts to improve the malware in version 2, complicate defenses, and frustrate security researchers. According to SophosLabs, Vawtrak version 2 includes some updates that break existing tools used to analyze the malware:
“These changes involve increased levels of obfuscation and changes to the encryption used. … [T]he motivation for the change would appear to be an attempt to temporarily break existing tools that may implement the algorithms used by previous Vawtrak samples.”
SophosLabs also discovered that the Vawtrak authors made version 2 leaner with a smaller footprint for the initial payload used for infection. This leaner version of Vawtrak could allow the authors to introduce advanced features to be added and deployed as modules.
For a more technical analysis of Vawtrak version 2 and additional research insights into this persistent threat, download the SophosLabs research paper.
You can read the original article here.
It’s a challenge for network security professionals to detect, never mind block, every intrusion. What’s troubling is how much time it can take for an organization to realize that its network security system has been breached. In its latest report on cyber security trends, “M-Trends 2016,” FireEye found that it took a median of 146 days for an organization to recognize that its security had been compromised. (This statistic is based on Mandiant’s experience responding to breaches. Organizations that detected a breach on their own or resolved the breach without Mandiant’s involvement are not included in the median.)
Some infamous security breaches weren’t detected for months; the U.S. Office of Personnel Management data breach is one instance that comes to mind. It took OPM staff over a year to become aware of the breach. TalkTalk’s breach was another that made headlines, and raised questions about how long it took for security staff to detect the breach and respond to it. In that incident “criminals accessed details of 156,959 accounts and 15,656 bank account numbers,” according to Express news.
The fact that some breaches have gone unnoticed for days, or even months is cause for concern. That’s way too much time, considering that hackers can infiltrate a network and obtain crucial data in a matter of minutes. Why did it take so long for TalkTalk to realize the security breach? One factor was a distributed denial of service (DDoS) attack. The Guardian reported that “TalkTalk said a distributed denial of service (DDoS) attack – one that overwhelms a website with traffic, taking it offline – was used as a smokescreen for the attack.”
DDoS Attacks Serve As Smokescreens
Corero’s research of its customer base found that 95% of DDoS attacks average less than 30 minutes in duration, and 93% of attacks are 1Gbps or less in size. Such partial link saturation attacks are often called “Dark DDoS attacks” because they can serve as a smokescreen for a security breach that exfiltrates sensitive data. A Dark DDoS attack distracts IT security staff by inundating online systems with junk traffic, while hackers penetrate other network services that are still up and running and vulnerable to attack.
Even if you have a legacy DDoS mitigation solution (such as a cloud scrubbing service), you’re not fully protected from a Dark DDoS attack, because scrubbing solutions still rely too much on human observation and intervention, which results in a time delay. A scrubbing center solution is usually activated at least 30 minutes after the attack has been initiated—by then some damage could already be done, either in terms of affecting a network or website, or stealing sensitive data.
For this reason, it’s more important than ever to have an automated, inline DDoS mitigation appliance in place, which provides 24/7/365 protection from DDoS attacks. According to Dave Larson, COO of Corero Network Security,
“The only proper defense is to use an automatic, always-on, in-line DDoS mitigation system, which can monitor all traffic in real-time, negate the flood of attack traffic at the Internet edge, eliminate service outages and allow security personnel to focus on uncovering any subsequent malicious activity, such as data breaches.”
You can read the original article here.
For IT security teams, it’s nearly impossible to keep up with the ever-changing cyber threat landscape; not only are there are numerous types of threats, but some attacks are so small in scale that they often escape human detection. Large-scale, volumetric DDoS attacks may cripple websites and grab headlines, but small-scale, low-threshold attacks can be even more nefarious and damaging.
Visibility and Response Time are Critical
The time it takes to detect and respond to a distributed denial of service (DDoS) attack is critical. Human intervention is insufficient for most cyber security attacks because humans can’t immediately see every attack, and they certainly can’t respond fast enough (in real time) to block all infiltrations.
If you can’t recognize a DDoS attack, how can you even begin to defend against it? Hackers need only a few minutes to overrun traditional security solutions and steal sensitive data or map a network to find its vulnerabilities. Even when humans do notice an attack, by the time they respond, the damage may already be done. That’s why IT professionals need granular, real-time network security visibility to monitor and analyze traffic.
Vikram Phatak, CEO and Chairman of NSS Labs recently said, “…attacks happen in computer time, but responses take place in human time. “Companies typically patch monthly, but the bad guys change their approach hourly…Automating the response process shortens the patch window from a week to seconds.”
Automated DDoS Protection is Cost-Effective
In an era when the vast majority of DDoS attacks are under 1 Gbps, and can evade a traditional cloud-based scrubbing center, it’s cost-effective to automate security systems as much as possible. An automated, in-line DDoS protection solution is less expensive than human security staff, and more accurate. That doesn’t mean that security staff are unnecessary, but rather that they need the automated technology to help them be more productive.
The cost of a cyberattack can be enormous, in terms of lost customer trust, revenues, and staff time spent cleaning up the damage. When it comes to cyber threats, a proactive, automated approach makes more sense than a reactive, manual approach.
You can read the original article here.
Mobile devices… everybody has them. We use them every day (sometimes for large parts of the day) for increasingly productive and amazing things – to take selfies, peruse the news, surf the web, compose music, send saucy text messages, make art, and other creative things.
Most also want to use them at work – to read work emails, view and share files, access the company intranet, check the latest revenue spreadsheets, make last-minute edits to the big presentation, and so on. But with the explosion of mobile device usage in business comes the inevitable headache of ensuring that all sensitive and confidential company information stays secure. Data protection regulations must be followed, security policies need to be adhered to and intellectual property must be kept confidential.
As the devices in an organization multiply like rabbits, overworked and understaffed IT departments have to work hard to not lose control. Employees bring their own smartphones and computers to work and expect the same level of access as with corporate-owned devices, which is enough to give any IT admin nightmares.
The best way to cope, while continuing to allow users to work the way they want and to be as productive as possible, is to find a solution that can manage all devices with one secure, time-saving and super-simple solution. Sophos Mobile Control does just that.
We’re very excited to announce the new Sophos Mobile Control 6.1, where in addition to managing traditional iOS, Android and Windows Phone devices you can now also manage Windows 10 laptops, desktops and tablets from the same console. This lets you rest easy knowing you have a uniform company and security policy in place – both for company and privately-owned devices, regardless of whether it’s a phone, desktop or laptop.
Even if contractors, consultants or employees bring a personal Windows 10 laptop to the office, enrollment, provisioning email and granting access to company resources is done with a few clicks in the straightforward management console. It’s also equally easy for the user to remove the computer from company control when access is no longer needed.
Contain yourself, and your users
An additional complication with using privately-owned devices in a company is to make sure that business data stays safe and separated from personal information on the device. Users want their information to stay private and companies want to control access to their sensitive data.
Sophos Mobile Control 6.1 lets you easily configure powerful encrypted containers for documents, emails, calendars and contacts across different OS versions and different devices. If a device becomes compromised or goes missing, access to the data in the containers can instantly be removed by IT. You can even create access control restrictions based on time, Wi-Fi or geo-location.
Best of all, when a user leaves the company, the IT admin can simply remove access to the containers without having to resort to wiping the entire device. Those collections of cat pictures, funky tunes and retro monophonic ringtones are totally safe!
All this means that with Sophos Mobile Control 6.1 you will spend less time and effort managing devices, but you’ll still allow users to be as productive with mobile devices in your business as they deserve to be, without any of the associated risk.
Read more about Sophos Mobile Control. Try the demo now!
You can read the original article here.
If you think your antivirus alone is enough to stay safe from today’s advanced malware threats, you might want to get a second opinion.
Today’s malware is difficult to detect, difficult to remove and difficult to recover from. We estimate that less than 10% of all the new samples analyzed by SophosLabs is previously known malware. You wouldn’t want to gamble with those odds, and you surely don’t want to gamble with your endpoint security.
Sophos Next-Generation Endpoint Security uses signature-less threat detection and response capabilities to better protect you against zero-day attacks, advanced threats and crypto-ransomware that can evade traditional, signature-based endpoint products.
Now we’ve added another tool to our arsenal. We’re calling it Sophos Clean, the next generation of malware detection and removal tools.
When Sophos acquired SurfRight last December, we knew we were getting a great company with innovative technology to complement our industry leading, next-gen endpoint protection solution.
As an added bonus, we acquired SurfRight’s popular HitmanPro malware scanning and removal tool, used by more than 23 million users worldwide. Among its industry accolades, HitmanPro recently received a Q1 2016 MRG Effitas 360 Degree Assessment award, one of just five products certified for neutralizing and successfully remediating all threats in real-world testing.
Now we’ve built Sophos Clean on top of the cutting-edge HitmanPro technology, using progressive behavior analytics, forensics and collective intelligence to discover and remove all traces of malware threats that your antivirus might miss.
Resilient malware attacks critical system files or boot records to manipulate Windows and antivirus software – even before the operating system boots. Sophos Clean can remove persistent threats from within the operating system and replace infected Windows resources with safe original versions. Reinfection attempts are proactively blocked until threat remediation has finished.
Sophos Clean is certainly thorough, but it’s also fast.
With a minimal footprint of just 11 MB, Sophos Clean can scan and remediate infections in less than five minutes, because it can immediately distinguish safe applications from malicious software through advanced behavior analysis. And it checks against our Sophos cloud database of trusted applications, reducing instances of false positives.
The on-demand scan does not need to be installed, which is particularly useful in cases of ransomware infection or in situations where malware is manipulating the installed antivirus software and its updates.
Sophos Clean runs alongside any anti-malware protection you already have. You can scan directly from a USB flash drive, CD/DVD or network attached storage.
Simple. Fast. Clean.
Try a 30-day free trial of Sophos Clean today.
You can read the original article here.
Miercom, a leading, independent test center, recently conducted a comparative test of UTM/Next-Gen Firewall appliances from leading network security vendors including Sophos, Fortinet, Check Point, Dell SonicWALL and WatchGuard.
Miercom ran an extensive set of tests, including raw firewall throughput at a variety of real-world packet sizes. We were pleased with the results, as our XG 135w outperformed similar competing models in all tests by a significant margin.
The Sophos XG 135w set its baseline throughput with firewall enabled at 6560 Mbps, 67.7% more than the competing vendor average.

Miercom also measured performance under real-world conditions, with a variety of important security features enabled such as IPS, application control, antivirus and IPS. The Sophos XG 135w ranked tops in every test, including the most demanding with all security features enabled:
In full UTM mode, the Sophos XG 135w claims the highest performance rate. Its throughput surpasses the competitive performance by 31.3%.
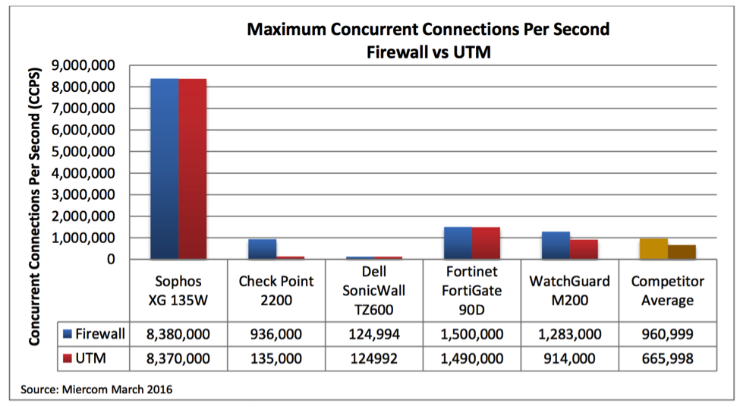
With modern web applications placing increasing demands on firewall connection limits, Miercom also ran a series of demanding connection tests, which are ideal for revealing performance bottlenecks imposed by inadequate RAM and processing speed.
Again, the Sophos XG 135w proves it offers outstanding value – with its high-performance Intel multi-core technology and generous amounts of RAM – providing an order-of-magnitude advantage over competing Firewalls.
The Sophos XG 135w baseline maximum CCPS was 88.5% higher than the competitor average. Its UTM maximum decreased by 10,000 CCPS and was 92% higher than the average. Its concurrent connection rate was extremely high but also had a fairly insignificant decrease when all UTM features were applied.

The bottom line
We couldn’t be more pleased with the results of this comparative testing. But honestly, we’re not that surprised.
We’ve engineered our XG and SG Series appliances to offer the ultimate in state-of-the-art performance, with features other vendors just don’t offer – like high-performance Intel multi-core CPUs, ample RAM, and solid-state storage. Plus we offer the best value and ease-of-use in the industry.
Quite simply, Sophos offers the best price-performance ratio out there, and it’s nice to see Miercom’s testing support that.
Download the Miercom report for full details and results from all their testing.
You can read the original article here.
Looking into current Security Information and Event Management (SIEM) systems, one can notice that all of them attempt to meet certain criteria, such as the native support provided for different log sources and the design of modern features in order to perform data examination and analysis on the sheer volume of the generated log data.
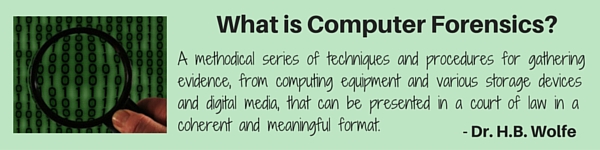
Among these criteria, the compliance management initiatives and the availability of computer forensics capabilities lay at the heart of the discussion. In the present post, the issue under scrutiny is what is computer forensics and how can it be used in today’s world.
A Historic Perspective
Forensics has been around since the dawn of justice. The well-known examples of studying fingerprints or blood groupings and DNA have been used for a long time in order to determine the nature of a crime and locate the perpetrator. Around 1910, Albert Osborn became the first person to develop the essential features of documenting evidence during the examination process. Later, in 1984 the Computer Analysis and Response Team (CART) was established to provide support to FBI’s field offices searching for computer evidence.
Computer forensics, -also called Digital Forensics- has emerged due to the vast increase of cyber activity among the general public. This growth led to greater awareness of the importance of Computer Security and the protection against computer-facilitated crimes. However, the two terms are entirely different despite that they are often closely associated.
- Computer security focuses on techniques and technologies in order to prevent the unauthorized access on computer systems and mainly protect against violation of confidentiality, integrity and availability of data managed by the systems.
- Computer forensics is primarily concerned with the acquisition, preservation and analysis of data gathered by a compromised system after an unauthorized access has taken place.
Cyber Crime Calls for Forensics
Our dependency on computer systems has given way to novel cyber criminal activities. Theft of intellectual property, damage of company service networks, financial fraud, system penetration and data exfiltration are just few of the computer-facilitated crimes that are being committed even as we speak. They differentiate in terms of how the attack takes place, either as external or insider attacks, where a breach of trust from employees within an organization is involved.
Forensics investigation always comes after the attack has been launched and detected, and it follows certain stages and procedures in order to guarantee that the collected digital evidence can be used by law enforcement to track and prosecute cyber criminals.
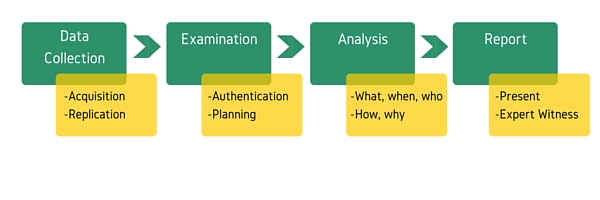
Why is Computer Forensics Needed?
Picture a hypothetical scenario where your organization’s premises have been breached by criminals who broke into and stole valuable assets like money, equipment or confidential reports. The first thing that any responsible executive would do is to evaluate the situation and call law enforcement investigators in order to examine the area and gather any useful evidence.
Now, let’s suppose that the crime had been committed electronically, by breaching the organization’s network, acquiring important data and getting access to undisclosed information. Keep also in mind, that the intruder could be an employee of the company using the organization’s computers. As with the case of a physical crime, the person in charge should evaluate the situation, which in the computer security case means to correctly evaluate the alerts coming from host and network intrusion detection and prevention systems (IDPS) and then use the correct tools in order to collect and analyze any data that could be useful digital evidence.
Computer forensics is the next step of the procedure, where you apply contemporary techniques to gather and preserve evidence from the computing devices of interest in a way that is suitable for admission in a court of law. Imagine how flexible the procedure can become if the appropriate tools for evaluating the situation have been preconfigured for dealing effectively with such cases. Finally, consider that cyber crimes occur much more frequently than physical ones, especially when referring to organizations as victims.
Strategic Planning for Business
Despite Dr. Wolfe’s definition, computer forensics as a science can also be used as application in cases that do not or do not want to involve a court of law. Especially in the case of an insider attack, forensics tools can be used to gather evidence that the executive can then use against the employee in order to prove his involvement in the attack. In general, if the organization is concerned about resolving any problems caused by computer security breaches, it would be reasonable to look into the advanced search capabilities of a SIEM platform and emphasize on the reporting and data visualization features of the SIEM solution. It will save valuable time and resources of an organization if its SIEM is set up in a simple and easy to use way for storing and locating data and instantaneously generating the appropriate reports or other graphic formats.
However, performance is less valuable without context in the forensics case. Much of the current debate in the computer security space tends to accentuate the ability of convergence between computer forensics and SIEM in the area of real-time security analytics rather than differentiate the two areas. The underlying issue is what features do the current SIEM solutions provide that can assist in data examination and analysis and which features should be included in a SIEM platform in order to satisfy some of the computer forensics requirements.
You can read the original article here.
There are many misconceptions about cloud security, and it starts with basic misunderstandings about what “the cloud” even is.
Essentially, the cloud is anything hosted and accessed virtually. Webmail systems like Gmail, and social networking sites like Facebook and Twitter are in the cloud. Really, the entire internet is the cloud!
As Sophos experts explain in a new whitepaper describing best practices for cloud security, the most important thing to remember is that when you put data in the cloud, you need to understand how it’s being protected. You shouldn’t assume that security is being taken care of for you.
To help you take the necessary steps to protect your online assets in the cloud, this free Sophos whitepaper defines different cloud models and the unique benefits and challenges of each type; and offers tips for implementing security best practices.
The paper also delves into Amazon Web Services (AWS) and the shared responsibility model – it explains the kinds of security AWS provides, and what security you need to put in place yourself.
Sophos UTM: modular security that auto-scales with the AWS cloud
Sophos UTM with Auto Scaling gives you complete security, from the network firewall to endpoint antivirus, in a single modular system. Sophos UTM integrates with the AWS infrastructure to provide high availability and scalability. And it simplifies your IT security and saves money by combining multiple security solutions, and increases visibility through detailed logs and reports.
Sophos is an advanced tier AWS technology partner, and our security products protect thousands of customer environments running on AWS. We’ve also been awarded the AWS Security Competency designation.
Learn more at sophos.com/AWS.
You can read the original article here.
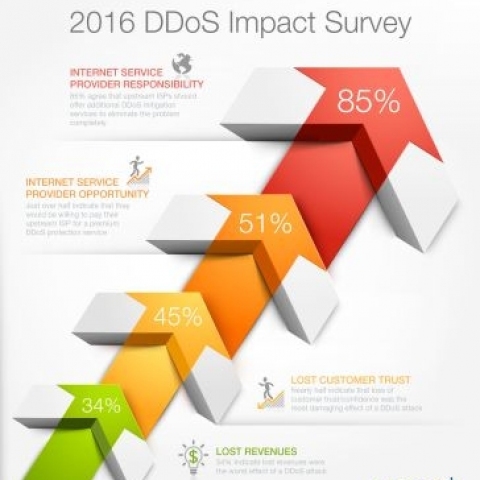
Corero released the results of our annual DDoS Impact Survey, which polled technology decision makers, network operators and security experts about key DDoS issues and trends that Internet service providers and businesses face in 2016.
Nearly half (45%) of the survey participants indicated that loss of customer trust is the most damaging consequence of DDoS attacks to businesses. Additionally, 34% of survey participants said lost revenue was the worst effect. Sadly that is not surprising, as network or website service availability is crucial to ensure customer trust and satisfaction, and vital to acquire new customers in a highly competitive market. When an end user is denied access to Internet-facing applications or if latency issues obstruct the user experience, it immediately impacts the bottom line.
Certainly, DDoS attacks get the most attention when a firewall fails, service outage occurs, a website goes down or customers complain. But companies should be concerned about DDoS attacks even when the attacks are not large-scale, volumetric attacks that saturate a company’s network and associated server infrastructure. Industry research, as well as our own detection technology, shows that cyber criminals are increasingly launching low-level, small DDoS attacks.
The problem with such attacks is two-fold: small, short-duration DDoS attacks still negatively impact network performance, and—more importantly, such attacks often act as a smokescreen for more malicious attacks. While the network security defenses are degraded, logging tools are overwhelmed and IT teams are distracted, the hackers may be exploiting other vulnerabilities and infecting the environment with various forms of malware. Small DDoS attacks often escape the radar of traditional scrubbing solutions. Many organizations have no anti-DDoS systems in place to monitor DDoS traffic, so they are not even aware that their networks are being attacked regularly.
The survey also asked participants about their current methods of handling the DDoS threat; nearly one third (30%) of respondents rely on traditional security infrastructure products (firewall, IPS, load balancers) to protect their businesses from DDoS attacks. Those companies are very vulnerable to DDoS attacks because it’s well documented that traditional security infrastructure products aren’t sufficient to mitigate DDoS attacks.
An overwhelming majority (85%) of respondents indicated they believe upstream Internet Service Providers should offer additional security services to their subscribers to remove DDoS attack traffic completely. Furthermore, 51% responded that they would be willing to pay their Internet Service Provider(s) for a premium service that removes DDoS attack traffic before it is delivered to them, and 35% indicated they would allocate 5-10% of their current ISP spend to subscribe to this type of service. Clearly there is market demand for protection services from Internet Service Providers, and organizations are willing to pay for a service that protects them from DDoS attacks.

You can read the original article here.