News
CyberArk, the global leader in privileged access security, today issued a new research report, “The CISO View: Protecting Privileged Access in DevOps and Cloud Environments.” Based on the direct experiences of a panel of Global 1000 CISOs, the report provides advice for security teams to help effectively assess risk, drive developer collaboration, and prioritize steps to protect DevOps processes while maintaining developer velocity.
The report is part of The CISO View industry initiative and features contributions from executives at leading organizations who are adopting DevOps methodologies and tools, including American Express Company, American Financial Group, Asian Development Bank, Carlson Wagonlit Travel, CIBC, GIC Private Limited, ING Bank, Lockheed Martin, NTT Communications, Orange Business Services, Pearson, Rockwell Automation and Starbucks. Sponsored by CyberArk, the initiative brings together leading CISOs for peer-to-peer information sharing to help security teams build effective cyber security programs.
While security strategies should address privileged access and the risk of unsecured secrets and credentials, they should also closely align with DevOps culture and methods to avoid negatively impacting developer velocity and slowing the release of new services. Despite this, 73 percent of organizations surveyed for the 2018 CyberArk Global Advanced Threat Landscape report have no strategy to address privileged access security for DevOps.
The report summarizes five key recommendations based on the real-world experiences of participating CISOs, including:
- Transform the security team into DevOps partners – Ensure security practitioners and developers have the right skills, make it easy for developers to do the right thing, encourage collaboration and adopt agile DevOps methods within security.
- Prioritize securing DevOps tools and infrastructure – Set and enforce policies for tools selection and configuration, control access to DevOps tools, ensure least privilege and protect and monitor infrastructure.
- Establish enterprise requirements for securing credentials and secrets – Mandate the centralized management of secrets, extend auditing and monitoring capabilities, eliminate credentials from tools and applications, and develop reusable code modules.
- Adapt processes for application testing – Integrate automated testing of code, compel developers to fix security issues using a “break the build” approach and consider a bug bounty program.
- Evaluate the results of DevOps security programs – Test secrets management solution deployments, measure and promote improvements and educate auditors.
“This CISO View report captures the experiences and recommendations of senior executives who are securely embracing DevOps workflows,” said Marianne Budnik, CMO, CyberArk. “For organizations embarking on digital transformation initiatives, it has never been more important to align security and risk postures across new tools and technologies. In understanding organizational and operational challenges, security teams can more effectively drive productive discussions across executive, security and developer teams.”
This report is the third in The CISO View report series, which was developed in conjunction with independent research firm Robinson Insight and relies on the insights and guidance contributed by The CISO View panel of Global 1000 CISOs, members of the security community and other industry experts.
To download “The CISO View: Protecting Privileged Access in DevOps and Cloud Environments” and other reports in the series, visit https://www.cyberark.com/cisoview/.
Sophos XG Firewall and Synchronized Security continue to innovate and push the envelope of what’s possible with cybersecurity.
If you’ve had a chance to review our latest 2019 Threat Report, you know that threats and attacks are changing, and so is the role your firewall plays in providing a defense.
For most of the past decade, attackers have built up a vast repertoire of automation, coupled with exploitable vulnerabilities, in an attempt to rapidly attack targets and evade security measures or protection at the network and endpoint level.
But now, some sophisticated attackers are turning to more targeted and inherently unpredictable manual network hacks, using brute force to gain a foothold on the network, and strike out from there as if they were a resident network administrator. In some respects, we’ve now come full-circle with modern attacks now taking advantage of age-old security issues like weak passwords.
The role of the firewall in protecting against these hacks and attacks has similarly evolved. Long gone are the days where the firewall was like a medieval moat and castle wall for your protected network. We’re now at a point where you can’t necessarily trust who or what is operating within the proverbial castle walls.
Forrester refers to this situation as “zero-trust”. Essentially it means that devices and users on your network need to establish or prove trust, and if something proves untrustworthy – take action. It’s a great model that’s having widespread positive impacts on IT security. A perfect example is the use of multi-factor authentication as an extremely effective tool in establishing user trust.
On the firewall side, network segmentation or even micro-segmentation is gaining a lot of momentum in response to the evolving threat landscape.
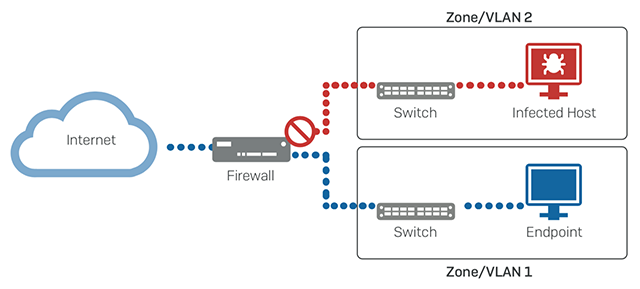
The principle is sound – segment your network into smaller and more granular subnets, and secure them together through your firewall to limit exposure in the event that one segment becomes compromised. In practice, it works great, but in some cases it can add unwanted expense, infrastructure, management overhead, and impact performance.
While the ideal solution would obviously be to firewall every device on the network separately, it’s simply not practical. However, you can get one of the key benefits of that strategy, today.
Introducing Lateral Movement Protection
Sophos XG Firewall v17.5 recently introduced Lateral Movement Protection, a new Synchronized Security feature that effectively provides an adaptive micro-segmentation solution. With Lateral Movement Protection, each individual endpoint is effectively on its own segment – able to be isolated in response to an attack or threat – regardless of the network topology. And without any added cost, infrastructure, overhead, or performance impact.
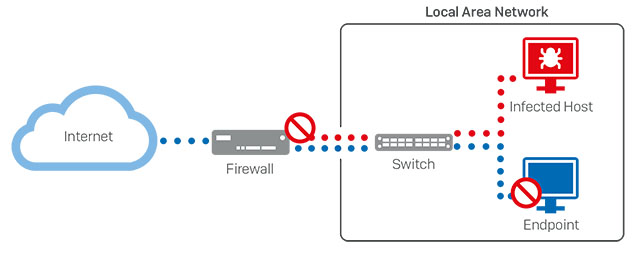
How do we do it?
By integrating our firewall and endpoint products together, they can share health, status and other important security information through a continuous Security Heartbeat™ connection. That enables both products to use this shared telemetry to respond to an active adversary or threat on the network. When any kind of attack is detected, the endpoint Heartbeat status changes, and triggers an automated response that has the firewall coordinating and synchronizing a defense.
Not only will the firewall cut-off network access for the compromised device at the firewall, it will also advise all the healthy endpoints on the network to isolate and ignore all traffic originating from the compromised host. The combined solution provides an adaptive micro-segmentation – at the individual endpoint level. And it doesn’t require any additional infrastructure or management, and has zero performance impact. It’s the ultimate emergency response strategy, for any network.
How do you get it?
All you need is our award-winning XG Firewall and the world’s best next-gen endpoint, Intercept X. They are both super easy to deploy. In fact, you don’t even need to replace your existing firewall to get all the great benefits of Sophos Synchronized Security.
You can deploy XG Firewall inline with your existing firewall and even deploy Intercept X alongside your existing desktop AV product – it’s easy, risk-free, and brings tremendous visibility, protection and response benefits to your network.
Firewall best practices
Check out our Firewall Best Practices Guide for more information on how to optimize your network protection.
Sophos, a global leader in network and endpoint security, today announced that it has acquired next-generation cloud infrastructure security company, Avid Secure. Avid Secure offers an artificial intelligence-based cloud security analytics, compliance, and DevSecOps platform to provide effective end-to-end protection in public cloud services such as AWS, Azure, and Google.
Founded in 2017 by a team of highly distinguished leaders in IT security, Avid Secure uses artificial intelligence and automation to address the real-world challenges of effective cloud security including lack of workload visibility, and the constant monitoring required to stay ahead of today’s sophisticated attacks. Avid Secure is a small, privately owned company with headquarters in San Francisco, Calif. and engineering operations in Gurgaon, India.

“The accelerated adoption of public cloud environments is presenting new data security challenges to organizations. With the cloud workload protection and the cloud security posture management software from Avid Secure, Sophos will expand its current capabilities in cloud security and drive leadership in this growing space,” commented Dan Schiappa, senior vice president and general manager of Products at Sophos. “We welcome the Avid Secure team to Sophos and are excited to bring their transformational technology into our portfolio, strengthening our ability to offer the best protection for our customers’ data on endpoints and networks, wherever their services are hosted.”
“We built the Avid Secure platform to revolutionize the security of public cloud environments in a process efficient way,” said Nikhil Gupta, CEO and co-founder at Avid Secure. “We are proud of our innovative AI powered technology that provides enterprises with end-to-end continuous security analytics, visibility, and compliance to protect their data and maximize their investments in public cloud services. The opportunity to join Sophos in their mission to evolve cybersecurity into an intelligent, integrated system presented a perfect fit for our engineering vision. I, and the whole team at Avid Secure look forward to what we can achieve together.”
This three-day training program was designed and intended for experienced technical professionals who want to install, configure and support the XG Firewall in production environments and is the result of an in-depth study on the next generation firewall of Sophos.
The program consists of presentations and practical workshops for the enhancement of teaching content. Due to the nature of the traditions and the varied experience of the trainees, open discussion is encouraged during the training.
(3 days Training)
Tuesday 26 February 2019 – Thursday 28 February 2019
Requirement
Participants should have the Xg Engineer Certification
Recommended Knowledge
Knowledge of networking to a CompTIA N+ level
Knowledge of IT security to a CompTIA S+ level
Experience configuring network security devices
Be able to troubleshoot and resolve issues in Windows networked environments
Experience configuring and administering Linux/UNIX systems
Content
- Module 1: Enterprise Deployment Scenarios
- Module 2: Advanced Firewall
- Module 3: Authentication
- Module 4: Webserver Protection
- Module 5: RED Management
- Module 6: Wireless Protection
- Module 7: Enterprise VPN
- Module 8: High Availability
- Module 9: Troubleshooting
- Module 10: Sizing
Certification
+ exam: Sophos XG Architect
Duration 3 days
Agenda
Trainer: Micheal Eleftheroglou
Day 1 Tuesday 26 February 2019
9:30-10:15 Module 1: Enterprise Deployment Scenarios Part I
- Bridge mode
- Gateway mode
- Mixed mode
10:15-10:30 break
10:30-12:00 Enterprise Deployment Scenarios Part I
- VLAN
- Link Aggregation
- Routing protocols
12:00-12:15 Break
12:15-13:45 Advanced Firewall Part I
- Stateful inspection
- Strict policy
- Fast path
- Intrusion prevention
- Anti Dos/floofing
- Advanced Threat Protection
13:45-14:45 Break Lunch
14:45-16:15 Advanced Firewall Part II
- Asymmetric routing
- Local NAT policy
- DHCP options
- Bind to existing DHCP scope
- Country list
- Drop packet capture
- IPS tuning
16:15-16:30 Break
16:30-17:15 Webserver Protection
- Overview
- Web Servers
- Application Protection policies
- Path specific routing
- Authentication policies
- Certificates
Day 2 Wednesday 27 February 2019
9:30-10:15 Module 4: Authentication
- Single sign-on (SSO)
- LDAP integration
- Secure LDAP
- STAS (Sophos Transparent Authentication Suite
- Troubleshooting STAS
10:15-10:30 Διάλειμμα
10:30-12:00 Authentication part II
- Sophos Authentication for Thin clients (SATC)
- Troubleshooting SATC
- NTLM
- Troubleshooting NTLM
12:00-12:15 Break
12:15-13:45 Module 5: Red Management
- Overview
- RED Models
- Deployment
- Adding a RED interface
- Balancing and failover
- VLAN port configuration
13:45-14:45 Break- Lunch
14:45-15:30 Module 6: Wireless Protection
- Overview
- Access Points
- Wireless networks
- Security modes
- Deployment
- Built-in wireless
- Mesh networks
- Radius authentication
- Class Activity
15:30-15:45 Break
15:45-17:15 Module 7: Enterprise VPN
- Huge and spoke topology
- Ipsec VPN configuration
- Ipsec VPN policies
- NAT overlap
- Route precedence
- VPN failover
- Logs
- Troubleshooting
Day 3 Thursday 28 February 2019
9:30-11:00 Module 8: High Availability
- Overview
- Prerequisites
- HA packet flow
- Configuration
- HA status
- Console commands
- Logs
- General Administration
11:00-11:15 Break
11:15-12:00 Module 9: Troubleshooting
- Consolidated Troubleshooting Report
- SF loader
- Tcpdump
12:00-12:15 Break
12:15-13:45 Module 10: Sizing
- Hardware appliance models
- Hardware appliance sizing
- Software and virtual devices
- Sizing scenarios
- Class activity
13:45-14:45 Break – Lunch
14:45-17-15 Labs and Exams
We know from talking to our customer and partner community that XG Firewall delivers tremendous value to customers by providing outstanding visibility, unmatched protection, and a unique and immediate response to threats on the network.
We also love to hear what industry experts think about XG Firewall, and we thought you might want to hear what they have to say as well.
CRN Network Security Product of the Year
 For the second year in a row, XG Firewall was awarded CRN’s Network Security Product of the Year. This is a very prestigious award, as the winner is determined by solution providers that use these products every day. They consider a number of factors when determining their ratings, including but not limited to product quality and reliability; richness of product features and functionality; technical innovation; compatibility and ease of integration; and demonstrated ability to create new customer relationships or improve existing ones. This year’s survey garnered over 3,600 responses, and we outranked Fortinet, Palo-Alto Networks, Cisco, and Forcepoint to claim the top prize again this year.
For the second year in a row, XG Firewall was awarded CRN’s Network Security Product of the Year. This is a very prestigious award, as the winner is determined by solution providers that use these products every day. They consider a number of factors when determining their ratings, including but not limited to product quality and reliability; richness of product features and functionality; technical innovation; compatibility and ease of integration; and demonstrated ability to create new customer relationships or improve existing ones. This year’s survey garnered over 3,600 responses, and we outranked Fortinet, Palo-Alto Networks, Cisco, and Forcepoint to claim the top prize again this year.
PC Pro 5-Star “Recommended” review
 PC Pro is a monthly magazine consumed by 24,000 IT professionals. They recently did a deep-dive review of our XG 125w and had many great things to say. They concluded:
PC Pro is a monthly magazine consumed by 24,000 IT professionals. They recently did a deep-dive review of our XG 125w and had many great things to say. They concluded:
A superbly versatile gateway appliance that combines in-house security with cloud management capabilities.
IT Pro 5-star “Editors Choice” review
 IT Pro is a tech-focused website with an audience of 1.4 million IT professionals and decision makers.
IT Pro is a tech-focused website with an audience of 1.4 million IT professionals and decision makers.
The review (which you can read in full here) concluded:
Along with a pleasantly swift deployment, the Sophos XG 125w impressed us with its depth of security features. Adding in its seamless integration with Sophos Central, the high performance and integral 11ac wireless services makes it our recommended gateway security appliance for SMEs.
Gartner UTM Magic Quadrant Leader
![]() As you may know, Sophos was also recently named a Leader in the Gartner Magic Quadrant for Unified Threat Management (SMB Multifunction Firewalls) for 2018.
As you may know, Sophos was also recently named a Leader in the Gartner Magic Quadrant for Unified Threat Management (SMB Multifunction Firewalls) for 2018.
NSS Labs NGFW group test
![]() Sophos XG Firewall also achieved excellent results in our latest test with NSS Labs, blocking 100% of all evasions with outstanding performance in all other areas as well.
Sophos XG Firewall also achieved excellent results in our latest test with NSS Labs, blocking 100% of all evasions with outstanding performance in all other areas as well.
New to XG Firewall?
If you’re new to XG Firewall, you can learn more about why industry experts consistently rank XG Firewall amongst the top in the industry.
It’s the beginning of a new year, and we should take some time to look the security trends we expect to see over the next 12 months.
1. Security teams will need more development and engineering skills
Security teams used to focus on firewalls and endpoints, and many security professionals cut their teeth as system and network administrators. Nowadays, infrastructure is defined by code, breaches are increasingly caused by weak applications and automation is essential for understaffed teams.
This is changing the skillset required by security professionals, who need a deep understanding of applications and an ability to build automation into their tools and processes.
2. Organisations will increase their focus on software supply chains
These days, everyone relies a huge amount on open source libraries. These are often maintained very informally by loose-knit communities that are easy to infiltrate. This used to be the domain of nation states but the criminals are getting in on the action. Organisations will need to focus on keeping this area secured.
3. Application security will continue to grow
We are getting better at protecting endpoints, and attackers are shifting their focus. Legacy applications will continue to be a fertile hunting ground, and security and IT departments will need to keep up with this growing trend.
4. Threat hunting really will be driven by machine learning
It’s a bit of a cliché, but machine learning will no longer be something that you just buy. Tools and techniques that were previously the domain of data science experts are getting easier to use. It won’t be long before larger security operation centre teams are using the tools directly, rather than via models that are embedded in products.
5. Zero-trust starts to become achievable
Fourteen years after the Jericho Forum declared the end of the network perimeter, we are getting close to the point where many enterprises have a realistic chance of keeping their users off “trusted” networks. The tools, knowledge and technologies for achieving a true zero-trust architecture are rapidly maturing, and this year will continue to see improvements in this area.
Today, Amazon Web Services (AWS) announced the AWS Security Hub, with Sophos as a launch partner.
Sophos supports this industry-wide effort to consolidate and bring focus to high-priority security alerts on AWS. We believe that visibility is the best defense against today’s threats, highlighting as early as possible any alerts and events that could represent compromise.
We applaud AWS efforts to provide APIs for the AWS Security Hub. This enables sharing of security information across the AWS ecosystem, including that from Sophos, whose products generate and correlate events and alerts.
The approach that AWS has taken with Security Hub parallels the approach that we followed with Sophos Central: collecting security information and presenting it on a single screen for easy viewing, as shown below.
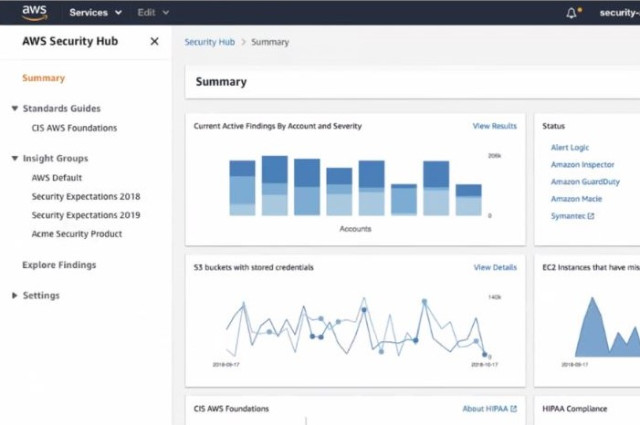
Since AWS is increasingly an extension of customers’ on-premises systems for business-critical applications, protection of AWS applications and data is essential. Now that Sophos integrates with AWS Security Hub, alerts about the AWS environment can be viewed in Sophos Central for easier management. Sophos Central provides visibility not only to events across AWS, but also across on-premises and other environments.
With protection from the industry-leading Sophos Intercept X and XG Firewall products, Sophos Central then correlates that information and automates the response with Synchronized Security.
SHI, a Sophos partner who assists customers migrating to AWS, now recommends use of AWS Security Hub. SHI has tested the connection between AWS Security Hub and Sophos Central, and sees significant benefit from the integration.
“The integration of Sophos Server Protection with the AWS Security Hub provides tremendous confidence for our customers and enables us to help migrate more organizations to the Amazon public cloud” said Chief Cloud Officer, Lee Ziliak
Sophos has also added protection of AWS S3 storage in addition to the current protection for AWS EC2 instances in Sophos Intercept X for Server. Now both EC2 instances and S3 storage buckets are discoverable from customer AWS accounts, easily enabling appropriate security policies to be applied and managed from the map display in Sophos Central, as shown below.
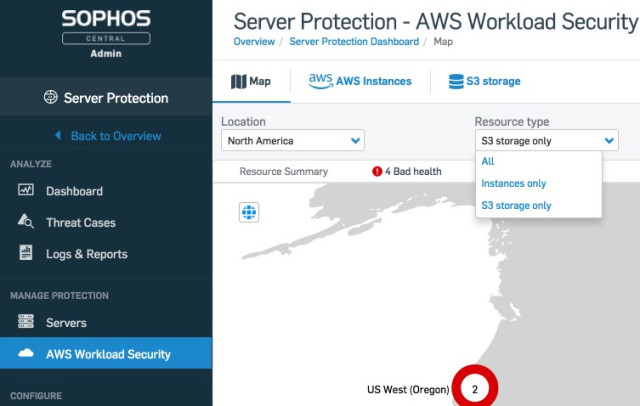
With the efforts of AWS, and the integration and protection that Sophos has added, customers of Sophos Intercept X for Server can now protect business-critical workloads and data stored on AWS, as well as on premises.
You can find out more about the partnership on our website.
For organizations whose cyber defenses may have been going the way of one dimensional, threat hunting has breathed new life into sputtering security programs.
Broadly defined as the manual practice of applying tools, tactics, procedures and intelligence to uncover advanced network attacks that have slipped past existing defenses, threat hunting is surging in popularity.
Able to easily bypass traditional, signature-based security, persistent attackers are using stealthy means to fly under the radar and travel unrestricted across corporate databases, networks and applications – and you need to assume they are already inside yours.
So how do you find them?
While actions such as log and event analysis (automated threat detection) and technologies like endpoint detection and response (EDR) have emerged to help organizations become more proactive at flagging and rebuffing these sophisticated foes, threat hunting pushes the needle even further forward with a human-driven component. Trained personnel pursue attackers while leveraging many of the same capabilities and thought processes that the adversaries use themselves.
Even if your ultimate security goal may be to pre-empt the mega breach, threat hunting is out to discover anything out of the ordinary that could indicate something is amiss in your environment – in the process vastly growing visibility into your network, reducing risk and expanding security maturity. Oftentimes, this means unearthing something that is far less deleterious – and far less thought about – than an advanced persistent threat actor, but critical nonetheless, as non-routine activity of any kind may affect your organization’s operations and bottom line.
What your team may discover on a threat hunt (or via powerful security operations center-backed experts hunting on your behalf) could range from an honest mistake to a spiteful employee to a full-blown hacker incident. As an accountable and responsible security professional, you should want to know about all of them.
1) Hackers “Living off the Land”
As simple as it is to find fault with the current state of security, many businesses are making things more onerous than ever on network intruders to succeed. You may be surprised to learn that this reality has forced miscreants to turn to self-sustainable practices. A tactic known as “living off the land” has grown in popularity in recent years among all types of malicious hackers and typically involves them using tools already approved and installed by your IT team – for instance, PowerShell, a legitimate admin tool used to automate tasks – and using them to run exploits (especially fileless attacks), harvest credentials and traverse the network.
2) Unusual User Behavior
Threat hunts can also turn up anomalous user activity, which may hint at possible threats involving a rogue insider. Actions that could indicate a wayward employee include multiple requests to escalate privileges, large data exfiltration at odd hours, late-night logins and the mass downloading or deletion of files – all of which are uncharacteristic of their normal duties and potentially indicative they are planning, for example, to switch jobs or exact revenge on the business.
3) Old or Unused Machines
In an era of technology sprawl, it may be easy to lose track of active workstations and other systems, which still introduce risk to a company. One of Trustwave’s threat hunters told me about one case in which his team identified IP addresses within a network that were behaving strangely. The hunters turned that information over to the customer, which took three weeks to physically identify the offending machines – they were stored away, apparently unknowingly, in a cabinet somewhere.
4) Policy Breakers Cutting Corners
The insider threat doesn’t always involve malice – sometimes an employee is trying to do the right thing, albeit “overlooking” security policies and ramifications. Going back to the earlier PowerShell example, a worker in accounting may have discovered the tool to be useful for automating reporting but is unaware that attackers may be also able to leverage it to run malicious scripts.
5) Shadow IT
There are plenty of ways to invite malicious content or data-leakage risks into your organization, and the proliferation of web- and cloud-based software has opened that door even wider. While many employees (including C-level executives) are installing applications, often citing their desire to use them to improve productivity, they usually end up being unmanaged and grow a business’ attack surface. Sometimes, a user’s motivation for such a download isn’t as work-focused: Our aforementioned threat hunter recently turned up a “Pokemon Go” mining operation in which a member of the IT team was using several systems to “catch” the animated creatures.
With the knowledge of what a threat hunt helps bring to the surface, you can immediately take risk-reducing actions within your organization. Remember, it’s not always the APT adversary who can bring you down.
You can read the original article, here.
Martin Sugden, CEO of Boldon James, was in Brazil last week and shared a warning that organizations need to comply with LGPD: “companies need to know what kind of information they have, were it is stored and how to deal with it”.
While organizations are increasingly concerned with data protection, many do not have the right tools to protect their information, and do not apply data classification to their data collection, processing, and handling processes. Systems have been designed to view data as belonging to the company not the individual that shared it with the organization. With the arrival of GDPR and LGPD, organizations are having to adapt to the new reality.
Martin Sugden, CEO of Boldon James, was in Brazil last week to meet clients and local partners and on November 29 he met with key members from the local business media to discuss how organizations comply with LGPD: “Companies need to know what kind of information they have, where it is stored and how to deal with it”.
According to Sugden, “Once you understand what information you have, and where the information is held you can make informed decisions about the level of security to be applied from who can access it to should it be encrypted or anonymized to do, I even need to keep it. The current security strategy must take into account that GDPR and LGPD rules are rigid and that any information should be protected wherever it is, including mobile devices, in the supply chain or with advisers. Your users need to be trained and understand your policies”, he commented.
“Recent surveys point out that at least 1/3 of IT executives claim that mobile security is one of their biggest concerns, especially as modern working practices involving mobile devices, social media and BYOD make it easy to lose or inadvertently share data”, said Martin Sugden.
According to the CEO of Boldon James, financial services companies report the most concerns about data security, but it is these companies that invest more in data classification policies and tools. With the GDPR and LGPD, the banking and financial institutions must increase their investments in data security. “Other organizations should follow the same path, so they can better protect their vital business data”, Sugden emphasizes.
Boldon James has been working for 30 years on the development of data classification techniques, being responsible for numerous pioneering data classification projects in large companies in several countries.
The Boldon James Classifier solution allows labels to be filtered to handle, hold, or send documents safely outside of organizations, either to mobile devices, partners or customers. For example, last year a USB was found on a London street with 76 highly classified files regarding the travel routes taken by Queen Elizabeth when using Heathrow airport, including airport patrol timings and the identity of personal protection officers who had access to certain secret areas at the airport. This data should not be downloadable and if it was it should be encrypted. A simple classification label using Classifier would have triggered a Rights Management tool to stop this happening.
“Do you know what is critical in your company? If data classification technology were to be applied in conjunction with say a Data Loss Prevention solution or Rights Management, this sensitive data loss would most likely not happen”, said Martin Sugden.
You can read the original article, here.
Sophos is pleased to announce that the early access program (EAP) for XG Firewall management through Sophos Central is now available for you to take a test drive.
As you probably know, Sophos Central is the ultimate cloud-management platform for all of your Sophos products, and it now includes XG Firewall. It makes day-to-day setup, monitoring, and management of your network protection easy. You can quickly and easily add all your XG Firewalls into Sophos Central, giving you secure access to your entire estate from anywhere.
With XG Firewall joining Sophos Central, you can now manage all your Sophos Synchronized Security products from a single cloud console. Intercept X and the rest of the Sophos suite of protection are all there, at your fingertips: mobile, email, wireless, and more.
How to get started in three easy steps:
Check out this step-by-step knowledgebase article for full details, but it’s really as simple as 1, 2, 3:
- First, you’ll need a Sophos Central account if you don’t already have one. Head on over to cloud.sophos.com to create a trial account or login, and while you’re there, enroll in the Early Access Program by clicking your account in the upper right corner of the console.
- Next, login into your firewall and add your Sophos Central credentials to the Central Synchronization screen and select the option to Manage from Sophos Central.
- Then, return to Sophos Central and confirm adding your Firewall. That’s it! Now you can securely access your firewall from anywhere through Sophos Central.
Join the EAP Community Forum to share your feedback with the Sophos team and others.
Additional features coming soon
Over time, additional features will be added to Sophos Central management of your XG Firewall including:
- Backup management and storage for your regularly scheduled firewall backups
- Firmware update management to make multiple firewall updates easy
- Light-touch deployment to enable easy remote setup of a new firewall
And much more!
FAQ
Below are the most frequently asked questions about Sophos Central Management of XG Firewall. You can add your own to the EAP Community Forum where our team will do our best to answer.
Question: Is there a limit on how many firewalls or what type can be managed by Sophos Central?
No, there is no limit. Sophos Central can manage any XG Firewall, hardware, virtual, software or Azure as long as it has a WAN internet connection to connect to Sophos Central.
Question: Is there a charge for Sophos Central management of XG?
No, there is no charge and no special license required for either the EAP or when this capability is generally available. Anyone can setup a Sophos Central account at no charge to manage their XG Firewalls.
Question: Do I need other Sophos products to take advantage of Sophos Central Management of XG Firewall?
No, you don’t need any other Sophos Product to take advantage of Sophos Central Management of your XG Firewalls.
Question: How does the connection and information sharing work between XG and Sophos Central?
XG Firewall initiates a secure TLS encrypted connection with Sophos Central to share information. Since the connection is outbound from the firewall, it is completely secure and a simple way to manage firewall devices remotely without exposing the management interface login on the WAN. No port or other configuration is required. Since there is no storage of the configuration or log or reporting data in Sophos Central, there is no synchronization required – any changes made through Central are taking place on the device as they are made.
Question: Does Sophos Central copy or store any of the data from my Firewall in the cloud?
No, all your Firewall data and configuration information remains on your Firewall.
Question: What version of firmware is required on XG Firewall to manage it from Sophos Central?
XG Firewall v17.5 (or later) is required. This was released in late November and is currently being rolled out in stages to customer systems. If you haven’t already received the automatic update notice in your Firewall console, you can download the firmware update from MySophos.
Question: What are the various central management products that are available for XG Firewall and their differences?
Sophos Central is ideal for Sophos customers who want to monitor and manage their firewalls conveniently alongside their other Sophos products in Sophos Central: It offers a full list of all your firewalls under management along with quick access to manage any of them individually (one-at-a-time). It does not yet offer any policy template tools or alerting and monitoring like Sophos Firewall Manager.
Sophos Firewall Manager (SFM) is our on-premise product that enables rich powerful multi-device management features. It is ideal for organizations managing a large number of devices or those who want to take advantage of the policy template and other multi-device management tools.
You can read the original article, here.
50% of employees admit to clicking links from unknown senders. But which 50%? It’s time for a targeted approach to cybersecurity training.
Teaching users with simulated phishing attacks and training is half the battle in the race against phishing attacks. But what about the real test for users? The phishing emails, the unverified USBs, the ones that cripple the customer database on a Sunday at 1am?
Sophos Phish Threat now offers a breakthrough in cybersecurity training with Sophos Synchronized Security. By connecting Sophos Email and Phish Threat, we’ve taken the guesswork out of finding those riskier users in your organization – those who need a more targeted approach to training.
A breakthrough in cybersecurity training
50% of employees* admit having clicked on an email link from an unknown sender in the last 6 months that turned out to be malware or a scam. Regular attack simulations and security awareness training make all the difference, with existing Phish Threat customers able to reduce susceptibility to attack by 31% in just four tests (that’s opening and still clicking to you and me).
But while you train all users on cyberthreats, how do you find and train the weakest links in your organization?
Sophos Synchronized Security now lets you do that by connecting Sophos Email and Phish Threat. It helps you identify users who regularly click malicious links or violate other security policies, and lets you enroll them directly into targeted training.
Sophos Email and Phish Threat
Available now, Sophos Email Advanced is the first Secure Email Gateway to feed intelligence directly to a security awareness training solution for the best results.
The new Sophos Email Advanced At Risk Users report highlights which users are clicking email links rewritten by Time-of-Click URL protection, and identifies those who have either been warned or blocked from visiting a website due to its risk profile. You can then enroll those users in Phish Threat simulations and security awareness training with one click – increasing their threat awareness and reducing risk.
Take the guesswork out of training today
The greatest risk from attackers is not individual campaigns, but instead connected attacks, where vehicles like phishing are used to first penetrate your defenses.
Sophos is already the only vendor to offer a layered security defense, with protection at every point of the attack chain. Synchronized Security goes beyond that to take the guesswork out of finding those users who need a more targeted approach to training. Find out more about Sophos Email and Sophos Phish Threat today, and take the 30 day free trial.
More than ever, customers understand their right to data privacy. As major brands continue to lose sensitive data to cybercriminals in high-profile cloud security failures, customer trust in companies across industries is fading. Only 25 percent of consumers believe most companies handle their data responsibly, according to PricewaterhouseCoopers (PwC). As a result, secure, transparent data handling practices are more imperative than ever.
New regulations signal that governing bodies are also taking the enterprise’s responsibility for data privacy very seriously. The Brazil Privacy Act and the California Consumer Privacy Act support the consumer’s right to understand how their data is collected and used, and the New York Department of Financial Services (NYDFS) requirements are among the first regulations to address cloud security risks. Proposed rules require financial institutions to conduct vulnerability assessments and practice data classification and safe data management, whether the data resides on-premises or in the cloud.
Misconfigurations Cause Database Security Mayhem
Despite increased pressure to protect customer data, security teams are still struggling to address database security risks. Misconfigured servers, networked backup incidents and other system misconfigurations resulted in the exposure of 2 billion data records in 2017, according to the “IBM X-Force Threat Intelligence Index 2018” — that’s a 424 percent increase in such data breaches over last year’s total.
Cybercriminals are innovating quickly to take advantage of enterprise cloud security challenges. Many are using and creating open source tools to scan the web for unprotected cloud storage and, in some cases, locking these systems for ransom. Results from a Threat Stack study indicated that the majority of cloud databases are unprotected or otherwise misconfigured. Researchers attributed the prevalence of misconfigurations to employee negligence and insufficient IT policies.
Why The Enterprise Cloud Is Vulnerable
Still, it would be unfair to blame the current state of enterprise cloud security on employee negligence — at least, not entirely. Critical misconfigurations are technically the result of inadvertent insider error, but the reality is a bit more complex. Correcting configurations and compliance risks is difficult because security teams lack actionable visibility into cloud risks. There’s a glut of security risk to deal with, and traditional approaches to assessing risk result in an abundance of data with little actionable intelligence.
The enterprise cloud environment is complex and difficult to capture with vulnerability assessment tools designed for physical network and endpoint risk assessments. The unstructured, NoSQL landscape of the big data on cloud evolves on a near-daily basis to accommodate new forms of unstructured data. It’s no wonder that trying to assess database security risk across heterogeneous environments is often compared to finding a needle in a haystack.
Layered vulnerability assessments are crucial to protect against cloud security and compliance risks. Under some recent regulatory requirements, in fact, vulnerability assessments are mandatory. However, the enterprise needs vulnerability solutions that can support the scale of cloud database-as-a-service (DBaaS), traditional on-premises databases, warehouses and big data environments in a meaningful way.
Advanced analytics are necessary to sort through complex event data to correlate patterns and find true outliers that are associated with meaningful risk of data loss or advanced threats. The sheer volume and variety of data in the enterprise cloud requires proactive vulnerability assessment. A vulnerability assessment solution should automate risk prioritization, recommend remediation and simplify complex compliance requirements.
How To Achieve Real-Time Security And Compliance In Cloud Or Hybrid Environments
Reducing risk requires visibility and control with an adaptive, real-time approach to understanding exposure. In a database environment, assessments should actively examine privileges, authentication, configuration, versioning and patching. Finding and remediating advanced threats from insiders, ransomware and data breaches requires advanced analytics. Your vulnerability assessment solution should rank risks based on the importance of data and breach likelihood and recommend remediation actions.
Security and risk are convening in the enterprise, and vulnerability tools should deliver risk intelligence that can be shared with the chief information officer (CIO), chief security officer (CSO) and chief risk officer (CRO). Enterprise cloud environments are complex, but a vulnerability assessment tool can provide a consolidated and actionable view into risk, remediation, compliance and policy. To drive continued value, however, a vulnerability assessment solution must scale to new services as new applications, databases and cloud services are deployed over time.
The cloud has shifted the landscape and created the need for a new approach to assessing risks. If understanding compliance and configurations feels like finding needles in a haystack, it may be time to automate. Data privacy is now a compliance and customer imperative, and understanding the state of your databases is critical, so aim to scale your security assessments with a solution designed for the complexities of the enterprise cloud environment.
You can read the original article, here.
Sophos Intercept X with EDR has been recognized again as an industry leader. Among the winners in Computing’s Security Excellence Awards, Intercept X took home the award for Security Innovation of the Year for the second year in a row.
The Security Excellence Awards, which took place on 21 November in the heart of London, is hosted by UK-based tech magazine Computing as part of its annual Enterprise Security & Risk Management Summit. The ceremony celebrates the industry’s best security companies, solutions, products and personalities across 20 categories.

On the Security Innovation of the Year award, Computing says:
“The security industry and its products are continually evolving, as it keeps pace with the new tricks and tactics developed by hackers to attack corporate networks. This award will be given to the product or service which demonstrates something truly new and original”.

Learn more about our award-winning Intercept X Advanced with EDR or try it for free today.
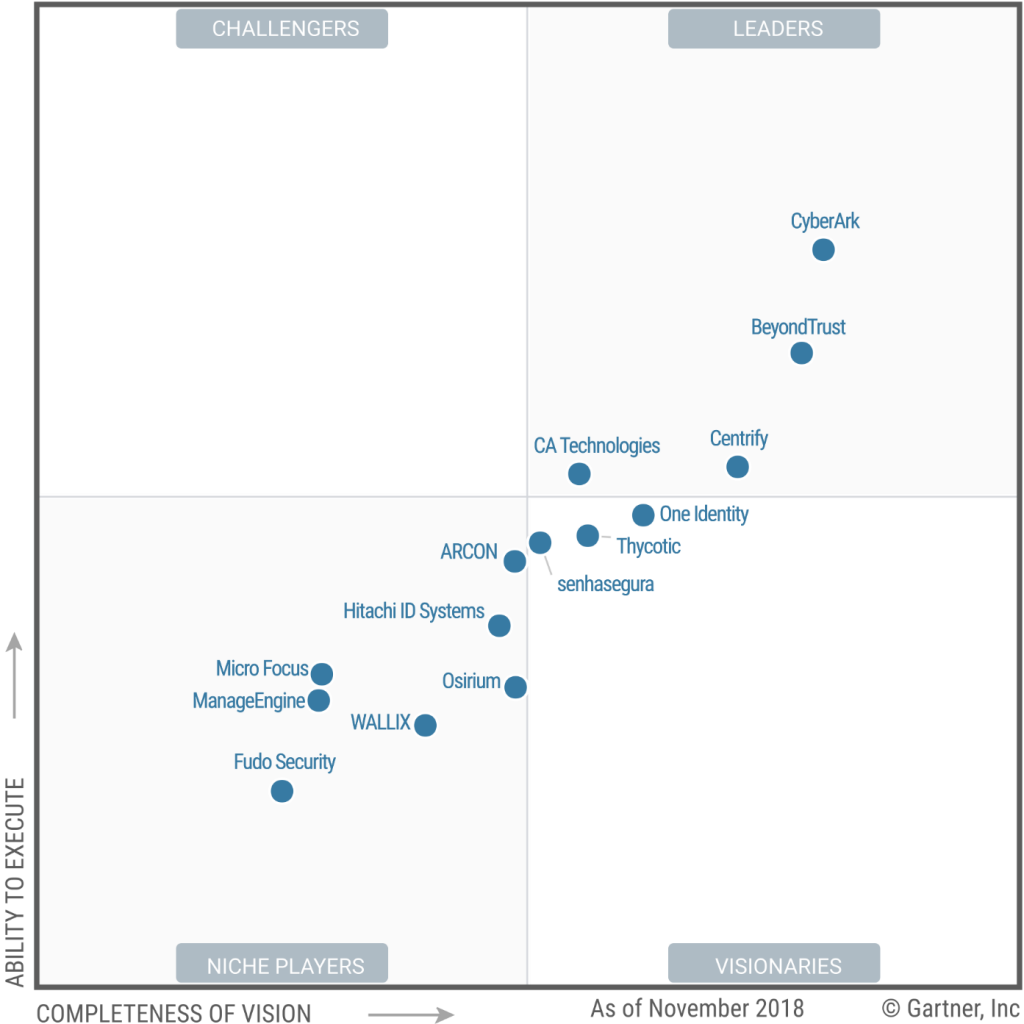
Today marks a major milestone with the release of the first-ever Gartner 2018 Magic Quadrant for Privileged Access Management.* CyberArk was named a Leader, positioned highest for ability to execute and furthest for completeness of vision.
As the market pioneer, not only is this a major accomplishment for us as an organization, but it’s also an important milestone for the market at large. According to the report, “Privileged access management is one of the most critical security controls, particularly in today’s increasingly complex IT environment. Security and risk management leaders must use PAM tools in a long-term strategy for comprehensive risk mitigation.”
As the company recognized for establishing the market category, we are extremely proud to be named a Leader. We remain laser-focused on helping organizations to secure the enterprise by delivering innovative solutions that break the attack chain and protect their most valuable assets. We will continue our work to make a quantifiable impact on the security of companies and governmental organizations around the world, enabling them to adopt digital transformation strategies with confidence.
As we celebrate being named a Leader in the Gartner Magic Quadrant for Privileged Access Management, we’d like to thank all of our incredible customers, partners and employees who have been, and will continue to be, the cornerstone of our success.
Read the Full Report
Download the full 2018 Magic Quadrant for Privileged Access Management report here. To learn more about the CyberArk Privileged Access Security Solution or to see what customers and other industry experts say about us, visit our website.
You can read the original article, here.
CyberArk announced it was named a Leader in “The Forrester Wave: Privileged Identity Management, Q4 2018.”1 Based on Forrester’s evaluation of the 11 most significant privileged identity management vendors, CyberArk ranks highest in both the current offering and market presence categories.
According to the report, “The [CyberArk] solution has strong password safe, session management, and privileged threat analytics, as well as the broadest DevOps support of any vendor evaluated in this Forrester Wave.” CyberArk received the highest possible score in report criteria including customer satisfaction; privileged threat/behavior analytics; privilege delegation and escalation; privileged session monitoring plans; and container support plans.
The CyberArk Privileged Access Security Solution is the most comprehensive solution on the market for protecting against the exploitation of privileged accounts, credentials and secrets anywhere – including on the endpoint and across on-premises, hybrid cloud and DevOps environments.
“This Forrester Wave report reinforces, in our opinion, the importance of privileged identity management for controlling both human user and machine access to an organization’s most sensitive assets and information,” said Marianne Budnik, CMO, CyberArk. “We are proud to be named a Leader by Forrester, and appreciate the support of our customers and partners who look to CyberArk as a trusted advisor and partner in their efforts to invest in modern infrastructure, improve business agility and drive new opportunities for growth.”
To download a complimentary copy of The Forrester Wave: Privileged Identity Management, Q4 2018 report, visit https://www.cyberark.com/resource/forrester-wave-privileged-identity-management/
The product behind the most successful Early Access Program (EAP) in Sophos history, Intercept X Advanced with EDR, is now generally available to all.
In September we first made our new endpoint detection and response (EDR) capabilities available and the response has been overwhelming. In just two months we have had close to 1,000 customers and 28,000 endpoints use Intercept X Advanced with EDR, and the feedback has been incredible.
What are EAP participants saying about Intercept X Advanced with EDR?
- It makes our team more efficient
- The ability to isolate a machine while we investigate is really helpful
- Everything we have asked it has done … and it did things we didn’t think about
- It makes it easy to understand at lightning speed what is happening, so we can quickly remediate
We asked EAP participants how they are using Intercept X with EDR and their top use cases include:
- Report on the state of their security and compliance posture
- Detect attacks that may have gone unnoticed
- Search for indicators of compromise across all their endpoints
- Determine the scope and impact of an incident
- Investigate attacks that are tagged as suspicious (but may not be malicious)
- Conduct previously unattainable malware analysis
- Quickly remediate incidents by cleaning and blocking the file across all their machines
Sophos Intercept X Advanced with EDR integrates intelligent endpoint detection and response with the industry’s top-rated malware detection, top-rated exploit protection, and other unmatched endpoint protection features. It replicates the tasks normally performed by skilled analysts, so organizations can add expertise without having to add staff.
Unlike other EDR solutions which rely on highly skilled human analysts to ask questions and interpret data, Intercept X Advanced with EDR is powered by machine learning and enhanced with curated SophosLabs threat intelligence. When an investigation is concluded, analysts can respond with a click of a button.
Learn more or try it for free today.
You know the old saying, “The rich get richer”? Well, our UTM 9 platform is feature rich, but every year we pack more and more features into it. This year is no exception with our UTM 9.6 release.
Here’s what’s included in UTM 9.6
Let’s Encrypt integration
- Generate and renew Let’s Encrypt certificates from within the UTM
- Generated certificates can be used in all UTM components
Web Application Firewall (WAF) page customization
- Custom themes for all error pages that are delivered via the WAF
- Enables the use of a custom corporate identity on all pages
Manual Sandstorm submission
- Allows an admin to upload a file for detonation within Sophos Sandstorm
- Files that have not been received via email or web download can also be analyzed with Sophos Sandstorm
Persistent Sandstorm reports
- Enhanced reporting for Sandstorm activity over time and with historic information
- Reporting also covers hash lookup based results from Sophos Sandstorm
Other enhancements
- Unified RED firmware with improved 3G/4G support
- Submission port support in SMTP proxy
- Configurable listen address in SMTP proxy
- New advanced thread protection library with better performance and protection
The full release notes can be found on the Sophos Community.
How to get it
The release will be rolled out automatically in phases over the coming weeks. For anyone that wants the latest and greatest now, you can download the latest firmware yourself.
If you have any questions, check out the Sophos UTM 9 Community Forums.
We’re excited to announce that we’ve been awarded Security Vendor of the Year at the CRN UK Channel Awards 2018!
The CRN Channel Awards celebrated its 25th anniversary by recognising exceptional achievements in the UK channel industry over the past 12 months.
 In CRN’s words: Security Vendor of the YearThe award recognises the overall contribution that [Sophos] is making to business development in the channel, in terms of its product range and development, channel and marketing programmes, and service and support.
In CRN’s words: Security Vendor of the YearThe award recognises the overall contribution that [Sophos] is making to business development in the channel, in terms of its product range and development, channel and marketing programmes, and service and support.
Sophos focuses 100 percent of its resources on building products and programs with the needs of channel partners in mind. If you’re interested in working with us, take a look at the Sophos Partner Program and learn how, together, we can take your business to the next level.
You can read the original article, here.
For a second consecutive year, Sophos has been named a CRN Tech Innovator for Intercept X with deep learning.
The Channel Company’s annual CRN Tech Innovator Awards honor standout hardware, software, and services that are moving the IT industry forward.
The editors at CRN evaluated 300 products across 34 technology categories using criteria including technological advancements, uniqueness of features, and potential to help solution providers solve end users’ IT challenges. Sophos Intercept X with deep learning took top honors in the Security – Endpoint category.
Unlike other endpoint solutions, Sophos Intercept X with deep learning stops never-before-seen malware, unknown exploit variants, stealth attacks, and ransomware. Intercept X learns the observable threat landscape, processes hundreds of millions of samples, and makes more accurate predictions at a faster rate than traditional machine learning solutions.
When used together with other Sophos protection such as XG Firewall or Intercept X for Server, Intercept X shares threat intelligence, enabling automated responses to threats that don’t require manual intervention. Through Sophos Central, administrators can remotely install Intercept X to run alongside existing endpoint security software from any vendor, immediately boosting their endpoint protection.

In addition to CRN, SE Labs and other independent third-party testers and analysts consistently rank Sophos Intercept X as the industry’s top endpoint protection product. But you don’t need to take their word for it. We’re always happy to show you how Intercept X performs against real-world endpoint attacks, including never-before-seen malware, ransomware, and exploits.
To learn more about Intercept X, download the Intercept X Advanced with EDR datasheet or sign up for a demo.
You can read the original article, here.
The team is hard at work putting the finishing touches on our next major release of XG Firewall, and it is a huge release! XG Firewall v17.5 brings some amazing new Synchronized Security features as well as many of your most-requested features.
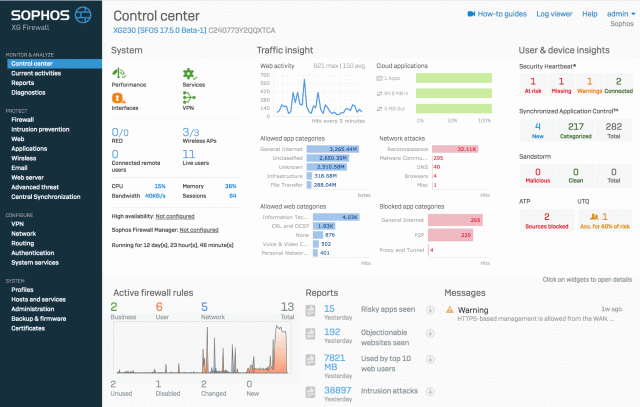
The best part is you can start taking advantage of many of these new capabilities today, as part of the Early Access Program.
What’s new in XG Firewall v17.5
Here’s a quick overview of the key new features in v17.5:
- Synchronized Security – lateral movement protection – extends our Security Heartbeat™ automated threat isolation to prevent any threat from moving laterally or spreading across the network, even on the same subnet. The firewall instructs all healthy endpoints to completely isolate any unhealthy endpoints.
- Synchronized User ID – utilizes Security Heartbeat™ to greatly streamline authentication for user-based policy enforcement and reporting in any Active Domain network by eliminating the need for any kind of server or client agent.
- Education features – such as per-user policy-based control over SafeSearch and YouTube restrictions, teacher enabled block-page overrides, and Chromebook authentication support.
- Email features – adds Sender Policy Framework (SPF) anti-spoofing protection and a new MTA based on Exim, which closes a couple of top requested feature differences with SG Firewall.
- IPS protection – is enhanced with greatly expanded categories enabling you to better optimize your performance and protection.
- Management enhancements – including enhanced firewall rule grouping with automatic group assignment, and a custom column selection for the log viewer.
- VPN and SD-WAN failover and failback – including new IPSec failover and failback controls and SD-WAN link failback options.
- Client authentication – gets a major update with a variety of new enhancements such as per-machine deployment, a logout option, support for wake from sleep, and MAC address sharing.
- Sophos Connect – is our new IPSec VPN Client, free for all XG Firewall customers, that makes remote VPN connections easy for users, and supports Synchronized Security.
In addition, coming in a following maintenance release we have:
- Wireless APX access point support – provides support for the new Wave 2 access points providing faster connectivity and added scalability.
- Airgap support – for deployments where XG Firewall can’t get updates automatically via an internet connection (due to an “airgap” or physical isolation) – XG Firewall can now be updated via USB.
Sophos Central management of XG Firewall
With v17.5, XG Firewall is also joining Sophos Central. The Early Access Program for Sophos Central Management of XG Firewall is expected to start soon.
You will be able to manage XG Firewall from within Sophos Central along with all your other Sophos Central products. And there’s a few great new features coming along with Sophos Central Management of XG Firewall:
- Secure access and management with single-sign-on through Sophos Central from anywhere.
- Backup management and storage for your regularly scheduled firewall backups.
- Firmware update management to make multiple firewall updates easy.
- Light-touch deployment to enable easy remote setup of a new firewall.
Get early access now!
Head on over to the XG Firewall Community Forums to get the v17.5 EAP firmware update, additional information on what’s new, and to share your feedback with the Sophos Product Team and the rest of the community.
You can read the original article, here.