News
By classifying data according to its value or sensitivity, organisations can reduce the risk of security breaches by ensuring that appropriate protections are implemented and consistently enforced. Having identified your ‘crown jewels’, and other data that needs safeguarding, it’s time to carry out a discovery exercise to find out exactly what you’ve got, where it is and who might have access to it.

Unknown data makes you vulnerable to attack. The best thought-out security policy is ineffective if you’re not certain what you hold and, therefore, what controls you need to put on it. Data governance, compliance with regulation such as the EU GDPR and ITAR and – just as importantly – demonstrating that compliance are also impossible when you don’t know where key documents reside and who has access to them.
A discovery exercise will give you visibility of your data and how it’s being accessed and used. This enables the protection strategy and solutions to be built around the types of data you have. It provides an opportunity to cut retention costs, too, by disposing of redundant data; mid-sized organisations spend £435k per year on storing and managing obsolete data, according to the Vertitas Databerg report. Discovery also makes it easier to use data as a resource, deriving insights that will inform strategies and improve operations.
You need to establish:
- what data you hold
- what is being collected
- what is being created
- where it’s stored or located
- why you have it
- how sensitive it is, and
- who is accessing, using or sharing it.
Getting a grip on this is a challenge. Alongside structured data held in on-site databases, companies typically have huge volumes of unstructured data such as emails, PowerPoint decks, Excel files and PDF documents.
Information is also stored and shared across an expanding variety of systems, devices and platforms, including the cloud, collaboration tools like Microsoft SharePoint, file share sites like Dropbox and OneDrive, and ‘shadow IT’ (unsanctioned tools and apps not designed for enterprise use).
Data discovery tools and software provide an efficient and accurate way to find assets you can then classify. They examine file stores and databases, scanning for certain types of information, key words, criteria and classification metadata. This enables you to see what your data is, its location, and who has access. According to Forrester 44% of North American and European technology decision-makers use data discovery tools.
Once you’ve defined the data within your business you’ll be able to home in on the most valuable and confidential information and make accurate decisions about how it should be handled, and who is allowed to access which files. You’ll then be ready to classify it according to its importance or sensitivity to ensure data is appropriately controlled.
Using data classification as part of a strategy to secure corporate data assets is sometimes referred to as ‘locking up the crown jewels’. But data security neither starts nor ends with the act of controlling access to information. Nor should a security policy be limited to protecting only the most valuable data; even less critical information can damage the business if it’s lost or leaked at the wrong time.

First, you need to build a strong foundation of knowledge around your data, to understand exactly what you hold and the potential risks to its security. Picture your organisation as the Tower of London. If you don’t know where your crown jewels (and less sparkly assets) are you’ll end up locking every door – or leaving the wrong doors open, exposing them to risk.
This process begins with identifying the types of data that are of greatest importance to the business, so you can pinpoint where you need to focus protection and controls.
Your most valuable and confidential data (your crown jewels) might include:
- Data assets – such as the information on a CRM database
- Business-critical documents including strategic plans and agreements
- Documents or information that are subject to regulations
- Intellectual property (IP), such as product designs and technical specs
- Personal information – for instance employees’ details.
More often than not, however, a company’s most vulnerable point will not be its crown jewels; it’s likely they’ll already have been recognised and heavily protected. It’s the more everyday sensitive data that people don’t think about, like customer lists, contracts, or time sensitive documents such as company results and press releases that are most likely to be leaked or lost. This data must also be identified and protected.

A helpful way of determining the value of a piece of information – and the risks to be managed – is to think about the impact if it was leaked or lost. Would it harm the business, for example by damaging the brand, incurring a fine from the regulators (for breaching the EU GDPR, for example) or eroding competitive advantage? If it got into the public domain, would it expose your customers, partners or suppliers? Would it put an employee’s security or privacy at risk? Would you be breaching a contract?
Once you’ve defined the data that is most at risk, you can start to find out where your sensitive data is located.
Despite the past year’s global focus on GDPR and other data privacy regulations designed to give consumers more power over their data, more than half (55 percent) of consumers still don’t know how brands are using their data, according to the Acquia survey of more than 1,000 U.S.-based consumers.
On top of that, 65 percent don’t even know which brands are using their data.
Additional key findings from the survey include:
- 59 percent of consumers wait at least a month before sharing any personal data with brands
- 49 percent of respondents are more comfortable giving personal information to brands with a physical store presence
- 65 percent of respondents would stop using a brand that was dishonest about how it was using their data
California’s CCPA data privacy law and Maine’s Internet privacy protection bill, some of the most restrictive in the nation, are standing behind the consumers who want to understand and control their data – and other states are following. Brands trying to reach those consumers will need to act accordingly, and the stakes are high.
Acquia’s research found that consumers are not willing to give brands a second chance to protect the integrity of their data. This means that businesses have only one chance to make sure their customers know that their personal information, and their privacy, is in safe hands.
The recent focus on data privacy legislation globally puts a spotlight on brands who are also facing consumer demands for personalized online experiences. This requires brands to perform a balancing act of delivering hyper-personalized experiences while also being more careful than ever with consumer data.
Consumers are typically waiting at least a month before sharing any personal data with brands. This underscores their desire to build relationships, taking time to get to know brands before trusting them.
With this in mind, transparency will be key for brands looking to earn this trust; proposed U.S. legislation requiring Internet giants to disclose the value of user data indicates the growing demand for transparency when it comes to personal data.
The organizations who answer this mandate with clear policies on data usage will be most effective at building the trust of these consumers.
In addition to being hesitant to share their data right away, almost half of respondents said they are more comfortable giving personal information to brands with a physical store presence — that’s how much they distrust the Internet.
It’s now up to digital brands to re-earn that trust — even if they aren’t responsible for creating the concern in the first place.
“Brands have a responsibility to educate consumers about data usage, proving that they can trust the Internet again,” said Tom Wentworth, SVP, product marketing, Acquia. “Allowing consumers to opt in or out of data sharing will become more common over time as brands recognize that giving consumers back control of their data is not only the right thing to do, but it will also benefit their business in the end.”
You can read the original article, here.
Earlier this year the North Carolina county of Cabarrus in the U.S.A. was hit by a BEC scam, incurring loses to the tune of over $1.7m. Sadly, this is just one example of an increasingly common – and devastating – attack.
Business Email Compromise (BEC) is where cybercriminals combine social engineering with phishing techniques to trick targeted individuals at organizations into transferring funds or data.
Common approaches include hacking email accounts, spoofing the email addresses of senior executives, compromising trusted supplier emails, and spoofing bank and lawyer emails.
BEC attacks are targeted and time-consuming, with cybercrooks often working to compromise a single organization over several months – motivated by the very high potential gains.
And it’s working. BEC attacks are on the rise and 53% of organizations hit by a cyberattack last year say they were victims of phishing.
Minimize your risk
BEC attacks exploit the weakest link in the cybersecurity chain: people. They’re all about tricking people into falling for their spoofed emails, forged documents, and fake information.
All team members are potential targets for a BEC attack, not just finance, HR and senior executives – while they may not authorize big payments themselves, they may inadvertently give hackers information that helps them, or even access to company systems.
That’s why user education and training is key to minimizing the risk of a BEC attack. Through raising awareness of the issue and educating your teams on how to spot suspicious communications, you reduce the likelihood of being hit.
Sophos can help
Sophos Phish Threat is a phishing simulation and training tool that lets you raise user awareness by emulating the tactics used by real phishing attackers. You can set up test phishing campaigns in minutes.
It also includes online training to educate people on how to spot and stop the real thing. Plus, you can measure progress to track improvement and demonstrate ROI to the business.
Try Phish Threat, for free, for 30-days.
In addition, our free anti-phishing toolkit gives you a fantastic set of resources to educate your team on phishing. It includes posters for your workplace, a PowerPoint presentation for meetings, examples of phishing emails, and top tips to spot phishy emails. Get your copy today.
Artificial intelligence and machine learning are persistently in the headlines with rich debate over its next advances. Will cybercriminals further leverage machine learning to craft attacks? Can defenders build a machine learning model capable of detecting all malware?
We believe machine learning is an essential and critical piece of cybersecurity, but it must be only one part of a broader solution to be effective.
It’s unwise for any security product to rely solely on machine learning as its primary or singular layer of defense. An all-eggs-in-one-basket approach leaves attackers with a single door to break down. A product with a true multi-technology approach, such as Sophos Intercept X, presents a complementary and reinforcing set of obstacles that must all be overcome at the same time for an attack to succeed.
Machine learning is one of an ensemble of protection technologies in Intercept X designed to identify malware and potentially unwanted applications, including those that have never been seen before. We go further in our application of machine learning, beyond simply making predictions on files. We also include “advisors” in our Endpoint Detection and Response product to provide additional information to aid in decision making. These advisors have the effect of providing the intuitions of expert malware analysts to the handling of suspicious (as compared to categorically malicious) events or artifacts.
Machine learning: A target
Cybercriminals have always sought out new and easy ways to break into systems and maneuver around networks. It is reasonable to assume they would look for ways to target a machine learning model and trick it into thinking an attack is “safe”. Sophos has prepared for such an event and other types of potential and evolving attack techniques.
Our strategy to remain resilient to these attacks has been to conduct diligent industry-leading research into neural networks and their architecture, as well as to consolidate next-generation and traditional security technologies into a single solution. This includes layers of analytics, behavioral detections, static detections, heuristics, machine learning models, anti-exploitation techniques, anti-ransomware technology, and more. We call this “The Power of the Plus”.
Only through careful architecture alongside independent, agnostic, and complementary protection technologies can the power of machine learning be safely utilized.
Sophos Offensive Research
Sophos has been conducting offensive security research of machine learning models for over two and a half years as part of our internal research into the security of machine learning and improving product resilience.
As far back as February 2017, we built an advanced, product-agnostic proof-of-concept that could trick most, if not all, machine learning models by mutating a known-good file into a malicious file. The vast majority of models would believe the file was the original, known-good file. Even today, this proof-of-concept deceives the majority of machine learning models in endpoint security solutions. Note: We chose against making this research widely available to prevent it getting into adversaries’ hands.
By preempting our adversaries and understanding the approaches they could take, we underscore the importance of our strategy to provide multiple defensive technologies covering a broad spectrum of techniques and capabilities.
Cybersecurity by Sophos
The SophosLabs Data Science team are major contributors to the field of artificial intelligence research, as evidenced by the technical papers on our website or listings on Google Scholar. Extensive and continuous research and publication of our defensive innovations is a pillar of our ethos. The results of this research influences and determines the composition and orchestration of our layers of protection technologies in Intercept X and all other Sophos solutions.
Our research influences ongoing optimizations in our products to make them less susceptible to attempted adversarial attacks. In addition, our layers of defense are designed to make convictions independently so that, should one layer miss a threat, another layer stands strong to protect the system.
Digital security and physical security have many parallels. Think of a building and how it could be protected. If you were to build nothing but a giant wall, it may prove difficult to climb over but eventually someone will find a way to get over it (or under it).
Now consider a fortress. Armed guards, attack dogs, CCTV, tripwires, barbed wire, motion sensors. It may be possible to hop the wall, but you still have many additional hurdles ahead of you.
Single layers are simple to build but are also simple to bypass. Our goal has always been to build fortresses.
Not long ago on the CyberArk Conjur blog, our DevOps community manager and evangelist John Walsh explored the history and evolution of open source software. It’s a great read that highlights the clear relationship between open source adoption and DevOps success in the enterprise, along with the power of community engagement and information sharing.
We’ve embraced this team player approach with CyberArk Conjur and our fast-growing CyberArk Marketplace, which features community contributions. Furthering this commitment to collaboration and transparency, today we published our product documentation library online, making it freely available to everyone – no login required.
Featuring newly simplified and enhanced documentation on CyberArk version 10.10, CyberArk Docs makes it even easier to get your questions answered – fast.
Considering a privileged access security solution? Whether your organization is just getting started or already focused on implementing advanced privileged access security strategies to align with digital transformation initiatives, CyberArk Docs is a good place to start. Get to know CyberArk by browsing documentation by product: Core Privileged Access Security, CyberArk Privilege Cloud, Endpoint Privilege Manager and Application Access Manager. On each of these product pages, it’s easy to find information on security fundamentals, how to get started with a deployment, how to configure or manage your environment and how to install or upgrade components. The site is easy to navigate, offering documents organized by functional role with information for end users, administrators and developers.
CyberArk Docs is also part of our broader CyberArk Technical Community site, available to current customers and partners, where you can connect and engage with peers and subject matter experts on CyberArk products and services. Through the Technical Community you can now browse and download helpful documentation from CyberArk Docs, take advantage of our comprehensive knowledge base, access a wide range of online training courses and post integrations and reviews on the CyberArk Marketplace. There’s also a simple way to submit support cases and enhancement requests.
CyberArk Docs is just one of the many ways we’re extending value to the broader cybersecurity community. Inspired by open source, our goal is to make it easier for end-users, admins, developers and security professionals alike to access the information and tools they need to collaborate, innovate, build and succeed.
Check CyberArk Docs out today.
You can read the original article, here.
37% of cyberattacks are discovered on servers, making them the most likely place to identify an attack in an organization. That’s one of the alarming stats taken from a recent Sophos survey of 2,700 IT managers around the world.
But why are servers such tempting targets for hackers?
1. Servers are high value
Servers often contain an organization’s most valuable data. For example, personally identifiable information (PII) such as employee and customer records could be stolen if they’re not adequately secured (for example, with encryption) on the server.
Regulations, such as the recently introduced GDPR that protects EU citizens’ data, levy significant fines for non-compliance. Attackers know this and will threaten to release sensitive data if their demands are not met.
2. Server downtime is costly
Servers are the lifeblood of organizations and are critical to their day-to-day functions. Unexpected downtime can seriously impact productivity by removing access to important files or communication tools such as Microsoft Teams or Skype. Ransomware attacks can cause organizations to grind to a halt unless a ransom is paid.
In instances where an organization is reliant on servers for commercial function (e.g. an e-commerce site) downtime can be even more severe.
3. Servers are the perfect staging ground
Servers are usually well connected in an organization’s network. They are also online and running 24/7, which makes them an ideal platform for launching further attacks and performing reconnaissance looking for weak spots to exploit across the network. If you can’t identify a compromised server, the gates to your IT kingdom could be wide open.
So what needs to be done to secure your organization’s servers? The answer is in the right combination of advanced protection, visibility with powerful tools like Endpoint Detection and Response (EDR) and server specific features such as File Integrity Monitoring.
Sophos Intercept X for Server has them all, keeping your organization secure against advanced threats including ransomware and exploits. It gives you the tools you need to hunt down evasive threats and it locks down your servers so they can’t be tampered with. Take a look at our Server Buyers Guide to see the full list of features your server protection solution needs to have.
You can read the original article, here.
For years, security was cited as a prime reason not to put sensitive data or valuable workloads into the public cloud. It’s safe to say that situation has changed. In fact, the CyberArk Global Advanced Threat Landscape Report 2019: Focus on Cloud found that the vast majority (94 percent) of the 1,000 global organizations surveyed used cloud services in some way, shape or form. We see that that use is often to support digital transformation initiatives.
The public cloud isn’t being used for low-value data or unimportant assets. For instance, nearly half of the respondents are using SaaS-based business critical applications and a similar percentage use the public cloud for regulated customer data.
So far, so unsurprising.
The eye-opening discovery was the contrast between what organizations see as the major benefit derived from their use of cloud versus their understanding of their cloud security accountability.
The prime benefit that the organizations surveyed hoped to see from their usage of cloud was the ability to offload security to the cloud vendor, either completely or in part. This was potentially alarming, to say the least. Cloud vendors take responsibility for certain aspects of security when companies use their services, but they are very clear about where their clients must step in and assume accountability. Protecting customer data remains the responsibility of the client.
Then, we found that three quarters of survey respondents, perhaps blindly, entrust the security of their cloud workloads completely to the cloud vendor while half this number realize that this will not provide them with broad protection – but do it anyway. At this point, it’s obvious that the shared security responsibility model, which is clearly communicated by major cloud vendors, is either not well-understood or being ignored by many organizations.
Our report looked further into how privileged credentials are protected in the cloud and whether the high-value privileged credentials that give access to the most sensitive cloud-based data and assets were being properly secured.
It shows widespread lack of awareness about the existence of privileged accounts, secrets and credentials in IaaS and PaaS environments as well as the lack of a strategy to secure them. With less than half of all respondents reporting having a privileged security plan for the cloud, our findings indicate that organizations could be placing themselves – and their customers’ data – at significant risk.
For more details, download our eBook.
The recent attack by China on Cellular companies – called Operation Soft Cell – is part of an espionage campaign that leverages privileged access in privileged accounts. Compromising credentials remains the weapon of choice for attackers and a top attack pattern.
We first encountered this pattern when Edward Snowden revealed Operation Socialist, a CIA and British Global Communication Headquarters (GCHQ) campaign that allegedly attempted to take control of one of the most widely spread telecommunications networks in the country – Belgian telecommunications company Belgacom. Access to Belgacom would allow intelligence agencies to obtain the metadata required to track specific target individuals. Aside from this new attack coming from a very different quarter, China’s APT 10 rather than the GCHQ, the attacks are very similar.
Operation Socialist, like the recent Soft Cell operation, leveraged privileged access and privileged accounts to take control of telecommunication systems and persist while remaining in the shadows. Neither of these attacks needed to exploit vulnerabilities or reveal sophisticated and aggressive tools, which cost a lot to develop. In both cases, the groups compromised the organization’s privileged accounts – namely domain admin accounts. Domain admin accounts have administrator rights over an entire domain, making them extremely useful to an attacker.
Domain admin accounts and other well-known privileged accounts are usually tightly-controlled and monitored. However, there were still vulnerabilities to exploit. The attackers probably went after shadow admins, which are privileged accounts that aren’t members of the privileged Active Directory group, letting them fly under the radar and often go overlooked by organizations’ security teams.
These type of accounts have special privileges that allow an attacker to gain control of a complete network control without being a member of a privileged group. Consequently, the attack leaves little trace, while still providing the attacker with flexibility. In the Soft Cell operation, the attackers launched a VPN service to allow them shadow access to the network – possibly based on shadow admin accounts.
Using shadow admins to gain access isn’t the only short cut that the attackers from Operation Soft Cell and Operation Socialist used. In both of these cases, the attacks on the telecom companies targeted the supply chain. Just like hardware manufacturing facilities, software companies that provide product updates or internet traffic backbone servers are vulnerable to supply chain attacks.
This has become common with many attackers redirecting their efforts from well-defended organizations to their less-secure supply chains. Attackers who want intimate and persistent access to a company’s data and IP can replace sending phishing emails to vast numbers of employees with bugging the company’s hardware. Attackers who want access to an individual’s metadata, location and calls for a longer period of time, can replace exposing a costly WhatsApp vulnerability with compromising a specific individual’s phone.
You can read the original article, here.
In the last week both British Airways (BA) and Marriott Hotels have hit the headlines because of eyewatering GDPR fines – $229 million for BA and $123 million for Marriott.
The fines show that the GDPR (General Data Protection Regulation), has given enforcers like the UK’s ICO (Information Commissioner’s Office), some serious teeth. BA’s fine is almost 400 times larger than the ICO’s previous record fine – a $645,000 penalty handed to Facebook for the Cambridge Analytica scandal.
With these new fines in mind, it’s a good time to make sure you’ve minimized your risk of being next in line.
GDPR is focused on protecting European Union citizens and it applies to anyone who holds personal data on an EU citizen, wherever in the world you are based. Marriott, a U.S. organization, is a case in point.
Here are five best practices we recommend all organizations follow to minimize the risk of a GDRP data loss fine:
- Patch early, patch often. Minimize the risk of a cyberattack by fixing vulnerabilities that can be used to gain entry to your systems illegally. There is no perimeter, so everything matters: patch everything.
- Secure personal data in the cloud. Treat the cloud like any other computer – close unwanted ports and services, encrypt data and ensure you have proper access controls in place. And do it on all your environments, including QA and development.
- Minimize access to personal data. Reduce your exposure by collecting and retaining only the information you need, and making sure the only people with access to it are the people who need it to do their jobs.
- Educate your team. Ensure that everyone who might come in to contact with personal data knows how they need to handle it – this is a GDPR requirement.
- Document and prove data protection activities. Be able to show that you have thought about data protection, and have taken sensible precautions to secure personally identifiable information.
Sophos can help
First up, to minimize the risk of attackers getting to your data, we offer a complete portfolio of cybersecurity solutions, including Intercept X endpoint protection and XG Firewall. Check them out with our free online demos today.
If you’re using Amazon Web Services (AWS), Microsoft Azure, or Google Cloud Platforms (GCP), take a look at our guide to Securing the Public Cloud: Seven Best Practices. It explains what you are (and are not) responsible for, and how to protect data and workloads in the public cloud.
When a laptop goes missing, you need to be able to show it was encrypted. Sophos Central Disk Encryption is the easiest way to centrally manage BitLocker and FileVault encryption, and to prove that you have it deployed.
Think about how much personal data you have on your work mobile phone – it’s just as much a security risk as your laptop. Sophos Mobile enables you to remotely lock and wipe a lost mobile device – and also demonstrate that it is encrypted.
Sophos Disk Encryption and Sophos Mobile are available through Sophos Central. If you’re already using Central you can start a free trial in a couple of clicks from within your console. If you’re not, download a free trial today.
You can read the original article, here.
Given the simplicity and cost-effectiveness of the public cloud, it’s no surprise that more and more organizations are turning to Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP).
You can spin up a new instance in minutes, scale resources up and down whenever you need while only paying for what you use, and avoid high upfront hardware costs.
While the public cloud solves many traditional IT resourcing challenges, it does introduce new headaches. The rapid growth of cloud usage has resulted in a fractured distribution of data, with workloads spread across disparate instances and, for some organizations, platforms.
As a result, keeping track of the data, workloads, and architecture changes in those environments to keep everything secure is often a highly challenging task,
Public cloud providers are responsible for the security of the cloud (the physical datacenters, and the separation of customer environments and data). However, if you put data and workloads in the public cloud you are also responsible for securing them.
Misunderstandings around this distribution of ownership is widespread and the resulting security gaps have made cloud-based workloads the new pot of gold for today’s savvy hackers. (For more details read Matt Boddy’s recent research: Cyberattacks on Cloud Honeypots).
Seven steps to securing the public cloud
The secret to effective public cloud security is improving your overall security posture. You need to ensure your architecture is secure and configured correctly, and that you have visibility into both your architecture and who is accessing it.
There are many elements to public cloud security and it can be difficult to know where to start. If you’re using the public cloud – or thinking about migrating – we recommend these seven steps to help maximize your security.
Step 1: Learn your responsibilities
This may sound obvious, but security is handled a little differently in the cloud. Public cloud providers such as Amazon Web Services, Microsoft Azure, and Google Cloud Platform run a shared responsibility model – meaning they ensure the security of the cloud, while you are responsible for anything you place there.
Step 2: Plan for multi-cloud
Multi-cloud is no longer a nice-to-have strategy. Rather, it’s become a must have strategy. There are many reasons why you may want to use multiple clouds, such as availability, improved agility, or functionality. When planning your security strategy, start with the assumption that you’ll run multi-cloud – if not now, at some point in the future. In this way you can future-proof your approach.
Step 3: See everything
If you can’t see it, you can’t secure it. That’s why one of the biggest requirements to getting your security posture right is getting accurate visibility of all your cloud-based infrastructure, configuration settings, API calls and user access.
Step 4: Integrate compliance into daily processes
The dynamic nature of the public cloud means that continuous monitoring is the only way to ensure compliance with many regulations. The best way to achieve this is to integrate compliance into daily activities, with real-time snapshots of your network topology and real-time alerts to any changes.
Step 5: Automate your security controls
Cybercriminals increasingly take advantage of automation in their attacks. Stay ahead of the hackers by automating your defenses, including remediation of vulnerabilities and anomaly reporting.
Step 6: Secure ALL your environments
You need a solution that can secure your all environments (production, development, and QA) both reactively and proactively.
Step 7: Apply your on-premise security learnings
On-premise security is the result of decades of experience and research. Use firewalls and server protection to secure your cloud assets against infection and data loss, and keep your endpoint and email security up to date on your devices to prevent unauthorized access to cloud accounts.
Moving from traditional to cloud-based workloads offers huge opportunities for organizations of all sizes. Yet securing the public cloud is imperative if you are to protect your infrastructure and organization from cyberattacks.
To learn more, download our new guide: Securing the Public Cloud: Seven Best Practices
Tourists aren’t the only ones looking at Florida this summer. As the Sunshine State ramps up to greet a flock of vacationers, it’s also facing some far less welcome visitors.
Over the last few weeks, cybercriminals have targeted Florida with advanced ransomware attacks requesting heavy payments in return for restoring data. In one example, the city of Riviera Beach agreed to pay over $600,000 in ransom after its systems were crippled.
Of course, ransomware attacks aren’t limited to Florida and are now commonplace across the globe as cybercriminals continue to evolve their techniques.
How to avoid becoming the next ransomware victim
Sophos Intercept X Advanced gives you the world’s best protection against ransomware. And you can protect your organization for free, for 30 days.
It includes multiple layers of security that deliver unparalleled protection against sophisticated, advanced attacks.
- CryptoGuard technology stops the unauthorized encryption of files by ransomware, rolling any impacted files back to their original state. It’s the ultimate ransomware killer.
- Anti-exploit protection prevents ransomware from using vulnerabilities in software products to infiltrate and spread through organizations.
- The powerful Deep Learning engine uses cutting-edge machine learning to identifiy and block never-before-seen ransomware before it executes.
Watch Intercept X in action against MegaCortex ransomware
Try it yourself
Intercept X uses multiple techniques to defend against ransomware, instantly elevating your defenses. Download and get started today.
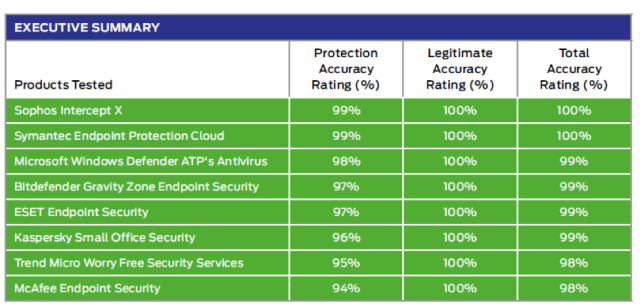
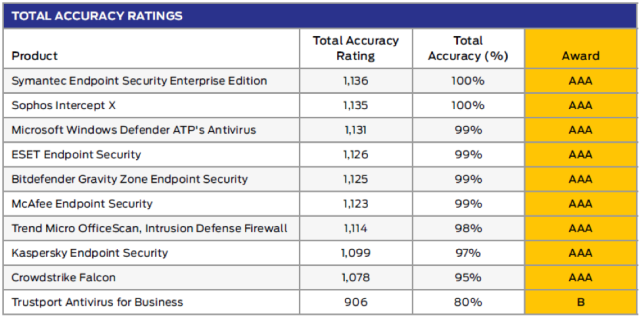
Sophos Intercept X continues to perform well in third party tests, and we thought we’d share a few recent results.
Those results include a 100% total accuracy rating by SE Labs, a #1 ranking by AV-Comparatives for malware protection, and an Editors’ Choice designation by PC Magazine.
Our Mac protection also joins in on the fun with a new result from AV-Test. Scoring 18 out of 18, Sophos received the only perfect score in the test.
SE Labs
SE Labs conducts quarterly tests for both enterprise and SMB protection. We’re excited to report that we received a 100% total accuracy rating in both Q1 2019 tests.
AV Comparatives
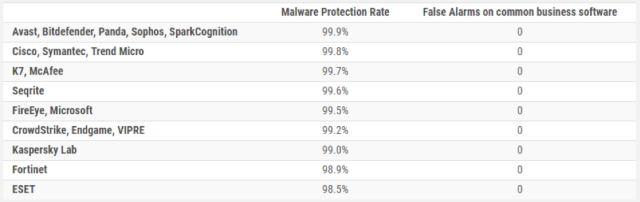
Intercept X made its first public AV-Comparatives Business Security Test appearance and ranked #1 for malware detection on Macs. We earned a 99.7% detection rate with just 1 false alarm in the “real-world” test, and 99.9% detection and 0 false alarms in the “malware” test.
 PC Magazine
PC Magazine
Intercept X received an “Excellent” Rating and the “Editors’ Choice” award.
PC Magazine declared that Intercept X is “an instant win for anyone looking to provide a defense against ransomware for any sized business.”
The reviewers went on to say it “has a wide range of sophisticated features to guard against malware of all forms, and has earned the praise of several independent labs as well as earned our Editors’ Choice designation in our ransomware protection for business review roundup”.
AV-Test
Sophos scored a 6 out of 6 on protection, performance, and usability – the only perfect score among vendors tested in June 2019.
Intercept X third party test results and top analyst reports
- AAA Rated for Enterprise – 100% total accuracy rating
- AAA Rated for SMB – 100% total accuracy rating
- Ranked #1 for Security Effectiveness
- Ranked #1 for Total Cost of Ownership (TCO)
- Ranked #1 for Malware Protection (99.9% detection, 0 false alarms)
MRG Effitas
- Ranked #1 for Malware Protection
- Ranked #1 for Exploit Protection
Editors’ Choice
AV-Test
- Top Product: 6/6 Protection, 6/6 Usability, 5.6/6 Performance
- #1 macOS protection: 6/6 Protection, 6/6 Usability, 6/6 Performance
- Leader: 2018 EPP Magic Quadrant
- Leader: 2018 Endpoint Security Wave
Since September 2014 (that makes 29 tests in a row!), Sophos Mobile Security has achieved the highest possible score in the AV-Test for Android malware detection, earning maximum scores across all categories.
In the May test we scored 6.0 for protection – the highest possible score – and had no false positive detections.
Our intuitive interface that makes management a simple task earned us a score of 6.0 in the usability section.
And we scored the maximum in the features category due to powerful features including remote locking and wiping, and safe browsing.
Take a look at the AV-Test review for all of the details, and try Sophos Mobile Security for free on the Google Play Store.
At Sophos, we appreciate how hard it is to solve security problems when developing applications – after all, we’ve dedicated the past 30 years to innovating and improving computer security.
Since founding SophosLabs, we’ve leveraged the expertise of our security engineers and researchers, and their intelligence and analysis services, using these as the foundation of many of our solutions to the most difficult cybersecurity problems.
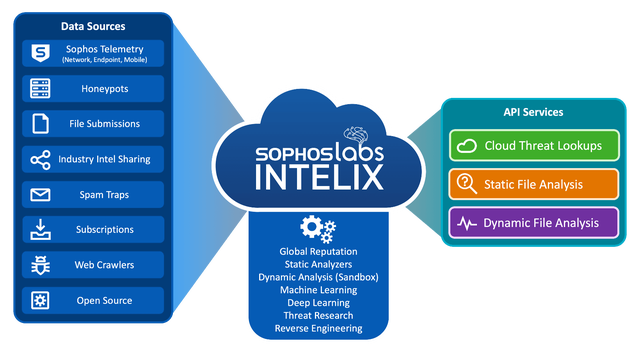
Today, we are opening the doors on the Early Access Program for SophosLabs Intelix, our new cloud-based, threat intelligence and threat analysis platform, which is built from the same SophosLabs services that underpin our industry-leading solutions.
SophosLabs Intelix works via Application Programming Interfaces (APIs), part of our a Representation State Transfer (REST) web service. This approach ensures that all software developers of different skill levels should have no trouble getting access to our new services.
SophosLabs Intelix allows software developers around the globe to harness high quality, curated threat intelligence and rich, detailed threat analysis in their own tools, applications, and services. All without compromising on quality, performance or security, and removing the need to consume, aggregate and correlate multiple services from different vendors.
SophosLabs Intelix will initially offer three key services:
- Cloud Threat Lookups quickly identify known threats in files, URLs, and APKs.
- Static File Analysis analyses files using machine learning and static analysers.
- Dynamic File Analysis executes files in a sandbox to reveal their behaviour and intent.
The Sophos Labs Intelix APIs will be available via the AWS Marketplace. Users have the choice between a monthly free tier or Pay As You Go (PAYG) pricing. The monthly free tier will allow each user a set number of API calls to each service for free, paying only for the requests that exceed the monthly free allowance.
For our partner community, SophosLabs Intelix is joining our Sophos Cloud Security Provider Program, adding to the range of technologies and solutions our partners can offer their customers.
Through enabling software developers to tap into the same technologies we use to drive our security solutions, we hope developers will innovate on top of our APIs, kick-start new security solutions, build more secure applications and services, and help make the digital world a safer place to be.
Cybercriminals are becoming increasingly proficient at infiltrating enterprises to steal data for profit, acquire intellectual assets or to simply cause destruction. High profile breaches frequently making the headlines however are just the tip of the iceberg with global losses due to cybercrime projected to hit a staggering eight trillion dollars by 2020.
Enterprises today are now contending with highly organized adversaries who are persistent and have deep pockets and the technological resources that rival most Fortune 100 companies; keeping pace has been arduous. The infographic below depicts the top three cybersecurity issues challenging organizations as they steer towards digital transformation and where a trusted security partner can have significant impact.
Privileged access security is a key pillar of an effective security program. We take our role as a trusted adviser to our customers very seriously and are constantly looking for new ways to help evolve existing privileged access security programs – or guide organizations that are getting started – to prioritize risk and identify opportunities to measure success and demonstrate quantifiable value to the business. CyberArk has interviewed hundreds of organizations, including customers and those who have not yet adopted a privileged access security solution, to determine the biggest hurdles companies face when it comes to privileged access security and what they need to overcome them. We found three key trends:
- Organizations, especially those with resource constraints (basically every company, everywhere), struggle to identify the security goals that provide the most security value to their business in terms of both cybersecurity risk reduction and ROI.
- Companies that adopted a PAM solution were able to accomplish the goals they originally set out to achieve, but they didn’t know where to go next to continue improving their security. They often spoke of “best practice” programs they wanted to follow, but had difficulty applying those programs in a way that provided tangible outcomes specific to their needs.
- Organizations are looking for cybersecurity tools that provide clear advice, backed by quantitative methods to help guide them along their security journey.
CyberArk is proud to introduce the CyberArk Privileged Access Security Assessment Tool to guide organizations across all three fronts.
During an assessment, a technical expert from CyberArk or one of our certified partners will sit with your team, walk you through the process with cybersecurity assessment tool and discuss how your organization is protecting privileged accounts and access today. We frame this conversation on the CyberArk Privileged Access Security Cyber Hygiene Program, which defines seven goals organizations should strive to accomplish to build a comprehensive program to secure privileged access. Based on our findings, the CyberArk Privileged Access Security Assessment Tool will deliver three outputs that will inform not only your technical teams, but also business and IT leaders who are becoming increasingly interested in what security teams are doing to protect the brand.
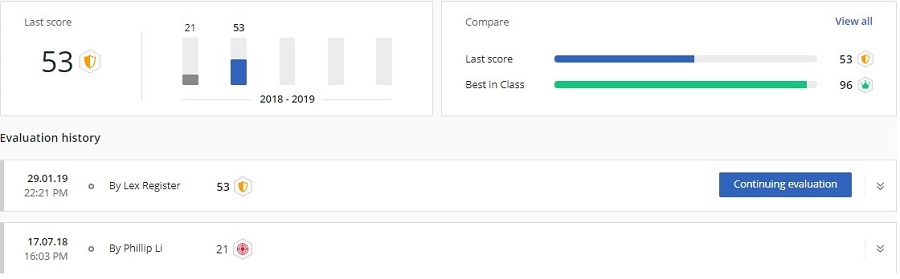
Output 1: Privileged Access Security Score
Security score and evaluation history from the Privileged Access Security Assessment tool
You can think of the privileged access security score as similar to a FICO or NPS score in that it reflects concrete metrics and can be tracked over time. The score is based on feedback provided to assessment and evaluation criteria developed by CyberArk. The Privileged Access Security Score is something tangible that organizations and security leaders can use to demonstrate the progress they’ve made in building a strong privileged access security program.
Output 2: Rich comparison data
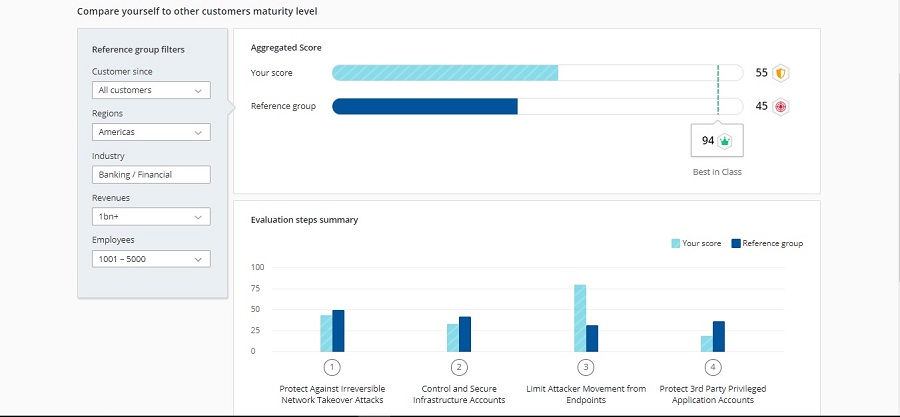
Comparison data from the Privileged Access Security Assessment tool
The rich comparison data provides a comparison against peers based on industry, company revenue, number of employees and a variety of other distinctions. We call this collection of attributes a reference group. This data is crucial for leaders interested in understanding how their investment compares to others in their reference group.
Output 3: Assessment report, complete with specific recommendations

For companies that have completed an assessment already, this output has been cited as the most significant in terms of direct value to the business. The assessment report provides companies with a recap of their most recent assessment, a visual history of their assessments, the comparison data from above and, most importantly, specific advice based on their individual feedback.
We give companies technical and process recommendations for the two of the seven goal of the assessment. These are the areas they should prioritize in the next 12-24 months and the assessment report clearly defines the actions to take to improve privileged access security and protect your organization’s business.
Read the press release to learn more about how the industry, including leading cyber security insurance firms, are leveraging Privileged Access Security Assessment Tool from CyberArk. Get started by filling out a request form or by reaching out to your CyberArk representative.
Read the original article, here.
As Shep Hyken recently noted, personalization continues to become more personal in the customer service field. Personal information (PI) is the future of business, as it provides clients with a customized experience and helps businesses eventually sell more.
However, it means companies will have to curb the wave of consumer rights advocacy and comply with at least one privacy regulation, such as the California Consumer Privacy Act (CCPA), the General Data Protection Regulation (GDPR), the recently proposed U.S. federal privacy law Data Care Act and so on.
One may treat privacy legislation, with its strict requirements and enormous penalties, as a big stumbling block for business, but I perceive it as a huge enabler. Here are five ways privacy regulations may help boost your business.
1. Optimize business processes.
Privacy regulations enable greater transparency around the data collected by your company. For example, the CCPA requires businesses to disclose the “categories and specific pieces of personal information the business has collected” about them. Though not all privacy laws require you to explicitly inform customers on that information, companies still need to thoroughly audit the data they have to understand what kind of information they store and why.
This is a brilliant opportunity to ask yourself why you collect this data, whether you use it efficiently and how you can optimize its use. This deeper understanding of the data flow will provide more visibility into your business processes and help optimize them or find new ways of leveraging gathered data (by providing extra personalized experiences, for example).
2. Improve data management and achieve cost efficiency.
Another question you may ask yourself after auditing the data is whether you really need all of this data. Most likely, you don’t need it all. Thus, ongoing auditing for the sake of compliance will actually enable your company to prune out unnecessary data, such as redundant, obsolete and trivial (ROT) files, that have no value to your business.
By cleaning up repositories, you can slash costs on data processing and storage, get more predictive bills if you store data in the cloud and wisely allocate your budget.
3. Create a global knowledge base for employees.
Privacy laws grant consumers control over the data businesses hold on them, such as the CCPA’s right to erasure or the GDPR’s right to be forgotten, the right to access and modify data and so on. To handle these requests, you should improve the findability of data (i.e., reorganize repositories and make data globally indexed and searchable).
It’s hard to achieve this without investing in additional technologies, such as data classification and enterprise search software. But it wouldn’t be cost-efficient to spend X amount of money and human resources to deploy this technology just to satisfy occasional data subject requests. This is like buying a Porsche just to drive your children to school down the block.
Instead, you can use additional capabilities to reorganize and index the data you have, or at least the data business employees might need — not just consumers’ PI. This way, your company will improve its corporate memory. Moreover, employees will be more efficient while working with accessible, exhaustive and searchable data, won’t lose business opportunities and will keep contributing to the company’s long-term growth.
4. Achieve audience loyalty and trust.
To truly benefit from the privacy legislation, it’s important to step up and voluntarily take extra responsibilities by extending privacy requirements to all of your clients, not just those who are protected by the CCPA (California consumers), the GDPR (EU residents) or any other standard. By meeting customer demands for data privacy globally, your business will create a stronger bond between your brand and clients.
This can be used as part of impactful positioning that will give you a competitive advantage and help you stand out from the crowd. You can demonstrate to clients that your company is done with annoyingly formal checkboxes and cookie notifications. Instead, show that you are eager to provide them with a clear privacy policy statement explaining how all your customers can benefit from entrusting you with their PI and what measures your company takes to secure it.
The greatest way to tackle data privacy is by being honest and straightforward about it. When people become increasingly suspicious about their privacy, such an attitude is a way to go.
5. Revamp the security strategy.
The cost of data breaches and business downtime due to theft or loss of critical data continues to grow. So, another benefit of privacy legislation is encouraging companies to overhaul their security policies.
Indeed, it is almost impossible to only protect regulated data and leave the rest of the IT infrastructure out of scope. Therefore, your company will have to establish stricter control over activity across the entire IT environment, initiate solid data protection workflows and better comprehend IT risks. In the long run, this will help you invest more adequate resources in security and decrease the risk of severe security incidents.
There’s no doubt that achieving compliance with data privacy laws is stressful and resource-intensive, and many companies will be prone to taking a formal approach to it. However, don’t be shortsighted. Adhering to data privacy standards is more than marking a checkbox — it is a way to greatly boost your business, stay ahead of the competition and meet the global demand for business consciousness and respect for human privacy.
Read the original article, here.
Cybersecurity isn’t getting any easier. To better understand the day-to-day reality for IT teams we recently commissioned a survey of 3,100 IT managers in 12 countries.
This independent, vendor-agnostic study revealed a number of common challenges:
- Security: 68% of organizations had experienced a threat that got through their defenses in the last year, 90% of which were running up-to-date cybersecurity at the time.
- Visibility: 43% of network traffic is unclassified, meaning IT teams are unable to see and control it.
- Resourcing: 2 in 3 IT managers say their budgets for cybersecurity (technology and people) is too low, and 80% wish they had a stronger security team in place.
As these results show, despite ongoing investment in cybersecurity the traditional approach isn’t working. Why? Because cybercriminals connect multiple techniques in their advanced attacks, but most security products still work in isolation.
It’s time for a different approach.
Synchronized Security is the cybersecurity system where Sophos endpoint, network, mobile, Wi-Fi, email, and encryption products work together, sharing information in real time and responding automatically to incidents:
- Isolate infected endpoints, blocking lateral movement
- Restrict Wi-Fi for non-compliant mobile devices
- Scan endpoints on detection of compromised mailboxes
- Revoke encryption keys if a threat is detected
- Identify all apps on the network
Everything is managed through a single, web-based management console, so you can see and control all your security in one place.
The Best Threat Intelligence Technology at the SC Awards 2019 Europe is testimony to how Synchronized Security is transforming the way organizations manage their security.
By automating incident response, delivering new security insights, and simplifying management it reduces risk, enhances cross-estate visibility, and enables organizations to scale their security without scaling their resources.
Watch this short video to hear what our customers have to say about Synchronized Security.
Read the original article, here.
CVE-2019-07-08, nicknamed BlueKeep, is a critical remote code execution vulnerability in Windows’ Remote Desktop Services. The bug is considered ‘wormable’ and so severe that Microsoft took the highly unusual step of including patches for the unsupported Windows XP and Windows Server 2003 in its May Patch Tuesday output, alongside patches for the affected operating systems it does support.
If this flaw is successfully exploited it could be used to create self-replicating malware like Slammer, WannaCry or NotPetya – a trio of network worms that used exploits to invade networks and spread globally in a matter of hours.
Patches that could have stopped those worms from spreading were available months before the outbreaks occurred. The race is now on to make sure history doesn’t repeat itself with CVE-2019-07-08.
So far the signs aren’t good. Two weeks after Microsoft’s patches dropped a scan revealed that a million unpatched devices were accessible over the internet, with likely millions more hidden from view, inside corporate networks.
Yesterday, the NSA (the U.S.A.’s National Security Agency) was moved to issue its own advisory, urging organizations to get on with the business of patching.
“It is likely only a matter of time before remote exploitation code is widely available for this vulnerability. NSA is concerned that malicious cyber actors will use the vulnerability in ransomware and exploit kits containing other known exploits, increasing capabilities against other unpatched systems”.
Patching doesn’t get much more urgent than this but, as previous outbreaks have shown, it takes time.
An exploit could appear at any time so you need a way to protect yourself now, until the patching is done. As both Microsoft and the NSA say in their advisories, your Firewall can be your line in the sand.
Protect your organization against BlueKeep
All firewalls can pull up the drawbridge by blocking access to port 3389, which disables external RDP access for all machines, including the ones that nobody told your IT team about.
Besides blocking and unblocking vulnerable ports, Sophos XG Firewall provides other more nuanced and sophisticated layers of security. Its built in Intrusion Prevention System (IPS) looks at network traffic for exploits and stops them from passing through your network perimeter, or traversing the segments of your internal network.
At the same time that Microsoft announced the CVE-2019-07-08 vulnerability, SophosLabs issued an IPS update for all Sophos customers to ensure their XG Firewall-protected networks could stop these kinds of attacks dead in their tracks.
While we have a full guide on how to protect your network, here are the essential firewall best practices to stop vulnerabilities like BlueKeep from exposing your network:
- Reduce the attack surface by reviewing your port-forwarding rules and eliminating any non-essential open ports. Where possible use a VPN rather than port-forwarding to access internal network resources from the outside.
- Minimize the risk of lateral movement by using XG Firewall and Sophos Synchronized Security, and consider segmenting your LANs into smaller subnets and assign them to separate zones that are secured by the firewall.
- Apply IPS protection to the rules governing traffic to and from any Windows hosts on your network, and between your network zones to prevent worms from spreading between LAN segments.
XG Firewall and Synchronized Security are your best protection against the latest threats with industry leading protection and performance. Download our Firewall Best Practices to Block Ransomware guide to learn more.
Read the original article, here.