News
Intercept X has launched a new early access program (EAP) that brings protection enhancements including Anti-Malware Scanning Interface Protection (AMSI) and Malicious Network Traffic Protection.
AMSI is a Microsoft interface in Windows 10, Windows Server 2016 and later that allows for the scanning of script files even when obfuscated, as well as .NET 4.8 assemblies.
Obfuscated PowerShell scripts are a very common method for attackers to compromise systems. By leveraging AMSI Intercept X gets even better at detecting and blocking these attacks.
Malicious Network Traffic Protection, also known as Intrusion Prevention System (IPS), scans inbound and outbound traffic for malicious attack patterns, with rules based on Snort methodology.
This helps in several key ways, for example, if an employee takes their laptop to a café where they have no firewall protection, IPS will identify and block malicious traffic patterns. Outbound traffic scanning also helps block lateral movement from a compromised device, stopping the threat from spreading across the network.
The EAP is open right now and available to everyone using Intercept X Advanced and Central Endpoint Protection. Support for Intercept X for Server Advanced will be added during the EAP. To join head over to the community page.
We’ve seen the introduction to user-driven security, and the three main steps to implementing a user-driven approach to security. The last instalment of this three part series covers the three main benefits to your organisation:
1. Reduces Risk of Losing Sensitive Information
If you know where your sensitive data is, you can control: how it’s protected, where it’s stored and who can access it. As such, the risk of losing sensitive data is massively reduced. Additionally, if you have a policy of, for example, encrypting ‘top secret’ data, it mitigates the damage that can be caused even if the data did end up in the wrong hands.
2. Increases Productivity
Put simply, if users understand the value of the data, they will be able to make quicker and more confident decisions on how to handle it. Equally, in part 2 of this blog series I mentioned DLP tools. These tools are designed, as the name would suggest, to prevent the loss of sensitive data. In practice, what tends to happen is one of two things: 1) the rules are too relaxed, which causes problems with security, or 2) the rules are too strict and block activity from happening, which causes problems with productivity. Allowing DLP tools to read the metadata tags helps to overcome both of these problems.
3. Streamlines the detection and remediation processes involved in a cyber-attack
There are some great tools available that quickly identify data/cyber-attacks and help to remediate them. These tools tend to be driven by algorithms that read log/network information to identify anomalous behaviour, and one of the most important components of these algorithms is context. The metadata tags provided by data classification provide incredibly important context for these tools that impacts the way in which attacks are responded to. To elaborate on this, imagine a cyber-attack has occurred and data has been lost. Wouldn’t it be great if you could also identify, amongst other things, how sensitive the data was and what protection had been applied to it? It would certainly make a conversation with the ICO a lot easier if you could confirm that no data containing personal information had been lost, for example.
Next Steps
Download our fact sheet on business-centric data classification to discover how you can wrap a protective governance shield around your data throughout its lifecycle, blending together best practices in user-driven and automated classification techniques to meet the unique needs of your business today and tomorrow.
We are excited to open the Early Access Program (EAP) of XG Firewall v18 to all Sophos customers and partners. This release offers a ton of great new features and innovations:
- Xstream Architecture delivers extreme new levels of visibility, protection and performance.
- Threat Intelligence Analysis stops zero-day threats before they get on your network.
- Top requested features and innovative enhancements make XG Firewall easier to deploy and manage.
Xstream Architecture
One of the highlights of v18 is the new Xstream packet processing architecture. It provides superior high-speed security from the latest threats; uncompromising visibility into encrypted traffic flows; and accelerated performance for your most important traffic.
The new architecture has three major components:
- Xstream DPI Engine – Deep packet threat protection for AV, IPS, Web, App Control and SSL Inspection in a single proxy-less streaming engine.
- Xstream SSL Inspection – Industry-leading performance, flexibility, and transparency into all SSL/TLS-encrypted traffic, including support for TLS 1.3 across all ports and applications.
- Xstream Network Flow FastPath – Automatic and policy-based intelligent offloading of trusted traffic processing at wire speed to ensure your trusted mission-critical traffic is always on the fast path.
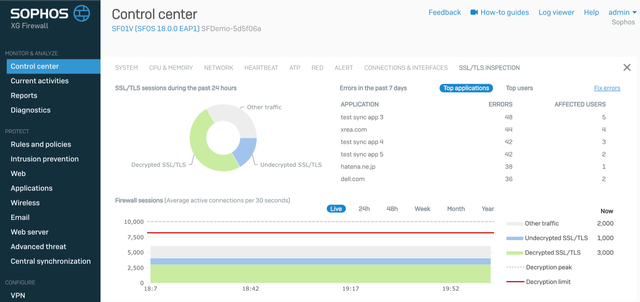
One of the new features in v18 is the new Xstream SSL Inspection widget on the Control Center for at-a-glance insights into your encrypted network traffic.
Threat Intelligence Analysis
Threat Intelligence Analysis is powered by SophosLabs and our leading deep-learning technology. Using a range of threat modelling techniques to analyze files being downloaded or arriving via email, this feature identifies and stops the latest zero-day threats before they get on the network.
To see the types of files entering the network you can get a quick overview in the form of a visual Threatometer (as shown below) and the full details in a comprehensive report.

Your top requested features
You asked and we listened – XG Firewall v18 also includes your top requested features as well as other innovative enhancements related to SD-WAN, NAT, networking, firewall rule management, notifications and alerts, and much more. Take a look at the full list of features for complete details.
Help shape it
To take part in the program, head over to our Community Forums to get the latest firmware, meet your fellow EAP participants and Sophos staff, and share your feedback.
s modern organizations are evolving their use of the public cloud to leverage scalable computing, storage, and network services, cybercriminals are adapting their techniques to exploit hidden vulnerabilities in network architecture.
Your IT security, therefore, needs to evolve to match these new tactics and threats.
Sophos Cloud Optix enables your organization to accurately visualize and secure cloud infrastructure continuously, and confidently. Our intelligent cloud solution provides a single view of security posture across Kubernetes clusters, Amazon Web Services, Microsoft Azure, Google Cloud Platform, and infrastructure-as-code environments.
Cloud Optix on AWS Marketplace
More than 200,000 active AWS Marketplace customers can now easily access Cloud Optix, on a per host, per hour basis for flexible scaling, with no minimum term contract.
Benefits of Cloud Optix on AWS Marketplace:
- Create your Cloud Optix account directly through AWS Marketplace.
- Simply pay per cloud asset, per hour with no minimum contract.
- Get the same great management experience with your own dedicated Cloud Optix console.
- Manage environments across AWS, Azure and GCP through the same console.
- Pay AWS for the assets that Cloud Optix protects.
About Cloud Optix
Our cloud security provides a full topology view of cloud infrastructure and, combining the power of AI and automation, identifies and predicts hidden threats across the virtual network.
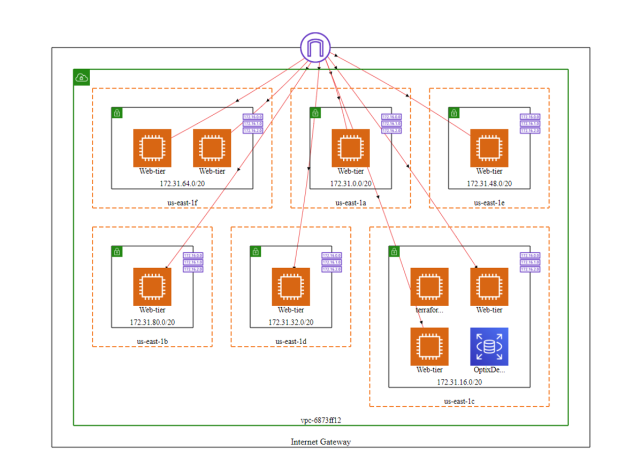
Cloud Optix applies root cause analysis, risk-based prioritization, and remediation support to security and compliance alerts so that you have the tools to automate security and decrease incident response times.
- AI enables traceability of unusual user access, api calls, and changes in configuration.
- Integrated security checks identify vulnerabilities in IAC templates that automate the deployment of new infrastructure in your cloud environments.
- Security best practices are continually monitored to ensure you stay in compliance, and any misconfigured changes can be identified and fixed quickly.
Recognized as a channel-first, channel-best leader in providing innovative solutions like Cloud Optix, Sophos has now topped the list of AWS Partner Network partners for our dedication to helping AWS customers build, market and grow successful cloud businesses, earning us AWS Partner Network (APN) Technology Partner of the Year 2019.

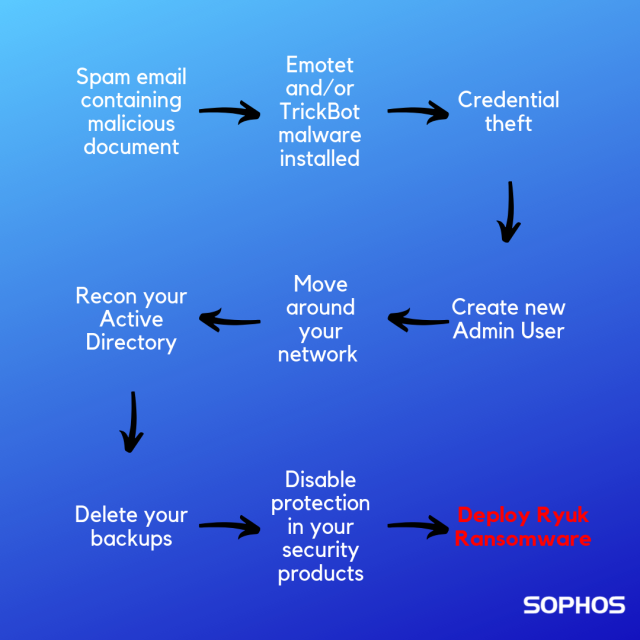
In recent weeks SophosLabs has seen a significant spike in Ryuk ransomware. This particularly nasty threat is delivered via a sophisticated, multi-stage attack, paralyzing organizations and leaving them hostage to crippling ransoms.
To understand how to stop Ryuk it’s helpful to know how the attacks unfold.
The actors behind Ryuk are active adversaries who combine advanced attack techniques with interactive, hands-on hacking to increase their rate of success.
They typically target organizations that cannot withstand any downtime, such as newspapers, municipalities, and utilities, to increase the likelihood of payment. And speaking of payments – they’re big. Often 6-figure sums payable in Bitcoin.
Ryuk attacks are complex. They frequently start with an Emotet or TrickBot attack, delivered via malicious attachments in spam emails, which enables the cybercriminals to get on your network.
Once there, they steal credentials and create a new admin user. With their escalated admin privileges in place, the hackers can move around your network, survey your Active Directory, and delete your backups.
After removing your safety net they attempt to disable your cybersecurity products before finally releasing the Ryuk ransomware, encrypting your files and demanding huge ransom payments.
Stopping Ryuk with Sophos Intercept X Advanced
Stopping Ryuk isn’t just about stopping one piece of software, it’s about stopping an active adversary and disrupting the attack chain that puts them in a position to run Ryuk. Sophos Intercept X Advanced includes a range of technologies to detect and disrupt different stages of the attack, including:
- Detecting and blocking the exploit techniques used to download and install Emotet and Trickbot (often via PowerShell or WMI), preventing the hackers from getting on your network.
- Blocking lateral movement across your network by working in real-time with Sophos XG Firewall.
- Preventing credential theft, thereby stopping unauthorized access to your systems and the escalation of admin privileges.
- Stopping the ransomware from executing by examining its “DNA” with our deep learning neural network.
- Detecting and rolling-back the unauthorized encryption of files via the CryptoGuard capabilities
Watch this video to see the CryptoGuard capabilities in Intercept X roll back Ryuk ransomware.
Try Intercept X’s anti-ransomware protection for yourself with 30 day free trial
Your dedicated team of threat hunters and response experts
While many strains of ransomware are distributed via large-scale spam campaigns, Ryuk uses automated means to gain an initial foothold, then employs human ingenuity to evade detection. In other words, there’s a human behind the attack whose goal is to circumvent or manipulate your existing security controls.
For active adversary attacks like these, having a dedicated team of threat hunters and response experts can make all the difference. The Sophos Managed Threat Response team proactively hunt, detect and respond to attacks in real-time to neutralize ransomware and other advanced threats before they can compromise your data. Find out more about Sophos MTR today.
Best practices to stop ransomware
Whatever the size of your company and whatever industry you’re in, we recommend you follow these best practices to minimize your risk of falling victim to a ransomware attack:
- Educate your users. Teach them about the importance of strong passwords and roll out two-factor authentication wherever you can.
- Protect access rights. Give user accounts and administrators only the access rights they need and nothing more.
- Make regular backups – and keep them offsite where attackers can’t find them. They could be your last line of defense against a six-figure ransom demand.
- Patch early, patch often. Ransomware like WannaCry and NotPetya relied on unpatched vulnerabilities to spread around the globe.
- Lock down your RDP. Turn off RDP if you don’t need it, and use rate limiting, 2FA or a VPN if you do.
- Ensure tamper protection is enabled. Ryuk and other ransomware attempt to disable your endpoint protection. Tamper protection is designed to prevent this from happening.
- Educate your team on phishing. Phishing is one of the main delivery mechanisms for ransomware.
- Use anti-ransomware protection. Sophos Intercept X and XG Firewall are designed to work hand in hand to combat ransomware and its effects. Sophos Managed Threat Response (MTR) provides a team of threat hunters who proactively hunt, detect and neutralizeattacks that require human intervention.
We’re very excited to extend our customers’ protection against the most advanced threats with the launch of our new service: Sophos Managed Threat Response (MTR). The resellable service provides organizations with a dedicated 24/7 security team to neutralize the most sophisticated and complex threats.
Few organizations have the right tools, people, and processes in-house to effectively manage their security program around the clock while proactively defending against new and emerging threats. Unlike many MDR services that focus exclusively on monitoring and threat notification, the Sophos MTR team takes targeted actions on your behalf to neutralize even the most sophisticated and complex threats.
With Sophos MTR, your organization is armed with a 24/7 team of threat hunters and response experts who:
- Proactively hunt for and validate potential threats and incidents
- Use all available information to determine the scope and severity of threats
- Apply the appropriate business context for valid threats
- Provide actionable advice for addressing the root cause of recurring incidents
- Initiate actions to remotely disrupt, contain, and neutralize threats
Machine-accelerated human response
Built on our Intercept X Advanced with EDR technology, Sophos MTR fuses machine learning technology and expert analysis for improved threat hunting and detection, deeper investigation of alerts, and targeted actions to eliminate threats with speed and precision. This fusion of Sophos’ consistently top-rated endpoint protection and intelligent EDR, with a world-class team of security experts results in what we call “machine-accelerated human response.”
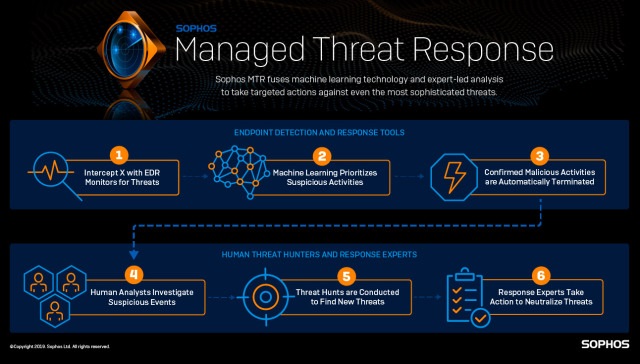
Complete transparency and control
Sophos MTR is customizable, with different service tiers and response modes to meet the unique and evolving needs of organizations of all sizes and maturity levels.
With Sophos MTR you own the decisions, and control how and when potential incidents are escalated, what response actions (if any) you want us to take, and who should be included in communications. Sophos MTR features three response modes so you can choose the best way for our MTR team to work alongside you during incidents:
Notify: We notify you about the detection and provide information to help you in prioritization and response.
Collaborate: We work with your internal team or external point(s) of contact to respond to the detection.
Authorize: We handle containment and neutralization actions and will inform you of the action(s) taken.
Visit Sophos.com/MTR or download the datasheet to learn more.
CyberArk is pleased to announce that our as-a-service CyberArk Privilege Cloud offering is now available on Amazon Web Services (AWS) Marketplace. CyberArk Privilege Cloud is a SaaS offering built to protect, control and monitor privileged access across on-premises, cloud and hybrid infrastructures.
Designed from the ground up for security, CyberArk Privilege Cloud helps organizations efficiently manage privileged account credentials and access rights, proactively monitor and control privileged account activity and quickly respond to threats. This added security comes without the need to manage additional on-premises infrastructure, so organizations can focus on their core competencies.
The availability of CyberArk Privilege Cloud marks the fourth CyberArk offering to be available on AWS Marketplace, joining Conjur Open Source, the CyberArk Privileged Access Security Solution and the CyberArk Privileged Access Security Solution for GovCloud – reinforcing the depth of the CyberArk relationship with AWS.
CyberArk is the trusted leader in privileged access security, helping the world’s leading organizations to protect against external attackers and malicious insiders in the cloud, on-premises and everywhere in between. Organizations use CyberArk solutions to protect the cloud workloads they deploy and run on AWS, securing their privileged accounts and credentials at each stage of their cloud journey.
CyberArk Privilege Cloud offers support to several powerful integrations with AWS to bolster security for organizations’ cloud assets, including the integration with the AWS Security Token Service (STS) and Amazon Inspector. CyberArk Privilege Cloud customers can also download the AWS Automatic onboarding solution from our public GitHub, which uses AWS CloudWatch events to detect newly provisioned EC2 instances and automatically onboards and manages the privileged accounts.
To check out the CyberArk solutions available for download and purchase on AWS Marketplace, click here!
It’s crucial it is that your defenses evolve faster than the attacks. To help get the right protection, here are three questions you should be asking of your endpoint solution:
Does your solution have industry-leading anti-exploit technology? Attackers must be prevented from using software vulnerabilities to distribute and install ransomware.
How will your solution stop attacks it’s never seen before? Your defense system must be able to identify unknown, unseen, and previously unidentifiable executables.
Should ransomware find its way onto one of your endpoints, how will your solution deal with it? A best-in-class solution should not only stop attacks, but also roll affected files back to their previous safe states.
Give your organization the best possible cyber defenses with Intercept
X Advanced with EDR. By combining cutting-edge protection technologies with intelligent EDR, Intercept X delivers unmatched threat protection and response.
Try for yourself and see why more and more customers are trusting Sophos for their cybersecurity.
Following on from our introduction to user-driven security, and why people are seen as such a risk in business. We are now looking at the three main steps you can take to turn your people from a risk into your greatest security assets:
Step 1 – Educate your users
Build a custom training program for your employees that encompasses all areas of security, but places a particular focus on data. This will teach users the value of the data they are handling to ensure they work with data in a way that complies with your internal security policies and adheres to the relevant regulations.
Step 2 – Classify your data
How can you appropriately protect data if you don’t know its true value? (Answer: YOU CAN’T!). In the same way that when you move house, if you had a lorry full of brown boxes with no labels, you’d be in a bit of a mess at the other end, exactly the same applies to data. You should be able to quickly identify how sensitive the content is and how it should subsequently be handled, stored and protected. Boldon James Classifier applies both visual labels and metadata to ensure users and downstream technologies handle the data appropriately. Classifier is a user-driven tool that prompts users to classify data at the point of creation. To avoid mistakes and further improve user education, the tool scans data to ensure the label selected adheres to your policies and prevents the ‘under-classification’ of data. So essentially working on a ‘Trust but Verify’ basis.
Step 3 – Enhance your existing technologies and enforce your security policies
User training and data classification enables businesses to enforce their security polices in a way that is difficult to achieve by any other means. The metadata applied during the classification process can be read by several complimentary technologies and enhances their performance. For example, Data Loss Prevention (DLP) tools can simply scan the metadata and apply relevant handling rules based on this.
You can read the original article, here.
We’re delighted to announce that Gartner has named Sophos a Visionary in the Network Firewall Magic Quadrant for 2019. We believe that this recognition confirms Sophos XG Firewall as one of the best next-generation firewalls on the market.
At Sophos we have been evolving and moving the network firewall space forward:
- Sophos has developed the ultimate cybersecurity ecosystem for management, visibility and protection with Sophos Central cloud management and Synchronized Security.
- We have positively changed the industry with Security Heartbeat and our integration of XG Firewall with Intercept X – providing the ultimate threat visibility, protection and response.
- And we have also been responsive to the emerging needs of businesses as they move their datacenters and application usage to the cloud, providing visibility to cloud application usage and cloud infrastructure protection.
We believe Gartner’s placement of us as a Visionary in the Network Firewall Magic Quadrant for 2019 is a testimony to our continued:
- cloud strategy and product innovation
- responsiveness in addressing top industry challenges
- synchronized Security and protection capabilities
- strong vision and relentless roadmap execution
- excellent customer experience.
And, we’re just getting started. New innovative breakthroughs in network visibility, protection and performance are coming very soon in XG Firewall v18 which is expected to kick off with an Early Access Program later this month.
To find out what Gartner says about the Enterprise Firewall marketplace download the complete Magic Quadrant report (registration required).
Artificial Intelligence, User Behaviour Analytics, Zero-Trust… these are the buzzwords the security industry is currently dominated by. The developments to cyber security technology which have been made over the last few years are incredible, developments that are absolutely essential in the progression towards a more secure world. A key assumption in a lot of this development is that humans are simply a risk that needs to be mitigated by technology. To a certain extent, this is absolutely the right approach. However, despite everything we can do from a technology perspective, malicious actors will always exist and people will continue making innocent mistakes. Technology cannot solve every problem. So how can we effectively mitigate this risk? I believe we should adopt a more positive approach; an approach in which the aim is to transform humans from a security risk into a security asset. In short: user-driven security.
What do we mean by user-driven security?
User-driven security is a methodology which understands how people interact with data, why people make mistakes and ways to identify and prevent innocent mistakes/malicious activity. Using these insights, businesses are able to implement a simple strategy that involves educating users to understand how to operate in a more secure way, incorporating security policy as part of their day to day workflow and using the information provided by users to enhance the cyber security technology the business already uses. This process can make businesses more secure and more efficient.
Why are people seen as a risk?
When you look into the plethora of research available on the reasons behind, and causes of, data loss, it’s clear to see why people are seen as such a risk. For example, The Information Commissioner’s Office (ICO) produces statistics about the main causes of data security incidents and in cases where they have taken action, human error and process failure tend to be the leading cause. More specifically, the reasons tend to be things such as: loss/theft of paperwork, data sent to the wrong recipient or loss/theft of an unencrypted device. It’s easy to see how and why these events can occur so easily. Let’s take a look at three of the key reasons:
- People are busy and huge amounts of data are created every second
- Data is becoming the most valuable asset a business has, which incentivises malicious actors to try and steal it
- Businesses (and therefore, employees) don’t tend to understand the value of each piece of data they create
The effective use of technology does go a long way to overcoming some of these challenges. However, using technology alone still leaves gaps and in some instances has an adverse effect on productivity.
Next in this three part series, Aaron will be looking at the 3 main steps you need to take for a user-driven approach.
Sophos Intercept X has beaten 11 other endpoint protection products in the latest tests by MRG Effitas.
The Q2 2019 MRG Effitas 360 Degree Assessment and Certification compared 12 endpoint protection products using “metrics that matter” to replicate real-world scenarios.
Sophos Intercept X was tested in its default, out-of-the-box configuration and was able to protect the test system from infection in every scenario:
- Blocked – 100% of zero day, in the wild attacks
- Blocked – 100% of malware tested (trojans, ransomware and other malicious applications)
- Blocked – 100% of exploits and file-less attacks
- Blocked – 100% of adware and PUAs
- No false positives
No other vendor achieved results this strong without configuration changes.
MRG releases a new version of this test every quarter. This is the first time Sophos has participated publicly. You can download the full report here.
Intercept X Third Party Test Results
Intercept X Advanced is the world’s best endpoint protection. In addition to plaudits by SE Labs, it’s consistently performed at or near the top of multiple third-party tests.
SE Labs
- AAA Rated for Enterprise – 100% total accuracy rating
- Best Small Business Protection Award – AAA rated for SMB, 100% total accuracy rating
NSS Labs
- Ranked #1 for Security Effectiveness
- Ranked #1 for Total Cost of Ownership (TCO)
AV-Comparatives
- Ranked #1 for Malware Protection (99.9% detection, 0 false alarms)
MRG Effitas
- 100% block rate, 0 false positives – 360 Degree Assessment
- Ranked #1 for Exploit Protection
- Ranked #1 for Malware Protection
PC Magazine
- Editor’s Choice, Best Ransomware Protection for Business 2019
AV-Test
- AV-Test (Windows) – Top Product
- AV-Test (Mac) – Perfect Score
- AV-Test (Android) – Perfect Score
One reason Intercept X excels like this is because it offers multiple layers of security in a single solution and a single agent to deliver unparalleled protection against advanced attacks.
Under the hood, Intercept X integrates deep learning malware detection, anti-exploit technology, active-adversary protection, specific anti-ransomware technology and a host of foundational endpoint security techniques.
Sophos, a global leader in network and endpoint security, today announced it was named the 2019 Best Small Business Endpoint security solution by SE Labs in its inaugural “Annual Report.” The new report recognizes Intercept X Advanced as the industry’s best for endpoint threat protection based on strong product performance following months of in-depth testing.
SE Labs “tested more than 50 different products using over 5,000 targeted attacks. These attacks were run in a realistic way using publicly available hacking tools,” according to the report. “To ensure our testing is as realistic and useful as possible, we monitor real-world breaches from a technical point of view. This allows us to adapt and change our testing in a similar way to how real attackers operate.”
Intercept X Advanced consistently ranks best at detecting and stopping attacks. It achieved 100 percent Total Accuracy Ratings for enterprise and small business endpoint protection in SE Labs’ 2019 endpoint protection test reports. It’s also earned AAA ratings in every SE Labs test to date.
“Cybercriminals are constantly evolving their methods, launching new attacks in attempt to go undetected,” said Dan Schiappa, chief product officer at Sophos. “Automated, active attacks targeting businesses of all sizes are on the rise, and organizations need advanced endpoint protection now more than ever. Sophos is committed to stopping never-before-seen, zero day cyberattacks, plus ransomware and other attacks that cybercriminals are persistently using. This award is validation that we’re helping organizations stay one step ahead.”
Intercept X Advanced is the industry’s most sophisticated endpoint prevention solution, offering multiple layers of security to deliver unparalleled protection against advanced attacks. Leveraging deep learning and anti-exploit technology, Intercept X Advanced stops the widest range of threats by employing a comprehensive defense-in-depth approach to endpoint protection.
News hit this week that 22 government organizations in the Lone Star State were recently hit by coordinated ransomware attacks. It’s a stark reminder that as attacks continue to evolve, it’s crucial that your defenses evolve even faster.
Ask about these three big, protective layers against advanced attacks
So how can you help ensure your organization isn’t the next ransomware victim?
For starters, does your solution have industry-leading anti-exploit technology to ensure attackers can’t use unpatched, vulnerable software programs to distribute and install ransomware?
Sophos Intercept X Advanced blocks more exploit techniques than any other endpoint protection product on the market. It’s not enough to just have exploit protection: the number of exploit techniques a product protects against is also extremely important. Luckily, if it can be exploited, Intercept X Advanced has the best chance of neutralizing it.
Should that not stop an attack – or should an exploit not be leveraged – how will your solution stop attacks it’s never seen before?
Our award-winning deep learning engine can identify unknown, unseen, and previously unidentifiable executables with greater accuracy than – you guessed it – any other vendor on the market.
And finally, should the unthinkable happen – should ransomware find its way onto one of your endpoints and start executing – how will your solution deal with it?
The second-to-none CryptoGuard anti-ransomware technology found in Intercept X Advanced not only offers the best ransomware protection on the planet to stop attacks in their tracks, but also uses proprietary shadow-copy technology to roll affected files back to their previously-safe states, and cleans up affected registry entries – all in the blink of an eye. It’s not enough to just stop a ransomware attack: it needs to be reversed and cleaned up as well, so you can get on with your day.
These are just three of the ways that Intercept X can thwart an attack, all backed up by a very long list of pre-execution, runtime, and post-execution features.
Seeing is believing
Here’s a closer look at what happens when a popular ransomware variant tangles with Intercept X technology:
Take it for a spin
Of course, the best way to experience the power of Intercept X Advanced is to try it yourself. Download a free 30-day trial, and you’ll be up and running in minutes. Evolve your defenses today!
You can read the original article, here.
Data breaches are on the rise – it’s a fact. In times like these, it’s important to ask yourself – are you being vigilant? And crucially, are you in the know?
The following statistics have been taken from the recent 2019 Verizon Data Breach Investigations Report and identify those behind the breaches, as well as the victims. The report looked at 41,686 security incidents, of which 2,013 were confirmed data breaches.
The victims
Looking at the victim demographics and industry analysis specifically, of the 20 industries covered in the report, only the Public Sector ranked higher than Healthcare and Finance for the number of known recorded breaches…
- 16% were breaches of Public Sector entities
- 15% were breaches involving Healthcare organisations
- 10% were breaches of the Financial industry
These industries remain in the top three for victims affected, and unsurprisingly, are the three industries that hold the most PII (personally identifiable information) and sensitive consumer data. Indeed, according to the report, internal data, credentials and personal information ranked highest in the top data varieties compromised in breaches.
Healthcare organisations specifically carry huge amounts of PHI (protected healthcare information), that if found its way into the wrong hands, could be detrimental for all involved. According to HIPAA Journal’s April 2019 Healthcare Data Breach Report, April was the worst month for healthcare data breaches since reports began back in October 2009. For example, Gulf Coast Pain Consultants, LLC d/b/a Clearway Pain Solutions Institute recently announced that their Electronic Medical Record System was accessed without authorisation, exposing approximately 35,000 records of patient data which included social security numbers and insurance information.
The culprits
So who is responsible? The report identifies that outsiders remain the principal threat through use of hacking and malware, among others. But crucially, privilege abuse and data mishandling still rank highly in the top misuse varieties in breaches…
- 69% perpetrated by outsiders
- 34% involved internal actors
- 15% were misuse by authorised users
From the figures above, it is clear to see that insider threat is proportionate to that of outsiders, and not something to be ignored. Recent reports suggest that long before Facebook, Twitter and Instagram, Myspace employees were abusing their access rights by using a specific tool to spy on its users. And just the other month it was announced that Snapchat employees had been doing the same to access location information, saved Snaps, phone numbers and email addresses.
The importance of being vigilant
It’s important to recognise that when breaches occur, sometimes they can lie unnoticed for a substantial amount of time. Verizon’s report highlights that 56% of breaches took months or longer to discover; something to make you think given recent changes in global data protection regulations. The result of discrepancies such as this can lead to potentially devastating fines and irreparable reputational damage for your organisation, among other detrimental consequences.
It’s crucial to get employees on side and playing a part of the security team within the organisation, as they really are one of the greatest assets in the security ecosystem. This “security first” mentality in users helps with practising good vigilance: being aware of potentially suspicious behaviour, as well as handling sensitive data responsibly.
Alongside vigilant staff, data classification software can also play a crucial part in preventing data breaches by improving user awareness and data control to protect business critical data, as well as offering built-in reporting tools such as Boldon James Classifier Reporting, to monitor and report on classification events, and the handling of classified data within the organisation.
You can read the original article, here.
To understand the need for Endpoint Detection and Response (EDR), let’s begin by discussing the cybersecurity environment.
To give a sense of scale, our own cybersecurity experts in SophosLabs process 500,000 never-seen-before malware samples each day. In 2018, the National Institute of Standards and Technology (NIST) reported that 16,451 software vulnerabilities were discovered. The challenge for defenders keeps growing, leading to a desire for better visibility and detection capabilities.
Organizations are having to deal with multiple threats trying to enter their environments on a daily basis. Naturally, many of these threats are stopped outright with strong cybersecurity defenses. But those which are evasive, uncommon, or unclear can slip through, which is where EDR comes into play. EDR was borne out of a need to supplement existing endpoint protection tools.
To make this easier to understand, let’s use a visual example: 
1. Benign
These are non-malicious programs that are part of daily life in the vast majority of organizations, such as Microsoft Word, Outlook or Google Chrome. We don’t want to interfere with them, as this would cause disruption to the wider business.
2. Gray area or ‘the gap’
This area concerns items which aren’t obviously good or bad, so we don’t know whether they are fine to leave or should be blocked without performing further, manual investigation.
EDR was developed to investigate the gap. Are these items actually malicious, requiring action such as isolating affected devices or performing cleanup? Are they Potentially Unwanted Applications (PUAs)? Or something benign that can be ignored?
As threats evolve, many are becoming stealthier, using specific methods to fool antivirus solutions. EDR gives organizations the tools to hunt for suspicious Indicators of Compromise (IOC) and pick up on these hidden threats.
3. Malicious
Malicious files should be stopped outright by strong endpoint and server defenses. These are convicted as malicious and don’t require human interaction. Unfortunately, some traditional EDR tools fail here, letting through malware that should have been caught. This is because their strengths lie with post-event detection rather than pre-emptive protection.
What to look for in an EDR solution
EDR tools can vary wildly in terms of ease of use and granularity of analysis. The key questions to ask when evaluating an EDR solution are:
- Does it require additional resources, or can you get value from it with your current team?
- Does it help you prioritize your time by showing you the most suspicious items?
- Can you see how a potential threat came in and what it interacted with?
- Do you get intelligence on the suspicious item, such as from machine learning or cybersecurity specialists?
- Is it easy to take action when you have made a decision? For example, blocking a threat or isolating a device?
Read the Top 5 Reasons You Need EDR whitepaper to get more detail on EDR and why it has become a necessity for most organizations. Then take a look at Sophos Intercept X with EDR that combines industry leading protection with powerful, straightforward to use EDR capabilities.
You can read the original article, here.
Ransomware has recently vaulted to the top of the news again, as devastating attacks continue to impact government, education and business operations in many jurisdictions, particularly in the United States.
These attacks start in a number of ways – some start with a phishing email, others begin with hackers leveraging vulnerabilities in networking stacks to gain a foothold and move quickly to other systems on the network. The most famous network vulnerability exploited in a ransomware attack was EternalBlue a couple of years ago. But since then, new vulnerabilities like BlueKeep have been discovered (and patches made available), but there are still many networks out there that are vulnerable.
Unfortunately, many of these network stack vulnerabilities are ‘wormable’ which means that hackers and malware can exploit these holes in an automated method with no user interaction, enabling the infection to spread quickly and easily to a wide group of systems.
Of course, deploying an industry leading anti-ransomware endpoint protection product like Sophos Intercept X, and maintaining a strict patch management strategy are top best practices. But there are also other best practices you should consider to help keep ransomware, hackers, and attacks off your network in the first place.
Your firewall provides essential protection against exploits like EternalBlue and BlueKeep by closing up or protecting vulnerable ports, as well as blocking attacks using an Intrusion Prevention System (IPS). IPS looks at network traffic for vulnerabilities, and exploits and blocks any attempt for attackers to get through your network perimeter or even cross boundaries or segments within your internal network.
While we have a full guide on how to protect your network, here are the essential firewall best practices to prevent ransomware attacks from getting into and moving laterally on your network:
- Reduce the surface area of attack: Review and revisit all port-forwarding rules to eliminate any non-essential open ports. Where possible use VPN to access resources on the internal network from outside rather than port-forwarding. Specifically for RDP, ensure port 3389 is not open on your firewall.
- Apply IPS protection: Apply suitable IPS protection to the rules governing traffic to/from any Windows hosts on your network.
- Minimize the risk of lateral movement: Use XG Firewall and Synchronized Security to protect against threats moving laterally on your network and consider segmenting your LANs into smaller subnets, assigning those to separate zones that are secured by the firewall. Apply suitable IPS policies to rules governing the traffic traversing these zones to prevent worms and bots from spreading between LAN segments.
XG Firewall and Synchronized Security are your best protection against the latest threats with industry leading protection and performance. Stop the latest hacks and attacks dead in their tracks.
Download the guide to learn more.
You can read the original article, here.
For the 11th time in the last 11 reports, Sophos has been named a Leader in the 2019 Gartner Magic Quadrant for Endpoint Protection Platforms.
What makes Sophos a Leader?
We believe our placement is driven by our strong endpoint protection, real-world endpoint detection and response (EDR) usability, as well as our unifying platform, Sophos Central. We believe Gartner recognized Sophos for our proven record at stopping ransomware, the deep learning technology that blocks never-seen-before malware, and our anti-exploit technology.
Summary
We believe being positioned as a leader in the Magic Quadrant for EPP 11 times in a row is a fantastic achievement for Sophos. As the endpoint protection marketplace changes, we continue to evolve as well, driven by our increased brand awareness in enterprise organizations and 3rd party test results. Additionally, as EDR has become more tightly integrated with endpoint protection, Sophos is leading the way with an EDR offering that adds expertise, without adding headcount.
We believe we will retain this positioning going forward thanks to our continued excellence in endpoint protection, industry leadership in artificial intelligence, massive growth and ongoing enhancements for our EDR offering, and our upcoming managed detection and response (MDR) launch.
Intercept X Third Party Test Results
- AAA Rated for Enterprise – 100% total accuracy rating (Jan-Mar 2019)
- AAA Rated for SMB – 100% total accuracy rating (Jan-Mar 2019)
NSS Labs
- Ranked #1 for Security Effectiveness
- Ranked #1 for Total Cost of Ownership (TCO)
AV-Comparatives
- Ranked #1 for Malware Protection (99.9% detection, 0 false alarms)
MRG Effitas
- Ranked #1 for Malware Protection
- Ranked #1 for Exploit Protection
- Editor’s Choice
AV-Test
- AV-Test endpoint “Top Product”: 6/6 Protection, 6/6 Usability, 5.5/6 Performance
- AV-Test (Mac): Perfect Score 6/6 Protection, 6/6 Usability, 6/6 Performance
- AV-Test (Android): Perfect Score
You can read the original article, here.
A corporate data security policy that sets out how valuable information should be handled will be ineffective unless it’s consistently and accurately enforced. Organisations often have a written policy that’s available on their company intranet and handed to new starters. In practice, however, employees are rarely sure how to apply it to their daily activities.
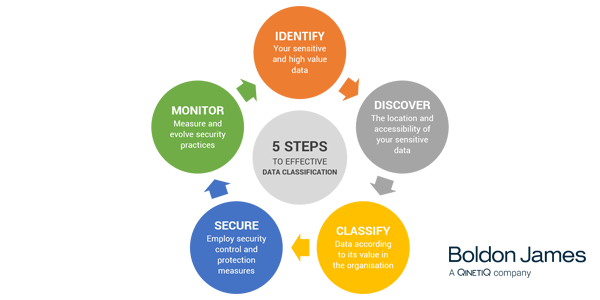
The security policy needs to be made actionable – and the best way of doing this is with the classification of data. This is the first of the two steps that involve actively securing data, with the second being the implementation of technology solutions that will protect it downstream. Classification makes those solutions more effective.
Data classification is the categorisation of data according to its level of sensitivity or value, using labels. These are attached as visual markings, and also embedded into the metadata of the file. When classification is applied in association with downstream security solutions, the metadata ensures that the data can only be accessed or used in accordance with the rules that correspond with its label.
It’s possible to completely automate the process, but our clients get the best results when they combine human input with the use of software toolsets to support successful implementation. This is known as user-driven data classification.
With this approach the employee is responsible for deciding which label is appropriate, and attaching it at the point of creating, editing, sending or saving. The user’s insight into the context around the data leads to more accurate classification decisions than a computer could ever make.
Defining the classification policy
First, be clear on who should have access to each type of data. The work you did in step 1 and step 2 will prepare the ground for this. Next, decide how many categories you’ll have. Aim for three or four – the fewer the options the simpler it is for users. Labels that indicate Confidential, Internal only and Public are a good start, with perhaps a fourth category relating to information that’s subject to regulatory controls – such as EU GDPR, ITAR controlled or HIPAA/HITECH restricted.
Selecting your classification tool
The right technology will help your users to consistently apply the classification scheme, and will also add the all-important metadata. The most effective tools make classification a seamless part of business-as-usual; integrating the labelling process into the standard applications employees already use. Ensuring breadth of coverage across operating systems and application types is vital to future-proof your investment.
See recent reviews on Boldon James Classifier Foundation Suite here.
Rolling out data classification in your organisation
Start by classifying your ‘live’ data – the emails, files and documents that are being created and handled right now. If you’ve followed steps 1 and 2 you’ll know exactly what and where it is. By doing this, you’re ensuring that all your ‘crown jewels’ will be safely locked up from this point forward. When that is established decide how to label the existing and legacy data that is stored and held around the organisation. This process usually works well in combination with a discovery agent or tool.
Once you’ve labelled your data, it’s time to turn your attention to the enterprise security solutions and information management technologies that will control and protect it throughout the remainder of its journey.
Next steps
Download our whitepaper: The 5 Steps To Effective Data Protection – this will guide you through the 5 steps to implementing effective data protection within your organisation, and detail how data classification can also enhance previously implemented tools, such as data loss prevention tools (DLP), data discovery tools, data governance tools and more.
By classifying data according to its value or sensitivity, organisations can reduce the risk of security breaches by ensuring that appropriate protections are implemented and consistently enforced. Having identified your ‘crown jewels’, and other data that needs safeguarding, it’s time to carry out a discovery exercise to find out exactly what you’ve got, where it is and who might have access to it.

Unknown data makes you vulnerable to attack. The best thought-out security policy is ineffective if you’re not certain what you hold and, therefore, what controls you need to put on it. Data governance, compliance with regulation such as the EU GDPR and ITAR and – just as importantly – demonstrating that compliance are also impossible when you don’t know where key documents reside and who has access to them.
A discovery exercise will give you visibility of your data and how it’s being accessed and used. This enables the protection strategy and solutions to be built around the types of data you have. It provides an opportunity to cut retention costs, too, by disposing of redundant data; mid-sized organisations spend £435k per year on storing and managing obsolete data, according to the Vertitas Databerg report. Discovery also makes it easier to use data as a resource, deriving insights that will inform strategies and improve operations.
You need to establish:
- what data you hold
- what is being collected
- what is being created
- where it’s stored or located
- why you have it
- how sensitive it is, and
- who is accessing, using or sharing it.
Getting a grip on this is a challenge. Alongside structured data held in on-site databases, companies typically have huge volumes of unstructured data such as emails, PowerPoint decks, Excel files and PDF documents.
Information is also stored and shared across an expanding variety of systems, devices and platforms, including the cloud, collaboration tools like Microsoft SharePoint, file share sites like Dropbox and OneDrive, and ‘shadow IT’ (unsanctioned tools and apps not designed for enterprise use).
Data discovery tools and software provide an efficient and accurate way to find assets you can then classify. They examine file stores and databases, scanning for certain types of information, key words, criteria and classification metadata. This enables you to see what your data is, its location, and who has access. According to Forrester 44% of North American and European technology decision-makers use data discovery tools.
Once you’ve defined the data within your business you’ll be able to home in on the most valuable and confidential information and make accurate decisions about how it should be handled, and who is allowed to access which files. You’ll then be ready to classify it according to its importance or sensitivity to ensure data is appropriately controlled.