News
The coronavirus and resulting changes to work practices have a number of cybersecurity repercussions. This article brings together all of our advice to support people through this challenging time, including best practices for secure remote working as well as information on cyberthreats that exploit COVID-19.
We will continue to update this page as new resources and research findings become available.
Non-stop Sophos protection during the coronavirus pandemic
We’d like to reassure our customers and partners that our ability to protect them is uncompromised. All departments, including threat intelligence, protection and response from SophosLabs, Managed Threat Response and Global Support Services are operating as normal to provide 24×7 detection, protection and technical support. Read our full statement.
FREE personal PC and Mac protection for all Sophos customers
For the duration of the COVID-19 global health concern, all Sophos customers can protect their employees’ personal PCs and Macs for free with our Sophos Home Commercial Edition program.
It gives your staff the same business-grade protection that our commercial customers already enjoy, providing added security and peace of mind when working remotely. For more information and to request your free access, please reach out to your Sophos representative.

Best practices for secure remote working
Coronavirus and remote working: what you need to know
This article explores the behaviors and technologies you need to keep your organization protected from cyberthreats while enabling people to work remotely. This guidance is applicable to all organizations.
Facilitating remote working with Sophos XG Firewall
Sophos XG Firewall and SD-RED devices provide multiple solutions for secure remote connectivity. This article looks at the specific features in XG Firewall that support remote working and provides information on configuring IPsec and SSL VPN connections.
Securing remote working with Sophos Endpoint Protection
Sophos Endpoint Protection is designed to secure everyone, whether they’re office-based or working elsewhere. In this article we explore how to set up remote workers, including how to create web filtering and peripheral control policies.
Coronavirus threat research from Sophos
Coronavirus warning spreads Trickbot malware
Our SophosLabs researchers recently discovered a spam campaign targeting Italy that ultimately results in infection by a well-known strain of Windows malware called Trickbot. We anticipate that attackers will try to use similar approaches in other countries.
Coronavirus “safety measures” email is a phishing scam
The Sophos security team detected a phishing attack purporting to be from the World Health Organization.
Sophos Endpoint Protection is designed to secure everyone, whether they’re office-based or working elsewhere. With many customers enabling or exploring remote working for their employees, this article highlights key capabilities that help you keep your users and data secure while working from home.
Setting up remote workers
The Sophos Central management platform makes it easy to set up and protect employees who are working from home, even if they are a new user or are using a personal device.
To get started you can download the installer file for whichever components you wish to deploy. Alternatively you can use email deployment which is perfect for users who are not currently on the network or for users who need to perform the installation themselves.
If users are not already imported or synchronized via Active Directory synchronization, you need to import their email addresses into Sophos Central. Once complete, simply click the Send Installers to Users button that is highlighted in the image below.
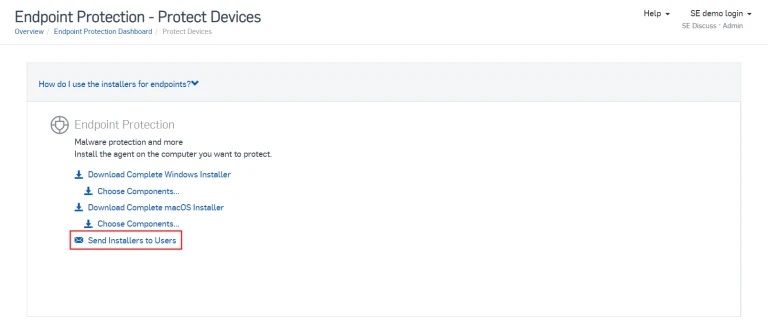
A simple wizard will guide you through picking which components to deploy. The user will receive an email with instructions on what to do and a link to the installer for them to run themselves.
For more information on the various deployment methods for our endpoint protection agent, see Knowledge Base article 119265.
Keeping employees safe on the web
When a user is in an office, traditionally it’s your company firewall that enforces web filtering rules. However, unless they are using a VPN, when people work from home their laptop needs to pick up that role and enforce any web filtering rules defined by your organization.
At the same time, working from home can also lead to changes in behaviour as users adopt a ‘home use’ rather than ‘work’ mindset. This can lead them to use their company device for non-work purposes.
The Web Control capabilities in Sophos Endpoint Protection stops risky file types being downloaded and blocks access to inappropriate websites. Read our step-by-step guidelines for creating a Web Control policy.
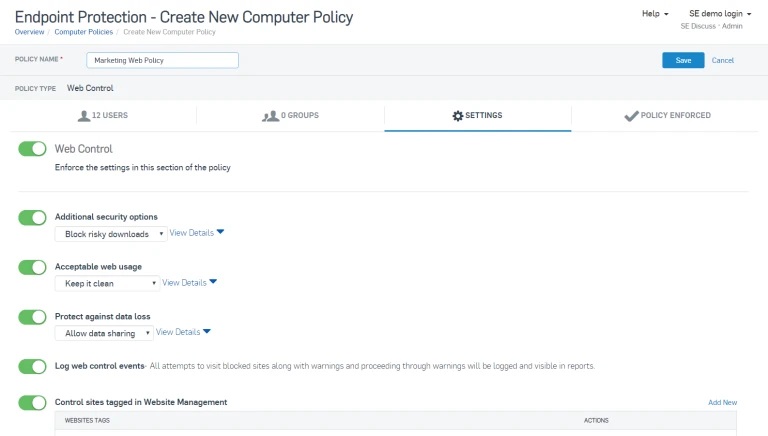
Controlling which peripherals employees can plug into their devices
14% of cyberattacks entered the organization via USB sticks or external devices, according to our recent survey of 3,100 IT managers. With more people working from home, there is potential for people to plug new devices into their company laptop.
Peripheral Control in Sophos Endpoint Protection enables you to control what employees can and can’t plug into their corporate devices. Read our step-by-step guidelines for creating a Peripheral Control policy.
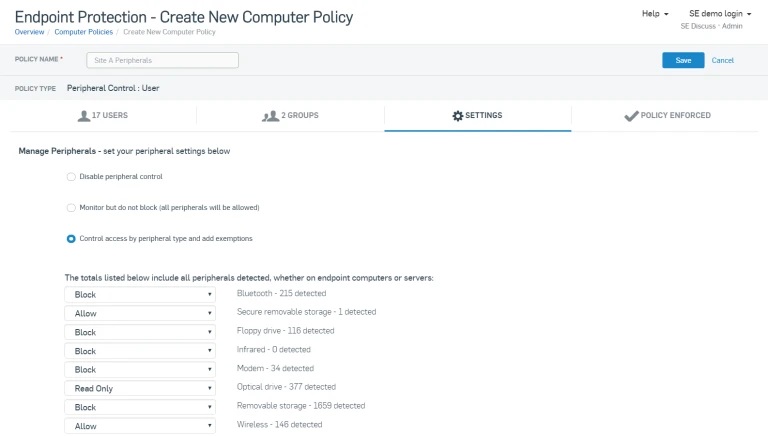
For more information on how to enable safe and secure remote working, visit our remote working page or speak with your Sophos representative.
As organizations look to keep their workforce connected and productive, the ability for employees to work from home or any another location has become critical. While coronavirus (COVID-19) is driving the current increase in remote working, long commute times, severe weather and the need for greater flexibility are just some of the other reasons companies are looking at alternatives to working in an office.
Sophos XG Firewall and SD-RED devices provide businesses, schools, hospitals and other organizations with multiple solutions for secure remote connectivity. Employees can have access to applications, email and resources on the network from their own home, just as if they were onsite. And, you can keep them safe with features like web filtering which controls access to websites containing harmful and inappropriate content. Here’s how:
XG Firewall and Connect client
If you own an XG Firewall (hardware or virtual appliance), you have a perpetual Base license that includes both IPsec and SSL VPN connectivity. You can choose either or both to provide your remote workers with access to the corporate network.
Setting up IPsec-based remote access is managed through Sophos Connect client on XG Firewalls running v17.5 or newer firmware. Connect client is focused on ease of use and reliability to ensure an extremely positive user experience. Just select your desired network or office and click “Connect” to establish an encrypted VPN tunnel that secures the transmission of traffic (data, applications, etc.) between the firewall and remote device. On the client side, the remote device uses free Connect client software for either Windows or macOS to create the VPN connection.
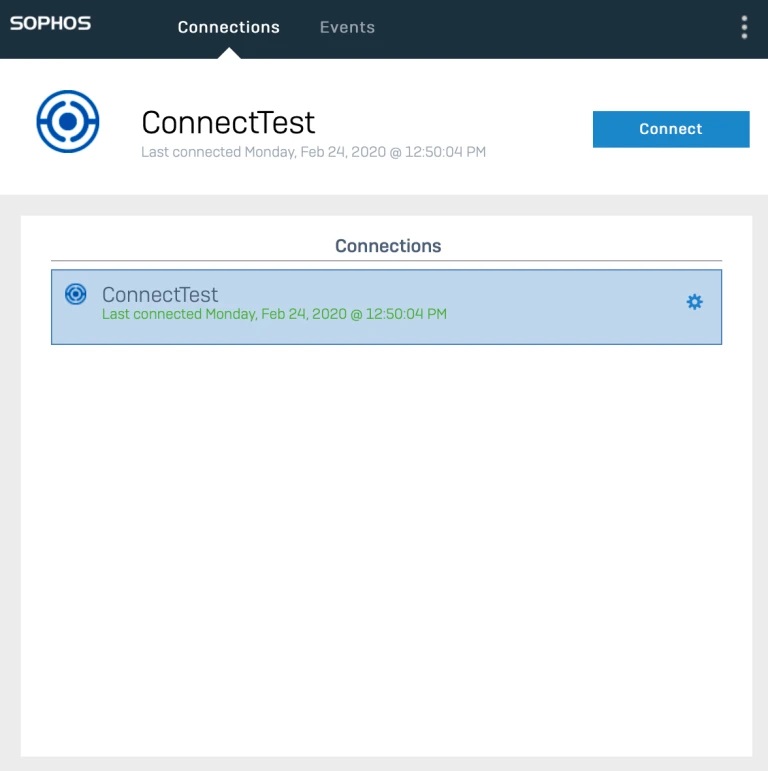
SD-RED
An alternative solution for connectivity from home is Sophos SD-RED. These low-cost Remote Ethernet Devices create a secure Layer 2 VPN tunnel to a central XG Firewall. SD-RED makes a great remote access solution for connecting remote sites, as well as for individual employees who deal with particularly sensitive information, such as executives.
No technical expertise is needed to connect the device. Simply note the device ID in your XG Firewall and ship it to the employee. As soon as it’s plugged in and connected to the internet, the SD-RED appliance contacts your XG Firewall and establishes a secure dedicated VPN tunnel. You can connect to the device directly or wirelessly through a Sophos APX wireless access point.
IPsec or SSL VPN: Which remote access solution is right for me?
With both IPsec and SSL VPN options available to you in XG Firewall, how do you choose the one that’s right for you? Here are some points to consider when evaluating your environment:
IPsec VPN – Sophos Connect client
Strengths:
- Easy for administrators to bulk deploy and provision
- Intuitive to use
- Consistent performance
- Windows and macOS support
Challenges:
- IPsec occasionally blocked on hotel/public hotspot networks
- No automated user group provisioning
- Currently limited to 255 simultaneous connections
SSL VPN
Strengths:
- Provision access by user groups
- Works in more restricted environments
Challenges:
- Agent deployment geared to end user self-installation
- User action required to deploy VPN policies
- Windows-only support
Resources
Sophos has a series of tools to help you learn more about configuring IPsec and SSL VPN connections for secure remote access using your XG Firewall:
• XG Firewall: Useful links for configuring VPN remote access – Community article
• Using Sophos Connect VPN client – Community article
• XG Firewall: Sophos Connect client – Knowledge Base article
• Sophos Connect client – User Assistance article
• Sophos Connect VPN client – Video
• XG Firewall: How to deploy Sophos Connect via Group Policy Object (GPO) – Knowledge Base article
• XG Firewall: How to configure SSL VPN remote access – Knowledge Base article and video
• XG Firewall: Licensing guide – Knowledge Base article
• XG Firewall: Performance testing methodology – Knowledge Base article
Securing remote connections
With sensitive information travelling back and forth between the firewall and remote devices over the internet, ensuring the traffic is secured from threats is critical. If your XG Firewall has a TotalProtect Plus or FullGuard Plus license, traffic is scanned for ransomware, viruses, intrusions, and other threats in both directions, providing comprehensive protection.
Extend your protection with Synchronized Security
When your remote device has an active Sophos Intercept X license, it can share real-time threat, health and security information with XG Firewall via the Security Heartbeat ™. If a remote device becomes infected, XG Firewall isolates the device until it is cleaned, preventing the infection from moving laterally to other devices on the network.
Stay home, stay connected
Whatever reason your workforce is at home, you can help them stay connected with your XG Firewall. Check out the resources in this article, and for more information, speak with your local Sophos sales team. Stay tuned for enhancements to Connect client in an upcoming XG Firewall v18 maintenance release.
Following the continued spread of coronavirus (COVID-19) across the globe, we’d like to reassure our customers and partners that our ability to protect them is uncompromised. All departments, including threat intelligence, protection, and response from SophosLabs, Managed Threat Response, and Global Support Services are operating as normal to provide 24×7 detection, protection, and technical support. These business units already use a global follow-the-sun delivery strategy that allows Sophos to maintain continuity during the regular course of business and is continually improved as needed.
Sophos also has in place a robust set of technologies that enables the majority of our global employees to work from home. As a precautionary measure, and to help prevent the spread of coronavirus, we have advised employees in countries reporting a rising number of cases to work from home. We are fully enabled to continue day-to-day business, including product development and other important efforts, remotely.
We recognize that many other organizations are requiring employees to work from home and need secure connectivity. Customer information with tips on configuring VPN remote access with XG Firewall is available on our Sophos Community page. This article provides a quick and easy reference guide to getting started and more. We have also published practical security guidance for anyone enabling or exploring remote working.
Sophos is abiding by the ongoing and changing government guidelines and implementing a range of precautionary measures to help reduce the global spread of coronavirus (COVID-19) to protect the health and wellbeing of our employees, partners, and customers. These include restricting both international and domestic business travel for all employees, reducing participation in events, and switching in-person meetings to video conference.
We have established a cross-functional working group to stay coordinated on actions across our global operations, to support employee health and safety while minimizing disruption to our business. We continue to monitor this rapidly evolving situation and will update all our employees, partners, and customers with any changes.
We encourage everyone to maintain high cybersecurity vigilance at this difficult time. Cybercriminals are already exploiting coronavirus in their attacks and SophosLabs recently published new research into a Trickbot campaign that targets coronavirus fears in Italy. For quick updates to new findings about these types of attacks, please follow SophosLabs on Twitter.
Coronavirus has brought remote working to the top of everyone’s mind. With many organizations already enabling or exploring remote working, here are 11 tips to help your users, and your company, stay secure while protecting everyone’s physical health.
1. Make it easy for users to get started
Remote users may need to set up devices and connect to important services (Mail, Internal Services, SalesForce, etc.) without physically handing them over to the IT department. Look for products (security and otherwise) that offer a Self Service Portal (SSP) that allows users to do things themselves.
2. Ensure devices and systems are fully protected
Go back to basics – ensure all devices, operating systems and software applications are up to date with the latest patches and versions. All too often malware breaches an organization’s defenses via a rogue unpatched or unprotected device.
3. Encrypt devices wherever possible
When people are out of the office there is often a greater risk of lost or stolen devices; for example, phones left in cafes, laptops stolen from cars. Most devices include native encryption tools such as BitLocker – be sure to use them.
4. Create a secure connection back to the office
Using a Virtual Private Network (VPN) ensures that all the data transferred between the home user and the office network is encrypted and protected in transit. Plus, it makes it easier for employees to do their jobs.
5. Scan and secure email and establish healthy practice
Home working will likely lead to a big increase in email as people can no longer speak to colleagues in person. The crooks are wise to this and already using the coronavirus in phishing emails as a way to entice users to click on malicious links. Ensure your email protection is up-to-date and raise awareness of phishing.
6. Enable web filtering
Applying web filtering rules on devices will ensure that users can only access content appropriate for ‘work’ while protecting them from malicious websites.
7. Enable use of cloud storage for files and data
Cloud storage enables people to still access their data if their device fails while working remotely. Don’t leave files and data in the cloud unprotected and accessible by anyone. At the very least, employees must successfully authenticate. Multi factor authentication takes that a step further.
8. Manage use of removable storage and other peripherals
Working from home may increase the chance of people connecting insecure devices to their work computer – to copy data from a USB stick, or to charge another device. Considering that 14% of cyberthreats get in via USBs/external devices*, it’s a good idea to enable device control within your endpoint protection to manage this risk.
9. Control mobile devices
Mobile devices are susceptible to loss and theft. You need to be able to lock or wipe them should this happen. Implement application installation restrictions and a Unified Endpoint Management solution to manage and protect mobile devices.
10. Make sure people have a way to report security issues
With home working people can’t walk over to the IT team if they have an issue. Give people a quick and easy way to report security issues, such as an easy-to-remember email address.
11. Make sure you know about “Shadow IT” solutions
With large numbers of people working from home, Shadow IT – where non-IT staff find their own ways of solving issues – will likely increase. Sophos recently discovered ‘public’ Trello boards containing names, emails, dates of birth, ID numbers, and bank account information. Ensure users report use of such tools.
If you’d like more information we’re running a series of webinars on this topic in the coming weeks. Register for you spot today.
All roads lead to Rome, or at least that is what the proverb says, meaning no matter what route you take, you will always end up with the same result. Unfortunately, this isn’t something you can say for sensitive data. At Boldon James, we have spent the past twenty years working with defence and intelligence environments, and can report that often many roads exist, but only one of those is operational.
What am I referring to with this proverb? Well, it’s how we classify sensitive data. Applying a classification to an email message should be straight forward: mark it as ‘sensitive’, store as a piece of metadata on the email and send it. The email was probably the first type of electronic data to have a dedicated place to store a Classification. The 1988 X.400 standards included a ‘Security Label’, which was used by defence and intelligence systems for transmitting classified email messages (the phrase ‘Security Label’ is an X.400 term for what this blog will refer as the ‘Classification’).
You would imagine having only one location to look for the Classification made interoperability easy. However, the downside of X.400 was the strict binary encoding (ASN.1), meaning the recipient of an X.400 Security Label had to first understand the binary, and convert this into text for display to the end-user. If system ‘A’ used a different binary encoding to system ‘B’, the two systems couldn’t interoperate, and with neither system willing to alter their encoding, because of the legacy data they had stored, the solution resulted in complex gateways to convert between the two encoding formats.
We’ve largely left the X.400 world behind us, and moved into the SMTP world where everything is plain text, operates over the internet and is generally a lot easier than X.400. However, in the SMTP world, we don’t:
a) have a standard place to store a Classification or,
b) a standard format for the Classification.
Is this progress? Today, we’ve seen the Classification stored in the subject field, the first line of text in the email body, and a multitude of customised x-headers. Interoperability is generally achieved by adding additional Classifications onto the email. It’s not uncommon to find four or five variants of the Classification (in differing formats) on the email message; in which case, how do we know which one is the reference Classification? The more systems we have that label and share sensitive data, the more interoperability issues we will begin to see – as we realise that in fact not all roads leads to Rome.
In the defence world, NATO has been looking at data-centric security and written standards (STANAG 4774 and 4778) which defines a standard place and format for storing the Classification on an email message (and also to cryptographically bind that Classification to the email message). Boldon James is involved in prototyping these standards at various defence events; have we reached the time when the commercial world needs similar standards, allowing all roads return to Rome (or wherever your favourite City is!)?
Earlier this week the personal details of more than 10.6 million MGM Resort hotels guests were published on a hacking forum, the result of a cloud server data breach.
With this in mind, we take a look at some things you can do to avoid falling victim to a public cloud attack, including how Sophos can help you see and secure your data in the public cloud.
Know your responsibilities
Before anything else, you need to understand what you are responsible for when it comes to storing data in the public cloud.
Public cloud providers such as AWS, Azure, and Google offer customers a great deal of flexibility in how they build their cloud environments.
But the consequence of all this flexibility is that they can’t completely protect your virtual network, virtual machines, or data while in the cloud. Instead they run a Shared Responsibility model – they ensure security of the Cloud, while you are responsible for anything you place in the Cloud.
Aspects such as physical protection at the datacenter, virtual separation of customer data and environments – that’s all taken care of by the public cloud providers.
You might get some basic firewall type rules to govern access to your environment. But if you don’t properly configure them – for instance, if you leave ports open to the entire world – then that’s on you. So learn what you’re responsible for – and act on it.

Watch our shared responsibility video to learn more.
Five steps to minimize your risk of attack
Here are five essential steps you should take to minimize your risk of a cloud-based attack, and protect your data.
Step 1: Apply your on-premises security learnings
On-premises security is the result of decades of experience and research. When it comes to securing your cloud-based servers against infection and data loss, it’s a good idea to think about what you already do for your traditional infrastructure, and adapt it for the cloud:
Next-gen firewall
Stop threats from getting onto your cloud-based servers in the first place by putting a web application firewall (WAF) at your cloud gateway. Also look to include IPS (to help with compliance) and outbound content control to protect your servers/VDI.
Sophos XG Firewall protects your cloud and hybrid environments. And, with pre-configured virtual machines in Azure and AWS, you can be up and running quickly.
Server host protection
Run effective cybersecurity protection on your cloud-based servers, just as you would your physical servers.
Sophos Intercept X for Server protects your AWS and Azure workloads from the latest threats. Watch this video overview to see it in action.
Endpoint security and email protection
While your network may be in the cloud, your laptops and other devices are staying on the ground, and all it takes a phishing email or spyware to steal user credentials for you cloud accounts.
Ensure you keep endpoint and email security up to date on your devices to prevent unauthorized access to cloud accounts.
Step 2: Identify all your cloud assets
If you can’t see the data in the public cloud, you can’t secure it.
That’s why one of the most important factors in getting your cloud security posture right is getting accurate visibility of your infrastructure and how traffic flows through it. This will allow you to identify anomalies in traffic behavior – such as data exfiltration.
Step 3: Build a complete inventory
Build a complete inventory of your cloud estate, including server and database instances, storage services, databases, containers and serverless functions.
As well as looking at numbers of assets, also look for weak spots. Potential risk areas include:
- Databases with ports open to the public internet that could allow attackers to access them
- Cloud storage services set to public
- Virtual hard drive and Elastic Search domains set to public
Step 4: Regularly review identity access management
Actively manage user roles, permissions, and role-based access to cloud services. The scale and interwoven nature of individual and group access to services creates an enormous challenge, and attackers will exploit that gap in security.
Ensure you have visibility over all access types, and their relationships to cloud services to identify overprivileged access and review your policies accordingly. Afterall, if a hacker obtained these credentials, they could search far and wide across your cloud accounts for sensitive data.
Step 5: Actively monitor network traffic
Look for the telltale signs of a breach in your network traffic, with unusual traffic spikes a key indicator of data exfiltration.
The dynamic nature of the cloud means that traffic and assets are changing frequently, so humans generally struggle to track all these data points.
Instead use AI to harness these data sources and build a picture of what “normal” traffic is, then when activities occur outside “normal” you can be alerted instantly to unusual, and potentially malicious behavior.
Sophos Cloud Optix makes it easy for you to see all your cloud databases and workloads. It also enables you to identify potential vulnerabilities within your architecture so you can prevent a potential breach point.
Start an instant no-obligation online demo to see Cloud Optix in action for yourself.
As organizations move quickly to do their part in stopping the spread of COVID-19 people are working remotely more than ever before. At CyberArk we have taken action to protect the health and safety of our global community of customers, partners and employees – including having our employees across the globe work from home.
It’s not always easy for organizations to move to full remote work, especially having to balance productivity and security. Sudden, unexpected changes in the amount of work being done from home affects the workflows of remote users – especially those requiring privileged access – and most of the time, organizations don’t have the ability to properly scale. Additionally, attackers are working to capitalize on people’s fears and desire for information, which underscores the need to safeguard critical systems and assets.
Utilizing technology to overcome these challenges can help make these trying times a bit easier. Whether that’s making greater use of video chat and conference calling or allowing secure access to internal systems from anywhere, technology is helping business to continue with as little disruption as possible.
Recently we launched a new use case for CyberArk Alero to address the needs of all remote users (employees and vendors) by providing secure remote access to critical systems managed by CyberArk.
Starting today, we’ll be offering qualified customers the use of CyberArk Alero at no cost through the end of May in hopes that it will help ease some of the burden associated with the changing work environment. There are many ways that we, as individuals and as a company, are working to help our communities during this trying time. As business continuity plans are being tested, we hope to help organizations keep business running securely while putting the health and safety of all of us first.
Sophos Mobile Control Architect Training (2 days Training) – Tuesday, March 31st 2020 – Wednesday April 1st, 2020
Requirement
Have completed and passed the Sophos Mobile Certified Engineer course and any subsequent delta modules up to version 8.5
Recommended Knowledge
- Knowledge of how setup a Windows Active Directory environment with servers and workstations
- Experience of Windows networking and the ability to troubleshoot issues
- Understand the principles of DMZs, proxies and reverse proxies
- Experience using Microsoft SQL Server and Microsoft Exchange Server
- Experience with webservers or another web facing infrastructure
- Be familiar with iOS, Android and Window mobile devices
Content
- Module 1: Solution Overview & Architecture
- Module 2: Installation
- Module 3: Configuration & Management
- Module 4: Containers
- Module 5: Sophos Mobile Security
- Module 6: EAS Proxy
- Module 7: Network Access Control
- Module 8: Server Maintenance
Certification
To become a Sophos Certified Architect, trainees must take and pass an online assessment. The assessment tests their knowledge of both the presented and practical content. The pass mark for the assessment is 80%, and is limited to 3 attempts
Duration 2 days
Lab Environment
Each student will be provided with a pre-configured environment which simulates a company network with two sites, a head office and a branch office and contains Windows Servers, a Windows Desktop and three XG Firewalls

Agenda
Trainer: Micheal Eleftheroglou
Day 1 Tuesday 31 March 2020
9:30-10:30 Module 1: Solution Overview & Architecture
- Review Sophos Mobile knowledge from the Engineer course
- Explore the architecture of Sophos Mobile and deployment options
- Understand communication protocols, clustering and sizing the solution
10:30-10:45 break
10:45-11:45 Module 2: Installation
- Understand the supported devices, servers and database versions for Sophos Mobile
- Understand the installation process
- Understand the installation pre-requisites and tools used to ensure these are met
- Configure an External Directory
- Configure post-installation settings
- Understand cluster configuration and user roles
- Explain the migration tool and troubleshooting steps during installation.
11:45-13:15 Lab 1 Installation
- Prepare the Sophos Mobile Server
- Create an SSL certificate using the Sophos Mobile SSL Certificate Wizard
- Install Sophos Mobile using an existing database and PKCS12 certificate file
- Create and install an APNs certificate
- Configure the internal EAS proxy
- Install the CA Certificate (for iOS devices only)
13:15-14:15 Lunch
14:15-16:15 Module 3: Configuration & Management
- Configure Super Admin settings and customer settings
- Understand configuration inheritance
- Configure SCEP and troubleshoot common issues
- Configure mobile devices
- Understand Device Profiles, Apple VPP, Apple DEP, Android for Work & Device Owner
- Configure Task Bundles and Device groups
- Configure the Self Service Portal
- Configure compliance policies
- Understand how to remove a device from Sophos Mobile
- Troubleshooting common issues
16:15-16:30 Break
16:30-17:30 Lab 2: Configuration & Management
- Configure Super Admin level settings
- Configure inheritance and view assigned configuration
- Create a customer and configure customer level settings
- Enroll a mobile device (Android or iOS)

Day 2 Wednesday 1 April 2020
9:30-10:00 Module 4: Containers
- Explain what Container-only Management is
- Describe which components are included in the Sophos Container
- Explain how document encryption works with Secure Workspace
- Describe the possible compliance actions available
- Explain Samsung KNOX
10:00-10:30 Lab 3: Sophos Container
- Manage documents in Sophos Mobile
- Create an encrypted file using the SafeGuard client
- Configure and test a Sophos Container Policy (Android and iOS)
10:30-10:45 Break
10:45-11:15 Module 5 Sophos Mobile Security
- Explain what Sophos Mobile Security is
- Describe how App Reputation works
- Understand how to manage Sophos Mobile Security
- Troubleshoot common issues
11:15-11:30 Lab 4: Sophos Mobile Security
- Configure a Sophos Mobile Security policy
- Test the Sophos Mobile Security policy (Android only)
11:30-12:00 Module 6: EAS Proxy
- Describe what EAS Proxy is used for
- Review use of EAS Proxy with Lotus Notes Traveler and O365 support
- Understand the deployment scenarios for EAS Proxy
- Explain clustering and certificate base authentication
- Work through an installation of EAS Proxy
- Troubleshoot common issues and understand the log files generated
12:00-12:20 Lab 5: EAS Proxy
- Install an External EAS Proxy
- Configure the UTM as a reverse proxy for the External EAS proxy
- Update the EAS settings to use the External EAS proxy (Android or iOS)
- Review the external EAS proxy log file
12:20-12:50 Module 7: Network Access Control
- Explain how NAC works
- Configuration NAC
- Describe device compliance options with NAC enabled
- Troubleshoot common issues and understand the log files generated
12:50-13:20 Lab 6: Network Access Control
- Enable Network Access Control
- Test Network Access Control (Android or iOS)
- Unenroll your device
- Remove lab configuration
13:20-14:20 Break – Lunch
14:20-15:00 Module 8:Server Maintenance
- Explain the daily maintenance schedule
- Describe when and how to update Sophos Mobile
- Understand what steps to take if changes are made to your environment
- Understand the deployment scenarios for Sophos Mobile
15:00-15:15 Lab 7: Cluster Configuration Simulation
- Complete the simulation
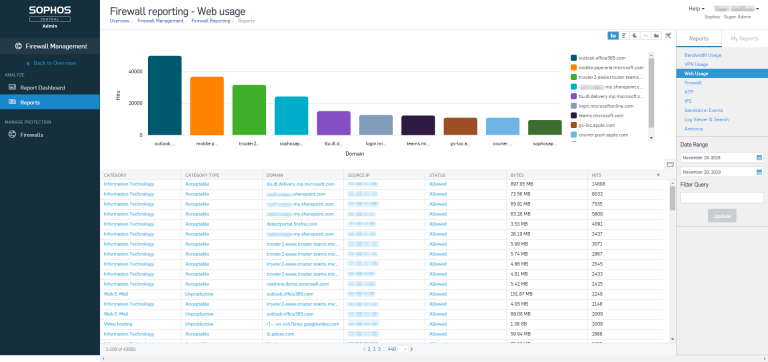
XG Firewall v18 is here, and with it comes a slew of terrific new features that address the visibility, protection, and performance problems organizations face every day.
One of the more exciting enhancements in v18 adds is Central Firewall Reporting (CFR), Sophos’ new cloud-based reporting tool.
Sophos CFR enables customers to create historical reports on network activity with a great deal of customization. It’s extremely flexible, and it’s included for free on any XG Firewall capable of running the v18 firmware.
Greater insight through analytics
If you are in any way responsible for your organization’s network, here’s a simple question to ask yourself:
Do I have a good understanding of the user activities, applications, network events, risks, and performance in our security environment?
If you don’t or the solution you’re using only scratches the surface, a reporting tool that provides deeper insight in these areas could be just what you need. Armed with deeper analytics, you can implement policy changes to drive efficiencies that enhance productivity while also protecting against cyber threats.
Flexible, customizable reporting
Creating reports on the topics that are important to you should be easy, and with CFR it is.
An integral component of Sophos Central, Central Firewall Reporting provides organizations with a flexible set of options to capture network activity through your Sophos Central account and XG Firewall.
Using the interactive dashboard, you can drill down into the syslog data for a granular view that is presented in a visual format for easy understanding. The data can then be analyzed for trends that could lead to gaps in security, requiring policy changes.
Key features in Central Firewall Reporting
With Central Firewall Reporting, you can create reports to fit your needs using one of the pre-defined report templates and customizing it the way you want. Here are some of the key features:
- Up to seven days of historical reporting
- Rich, granular data organized into easy-to-understand reports
- Pre-defined, out-of-the-box report templates
- Flexible report table and charts allow you to customize each report
- Report Dashboard provides an at-a-glance view from the XG Firewall for network operational health, policy control events, and all security-driven events
- Visual representation of data displayed in graphical form
- Search and retrieval of all log data from the XG Firewall
What’s next for CFR?
Because Central Firewall Reporting is cloud-based, we’ll roll out additional features and report templates without requiring any firmware update to your XG Firewall. Even bigger, however, is a new reporting service with more features and built-in reports.
Complementing the free version of Central Firewall Reporting, CFR Premium is a “for pay” service that unlocks more capabilities and built-in report templates along with historical reporting up to one year.
CFR Premium is designed for organizations with more connected devices that generate larger amounts of syslog data and want the flexibility to add storage capacity as needed. Look out for the launch in the coming months.
In the meantime, try out the free version to see the types of custom reports you can create and the insights you’ll get into network activity. For more information, see the CFR web page on our website.
XG Firewall v18 is now available, and it’s sporting the all-new Xstream Architecture, which delivers extreme levels of visibility, protection and performance.
We’ve packed this release with new and enhanced features for you, including:
- Xstream SSL inspection. Get unprecedented visibility into your encrypted traffic flows, support for TLS 1.3 without downgrading, powerful policy tools, and supreme performance.
- AI-powered threat intelligence. Extend your protection against zero-day threats and emerging ransomware variants with multiple best-in-class machine learning models and unmatched insights into suspicious files entering your network.
- Application acceleration. Optimize network performance by putting your important application traffic on the fast path through the firewall and routing it reliably out through your preferred WAN connection.
Watch the overview video to see everything that’s new in XG Firewall v18:
Sophos Central
XG Firewall v18 also includes support for all new central management, reporting, and deployment options launching on Sophos Central next week:
- Group firewall management. Easily keep your full estate of firewalls consistent using groups that automatically keep policies, objects, and settings synchronized.
- Central reporting. Network activity and insights across all your firewalls are now at your fingertips in Sophos Central, with several pre-packaged reports and flexible reporting tools to create your own.
- Zero-touch deployment. Conveniently setup a new firewall in Sophos Central, export the config, load it on a flash drive and have your new firewall automatically connect back to Sophos Central without having to touch it.
And, there’s more!
In addition, there are also a ton of other new features that will enhance your protection, visibility, management experience, and network versatility:
- Synchronized SD-WAN brings the power of Synchronized Security to reliably and accurately route application and user-based traffic over your preferred WAN links
- Firewall, NAT, and SSL Inspection rules and policies are now more powerful, flexible and easier to work with than ever before
- Plug-and-play high-availability (HA) makes it easy to enable business continuity and adds peace-of-mind – simply connect two XG Series appliances together and you’ll be up and running in no time
- Real-time flow monitoring provides at-a-glance insights into active bandwidth consuming hosts, applications, and users
- Expanded notifications and alerts ensure you never miss an important network security event whether it’s related to a threat, service, or important performance metric
How to get XG Firewall v18
As usual, this firmware update comes at no charge for licensed XG Firewall customers. The firmware will be rolled-out automatically to all systems over the coming weeks, but you can manually update at any time via MySophos.
Head on over to the XG Firewall Community Blog to get the full release notes.
Also check that your current hardware appliance supports v18.
Making the most of your new XG Firewall features
Free online training – available to all XG Firewall customers, our delta training program will help you make the most of the new features in XG Firewall v18.
It walks you through the key enhancements since v17.5 and takes about 90 minutes to complete. Get started on the XG Firewall training program.
Customer resources and how-to videos – be sure to visit the Customer Resource Center for the latest how-to videos and links to documentation, the community forums, training and other resources.
Take advantage of Partner and Sophos Professional Services: To augment your local Sophos partner’s services, we offer services to help you getting up and running and make the most of your XG Firewall, including the latest capabilities in v18.
While Sophos Professional Services can help with any task, here are the most common services they provide:
- XG Firewall deployment and setup
- XG Firewall v18 DPI, FastPath and SSL Engine Optimization
- XG Firewall Health Checks
Here are some direct links to helpful resources:
- Customer Training Portal (free Delta Training)
- Customer Resource Center (with how-to videos)
- Community Forum Recommended Reads
- What’s New and Release Notes
- XG Firewall v18 Complete Documentation
New to XG Firewall?
If you’re new to XG Firewall, see how it provides the world’s best network visibility, protection and response on the new XG Firewall website.
We have all seen films where the defences of a medieval castle prevent the attackers from gaining entry – the deep moat, unscalable walls and impenetrable portcullis. From within the castle, the firing of arrows, canons and boiling oil poured onto the attackers all help protect the castle residents inside.
In many ways, a lot of the commercial, defence and intelligence organisations have treated their IT networks in the same way – protect the perimeter, and your information inside will remain safe. Unfortunately, today this isn’t the case; the perimeter protecting your information is widening. With the boom of Cloud services, an increasingly mobile workforce and the need to share information, the protection of the perimeter becomes even more difficult when we’re unsure exactly where the perimeter is, and the more opening doors we place in our perimeter, the harder it becomes to protect.
We still need to protect the perimeter using our existing network-centric security tools, but also need to protect the information we store inside our network. An information-centric approach uses classification and encryption to protect the information wherever it moves, placing less importance on where your information resides.
Classification of your information at the point of creation is key to the success of information-centric security; this is very familiar to the defence and intelligence communities but may require an important mindset change to some commercial organisations. Once your information is correctly classified, you begin to understand the sensitivity of your information, and can treat it accordingly – a document containing project plans is more sensitive than a document with today’s restaurant menu, for example.
Metadata is the usual method for storing the classification with your information, but for protection of your information, the classification must be cryptographically bound to your information (this prevents your sensitive document becoming insensitive). Also, to facilitate information sharing, the metadata cannot be bespoke to your organisation; otherwise sharing information is made more difficult with unreadable classification metadata.
With the information classified and protected using a common format, the organisation can now begin to apply access control policies to control the flow of information throughout the entire network. Who needs access to the information, the location of the user, the type of device they are using are all factors that may affect whether a user has access to the sensitive project plan document.
The ability to control the sharing of information is made easier with information-centric security. Ongoing, rights management technology can be applied (using an open standard) to control access to the information after it was shared, as we may only want to share sensitive information externally for a limited time.
Data is the building blocks for information, and it is information we use in our everyday lives. By adopting an information-centric security approach, we can begin to control, protect and monitor our data wherever it resides.
This three-day training program was designed and intended for experienced technical professionals who want to install, configure and support the XG Firewall in production environments and is the result of an in-depth study on the next generation firewall of Sophos. The program consists of presentations and practical workshops for the enhancement of teaching content. Due to the nature of the traditions and the varied experience of the trainees, open discussion is encouraged during the training.
(3 days Training)
Tuesday 17 March 2020– Thursday 19 March 2020
Requirement
XG Firewall _ Certified Engineer course and delta modules up to version 18.0
Recommended Knowledge
Knowledge of networking to a CompTIA N+ level
Knowledge of IT security to a CompTIA S+ level
Experience configuring network security devices
Be able to troubleshoot and resolve issues in Windows networked environments
Experience configuring and administering Linux/UNIX systems
Content
Module 1: Deployment
Module 2: Base Firewall
Module 3: Network Protection
Module 4: Synchronized security
Module 5: Web server Protection
Module 6: Site to site connections
Module 7: Authentications
Module 8: Web Protection
Module 9: Wireless
Module 10: Remote Access
Module 11: High Availability
Module 12: Public Cloud
Certification
+ exam: Sophos XG Architect
Duration: 3 Days
Agenta
Trainer: Micheal Eleftheroglou
Day 1 Tuesday 17th March 2020
9:30-10:45 Module 1: Module 1: Deployment and Lab
- Recall important information from Engineer courses
- Deployment modes supported by the XG Firewall
- Understand a range of scenarios where each deployment mode would commonly be used
- Use built-in tools to troubleshoot issues
- Labs
10:45-11:00 Break
11:00-13:00 Module 2: Base Firewall
- Explain how the XG firewal can be accessed
- Understand the types fo interfaces that can be created
- Understand the benefits of Fast Path Technology
- Configure routing per firewall rule
- Understand best practice for ordering firewall rules
- Explain what Local NAT policy is and known how to configure it.
13:00-14:00 Break
14:00-16:00 Base Firewall
- Activate the Sophos XG Firewalls
- Post installation Configuration
- Bridge interfaces
- Create a NAT rule to load balance access to servers
- Create a local NAT policy
- Configure routing using multiple WAN links
- Configure policy-based routing for an MPLS scenario
- Install Sophos Central
16:00-16:15 Break
16:15-17:15 Module 3: Network Protection and Lab
- Explain what IPS is and how traffic can be offloaded to Fastpath
- Demonstrate how to optimize workload y configuring IPS policies
- Examine advanced Intrusion Prevention and optimize policies
- Configure advanced DOS Protection rules
- Demonstrate how the strict policy can be used to protect networks
- Labs- Create Advanced DoS Rules
Day 2 Wednesday 18th March 2020
9:30-11:00: Module 4: Synchronized Security and Labs
- Explain how Security Heartbeat works
- Configure Synchronized Security
- Deploy Synchronized Security in discover and inline modes
- Understand the advantages and disadvantages of deploying
- Synchronizes Security in different scenarios
- Labs
- Configure source-Based Security
- Hearteat firewall rules
- Destination based Security Heartbeat
- Missing Security Heartbeat
- Lateral Movement Protection
11:00-11:15 Break
11:15-13:45 Module 5 Webserver Protection and Labs
- Explain how Websever Protection works
- Describe protection features for a web application
- Configure Web Server authentication
- Publish a web service using the Web Application Firewall
- Use the preconfigured templates to configure Web Server Protection for common purposes
- Configure SlowHTTP protection
- Labs (Web Application Firewall)
- Labs (Load balancing with Web Server Protection)
- Labs (Web Server Authentication and path-specific routing)
13:45-14:45 Break and Launch
14:45-17:45 Module 5: Red Management
- Configure and deploy site to site VPNs in a wide range of environment
- Implement IPsec NATing and failover
- Check and modify route precedence
- Create RED tunnels between XG firewalls
- Understand when to use RED
- Labs ( Create an IPsec site to site VPN
- Labs ( Configure VPN network NATing )
- Labs (Configure VPN failover)
- Labs (Enable RED on the XG firewall)
- Labs (Create a RED tunnel between two XG Firewalls
- Labs (Configure routing for the RED tunnel)
- Labs (Configure route-based VPN)
Day 3 Thursday 19th March 2020
9:00-10:00 Module 7: Authentications and Labs
- Demonstrate how to configure and use RADIUS accounting
- Deploy STAS in large and complex environment
- Configure SATC and STAS together
- Configure Secure LDAP and identify the different secure connections available
- Labs (configure an Active Directory Authentication server)
- Labs (configure single sing-on using STAS
- Labs (Authenticate users over a site to site VPN)
10:00-11:15 Module 8: Web Protection
- Choose the most appropriate type for web protection in different deployment scenarios
- Enable web filtering using the DPI engine or legacy web proxy
- Configure TLS inspection using the DLP engine or legacy web proxy
- Labs (Install the SSL CA certificate)
- Labs (Configure TLS inspection rules)
- Labs (Create a custom web policy for users)
11:15-11:30 Break
11:30-12:15 Module 9: Wireless
- Explain how Sophos Access Points are deployed and identify some common issues
- Configure RADIUS authentication
- Configure a mesh network
12:15-13:05 Module 10: Remote Access
- Configure Sophos Connect and manage the configuration using Sophos Connect Admin
- Configure an IPsec remote access VPN
- Configure an L2TP remote access VPN for mobile devices
- Labs (Sophos Connect)
13:05-14:25 Module 11: High Availability
- Explain what HA is and how it operates
- Demonstrate how to configure HA and explain the difference between quick and manual configuration
- List the prerequisites for high availability
- Perform troubleshooting steps andc heck the logs to ensure that HA is set up correctly.
- Explain the packet flow in high availability
- Demonstrate how to disable HA
- Labs (Create an Active-Passive cluster)
- Labs (Disable High Availability)
14:25-15:05 Break and Launch
15:05-16-15 Public Cloud and Labs
- Deploy XG firewall in complex network enviroments
- Explain how XG firewall process traffic and use this information to inform the configuration
- Configure advanced networking and protection features
- Deploy XG firewall on public cloud infrastructure
- Labs (Put a service in debug mode to gather logs)
- Labs (Retrieving log files)
- Labs (Troubleshoot an issue from an imported configuration file)
- Labs (Deploy an XG Firewall on Azure (simulation)
16:15 (Exams)
Η νέα αρχιτεκτονική Xstream στο XG Firewall v18 περιλαμβάνει μια ολοκαίνουργια, υψηλής απόδοσης λύση επιθεώρησης SSL που προσφέρει την καλύτερη ορατότητα της βιομηχανίας σε κρυπτογραφημένες ροές κίνησης (δεδομένων), υποστήριξη για TLS 1.3 χωρίς υποβάθμιση και ιδιαίτερα υψηλά επίπεδα απόδοσης.
Με τον όγκο της κρυπτογραφημένης κίνησης να βρίσκεται τώρα κοντά στο 80% και να αυξάνεται σταθερά, η επιθεώρηση SSL αποτελεί κορυφαίο ζήτημα για πολλούς οργανισμούς. Και με το δίκιο τους.
Αυτός ο όγκος κρυπτογράφησης όχι μόνο δημιουργεί ένα τεράστιο τυφλό σημείο, που οι χάκερς εκμεταλλεύονται, αλλά έχει ωθήσει και τα περισσότερα τείχη προστασίας σε σημεία πέρα από τις δυνατότητες τους. Πολλοί οργανισμοί είναι ανίκανοι να κάνουν πολλά για το πρόβλημα με αποτελέσμα τα firewalls τους ουσιαστικά καθίστανται ξεπερασμένα.
Η νέα αρχιτεκτονική Xstream του XG Firewall παρόλα αυτά έχει σχεδιαστεί για το σύγχρονο κρυπτογραφημένο διαδίκτυο.
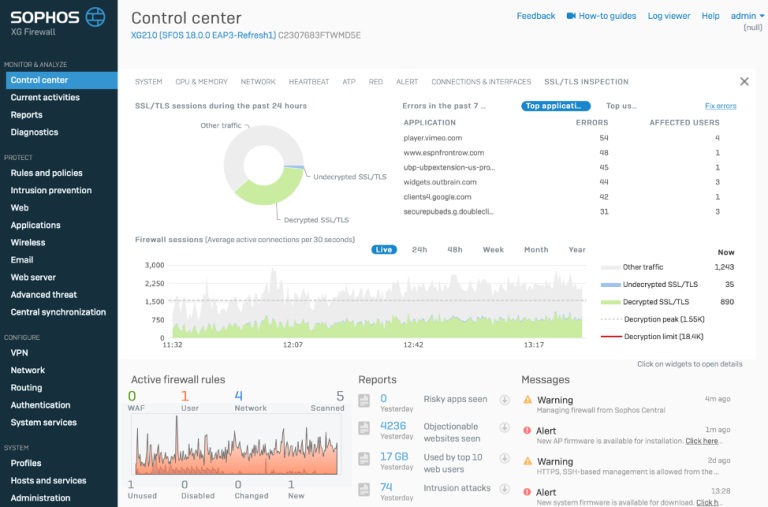
Εξαιρετική ορατότητα σε κρυπτογραφημένες ροές κίνησης
Το XG Firewall είναι μοναδικό στην παροχή ορατότητας πρωτοφανούς επιπέδου στις κρυπτογραφημένες ροές κίνησης. Μόλις συνδεθείτε, μπορείτε με μια ματιά να έχετε εικόνα για τον όγκο κρυπτογραφημένης κίνησης στο δίκτυό σας, να βλέπετε πόση από αυτή αποκρυπτογραφείται ενεργά αλλά και αν υπάρχουν προβλήματα συμβατότητας.
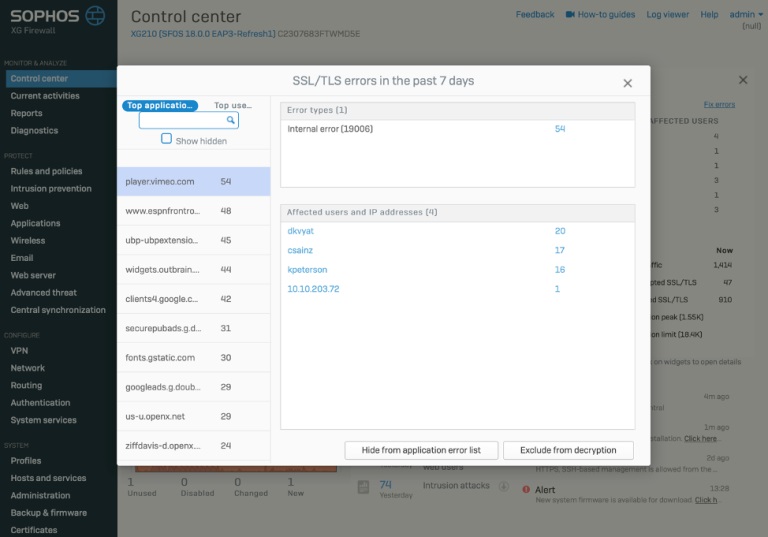
Με μερικά μόνο κλικ επίσης είστε σε θέση να επιλύσετε τυχόν πιθανά ζητήματα για να εξασφαλίσετε μια εξαιρετική εμπειρία χρήσης.
Εξαιρετική εστίαση στην ασφάλεια και υποστήριξη για TLS 1.3 (χωρίς υποβάθμιση)
Οι περισσότεροι προμηθευτές τειχών προστασίας και UTM θα ισχυριστούν ότι παρέχουν υποστήριξη TLS 1.3 ωστόσο στην πραγματικότητα υποβαθμίζουν τις κρυπτογραφημένες συνεδρίες σε TLS 1.2. Το XG Firewall σχεδιάστηκε για να αναλάβει τις απαιτήσεις του σύγχρονου κρυπτογραφημένου διαδικτύου με πλήρη υποστήριξη του προτύπου TLS 1.3.
Το TLS 1.3 είναι το πιο πρόσφατο πρότυπο για όλους τους καλούς λόγους. Έτσι, επιλύει σημαντικά ζητήματα ασφάλειας και απόδοσης που υπάρχουν με το TLS 1.2. Η υποβάθμιση (downgrading) δημιουργεί ένα άνοιγμα για επιθέσεις και ρίχνει την απόδοση.
Με την υποστήριξη του TLS 1.3 να αυξάνει διαρκώς μεταξύ των μεγάλων web servers και των οργανισμών hosting, κανείς δεν πρέπει να εξετάσει την αγορά ενός τείχους προστασίας σήμερα χωρίς κατάλληλη υποστήριξη για το πρότυπο TLS 1.3.
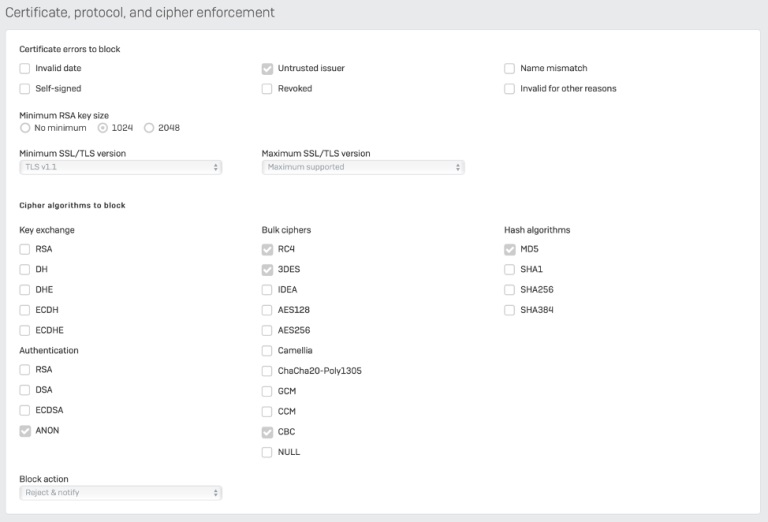
Το XG Firewall προσφέρει επιπλέον -μεταξύ άλλων- τα καλύτερα controls στην βιομηχανία για την διαχείριση μη ασφαλών και παλαιότερων σουιτών κρυπτογράφησης (cipher) χάρη στις ολοκληρωμένες επιλογές που διαθέτει ως μέρος των νέων προφίλ αποκρυπτογράφησης (Decryption Profiles) που μπορούν να χρησιμοποιηθούν στους κανόνες επιθεώρησης TLS.
Έχετε πλήρη επιχειρησιακού επιπέδου controls για να επιτύχετε την τέλεια ισορροπία μεταξύ ασφάλειας, ιδιωτικότητας, απόδοσης και συμμόρφωσης για τον οργανισμό και την επιχείρηση σας.
Εκπληκτική απόδοση
Η νέα αρχιτεκτονική Xstream στο XG Firewall v18 προσφέρει εξαιρετική απόδοση σε όλες τις λειτουργίες του τείχους προστασίας, συμπεριλαμβανομένης και της επιθεώρησης SSL.
Η νέα αρχιτεκτονική επεξεργασίας πακέτων συμπεριλαμβάνει μία ολοκαίνουργια μηχανή συνεχούς ροής βαθιάς επιθεώρησης πακέτων, που όχι μόνο παρέχει αποκρυπτογράφηση SSL υψηλής απόδοσης αλλά και hands-off αποκρυπτογράφηση περιεχομένου για IPS, προστασία ιστού, AV (antivirus), αναγνώριση και έλεγχο εφαρμογών και όλα τα παραπάνω από μία μοναδική μηχανή.
Χρησιμοποιώντας τα πλέον σύγχρονα μοντέλα μηχανικής εκμάθησης, η νέα υπηρεσία πληροφοριών απειλών (threat intelligence) αναλύει επίσης τα εισερχόμενα αρχεία με ενεργό κώδικα σε πραγματικό χρόνο, για να εντοπίσει απειλές που είναι άγνωστες και δεν έχουν ακόμα παρατηρηθεί, ώστε να διατηρεί τα τελευταία φορτία ransomware και άλλες απειλές εκτός του εταιρικού δικτύου σας.
Με το νέο χαρακτηριστικό Xstream SSL Inspection στο XG Firewall v18, τα κρυπτογραφημένα αρχεία δεν μπορούν πλέον να «κρύβουν» απειλές που ενδέχεται να περάσουν απαρατήρητες από το τείχος προστασίας του δικτύου σας.
Που να μάθετε περισσότερα
Για περισσότερες πληροφορίες σχετικά με τις προκλήσεις που αντιμετωπίζουν τα περισσότερα τείχη προστασίας όσον αφορά στην σωστή επιθεώρηση της κρυπτογραφημένης κίνησης TLS, το τεράστιο τυφλό σημείο που αυτό δημιουργεί και για το πώς οι χάκερ χρησιμοποιούν όλο και περισσότερο την κρυπτογράφηση προς όφελός τους, μπορείτε να διαβάσετε την πιο πρόσφατη αναφορά της Sophos: Έχει η κρυπτογράφηση καταστήσει το υφιστάμενο τείχος προστασίας σας ασήμαντο;
Αν δεν γνωρίζετε το XG Firewall, ρίξτε μία ματιά σε όλα τα άλλα πλεονεκτήματα που παρέχει όσον αφορά στην ορατότητα, στην προστασία και στην απόδοση του δικτύου σας και ξεκινήσετε άμεσα με ένα online demo.
CRN, a brand of The Channel Company, recently unveiled its 100 Coolest Cloud Companies of 2020, and Sophos has made the list as a top cloud security vendor.
We were selected for our innovation in product development, the quality of our services and partner programs, and our success in helping customers save money and maximize the impact of their cloud computing technology.
We were also recognized for enabling organizations to manage a multi-layered security strategy across the office, data center and cloud from a single console, Sophos Central.
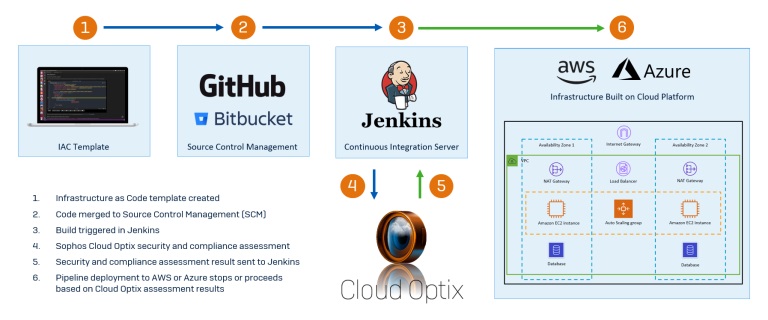
With our cloud tools you can protect AWS, Azure, GCP, Kubernetes and infrastructure as code environments from the latest malware, ransomware and vulnerabilities.
We provide next-gen server workload protection, virtual firewall series and Sophos Cloud Optix, a powerful tool that automates and simplifies the detection and response of cloud security vulnerabilities and misconfigurations to reduce risk exposure.
Among the many differentiators offered by our public cloud security suite is the AI at the heart of Cloud Optix. Instead of inundating teams with massive numbers of undifferentiated alerts, Cloud Optix uses AI to significantly reduce alert fatigue and shrink incident response and resolution times.
It does this by identifying the risk profiling security and compliance risks, with contextual alerts that group affected resources, and providing detailed remediation steps, including direct links to the cloud provider’s console. This ensures teams focus on and fix their most critical security vulnerabilities fast.
In addition, Cloud Optix makes software development fast and secure with API-driven architecture that seamlessly integrates with existing DevOps tools and processes.
It analyzes infrastructure as code templates at any stage of the development pipeline automatically or on-demand, and ensures templates do not introduce vulnerabilities that could be exploited in a cyberattack. This proactive approach helps organizations meet security and compliance standards.
Bob Skelley, CEO of The Channel Company, said of the awards:
“The IT channel relies on cloud services as the foundation for building modern, transformational solutions. CRN’s annual list of 100 Coolest Cloud Companies seeks to honor the top cloud providers, whose mission and actions support innovation in cloud-based technologies. Our team congratulates these honorees and thanks them for their commitment to leading positive change in cloud technology”.
Receiving praise from trusted third parties in cloud security isn’t new for us though. Cloud Computing magazine recently announced us as a winner of the 2019 Cloud Computing Security Excellence Award, and honoured Cloud Optix in two categories: those that most effectively leverage cloud platforms to deliver network security, and those providing security for cloud applications.
We give away free software so you can always stay safe. Check for security risks, remove viruses and protect your network. Try out our free tools below.

Sophos Home for PCs and Macs
Protect all the computers in your home with the free Sophos Home. The same antivirus, malware protection, and web filtering technology trusted by hundreds of thousands of businesses is now yours to take home.
- Stop malware, viruses, ransomware, and malicious apps
- Block unwanted web content, phishing attacks
- Easily manage remote computers from virtually anywhere
- Works on both Windows PCs and Macs
Download
Intercept X for Mobile

Device
Intercept X for Mobile continuously monitors for and alerts users and IT administrators to signs of potential compromise so they can rapidly remediate issues and automatically revoke access to corporate resources. Compliance checks detect jailbreaking, rooting, encryption status, and more, informing users and IT administrators of necessary operating system updates. Device health check recommendations further guide security settings.
Network
Intercept X for Mobile monitors network connections for suspicious activity in real time, warning users and IT administrators of potential Man-in-the-Middle (MitM) attacks. Web filtering and URL checking also stop access to known bad sites, and SMS phishing detection spots malicious URLs.
Apps
Intercept X for Mobile detects malicious and potentially unwanted applications installed on devices, protecting against malware, ransomware and fleeceware.
Download Google Play | Apple App Store

HitmanPro – Malware Removal Tool
Our malware removal tool for Windows scans your entire computer for any issues, and if anything is found, you’ll have a free 30-day license to remove the threat. Don’t wait until you get infected, you can run it anytime to see how well your current antivirus or endpoint protection software is performing.
- Removes viruses, Trojans, rootkits, spyware, and other malware
- No setup or install needed
- Free second opinion scanner tells you what was missed
Download Business | Home
Sophos XG Firewall Home Edition

Give your home network a much needed security boost. The Home Edition of the Sophos XG Firewall features full protection for your home network, including anti-malware, web security and URL filtering, application control, IPS, traffic shaping, VPN, reporting and monitoring, and much more.
- Full protection for your home users and your home network
- Integrated, hardened Linux operating system
- Runs on Intel-compatible hardware
Download

Virus Removal Tool
Our free Virus Removal Tool is a quick and easy way to find and get rid of any threats lurking on your computer. Our tool identifies and cleans up infections your antivirus might have missed.
- Removes viruses, Conficker, rootkits, and fake antivirus
- Supports Windows XP SP2 and up
- Works alongside your existing antivirus
Download
Sophos UTM Home Edition

This software version of the Sophos UTM Firewall features full network, web, mail and web application security, with VPN functionality, for as many as 50 IP addresses. The Sophos UTM Home Edition contains its own operating system and overwrites all data on the computer during the installation process. Therefore, a separate, dedicated computer is needed.
- Fully-equipped software version of the Sophos UTM appliance
- Full web application security with VPN
- Protects up to 50 IP addresses
Download

Sophos Antivirus for Linux Free Edition
Protect your mission critical Linux servers and stops all threats—even those designed for Windows. We keep our antivirus light and easy, so your Linux servers can remain lighting fast. It works quietly in the background with your choice of scanning on-access, on-demand or on a schedule.
- Finds and blocks malware
- Installs easily and runs quietly
- Supports the most popular Linux distributions
- Upgradeable for support and centralized management
Download
Phishing emails impersonating well-known brands and VIPs within an organization are a big problem for security teams to deal with. So, we’re excited to announce that you’ll now be able to detect and block these impersonation attacks with Sophos Email Advanced.
Email impersonation phishing attacks in action
In our latest study, we found that five out of ten organizations view malicious emails as their top security concern, with 53% experiencing a phishing attack in the past twelve months.
Impersonation attacks are often the hardest to combat, and usually with no malicious payload to detect. In these attacks, criminals regularly try to deceive employees, using the name of a trusted sender to encourage victims to reply, click a link, open an attachment, and so on.
Relying on users to merely scan email sender addresses, these attacks use simple display name forgery to change the visible part of the email address that we see in many common email clients.
Changing the display name to that of a trusted brand or a senior executive within the organization is a simple but effective technique for attackers.
These attacks reign down from free email accounts, and in more targeted attacks, are known to use lookalike domain names, like that of the corporate domain.
The latest highlights
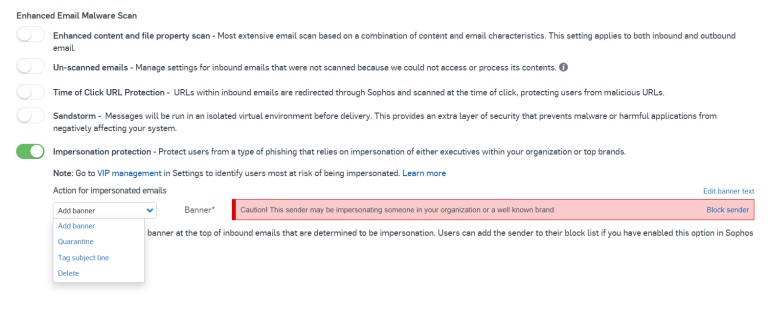
The most recent enhancement for Sophos Email Advanced offers crucial protection against these impersonation phishing attacks as well as several great advancements:
- Compares the display name of inbound emails to the display name of commonly abused cloud service brand names and to VIPs within the customers organization to check for matches. These could be the CEO, CFO, and HR Director, etc.
- Provides a simple wizard to identify and add VIPs within the organization to your policy for analysis with all inbound messages.
- Compares header information, analyzing the display name in relation to the full email address and domain name used, to identify free email domains, lookalike domains of popular cloud services such as Microsoft, Amazon, and VIP name impersonation attempts.
Identifying VIPs
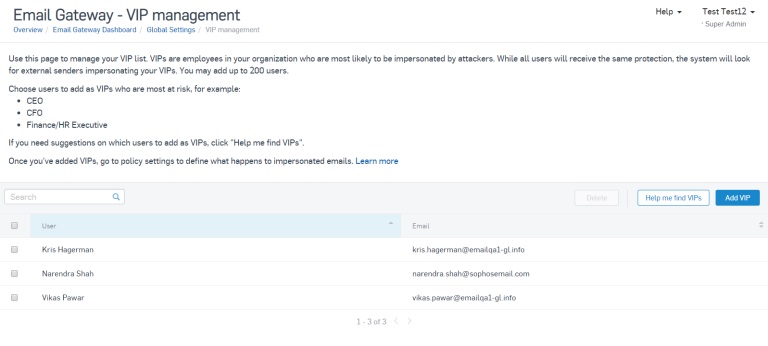
VIPs are employees in the organization who are most likely to be impersonated by phishing attackers.
While all users will receive the same protection, the system will look for external senders impersonating your VIPs, and you can add up to 200 VIPs to the list.
Creating a VIP list in Sophos Central couldn’t be simpler. You can choose to “Add VIPs” by searching your user list for known individuals.
Alternatively, if active directory synchronization has been enabled, select “Help me find VIPs” and Sophos Email will look for users with titles that are in line with job roles most likely to be impersonated:
- CEO
- President
- Chief Financial Officer
- CFO
- Finance Director
- Human Resources Director
- HR Director
Acting on the threat
This new service allows email administrators to act on potential threats with policy controls to quarantine suspicious messages, tag the subject line, delete them or warn users with a banner added to inbound emails.
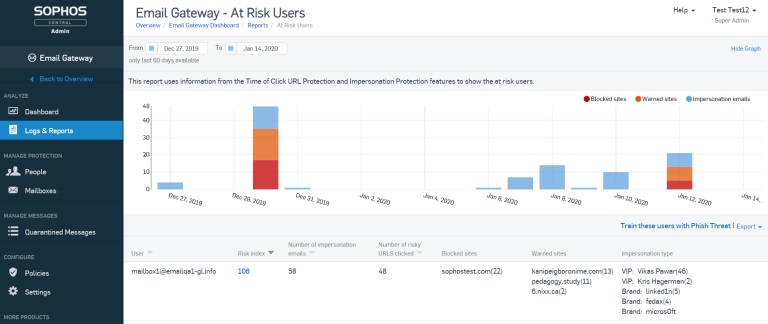
The enhanced “At Risk Users” report gives a deeper level of visibility into these phishing threats. It provides a breakdown of phishing impersonation attempts received, as well as any users who have either been warned or blocked from visiting URLs with malicious content. Drill-down levels provide further insight, including:
- Number of impersonation emails received by user allows you to easily see those most targeted
- Impersonation type: VIP or brand impersonation
- Summary information for each phishing email including display name and email address used, and whether the recipient replied
- Full visibility of email header, message content and attachment types
Superior phishing protection
The level of phishing protection added to Sophos Email in this latest release offers incredible value, with simple controls that help ensure protection is in place quickly.
Social engineering
Suspicious messages can be blocked, quarantined, tagged with a subject line or have a warning banner added.
As well as the new impersonation protection, Sophos Email scans all inbound email in real-time, searching for key phishing indicators with SPF, DKIM and DMARC authentication techniques and email header anomaly analysis.
Malicious URLs and attachments
Real-time malicious URL detection and AI-powered sandboxing.
For phishing protection against malicious URLs or attachments that may contain malware, Sophos Email provides real-time URL scanning and Time of Click URL rewriting to analyze any URL before it gets clicked. Then Sophos Sandstorm, our AI-powered cloud sandbox, detonates suspicious files to ensure malware never reaches the inbox.
User education
Intelligent cybersecurity awareness training.
Sophos Synchronized Security connects Sophos Email to Phish Threat, the Sophos phishing simulation and training platform.
Users who have been warned or blocked from visiting a risky website or replying to a spear phishing email are identified and then seamlessly enrolled onto targeted phishing simulations and training to improve awareness. A Phish Threat license is required.
To find out more visit the Sophos Email Security page.
The term “classification” has been thrown around progressively by software companies that offer related products like data governance and DLP. In some cases, the vendor will define “classification” as the ability to discover and protect data, which is a very new and misleading use of the word. Traditionally “classification” was related to visual and metadata markings, like the control markings used by the intelligence community. Outside of that community, a full range of standard classifications and their related markings can be found in the CUI (controlled unclassified information) handbook. CUI is just one of many classification systems that involve markings. In other words, those systems require that the data is somehow “marked.” Protecting a file with DLP or encryption is not the same thing as “marking” the file as confidential.
For those who are unfamiliar with classification, it can be confusing when certain terms are thrown around. For instance, what is the difference (if any) between classifications, values, file properties, metadata markings, visual markings, and marking formats? Let’s look at a real world example, and put these terms into context.
If a sensitive document is marked with [TOP SECRET] in the header, then we could say that the classification is “top secret”, which in an abstract way is describing an option within a category. In the Classifier Admin console, those categories are called “selectors” and the options are called “values.” So the value might be “top_secret”, and there can be alternate values, like “TOP SECRET”. When those values are written to locations, like the header in MS Word, they can be formatted using any combination of fonts, font sizes, colors, justification, brackets and other punctuation. In other words, placing [TOP SECRET] in the header requires a marking format that writes the classification value in all caps and encapsulates it in brackets.
Markings that appear in the header are considered to be visual markings (aka visible markings). Any non-visual marking is called a metadata marking. Classifier, for instance can place metadata in the file properties (document properties and custom document properties) of a Word document. This metadata may use the same “[TOP SECRET]” marking format that was used for the header. As an alternative, the metadata can be more encoded, e.g., [xyzTopSecx] or [TS]. The Classifier label detection mechanism (and other software, e.g., DLP and data governance tools) will be configured to equate those markings with the “top secret” level. If the DLP detects [xyzTopSecx] in the keywords document property, then the file will be protected from leaving the organisation.
“Classification” products must be able to read and write labels in the manner described above. The alternative is that data is simply discovered and protected. Fingerprinting might be the closest substitute to classification. At first glance fingerprinting gives us a way to track and identify specific files. That is a powerful value add that can be important in certain use cases. The challenge is that the fingerprint database can be large, and communications can take excessive bandwidth (depending on how it’s used). Furthermore, fingerprinting is typically on or off. Either the fingerprint is applied or not. There is no “public fingerprint” vs. “confidential fingerprint”. So true classification stands alone as the only solution to complex classification needs, like the categories used in regulatory compliance like CUI.
Contact us today to find out more about protecting your sensitive data using a classification tool that really does classify your data how you need it to.
Today, businesses everywhere are investing in infrastructure to support growth – whether that’s moving to the cloud or automating tasks and processes. However, the newly introduced devices, application stacks and accounts that come with this modernization all present additional opportunities for attacker exploitation. For any organization – big or small – identifying and addressing security risks across this expanding attack surface can be a formidable challenge.
Privileged access management (PAM) programs that secure pathways to critical business information are foundational to an effective corporate cybersecurity program. Why? Attackers view privileged accounts as one of the best ways to gain a foothold within an organization’s infrastructure. In fact, the vast majority of cyber attacks involve compromised privileged credentials and PAM solutions provide a critical layer of defense.
But, while securing privileged access consistently tops the lists of projects that can reduce risk and improve operational efficiency, some misconceptions surrounding PAM persist. Today, we’re going to bust five of the most prevalent PAM myths.
Myth #1: Because privileged access exists everywhere, it is impossible to secure.
While the scope of privileged access can be intimidating based on the complexity of your environment, dedicated PAM solutions and related policies can actually shrink the attack surface by shutting down pathways to critical resources.
Leading PAM solutions can automatically map privileged credentials across cloud and hybrid environments, saving security teams significant time and effort. And for those unsure of where privileged accounts exists, there are free tools like CyberArk Discovery & Audit to help organizations gain visibility into their privileged account landscape.
Additionally, modern PAM tools also incorporate automatic rotation of SSH keys and other privileged credentials at regular intervals to eliminate the time-consuming and error-prone manual tasks required for regulatory compliance. Meanwhile, automatic session monitoring capabilities systematically record all privileged account sessions and identify which users are operating privileged accounts.
Finally, the best PAM tools also provide detailed session monitoring recordings that can be sorted into searchable metadata for compliance and incident response teams and leverage user behavior analytics to automatically detect and suspend risky privileged sessions.
The impossible just became achievable. Between account mapping, automatic credential rotation and detailed session monitoring, privileged access can be uncovered, managed and secured.
Myth #2: Privileged access management tools are challenging for administrators to manage.
That may have been true in the past, but today’s PAM solutions greatly ease and simplify administrator workloads. Collecting all privileged accounts in a centralized vault eliminates the need to manually search for and manage privileged credentials. In increasingly dynamic network environments, centrally locating the necessary tools to appropriately manage users’ privileged access can improve the efficiency and efficacy of IT projects. Automation tools also enable administrators to eliminate time-intensive tasks in favor of more strategic initiatives.
Especially as organizations move to the cloud, PAM tools can be particularly useful to address emerging risks of cloud migration. When adopting a hybrid or public cloud infrastructure, even slight misconfigurations can create new vulnerabilities. Having holistic tools in place to discover risks associated with privileged access can improve an organization’s security posture.
Myth #3: Identity and Access Management (IAM) solutions are sufficient to protect privileged access.
It’s true that IAM tools and Multi-Factor Authentication (MFA) methods are strategic investments – but they do not replace the value of a PAM solution. PAM solutions can independently protect privileged accounts with human and non-human identities like application accounts used in robotic process automation (RPA) or DevOps – something IAM solutions simply aren’t designed to do.
Focused on risk reduction, PAM tools can also protect privileged business users from sophisticated social engineering attacks capable of bypassing MFA. Most importantly, IAM tools require direct connection to user databases like Active Directory (AD). These connections are often hosted on-premises. If any on-premises server is compromised, attackers can gain control over AD to implement Kerberos attacks, such as Golden Ticket, and exist undetected in a company’s network. PAM can provide a vital security layer for servers hosting IAM’s direct connection to user databases like AD.
To create a strong enterprise security fabric, IAM systems and PAM solutions should be deployed as collaborative tools.
Myth #4: Privileged Access Management solutions interfere with operational efficiency.
The truth is that the daily tasks of most workers don’t require elevated privileges – and therefore PAM solutions won’t impact them at all. For those who do require elevated privileges, leading PAM tools offer a variety of user-friendly formats, including RDP, SSH and web-native access, to provide credential vaulting and session management in the background of their daily workflows. Native and transparent access provides organizations with comprehensive privileged session recordings while minimizing disruption for end users.
In fact, using PAM tools to automate time-consuming tasks for IT and security employees can improve productivity by freeing up time for higher-value projects. Audit teams can achieve the same benefits by automating compliance tasks — especially in highly regulated industries like healthcare and banking. Manually sorting through all sessions that involve privileged credentials to find high-risk activity can be extremely time consuming. PAM solutions can automate these tasks and identify risky behavior for audit teams, freeing them up to spend their time on other critical tasks.
Modern PAM solutions can actually be a boon to operational efficiency – not an impairment.
Myth #5: It’s Difficult to Calculate ROI for Privileged Access Management solutions.
The average cost of a data breach in 2019 came in at nearly $4 million dollars. Notably, this figure does not include the additional costs of lost business from reputation damage and theft of intellectual property. Privileged access is a focal point for organizations to demonstrate where security solutions can have a high impact.
In any security program, cost-efficiency is key. Organizations must take a risk-based approach, applying finite resources where they can achieve quick wins and long-lasting impact. And it’s in this area where PAM solutions can really shine. PAM is a high-leverage point where modest investments can achieve outsized ROI and risk reduction.
After deploying a PAM solution, organizations can scan their systems to see the decrease in the number of unsecured and unprotected systems. Since any unmanaged privileged account is a potential attack vector, each privileged account that has been discovered, secured and protected by a PAM solution is a direct reduction in the exposed attack surface and proof of ROI.
Effective security starts with protecting an organization’s most valuable information, and as a common target in most cyber attacks, unmanaged and unprotected privileged access represents a significant threat. By locking down privileged credentials, organizations deprive attackers of their preferred routes to critical data and assets. Simultaneously, session monitoring and threat detection capabilities can help teams detect and investigate misuse of privileged credentials — improving an organization’s response time to in-progress attacks.
Furthermore, many PAM solutions can PAM solutions can integrate with other enterprise software solutions – from IoT device gateways DevOps tools and network devices to vulnerability management systems – enhancing their value and streamlining security operations on the whole.
Want to learn more? Check out CyberArk’s approach to Privileged Access Management or visit our resource center to find out more about the efficiency and security benefits of PAM.
Sophos Mobile 9.5 is now available in Sophos Central, bringing a host of exciting improvements. Key enhancements include:
Sophos Intercept X for Mobile
Leveraging deep learning anti-malware technology, Intercept X for Mobile protects users, their devices, and corporate data from known and never-before-seen mobile threats.
Device, network and application protection will be delivered in a completely redesigned interface, which enables easy management and identification of any security holes on users’ devices.
Device Security continuously monitors for potential compromise and sends alerts so IT admins can rapidly and automatically remediate issues and revoke access to corporate resources.
Network Security monitors network connections for suspicious activity in real time, warning IT admins and users of potential Man-in-the-Middle (MitM) attacks. Web filtering and URL checking also stop access to known bad sites, protecting users from unsuitable content, and SMS phishing detection spots malicious URLs.
Application Security detects malicious and suspicious applications installed on devices, protecting against malware, ransomware and potentially unwanted apps like Fleeceware.
Intercept X for Mobile can be deployed via Sophos Mobile or 3rd party UEM Products, e.g. Microsoft Intune, allowing administrators to build conditional access policies, restricting access to applications, data and corporate resources when threats are detected.
Chromebook security – education-focused security
With this release we add a great new feature, Chromebook security!
This is ideal when working with schools, as we all know kids are pretty smart when it comes to technology these days and will find ways around security. Let’s help school admins with that task.
- Web protection that’s ideal for education
- On & off-campus web filtering
- Enrolment via Sophos Mobile or G Suite
Sophos Mobile 9.5 updates
Our secure UEM solution in Central lets customers manage, secure and configure mobile and traditional endpoint devices, apps and content. The latest update, Sophos Mobile 9.5, includes device management enhancements:
- Improved task bundle wizard
- Android Enterprise QR code enrollment
- Support for Samsung OEM config
- Enhanced security reporting
How to get Sophos Mobile 9.5
If you’re a current Sophos Central Mobile customer you won’t need to do anything, you’ll automatically get the upgrade. For on premise customers, you’ll need to manually upgrade to 9.5.
And, if you’ve never tried Sophos mobile before, download Intercept X for Mobile for free – on Android or iOS – and test our industry leading mobile protection for yourself!
Don’t take our word for it, have a look at the independent test – we’ve been named a leader in the IDC report and on top of that we aced the Miercom and AVTest tests.

























