News
Η NSS, διεθνής διανομέας Value Added Distributor (VAD) λύσεων πληροφορικής υψηλής τεχνολογίας ανακοινώνει σήμερα τη συνεργασία της με την BeyondTrust, παγκόσμιο ηγέτη στη διαχείριση προνομιακής πρόσβασης (Privileged Access Management) και ασφαλούς απομακρυσμένης πρόσβασης (Secure Remote Access). Η NSS θα διανέμει στην Ελληνική και Κυπριακή αγορά, καθώς και στα Βαλκάνια και τη Μάλτα, την πιο απρόσκοπτη λύση για την αποτροπή παραβιάσεων δεδομένων που σχετίζονται με κλοπή διαπιστευτηρίων, κακή χρήση προνομίων και παραβίαση της απομακρυσμένης πρόσβασης. Ως διεθνής διανομέας λύσεων ασφάλειας στον κυβερνοχώρο στην περιοχή, η NSS βρίσκεται σε στρατηγική θέση για να διανέμει στην αγορά την πλήρη σουίτα εργαλείων Privileged Access Management (PAM) της BeyondTrust.
Το χαρτοφυλάκιο Privileged Access Management της BeyondTrust αποτελεί μια ολοκληρωμένη λύση που παρέχει ορατότητα και δυνατότητες ελέγχου σε όλους τους προνομιακούς λογαριασμούς αλλά και τους προνομιακούς χρήστες. Ενοποιώντας ένα ευρύτατο σύνολο δυνατοτήτων ασφάλειας προνομιακής πρόσβασης, η πλατφόρμα απλοποιεί τις υλοποιήσεις, μειώνει τους κινδύνους που σχετίζονται με τα προνομιακά διαπιστευτήρια, μειώνει τα κόστη και βελτιώνει σημαντικά τη χρηστικότητα.
«Ως στρατηγικός συνεργάτης μας, η NSS θα είναι σε θέση να εκμεταλλευτεί το μοντέλο Universal Privilege Management της BeyondTrust, μια σύγχρονη προσέγγιση που αντιμετωπίζει το σύνολο προνομίων σε έναν οργανισμό», δήλωσε ο Alexis Serrano, Director – Channel & Alliances EMEIA της BeyondTrust. «Συνδυάζοντας την τεχνογνωσία και τη βαθειά γνώση της αγοράς που διαθέτει η NSS στην περιοχή αλλά και το εκτεταμένο δίκτυο συνεργατών της, με τις καλύτερες λύσεις της BeyondTrust, αυτή η συνεργασία θα βοηθήσει τις επιχειρήσεις και τους οργανισμούς να βελτιώσουν τις στρατηγικές ασφάλειας και την επιχειρησιακή τους αντοχή», συμπληρώνει ο κος Alexis Serrano, Director – Channel & Alliances EMEIA της BeyondTrust.

«Ως ηγέτης στη διαχείριση της προνομιακής πρόσβασης (PAM) με πολλές περγαμηνές και διεθνείς διακρίσεις από αναλυτές όπως η Gartner, στην NSS, είμαστε ενθουσιασμένοι που φέρνουμε τις λύσεις της BeyondTrust στην ευρύτερη αγορά της Ελλάδος, της Κύπρου, των Βαλκανίων αλλά και της Μάλτας», δήλωσε ο Γιώργος Καπανίρης, Εκτελεστικός Διευθυντής της NSS. «Η ολοκληρωμένη λύση PAM της BeyondTrust θα μας επιτρέψει να καθοδηγήσουμε τους πελάτες μας σε ένα ταξίδι που τους επιτρέπει να αντιμετωπίσουν κρίσιμα τρωτά σημεία και να αρχίσουν αμέσως να συρρικνώνουν την επιφάνεια επίθεσης στις υποδομές τους».
Η ευέλικτη και επεκτάσιμη πλατφόρμα της BeyondTrust, δίνει τη δυνατότητα στους οργανισμούς να κλιμακώσουν εύκολα την ασφάλεια προνομίων καθώς οι απειλές εξελίσσονται σε περιβάλλοντα τελικού σημείου, διακομιστή, cloud, DevOps αλλά και συσκευών δικτύου. Η πλατφόρμα της BeyondTrust ενοποιεί την ευρύτερη σειρά προνομιακών δυνατοτήτων πρόσβασης με κεντρική διαχείριση, αναφορές και αναλυτικές αναφορές, επιτρέποντας στους διαχειριστές, αλλά και στους επικεφαλείς ασφάλειας να λάβουν αποφασιστικές και ενημερωμένες ενέργειες και αποφάσεις για να αντιμετωπίσουν τους επιτιθέμενους. Η ολιστικής προσέγγισης πλατφόρμα ξεχωρίζει για τον ευέλικτο σχεδιασμό της που απλοποιεί τις ενοποιήσεις, βελτιώνει την παραγωγικότητα των χρηστών και μεγιστοποιεί τις επενδύσεις πληροφορικής και ασφάλειας.
Η BeyondTrust δίνει στους οργανισμούς την ορατότητα και τον έλεγχο που χρειάζονται για τη μείωση του κινδύνου, την επίτευξη των στόχων συμμόρφωσης και την ενίσχυση της επιχειρησιακής απόδοσης. Η NSS θα αξιοποιήσει τις καινοτόμες λύσεις συνολικού ελέγχου προνομιακής πρόσβασης της BeyondTrust για να συμπληρώσει τις λύσεις τεχνολογίας που προσφέρει ήδη στην ευρύτερη περιοχή όπου δραστηριοποιείται. Αυτή η συνεργασία θα επιτρέψει στην NSS να παρέχει μια προσαρμοσμένη λύση PAM που να ανταποκρίνεται στις μοναδικές απαιτήσεις κάθε πελάτη της. Μάθετε περισσότερα στην ιστοσελίδα της NSS https://www.nss.gr.
Managing IT security takes a lot of time. Well, 26% of an IT team’s time to be precise, based on feedback from the 3,100 IT managers we surveyed last year.
With time an increasingly precious commodity, the good news for XG Firewall users is that you can double the efficiency of your security team while also increasing your protection. How? By running Intercept X with EDR as your endpoint protection.
Double the efficiency of your IT team
Like XG Firewall, Intercept X is part of the Sophos cybersecurity system, and you can manage both solutions through the Sophos Central platform.
This eliminates the need to jump from console to console to see what’s going on. No more struggling to track data across platforms. Instead you have a single security console with consolidated alerts visible from the dashboard.
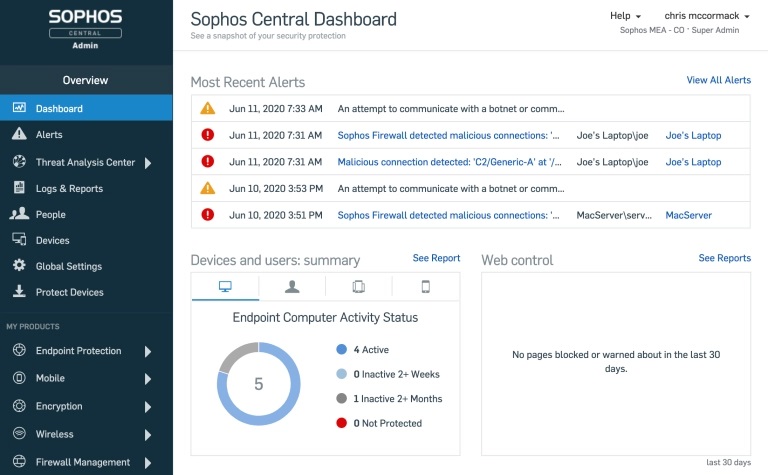
The Sophos Central Dashboard consolidates alerts across all products for instant visibility.
XG Firewall and Intercept X also share threat, health and user data, enabling you to quickly investigate any incidents that do occur.
When the firewall shows you the device name rather than just the IP address life becomes significantly easier.
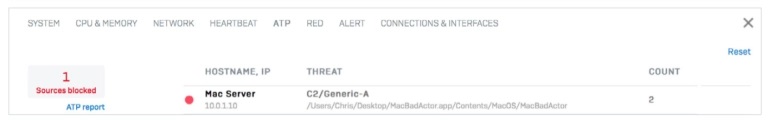
See the name as well as the IP address of affected devices
In fact, customers tell us they’ve seen day-to-day security admin fall by 90% since they started running XG Firewall and Intercept X together, managed through Sophos Central.
Elevate your protection
Intercept X with EDR lets you elevate your protection by combining market-leading technologies with the ability to identify the root causes behind security and IT operations incidents.
Like your XG Firewall, Intercept X is powered by Sophos’ deep learning engine. It also gives you the most comprehensive exploit and ransomware protection on the market.
In addition, the new EDR capabilities enable you to see what’s really going on across your environment.
Fully-customizable queries quickly give you the answers to questions such as:
- Why is a device running slowly?
- Are machines pending a re-boot?
- Where is RDP enabled?
- Are any programs trying to connect with a non-standard port?
Armed with this information you can stop potential incidents before they occur, and address underlying issues.
Try for yourself
If you’re managing your XG Firewall through Sophos Central you can start a no-obligation free trial of Intercept X with EDR in just three clicks.
Simply scroll to the Free Trials link in the main left-hand navigation and follow the instructions.

If you’re not yet using Sophos Central, start a trial via our website. You’ll be up and running in a matter of minutes.
Hear from customers
To learn more about the benefits of running XG Firewall and Intercept X, read the Sophos Business Impact report.
It shares the experiences of five customers across North America, Europe, and Asia, quantifying the impact on their team and their organization.
Think you know what you’ve got in the cloud? Think again.
The accessibility of the public cloud is a double-edged sword: while it enables teams to spin up new resources in minutes, it also makes it hard for IT teams to keep track of everything that needs to be secured.
Take control of your cloud security with a free inventory assessment and security check, powered by Sophos Cloud Optix. Activate a free trial to get to get 30 days commitment-free usage:
- Comprehensive inventory of everything you’ve got in the cloud: virtual machines, storage, containers, IAM Users etc.
- Covers Amazon Web Services, Microsoft Azure, Google Cloud Platform, Kubernetes clusters, and Infrastructure-as-Code environments
- Automatically scans for security gaps so you can address areas of weakness
- No agent, no install, no tie-in
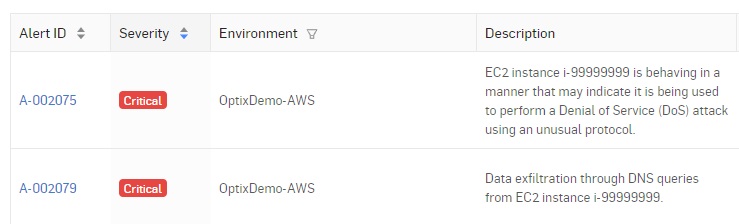
Real-time security alerts, enabling you to take immediate action
Detect and prevent cloud security and compliance gaps
Cloud Optix is an agentless SaaS solution that integrates with your cloud infrastructure accounts using the native cloud provider APIs, logs, and cloud services.
It uses information from these sources to give you a detailed inventory of assets in your cloud accounts and provide an intuitive topological view of the environment’s architecture and traffic flows.
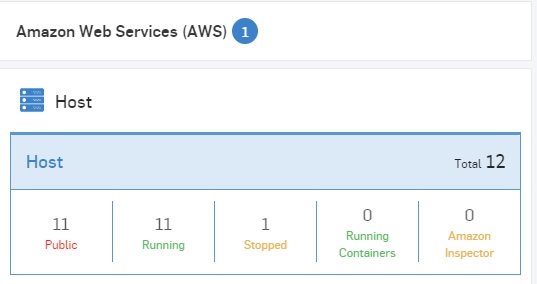
Inventory of all your resources
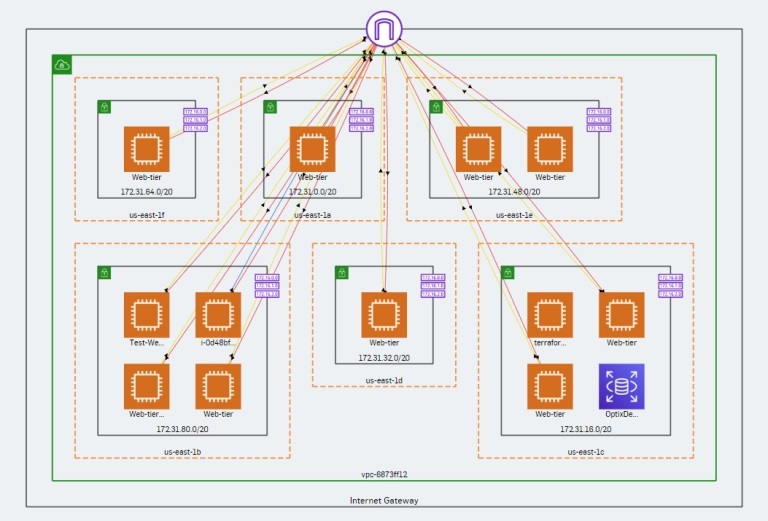
Topological view of your architecture and traffic flows
Cloud Optix also provides up-to-the-minute reports. These make it easy to stay in compliance with both regulatory requirements and internal security policies, including monitoring your daily spend.
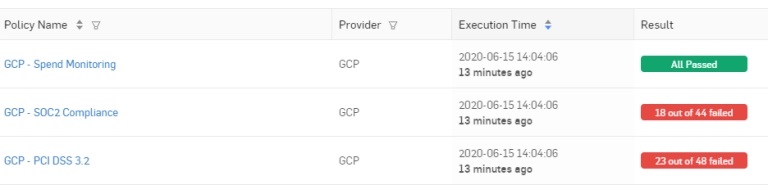
Stay in compliance with real-time reports
Get up and running in minutes
Cloud Optix is managed through the Sophos Central security platform. There are two ways to activate your free usage period:
- Already using Sophos Central: Click on the Free Trials link at the bottom of the left-hand menu in your Central admin console.
- New to Sophos Central: Request a free trial via our website. Your trial will give you access to Cloud Optix as well as all the other security services available in Sophos Central (endpoint protection, server protection etc.).
Next, follow the on-screen step-by-step instructions that will walk you through adding your AWS, Azure and GCP environments. For more information, read the Getting Started guide.
Should you need help at any point, check out the community forum or reach out to our technical support team.
What happens when the trial period is over?
If you wish to continue using Cloud Optix at the end of the free usage period, simply purchase a subscription. Otherwise, you can just stop using the service. There’s no tie-in, no catch, no obligation.
XG Firewall v18 got off to a tremendous start with thousands of customers upgrading on launch day to take advantage of the new Xstream Architecture and other great enhancements.
Today, the product team is pleased to announce a new release of XG Firewall v18, maintenance release 1 (MR1), that is now available for all XG Firewall devices.
This latest release includes all security hotfixes as well as over fifty performance, reliability and stability enhancements and support for our new SD-RED devices.
Upgrading to v18 MR1 is seamless from v17.5 MR6 and above and from any other v18 release version. You will soon start seeing the new release appear in your console with a firmware upgrade notification, but you don’t need to wait, you can grab the new release anytime from the MySophos Licensing Portal: Upgrade Today!
What’s new and in it for you
Watch this brief 5-minute overview of what’s new in XG Firewall v18:
Here are the top new enhancements:
- Xstream Architecture: A new streaming DPI engine, high-performance TLS 1.3 inspection, AI-powered threat intelligence with in-depth reporting, and FastPath application acceleration.
- Sophos Central: Group firewall management and cloud reporting make management easier and provide deeper insights into network activity with flexible report customization tools and a new license for extending your firewall data storage in the cloud.
- Synchronized SD-WAN: brings the power of Synchronized Security to reliably and accurately route application and user-based traffic over preferred WAN links.
- Plug-and-Play High Availability (HA): makes it easy to enable business continuity and adds peace-of-mind – simply connect two XG Series appliances together and you’ll be up and running in no time and now Sophos Central also supports HA pairs.
- Real-time flow monitoring: Get at-a-glance insights into active bandwidth consuming hosts, applications, and users – a fan favorite feature from our UTM 9 platform.
- Expanded notifications and alerts: You will never miss an important network security event whether it’s related to a threat, service, or important performance metric.
- New SD-RED Model Support: With MR1, take advantage of our all-new SD-RED 20 and SD-RED 60 models that provide added performance, modular connectivity, and redundant power for the ultimate solution to remote branch or device connectivity.
Upgrading XG Firewall firmware is easy. Watch this video for a refresher.
Start enjoying the benefits of added visibility, protection and performance with XG Firewall v18 MR1 today!
Migrating from SG UTM
Sophos SG UTM customers interested in taking advantage of all the great new enhancements in XG Firewall can do so for free – anytime. A valid license can be transferred over at no extra charge and Sophos Professional Services is happy to help with migration if desired. Existing SG Series hardware is fully supported (except for the SG 105 which lacks the minimum required 4 GB of RAM). However, you may want to take this opportunity to consider refreshing your hardware to take full advantage of all the new capabilities such as TLS inspection. Check out this recent article for full details.
Migrating from Cyberoam
Migrating from Cyberoam to XG Firewall v18 is strongly encouraged to get all the added usability, security and performance benefits of XG Firewall. Contact your preferred Sophos partner to inquire about upgrading to the latest high-performance XG Series appliance hardware.
New to XG Firewall
If you’re new to XG Firewall, see why it offers the world’s best visibility, protection and response.
At the start of the year the Ponemon Institute launched the 2020 Cost of Insider Threats Global Report. The report highlighted the number of cybersecurity incidents caused by insiders increased by a whopping 47% since 2018. This meant the average annual cost of insider threats had also skyrocketed in only two years, rising 31% to £12.20 million.
Whilst the term “insider threat” can seem malicious, the report highlighted insider incidents are more likely to be caused by negligent employees or contractors. The report supported the trend by showcasing the root cause of most incidents (63 percent) was by negligent insiders. The total figure showed a careless employee or contractor was the root cause of 2,962 of the 4,716 incidents reported, and 1,105 incidents were caused by criminal and malicious insiders.
Non accountable behaviours
Whilst there are various type of insider threats; malicious insiders often seek financial gain or look for revenge. Unintentional insider threats, on the other hand, are more well-meaning but are no less dangerous. These employees will more likely fall victim to social engineering techniques or phishing emails.
Ignorance forms a key issue when it comes to employees handling data. Many of these individuals were never trained on their personal responsibility over company data, and have little knowledge of the company’s security practices. As such, they are highly susceptible to threats mentioned above.
Why they are dangerous?
Apart from the economic factor, these threats are hard to identify, and an operational disaster. Identifying these threats internally can be troublesome, since insider threats already have access to the network with authorised credentials, their access does not flag on a traditional monitoring system. They often already have access to sensitive data, awareness of the existing security measures in place and how to get around them. Combine this all with a lack of visibility into user access and data activity, the difficulty of identifying threat actors is incredibly challenging.
Mitigating the threat
One of the best ways an organisation can combat this issue is by fulfilling their compliance obligations through the adoption of a Privacy by Design approach. This is an approach that takes privacy into account throughout the whole process, ensuring that a business’s systems, policies and processes and technologies is accounted for. Privacy by Design needs to start with data classification. The sheer volume of unstructured data within organisation, combined with the ever-increasing technical abilities of hackers and the fallibility of employees, makes it impossible to rely on people and processes alone to ensure that sensitive data is handled appropriately. Data classification embeds a culture of compliance by involving users to identify, manage and control the sensitive data they work with, while automating parts of the protection process to enforce rules and policies consistently. Data is classified at source so the organisation’s rules can be applied at the outset.
An organisation’s first step is to understand what data they have have, who is using it, how it is being stored, classified and shared, and whether it is company-sensitive; this is key to any data protection strategy. Once the organisation has defined what data it has, the next step is to classify it. Data classification is the categorisation of data according to its level of sensitivity or value, using labels. These are attached as visual markings and metadata within the file. When a classification is applied, the metadata ensures that the data can only be accessed or used in accordance with the rules that correspond with its label. This means the organisation would need to define its classification policy first and decide who should have access to each type of data. Once this is done, the next step will be to select an appropriate classification tool; the right technology will help users to consistently apply the classification scheme with ease. The most effective tools make classification a seamless part of business-as-usual. Once data is appropriately classified, security tools such as Data Loss Prevention (DLP), policy-based email encryption, access control and data governance tools are exponentially more effective, as they can access the information provided by the classification label and metadata that tells them how data should be managed and protected.
With the increase of regulation and its impact on business liability, organisations will need to invest in technology and policies that will help them to respond to, and prevent, insider threats from moving out externally. This will mean organisations would be able to identify what data has left their network, and how to prevent data leaving in the future by looking for similar information on all other data assets.
Since the first outbreaks of Covid19 in Europe and seeing the containment measures taken by different countries such as Italy or Spain, many companies have been preparing so that their employees could work remotely from home without taking into account the risks and security of their sensitive information.
The advantages of remote work and its risks
According to Gallup Human Resources consulting firm, 54% of American workers work remotely part time or continuously. Many studies claim that remote workers are more productive and profitable than office-based employees. In Europe, the data for occasional remote workers compared to total workers is much lower, although there are huge differences by country.
Among the advantages that have led companies to adopt remote work has been the reconciliation of work and family life, increased productivity, avoidance of stress when travelling to work, and cost reduction.
In a short space of time Covid19 has imposed itself on these advantages in recent weeks and has forced many companies to take measures to remote work and minimize downtime.
However, not everything is an advantage when it comes to remote work. Among the barriers to adoption are isolation and disconnection from the organization and culture of the company (lack of visibility in terms of business management, isolation), lack of visibility and control over worker responsibility (is he doing what he has been asked to do?), difficulties in communication (including changing time zones), maintaining separation between personal and work life and cybersecurity (keeping workers and company data safe).
Tools to facilitate remote work
Due to the threat of the Covid19, many companies have rushed to make work easier for employees. Companies are using, among others, the following technologies to facilitate remote work:
- Productivity tools: Access to documentation suites such as Office, Adobe and others so that employees can continue with their daily operations.
- Videoconferencing: WebEx, Zoom, GoToMeeting, etc. tools to hold online meetings or improve communication between remote teams.
- Collaborative workspaces Teams, Slack, etc. and similar tools that facilitate remote collaboration.
- Access to BackOffice tools: ERPs, CRMs, and other corporate tools via Cloud access or via VPN/RDP.
- Cloud storage systems: Access to corporate documentation via Cloud systems or remote access to corporate file servers.
 Is sensitive information safe whith remote work?
Is sensitive information safe whith remote work?
But, what about information security? It is important to enable productivity and communication tools, but we must not neglect security: Use of secure authentication systems, VPNs to avoid publishing remote access to servers, etc.
The urgency for companies to implement remote work measures has led, for example, to the establishment of unsafe communication channels from workers’ homes to company systems. For example, enabling access to servers via RDP (Remote Desktop Protocol), without an adequate VPN connection.
One thing is clear, the organization’s sensitive information is going to be more dispersed and widespread than ever before. It will be carried from the company’s systems to home computers with improvised and minimal security measures that cannot be at the level of corporate security systems.
Protect sensitive documents and keep them under control
Now sensitive information has been moved to the cloud, home computers, etc. How can I easily and conveniently put measures in place to keep it protected and under control, even if it is on computers outside the organization?
SealPath, Protection and Control tool allow you to have your data encrypted, even if it is on a remote computer, control access permissions (view only, edit, copy and paste, etc.) and audit access to information. Not only that, but you can revoke access to certain protected information if necessary to prevent possible data leaks.
By following these steps with SealPath you can have your information protected within minutes and under control on all employees’ computers, even if they are at home:
- Register your users in SealPath from the web control panel. They will receive a registration confirmation and instructions to install the SealPath software.
- Create a corporate policy with SealPath where you only allow access to the company’s internal staff (users of the company’s domain).
- Protects sensitive documentation that will be accessible by users from home through file servers, cloud applications, etc. Protection can be done automatically and unattended with SealPath for File Servers to secure data from file servers, SharePoint, Office 365, etc.
Once users access the information from their home computer, they can do so with the permissions assigned to them in that policy. Documentation will be encrypted, and all access will be authenticated.

With SealPath, it’s easy to get your data to travel with the security your business needs. Sensitive documentation will be out, but with corporate security “attached” to it. The work environment may not be as secure as it usually is, but the security enhancement SealPath easily applies eliminates this risk.
What other advantages does SealPath offer to secure information in this new remote work environment?
- The fact that a worker is not physically in the office increases the risk of phishing and identity theft. If confidential or critical information is given to a cybercriminal posing as a co-worker or a company executive, if this information . t can even be easily blocked completely if it is detected that this information has fallen into the wrong hands.
- These days, companies will see access to the network and information repositories from unknown devices. It will be difficult to determine whether these devices are legitimate or not. If critical information is protected with SealPath in the information repositories, the intrusion from an unauthorized device can only take encrypted information that will not be accessible after it is stolen.
Want to know more? Contact us and our experts will advise you on how to secure your information with SealPath quickly and within a few hours so that your employees can work comfortably and safely from home.
Sophos Connect is our free remote-access VPN client designed specifically to enable remote workers to access your XG Firewall protected network from anywhere. And Sophos Connect 2.0 now includes many new features that you can start taking advantage of right away.
You should also know that as a licensed XG Firewall customer, there’s no extra charge for remote-access VPN connections – you can utilize as many as you want (up to your firewall’s capacity) to support your remote workforce – included for free as part of your base license.
What’s new in Sophos Connect 2.0
The early access program for Sophos Connect 2.0 is now underway, adding support for SSL VPN on Windows as well as a number of other enhancements.
- SSL VPN support for Windows
- Bulk deployment of SSL and/or IPSec VPN configurations via an enhanced provisioning file
- The same convenient deployment as in Sophos Connect v1 for IPSec
- Support for one-time-passwords (OTP)
- Improved DUO multi-factor-authentication (MFA) support (when connecting to XG Firewall v18)
- Auto-Connect option
- Option to execute a logon script when connecting
- Remote gateway availability probing
- Automatic synchronization of the latest user policy if the SSL policy is updated on the firewall (when using the provisioning file to deploy) as well as a manual re-synchronization of the latest policy
- Automatic failover to next firewall WAN link if one link fails
- File extension association for policy files – import a policy file into Sophos Connect just by double-clicking it in Windows Explorer, or opening the file attached in an email
Getting started
Head on over to the XG Firewall Community to get started with the early access program. There are full details on all the changes, instructions on how to use the new provisioning file, and the download itself. Full instructions are also available online.
SSL vs IPSec
With Sophos Connect 2 now supporting both SSL and IPSec VPN technologies, you might be wondering about the pros and cons of each and which one you should use.
In general, SSL VPN, which can work over port 443 just like any encrypted website connection, will present fewer obstacles and work from more varied locations such as public WiFi hotspots and hotel networks.
IPSec is typically more efficient but uses UDP ports 500 and 4500 which can often result in connections being blocked by 3rd party firewalls. If the user has full control over their firewall or router, and can open these ports, then they will find IPSec offers more predictable performance.
One of the great new benefits of Sophos Connect 2 is that you can now offer both with a single client, but we encourage you to take advantage of the new SSL VPN capability for the added flexibility it offers.
Sophos XG Administration. Αυτό το μάθημα έχει σχεδιαστεί για επαγγελματίες τεχνικούς που θα αναλάβουν τη διαχείριση του Sophos XG Firewall και παρέχει όλες τις απαραίτητες δεξιότητες για τη πραγματοποίηση κοινών καθημερινών εργασιών. 
Στόχοι
Με την ολοκλήρωση αυτού του μαθήματος, οι εκπαιδευόμενοι θα μπορούν:
- Να γνωρίζουν όλα τα βασικά χαρακτηριστικά καθώς και πως να προστατεύονται από απειλές
- Να ολοκληρώνουν απλές εργασίες διαμόρφωσης
- Να διαμορφώνουν/ ρυθμίζουν τις συχνότερα χρησιμοποιούμενες λειτουργίες
- Να προβάλλουν και να διαχειρίζονται αρχεία καταγραφής συμβάντων και αναφορές
- Να προσδιορίζουν και να χρησιμοποιούν εργαλεία αντιμετώπισης προβλημάτων
Προαπαιτούμενα
Δεν υπάρχουν προϋποθέσεις για αυτό το μάθημα. Ωστόσο, συνιστάται να:
- Γνωρίζετε δικτύωση σε επίπεδο CompTIA N+
- Να είστε εξοικειωμένοι με τις βέλτιστες πρακτικές ασφάλειας
- Να έχετε εμπειρία διαμόρφωσης συσκευών ασφαλείας δικτύου
Πιστοποίηση
Για να γίνουν πιστοποιημένοι διαχειριστές της Sophos, οι εκπαιδευόμενοι θα πρέπει να δώσουν και να περάσουν από μια διαδικτυακή αξιολόγηση/ εξέταση. Η αξιολόγηση ελέγχει τις γνώσεις τους τόσο για το περιεχόμενο που παρουσιάστηκε όσο και για το πρακτικό περιεχόμενο και περιέχει 40 ερωτήσεις. Η βάση για να περάσετε την αξιολόγηση είναι 80% και περιορίζεται σε 4 προσπάθειες.
Πρόγραμμα
Η εκπαίδευση αναμένεται να διαρκέσει τρεις (3) ημέρες (24 ώρες) για να ολοκληρωθεί, εκ των οποίων περίπου οι μισές θα δαπανηθούν σε πρακτικές ασκήσεις.
Περιεχόμενο
Η εκπαίδευση περιέχει 10 ενότητες:
- Ενότητα 1: Επισκόπηση XG Firewall
- Ενότητα 2: Ξεκινώντας με το XG Firewall
- Ενότητα 3: Προστασία δικτύου
- Ενότητα 4: Προστασία Web Server
- Ενότητα 5: Site-to-Site Connections
- Ενότητα 6: Έλεγχος ταυτότητας
- Ενότητα 7: Προστασία Ιστού και Έλεγχος Εφαρμογών
- Ενότητα 8: Προστασία ηλεκτρονικού ταχυδρομείου (email)
- Ενότητα 9: Wireless Protection
- Ενότητα 10: Απομακρυσμένη πρόσβαση
- Ενότητα 11: Logging, Reporting και Troubleshooting
Sophos XG Administration. This course is designed for technical professionals who will be administering Sophos XG Firewall and provides the skills necessary to manage common day-to- day tasks. 
Objectives
On completion of this course, trainees will be able to:
- Recognize the main technical capabilities and how they protect against threats
- Complete common configuration tasks
- Configure the most commonly used features
- View and manage logs and reports
- Identify and use troubleshooting tools
Prerequisites
There are no prerequisites for this course; however, it is recommended you should:
- Be knowledge of networking to a CompTIA N+ level
- Be familiar with security best practices
- Experience configuring network security devices
Certification
To become a Sophos Certified Administrator, trainees must take and pass an online assessment. The assessment tests their knowledge of both the presented and practical content and contains 40 questions. The pass mark for the assessment is 80%, and is limited to 4 attempts.
Schedule
Training is expected to take three (3) days (24 hours ) to complete, of which approximately half will be spent on the practical exercises.
Content
The training contains 10 modules:
- Module 1 : XG Firewall Overview
- Module 2 : Getting Started with XG Firewall
- Module 3 : Network Protection
- Module 4 : Web Server Protection
- Module 5 : Site-to-Site Connections
- Module 6 : Authentication
- Module 7 : Web Protection and Application Control
- Module 8 : Email Protection
- Module 9 : Wireless Protection
- Module 10 : remote Access
- Module 11: Logging, Reporting and Troubleshooting
Imagine cutting the time you spend on day-to-day security admin by over 90% and slashing the number of security incidents that need investigation by 85%. Almost sounds too good to be true, doesn’t it?
Almost. Because these are the real-world benefits that organizations are seeing from running a Sophos cybersecurity system, revealed in the Sophos Business Impact report.
With Sophos Intercept X protection on endpoints, Sophos XG Firewall at the gateway, and everything managed through Sophos Central, Sophos customers are seeing quantifiable improvements in both protection and IT efficiency.

Customer Impact
We interviewed five customers across North America, Europe, and Asia to understand the impact the Sophos cybersecurity system has had for them.
Each customer’s scenario was different, with varying organizational structures, challenges, and business requirements. However, one major finding was common to all:
Customers said that they would need to double their security headcount to maintain the same level of protection if they didn’t have a Sophos next-gen cybersecurity system.
They also told us that they experience fewer security incidents and can identify and respond quicker to issues that do occur.
Customer A: Healthcare Provider, USA
Customer A is a regional healthcare provider whose services include inpatient and outpatient care, medical practices, nursing homes, and a range of specialist services. They have 4,500 employees, including 80 IT staff, of which three are dedicated to cybersecurity. Benefits they have seen from running Sophos include:
- 50% reduction in IT security resource requirements
The customer currently employs three dedicated cybersecurity heads. They calculated they would need to employ three additional full-time security analysts solely to cover incident response if they didn’t use Sophos. - 90%+ reduction in day-to-day security administration
The IT security manager spends 30 minutes each day reviewing logs and investigating anything of concern. Prior to Sophos, it used to take him an entire day to get the same level of information and confidence. - 85% reduction in security incidents
Prior to Sophos, they experienced on average three incidents each day that were worthy of further investigation. With Sophos this has dropped to an average of one every three days. - 90%+ reduction in time to investigate an incident
Before Sophos it used to take around three hours to conduct a thorough investigation into an incident, which included getting local access to the affected computer. Now it takes a maximum of 15 minutes with everything done remotely via the Sophos Central platform.
Customer B: Education Services Provider, India
Customer B provides educational services to colleges and universities across India and the wider Southeast Asia area. They secure tens of thousands of students via a centralized IT team based out of their head office in Bangalore, together with a team of local IT managers on site. The impact of running a Sophos cybersecurity system includes:
- 50% reduction in staff needed for day-to-day security management
Previously, they employed four engineers to manage day-to-day security. Since moving to Sophos, they have only needed two engineers to cover security across the company. - 94% reduction in time to identify high-risk areas that require investigation
Prior to Sophos it took the customer three to four hours to identify critical issues they needed to focus on for further investigation. Now it takes just 10 to 15 minutes to identify the security priorities across the organization in Sophos Central. - 98% reduction in time to identify the source of bad traffic on the network.
With the previous network security implementation it would take two days (and sometimes longer) to identify which device on the network was causing performance or security issues. Now it takes just 15 minutes to pinpoint the issue and start addressing it. - 95% reduction in time spent managing firmware updates
Before Sophos each firmware update would take between three and four hours. Now it takes just 10 minutes per update. With 20 to 25 updates a year, this equates to a savings of 75 hours a year.
To learn more and to check out all five case studies, read Cybersecurity Evolved: The Sophos Business Impact.
If you’d like to try out Sophos solutions for yourself you can start an instant online demo at www.sophos.com/demo.
We are thrilled to announce that the latest version of Sophos EDR (endpoint detection and response) is now available in Intercept X Advanced with EDR and Intercept X Advanced for Server with EDR.
This release brings powerful new capabilities that enable both IT admins and security analysts to ask detailed IT operations and threat hunting questions across their entire estates. It also provides new functionality to remotely respond with precision.
Existing EDR customers will see these new features appear in their Sophos Central consoles throughout June (see below for additional rollout details).
Upgrade your IT security operations
Maintaining proper IT hygiene can be a significant time investment for IT admins. Being able to identify which devices need attention and what action needs to be taken can add another layer of complexity.
With Sophos EDR you can now do just that, quickly and easily. For example:
- Find devices with software vulnerabilities, unknown services running or unauthorized browser extensions
- Identify endpoints and servers that still have RDP and guest accounts enabled
- See if software has been deployed on devices, e.g. to make sure a rollout is complete
- Remotely access devices to dig deeper and take action such as installing software, editing configuration files and rebooting a device
Hunt and neutralize threats
Tracking down subtle, evasive threats requires a tool capable of detecting even the smallest indicator of compromise.
With this release Sophos EDR is significantly enhancing its threat hunting capabilities. For example:
- Detect processes attempting to make a connection on non-standard ports
- Get granular detail on unexpected PowerShell executions
- Identify processes that have recently modified files or registry keys
- Remotely access a device to deploy additional forensic tools, terminate suspect processes, and run scripts or programs
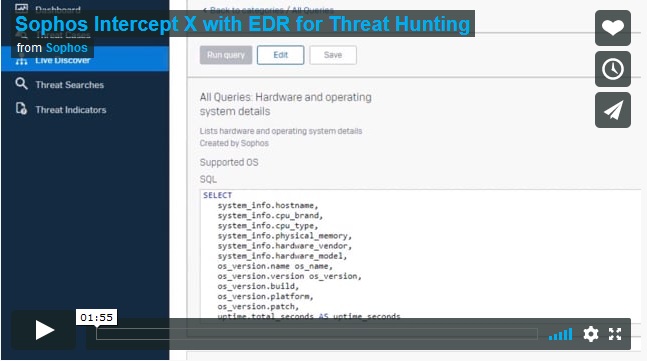
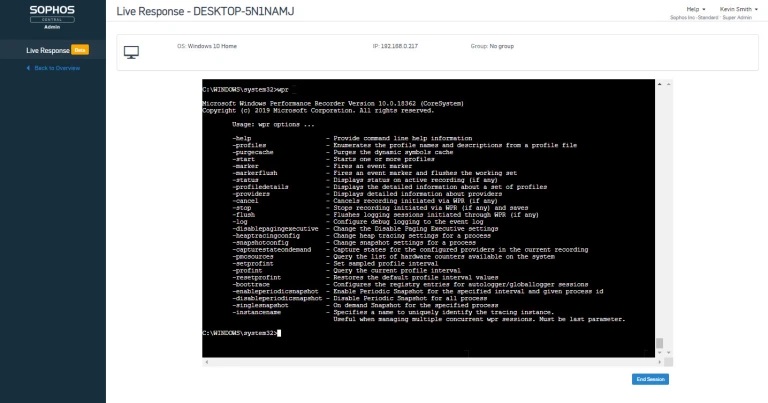
Introducing Live Discover and Live Response
The features that make solving all the important examples above possible are Live Discover and Live Response.
Live Discover allows you to examine your data for almost any question you can think of by searching across endpoints and servers with SQL queries. You can choose from a selection of out-of-the-box queries, which can be fully customized to pull the exact information that you need both when performing IT security operations hygiene and threat hunting tasks. Data is stored on-disk for up to 90 days, meaning query response times are fast and efficient.
Live Response is a command line interface that can remotely access devices in order to perform further investigation or take appropriate action. For example:
- Rebooting a device pending updates
- Terminating suspicious processes
- Browsing the file system
- Editing configuration files
- Running scripts and programs
And it’s all done remotely, so it’s ideal in working situations where you may not have physical access to a device that needs attention.
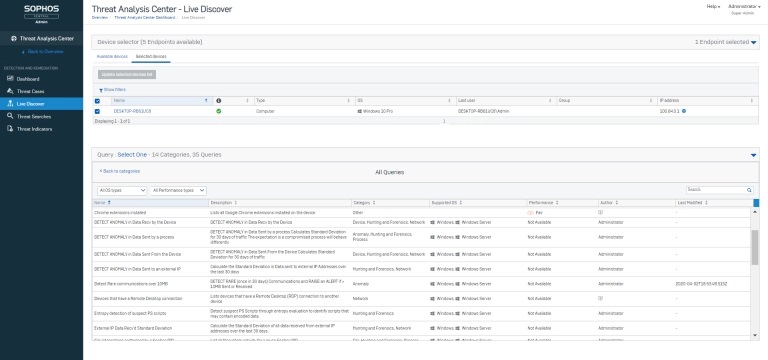
Try out these powerful new features
Check out this video to see the new features in action and how they can help you save time and get the answers you need
Intercept X and Intercept X for Server customers, as well as customers with other products managed via Sophos Central that want to try out the new EDR functionality, can do so from 23 June. Head to the Sophos Central console, select ‘Free Trials’ in the left-hand menu and choose the ‘Intercept X Advanced with EDR’ or ‘Intercept X Advanced for Server with EDR’ trials.
If you’re new to Sophos Central, start a no-obligation free trial of Intercept X Advanced with EDR today. You’ll get world class protection against the latest cybersecurity threats in addition to powerful EDR capabilities. Get started.
Product rollout timing
All Sophos EDR customers will automatically see these new features added throughout June to their Sophos Central consoles. Customers who have participated in the Early Access Program should receive the new version today. All other customers should receive the new version by 23 June.
Live Discover is available on Windows and Linux now, with Mac support coming soon. Live Response is available on Windows now, with Linux and Mac support coming soon.
Did you know that even Microsoft Office 365 customers aren’t automatically protected against data loss? Businesses therefore need to take action themselves if they want to preserve their emails in the long term.
An email archiving solution can be a key component when it comes to protecting and retaining business-critical emails in the long term. But a decision as to which solution is best suited to the needs of a company is often not an easy one to take.
In order to help companies reach a decision in this regard, the market research institute Osterman Research has produced a white paper on how small and mid-sized businesses (SMBs) can adequately protect their business-critical data. The white paper examines which features your company needs and whether your business would be better served by a third-party solution like MailStore Server or the native archiving options integrated in Microsoft Office 365.
Main Points of Discussion in the White Paper
The white paper provides a comparison of the various archiving options available in Microsoft Office 365:
- Exchange Online Archiving (EOA)
- In-Place Archiving
- AutoArchive (also known as “archive to .PST”), and
- the “Archive” button in Microsoft Outlook
In addition, it examines the following key discussion points:
Taking Responsibility for Your own Data
Responsibility for protecting and preserving data lies with the customer, not Microsoft (“shared responsibility model”).
Risk of Data Loss
Emails should be protected against accidental or malicious deletion; otherwise, fulfilling legal, regulatory and best practice obligations could be a difficult task. Even if Microsoft Office 365 is fundamentally capable of restoring accidentally deleted data, situations can arise that impede or even seriously jeopardize daily business operations.
Difference Between Backup and Archiving Solutions
Backup and archiving solutions pursue different goals: backups are a snapshot of a single moment in time; they are necessary for tactical reasons so that data can be recovered quickly in the case of system failure or malfunction. In contrast, archiving is used strategically so that data can be preserved over a long period of time in an unchanged format and searched through.
Self-Service for End Users
A third-party email archiving solution allows end users to search through their own data quickly and efficiently and restore emails, thus taking the strain off IT staff.
Independence from Microsoft
Without a third-party email archiving solution, users would be unable to access their own emails if the Microsoft Office 365 service were to fail. So, a third-party solution can help to avoid a vendor lock-in while preserving the portability of your archived emails.
Total Cost of Ownership (TCO)
As Microsoft’s Exchange Online Archiving is available only in plans E3 and E5, a third-party solution can be a much more affordable proposition.
Are you interested in finding out more about the results and guidance contained in the white paper? Then download the white paper of Osterman Research right now!
Do you know it? Do you ever use it? Have you ever hit it by accident when trying to delete an email? We’re talking about that mysterious Archive button in your Microsoft Outlook ribbon. Some find it useful; we reckon it can be misleading. Because you don’t need to be an expert in email archiving to know that the Archive button doesn’t meet the requirements of a professional archiving product when it comes to processing emails.
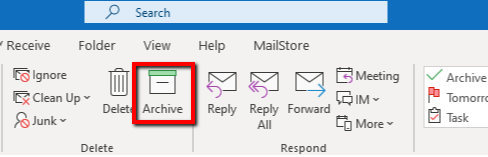
The Archive Button Moves Emails
So what does the button actually do? Basically, it enables you to move an email from your inbox to an archive folder, that’s still part of your personal inbox. While it may go under the name of archiving, all the option really does is shift emails from the inbox to a separate folder called “Archive” instead of deleting them; the emails aren’t actually transferred to a genuine archive. By definition, an archive is the final storage place of documents at the end of a chain of prior usages and, as such, must be capable of retaining this material permanently, e.g. by deploying special safeguards. The arrival of the EU GDPR and other such regulatory requirements mean that email archiving has become quite a complex matter in everyday corporate practice. At the same time, an archive’s job is to ensure that all its records – in this case, emails – remain preserved, available, and retrievable at all times.
Mailbox Volume not Reduced
Also, because this form of “archiving” doesn’t reduce the overall data volume in your mailbox (and on the email server), it doesn’t help solve issues relating to mailbox quotas. If you’re the sort of person who likes to create endless subfolders in your inbox and spend lots of time moving incoming emails to these folders, then the Archive button could help you save time. Because by doing so, you keep your inbox lean, ALL your emails are kept in the same Archive folder, and you can use Outlook’s search function to find emails in this folder. To what extent these sometimes lengthy searches eat into any time savings made is for you to judge.
What Does the Term Archive Mean at Microsoft?
The concept of email archiving isn’t always clear-cut and can be interpreted differently according to objectives, applications, and functions. Microsoft, for example, uses the word “archive” for other functions in its Outlook, Exchange Server, and Microsoft 365 products:
- AutoArchive (Microsoft Outlook): AutoArchive is an outdated option embedded in Microsoft Outlook that allows you to move emails to a separate PST file stored on your computer’s hard drive. Although still available today (File / Info / Tools / Mailbox Cleanup / AutoArchive), it’s not to be recommended: it’s common knowledge that PST files are difficult to process, hard to back up, and prone to corruption – you should get rid of them altogether!
- In-Place Archive (Exchange Server; Microsoft 365): Companies using Microsoft Exchange Server either on-premises or as part of their Microsoft 365 instance can use the available email archiving option by creating a “personal archive” or an “In-Place Archive” for every user mailbox, thus achieving the maximum possible integration of the archiving functionality in Exchange Server and Microsoft Outlook. This type of archiving can, however, place huge demands on the IT infrastructure. Especially in the case of small and mid-sized businesses, these additional requirements and the extra financial investment necessary can pose a challenge. Implementing MailStore Server can provide considerable relief in cases like this.
- Exchange Online Archiving (Microsoft 365): Microsoft 365 provides an online archive for the long-term storage of emails, and especially for overflowing mailboxes. The online archive is displayed as a separate mailbox in the left pane of Outlook. Once set up, older messages are automatically transferred to the online archive so as to keep the size of the primary Outlook mailbox in check. Businesses should keep in mind, however, that Exchange Online Archiving (EOA) is included in specific Microsoft 365 plans only. With many other subscriptions, you will need to add EOA as an additional, paid service to your existing Microsoft 365 plan.
Whitepaper Sheds Light on Email Archiving With Microsoft 365
Email archiving in Microsoft 365, in particular, provides a company with endless options. A whitepaper drawn up by Marketing Research Institute Osterman Research on behalf of MailStore offers a profound insight into the benefits and limitations of the product’s native features.
The paper examines, among other aspects, those features your company really needs and whether your business would be better served by a third-party solution like MailStore Server or the native archiving options provided by Microsoft 365.
“In general, we believe that businesses stand to benefit from our email archiving software on six counts,” says Björn Meyn, Product Manager at MailStore. “Besides the opportunity to fulfill regulatory and compliance requirements, protection against data loss, and the elimination of mailbox quotas, companies can increase their productivity and efficiency, while saying “goodbye” to PST files once and for all. There’s also the advantage of independence from email service providers! And if the email system should ever fail or data be lost, authorized users within the company can simply access their emails via the archive.”
According to data from the “US Bureau of Labor Statistics” some 3 million Americans leave their jobs voluntarily, and according to another study by BambooHR, in a survey of 1000 workers, a third admitted to having spent less than 6 months in a job before changing.
These figures are for the United States, but in Europe the numbers of workers who leave are similar. According to this ADP study, one third of European workers plan to change jobs in the next three years. There is also talk of a war for talent in different sectors such as technology, health services and professional services, in this other Glassdoor report on employment trends for 2020.
Without going into the reasons, advantages or disadvantages of these turnover rates, companies are continually faced with the reality of workers moving to other companies that may or may not be competitors. During the time that workers have been in the company they have had access to private or confidential information to a greater or lesser extent depending on the type of position or company.
Ex-employees often take confidential data and information with them
According to a study conducted by Osterman Reasearch, 69% of the organizations surveyed have suffered a loss of data or knowledge as a result of employee departure: Whether intentional or by mistake, employees may take financial, confidential, customer information, product data, marketing, roadmaps as well as intellectual property to other companies.
There is concern about this type of situation in the management of companies of any size: Employees who go to other companies or to the competition and may carry know-how with them that may lead to loss of competitive advantage. We also find in the press continuously striking cases, but the reality is that it happens every day in different sectors and company sizes.
Sometimes, when a worker leaves the company, they usually see nothing wrong with taking with them data they have been working with during the time they have been in the company. This is true in any sector and any type of job.
For example, a salesperson may see it as normal to take all of the organization’s customer contact data with them, with email, positions, phone numbers, etc. Or if someone works in the engineering field, they may consider it fair to take information about projects, procedures, quality guides, support, designs, etc. that they have been working on. The same applies to software: source code of the applications they have been working on, documentation, projects, etc.
The most common thing is that the person who takes this information does not have any malicious intention. He simply goes to another position in another company, and to do his job well and meet expectations, he considers that at some point he can use this information from the previous position.
How to prevent ex-employees from carrying documents and sensitive information?
The problem is that a good part of companies face this kind of situation when it is already too late. When the employee has left, and it is difficult to know if the sensitive documentation has already been taken, or it is difficult to prove it.
Beyond ethical issues, this is a reality that many companies face on a daily basis. What can be done to prevent this type of situation? We can find different kinds of approaches:
- Notify employees of ownership of information: This is usually done when a person joins the workforce and is given company guidelines or policies or clauses in the contract. The reality is that this is not always read and over time it is forgotten
- Implementing device control tools: Which prevent copying to USBs, etc. These systems have already become obsolete with the boom of the cloud, access to mobile devices, etc. as the information can be anywhere
- With policies to prevent information leaks through DLP systems, CASB, etc: However, many times employees need to work with the information at home, pass it to unmanaged devices, etc. and it is not always possible to prevent sensitive information from being left out of the control of these types of tools.
- Monitoring user behavior (UEBA tools; User Entity Behaviour Analytics) that indicate if a user is having strange behavior patterns regarding the management of sensitive documentation. Perhaps it can be useful if we detect many downloads the week before leaving the company, but many times the information goes out of the control of the company months before, normally, simply because the workers must use it at home, etc.
These methods or systems are limited and often organizations try to use them when it’s too late and the damage has already been done. However, in extreme situations, there is no choice but to use the legal route with the very high costs that this can entail for the organization.
The most effective solution: Data-centric protection
Information can be anywhere, and if it is of value to the company, we must protect it wherever it is. We can protect this type of information through data-centric protection technologies such as SealPath. How so?
- Keep information secure and under control whether it is within the company or if an employee takes it home to work, to other devices etc.
- Limit what others can do with the documents: View only, view and edit only, but not print or copy and paste, etc.
- Have a complete accessibility control: Who accesses it, when, or if someone is trying to open it without permission
- Be able to block access to information in real time even if it is no longer in our hands and is on other computers or networks
[ Know More: DOWNLOAD SEALPATH DATASHEET ]
Protect your sensitive information now, and without waiting for someone to leave and take valuable company data with them. Contact SealPath and we will show you how we can help.
Structure… it is something we humans need in our life to function and survive. We rely on routines and structure to bring an element of predictability to our lives, which in turn makes us feel safe. I think it is fairly safe to say that the situations that have evolved quickly around us in the last few weeks due to the effects of Covid-19 has rocked a lot of the structure in people’s day-to-day lives. For most organisations, these changes in structure have seen the majority of their workforce shifting from office-based working to remote, home working.
For many users, this is a big change, and organisations have been working hard to prepare their users as best they can to provide as much structure as they can amidst these current changes. However, the one thing that organisations cannot afford to risk here is the structure when protecting their data.
Structure is ever more important when dealing with remote users, especially when it has been enforced rather than a choice made by the user. Moving to a home environment means we can lose a lot of the structure provided to us in an office. Away from the common working practices and thought processes of an office environment, remote working factors in more challenges, and it means we may lose sight of the things that are normal to us or are taken for granted in in day-to-day work life. For example, users may face unfamiliar distractions, and be challenged by different focuses and mindsets. Working all these factors in, remote working is a different beast to the safety, and structure, of the office.
Therefore, we may find users are occasionally distracted from performing tasks as they usually would, and security may not be the top of their agenda. Organisations need to make sure they are providing users with the tools to ensure that guards are not being let down simply because of a location and focal change – in essence sticking to the same standards and associated structure that would be provided in the office environment.
Whether working at home or in the office, a structured data protection policy, using solutions such as data classification and DLP, reinforces the need to control how data is managed. Using these tools, employees are reminded and empowered to apply security policy through the hands on classification of all documents and emails as they are created. Documents and data are protected, security policy is embraced and corporate compliance standards are met.
Boldon James Classifier gives your employees structure to data protection. The process begins by setting a classification policy in line with the business requirements, and every new document created must be classified in line with that policy, a structure by which they can follow easily. It takes the pressure off decision making for the user, as they can follow the correct path using customised prompts in order to best classify the document as required. It may seem a trivial step to providing structure for your employees, but these routines allow users to feel safe that they are doing the right thing in protecting sensitive data, giving them one less thing to worry about.
With your users empowered in this way, they are less likely to make mistakes, and organisations know that no matter where their users are, they can continue to ensure sensitive data is being protected in line with regulatory compliance, meaning you can remain safe, compliant and in control.
A new ransomware variant dubbed “ColdLock” has emerged in Taiwan where it’s having a devastating effect on impacted organizations.
Fortunately, Sophos Intercept X gives the cold shoulder to ColdLock, blocking the attack before it can hold you hostage.
Stop ColdLock with Intercept X
ColdLock is a file-less attack. It runs from a PowerShell script where the ransomware code is directly loaded into memory and then executed, all without writing an executable file to the disk.
Intercept X is packed with technologies that protect your organization from ColdLock and other ransomware variants:
- Exploit protection stops the techniques used in file-less, malware-less, and exploit-based attacks.
- CryptoGuard technology stops the unauthorized encryption of files by ransomware, rolling any impacted files back to their original state.
- The deep learning engine uses cutting-edge machine learning to identify and block never-before-seen ransomware before it executes.
- Credential Theft stops privilege escalation, preventing hackers from moving round your system
Plus, the built-in EDR tools give you detailed insight into what happened, so you can see where the threat got in, what it touched, and when it was blocked.
See Intercept X in action
Try out the demo!
Log in to our fully populated demo environment to try Intercept X for yourself. No obligation, no waiting, no set up. Just a ready-to-go demo.
Stories of organizations crippled by ransomware regularly dominate the IT news headlines, and accounts of six- and seven-figure ransom demands are commonplace. But, do the news stories tell the full story?
To understand the reality behind the headlines, Sophos commissioned an independent survey of 5,000 IT managers across 26 countries. The findings provide brand new insight into what actually happens once ransomware hits. Be prepared to be surprised.
The 2020 ransomware reality
The survey provides fresh new insight into the experiences of organizations hit by ransomware, including:
- Almost three quarters of ransomware attacks result in the data being encrypted.
51% of organizations were hit by ransomware in the last year. The criminals succeeded in encrypting the data in 73% of these attacks. - 26% of victims whose data was encrypted got their data back by paying the ransom.
A further 1% paid the ransom but didn’t get their data back. Overall, 95% of organizations that paid the ransom had their data restored. - 94% of organizations whose data was encrypted got it back.
More than twice as many got it back via backups (56%) than by paying the ransom (26%). - Paying the ransom doubles the cost of dealing with a ransomware attack.
The average cost to rectify the impacts of the most recent ransomware attack (considering downtime, people time, device cost, network cost, lost opportunity, ransom paid etc.) is US$732,520 for organizations that don’t pay the ransom, rising to US$1,448,458 for organizations that do pay. - Despite the headlines, the public sector is less affected by ransomware than the private.
45% of public sector organizations were hit by ransomware last year, compared to a global average of 51%, and a high of 60% in the media, leisure, and entertainment industries. - One in five organizations has a major hole in their cybersecurity insurance.
84% of respondents have cybersecurity insurance, but only 64% have insurance that covers ransomware. - Cybersecurity insurance pays the ransom.
For those organizations that have insurance against ransomware, 94% of the time when the ransom is paid to get the data back, it’s the insurance company that pays. - Most successful ransomware attacks include data in the public cloud.
59% of attacks where the data was encrypted involved data in the public cloud. While it’s likely that respondents took a broad interpretation of public cloud, including cloud-based services such as Google Drive and Dropbox and cloud backup such as Veeam, it’s clear that cybercriminals are targeting data wherever it stored.
For the details behind these headlines, read The State of Ransomware 2020 report.
Sophos Intercept X: Protection against ransomware
Ransomware actors combine sophisticated attack techniques with hands-on hacking. Sophos Intercept X endpoint protection gives you the advanced protection technologies you need to disrupt the whole attack chain, including:
- Encryption rollback. CryptoGuard technology blocks the unauthorized encryption of files and rolls them back to their safe state in seconds.
- Exploit protection. Deny attackers by blocking the exploits and techniques used to distribute malware, steal credentials, and escape detection.
- AI-powered threat protection. Artificial intelligence detects both known and unknown malware without relying on signatures
Start an instant online demo to see how Intercept X works in a full environment. You’ll be up and running in less than a minute.
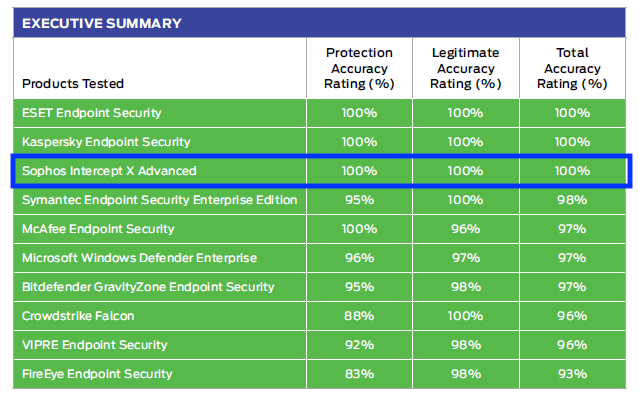
We are thrilled to announce that Intercept X received a 100% total accuracy rating in the enterprise, SMB, and consumer protection tests by SE Labs.
Whether you are protecting your employees at work, or them and their families at home, you will get outstanding protection with Intercept X technology.
The world’s best endpoint protection
Intercept X is the strongest endpoint security on the market, delivering more advanced protection in one solution than anything else out there.
Deep learning AI excels at detecting and neutralizing threats that have never been seen before. Anti-ransomware protection blocks malicious encryption processes and returns affected files to safe, unencrypted states. Advanced defenses against fileless, memory-based attacks keep your organization safe against the latest obfuscated, script-based threats.
Intercept X also includes options for Endpoint Detection and Response (EDR), so you can perform detailed threat hunting and IT security operations hygiene across your endpoints and servers, and a managed service (MTR) that gives you access to a team of Sophos cybersecurity specialists that will hunt threats and take appropriate action on your behalf.
Constant innovation
Our team of cybersecurity experts are constantly enhancing the powerful features in Intercept X. This year alone we’ve incorporated:
- AMSI protection – enhanced protection against fileless attacks, such as obfuscated PowerShell scripts
- Intrusion Prevention System – protects devices against network-based attacks (currently in early access)
- EFSGuard, CTFGuard, and more
Try Intercept X for free
Testing the powerful features in Intercept X couldn’t be more straightforward. Take a free 30 day trial, or if you’d like to learn more head over to Sophos.com.
For a limited time, Sophos customers can add Sophos Home edition at no addition cost.
To view the detailed results from SE Labs: Enterprise | SMB | Consumer
Αυτό το τριήμερο πρόγραμμα εκπαίδευσης σχεδιάστηκε και προορίζεται για έμπειρους τεχνικούς που θέλουν να εγκαθιστούν, αναπτύσσουν, διαμορφώνουν και να υποστηρίζουν το XG Firewall σε παραγωγικά περιβάλλοντα και είναι το αποτέλεσμα βαθιάς μελέτης πάνω στο τείχος προστασίας επόμενης γενιάς της Sophos.
Το πρόγραμμα αποτελείται από παρουσιάσεις και πρακτικές ασκήσεις εργαστηρίων για την ενίσχυση του διδακτικού περιεχομένου. Λόγω της φύσης της παράδοσης και της ποικίλης εμπειρίας των εκπαιδευομένων, ενθαρρύνεται η ανοικτή συζήτηση κατά τη διάρκεια της εκπαίδευσης/ κατάρτισης.
Sophos XG Architect Training (Τρίτη 16 Ιουνίου 2020– Πέμπτη 18 Ιουνίου 2020)
(3 days Training)
Προαπαιτούμενα
XG Firewall _ Certified Engineer course and delta modules up to version 18.0
Συνιστώμενες γνώσεις
- Knowledge of networking to a CompTIA N+ level
- Knowledge of IT security to a CompTIA S+ level
- Experience configuring network security devices
- Be able to troubleshoot and resolve issues in Windows networked environments
- Experience configuring and administering Linux/UNIX systems
Περιεχόμενο της εκπαίδευσης
- Module 1: Deployment
- Module 2: Base Firewall
- Module 3: Network Protection
- Module 4: Synchronized security
- Module 5: Web server Protection
- Module 6: Site to site connections
- Module 7: Authentications
- Module 8: Web Protection
- Module 9: Wireless
- Module 10: Remote Access
- Module 11: High Availability
- Module 12: Public Cloud
Certification
+ exam: Sophos XG Architect
Διάρκεια: 3 ημέρες
Πρόγραμμα
Εκπαιδευτής: Μιχάλης Ελευθέρογλου
Ημέρα 1η 16 Ιουνίου 2020
9:30-10:45 Module 1: Module 1: Deployment and Lab
- Recall important information from Engineer courses
- Deployment modes supported by the XG Firewall
- Understand a range of scenarios where each deployment mode would commonly be used
- Use built-in tools to troubleshoot issues
- Labs
10:45-11:00 Διάλειμμα
11:00-13:00 Module 2: Base Firewall
- Explain how the XG firewal can be accessed
- Understand the types fo interfaces that can be created
- Understand the benefits of Fast Path Technology
- Configure routing per firewall rule
- Understand best practice for ordering firewall rules
- Explain what Local NAT policy is and known how to configure it.
13:00-14:00 Διάλειμμα
14:00-16:00 Labs
- Activate the Sophos XG Firewalls
- Post installation Configuration
- Bridge interfaces
- Create a NAT rule to load balance access to servers
- Create a local NAT policy
- Configure routing using multiple WAN links
- Configure policy-based routing for an MPLS scenario
- Install Sophos Central
16:00-16:15 Διάλειμμα
16:15-17:15 Module 3: Network Protection and Lab
- Explain what IPS is and how traffic can be offloaded to Fastpath
- Demonstrate how to optimize workload y configuring IPS policies
- Examine advanced Intrusion Prevention and optimize policies
- Configure advanced DOS Protection rules
- Demonstrate how the strict policy can be used to protect networks
- Labs- Create Advanced DoS Rules
Ημέρα 2η Τετάρτη 17 Ιουνίου 2020
9:30-11:00: Module 4: Synchronized Security and Labs
- Explain how Security Heartbeat works
- Configure Synchronized Security
- Deploy Synchronized Security in discover and inline modes
- Understand the advantages and disadvantages of deploying
- Synchronizes Security in different scenarios
- Labs
- Configure source-Based Security
- Hearteat firewall rules
- Destination based Security Heartbeat
- Missing Security Heartbeat
- Lateral Movement Protection
11:00-11:15 Διάλειμμα
11:15-13:45 Module 5 Webserver Protection and Labs
- Explain how Websever Protection works
- Describe protection features for a web application
- Configure Web Server authentication
- Publish a web service using the Web Application Firewall
- Use the preconfigured templates to configure Web Server Protection for common purposes
- Configure SlowHTTP protection
- Labs (Web Application Firewall)
- Labs (Load balancing with Web Server Protection)
- Labs (Web Server Authentication and path-specific routing)
13:45-14:45 Διάλειμμα και Γεύμα
14:45-17:45 Module 6: Site to site connections and Labs
- Configure and deploy site to site VPNs in a wide range of environment
- Implement IPsec NATing and failover
- Check and modify route precedence
- Create RED tunnels between XG firewalls
- Understand when to use RED
- Labs ( Create an IPsec site to site VPN
- Labs ( Configure VPN network NATing )
- Labs (Configure VPN failover)
- Labs (Enable RED on the XG firewall)
- Labs (Create a RED tunnel between two XG Firewalls
- Labs (Configure routing for the RED tunnel)
- Labs (Configure route-based VPN)
Ημέρα 3η Πέμπτη 18 Ιουνίου 2020
9:00-10:00 Module 7: Authentications and Labs
- Demonstrate how to configure and use RADIUS accounting
- Deploy STAS in large and complex environment
- Configure SATC and STAS together
- Configure Secure LDAP and identify the different secure connections available
- Labs (configure an Active Directory Authentication server)
- Labs (configure single sing-on using STAS
- Labs (Authenticate users over a site to site VPN)
10:00-11:15 Module 8: Web Protection
- Choose the most appropriate type for web protection in different deployment scenarios
- Enable web filtering using the DPI engine or legacy web proxy
- Configure TLS inspection using the DLP engine or legacy web proxy
- Labs (Install the SSL CA certificate)
- Labs (Configure TLS inspection rules)
- Labs (Create a custom web policy for users)
11:15-11:30 Διάλειμμα
11:30-12:15 Module 9: Wireless
- Explain how Sophos Access Points are deployed and identify some common issues
- Configure RADIUS authentication
- Configure a mesh network
12:15-13:05 Module 10: Remote Access
- Configure Sophos Connect and manage the configuration using Sophos Connect Admin
- Configure an IPsec remote access VPN
- Configure an L2TP remote access VPN for mobile devices
- Labs (Sophos Connect)
13:05-14:25 Module 11: High Availability
- Explain what HA is and how it operates
- Demonstrate how to configure HA and explain the difference between quick and manual configuration
- List the prerequisites for high availability
- Perform troubleshooting steps andc heck the logs to ensure that HA is set up correctly.
- Explain the packet flow in high availability
- Demonstrate how to disable HA
- Labs (Create an Active-Passive cluster)
- Labs (Disable High Availability)
14:25-15:05 Διάλειμμα και Γεύμα
15:05-16-15 Public Cloud and Labs
- Deploy XG firewall in complex network enviroments
- Explain how XG firewall process traffic and use this information to inform the configuration
- Configure advanced networking and protection features
- Deploy XG firewall on public cloud infrastructure
- Labs (Put a service in debug mode to gather logs)
- Labs (Retrieving log files)
- Labs (Troubleshoot an issue from an imported configuration file)
- Labs (Deploy an XG Firewall on Azure (simulation)
16:15 (Εξετάσεις)
This three-day training program was designed and intended for experienced technical professionals who want to install, configure and support the XG Firewall in production environments and is the result of an in-depth study on the next generation firewall of Sophos. The program consists of presentations and practical workshops for the enhancement of teaching content. Due to the nature of the traditions and the varied experience of the trainees, open discussion is encouraged during the training.
Sophos XG Architect Training (Tuesday 16 June 2020– Thursday 18 June 2020)
(3 days Training)
Requirement
XG Firewall _ Certified Engineer course and delta modules up to version 18.0
Recommended Knowledge
- Knowledge of networking to a CompTIA N+ level
- Knowledge of IT security to a CompTIA S+ level
- Experience configuring network security devices
- Be able to troubleshoot and resolve issues in Windows networked environments
- Experience configuring and administering Linux/UNIX systems
Content
- Module 1: Deployment
- Module 2: Base firewall
- Module 3: Network Protection
- Module 4: Synchronized security
- Module 5: Web server Protection
- Module 6: Site to site connections
- Module 7: Authentications
- Module 8: Web Protection
- Module 9: Wireless
- Module 10: Remote Access
- Module 11: High Availability
- Module 12: Pulic Cloud
Certification
+ exam: Sophos XG Architect
Duration 3 days
Agenda
Trainer: Micheal Eleftheroglou
Day 1 Tuesday 16 June 2020
9:30-10:45 Module 1: Deployment and Lab
- Recall important information from Engineer courses
- Deployment modes supported by the XG Firewall
- Understand a range of scenarios where each deployment mode would commonly be used
- Use built-in tools to troubleshoot issues
- Labs
10:45-11:00 break
11:00-13:00 Module 2: Base Firewall
- Explain how the XG firewal can be accessed
- Understand the types fo interfaces that can be created
- Understand the benefits of Fast Path Technology
- Configure routing per firewall rule
- Understand best practice for ordering firewall rules
- Explain what Local NAT policy is and known how to configure it.
13:00-14:00 Lunch
14:00-16:00 Labs
- Activate the Sophos XG Firewalls
- Post installation Configuration
- Bridge interfaces
- Create a NAT rule to load balance access to servers
- Create a local NAT policy
- Configure routing using multiple WAN links
- Configure policy-based routing for an MPLS scenario
- Install Sophos Central
16:00-16:15 Break
16:15-17:15 Module 3:Network Protection and Lab
- Explain what IPS is and how traffic can be offloaded to Fastpath
- Demonstrate how to optimize workload y configuring IPS policies
- Examine advanced Intrusion Prevention and optimize policies
- Configure advanced DOS Protection rules
- Demonstrate how the strict policy can be used to protect networks
- Labs- Create Advanced DoS Rules
Day 2 Wednesday 17 June 2020
9:30-11:00 Module 4: Synchronized Security and Labs
- Explain how Security Heartbeat works
- Configure Synchronized Security
- Deploy Synchronized Security in discover and inline modes
- Understand the advantages and disadvantages of deploying
- Synchronizes Security in different scenarios
- Labs
- Configure source-Based Security
- Hearteat firewall rules
- Destination based Security Heartbeat
- Missing Security Heartbeat
- Lateral Movement Protection
11:00-11:15 Break
11:15-13:45 Module 5 Webserver Protection and Labs
- Explain how Websever Protection works
- Describe protection features for a web application
- Configure Web Server authentication
- Publish a web service using the Web Application Firewall
- Use the preconfigured templates to configure Web Server Protection for common purposes
- Configure SlowHTTP protection
- Labs (Web Application Firewall)
- Labs (Load balancing with Web Server Protection)
- Labs (Web Server Authentication and path-specific routing)
13:45-14:45 Break and Lunch
14:45-17:45 Module 6: Site to site connections and Labs
- Configure and deploy site to site VPNs in a wide range of environment
- Implement IPsec NATing and failover
- Check and modify route precedence
- Create RED tunnels between XG firewalls
- Understand when to use RED
- Labs ( Create an IPsec site to site VPN
- Labs ( Configure VPN network NATing )
- Labs (Configure VPN failover)
- Labs (Enable RED on the XG firewall)
- Labs (Create a RED tunnel between two XG Firewalls
- Labs (Configure routing for the RED tunnel)
- Labs (Configure route-based VPN)
Day 3 Thursday 18 June 2020
9:00-10:00 Module 7: Authentications and Labs
- Demonstrate how to configure and use RADIUS accounting
- Deploy STAS in large and complex environment
- Configure SATC and STAS together
- Configure Secure LDAP and identify the different secure connections available
- Labs (configure an Active Directory Authentication server)
- Labs (configure single sing-on using STAS
- Labs (Authenticate users over a site to site VPN)
10:00-11:15 Module 8: Web Protection
- Choose the most appropriate type for web protection in different deployment scenarios
- Enable web filtering using the DPI engine or legacy web proxy
- Configure TLS inspection using the DLP engine or legacy web proxy
- Labs (Install the SSL CA certificate)
- Labs (Configure TLS inspection rules)
- Labs (Create a custom web policy for users)
11:15-11:30 Break
11:30-12:15 Module 9: Wireless
- Explain how Sophos Access Points are deployed and identify some common issues
- Configure RADIUS authentication
- Configure a mesh network
12:15-13:05 Module 10:Remote Access
- Configure Sophos Connect and manage the configuration using Sophos Connect Admin
- Configure an IPsec remote access VPN
- Configure an L2TP remote access VPN for mobile devices
- Labs (Sophos Connect)
13:05-14:25 Module 11: High Availability
- Explain what HA is and how it operates
- Demonstrate how to configure HA and explain the difference between quick and manual configuration
- List the prerequisites for high availability
- Perform troubleshooting steps andc heck the logs to ensure that HA is set up correctly.
- Explain the packet flow in high availability
- Demonstrate how to disable HA
- Labs (Create an Active-Passive cluster)
- Labs (Disable High Availability)
14:25-15:05 Break – Lunch
15:05-16-15 Public Cloud and Labs
- Deploy XG firewall in complex network enviroments
- Explain how XG firewall process traffic and use this information to inform the configuration
- Configure advanced networking and protection features
- Deploy XG firewall on public cloud infrastructure
- Labs (Put a service in debug mode to gather logs)
- Labs (Retrieving log files)
- Labs (Troubleshoot an issue from an imported configuration file)
- Labs (Deploy an XG Firewall on Azure (simulation)
16:15 (Exams)