News
This three-day training program was designed and intended for experienced technical professionals who want to install, configure and support the XG Firewall in production environments and is the result of an in-depth study on the next generation firewall of Sophos. The program consists of presentations and practical workshops for the enhancement of teaching content. Due to the nature of the traditions and the varied experience of the trainees, open discussion is encouraged during the training.
Sophos XG Architect Training (Tuesday, November 3rd 2020– Thursday, November 5th 2020)
(3 days Training)
Requirement
XG Firewall _ Certified Engineer course and delta modules up to version 18.0
Recommended Knowledge
- Knowledge of networking to a CompTIA N+ level
- Knowledge of IT security to a CompTIA S+ level
- Experience configuring network security devices
- Be able to troubleshoot and resolve issues in Windows networked environments
- Experience configuring and administering Linux/UNIX systems
Content
- Module 1: Deployment
- Module 2: Base firewall
- Module 3: Network Protection
- Module 4: Synchronized security
- Module 5: Web server Protection
- Module 6: Site to site connections
- Module 7: Authentications
- Module 8: Web Protection
- Module 9: Wireless
- Module 10: Remote Access
- Module 11: High Availability
- Module 12: Pulic Cloud
Certification
+ exam: Sophos XG Architect
Duration 3 days
Agenda
Trainer: Micheal Eleftheroglou
Day 1 Tuesday, November 3rd, 2020
9:30-10:45 Module 1: Deployment and Lab
- Recall important information from Engineer courses
- Deployment modes supported by the XG Firewall
- Understand a range of scenarios where each deployment mode would commonly be used
- Use built-in tools to troubleshoot issues
- Labs
10:45-11:00 break
11:00-13:00 Module 2: Base Firewall
- Explain how the XG firewal can be accessed
- Understand the types fo interfaces that can be created
- Understand the benefits of Fast Path Technology
- Configure routing per firewall rule
- Understand best practice for ordering firewall rules
- Explain what Local NAT policy is and known how to configure it.
13:00-14:00 Lunch
14:00-16:00 Labs
- Activate the Sophos XG Firewalls
- Post installation Configuration
- Bridge interfaces
- Create a NAT rule to load balance access to servers
- Create a local NAT policy
- Configure routing using multiple WAN links
- Configure policy-based routing for an MPLS scenario
- Install Sophos Central
16:00-16:15 Break
16:15-17:15 Module 3:Network Protection and Lab
- Explain what IPS is and how traffic can be offloaded to Fastpath
- Demonstrate how to optimize workload y configuring IPS policies
- Examine advanced Intrusion Prevention and optimize policies
- Configure advanced DOS Protection rules
- Demonstrate how the strict policy can be used to protect networks
- Labs- Create Advanced DoS Rules
Day 2 Wednesday, November 4th, 2020
9:30-11:00 Module 4: Synchronized Security and Labs
- Explain how Security Heartbeat works
- Configure Synchronized Security
- Deploy Synchronized Security in discover and inline modes
- Understand the advantages and disadvantages of deploying
- Synchronizes Security in different scenarios
- Labs
- Configure source-Based Security
- Hearteat firewall rules
- Destination based Security Heartbeat
- Missing Security Heartbeat
- Lateral Movement Protection
11:00-11:15 Break
11:15-13:45 Module 5 Webserver Protection and Labs
- Explain how Websever Protection works
- Describe protection features for a web application
- Configure Web Server authentication
- Publish a web service using the Web Application Firewall
- Use the preconfigured templates to configure Web Server Protection for common purposes
- Configure SlowHTTP protection
- Labs (Web Application Firewall)
- Labs (Load balancing with Web Server Protection)
- Labs (Web Server Authentication and path-specific routing)
13:45-14:45 Break and Lunch
14:45-17:45 Module 6: Site to site connections and Labs
- Configure and deploy site to site VPNs in a wide range of environment
- Implement IPsec NATing and failover
- Check and modify route precedence
- Create RED tunnels between XG firewalls
- Understand when to use RED
- Labs ( Create an IPsec site to site VPN
- Labs ( Configure VPN network NATing )
- Labs (Configure VPN failover)
- Labs (Enable RED on the XG firewall)
- Labs (Create a RED tunnel between two XG Firewalls
- Labs (Configure routing for the RED tunnel)
- Labs (Configure route-based VPN)
Day 3 Thursday, November 5th, 2020
9:00-10:00 Module 7: Authentications and Labs
- Demonstrate how to configure and use RADIUS accounting
- Deploy STAS in large and complex environment
- Configure SATC and STAS together
- Configure Secure LDAP and identify the different secure connections available
- Labs (configure an Active Directory Authentication server)
- Labs (configure single sing-on using STAS
- Labs (Authenticate users over a site to site VPN)
10:00-11:15 Module 8: Web Protection
- Choose the most appropriate type for web protection in different deployment scenarios
- Enable web filtering using the DPI engine or legacy web proxy
- Configure TLS inspection using the DLP engine or legacy web proxy
- Labs (Install the SSL CA certificate)
- Labs (Configure TLS inspection rules)
- Labs (Create a custom web policy for users)
11:15-11:30 Break
11:30-12:15 Module 9: Wireless
- Explain how Sophos Access Points are deployed and identify some common issues
- Configure RADIUS authentication
- Configure a mesh network
12:15-13:05 Module 10:Remote Access
- Configure Sophos Connect and manage the configuration using Sophos Connect Admin
- Configure an IPsec remote access VPN
- Configure an L2TP remote access VPN for mobile devices
- Labs (Sophos Connect)
13:05-14:25 Module 11: High Availability
- Explain what HA is and how it operates
- Demonstrate how to configure HA and explain the difference between quick and manual configuration
- List the prerequisites for high availability
- Perform troubleshooting steps andc heck the logs to ensure that HA is set up correctly.
- Explain the packet flow in high availability
- Demonstrate how to disable HA
- Labs (Create an Active-Passive cluster)
- Labs (Disable High Availability)
14:25-15:05 Break – Lunch
15:05-16-15 Public Cloud and Labs
- Deploy XG firewall in complex network enviroments
- Explain how XG firewall process traffic and use this information to inform the configuration
- Configure advanced networking and protection features
- Deploy XG firewall on public cloud infrastructure
- Labs (Put a service in debug mode to gather logs)
- Labs (Retrieving log files)
- Labs (Troubleshoot an issue from an imported configuration file)
- Labs (Deploy an XG Firewall on Azure (simulation)
16:15 (Exams)
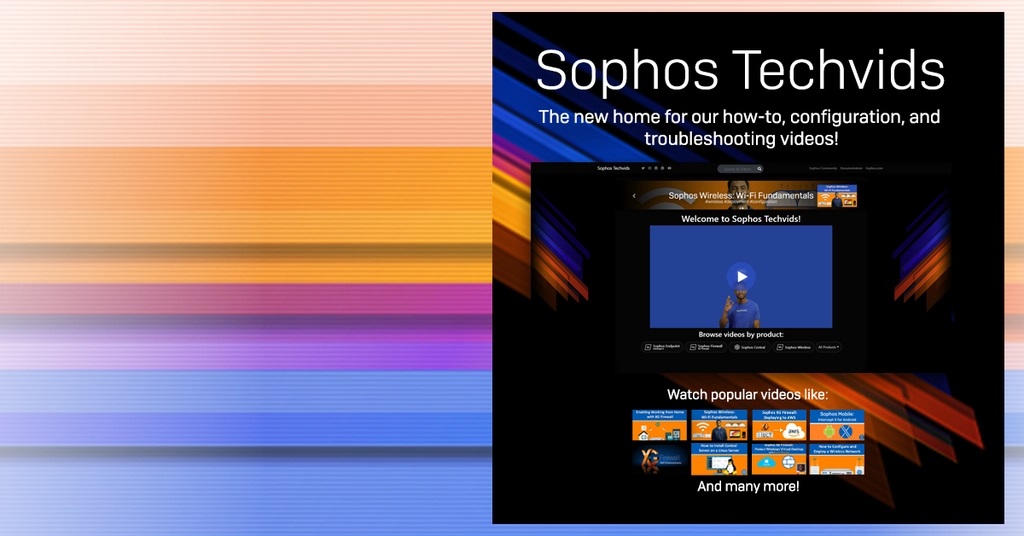
We’re excited to announce the launch of our new Sophos Techvids video hub!
This new platform features our extensive video library (90+ and counting!) of how-to, configuration, and troubleshooting videos, and improves the viewing experience by introducing new and interactive features such as in-video surveys and easy-to-use navigational elements.
Check out: https://techvids.sophos.com
Interactive in-video features
Feedback surveys: In-video prompts and surveys provide an easy way to share your feedback to help us improve future videos.
Interactive video navigation: Available on most of our current videos, the navigational top-bar is interactive. Click to skip directly to the section of the video you want to view.
Not sure where to start? Here are our most popular videos:
- XG Firewall (v18): How to configure SSL VPN remote access
- XG Firewall (v18): NAT enhancements
- Central Endpoint: How to run the Sophos ZAP Tool
- Central Endpoint: How to recover tamper protected windows devices
- Sophos Wireless: Wi-Fi fundamentals
Check out the entire collection at https://techvids.sophos.com today!
We are proud to announce that Sophos has been recognized as a Leader in the IDC MarketScape: Worldwide Mobile Threat Management Software 2020 Vendor Assessment.
The report provides an overview of mobile threat management (MTM) security solutions, also referred to as mobile threat defense (MTD) solutions – an increasingly important security market segment in today’s world, where an increasingly mobile workforce is doing more work on mobile devices than ever.
We believe this placement for Sophos Intercept X for Mobile is a testament to the strength of the Intercept X deep learning engine used across Sophos’ endpoint security range of products. Together with the flexibility of strong management and security capabilities in Sophos Central, the cloud-based management platform for all Sophos products lets organizations manage their mobile, endpoint, server, and network security in the same console.
Furthermore, we believe that this placement is due to Intercept X for Mobile’s seamless integration with the powerful endpoint management capabilities of Sophos Mobile, giving organizations the best of both worlds for mobile threat management (MTM) and unified endpoint management (UEM).
According to the report, “Sophos’ combination of MTM and UEM products is rare among MTM vendors and unique among vendors in this study.”
Intercept X for Mobile is available for Android, iOS, and Chrome OS and offers users world-class device, network, and app security, protecting against the latest mobile threats such as ransomware, network attacks, and exploits. According to the report, “This combination [of MTM and UEM] gives Sophos a strong advantage in situations where enterprises want a single vendor for both mobile device management and security enforcement.”
Sophos Intercept X for Mobile also integrates with a broad range of third-party platforms, including Microsoft Intune and other top UEM vendors – providing organizations with a flexible solution to protect against mobile threats within their unique existing security infrastructures.
To learn more about Intercept X for Mobile, head over to Sophos.com or download and try it for yourself at Google Play or the App Store.
Sophos XG Administration Training. This course, which will be held from 13 to 14 October 2020, 09:30-17:30 via Webex due to Covid-19, is designed for technical professionals who will be administering Sophos XG Firewall and provides the skills necessary to manage common day-to- day tasks. 
Objectives
On completion of this course, trainees will be able to:
- Recognize the main technical capabilities and how they protect against threats
- Complete common configuration tasks
- Configure the most commonly used features
- View and manage logs and reports
- Identify and use troubleshooting tools
Prerequisites
There are no prerequisites for this course; however, it is recommended you should:
- Be knowledge of networking to a CompTIA N+ level
- Be familiar with security best practices
- Experience configuring network security devices
Certification
To become a Sophos Certified Administrator, trainees must take and pass an online assessment. The assessment tests their knowledge of both the presented and practical content and contains 40 questions. The pass mark for the assessment is 80%, and is limited to 4 attempts.
Schedule
Training is expected to take two (2) days (24 hours ) to complete, of which approximately half will be spent on the practical exercises.
Content
The training contains 10 modules:
- Module 1 : XG Firewall Overview
- Module 2 : Getting Started with XG Firewall
- Module 3 : Network Protection
- Module 4 : Web Server Protection
- Module 5 : Site-to-Site Connections
- Module 6 : Authentication
- Module 7 : Web Protection and Application Control
- Module 8 : Email Protection
- Module 9 : Wireless Protection
- Module 10 : remote Access
- Module 11: Logging, Reporting and Troubleshooting
For many organizations, Macs are a regular fixture in their IT estates. Whether they comprise just a few devices or a significant proportion, Macs need the same levels of cybersecurity protection and visibility as their Windows cousins.
Which is why in addition to proven protection from the latest Mac threats, Endpoint Detection and Response (EDR) is now available for Mac users in addition to Windows and Linux.
Intercept X Advanced with EDR gives both IT admins and cybersecurity experts the power to answer critical IT operations and threat hunting questions, and then remotely take any necessary actions.
Upgrade your IT security operations
Maintaining proper IT hygiene can be a significant time investment for IT admins. Being able to identify which devices need attention and what action needs to be taken can add another layer of complexity.
With Sophos EDR, you can now do just that – quickly and easily. For example:
- Find devices with software vulnerabilities, unknown services running, or unauthorized browser extensions
- Identify devices that have unwanted software
- See if software has been deployed on devices, e.g. to make sure a rollout is complete
- Remotely access devices to dig deeper and take action, such as installing software, editing configuration files, and rebooting a device
Hunt and neutralize threats
Tracking down subtle, evasive threats requires a tool capable of detecting even the smallest indicators of compromise.
With this release, Sophos EDR is significantly enhancing its threat hunting capabilities. For example:
- Detect processes attempting to make a connection on non-standard ports
- Get granular detail on unexpected script executions
- Identify processes that have created files or modified configuration files
- Remotely access a device to deploy additional forensic tools, terminate suspect processes, and run scripts or programs
Introducing Live Discover and Live Response
The features that make solving all the important examples above possible are Live Discover and Live Response.
Live Discover allows you to examine your data for almost any question you can think of by searching across Mac devices with SQL queries. You can choose from a selection of out-of-the-box queries, which can be fully customized to pull the exact information that you need, both when performing IT security operations hygiene and threat hunting tasks. Data is stored on-disk for up to 90 days, meaning query response times are fast and efficient.
Live Response is a command line interface that can remotely access devices in order to perform further investigation or take appropriate action. For example:
- Rebooting a device pending updates
- Terminating suspicious processes
- Browsing the file system
- Editing configuration files
- Running scripts and programs
And it’s all done remotely, so it’s ideal in working situations where you may not have physical access to a device that needs attention.
Try the new features
Existing Intercept X Advanced with EDR customers will automatically see their Mac devices appearing for selection in Live Discover and Live Response by September 16.
Intercept X and Intercept X for Server customers that would like to try out EDR functionality can head to the Sophos Central console, select ‘Free Trials’ in the left-hand menu and choose the ‘Intercept X Advanced with EDR’ or ‘Intercept X Advanced for Server with EDR’ trial.
If you’re new to Sophos Central, start a no-obligation free trial of Intercept X Advanced with EDR today. You’ll get world class protection against the latest cybersecurity threats in addition to powerful EDR capabilities. Get started.
Live Discover and Live Response are available for Windows, Mac, and Linux devices.
Sophos is pleased to announce that CRN®, a brand of The Channel Company, has named Sophos in its 2020 Cloud Partner Program Guide. This annual list identifies industry-leading cloud technology vendors with innovative partner programs that empower and accelerate the growth of solution providers’ cloud initiatives.
In the last year, Sophos has expanded its capabilities in cloud security to protect the life of cloud infrastructure. Securing cloud infrastructure, cloud access, and configurations from the development cycle through to the ongoing security of live cloud services:
- All-in-one network security with XG Firewall and Sophos UTM
- Cloud workload protection with Intercept X Advanced for Server with EDR
- Detect insecure cloud deployments and compliance failures with Cloud Optix
- Automate pipeline security with Cloud Optix for secure DevOps
With accelerated adoption of public cloud environments presenting new data security challenges for the channel, the expansion of Sophos’ current capabilities in cloud security will enable partners to help their customers evolve and adapt to the changing threats and infrastructure landscape, and protect their data endpoints and networks irrespective of their environments.
Sophos’ Cloud Security Provider (CSP) program offers training, recognition, and financial incentives to help partners support their customers using or migrating to the public cloud. Sophos was the first next-gen security vendor to introduce a program specifically designed to help partners address this revenue growth opportunity and make the purchase and management of its products in Microsoft Azure, Amazon Web Services, and Google Cloud Platform channel-friendly.
In tandem with the CSP program, Sophos works together with AWS to support our partners on AWS Marketplace. The result is making Sophos public cloud services available through AWS Marketplace Consulting Partner Private Offer (CPPO), and Solution Provider Private Offer (SPPO) programs. This provides Sophos partners with exclusive pricing for Sophos AWS Marketplace security solutions and enables customers to draw down any AWS spend commitments (EDP) they have in place. It can also help them reach their spend commitment faster and potentially unlock deeper AWS discounts.
More information about Sophos’ Sophos’ Cloud Security Provider (CSP) program can be found online at www.sophos.com/csp.
The Cloud Partner Program Guide can be viewed online at www.crn.com/cloud-ppg. Additional coverage will be featured in the October issue of CRN Magazine.
Like many other companies, the MailStore team has spent several weeks working from home during the first half of the year, diligently developing our archiving solutions in the process. The team’s success is underlined by today’s release of MailStore Version 13, which we’d like to present to you now.
With several new features and numerous improvements, our new version will not only please admins but end users and business owners too. “We’ve divided these features into four main categories,” explains Björn Meyn, Product Manager at MailStore. “Firstly, we’ve improved our software’s interaction with the key cloud-based services Microsoft 365 and Google G Suite, ensuring much easier integration with these services. MailStore 13’s second focal point is supporting modern authentication through OAuth2 and OpenID Connect. Increased security and an improved user experience are our third and fourth main categories. Long-standing MailStore customers will know that we take both these topics very seriously and that they play a major role in absolutely every release.”
What Admins Can Expect From V13
MailStore 13 offers several new features and improvements that simplify the work of administrators. Here are some of the features that are particularly relevant for admins:
Improved Support of Cloud-Based Services and Modern Authentication
MailStore Server and the MailStore Service Provider Edition (SPE) now support OAuth2 and OpenID Connect, which significantly enhances MailStore’s integration in the cloud-based environments of Microsoft 365 and Google G Suite. This is good news for admins, as it not only enhances MailStore’s user friendliness in combination with these cloud-based services, but also increases security. Administrators benefit from standardized login policies by being able to use the same settings of their Microsoft 365 or Google G Suite clients for MailStore Server (including e.g. multi-factor authentication) without having to enable legacy authentication or the less secure application access. The new two-step login process emulates the login routines used in modern web applications, and MailStore no longer has to process the passwords of remote users during authentication.
In addition, the new dedicated Microsoft 365 archiving and export profiles make it easier for admins to configure profiles. Here too, the support of modern OAuth2 authentication not only improves security but also integration with Microsoft 365.

Network Share Management
MailStore Server admins now benefit from improved management of network share settings. These settings can now be managed more comfortably and securely via MailStore Server’s Service Configuration rather than via the startup script – e.g. when using a NAS.

Group Policies
Creating group policies for the MailStore Client and the MailStore Outlook Add-in is now easier than ever before: in the case of MailStore Server, the templates are now included in the installation, while in the SPE, they can be downloaded from the Client Access Server’s default page. In Version 13, these templates are available in all languages supported by MailStore.
Certificate Validation
A further improvement for MailStore Server and SPE administrators is the new certificate validation. This has been aligned with the validation process used in most of the important web browsers, enabling administrators to create and implement standardized security and certificate policies for all MailStore clients (MailStore Client, Outlook-Add-in and Web Access).
Encrypted Connections Only
In Version 13, the support of unencrypted connections to MailStore Server has been completely removed. So, administrators can rest assured that all MailStore Server installations permit only encrypted connections with the archive, which can be particularly useful for administrators managing several installations.
Let’s Encrypt™-Certificates
Administrators can now specify a port on which MailStore Server should listen out for the validation requirements of Let’s Encrypt™ TLS-Certificates, thus avoiding port collisions e.g. when MailStore Server is being run with other services on a computer or where only a limited number of IP addresses is available. This simplifies the use of Let’s Encrypt certificates.
MailStore Gateway
In Version 13, administrators can immediately see how many messages are in a MailStore Gateway mailbox. The new version also allows mailboxes still containing messages to be forcibly deleted. Furthermore, the Management Web Interface port can be modified if the standard port is being used by different applications, or the administrator wishes to turn it into a standard HTTPS Port 443.
How End Users Stand to Benefit From the New Version
MailStore 13 also offers several new and improved features aimed at simplifying archive handling for the end user. These include:
Modern Authentication
MailStore Server and SPE users can now login to MailStore using their customary Microsoft 365 or Google G Suite login details. So, rather than having to remember separate passwords for MailStore, all they need to do is use their Microsoft 365 or Google G Suite login data. This way they can also benefit from the additional security features of these cloud-based services when accessing their archive, such as multi-factor authentication.
Removal of Mobile Web Access
Customers who previously used Mobile Web Access for MailStore Server and the SPE are now able to use our modern and secure responsive Web Access. The legacy Mobile Web Access is no longer available in Version 13.
Client-Based Improvements
MailStore Server and SPE users benefit from a number of improvements when it comes to accessing and using the archive. The loading time of the responsive Web Access, in particular, has been significantly reduced. Various other minor improvements as well as comprehensive updating of all web components have been carried out for an even smoother search experience, particularly on mobile devices. The responsive display on mobile devices has also been improved significantly and features, among other things, a larger reading area. Meanwhile, the new “jump to folder” function allows you to switch directly to a desired folder by clicking on the folder path in the message view, which makes it even easier to find emails belonging to the same project or public folder. Time information is also displayed alongside the date in the MailStore Client’s message list.

Encrypted Connections Only
In Version 13, unencrypted connections to MailStore Server are no longer supported. This means that end users receive fewer warning messages when using a modern web browser to access the archive, while being able to rely on secure connections with MailStore Server. It’s also easier for end users to verify the security of a connection via their browser (e.g. via the lock symbol in Chrome’s address bar). This is particularly useful when using non-trusted connections, such as public wireless networks at airports.
Certificate Validation
In both MailStore Server and the SPE, this has been aligned with the certificate validation routine of the most important web browsers, enabling end users to identify breaches of security policies across all clients (MailStore Client, Outlook Add-in and Web Access).
Why Business Owners Can Look Forward to V13
It goes without saying that management also stands to benefit when email handling is simplified for administrators and end users. However, there are three more arguments in favor of MailStore 13 that are particularly relevant for business owners:
Improved Support of Cloud-Based Services and Modern Authentication
Business owners can trust in their investment in MailStore in the long-term, as a key part of our philosophy is to permanently support current industry standards and technologies – and that goes for important cloud-based services such as Microsoft 365 and Google G Suite.
Encrypted Connections and Standardized Certificate Validation
Business owners can also rest assured that MailStore will continually upgrade the security concept of its software in line with industry standards and security recommendations. That said, we always keep in mind the requirements and the IT infrastructure of small and medium-sized businesses. Our motto is “Security by Default”. This makes MailStore a reliable long-term choice when it comes to email archiving solutions.
GDPR-Certified
Just like the previous version, MailStore Server 13 has been rigorously audited by an independent data protection expert under General Data Protection Regulation (GDPR) rules. This certification verifies that MailStore Server – when used appropriately – meets the personal data processing requirements set out in the GDPR. Thanks to these regular and independent software audits, business owners can rest assured that MailStore Server can help them meet their obligations under the GDPR, for example by defining sophisticated retention policies. The official certificate on the audit results can be requested by our interested customers and partners via sales@mailstore.com. Registered MailStore partners can also download the certificate from our Partner Portal.
For managed service providers who offer their customers email archiving as a service using the MailStore Service Provider Edition, the following applies: MailStore SPE version 13 was also audited and certified according to the same criteria as MailStore Server in accordance with the EU’s GDPR. Registered MailStore partners can download the certificate from our Partner Portal or request it by e-mail from partners@mailstore.com.
And What About MailStore Home Users?
While the focus of Version 13 undeniably lies with our commercial products MailStore Server and the MailStore SPE, home users of our free archiving solution MailStore Home are not left empty-handed. In Version 13, MailStore Home also includes the practical “jump to folder” function, which allows emails from the same folder to be easily located by clicking on the folder path. End users can also be more creative with their passwords, which can now include spaces at the beginning and end. Other minor improvements and fixes result in an improved user experience for end users with MailStore Home.
Availability
Version 13 of MailStore Server and the MailStore SPE is now available to download from the company website at zero cost for all existing customers with valid Update & Support Service. Customers whose Update and Support Service has expired can renew via a paid upgrade and also update to the new version.
Interested companies might also want to download the version as part of a free 30-day trial.
Service providers interested in the MailStore SPE can register free of charge here to obtain all the relevant information including access to a free trial version.
MailStore Home can be downloaded from the Products page of our website.
For Gustavo Cornejo Lizama, Network Manager for a large public sector organization in Santiago, Chile, moving to a Sophos cybersecurity system has halved his team’s workload.
A team of twenty IT professionals supports the organization’s one thousand employees, however only three ‑ a security expert and two admins ‑ focus on cybersecurity.
To protect against malware and other threats, they use a Sophos cybersecurity system: a Sophos XG Firewall along with Sophos next-gen endpoint and server protection.
Everything is managed through the cloud-based Sophos Central administrative console.
Gustavo shared the impact the Sophos system had on their day-to-day cybersecurity operations.
Life before Sophos: entire work days spent monitoring cybersecurity
With their previous cybersecurity products, Gustavo and team faced a huge amount of daily administration and were slowed down by network issues.
In fact, they used to spend a full eight hours a day between them monitoring for security issues. This took up a significant proportion of their overall capacity, limiting the team’s ability to work on other tasks.
Life after Sophos: 50% reduction in admin time plus improved bandwidth
Since switching to the Sophos system, Gustavo and team have been able to reduce the time spent monitoring for security issues from eight hours to four hours a day.
Management is now simpler and easier, as they can control everything through the Sophos Central console. At the same time, they also experience far fewer network issues.
One feature which has been particularly beneficial is the ability to identify and control all applications on the network, which we call Synchronized App Control.
Sophos endpoint protection and XG Firewall constantly share information in real time, enabling the firewall to identify all apps, including those that would prefer to remain hidden.
Armed with this insight, Gustavo has been able to block social media and streaming, resulting in improved user productivity and bandwidth.
Favorite feature
A favorite feature of Gustavo and team is the ability to manage firewall, server, and endpoint security through a single cloud-based platform, giving them one-stop shopping for security management. Everything they need is at their fingertips with a single login.
Whether managing bandwidth, controlling apps, or dealing with general security issues, everything is handled through a unified console, cutting the time spent on these weighty tasks in half.
See it in action
Watch this demo video to see just how easy day-to-day security management is with a Sophos system.
To try the system for yourself, the easiest way is to start a free trial of one of our products.
And for anything else, or to discuss your own challenges, the Sophos team is here to help.
The COVID-19 era has ushered in a global organisational transition to remote working policies and highlighted the need to bolster protection against cyber-attacks and inadvertent data misuse at the hands of employees.
Top cybersecurity leaders outline key areas to facilitate successful remote workforce environments in this latest article by HelpNetSecurity, including HelpSystems CEO Kate Bolseth, who discusses the value of data classification in protecting vulnerable corporate assets.
“One thing must be clear” Kate Bolseth writes: “your entire management team needs to assist in establishing the right infrastructure in order to facilitate a successful remote workforce environment.
Before looking at any solutions, answer the following questions:
- How are my employees accessing data?
- How are they working?
- How can we minimize the risk of data breaches or inadvertent exposure of sensitive data?
- How do we discern what data is sensitive and needs to be protected?
The answers will inform organizational planning and facilitate employee engagement while removing potential security roadblocks that might thwart workforce productivity. These guidelines must be as fluid as the extraordinary circumstances we are facing without creating unforeseen exposure to risk.
When examining solutions, any option worth considering must be able to identify and classify sensitive personal data and critical corporate information assets. The deployment of enterprise-grade security is essential to protecting the virtual workforce from security breaches via personal computers as well as at-home Wi-Fi networks and routers.
Ultimately, it’s the flow of email that remains the biggest vulnerability for most organizations, so make sure your solution examines emails and files at the point of creation to identify personal data and apply proper protection while providing the link to broader data classification”.
We’re pleased to announce the addition of new reporting capabilities for Sophos Central Firewall Reporting (CFR). If you’re a customer of CFR Advanced, you’ll see new options to save, schedule, and export your favorite reports in Sophos Central, further extending your powerful custom reporting capabilities in the cloud.
What’s new and how to use it
- Save reports as templates – Central Firewall Reporting Advanced lets you save custom report templates. First, customize a report with the columns, filters, and chart type you want. Then save it in your template library for quick access whenever you need to run it.
- Schedule reports – Getting your favorite and custom reports is now even easier, as you can schedule them to be delivered your inbox or picked up in Sophos Central at your convenience. The scheduler allows you to set a frequency for your reports, including daily, weekly, and monthly options.
- Export your reports – Reports can now be exported in HTML, CSV, and (coming next month) PDF formats. As an additional bonus, the exported reports provide up to 100,000 records in a report, whereas the interactive reports in Central are limited to 10,000 records. Download your favorite report for offline viewing directly from Sophos Central or have it delivered to your inbox.

You have complete control over the scheduling frequency, report format, and delivery…

We will be covering Central Firewall Reporting in more detail in an upcoming article in our Making the Most of XG Firewall v18 series.
What you need
CFR Advanced is a new subscription license that offers additional firewall log data storage for historical reporting, and now adds these new features for saving, scheduling, and exporting reports.
CFR Advanced subscriptions are on a per-firewall basis, so each firewall you wish to report on in Sophos Central will require its own CFR Advanced license.
CFR Advanced licenses are purchased in 100GB storage quantities. You can use the storage estimation tool (at sophos.com/cfrsizing) to quickly determine the estimated storage required for your particular needs.
XG Firewall v18 is required to take advantage of Central Firewall Reporting. We encourage everyone to upgrade today to take advantage of all the great new performance, security, and feature enhancements.
Talk to your preferred Sophos partner today about adding CFR Advanced to your account so you can take full advantage of the rich customizable reporting options in Sophos Central.
New to Sophos Central Reporting?
If you’re new to Sophos Central Reporting, you can try it for free. Simply set up your firewalls for Sophos Central management and log into Sophos Central to give it a go.
You can learn more about what’s included with Sophos Central management and reporting on our website or download the PDF brochure. And if you’re new to Sophos XG Firewall, be sure to check out how you can add the best visibility, protection, and response to your network.
Security services bestow organizations with the security expertise they desperately need to combat ever-increasingly capable threat actors, as illustrated by the momentum in uptake of our Managed Threat Response service.
It has been less than 11 months since the launch of Sophos Managed Threat Response, our 24/7 human-led threat hunting, detection, and response service.
Our performance in that time is proof that our strategy of fusing technology, people, and process to act as an extension of organizations’ security and IT teams is a winning one. And we’re just getting started.
It gives me immense pride to announce that we have just surpassed 1,000 customers defended by Sophos MTR, underlining the profound need for security expertise across all verticals, industries, and sectors.
Against the chaotic backdrop of social and economic pressures brought on by the pandemic, those in the IT profession have continued to achieve the seemingly impossible: do more with less, in isolation.
Supporting remote workforces to achieve their goals both effectively and safely is a monumental task. Before this pandemic, there was already a global shortage of skilled cybersecurity professionals: an estimated workforce gap of 4.07 million. Securing an organization has never been a trivial matter, and the current climate has only worsened the impact of this shortage.
As a leader in cybersecurity across endpoint, network, and cloud, we are incredibly fortunate. Where most organizations struggle to both hire and retain security professionals, we are resilient to these struggles due to the sheer scale at which we operate.
When our staff walk over to the (albeit now virtual) water cooler, they talk security with other security people. When they’re in need of guidance, they can talk directly with industry veterans and experts within MTR, SophosLabs, and across our whole organization.
When they’re looking for a new challenge, that challenge already exists within our various research, development, and service groups, as well as within the diversity of our customer landscape. It’s an environment that attracts and hones the best operators in the industry, and that provides a virtuous circle of optimizations between technology and those human operators.
It is an honor to be afforded the trust and responsibility to assist in defending so many organizations across the globe in such a short space of time. This is an important milestone for us, one that enables us to protect more customers than ever in an ever-more effective fashion. But our achievement to date is just the beginning.
Joe Levy
Sophos Chief Technology Officer (CTO)
Ransomware continues to plague organizations, with over half of companies surveyed across 26 countries revealing that they were hit by ransomware in the last year.
Modern firewalls are highly effective at defending against ransomware attacks, but they need to be given the chance to do their job.
Our guide, Firewall Best Practices to Block Ransomware, explores how ransomware attacks work, how they can be stopped at the gateway, and best practices for configuring your firewall to optimize your protection.
Eight firewall best practices to block ransomware
To maximize the effectiveness of your anti-ransomware defenses, we recommend you:
- Start with the best protection, including a modern high-performance next-gen firewall with IPS, TLS inspection, zero-day sandboxing, and machine learning ransomware protection.
- Lock down RDP and other services with your firewall. Your firewall should be able to restrict access to VPN users and only allow sanctioned IP addresses.
- Reduce the surface area of attack as much as possible by thoroughly reviewing and revisiting all port-forwarding rules to eliminate any non-essential open ports. Where possible, use VPN to access resources on the internal network from outside rather than port-forwarding.
- Be sure to properly secure any open ports by applying suitable IPS protection to the rules governing that traffic.
- Enable TLS inspection with support for the latest TLS 1.3 standards on web traffic to ensure threats are not entering your network through encrypted traffic flows.
- Minimize the risk of lateral movement within the network by segmenting LANs into smaller, isolated zones or VLANs that are secured and connected together by the firewall. Be sure to apply suitable IPS policies to rules governing the traffic traversing these LAN segments to prevent exploits, worms, and bots from spreading between LAN segments.
- Automatically isolate infected systems. When an infection hits, it’s important that your IT security solution be able to quickly identify compromised systems and automatically isolate them until they can be cleaned up (such as with Sophos Synchronized Security).
- Use strong passwords and multi-factor authentication for your remote management and file sharing tools so that they’re not easily compromised by brute-force hacking tools.
These best practices and more are covered in greater detail our new Firewall Best Practices to Block Ransomware whitepaper.
Give your organization the best network protection with Sophos
Sophos XG Firewall gives you the best possible network protection against ransomware and other advanced threats, including cryptomining, bots, worms, hacks, breaches, and APTs.
- Industry-leading IPS stops attackers using the latest network exploits to infect your organization
- Deep learning technology identifies new and zero-day ransomware variants before they get on your network
- Sophos Sandstorm analyzes suspicious files in a safe cloud environment
XG Firewall also provides a simple, elegant way to manage your RDP, as well as support for the latest TLS 1.3 standards.
Visit Sophos.com/Firewall today to learn more and try it yourself!

In our recent survey of 5,000 IT Managers across 26 countries, 51% of respondents revealed that they were hit by ransomware in the last year. In 73% of those incidents, attackers succeeded in encrypting data. Furthermore, the average global cost to remediate these attacks was an eye-watering $761,106.
An endpoint protection solution is one of the most effective methods to protect against ransomware – but only if it’s properly configured.
Our new guide, Endpoint Protection Best Practices to Block Ransomware, explores how ransomware attacks work, how they can be stopped, and best practices for configuring your endpoint solution for the strongest protection possible.
Seven endpoint protection best practices to block ransomware
To maximize the effectiveness of your anti-ransomware defenses, we recommend:
- Turning on all policies and ensuring all features are enabled. It sounds obvious, but this is a surefire way that you’ll get the best protection out of your endpoint solution. Be sure to enable features that detect file-less attack techniques and ransomware behavior.
- Regularly reviewing your exclusions. Exclusions are sometimes leveraged to soften complaints from users who feel your protection solution is slowing down their systems. Malware that manages to make its way into excluded directories will likely succeed because it’s excluded from being checked.
- Enabling multi-factor authentication (MFA) within your security console. MFA provides an additional layer of security after the first factor, which is often a password.
- Ensuring every endpoint is protected and up to date. Checking your devices regularly to know if they’re protected and up to date is a quick way to ensure optimum protection.
- Maintaining good IT hygiene. Not only does this mitigate your cybersecurity risk, but it can save you a lot of time when it comes to remediating potential incidents in the future.
- Hunting for active adversaries on your network. Malicious actors are more cunning than ever. Take advantage of endpoint detection and response (EDR) technologies in your endpoint solution to identify advanced threats and active adversaries, and take swift action to stop threats.
- Closing the gap with human intervention. Hackers typically spend time exploring your network before deploying ransomware. The best way to detect this malicious activity is to combine human expertise with advanced endpoint technology.
These best practices and more are covered in greater detail our new Endpoint Protection Best Practices to Block Ransomware whitepaper.
How Sophos keeps you protected from ransomware
Sophos Intercept X includes all the features you need to help protect your organization from advanced ransomware attacks like Ryuk, Sodinokibi, Maze, and Ragnar Locker.
- Deep learning identifies and blocks known and unknown ransomware variants
- Anti-exploit technology stops the delivery and installation of ransomware
- CryptoGuard identifies and rolls back the unauthorized encryption of files
Sophos EDR, available for endpoints and servers, lets you hunt for threats and maintain good IT operations hygiene across your entire estate.
If you want to add human expertise to your layered security strategy, Sophos Managed Threat Response (MTR) proactively hunts for and neutralizes threats on your behalf.
Remote Desktop Protocol (RDP), while a legitimate tool, is also a common ingress point for attackers looking to break into an organization. A recent Sophos survey found that in 9% of ransomware attacks, RDP was the method used to gain entry.
Fortunately, Intercept X Advanced with EDR makes it easy to identify devices that have open RDP connections and remotely shut them down, all from a single management console.
Sophos EDR includes Live Discover, which leverages a collection of pre-written, fully customizable SQL queries to answer IT operations and threat hunting questions.
To begin, we select which devices we want to check.

There are a variety of different categories to choose from depending on your needs. We have a couple of options for RDP. Identifying devices with running processes that have active RDP connections or finding devices that have RDP enabled.

In this case we want to do the latter, so we’re going to create a short query for the task. A quick search of the Live Discover query sharing forum gives us exactly what we need. A couple of clicks later and we have our query ready to run (we also had the option to select a pre-written query to identify devices with active RDP connections).

The query identifies a device that has RDP enabled. From the same console, we launch a Live Response remote terminal session to the device and use the command line interface to disable RDP.

It’s that easy to detect RDP and disable it across your entire endpoint and server estates. To learn more about Sophos EDR head over to Sophos.com or to try it for yourself, you can start a no-obligation 30-day trial.
We’re excited to announce that we have launched the new Sophos Support Portal, which makes it much easier for you to track and manage all your support cases.
You can now visit support.sophos.com to access and create support cases.
What’s new
- Create and manage your own support cases
- Your Sophos partner can manage cases on your behalf
- More interactive ways to update and track a case
- View and manage cases created by others on your team
- Chat in real time with our support engineers
- Find suitable solutions in our knowledgebase
- Manage your team’s access to the Support Portal
How to get started
Please note that the process to create a support case has now changed. From now on, you will need to log into the new Sophos Support Portal with your SophosID. If you do not have a SophosID yet, you’ll be able to create one as part of the registration process. Registration is quick and easy. You can find more information on how to register on our Community page.
Once logged in, you can conveniently create, manage, and follow cases in the Support Portal.
You can also still call in to our support centers to open a case. You can find our phone numbers on the support pages.
Migration of existing cases
Active cases have been migrated to the new Support Portal. If you have an open case with us, you should have received an email with your new case number and further instructions. Please don’t worry that your old case has been closed, as that is just a result of the migration to the new portal.
Your Sophos partner can file cases on your behalf
Your Sophos partner is now able to manage cases on your behalf and escalate cases to support management. This Community page includes a link to the knowledgebase article that explains how you can give your partner access to view your assets and create cases on your behalf. You will still be able to log in and track cases that your partner is managing for you.
Visit our Community page for a demo and the latest information or if you need any help.
We often get asked about the inner workings of Netsparker’s vulnerability scanning engine. People familiar with network and virus scanners also ask what vulnerability databases we use and how often we update them. In reality, it’s all a lot more interesting than ticking boxes on a list of known issues. Time to set the record straight about how a cutting-edge web vulnerability scanner works.
Two Sources of Vulnerability Information
When most people hear the word “scanner”, they think of software that looks for known risks. This is generally what virus scanners and network scanners do: check targets against a list of known issues, such as (respectively) malware signatures and CVE vulnerability reports. So when customers see how effective Netsparker is, their first question is often: “What vulnerability database do you use?” Well, the short answer is: “None, mostly.” The full answer is that Netsparker is an advanced heuristic scanner that also checks for known web application vulnerabilities – but let’s break this down a bit.
The Mundane Part: CVEs
The idea of relying on a vulnerability database comes from the systems and network security world, where a software or hardware bug is discovered, publicly disclosed, and added to a vulnerability database such as CVE. Network scanners, for example, work by finding such known issues in target systems. To fix the vulnerability, you simply patch or update the affected component.
Some CVEs also apply to web applications. These are bugs in widely-used products that need to be patched to avoid attacks. As one part of its scanning process, Netsparker checks for such issues based on the CVE registry and other vulnerability databases, so scans also cover vulnerabilities such as Heartbleed (CVE-2014-0160) or POODLE (CVE-2014-3566). In fact, the Netsparker security advisory program actively contributes to finding bugs in open-source packages by scanning them for vulnerabilities during engine testing. To learn how our security researchers do this, see our article on vulnerability disclosures.
Although an important part of overall security, checking for known issues is relatively easy and not terribly exciting. Things get interesting when you have to check for unknown issues – and this is when you find out how effective your web application security solution truly is.
The Really Clever Part: Heuristics
The vast majority of web application vulnerabilities are brand new issues that were introduced in new code in custom-built applications – so how are you supposed to know about them? This is the main difference between web application security testing and signature-based security checks: web vulnerability scanning is primarily about finding new vulnerabilities resulting from underlying weaknesses categorized in the CWE system. To find previously unknown issues, Netsparker uses a cutting-edge heuristic scanning engine that probes websites and applications for vulnerabilities just like a penetration tester would.
Netsparker uses a variety of advanced heuristic techniques to find all entry points in web applications and test them for vulnerabilities. This includes automatic URL rewriting to provide maximum scan coverage, automated fuzzing to generate unexpected inputs that may reveal a weakness, and proprietary Proof-Based Scanning™ technology to safely test weaknesses and provide proof that the vulnerability is real.
Because web vulnerability scanners don’t rely on signatures, their effectiveness is highly dependent on the quality and maturity of the underlying heuristic scanning engine. If the scanning engine is too eager to flag suspicious responses as signs of vulnerabilities, it will flood the user with false positives. If it is too cautious or simply not advanced enough, it will miss real vulnerabilities or even bypass whole pages, for example because it can’t deal with authentication. As an industry veteran and technology leader, Netsparker knows how to strike the right balance.
Get the Best of Both Worlds
The purpose of a web application security solution is to help the user improve security more efficiently than with manual testing alone. This goes way beyond vulnerability databases and even beyond scanning itself. To get measurable security improvements, you need a holistic view of web application security that pulls together accurate information from all relevant sources and applies it through effective automation.
Netsparker combines high-quality heuristic results from its industry-leading vulnerability scanning engine with information about known issues listed in vulnerability databases. All these vulnerability results are complemented by asset discovery and crawling information, warnings about outdated web technologies, detailed vulnerability descriptions complete with suggested remedies, best-practice recommendations, compliance reports, and more. This gives you a complete picture of what you need to fix in your web environment, so you can start getting real value from Netsparker in a matter of days.
As cybercriminals continue to take advantage of the public cloud in their attacks, Sophos commissioned an independent survey of 3,521 IT managers across 26 countries* to reveal the reality of cloud security in 2020.
The 2020 cloud security reality
The survey provides fresh new insight into the cybersecurity experiences of organizations using the public cloud, including:

- Almost three-quarters of organizations hosting data or workloads in the public cloud experienced a security incident in the last year. Seventy percent of organizations reported they were hit by malware, ransomware, data theft, account compromise attempts, or cryptojacking in the last year.
- Data loss/leakage is the number one concern for organizations. Data loss and leakage topped our list as the biggest security concern, with 44% of organizations seeing data loss as one of their top three focus areas.
- Ninety-six percent of organizations are concerned about their current level of cloud security. Data loss, detection and response, and multi-cloud management top the list of the biggest concerns among organizations.
- Multi-cloud organizations reported more security incidents in the last 12 months. Seventy-three percent of the organizations surveyed were using two or more public cloud providers and reported more security incidents as those using a single platform.
- European organizations may have the General Data Protection Regulation (GDPR) to thank for the lowest attack rates of all regions. The GDPR guidelines’ focus on data protection, and well-publicized ransomware attacks have likely led to these lucrative targets becoming harder for cybercriminals to compromise in Europe.
- Only one in four organizations see lack of staff expertise as a top concern despite the number of cyberattacks reported in the survey. When it comes to hardening security postures in the cloud, the skills needed to create good designs, develop clear use cases, and leverage third-party services for platform tools are crucial but underappreciated.
- Two-thirds of organizations leave back doors open to attackers. Security gaps in misconfigurations were exploited in 66% of attacks, while 33% of attacks used stolen credentials to get into cloud provider accounts.
For the details behind these headlines, and to see how your country stacks up, read The State of Cloud Security 2020 report.
Secure the cloud with Sophos
However you’re using the public cloud, Sophos can help you keep it secure.
- Secure all your cloud resources. Get a complete inventory of multi-cloud environments (virtual machines, storage, containers, IAM Users etc.). Reveal insecure deployments, suspicious access, and sudden spikes in cloud spend. Learn more
- Secure your cloud workloads. Protect virtual machines, the virtual desktops running on those machines from the latest threats, including ransomware, fileless attacks, and server-specific malware. Learn more
- Protect the network edge. Secure inbound and outbound traffic to your virtual network, virtual desktop environments, and provides secure remote access to private applications running in the cloud. Learn more
For more information and to discuss your cloud security needs, request a call back from one of security experts.
* Australia, Belgium, Brazil, Canada, China, Colombia, Czech Republic, France, Germany, India, Italy, Japan, Malaysia, Mexico, Netherlands, Nigeria, Philippines, Poland, Singapore, South Africa, Spain, Sweden, Turkey, UAE, United Kingdom, United States
ProLock ransomware emerged on the threat scene in March, a retooled and rebranded version of PwndLocker.
As SophosLabs reveals in its detailed analysis, while ProLock ransomware gives you the first eight kilobytes of decryption for free, it can still cause significant business disruption and economic damage.
Protect against ProLock with Sophos Intercept X
Intercept X gives you multiple layers of protection against ProLock, keeping the data on your endpoints and servers safe:
- CryptoGuard identifies and rolls back the unauthorized encryption of files. In fact, Sophos first detected ProLock when CryptoGuard caught it on a customer network
- Deep learning identifies and blocks ProLock without signatures
- Signatures block variants of ProLock either as Troj/Agent-BEKP or Malware/Generic-S
If you’re running Sophos Intercept X you can relax knowing that you are automatically protected against ProLock, as all three of the above features are enabled by default in our recommended settings.
(If you’re not yet running Intercept X and want to give it a try, visit the web page to learn more and start a no-obligation free trial.)
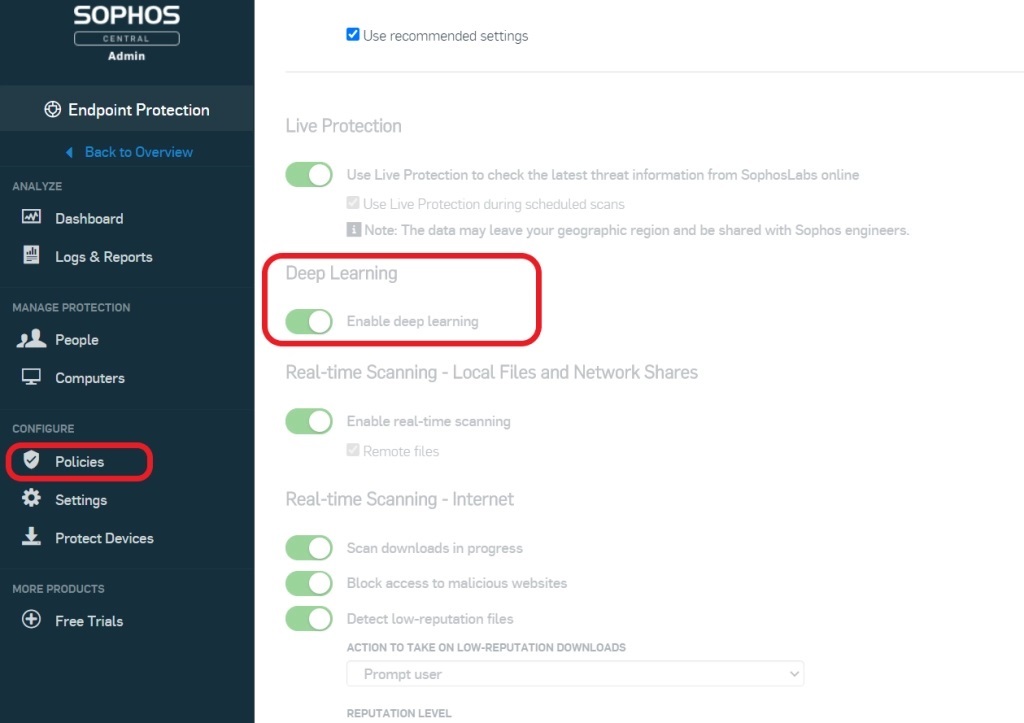
To check that you have CryptoGuard and Deep Learning enabled:
- Open your Sophos Central Admin console and select Endpoint Protection in the left-hand menu
- Select Policies
- Review the list of threat protection policies already created
- Toggle the buttons to make any necessary changes
Endpoint protection and firewall best practices to block ransomware
51% of IT managers surveyed for our recent State of Ransomware 2020 report said their organization was hit by ransomware last year, and that cybercriminals succeeded in encrypting data in 73% of incidents.
With stats like these it’s worth taking the time to ensure all your ransomware defenses are up-to-date.
The earliest detection of ProLock by Sophos was traced to a compromised server, most likely through an exploit of a Remote Desktop Protocol (RDP).
Putting RDP access behind a virtual private network and using multi-factor authentication for remote access are just a couple of the best practices we recommend to reduce your ransomware risk.
For additional best practices, take a look at our guides Endpoint Protection Best Practices to Block Ransomware and Firewall Best Practices to Block Ransomware.
We are excited to announce that Intercept X for Server Advanced with EDR has been enhanced with powerful cloud visibility features from Cloud Optix.
In addition to even more detail on your AWS, Azure, and GCP cloud workloads, this integration gives customers critical insights into their wider cloud environments, including security groups, hosts, shared storage, databases, serverless, containers, and more.
See your complete cloud environment
The dynamic nature of cloud environments – with assets being spun up and down as and when necessary to meet changing demands – can make security and compliance assessments time-consuming. In many cases, you’ll need to log into multiple consoles and manually collate information to get a full picture.
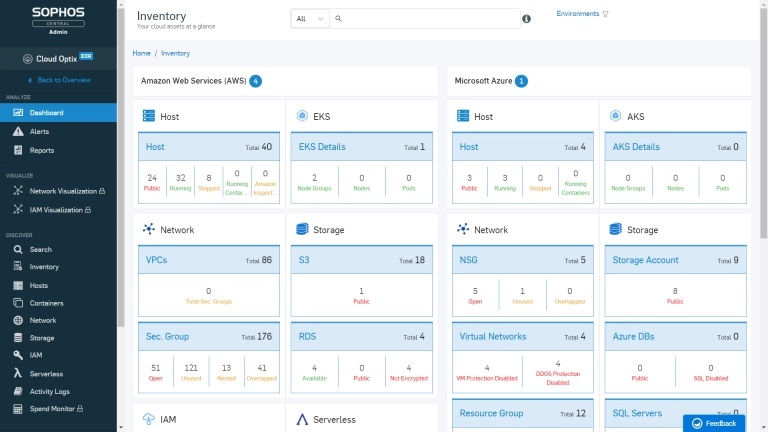
With Sophos, it’s easy. You get details about your entire cloud infrastructure across different public cloud providers on one screen, in a single management console. You can dive directly into assets to get more detail about your asset inventory and cloud security posture.
Secure your complete cloud environment
Automated scans will detect any insecure deployments, with guided recommendations about how to fix potential issues. Additionally, guardrails can be deployed to lock down configurations, ensuring that they can’t be accidentally or maliciously tampered with and left in an unsafe state.
Artificial intelligence tracks normal behavior patterns, looking for any suspicious activity such as anomalous traffic patterns or unusual login attempts to cloud accounts. Issues are then flagged and prioritized by risk level if they require manual intervention.
Here’s the full list of what’s available:
- Cloud asset inventory – see a detailed inventory of your entire cloud infrastructure (e.g. cloud hosts, serverless functions, S3 buckets, databases, and cloud workloads), eliminating the need for time-consuming manual collation
- Access and traffic anomaly detection – unusual login attempts and suspicious traffic patterns are automatically detected and blocked or flagged to the admin as appropriate
- Security scans – daily and on-demand scans monitor your cloud environment to ensure its on-going security. Issues are automatically resolved where possible, with admin notification if manual intervention is required
- Configuration guardrails – stop accidental or malicious tampering with configurations that could negatively impact security posture
- Compliance policies – ensure that your cloud environment conforms to Center for Internet Security (CIS) best practices, helping keep your security posture at its best
- Alert management integrations – receive email notifications when manual intervention is required
Powerful visibility and protection for every setup
This exciting new cloud functionality is available to all Intercept X Advanced for Server with EDR customers at no additional cost. Log into your Sophos Central console, select Cloud Optix, and you can get started right away.
Current customers using Sophos Central that would like to try out this new functionality – in addition to the recently released EDR IT operations and threat hunting capabilities – can start a trial from within the Sophos Central console.
If you don’t have a Sophos Central account, you can register for a trial on Sophos.com.
Intercept X Advanced for Server with EDR and Intercept X Advanced with EDR give organizations unparalleled visibility and protection across their cloud, on-premises, and virtual estates. Cloud Optix shines a spotlight on complete cloud environments, showing what’s there, what needs securing, and making sure that everything stays safe and secure.
Most privileged access management solutions just focus on passwords. BeyondTrust is different. Our innovative Universal Privilege Management approach to cyber security secures every user, asset, and session across your enterprise. Deployed as SaaS or on-premises, BeyondTrust’s Universal Privilege Management approach simplifies deployments, reduces costs, improves usability, and reduces privilege risks.
Go Beyond Passwords
Passwords are important. That’s why you can audit and manage every privileged account with BeyondTrust. This includes everything from privileged user passwords, app-to-app credentials, service accounts, DevOps secrets, and more.
But passwords are just the beginning. The BeyondTrust platform integrates privileged password security with endpoint and remote access security, drastically reducing your attack surface and windows of exposure. This is Universal Privilege Management.
Productivity, Not Friction
Privileged users handle critical tasks that keep your business running. The last thing you want to do is slow down legitimate business activity with annoying security measures.
BeyondTrust is non-intrusive to users. Our software helps power some of the most efficient organizations on the planet. Centralized reporting and management, integrations with your existing systems, and automated privilege management enable security that’s virtually invisible to users.
Accelerated Time to Value
Our customers get more than software. They get 30+ years of accumulated security expertise and best practices productized in software form.
Built-in templates and workflows let you see value on day one. Flexible deployment options, including cloud deployments and virtual appliances, let you start right away. Our customers report fast user adoption, which rapidly reduces your risk.
The BeyondTrust Advantage
BeyondTrust serves more organizations than any other Privileged Access Management vendor. More than 20,000 customers, including 70% of the Fortune 500, trust us to improve cyber security and efficiency. We’ve helped more customers deploy in the cloud than anyone else. And customers rate our support organization with 96% satisfaction.