News
The Forrester Wave is an evaluation of vendors in the software, hardware, or services markets, driven by the analysis of data collected from the marketplace and the experience of participating analysts. BeyondTrust was among the 10 most significant Privileged Identity Management vendors that Forrester invited to participate in its Q4 2020 Forrester Wave evaluation.

BeyondTrust received the highest scores possible in the following criteria:
- Credential and Secrets Management
- Session Monitoring and Recording
- Remote Access and Support
- Deployment
- Insights and Reporting
Source: BeyondTrust
December 2, Athens, Greece – NSS, an international value-added distributor of leading cutting-edge IT solutions, today announced its partnership with Datto, the leading global provider of cloud-based software and technology solutions purpose-built for delivery by managed service providers (MSPs). This strategic distribution agreement brings Datto’s enterprise-grade technology to small and medium enterprises in Southeast Europe.
Founded in 2007 in the U.S., Datto is a global leader in business continuity and disaster recovery, business management, and networking solutions. The presence of Datto’s technology in Southeast Europe will enable IT solution providers and resellers to continue to grow and address the IT needs of SMEs. With this agreement, Datto’s cloud-based software and technology solutions will be available to MSPs by NSS. Datto’s solutions are built to integrate with “best of breed” tools, software, and applications that MSPs use most.
“Datto is expanding in Europe and sees a great opportunity to bring our critical technology, tools, and expertise to businesses in Greece, Cyprus, Malta and Bulgaria,” said James Vyvyan, VP Sales EMEA, Datto. “We’ve chosen a trusted go-to-market partner in NSS, and look forward to working together to deliver IT solutions through MSPs in an increasingly complex IT environment.”
“As a leader in cloud-based software and technology solutions, we are thrilled to add Datto’s offering to our portfolio and distribute these critical solutions,” said George F. Kapaniris, Executive Director, NSS. “We look forward to helping MSPs protect their end customers and grow their businesses”.
NSS will distribute Datto’s solutions in the markets of Greece, Cyprus, Malta and Bulgaria. By offering Datto’s comprehensive and unique set of cloud-based solutions, NSS is expanding its portfolio to meet the increasing IT requirements and security needs of businesses during the age of digital transformation.
To find out more please visit: https://www.nss.gr/en/products/systems/datto/

About NSS
NSS is an international Value Added Distributor of Affordable Cutting Edge IT solutions, covering technology areas that include information security, network optimization, communications and infrastructure systems. NSS has strategic partnerships with superior vendors offering products & services with leading technologies that place the company ahead of the competition in today’s crowded market. NSS products can be acquired through a selected channel of resellers in Greece, Cyprus, Malta, the Balkan and Adriatic Countries.
Αθήνα, 2 Δεκεμβρίου 2020 – Η NSS, Διεθνής Διανομέας Προστιθέμενης Αξίας (Value-Added Distributor / VAD) λύσεων πληροφορικής υψηλής τεχνολογίας ανακοίνωσε τη συνεργασία της με την Datto, παγκόσμια ηγέτιδα στην παροχή cloud-based λογισμικού και εξειδικευμένων τεχνολογικών λύσεων που απευθύνονται σε MSPs (Managed Service Providers). Αυτή η στρατηγική συμφωνία διανομής φέρνει τις τεχνολογίες επιχειρησιακής κλάσης της Datto σε μικρές και μεσαίες επιχειρήσεις στη Νοτιοανατολική Ευρώπη.
Η Datto, που ιδρύθηκε το 2007 στις Η.Π.Α. αποτελεί παγκόσμιο ηγέτη στους τομείς της Διαχείρισης Επιχειρησιακών Διαδικασιών (Business Management), την Αποκατάσταση από Καταστροφή (Disaster Recovery), την Επιχειρησιακή Συνέχεια (Unified Continuity) και τις Λύσεις Δικτύωσης. Η παρουσία των τεχνολογιών της Datto στη Νοτιοανατολική Ευρώπη θα επιτρέψει στους παρόχους λύσεων πληροφορικής και στους μεταπωλητές να συνεχίσουν να αναπτύσσονται και να ανταποκρίνονται στις ανάγκες πληροφορικής των μικρομεσαίων επιχειρήσεων. Με αυτή τη συμφωνία, το cloud-based λογισμικό και οι τεχνολογικές λύσεις της Datto θα είναι διαθέσιμες στους MSPs από την NSS. Οι λύσεις της Datto σχεδιάστηκαν για να συνδυάζονται επίσης άψογα με τα πιο διαδεδομένα εργαλεία, το λογισμικό και τις εφαρμογές που χρησιμοποιούν οι MSPs σήμερα στην αγορά.
«Η Datto επεκτείνεται στην Ευρώπη και έχουμε μπροστά μας μια μεγάλη ευκαιρία να φέρουμε την τα τεχνολογικά εργαλεία υψηλής απόδοσης και την τεχνογνωσία που διαθέτουμε σε επιχειρήσεις στην Ελλάδα, την Κύπρο, τη Μάλτα και τη Βουλγαρία» δήλωσε ο James Vyvyan, Αντιπρόεδρος Πωλήσεων EMEA της Datto. «Επιλέξαμε την NSS, έναν αξιόπιστο εταίρο για τη μετάβαση μας στην αγορά και ανυπομονούμε να συνεργαστούμε για την παροχή λύσεων πληροφορικής μέσω των MSPs στο ολοένα και πιο περίπλοκο περιβάλλον πληροφορικής σήμερα» συμπλήρωσε ο κ. James Vyvyan.
«Ως ηγέτης στο λογισμικό που βασίζεται στο cloud και τις τεχνολογικές λύσεις που έχουν δημιουργηθεί ειδικά για τους παρόχους διαχειριζόμενων υπηρεσιών (MSPs), είμαστε ενθουσιασμένοι οι εξαιρετικές λύσεις της Datto προστίθενται στο χαρτοφυλάκιο των προϊόντων που διανέμουμε», δήλωσε ο Γιώργος Καπανίρης, Εκτελεστικός διευθυντής της NSS. «Ανυπομονούμε να βοηθήσουμε τους MSPs να προστατεύσουν τους πελάτες τους και να αναπτύξουν τις επιχειρήσεις τους».
Η NSS θα διανέμει τις λύσεις της Datto στις αγορές της Ελλάδας, της Κύπρου, της Μάλτας και της Βουλγαρίας. Προσφέροντας το ολοκληρωμένο και μοναδικό σύνολο τεχνολογικών λύσεων που βασίζονται στο σύννεφο της Datto, η NSS επεκτείνει το χαρτοφυλάκιο της για να ανταποκριθεί στις ολοένα αυξανόμενες απαιτήσεις πληροφορικής και ασφάλειας των επιχειρήσεων στην εποχή του ψηφιακού μετασχηματισμού.
Μάθετε περισσότερα στην ιστοσελίδα της NSS: https://www.nss.gr/el/products/systems/datto/

Σχετικά με την NSS:
Η NSS είναι ένας διεθνής διανομέας λύσεων πληροφορικής υψηλής τεχνολογίας, που καλύπτει τεχνολογικούς τομείς όπως η ασφάλεια πληροφοριών, η βελτιστοποίηση των δικτυακών υποδομών, οι επικοινωνίες και τα συστήματα υποδομών. Η NSS έχει συνάψει στρατηγικές συνεργασίες με κορυφαίους προμηθευτές που προσφέρουν τεχνολογίες αιχμής και τοποθετούν την εταιρεία μπροστά από τον ανταγωνισμό στη σημερινή αγορά. Τα προϊόντα που προσφέρει η NSS είναι διαθέσιμα μέσω ενός επιλεγμένου καναλιού μεταπωλητών στην Ελλάδα, την Κύπρο, τη Μάλτα, στα Βαλκάνια και στις χώρες της Αδριατικής.
In a move that we believe highlights our ongoing commitment to innovation and market leadership, Gartner has named Sophos as one of only two Visionaries among 18 vendors included in the 2020 Magic Quadrant for Network Firewalls.
A defining strength of Sophos XG Firewall is Synchronized Security, our XDR-style integration that enables our endpoint, firewall, and other next-generation security solutions to share information and automate detection and response in ways that isolated point solutions cannot. Customers say that they would need to double their security headcount to maintain the same level of protection without Synchronized Security. They also tell us that they experience fewer security incidents and can identify and respond quicker to issues that do occur.
Extended Detection and Response (XDR) capabilities that reduce the complexity of security configuration, threat detection, and response have emerged as one of the most critical needs as security and risk management leaders struggle with too many security tools from different vendors with little integration of data and a lack of orchestrated response.
“The primary value propositions of an XDR product are to improve security operations productivity and enhance detection and response capabilities by including more security components into a unified whole that offers multiple streams of telemetry, presenting options for multiple forms of detection and concurrently enabling multiple methods of response” Gartner, “Innovation Insight for Extended Detection and Response” (2020).
We believe Gartner’s recognition demonstrates our innovation in XDR and clear understanding of what security leaders need to achieve greater visibility, easier management, and better threat detection and response across their entire ecosystem.
Staying ahead of the evolving threat landscape
Advanced adversaries continually change and escalate their tactics, techniques, and procedures (TTPs) to circumvent legacy security controls, prolong or evade detection, and execute successful attacks. In 2020, in particular, adversary groups and malware strains have evolved, as evidenced with Maze, WastedLocker and other modern ransomware attacks.
Keeping pace with sophisticated attackers requires constant innovation. Earlier this year, we introduced a new “Xstream” architecture for Sophos XG Firewall, ushering in a host of new and enhanced features, including:
- Inspection of TLS 1.3 to detect cloaked malware: New port-agnostic TLS engine doubles crypto operation performance over previous XG versions
- Optimized critical application performance: New FastPath policy controls accelerate – up to wire speed – the performance of SD-WAN applications and traffic, including Voice over IP, SaaS, and others
- Threat analysis with SophosLabs intelligence: Protection against zero-day threats and emerging ransomware variants with multiple best-in-class machine learning models and unmatched insights into suspicious files entering your network.
- Adaptive traffic scanning: The newly enhanced Deep Packet Inspection (DPI) engine dynamically risk-assesses traffic streams and matches them to the appropriate threat scanning level, enhancing throughput by up to 33% across most network environments
- Comprehensive cloud management and reporting in Sophos Central: Centralized management and reporting capabilities in Sophos Central provide customers with group firewall management and flexible cloud reporting across an entire estate without additional charge
Visit our website for more information on XG Firewall and the Xstream architecture.
In the world of IT security in general, 2020 so far could be called the year of ransomware. The news is full of reports of new ransomware attacks and based on the trends so far, we can expect the situation to keep getting worse.
Many organizations, aware of this situation, concentrate their efforts on protecting themselves against ransomware. This often means that they shift their budgets away from web security. Unfortunately for them, it means they are actually making their IT systems less secure against ransomware.
Here are 5 reasons why taking care of your web security is very important to avoid ransomware.
1. Ransomware Is a Result of Attack Escalation
Ransomware is not the attack itself, it is the result of the actual attack.
If we were to compare the effect of ransomware to an illness, ransomware software would represent a virus or bacteria. Once the virus or bacteria gets into the body of the host, it is able to multiply and infect the entire system, often with fatal results. It is the same with ransomware, once it enters the system, it may be impossible to stop.
However, just like a bacteria or a virus does not simply fly from one host to another, neither does ransomware. It must somehow be introduced into the system. And the most effective measures of defense are at this stage – aimed to prevent ransomware from entering the system in the first place.
Just like bacteria and viruses, ransomware may be delivered using different paths. For example, a bacteria or a virus may spread by touch or by saliva droplets. Similarly, ransomware may just as easily be delivered by phishing and social engineering or by exploiting vulnerabilities in the system. And nowadays, most such vulnerabilities are web vulnerabilities (for an explanation of why – see Reason 3 below).
Conclusion: To protect from ransomware, you must completely focus on protecting yourself against the attacks that can be used to deliver ransomware to your systems. Once ransomware is in your system, it is too late.
2. Web Attacks Are Used to Spread Ransomware
Phishing and social engineering are believed to be the most common way to deliver ransomware. However, phishing is often empowered by common web vulnerabilities such as cross-site scripting (XSS). Such vulnerabilities allow attackers to use renowned domain names, for example, your business name, to deliver attacks to your employees and others.
Just imagine that your web application has an XSS vulnerability. This allows the attacker to send your employees an URL with your domain name. However, upon visiting this domain, your employee would be automatically redirected to a malicious download location and download a ransomware installer. Do you think that your employees won’t fall for such a trick? Think again.
Even worse, the attacker may use your vulnerable web application to attack your business partners, your customers, and even the general public, exposing your system weakness and harming your reputation irreparably. If you want to avoid this, you must make sure that none of your systems that use your domain names have such XSS vulnerabilities.
Conclusion: Your web vulnerabilities may enable phishing attacks against your own organization, your partners, your clients, or even the general public. This may cause irreparable harm to your reputation.
3. Move to Cloud Means that More Criminals Aim for the Cloud
As mentioned in Reason 1, ransomware may be delivered to the target system using different methods, very often taking advantage of vulnerabilities. A while ago, most such vulnerabilities would exist in on-premises systems – these would be network vulnerabilities, for example, resulting from out-of-date software or misconfiguration of local networks. Now, especially in 2020 when most businesses moved to remote work, on-premises networks are losing even more ground.
Such on-premises networks are being replaced by the cloud. And the cloud is based completely on web technologies. Therefore, the move to the cloud is associated with the growing importance of web vulnerabilities. Vulnerabilities that used to, perhaps, affect just marketing websites now may affect business-critical systems and business-critical data.
The creators of ransomware also stay ahead of the times. They are aware that it is no longer enough for a malicious encryptor to crawl through a local network and infect local desktops and servers. They are aware that nowadays, more and more potential victims use thin clients (browsers) and access data that is being stored in the cloud. Therefore, they realize that they must take advantage of more and more web/cloud vulnerabilities to ensure their ransomware software is the most effective.
Conclusion: Most organizations either already use the cloud or are moving to it, making network security obsolete. Focusing on network security instead of web security in this day and age makes security efforts futile.
4. Organizations Do Not Report Attack Details
It is very difficult to know how to defend your business against ransomware because other organizations that have fallen victim to ransomware most often do not share their experiences. They simply inform the public that they have been the victim of a ransomware attack – nothing more.
Such behavior is understandable. First of all, attacked organizations may be unable to fix their security weaknesses immediately. Second of all, organizations are afraid to share attack vector details so that they don’t make themselves more open to other attacks. Third of all, many organizations wrongly believe that admitting their mistakes may hurt their reputation.
Unfortunately, this behavior slows down the development of efficient protection methods and has an overall negative impact on IT security worldwide. This situation could be compared to a country that was affected by a deadly virus and would not share any details about it for political reasons.
Conclusion: Not sharing the details of attack vectors used to deliver ransomware to victim systems makes it more difficult for other businesses to avoid ransomware.
5. Media Focuses on the Problem, Not the Solution
What makes the situation even worse is the fact that in those rare cases when attack details are known, most media decide not to mention any such details. This is true in the case of all security breaches. Instead, the media focus on popular topics such as the business impact of the ransomware attack.
For example, to find out that the Capital One data breach from 2019 was caused by a server-side request forgery (SSRF), you would have to dig very deep in search engines. Most media sources did not bother to mention this crucial information.
In the light of media and business behavior that leads to ransomware being even more of a problem for businesses everywhere, it is a pleasant surprise to see that there are major enterprises that follow the best possible practices. There is probably no better example of this than Cloudflare. For example, when in 2019 Cloudflare experienced a major outage caused by human error and the use of a web application firewall (WAF), they described the entire incident using an impressive level of detail – and this is their regular practice.
Conclusion: We heartily recommend that the media share known attack details. If we share the information and learn about the first steps of a ransomware attack, we will all have a better chance to protect ourselves against such attacks in the future.
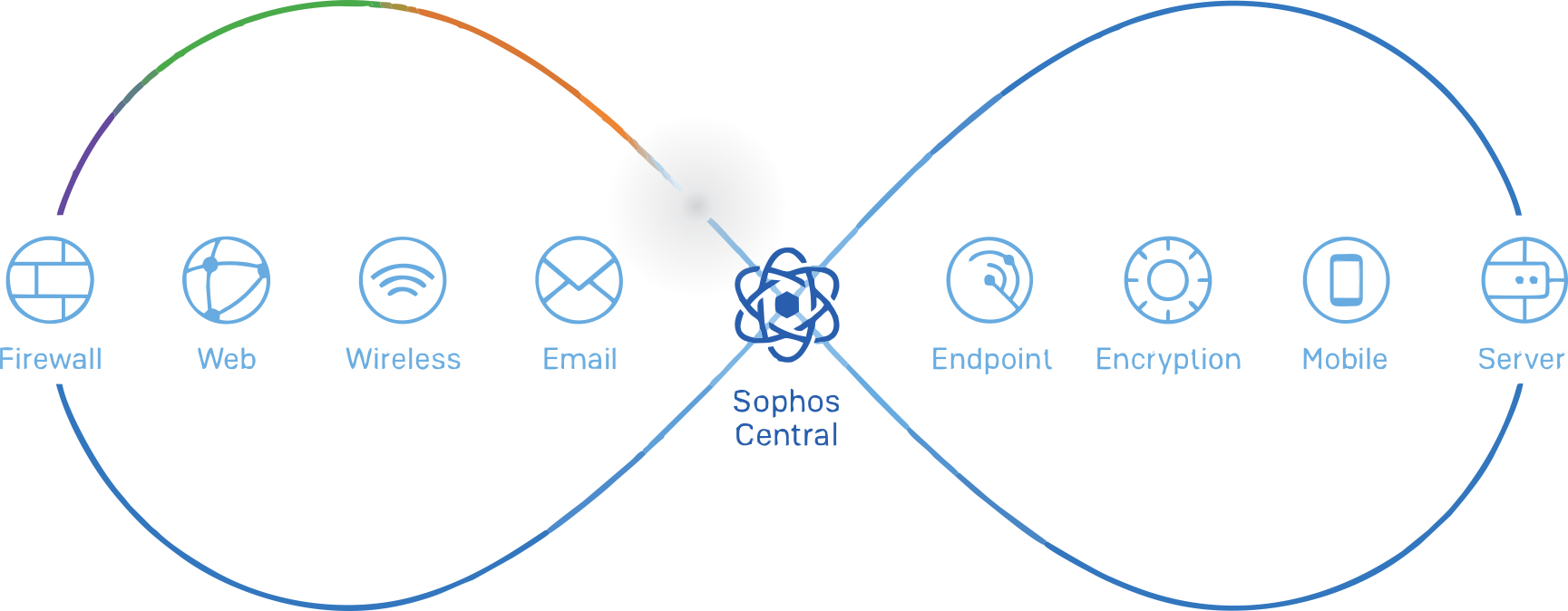
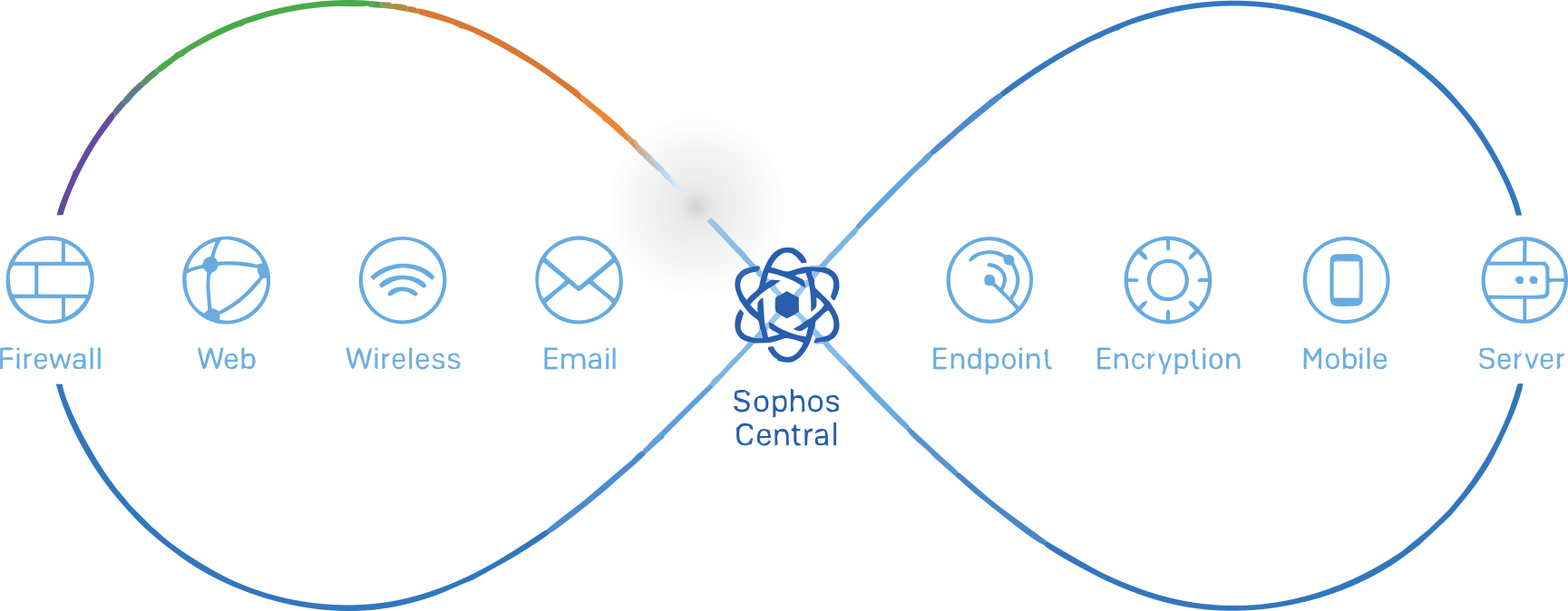
If you’re one of the many organizations already managing your network through Sophos Central, you’re intimately familiar with the benefits it provides for easy management and reporting.
If you’re still managing your XG Firewall customer networks through Sophos Firewall Manager (SFM) or using iView for central reporting, you probably realize that these platforms are aging, struggling to stay current, and difficult to learn and use.

These legacy platforms are being retired with end-of-life coming up soon. These aging platforms are not scalable, do not meet our standards for security, and are difficult and expensive to maintain.
Now is the time to switch to Sophos Central for all your firewall management and reporting needs. Sophos Central offers a completely modern platform with the ultimate in security, scalability, and performance, all while enabling us to accelerate feature development to add tremendous time savers for you and your team.
Why Sophos Central?
Have a quick look at all the great central management capabilities in this short video:
Why customers love Sophos Central:
- Better usability – workflows are more intuitive, streamlined, efficient, and task oriented
- Better accessibility – check on your network from anywhere, at anytime
- Better features – with a modern development platform and architecture, we can accelerate our roadmap to deliver more features faster
- Better integration – you can not only centrally manage your firewalls, but all your other Sophos products from a common interface – and this integration is essential for Synchronized Security, XDR, MTR, ZTNA and the future of cybersecurity
Features and capabilities you get today with Sophos Central:
- Group firewall management – makes managing multiple firewalls easy, including recently added support for HA pairs
- Zero-touch deployment – saves time and money deploying new firewall devices
- Backup management – a central repository for all your firewall backups
- Central inventory – see all your firewall devices under management at a glance
- Central secure access – with full control over which admins can access which firewalls so you don’t need to expose your webadmin access to the WAN
- Firmware updates and scheduling – with one-click ease and new scheduling options
- Audit logging and tracking – with a full change log history and synchronization status
- High-availability management – supported as of v18 MR3 to manage HA pairs together
- Central Firewall Reporting – with useful built-in reports, flexible custom report building tools, export and scheduling options, and multi-firewall reporting
What’s next?
Firmware update scheduling – update scheduling is already included in Sophos Central, but you need v18 MR3 running on your firewalls to take advantage of it, making it helpful for the next firmware update.
SD-WAN orchestration – giving you point-and-click options to establish multiple site-to-site VPN networks.

Below, you can see a full list of features in Sophos Central today, what’s coming soon, and compare that with the legacy SFM/CFM platforms. Sophos Central already includes much requested features that that are missing today in the legacy platforms, and more enhancements are coming soon.

Making the switch
If you haven’t already, now is the time to make the switch. Migrating management and reporting for your XG Firewalls to Sophos Central is as easy as 1-2-3…
- Register your firewall to Sophos Central
- Enable Management and Reporting
- Approve the management in Sophos Central

If you have many firewalls to migrate, there is an open-source tool available to help automate the process.
If you require assistance with migration, your nearby Sophos Partner can provide all the help you need, or you can reach out to our Professional Services team.
If you want to learn more about Sophos Central and what it can do for you, check out our website for more information.
This course provides an in-depth study of Sophos Central, designed for experienced technical professionals who will be planning, installing, configuring and supporting deployments in production environments. It consists of presentations and practical lab exercises to reinforce the taught content, and electronic copies of the supporting documents for the course will be provided to each trainee through the online portal. The course is expected to take 3 days to complete, of which approximately 9 hours will be spent on the practical exercises.
Requirement
Prior to attending this course, trainees should:
- Complete the Sophos Central Endpoint and Server Protection and should have passed the Certified Engineer exam
- Experience with Windows networking and the ability to troubleshoot issues
- A good understanding of IT security
- Experience using the Linux command line for common tasks
- Experience configuring Active Directory Group Policies
- Experience creating and managing virtual servers or desktop
Target audience:
This course is designed for technical professionals who will be planning, installing, configuring and supporting deployments in production environments. And for individuals wishing to obtain the Sophos Central Certified Architect certification.
Objectives:
On completion of this course, trainees will be able to:
- Design an installation considering all variables
- Undertake a multi-site installation appropriate for a customer environment
- Explain the function of core components, how they work, and how to configure them
- Track the source of infections and cleanup infected devices
- Perform preliminary troubleshooting and basic support of customer environments
Certification:
To become a Sophos Certified Architect, trainees must take and pass an online assessment. The assessment tests their knowledge of both the presented and practical content. The pass mark for the assessment is 80%, and is limited to 3 attempts.
Duration: 3 days
Content
- Module 1: Deployment Scenarios (60 mins)
- Module 2:Client Deployment Methods (65 mins)
- Module 3:Endpoint Protection Policies (80 mins)
- Module 4:Server Protection Policies (30 mins)
- Module 5:Protecting Virtual Servers (60 mins)
- Module 6:Logging and Reporting (45 mins)
- Module 7: Managing Infections (45 mins)
- Module 8: Endpoint Detection and Response (30mins)
- Module 9:Management (65 mins)
Course content
Module 1: Deployment Scenarios (60 mins)
-
- Identify some of the common challenges when deploying Central
- Deploy Update Caches – Set up Message Relays
- Configure AD Sync Utility
- Identify where Update Caches and Message Relays should be used
- Labs (45 mins)
- Register and activate a Sophos Central evaluation
- Install Server Protection
- Install and Configure AD Sync Utility
- Deploy an Update Cache and Message Relay
Module 2: Client Deployment Methods (65-75 mins)
- Identify the recommended steps for deploying Sophos Central
- Explain the installation process, and identify the different types of installer
- Automate deployment for Windows, Linux and Mac computers
- Migrate endpoints from Enterprise Console
- Locate installation log files
- Remove third-party products as part of a deployment
- Labs (75-90 mins)
- Enable Server Lockdown
- Deploy using Active Directory Group Policy
- Use the Competitor Removal Tool
- Deploy to a Linux Server using a Script
Module 3: Endpoint Protection Policies (80-90 mins)
- Describe the function and operation of each of the components that make up an Endpoint Protection and Intercept X
- Configure policies to meet a customer’s requirements and follow best practice
- Test and validate Endpoint Protection
- Configure exclusions
- Configure Data Loss Prevention
- Labs (100-120 mins)
- Test Threat Protection Policies
- Configure and Test Exclusions
- Configure Web Control Policies
- Configure Application Control Policies
- Data Control Policies
- Configure and test Tamper Protection
Module 4: Server Protection Policies (30 mins)
- Configure Server Protection Policies
- Configure and Manage Server Lockdown
- Labs (65-75 mins)
- Configure Sever Groups and Policies
- Manage Server Lockdown
- Test Linux Server Protection
Module 5: Protecting Virtual Servers (60 mins)
- Connect AWS and Azure accounts to Sophos Central – Deploy Server Protection to AWS and Azure
- Deploy and Manage Sophos for Virtual Environments
- Labs (60 mins)
- Download the installer for the Security Virtual Machine
- Install the Security Virtual Machine (SVM) on a Hyper-V Server
- Configure Threat Protection policies to apply to the Security VMs and the Guest VMs they protect
- Perform a manual installation of the Guest VM Agent and view logs
- Test and configure a script to deploy the GVM Agent
- Manage Guest VMs from the Central Console
- Test Guest VM Migration
Module 6: Logging and Reporting (45 mins)
- Explain the types of alert in Sophos Central, and be able to read an RCA
- Use the Sophos Central logs and reports to check the health of your estate
- Export data from Sophos Central into a SIEM application
- Locate client log files on Windows, Mac OS X and Linux
- Labs (55-60 mins)
- Generate and analyze an RCA
- Configure SIEM with Splunk
Module 7: Managing Infections (45-60 mins)
- Identify the types of detection and their properties
- Explain how computers might become infected
- Identify and use the tools available to cleanup malware
- Explain how the quarantine works and manage quarantined items
- Cleanup malware on a Linux Server
- Labs (40 mins)
- Source of Infection Tool
- Release a File from SafeStore
- Disinfect a Linux Server
Module 8: Endpoint Detection and Response (30 mins)
- Explain what EDR is and how it works
- Demonstrate how to use threat cases and run threat searches
- Explain how to use endpoint isolation for admin initiated and automatic isolation
- Demonstrate how to create a forensic snapshot and interrogate the database
- Labs (30 mins)
-
- Create a forensic snapshot and interrogate the database
- Run a threat search and generate a threat case
Module 9: Management (65 mins)
- Use the Controlled Updates policies appropriately
- Enable multi-factor authentication
- Use the Enterprise Dashboard to manage multiple sub-estates
- Identify the benefits of the Partner Dashboard
- Identify common licensing requirements
- Labs (25 mins)
- Enable Manually Controlled Updates
- Enable Multi-Factor Authentication
Agenda
Trainer: Michael Eleftheroglou
Day 1, Tuesday, November 24th, 2020
9:30-10:30 Deployment Scenarios
10:30-10:45 Break
10:45-11:30 Labs
11:30-11:45 Break
11:45-13:00 Client Deployment Methods I
13:00-14:00 Break Lunch
14:00-15:30 Labs
15:30-15:45 Break
15:45-17:15 End Point Policies
Day 2, Wednesday, November 25th, 2020
9:30-11:15 Labs
11:15-11:30 Break
11:30-12:00 Server Protection Policies
12:00-12:15 Break
12:15-13:30 Labs
13:30-14:30 Break- Lunch
14:30-15:30 Protecting Virtual servers
15:30-15:45 Break
15:45-16:45 Labs
16:45-17:30 Logging and Reporting
Day 3, Thursday, November 26th, 2020
9:30-10:30 Labs
10:30-10:45 Break
10:45- 11:30 Managing Infections
11:30-12:00 Labs
12:00-12:10 Break
12:10-12:40 Endpoint Detection and Response
12:40-13:45 Management
13:45-14:45 Break – Lunch
14:45-17-15 Labs and Exams
The latest update to Sophos Central Firewall Reporting (CFR) Advanced adds reporting across multiple devices, enabling you to easily get a holistic view into network activity and threats across your entire estate.
Reporting is also more accessible in Sophos Central, with two new direct main menu options under Firewall Management for the Report Hub Dashboard and the Report Generator tools.
There’s also a new drop down box enabling you to select entire groups or individual firewalls to include in the dashboard view and reports.

These features are included and automatically enabled at no extra charge for customers with a CFR Advanced subscription.
The new multi-firewall reporting enables easy visibility into the security posture across your entire network with just a few clicks. You can quickly and easily identify threat activity across all your devices, including Sandstorm suspicious file sandboxing events, AV, IPS, geo information, and much more.

How to get started
You can try CFR for free with limited storage and features for about seven days of data retention to see how it works and then contact your preferred Sophos Partner or Sophos directly to get going on CFR Advanced today.

Setup is easy: simply log into the firewall and select “Central Synchronization” from the main menu to add a firewall to Sophos Central. Then log into Sophos Central to confirm.
Switching from Sophos iView
Sophos iView is a legacy firewall reporting platform that is coming to end of life at the end of this year. Sophos Central Firewall Reporting provides a far more advanced and scalable reporting and analytics platform that replaces iView, enabling us to accelerate our roadmap and deliver more exciting new functionality sooner.
If you’re still using iView, now is the time to switch. It’s super easy. Get started sending your log data to Sophos Central today.
We are thrilled to announce that for the second year in a row, SE Labs has named Sophos Intercept X the 2020 Best Small Business Endpoint product.
SE Labs makes use of multiple techniques to put endpoint solutions through rigorous testing regimes.
In their own words:
“If you want to see how well security products work, you need to test them like you’re the bad guy. This is what we at SE Labs specialise in. Realistic and accurate copycatting cyber criminals and spies to see what happens to anti-malware, endpoint protection and other security products.”
This award complements the performance of Intercept X in other SE Labs tests for small business, enterprise, and home endpoint protection – where Intercept X recently achieved 100% Total Accuracy Rating in all three tests.
For more information read the SE Labs blog, head straight to the report, and take a look at Sophos Intercept X.
Morey Haber, chief technology officer and chief information security officer at BeyondTrust, said government agencies seeking to protect remote devices used by employees who are teleworking due to the COVID-19 pandemic should implement cloud-based security tools and privileged access management.
“Cloud-based tools can monitor a managed resource more effectively in all environments,” Haber wrote. “With that always-on approach to security, IT administrators can see and respond to potential threats in real time as they arise.”
To secure access to databases, applications and networks, agencies should “secure privileged accounts and credentials by adding a layer of complexity, never exposing the password to the user and rotating credentials after each use,” he said.
Haber called on agencies to safeguard remote access pathways that link to the company’s network, implement the least privilege and ensure that precise privileges are only provided to every session or endpoint for a limited time period to carry out an authorized activity.
He also noted that agencies should protect the telework environment from security vulnerabilities by using platforms from “trusted vendors that understand the challenges facing government agencies and are certified against the appropriate security controls.”
Ninety-seven percent of business decision-makers say that COVID-19 has sped up digital transformation and the use of cloud services at their companies*.
Customers may have a carefully mapped out strategic plan for cloud migration, or circumstances beyond their control such as Covid-19 may have caused them to rethink and move faster than they’d have anticipated. Either way, organizations all have a common goal: to optimize IT and security costs.
And it’s no different for cloud infrastructure. That’s why Sophos is helping organizations to answer the question: “How can I optimize AWS and Azure costs?”
They can achieve their goals with Cloud Optix, which provides a new range of cost optimization tools that allow customers to ensure security and compliance of cloud infrastructure, while also saving money on AWS and Azure service costs – all in a single Cloud Optix subscription.
Available for new and existing customers from launch, Cloud Optix will help organizations:
- Optimize AWS and Azure infrastructure costs in a single console
- View comprehensive daily and monthly costs, along with intuitive filters to provide analysis of individual cloud environments, services, and regions with ease
- Track spend for multiple services side by side on a single screen to improve visibility and reduce wasted spend
- Identify unusual activity indicative of abuse, highlighting top services contributing to spend with customizable alerts
- Receive detailed independent Sophos recommendations to optimize AWS costs, and integrate with both the AWS Trusted Advisor and Azure Advisor services within the Cloud Optix console
- Compare monthly analysis of granular changes to service spend with clear executive summaries
Helping you focus your teams
We’re so confident in our technology that the team at Sophos uses Cloud Optix to protect the Amazon Web Services environments used to host Sophos Central itself – a cloud security platform trusted by over 150,000 customers. And a primary reason is that Cloud Optix shows them where to focus attention in order to proactively stop any potential breach points before they happen – an approach which is carried through to spend monitoring.
Cloud Optix helps SecOps and DevOps teams focus on and fix their most critical security vulnerabilities before they are identified and exploited in cyberattacks. It provides a complete picture of your cloud assets across multi-cloud environments by monitoring costs, detecting insecure cloud configurations and deployments, and detecting access anomalies, over-privileged IAM roles, and compliance failures from the development cycle through to the ongoing security of live cloud services.
Find out how much you can save
Cloud Optix is part of our complete portfolio of cloud security products and services, including EDR, MTR, Firewall, CWPP, CSPM, and SaaS email security. You can start a trial and find out more about Cloud Optix here.
The annual appointment for the telecom, IT and media industries is here once more. This year, it focuses on the upcoming 5G networks, Digital Transformation, and new technologies that will reshape the landscape.
Now, that the age of digital transformation is already upon us, with cloud and virtualization becoming mainstream, «security» is vital for all organizations and companies. As threats become more and more complex, sophisticated and evasive, prioritizing the security of your applications, your assets and your client’s sensitive data and information, has become business critical.
Sophos Engineer, Grzegorz Nocon, in his speech «Threat Notification Isn’t the Solution – It’s a Starting Point» (4th of November, 14:00 – 14:30, 2nd Session) will talk about the «threat landscape» and the solutions you should consider for your security posture.
Sophos, is one of the leading security vendors that offers total protection and control over known and unknown attacks, malware, spyware, unwanted programs and spam, providing a line of different products and solutions. Sophos started to produce antivirus and encryption products nearly 30 years ago. Today Sophos products help to secure the networks used by 100 million people in 150 countries and 100,000 businesses.
NSS is an international Value-Added Distributor of affordable cutting-edge IT solutions, covering technology areas including information security, networking, unified communications and infrastructure systems, and is the distributor of Sophos products and services in Greece, Cyprus, Malta and the Balkan countries.
About the Conference:
Transforming Greece: The 5G and Fiber Enablers – The Future is Now!
Ever since mobile telephony came into play, every decade it is shaped by a new generation. In the 80s we had 1G, in the 90s 2G, in the first decade of the 21st century 3G, in that of the 10s 4G popped up, and now it is time for 5G. With the 5th generation seen as a true “revolution”, as changes and new features that 5G brings, create a new landscape and provide opportunities for launching solutions and applications, which -at this moment- we possible have not even thought of, even though our country has shown to be particularly sensitive in 5G development.
Greece prepares to enter the 5G era. The bidding contest for frequencies to be used in 5th generation networks will be complete by the end of 2020, and in early 2021 Greek providers are expected to commercially launch 5G networks.
The coming of 5G, along with challenges, opportunities, as well as issues it brings, will be the main discussion subject at InfoCom World 2020, the largest Conference about the telecoms industry in Greece, organized by Smart Press. On a different, physical format, due to the COVID-19 pandemic, this year’s ICW aims to set up a platform for discussing and exchanging views on 5th generation mobile networks, and how their potential can be utilized so Greece can take its next steps in the digital era.
ICW 2020 includes, among other subjects, challenges about developing 5G infrastructure, setting up an ecosystem of applications and solutions that utilize 5G, as well as the strategy this country needs to follow, in order to be among the states with a larger role in the new era, taking advantage of opportunities that both 5G and the 4th Industrial Revolution, offer. It’s a fact that as much as 4G affected our perception of telecoms, 5G will affect all aspects of our daily lives (work, learning, news, entertainment, productivity), and by that standard, all who use digital technology. The future is already here.
More, here.
Based on a comprehensive survey of 5,000 IT managers across 26 countries, Cybersecurity: The Human Challenge provides brand new insights into the state of cybersecurity skills and resources across the globe.
It reveals the realities facing IT teams when it comes to the human-led delivery of cybersecurity, and explores how organizations are responding to the skills challenges they face.
The study also exposes unique insights into the relationship between an organization falling victim to ransomware and their day-to-day cybersecurity practices.
Key findings
IT teams are showing progress in many battles
- IT teams are on top of patching. Three-quarters of IT teams apply patches to desktops, servers, applications, and internet-facing assets within a week of release. Servers and internet-facing assets are patched most quickly, with 39% of respondents patching them within 24 hours.
- Prevention is prioritized. On average, IT teams dedicate nearly half their time (45%) to prevention. After that, 30% of time is spent on detection and the remaining 25% is spent on response.
- IT managers are keeping up to date with cybersecurity. The majority (72%) say that they and their teams are up to date with or ahead of cybersecurity threats. Just 11% think they are significantly behind.
Improving cybersecurity requires people – who are in short supply
- There is an urgent need for human-led threat hunting. Forty-eight percent of respondents have already incorporated human-led threat hunts in their security procedures and a further 48% plan to implement them within a year.
- The cybersecurity skills shortage is directly implementing protection. Over a quarter (27%) of managers said their ability to find and retain skilled IT security professionals is the single biggest challenge to their ability to deliver IT security, while 54% say it is a major challenge.
Organizations are changing the ways they deliver security
- Improving operational efficiency is a key priority. Four in ten (39%) respondents said that improving operational efficiency and scalability is one of their biggest priorities for the IT team this year.
- Outsourcing IT security is rising fast. Currently, 65% outsource some or all of their IT security efforts. This is set to rise to 72% by 2022. The percentage of organizations that exclusively uses in-house staffing will drop from 34% to 26%.

Ransomware victims display different behaviors and attitudes than those who haven’t been hit
- Ransomware victims are more exposed to infection from third parties. Twenty-nine percent of organizations hit by ransomware in the last year allow five or more suppliers to connect directly to their network – compared to just 13% for those that weren’t hit.
- Ransomware damages professional confidence. IT managers whose organizations were hit by ransomware are nearly three times as likely to feel “significantly behind” on cyberthreats than those that weren’t (17% vs. 6%).
- Being hit accelerates implementation of human-led threat hunting. Forty-three percent of ransomware victims plan to implement human-led hunting within six months, compared to 33% for those that didn’t suffer an attack.

- Victims have learned the importance of skilled security professionals. More than one-third (35%) of ransomware victims said recruiting and retaining skilled IT security professionals is their single biggest challenge when it comes to cybersecurity, compared to just 19% who hadn’t been hit.

Download the full PDF report for more findings, including results for each of the 26 countries surveyed.
About the survey
Sophos commissioned specialist research house Vanson Bourne to survey 5,000 IT managers during January and February 2020. Sophos had no role in the selection of respondents and all responses were provided anonymously.
Respondents came from 26 countries across six continents: Australia, Belgium, Brazil, Canada, China, Colombia, Czech Republic, France, Germany, India, Italy, Japan, Malaysia, Mexico, the Netherlands, Nigeria, the Philippines, Poland, Singapore, South Africa, Spain, Sweden, Turkey, UAE, the UK, and the US.
Fifty percent of respondents were from organizations of between 100 and 1,000 employees, and 50% were from organizations of between 1,001 and 5,000 employees. Respondents came from a range of sectors, both public and private.
Sophos XG Firewall has joined the robust and growing Nutanix ecosystem that is enabling global enterprises to converge and virtualize their IT infrastructure.
XG Firewall is now Nutanix AHV and Nutanix Flow ready to provide protection for networked applications and traffic in Nutanix virtualized environments. XG Firewall delivers the same kind of easy deployment, management and performance that Nutanix AHV is known for.
Nutanix is the industry leader in hyperconverged infrastructure (HCI) that makes the underlying datacenter and cloud infrastructure invisible, abstracting and elevating it to enable businesses to focus on their applications and services. The Nutanix AHV hypervisor converges private, public, and distributed clouds, bringing simplicity and agility to infrastructure management.

XG Firewall v18 with the new Xstream Architecture running on Nutanix AHV provides deeper visibility into applications, network activity, and threats – able to stop even previously unseen attacks.
Nutanix Flow is a software defined network policy engine built into AHV that provides easy and granular policy-driven application micro-segmentation.
XG Firewall has been validated to provide two modes of operation within Nutanix AHV infrastructure:
- XG firewall can provide standard NGFW protection on Nutanix AHV similar to any other physical, virtual, cloud, or hybrid network.
- In addition, non-IP bridge mode in XG can be used within the network as part of Nutanix Flow’s micro-segmentation to transparently redirect VM traffic through a virtual XG Firewall running in bridge mode on every AHV host to protect east-west traffic.

XG Firewall can protect traffic entering and leaving the Nutanix AHV infrastructure while also securing traffic moving within the Nutanix Flow software defined network, taking advantage of the granular redirection capabilities of Nutanix Flow micro-segmentation that ensures security protection policies are optimized for individual applications.
XG Firewall’s full suite of protection capabilities will help secure Nutanix applications and network traffic flows, including TLS inspection, intrusion prevention, application control, web protection and filtering, and zero-day threat protection with sandboxing and threat intelligence.
Visit Sophos.com/Firewall to learn more about XG Firewall products.
New Acunetix and Netsparker Training Webinars in November. Use any of our availabilities below to book your free training session with one of our specialists.

Privileged Remote Access & Remote Support
Join our Free Webinar on Wednesday, October 21st, 2020 @ 11:00 and learn how to control, manage, and audit a vendor or an internal remote privileged access.
CLICK HERE TO REGISTER TO THE EVENT

BeyondTrust Privileged Remote Access provides visibility and control over third-party vendor access, as well as internal remote access, enabling organizations to extend access to important assets, but without compromising security.
CLICK HERE TO REGISTER TO THE EVENT
Meet BeyondTrust Ecosystem

[vc_row][vc_column column_width_percent=”100″ position_vertical=”middle” align_horizontal=”align_center” gutter_size=”3″ overlay_alpha=”50″ shift_x=”0″ shift_y=”0″ shift_y_down=”0″ z_index=”0″ medium_width=”0″ mobile_width=”0″ css=”.vc_custom_1603096348997{border-top-width: 0px !important;border-bottom-width: 0px !important;padding-top: 0px !important;padding-bottom: 0px !important;}”][vc_column_text css=”.vc_custom_1603092557855{margin-top: 0px !important;margin-bottom: 0px !important;border-top-width: 0px !important;border-bottom-width: 0px !important;padding-top: 0px !important;padding-bottom: 0px !important;}”]

Privileged Remote Access &
Remote Support
[/vc_column_text][/vc_column][/vc_row][vc_row unlock_row=”” row_height_percent=”0″ overlay_alpha=”50″ gutter_size=”3″ column_width_percent=”100″ shift_y=”0″ z_index=”0″ css=”.vc_custom_1603096713732{border-right-width: 0px !important;border-left-width: 0px !important;padding-right: 0px !important;padding-left: 0px !important;}”][vc_column column_width_percent=”100″ align_horizontal=”align_center” gutter_size=”3″ overlay_alpha=”50″ shift_x=”0″ shift_y=”0″ shift_y_down=”0″ z_index=”0″ align_medium=”align_center_tablet” medium_width=”0″ align_mobile=”align_center_mobile” mobile_width=”0″ css=”.vc_custom_1603096930728{border-top-width: 0px !important;border-right-width: 0px !important;border-bottom-width: 0px !important;border-left-width: 0px !important;padding-top: 0px !important;padding-right: 0px !important;padding-bottom: 0px !important;padding-left: 0px !important;}”][vc_custom_heading]
In case you missed last Wednesday’s webinar
on Remote Working Solutions by BeyondTrust
and still want to learn how to control, manage, and audit a vendor or an internal remote privileged access, we have prepared a complete recording for you to watch anytime you prefer.
[/vc_custom_heading][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_gallery el_id=”gallery-131064″ medias=”99600″ gallery_back_color=”color-150912″ gutter_size=”3″ media_items=”media|custom_link|original” screen_lg=”1000″ screen_md=”600″ screen_sm=”480″ single_width=”12″ images_size=”sixteen-nine” single_back_color=”color-150912″ single_shape=”round” single_overlay_opacity=”50″ single_padding=”2″ items=”eyI5OTU5N19pIjp7InNpbmdsZV93aWR0aCI6IjgifX0=”][/vc_column][/vc_row][vc_row][vc_column column_width_percent=”100″ align_horizontal=”align_center” gutter_size=”3″ overlay_alpha=”50″ shift_x=”0″ shift_y=”0″ shift_y_down=”0″ z_index=”0″ medium_width=”0″ mobile_width=”0″][vc_custom_heading]Learn more about BeyondTrust’s Services & Ecosystem [/vc_custom_heading][vc_single_image media=”98982″ media_width_percent=”100″ media_link=”url:https%3A%2F%2Fwww.nss.gr%2Fen%2Fproducts%2Fsecurity%2Fbeyondtrust%2F||target:%20_blank|”][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_custom_heading heading_semantic=”h4″ text_size=”h3″]
If you need us to contact you please either fill in the following info or call our Customer Line +302118000330
[/vc_custom_heading][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][contact-form-7 id=”99312″][/vc_column][/vc_row]
The use of cloud services has soared this year, with 97% of business decision-makers saying that COVID-19 has sped up digital transformation and the use of cloud services at their companies. Organizations that haven’t embraced cloud already are likely to have it on their roadmap.
Speaking with over 3,500 IT Pros in the Sophos State of Cloud Security report, 70% of organizations already hosting data and workloads in the public cloud have reported security incidents in the last 12 months.
At Sophos, we want to help organizations identify and respond to these cloud threats faster, wipe out potential breach points, and optimize cloud spend. You can now do that for free with Cloud Optix on AWS Marketplace.
The free cloud security posture management tool
Cloud Optix, the Sophos cloud security posture management tool, protects Amazon Web Services, Microsoft Azure, and Google Cloud Platform environments. It continually monitors cloud service configurations, and detects suspicious activity, insecure deployments, and over-privileged IAM roles – all while helping optimize your cloud costs. Simply put: it stops potential cloud environment breach points before they are detected and compromised.
Monitor 25 cloud assets for free via AWS Marketplace
Sophos now provides customers with the ability to monitor 25 cloud assets absolutely free. To activate, sign up via the Cloud Optix AWS Marketplace listing, then once logged into your Cloud Optix account, simply activate the free tier from the top right corner of the Cloud Optix dashboard.
How the Cloud Optix free tier works:
- Customers are able to monitor 25 cloud assets for free (see how Cloud Optix counts assets)
- This is an optional free usage tier. To activate, customers should sign up via the Cloud Optix AWS Marketplace listing, then once logged into their Cloud Optix accounts, simply activate the free tier from the top right corner of the Cloud Optix dashboard as shown above.
- Once activated, customers will only be billed for usage that exceeds this limit.

Start protecting your public cloud environments today
Risk-free setup
No downloads are required. Cloud Optix is an agentless, SaaS-based service that’s simple to set up, with read-only access to cloud environments. For help configuring the service, visit the Cloud Optix online help guide.
For more information about our cloud security posture management solution, visit the Cloud Optix page on the Sophos website.
Note: Customers signing up for Cloud Optix via AWS Marketplace will manage the product from a standalone console, providing all the functionality available for Cloud Optix via Sophos Central.
This course provides an in-depth study of Sophos Central, designed for experienced technical professionals who will be planning, installing, configuring and supporting deployments in production environments. It consists of presentations and practical lab exercises to reinforce the taught content, and electronic copies of the supporting documents for the course will be provided to each trainee through the online portal. The course is expected to take 3 days to complete, of which approximately 9 hours will be spent on the practical exercises.
Requirement
Prior to attending this course, trainees should:
- Complete the Sophos Central Endpoint and Server Protection and should have passed the Certified Engineer exam
- Experience with Windows networking and the ability to troubleshoot issues
- A good understanding of IT security
- Experience using the Linux command line for common tasks
- Experience configuring Active Directory Group Policies
- Experience creating and managing virtual servers or desktop
Target audience:
This course is designed for technical professionals who will be planning, installing, configuring and supporting deployments in production environments. And for individuals wishing to obtain the Sophos Central Certified Architect certification.
Objectives:
On completion of this course, trainees will be able to:
- Design an installation considering all variables
- Undertake a multi-site installation appropriate for a customer environment
- Explain the function of core components, how they work, and how to configure them
- Track the source of infections and cleanup infected devices
- Perform preliminary troubleshooting and basic support of customer environments
Certification:
To become a Sophos Certified Architect, trainees must take and pass an online assessment. The assessment tests their knowledge of both the presented and practical content. The pass mark for the assessment is 80%, and is limited to 3 attempts.
Duration: 3 days
Content
- Module 1: Deployment Scenarios (60 mins)
- Module 2:Client Deployment Methods (65 mins)
- Module 3:Endpoint Protection Policies (80 mins)
- Module 4:Server Protection Policies (30 mins)
- Module 5:Protecting Virtual Servers (60 mins)
- Module 6:Logging and Reporting (45 mins)
- Module 7: Managing Infections (45 mins)
- Module 8: Endpoint Detection and Response (30mins)
- Module 9:Management (65 mins)
Course content
Module 1: Deployment Scenarios (60 mins)
-
- Identify some of the common challenges when deploying Central
- Deploy Update Caches – Set up Message Relays
- Configure AD Sync Utility
- Identify where Update Caches and Message Relays should be used
- Labs (45 mins)
- Register and activate a Sophos Central evaluation
- Install Server Protection
- Install and Configure AD Sync Utility
- Deploy an Update Cache and Message Relay
Module 2: Client Deployment Methods (65-75 mins)
- Identify the recommended steps for deploying Sophos Central
- Explain the installation process, and identify the different types of installer
- Automate deployment for Windows, Linux and Mac computers
- Migrate endpoints from Enterprise Console
- Locate installation log files
- Remove third-party products as part of a deployment
- Labs (75-90 mins)
- Enable Server Lockdown
- Deploy using Active Directory Group Policy
- Use the Competitor Removal Tool
- Deploy to a Linux Server using a Script
Module 3: Endpoint Protection Policies (80-90 mins)
- Describe the function and operation of each of the components that make up an Endpoint Protection and Intercept X
- Configure policies to meet a customer’s requirements and follow best practice
- Test and validate Endpoint Protection
- Configure exclusions
- Configure Data Loss Prevention
- Labs (100-120 mins)
- Test Threat Protection Policies
- Configure and Test Exclusions
- Configure Web Control Policies
- Configure Application Control Policies
- Data Control Policies
- Configure and test Tamper Protection
Module 4: Server Protection Policies (30 mins)
- Configure Server Protection Policies
- Configure and Manage Server Lockdown
- Labs (65-75 mins)
- Configure Sever Groups and Policies
- Manage Server Lockdown
- Test Linux Server Protection
Module 5: Protecting Virtual Servers (60 mins)
- Connect AWS and Azure accounts to Sophos Central – Deploy Server Protection to AWS and Azure
- Deploy and Manage Sophos for Virtual Environments
- Labs (60 mins)
- Download the installer for the Security Virtual Machine
- Install the Security Virtual Machine (SVM) on a Hyper-V Server
- Configure Threat Protection policies to apply to the Security VMs and the Guest VMs they protect
- Perform a manual installation of the Guest VM Agent and view logs
- Test and configure a script to deploy the GVM Agent
- Manage Guest VMs from the Central Console
- Test Guest VM Migration
Module 6: Logging and Reporting (45 mins)
- Explain the types of alert in Sophos Central, and be able to read an RCA
- Use the Sophos Central logs and reports to check the health of your estate
- Export data from Sophos Central into a SIEM application
- Locate client log files on Windows, Mac OS X and Linux
- Labs (55-60 mins)
- Generate and analyze an RCA
- Configure SIEM with Splunk
Module 7: Managing Infections (45-60 mins)
- Identify the types of detection and their properties
- Explain how computers might become infected
- Identify and use the tools available to cleanup malware
- Explain how the quarantine works and manage quarantined items
- Cleanup malware on a Linux Server
- Labs (40 mins)
- Source of Infection Tool
- Release a File from SafeStore
- Disinfect a Linux Server
Module 8: Endpoint Detection and Response (30 mins)
- Explain what EDR is and how it works
- Demonstrate how to use threat cases and run threat searches
- Explain how to use endpoint isolation for admin initiated and automatic isolation
- Demonstrate how to create a forensic snapshot and interrogate the database
- Labs (30 mins)
-
- Create a forensic snapshot and interrogate the database
- Run a threat search and generate a threat case
Module 9: Management (65 mins)
- Use the Controlled Updates policies appropriately
- Enable multi-factor authentication
- Use the Enterprise Dashboard to manage multiple sub-estates
- Identify the benefits of the Partner Dashboard
- Identify common licensing requirements
- Labs (25 mins)
- Enable Manually Controlled Updates
- Enable Multi-Factor Authentication
Agenda
Trainer: Michael Eleftheroglou
Day 1, Tuesday, November 17th, 2020
9:30-10:30 Deployment Scenarios
10:30-10:45 Break
10:45-11:30 Labs
11:30-11:45 Break
11:45-13:00 Client Deployment Methods I
13:00-14:00 Break Lunch
14:00-15:30 Labs
15:30-15:45 Break
15:45-17:15 End Point Policies
Day 2, Wednesday, November 18th, 2020
9:30-11:15 Labs
11:15-11:30 Break
11:30-12:00 Server Protection Policies
12:00-12:15 Break
12:15-13:30 Labs
13:30-14:30 Break- Lunch
14:30-15:30 Protecting Virtual servers
15:30-15:45 Break
15:45-16:45 Labs
16:45-17:30 Logging and Reporting
Day 3, Thursday, November 19th, 2020
9:30-10:30 Labs
10:30-10:45 Break
10:45- 11:30 Managing Infections
11:30-12:00 Labs
12:00-12:10 Break
12:10-12:40 Endpoint Detection and Response
12:40-13:45 Management
13:45-14:45 Break – Lunch
14:45-17-15 Labs and Exams
Αυτό το τριήμερο πρόγραμμα εκπαίδευσης παρέχει μια εις βάθος μελέτη του Sophos Central, και σχεδιάστηκε για έμπειρους επαγγελματίες τεχνικούς που σκοπεύουν να προγραμματίσουν, να εγκαταστήσουν, να διαμορφώσουν και να υποστηρίξουν την ανάπτυξη του σε παραγωγικά περιβάλλοντα. Αποτελείται από παρουσιάσεις και πρακτικές εργαστηριακές ασκήσεις για την ενίσχυση της διδακτικής ύλης και του περιεχομένου ενώ ηλεκτρονικά αντίγραφα των εγγράφων για το μάθημα θα παρέχονται σε κάθε εκπαιδευόμενο μέσω της ηλεκτρονικής πύλης. Το μάθημα αναμένεται να διαρκέσει 3 μέρες για να ολοκληρωθεί, εκ των οποίων περίπου 9 ώρες θα δαπανηθούν για πρακτικές ασκήσεις.
Προαπαιτούμενα
Πριν από την παρακολούθηση του μαθήματος, οι συμμετέχοντες θα πρέπει να έχουν:
- Ολοκληρώσει τα Sophos Central Endpoint και Server Protection και θα πρέπει να έχουν περάσει τις εξετάσεις Certified Engineer
- Εμπειρία με δίκτυωση Windows networking και ικανότητα επίλυσης προβλημάτος
- Καλή κατανόηση της ασφάλειας IT
- Εμπειρία χρήσης του command line στο Linux για απλές εργασίες
- Εμπειρία διαμόρφωσης Active Directory Group Policies
- Εμπειρία στη δημιουργία και στη διαχείριση εικονικών servers ή desktop
Απευθυνόμενο κοινό:
Το συγκεκριμένο τριήμερο πρόγραμμα εκπαίδευσης παρέχει μια εις βάθος μελέτη του Sophos Central, και σχεδιάστηκε για έμπειρους επαγγελματίες τεχνικούς που σκοπεύουν να προγραμματίσουν, να εγκαταστήσουν, να διαμορφώσουν και υποστηρίξουν την ανάπτυξη του σε παραγωγικά περιβάλλοντα. Επίσης απευθύνεται σε άτομα που θέλουν να αποκτήσουν την πιστοποίηση Sophos Central Certified Architect.
Στόχοι:
Μετά την ολοκλήρωση αυτού του μαθήματος, οι εκπαιδευόμενοι θα είναι σε θέση να:
- Σχεδιάζουν μία εγκατάσταση λαμβάνοντας υπόψη όλες τις παραμέτρους και μεταβλητές
- Αναλαμβάνουν μία εγκατάσταση πολλαπλών τοποθεσιών κατάλληλη για το περιβάλλον ενός πελάτη
- Εξηγούν τη λειτουργία βασικών στοιχείων, να γνωρίζουν τον τρόπο λειτουργίας τους αλλά και πως να τα διαμορφώνουν
- Ανιχνεύουν την πηγή των μολύνσεων και να καθαρίζουν τις μολυσμένες συσκευές
- Εκτελούν προκαταρκτικά troubleshooting καθώς και να παρέχουν βασική υποστήριξη σε περιβάλλοντα πελατών
Πιστοποίηση
Για να λάβουν την πιστοποίηση Sophos Certified Architect, οι εκπαιδευόμενοι θα πρέπει να δώσουν εξετάσεις και να περάσουν την ηλεκτρονική αξιολόγηση. Η αξιολόγηση δοκιμάζει τις γνώσεις τόσο για το περιεχόμενο που παρουσιάστηκε όσο και για το περιεχόμενο σε πρακτικό επίπεδο. Το ποσοστό επιτυχίας για την αξιολόγηση είναι 80% και περιορίζεται σε 3 προσπάθειες.
Διάρκεια: 3 ημέρες
Περιεχόμενο προγράμματος εκπαίδευσης
- Module 1: Deployment Scenarios (60 mins)
- Module 2:Client Deployment Methods (65 mins)
- Module 3:Endpoint Protection Policies (80 mins)
- Module 4:Server Protection Policies (30 mins)
- Module 5:Protecting Virtual Servers (60 mins)
- Module 6:Logging and Reporting (45 mins)
- Module 7: Managing Infections (45 mins)
- Module 8: Endpoint Detection and Response (30mins)
- Module 9:Management (65 mins)
Περιεχόμενο Εκπαιδευτικού Μαθήματος
Module 1: Deployment Scenarios (60 λεπτά)
-
- Identify some of the common challenges when deploying Central
- Deploy Update Caches – Set up Message Relays
- Configure AD Sync Utility
- Identify where Update Caches and Message Relays should be used
- Labs (45 mins)
- Register and activate a Sophos Central evaluation
- Install Server Protection
- Install and Configure AD Sync Utility
- Deploy an Update Cache and Message Relay
Module 2: Client Deployment Methods (65-75 λεπτά)
- Identify the recommended steps for deploying Sophos Central
- Explain the installation process, and identify the different types of installer
- Automate deployment for Windows, Linux and Mac computers
- Migrate endpoints from Enterprise Console
- Locate installation log files
- Remove third-party products as part of a deployment
- Labs (75-90 mins)
- Enable Server Lockdown
- Deploy using Active Directory Group Policy
- Use the Competitor Removal Tool
- Deploy to a Linux Server using a Script
Module 3: Endpoint Protection Policies (80-90 λεπτά)
- Describe the function and operation of each of the components that make up an Endpoint Protection and Intercept X
- Configure policies to meet a customer’s requirements and follow best practice
- Test and validate Endpoint Protection
- Configure exclusions
- Configure Data Loss Prevention
- Labs (100-120 mins)
- Test Threat Protection Policies
- Configure and Test Exclusions
- Configure Web Control Policies
- Configure Application Control Policies
- Data Control Policies
- Configure and test Tamper Protection
Module 4: Server Protection Policies (30 λεπτά)
- Configure Server Protection Policies
- Configure and Manage Server Lockdown
- Labs (65-75 mins)
- Configure Sever Groups and Policies
- Manage Server Lockdown
- Test Linux Server Protection
Module 5: Protecting Virtual Servers (60 λεπτά)
- Connect AWS and Azure accounts to Sophos Central – Deploy Server Protection to AWS and Azure
- Deploy and Manage Sophos for Virtual Environments
- Labs (60 mins)
- Download the installer for the Security Virtual Machine
- Install the Security Virtual Machine (SVM) on a Hyper-V Server
- Configure Threat Protection policies to apply to the Security VMs and the Guest VMs they protect
- Perform a manual installation of the Guest VM Agent and view logs
- Test and configure a script to deploy the GVM Agent
- Manage Guest VMs from the Central Console
- Test Guest VM Migration
Module 6: Logging and Reporting (45 λεπτά)
- Explain the types of alert in Sophos Central, and be able to read an RCA
- Use the Sophos Central logs and reports to check the health of your estate
- Export data from Sophos Central into a SIEM application
- Locate client log files on Windows, Mac OS X and Linux
- Labs (55-60 mins)
- Generate and analyze an RCA
- Configure SIEM with Splunk
Module 7: Managing Infections (45-60 λεπτά)
- Identify the types of detection and their properties
- Explain how computers might become infected
- Identify and use the tools available to cleanup malware
- Explain how the quarantine works and manage quarantined items
- Cleanup malware on a Linux Server
- Labs (40 mins)
- Source of Infection Tool
- Release a File from SafeStore
- Disinfect a Linux Server
Module 8: Endpoint Detection and Response (30 λεπτά)
- Explain what EDR is and how it works
- Demonstrate how to use threat cases and run threat searches
- Explain how to use endpoint isolation for admin initiated and automatic isolation
- Demonstrate how to create a forensic snapshot and interrogate the database
- Labs (30 mins)
-
- Create a forensic snapshot and interrogate the database
- Run a threat search and generate a threat case
Module 9: Management (65 λεπτά)
- Use the Controlled Updates policies appropriately
- Enable multi-factor authentication
- Use the Enterprise Dashboard to manage multiple sub-estates
- Identify the benefits of the Partner Dashboard
- Identify common licensing requirements
- Labs (25 mins)
- Enable Manually Controlled Updates
- Enable Multi-Factor Authentication
Πρόγραμμα
Εκπαιδευτής: Μιχάλης Ελευθέρογλου
1η Μέρα, Τρίτη 17 Νοεμβρίου, 2020
9:30-10:30 Deployment Scenarios
10:30-10:45 Break
10:45-11:30 Labs
11:30-11:45 Break
11:45-13:00 Client Deployment Methods I
13:00-14:00 Break Lunch
14:00-15:30 Labs
15:30-15:45 Break
15:45-17:15 End Point Policies
2η Μέρα, Τετάρτη 18 Νοεμβρίου, 2020
9:30-11:15 Labs
11:15-11:30 Break
11:30-12:00 Server Protection Policies
12:00-12:15 Break
12:15-13:30 Labs
13:30-14:30 Break- Lunch
14:30-15:30 Protecting Virtual servers
15:30-15:45 Break
15:45-16:45 Labs
16:45-17:30 Logging and Reporting
3η Μέρα, Πέμπτη 19 Νοεμβρίου, 2020
9:30-10:30 Labs
10:30-10:45 Break
10:45- 11:30 Managing Infections
11:30-12:00 Labs
12:00-12:10 Break
12:10-12:40 Endpoint Detection and Response
12:40-13:45 Management
13:45-14:45 Break – Lunch
14:45-17-15 Labs and Exams