News
Many IT organizations use shared accounts for privileged users, administrators, services, or applications so that they can have the access they need to perform an activity. Account sharing often entails use of the same account credentials to authenticate multiple users. Without proper management controls in place, the practice of account sharing presents significant security and compliance risks from intentional, accidental, or indirect misuse of shared privileges.
Even for the savviest IT teams, the task of managing shared accounts introduces complexities and risks:
- Embedded and hardcoded passwords present opportunities for misuse by both insiders and external attackers on the network.
- Passwords for application-to-application and application-to-database access are often left out of management strategies.
- Static passwords can easily leave the organization, and manual password rotation tends to be unreliable.
- Auditing and reporting on privileged access is complex and time consuming, since it is difficult, or impossible, to attribute any of the session activities of a shared account back to a single identity.
5 Best Practices: Gaining Accountability over Shared Accounts
Recent breaches exploiting privileged credentials have underscored the imperative to improve control and accountability over access to shared accounts. So, how do organizations ensure accountability of shared privileged accounts to meet compliance and security requirements without impacting administrator productivity? Consider these five best practices:
1. Deploy a single, hardened, appliance-based enterprise password management solution with broad platform support and functionality
Ensure your solution provider deploys their privileged password and session management solution in a single hardened or virtual appliance that features broad support of operating systems, databases, applications, devices, and directories. Remember, it’s more than just user passwords. Consider the complexity and risk of managing privileged passwords for service accounts, between applications (A2A), and to databases (A2DB). Everything your solution provider does should be about reducing the interfaces and administration required.
2. Discover and profile to give greater control
Leverage a distributed network discovery engine to scan, identify, and profile all users and services – and then automatically bring the systems and accounts under management. Discovering and profiling all known and unknown assets, shared accounts, user accounts, and service accounts, and then placing them under intelligent rules gives greater control and significantly improved consistency of policy enforcement.

3. Monitor and manage sessions, with full playback
Your solution should record privileged sessions in real-time via a proxy session monitoring service for SSH and RDP without revealing the password. DVR-style playback provides detailed auditing of shared account access, helping to meet password protection and audit regulations for compliance mandates listed in SOX, HIPAA, GLBA, PCI DSS, FDCC, FISMA, and others.
The solution should also be able to identify suspicious sessions in real-time and initiate a workflow to pause or terminate them.
4. Make it easy on yourself by using standard desktop tools
Driving a strong, consistent organizational security posture is a challenging effort. Introducing new workflows makes this effort even harder. Having to log in to a solution each time a user needs to access a system creates adoption and training challenges.
Solutions must support standard desktop tools such as PuTTY, RDP, SSH and Microsoft Terminal Services Client. This means you can leverage commonly used management tools so your user can smoothly work within their established workflows.,
5. Gain greater insights through reporting and analytics
Look for a single pane-of-glass to collect, correlate, trend, and analyze key metrics. You need to understand key insights into:
- Privileged accounts
- Password age
- SSH keys
- Service accounts running with user accounts
- User accounts with administrative rights on Windows/Mac and Unix/Linux
- Remote Access Tools
These insights help you identify areas that require action before they become a security concern.

Solutions for Securing Shared Privileged Accounts
BeyondTrust Password Safe automates password and session management, providing secure access control, auditing, alerting and recording for any privileged account – from local or shared administrator to service to application accounts.
Team Passwords is a feature designed to securely store credentials owned by small groups within Password Safe, in a fully auditable controlled environment. This feature delivers secure password practices teams in the organization outside of traditional privileged admin user roles.
By improving the accountability and control over privileged access with Password Safe, IT organizations can reduce security risks and achieve compliance objectives.
Source: BeyondTrust
Remote access has been a component of the network since the days of acoustic, dial-up modems and the blazing fast speeds of 56 kbps. Well, perhaps not blazing fast. These modems eventually gave way to faster and more secure technologies, with virtual private networks (VPNs) hitting the market in the early 2000s. In today’s pandemic-dominated, work-from-home (WFH) environment, VPNs simply cannot cut it anymore, falling victim to security vulnerabilities, speed limitations and lack of scaling. Replacing VPNs for secure, high-performance remote access is Zero Trust Network Access (ZTNA).
By requiring that every component of the transaction of accessing a network, its resources and applications, and its data are authenticated and authorized, ZTNA goes well beyond the Russian proverb: Trust but verify. Zero trust environments, which significantly reduce risk by constantly authenticating every user, device, application and transaction, are based on the mantra: Never trust; always verify.
Essence of zero trust
ZTNA is a fundamental component of the Secure Access Service Edge (SASE) security framework. It ensures that users and devices are who and what they claim to be and can be instrumental in protecting a network from ransomware attacks. While this article focuses on Sophos ZTNA for enhancing remote access beyond the popular VPN, a detailed explanation of how Sophos ZTNA can be used to fight ransomware can be found here.
“Zero trust is a way of thinking, not a specific technology or architecture,” wrote Gartner Distinguished VP Analyst Neil MacDonald in the research firm’s article New to Zero Trust Security? Start here. “It’s really about zero implicit trust, as that’s what we want to get rid of.”
A better option for remote access
The pandemic enticed cyber criminals to target remote workers, forcing organizations to rethink how they implement their zero-trust strategy. As more employees work from home, the corporate imperative for cybersecurity changes. Where once a handful of employees worked remotely, today entire companies are becoming virtual.
Transitioning to a remote workforce changes the risk profile for the corporate network and endpoints, further stressing network security resources that might be underpowered for the massive relocation of staffers and create a larger network surface for attackers. To address this fluid network security challenge, many companies with traditional, on-premises organizations and standard perimeter defenses from the early 2000s are turning to a zero-trust model to reduce the attack surface while concurrently ensuring that every user and device that logs in is fully authenticated. They are doing this, in part, by retiring their VPNs and substituting ZTNA.
The differences between how VPNs and ZTNA approaches address security, scaling and bandwidth are noteworthy. VPNs provide basic network access. If a user has the proper credentials — often just a username and password — they get access to the entire corporate network and all that is attached to it, just as they would if they were sitting in the office at a network-attached workstation within the firewalls.
ZTNA delivers strong defenses against potential bad actors by eliminating the implicit trust and lateral movement of VPNs. Additionally, VPNs tend to be slow and were not designed to operate in environments where most workers were off-site, away from the strong fortifications of network firewalls and the rest of the network security infrastructure. ZTNA offers a better alternative for remote access by providing superior security and threat protection, a more scalable management experience and a more transparent, frictionless experience for end-users.
As workers move out of the friendly confines of the corporate network and work from home, they create millions of new, vulnerable endpoints, often outside the control of the corporate IT staff. These endpoints are ripe targets for attackers, since a large percentage of the endpoints might not have corporate-class security protections.
Additionally, the large number of newly minted external users created a huge burden on the overburdened corporate VPNs. While VPNs have defined bandwidth parameters, ZTNA is flexible, scaling up to meet the greater network burden from WFH employees.
Connecting via ZTNA gives a user access to a specific application on the corporate network, not universal access. The applications, users and devices are micro-segmented to limit the ability of the user to move through the network, a common ploy of cyberattackers and malware. With the integration of device health to automatically limit compromised devices from accessing business resources. Sophos ZTNA takes full advantage of its unique integration with the full Sophos ecosystem especially Sophos Intercept X endpoints.
The Sophos ZTNA difference
Sophos ZTNA is a much more secure and easy-to-manage remote access approach that delivers a transparent, friction experience for end-users. Moving to a zero-trust model significantly reduces risk while protecting the network from potential attackers, including those who plan to deposit malware on a system or leave breadcrumbs for employees to find, leading them to compromised websites. Among its key capabilities are:
- It removes the need for VPN clients, reducing the attack surface and making it harder for adversaries to get on your network
- Ransomware actors commonly exploit weaknesses in VPN clients (vulnerabilities, misconfigurations) to get into their victims’ networks, but ZTNA removes that avenue by eliminating VPNs
- ZTNA constantly checks user and device security, delivering continuous high-level of controls and preventing attackers from exploiting a previously authenticated user’s access
- It makes it easy to apply granular access controls, enabling companies to easily restrict access to resources just to those who need it, further reducing the attack surface
- It is managed from the same Sophos Central console that customers use to manage their other Sophos products, and uses the same agent as the Sophos endpoint protection, reducing device overhead
- With the average cost of ransomware remediation now $1.85 million, small- and mid-sized organizations investing in secure remote access via a ZTNA approach is a cost-effective investment with a discernible return on investment
Sophos ZTNA delivers transparent, clientless access for web-based applications. Among the applications a ZTNA client protects are Remote Desktop Protocol (RDP); the Secure Shell Protocol (SSH), virtual network computing (VNC), a remote-control application and other TCP/UDP-heavy applications. In fact, RDP is one of the problematic applications often used by malware to permit attackers access to infected networks. As such, many cyber insurance companies recommend that that RDP access be removed entirely from corporate networks as a condition of obtaining cyber insurance.
Learn more
For more information, read about Sophos ZTNA here. We also provide a detailed explanation of how it offers cloud-delivered, cloud-managed management and how Sophos ZTNA is the only zero trust network access solution that is tightly integrated with Sophos Intercept X.
Source: Sophos
The product team is pleased to announce the latest maintenance release update for SFOS with important customer and partner requested features, as well as important security, performance, and reliability fixes.
It is a critically important cybersecurity best-practise to keep your firewall updated with the latest firmware.
SFOS v18.5 MR3 Highlight:
DHCP Boot Option Configurations – This new feature addresses an important customer and partner request to enable additional DHCP boot options for clients on the network such as VoIP phones or other types of devices that have unique DHCP requirements.

Additional Updates:
- Support for kernel dump reporting to improve trouble shooting and root-cause-analysis in the event of an issue
- Email protection anti-spam engine updated to Sophos Anti-Spam Interface
- Several important security, performance and reliability enhancements including a fix for a recently disclosed OpenSSL DoS vulnerability
How to get it
As usual, this software update is no charge for all licensed Sophos Firewall devices and should be applied to all supported firewall devices as soon as possible.
It will be rolled out to all connected devices over the coming days. A notification will appear on your local device or Sophos Central management console when the update is available allowing you to schedule the update at your convenience. Otherwise, you can manually download the latest firmware from MySophos and update anytime.
Sophos Firewall OS v18.5 MR3 is a fully supported upgrade from v17.5 MR14 and later, v18 MR3 and later, and all previous versions of v18.5.
Are you Using Remote Access VPN on your Firewall?
If you’re using remote access VPN on your Sophos Firewall, you will want to know that we recently launched Sophos ZTNA which offers a much better solution for connecting remote workers. It offers better security in many ways (especially from Ransomware attacks), easier management, easier deployment, and a much more transparent end-user experience. Check it out.
Source: Sophos
[vc_row][vc_column][vc_column_text]When the OWASP Top 20 Vulnerabilities was first published it revolutionized our industry’s approach to vulnerability management. Instead of playing wack-a-mole with thousands of individual vulnerabilities every time a new one was discovered, we approached vulnerability management by primarily addressing these Top 20 Techniques.
Still considered “advanced”, behavioral detection has just begun to hit the mainstream. But, as the incident response (IR) cases we support continually confirm, adoption is still lagging for 90% of the mid- and SMB market. It’s in no way controversial anymore to state that, in order to detect and stop modern attacks, organizations need to have behavioral monitoring capabilities, especially on the endpoint.
One problem is that we’ve been led to believe that if we adopt behavioral detection, we need to spend a lot to maximize coverage of all the various attacker behaviors. This is a disservice.
Our intention in detection among most organizations (aka, the ones that don’t have a full-time threat intel team) should be to stop focusing on individual, novel attack techniques and concentrate defenses against the Top 20 most commonly observed ATT&CK techniques that are also achievable to monitor. These are the ones that actually matter, and the ones that will catch more bad guys, more often.
The following list is consolidated from our own data and cross-referenced with various forensic reports on observed attacks over the last few years:[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column][vc_column_text]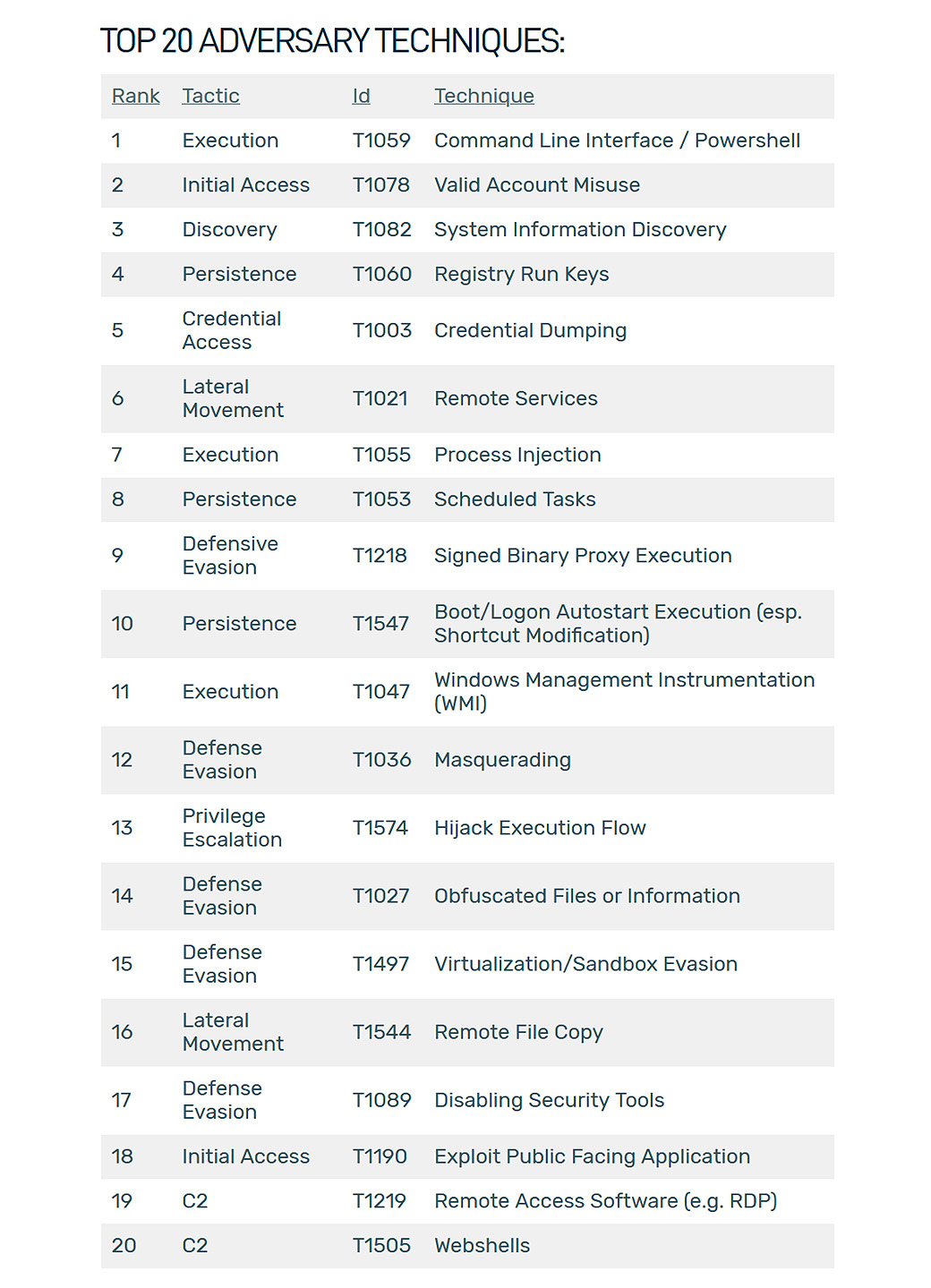 [/vc_column_text][/vc_column][/vc_row][vc_row][vc_column][vc_column_text]When it comes to these these behaviors, common doesn’t mean commodity or “less advanced”, these are common because successful attackers use them to evade legacy protection/prevention. These are the techniques the advanced players are using and they are in the hands of the commodity players through frameworks like Cobalt Strike.
[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column][vc_column_text]When it comes to these these behaviors, common doesn’t mean commodity or “less advanced”, these are common because successful attackers use them to evade legacy protection/prevention. These are the techniques the advanced players are using and they are in the hands of the commodity players through frameworks like Cobalt Strike.
Thus, making your detection capabilities robust against these 20 techniques will deliver more bang for your buck than any other approach while saving you time and money from hunting “Bluebird” techniques and behaviors you’re more than likely not going to see in your one network.
Is Top 20 enough?
Yes!
We respond to a lot of attacks and have been doing threat hunting and response in organizations large and small for over a decade. In that time, there have been very few attacks that don’t exhibit behaviors that overlap with the above list of 20 that you could be monitoring for today.
When SolarWinds Solarigate a.k.a. SUNBURST hit in December 2020, everyone said this was novel; and the entry vector certainly was. Once you dug in though, the same top 20 behaviors could be observed: The novel supply chain vulnerability was used to spawn malicious Powershell (T1059), scripts (T1059), memory injections (T1055), lateral movement (T1544) techniques, and credential dumping (T1003).
When Hafnium hit Exchange Servers using the latest Exchange zero-days we saw the same things: new novel entry vectors leading to many of the same top 20 common behaviors like WebShells (T1505) spawning PowerShell commands (T1059) and injecting Cobalt Strike into memory (T1055).
Everyone effectively monitoring for the top 20 attacker behaviors had the visibility to see these attacks unfold and my prediction is the next big vulnerability will be found by monitoring for them as well.
Conclusion
Ultimately, the Top 20 approach is an acknowledgment that not all techniques are necessary to alert or monitor to detect attacks. Defense in Depth still works: every tactic and technique you have visibility into is a detection opportunity in the attack chain, and the top 20 is broad enough to cover you against even some of the most advanced attackers. We are all strapped for resources; don’t chase the highest coverage and focus on the top 20. With these 20, there are exceedingly few attacks that could ever get past your notice.
Source: Datto[/vc_column_text][/vc_column][/vc_row]
SEP sesam version Jaglion – the hybrid of jaguar and lion symbolises the combination of the best features that have been impressively implemented with the latest version of SEP sesam Hybrid Backup.
Jaglion includes even more diverse new features and adapts even better to the growing needs of changing IT environments.
But not only new agents, but also significantly improved features, variety, performance, data security and usability will make your life easier.
The SEP sesam backup and recovery software is so far unique in the EU. Especially the range of functions, the performance and the user friendliness stand out.
Our software was developed to be able to restore data extensively and with high reliability.
The use of Si3 NG inline deduplication also makes it possible to detect duplicate data fragments and thus optimise the recovery process. This is because duplicate documents are only recovered once. Previous recovery systems usually only restore all or selected data, which causes significant additional work.
SEP data recovery is more reliable and, thanks to the aforementioned data optimisation, faster than conventional systems. The use of the latest hardware and software technologies and the developed interfaces allow data recovery from different systems and increase performance, scalability and backup speed.
Furthermore, SEP sesam is easier to maintain than other systems and its reliability is higher than that of other systems due to its complex design. There is currently no comparable system on the market in the EU that provides such an overall performance and delivers the technical data security for the GDPR.
Simplification/ User-friendliness
- Simple browser-based recovery of many databases & applications
- Ensuring the completeness of the backup -forgetting impossible! -> Extensive engine for rule-based automation of job creation of new VMs or DBs
- For all hypervisors, simplify at a glance the backup of a large number of VMs and automate the process.
- New GUI and WebUI options
- Display of VMs in Vcenter structure
- OLVM: New task type for agentless snapshot-based backups of all virtual machines
- New functions for EU GDPR compliance through simplified media management
Diversity
- Nutanix AHV Support – 10th hypervisor
- Fail-safe change tracking based on Resilient Change Tracking (RCT) for securing Hyper-V virtual machines
- HPE Cloud Volumes – direct HPE backups and especially replications to the cloud
- Enlargement/Update of the Support Matrix
- Extended SEP sesam REST API V2
- Sparse Files Support for Linux Sparse files
Performance & Optimization
- Improved performance, scaling and storage savings – Si3-NG Dedup
- 20% – 40% faster recovery and migration through optimised tape processing
- VFS (Sesam Virtual File System) performance improvements enable 100x faster access to vSphere VMs booted directly from SEP sesam datastore.
- Improved performance and massively increased scalability: Windows Backup Server optionally based on PostgreSQL
Security
- New authentication & authorisation concept
- Certificate-based authentication
- Backup role for MSPs and IT-centric customers
- MSP options: Account-based permissions for VMs, new MSP report
- Immutability of backups: HPE StoreOnce & Immutable Flag
Source: SEP
What is Conti Ransomware?
Conti is a ransomware-as-a-service (RaaS) affiliate program, first appearing in early 2020. Associated with Russian-speaking cybercrime actors, Conti ransomware developers sell or lease their ransomware technology to affiliates, who then use that technology to carry out their attacks.
The group behind Conti has published a website where they leak documents extracted by the attackers. Data belonging to hundreds of different sectors and organizations have been shared on the Conti extortion site.

How does Conti ransomware work?
Conti automatically scans networks for valuable targets, encrypting every file it finds and infecting all Windows operating systems. Conti acts in a similar manner to most ransomware, but it has been engineered to be even more efficient and evasive. Once executed on the victim’s endpoint, Conti works by:
- Immediately encrypting files and changing the file extension of the encrypted files. Each sample has a unique extension that the malware adds to the encrypted files.
- Attempting to connect to other computers on the same network subnet using the SMB port (445).
- Leaving a ransom note in every folder that has the filename readme.txt/conti_readme.txt

Initial deployment
The attack kill chain begins as soon as the actors first gain access to the network. This often occurs via an email phishing campaign that contains malicious attachments – such as a macro-enabled Microsoft Word document or password-protected zip file, which installs a first-stage malware (such as BazarLoader or Cobalt Strike) onto target systems. Conti today is sold behind a RaaS affiliation program and operated by different threat actors. Once Conti is executed, it initiates its encryption and spreading routines.
Evasion techniques
The Conti code is sophisticated with many obfuscation techniques designed to evade the common security techniques and security teams – including a multithreading technique used to encrypt all the files quickly. This allows for maximum damage before it can be identified and stopped by endpoint security products. Conti uses 32 concurrent CPU threads to hasten the encryption process, making it much faster than most ransomware.
The ransomware uses relatively common anti-analysis techniques, which are runtime API loading and obfuscating specific API calls by using hash values. It also uses an API-unhooking mechanism built inside to disable EDR-based API hooks.
Conti’s developers have hardcoded the RSA public key into the data section of the PE file, which the ransomware uses to perform its encryption. This means that it can begin encrypting files even if the malware is unable to reach its C&C servers.
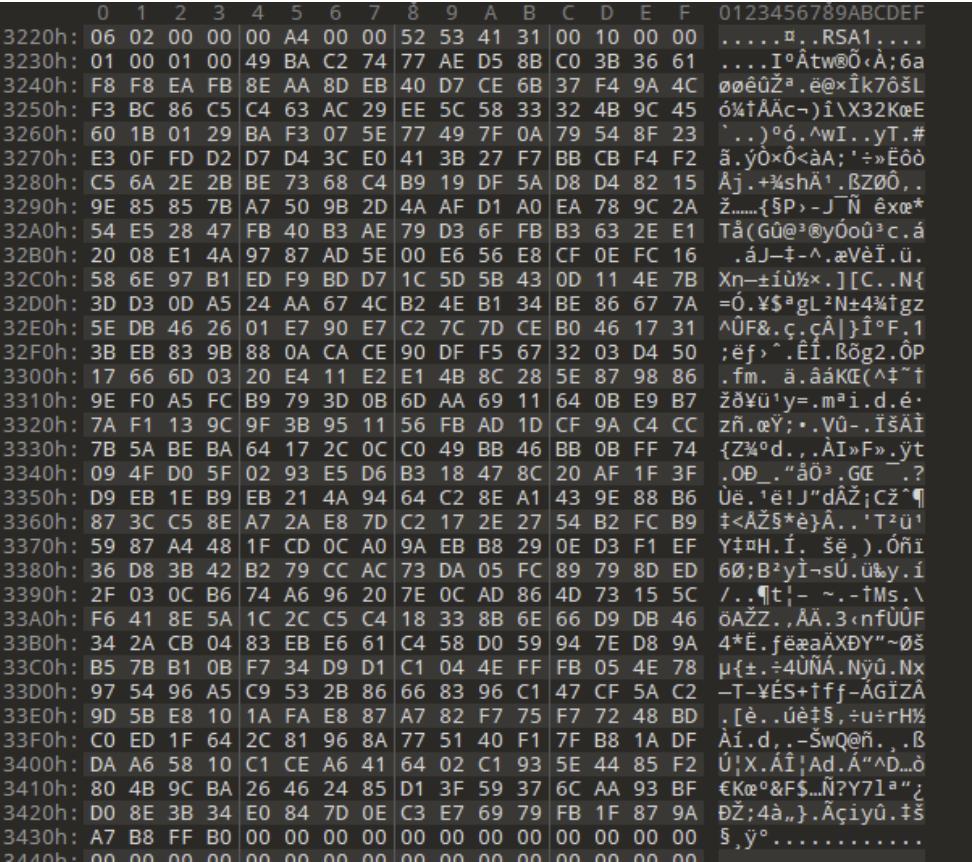
Lateral movement
The Conti ransomware immediately moves laterally within the network. It does this by attempting to connect to other computers on the same network subnet using the SMB port. If it finds any shared folders it can access, it will try to encrypt the files on the remote machines as well.

Four ways to protect against Conti ransomware
There are 4 primary ways of protecting against Conti Ransomware:
1. Detect Conti pre-delivery
In the vast majority of Conti ransomware attacks, the phishing email is the starting point. Therefore, the logical and best place to start is with an email protection solution that detects advanced threats, such as Datto SaaS Defense. As a result, the threat is stopped upstream, preventing further damage.
2. Protect each endpoint
Next, it’s important to protect individual endpoints from infection. A remote monitoring and management (RMM) tool is critical here to ensure that no individual machines have been compromised and any attempt to infect individual machines is picked up and dealt with as early as possible.
3. Prevent the lateral movement of the ransomware
As we’ve seen, Conti ransomware will attempt to move laterally within the organization using SMB. Again, at this stage, an RMM tool is your best chance of keeping your network secure and isolating the infected machine, without necessitating a complete shutdown of the entire network.
4. Back up your data
Properly backed-up data is key to ensuring business continuity in the case of an attack – and something that helps you sleep well at night. Specifically for MSPs, this is critical in ensuring your clients have a backup solution. When it comes to data backup, there are numerous backup solutions available including:
- A full Business Continuity and Disaster Recovery (BCDR) suite: for example, Datto Unified Continuity which covers all business continuity and disaster recovery needs including protecting servers, files, PCs, and SaaS applications.
- Datto SIRIS, a reliable, all-in-one business continuity and disaster recovery solution built for MSPs to prevent data loss and minimize client downtime.
- Datto ALTO, a small but powerful business continuity and disaster recovery solution built for MSPs to minimize downtime and efficiently prevent data loss for their small business clients.
- Datto Cloud Continuity for PCs which protects MSP clients’ Windows-based computers from downtime and data loss and rapidly recovers data in case of disaster.
- SaaS Protection, which offers reliable and secure cloud-to-cloud backup for Microsoft 365 and Google Workspace to ensure critical cloud data is protected.
Conti ransomware isn’t going anywhere
Unfortunately, Conti ransomware is here to stay. We’ve seen recent news regarding activity from the Conti ransomware group as well as new variants that are sure to cause further damage in the future. With a robust defense and response plan for Conti ransomware, you can ensure users, clients, and your organization are protected against Conti and other ransomware attacks.
Discover how Datto can help protect your business against ransomware attacks.
Source: Datto
In sports, there is a saying that if the opponent cannot score, they cannot win. A similar sentiment works for cybersecurity: If the attacker cannot penetrate your organization, they cannot compromise it.
Taking that a step further, the most effective way to eliminate the possibility of a breach escalating into a business-threatening attack is to stop it before it starts — reduce your attack surface to the minimum you can so you can identify a potential incident before it gets a foothold and eliminate it.
Optimizing prevention
Today, users and data can be anywhere. Users can work from the office, airport, coffee shop, or work from home. Data can reside in the cloud, a business partner’s network, or on an employee’s mobile device. These factors and more change your attack surface. The volume of potential and successful breaches is increasing as attackers take advantage of automation, artificial intelligence (AI), and malware delivery platforms in their attacks.
Here are some interesting data points from Sophos’ survey of 5,400 IT and security professionals: 61% of IT managers report an increase in attacks on their organization in the past year. Also, the complexity of attacks is increasing. Adversaries increasingly use sophisticated tactics, techniques, and procedures (TTPs) in their attacks. Some 54% of IT managers say attacks are now too advanced for the IT team to deal with on their own.
This is why optimizing prevention is a vital part of Sophos’ endpoint protection strategy.

They say an ounce of prevention is worth a pound of cure. In the cybersecurity world, preventing a single ransomware attack could result in saving millions of dollars simply by stopping the threat before it even has a chance to enter your organization.
First, you need to reduce the attack surface, removing opportunities for attackers to penetrate your organization. Some examples of how Sophos achieves this is by:
- Blocking potentially unwanted applications
- Blocking malicious or suspect websites based on content or URL rating
- Controlling which applications are allowed to run in the organization
- Controlling which devices are allowed on the organization’s network or able to access cloud assets
- Locking down server configurations in a single click
The next step is to prevent attacks from running, using layered protection technologies to stop both the threats and the tactics attackers use, including:
- Artificial intelligence (AI)-based behavior prevention that blocks the unknown based on techniques, behaviors, and anomalies
- Behavior-based anti-ransomware technology
- Exploit prevention that stops the techniques attackers use, protecting against attacks that leverage previously unknown vulnerabilities
Last year’s Kaseya attack is a prime example of the importance of prevention — by the time the attack was detected, it was too late, and the files were encrypted. Not a single Sophos customer with our next-gen endpoint protection correctly deployed had their files encrypted in that attack.
The prevention capabilities in Sophos Intercept X endpoint protection block 99.98% of threats (AV-TEST average score Jan-November 2021). Defenders are then able to better focus on the suspicious signals that require human intervention.
Minimize time to detect and respond
Today’s sophisticated attackers often exploit legitimate IT tools and security holes to penetrate their victim’s network. Every second counts when an adversary is in your environment. Yet all too often, defenders are slowed down by an overwhelming volume of alerts, limited visibility, a lack of insight, and slow, manual processes.
By optimizing prevention, Sophos enables defenders to focus on fewer, more accurate detections and streamline the investigation and response process.
To illustrate the point, I’d like to share data from Sophos Managed Threat Response (MTR), our 24/7/365 managed detection and response (MDR) service. The mean time to detect (MTTD) the attack is less than one minute. Enriched investigation techniques result in a mean time to investigate (MTTI) of 25 minutes, and the mean time to resolution (MTTR) is 12 minutes. This results in a total time from detecting the threat to resolving it of 38 minutes.
Let’s put those 38 minutes into perspective. According to the research firm Statista, the average duration of business interruption and downtime after a ransomware attack is 22 days. And that’s alongside the ever-increasing recovery costs, which have more than doubled in the past year.
Stop more threats, faster
In a challenging cybersecurity environment, optimizing prevention and minimizing time to detect and respond leads to much faster remediation of threats. Ultimately, it enables you to achieve better security outcomes.
To learn more and discuss how we can help with your security challenges, visit our website and speak with a member of the team.
Source: Sophos
On May 7, 2021, the largest oil pipeline system in the US suffered a major cyber attack.
A hacker group identified as DarkSide intruded into the colonial pipeline system and stole 100 gigabytes of data within a couple of hours. Following the data theft, attackers infected the pipeline’s IT network with ransomware. The consequences were severe. Fuel disruption, a peak in prices are just the tip of the iceberg. The colonial pipeline had to pay a hefty price of 75 bitcoins (worth $4.4 million at that time) as ransom in hopes of quick recovery. Although, a month later, the company was able to recover much of the ransom payment with the FBI’s help. But this attack woke us all up to the sheer need to protect our digital assets.
One such critical digital asset is web-based applications and services. They have become an indispensable aspect of our everyday life. Verizon’s 2021 Data Breach Investigations Report shows that:
Nearly two-in-five (39%) data breaches arise from web app compromises.
That’s why web application security has become the need of the hour.
Web application security encompasses the security of websites, web applications, and web services such as APIs. So let’s discuss the importance of securing your web applications and the best practices you can follow in this blog.
Why Is Web Application Security More Important in 2022?
Web applications have become quite prevalent in recent years. From online banking to online shopping, we rely on web apps for a wide range of uses in our everyday life.
This wide popularity, in turn, attracts the attention of cybercriminals. Hackers always remain on their toes to find vulnerabilities in web apps and exploit them to their advantage. A recent report by PurpleSec revealed that:
Over 18 million websites suffer malware infections at a given time each week.
Unsecured applications can result in massive service outages and downtime, leading to sales and revenue losses. As per recent estimates by Cybersecurity Ventures, ransomware costs are expected to reach $265 billion by 2031. This goes to show how dearly web application vulnerabilities can cost businesses if they are not taken care of.
In addition to financial losses, the absence of web application security can also threaten the company’s reputation and its goodwill among customers. For example, you lose your sensitive data and lose your customers’ trust during data breaches.
Moreover, the government is now cracking down on companies that do not follow adequate security practices. Some compliances like GDPR, PCI, and more, have been formulated to enforce web security and protect user privacy. Failing to abide by these compliances can lead to heavy fines, penalties, and lawsuits.
How Can You Secure Your Web Applications?
The stats mentioned above only enforce maintaining healthy practices to secure your web applications from the prying eyes of hackers. The most common threat to your web application is cyber security attacks. These include SQL injection, DDoS attacks, broken authentication, and cross-site scripting.
While we cannot stop hackers from inventing new fraud schemes and exploiting applications, we can learn the best web application security practices to mitigate the risks involved.
So, with that agenda in mind, let’s dive in!
1. Keep malicious traffic at bay with Web Application Firewalls
A web application firewall (WAF) is designed to secure web applications from application-layer attacks. It offers robust protection against the most critical web application vulnerabilities, such as cross-site scripting, injection attacks, cross-site forgery, broken authentication, among others.
You can think of WAF as a shield between the web application and the client. It constantly monitors and inspects the HTTP traffic going in and out of web applications. If the traffic is found to be safe, WAF allows it to pass through. On the contrary, malicious traffic is blocked from web apps to prevent threats and attacks.
The web application firewall uses a set of rules, also known as policies, to differentiate between safe and malicious traffic. These policies are customizable and can be tailored to meet the unique needs of your web application.
Web application firewalls can be configured in multiple ways. The two most common types of WAFs are:
- Hardware-based WAFs
- Cloud-based WAFs
Both have their advantages and disadvantages. So choosing the appropriate option for yourself is a matter of understanding your unique business needs and making the decision accordingly.
2. Encrypt sensitive data in transit with TLS
Data security is crucial for web applications. For example, when someone shares confidential information on your application, like personal details or bank credentials, they expect that information to be safely delivered and stored on your web server. That’s where TLS steps in to help.
Transport layer security (TLS) encrypts the communication between client and server via HTTPS protocol. As a result of this encryption, your web application remains protected against data breaches. In addition, TLS also authenticates the parties exchanging the information to prevent any unauthorized data disclosure and modification.
TLS protocol has become a standard security practice in recent years. It is also helpful from the SEO standpoint since Google uses a secure connection as a ranking signal.
To implement TLS on your website, you need to buy a TLS certificate from a certificate authority. Then, install it on your origin server. One can recognize TLS encryption by the padlock icon that appears right before the URL in the address bar. Besides, if the URL begins with “HTTPS”, it’s also a sign that your browser is connected via TLS.
3. Improve your security system with Pen Testing
Pen testing works on one principle: Hack your web app before hackers do.
It may sound outlandish at first, but it’s not. Here’s why.
If you can find vulnerabilities in your web application and take security measures to fix them, your chances of getting hacked in the future will drastically reduce.
That’s the idea behind penetration testing, popularly known as pen test or pen-testing. It’s a preventive measure to reduce, if not eliminate, cyber attacks.
In this cybersecurity exercise, cybersecurity experts, with permission, attempt to find and exploit vulnerabilities in your system.
They use different penetration tools like Nmap, Wireshark, Metasploit, etc., for this purpose. This simulated attack intends to test the effectiveness of your existing security policies and identify unknown vulnerabilities that hackers could exploit. It also discovers loopholes that have the potential to lead to data theft. Thus, the test reports help you identify vulnerabilities before hackers, helping you update your security solutions and patch vulnerabilities in time.
4. Inculcate security practices in the design and development phase
The majority of security incidents are caused due to defects in the design and code of the software. That’s why integrating security practices in the application design and development phase is crucial.
When it comes to the design phase, some of the best security practices include performing threat analysis, implementing design principles like server-side validation to mitigate risks, and building a security test plan.
For secure coding, developers should be educated about the OWASP Top 10 vulnerabilities and the OWASP secure coding practices they can adopt to prevent those vulnerabilities. Developers should also make a habit of scanning their code to catch security vulnerabilities early in the development phase. They can integrate security tools into the DevOps pipeline to find any vulnerability that may have sneaked into their code. This will allow them to revise their code quickly and nip the problem in the bud.
OWASP has also worked actively to identify the best coding security practices that can be integrated into the software development lifecycle to mitigate the most common software vulnerabilities.
5. Adopt a cyber security framework
The last element on our best cyber security practices list is employing a cyber security framework. A cyber security framework is a set of standards, guidelines, and practices that an organization can follow to manage its cyber security risks. The framework aims to reduce the company’s exposure to cyberattacks and identify the most prone areas to these attacks.
There are different types of cyber security frameworks. Some popular ones that dominate the market include the NIST cybersecurity framework, CIS, and ISO/IEC 27001. When it comes to choosing a cyber security framework for your organization, adopt the one that can protect the most vital areas of your business. You can also look at existing security standards prevalent in your industry for inspiration.
Conclusion
The dynamics of the web are ever-changing. Overlooking web application security can lead your business to massive revenue losses and reputational damages. The web application security practices discussed in this blog post will guide you to take actionable steps and set up a web security strategy that offers 24/7 protection and improve your web application’s credibility.
Source: Array Networks
The current Russia-Ukraine crisis is unprecedented. One aspect of the current crisis is the very real concern around increased cyberattacks on an unprecedented scale.
The concern is reasonable: there’s simply no way to know what’s going to happen next. And the concern stems not just from nation-state actors and their proxies: cybercriminals, hacktivists, and vandals also thrive in times of chaos and uncertainty like this.
With all these unknown and unknowable cyber risks and threats swirling around, it’s understandable that people are worried and even afraid and not sure what to do.
The important thing to remember is that we do know what we can do to better protect ourselves during this crisis. These are the same things that we can and should be doing every day and during every crisis. We just need to remember them and act on them.
Focusing and executing on five specific, concrete areas of action can help you better protect yourself and your organization from attacks during this time of increased uncertainty:
- Alert and educate your users about the increased risks
- Update systems, mobile, IoT and network devices and apps
- Run and update security software
- Secure remote access accounts and devices
- Make and verify backups
Alert and educate your users about the increased risks
User education is always a key part of any cybersecurity program. People form the last defense against attack. With all that’s going on, many people may not be thinking about the increased cybersecurity risk and their role in helping to protect themselves and their organization. Help people understand we’re in a time of increased risk and that they need to exercise even more caution than usual against phishing, malicious links and attachments.
Update systems, mobile, IoT and network devices and apps
Keeping systems up to date with patches against vulnerabilities is always important but right now even more so. While people have gotten used to updating their mobile devices and computers using automatic updates, it’s important to also remember to update IoT devices, routers and remote access software and devices. Make it a priority to ensure that you’re updating everything, not just mobile devices and computers.
Run and update security software
Having security software on all your endpoints is important to provide protection against attacks. Out-of-date or misconfigured security software however not only fails to protect but can give a false sense of security. Take time to ensure that you not only have security software in place but that’s it’s fully up-to-date and configured properly. Take the time to verify you’ve got automatic updates working on your security software either by logging into it or through the management console.
Secure remote access accounts and devices
Lately, we’ve seen ransomware and more sophisticated attacks carried out successfully by using remote access to access the target network. This problem has become more serious since the pandemic began and remote access became more common. Two specific things that you should do to better protect your organization against these kinds of attacks is to make sure that your remote access devices and software are up-to-date, and that only valid accounts have remote access capabilities. If you’re not using multi-factor authentication (MFA) to protect your remote access you should look at implementing that as soon as possible as well.
Make and verify backups
Good, reliable, usable backups are your parachute and safety net rolled into one. Having good, reliable, usable backups can help you recover from ransomware and major cyberattacks. They can also help you recover from physical threats like natural or human made disasters. But backups only work if the backups are done correctly and can be restored. Take time to ensure that not only do you have a good backup strategy in place, including storing backups off-site, but that you can successfully restore from those backups quickly and effectively. A good rule of thumb is the “3-2-1 Rule”:
- 3 copies of your backups, including the one you’re using now
- 2 different storage locations for those backups
- 1 of which is offsite/offline
Conclusion
The reality is that we never know what’s going to happen each day. But times like right now bring that uncertainty into clearer focus and help us see that truth more clearly. And the reality is that the cyber threat environment for everyone is significantly higher: chaotic times breed more chaotic times and actions. All this uncertainty it can be overwhelming so that you don’t know what to do. And in the face of extraordinary threats, it can also seem like following ordinary guidance is insufficient. But the reality is that in times and situations like this, keeping focused on the basics still provides a solid foundation that can help you better protect yourself and your organization.
Source: Sophos
Sophos ZTNA provides a number of advantages over remote-access VPN – enabling remote workers to access the applications they need with much stronger security, all while making management a lot easier and providing a smoother end-user experience.
Better security
Sophos ZTNA provides better security for four reasons:
- Sophos ZTNA removes the need for vulnerable old VPN client software on end-user laptops, which has increasingly become the target of ransomware attackers
- Sophos ZTNA integrates device health into connection policies, enabling non-compliant or compromised devices to be denied connections to corporate applications and data
- Sophos ZTNA only connects users to specific applications – not the entire network, eliminating lateral movement
- Sophos ZTNA is unique in integrating with Sophos Intercept X to provide a single-agent solution that combines the world’s best next-gen endpoint with ZTNA – better protecting not just user devices, but also their identities, and the applications and networks they connect to
Simpler management
While remote-access VPN has become a full-time job for many, Sophos ZTNA makes day-to-day management easier:
- It’s easy to deploy. If your apps are all browser based, you can use the clientless option. If you need remote system access, our single agent integrated with Intercept X is also super easy to deploy. And the gateways are also easily set up: all from Sophos Central.
- It’s quick and painless to set up your identity provider in the cloud – particularly if you use Active Directory, as you can easily sync with Azure AD. It’s therefore easy to manage users as they come and go from the organization.
- It’s very simple to add new applications and make them accessible through policies to just the users that need access.
- There is tremendously rich and valuable reporting that provides great insights into bandwidth and resource utilization, allowing you to monitor usage and plan capacity for your networked applications.
Easier to use
Sophos ZTNA is much more reliable, seamless, and transparent than old-school VPN. It doesn’t slow users down, drop connections at the most inopportune time, or create headaches when attempting to connect – from anywhere.
Sophos ZTNA demo video
See Sophos ZTNA in action in this comprehensive demo video, which shows how a system can be set up using clientless access with a couple of different users, applications, and policies. Supporting remote workers shouldn’t be hard, and with Sophos ZTNA, it’s not.
Source: Sophos
In The New Normal in Cybersecurity Part 1, we examined three leading trends in the cybersecurity community over the past year. In this installment, we will take a look into the future and make predictions about where the cybersecurity landscape is potentially headed in 2022 and beyond.
#1: New Laws and Regulations
In the future, it’s likely that new laws and regulations will be enacted as the U.S. government increases its focus on cybersecurity activities, including increased data privacy legislation, increased executive liability, regulations around ransomware payments and rules of engagement for bad actors, and more focused controls over cyber liability insurance. Let’s take a look at each of these items more fully.
We have already seen the Executive Order from President Biden aimed at improving the security of Federal Government networks. With threat actors showing a focus on taking down critical infrastructure, the government will likely step up its efforts to address attacks and data privacy breach requirements. Specifically, for 2022 and beyond, there will most likely be increased emphasis on financial reporting aspects when it comes to privacy, including the cost of a breach to the organization.
Another likely forecast for the future is the increase of liability. Looking across all the information companies have and what the U.S. government possesses, it is critical to determine the steps organizations can take to help one another—and how will that impact liability. For example, when it comes to sharing information, how can security professionals and organizational leaders preserve their own company if they share information? Can shareholders and individuals’ right of action use this information against the company? Addressing liability related to data sharing will be a significant emphasis going forward, so the security community can pull pieces of information together and actually get ahead of the curve without facing significant barriers of liability. Listen to more on this from Chris Reffkin, Chief Information Security Officer, HelpSystems.
In the future, we will also likely see more executives scrutinized for not identifying what those data points and red flags mean to the organization in a compromised situation. The public will judge companies more harshly for not taking the right actions or being aware of security concerns within their organization. As organizations grow, executives must take a very active role in cybersecurity—and in the event that something happens, they have specific multi-layer strategies that prove despite their best efforts, an incident occurred.
Finally, with cyber insurance rates skyrocketing, it is essential for organizations to demonstrate good cyber hygiene to retain their policies at an affordable rate. If companies have poor cyber practices, they will likely not get coverage for the future or will encounter cost-prohibitive policies they cannot afford. As we have seen, cyber insurance carriers have exited the market at an alarming rate, so we may see the shift of companies moving toward a self-insurance model, rather than relying on a third-party provider.
#2: Heightened Cyberthreat Landscape
Now and into the coming year, organizations must buckle down on cybersecurity basics to protect against bad actors. And prevention really is the key to this. Once an attack has taken place, organizations scramble to respond and are reactive to the situation. Companies must take a proactive approach to focus their efforts on security fundamentals. Looking to 2022 and beyond, we will likely see:
- Increased Supply Chain Attacks
- Increased OT/IoT Attacks
- Increased Ransomware-as-a-Service
- Increased Use of Unique and Custom Cybersecurity Toolsets
Let’s highlight more in-depth two of these points. In the future, ransomware-as-a-service will likely increase tremendously. Why? Because breaching a network and gaining a foothold is still a viable option for bad actors. With so many flaws that exist in an organization’s security posture, breaches are common. Ransomware is really just automating a series of steps post exploit. So until the security fundamentals are shored up, these quick smash and grabs are still possible, particularly for SMBs.
Finally, in 2022 and beyond, we will likely see an increase in more skilled bad actors customizing their toolkits for specific targets. They are more difficult to detect, but it also gives them a custom signature. We will also likely witness more bad actors creating a business out of this. Because they have customized their toolkits and have gained a foothold—where the compromise may be undetected for days, months, weeks, or years—bad actors are creating a viable offering, providing illicit access as a means to insert additional malware, ransomware, trojans, backdoors, and to extort more ransom from the organization.
#3: Changes in Market and Organizational Behavior
With all the changes and forces at work, organizations are becoming overwhelmed. They have too many security solutions to monitor and cannot keep up with the demand for alerting and mitigation. In the future, by necessity, companies will look to consolidate their cybersecurity vendors and seek to get security tools and services from a single source or fewer sources. A recent IBM study found that, on average, companies use 45 cybersecurity tools in their networks. With the cybersecurity tech stack spiraling out of control, organizations will look to simplify their approach and work with security providers that can consolidate the greatest number of services under one umbrella.
Finally, and perhaps most overdue, cybersecurity will finally gain a seat at the board table. Organizations cannot unsee what has occurred over the last few years. Now there is greater recognition—and funding—for cybersecurity strategies and solutions. This means we will likely experience a marked shift around organizational playbooks. Specifically, from a risk management activity perspective, companies will move from a focus on asset protection to a focus on loss prevention. They will invest in loss prevention capability, bringing in data security and protection officers and bulking up their security teams. Executives and board members will also likely become more involved in cybersecurity as the need will only intensify in the coming years.
Adapting to a More Uncertain Future
Agile risk management will continue to play an even greater role as organizations adapt to changing conditions and global events. And while there is no guarantee the predictions for 2022 and beyond will come true, there is one thing that is for certain—cybersecurity is more essential than ever. At HelpSystems, we are bringing together cybersecurity solutions, including infrastructure protection, data security, and identity and access management, with intelligence and automation solutions, including threat intelligence, IT and security automation, and centralized analytics, to help companies protect business-critical data and build a more secure, autonomous organization.
Source: HelpSystems
Τhe past year has shown organizations that uncertainty and a transformed reality are the new normal in business. While remote work was intended as a temporary response to the global pandemic, it is now considered a regular part of the business environment—fundamentally altering the way companies operate. This means organizations have had to respond in real-time to shift their cybersecurity strategies and keep up with an expanding IT infrastructure, the explosion of IoT devices, and a new wave of threats from more sophisticated attackers. In Part 1 of this two-part series, we will examine the top three cybersecurity trends of 2021 and examine their implications on organizational security.
#1: Shifting Organizational Behavior
While 2020 seemed like an anomaly at the time, the events of 2021 have shown us that drastic changes are still at work globally—from the continuing dominance of COVID-19 to the social justice movement sweeping through communities to the great resignation of the workforce to a large portion of workers still remote. During the last year, organizations have experienced ongoing shifts, including:
- Increased due diligence of partnerships and M&A activity
- More adoption of a Secure-by-Design approach from product development
- Increased adoption of cybersecurity mesh strategies
- Heightened demand for interoperability
- Continuance of the remote workforce model
- Movement toward greater sustainability based on pressure from customers and shareholders
These large forces make it clear that organizations, and particularly the cybersecurity community, must adopt a more proactive approach into making their business more secure and more flexible. Organizations have been required to adapt to this new normal to accommodate the constant drumbeat of accelerated changes. From a security standpoint, vulnerability management has become more important than ever. Organizations pivoted overnight from operating on premise into a fully remote scenario. In addition, businesses faced a potential slew of new attack vectors. And from a connectivity perspective, security professionals now were facing corporate systems working from unmonitored networks, with the perimeter now expanding into workers’ homes.
The Continued Importance of People, Process, and Technology
Interestingly, the new remote work model has provided both pros and cons to security. For example, home systems and computers may not have the same paths to lateral movement and attacking as in an office, so threat actors have had to adapt to this change. Conversely, from a social engineering perspective, organizations that previously relied exclusively on stopping attacks from a technology perspective have had to recognize the valuable contributions people and processes play in building a strong foundation for overall security. The last year has shown companies the importance of embracing and adopting a defensive posture that includes the combination of people, processes, and technology working together to protect the organization. Joe Vest, Senior Security Consultant for Cobalt Strike by HelpSystems, provides further insights on this.
#2: Cyberthreat Evolution
2021 also saw a transformation in the approach and type of cyberthreats. At the beginning of the pandemic, bad actors started targeting the healthcare industry, with medical facilities and hospitals falling victim to attacks. But during the last year, this expanded into critical infrastructure—like oil and gas—and moved into multi-stage, multi-pronged attacks that are more sophisticated than ever before across multiple verticals.
Companies are having to shift resources to cover potential attack vectors and, in terms of IoT, there is no way to know how secure those devices are that are accessing the network. This makes it incredibly important to ensure network traffic analysis tools are in place and protections are sufficient to minimize attacks.
From a ransomware perspective, the security industry as a whole has shown that it is not keeping pace with bad actors. Organizations—especially small-to-medium-sized businesses (SMBs)—are vulnerable because they often do not have the means to do detection and response. And once an incident happens, ransomware becomes more effective. Once an entity has been identified as willing to pay the ransom, the organization opens itself up to more targeted, multi-pronged attacks. It is clear that organizations cannot patch their way out of problems any more—instead it takes a multi-layered security approach to defend against ransomware. Watch Mieng Lim, Vice President, Product Management, Digital Defense by HelpSystems, discuss how paying a ransom can hurt more than it helps.
#3: Adapting Defensive Strategies
While cyberthreats have evolved over the last year, cybersecurity has also seen a number of shifts in defensive strategies. One strategy organizations have employed more frequently is combining penetration testing with vulnerability management. Whether attempting to take on internal pen testing or engaging with pen testing services from a third-party engagement, this defensive strategy taps into the strengths of both vulnerability management and pen testing to reveal and prioritize security weaknesses before a threat actor might.
However, this is only one aspect of threat-based testing. The rise of other combat strategy trends during 2021 included:
- Broader Deployment of Multi-Factor or Two-Factor Authentication
- Strengthening Identity Governance and Access Management Policies
- Enhancing Overall Application and Data Security
Organizations that adopted these multi-layer strategies were more effective in reducing their attack surfaces, and in the identification and discovery of potential threats. In other words, security teams that successfully leveraged adaptive security tools to monitor events, and then employed specific processes to determine if those activities were anomalous in their environment, were more successful in minimizing loss and preventing further damage across the business.
Learning from the Past, Moving Toward Greater Protection in the Future
If the continued events of 2021 have reinforced anything, it is that organizations should not be surprised by disruptions or caught off guard in protecting their networks and infrastructure from attack. The best safeguard within this turbulent environment is to put in place a multi-layered security approach that is both proactive to prevent potential attacks and responsive when attacks can—and likely will—occur.
Source: HelpSystems
We are pleased to announce exciting enhancements to the Investigations dashboard and integration of Microsoft 365 data into Sophos XDR.
Minimize time to investigate with the Investigations dashboard
Time is of the essence when investigating an incident. Understanding scope and impact is critical to forming a fast, effective response. The Investigations dashboard is designed to help busy teams work even more effectively.
Save time, see the bigger picture with aggregated detections
Multiple, separate threat detections in the same broader incident are automatically correlated and assigned to the same investigation. For example, detections that trigger the same threat classification rule within 24 hours will be added to a single investigation, eliminating the need for an analyst to add them manually. Detections affecting the same devices will also be automatically added to the same Investigation, saving the SOC team valuable time and helping them quickly understand the broader scope and impact of an incident.
Analysts can also manually add detections to an investigation or create an investigation, with a multi-select checkbox to minimize click time.
Respond faster thanks to automatic email notification
When a new investigation is created, relevant team members are automatically notified to respond as quickly as possible. The email includes a summary of the investigation with crucial information to get the analyst up to speed, such as investigation ID, detections risk score, number of impacted devices and a quick link to the investigation. When a new team member is assigned to an in-progress investigation, they will be automatically notified.
Work as a cohesive team using dynamic notes
The Investigation notes section enables teams to share progress and results quickly. Freeform text can be added making it easy for teams with multiple analysts to collaborate, share intelligence and respond faster to threats.
See the bigger picture –new Microsoft 365 data integration
Many organizations use the Microsoft 365 platform, making it a valuable piece of the cybersecurity puzzle. The new MS 365 connector in Sophos Central enables XDR users to include this rich data source in their threat investigations and IT operations security maintenance. For example, to identify users with suspiciously high numbers of failed login attempts.
Getting started
All Sophos XDR customers can access the Investigations dashboard from Sophos Central. Most of these powerful features are already available to Sophos XDR customers, with the last few arriving by February 7, 2022. To access MS 365 data, the connector needs to be enabled: log into Sophos Central -> Third-party integrations -> Microsoft 365 user activity logs.
If you’d like to try out Sophos XDR, you can either start an in-product trial (if you have a Sophos Central account) or take a trial of Intercept X, which includes XDR.
Source: Sophos
Security Information and Event Management (SIEM) solutions are often seen as a necessity only for large enterprises with massive environments to monitor for security threats. While this may have been true over a decade ago, in the early days of SIEM. Since then organizational IT infrastructures have become increasingly multifaceted, and the threat landscape continues to evolve. These days, small to medium sized businesses (SMBs) also struggle to manually manage the security of their IT environments. But how exactly can a SIEM benefit your SMB? Read on to find out.
1. SIEMs Efficiently Prioritize and Escalate Threats.
A breach can be devastating for any organization, and SMBs are no exception. In fact, 60% of small companies close within six months of a successful cyber-attack. Swift detection to prevent an attack or reduce dwell time is critical to limiting damage. SIEMs are well known for their ability to monitor and detect threats in real time. Once detected, a SIEM can determine its risk prioritization, escalating the event to ensure it quickly gets to the right person. Additionally, some SIEMs normalize data into readable language so security teams don’t have to waste time translating what an event means. They can also correlate events, providing additional context to aid in threat investigation and analysis.
2. SIEMs Reduce Alert Fatigue.
SMBs often have complex environments just like larger enterprises. Any modern organization now requires a sizeable portfolio to manage even basic day-to-day operations. This has become even more true with the increase of remote work. With every asset added to an infrastructure comes new potential threat vectors and more security event notifications. Even small organizations can end up with hundreds, if not thousands, of security events every day. With this many alerts coming through, it’s no surprise that dangerous security risks or suspicious behavior can pass by unnoticed.
Instead of manually sifting through these events, a SIEM allows you to filter alerts so you only get the notifications you want. SIEMs even allow you to tailor these filters for each data stream, since an event may indicate a threat on one device, it may be completely benign on another. This ensures that there aren’t just a reduced number of notifications, but also that these are alerts worth looking into.
3. SIEMs Centralize Security.
As mentioned above, SMBs may have limited personnel, so it’s critical to have tools that enable these smaller security teams to work smarter. Complex infrastructures don’t just produce hundreds of security events, they produce them in different places. Critical alerts may be missed simply because there are too many consoles to check. A SIEM can consolidate any number of data streams, providing a singular source of truth. Typically, a SIEM has a console that can be tailored to your needs, with dashboards or displays that provide details of your choosing. Some SIEM tools, like Event Manager, even allow for integration of unique or unusual data sources, like third party applications, to fully centralize your security monitoring.
4. SIEMs Assist with Compliance Efforts.
SMBs are not exempt from security regulations like PCI-DSS, SOC, CMMC, and GDPR. SIEMs have various features that can help an organization stay compliant with regulations. For example, PCI DSS requires keeping logs of any changes, additions, or deletions to a root account, all of which a SIEM can flag. Additionally, SIEMs have detailed audit trails and can generate reports that can provide proof of compliance to assessors.
Choosing the Right SIEM for Your SMB
Since many SIEMs are geared towards large enterprises, they may not always be suited for SMBs, who may be working with more limited budgets. However, there are a variety of mid-range SIEM solutions on the market that are easy to use and provide better value than some of the heavy-weight options without the over-complexity.
One option to consider is Event Manager. Event Manager is a simplified SIEM solution that’s easier to manage than an enterprise-level option, but still has the capabilities and features needed to seamlessly scale alongside a company, including centralized monitoring, swift incident response, and both built-in and tailored integrations. Additionally, Event Manager comes with a team of cybersecurity experts who can help with deployment and regular tuning. Finally, Event Manager’s pricing model ensures that SMBs can grow without unexpected jumps in cost. While many SIEM solutions license by the amount of data processed, which can be unpredictable and costly, Event Manager uses predictable device-based pricing.
No matter the solution you choose, a SIEM can help any SMB gain visibility into their environment, providing insights on critical access and reducing the risk of security breaches.
Source: HelpSystems
At Sophos, we’re committed to helping organizations secure essential resources and we’re proud to be recognized for the continued expansion of our cloud security portfolio.
As a global leader in cloud security, we’ve been recognized by CRN®, a brand of The Channel Company, in its annual list of the Coolest Cloud Companies. This list honors groundbreaking cloud technology providers across five key categories, including cybersecurity
Trusted to prevent cybersecurity incidents by 70% of the world’s top universities and top Fortune 500 companies, it’s never been more critical for such organizations to adopt cloud services and to optimize security posture, block advanced threats, and have expert resources available to monitor the security of these environments 24/7.
“Sophos is best in class when it comes to breadth and depth of innovative cybersecurity offerings that optimize protection against the most sophisticated and complex never-seen-before threats,” said Scott Barlow, Sophos Vice President of Global MSP and Cloud Alliances.
Our approach combines prevention, detection, and response across endpoint, cloud workloads, networks, configuration, and compliance – with 24/7 Managed Detection and Response (MDR) services to secure data, proactively prevent vulnerabilities, and block advanced threats.
In the last year, we’ve expanded our capabilities across all the following areas:
- Multi-cloud threat detection and response with Sophos XDR
- IAM security: User activity anomaly detection
- Sophos achievement of AWS Level 1 MSSP Competency status
- The acquisition of Capsule8: New Linux server and container security capabilities
- The acquisition of Refactr: Security Orchestration Automation and Response Capabilities
Commitment to the channel
Each year, the CRN Cloud 100 are recognized as forward-thinking cloud suppliers that have demonstrated an unwavering commitment to working with channel partners. Our commitment to the channel and our continued innovation in product and service development is enabling partners to better protect their customers and evolve to the changing threat and infrastructure landscapes: to better protect their data endpoints and networks, irrespective of environment.
This includes the relaunch of the Sophos Cloud Security Provider (CSP) program to provide training, recognition, and financial incentives to help partners support their customers using or migrating to the public cloud. We were the first next-gen security vendor to introduce a program specifically designed to help partners address this revenue growth opportunity and make the purchase and management of our products in Microsoft Azure, Amazon Web Services, Google Cloud Platform, and Oracle Cloud Infrastructure channel-friendly.
Modernizing cybersecurity procurement through cloud marketplaces is another key aspect of the commitment to the channel and our customers, ensuring our partners continue to provide the best service for any organization. Sophos Cloud Security is available in AWS Marketplace to help customers improve procurement processes in order to match the speed of cloud while maintaining governance – and, at the same time, enabling customers to continue purchasing through their preferred Sophos Partner in AWS Marketplace.
Take a demo of Sophos Cloud Security today, or for more information visit Sophos.com/Cloud.
The Sophos Cloud Security Provider partner program is free to join at Sophos.com/CSP.
A study of 5,400 IT professionals has revealed a correlation between direct experience of ransomware and adoption of a zero trust approach.
Organizations that had experienced a ransomware attack in the previous year (defined as multiple devices being impacted but not necessarily encrypted) reporting considerably higher levels of awareness of the zero trust approach and were more advanced in their implementation of zero trust network access (ZTNA) solutions than those that hadn’t experienced an incident.
It is likely that these organizations’ direct experience of ransomware accelerated the implementation of a zero trust approach to help prevent future attacks.
The findings result from an independent survey of 5,400 IT professionals in organizations with between 100 and 5,000 employees that was conducted by research house Vanson Bourne on behalf of Sophos in 2021.
The role of ZTNA in preventing ransomware attacks
Breaching the victim’s network is one of the first steps in a ransomware attack. The rapid increase in remote working over the last two years has hugely increased the opportunity for attackers to exploit vulnerable VPN clients to get a foothold in an organization. Once inside, they are often free move laterally throughout the network, escalating privileges and progressing the attack.
By eliminating vulnerable VPN client software, granularly controlling access based on device health and identity, and micro-segmenting applications, ZTNA stops attackers from both breaching the organization and from moving around it, even if they obtain legitimate credentials.
[To learn more about the role of lateral movement in ransomware attacks, read the Sophos research report Windows Services Lay the Groundwork for a Midas Ransomware Attack that details how adversaries exploited remote services and access tools to hold a technology company to ransom.]
Finding one: Ransomware victims have much greater familiarity with the ZTNA approach
IT professionals in organizations that had been hit by ransomware in the previous year are almost 50% more likely be ‘very familiar’ with the ZTNA approach than those whose organizations hadn’t experienced an incident (59% vs 39%). This rises to 71% among those whose organizations had been hit and they paid the ransom.
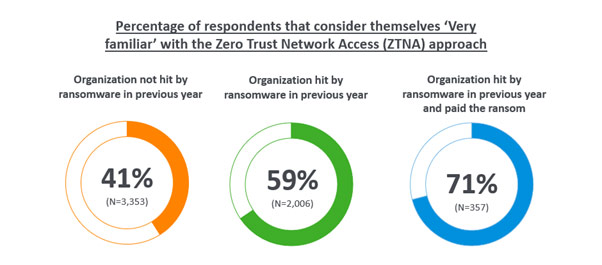
Further illustrating this point, just 10% of ransomware victims have little or no familiarity with ZTNA, compared with 21% of those whose organization hasn’t fallen victim.
Finding two: Ransomware victims are more advanced in their adoption of the zero trust approach
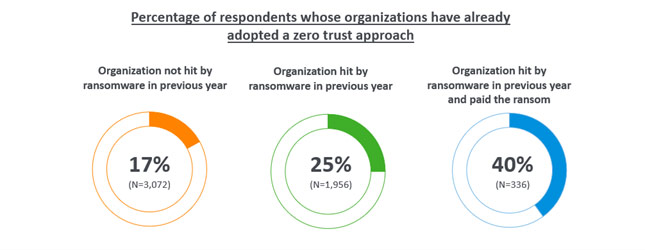
One quarter (25%) of those whose organization experienced a ransomware attack in the previous year have already fully adopted a zero trust approach, rising to 40% of those whose organizations were hit and paid the ransom. In comparison, just one sixth (17%) of those that hadn’t experienced an attack have already fully migrated to this approach.
Finding three: Ransomware victims have different motivations for adopting a zero trust approach
Respondents were asked about their motivations for adopting a zero trust approach and, while there were several commonalities, there were also clear areas of difference.
- ‘To improve our overall cybersecurity posture’ was the most common motivator among both victims and non-victims
- The second most common motivator among ransomware victims was the desire to ‘simplify our cybersecurity operations’ (43%), potentially reflecting that complex security had contributed to their previous attack
- Ransomware victims are also heavily motivated by ‘supporting our move to increased use of the cloud’ (42%). This dropped to 30% amongst those that hadn’t experienced a recent attack
- Similarly, ransomware victims were also much more likely to say that ‘to move from a CAPEX to an OPEX model´ was one of the main factors behind their zero trust approach adoption (27% vs. 16%, and rising to 34% among those that had been hit by ransomware and paid the ransom)
Finding four: The pandemic was more likely to positively impact the zero trust adoption plans of ransomware victims
For many organizations the pandemic had a positive impact on their plans for adopting a zero trust approach. For many, it created a need for zero trust that they didn’t have before. This is understandable: many companies and public bodies were previously wholly office-based and so didn’t have a need to provide secure remote access.
Half (50%) of ransomware victims and 36% of non-victims reported that the pandemic enabled them to move budget to adopting a zero trust approach, while many also reported that it enabled them to divert people and/or money from other activities to the move to zero trust.
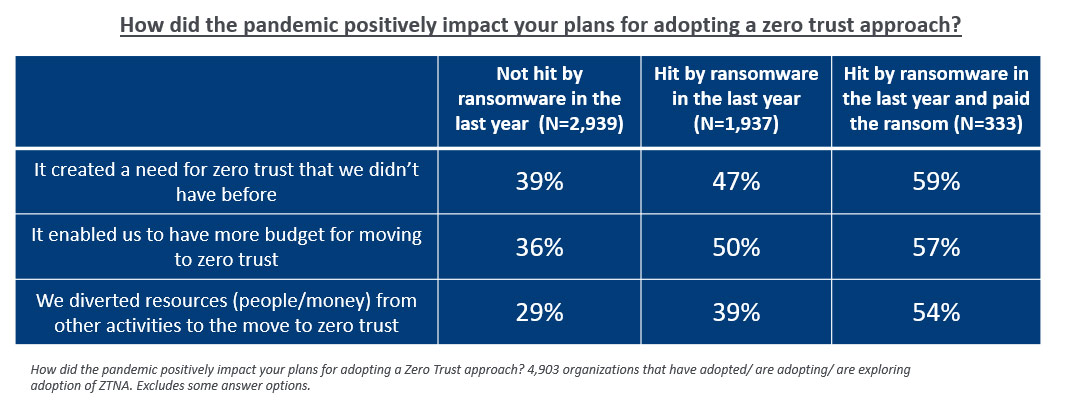
The survey findings highlight that organizations that fell victim to ransomware and paid the ransom were most likely to experience a positive pandemic impact on their zero trust adoption. It seems that pain of the ransomware attack might have concentrated minds and resources on effectively mitigating a future ncident.
Introducing Sophos Zero Trust Network Access (ZTNA)
Sophos ZTNA is a much more secure and easy-to-manage remote access solution that delivers a transparent, frictionless experience for end-users.
- By removing the need for VPN clients, Sophos ZTNA reduces the attack surface, making it harder for ransomware actors to get on your network
- Sophos ZTNA constantly checks user and device security, delivering continuous high-level of controls and preventing attackers from exploiting a previously authenticated user’s access
- Granular access controls enable you to easily restrict access to specific resources to those who need them, preventing adversaries from moving laterally across your network
- Sophos ZTNA uses the same agent as Sophos Intercept X endpoint protection, enabling customers to enhance their protection without adding device overhead
- It is managed from the cloud-based Sophos Central platform, enabling customers to manage all their Sophos solutions via a single interface for enhanced day-to-day management and control
With the average cost of ransomware remediation now $1.85 million for small and mid-sized organizations, moving to secure remote access via Sophos ZTNA is a sensible investment.
Try for yourself
If you’d like to try Sophos ZTNA for yourself, start a no-obligation test drive:
- Complete the short form on our website. You’ll be up and running in no time!
- Existing Sophos Central users can click on the Free Trials link in the bottom left corner of the console and select Sophos ZTNA
Source: Sophos
[vc_row][vc_column width=”1/1″][vc_single_image media=”101812″ media_width_percent=”100″ alignment=”center”][vc_empty_space empty_h=”2″][vc_button button_color=”color-150912″ size=”btn-xl” border_animation=”btn-ripple-out” custom_typo=”yes” font_family=”font-762333″ font_weight=”900″ letter_spacing=”fontspace-210350″ border_width=”2″ display=”inline” link=”url:mailto%3Asales%40nss.gr%3Fsubject%3DSophos%20XGS%20Architect%20Training%26body%3DI%20would%20like%20to%20participate%20in%20the%20XGS%20Architect%20Training%20on%20March%208%20to%2010%2C%202022||target:%20_blank|” icon=”fa fa-hand-o-right”]Book Your Training Today![/vc_button][vc_button button_color=”color-283957″ size=”btn-xl” border_animation=”btn-ripple-out” custom_typo=”yes” font_family=”font-377884″ font_weight=”900″ letter_spacing=”fontspace-210350″ border_width=”2″ display=”inline” link=”|||” icon=”fa fa-volume-control-phone”]Call us now for more +30 211 8000 330[/vc_button][vc_empty_space empty_h=”2″][vc_separator sep_color=”color-210407″][/vc_column][/vc_row][vc_row][vc_column][vc_column_text]
Sophos XG Architect Training
Τρίτη 8 Μαρτίου 2022 – Πέμπτη 10 Μαρτίου 2022
(3 ημέρες εκπαίδευσης)
Αυτό το τριήμερο πρόγραμμα εκπαίδευσης σχεδιάστηκε και προορίζεται για έμπειρους τεχνικούς που θέλουν να εγκαθιστούν, αναπτύσσουν, διαμορφώνουν και να υποστηρίζουν το XG Firewall σε παραγωγικά περιβάλλοντα και είναι το αποτέλεσμα βαθιάς μελέτης πάνω στο τείχος προστασίας επόμενης γενιάς της Sophos. Το πρόγραμμα αποτελείται από παρουσιάσεις και πρακτικές ασκήσεις εργαστηρίων για την ενίσχυση του διδακτικού περιεχομένου. Λόγω της φύσης της παράδοσης και της ποικίλης εμπειρίας των εκπαιδευομένων, ενθαρρύνεται η ανοικτή συζήτηση κατά τη διάρκεια της εκπαίδευσης/ κατάρτισης.
Προαπαιτούμενα
XG Firewall _ Certified Engineer course and delta modules up to version 18.5
Συνιστώμενες γνώσεις
- Knowledge of networking to a CompTIA N+ level
- Knowledge of IT security to a CompTIA S+ level
- Experience configuring network security devices
- Be able to troubleshoot and resolve issues in Windows networked environments
- Experience configuring and administering Linux/UNIX systems
Περιεχόμενο της εκπαίδευσης
- Module 1: Deployment
- Module 2: Base Firewall
- Module 3: Network Protection
- Module 4: Synchronized security
- Module 5: Web server Protection
- Module 6: Site to site connections
- Module 7: Authentications
- Module 8: Web Protection
- Module 9: Wireless
- Module 10: Remote Access
- Module 11: High Availability
- Module 12: Public Cloud
Certification
+ exam: Sophos XG Architect
Διάρκεια: 3 ημέρες
Πρόγραμμα
Εκπαιδευτής: Μιχάλης Ελευθέρογλου
Training room :NSS ATC training room 3rd floor (available also by webex)
Ημέρα 1η, Τρίτη 8 Μαρτίου 2022
9:30-10:45 Module 1: Deployment and Lab
- Recall important information from Engineer courses
- Deployment modes supported by the XG Firewall
- Understand a range of scenarios where each deployment mode would commonly be used
- Use built-in tools to troubleshoot issues
- Labs
10:45-11:00 Διάλειμμα
11:00-13:00 Module 2: Base Firewall
- Explain how the XG firewall can be accessed
- Understand the types fo interfaces that can be created
- Understand the benefits of Fast Path Technology
- Configure routing per firewall rule
- Understand best practice for ordering firewall rules
- Explain what Local NAT policy is and known how to configure it.
13:00-14:00 Γεύμα
14:00-16:00 Labs
- Activate the Sophos XG Firewalls
- Post installation Configuration
- Bridge interfaces
- Create a NAT rule to load balance access to servers
- Create a local NAT policy
- Configure routing using multiple WAN links
- Configure policy-based routing for an MPLS scenario
- Install Sophos Central
16:00-16:15 Διάλειμμα
16:15-17:15 Module 3:Network Protection and Lab
- Explain what IPS is and how traffic can be offloaded to Fastpath
- Demonstrate how to optimize workload y configuring IPS policies
- Examine advanced Intrusion Prevention and optimize policies
- Configure advanced DOS Protection rules
- Demonstrate how the strict policy can be used to protect networks
- Labs- Create Advanced DoS Rules
Ημέρα 2η, Τετάρτη 9 Μαρτίου 2022
9:30-11:00 Module 4: Synchronized Security and Labs
- Explain how Security Heartbeat works
- Configure Synchronized Security
- Deploy Synchronized Security in discover and inline modes
- Understand the advantages and disadvantages of deploying
- Synchronizes Security in different scenarios
- Labs
- Configure source-Based Security
- Hearteat firewall rules
- Destination based Security Heartbeat
- Missing Security Heartbeat
- Lateral Movement Protection
11:00-11:15 Διάλειμμα
11:15-13:45 Module 5 Webserver Protection and Labs
- Explain how Websever Protection works
- Describe protection features for a web application
- Configure Web Server authentication
- Publish a web service using the Web Application Firewall
- Use the preconfigured templates to configure Web Server Protection for common purposes
- Configure SlowHTTP protection
- Labs (Web Application Firewall)
- Labs (Load balancing with Web Server Protection)
- Labs (Web Server Authentication and path-specific routing)
13:45-14:45 Διάλειμμα και γεύμα
14:45-17:45 Module 6: Site to site connections and Labs
- Configure and deploy site to site VPNs in a wide range of environment
- Implement IPsec NATing and failover
- Check and modify route precedence
- Create RED tunnels between XG firewalls
- Understand when to use RED
- Labs ( Create an IPsec site to site VPN
- Labs ( Configure VPN network NATing )
- Labs (Configure VPN failover)
- Labs (Enable RED on the XG firewall)
- Labs (Create a RED tunnel between two XG Firewalls
- Labs (Configure routing for the RED tunnel)
- Labs (Configure route-based VPN)
Ημέρα 3η, Πέμπτη 10 Μαρτίου 2022
9:00-10:00 Module 7: Authentications and Labs
- Demonstrate how to configure and use RADIUS accounting
- Deploy STAS in large and complex environment
- Configure SATC and STAS together
- Configure Secure LDAP and identify the different secure connections available
- Labs (configure an Active Directory Authentication server)
- Labs (configure single sing-on using STAS
- Labs (Authenticate users over a site to site VPN)
10:00-11:15 Module 8: Web Protection
- Choose the most appropriate type for web protection in different deployment scenarios
- Enable web filtering using the DPI engine or legacy web proxy
- Configure TLS inspection using the DLP engine or legacy web proxy
- Labs (Install the SSL CA certificate)
- Labs (Configure TLS inspection rules)
- Labs (Create a custom web policy for users)
11:15-11:30 Διάλειμμα
11:30-12:15 Module 9: Wireless
- Explain how Sophos Access Points are deployed and identify some common issues
- Configure RADIUS authentication
- Configure a mesh network
12:15-13:05 Module 10:Remote Access
- Configure Sophos Connect and manage the configuration using Sophos Connect Admin
- Configure an IPsec remote access VPN
- Configure an L2TP remote access VPN for mobile devices
- Labs (Sophos Connect)
13:05-14:25 Module 11: High Availability
- Explain what HA is and how it operates
- Demonstrate how to configure HA and explain the difference between quick and manual configuration
- List the prerequisites for high availability
- Perform troubleshooting steps andc heck the logs to ensure that HA is set up correctly.
- Explain the packet flow in high availability
- Demonstrate how to disable HA
- Labs (Create an Active-Passive cluster)
- Labs (Disable High Availability)
14:25-15:05 Διάλειμμα και γεύμα
15:05-16-15 Public Cloud and Labs
- Deploy XG firewall in complex network enviroments
- Explain how XG firewall process traffic and use this information to inform the configuration
- Configure advanced networking and protection features
- Deploy XG firewall on public cloud infrastructure
- Labs (Put a service in debug mode to gather logs)
- Labs (Retrieving log files)
- Labs (Troubleshoot an issue from an imported configuration file)
- Labs (Deploy an XG Firewall on Azure (simulation)
16:15 (Εξετάσεις)[/vc_column_text][vc_single_image media=”101812″ media_width_percent=”100″ alignment=”center”][vc_empty_space empty_h=”2″][vc_button button_color=”color-150912″ size=”btn-xl” border_animation=”btn-ripple-out” custom_typo=”yes” font_family=”font-762333″ font_weight=”900″ letter_spacing=”fontspace-210350″ border_width=”2″ display=”inline” link=”url:mailto%3Asales%40nss.gr%3Fsubject%3DSophos%20XGS%20Architect%20Training%26body%3DI%20would%20like%20to%20participate%20in%20the%20XGS%20Architect%20Training%20on%20March%208%20to%2010%2C%202022||target:%20_blank|” icon=”fa fa-hand-o-right”]Book Your Training Today![/vc_button][vc_button button_color=”color-283957″ size=”btn-xl” border_animation=”btn-ripple-out” custom_typo=”yes” font_family=”font-377884″ font_weight=”900″ letter_spacing=”fontspace-210350″ border_width=”2″ display=”inline” link=”|||” icon=”fa fa-volume-control-phone”]Call us now for more +30 211 8000 330[/vc_button][vc_separator sep_color=”color-210407″][/vc_column][/vc_row]
[vc_row][vc_column width=”1/1″][vc_single_image media=”101812″ media_width_percent=”100″ alignment=”center”][vc_empty_space empty_h=”2″][vc_button button_color=”color-150912″ size=”btn-xl” border_animation=”btn-ripple-out” custom_typo=”yes” font_family=”font-762333″ font_weight=”900″ letter_spacing=”fontspace-210350″ border_width=”2″ display=”inline” link=”url:mailto%3Asales%40nss.gr%3Fsubject%3DSophos%20XGS%20Architect%20Training%26body%3DI%20would%20like%20to%20participate%20in%20the%20XGS%20Architect%20Training%20on%20March%208%20to%2010%2C%202022||target:%20_blank|” icon=”fa fa-hand-o-right”]Book Your Training Today![/vc_button][vc_button button_color=”color-283957″ size=”btn-xl” border_animation=”btn-ripple-out” custom_typo=”yes” font_family=”font-377884″ font_weight=”900″ letter_spacing=”fontspace-210350″ border_width=”2″ display=”inline” link=”|||” icon=”fa fa-volume-control-phone”]Call us now for more +30 211 8000 330[/vc_button][vc_separator sep_color=”color-210407″][/vc_column][/vc_row][vc_row row_height_percent=”0″ back_color=”color-lxmt” overlay_alpha=”50″ gutter_size=”3″ column_width_percent=”100″ shift_y=”0″ z_index=”0″][vc_column width=”1/1″][vc_custom_heading heading_semantic=”h1″ text_font=”font-377884″ text_size=”h1″ text_weight=”900″ text_color=”color-210407″]
Sophos XGS Architect Training
[/vc_custom_heading][/vc_column][/vc_row][vc_row row_height_percent=”0″ overlay_alpha=”50″ gutter_size=”3″ column_width_percent=”100″ shift_y=”0″ z_index=”0″ shape_dividers=””][vc_column width=”1/1″][vc_button button_color=”color-161549″ size=”btn-xl” radius=”btn-round” custom_typo=”yes” font_family=”font-377884″ font_weight=”900″ border_width=”0″ link=”|||rel:nofollow”]April 1st 2022 is an important date for you as a Sophos partner.[/vc_button][vc_column_text]
On this day, a new compliance period for your partner level classification will start.
[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column][vc_column_text]
Tuesday 8 March 2022 – Thursday 10 March 2022
(3 days Training / hybrid & online)
This three-day training program was designed and intended for experienced technical professionals who want to install, configure and support the XGS Firewall in production environments and is the result of an in-depth study on the next generation firewall of Sophos. The program consists of presentations and practical workshops for the enhancement of teaching content. Due to the nature of the traditions and the varied experience of the trainees, open discussion is encouraged during the training.
Requirement
- XGS Firewall _ Certified Engineer course and delta modules up to version 18.5
Recommended Knowledge
- Knowledge of networking to a CompTIA N+ level
- Knowledge of IT security to a CompTIA S+ level
- Experience configuring network security devices
- Be able to troubleshoot and resolve issues in Windows networked environments
- Experience configuring and administering Linux/UNIX systems
Content
- Module 1: Deployment
- Module 2: Base firewall
- Module 3: Network Protection
- Module 4: Synchronized security
- Module 5: Web server Protection
- Module 6: Site to site connections
- Module 7: Authentications
- Module 8: Web Protection
- Module 9: Wireless
- Module 10: Remote Access
- Module 11: High Availability
- Module 12: Pulic Cloud
Certification
+ exam: Sophos XGS Architect
Duration 3 days
Language: English
[/vc_column_text][/vc_column][/vc_row][vc_row row_height_percent=”0″ back_color=”color-lxmt” overlay_alpha=”50″ gutter_size=”3″ column_width_percent=”100″ shift_y=”0″ z_index=”0″][vc_column width=”1/1″][vc_custom_heading heading_semantic=”h1″ text_font=”font-377884″ text_size=”h1″ text_weight=”900″ text_color=”color-210407″]
Agenda
[/vc_custom_heading][/vc_column][/vc_row][vc_row][vc_column][vc_column_text]
Trainer: Micheal Eleftheroglou
Training room: NSS ATC training room 3rd floor (available also by webex)
Day 1 Tuesday, March 8th, 2022
9:30-10:45 Module 1: Deployment and Lab
- Recall important information from Engineer courses
- Deployment modes supported by the XGS Firewall
- Understand a range of scenarios where each deployment mode would commonly be used
- Use built-in tools to troubleshoot issues
- Labs
10:45-11:00 break
11:00-13:00 Module 2: Base Firewall
- Explain how the XGS firewall can be accessed
- Understand the types fo interfaces that can be created
- Understand the benefits of Fast Path Technology
- Configure routing per firewall rule
- Understand best practice for ordering firewall rules
- Explain what Local NAT policy is and known how to configure it.
13:00-14:00 Lunch
14:00-16:00 Labs
- Activate the Sophos XGS Firewalls
- Post installation Configuration
- Bridge interfaces
- Create a NAT rule to load balance access to servers
- Create a local NAT policy
- Configure routing using multiple WAN links
- Configure policy-based routing for an MPLS scenario
- Install Sophos Central
16:00-16:15 Break
16:15-17:15 Module 3:Network Protection and Lab
- Explain what IPS is and how traffic can be offloaded to Fastpath
- Demonstrate how to optimize workload y configuring IPS policies
- Examine advanced Intrusion Prevention and optimize policies
- Configure advanced DOS Protection rules
- Demonstrate how the strict policy can be used to protect networks
- Labs- Create Advanced DoS Rules
Day 2 Wednesday, March 9th, 2022
9:30-11:00 Module 4: Synchronized Security and Labs
- Explain how Security Heartbeat works
- Configure Synchronized Security
- Deploy Synchronized Security in discover and inline modes
- Understand the advantages and disadvantages of deploying
- Synchronizes Security in different scenarios
- Labs
- Configure source-Based Security
- Hearteat firewall rules
- Destination based Security Heartbeat
- Missing Security Heartbeat
- Lateral Movement Protection
11:00-11:15 Break
11:15-13:45 Module 5 Webserver Protection and Labs
- Explain how Websever Protection works
- Describe protection features for a web application
- Configure Web Server authentication
- Publish a web service using the Web Application Firewall
- Use the preconfigured templates to configure Web Server Protection for common purposes
- Configure SlowHTTP protection
- Labs (Web Application Firewall)
- Labs (Load balancing with Web Server Protection)
- Labs (Web Server Authentication and path-specific routing)
13:45-14:45 Break and Lunch
14:45-17:45 Module 6: Site to site connections and Labs
- Configure and deploy site to site VPNs in a wide range of environment
- Implement IPsec NATing and failover
- Check and modify route precedence
- Create RED tunnels between XGS firewalls
- Understand when to use RED
- Labs ( Create an IPsec site to site VPN
- Labs ( Configure VPN network NATing )
- Labs (Configure VPN failover)
- Labs (Enable RED on the XGS firewall)
- Labs (Create a RED tunnel between two XGS Firewalls
- Labs (Configure routing for the RED tunnel)
- Labs (Configure route-based VPN)
Day 3 Thursday, March 10th, 2022
9:00-10:00 Module 7: Authentications and Labs
- Demonstrate how to configure and use RADIUS accounting
- Deploy STAS in large and complex environment
- Configure SATC and STAS together
- Configure Secure LDAP and identify the different secure connections available
- Labs (configure an Active Directory Authentication server)
- Labs (configure single sing-on using STAS
- Labs (Authenticate users over a site to site VPN)
10:00-11:15 Module 8: Web Protection
- Choose the most appropriate type for web protection in different deployment scenarios
- Enable web filtering using the DPI engine or legacy web proxy
- Configure TLS inspection using the DLP engine or legacy web proxy
- Labs (Install the SSL CA certificate)
- Labs (Configure TLS inspection rules)
- Labs (Create a custom web policy for users)
11:15-11:30 Break
11:30-12:15 Module 9: Wireless
- Explain how Sophos Access Points are deployed and identify some common issues
- Configure RADIUS authentication
- Configure a mesh network
12:15-13:05 Module 10:Remote Access
- Configure Sophos Connect and manage the configuration using Sophos Connect Admin
- Configure an IPsec remote access VPN
- Configure an L2TP remote access VPN for mobile devices
- Labs (Sophos Connect)
13:05-14:25 Module 11: High Availability
- Explain what HA is and how it operates
- Demonstrate how to configure HA and explain the difference between quick and manual configuration
- List the prerequisites for high availability
- Perform troubleshooting steps andc heck the logs to ensure that HA is set up correctly.
- Explain the packet flow in high availability
- Demonstrate how to disable HA
- Labs (Create an Active-Passive cluster)
- Labs (Disable High Availability)
14:25-15:05 Break – Lunch
15:05-16-15 Public Cloud and Labs
- Deploy XGS firewall in complex network enviroments
- Explain how XGS firewall process traffic and use this information to inform the configuration
- Configure advanced networking and protection features
- Deploy XGS firewall on public cloud infrastructure
- Labs (Put a service in debug mode to gather logs)
- Labs (Retrieving log files)
- Labs (Troubleshoot an issue from an imported configuration file)
- Labs (Deploy an XGS Firewall on Azure (simulation)
16:15 (Exams)[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_separator sep_color=”color-210407″][vc_empty_space empty_h=”2″][vc_button button_color=”color-150912″ size=”btn-xl” border_animation=”btn-ripple-out” custom_typo=”yes” font_family=”font-762333″ font_weight=”900″ letter_spacing=”fontspace-210350″ border_width=”2″ display=”inline” link=”url:mailto%3Asales%40nss.gr%3Fsubject%3DSophos%20XGS%20Architect%20Training%26body%3DI%20would%20like%20to%20participate%20in%20the%20XGS%20Architect%20Training%20on%20March%208%20to%2010%2C%202022||target:%20_blank|” icon=”fa fa-hand-o-right”]Book Your Training Today![/vc_button][vc_button button_color=”color-283957″ size=”btn-xl” border_animation=”btn-ripple-out” custom_typo=”yes” font_family=”font-377884″ font_weight=”900″ letter_spacing=”fontspace-210350″ border_width=”2″ display=”inline” link=”|||” icon=”fa fa-volume-control-phone”]Call us now for more +30 211 8000 330[/vc_button][vc_single_image media=”101812″ media_width_percent=”100″ alignment=”center”][/vc_column][/vc_row]
We created our blog series Tech Tips to familiarize all interested parties, customers, and partners with product features and user scenarios related to MailStore Server. The accompanying video format provides step-by-step instructions. In this Tech Tips Mini-Series, we would like to give you useful tips on how to archive your emails from Microsoft 3651 as a new MailStore Server customer.
Why You Should Use MailStore Server With Microsoft 365
Even though emails can be archived natively in Microsoft 365, there are many reasons to use an external email archiving solution such as MailStore Server in combination with Microsoft 365. The reasons for this have been summarized for you in a free white paper from market research institute Osterman Research. Many companies believe, for example, that it is no longer necessary to protect and preserve their own business critical data after migrating to the (public) cloud because they assume that the cloud provider is responsible for backing up their data. However, this belief is completely misguided.
Microsoft 365 customers are responsible for the protection and storage of their data, which includes archiving and regularly backing up business data. As a public cloud service provider, Microsoft is merely responsible for the availability of their service and protecting it from outages. That is why companies that use such a public cloud service should take measures to protect themselves from the risk of data loss. MailStore Server not only provides protection and makes your emails in Microsoft 365 centrally and independently available, but also, among other things, provides a fast self-service that allows end users to search for and restore emails and file attachments using the email archive. You can find even more reasons for using MailStore Server in combination with Microsoft 365 on our blog.
Modern Authentication as a Standard at MailStore
More and more companies are switching to Microsoft 365. This trend is picking up faster with support for Microsoft Windows SBS 2011 having ended and with Microsoft Exchange Server 2010 soon to follow suit. Since Microsoft has announced the end of basic authentication, modern authentication based on OAuth2 will become a must for many companies soon.
MailStore Server supports modern authentication and with that, provides not only an optimal integration into the cloud environment of Microsoft 365, but also the necessary security. For example, as a Microsoft 365 user, you simply use your usual log-in procedure for your Microsoft 365 tenant in order to log in to MailStore Server, which includes, for example, multi-factor authentication.
In this Tech Tip, we would like to explain how to archive your emails from Microsoft 365 as a new MailStore Server customer, thus providing you with long-term protection against data loss, and making the data available and retrievable at all times. Here are two videos that show you how to connect MailStore Server with your Microsoft 365 tenant using modern authentication, synchronize users (part 1), and customizing archiving profiles (part 2).
Part 1: Preparation of Your Microsoft 365 Tenant and User Synchronization
In this video, we describe the initial configuration and connection of MailStore Server to Microsoft 365. At the same time, we show you how to connect MailStore Server to your Microsoft 365 tenant, in order to synchronize user information from Microsoft 365. We address, among other things, how to register MailStore Server as an app in Azure AD and assign the necessary permissions. Finally, we show you how to perform the user synchronization.
You can find all the detailed steps in our MailStore Server Help and step-by-step instructions in our Tech Tip video:
Part 2: Customizing the Archiving Profile in MailStore Server
In the second video, we would like to show you how to completely archive your Microsoft 365 mailboxes. Please make sure that you have already carried out all the steps from the previous Tech Tip video (part 1). Then you can proceed with selecting the archiving profile. We explain how to archive existing as well as future emails with MailStore Server via “journal archiving” (also known as journaling). We recommend our free MailStore Gateway add-on program as an external journal mailbox. We also explain how to define deletion rules, for example.
You can find all the detailed steps in our MailStore Server Help. In the following video, you will receive practical step-by-step instructions on customizing archiving profiles:
Are You Already Using MailStore Server?
If you are already using MailStore Server with an on-premises Exchange Server, you can very easily transfer your existing archive when switching to Microsoft 365. With MailStore Server, your emails continue to be archived just as before – helping you to meet a growing number of compliance requirements. Our Tech Tip Migrating Existing MailStore Server Customers from Microsoft Exchange Server to Microsoft 365 provides you with practical step-by-step instructions. You can also find the step-by-step guide on how you can switch your archiving from Microsoft Exchange Server to Microsoft 365 in our MailStore Server Help.
Source: MailStore
In a world in which the data threat landscape is becoming bigger, stronger, and more malicious, protecting your organization’s sensitive information from a breach is becoming all the more critical every day. Taking the proper steps to ensure that your data security strategy fits your industry and specific organizational needs is of the utmost importance to find solutions that will keep you the most secure with the least amount of headache.
Why is Finding the “Right” Solutions Important?
When it comes to protecting your organization’s sensitive data, there is never a one-size-fits-all solution. Your cybersecurity strategy could look vastly different from your competitor’s when considering the size of your organization, your industry, customers, the types of data you create and share, and much more. Finding the solutions that are tailored to the needs of your organization will ensure that your organization, its employees, and its customers all remain safe from cybercrime.
With that in mind, though, finding the best data security solutions for your organization in and of itself can be quite the undertaking. If your company has existing cybersecurity infrastructure in place, finding another vendor with separate, yet still compatible solutions can be a challenge. Furthermore, finding a new vendor and replacing your current infrastructure entirely can be even more of a hassle.
Unfortunately, this does not take away the fact that having cybersecurity measures in place is steadily becoming more and more necessary. Cybersecurity Ventures’ latest prediction is that ransomware damages alone will have cost $20 billion in 2021. Meanwhile, phishing attacks have been on a steep incline as a direct result of the COVID-19 pandemic, and they do not appear to be stopping any time soon. By 2025, global cybercrime damages are expected to top $10.5 trillion annually.
What this likely means for you is finding a vendor that can provide you with data security solutions right away and grow with you for the foreseeable future is of critical importance. HelpSystems’ ever-growing, modular suite of data security solutions can be tailored to provide you with the necessary protections you need for your sensitive information now and adapt as your organization changes and grows. But where do you start?
5 Questions to Help You Choose the Right Solutions
HelpSystems has a large and still-growing suite of data security solutions that seamlessly integrate with one another and provide the world-class protection that your organization needs. That being said, even for IT and cybersecurity professionals, knowing how to choose the right solutions, let alone clearly defining your organization’s data security challenges, can be quite convoluted. We recommend asking yourself the following five questions to help make that process easier.
1. Are there any known weak points in your data’s life cycle?
If you are already aware of the most vulnerable points in your data’s life cycle, then you’re already a step ahead. Knowing if your data is most at-risk for compromise at the moment it’s created, when it’s in transit, or when it’s resting at its final destination is critical when choosing the most relevant solutions for your organization.
2. What security measures and solutions does your organization already have in place?
Ultimately, HelpSystems wants your data security solutions to be seamless and compatible with one another rather than cause friction. If you already have existing cybersecurity infrastructure in place, we’ll work to find the solutions that will complement those existing measures. If you’re shopping for several solutions at once, you can rest easy knowing that our data security solutions integrate flawlessly and are meant to work with each other now and in the future. If you find yourself needing more solutions later on, we can always discuss your future requirements and work with you to evaluate potential solutions to add on.
3. What sensitive data could cause your organization harm if compromised?
Once again, when it comes to protecting data, there is never a one-size-fits-all solution. Not all data security solutions will support all file types, and sometimes a solution will be better suited for data at rest rather than data in motion (and vice versa). Knowing what types of data your organization frequently uses is key in knowing what solutions will make the most sense for you.
Similarly, understanding which of those files and data are most sensitive is just as important. What data could cause the most damage to your organization if it were to be shared with the wrong people or be exposed to attackers? Will the loss of that sensitive data lose your organization’s competitive advantage, harm your employees and/or customers, or lead to financial damages?
4. Are you confident that your organization’s sensitive data is being handled properly?
Looking internally, are you confident that your organization’s employees are following the proper procedures with your sensitive data? Employee negligence is considered one of the biggest cybersecurity risks to U.S. businesses, and Shred-it found in their most recent Data Protection Report (DPR) that as much as 22% of data breaches are caused by employee error, and another 40% come from “trusted” insiders or external business partners. Understanding how much visibility you have over your employees and their actions is fundamental in deciding which data security solutions you may need.
5. Is your organization subject to regulatory compliance?
Last, but not least, is knowing whether or not your organization is subject to compliance regulations. Regardless of whether you need to comply with PCI DSS, GDPR, CUI, or other requirements, you must find a data security vendor whose solutions address the requirements of those regulations, and if need be, help you to navigate the complexities of those regulations as well.
Source: HelpSystems

























