News
[vc_row][vc_column][vc_column_text]
Whether you’ve been naughty or nice, someone will try and stuff a scam down your chimney either way. The FBI is warning of several likely ways to be parted from your funds or logins, and we’re going to give some additional context along with tips to avoid these digital lumps of coal.
Social media shopping scams
The FBI says:
Consumers should beware of posts on social media sites that appear to offer vouchers or gift cards. Some may appear as holiday promotions or contests. Others may appear to be from known friends who have shared the link. Often, these scams lead consumers to participate in an online survey that is designed to steal personal information.
We say:
Social media scams largely lean into cryptocurrency giveaways and other similar get rich quick schemes. You may see the occasional gift card thrown into the mix, but these tend to be related to survey scams. Having said that, we covered 3 popular forms of gift card scam in the run up to Black Friday:
-
Fake gift cards for sale at a discount. If it’s too good to be true, it probably is. Search out the official card distributor and check if they actually do have a sale on, and then purchase directly.
-
Gift card generators. Tools which claim to create genuine codes have been around for years, and they’re all fake. At best you’ll see one of the previously mentioned surveys. At worst, you could run into malware.
-
Services you encounter online which claim to perform a task in return for gift cards should be avoided. You’ll send them a code, and never hear from them again.
Work from home scams
The FBI says:
Consumers should beware of sites and posts offering work they can do from home. These opportunities rely on convenience as a selling point but may have fraudulent intentions. Consumers should carefully research the job posting and individuals or company offering employment
We say:
Work from home scams are big business over the holiday season, especially with people potentially looking for a little extra cash in the run up to the new year. These scams became incredibly popular with the advent of the COVID-19 pandemic, often tying into cryptocurrency.
Other scams of this nature will make use of cryptocurrency ATMs and QR codes. They’ll set up fake job hunt websites for you to upload your resume to, or post bogus ads on real sites. If you take part in an interview via WhatsApp or Telegram, that may be a red flag. If they send you money to buy work equipment, and then ask you to send the rest of the money to another bank account, that’s a whole box of red flags. You may well be walking into a short lived career as a money mule. It’s simply not with the risk.
Charity scams
The FBI says:
Fraudulent charity scams, in which perpetrators set up false charities and profit from individuals who believe they are making donations to legitimate charitable organizations. Charity fraud rises during the holiday season, when individuals seek to make end-of-year tax deductible gifts or are reminded of those less fortunate and wish to contribute to a good cause. Seasonal charity scams can pose greater difficulties in monitoring because of their widespread reach, limited duration and, when done over the Internet, minimal oversight.
We say:
One of the biggest drivers of fake charity sites is still the invasion of Ukraine. Fake donation sites are easy to set up, and copying genuine content from the real thing is also straightforward.
These sites will often tug at the heart strings, claiming to help children stranded in Ukraine with (what else?) cryptocurrency. Occasionally these scams lurk in the replies of Twitter threads, often imitating the person who originally posted.
In the UK you can search the charity register. I’m not aware of a similar service in the US, but you’re likely going to find a link to the charity you’re looking for on the Forbes top 100 list.
Smartphone app scams
The FBI says:
Some mobile apps, often disguised as games and offered for free, are designed to steal personal information. Before downloading an app from an unknown source, consumers should research the company selling it or giving it away and look online for third-party reviews of the product.
We say:
Bogus apps are something you can expect to run into all year round, but this is still good advice for the most part. I say “most part”, because the above suggests that only apps from an unknown source could be an issue. Whether you’re using an official app store or downloading apps from third party sources, there could be something lurking in that app. Dubious apps can work their way onto your device via a low tally of installation permission requests and then set about getting up to mischief, and that’s from an official store.
Even if the app you installed is legitimate it can be abandoned by the developers and cause problems of its own, potentially leaving you open to exploits. What you need to do:
-
Stick to official stores. Yes, they do also fall victim to malware apps posing as the real thing. You’re still better off doing this than allowing unknown installs to your device and grabbing files from who knows where.
-
Check the number of installs, how long the file has been available, developer information, and the reviews. Use information from outside the official store to see if anyone is complaining about it in security circles. Check if the app is still supported. If the app is brand new, you may wish to wait a while before installing.
-
When your Android phone begins to show signs of infection, it’s time to follow our list of security tips and run a scan.
Don’t let the scammers spoil your fun
We hope a combination of the FBI’s warnings and our additional hints and tips will keep you safe over the coming weeks. Unfortunately scammers don’t tend to take time off over Christmas, so it’s essential to keep your guard up. As for that lump of coal: return to sender.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.
Source: Malwarebytes
[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_separator sep_color=”color-150912″][vc_custom_heading text_font=”font-762333″ text_weight=”200″ text_color=”color-210407″ subheading=”Fill in your details or call 211 8000 330″]Get maximum security now!
[/vc_custom_heading][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][contact-form-7 id=”101883″][/vc_column][/vc_row]
This quarter too, we’re happy to present a new version of our email archiving software: Version 22.4 of MailStore Server, the MailStore Service Provider Edition (SPE), and MailStore Home is available right now.
The new version of our MailStore Service Provider Edition supports multi-factor authentication. We’ve also improved how the software in all three products manages the available resources. It goes without saying that Version 22.4 of MailStore Server and the MailStore Service Provider Edition will also be GDPR-certified.
New Features for the MailStore SPE, MailStore Server and MailStore Home
Find out more about the improvements you can expect in Version 22.4 of the MailStore Service Provider Edition, MailStore Server and MailStore Home.
Support of Multi-Factor Authentication for the MailStore Service Provider Edition
Once again, we’ve enhanced the security of our MailStore Service Provider Edition. Access to the management console by administrators can now be secured via multi-factor authentication. After entering a username and password, administrators are now prompted to input an access code from an authenticator app of their choice in order to be able to access the management console.
If the administrator then wishes to use the management API, a separate API password must be generated. The API password is generated in the management console and is required by every system administrator for whom multi-factor authentication has been activated. This allows the API to be used without the need to enter a second factor, e.g. for automation purposes.
Improved Resource Management for the MailStore SPE, MailStore Server, and MailStore Home
Once again, we’ve improved resource management in all three software solutions. Specifically, this means that we’ve optimized how the available memory is used when running our software.
Updated Certification: Meeting Data Privacy Requirements
As usual, the latest version of our software, Version 22.4 of MailStore Server and the MailStore SPE, has been certified by an independent data privacy expert.
The certification takes into account all relevant aspects of the European General Data Protection Regulation (GDPR) and affirms that, when used appropriately, both MailStore Server and the MailStore SPE meet all the requirements governing the processing of personal data set out in the GDPR.
You can request a copy of the official GDPR audit certificate from sales@mailstore.com.
Registered MailStore partners can download the certificates from our Partner Portal or request it by email from partners@mailstore.com.
Availability
You can download the new version of MailStore Server and the MailStore Service Provider Edition free of charge from our website.
If your MailStore Server Update & Support Service has expired, please contact us to purchase an upgrade that will allow you to use the latest version of MailStore Server. Read here to find out about other good reasons for having an active Update & Support Service agreement in place.
Interested companies can also download MailStore Server Version 22.4 as part of a free, 30-day trial. If you are an MSP and are interested in offering email archiving as a service based on the MailStore SPE, please contact our sales team at partners@mailstore.com. Alternatively, you can sign up as an authorized MailStore Partner with us right now for free.
Source: MailStore
[vc_row][vc_column width=”1/1″][vc_single_image media=”103531″ media_width_percent=”100″ css_animation=”zoom-out” animation_speed=”1000″ animation_delay=”400″][vc_empty_space empty_h=”2″][vc_button button_color=”color-150912″ size=”btn-xl” border_animation=”btn-ripple-out” custom_typo=”yes” font_family=”font-762333″ font_weight=”900″ letter_spacing=”fontspace-210350″ border_width=”2″ display=”inline” link=”url:mailto%3Asales%40nss.gr%3Fsubject%3DBOOKmySEAT%3A%20Sophos%20Firewall%20Administration%20for%20End-users%20Training%26body%3DI%20would%20like%20to%20participate%20in%20the%20Sophos%20Firewall%20Administration%20for%20End-users%20Training%20on%20the%209th%20%26%2010th%20of%20January%202023||target:%20_blank|” icon=”fa fa-hand-o-right”]Book Your Training Today![/vc_button][vc_button button_color=”color-283957″ size=”btn-xl” border_animation=”btn-ripple-out” custom_typo=”yes” font_family=”font-377884″ font_weight=”900″ letter_spacing=”fontspace-210350″ border_width=”2″ display=”inline” link=”|||” icon=”fa fa-volume-control-phone”]Call us now for more +30 211 8000 330[/vc_button][vc_separator sep_color=”color-210407″][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_custom_heading heading_semantic=”h1″ text_font=”font-762333″ text_size=”h1″ text_weight=”200″ text_color=”color-xsdn”]Sophos Firewall Administration for End-users Training
[/vc_custom_heading][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_column_text]
In January 2023: Monday 9 & Tuesday 10
(2 days crash Training / NSS Training Center – remote / on premises)
A two-days crash training program which is designed for technical professionals who will be administering Sophos Firewall and provides the skills necessary to manage common day-to- day tasks.
Trainer: Micheal Eleftheroglou
Training room: NSS ATC training room 3rd floor
Objectives
On completion of this course, trainees will be able to:
- Explain how Sophos Firewall help to protect against security threats
- Configure firewall rules, policies, and user authentication
- Demonstrate threat protection and commonly used features
- Perform the initial setup of an Sophos Firewall and configure the required network settings
- Identify and use troubleshooting tools, reporting and management tasks
Prerequisites
There are no prerequisites for this course; however, it is recommended you should:
- Be knowledge of networking
- Be familiar with security best practices
- Experience configuring network security devices
Certification
To become a Sophos Certified Administrator, trainees must take and pass an online assessment.
The assessment tests the knowledge of both the presented and practical content.
The pass mark for the assessment is 80% and is limited to 4 attempts.
Content
-
-
- Module 1: Firewall Overview
- Module 2: Getting started with Firewall
- Module 3: Network Protection
- Module 4: Webserver Protection
- Module 5: Site-to-site Connections
- Module 6: Authentications
- Module 7: Web Protection and Application control
- Module 8: Application Control
- Module 9: Email Protection
- Module 10: Wireless Protection
- Module 11: Remote Access
- Module 12: Logging, Reporting and Central Management
-
Certification + Exam:
SOPHOS FIREWALL ADMINISTRATOR
Duration 2 Days Remote + Labs
Athens Cyberpark training room 3rd floor (Aggistis 1 & Paggaiou)
Language: Greek & English[/vc_column_text][/vc_column][/vc_row][vc_row row_height_percent=”0″ back_color=”color-210407″ overlay_alpha=”50″ gutter_size=”3″ column_width_percent=”100″ shift_y=”0″ z_index=”0″][vc_column width=”1/1″][vc_custom_heading text_font=”font-762333″ text_weight=”200″ text_color=”color-xsdn”]Agenda[/vc_custom_heading][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_column_text]DAY 1
09:30 – 10:30 Module 1: Firewall Overview
10:30 – 10:45 Break
10:45 – 12:30 Module 2: Getting started with Firewall
12:30 – 13:00 Labs (getting familiar)
13:00 – 13:30 Lunch
13:30 – 14:30 Module 3: Network Protection
14:30 – 15:30 Module 4: Webserver Protection
15:30 – 15:45 Break
15:45 – 17:05 Module 5: Site to Site Connection
DAY 2
09:00 – 10:20 Module 6: Authentications
10:20 – 11:20 Module 7: Web Protection and Application Control
11:20 – 11:30 Break
11:30 – 12:00 Module 8: Application Control
12:00 – 12:50 Module 9: Email Protection
12:50 – 13:30 Lunch
13:30 – 14:15 Module 10: Wireless Protection
14:15 – 15:05 Module 11: Remote Access
15:05 – 15:20 Break
15:20 – 16:20 Module 12: Logging, Reporting and Central Management
16:20 Labs discussion[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_separator sep_color=”color-210407″][vc_empty_space empty_h=”2″][vc_button button_color=”color-150912″ size=”btn-xl” border_animation=”btn-ripple-out” custom_typo=”yes” font_family=”font-762333″ font_weight=”900″ letter_spacing=”fontspace-210350″ border_width=”2″ display=”inline” link=”url:mailto%3Asales%40nss.gr%3Fsubject%3DBOOKmySEAT%3A%20Sophos%20Firewall%20Administration%20for%20End-users%20Training%26body%3DI%20would%20like%20to%20participate%20in%20the%20Sophos%20Firewall%20Administration%20for%20End-users%20Training%20on%20the%209th%20%26%2010th%20of%20January%202023||target:%20_blank|” icon=”fa fa-hand-o-right”]Book Your Training Today![/vc_button][vc_button button_color=”color-283957″ size=”btn-xl” border_animation=”btn-ripple-out” custom_typo=”yes” font_family=”font-377884″ font_weight=”900″ letter_spacing=”fontspace-210350″ border_width=”2″ display=”inline” link=”|||” icon=”fa fa-volume-control-phone”]Call us now for more +30 211 8000 330[/vc_button][vc_single_image media=”103531″ media_width_percent=”100″ alignment=”center” css_animation=”zoom-out” animation_speed=”1000″ animation_delay=”400″][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][/vc_column][/vc_row]
Datto, the leading global provider of security and cloud-based software solutions purpose-built for managed service providers (MSPs), has just introduced Datto EDR. Developed to provide highly effective endpoint detection and response capabilities, Datto EDR is tailored for today’s MSPs and small to midsize businesses (SMBs) in an affordable, easy to use, manage and deploy package.
Having the right cybersecurity tools in place is more important than ever. Year-over-year ransomware attacks increased by 92.7% and the average cost of an attack on a small business was $8,000 per hour from the time of attack to the time of remediation. Most endpoint detection and response tools require skilled and trained security analysts, who are in high demand and short supply, but Datto EDR uses MITRE ATT&CK framework to provide helpful clarity to teams, reducing the security expertise needed to effectively respond.
“Standard security tools aren’t enough anymore,” said Chris McKie, VP of Product Marketing for Security and Networking Solutions. “Threat actors have found ways to circumvent traditional security measures, making EDR tools more important than ever for catching suspicious activity and keeping businesses safe from increasingly sophisticated cyberattacks.”
Nearly all EDR products are designed and built for enterprise, which means they’re often costly and highly complex, requiring a team of highly trained security experts to effectively manage it. Without this trained staff, many organizations have been left without effective EDR tools.
Datto EDR has been specially built to help MSPs who want to improve their security posture and expand their security offerings to their SMB customers. This highly effective tool provides additional layers of endpoint security by detecting suspicious behaviors that sophisticated threat actors leverage to bypass when using traditional antivirus. Each alert in the dashboard comes with a response function, which will help teams through the remediation process with detailed mitigation recommendations for the most common threats, allowing MSPs to become more self-sufficient.
Datto EDR is an effective threat detection solution with readily available and knowledgeable technical support. Its efficient and actionable alerts can be quickly interpreted to decide on the appropriate next steps with quick deployment options that don’t interfere with day-to-day business operations. Further, continuous monitoring of process, memory, and behavior across all endpoints limits the time it takes to detect intrusions.
Part of Kaseya’s IT Complete Platform, Datto EDR expands the security suite to provide the maximum coverage across multiple vectors. Datto EDR is integrated with Datto RMM and Kaseya One to address the challenges of do-it-all, multifunctional IT professionals. It offers one vendor with everything you need, woven together to save you time, smart enough to help you get more done, and at an affordable price point.
For more information or to request a demo of Datto EDR, visit https://www.datto.com/request/datto-edr/.
Source: Datto
User Account Control (UAC) is a security feature in the Windows Operating System designed to mitigate the impact of malware. All users have triggered a UAC prompt at some point. Tasks that may trigger a UAC prompt include trying to install an application or change a setting that requires administrator privileges. A UAC prompt is the pop up that appears and requests the user to confirm they indeed want the install or other change to happen.
Windows Vista introduced the UAC prompt to improve on the security challenges experienced in Windows XP. The UAC prompt has not significantly changed since then, except for some visual improvements in Windows 10.
Why the Need for UAC?
When an application launches in Windows, it is assigned an access token. This token defines the privileges and access for the application. The principle behind Windows UAC is to give local administrators two tokens, one standard token and one admin token.
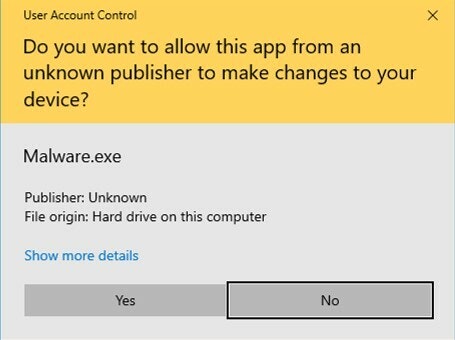 Initially, only a standard token is issued. However, when an application specifically requests an admin token, by default, it triggers a UAC prompt message to appear. If the user clicks “yes” on the UAC prompt to proceed with execution of their request, then an admin token is issued. The admin token then enables the application to run with a high level of privilege.
Initially, only a standard token is issued. However, when an application specifically requests an admin token, by default, it triggers a UAC prompt message to appear. If the user clicks “yes” on the UAC prompt to proceed with execution of their request, then an admin token is issued. The admin token then enables the application to run with a high level of privilege.
An admin token is like an ‘access all areas’ pass that allows the application to do almost anything on the system. So, when an application with an admin token is compromised, an attacker can inflict considerable damage.
Insertion of the UAC step helps minimize the number of applications running with admin tokens that an attacker can exploit. In addition, user account control reduces the risk of an attacker acquiring an admin token without triggering a message to the user for approval.
Since the majority of applications don’t need an admin token to function, users aren’t bombarded with pop ups. Thus, we seem to have an effective security feature in place. But wait, this isn’t the end of the story.
Before you scroll to the top of the article to check if I am contradicting myself, I said earlier that Windows User Account Control is a security feature not a boundary. In fact, Microsoft describes UAC as “a fundamental component of Microsoft’s overall security vision”. While many folks continue to portray UAC as a security boundary, technically, it isn’t.
Over the years, numerous security researchers and threat actors have successfully explored ways to run their tools without triggering UAC. When these tactics have been reported to Microsoft’s bug bounty program, the Microsoft response has been “UAC is not a security boundary”.
Microsoft doesn’t want their own applications triggering lots of pop-up UAC prompts. Thus, Microsoft created a mechanism so that applications they trust will avoid triggering the UAC prompt. The security downside to this is that trusted applications can then be exploited, or piggy-backed off, to bypass UAC.
Because UAC isn’t considered a security boundary, these bypasses are not viewed as bugs and are not patched. At the time of writing this blog, the UACME project (https://github.com/hfiref0x/UACME – note, some network filters will block this page) lists 76 different UAC bypass techniques. Many of these bypass techniques are actively used in malware to silently elevate privilege on a Windows endpoint. Far more bypasses exist in the wild—those 76 just represent the most popular ones.
Solving UAC challenges with Endpoint Privilege Management
UAC problems like the above seem to create a terrible situation, as end users need admin tokens to perform common activities, like install software, install printers, and change settings. If you remove local admin privileges, the end users are secure, albeit less productive. Moreover, users might spend all day raising help desk tickets. Alternatively, if you provision local admin privileges to them, then a threat actor may bypass the operating system’s UAC security mechanism and wield the admin privileges against you.
Fortunately, modern Endpoint Privilege Management tools like BeyondTrust’s Privilege Management for Windows effectively address this challenge, and more. The BeyondTrust solution allows you to immediately remove local admin privileges from all users, which substantially reduces your attack surface. Privilege Management for Windows intercepts UAC and elevation requests and seamlessly elevates just the applications your users need for their role, based on policy.
For known and trusted applications, you can use simple policy rules or out-of-the-box policy templates to seamlessly launch these applications without having to prompt the user. Then, for unknown applications or tasks, you can ask the user to justify why they need a specific application, perform reputational checks, verify the application publisher, or trigger step-up authentication via MFA to ensure both the application and user are who they say they are.
Privilege Management for Windows provides Quick Start templates that make it practical for organizations to tackle common least privilege policy use cases from Day 1, enabling rapid leaps in risk reduction. In addition, custom access tokens allow you to assign privileges at a granular level to ensure no user or application is over-privileged
Don’t fall into the pitfalls of either exposing your organization to the risk of over-privileged local admin users or hampering productivity by under-privileging users. Find the balance between security and productivity, follow security best practices, and, most importantly, build a secure foundation that prevents attackers from gaining privileged access to systems.
 Endpoint Privilege Management | BeyondTrust
Endpoint Privilege Management | BeyondTrust
Learn more about BeyondTrust Endpoint Privilege Management.
Source: BeyondTrust
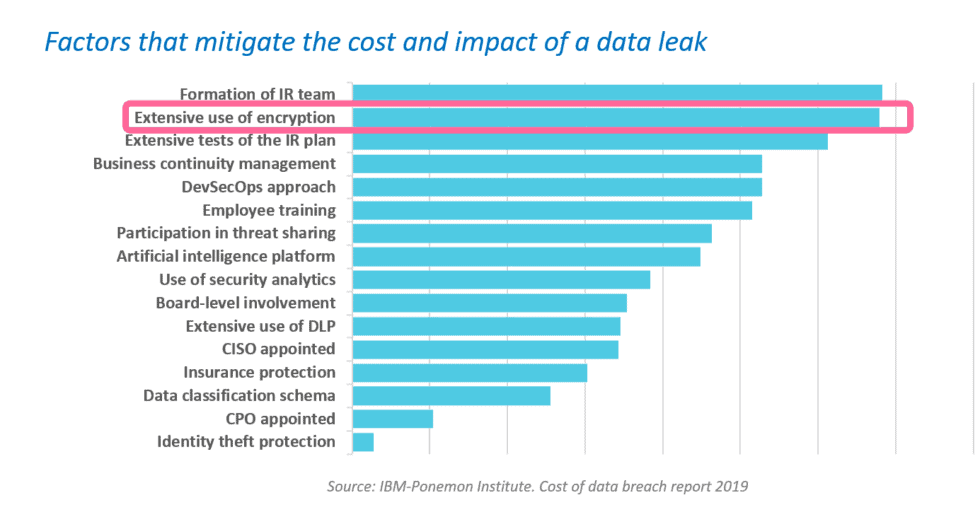
Discover the seven network security measures that can help mitigate the risk of a ransomware attack.
66% of organizations were hit by ransomware last year* demonstrating that adversaries have become considerably more capable at executing attacks at scale than ever before.
Modern attacks leverage legitimate IT tools such as Remote Desktop Protocol (RDP) to gain access to networks, making initial detection notoriously difficult. The root of the problem is that there’s too much implicit trust in the use of these tools which has repeatedly proven unwise.
Implementing robust network security measures is a sure-fire way to mitigate this risk. In our new whitepaper, Best Practices for Securing Your Network from Ransomware, and in this article, we share practical network security tips to help elevate your ransomware protection.
1. Micro-segment your network
Micro-segmenting allows you to limit the lateral movement of threats. One way to achieve this is to create small zones or VLANs and connect them via managed switches and a firewall to apply anti-malware and IPS protection between segments. This lets you identify and block threats attempting to move laterally across your network.
2. Replace remote-access VPN with a Zero Trust Network Access solution (ZTNA)
ZTNA is the modern replacement for remote-access VPN. It eliminates the inherent trust and broad access that VPN provides, instead using the principles of Zero Trust: trust nothing, verify everything. To learn more about the benefits of ZTNA over VPN, read our article here.
3. Implement the strongest possible protection
Always deploy the highest level of protection on your firewall, endpoints, servers, mobile devices, and remote access tools. In particular:
- Ensure your firewall has TLS 1.3 inspection, next-gen IPS, and streaming DPI with machine learning and sandboxing for protection from the latest zero-day threats
- Ensure your endpoints have modern next-gen protection capabilities to guard against credential theft, exploits, and ransomware
4. Reduce the surface area of cyberattacks
We recommend that you review your firewall rules and eliminate any remote access or RDP system access through VPN, NAT, or port-forwarding, and ensure that any traffic flows are properly protected. Eliminating exposure from remote access goes a long way in reducing the number of in-roads for attackers to launch ransomware attacks.
5. Keep your firmware and software patched and up-to-date
This is important for both your network infrastructure (such as your firewall or remote-access software or clients) and your systems given that every update includes important security patches for previously discovered vulnerabilities.
6. Use multi-factor authentication (MFA)
Ensure your network operates on a zero-trust model where every user and device has to continually earn trust by verifying their identity. Also, enforce a strong password policy and consider adopting authentication solutions like Windows Hello for Business.
7. Instantly respond to cyberattacks
Use automation technologies and human expertise to accelerate cyber incident response and remediation. Ensure your network security infrastructure helps you automatically respond to active attacks so you can isolate a compromised host before it can cause serious damage.
An increasingly popular way to achieve this is via a managed detection and response (MDR) service. MDR is a fully managed, 24/7 service delivered by experts who specialize in detecting and responding to cyberattacks that technology solutions alone cannot prevent. To learn more on the benefits of MDR, read our article here.
Learn more
To explore these best practices in greater detail and to learn how Sophos network security solutions elevate your ransomware protection, download our whitepaper here.
Sophos provides everything you need to fully secure your network from attacks, including firewalls, ZTNA, switches, wireless, remote-edge devices, messaging protection, MDR, next-gen endpoint protection, EDR and XDR. Plus, everything’s managed via a single cloud management console — Sophos Central — and works together to deliver Synchronized Security and cross-product threat detection and response.
For more information and to discuss how Sophos can help you, speak with one of our advisors or visit www.sophos.com today.
Πηγή: Sophos
We’re thrilled to announce that Sophos Firewall has been named the best network security solution for small and medium-sized businesses by CRN®, a brand of The Channel Company. The recognition marks Sophos’ seventh consecutive year as a winner in the CRN Tech Innovator awards, which honor the channel’s most innovative technologies.
“Sophos Firewall is an essential layer of protection against malicious traffic and threat actors targeting corporate and remote users who are traversing today’s hybrid business environment,” said Raja Patel, senior vice president of products at Sophos. “Sophos Firewall’s programable Xstream Flow Processors enable us to innovate and add new features and capabilities over time, without forcing a hardware upgrade. This provides our channel and customers with a future-proof scalable platform with tremendous value that continues to grow with every release.”
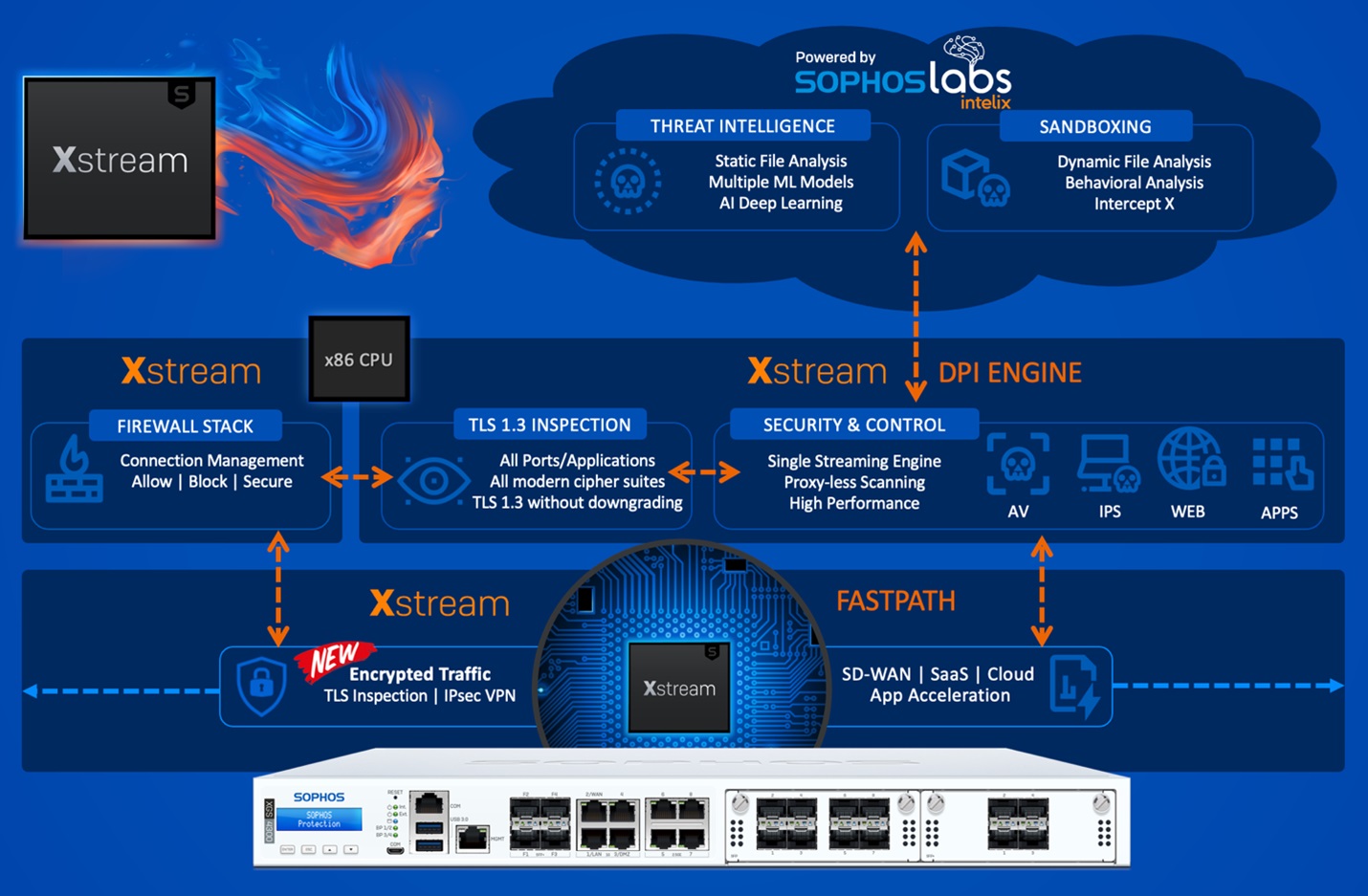
Sophos Firewall delivers unrivaled network visibility, protection and response for organizations of all sizes and across all sectors. It delivers the industry’s best zero-day threat protection, identifying and stopping advanced cyberthreats, and its innovative and unique Xstream architecture is engineered to deliver extreme levels of performance in accelerating important software-as-a-service (SaaS), software-defined wide area network (SD-WAN) and cloud application traffic.
As part of the Sophos Adaptive Cybersecurity Ecosystem, Sophos Firewall shares real-time threat intelligence with Sophos’ broad portfolio of solutions and services for faster and more contextual and synchronized protection, detection and response. It’s further powered by predictive, real-time and deeply researched threat intelligence from Sophos X-Ops, a cross-operational task force linking SophosLabs, Sophos SecOps and SophosAI, and is easily managed in the cloud-native Sophos Central platform or by Sophos Managed Detection and Response (MDR).
Don’t forget that the new Sophos Firewall v19.5 is in early access right now and will become generally available this month. This blog series covers all the new features.
“Our CRN Tech Innovator Awards recognize those technology vendors that are making the biggest impacts in digital transformation for solutions providers with unique, cutting-edge products and services,” said Blaine Raddon, CEO of The Channel Company. “It is my pleasure to congratulate each and every one of our 2022 CRN Tech Innovator Award winners. We’re delighted to recognize these best-in-class vendors that are driving transformation and innovation in the IT space.”
A complete list of winners will be featured in the December issue of CRN and can be viewed online at crn.com/techinnovators.
Source: Sophos
We’re delighted to share that Sophos endpoint security products ranked as industry best in SE Labs’ protection tests in the third quarter of 2022, achieving AAA ratings across the board.
Sophos earned a 100% rating for Protection Accuracy, Legitimate Accuracy, and Total Accuracy in the Enterprise and SMB categories in this latest round of testing.
Commenting on the results, Simon Edwards, CEO of SE Labs, said:
“Sophos Intercept X stopped all threats and allowed all legitimate applications. The AAA award is well deserved and shows that Sophos goes well beyond basic functionality. The solution can handle both common and customized threats, without blocking the software you need to run on your computer.”
Protection powered by world-leading threat intelligence
Our endpoint solutions include Sophos Intercept X and Sophos XDR (extended detection and response), which combine anti-ransomware technology, deep learning artificial intelligence, exploit prevention, and active adversary mitigations to stop attacks.
All our solutions are powered by threat intelligence from Sophos X-Ops, a cross-operational task force linking SophosLabs, Sophos SecOps, and SophosAI, bringing together deep expertise across the attack environment. Armed with this understanding, we can build powerful, effective defenses against even the most advanced threats.
Sophos endpoint solutions are easily managed in the cloud-native Sophos Central platform or by Sophos Managed Detection and Response, a 24/7 managed detection and response (MDR) service used by more than 12,600 organizations worldwide.
The importance of high-quality third-party testing
At Sophos, we place great value on high-quality, independent testing and participate in numerous tests throughout the year.
As Simon Reed, Senior Vice President of SophosLabs says, “Sophos believes in the informational and transparency value of regular participation in third-party testing.”
Of course, tests are most valuable when they challenge solutions in real-world scenarios. As Simon Edwards of SE Labs explains:
“How hard do you want your security testing to be? We could take a product, scan a real virus and record that it detected a threat. Great, but what does that tell us? It’s a very basic test that only verifies that the software actually is an anti-malware product. You can’t tell if it’s better than other anti-malware products, because it’s just one file being scanned and detected. You don’t even know if the product could protect against the threat, just that it detected it. So, we turned up the dial and threw a wider range of attacks at the products. Each solution was exposed to the same threats, which were a mixture of targeted attacks using well-established techniques and public email and web-based threats that were found to be live on the internet at the time of the test.”
At Sophos, we’re delighted with our exceptional performance in the latest SE Labs tests and – most importantly – that we provide our customers with world-leading endpoint protection that defends against even the most advanced adversaries.
Test drive Sophos for yourself
Sophos defends more than 500,000 organizations from active adversaries, ransomware, phishing, malware, and more. Speak to our security advisers to discuss how we can help you, and take a test drive of our solutions today.
Source: Sophos
Today, we are releasing the 2023 edition of Sophos’ annual threat report. Based on a combination of telemetry, incident response data, and other threat intelligence gathering, the report presents a snapshot of the threat landscape today and examines the trends we’ve seen emerging in malicious activity. And one of the clearest trends is the continued evolution of a mature cybercrime industry that mirrors in many respects the trends in legitimate software and digital services.
Ransomware operators were a leading adopter of the “as-a-service” model for cybercrime. In 2022, we saw the model adopted more widely across the cybercrime space, with underground digital marketplaces now offering virtually all of the components of the cybercrime toolkit to those willing to pay for them—targeting and initial compromise of victims, evasion and operational security, and malware delivery, among others.
Also widely available are professional attack tools—complete with “cracked” or bypassed licensing. Cobalt Strike, intended to be used by security professionals to emulate advanced attackers, is now seen in a majority of ransomware incidents. Brute Ratel, another advanced exploitation tool advertised as a Cobalt Strike replacement, is also now widely available and has been seen in a handful of ransomware incidents thus far.
The operations of ransomware operators themselves continue to mature. LockBit 3.0, for example, now offers a bug bounty program to crowd-source testing of its malware and performs market research in the criminal community to improve the group’s operations. Other groups have offered “subscription” programs for their leak data.
All of this has happened against the backdrop of the continued war in Ukraine, which led to divisions and break-ups in Russian-language cybercrime groups, with resulting doxing and data breaches from Conti and other ransomware groups. It also led to a rash of new fraud, using the government of Ukraine’s appeal for funds as the lure for a wave of cryptocurrency scams and other financial fakery.
Abuse of other legitimate software, as well as components of the Windows operating system itself, continue to challenge defenders. Criminal actors continued to expand use of legitimate executables (such as “trial” versions of commercial software products, including remote access tools), and of “living off the land binaries” (LOLBins) to evade detection and launch malware.
We also saw a return to “bring your own driver” attacks, with malicious actors using vulnerable drivers from legitimate software to elevate privilege and attempt to shut down endpoint detection and response products to evade detection.
On the mobile front, we continued to see malicious or fraudulent fake applications evading detection by the major mobile app marketplaces. Some of these apps are part of a rapidly expanding class of cybercrime: financial trading fraud. Sophos has tracked the rapid expansion of crypto and other trading scams, such as “pig butchering” schemes, over the past year; these schemes have found new ways to use fake applications to dupe victims into exposing their mobile crypto wallets or to get them to directly transfer funds, including abuse of Apple’s iOS ad-hoc application deployment schemes.
More details on these and other findings can be found in the full report.
Source: Sophos
Sophos Firewall OS v19.5 is a free upgrade for all licensed Sophos Firewall customers.
We are pleased to announce that Sophos Firewall OS v19.5 is now released and generally available. This update to Sophos Firewall brings a number of exciting enhancements and top requested features.
What’s new
Xstream SD-WAN
- SD-WAN load balancing builds on the powerful SD-WAN capabilities introduced in v19 to add load balancing across multiple SD-WAN links for added performance and redundancy.
- IPsec VPN capacity is also significantly increased, enabling up to double the number of concurrent tunnels depending on your XGS Series model.
- Dynamic routing with OSPFv3 (IPv6), which has been one of our top requested features, bringing enhanced routing, flexibility, security, and performance.
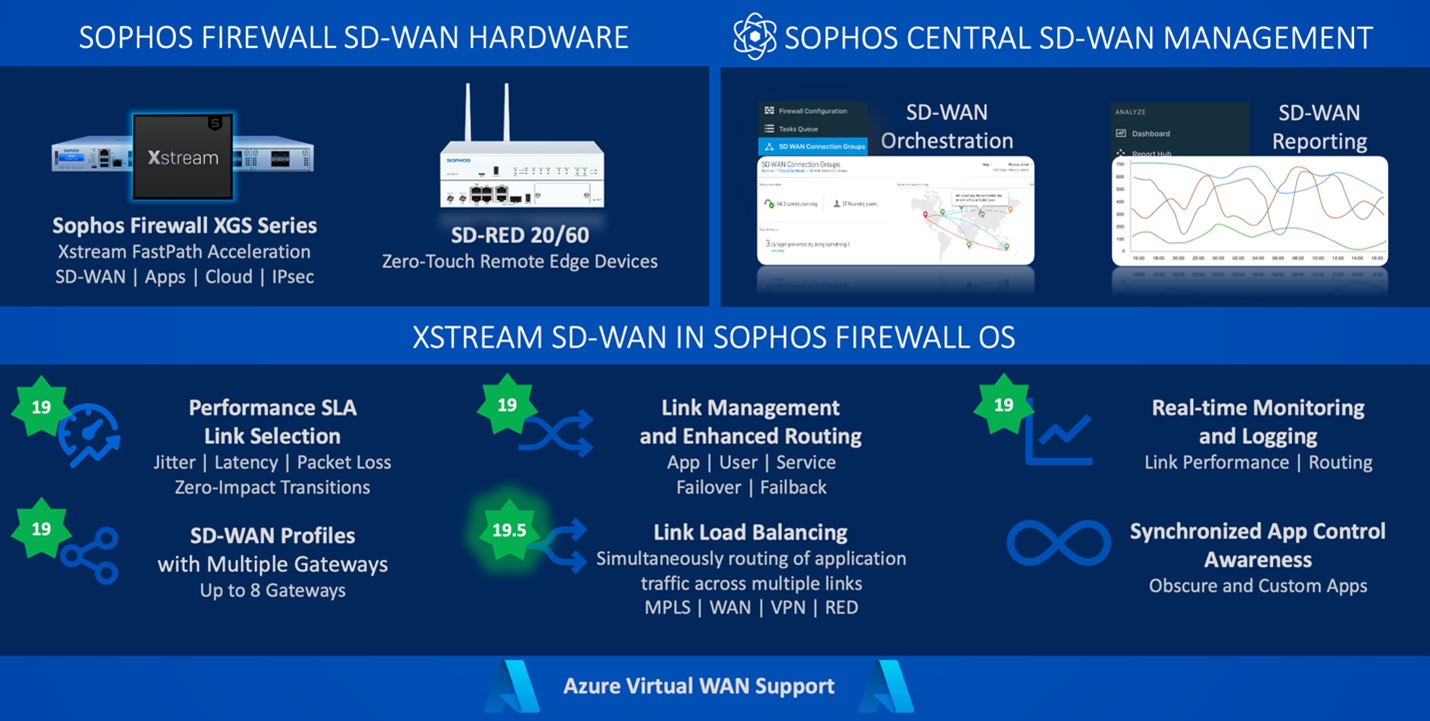
Xstream protection and performance
- Xstream FastPath acceleration of TLS-encrypted traffic takes advantage of the hardware crypto capabilities in the Xstream Flow Processor to accelerate TLS encrypted traffic flows on the FastPath of the XGS 4300, 4500, 5500, and 6500. This provides added performance headroom for traffic that requires deep-packet inspection.
High availability
- Several status, visibility, and ease-of-use enhancements improve the operation of high availability (HA) configurations.
- Redundant link support enables your high availability devices to be connected with multiple redundant HA links for resiliency and reliability.
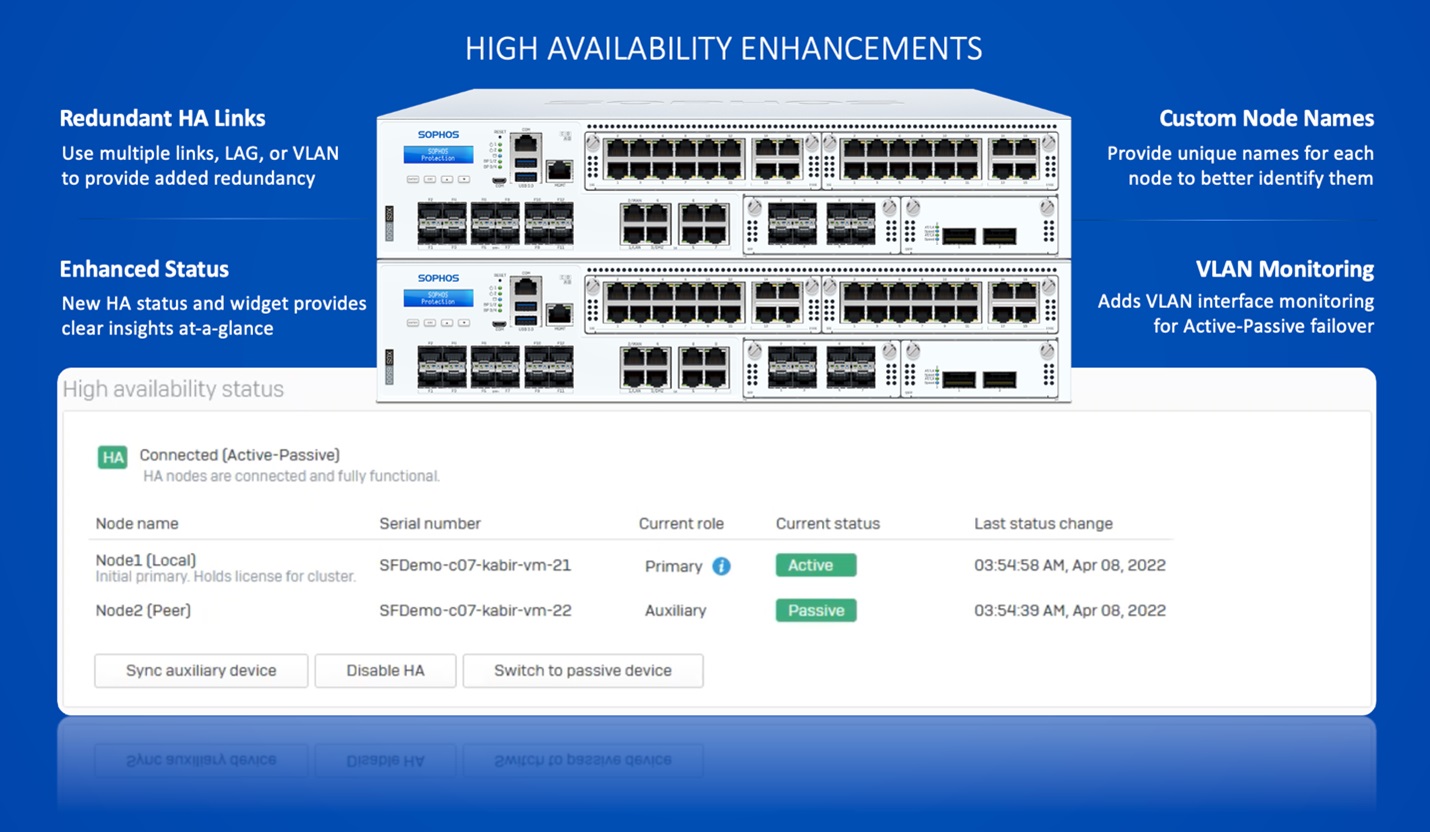
Quality-of-life enhancements
- Azure AD integration for SSO web console login offers an alternate and easier method of authentication.
- Host and service object search enables you to perform free text searches for host and service objects by name or value.
- Enhanced .log file storage enables advanced troubleshooting.
- Enhanced 40G interface support with auto-detection of advanced port configurations on XGS 5500 and 6500 models.
Get the full list of what’s new
Download the full What’s New guide for a complete overview of all the great new features and enhancements in v19.5.
See the new features in action
How to get the firmware, documentation, and training
As usual, Sophos Firewall OS v19.5 is a free upgrade for all licensed Sophos Firewall customers and should be applied to all supported firewall devices as soon as possible, as it not only contains great features and performance enhancements, but also important security fixes.
This firmware release will follow our standard update process. You can manually download SFOS v19 from the Licensing Portal and update any time.
Otherwise, it will be rolled out to all connected devices over the coming weeks. A notification will appear on your local device or Sophos Central management console when the update is available, allowing you to schedule the update at your convenience.
Sophos Firewall OS v19.5 is a fully supported upgrade from any v18.5 firmware as well as v19, including the recent v19 MR1 build 365 release, and the v19.5 EAP build. Please refer to the Upgrade Information tab in the release notes for more details.
Full product documentation is available online and within the product.
Update training (for v19 to v19.5) is available on the Sophos Training Portal.
Source: Sophos
Sophos MDR recorded an exceptional performance with results that validate our position as one of the top performing security services vendors in the market.
On November 9, 2022, MITRE Engenuity™ released the results from their first-ever ATT&CK® Evaluation for Security Services Providers. The evaluations highlighted results across 15 security services providers, assessing their capabilities in detecting, analyzing, and describing adversary behavior.
Sophos Managed Detection and Response (MDR) successfully reported malicious activity across all 10 MITRE ATT&CK® steps, excelling in its ability to detect and respond to sophisticated threat actors with speed and precision.
Why MITRE Engenuity introduced an ATT&CK Evaluation for managed services
For nearly 5 years, MITRE Engenuity has conducted independent evaluations of cybersecurity products using an open methodology based on the ATT&CK knowledge base. These evaluations are predicated on real-world attack emulations that simulate the tactics, techniques, and procedures (TTPs) of relevant advanced persistent threats (APTs) and task vendor participants with demonstrating their ability to detect, analyze, and describe those activities.
The primary objective of ATT&CK Evaluations is to help cybersecurity solution providers—and the organizations they support—make better decisions to combat cyberthreats and improve threat detection capabilities. However, MITRE survey results have shown that it’s challenges related to people (training and hiring), not cybersecurity products and technology, that are the main limitation preventing organizations from advancing their security operations programs.
In its survey of more than 400,000 information security professionals worldwide, MITRE Engenuity found that 58% of organizations rely on managed services to either complement their in-house security operations center (SOC), or serve as their main line of defense. This number was even higher (68%) when considering companies under 5,000 employees. At the same time, roughly half of these organizations reported a lack of confidence in their managed service’s people or technology.
In response to the rapid adoption of managed services and associated cybersecurity challenges, MITRE Engenuity developed and administered a new evaluation methodology that allows end users to better understand how security services like Sophos MDR address adversary behavior.
What is OilRig?
The MITRE Engenuity ATT&CK Evaluation for Security Service Providers evaluated Sophos MDR and other vendors’ abilities to detect and analyze attack tactics and techniques simulating those used by OilRig, an Iranian government-affiliated threat actor – also known as APT34 and Helix Kitten.

OilRig has conducted operations relying on social engineering, stolen credentials, and supply chain attacks, resulting in the theft of sensitive data from critical infrastructure, financial services, government, military, and telecommunications.
This threat actor was selected for use in the MITRE ATT&CK Evaluation for Security Service Providers based on its evasion and persistence techniques, its complexity, and its relevancy to industry.
Unlike MITRE Engenuity’s ATT&CK Evaluations for Enterprise, which follow an open book methodology where participating vendors know in advance the adversary being emulated, the MITRE Engenuity’s Security Services evaluation did not disclose the adversary group or the technique scope.
How did Sophos MDR perform in the MITRE Engenuity ATT&CK Evaluation for Security Service Providers?
Sophos Managed Detection and Response (MDR) successfully reported malicious activity across all 10 MITRE ATT&CK steps, excelling in its ability to detect and respond to sophisticated threat actors with speed and precision. This was a detection-only evaluation, meaning that MITRE Engenuity did not evaluate vendors’ ability to execute threat response actions.
It is important to note that ATT&CK Evaluations are not competitive analyses and do not designate a “winner.” And while there is no singular way for analyzing, ranking, or rating the participating vendors, Sophos MDR recorded an exceptional performance with results that validate our position as one of the top performing security services vendors in the market.
For more details about the evaluations and their results, visit https://attackevals.mitre-engenuity.org/managed-services/managed-services.
Source: Sophos
A few years ago we saw how a new wave and trend in ransomware attacks. In the attacks on the City of Pensacola and the New Jersey synagogue, not only had the data been encrypted, it had been exfiltrated and the attackers were demanding a ransom for not making it public.
The impact of these types of attacks goes beyond encryption and the need to recover backups, but puts companies at risk of suffering significant financial and reputational losses from lawsuits, litigation and non-compliance with regulations.
In the last years we saw how this trend has gone further and some organizations have even decided to pay attackers to avoid penalties or litigation.
Publication of company data by DDoSecrets activists
Some time ago, the activists known as “Distributed Denial of Secrets” DDoSecrets published on their website more than 1 terabyte of sensitive data that were exfiltrated in ransomware attacks and had been picked up from “dark web” sites. This data includes more than 750,000 emails and documents from different companies. Additionally, this group of transparency activists is privately offering massive amounts of business data to a select group of journalists and academic researchers. These data come from companies in different sectors such as financial, pharmaceutical, energy, manufacturing, retail, software, real estate.

According to DDoSecrets, if there is information, technical data, specifications, etc. of a company in any sector that can accelerate the progress of a certain industry or make people’s lives safer, they have a duty to make this information available to journalists and people in academia so that they know the dark way in which these companies typically operate.
1.2 GB of published data from the Scottish Environmental Protection Agency
The Scottish Environment Protection Agency (SEPA) had confirmed that, after refusing to pay a ransom, an organized group of hackers had published 1.2 GB of data extracted as a result of a ransomware attack. According to the agency at least 4,000 files have been stolen that included workers’ personal information purchasing information, documents on ongoing projects, and information related to the agency’s corporate plans.
Data published after exfiltrations in financial and wealth management companies
At the end of 2020 stolen data from different financial and wealth management companies published were found on sites operated by Sodinokibi and NetWalker ransomware gangs. The way of operating is the one that we have already commented, first the confidential data of these organizations are stolen to later request a ransom for not publishing this data. This data contained employee files, audits, financial documents, payroll data, customer files, etc. Even the Sodinokibi criminal gang auctioned this data on different forums on the Dark Web.
Attacks targeting executives to extract confidential information
Ransomware gangs are targeting the computers or devices of senior company executives to obtain sensitive information that they can later use to extort money from companies for hefty ransoms. According to ZDNet, discovered this tactic after talking to a company that had paid a multi-million dollar ransom to the Clop ransomware gang. After several calls, they discovered that this was not an isolated case.
This group focuses on extracting files and emails from executives that can be useful to threaten them and put the company’s management under pressure to obtain a ransom. Ransomware attacks usually go for the “crown jewels” or those data that have the most value for the company, so it is not surprising that sooner or later they focused their objectives on the group of company executives.
27% of organizations decide to pay the ransom
According to a survey conducted by security maker Crowdstrike, among all organizations attacked by ransomware 27% decide to pay the ransom, with the average being USD 1.1M. Many decide to make the payment to avoid fines for non-compliance with regulations, or to face litigation and millionaire lawsuits or simply to avoid further scandals that can seriously damage their reputation.
For example, the University Hospital of New Jersey paid 670K USD to the SunCrypt ransomware band to prevent the publication of 240 GB of stolen data including patient data. After 48,000 documents pertaining to the hospital were published, a representative of the hospital contacted the attackers via its payment portal on the dark web to negotiate the cessation of new publications of patient data.
To pay or not to pay the ransom
Of course, the FBI strongly advises against paying a ransom, partly because it does not guarantee that the criminal organization won’t have access again to your data or that it won’t be published. Furthermore, it incites attackers to increase their actions against other organizations and to continue profiting from extortion. In any case, the FBI understands that when companies are unable to continue with their functions, they will evaluate all options to protect their shareholders, employees and customers. On the other hand, the controversy arises as to whether paying a ransom may violate laws on financing terrorist activities, money laundering, etc.
Data encryption as a means to protect against a ransomware attack
Data encryption protects information wherever it moves. If the data has been encrypted, it will be inaccessible or useless to cybercriminals. The data may be re-encrypted by the malware, but if it is extracted, they cannot be published as is happening in recent attacks where data is extracted in clear and extorted with the potential publication of the same.
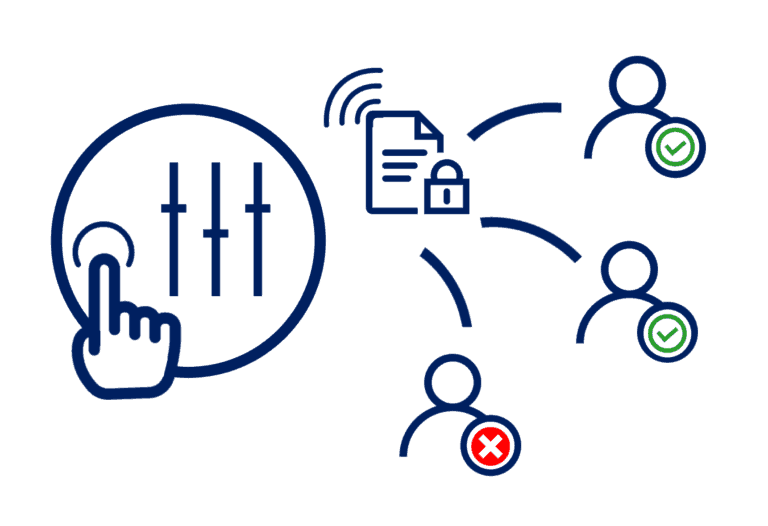
Organizations must not only consider a traditional encryption solution to protect themselves from these attacks, but also one that have control on access and identity so makes it possible to restrict access permissions (View, edit, print, etc.).
How SealPath can help prevent the effects of a ransmoware attack
With a data-centric security solution like SealPath:
- The data will remain protected when is at rest, in transit and in use.
- It is possible to limit access permissions, so that if a document is shared with a third party, they can open it and work with the document without having to unprotect it, thus the copies remain encrypted wherever they behave.
- It is possible to control the identity of the people who can access a certain file. In this way, if an identity has been compromised, it is possible to revoke access to the documents to it.
SealPath also offers a complete audit of accesses to protected information, so that users’ activity on sensitive documentation of the organization can be seen. If you want to know more, click below, and you will see the features of SealPath’s data protection solution.
Don’t wait to ask yourself whether or not the ransom is worth paying, put the means first to have your data safe and under control in any location and safe from possible ransomware attacks. Contact our team here and we will help you as soon as possible.
Source: SealPath
IT-SA EXPO&CONGRESS IS EUROPE’S LARGEST TRADE FAIR FOR IT SECURITY…
…and one of the most important dialogue platforms for IT security solutions.
The trade fair covers the entire range of products and services in the field of cybersecurity: hardware, software, training and consulting services as well as Security as a Service. Important topics at it-sa are cloud and mobile security, data and network security, the protection of critical infrastructures, and industrial Security.
Since 2009, it-sa Expo&Congress in Nuremberg has been the meeting place for decision-makers, experts and IT security officers from all sectors of the economy. Whether they represent industry, the service sector or public administration, the exhibitors at it-sa offer customized and individual solutions.

On the exhibitor side, it-sa addresses the entire IT security market, including physical IT security. The event thus offers trade visitors a showcase of the IT security industry from Germany and abroad that is unique in Europe. Outstanding innovations by young companies in the field of cyber security will be honored with the ATHENE Startup Award UP@it-sa.
The freely accessible lecture program and product-neutral contributions and discussion panels from the it-sa insights series provide trade fair visitors to it-sa with the latest expertise in the industry. In addition, the congress program Congress@it-sa, organized in cooperation with renowned associations and organizations, offers an intensive dialogue on current topics in IT security.
NSS’s Executive Director, George F. Kapaniris, visited Europe’s largest cyber security exhibition/conference and had meetings with partners and prominent executives from the cyber security field, including SOPHOS, BeyondTrust, Fortra (HelpSystems), Cherry Solutions and others.
NSS is an international Value Added Distributor of leading edge IT solutions, covering technology areas including information security, networking, unified communications, data storage, virtualization, and data centre infrastructure systems. Through high technology and deep knowledge of the marketplace, NSS executes the due diligence to select leading edge strategic partnerships with superior vendors and leading technologies that give our channel an opportunity to differentiate from the competition in a crowded market through first class proven solutions.



NSS offers its resellers a portfolio of products that integrate to each other ideally for creating innovative solutions. NSS together with the channel partners can develop opportunities and convert them to sales. NSS having developed a circle of trust with the vendors use trade-in options to encourage new business together with the channel. Last but not least, NSS is applying waste management practices in order to dispose of used equipment securely and responsibly, sometimes even helping in acquiring the new equipment offered. NSS Professional services include extensive presales, implementation, configuration and training. NSS has an impressive pool of skilled engineers and consultants to support the VARs.
HelpSystems announced today that it has become Fortra™ a name synchronous with security and defense. This evolution reflects the company’s enhanced commitment to helping customers simplify the complexity of cybersecurity in a business environment increasingly under siege. With a stronger line of defense from a single provider, organizations of all kinds can look to Fortra to increase security maturity while reducing the burdens to everyday productivity.
“The cybersecurity industry is always changing, and we’re evolving along with it,” said Kate Bolseth, CEO, Fortra. “This is a pivotal, exciting moment for us as we’re defining a new, bold path forward that will bring positive change to the industry and our customers. Everyone at Fortra is rallying behind this movement to tackle seemingly unmanageable security challenges and alleviate the constant worry many of our customers face. As Fortra, we want our customers to think of us as their cybersecurity ally, with them every step of the way.”
 In recent years, Fortra has grown to more than 3,000 employees with offices in 18 countries and over 30,000 global customers. As part of this evolution, the company shifted its focus to cybersecurity and automation, building a best-in-class portfolio with key capabilities in data security, infrastructure protection, and managed security services. These acquisitions have included Alert Logic, Digital Guardian, Cobalt Strike, Tripwire, Digital Defense, Terranova Security, Agari, PhishLabs, Core Security, GoAnywhere, Titus, and other well-known software and services providers.
In recent years, Fortra has grown to more than 3,000 employees with offices in 18 countries and over 30,000 global customers. As part of this evolution, the company shifted its focus to cybersecurity and automation, building a best-in-class portfolio with key capabilities in data security, infrastructure protection, and managed security services. These acquisitions have included Alert Logic, Digital Guardian, Cobalt Strike, Tripwire, Digital Defense, Terranova Security, Agari, PhishLabs, Core Security, GoAnywhere, Titus, and other well-known software and services providers.
Such a rich collection of proven solutions has built the organization’s roster of industry experts and enabled innovative integrations to help customers solve challenges in new, streamlined ways. These integrations incorporate emerging threat intelligence for more effective protection against rapidly evolving cyberthreats. In fact, Fortra’s 350-person threat research and intelligence team stays abreast of emerging threats not only to guide customers in their defense efforts, but also to infuse its software and services with critical insights.
“We’re proud of our role as a trusted leader in the industry and will continue to give our customers the same people-first support and best-in-class solution portfolio they’ve come to expect, making cybersecurity stronger and simpler than ever before,” Bolseth said.
HelpSystems Is Now Fortra
The realm of cybersecurity and automation is always changing, and we’re evolving right alongside it. Say hello to Fortra, the new face of HelpSystems. We’re bringing you the same people-first support you’ve come to expect from HelpSystems, only now we’ve been Fortra-fied with the purpose of providing you with exceptional protection and peace of mind along every step of your journey.
Our team of expert problem solvers is ready to find answers to your organization’s toughest problems, and our best-in-class portfolio ensures that we’ll land on an integrated, scalable solution that’s right for you.
We’re tenacious in our pursuit of a stronger, simpler future for cybersecurity.
Who’s with us?

The Fortra Story
Problem solver. Proactive protector. Relentless ally.
These three pillars represent who Fortra is as a positive changemaker for cybersecurity. Our approach is different, and we’re proud of that. We transformed the industry by bringing the leading solutions into one best-in-class portfolio, creating a stronger line of defense from a single provider.
But we know cybersecurity is always changing, and we should never get too comfortable. It’s why our team of experts is dedicated to building leading solutions and adapting to stay ahead of the ever-evolving threat landscape.
We also understand that we’re more powerful together, so we prioritize collaboration with customers. We take the time to listen to each organization’s concerns, and provide the right solutions to help put worries to rest. Because ultimately, we know that the road to creating a stronger, simpler future for cybersecurity begins with the daily commitment of finding better ways to reduce risk while supporting productivity.
We’re Stronger When We’re All Stronger
 At Fortra we’re on a journey to help organizations everywhere realize their full potential. Our Diversity, Equity, and Inclusion (DEI) Council is effecting meaningful change in our organization – change that will make us stronger and enable us to build more equitable communities.
At Fortra we’re on a journey to help organizations everywhere realize their full potential. Our Diversity, Equity, and Inclusion (DEI) Council is effecting meaningful change in our organization – change that will make us stronger and enable us to build more equitable communities.
The right way to do that is to channel the passion, talent, and perspectives of a diverse team. We strive for equity for all and recognize we’re better when we involve everyone, inclusive of age, sex, race, nationality, gender identity, sexual orientation, religious affiliation, parental status, marital status, military service, disability status, neurodiversity, and all other qualities that create unique individuals.
Learn more at Fortra.com
Hackers have a deep playbook for penetrating networks. Even when managed service providers (MSPs) provide their clients with a robust defense, malicious actors can still infiltrate systems to launch ransomware or other attacks.
Small and medium-sized businesses (SMBs) look to MSPs for help because they can’t protect themselves in the face of mounting threats. For example, a recent study showed that ransomware attacks have nearly doubled since 2020, just one of many attack vectors that can severely impact company operations.
While MSPs are increasingly well-versed in cybersecurity measures, they can become overwhelmed. Software tools such as antivirus (AV) and endpoint detection and response (EDR) help them to detect when security issues arise. However, many MSPs do not have the necessary capabilities to carry out threat hunting and incident response for digital forensics investigations and analyzing malware.
Highly trained cybersecurity professionals with the skills to provide advanced threat protection (ATP) are expensive to hire and in high demand. The vast majority of MSPs are not in the position to build up a massive ATP infrastructure and team, but they do have a quality option: managed detection and response (MDR).
Also known as a managed security operations center (SOC), or MDR, managed SOC provides the highest level of threat protection to MSPs and their clients. It combines technology solutions with expert human teams for advanced threat hunting, monitoring and incident response. Armed with MDR, MSPs can identify threats and quickly limit their impact without having to add costly additional staff.
What is MDR? A cybersecurity necessity
The role of managed SOC, or MDR, solutions has evolved significantly in an MSP’s practice. For an increasingly large proportion of SMB clients, MDR has gone from a nice-to-have to a necessity.
This shift is reflected in the core tenets of the NIST cybersecurity framework, a set of interconnected steps for managing risk to critical infrastructure. They are:
- Identify
- Protect
- Detect
- Respond
- Recover
Most organizations today – MSPs, small businesses, IT departments – spend 85% of their budget on “protect”, leaving only a small portion to spend on the other four phases. However, there is a growing awareness that a change in cybersecurity investment is now needed. The leading research firm Gartner recently observed:
“IT risk and security leaders must move from trying to prevent every threat and acknowledge that perfect protection is not achievable. Organizations need to detect and respond to malicious behaviors and incidents, because even the best preventative controls will not prevent all incidents.”
Adding MDR and managed SOC are how MSPs address this reality. For example, protection measures such as AV and firewall may detect malicious files, but additional security must now go far beyond that.
That’s because hackers are increasingly using techniques to infiltrate networks that do not appear malicious on the surface, allowing them to evade defenses. Once a hacker has entered an SMB’s network with this technique, they can dwell unseen in the system, gathering critical information before they strike.
For instance, bad actors know that they can use a normal tool like the Windows PowerShell command-line interface (CLI) for abnormal activities. Working from PowerShell, a hacker can then pull the Mimikatz open-source application to watch for and harvest authentication credentials as packets move through the system. AV software won’t register something like that as a malicious act, but it’s certainly a suspicious one, especially if the commands are originating from a hostile nation.
MDR helps MSPs to spot bad behaviors that get past AV and other traditional protective measures. With a solution like Datto Managed SOC in place, MSPs are alerted of these hidden compromises so they can find, contain and neutralize such an attack before it becomes a major problem.
Better economics
From a security standpoint, MDR makes sense, especially as ransomware gangs and other bad actors become increasingly sophisticated.
Outsourcing MDR to a managed SOC is also the right budgetary choice for an MSP – and often the only feasible option. That’s because building a SOC from the ground up in-house is prohibitively expensive. Without even accounting for the technology infrastructure, the staffing costs can be staggering. In order to run 24/7 a SOC needs at least three expert security analysts, but it reasonably requires several more than that.
However, skilled MDR professionals are in high demand now and are commanding equally high salaries. That leads to a Catch-22 for MSPs who are considering homegrown MDR services: Do you invest heavily in setting up your in-house SOC first and then try and get the clients? Or do you sell clients on it and then try to build up the staff and services to keep your promises? It’s an expensive risk on the one hand, a reputational risk on the other.
The more sensible path for MSPs is to white label their MDR by outsourcing a managed SOC service. That’s how MSPs are responding to this growing need in the market, in a way that they couldn’t do otherwise.
The role of remediation
With MDR in place via a managed SOC, MSPs can go on the offensive by detecting and containing security threats before they spread. This threat hunting is key to cybersecurity remediation, which is the process of identifying and fixing IT security problems. Remediation also involves resolving any issues that might have arisen after a breach.
 Threat hunting is a more mature security activity requiring deep experience in forensics and incident response – initiatives that most MSPs lack the people, training and tools to undertake. The operations of more and more SMBs are transitioning to digital infrastructure, however, meaning that anyone can become a target. That’s because any kind of customer information today has value, so it can be stolen and resold on the dark web.
Threat hunting is a more mature security activity requiring deep experience in forensics and incident response – initiatives that most MSPs lack the people, training and tools to undertake. The operations of more and more SMBs are transitioning to digital infrastructure, however, meaning that anyone can become a target. That’s because any kind of customer information today has value, so it can be stolen and resold on the dark web.
When an MSP offers MDR, cybersecurity becomes proactive. Managed SOC experts are trained to root out bad actors that have infiltrated SMB endpoints and networks and contain those threats. As discussed above, that goes beyond negating the likes of malware, ransomware, distributed denial of service (DDOS) attacks, and phishing: MDR professionals recognize seemingly normal activities that can devastate a business if left unchecked.
Managed SOC is MDR: How to find the right provider
The right MDR ensures that MSPs can instantly extend their team to include world-class personnel who are experts in 24×7 threat monitoring.
MSPs should look for a managed SOC that protects clients across their entire infrastructure including endpoints, networks and the cloud. Efficient log monitoring, threat intelligence and hunting, breach detection, intrusion monitoring, advanced malware prevention, and PSA ticketing should all be included. These features are essential for comprehensive protection and effective remediation that won’t tax MSP personnel.
Improve your security offerings and experience the confidence that comes with continuous protection against attackers. Schedule a demo of Datto Managed SOC.
Source: Datto
I am thrilled to announce the launch of new third-party security technology compatibilities with Sophos Managed Detection and Response (MDR), our industry-leading service that currently secures more than 12,000 customers worldwide.
By integrating data and telemetry from third-party endpoint, cloud, identity, email, firewall, and other security technologies as part of the Sophos Adaptive Cybersecurity Ecosystem, Sophos MDR can better detect and remediate attacks with speed and precision across diverse customer and operating environments.
Compatibility with your complete cybersecurity environment
Recognizing their commitment to Sophos, all Sophos MTR customers will automatically be upgraded–at no additional charge–to Sophos MDR Complete, our top-tier subscription, later this year. We’re grateful to them for their enthusiastic support over these past three years, and we want to continue to exceed their expectations, so we designed Sophos MDR to make the transition completely effortless and transparent.
We’ve also learned a lot from them: The number one request has always been support for third-party products and platforms, including other endpoint solutions. With these new integrations, security data and telemetry from vendors such as Microsoft, CrowdStrike, Palo Alto Networks, Fortinet, Check Point, Amazon Web Services (AWS), Okta, Google, and many others can be automatically consolidated, correlated, and prioritized with insights from the Sophos Adaptive Cybersecurity Ecosystem and our Sophos X-Ops threat intelligence unit.
MDR that meets you where you are
Every organization has some investment in cyber-risk mitigation technology, but no matter the strength of that defense, a determined attacker will eventually defeat technology alone. It’s helpful to use a shield metaphor when thinking about this: shields buy you time when under attack, but you must use that time to react, or your shield will eventually fail. Missed signals or reaction delays due to complex multi-vendor environments can mean the difference between defense success and failure.
Leveraging a comprehensive cross-product set of telemetry, our teams of experts can quickly and accurately detect and remediate threats across the broad range of a customer’s existing environment, including complex, multi-security vendor scenarios, before they turn into something more damaging, like ransomware or a wide scale data breach.
“The approach that many cybersecurity technology providers have taken with their Extended Detection and Response, and their resulting MDR offerings, is to focus on integrating only their own proprietary hardware and software products, resulting in a closed and limited ecosystem offering. The challenge of this approach is that attributes of existing IT architectures may not be negotiable, given the realities of commercial contracts, technical debt, or IT complexity. By expanding its MDR offering to include compatibility with third-party cybersecurity products, Sophos is delivering a more technology-agnostic managed service that truly meets customers where they are and the realities they are forced to embrace.”
Frank Dickson, group vice president, IDC’s Security and Trust research practice
Openness and compatibility have become absolute essentials for effective cyber defenses, and Sophos MDR delivers superior outcomes in the face of today’s challenges.
24/7 threat hunting designed around your business
The need for always-on security operations has become an imperative. However, the complexity of modern operating environments and the velocity of cyberthreats make it increasingly difficult for most organizations to successfully manage detection and response on their own. Sophos MDR is customizable with different service tiers and threat response options. Customers choose the level of response according to their needs:
- Sophos MDR operations team executes full-scale incident response for you
- We co-manage threat response in collaboration with your team
- Your security operations group gets detailed alert notifications and remediation guidance to help them manage threat response
“Unlike many MDR services in the market today, you don’t have to make any compromises with Sophos – you can keep the cybersecurity tools you already have in place, choose what level of support you need, and what outcomes you want to achieve. Sophos is setting a new standard for how MDR should be delivered, and I won’t be surprised when other providers follow in its footsteps.”
Jeremy Weiss, executive technology strategist, CDW
Availability
Integrations with select third-party security technologies will be generally available at no charge by year end. Customers can also purchase additional integration packs for other compatibility, with pricing based on the number of seats.
Get started with Sophos MDR today
To learn more about Sophos MDR and to discuss how we can you stop advanced cyberthreats, speak with a security adviser and get a custom quote today.
Source: Sophos
Sophos received the highest possible rating in the Product Vision, Execution Roadmap, Supporting Products and Services, Efficacy, Threat Intelligence, Zero Trust environments, and IP Sec and VPN criteri.
Sophos is proud to announce our recognition as a Strong Performer in The Forrester Wave™: Enterprise Firewalls, Q4 2022. We were among a select group of companies that were invited to participate in this report, and we believe it is due to the size, strength, and growth of our Sophos Firewall customer base.
Forrester identified the 10 top vendors in the market, conducted a thorough evaluation against 25 criteria, and Sophos tied for the 2nd highest score in the Strategy category.
Sophos received the highest possible rating in the Product Vision, Execution Roadmap, and Supporting Products and Services criteria, all of which were within the Strategy category. We believe this is a testimony to the aggressive execution of our strategy and roadmap that has delivered several ground-breaking releases. These releases include our Xstream Architecture, powerful XGS Series product line with Xstream Flow Processors, and recent addition of Xstream SD-WAN capabilities, providing our customers and channel partners with differentiated industry-leading protection and performance.
According to the Forrester report: “Sophos has a bold near-term vision for hybrid network security…[and has] added both cloud and on-prem ZTNA, building toward a Zero Trust edge architecture.”
Sophos Firewall also received the highest possible marks in the Efficacy and Threat Intelligence criteria. We are continually enhancing the security technology in Sophos Firewall backed by our world-class Sophos X-Ops team which leverages the predictive, real-time, and real-world threat intelligence from SophosLabs, SophosAI, and our Sophos SecOps teams. Together, this collaboration and integration delivers stronger, more innovative protection, detection and response capabilities. Sophos Firewall is also uniquely integrated with our next-gen endpoint, XDR, and MDR platforms to deliver unmatched visibility and response to active threats.
According to the Forrester report: “Sophos excels at efficacy and quarantine… enthusiastic customer references cited the vendor’s integration with its endpoint software that can autoquarantine infected (and missed-heartbeat) hosts.”
In summary, the Forrester report concluded: “Sophos is an excellent fit for small and medium-size businesses with on-premises users or many distributed locations.”
Sophos Firewall and the XGS Series appliances
Sophos Firewall and the XGS Series appliances with dedicated Xstream Flow Processors provide the ultimate in next-gen firewall visibility, protection, and response with SD-WAN application acceleration, high-performance TLS inspection, and powerful machine learning-based threat protection.
Speak to our network security experts to learn more and get a custom quote, or explore the online demo today.
Source: Sophos
We’ve expanded our Managed Detection and Response service (originally called Sophos MTR) and given it a new name: Sophos MDR. Recognizing their commitment to Sophos, Sophos MTR customers will be upgraded–at no additional charge–to Sophos MDR Complete, our top-tier of service, later this year. Customers will enjoy the same great level of service, plus a host of new capabilities including extended data retention and a new monthly threat landscape webcast.
Delivering the No. 1 customer request: compatibility with non-Sophos tools
With Sophos MDR Complete, analysts can detect and respond to threats across the cybersecurity ecosystem by leveraging security data from both Sophos and non-Sophos security tools. Customers can take advantage of:
- Free integrations with Sophos next-gen technologies, including our endpoint, firewall, cloud, and email protection solutions as well as the new Sophos Network Detection and Response (NDR) solution.
- Compatibility to run alongside 3rd party endpoint protection solutions
- Free integration with the Microsoft portfolio through Graph Security
- 3rd party integrations, available for purchase with add-on licenses for virtually any other security tool that generates threat detection data, including Palo Alto Networks, Fortinet, Check Point, Rapid7, Amazon Web Services (AWS), Google, Okta, Darktrace, and many others
The more we can see, the more we can detect and the faster we can respond. With each additional data source, our analysts gain deeper visibility as they begin to see around corners and into the actions taking place beyond the endpoint. By automatically correlating data from Sophos and non-Sophos tools, we can see higher fidelity detections and reduce manual investigation times. And customers get more out of the tools they already have.
There are so many benefits to expanding your detection and response ecosystem to include your existing security solutions. For example:
- Firewall and network telemetry can identify rogue assets and unprotected devices, as well as insider threats and novel attacks
- Email alerts can pinpoint initial entry into the network and attempts to steal account names and passwords
- Identity data can point to unauthorized network entry and attempts to move through higher levels of permissions
- Cloud alerts can indicate unauthorized network access, efforts to steal account names and passwords, and access to proprietary data
Plus much more!
To learn more about our third-party integrations and discuss extending your security defences with full-environment threat detection and response, reach out to your Sophos account team or Sophos partner.
Extended data storage and monthly webcast
For all Sophos MDR service tiers, including Sophos MDR Complete, we are increasing standard data storage to 90 days at no additional cost. With the median dwell time for intrusions not involving ransomware coming in at 34 days*, this extended data storage will better enable analysts to determine the root cause of incidents and, in turn, better advise on how to harden defenses to prevent further attacks. Customers who require a longer data retention period, for example to meet compliance or regulatory requirements, can take advantage of an add-on license for a full year of data storage.
It can be challenging to keep up with the fast pace of security threats. We are excited to introduce an exclusive monthly webcast for MDR Complete customers, the Sophos MDR ThreatCast, where we’ll share observations on recent threat activity across our 12,000+ customer base. Attendees will get to know the team of threat analysts and researchers working behind the scenes to protect their organizations and deepen their understanding of the threat landscape.
Scale incident response
Like Sophos MTR Advanced, with MDR Complete, once suspicious activity is detected, the MDR operations team contains and eradicates the threat. Their systematic approach enables them to identify the root cause and then use these insights to elevate protection across the entire customer base.
We’ll take care of the upgrade for you
All Sophos MTR customers will be automatically upgraded to Sophos MDR Complete later this year. We’ll take care of everything for you – no need to do anything.
Not yet using Sophos MDR?
Sophos MDR meets you where you are. Our expert analysts detect and respond in minutes to threats across your entire environment, 24/7/365, whether you need full-scale incident response or assistance making more accurate decisions. To learn more, visit www.sophos.com/mdr or speak with an adviser today.
Source: Sophos
How to prevent data leakage from insider attacks
Insider threats involve stealing information and conducting malicious activity. A sophisticated insider threat actor may use tools traditionally associated with an external threat. For instance, an insider engaging in malicious behavior could install data-capturing software, exploit a system missing security patches, and access resources using backdoors to conduct data-gathering activity.
Ultimately, we need to recognize insider threats are able to succeed due to at least one of the following:
A. Excessive/inadequately managed privileges (covered in steps 1 – 5 below)
B. Poor security hygiene (vulnerability, configuration management, and audit/log management, covered in steps 5 – 10 below)
With the above (A+ B) in mind, all organizations should implement these security best practices to mitigate insider threat risks:
1. Enforce least privilege and separation of privilege: No one should ever use an administrative account for day-to-day usage (i.e. email, web searches, etc.). This also applies to administrators as the potential risk is much higher should their account be compromised, such as by clicking on a malicious phishing link. All users should be restricted to standard user permissions and only have the ability gain momentary privileged access via controlled and monitored workflows. Privileged Access Management (PAM) solutions are specifically designed to manage this use case.
2. Restrict data access: Only administrators or role-specific employees (not executives) should have access to data en masse. This prevents an insider from dumping large quantities of information, or an executive’s account being hacked and leveraged against the organization to exfiltrate data.
3. Mature identity and access management (IAM) policies: All access to sensitive data should only be for valid employees. Former employees, contractors, and even auditors, should not have routine access. Accounts should be removed or deleted per your organization’s policy. Implement a just-in-time-access model to eliminate standing privileges and ensure all privileged access is finite.
4. Use Enterprise Password Managers: Employees come and go. If the passwords are the same as people leave and new hires are onboarded, the risk to sensitive data increases since former employees technically still have known passwords to the company’s sensitive information. Passwords should be random and unpredictable. Use password management solutions to automate password security best practices via a centralized vault.
5. Implement robust monitoring: Monitoring user behavior and network activity is critical to detecting anomalous, or otherwise dangerous, activity and acting early enough before it causes damage. Privileged activity is especially important to monitor as it poses the most risk for damage and can mean an attack is on its way to quickly escalating. Monitor logs, sessions, keystrokes, and applications and also implement screen recording. If an insider accesses a sensitive system to steal information, session monitoring can document their access and identify how and when they extracted the information. Data loss prevention (DLP) solutions may also help here, but only if the point of egress is considered a risk, or there are regulatory compliance ramifications.
6. Ensure anti-virus or endpoint protection solutions are installed, operating, and stay up-to-date to identify any malware being used by an insider threat.
7. Allow Windows and third-party applications to auto-update, or deploy a patch management solution to apply relevant security patches in a timely manner to remediate the risks of a vulnerability being exploited.
8. Utilize a vulnerability assessment or management solution to determine where risks exist in the environment and correct them in a timely manner so an insider cannot exploit a security weakness.
9. Implement an Application Control solution with Trusted Application Protection (TAP) to ensure only authorized applications execute with the proper privileges to mitigate the risk of rogue, surveillance, or data collection utilities. Ideally, the solution also has fileless threat protection capabilities that can apply context to activities and requests from trusted applications, including blocking child process.
10. Where possible, segment users from systems and resources to reduce “line-of-site” risks. That is, make sure your network is segmented–not flat—to avoid over-reaching access.
Most businesses fail at adequately implementing these basic security controls. However, following the above 10 practices can significantly help protect against insider threats as well as other attack vectors.
Implementing insider threat protection
Insider threats are not going away. The goal is to stop the data leakage and be aware an insider has multiple attack vectors to achieve their goals.
As security professionals, we need to mitigate the insider risks at the source. A briefcase of paper represents an insider threat, but is probably not as relevant as a USB stick with your entire database of client information.
In the end, an insider typically still needs privileges to steal all this information. Removing excessive privileges, such as by implementing privileged access management (PAM) controls and closing open security holes via vulnerability management will help minimize your attack surface from insider exploits, as well as many other types of attacks. In addition to security controls over access, organizations need to layer strong monitoring capabilities for insider threat detection. Finally, training security analysts and other IT staff on insider threat indicators, and how to respond to them, is important in nullifying any active risk.
Source: BeyondTrust
What is an insider threat?
An insider threat is an internal persona acting as a trusted asset (employee, contractor, vendor, partner, etc.) behaving as a threat actor. Typically, the insider exhibits malicious behavior with intent, but sometimes, they are unaware of their actions are directed by an external threat actor. Regardless, the insider misuses their access and privileges for illicit purposes intentionally, or as directed by an external force.
Today, we need to be realistic about what an insider threat is and acknowledge that they have occurred, in various forms, for ages. Years of threat data shows us that insider threats are typically the hardest to detect, while also posing the most potential for damage. By recognizing insider threat indicators, organizations can detect insider attacks faster and prevent, or mitigate, the damage.
The risks of insider threats
By now, most security professionals are well-versed regarding the risks from insider threats. Years ago, these attacks regularly captured news headlines, but today they are the silent threat few organizations want to disclose or publicly admit.
Regardless of the malicious techniques an insider threat actor employs, they are not behaving in the best interest of the company. The insider is potentially breaking the law, and likely exfiltrating information they do not have permission to possess, or performing other damaging actions.
A longstanding example of an insider threat is the stealing of clients lists by a salesperson, executive, etc., who is planning to leave the organization. Perhaps they have photocopied or printed the client lists and purchase orders so they have a competitive edge when starting at their next role with a new employer.
Today, with electronic media, and the Internet, an insider can egresse substantive volumes of data without anyone noticing. And, as a reminder, that file cabinet of sensitive information can fit on a USB thumb drive in a person’s pocket or be posted to a personal cloud-based file share, making the contents even more susceptible to additional threats.
While insider threats are perpetrated with ever-more ease thanks to modern modern technology, it’s a subject most organizations find difficult to discuss.
Human beings will do unusual things in the most dire of situations, but if they are not permitted to, many insider threat risks can be mitigated.
A shortlist representing some of the more interesting and well-documented insider threats include:
- Edward Snowden – NSA insider threat and self-proclaimed whistle blower. (Government)
- Elliot Greenleaf Law Firm – Multiple attorneys extracted and deleted sensitive information (Legal)
- South Georgia Medical Center – A former employee downloaded personal information (Healthcare)
How to assess your vulnerability to insider threats
As we evaluate how to identify and mitigate the risks associated with insider threats, consider these facts regarding your organization:
- How many people have access to sensitive information en masse?
- Who can export large quantities of information from a query or third-party system?
- Are all the active accounts valid?
- Are all accounts related to people that are still employed at the organization or via third parties?
- How do you identify rogue or shadow IT accounts?
- How often do you change the passwords for sensitive accounts?
- Do you monitor privileged access to sensitive systems and data?
In fairness, honestly answering those questions could be opening Pandora’s box. You may not like the answers, or not even know where to begin to get the answers. Nonetheless, you should answer them all if you care about addressing insider threat risk. First, you need to understand your baseline risk and where you should prioritize your next mitigation actions.
Common insider threat indicators & how to detect them
The best way to detect insider threats is to look for indicators of compromise (IoCs) that can be attributed to inappropriate behavior. Sometimes, these can be difficult to detect compared to normal operations, but there is almost always a symptom that will allude to malicious intent.
To that end, consider the following insider threat indicators along with the detection methods:
- Unusual copying, downloading, or movement of sensitive information: This becomes especially concerning when the data or information is moved to an atypical or unauthorized destination. Simply interacting with sensitive data can be an indicator of compromise for unauthorized individuals. This is relatively easy to detect based on identities and access logs. However, if the insider normally and frequently interacts with the data, then it’s the unusual destination that may indicate illicit activity. Destinations can include unauthorized, removable media such as USB drives, cloud-based file storage solutions, and even email.
- Anomalous network search activity: A common assumption is that an insider threat actor knows what data they are looking for and where to find it. That is not always true. Insider threats can be as opportunistic as the next attacker. Malicious Insiders may actively search networks, intranets, ports, applications, etc. for sensitive information that they can extract and leverage. Therefore, monitor for applications and identities performing broad searches and network scans to locate files, buckets, and applications that can give up information as a part of the attack chain.
- Unusual access and login anomalies: If the insider lacks access to data or systems as a part of the business role, but suddenly starts making attempts at access, it could indicate an insider attack is underway. Monitoring authentication and authorization activity is critical to detect for indicators of compromise. If you consider all enterprise assets, consolidation of logs to a SIEM is crucial to gain this perspective. One-off activity will help identify potential anomalies, especially when such access is new. This requires more than just pattern matching in a SIEM and the advanced capability to look for one-time behaviors.
- Misuse of native, or other already installed, tools: Insider threat actors often use tools to help extract information from key systems to satisfy their nefarious missions. Detection of foreign tools can flag an indicator of compromise. However, if the insider is savvy, they may execute a living-off the land (LotL) attack. This entails leveraging native toolsets and other trusted enterprise tools to progress their attack. In that case, behavior becomes the key indicator of compromise. Behaviors to monitor for include access outside of normal business hours, access without proper change control, and network access from unusual or foreign locations. Advanced application control that also protects against fileless threats, such as misuse of trusted applications, is a an important tool for identifying and protecting against these insider threat activities.
Source: BeyondTrust