News
Sophos has released its annual State of Ransomware 2023 report, revealing deep insights into the ransomware challenges facing businesses today based on a survey of 3,000 IT/cybersecurity professionals across 14 countries.
Attack rates remain level, but data encryption has increased
66% of organizations surveyed said they were hit by ransomware in the last year. This is the same attack rate as reported in our 2022 study, suggesting that the rate of ransomware attacks has remained steady despite any perceived reduction in attacks. The education sector reported the highest level of ransomware attacks, with 79% of higher education organizations surveyed and 80% of lower education organizations surveyed saying that they were victims of ransomware.
Data encryption from ransomware is at the highest level in four years with adversaries succeeding in encrypting data in 76% of attacks. Furthermore, in 30% of cases where data was encrypted, data was also stolen, suggesting this “double dip” method (data encryption and data exfiltration) is becoming commonplace.
The most common reported root cause of attack was an exploited vulnerability (involved in 36% of cases), followed by compromised credentials (involved in 29% of cases). This is in line with recent, in-the-field incident response findings from Sophos’ 2023 Active Adversary Report for Business Leaders report.
Paying the ransom doubles recovery costs
Overall, 46% of organizations surveyed that had their data encrypted paid the ransom and got data back. Larger organizations were far more likely to pay with more than half of businesses with revenue of $500 million or more admitting that they paid the ransom.
However, the survey also shows that when organizations paid a ransom to get their data decrypted, they ended up doubling their non-ransom recovery costs ($750,000 in recovery costs versus $375,000 for organizations that used backups to get data back).
Moreover, paying the ransom usually meant longer recovery times, with 45% of those organizations that used backups recovering within a week, compared to 39% of those that paid the ransom.
“Incident costs rise significantly when ransoms are paid. Most victims will not be able to recover all their files by simply buying the encryption keys; they must rebuild and recover from backups as well. Paying ransoms not only enriches criminals, but it also slows incident response and adds cost to an already devastatingly expensive situation.”
Chester Wisniewski, field CTO, Sophos
Mitigating the ransomware risk
Megan Stifel, executive director of the Ransomware Task Force and chief strategy officer, Institute for Security and Technology comments:
“Sophos’ latest report is a clarion reminder that ransomware remains a major threat, both in scope and scale. This is particularly true for ‘target-rich, resource-poor’ organizations that don’t necessarily have their own in-house resources for ransomware prevention, response and recovery.
One way to boost security, which is aligned with Sophos’ findings in the report, is to implement the Ransomware Task Force’s Blueprint for Ransomware Defense, a framework of 48 safeguards based on the CIS IG1 Controls. It’s past time for the private and public sector to band together and collectively fight ransomware, which is why we are excited to work with cybersecurity providers like Sophos.”
Additionally, Sophos recommends the following best practices to help defend against ransomware and other cyberattacks:
1. Strengthen defensive shields, including:
- Security tools that defend against the most common attack vectors, including endpoint protection with strong anti-exploit capabilities to prevent exploitation of vulnerabilities, and Zero Trust Network Access (ZTNA) to thwart the abuse of compromised credentials
- Adaptive technologies that respond automatically to attacks, disrupting adversaries and buying defenders time to respond
- 24/7 threat detection, investigation and response, whether delivered in-house or by a specialist Managed Detection and Response (MDR) provider
2. Optimize attack preparation, including making regular backups, practicing recovering data from backups and maintaining an up-to-date incident response plan
3. Maintain good security hygiene, including timely patching and regularly reviewing security tool configurations
About the survey
Data for the State of Ransomware 2023 report comes from a vendor-agnostic survey of 3,000 cybersecurity/IT leaders conducted between January and March 2023. Respondents were based in 14 countries across the Americas, EMEA and Asia Pacific. Organizations surveyed had between 100 and 5,000 employees, and revenue ranged from less than $10 million to more than $5 billion.
Read the State of Ransomware 2023 report for global findings and data by sector.
Source: Sophos
We’re delighted to share that Sophos Intercept X Endpoint Protection ranked as the industry best in SE Labs’ protection tests in the first quarter of 2023, achieving AAA ratings across the board. In both the Enterprise and SMB categories, we achieved the following:
- 100% rating for Protection Accuracy
- 100% rating for Legitimate Accuracy
- 100% rating for Total Accuracy
Here are the links to the latest reports: Endpoint Security: Enterprise | Endpoint Security: Small Business
Sophos Endpoint: world-leading protection against advanced threats
With decades of cyberthreat intelligence, Sophos designs endpoint protection for real-time defense against modern-day advanced attacks. With a focus on preventing attacks as early as possible, Sophos strategy is to deliver multiple layers of protection to defend the entire attack chain against the many different threat vectors that attackers use to escalate and carry out attacks.
This prevention-first approach reduces breaches and improves detection and response. These SE Labs results testify to the superior cybersecurity outcomes enjoyed by over 300,000 organizations that trust Sophos for their endpoint security.
“Sophos produced extremely good results due to a combination of their ability to block malicious URLs, handle exploits and correctly classify legitimate applications and websites”
–SE Labs
The need to simulate modern-day attacks
Reputable third-party testing is an important tool to help organizations make informed decisions about their technology stacks and security investments. However, as attacks increase in volume and complexity, meaningful results can only be achieved when the tests reflect organizations’ real-world realities.
SE Labs is one of the few security testers in the industry that simulates modern-day attack tools and the tactics, techniques, and procedures (TTPs) that cybercriminals and penetration testers use in the real world.
As Simon Edwards, CEO of SE Labs, explains:
“It is essential for organizations to be able to rely on credible, full attack chain tests that duplicate real-world scenarios. It is not only about throwing a wider range of attacks at the products, but each step of the attack must be realistic too. You can’t just make up what you think attackers are doing and hope you’re right. This is why SE Labs tracks cybercriminal behaviors and builds tests based on how attackers try to compromise victims.”
Test drive Sophos Endpoint for yourself
Sophos Endpoint secures over 300,000 organizations worldwide from active adversaries, ransomware, phishing, malware, and more. Please speak to our security advisers to discuss how we can help you, and take a test drive today.
Source: Sophos
From generating strong passwords to monitoring the security policies and practices of a company, password managers are powerful solutions that defend companies against cyberthreats and improve employee productivity.
Continue reading to learn more about why password management is critical to every organization’s cybersecurity strategy.
What is a Cybersecurity Strategy?
A cybersecurity strategy is a plan for organizations to secure their assets, reduce their cyber risk and protect against cyberthreats. An effective cybersecurity strategy incorporates multiple layers of security and has solutions in each layer to fortify an organization’s defenses.
Improving Your Cybersecurity Strategy Starts With Employees
Employees often store passwords on sticky notes, in a spreadsheet or other unencrypted electronic documents. These unsafe practices stem from the challenge of trying to remember strong, unique passwords for every online account.
When creating passwords, many employees use birthdays, addresses, names of their pets, their favorite sports team or any number of easily guessable combinations. Employees often give up trying to remember unique passwords and repeat the same password – or a version of it – across several accounts. The danger of reusing passwords is if any account is breached, then cybercriminals immediately have access to every other account that uses the same password.
Password managers are cybersecurity tools that aid employees in generating strong, unique passwords and storing them in an encrypted digital vault, accessible from any device. It removes the burden of having to remember multiple passwords and eliminates the risk of employees using weak passwords or the same password across multiple accounts, which places all company accounts and data at risk.
Make Password Management a Part of Your Cybersecurity Strategy
Here are a few reasons why businesses need to incorporate password management as a part of their cybersecurity strategy.
Provides password visibility
Most businesses have limited visibility into the password practices of their employees which greatly increases cyber risk. Password managers enable organizations to have visibility over the password hygiene and risk factors that can result in a data breach.
Provides secure password-sharing capabilities
Each user can securely and easily share password records with varying levels of permissions. Shared information is fully encrypted in transit and at rest, ensuring that the record is not exposed at any point.
Increases employee productivity
Password managers increase employee productivity as they eliminate common password-related issues such as excess time searching for passwords, resetting forgotten passwords and contacting the helpdesk for assistance in resetting a password.
A password manager allows employees to take control of their passwords and use a unique, random and high-strength password for each and every site, system and application. Every employee is provided a secure, cloud-based digital vault that stores passwords and any other critical information such as encryption keys and digital certificates. A password manager will also generate strong, random passwords and automatically fill them in for users, which saves time and frustration.
Streamlines onboarding and offboarding processes
Businesses are constantly changing with new employees starting and current employees moving departments or leaving. It’s impossible for IT teams to manually provision, maintain and log all of the activities needed to keep systems secure and meet compliance standards. As people move throughout the organization, a password manager keeps their access updated. This includes locking an account when an employee leaves and the ability to transfer their vault to a trusted admin.
Enhances SSO solutions
A password manager can enhance Single Sign-On (SSO) by covering gaps such as legacy apps or platforms that don’t function with an organization’s SSO solution.
Helps meet compliance requirements
Password managers are key to meeting global compliance standards and best practices for strong cybersecurity policies. Strong password hygiene and password management systems are integral to any company’s InfoSec policy, regardless of size or industry.
Companies can spend millions on cybersecurity, and many do, but a world-class password manager should be the first investment for formidable, proactive protection.
Source: Keeper Security
Most password managers are very secure and safe to use. Depending on the password manager in question, some offer more security than others. To fully understand the security of password managers you’ll first have to understand what a password manager is.
What is a Password Manager?
A password manager is a cybersecurity tool that aids users in generating strong, unique passwords and storing them securely in an encrypted vault. The greatest benefit of using a password manager is that users no longer have to rely on memory or insecure means of storage to remember passwords for all of their accounts. The only password they’ll have to remember is their master password, which acts as the key to enter a user’s password vault.
Are Password Managers Actually Secure?
While password managers are created to be secure, not all password managers are created equal. The reason the security of password managers has recently come into question has to do with the LastPass password manager. LastPass has been in the news a great deal because of a series of security breaches, including this latest breach.
LastPass isn’t new to breaches. In 2015, LastPass suffered an attack that exposed user email addresses and security information. It’s important to note that unlike more secure password managers, LastPass does not encrypt website URLs and other metadata, which can result in stolen information being used to target users who were a part of the breach.
While LastPass’s history may be concerning to hear, there are password managers that have never been hacked– one of many reasons that password managers are still a cybersecurity best practice recommended by industry and government experts alike. Understanding the security architecture of specific password managers can give users peace of mind that their passwords are secure. Remember, a good password manager protects user data, even in a worst case scenario.
What About Browser Password Managers?
Browser password managers differ from standalone password managers for many reasons. One reason, in particular, is that browser-based password managers are not as secure. Here are a few reasons why.
- A compromised browser will lead to compromised passwords. If your device were to be infected with spyware, a cybercriminal would be able to see all the passwords you have stored in your browser. Passwords stored in browser password managers are stored in plaintext, so about all the cybercriminal would have to do is access your browser settings to view them.
- Browsers are often left logged in. Most people don’t usually log out of their browsers because it’s simply more convenient to stay logged in. However, this poses a major security risk as it makes it easy for anyone to retrieve passwords saved to your browser by just getting their hands on your device. If your device were to get stolen, this makes your accounts even more vulnerable to becoming compromised.
Most people use browser-based password managers due to the convenience of being able to access their passwords. However, not many people realize that convenience doesn’t always mean security – making browser-based password managers a dangerous option for storing passwords.
What is the Safest and Most Secure Password Manager?
The safest and most secure password management solution is Keeper Password Manager. Keeper Security is fanatical about data protection and was built with security as its top priority from day one. Customers are always kept up-to-date on all the steps being taken to secure their data and the improvements being made to the user-friendly platform.
Keeper’s zero-trust and zero-knowledge encryption model ensures that all contents in a user’s vault are protected with multiple layers of safeguards and encryption. Keeper is also the most certified, tested and audited password security platform – holding the longest-standing SOC 2 and ISO 27001 certifications in the industry.
What differentiates Keeper from its competitors, apart from having the most security certifications, is that we implement a multi-layered encryption system. All contents in a vault are encrypted in transit and at rest, including website URLs and other metadata. This is not the case for all password managers.
Learn more about Keeper’s commitment to data protection and why it’s the most secure password management solution available. You can also get started with a free 30-day trial to begin securing your passwords with the safest and strongest password manager on the market.
Source: Keeper Security
All examples of social engineering take advantage of human nature, such as the willingness to trust others, to trick individuals into divulging sensitive information.
Despite its prevalence, social engineering can be challenging to distill into a single formula. It’s one of the reasons 82% of data breaches involve the human element.
Social engineering has become the backbone of many cyber threats, from phishing emails to smishing and vishing attacks. This blog post will outline many popular social engineering techniques and the emotions hackers use to dupe their victims.
9 Most Common Examples of Social Engineering Attacks
In no particular order, here are nine common cyber threats that leverage social engineering tactics to gain access to sensitive information. While most of these attacks occur online, several can rear their heads in physical spaces like offices, apartment buildings, and cafes.
1. Phishing
The most pervasive way of implementing social engineering, hackers will use deceptive emails, websites, and text messages to steal sensitive personal or organizational information from unsuspecting victims.
Despite how well-known phishing email techniques are, 1 in 5 employees still click on those suspicious links
2. Spear Phishing
This email scam is used to carry out targeted attacks against individuals or businesses. Spear phishing is more intricate than your average mass phishing email, as it requires in-depth research on potential targets and their organizations
3. Baiting
This type of attack can be perpetrated online or in a physical environment. The cyber criminal usually promises the victim a reward in return for sensitive information or knowledge of its whereabouts.
4. Malware
A category of attacks that includes ransomware, victims are sent an urgently worded message and tricked into installing malware on their device(s).
Ironically, a popular tactic is telling the victim that malware has already been installed on their computer and that the sender will remove the software if they pay a fee.
5. Pretexting
This attack involves the perpetrator assuming a false identity to trick victims into giving up information. Pretexting is often leveraged against organizations with an abundance of client data, like banks, credit card providers, and utility companies.
6. Quid Pro Quo
This attack centers around an exchange of information or service to convince the victim to act. Normally, cyber criminals who carry out these schemes don’t do advanced target research and offer to provide “assistance,” assuming identities like tech support professionals.
7. Tailgating:
This attack targets an individual who can give a criminal physical access to a secure building or area. These scams are often successful due to a victim’s misguided courtesy, such as if they hold the door open for an unfamiliar “employee.”
8. Vishing
In this scenario, cyber criminals will leave urgent voicemails to convince victims they must act quickly to protect themselves from arrest or another risk. Banks, government agencies, and law enforcement agencies are commonly impersonated personas in vishing scams.
9. Water-Holing
This attack uses advanced social engineering techniques to infect a website and its visitors with malware. The infection is usually spread through a website specific to the victims’ industry, like a popular website that’s visited regularly.
How Does Social Engineering Happen?
Social engineering happens because of the human instinct of trust. Cyber criminals have learned that a carefully worded email, voicemail, or text message can convince people to transfer money, provide confidential information, or download a file that installs malware on the company network.
Consider this example of spear phishing that convinced an employee to transfer $500,000 to a foreign investor:
- Thanks to careful spear phishing research, the cyber criminal knows the company CEO is traveling.
- An email is sent to a company employee that looks like it came from the CEO. There is a slight discrepancy in the email address, but the spelling of the CEO’s name is correct.
- In the email, the employee is asked to help the CEO by transferring $500,000 to a new foreign investor. The email uses urgent yet friendly language, convincing the employee that he will be helping both the CEO and the company.
- The email stresses that the CEO would do this transfer herself, but she can’t make the fund transfer in time to secure the foreign investment partnership since she is traveling.
- Without verifying the details, the employee decides to act. He truly believes that he is helping the CEO, the company, and colleagues by complying with the email request.
- A few days later, the victimized employee, CEO, and company colleagues realize they’ve been the targets of a social engineering attack, resulting in a loss of $500,000.
Examples of Social Engineering Attack Scenarios
Savvy cyber criminals know that social engineering works best when focusing on human emotion and risk. Taking advantage of human emotion is much easier than hacking a network or looking for security vulnerabilities.
The following are some familiar notes successful social engineering attacks hit again and again.
Fear
You receive a voicemail saying you’re under investigation for tax fraud and must call immediately to prevent arrest and criminal investigation. This social engineering attack happens during tax season when people are already stressed about their taxes.
Cyber criminals prey on the stress and anxiety of filing taxes and use these fear emotions to trick people into complying with the voicemail.
Greed
Imagine if you could transfer $10 to an investor and see this grow into $10,000 without any effort on your behalf. Cyber criminals use the basic human emotions of trust and greed to convince victims that they really can get something for nothing.
A carefully worded baiting email tells victims to provide their bank account information, and the funds will be transferred the same day.
Curiosity
Cyber criminals pay attention to events capturing a lot of news coverage and then take advantage of human curiosity to trick social engineering victims into acting. For example, after the second Boeing MAX8 plane crash, cyber criminals sent emails with attachments that claimed to include leaked data about the crash.
The attachment installed a version of the Hworm RAT on the victim’s computer.
Helpfulness
Humans want to trust and help one another. After researching a company, cyber criminals target two or three employees with an email that looks like it comes from the targeted individuals’ manager.
The email asks them to send the manager the password for the accounting database—stressing that the manager needs it to ensure everyone gets paid on time.
The email tone is urgent, tricking the victims into believing they are helping their manager by acting quickly.
Urgency
You receive an email from customer support at an online shopping website that you frequently buy from, telling you they need to confirm your credit card information to protect your account.
The email language urges you to respond quickly to ensure that criminals don’t steal your credit card information.
Without thinking twice, you send the information, which results in the recipient using your details to make thousands of dollars of fraudulent purchases.
How to Protect Your Information from Social Engineering Attacks
Though social engineering tactics are common, the examples in this blog post underscore how difficult they can be to spot and, more importantly, resist. Reacting based on human nature pushes many people toward a cyber criminal’s desired outcome.
To safeguard against the prevalence of social engineering tactics, it’s essential to arm yourself with the right tools and knowledge. Our Cyber Security Hub offers a comprehensive cyber security resource, including the latest information on social engineering threats.
By staying informed and empowered with our hub, you can proactively protect yourself and your sensitive data from malicious cyber attacks. Access our Cyber Security Hub for free today to secure your digital assets and stay ahead of potential threats.
Cyber Security Hub: Access Exclusive Cyber Security Content
White Paper – How to Protect Your Data from Social Engineering
Source: Terranova
Sophos Intercept X with Extended Detection and Response (XDR) has been rated the #1 XDR solution by G2 users in their spring 2023 reports (March 2023). G2 distinctions and rankings are based solely on independent, verified customer reviews on G2.com, the world’s largest software marketplace and peer-review platform.

Check out the full reviews on G2.com and how Sophos was named a leader in several other categories, including Endpoint, EDR, Firewall, and MDR.
XDR for the real world
Designed for security experts and IT administrators alike, Sophos Intercept X with XDR enables analysts to detect, investigate, and respond to threats across their entire security environments quickly and accurately.
Building on the strong protection foundation of Sophos Intercept X Endpoint technology, our XDR solution brings together telemetry from endpoints, servers, mobile devices, network, email, and cloud solutions for optimal visibility and accelerated response. Alternatively, organizations looking just for Endpoint Detection and Response (EDR) capabilities can utilize the same detection and response tools, focusing solely on their endpoints.
The G2 rating endorses our commitment to a prevention-first approach that reduces breaches and improves detection and response.

Sophos Intercept X with XDR has had several impressive and innovative updates that enable customers to enjoy superior cybersecurity outcomes:
- Third-party integrations enable customers to extend their visibility into threats and conduct more complete investigations to swiftly eject attackers from their environments. Customers can already leverage telemetry from Microsoft Security Graph API, Office365 Audit and Cloud App Security, Azure Activity and Flow, AWS Security Hub, and Google Cloud Platforms to accelerate threat detection and response, and we have a strong 2023 roadmap to match the integrations offered by the Sophos Managed Detection and Response (MDR) service.
- Aggressive classification (security posture adjustment) allows admins to select a more aggressive detection threshold for alerting when they suspect an active adversary is present.
- Alert-only mode gives admins a greater choice over whether to automatically stop-and-prevent vs. allow-and-alert, based on the customer’s unique risk tolerance.
- On-device behavior analytics for suspicious process activity extends existing heuristic and ML model-based detections to leverage an on-device behavior engine. This level of analytics is run on the endpoint instead of in the cloud to ensure that devices are secure even when offline or unable to send data to the data lake.
- Document access activity tracking that can be used for threat hunting and investigations when suspicious files have been in your environment.
Check out Sophos Intercept X with XDR for yourself at Sophos.com/XDR and see why it’s the number one XDR solution rated by G2 customers.
Source: Sophos
The manufacturing sector is witnessing the “Industry 4.0” era: smart factories equipped with industrial IoT devices, robotics, and advanced analytics to revolutionize manufacturing operations.
But rapid digitalization, lack of cybersecurity standards to match the growth, IT/OT convergence, and the sector’s low tolerance for operational downtime are increasing its attack surface. Manufacturers are looking to find solutions to risks such as vulnerability exploitation, data spillage, and production sabotage that plague the industry today.
It’s not surprising that cybersecurity challenges for manufacturers are growing in volume and complexity: 55% of manufacturing organizations were hit by ransomware in 2021 – a 52% increase from 2020. 61% of manufacturers reported an increase in attack volume, 66% reported an increase in attack complexity, and 51% reported an increase in the impact of attacks.
Manufacturing’s evolving threat landscape
In addition to the growing professionalism and evolving tactics, techniques, and procedures employed by criminal groups, there are a few other factors that are pushing forward the cybersecurity challenge in this sector:
- Manufacturers need to secure access to their critical industrial control systems and data
- Phishing scams – more specifically spear-phishing attacks – are easy ways for attackers to gain access to manufacturing systems and valuable data
- Theft of intellectual property like product designs, formulas, process patents, and other unique know-how of a manufacturing organization by cybercriminals, competitors, and ex-employees
- Risk of insiders who have authorized access to proprietary data or controls to critical manufacturing operations, misusing their privileges to steal trade secrets, sabotage manufacturing processes, or damaging equipment via remote access
- Manufacturers rely on a vast and complex supply chain network that is vulnerable to cyber attacks
- Manufacturers need to protect their legacy or unpatched manufacturing control systems and processes
- Cybercriminals are targeting the cloud to exploit less established cybersecurity practices than in traditional on-premises environments
Sophos can help
Download our Cybersecurity Guide for Manufacturing Industry to learn how Sophos can help address the most common cybersecurity challenges facing the manufacturing sector.
Sophos MDR is our fully-managed, 24/7 service delivered by experts who specialize in detecting and responding to sophisticated cyberattacks that technology solutions alone cannot prevent. As the world’s most trusted MDR provider and with many hundreds of manufacturing sector customers, we have unparalleled depth and breadth of expertise when it comes to threats facing the manufacturing sector. Sophos MDR applies learnings from defending one manufacturing organization to all others in the sector, generating “community immunity” and elevating everyone’s defenses.
“With Sophos MDR we have reduced our threat response time dramatically.”
Tata BlueScope Steel
“Sophos MDR’s ability to remediate or remove threats in a swift manner and bring them to our attention frees us up to focus on high-value tasks.”
Tomago Aluminium
“Sophos releases the IT teams to undertake more proactive tasks instead of being drawn into managing security challenges.”
AG Barr
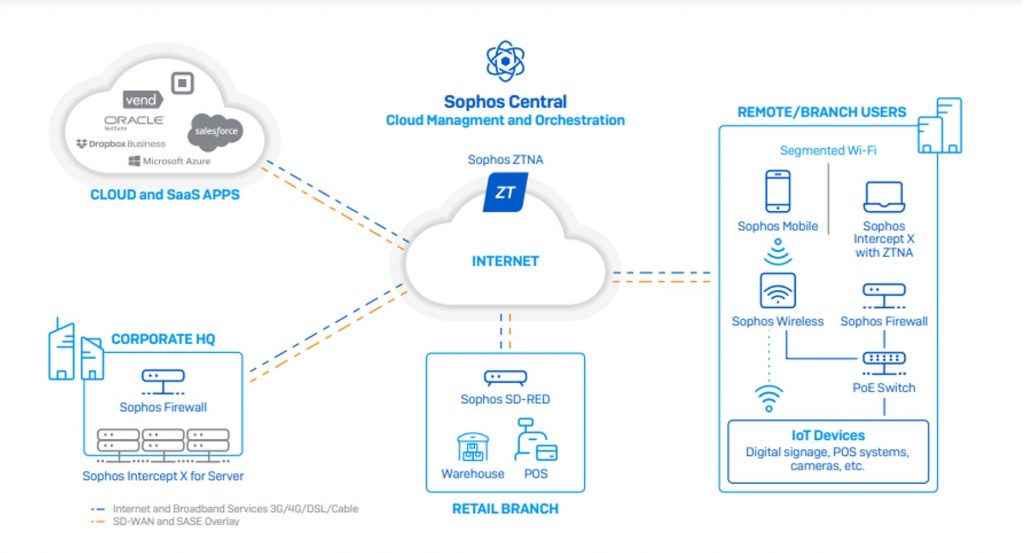
Sophos ZTNA eliminates vulnerable VPN clients, enabling you to offer secure and seamless access to resources for your remote users defined by policies. It removes implicit trust in your environment’s applications, users, and devices, allowing segmented access to your systems and resources to just those who need it.
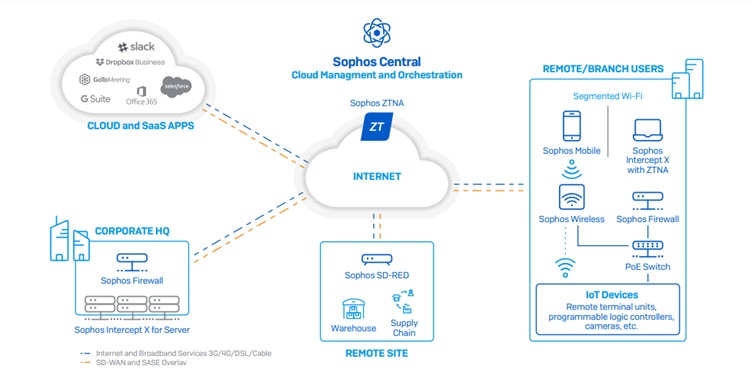
Sophos Secure Access Portfolio enables manufacturers to connect remote and branch sites, deliver critical cloud and SaaS applications such as Dropbox, Salesforce, and others, and share data and information between sites.
It includes:
- Sophos ZTNA to support secure access to applications
- Sophos SD-RED remote Ethernet devices to safely extend your network to branch locations and remote devices
- Sophos Wireless access points for easy and secure wireless networking
- Sophos Switch for secure access on the LAN
Everything is managed through a single cloud-based security platform, Sophos Central.
Speak with an expert
To learn more and discuss how Sophos can help you, contact your Sophos representative or request a call-back from our security specialists.
Source: Sophos
Less of a cyber security threat and closer to a scam, vishing refers to attempts to steal information or money over the phone by convincing the victim. These calls often use personal data acquired through previous cyber attacks to gain their victim’s trust.
This type of threat is definitely on the rise. Like many other hacks and scams, vishing is a popular attack type because it is simple to carry out, scales well and is often successful. It also requires very low technological investment and requires virtually no real coding knowledge beyond basic information that can be found online.
According to a recent Truecaller survey, 26% of Americans lost money due to a phone scam in 2022. This number shows that this type of attack is on the rise and that people are largely undereducated about them.
The most common type of vishing is impersonating an authority figure such as a government official, client, or coworker. The scammer’s goal is to obtain sensitive information such as a social security number. Still, these calls can become global threats if the victim is convinced to provide something with wider ramifications, such as a computer password.
In rare cases, the scammers will attempt to convince the employee to wire money or pay for a fake invoice to steal the company’s funds. No matter the goal or method used by the scammer, the only way to foil these attacks is through proper user awareness programs.
This article will look at seven common examples of vishing and explain them thoroughly so your users don’t fall into the trap.
1. AI-Based Vishing
AI is starting to become a tool to carry out wicked agendas, and we’re seeing it play out in social engineering scams like Vishing. AI works by detecting patterns and producing iterations of them without the need for constant human input—which means that it can automatically deploy processes once it has detected a pattern in its algorithm.
There is AI software now that can mimic a person’s voice, easily fooling employees into thinking that they’re speaking to their superiors or managers. In fact, in 2021, a large-scale cyber attack was carried out through voice cloning.
The attacker used AI to mimic the company director’s voice, convincing a bank manager through a phone call to transfer $35 million as part of the bank’s acquisition process.
This incident is one of the firsts that directly links AI to cyber threats, using deep voice technology to clone an executive’s speech, voice, and melodies to carry out a cyber attack. With voice patterns readily available from social media, YouTube, interview recordings, etc., AI poses a significant threat to all organizations.
2. Robocall
These attacks feed a prerecorded call to every phone number in a specific area code through computer software. The automated voice asks the victim to state their name and other information. The answers are recorded and used to steal money or open fraudulent credit cards.
Thankfully, these calls are becoming so common that most people know them and hang up when they receive them. Another telltale sign of these attacks is international or blocked numbers since the scammers have to cycle numbers to keep authorities off their trail regularly.
3. VoIP
While VoIP is a great technology that has allowed fantastic business innovations, scammers can easily create fake numbers to carry out attacks. This technique can be combined with a robocall but is often carried out by human callers.
The best way to thwart these calls is by asking for more information to be sent via email, where attacks are easier to detect, or by asking to carry out the rest of the call in person since the attacker won’t be able to do it.
4. Caller ID Spoofing
This attack can be especially pernicious because it uses software to fake a legitimate caller ID. Scammers will usually try to pass for an institution such as a tax agency, police department, or hospital to create urgency and get the victim to surrender information they usually wouldn’t.
These attacks are hard to spot, and the best way to evade them is the same as with VoIP by taking the call to another medium. Certain phones and physical security measures can detect these fake caller IDs and automatically reject them.
5. Dumpster Diving
As the name says, these attacks are carried out using information gathered through a business’ trash. Official company documents often contain enough personal data to launch a successful vishing attack.
The best way to counter dumpster diving is simple. Every company should shred all sensitive company documents before throwing them out. Whether using an external company or buying shredders for the office, it’s a worthwhile investment considering the potential risks.
6. Tech Support Call
This attack is widespread in large companies where employees might not know or have met members of the tech support department. Scammers will pretend they need to do a computer update or repair and ask for the victim’s password to do it.
Education is key to beating these attacks. Frequently remind users that you will never ask them to divulge their password over the phone and that they shouldn’t do so under any circumstance.
7. Voicemail Scam
This attack is different and involves voice mail notifications. Many smartphones and apps send emails to their users to notify them of stored voicemails. These emails will contain a link to listen to a voicemail. These fraudulent emails will lead users to a website that downloads malware onto their devices.
This scam can be evaded by ensuring users are adequately trained to notice phishing emails. These emails often have spelling mistakes and improperly sized logos and aren’t sent from official domain names.
8. Client Call
Often done by finding old invoices via dumpster diving, scammers perpetrating these attacks will pretend to be your company’s client and ask for an invoice to be paid. They’ll rely on a sense of urgency to convince the victim to wire funds and steal company money.
This scam is an excellent example of why every company should have a two-person approval for any invoice payment or wires. That way, another person not involved in the attack has to review the process and can detect fraudulent attempts.
Education Is Key
Vishing is definitely on the rise. The best way to counter this scam is by ensuring your users know they exist so they can recognize them. Vishing simulations are just as simple as phishing simulations and should be a core part of your cyber security awareness training campaigns.
The best way to see if your organization is at risk will always be to run some tests and adjust your defenses accordingly. Hackers will always rely on mundane situations and scenarios that make people let their guard down.
Reminding users of how these situations unfold and the telltale signs to look for is the most effective course of action to prevent vishing attacks. Once people are well trained in this regard, the steps to avert vishing attacks are simple and have a high success rate.
These attacks are the same whether they target a person or an entire business. Training your staff about vishing protects their whole life, at the office and at home.
Source: Terranova
Sophos Firewall has been rated the #1 firewall solution by G2 users in their spring 2023 Reports. G2 distinctions and rankings are based on independent, verified customer reviews on G2.com, the world’s largest software marketplace and peer-review platform.
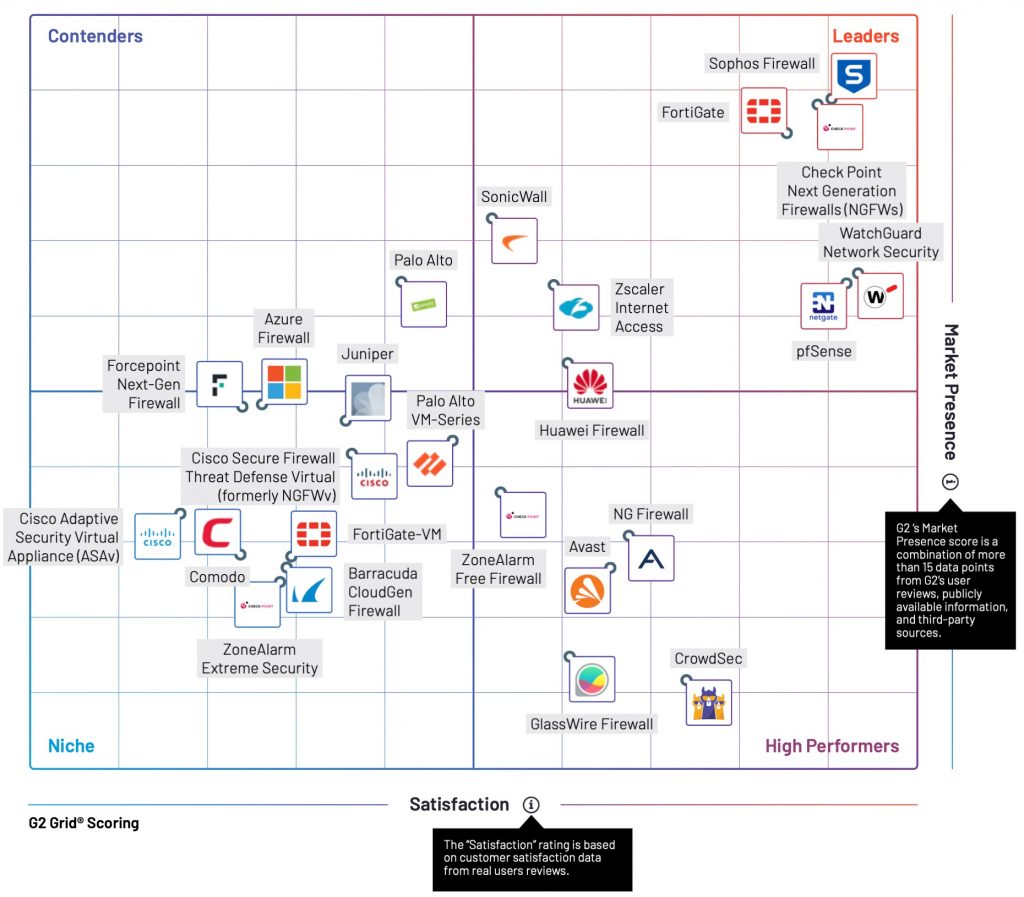
Sophos Firewall has been rated 4.6 out of 5 stars by IT professionals, topping the charts:
Here’s a small sampling of review headlines:
“Easy to use, highly functional, powerful firewall – great value”
“Network Security Made Simple with Sophos Firewall”
“Sophos: Firewall With Cutting edge Highlights And Functionalities”
“Leading AV and Firewall Protection Hands Down”
Check out the full reviews on G2.com and how Sophos was named a leader in several other categories including Endpoint, EDR, XDR and MDR.
These reviews are a great endorsement of our commitment to helping solve today’s top problems with securing modern networks. We do this by delivering a uniquely differentiated next-gen firewall that is extremely easy to deploy and use, offers the best value in the industry, and works alongside a complete portfolio of complimentary network security products – all managed from a single cloud console, Sophos Central.

Sophos Firewall and our Network Security portfolio has received a number of impressive and innovative updates in recent months that customers are raving about, including:
- New high-performance XGS 7500 and 8500 Models, setting a new benchmark in price-per-protected Mbps
- New 5G cellular connectivity modules for our XGS desktop appliance models with expansion bays
- New firmware releases for Sophos Firewall that bring added performance, full-featured SD-WAN capabilities, VPN optimizations, quality of life improvements, and much more
- ZTNA v2, which delivers ZTNA-as-a-service with cloud gateways and macOS support that makes connecting remote workers to networked applications easier and more secure than ever
Check out Sophos Firewall and our full ecosystem of Secure Access Products at Sophos.com/Firewall.
Source: Sophos
In the age of robots and artificial intelligence comes another player in the AI market: ChatGPT (Generative Pre-trained Transformer). Since its release, cyber security professionals have unlocked various opportunities with its features. Namely, it can answer prompts, write codes on demand, detect phishing emails, and crack passwords.
In a nutshell, ChatGPT can be an invaluable tool for security leaders. But who’s to say it can’t be used by cyber criminals for the other side of the same coin?
What is ChatGPT, and Why is it Important?
Launched by OpenAI in late 2022, ChatGPT aims to answer queries by pooling massive data from the internet to answer prompts. Its cyber security application is its ability to write different software languages and debug codes.
ChatGPT has grown in popularity, having recently launched ChatGPT Plus at $20/month. This pilot subscription plan is only available to users in the United States at the time of writing. The creators have initially launched ChatGPT in the U.S. under a research preview to hopefully gain insight into the tool’s strengths and limitations and improve it for widescale use.
While OpenAI says it has received millions of feedback and is in the process of making updates accordingly, cyber security experts are, as early as now, able to tell its implications in the industry—both good and bad.
With that, ChatGPT is setting the course to revolutionize how AI is utilized to further cyber security objectives and minimize threats. Although it still needs further research, it’s a promising tool for cyber security professionals.
The Pros and Cons of Using ChatGPT in Cyber Security
ChatGPT has a massive impact on the cyber security industry. This effect can be either good or bad, depending on how the technology is used and who uses it. While AI can be invaluable in detecting and stopping cyber attacks, there are also associated risks that cannot be ignored.
The Benefits of ChatGPT for Cyber Security Leaders
ChatGPT’s features are proving to be highly valuable for cyber security leaders, from improving their knowledge to helping them generate complicated code on demand.
Generating Code
ChatGPT makes it easier for cyber security professionals to generate code in any language, whether or not they have prior knowledge or experience. This makes it a very innovative platform that can advance a person’s understanding of cyber security, allowing them to ask follow-up questions to the AI or that complicated topics be simplified.
Better Decision-Making
Automation can help security professionals process and analyze large amounts of data in real time. This helps in improving decision-making abilities and enabling organizations to use their data more efficiently to make more informed business decisions.
The Cons of ChatGPT
…or the benefits of ChatGPT for cyber criminals.
Generating Malware Code
One of the biggest risks is ChatGPT being used to write malware code. While the company behind it has set up parameters to prevent this, many developers have put the security measures to the test. ChatGPT can detect and reject requests to write malware code.
However, cyber criminals can easily get around it by providing a detailed explanation of the steps to write the code instead of a direct prompt. ChatGPT will fail to identify this as a request to write malware and will effectively generate it.
Just by using different wordings and slight variations that do not pertain to malware, multiple scripts for complicated attack processes can be automated with ChatGPT. In effect, ChatGPT makes it easier for inexperienced attackers to keep up with the sophistication of cyber security measures.
With the use of AI and bypassing its security parameters, it can generate malware code to launch cyber attacks.
Creating Phishing Emails
Cyber criminals can also leverage ChatGPT to create phishing emails. They can ask it to generate a phishing prompt, although indirectly, to bypass the security measures and retrieve malicious code that can download reverse shells. These can potentially connect to a computer, allowing the attacker to access it and its files remotely.
Password Cracking
ChatGPT’s capacity to generate password candidates with speed and accuracy makes it more possible and even easier to identify passwords. If users don’t take the necessary precautions and protect their accounts from unauthorized access, ChatGPT can make it highly likely for attackers to identify their passwords and retrieve important data.
BEC
With ChatGPT, BEC detection can get more complicated. ChatGPT can potentially be used to generate new and unique content for every BEC attack, effectively bypassing detection tools. In the same way that ChatGPT makes writing phishing emails easier and faster, this technology may be used by attackers to carry out their agendas.
Is ChatGPT After Cyber Security Jobs?
There’s no doubt that ChatGPT can cut so much workload for cyber security professionals. But as of the moment, nothing can compare to human work—the latter is still more accurate and reliable than this AI technology.
More development is needed to improve the value and effectiveness of ChatGPT and similar technologies, especially in promoting cyber security.
Overall, however, ChatGPT can definitely find its positive footing in the industry. But in the wrong hands, it can also be used to carry out successful cyber attacks. Being that ChatGPT is still in its beta phase, we should expect better security parameters to prevent it from being used to negate cyber security efforts.
There have been quite a few controversies and bans involving ChatGPT since its release, some of which point to its negative cyber security implications. But OpenAI is adamant in saying its goal is to refine and expand its current ChatGPT offer based on user feedback and needs.
Source: Terranova
G2 just released their Spring 2023 Reports, and Sophos is the only cybersecurity provider named a Leader across the G2 Grid® Reports for Endpoint Protection Suites, Endpoint Detection and Response (EDR), Extended Detection and Response (XDR), Firewall Software and Managed Detection and Response (MDR). Additionally, G2 users also rated Sophos the #1 overall XDR and Firewall solutions.
Independent Sophos Customer Validation
G2 distinctions and rankings are based on independent, verified customer reviews on G2.com, the world’s largest software marketplace and peer-review platform. In G2’s Spring 2023 Reports, Sophos was a named an Overall Leader in five categories, as well as a Leader in 11 individual market segment Grids:
- Endpoint Protection Suites: Overall, Enterprise, Mid-Market, and Small Business Grids
- EDR: Overall, Enterprise, Mid-Market, and Small Business Grids
- XDR: Overall, Enterprise, and Mid-Market Grids
- Firewall: Overall, Mid-Market, and Small Business Grids
- MDR: Overall and Mid-Market Grids
We are honored that our services and products have been recognized by our customers and thank them for putting their trust in us.
Delivering Defense in Depth for Today’s Businesses
As adversaries have become more sophisticated and elusive, defenders should implement a defense-in-depth strategy that includes protection, detection, and response at every point along the attack chain to cover their entire environment. This layered approach should be inclusive of endpoint, network, email, and cloud security, as well as threat hunting and remediation services by security experts.
The fact that IT and security professionals recognize Sophos as the Leader across these key categories is validation that Sophos delivers the best and most comprehensive set of products and services required for modern day cybersecurity.
Uniquely, all Sophos customers are protected by Sophos X-Ops, a joint task force that brings together deep expertise across the attack environment from frontline threat hunters and incident responders to deep malware and AI specialists. Together they provide unparalleled insights into how threats are built, delivered, and operate in real time. Armed with this deep understanding, Sophos is able to build innovative, powerful, and effective defenses against even the most advanced threats.
Additional Sophos Customer and Analyst Validation
Alongside our G2 recognition, Sophos solutions are widely recognized by customers and the analyst community, including:
Sophos Endpoint
- Named a Leader in the 2022 Gartner® Magic Quadrant™ for Endpoint Protection Platforms for the 13th consecutive time
- Named a 2021 Gartner® Customers’ Choice™ for Endpoint Protection Platforms with a 4.8/5 customer rating on Gartner Peer Insights
Sophos Extended Detection and Response (XDR)
- Recognized as the #1 overall leader in the Omdia Universe for Comprehensive Extended Detection and Response (XDR)
Sophos Firewall
- Named a 2022 Gartner® Customers’ Choice™ for Network Firewalls with a 4.7/5 rating on Gartner Peer Insights
- Recognized as a Strong Performer on the Forrester Wave
Sophos Managed Detection and Response (MDR)
- Top rated and most reviewed vendor on Gartner® Peer Insights™ for Managed Detection and Response Services
- Top performer in the 2022 MITRE Engenuity ATT&CK Evaluation for Managed Services
Elevate your Cyber Defenses with Sophos
As the G2 ratings illustrate, Sophos provides unparalleled breadth and depth of protection. Our world-leading endpoint, network, email, cloud, and security operations solutions defend over 550,000 organizations from advanced cyberthreats, including ransomware.
Whether you’re looking to upgrade your firewall, enhance your endpoint defenses, streamline and accelerate your threat investigations, or add 24/7 human-led threat detection and response, we can help.
Our solutions are tremendous on their own – and even better together. Customers running both Sophos Intercept X Endpoint and Sophos Firewall consistently report that they are able to double the efficiency of their IT/cybersecurity team and realize a reduction of up to 85% in the number of security incidents that require investigation. With Sophos you can build a long-term security strategy with confidence. Wherever you start, and whatever your goals, Sophos can help you enjoy superior cybersecurity outcomes.
For more information on our services and products, speak to your Sophos partner or representative and visit our website.
Source: Sophos
Retail organizations routinely encounter a wide range of cyberattacks such as phishing, credential stuffing, ransomware, and supply chain attacks.
Many of these attacks are aimed at exfiltrating customers’ personal and financial information. In addition, attacks on point-of-sale (POS) systems are becoming popular. If attackers can gain entry into more critical systems like inventory and billing, it can cause operational disruptions.
Thanks to increased digitization and IoT integration, retailers’ potential attack surfaces have expaned as well. As such, the cybersecurity challenges for retailers continue to grow in volume and complexity.
In fact, 77% of retail organizations were hit by ransomware in 2021 – a massive 75% increase from 2020. More than half of retail organizations reported an increase in attack volume, complexity, and impact of cyberattacks on their organizations over the previous year. Read the full report here.
Retail’s evolving threat landscape
The growing professionalism of criminal groups and their evolving tactics, techniques, and procedures are significant drivers behind the complex retail threat landscape today. A few other factors are adding to the cybersecurity challenge in this sector as well:
- Phishing attacks trick customers and employees into giving attackers easy access to systems and payment data
- Attacks on unpatched POS systems hack transactional data and give unauthorized access to valuable information like credit card PINs
- Retail organizations rely on a vast network of third-party suppliers to keep their businesses and stocks moving, which adds complexity
- Retailers need to secure multiple devices, platforms, and customer-facing web and mobile apps to ensure positive customer experiences and operational efficiencies across distributed sites
- Business email compromise (BEC) scams are becoming commonplace in retail, where key executives are lured into divulging sensitive company information
- Retailers need to ensure compliance with regulations and standards such as PCI DSS, GDPR, HIPAA, and SOC2 due to the vast private and sensitive data they hold
- Cybercriminals are targeting the cloud to exploit less established cybersecurity practices than in traditional on-premises environments
Sophos can help
Download our Cybersecurity Guide for Retail to learn how Sophos can help address the most common cybersecurity challenges facing the retail sector.
Sophos MDR is our fully-managed, 24/7 service delivered by experts who specialize in detecting and responding to sophisticated cyberattacks that technology solutions alone cannot prevent. As the world’s most trusted MDR provider and with hundreds of retail customers, we have unparalleled depth and breadth of expertise when it comes to threats facing the retail sector. Sophos MDR applies learnings from defending one retail organization to all others in the sector, generating “community immunity” and elevating everyone’s defenses.
“Because Sophos MDR is there, we can prop up and mature other areas of the organization like vulnerability management, patching, and security awareness.”
– The Fresh Market, U.S.
“We appreciate that Sophos keeps on top of the latest activity and threats, so we can focus on delivering a secure, world-class service for customers and artists.”
– CD Baby, U.S.
Sophos ZTNA eliminates vulnerable VPN clients, enabling you to offer secure and seamless access to resources for your remote users. It removes implicit trust in your environment’s applications, users, and devices by providing policy-based, segmented access to your systems and resources to only those who need it.
Sophos Secure Access Portfolio enables retail organizations to connect remote and branch sites, deliver critical cloud and SaaS applications, and share data and information between sites.
It includes:
- Sophos ZTNA to support secure access to applications
- Sophos SD-RED remote Ethernet devices to safely extend your network to branch locations
- Sophos Wireless access points for easy and secure wireless networking
- Sophos Switch for secure access on the LAN
Everything is managed through a single cloud-based security platform, Sophos Central.
Speak with an expert
To learn more and discuss how Sophos can help you, contact your Sophos representative or request a call-back from our security specialists.
Source: Sophos
Over the last few weeks, there’s been a lot of coverage of OpenAI’s release of ChatGPT. The technology is piquing the interest of many for the innovative possibilities it brings to all sorts of communications, from answering questions to providing learning resources to troubleshooting tech issues. Unfortunately, many in the cybersecurity industry are concerned malicious actors will use this new tool for nefarious purposes, launching clever new ways to ensnare potential cybercrime victims.
Two Concerning ChatGPT Use Cases
One of these use cases is the ability for foreign threat actors to create legitimate-looking emails with proper grammar and spelling in languages they don’t speak. This makes phishing emails more challenging for recipients to identify since poorly-written messages are common clues that something is amiss.
Another dangerous ChatGPT scenario involves the creation of polymorphic malware. This is where the original malicious code mutates using techniques such as obfuscation and encryption but retains its functionality. This makes the malware more difficult to detect using traditional security controls.
How Did We Get Here?
The purpose of considering the cyberattack scenarios possible with ChatGPT is not to instill fear—there is already enough of that happening online. Rather, it’s important to take a step back and look at the history of the threat landscape and how it’s evolved to understand the current situation. Since the early days of computing and the internet, threat actors have always excelled at taking advantage of innovative technologies to develop new techniques for infiltrating networks and systems. This prompts the industry to innovate further by enhancing the available detection technologies or developing new detection techniques. It’s a constant game of cat and mouse.
Phishing and polymorphic malware have been around since the 1990s and have evolved over the past two decades. In that time, detection capabilities have changed alongside them to continuously get faster and more accurate. Some of these technologies include capabilities like heuristics, sandboxing, dynamic reputational scoring, and behavior analysis. Today, these are table stakes, but they were once groundbreaking new techniques created to address the emerging risks of their day.
How to Address the Challenges of ChatGPT
ChatGPT is expected to be the latest technique for threat actors, and vendors will continue to evolve their detection engines as well. Organizations should continue with their in-depth defense strategies and reliance on user awareness training programs, maintain a disciplined patch management program, and ensure they regularly test their defenses to uncover blind spots to harden those vectors.
Source: Fortra
In celebration of World Backup Day, we’re highlighting the best of backup with our partners who’ve done an outstanding job for their clients. These MSPs are a model for how to prepare your clients with the best backup and recovery strategies before an incident occurs.
These partners really stand out for their work in protecting their clients from downtime and data loss.
Most forward-thinking MSP: Ceeva
As SMBs transition to the cloud, they’re relying on the MSPs to ensure that their business continuity and disaster recovery (BCDR) coverage remains firmly in place. “Our customers tell us that minimizing downtime is the most important thing,” says Rick Topping, Vice President of Operations and Technology for Ceeva. “However, there are challenges for MSPs with the native Azure Backup system that Microsoft provides. The costs are not predictable and it doesn’t integrate with our existing systems, which makes it hard to know if you have a functioning backup.”
“Datto Continuity for Microsoft Azure is an ideal solution for Ceeva and our end customers,” says Topping. “We rely on Datto SIRIS for on-premises BCDR. When Datto launched DCMA we knew we’d be able to provide the same high performance that our customers expect.”
As SMBs continue gravitating toward the public cloud, Ceeva has the confidence that comes with a Datto solution made for the needs of MSPs. “Datto Continuity for Microsoft Azure gives us the reliability and trust we require for BCDR,” Topping concludes.
Best performance in a high-stakes situation: CMIT
“We got a call from the client at 9 am on a Saturday, letting us know they had been affected by ransomware,” said Linda Kuppersmith, the owner of CMIT Solutions Stamford & Hartford, “we were only responsible for backup and disaster for this particular client, so we did not get any ransomware alert.”
“We shortly discovered the backup was infected, that a backup failed at 4:20 am that Saturday.” Linda explained, “we further discovered 9/10 servers and 30/100 workstations were hit with ransomware.” The whole incident was catastrophic for the client freezing every transaction across the property, from restaurant services to checkout. Worse, it happened at one of the busiest times of the year.
The client “Was skeptical that recovery could be achieved without paying the considerable ransom since anything more than 2 days would be catastrophic for the business. We stated we were confident it would take nowhere near that time to virtualize good snapshots of the affected servers”, said Linda. The main database virtualized at 12:10 pm and finished virtualizing at 11:00 pm for a 1 TB oracle database service.”
We were able to get them virtualized and have the VPN connection from the cloud to the local LAN,” Linda continued, “Their systems were up and mostly operational just 10 hours later, with the resort being fully operational 13 hours after the backup failed.”
Achievement for going above and beyond: Total Communications
“When you start talking about backups, and then expand that into business continuity, they often say, ‘Wow! We haven’t really thought about this – how will we outfit our people when disaster strikes?’” says Scott Lennon, CEO of Total Communications. “Helping customers prepare is a major part of our offering.”
“Our goal is to be the right-fit technology partner by working with each client’s needs,” says Shawn Silver, COO of Total Communications. “We work to understand what they currently have for infrastructure and business continuity, then develop a plan that works within their budget. The goal is to be a whole-service client consultant.”
“We have a big footprint with Datto appliances – we’re currently overseeing more than 100 devices,” says Andrew Shmer, Computer Services Engineer for Total Communications. “SIRIS provides multiple recovery options in physical and virtual environments, for small and medium-sized businesses. Using SIRIS we can bring an organization back up and running within minutes when there’s an outage. Our customers are truly amazed by what SIRIS can do in those situations.
Source: Datto
[vc_row][vc_column][vc_column_text]
With the introduction of 5G to metropolises, public transportation companies, like Cyprus Public Transport, are aiming to modernize their transportation systems to support daily commuters. Other than enhancing the onboard experience, 5G technologies can better the monitoring and management of bus fleets.
Beginning operations not too long ago, Cyprus Public Transport now has a fleet of over 200 buses to serve everyday travels of Cypriots. In the start of 2022, they set in motion their plans to provide upgraded services, including Wi-Fi connectivity via 5G, for their buses.
The Challenge
 The main objective of Cyprus Public Transport’s plan was to provide fast mobile internet service for buses and bus stations. They knew this would be difficult to implement due to their large fleet. The network would require a centralized management system for the transportation company to easily manage all devices.
The main objective of Cyprus Public Transport’s plan was to provide fast mobile internet service for buses and bus stations. They knew this would be difficult to implement due to their large fleet. The network would require a centralized management system for the transportation company to easily manage all devices.
Additionally, Cyprus Public Transport wanted to use this network to generate a marketing platform to increase customer engagement. On top of ensuring reliable connectivity, they needed to design a network that can support this idea.
It is evident that the transport industry has entered a new era of progress with major advancements happening at a fast pace. The rollout of 5G in Cyprus Public Transport has the dynamics to accelerate these very beneficial changes lending today’s transport solutions more viable than ever.George Kouimintzis, Commercial Director of NSS
The Solution
 Cyprus Public Transport worked closely with COMIT Solutions and NSS Corp. to bring their plans to fruition, especially as this is an early adaptation of 5G technologies in Cyprus. For their fleet of over 200 buses, they deployed MAX Transit 5G routers to each vehicle. The MAX Transit 5G enables onboard Wi-Fi connectivity through its 5G connection.
Cyprus Public Transport worked closely with COMIT Solutions and NSS Corp. to bring their plans to fruition, especially as this is an early adaptation of 5G technologies in Cyprus. For their fleet of over 200 buses, they deployed MAX Transit 5G routers to each vehicle. The MAX Transit 5G enables onboard Wi-Fi connectivity through its 5G connection.
The MAX Transit 5G also comes with a customizable captive portal and supports external captive portals. InControl, Peplink’s cloud-based management platform was used to configure the 240 devices in buses.
It has been over a year since we have implemented a full fleet 5G project in Cyprus with great success. We are very happy with Peplink and their integration partner in Cyprus, COMIT Solution, they have assisted us in every step of the way from installation to rollout and ongoing support, their professionalism is reflected in the result.
The full fleet of the two cities Nicosia and Larnaca are in full use with a healthy consumption of data and going strong. It is notable to say this is the first implementation of a full fleet project in Europe. We are glad to be one of the first to bring fast Internet to public transportation making it more convenient for passengers. They now can work, enjoy music or video at very fast speeds on their commute to work.
Andreas Demetriades, IT Manager, CPT
The Result
 With the MAX Transit 5G in each bus, its simultaneous dual-band Wi-Fi reduces Wi-Fi congestion and interference, delivering reliable and uninterrupted internet to all passengers. The support for custom and external captive portals enables Cyprus Public Transport to connect to an advertising server and generate insightful reports on user demographics.
With the MAX Transit 5G in each bus, its simultaneous dual-band Wi-Fi reduces Wi-Fi congestion and interference, delivering reliable and uninterrupted internet to all passengers. The support for custom and external captive portals enables Cyprus Public Transport to connect to an advertising server and generate insightful reports on user demographics.
Pairing the MAX Transit 5G’s GPS capabilities with InControl makes fleet management possible, helping Cyprus Public Transport improve vehicle efficiencies. InControl itself eases deployment and management of devices across all buses for the transport company.
I use the bus daily to commute to work, the wifi service is really great, seems faster than my internet at home!“I feel more safe and secure using public transport knowing that I am always connected.”
“Knowing that our transport network works more efficiently, meaning better scheduling with less emissions, I feel great relief for the steps taken for the protection of the environment. I am proud to be part of it!”
Passengers of Cyprus Public Transport
Source: Peplink
[/vc_column_text][/vc_column][/vc_row]
Your Firewall is the heart of your network helping secure it from risks and threats. And while it’s a security product, and a critically important one, it also needs to be secured. This article outlines some of the best practices for hardening your Sophos Firewall.
1. Update The Firmware with Every Release
If you only take away one thing from this article, it’s this. And this recommendation doesn’t just apply to your firewall, but all of your networking infrastructure. Most Sophos Firewall OS firmware updates include important security fixes. The best way to harden your firewall is to ensure it’s running the latest firmware. For Sophos Firewall, we just released v19.5 MR1 which includes a number of great new features, a significant performance boost, and several fixes. You can always find the latest firmware release for your firewall simply by navigating to Backup and Firmware > Firmware (as shown below).

2. Enable Hotfixes
Occasionally, patches for vulnerabilities and other security fixes are released between regular firmware updates. This is done by applying hotfixes to your firewall automatically so its vitally important that this feature be enabled on your firewall. While it’s enabled by default, some customers have disabled this. If you are one of those, it’s highly recommended you go back and turn this feature on. This feature is found by navigating to Backup and Firmware > Firmware – check that “Allow automatic installation of hotfixes” is enabled (as highlighted at the bottom of the screen shot above).
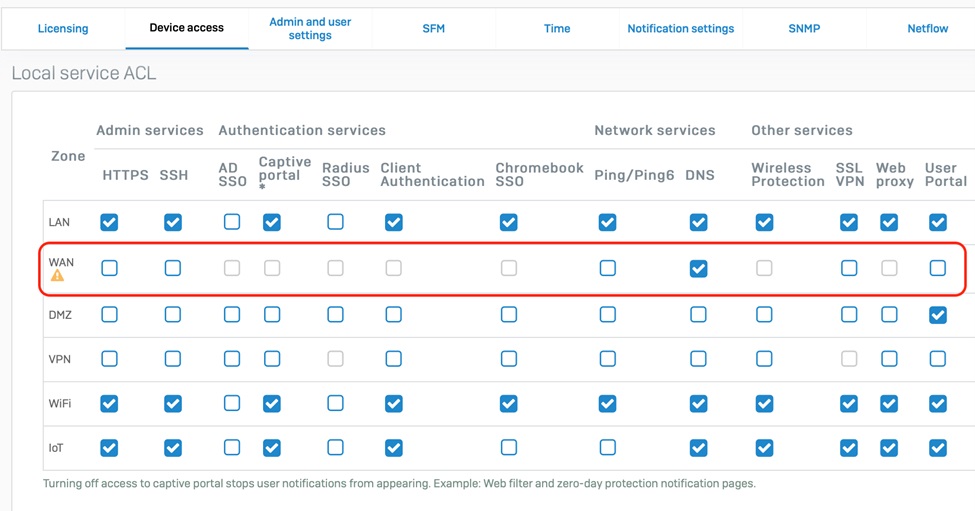
3. Limit Access to Firewall Services
Your Firewall offers a number of ways to limit access to services that are not required to reduce your exposure on the WAN. You should periodically check the device access settings and ensure that all unnecessary services are disabled (unchecked) on the WAN (see screen shot below). In particular, it’s strongly recommended that you disable remote admin via HTTPS and SSH, as well as the Captive Portal and User Portal on the WAN. Use Sophos Central, VPN or ZTNA to manage your firewall remotely. See the product documentation for instructions on how to manage device access.
4. Utilize Multi-Factor Authentication and Role-Based Administration
Enable multi-factor authentication (MFA) or one-time-passwords (OTP) and enforce strong passwords to protect your firewall from unauthorized access from stolen credentials or brute force hacking attempts. Sophos Firewall supports a rich set of MFA authentication options including new Azure AD single-sign-on authentication for webadmin access which can be super convenient (video / documentation).

You should also consider taking advantage of Sophos Firewall’s granular role-based administration profiles to limit access for administrators of the firewall. Provide read-only access to administrators that don’t absolutely need control over various firewall functions.
5. Additional Best Practices for Securing Your Network from Ransomware
While you’re looking at ways to better secure your network, I suggest you take a look at our recommended best-practices for securing your broader network from the latest ransomware and other advanced threats. If you’re a Sophos Firewall customer, you’re already well on your way to better protecting your network, but there may be other Sophos solutions you’re overlooking that can further help secure your organization.
Download the Guide to get the full set of best practices.
Source: Sophos
The cybersecurity challenges in the education sector continue to rise in volume and complexity. Educational institutions are a prime target for attack due to the vast amount of sensitive data they hold, from personal information on staff and students to valuable research data. Recently, the sector’s attack surface has increased, driven in-part by the growth in e-learning, accelerated use of collaborative apps, increased remote access, and the sheer number of devices and the diversity of operating systems on the network.
Illustrating the scale of the challenge, the frequency of ransomware attacks in education has increased considerably in recent years with 56% of lower education and 64% of higher education organizations reporting being hit by ransomware in 2021, up from 44% in 2020*. More broadly, almost half of education organizations reported an increase in the volume, complexity, and impact of cyberattacks on their organizations over the previous year. Read the full report here.
The education sector faces unique challenges
Evolving attacker tactics, techniques, and procedures (TTPs) and the growing professionalism of the cybercrime industry are significant drivers behind today’s complex threat landscape. A number of additional factors further compound the cybersecurity challenge facing the education sector:
- Students and staff need 24/7 access to online portals via a multitude of devices
- School districts and universities need to enable the secure exchange of personal data, digital teaching content, financial transactions, and more across different departments and sites
- The number of private and school-issued devices accessing the network continues to grow, as does the number of educational technologies and apps
- Encryption protocols used in collaboration and data sharing tools create blind spots for protection technologies, allowing cybercriminals to carry out malicious activities undetected, such as cloaking data exfiltration operations and hiding command-and-control traffic
- Schools need to ensure compliance with regulations and maintain student safety while using the internet
- Cybercriminals are actively attempting to exploit the use of cloud-based technologies as cybersecurity practices are less established than in traditional on-premises environments
Sophos can help
Download our Cybersecurity Guide for Educational Institutions whitepaper to learn how Sophos can help address the most common cybersecurity challenges facing the education sector.
Sophos MDR is our fully-managed, 24/7 service delivered by experts who specialize in detecting and responding to sophisticated cyberattacks that technology solutions alone cannot prevent. As the world’s most trusted MDR provider and with many hundreds of education sector customers, we have unparalleled depth and breadth of expertise when it comes to threats facing the education sector. Sophos MDR applies learnings from defending one education organization to all others in the sector, generating “community immunity” and elevating everyone’s defenses.
“The pen testers were shocked they couldn’t find a way in. That was the point we knew we could absolutely trust the Sophos service.”
University of South Queensland
“Since implementing Sophos, we’ve managed to free up significant operational hours that have allowed our teams to focus on initiatives that have increased our student satisfaction.”
London South Bank University
“The Sophos team acts as our goalkeepers, sitting behind us with their skill sets and giving us reassurance that they have our back.”
Inspire Education Group
Sophos ZTNA eliminates vulnerable VPN clients, enabling you to offer secure and seamless access to resources for your remote users defined by policies. It removes implicit trust in your environment’s applications, users, and devices, allowing segmented access to your systems and resources to just those who need it.
Sophos Secure Access Portfolio enables educational institutions to connect remote and branch sites, deliver critical cloud and SaaS applications such as Dropbox Education, G Suite, ClassDojo, etc., and share data and information between sites. It includes:
- Sophos ZTNA to support secure access to applications
- Sophos SD-RED remote Ethernet devices to safely extend your network to branch locations and remote devices
- Sophos Wireless access points for easy and secure wireless networking
- Sophos Switch for secure access on the LAN
Plus, to simplify management, everything is managed through a single cloud-based security platform, Sophos Central.

Speak with an expert
To learn more and discuss how Sophos can help you, contact your Sophos representative or request a call-back from our security specialists.
Source: Sophos
The traditional defenses against cybercriminals are no longer enough. Small and medium-sized businesses (SMBs) that are successfully exploited by attacks like ransomware can get hit hard. Here are some sobering cybersecurity statistics:
- 300% – the increase in reported cybercrimes since the arrival of Covid-19
- 92.7% – 2021 YoY increase in ransomware attacks
- 59% – the percentage of managed service providers (MSPs) who said that remote work has led to increased ransomware attacks
Even more troubling for MSPs: Their customers are right in the crosshairs of attackers who see SMBs as soft targets. More than 80% of ransomware victims were small businesses in Q4 2021. The impact of an attack can be dire, with 60% of small businesses experiencing a cyberattack subsequently going out of business.
Time is money for attacked organizations, who enter a race against the clock to eradicate the threat and return to normal operations. The average business interruption for SMBs is 20 days following a ransomware attack, at an average cost of $8,000 per hour of downtime until it’s fixed.
EDR: Safeguarding endpoints
These metrics are creating a sense of urgency for SMBs. They are looking to their managed service providers (MSPs) to help protect their endpoints, which now sprawl wider than ever due to the workforce increase in BYOD (bring your own devices) and mobile devices. While installing antivirus (AV) on each endpoint used to be sufficient, advanced endpoint threat detection and response (EDR) is now a must to better protect against costly attacks.
EDR’s additional safeguards are needed because MSPs today find themselves facing an asymmetrical battle: Hackers can attack at any time along any one vector. A threat actor only needs one open door to infiltrate systems – a vulnerability, human error, or advanced persistent threat (APT) can all provide entrée. Attacks can come from several different angles, including endpoints, email, cloud or over networks.
The advantage in this scenario goes to the attacker over their MSP counterpart, who must defend their customer everywhere against every technique, which could strike at any moment.
Cybersecurity frameworks such as NIST, ISO 27001, and COBIT provide MSPs with guidance and best practices to protect their clients’ data. While no single framework is “the best”, they are crucial for MSPs to establish strong policies and procedures, and a cybersecurity must-have.
Drilling down into these frameworks sheds important light on where AV and EDR differ, and why both are now necessary to defend SMB data. The NIST cybersecurity framework, for example, presents risk management for critical infrastructure as a set of interconnected steps: Identify, Protect, Detect, Respond and Recover.
Organizations today are spending 85% of their budget on the “protect” component. This leaves just a small portion to spend on the other four phases, but attitudes around this are changing. There is a growing awareness among MSPs, SMBs, and IT departments that they must shift how they invest in cybersecurity.
The rapid evolution of modern threats has given attackers new ways to bypass endpoint protection. Today’s attackers employ techniques such as:
- Living off the Land – Malicious programs aren’t needed by hackers who can dwell unseen under the surface, instead using common admin tools like the Windows Powershell Command Line Interface (CLI) to execute abnormal activities.
- Staged Malware & Attacks – Individually, each stage of an attack appears benign, but they are building up to a debilitating compromise.
- Disabling Endpoint Protection – Many attacks seek to disable AV and defensive tools before dropping their final stage, such as ransomware.
What’s the difference between AV and EDR?
Uses of these cyberattack techniques are gaining momentum. That’s why IT professionals today need both AV and EDR, working together, to defend endpoints – but what’s the difference between the two?
Antivirus software
Also known as anti-malware, antivirus (AV) is software used to prevent, detect and remove malware. Originally developed to detect and remove computer viruses, for many years AV was the primary source for defending networks against ransomware.
AV tools serve an important role in protecting endpoints from daily cyber threats – they provide the ability to detect and respond to malware on an infected computer. However, because they rely on signature detection or the ability of the software to detect “known threats”, sophisticated threat actors can bypass AV at will by using a variety of attack techniques that standard AV is unable to detect.
Additionally, antivirus software must be updated on a regular basis, if it is not up to date or a threat is not yet known, it will not be detected. This leaves many MSPs and their customers open to ransomware, fileless malware, credential harvesting, data loss and other cyber-attacks.
Endpoint threat detection and response (EDR)
Meanwhile, endpoint threat detection and response (EDR) is a layered, integrated endpoint security solution that monitors end-user devices continuously. EDR also collects endpoint data with a rule-based automated response.
An EDR platform records and remotely stores system-level behaviors of endpoints. Then it quickly analyzes these behaviors to detect suspicious activity and provide various response & remediation options.
EDR agents collect and analyze data from endpoints and respond to threats that have appeared to bypass existing antivirus (AV) protections and continues to analyze, detect, investigate, report and alert your security team of any potential threats even after.
How to choose the best EDR for MSPs
MSPs need EDR more than ever. However, the vast majority of EDR solutions are not made to fit their needs, and instead have been designed for enterprise use. These tools are often expensive, complex, and require a highly trained security team to manage them.
A big assist is arriving with advanced new solutions like Datto EDR, which was created especially for MSPs. Using Datto EDR, MSPs can improve their security posture while expanding the security offerings for the SMBs they protect. When selecting the best EDR for your MSP practice, you should ask the following questions:
- Is it easy to use and manage?
- Does it combat alert fatigue by enabling me to focus on the most important alerts?
- Can I quickly remediate problems that arise?
- How does it integrate with the other IT tools that I use, like RMM and managed SOC?
- Does it offer quality tech support?
- Is it cost-effective?
Other key features to evaluate in an EDR solution are its strengths in cyber-attack prevention, continuous monitoring and recording capabilities, rapid breach detection, automated response, and integrated threat defense.
Taken together, the right capabilities and feature set bring the cybersecurity advantage back to MSPs. Expertly informed alerts and response functions can guide your team through the remediation process with detailed recommendations, so you can address threats without needing a highly trained security team on staff.
Don’t stop at AV to protect client endpoints. The additional security of Datto EDR keeps MSPs and their customers ahead of advanced threats. Schedule a demo of Datto EDR.
Source: Datto
Cybersecurity has gained more importance in finance and banking for a few reasons. First, cyber threats are increasing in the volume and complexity. Second, the sector’s attack surface has grown thanks to digitization, the use of cloud apps, new fintech solutions, and other quality-of-life features for customers. As such, financial institutions now store large volumes of critically sensitive personally identifiable information (PII), corporate data, and financial information that must be carefully protected.
A 2022 Sophos survey of 444 IT professionals working in financial services revealed that 55% of organizations were hit by ransomware in 2021 – a 62% increase over the previous year. While 55% of organizations reported an increase in attack volume over the year before, 64% reported an increase in attack complexity and 55% reported an increase in the impact of attacks. Read t he full report here.
he full report here.
Factors contributing to rising cybersecurity risks in finance and banking
Evolving attacker tactics, techniques, and procedures as well as increasing professionalism in the cybercrime industry are significant drivers behind the sector’s complex threat landscape today.
There are a few others:
- Third-party vendors supporting the vital day-to-day operations of banks and financial institutions require remote access to critical resources, systems, and data. This increases the risk of misuse of access privileges, leading to credential and data theft.
- Anytime, easy access to critical business data on employees’ smartphones, tablets, and laptops threatens the security of sensitive financial and customer data.
- On-boarding new technologies and applications on the network, such as mobile banking, instant payment technology, e-signatures, digital signage, and videos introduces vulnerabilities into the system.
- The sector faces strict data security requirements by regulations and standards such as ISO/IEC 27001, GLBA, GDPR, SOX, and PCI DSS due to the vast private and sensitive data it holds.
- Local, state, and national branch sites share large amounts of sensitive information every day and also require continuous remote access to centrally located corporate resources and applications.
- The cloud is integral to the successful day-to-day operations of banks and financial institutions. But it has become a major target for cybercriminals looking to exploit less established cybersecurity practices than in traditional on-premises environments.
Sophos can help
To learn about how Sophos secures finance and banking organizations, download our Cybersecurity Guide for Finance and Banking whitepaper.
Sophos can help address the most common cybersecurity challenges facing finance and banking organizations:
Sophos MDR is our fully-managed, 24/7 service delivered by experts who specialize in detecting and responding to sophisticated cyberattacks that technology solutions alone cannot prevent. As the world’s most trusted MDR provider, we have unparalleled depth and breadth of expertise when it comes to threats facing the finance sector.
Leveraging extensive cross-product and cross-platform telemetry, we can generate “community immunity,” applying learnings from defending one finance and banking organization to all other customers in the sector, elevating everyone’s defenses.
“The IT team has saved at least 40 hours a week that would otherwise have been spent on security operations tasks.”
AAVAS Financiers Limited
“Sophos MDR helped us keep up with the growing volume and sophistication of cyberthreats without ramping up our security operations team.”
Tourism Finance Corporation of India Limited
Sophos ZTNA eliminates vulnerable VPN clients, enabling you to offer secure and seamless access to resources for your remote workers defined by policies. It removes implicit trust in your environment’s applications, users, and devices, allowing segmented access to your systems and resources to just those who need it.

Sophos Secure Access Portfolio enables financial institutions to connect remote and branch sites, deliver critical cloud and SaaS applications, and share data and information. It includes Sophos ZTNA to support secure access to applications, Sophos SD-RED remote Ethernet devices to safely extend your network to branch offices and remote devices, Sophos Wireless access points for easy and secure wireless networking, and Sophos Switch for secure access on the LAN. Everything is managed through a single cloud-based security platform, Sophos Central.
For more information and to discuss your requirements, contact your Sophos representative or request a call-back from our security specialists.
Source: Sophos
Businesses of all types are facing an increasingly challenging prospect when it comes to cybersecurity. Bad actors don’t discriminate, placing small and mid-sized businesses (SMBs) in just as much danger as large companies. Not only do SMBs offer threat actors a prime hunting ground for sensitive data and potential ransom payments, but many also serve as exploitable conduits into the networks of larger businesses as key components in the supply chain.
It’s critical that businesses of every size are ready for cybersecurity trouble. However, it can be a challenge to figure out how to prepare for it, especially for budget-conscious SMBs. Taking a look at the biggest cyberthreats that businesses face and affordable ways to take precautions against them can offer organizations insight into building the strongest possible defense for an organization.
Half of businesses will fall victim to a cyberattack or security breach
The cybersecurity climate for businesses has been steadily heating up. About half of the businesses that we surveyed for the Kaseya Security Insights Report 2022 told our researchers that they have been the victim of a successful cyberattack or security breach (49%). Digging deeper, one in five of our survey respondents said that their organization had experienced at least one successful cyberattack or security breach in the past 12 months. These alarming statistics illustrate the pressure that businesses and the IT professionals who secure them are under in today’s turbulent cybersecurity landscape, and that pressure won’t be letting up anytime soon.
“Businesses are facing a constantly escalating cyber threat level and they’ll continue to do so for the foreseeable future, with new groups of threat actors and more sophisticated attacks continuing to emerge,” says Jason Manar, Chief Information Security Officer (CISO) for Kaseya.
Prepare to face four major threats
SMBs face danger from a wide variety of cyber threats, but a few standouts are the most common. Phishing and email fraud, which includes cyberattacks like Business Email Compromise (BEC), is the top security threat to businesses today, with 55% of our survey respondents naming it as the biggest security challenge that their organizations face. Ransomware takes second place, the top threat for just under one-quarter (23%) of our survey respondents. Also on the list are password compromise (15%) and Account Takeover (6%).
Falling victim to any cyberattack can cost a business a fortune. The effects of a successful cyberattack on a business include lost revenue, reputation damage, downtime and wasted productivity, not to mention the high cost of mounting an incident response and recovery effort. About two-thirds of our survey respondents (63%) said that if their companies experienced a cyberattack like ransomware, while they would likely recover from the incident, they would likely lose data and incur expensive downtime. By taking a few smart steps, businesses can minimize the impact of a cyberattack or prevent one from landing altogether.
Every business needs an incident response plan
One of the top defensive tools that cybersecurity experts recommend for businesses is to create and test an incident response plan. U.S. National Institute of Standards and Technology (NIST) Special Publication 800-61 Rev. 2 Computer Security Incident Handling Guide is essential for anyone preparing an incident response plan. Incident response planning offers businesses another benefit too: it’s a valuable tool for preventing an incident from happening in the first place. Incident response planning gives businesses insight into where they might have security gaps or need better tools in their defensive buildout, reducing the chance that the company will experience an incident at all. Businesses should formalize a plan and run tabletop exercises to test their plan to ensure that they’ve covered everything.
“Knowing what to do and who to call in case of a cyberattack is the foundation of responding to that cyberattack quickly to limit the damage,” said Manar. “Without an incident response plan, the stress and pressure of the situation can lead to expensive mistakes.”
Get expert help detecting and mitigating threats
Cyber threats are constantly evolving and growing more complex as bad actors seek ways to get around cybersecurity safeguards. That makes them tricky for a company’s security team to detect. Accurate threat detection depends on solid threat intelligence and an expert eye to analyze it. A security operations center is often a necessary tool for handling these tasks. However, finding and hiring the experts that a business needs to form a security operations center (SOC) can be difficult and cost-prohibitive for SMBs. Managed SOC or Managed Detection and Response (MDR) is the solution to that dilemma.
Managed SOC offers businesses an easy and affordable way to put a team of security experts to work for them without expanding their payroll or building expensive infrastructure. Ideally, it should provide around-the-clock protection with real-time threat detection across three critical attack vectors: endpoint, network and cloud. Businesses gain access to a nerve center staffed by security pros that can hunt, triage, alert and work with their security team at critical moments, like when a threat is discovered or if they experience a cyberattack.
What can you do if the worst does happen?
In the United States, The U.S. Federal Bureau of Investigation (FBI) is the lead federal agency for investigating cyber attacks and intrusions. The Bureau has specially trained cyber squads in each of its 56 field offices that can help businesses handle a network intrusion, data breach or ransomware attack. A business experiencing one of those problems should contact their nearest FBI field office or report it at tips.fbi.gov. The FBI Internet Crime Complaint Center (IC3) provides businesses with advice on what to do if they fall victim to cybercrime or a cyberattack, including a breakdown of what information the FBI will request when tapped for help. Other federal agencies and many state governments and non-profits also offer assistance to businesses that fall victim to cybercrime.
“Don’t wait to call the authorities for help if your company is hit by a cyberattack – the sooner you start the process, the more you’ll benefit from the help they can give you to resolve the situation,” advises Manar, a former FBI Cyber Supervisory Special Agent.
Invest in affordable cybersecurity safeguards
In addition to incident response planning and partnering with a managed SOC, there are other budget-friendly safeguards a business can put in place to efficiently and effectively protect it from cyberattacks, including these tools:
Identity and Access Management (IAM) – Prevent intrusions via stolen, phished or compromised credentials by requiring proof of identity with IAM tools including two-factor authentication (2FA) or multifactor authentication (MFA). Microsoft says that that kind of technology alone can foil up to 99% of account-based cyberattacks.
Security Awareness Training – Transform employees from security liabilities into security assets with training that teaches them to identify cyber threats and handle data safely. Phishing simulations also help employees become savvy about spotting and avoiding cybercriminal traps.
Email Security – Investing in the best email security available is a smart decision since most of today’s nastiest cyberattacks like ransomware and BEC are email-based. Solutions that use AI and automation catch more threats than traditional email security or a Secure Email Gateway (SEG).
Backup and Recovery – Backing up a company’s data is a smart decision, especially in the ransomware era. Companies have several options to do it, like using an on-premises backup server. In today’s cloud-based world, cloud-based backup is the ideal choice for frictionless backup and easy recovery of a company’s data if needed.
Dark Web Monitoring – This defensive tool provides companies with 24/7/365 monitoring of business and personal credentials, including domains, IP addresses and email addresses, alerting the company’s IT team if any of that sensitive information appears in a dark web market, forum or data dump. This helps eliminate dark web risk exposure from password reuse, a common problem for businesses.
Endpoint Detection and Response (EDR) – EDR detects threats that evade other defenses so that you can quickly respond before damage is done. EDR relieves security team pressure with alerts that are mapped to the MITRE ATT&CK framework to provide context and helpful clarity reducing the security expertise required to effectively respond.
Get ready now for future cybersecurity challenges
Businesses should continue to expect to navigate a difficult security climate going forward. Recently, supply chain risk has become a major security concern, and that risk is escalating. More than half of the organizations that we surveyed (67%) told us that they conduct ongoing dark web monitoring for their suppliers’ domains as well as their own in order to combat supply chain risk. Smart organizations are also conducting frequent security awareness training to mitigate risks caused by phishing or employee behavior like mishandling data. Four-fifths of our survey respondents said that they regularly engage in security awareness training for all employees.
A strong commitment to cybersecurity is a foundational element of any modern company’s success, and it will only grow more important as the world continues its digital transformation. But mounting a solid defense against cyberattacks doesn’t have to break the bank. By taking sensible, affordable precautions like getting expert security advice, investing in quality security solutions and engaging in incident response planning, businesses can ensure that they’re ready for the cybersecurity challenges that they will experience today and tomorrow.
Source: Datto