News
A 2FA code, which stands for two-factor authentication code, is a form of Multi-Factor Authentication (MFA) that requires a generated code as an additional verification factor to a username and password. For example, when logging in to an account, instead of solely entering your credentials, you would also have to provide a second method of verification by entering a code from an authenticator app or one that is sent to your phone.
Continue reading to learn more about 2FA codes and how you can use them to protect your accounts.
How 2FA Codes Work
Before understanding how 2FA codes work, you first have to know the two types of 2FA codes. The first type is Time-based One-Time Passwords (TOTP) and the second is SMS-based One-Time Passwords (OTP).
TOTP codes are typically generated by authenticator apps that you can download on your phone. These codes regenerate every 30-60 seconds, so they’re different each time you use them. Some password managers also offer the option to generate and store TOTP codes so you don’t need a separate application. When using TOTP codes, it’s important to know that once the set time for them runs out, they expire, so you must always enter the most recent code that appears.
SMS OTP codes are sent to you via text message. You typically receive these text messages when you are attempting to log in to your account and have already entered your credentials correctly. To access your account, you’ll need to enter the code sent to you through text message to verify who you are.
Why Use 2FA Codes?
You should use 2FA codes to add an extra layer of security to your accounts and protect yourself in the event of a data breach.
Extra layer of security
2FA codes, like any other type of MFA, provide your accounts with an extra layer of security. In the case that someone were to guess your password or compromise it due to weak password practices, requiring a 2FA code would prevent them from being able to gain access to your account. This is because they don’t have the ability to see your 2FA codes – only you do.
It’s strongly recommended that you use more than two authentication factors for your accounts to add that critical extra layer of security.
Protects you in the event of a public data breach
Public data breaches are extremely common and often lead to customer data being leaked and published on the dark web. These breaches usually expose customers’ Personally Identifiable Information (PII) and login credentials. In the event that your credentials are involved in a public data breach, having a 2FA code on your account would prevent a threat actor from being able to successfully access it.
How Can I Get a 2FA Code?
There are different ways you can receive 2FA codes and some are more secure than others.
Authenticator apps
Authenticator apps are applications you download onto your phone. Google Authenticator and Microsoft Authenticator are two examples of authenticator apps. When using an authenticator app, you’ll first need to set it up with your account by scanning the Quick Response (QR) code that is given to you. Once it’s set up, every time you log in to that account, you’ll need to enter the 2FA code generated by the authenticator app. The 2FA code given to you is time-based so you’ll need to enter it before time runs out, which is usually 30-60 seconds.
SMS text messages
Another way you can get 2FA codes is by text message. This is the most popular way to receive 2FA codes since it’s the most convenient for users, but receiving 2FA codes this way is also the least secure. Security professionals strongly advise against using this method for receiving 2FA codes because they’re more vulnerable to being intercepted by a threat actor.
For example, if you were to become a victim of a SIM swapping attack, in which a threat actor swaps your SIM card to their phone, they would start receiving all your text messages and phone calls. This means they’d also be able to receive your 2FA codes that are sent through text message, which they can use to compromise your accounts.
Password managers
Certain password managers enable you to generate 2FA codes for your accounts. When you set up 2FA for an account in the same record you have your credentials stored, your 2FA code will autofill along with your credentials. In short, your 2FA codes and credentials will all be stored in the same place, meaning you don’t have to download different apps to access them. One password manager that provides users with the ability to generate and store 2FA codes is Keeper Password Manager.
How to Set Up Two-Factor Codes in Keeper
Keeper Password Manager is the password manager that offers the ability to generate and store 2FA codes in your password vault. Here’s how to set up 2FA codes when using Keeper:
- Log into your Keeper Vault.
- Locate the record for which you want to generate and store a 2FA code.
- Click on the record.
- In the record, click the edit button on the top right corner that looks like a pencil.
- Click where it says “Add Two-Factor Code.”
- From here, you’ll have the option to scan a QR code or enter the code given to you manually.
- Log into the account for which you want to set up a 2FA code.
- Find the option to enable two-factor authentication in your security settings (this will vary from account to account).
- If using Keeper on your phone, scan the QR code displayed during the setup process. If using Keeper on desktop, upload a screenshot of the QR code or manually enter the code provided.
Once you’ve set up the 2FA code in the associated record, your credentials and 2FA code will autofill when you log into your account. Having your 2FA code autofill not only saves you time but also ensures that you’re receiving your 2FA code securely since everything stored in your Keeper Vault is encrypted. Generating and storing your 2FA codes in Keeper takes away the risk of threat actors being able to intercept them.
If you don’t already have a password manager, you can start a free 30-day trial of Keeper Password Manager to see just how secure and convenient it is to store and generate your 2FA codes.
Source: Keeper Security
G2 just released their Fall 2023 Reports, and Sophos is the only cybersecurity provider named a Leader across the G2 Grid® Reports for Endpoint Protection Suites, Endpoint Detection and Response (EDR), Extended Detection and Response (XDR), Firewall Software and Managed Detection and Response (MDR). Additionally, G2 users also rated Sophos the #1 overall MDR and Firewall solutions.
Independent Sophos customer validation
G2 distinctions and rankings are based on independent, verified customer reviews on G2.com, the world’s largest software marketplace and peer-review platform. In G2’s Fall 2023 Reports, Sophos was a named an Overall Leader in five categories, as well as a Leader in 10 individual market segment Grids:
- Endpoint Protection Suites: Overall, Enterprise, Mid-Market, and Small Business Grids
- EDR: Overall, and Mid-Market Grids
- XDR: Overall and Mid-Market Grids
- Firewall: Overall, Enterprise, Mid-Market, and Small Business Grids
- MDR: Overall, Enterprise, and Mid-Market Grids
We are honored that our services and products have been recognized by our customers and thank them for putting their trust in us.
Delivering defense in depth for today’s businesses
As adversaries have become more sophisticated and elusive, defenders should implement a defense-in-depth strategy that includes protection, detection, and response at every point along the attack chain to cover their entire environment. This layered approach should be inclusive of endpoint, network, email, and cloud security, as well as threat hunting and remediation services by security experts.
The fact that IT and security professionals recognize Sophos as the Leader across these key categories is validation that Sophos delivers the best and most comprehensive set of products and services required for modern day cybersecurity.
Uniquely, all Sophos customers are protected by Sophos X-Ops, a joint task force that brings together deep expertise across the attack environment from frontline threat hunters and incident responders to deep malware and AI specialists. Together they provide unparalleled insights into how threats are built, delivered, and operate in real time. Armed with this deep understanding, Sophos is able to build innovative, powerful, and effective defenses against even the most advanced threats.
Additional Sophos customer and analyst validation
Alongside our G2 recognition, Sophos solutions are widely recognized by customers and the analyst community, including:
Sophos Endpoint
- Named a Leader in the 2022 Gartner® Magic Quadrant™ for Endpoint Protection Platforms for the 13th consecutive time
Sophos Extended Detection and Response (XDR)
- Recognized as the #1 overall leader in the Omdia Universe for Comprehensive Extended Detection and Response (XDR)
Sophos Firewall
- Named a 2022 Gartner® Customers’ Choice™ for Network Firewalls with a 4.7/5 rating on Gartner Peer Insights
- Recognized as a Strong Performer on the Forrester Wave
Sophos Managed Detection and Response (MDR)
- Named a 2023 Gartner® Customers’ Choice™ for Managed Detection and Response Services with a 4.8/5 rating on Gartner Peer Insights
- Top performer in the 2022 MITRE Engenuity ATT&CK Evaluation for Managed Services
Elevate your cyber defenses with Sophos
As the G2 ratings illustrate, Sophos provides unparalleled breadth and depth of protection. Our world-leading endpoint, network, email, cloud, and security operations solutions defend over 550,000 organizations from advanced cyberthreats, including ransomware.
Whether you’re looking to upgrade your firewall, enhance your endpoint defenses, streamline and accelerate your threat investigations, or add 24/7 human-led threat detection and response, we can help.
Our solutions are tremendous on their own – and even better together. Customers running both Sophos Intercept X Endpoint and Sophos Firewall consistently report that they are able to double the efficiency of their IT/cybersecurity team and realize a reduction of up to 85% in the number of security incidents that require investigation. With Sophos you can build a long-term security strategy with confidence. Wherever you start, and whatever your goals, Sophos can help you enjoy superior cybersecurity outcomes.
For more information on our services and products, speak to your Sophos partner or representative and visit our website.
Source: Sophos
Sophos Intercept X has been named a Customers’ Choice in the 2023 Gartner® Peer Insights™ Voice of the Customer report for Endpoint Protection Platforms.
Sophos earned a 4.8/5.0 rating in the report based on 451 verified reviews – no other vendor had a higher rating. Additionally, Sophos was recognized as the only Customers’ Choice vendor in the Education segment, and is also the only vendor named a Customers’ Choice across all industry segments in the report.
Access the full report here.
This latest recognition makes Sophos the only vendor to be named a Customers’ Choice in Endpoint Protection Platforms, Managed Detection and Response (MDR) Services, Network Firewalls, and Mobile Threat Defense in 2023 – a testament to Sophos’ ability to deliver a comprehensive, end-to-end cybersecurity platform protecting all facets of an organization.
Here are some examples of what customers had to say:
Prevent Breaches, Ransomware and Data Loss with Sophos Endpoint
Sophos Intercept X Endpoint works for you and with you, adapting your defenses in response to an attack. As threats increase in volume, complexity and impact, Sophos delivers better security outcomes for real-world organizations. To learn more, visit our website or speak to your Sophos partner or representative today.
Source: Sophos
In today’s digital world where organizations conduct the majority of their daily business and operations online, concerns about data privacy loom large. Customers are becoming more skeptical of how companies use their data, and governments and regulatory bodies are increasingly stepping in to regulate data collection. Consequently, the data privacy landscape is rapidly evolving, with industry and geographical data protection standards increasingly coming to the fore.
While the United States has the National Institute of Standards and Technology (NIST) Guide to Protecting the Confidentiality of Personally Identifiable Information, the European Union relies on the General Data Protection Regulation (GDPR) to protect personally identifiable information (PII) and consumer privacy. More region-wise laws and regulations, such as the California Consumer Privacy Act of 2018 (CCPA) and the California Privacy Rights Act of 2020 (CPRA), are also coming into effect every year. There are industry regulations as well, like the Health Insurance Portability and Accountability Act (HIPAA) for the health sector and the Payment Card Industry Data Security Standard (PCI DSS) for the finance sector, that make the regulatory world more convoluted.
As businesses strive to successfully navigate this ever-evolving, complex data protection regulation landscape, this presents a unique opportunity for managed service providers (MSPs). By providing data compliance services for businesses, MSPs can offer better value for their customers and generate a new and future-proof revenue stream. However, given the complexity and breadth of the regulatory compliance market, it’s not an easy ask.
MSPs often struggle to provide profitable data compliance services to customers due to various reasons, such as the high costs involved in implementing data compliance services, complexity of the compliance solutions and lack of skilled professionals. While these challenges restrict many MSPs from entering the compliance market, the MSPs that already offer compliance services often do so by thinning their margins or even operating at a loss. That’s where the integration of Datto Workplace with Compliance Manager GRC can be a game changer.
Secure collaboration solution meets simplified compliance management
Purpose-built for MSPs, Datto Workplace is one of the most secure and efficient enterprise file sync and share (EFSS) platform available in the market today. The platform enables users to access their files and collaborate securely from anywhere, on any device. By integrating with Compliance Manager GRC — a compliance management software — Datto Workplace now offers easy-to-use and robust data compliance features that can help MSPs create a new revenue stream or expand the margins on their existing data compliance services.
Users often store sensitive data in working files to achieve their productivity goals. By identifying, tagging and summarizing those PII data, Datto Workplace’s PII scan and summary feature prevents that data from getting leaked and empowers the business (your client) to stay compliant. Powered by Compliance Manager GRC, this feature automatically scans files and folders for sensitive data and PII, like Social Security numbers (SSN), U.S. driving licenses, birth dates and Automated Clearing House (ACH) numbers. It then flags and tags the files containing PII to bring heightened security awareness and provides a detailed PII summary report.
Notably, this unique automated feature of the platform also helps you to reduce your technicians’ workloads by up to 50% and eliminates the need for compliance-specific skill sets. For instance, another way to identify PII data in files and folders is by using Microsoft 365’s innate feature. However, it’s a manual and cumbersome process that requires up to 51 custom search queries to be created and maintained, which should then be followed by manual search results tracking.
Offer data compliance services at a healthy margin
MSPs can get this feature at a predictable, low cost. Datto Workplace and Compliance Manager GRC have flat-fee subscription models with no hidden or surprise costs to shock you. You get an immediate return on investment with larger margins without any CAPEX investment.
Datto is the world’s largest vendor of proven, reliable and secure BCDR solutions for MSPs. Go the Datto way, offer cost-efficient data compliance services to your clients and take your MSP game to the next level.
Source: Datto
Sophos Email has everything you’ve come to expect from a world-class email security solution.
It leverages the most advanced threat intelligence, behavioral analysis, machine learning, and reputation analytics to keep malicious email from ever reaching your users’ inboxes.
But it doesn’t stop there: state of the art language processing, display name analysis, look-a-like domain checks, and post-delivery protection put a stop to benign-looking messages that later turn out to be malicious.
Add to that an entire suite of data loss prevention and encryption tools, Microsoft 365 integration, powerful message handling features, and shared threat intelligence with other Sophos products that enables you to identify previously unseen indicators of compromise and remove suspicious files across environments.
It’s a core pillar of our portfolio that extends visibility across Microsoft 365, cloud server workloads, endpoints, the network and more.
But we’re not slowing down one bit. In fact, we’ve recently accelerated Sophos Email development to include a host of new features and technologies.
On-demand clawback
Sophos Email post-delivery protection automatically removes messages containing attachments and URLs that are benign at the time of delivery but later become active and malicious.
With on-demand clawback, administrators can now manually remove any message from users’ inboxes with the click of a button in the Sophos Central admin console. No more wading through Microsoft Exchange or security consoles and having to run PowerShell scripts.
This feature is available to all customers running Microsoft 365 with post-delivery protection enabled. It’s a great tool for removing messages that might not be malicious but that may contain sensitive or confidential information.
The next evolution of our clawback capabilities will be our API and alerting into the Managed Detection and Response (MDR) Console, which is due out this quarter and will provide our MDR analysts with the ability to remove threats and stop active malicious email campaigns directly from their consoles.
Mail flow rules (MFR) tamper protection
Also for Microsoft 365 customers is our new mail flow rules tamper protection. Changes to mail flow rules can inadvertently break mail flow. This new feature alerts customers and provides one-click resolution, restoration, and correction to configurations and mail flow.
Google directory sync
Using Google Workspace instead? We’ve added directory synchronization features that make it a snap to keep your Workspace users and mailboxes up to date inside the Sophos Central console. No need for manual configuration or roundabout synchronization with Microsoft Azure first.
Admin access to end-user lists
And that’s not all. We’ve added a new and highly-requested feature: admin access to end user allow and block lists, complete with import, export, and the ability to search, add, and delete entries directly from within the Sophos Central console. This feature was one of the top customer and field requests over the last 18 months and will reduce support tickets while enhancing the experience for both admins and end users.
And there’s more!
I’m from South Louisiana, so we call this “lagniappe” (a little extra).
We’ve also added new smart banners for plain-text messages and messages that might be unscannable due to key-signing, password protection, or encryption. And coming in the Q3 timeframe, we’re adding the ability to control which languages and countries of origin are allowed to deliver email to inboxes.
And that’s just the beginning. Check out Sophos.com/Email for further enhancements or reach out to your Sophos rep with any questions.
Source: Sophos
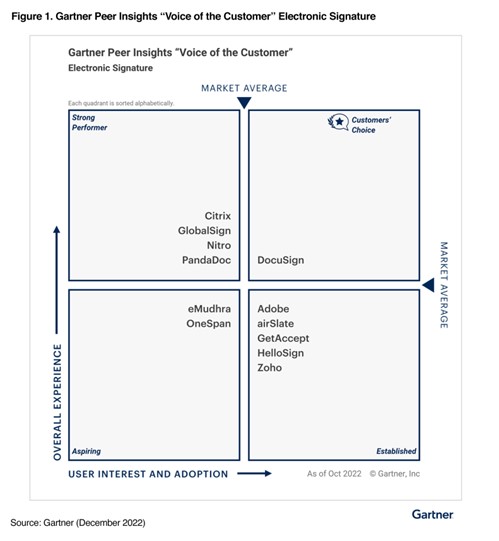
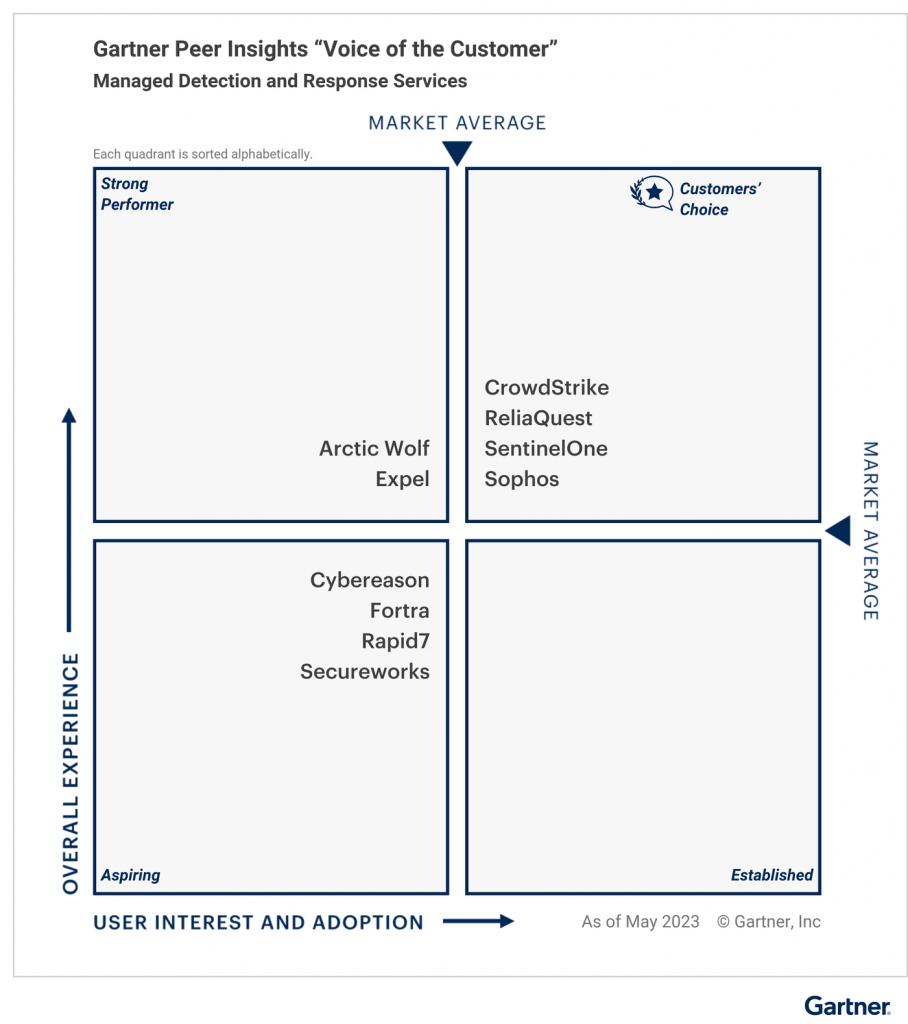
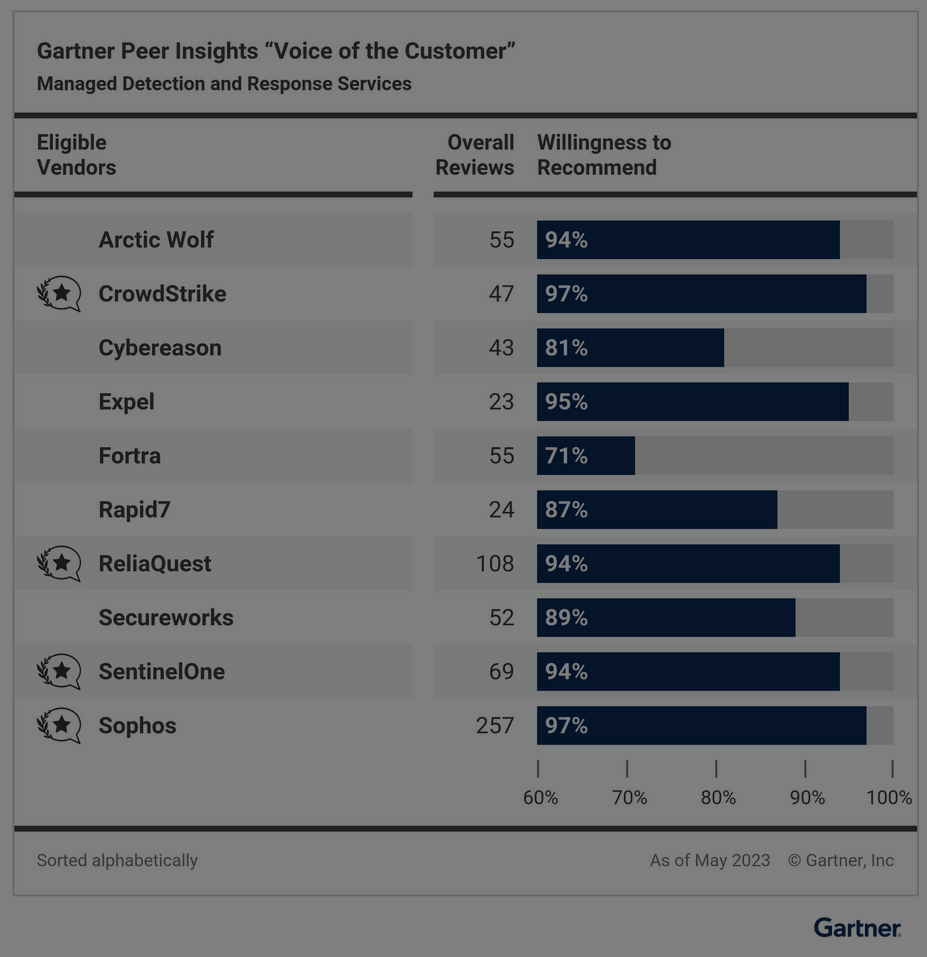
Sophos, a global leader in innovating and delivering cybersecurity as a service, today announced it has been named a Customers’ Choice for Managed Detection and Response (MDR) in the inaugural Gartner® Voice of the Customer Peer Insights™ report. Sophos received an overall customer rating of 4.8/5, based on 261 reviews, as of May 31 2023, with verified customer reviews praising the service.
The report highlights that Sophos was one of the vendors to receive the highest “Willingness to Recommend” score at 97%, and was also named Customers’ Choice for MDR in the Midsize Enterprise segment, which Gartner ranges between $50 million to $1 billion.
“Regardless of their size and target market, organizations are in the cross-hairs of cyberattackers and need constant 24/7 monitoring, threat detection and response as part of their cybersecurity strategy. The overwhelmingly positive response in the new Gartner Peer Insights report is, in our opinion, indiciative of the trust our customers have in us and the quality of our human-led threat detection and response expertise,” said Rob Harrison, vice president of product management at Sophos. “Our customers’ response also demonstrates the value of our MDR service’s unique ability to integrate and manage existing multi-vendor security environments in a range of markets, including larger, mid-market enterprises.”
Select Sophos MDR customer quotes from the report include:
- “Having Sophos support their own endpoint, firewall, and email security products with their own staff’s MDR service has taken our confidence in their critical responses to a new level,” said an IT manager in the manufacturing industry
- “Stop working so hard. Let Sophos MDR do it,” said a director of IT in the software industry
- “Knowing we have a team watching our organization 24/7/365 gives comfort,” said a manager of cybersecurity and government, risk and compliance in the manufacturing industry
Sophos MDR is the most widely used MDR offering with more than 17,000 customers across all industries, and is the most reviewed MDR solution on other Gartner Peer Insights and G2 reports. It is the only MDR service that can be delivered across end users’ existing third-party security deployments as well as Sophos offerings. Sophos recently launched Sophos MDR for Microsoft Defender, a fully-managed offering that provides the industry’s most robust threat response capabilities for organizations using Microsoft Security. The solution adds a critical layer of 24/7 protection across the Microsoft Security suite of endpoint, SIEM, identity, cloud, and other solutions to safeguard against data breaches, ransomware and other active adversary cyberattacks.
Vendors placed in the upper-right quadrant meet or exceed both the market average Overall Experience and the market average User Interest and Adoption.
A complimentary copy of the Gartner Peer Insights Voice of the Customer: MDR Services report is available for additional information.
Source: Sophos
There are many different types of phishing scams, but email remains the most common of them all. Responding to a sender, clicking on a link, or downloading a file that may not be trustworthy can lead to data corruption, leaked confidential information, and infected devices or networks.
Read the tips below or scroll down to view the full infographic.
Here is how to avoid becoming a phishing victim:
1.INSPECT THE SENDER’S EMAIL ADDRESS
Phishing involves using email addresses that contain suspicious elements to target victims, even sometimes spoofing a well-known site or brand. Be on the lookout for changed or added words or characters, as well as misspelled words within a domain name.
2.EXAMINE THE MESSAGE’S GREETING AND TONE
Be wary of emails that utilize a generic greeting and an urgent tone. Phishing emails target many people at once and implore the recipient to take immediate action, usually without a personalized opening line.
3.LOOK FOR VERIFIABLE SENDER CONTACT INFORMATION
Avoid responding to emails that don’t contain any return contact information for the sender, such as a phone number, email address, or office location.
4.DON’T SEND SENSITIVE INFORMATION VIA EMAIL
Even if the email has an urgent tone, never divulge confidential information in reply to an email. Cyber criminals leverage social engineering techniques to obtain personal data like names, addresses, banking information, and more that can be used for fraudulent activity.
5.AVOID CLICKING ON UNEXPECTED LINKS
Don’t click on links that come from unfamiliar email senders or organizations. You may be redirected to a website or start a download that can compromise your data or infect your device.
6.AVOID OPENING UNTRUSTWORTHY EMAIL ATTACHMENTS
Avoid opening email attachments from untrustworthy senders or simply to satisfy your curiosity. Suspicious attachments can be carriers of malware and ransomware payloads that can corrupt your data and harm your device.
7.INSTALL A PHISHING FILTER FOR YOUR EMAIL CLIENT
Ensure that you have a phishing filter that works with your desktop email software of choice. You can also install one for use in your browser. While it won’t keep out all phishing messages, it will greatly reduce the number of attempts that show up in your inbox.
95% of data breaches are due to human error.

Source: Fortra
Sophos has released The State of Ransomware in Education 2023, an insightful report based on a survey of 400 IT/cybersecurity professionals across 14 countries working in education. The findings reveal the real-world ransomware experiences of the sector.
Rate of attack and data encryption
The education sector reported the highest rates of ransomware attacks of all the industries surveyed. 80% of lower education providers and 79% of higher education providers reported that they were hit by ransomware in the 2023 survey, up from 56% and 64%, respectively, in our 2022 survey. The 2023 rates of attack are more than double than reported in our 2021 survey, when 44% of education providers experienced a ransomware attack.
Data encryption in the education sector has continued to rise: the rate in lower education has gone up from 72% to 81% year over year. Higher education reported a 73% rate of data encryption, similar to the 74% reported the year before.
18% of attacks in lower education were stopped before the data was encrypted, down from 22% the year prior. Encouragingly, higher education reported an increase in the rate of attacks stopped before data encryption, up from 22% in the 2022 report to 25% in the 2023 report.
Of the lower education organizations that had data encrypted, 27% said their data was also stolen. This figure reached 35% in higher education, suggesting that this “double dip” method (data encryption and data exfiltration) is becoming commonplace.
Root causes of attacks
Compromised credentials (36%) and exploited vulnerabilities (29%) were the top two most common root causes of the most significant ransomware attacks in lower education. Emails (malicious emails or phishing) were the starting points for nearly one-third of the attacks (30%), suggesting that the sector is highly exposed to email-based threats.
In higher education, exploited vulnerabilities (40%) were the most common root cause of ransomware attacks, followed by compromised credentials at 37%. Together, they account for over three-quarters of ransomware attacks (77%) in higher education. Email-based attacks (malicious email or phishing) are a less common root cause but still drive almost one in five ransomware incidents (19%).
Data recovery and the propensity to pay the ransom
All higher education and 99% of lower education organizations got their encrypted data back, higher than the 97% cross-sector average.
73% in lower education used backups for data recovery, while almost half (47%) paid the ransom. Higher education was among the bottom three sectors globally for backup use, with only two-thirds (63%) reporting the use of backups for data recovery. The sector also reported one of the highest rates of ransom payments for data recovery at 56%.
While the cross-sector recovery costs increased year over year, in lower education, they have remained level ($1.59M in the 2023 report vs. $1.58M the in 2022 report). In higher education, recovery costs have dropped considerably from the $1.42M reported in the 2022 survey to just over $1 million in the 2023 survey, suggesting that as ransomware rates increase, higher education organizations are getting better at recovering from attacks and are able to do so at a lower cost.
Read the full report here.
Mitigating the ransomware risk
Sophos recommends the following best practices to help defend against ransomware and other cyberattacks:
- Strengthen defensive shields, including:
- Security tools that defend against the most common attack vectors, including endpoint protection with strong anti-exploit capabilities to prevent exploitation of vulnerabilities, and Zero Trust Network Access (ZTNA) to thwart the abuse of compromised credentials
- Adaptive technologies that respond automatically to attacks, disrupting adversaries and buying defenders time to respond
- 24/7 threat detection, investigation and response, whether delivered in-house or by a specialist Managed Detection and Response (MDR) provider
- Optimize attack preparation, including making regular backups, practicing recovering data from backups and maintaining an up-to-date incident response plan
- Maintain good security hygiene, including timely patching and regularly reviewing security tool configurations
About the survey
Data for the State of Ransomware 2023 report comes from a vendor-agnostic survey of 3,000 cybersecurity/IT leaders conducted between January and March 2023, including 400 in the education sector: 200 from lower education (up to 18 years) and 200 from higher education (above 18 years) and including both public and private sector education providers. Respondents were based in 14 countries across the Americas, EMEA, and Asia Pacific. Organizations surveyed had between 100 and 5,000 employees, and revenue ranged from less than $10 million to more than $5 billion.
Source: Sophos
An elite team of incident response experts on standby to get you back to business quickly in the event of a breach.
With tangible ‘readiness’ now a key component for cyber resilience, I’m excited to announce the launch of the Sophos Incident Response Services Retainer. It provides all organizations (whether an existing Sophos customer or not) with speedy access to Sophos’ industry-first fixed-cost incident response service in the event of a breach.
The retainer also includes external vulnerability scanning and critical preparedness guidance, enabling organizations to proactively improve their security resilience by pinpointing and resolving issues that reduce the likelihood of a breach in the first place.
Every Minute Counts
The need for go-to incident response support that can activate immediately has never been higher, as revealed in the latest analysis of Active Adversary behavior by Sophos X-Ops:
- The median dwell time in ransomware attacks fell from nine days in 2022 to five in the first half of 2023
- Attackers take just 16 hours on average to reach Active Directory (AD)
- 90% of ransomware attacks occur outside standard weekday business hours
The Sophos retainer cuts red tape, allowing Sophos incident responders to quickly jump into active cyberattacks to investigate and remediate them, minimizing business impact.
The Importance of Preparedness
Planning and preparedness are complementary elements of an incident response strategy. Having a plan is essential, but you also need to be prepared to implement that plan at short notice – and as the research shows, more likely than not outside standard working hours. The Sophos Incident Response Services Retainer gives you on-demand access to a team of incident response experts that will rapidly stop active attacks and get you back to normal operations.
Reducing Cyber Risk for All Organizations
The Sophos Incident Response Services Retainer is available to non-Sophos organizations as well as customers already using Sophos’ endpoint, XDR, network, email, and other security products, or Sophos MDR Essentials. Endpoint configuration health checks and device audits are also included in the retainer for existing Sophos customers.
Organizations that prefer broader services in one package can purchase Sophos MDR Complete, which automatically includes full-scale incident response.
To learn more about this exciting new service, read the Service Brief and speak to your Sophos representative or partner.
Source: Sophos
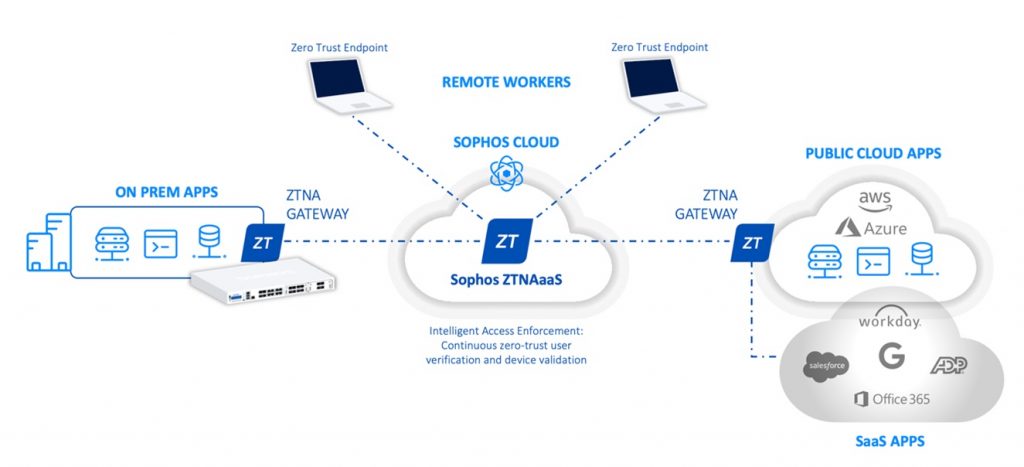
The Sophos Network Security Team is super pleased to announce a new product integration between Sophos ZTNA and Sophos Firewall.
With the recent release of SFOS v19.5 MR3 and an update today to Sophos Central, Sophos Firewall customers can now take advantage of the new integrated ZTNA gateway in their Sophos Firewall.
This integration makes ZTNA deployments easier than ever by not requiring a separate ZTNA gateway VM to be deployed in order to provide secure access to applications, systems, and data behind the firewall. Essentially, your Sophos Firewall now also serves double duty as a ZTNA gateway.
There are many benefits to this approach
- It reduces your hardware footprint and will ensure you do not have to invest in other platform licenses or hardware resources when deploying ZTNA
- It works everywhere a Sophos Firewall is deployed – head offices, branch offices, public cloud (Azure or AWS)
- Rapid deployment – in just a few minutes
- It works with firewalls in high availability (HA) mode for added resiliency and redundancy
- It enables easy remote management of your firewall via SSH or the Webadmin portal without exposing these to the WAN – greatly reducing your surface area of attack
- It’s free – there is no change in licensing and agent behavior: your ZTNA agents will work seamlessly across any of our gateway platforms – now including Sophos Firewalls
The early access program (EAP) will run from now until October 5th, 2023.
What you will need
- Sophos Firewall v19.5 MR3 (recently released)
- Sophos ZTNA term license account or a free trial (MSP Flex licensed customers can use this following GA in October)
- Role-based access control for both Firewalls and ZTNA
Getting started
Log into your Sophos Central Account to get started. Review the documentation and stop by the community forums to discuss the release. If you’re new to Sophos ZTNA, learn more at Sophos.com/ZTNA.
Source: Sophos
I’m proud to share that, for the fifth consecutive year, BeyondTrust has been recognized as a Leader in the Gartner® Magic Quadrant™ for Privileged Access Management! This year, BeyondTrust was recognized as one of only three PAM Leaders and was also positioned highest in Ability to Execute.
In our opinion, this Gartner® recognition validates BeyondTrust’s dynamic market adaptation, powerful product features, and the earned trust placed in us by a substantial and contented customer base. We believe receiving recognition for five years running as a PAM Leader in the Gartner® Magic Quadrant™ also reflects our commitment to innovation, deep understanding of evolving market needs, and relentless dedication to our customers.
Gain complimentary access to the report and read it for yourself anytime here.
Read on for our view on key takeaways from the 2023 PAM MQ™.
Our View: Key Takeaways from the 2023 Gartner® Magic Quadrant™ for Privileged Access Management
Gartner® Magic Quadrant™ research methodology provides a graphical competitive positioning of four types of technology providers in fast-growing markets: Leaders, Visionaries, Niche Players and Challengers. As companion research, Gartner Critical Capabilities notes provide deeper insight into the capability and suitability of providers’ IT products and services based on specific or customized use cases.
The BeyondTrust Platform addresses both established and transformational identity and security trends included in this year’s report.
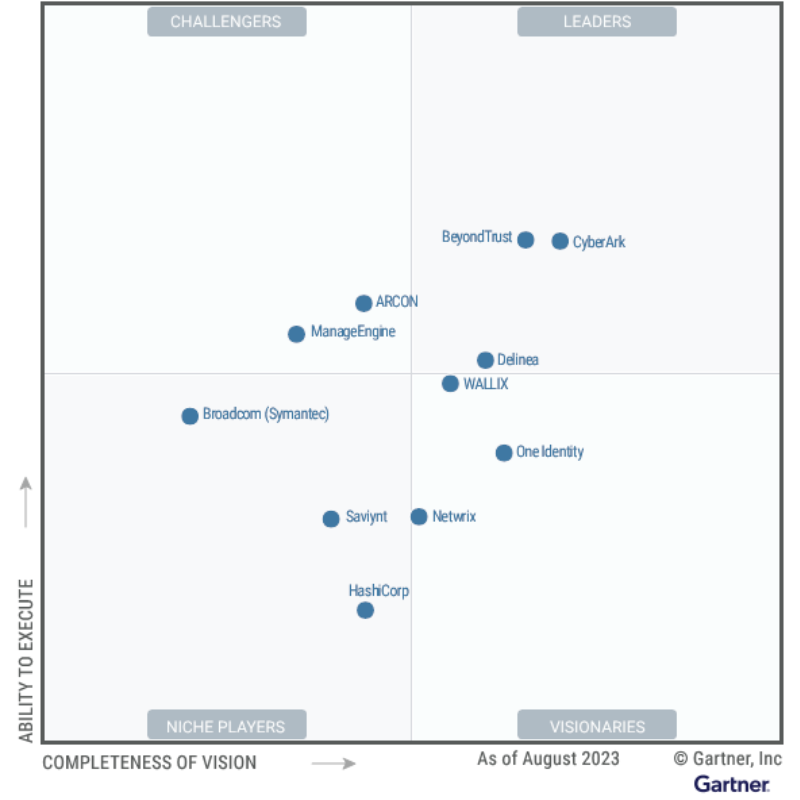
The 2023 Magic QuadrantTM for Privileged Access Management (PAM) has witnessed significant evolution, in part due to the growing involvement of cybersecurity insurers. These insurers are encouraging organizations to implement robust PAM strategies as a prerequisite for insurance coverage, thereby accelerating first-time PAM purchases.
Another notable trend is the rising interest in remote PAM use cases, spurred by the global shift to remote work and the outsourcing of core IT services. PAM solutions are broadening their scope to include remote vendors, contractors, and DevOps initiatives. Vendors like BeyondTrust are leading the way with specialized tools for remote PAM.
Get the full report to read deeper about the view of Gartner on these topics.
Why BeyondTrust Stands Out in Identity Security
As we’re consuming the report, here are a few reflections, on my part, on why we are a consistent Leader year over year.
Pioneering Protection Against Identity Threats
The digital landscape has grown increasingly intricate, due to factors like remote work and cloud adoption, making identity protection more challenging than ever. A majority of penetration tests reveal vulnerabilities related to over-privileged cloud identities, and attackers are now using advanced technologies like AI for more potent threats.
Our Identity Security Insights solution addresses these modern challenges head-on by integrating with trusted identity providers and cloud services. Offering real-time threat analysis, it provides a unified view of identities, entitlements, and privileged access, while suggesting actionable security enhancements.
Meeting Emerging Needs in Remote Access
Remote access has emerged as a key area of interest, accelerated by global remote working trends and the COVID-19 pandemic. Organizations are scrutinizing how to securely manage access for remote vendors, contractors, and technicians. These solutions now often include zero-trust features, providing far more than just VPN access, and they extend to specialized needs like cloud infrastructure access.
BeyondTrust provides robust and mature Vendor Privileged Access Management (VPAM) and Cloud Infrastructure Access capabilities as integral features of our Privileged Remote Access solution. Our VPAM functionality allows secure, streamlined access for trusted vendors, effectively eliminating the need for vulnerable VPNs and shared credentials. On the cloud infrastructure front, we empower your cloud developers and DevOps teams with seamless yet secure connectivity, bolstered by robust authentication and comprehensive audit trails.
Our Customers
But what truly speaks volumes? It’s not just accolades, but the real-world impact we’ve had on our clients. With an impressive NPS score of +55 and a CSAT score exceeding 95%, it’s evident that our efforts align with customer satisfaction and excellence.
Our Leadership placement in the MQ™ follows BeyondTrust having been recognized as a “Customers’ Choice” for both Privileged Access Management (PAM) and for Remote Desktop Software by Gartner Peer Insights. We believe a common thread between the Gartner MQ™ and this distinction is our customers and the trust they place in us. We’re honored to work alongside visionary organizations that drive us to innovate faster to solve their hardest digital identity challenges.
Here are just a few recent customer stories that showcase how BeyondTrust helps organizations improve their identity security posture:
- Investec transitioned from a theoretical framework to practical Zero Trust
- ServiceNow enhanced system access and authorization security
- Norton Healthcare successfully achieved HIPAA Compliance with BeyondTrust
Looking Ahead
Though the Gartner® Magic Quadrant™ provides a thorough, expert-driven overview of the PAM vendor landscape, BeyondTrust’s dedication to innovation remains unwavering. Following the April 2023 cut-off date highlighted in the report, BeyondTrust has rolled out a series of notable product launches. Here are some more recent product enhancements:
- Privilege Management for Windows and Mac included Analytics v2 enhancements for intuitive data aggregation, Role-Based Access for APIs to ensure granular control over permissions, and DLL Control to easily block risky DLLs.
- Remote Support was updated to offer FIDO2/YubiKey support for passwordless authentication and API Cookbooks to streamline Jump Item management.
- Privileged Remote Access saw new features like FIDO2/YubiKey support for remote users, streamlined vendor onboarding via automation, and optimized Jump Clients for cloud assets.
- Password Safe received a major upgrade, including Terraform Integration for enhanced CI/CD workflows, an Azure DevOps Extension for secure secret retrieval, and OAuth 2.0 standard implementation for secure authentication. The update also included improved accessibility via the web portal and enhanced audit and compliance reporting capabilities.
Notably, we also expanded strategic Technology Alliance Program initiatives like ServiceNow integration for Password Safe and a partnership between BeyondTrust’s Privileged Remote Access and PingOne DaVinci for streamlined least privilege access management.
These innovations collectively underscore BeyondTrust’s commitment to providing comprehensive and secure solutions that address a range of user needs and regulatory compliance demands, enhancing both efficiency and security posture for organizations.
Thank you for an Incredible Year—More Awaits in 2024
2023 has been a monumental year for BeyondTrust. We released significant new solutions and saw incredible customer and community growth. There are many trends and capabilities to consider, but you don’t need to go it alone. We’re pleased to provide access to the 2023 Gartner® Magic Quadrant™ for Privileged Access Management to help you evaluate solutions against your unique objectives and requirements. Download your complimentary copy of the report.
Source: BeyondTrust
Regular rotation of passwords, keys and privileged credentials is a critical best practice that greatly reduces an organization’s risk of falling victim to cyberattacks. By limiting the lifespan of a password, organizations can reduce the amount of time during which a compromised password may be valid.
Password, key and credential rotation – a feature of Privileged Access Management (PAM) – enables organizations to reset privileged credentials on an automated schedule. However, traditional PAM tools are complex, expensive, difficult to deploy and difficult to use – and do not monitor and protect every user on every device from every location.
Keeper’s new password rotation feature enables organizations to easily update users’ privileged credentials on an automated schedule through an easy-to-use centralized PAM platform.
Join Beta Program
Keeper Security Privileged Access Management (PAM) Insight Report
Keeper Security and TrendCandy Research surveyed 400+ IT and security professionals to determine the common challenges companies face with their current Privileged Access Management (PAM) tools. Not only are significant components of traditional PAM solutions not being used, but many respondents admit to never fully deploying the solutions they paid for. Key findings:
- 87% of respondents said they would prefer a simplified version of PAM that is easy to deploy and easy to use.
- 68% of respondents said their current PAM solution has several features they don’t need.
- 84% said they want to streamline their PAM solution in 2023.
KeeperPAM is Revolutionizing Privileged Access Management (PAM)
With KeeperPAM, credential rotation is simple:
- No cumbersome installs
- No need to open firewalls
- No need to create certificates
- No need to make network changes
- No agents are required
- No need to open any external ports, the solution uses SSL to communicate with Keeper
- No command line tools or scripting needed
- On-demand and automated rotation with a flexible schedule
- Rotate on-premises and cloud credentials/records
- Flexible post-rotation actions
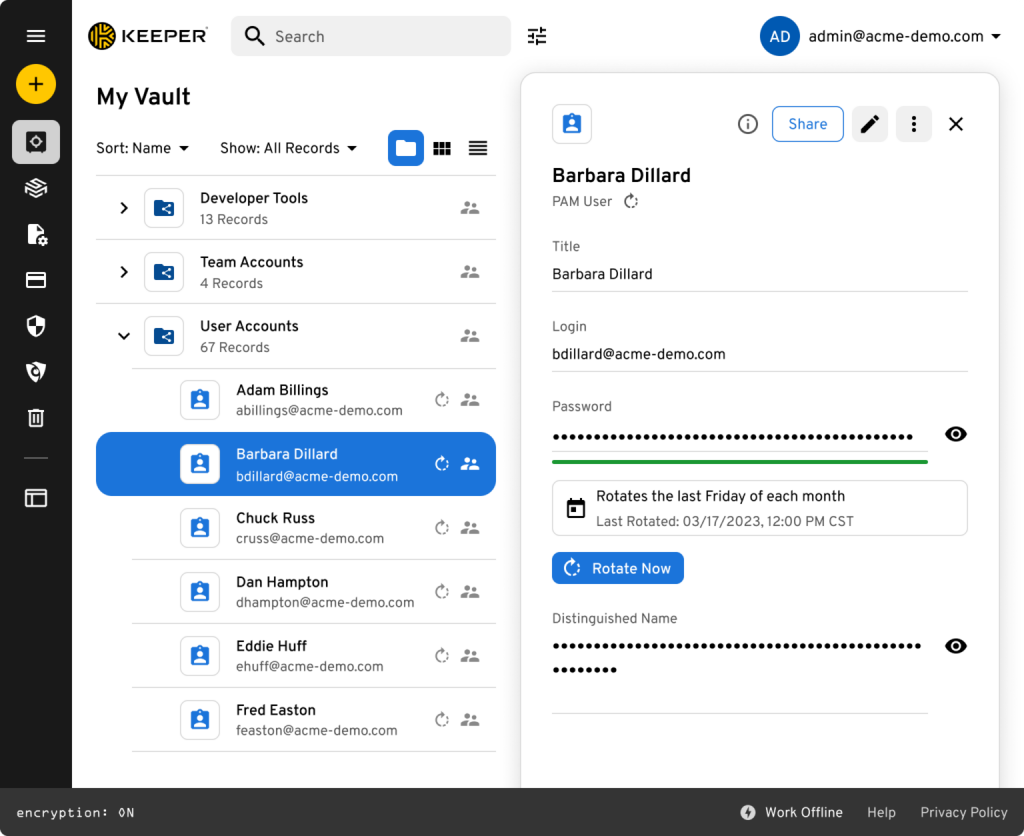
Keeper Security’s next-gen Privileged Access Management (PAM) platform – KeeperPAM – delivers enterprise-grade password, secrets and connection management in one unified solution. With Keeper’s password rotation feature, KeeperPAM enables organizations to automate the changing/resetting of system credentials like Active Directory (AD) user accounts, SSH keys, database passwords, AWS IAM accounts, Azure IAM accounts, Windows/Mac/Linux user accounts and more.
Credential-based attacks represent 82% of all data breaches (according to the 2022 Verizon Data Breach Investigations Report). By limiting the lifespan of a password, organizations can reduce the time that a compromised password may be valid.
Unlike traditional PAM solutions, the password rotation configuration in KeeperPAM is managed through the vault and admin console with a lightweight component on-premises to perform the rotation. KeeperPAM supports Keeper’s zero-knowledge, zero-trust architecture, which always encrypts and decrypts data at the local device level. Keeper never has access to the data in a user’s vault.
Password rotation through KeeperPAM is available on the Keeper Desktop App and Web Vault.
Password Rotation Features
- Automatically rotate credentials for machines, service accounts and user accounts across your infrastructure
- Schedule rotations to occur at any time or on demand
- Perform post-rotation actions such as restarting services, or running other applications as needed
- Secure storage of credentials in the Keeper vault
- Control and audit access to credentials
- Log all actions to Keeper’s Advanced Reporting and Alerts Module (ARAM)
- Create compliance reporting on shared privileged accounts
How KeeperPAM Password Rotation Works
Establish a Gateway
Keeper password rotation uses a lightweight and secure on-premises gateway service, which can be installed with a single command. The gateway creates an outbound connection to Keeper’s cloud security vault, establishing a secure tunnel for retrieving rotation requests.
The gateway then utilizes Keeper Secrets Manager (KSM) APIs to request and decrypt secrets for performing rotation and communicating with the target devices. Keeper’s password rotation ensures zero-knowledge security by performing all decryption locally on the gateway service.
Vault Configuration
Rotation is configured and managed entirely through the Keeper Web Vault or Desktop Application. Secrets, rotation schedules and network settings are all stored as encrypted records in Keeper’s cloud vault.
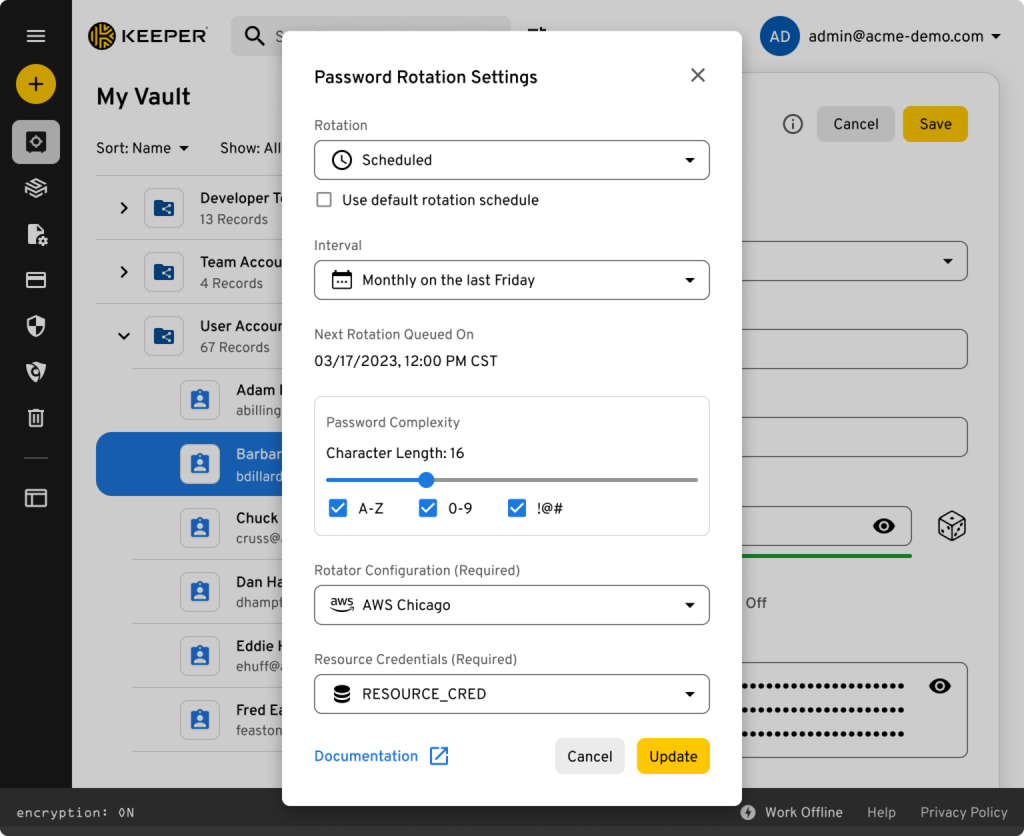
Rotation is easy to deploy and manage within a team. You can easily share access to records and manage which secrets are visible to the gateway using Keeper’s Shared Folders.
Source: Keeper Security
Business continuity, as defined by TechTarget, “is an organization’s ability to maintain critical business functions during a disaster.” There are many types of events that qualify as a disaster, including security breaches, natural disasters, supply chain disruptions and pandemics. Among these, an often overlooked critical event is the loss of internet connectivity.
For nearly all businesses, loss of internet connectivity means operations halt. For example, if the internet connection goes down, a retail organization cannot process payment cards. If a law firm loses internet connectivity, attorneys and paralegals cannot access critical online resources like Westlaw. Bottom line — business continuity is dependent on internet connectivity.
The National Institute of Standards and Technology (NIST) defines resilience to include “the ability to withstand and recover from deliberate attacks, accidents, or naturally occurring threats or incidents.” From a strategy and planning perspective, not only your IT systems but also your network needs to be resilient to function during and rapidly recover from major disruptions, which would include loss of internet connectivity.
This brings us to Datto and Datto’s commitment to business continuity and disaster recovery (BCDR). For years, Datto has been world-renowned for its BCDR and cybersecurity solutions — all designed to maintain business continuity. What’s often overlooked is Datto’s Networking solutions that also incorporate Datto’s vision of resilience and business continuity.
An example of this is the Datto Networking Appliance (DNA). Now available in Europe and Asia-Pacific, Datto DNA is an integrated, all-in-one secure router that features seamless and automatic failover to 4G cellular internet connectivity should the main internet connection go down. This ensures businesses can continue utilizing online services as if nothing disruptive happened at all.
The Datto DNA secure router adds firewalling (1.7 Gbps throughput), Layer 7 deep packet inspection, intrusion detection/prevention (IDS/IPS), web content filtering and more all into one desktop appliance. All of this gives businesses resilient, defense-in-depth security in one easy-to-use appliance.
As for routing, the Datto DNA features Layer 7 traffic management, hosted VoIP support, port aggregation, traffic shaping, support for up to eight VLANs and more, giving small businesses plenty of advanced routing features that optimize network traffic capacity while reducing network congestion and failure.
Integrated Wi-Fi provides fast and secure wireless LAN connectivity, eliminating the need to purchase additional wireless access points.
Cloud-based management, configuration, setup and ongoing management of the Datto DNA is handled via Datto Network Manager. With it, setting up a network can be done in minutes, not hours or days. Furthermore, new integrations with Datto Network Manager and Autotask allow you to manage alerts from Datto Network Manager and create Configuration Items (assets) for your networking devices in your Autotask database.
When your business absolutely, positively has to be connected online, you need resilient networking solutions that ensure business continuity. The Datto DNA secure router embodies this vision from Datto and is a perfect example of what resilient networking is all about. Your business runs on the internet, and if that connection fails, business stops. When it comes to internet connectivity, with Datto, failure is not an option.
Source: Datto
Skilled adversaries don’t break in. They log in.
Organizations that have invested in the Microsoft Security suite still need to protect against these advanced, human-led attacks that technology alone cannot prevent. However, the sheer volume of alerts generated by Microsoft security technologies, together with the complexity of the threat landscape and widespread shortage of in-house expertise and capacity, means that delivering effective security operations is an uphill task for most organizations:
- 71% of security teams struggle to determine which security alerts to investigate among the noise generated by their tools
- 52% of leaders say cyberthreats are now too advanced for their organization to deal with on their own, rising to 64% in small businesses
- The median threat response time is 16 hours, leaving attackers significant time to operate within the network
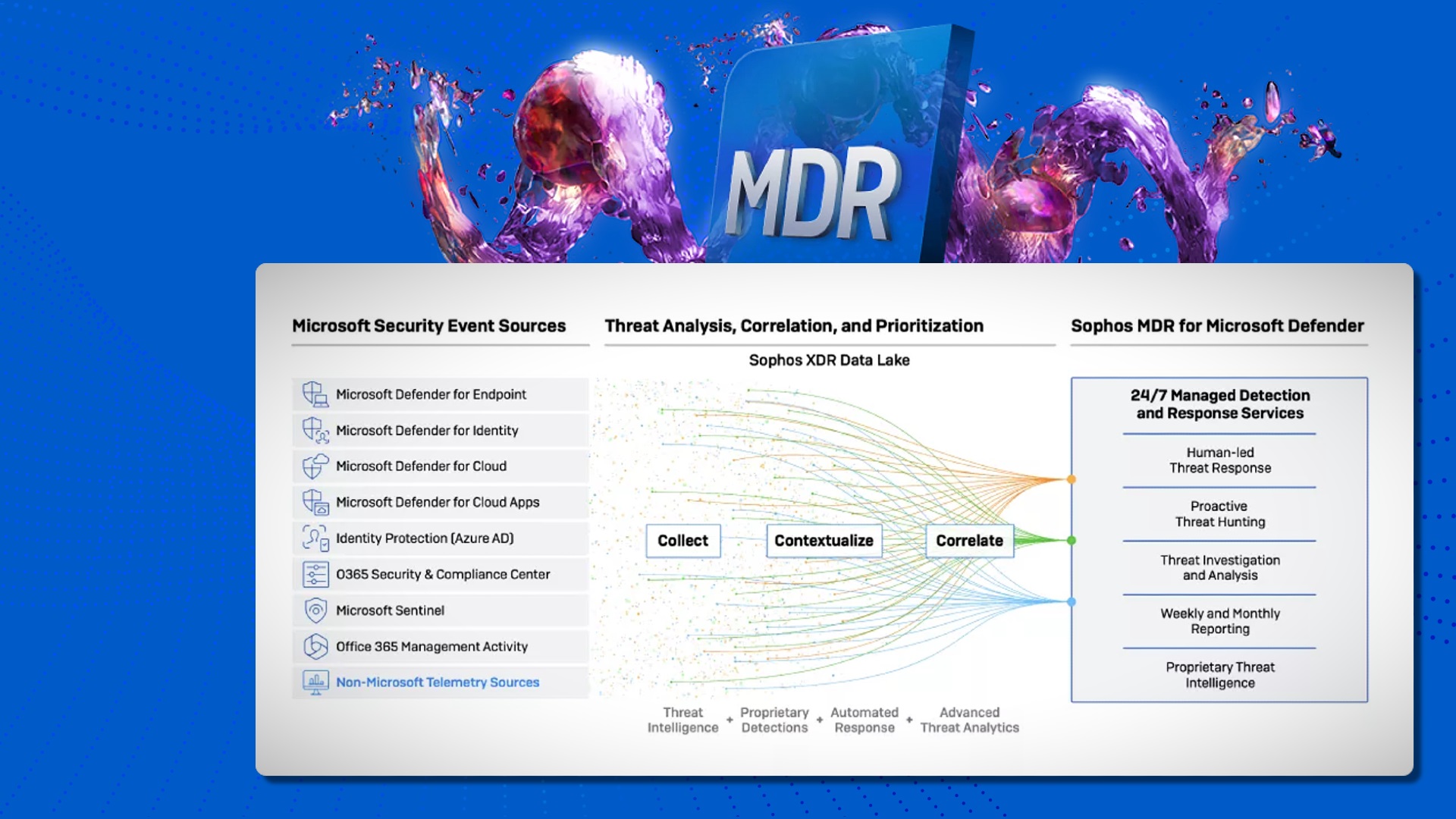
Introducing Sophos MDR for Microsoft Defender
Increasingly, organizations running Microsoft Defender are turning to specialist MDR providers such as Sophos to extend their cyber defenses. Given this pressing need, I am excited to announce the availability of Sophos MDR for Microsoft Defender. With this service, over 500 Sophos analysts monitor, investigate, and respond to Microsoft security alerts 24/7, taking immediate action to stop confirmed threats.
- Detect advanced threats using a wide range of Microsoft Security event sources together with proprietary Sophos detections and human-led threat hunts
- 24/7 expert-led threat response quickly stops attacks and terminates threats
- Integration with non-Microsoft security tools (Sophos or other providers) expands visibility and accelerates investigation response across the entire environment
With our experts taking care of security operations, organizations running Microsoft Defender can reduce cyber risk, increase the impact and efficiency of their existing security investments, and improve insurability.
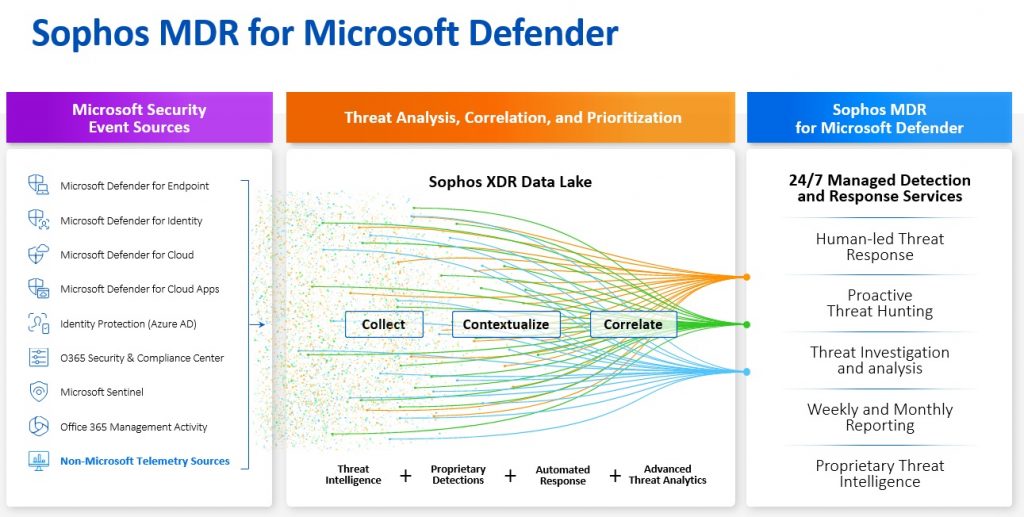
Unparalleled visibility that delivers accelerated detection and response
The more we see, the faster we act. Unlike other MDR offerings that limit support to Microsoft Defender for Endpoint or Microsoft Sentinel, Sophos MDR leverages signals from the full Microsoft Security suite, including:
- Microsoft Defender for Endpoint
- Microsoft Defender for Identity
- Microsoft Defender for Cloud
- Microsoft Defender for Cloud Apps
- Identity Protection (Azure Active Directory)
- MS O365 Security and Compliance Center
- Microsoft Azure Sentinel
- Office 365 Management Activity
Microsoft security solutions are only one part of a threat detection stack that typically includes firewalls, identity solutions, email security tools, NDR platforms, and public cloud security tools. Sophos MDR for Microsoft Defender provides a holistic approach to cybersecurity operations, integrating with almost any technology investment that generates security alerts – including tools from Microsoft, Sophos, and dozens of other providers.
By consolidating and correlating cross-product and cross-vendor telemetry in the Sophos XDR Data Lake, Sophos MDR increases the detection capability of our customers’ security stacks beyond the sum of the individual parts while also maximizing ROI on existing security investments.
Putting the R (Response) into MDR for Microsoft Defender
Identifying a threat is just part of the security operations process; unless you respond in a timely and effective manner, you remain fully exposed to attack. Yet all too often, third-party providers offer only minimal threat response capabilities in Microsoft Defender environments.
Sophos MDR for Microsoft Defender is different. It includes full threat response, containing threats to disrupt malicious activity. The non-exhaustive list of response actions that our analysts are capable of with Sophos MDR for Microsoft Defender includes:
- Terminating processes
- Disabling user accounts
- Forcing log off of user sessions
- Isolating host(s) utilizing Sophos Central
- Applying host-based firewall IP blocks
- Removing malicious artifacts
With Sophos MDR, you can relax knowing that we don’t just tell you about issues, we deal with them for you.
Future-proof your Microsoft defenses with the world’s most trusted MDR service
Testament to the superior outcomes our customers enjoy, Sophos MDR is the world’s most popular and most reviewed MDR solution, with a 4.8/5 rating on Gartner Peer Insights as of July 10, 2023, and a top rating on G2.
We secure more organizations than any other MDR provider, and this extensive experience across all industries and sectors enables us to provide unique “community immunity” to all our customers.
To learn more about Sophos MDR for Microsoft Defender and how it can support you, visit our website, read the service brief, or speak with a security expert today.
Source: Sophos
Today, companies all around the globe use Microsoft 365 cloud services and the advantages are self-evident. Companies no longer need to operate their own infrastructure to provide services on site. Programs and tools obtained simply via the cloud can be scaled easily and cost-effectively in line with user numbers. Especially when compared to a dedicated on-premises system, administration requires fewer IT resources. In addition, the service comes from a trusted, reliable provider. What’s more, whether you’re using Outlook as a mail client or Teams as a digital meeting room, all communication services are located on the same platform. By and large, Microsoft’s office software from the public cloud offers a wealth of communication and collaboration features at a reasonable price.
Nevertheless, companies are advised to install additional solutions for archiving and backing up emails in order to protect the business data they contain and keep this information available in the long term. Indeed, many companies are unaware that Microsoft 365 does not automatically archive and back up email data and, furthermore, that the archiving features built into Microsoft 365 do not offer the scope of services that can be expected from a professional third-party email archiving solution.
Reasons for Using a Professional Email Archiving Solution
 The primary objective of any email archiving solution is to store copies of all a company’s emails including file attachments over time in a form that is faithful to the original, quick to find, and permanently available. This enables a company to make optimum use of email as an information resource and reap the many benefits available. Among other things, a professional email archive helps prevent data loss, cut storage demands on the mail server, reduce the workload on an IT team, and comply with the statutory and regulatory requirements governing the retention of business-relevant documents.
The primary objective of any email archiving solution is to store copies of all a company’s emails including file attachments over time in a form that is faithful to the original, quick to find, and permanently available. This enables a company to make optimum use of email as an information resource and reap the many benefits available. Among other things, a professional email archive helps prevent data loss, cut storage demands on the mail server, reduce the workload on an IT team, and comply with the statutory and regulatory requirements governing the retention of business-relevant documents.
Summary of the Archiving Options Available in Microsoft 365
Microsoft offers several different options for securing emails depending on the plan chosen (Business Standard, Business Premium, Enterprise). Some of these features are provided free of charge as part of the basic Microsoft 365 package, while others are included only in the more expensive Enterprise plans. Below is a summary of the native archiving features in Microsoft 365:
- PST Archiving
Users can move emails to PST files and store them locally on their own computer or in the cloud.
- “Archive” Button in Outlook
The “Archive” button allows users to move emails to an archive folder. The emails remain in the Outlook mailbox; only the storage location of the emails change.
- Archive Mailbox Without Exchange Online Archiving
The archive mailbox is a separate mailbox with its own storage capacity to which emails can be moved. This archive mailbox must be set up by an administrator.
- Archive Mailbox With Exchange Online Archiving
With Exchange Online Archiving (EOA), users can move their emails to a separate archive mailbox to which administrators can apply their own archiving and retention policies.
Limitations of the Native Archiving Capabilities of Microsoft 365
However, IT decision-makers need to be aware of certain limitations concerning Microsoft 365’s on-board archiving options. Above all, in terms of security of storage, the use of PST files or the “Archive” button does not protect against data loss. Likewise, the separate archive mailbox provided in M365 (when not using Exchange Online Archiving) does not meet all the criteria of a professional email archiving solution. Only the archive mailbox that comes with Exchange Online Archiving (EOA) supports the functions and features required for professional email archiving, such as retention policies, legal holds and eDiscovery options. However, Exchange Online Archiving is only included in the more expensive M365 plans such as Business Premium and the upscale Enterprise plans.
The “Shared Responsibility” Model
Microsoft applies a policy of shared responsibility to its Microsoft 365 services. As such, Microsoft is responsible for ensuring that services under the Microsoft 365 label are permanently available and are offered redundantly. However, Microsoft does not consider itself responsible for protecting and retaining the data of its customers, and this also applies to any data contained in emails.
Due to the shortcomings and limitations that exist in M365 (depending on the selected archiving function) and the fact that customers are responsible for protecting and retaining their own email data, a professional third-party email archiving solution should be used.
What to Consider When Choosing an Email Archiving Solution for Use with M365
An email archiving solution can be a key element in terms of the long-term protection and retention of business emails. But the decision as to which solution is most compatible with the needs of a business is not always an easy one. Decision-makers are advised to examine the following criteria before choosing archiving software:
Independence From Microsoft
Without an external email archive, users will not be able to access their own emails if the Microsoft Office 365 service fails. A third-party solution will ensure that a vendor lock-in is avoided and the company’s emails will remain accessible even if the M365 service fails.
Self-Service for the End User
Some professional email archiving solutions provide users (not just the administrator) with a fast and efficient means of searching the email archive, as well as the ability to restore emails quickly and simply. This can relieve the burden on an IT team as they no longer need to be contacted to deal with such issues.
Protection Against Data Loss and Manipulation
Emails should be protected against accidental or malicious deletion; if they are not, compliance with legal requirements can be problematic. Even if Microsoft 365 is essentially capable of restoring data erased by mistake, situations can arise that impede or even seriously jeopardize daily business operations.
Compliance With Privacy Laws
When used appropriately, certified email archiving solutions ensure that emails are always processed in accordance with the relevant data privacy laws. Especially since the EU GDPR came into force, data privacy has been the focus of public attention. Even in countries outside the EU, increasing attention is being paid to this sensitive matter.
Reasonable Total Cost of Ownership (TCO)
Microsoft’s most powerful archiving option (Exchange Online Archiving) is included only in specific M365 premium plans that are generally tailored to the needs of larger businesses. Microsoft 365 plans tailored to small and mid-sized businesses (SMBs) do not include Exchange Online Archiving and this would need to be added as an extra paid service. In this case, a third-party solution could be more affordable.
Archiving and backing up emails are two models that fulfill very different purposes. The purpose of backups is to store data regularly over short to medium time frames, thus providing a snapshot of the data in question. Thus, a backup is a means of disaster recovery.
The primary objective of any email archiving solution is to ensure that email data remain available and recoverable over time. These aspects are particularly important for companies in the context of legal retention requirements for business-critical information. What is known as audit security plays a major role here, meaning that retained emails must be tamper-proof, and it must be possible both to log them and export them.
The Benefits of Independent Email Archiving Software
Third-party solutions can provide extra benefits over and above Microsoft’s native email archiving capabilities:
- An independent archiving solution allows content from email sources other than Microsoft 365 to be stored within the same archive. Managing several archiving solutions at the same time usually increases the cost and complexity of retaining business records. Using a central archive reduces the number of solutions that need to be administered by the IT team and searched through by users.
- Using an archive that is independent of the Microsoft 365 platform makes it easier to follow the 3-2-1 rule, which states that an organization should keep three copies of its data: two locally and one at a remote location separate from the primary system on which the data is created and stored.
- Many third-party archiving solutions support email de-duplication, which can significantly reduce storage requirements.
- Indexing a larger number of file types makes it easier to search for and retrieve emails and file attachments.
Conclusion: Third-Party Email Archiving Is a Necessary Addition to Microsoft 365
Although Microsoft 365 is doubtlessly a reliable, powerful and versatile platform, it does have its limits in terms of email archiving, and decision-makers in SMBs need to consider these shortcomings carefully. Business leaders and IT managers who are unaware of the facts are exposing themselves to unnecessary risk. A professional third-party email archiving solution can mitigate, even eliminate these risks altogether and should, therefore, be considered.
To assist companies in finding a suitable email archiving solution for use of Microsoft 365, the market research institute Osterman Research has produced a white paper on how small and medium-sized businesses that use Microsoft 365 can adequately protect their business email communications. The white paper explores which email archiving options exist, the risks to email data when using Microsoft 365, and what features your organization needs in order to adequately protect and manage the data contained in emails.
Are you interested in finding out more about the results and guidance contained in the white paper of Osterman Research?
FAQ
What Options Do Companies Have for Archiving Their Emails in Microsoft 365?
Microsoft provides several options for archiving emails in M365. They include the “Archive” button in Outlook, storing emails in the form of PST files, and using an archive mailbox that has to be configured separately (with or without Exchange Online Archiving). Alternatively, a professional third-party email archiving solution can be used.
Does Microsoft 365 Automatically Archive Emails?
No. Emails are not archived automatically in Microsoft 365. M365 users must take responsibility for securing their emails themselves and decide which email archiving option best meets their corporate and, potentially, legal requirements.
Do Companies Need to Archive Their Emails in Microsoft 365?
Yes. Emails containing business-critical information should always be archived to protect this precious information resource and exploit it to the full. As a rule, legislators also impose legal requirements on the retention of business-relevant emails and on data privacy, both of which render the use of a professional email archiving solution essential.
Is It Sufficient Just to Create Backups of My Emails in Microsoft 365?
No, the purpose of a backup is to save data (e.g. emails) and systems (e.g. the email server) regularly in the short and medium term, and is primarily a means of disaster recovery. Any data produced or modified between two storage cycles will not be protected against loss and manipulation. First and foremost, the objective of any email archiving solution is to store copies of all emails including their file attachments for many years in a form that is faithful to the original, quick to find, and permanently available. This is essential in order to fully exploit the precious information resource that is email, while meeting the laws governing the storage of emails and data privacy.
Source: MailStore
There are an incredible, and increasing number, of electronic signature tools and GlobalSign has been recognized as a Strong Performer for electronic signatures in the Gartner Peer Insights ‘Voice of the Customer’: Electronic Signature.
Documents Signed with Confidence, Integrity, and Trust
If you stopped to think about the importance of a signature to you and your business, there are probably several reasons you may want to introduce and incorporate electronic signatures into your business including efficiency, regulatory compliance, and increased security.
Behind strong business best practices is a robust digital signing solution. “The “Voice of the Customer” is a document that synthesizes Gartner Peer Insights’ reviews into insights for IT decision makers. This aggregated peer perspective, along with the individual detailed reviews, is complementary to Gartner expert research and can play a key role in your buying process, as it focuses on direct peer experiences of implementing and operating a solution.”
“This document will highlight some key insights for the electronic signature market based on 18 months of reviews, and will also point you to particular ways to use the site in your buying process.”
The “Voice of the Customer” report can play a key role in your buying process, as it focuses on direct peer experiences of buying, implementing and operating a solution.
Promoting Strong Business Best Practices with a Strong Signing Solution
Behind strong business practices is a strong signing solution, and with 95% of customers willing to recommend GlobalSign based on 43 reviews as of 31 October 2022, we have been named as a Strong Performer in the 2022 Gartner® Peer Insights™ “Voice of the Customer” report.
GlobalSign’s Digital Signing Service (DSS) helps organizations to sign quickly, easily, securely and with confidence. Through one API integration, DSS is designed to provide a solution which compliments your workflow to boost business efficiency, meet national and industry-specific regulations and provide scalability to your business.
Learn more about Gartner Peer Insights ‘Voice of the Customer’: Electronic Signature and download your complimentary copy of the report.
Source: GlobalSign
The supply chains of today’s global economy rely heavily on technology and information systems to deliver finished goods and services to the end user. However, for all the benefits of a hyperconnected economy this introduces, supply chains also carry with them a high degree of risk.
Systems typically have vulnerabilities which, if exploited by cybercriminals, can have a far-reaching impact. Attacks on the supply chain have risen by over 600%, according to a recent study by Interos, and groups of threat actors (like Magecart) are leveraging supply –chain-specific exploits that make headlines with high-profile attacks.
It’s no wonder that securing the digital supply chain has become a high priority for organizations who want to avoid disruption, protect sensitive data, and prevent brand damage.
Securing Your Partners
Enterprises should begin by identifying and understanding the risks brought in by each of their business partners. Security leaders need to assess the security controls in place, the mitigating and compensating controls, and how each vendor monitors their risk posture. This needs to be done for each business partner — there can be no weak link.
Typically, this is done by asking each partner to fill out a questionnaire, which can vary from a couple dozen questions to over one hundred. While potentially tedious, the purpose is to understand the risk of doing business with a particular partner and determining whether or not to accept that risk. Some companies are even issuing a “FICO score for cybersecurity”, which assigns a safety rating to each party.
Securing Your Own Organization
Organizations should also assess their own security culture. Every organization has within their security strategy prevention and detection controls. However, it is vital to continue to improve the culture of security awareness as human error continues to be one of the top drivers of a breach. In fact, 74% of all breaches are due to the human element, according to the 2023 Verizon Data Breach Investigation Report (DBIR).
One of the best ways to combat human error is with education. At this point, there is still much to learn about securing your enterprise from outside risks. Security awareness training for third-party risk management can help you understand the security shortcomings of a potential partner before taking on that risk.
Similarly, in-house security awareness training can help companies make sure they are not the ones putting others at risk. These programs identify and improve areas of security weakness so that employee behaviors don’t become a liability for the company or any of its partners downstream. This may entail adding phishing simulations, implementing new ways of engaging employees, and modifying communication strategies regarding current tactics being used by bad actors.
Companies should also take note of how their security team engages with the business. This will reveal if they are treated as functional partners, or if there are silos causing employees to view cybersecurity issues as an “IT only” problem.
Currently, the top areas of supply chain weakness involve cloud storage, databases, and compromised credentials. Those are areas touched every day by everyday employees, so it is those same employees that need to do the work to interact with those things safely. Improving the overall security culture will greatly reduce the chance of compromise as employees learn the warning signs of danger.
Securing Your Software Development Cycle
The software development process is another area that should be assessed within the context of a secure supply chain.
This is an area which will demonstrate if the security team is perceived as a valuable business partner or an inhibitor. For example, open-source code is popular to use as it can fast-track projects. However, there are no guarantees that open-source libraries have had proper security inspection.
If there is a good relationship, the business will engage the security team early in the process. They see the value in doing application security testing early because it surfaces vulnerabilities that teams can patch. This sets a course for them to then continue the process throughout the development cycle.
However, if security doesn’t get engaged until the end of the cycle, it’s usually a sign that either something is broken within the process or that security practices aren’t adequately valued. By engaging security only at the end, there is the risk of delays due to critical vulnerabilities. These flaws need to be patched, and this can lead to other issues such as delays in delivery and strained relationships between the business and the security team.
Enterprise Security Is Now a Team Sport
Supply chain security isn’t new, and most security leaders are going to struggle with it. Up until a few years ago, it may have even been a manageable affair. However, with the tech boom of the past few decades and the accelerated pace of the digital revolution, it is a problem that is growing bigger every day.
While secure supply chain management is something that will never be perfect, it’s up to each organization to do their due diligence before entering into business partnerships. A company’s fate becomes the same as its least protected partner, so vetting for cybersecurity weaknesses before signing the contract is an understandable and necessary part of doing business today.
That is why it is every organization’s responsibility to assess not only their partners, but themselves. In a digitally connected supply chain, what happens to one can affect everyone else. Companies should hold all partner organizations to high standards of industry security and expect the same of their own teams. After all, they may be part of someone else’s supply chain.
Source: Fortra
Sophos has released the State of Ransomware in Financial Services 2023, an insightful report based on a survey of 336 IT/cybersecurity professionals across 14 countries working in the financial services sector. The findings reveal the real-world ransomware experiences of the sector.
Rate of attack and data encryption
The 2023 survey revealed that the rate of ransomware attacks in financial services continues to rise. It went up from 55% in the 2022 report to 64% in this year’s study, which was almost double the 34% reported by the sector in the 2021 report. Although the sector experienced an increased attack rate, it was below the cross-sector average of 66%.
Financial services reported the highest encryption level in three years: 81% of organizations stated that their data was encrypted, a 50% rise over the 2022 report when 54% reported data encryption. Over one in ten attacks (14%) were stopped before the data was encrypted, down by 67% over last year’s report and the second lowest rate across all sectors in this year’s survey.
In a quarter of attacks (25%) where data was encrypted, data was also stolen, suggesting that this “double dip” method (data encryption and data exfiltration) is becoming commonplace.
Root causes of attacks
Exploited vulnerabilities (40%) and compromised credentials (23%) were the two most common root causes of the most significant ransomware attacks in the financial services sector. Emails (malicious emails or phishing) were the third most common root cause behind 33% of attacks experienced by the sector.
Data recovery and the propensity to pay the ransom
98% of financial services organizations got their encrypted data back, slightly higher than the 97% cross-sector average. 43% of financial services organizations paid the ransom to recover their encrypted data, while over two-thirds (69%) used backups for data recovery. Encouragingly, the rate of ransom payments in financial services is down from 52% in our 2022 study, while the use of backups to restore data has increased slightly from 66% in the 2022 report to 69% in this year’s report.
However, the proportion of financial services organizations paying higher ransoms has increased, with almost 39% paying a ransom of $1M or more in our 2023 study compared to just 5% in the year before. At the same time, the percentage of financial services organizations that paid less than $100,000 remained in line with last year’s report, coming in at around 40%.
Read the full report here.
Mitigating the ransomware risk
Sophos recommends the following best practices to help defend against ransomware and other cyberattacks:
- Strengthen defensive shields, including:
- Security tools that defend against the most common attack vectors, including endpoint protection with strong anti-exploit capabilities to prevent exploitation of vulnerabilities, and Zero Trust Network Access (ZTNA) to thwart the abuse of compromised credentials
- Adaptive technologies that respond automatically to attacks, disrupting adversaries and buying defenders time to respond
- 24/7 threat detection, investigation and response, whether delivered in-house or by a specialist Managed Detection and Response (MDR) provider
- Optimize attack preparation, including making regular backups, practicing recovering data from backups, and maintaining an up-to-date incident response plan
- Maintain good security hygiene, including timely patching and regularly reviewing security tool configurations
About the survey
Data for the State of Ransomware 2023 report comes from a vendor-agnostic survey of 3,000 cybersecurity/IT leaders conducted between January and March 2023, including 336 in the financial services sector. Respondents were based in 14 countries across the Americas, EMEA, and Asia Pacific. Organizations surveyed had between 100 and 5,000 employees, and revenue ranged from less than $10 million to more than $5 billion.
Source: Sophos
MailStore is delighted to have received the Business Excellence Award 2023 in the category “Best Independent Email Archiving Vendor”.
This year, the monthly international business magazine Acquisition International – “AI” for short – presented its Business Excellence Awards for the seventh time. Published for the first time in 2010 by UK B2B publishers AI Global Media Ltd., the magazine Acquisition International now provides 108,000 readers in more than 170 countries with news, comment and analysis on topical business issues and trends.
 Norbert Neudeck, Director of Sales at MailStore Software GmbH, was particularly delighted to receive the accolade: “Even after more than 15 years of MailStore history, many SMBs and software companies still do not attach the same importance to email archiving as they do to IT-related topics such as backups or anti-virus software. The benefits to be gained by a company when using a professional email archiving solution go far beyond legal compliance. So, we’re all the more gratified that our efforts have been honored in the Business Excellence Awards.”
Norbert Neudeck, Director of Sales at MailStore Software GmbH, was particularly delighted to receive the accolade: “Even after more than 15 years of MailStore history, many SMBs and software companies still do not attach the same importance to email archiving as they do to IT-related topics such as backups or anti-virus software. The benefits to be gained by a company when using a professional email archiving solution go far beyond legal compliance. So, we’re all the more gratified that our efforts have been honored in the Business Excellence Awards.”
The Business Excellence Awards honor companies from a wide range of business sectors, irrespective of how big or well-known they are. Nominations are submitted by the readers.
 A research team at Acquisition International then analyses all the publicly available information on nominees and a jury rates the companies on this basis. In order to win an award, a company must satisfy a whole array of different criteria in the areas of e.g. client management and client feedback, innovation, corporate growth, longevity and reputation.
A research team at Acquisition International then analyses all the publicly available information on nominees and a jury rates the companies on this basis. In order to win an award, a company must satisfy a whole array of different criteria in the areas of e.g. client management and client feedback, innovation, corporate growth, longevity and reputation.
Highlights in our case included the user-friendliness of our email archiving solutions, coupled with a fair pricing policy and first-rate customer support. In addition, our software facilitates the optimum use of email as an information resource, while supporting legal compliance in the area of document retention. Our software is constantly being developed, so users always have a simple, secure, flexible and scalable email archiving solution at their disposal.
Source: MailStore
The Digital Operational Resilience Act (DORA) was enacted in January 2023 and will be in full force January 2025. Even if regulators provide a grace period (just like they did for GDPR) and January 2025 seems like a long way off, time passes quickly. It is, therefore, essential for financial institutions regulated under DORA to start planning their compliance journey.
Given the ever-increasing risks of cyber attacks, the EU is strengthening the IT security of financial entities such as banks, insurance companies and investment firms. Today the Council adopted the Digital Operational Resilience Act (DORA) which will make sure the financial sector in Europe is able to stay resilient through a severe operational disruption.
DORA at a Glance
The press release from the European Council provides a concise description of DORA’s purpose:
“DORA sets uniform requirements for the security of network and information systems of companies and organizations operating in the financial sector as well as critical third parties which provide ICT (Information Communication Technologies)-related services to them, such as cloud platforms or data analytics services. DORA creates a regulatory framework on digital operational resilience whereby all firms need to make sure they can withstand, respond to, and recover from all types of ICT-related disruptions and threats. These requirements are homogenous across all EU member states. The core aim is to prevent and mitigate cyber threats.”
Understanding the intersection between DORA, GDPR, and NIS2 is crucial.
Companies regulated under DORA still need to comply with GDPR requirements. It’s important for IT service providers to understand that DORA brings its own set of challenges, separate from GDPR. If a company violates European privacy laws, it can also be in violation of financial services supervisory laws, which can lead to further consequences. Additionally, certain credit institutions and trading venues must follow the NIS2 directive in addition to DORA, but DORA takes precedence in case of any conflicting regulations due to its more specific nature (lex specialis).
DORA requirements are broken down into five foundational pillars to meet the act’s core objectives. Before we get into those, we must point to a few things deriving from DORA’s mission statement. One of them is that the EU Council recognizes that financial institutions are the most highly targeted entities and that security incidents may include business interruption. As per the Bank of England’s “Systemic Risk Survey Results 2022 H2” report, 74% of the participants consider cyberattacks to be the most significant risk in the short and long term. The second-highest risks are inflation and geopolitical incidents, which are almost equally concerning.
One important aspect of a robust security strategy is the ability to quickly recover and return to normal operations, which is exactly what DORA aims to achieve. Additionally, it’s worth noting that supply chains in the financial industry have historically lacked the same level of accountability as the institutions themselves. However, with the implementation of DORA, third-party vendors will now be closely monitored and regulated by industry regulators.
Breaking Down the Five Pillars of DORA
ICT Risk Management
The first pillar includes frameworks and guidelines to help financial institutions increase the maturity of their risk management programs. These guidelines aim to minimize the risk of attacks by reducing the attack footprint, detecting active attacks, and developing strategies to mitigate the impact of successful attacks. Solutions that align with this category comprise vulnerability management, application security testing, data and asset discovery, and penetration testing. Additionally, safeguarding endpoints, preventing data leaks, and securing public-facing web applications should be considered within this pillar.
Classification and Reporting of ICT-related Incidents
In the second pillar, there is some overlap with the first one, as it involves identifying signs of compromise in your IT infrastructure and handling any malicious activity. However, it also includes additional guidelines such as a classification system based on the impact and templates for reporting content. This pillar emphasizes maintaining integrity and managing configurations, as well as keeping your incident response plan up-to-date and documented. Solutions that utilize threat intelligence are crucial to detect elusive malicious activities that may have bypassed your initial defenses.
ICT Third-Party Risk Management
The third pillar focuses on supply chain risk management. Although the supply chain risk is typically implied in other mandates, DORA specifically addresses this risk due to the visibility of high-profile supply chain attacks in the last couple of years. To mitigate supply chain threats, organizations must have an inventory of all contractual agreements with ICT service providers and a process to evaluate potential new business partners and existing ones. Some additional considerations include phishing simulations and other security awareness training to help prevent employees from being socially engineered by bad actors masquerading as business partners. Additionally, it is crucial to have controls to prevent malicious files from being shared between partners. Financial institutions must also plan for potential service interruptions caused by their partners.
Digital Operational Resilience Testing
This fourth pillar emphasizes testing the institution’s plan for dealing with incidents. The aim is to detect any potential shortcomings and identify areas where improvements in efficiency and system strengthening can be made. Tabletop exercises serve as one effective method of testing your incident response plans. In addition, exploring adversary simulations and red teaming would be advisable, which can highlight any weaknesses and enhance your teams’ skills.
Information Sharing Between Financial Entities
The fifth pillar advocates for collaboration within the financial sector to combat shared adversaries. By exchanging intelligence, indicators of compromise, and the latest tactics, techniques, and procedures (TTPs) with peers in the industry, everyone can increase their ability to withstand challenges.
“Stronger Together”
Out of these pillars the fifth stands out a bit as it aligns to the theme of the 2023 RSA Conference, which is “Stronger Together”. There were multiple sessions where industry leaders were talking about how the security community needs to work together and share our insights to help improve our defenses against threat actors.
A few years ago, I worked with a former security leader of a global financial institution. He told me that although financial institutions compete with each other for new business, he collaborated regularly with his counterparts at these competitors because they all had the same goal, which was protecting their respective employers from the same types of attackers. Other industries would benefit from this same type of collaboration, so hopefully, we will see more of that in the years to come.
Source: Fortra