News
Generative AI tools present both a significant opportunity and a genuine risk. While GenAI can enhance, streamline, and augment a wide range of workflows, it also introduces the potential for misuse and the exposure of sensitive or proprietary data. As a result, many organizations are struggling with GenAI adoption. GenAI is top-of-mind for many IT teams, and most are in the early stages of experimentation but lacking the governance, controls, and safeguards required to adopt GenAI safely.
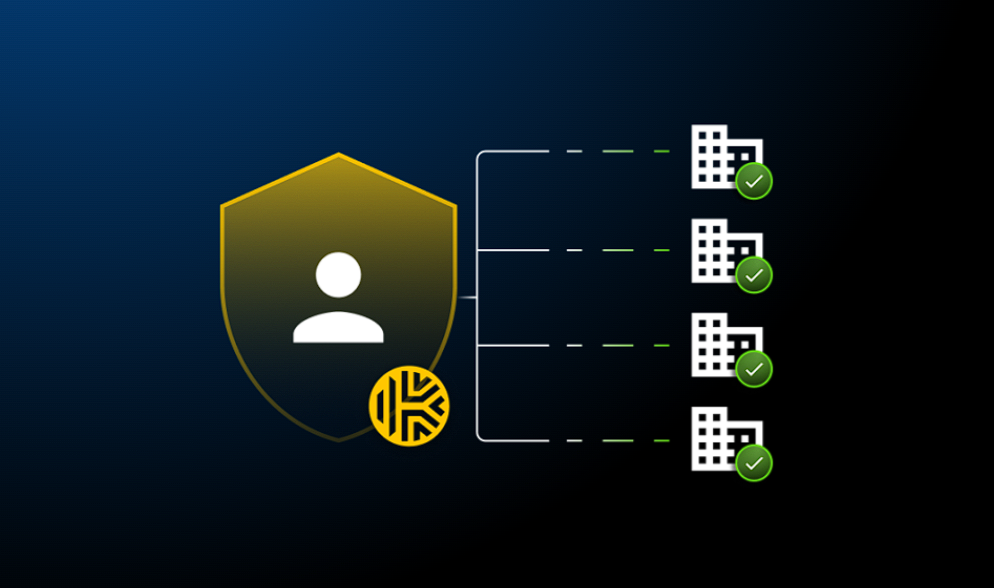
Sophos Workspace Protection, provides all the controls organizations need to safely and easily embrace GenAI such as:
- Get visibility into the GenAI tools and services currently being used
- Easily setup policies to block unsanctioned GenAI sites, apps, and tools both in and out of the browser
- Optionally warn users against the use of unsanctioned services so they can self-govern
- Use data boundary controls to block, warn, or allow file uploads or downloads and copy and paste operations to prevent sensitive data mistakes
What You Need:
Safe GenAI policies are made possible thanks to a few of the key capabilities that make up Sophos Workspace Protection:
- Sophos Protected Browser integrates a secure web gateway with rich policy controls and data boundary controls that provide a transparent and familiar experience for workers
- Sophos DNS Protection for Endpoints adds an additional layer of domain-level security and control that spans across all ports, protocols, and apps on the device
- Sophos Central provides a consistent easy management experience with rich insights and reporting
These products integrate seamlessly to make safe GenAI adoption easy.
How it Works:
Watch this video for a quick demonstration of how it works, and how easy it is to set up:
One of the powerful but easy capabilities of the Sophos Protected Browser are the data boundary controls – which does what it says on the tin. It establishes boundaries around data operations such as copy and paste, upload and download, and more, to keep data within allowed applications where necessary, and prevent potentially costly data sharing mistakes:
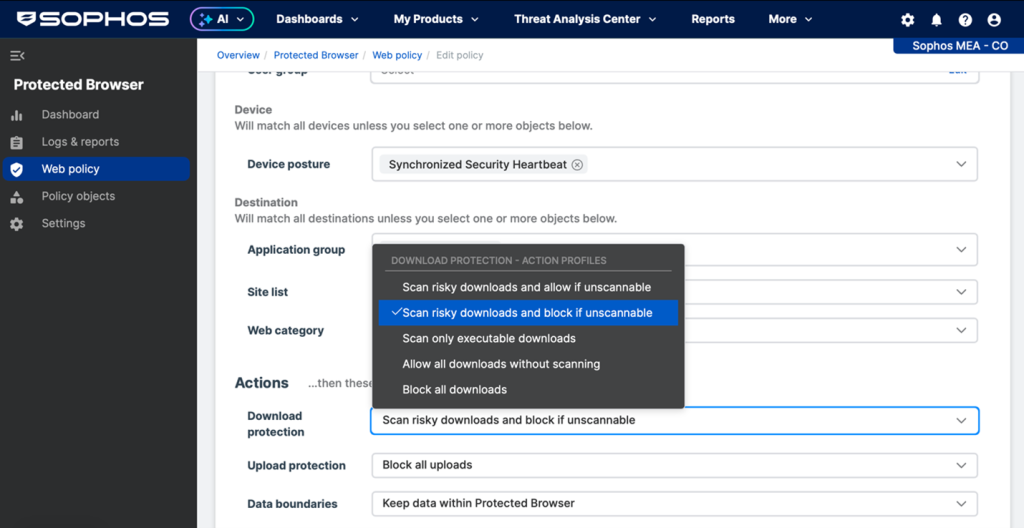
Sophos Protected Browser provides granular data boundary controls for uploads, downloads, copy and paste, and more.
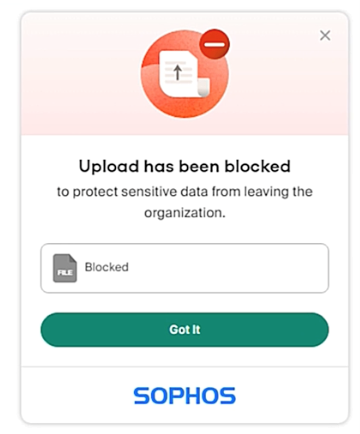
Users are notified when their actions are blocked.
Get a full overview of the data boundary control options in the online documentation.
Restricting Access Through Sophos Protected Browser Only:
For organizations looking to restrict all access to GenAI webservices through the Sophos Protected Browser only, this is also very possible when combined with Sophos Endpoint App Control which can block the use of all other browsers ensuring all interaction with GenAI is done through the Sophos Protected Browser.
Learn More about Sophos Workspace Protection:
Check out all the great capabilities and use cases for Sophos Workspace Protection and be sure to participate in the early access program for the new Sophos Protected Browser.
Source: Sophos
Most IT teams are doing impressive work under difficult conditions. Tickets get closed. Systems stay online. Users are supported. On paper, everything is functioning.
And yet, there’s a persistent feeling that progress is harder than it should be.
As expectations for faster, more consistent and more scalable IT service delivery rise, many teams are starting to feel overwhelmed. Too much time is still spent on manual documentation, repetitive service tasks and disconnected processes that slow response times and pull focus away from higher-impact, proactive work.
The natural assumption is that demand exceeds the team’s ability to keep up. More endpoints, more users, more complexity — surely the answer is more people.
But for many IT organizations, the challenge isn’t just a headcount numbers game. The real limitation is how much of the day is still consumed by manual, repetitive work.
Manual workloads quietly become the bottleneck
Manual, repetitive work rarely shows up as a red flag. It blends into the background of daily IT operations. A technician copies information from one system into another. Someone searches for documentation that exists — just not where they need it.
Each instance may seem minor, or even necessary, on its own. But over time, they accumulate. As IT environments grow more complex, manual tasks multiply, context becomes increasingly fragmented and resolution paths stretch longer than they should.
What used to feel manageable starts to feel overwhelming, simply because every task takes more effort than it should. This is the tipping point where managing manual workloads stops being routine and start becoming a liability.
Why manual repetitive work becomes technical debt
As IT environments evolve, processes built for speed eventually fall behind. Teams compensate by relying on workarounds, institutional knowledge and manual effort instead of consistent systems.
The cost isn’t obvious at first. However, over time, it shows up as:
- Longer resolution times for routine issues
- Inconsistent outcomes between technicians
- Burnout among the people who know the environment best
- Increased risk from missed steps and missing context
Over time, those manual tasks become a form of technical debt that IT teams struggle to escape. Technicians feel the debt first
Technicians are on the front lines, and they feel the burden most. A significant portion of their day is often spent searching for information across fragmented systems or recreating work because documentation is missing or outdated. Instead of resolving issues, they’re stuck navigating disconnected tools and repetitive, manual tasks.
Over time, this erodes momentum. Skilled technicians spend their days executing processes instead of improving them. The job becomes about keeping up rather than moving forward.
This is usually the first signal that manual work has crossed the line from “how things are done” to “what’s holding us back.”
Managers see the impact when scale stops working
For IT operations leaders, the consequences of manual workloads surface differently.
Scaling IT effectively requires more than hiring. Leaders are under pressure to keep pace with growing demand while also giving their teams room to develop skills and improve how work gets done. Organizations must balance workload, automation and upskilling to ensure teams can operate effectively today while preparing for what’s next.
Manual workloads introduce friction at every stage of the ticket lifecycle. When prioritization and triage rely on human review, tickets wait in queues, urgency is misjudged and critical issues are often buried behind lower-impact requests. As volumes grow, teams spend more time sorting and routing work than resolving it.
Why fixing individual tasks won’t solve the problem
When teams start to feel the weight of manual work, the first instinct is usually to automate pieces of it. A script here. A rule there. Maybe a new tool to speed up one step in the process. Those changes can help — but they rarely change how the work actually feels day to day.
That’s because automating isolated tasks inside broken workflows just creates faster fragments. Technicians still have to jump between monitoring alerts, ticket queues and documentation systems to understand what’s happening. Context still lives in multiple places. And work still depends on people stitching everything together by hand.
At that point, the problem isn’t effort or expertise. It’s that service delivery itself is fractured across disconnected systems.
Real progress starts when teams step back and ask a harder question: How should this work flow from start to finish?
Where AI actually changes the equation
That question — how work should flow end to end — is where AI begins to matter in a meaningful way.
Instead of automating individual steps, AI makes it possible to connect them. When service delivery runs through an integrated, AI-driven workflow, alerts flow directly into tickets, relevant context surfaces automatically and repetitive decisions no longer require human intervention.
Issues get resolved faster and service delivery starts to feel more predictable and consistent. Teams spend less time chasing information and more time fixing issues. Processes become consistent. Outcomes become repeatable. And the operation can scale without adding complexity, headcount or burnout.
AI doesn’t solve the problem by working harder. It solves it by changing how the work fits together.
The real shift IT operations need to make
Organizations that take this step reduce operational friction, lower costs and make service delivery easier to manage. It’s time to shift gears and strategically evaluate how AI can transform your IT operations and reduce the technical debt of manual workloads.
Those that wait risk falling behind, constrained by manual processes and fragmented systems that make it harder to respond quickly to evolving market demands and technology change.
IT operations are entering a new phase. Discover how AI is becoming a game changer for IT operations — from automating documentation workflows to accelerating ticket resolution and helping teams work smarter, not harder.
Source: Kaseya
Sophos has been named a 2026 Gartner® Peer Insights™ Customers’ Choice in the 2026 Gartner® Peer Insights™ Voice of the Customer Report for Endpoint Protection Platforms . This marks our first Gartner Peer Insights Customers’ Choice distinction of 2026 and a fifth consecutive Customers’ Choice for Sophos in the EPP category. This recognition comes directly from customer feedback, and we’re truly thankful for the time customers take to share their experiences and for the trust they place in Sophos.
In the 2026 Voice of the Customer report for Endpoint Protection Platforms, Sophos’ rating is based entirely on verified customer feedback based on 286 total reviews as of 30 November 2025:
- Named a Customers’ Choice vendor for the 5th consecutive time
- 4.9 / 5.0 overall rating – the highest rating among vendors in the Customers’ Choice Quadrant
- 4.8 / 5.0 rating for Product Capabilities – the highest among vendors in the Customers’ Choice Quadrant
- 98% Willingness to Recommend – tied for the highest among vendors in the Customers’ Choice Quadrant
We believe these results reflect Sophos’ focus on delivering powerful, easy-to-manage endpoint protection that combines advanced threat prevention, detection, and response across modern work environments.
Built for Modern Workspaces and Evolving Threats
We believe Sophos’ continued recognition in the Gartner® Peer Insights™ Voice of the Customer Reports for Endpoint Protection Platforms aligns with its broader strategy to secure today’s dynamic, hybrid work environments. With capabilities that extend beyond traditional endpoint security, Sophos helps organizations protect users, devices, and data wherever work happens. The recent introduction of Sophos Workspace Protection is the ideal complement to Sophos Endpoint, Sophos MDR, and Sophos Firewall and extends and unifies these great products and services to remote and hybrid workers everywhere they go.
Recognition Driven by Real Customer Experiences
Gartner Peer Insights is a free peer review and ratings platform designed for enterprise software and services decision makers. We feel being named a Customers’ Choice reflects both high overall ratings and strong willingness to recommend, consistently validating Sophos’ commitment to customer success. We are incredibly grateful to our customers worldwide for their continued trust and feedback, which directly contribute to shaping and improving Sophos’ solutions.
Here are some examples of what customers had to say about Sophos Endpoint:
“Our overall experience with Sophos Endpoint has been exceptionally positive. It delivers enterprise-grade protection without the complexity. The seamless integration and proactive defense against emerging threats have given our IT team complete peace of mind and significantly reduced our management overhead.” – CIO in the Manufacturing Industry, $50M-$250M, Review Link
“Everything about Sophos, from their admin tools to the user experience to the support and sales team, is top-notch. We have been using Sophos Endpoint for almost 13 years now, as Endpoint protection is the bare minimum requirement of our security-minded clients and audits. Every year, we add more and more users to our Endpoint protection, scattered across our five offices located in LA, NY, Austin, London, and Tokyo” – Director, IT Security and Risk Management in the Media Industry, $50M-$250M, Review Link
To learn more about how Sophos Endpoint can help your organization, visit: https://www.sophos.com/en-us/products/endpoint
Source: Sophos
The World Economic Forum’s Global Cybersecurity Outlook 2026 delivers a clear and uncomfortable truth: cyber risk is accelerating faster than our traditional defenses can keep up. AI-driven attacks, geopolitical volatility, supply-chain fragility, and widening cyber inequity reshape the threat landscape at a systemic level.
What stands out most, however, is not just what is changing—but where defenses are consistently failing.
Across AI misuse, ransomware, fraud, supply-chain compromise, and cloud outages, identity remains the dominant attack path. Whether human or non-human, identities have become the new control plane of modern cybersecurity.
In this blog, I break down five Identity Security lessons we can learn from the research.
Lesson 1: AI has turned identity abuse into a force multiplier
According to the report, 94% of organizations identify AI as the most significant driver of cyber risk, and 87% cite AI-related vulnerabilities as the fastest-growing threat. While much attention is placed on AI models themselves, the more systemic risk lies elsewhere.
AI agents, like other identities, don’t break in—they log in.
Attackers are using AI to:
- Scale phishing and impersonation with unprecedented realism
- Automate credential harvesting and privilege escalation
- Exploit over-privileged service accounts, APIs, bots, and AI agents
The report explicitly highlights that the multiplication of identities—especially AI agents and machine identities—has outpaced governance and security controls. These non-human identities (NHIs) now outnumber human users in most environments, yet remain largely invisible, unmanaged, and implicitly trusted.

Security takeaway:
If organizations continue to protect networks and endpoints while trusting identities by default, AI will simply accelerate compromise.
This is why it’s important to apply Zero Trust principles to Identity Security. If authentication and authorization are where your security controls end, you’re likely not implementing a Zero Trust approach.
Instead, security-first approaches like adaptive MFA and risk-based access controls for all identities – whether it’s humans, service accounts, APIs, AI agents, legacy systems, and more – ensure your strategy is based on continuous validation. Rather than, “Do the credentials/access match the identity?” you should be able to answer questions like “Does this access make sense to allow based on the risk signals?”
Lesson 2: Cyber-enabled fraud is an identity problem, not a financial one
The report reveals that 73% of respondents were personally affected by cyber-enabled fraud, making it the top concern for CEOs—surpassing ransomware.
What’s driving this surge?
- AI-powered impersonation
- Credential reuse
- Lateral movement using legitimate access
- Abuse of trusted identities rather than malware
Fraud today succeeds not because systems are unpatched—but because identity verification stops too early.
Once credentials are obtained, most environments still fail to:
- Continuously validate access
- Detect abnormal identity behavior
- Apply step-up authentication dynamically
Security takeaway:
Fraud prevention and identity security are now inseparable. Fraud begins and end with identity abuse, meaning that real-time, context-aware controls are needed to stop fraudulent activity before material damage is done.
From the report, it’s also clear that CEO and CISO priorities are shifting, yet the foundation for where they can come together remains the same: through strong Identity Security.
Lesson 3: Supply-chain attacks inherit trust—and abuse it
The WEF report identifies third-party and supply-chain vulnerabilities as the top cyber resilience challenge for large organizations. Crucially, the most common supply-chain risk is not malware—it is inherited trust.
When vendors, partners, or managed services connect:
- They often authenticate via service accounts
- Credentials are long-lived and rarely rotated
- Access is broad, persistent, and poorly monitored
Attackers don’t need to breach the perimeter if they can log in through a trusted identity.
Security takeaway:
Supply-chain security failures are identity governance failures. Supply-chain breaches succeed by abusing inherited trust, not by exploiting technology gaps. Organizations should treat third-party access as an identity risk by maintaining a clear inventory of vendor identities, enforcing least-privilege and time-bound access, and eliminating standing permissions wherever possible. Strong authentication should be prioritized for high-risk vendor access, and access reviews must align with contract and business lifecycles. Even without new tools, disciplined governance can significantly reduce supply-chain exposure.
Lesson 4: Cyber resilience depends on identity visibility, not just recovery plans
While 64% of organizations claim they meet minimum cyber resilience requirements, only 19% exceed them. Highly resilient organizations share one defining trait: deep visibility and control across identities.
The report’s Cyber Resilience Compass shows that resilient organizations:
- Continuously assess AI and identity risks
- Monitor access across IT, OT, and cloud
- Reduce standing privileges
- Treat identity as a shared ecosystem risk
Yet identity remains fragmented across directories, clouds, SaaS platforms, legacy systems, and machine workloads.
Security takeaway:
You cannot be resilient if you don’t know who or what is accessing your systems—and why. That’s why it’s so important to retain a living, dynamically-evolving graph visualizing which identities exist and their access paths. This acts as a unified source of truth that can expose exploitable gaps that need closing.
Lesson 5: Cyber inequity makes identity the weakest link
The report highlights a widening cyber inequity gap, driven largely by skills shortages—particularly in identity and access management roles, which are among the top three most understaffed security functions globally.
Complex IAM implementations, agent-based controls, and application rewrites are no longer realistic for many organizations.
Security takeaway:
Identity security must become simpler, not more complex. IAM upskilling needs to happen in tandem with identity-first security solution implementation; this is how we close the gap between IAM and cybersecurity teams while reducing operational burden. Cyber inequity makes identity the most fragile control post – especially where skills are resources are limited.
Implementing security solutions designed with identity teams in mind offers many benefits. By standardizing identity policies (e.g., enforcing MFA on all remote and privileged access), organizations reduce dependency on scarce expertise, lower configuration errors, and achieve consistent risk reduction. For example, you can apply one access standard to employees, contractors, and service accounts, cutting operational overhead while measurably shrinking the attack surface.
The strategic shift: From perimeter security to identity-centric Zero Trust
The Global Cybersecurity Outlook 2026 reinforces a fundamental shift: Cybersecurity is no longer about defending a defined perimeter—it’s about securing infrastructure and access in real-time.
AI, cloud, supply chains, and geopolitics have dissolved the perimeter. Identity is what remains.
Organizations that will succeed in 2026 and beyond are those that:
- Treat identity as critical infrastructure
- Secure non-human identities with the same rigor as human users
- Enforce Zero Trust dynamically, everywhere
- Reduce implicit trust across ecosystems
Silverfort was built precisely for this moment—to secure identities wherever they exist, however they authenticate, and whatever they access.
Silverfort’s platform approach to Identity Security recognizes that identities span cloud, on-prem, legacy systems, service accounts, and non-human workloads—yet they are secured through fragmented controls. By acting as a unified enforcement layer across all authentication paths, the platform enables consistent Zero Trust policies without agents or application changes. This allows organizations to reduce identity risk holistically, rather than incrementally securing identities one system at a time.
Final thought
The WEF report concludes that cyber resilience is a shared responsibility and a strategic imperative. Identity Security is where that responsibility becomes actionable.
In the age of AI-driven threats, every breach is an identity breach first.
The question for organizations is no longer if identity should be central to their security strategy—but how quickly they can make it so.
Source: SIlverfort
Multi-factor authentication (MFA) remains a cornerstone of cybersecurity, but attackers have learned to find workarounds.
As identity-driven attacks continue to rise, organizations must go beyond MFA to build resilience. Sophos experts and recent Gartner research agree: It’s time for an identity-first security strategy backed by continuous detection and response. For many organizations, keeping pace with identity threats feels overwhelming, especially as hybrid environments expand. But there’s a clear path forward.
Identity is now the primary attack surface
Chris Yule, director of threat intelligence for the Sophos X-Ops Counter Threat Unit, notes that more than 60% of incidents his team investigates stem from identity-related weaknesses. Phishing, stolen credentials, and social engineering are common entry points — methods that allow attackers to infiltrate without deploying traditional malware.
“The number one threat facing our customers today continues to be ransomware, both in terms of the number of incidents that we see and the impact that it can have when it hits,” Yule explained during a recent webinar. “Classic ransomware cases consistently show identity compromise as the critical first step.”
As organizations expand across hybrid and cloud environments, each new integration, from software-as-a-service (SaaS) apps to service accounts, becomes another entry point. Yet, as Yule noted, there will often be cyberattacks where there’s “very little malicious code in use.” Rather, they mainly use “privilege and trust to gain access to the environment and cause as much damage with that trust as possible.”
Why MFA alone isn’t enough
MFA is essential, but it’s not enough. Attackers have evolved, and identity-based threats now bypass even strong authentication. Organizations need continuous detection and response to stay ahead. In multiple business email compromise (BEC) cases, adversaries bypassed MFA using adversary-in-the-middle (AiTM) phishing kits.
An AiTM attack goes beyond traditional phishing. Instead of simply stealing credentials, the attacker intercepts and relays the victim’s login session in real time. When a user clicks a phishing link and enters their credentials on a fake site, the attacker forwards those details to the legitimate service and captures the entire authentication flow, including MFA responses, allowing them to hijack the session.
This reality aligns with findings that Gartner outlines in their report “CISOs Must Integrate IAM to Strengthen Cybersecurity Strategy .” This report notes that credential compromise remains the leading cause of breaches and that “sophisticated attackers are now targeting the [identity access management] IAM infrastructure itself.”
Gartner further cautions that while prevention is essential, “there is no such thing as fail-proof prevention.” Security teams must be prepared to detect and respond when identity defenses are bypassed.
Identity-first security: The next evolution
According to Gartner, cybersecurity leaders should “embrace identity threat detection and response (ITDR) and adopt identity-first security to enable zero trust and optimize the organization’s cybersecurity posture.”
Identity-first security reframes protection around who and what is connecting, rather than where they’re connecting from. Instead of static perimeter controls, it focuses on continuous trust assessment and adaptive access. In practice, this means:
- Monitoring identity posture continuously, not just enforcing login controls.
- Detecting and responding to abnormal behaviors like privilege escalation or lateral movement.
- Reducing the attack surface by addressing misconfigurations and overprivileged accounts.
Detection for the identity layer
Yule emphasized that Sophos built our Identity Threat Detection and Response (ITDR) service precisely to fill this gap.
“Historically, identity and access management and security operations have always been largely separate things,” Yule said. “And so, what we’ve tried to do with ITDR is look at the overlap of those.”
By continuously assessing identity posture, Sophos ITDR monitors for:
- Stolen or exposed credentials on the dark web.
- Accounts with excessive or unusual permissions.
- Application misconfigurations that enable privilege abuse.
This proactive approach complements Sophos Managed Detection and Response (MDR) and Extended Detection and Response (XDR), ensuring organizations can detect threats in action while also reducing the risk of identity exploitation before attacks begin.
Identity has become the cornerstone of modern cybersecurity, and building resilience starts with treating it as a core discipline. Together, ITDR, MDR, and XDR create a security fabric that is continuous, adaptive, and resilient.
“As we increase trust in different things, things become more complicated, things become more opaque, and it becomes harder to know and identify these micro vulnerabilities that could be exploited by somebody who is smart enough to figure it out,” Yule said.
Organizations that adopt identity-first security strategies gain the agility to detect and neutralize threats before they escalate.
Explore how Sophos Identity Threat Detection and Response (ITDR) helps organizations preempt and neutralize identity-based threats before they become breaches.
Source: Sophos
Managed Service Providers (MSPs) are third-party companies that typically handle a portfolio of other organizations’ IT operations or day-to-day activities. This puts MSPs on the front lines of cybersecurity for numerous businesses, often in highly regulated industries, handling some of their most sensitive data. Even the most experienced MSPs struggle to securely manage passwords, credentials, sensitive files and privileged access across dozens of client environments.
Many MSPs still manage client passwords using shared spreadsheets, sticky notes or unsecured browsers. This makes it difficult to track access, audit usage or enforce strong password policies across critical systems. Without centralized visibility, MSPs face inconsistent access controls, delayed incident response and increased exposure to credential-based attacks. To stay secure and efficient, MSPs need an easy, centralized way to protect client environments and enforce strong password practices at scale.
The need for MSPs to strengthen security
MSPs are increasingly adopting stronger security and password management practices to protect clients and improve operational efficiency. LEAP Managed IT, a North America-based MSP headquartered in Indiana, serves clients across the Midwest, including government agencies, financial institutions, law firms, nonprofits, healthcare organizations and more. The team needed a way to simplify password sharing among internal staff and managed clients while maintaining compliance with industry standards such as CMMC, PCI, HIPAA, ISO, GovRAMP and FedRAMP.
TeamLogic IT in West Denver, which supports 20 clients and 275 end users, faced similar challenges. Many clients relied on insecure methods, such as spreadsheets or email, to share passwords. The lack of centralized control made it difficult to revoke access or track changes when employees left.
Every second spent resetting passwords or tracking down credentials is time taken away from supporting clients and growing the business. A streamlined, secure approach allows MSPs to deliver faster service, reduce risk and demonstrate value in every client interaction.
What KeeperMSP® delivers
KeeperMSP is a Privileged Access Management platform built specifically for MSPs. Core functionality of the platform includes password and secrets management to prevent password-related data breaches and cyber attacks. It helps MSPs protect their own operations while delivering stronger security for every client they manage.
Designed to meet the unique needs of MSPs, KeeperMSP provides complete visibility into end users’ password habits through robust reporting and auditing tools that help enforce security and compliance requirements. This includes Role-Based Access Control (RBAC), Multi-Factor Authentication (MFA), SIEM event reporting and regulatory and industry compliance with the CCPA, GDPR and other standards.
Purpose-built for MSPs, backed by success
For LEAP Managed IT, integrating KeeperMSP with Microsoft Entra ID enabled the team to quickly roll out the platform to 50 employees and hundreds of client users. The company gained real-time visibility into password security and compliance, while technicians in the field could securely access credentials through Keeper’s browser extension and mobile app.
TeamLogic IT experienced similar benefits. Like many MSPs, the company supports dozens of businesses with diverse IT needs. Using KeeperMSP’s role-based access controls and One-Time Share feature transformed the way the team collaborates with clients. The company can now grant or revoke access instantly and share credentials securely without relying on outdated spreadsheets or PDFs.
Across both organizations, unified password management is delivering measurable results. With KeeperMSP, Leap Managed IT and TeamLogic IT continue to improve compliance reporting, reduce credential-related service tickets, streamline credential management best practices and strengthen client relationships.
Managing credentials at scale
According to a 2025 report by Global Market Insights, the MSP market is projected to increase from $69.68 billion to $115.83 billion by 2034, averaging a Compound Annual Growth Rate (CAGR) of 5.8%. MSPs are expected to continue offering highly compliant cloud services, particularly solutions that streamline necessary business functions while providing stronger protection against cyber threats. According to data compiled from Infrascale, cybersecurity threats remain the leading concern for MSPs, with 59.7% identifying it as their top challenge.
In a multi-client environment, MSPs face unique challenges that traditional password managers can’t solve. A purpose-built solution empowers MSPs to secure every client and maintain trust across industries and regulatory requirements. With the right platform, MSPs can reduce risk, streamline operations and deliver stronger security outcomes for every customer they support. Keeper enables MSPs to secure every client account with zero-trust architecture, intuitive management tools and scalable efficiency.
Start a free trial of KeeperMSP today to secure your clients’ most sensitive data, increase visibility and streamline credential management across your organization. Read the full Keeper + LEAP Managed IT Case Study to learn more.
Source: Keeper
AI has dominated cybersecurity headlines for years, but as we enter 2026, the conversation is shifting from hype to hard realities. Across incident response, threat intelligence, and security operations, Sophos experts see clearer signals of where AI is truly making an impact. For IT teams already stretched thin, this isn’t theoretical — it’s reshaping daily decisions.
Defenders are having to deal with the speed and unpredictability of AI adoption inside their organizations. Sophos survey data shows IT leaders are increasingly worried about unmanaged use, data exposure, and how AI-enabled tools can amplify small mistakes. The question is no longer whether to use AI, but how to apply it responsibly to reduce noise and operational strain.
Industry signals reinforce this shift. The Gartner® Hype Cycle™ for Security Operations, in our assessment, shows AI-powered capabilities — such as AI SOC agents, predictive modeling, and cybersecurity assistants — moving out of pure experimentation and toward more practical, augmentation-focused use cases. The emphasis is less on “autonomous AI” replacing humans, and more on AI accelerating triage, improving prioritization, and helping overstretched teams act faster and with greater confidence.
Looking ahead, Sophos experts expect AI’s real impact to be measured by outcomes, not novelty — a theme reflected in their predictions for the year ahead.
DPRK IT workers extend the use of AI for fraudulent employment
“North Korean IT workers could use Agentic AI to enhance the survivability of their fake personas, improve the responsiveness to remote requests, and conduct remote taskings more effectively.” – Rafe Piling, Director of Threat Intelligence, Sophos X-Ops Counter Threat Unit
AI will supercharge threat actor scale and sophistication
“In 2026, attackers will continue to use AI as a force multiplier. AI will make it easier to weaponize known vulnerabilities, orchestrate attack campaigns, lowering the barrier for basic hacking and enabling broad, rapid exploitation across the internet.
Payloads will be customized faster than ever, and social engineering will become increasingly tailored, including phishing that reflects open-source knowledge of individual targets. Deepfake audio and video will make BEC campaigns more convincing and far more credible, making them easier to succumb to.
AI will shift the balance of power by helping even low-skill threat actors operate with speed and precision once reserved for more experienced threat actors.” – John Peterson, Chief Development Officer
The real attack surface: Your AI application
“We’re likely to see major breaches from prompt injection attacks within the next year. For years, security teams have worked to shrink their internet footprint, knowing that anything exposed increases risk.
Firewalls, VPNs, and ZTNA all aimed to reduce that exposure. Now, almost overnight, we’ve created a new attack surface: rapidly deployed AI applications. Many are internet-facing, often unauthenticated, and connected to data many businesses would consider sensitive or confidential. Even more concerning, these applications are being granted the ability to take actions on behalf of the organization.
The speed of AI adoption is driving huge efficiency gains, but unless organizations slow down and assess these risks, they’ll reopen exposures we’ve spent decades trying to close.” – Tom Gorup, Vice President of SOC Operations
The next insider is your AI
“Organizations are racing to deploy LLMs and agents, even the ones they approve internally. By feeding these tools massive volumes of corporate data, they’re creating a new class of insider threat. When that data leaks, who’s responsible? Is the AI an ‘employee,’ and who carries the liability when it goes rogue, is compromised, or misconfigured?” – Chris O’Brien, Vice President of Security Operations
Customers will turn to channel partners to resolve the AI vs. Security priority gap
“In 2026, customers will wrestle with the tension between AI investment vs. core security investment vs. broader IT investments. They’ll be asking: ‘How much time, money and resources should I spend on AI?’ ‘Where do AI and security overlap?’ ‘What are the initial use cases that I trust AI to do?’
While SMBs and enterprises will answer those questions very differently, both will rely on vendors and partners as their trusted advisor. With more tools flooding the market and budgets under pressure, partners who help customers make sense of the noise and rationalize their stack will prevail.
The channel’s role is no longer about sourcing tools; it’s about guiding customers through complex decisions around risk, budget, security and AI strategy trade-offs across the entire customer lifecycle.” – Chris Bell, Senior Vice President of Global Channel, Alliances and Corporate Development
Trusting MDR when the analysts are AI
“In 2026, the Managed Detection and Response (MDR) market will reach an inflection point. The line between a managed detection service and an AI-driven tool will blur until customers can no longer tell which they’re buying. Vendors will market software as full MDR offerings, leaning on AI to compensate for limited human depth.
That shift will create real challenges: customers won’t know where human judgment ends, what’s automated, or who is actually monitoring their environment around the clock. Trust will become harder to calibrate when the ‘team’ behind your security is mostly code. As this ambiguity grows, buyers will struggle to evaluate competence, accountability, and reliability, forcing the industry to confront whether MDR is still a service, a tool, or something in between.” – Tom Gorup, Vice President of SOC Operations, Sophos
Source: Sophos
Sophos introduced Synchronized Security in 2015 with the ability for Sophos Firewall and Sophos Endpoint to share information and work together to automatically respond to threats. This pioneering approach, which transformed cybersecurity from a collection of point products to a security ecosystem, has been successfully reducing cyber risk and elevating security outcomes in the face of real-world threats for over a decade.
We’ve steadily expanded and evolved Synchronized Security since that initial launch, including interconnecting a broad range of products and services, extending response actions, and synchronizing our threat intelligence. Today, Sophos Workspace Protection becomes the latest addition to the Synchronized Security portfolio.
Security Heartbeat
Three key capabilities come together to enable Sophos solutions to work together:
- Security Heartbeat™ is a constantly beating device health status indicator that shows Red, Amber, or Green to reflect its real-time state.
- The Sophos Central platform, which enables Sophos solutions to share threat, health, and security information in real-time, including Security Heartbeat status.
- Sophos solutions are engineered to automatically take actions based on a device’s Security Heartbeat status.
By enabling Sophos solutions to work together, Synchronized Security and the Security Heartbeat capability reduce response time from minutes or hours to just seconds. They also extend the powerful risk reduction capabilities provided by individual Sophos solutions with an additional defense layer only available when security solutions work together.
And it’s free. Synchronized Security is included and enabled automatically at no extra charge for all Sophos customers.
Enabling a coordinated, automated response to threats
Step 1: Detect. If Sophos Endpoint detects a threat on a user’s device, it automatically changes the device’s Security Heartbeat status to Red and shares the new health status with the wider ecosystem.
Step 2: Isolate. Sophos Firewall and Sophos ZTNA immediately limit the Red status device’s access to network resources and applications, preventing data loss. Sophos Firewall can also block traffic from the compromised device to all healthy (Green status) endpoints on the network – including those on the same switch – eliminating the possibility of lateral movement even within the same LAN segment.
Step 3: Restore. Once the affected device is cleaned up, Sophos Endpoint automatically changes the Security Heartbeat status to Green, which instantly triggers Sophos Firewall and Sophos ZTNA to re-enable access.
What about middle-of-the-night attacks?
Synchronized Security is a powerful tool at any time of the day or night, but is particularly helpful outside standard working hours, when in-house resource availability is often reduced. With 88% of ransomware incidents starting during evenings, nights, and weekends, it’s also prime time for adversaries to launch an attack.
So, what happens if an attacker hacks into one of your servers late on a Friday? In a non-Sophos-protected environment, the adversary will have full access to the network over the entire weekend – giving them ample time to exfiltrate data, install backdoors, and deploy ransomware.
But in a Sophos-protected organization, any malicious activity detected on the server by Sophos Endpoint automatically triggers a Red Security Heartbeat health status, causing Sophos Firewall to effectively cut off the server from the rest of the network until it can be cleaned up – without anyone having to do anything.
Once the compromised server has been cleaned up, Sophos Endpoint will return its Security Heartbeat to Green, and full system access and connectivity will be restored automatically.
More than threat response
In addition to automatically responding to threats, Synchronized Security can share application information between Sophos Endpoint and Sophos Firewall. This enables Sophos Firewall to route, prioritize, or block application traffic it might not otherwise be able to identify.
For example, if you have a custom application that needs prioritization, most firewalls won’t recognize it and leave it at the mercy of all the other traffic on your network. With Sophos Firewall and Sophos Endpoint working together, traffic from your custom app can be easily identified and prioritized.
Sophos Endpoint can also share authenticated user information with Sophos Firewall to simplify user-based policy enforcement.
And it doesn’t stop there. For example, if a compromised device starts sending spam or phishing emails, it will trigger a Red health status, causing Sophos Email to automatically block messages before they reach users.
Another great example of Synchronized Security in action is Active Threat Response, which extends Synchronized Security to security operations teams. With Active Threat Response, an analyst working for Sophos as part of our MDR service, or your own analysts working with Sophos XDR, can trigger a Synchronized Security response using the new threat feed capability built into Sophos Firewall. Synchronized Security then acts on this information to identify any compromised host on the network and isolate it automatically until it can be cleaned up. Active Threat Response is also available for Sophos switches and AP6 access points.
The latest addition: Sophos Workspace Protection
Sophos Workspace Protection is an integrated bundle of security solutions that protects apps, data, workers, and guests easily and affordably – wherever they are. It includes Sophos ZTNA, which now supports Security Heartbeat, enabling you to automatically prevent compromised devices from connecting to important networked applications and data. This unique, automated threat response capability greatly limits the ability of a compromised device belonging to a remote worker from becoming an entry point for an attacker to the broader network.
Synchronized Security and Security Heartbeat are key reasons why Sophos ZTNA is a critically important security solution for remote access. Traditional VPN solutions have no way of knowing if a device has been breached and will allow any compromised device full access to the network. Sophos ZTNA, on the other hand, not only enforces multi-factor authentication to prevent breaches from compromised credentials, it also includes Synchronized Security to prevent devices from connecting when in a compromised state.
How to get Synchronized Security
Security Heartbeat is automatically included with Sophos Firewall, Sophos Endpoint, Sophos Email, Sophos Mobile, and now Sophos Workspace Protection. No extra products or solutions are required, no additional subscriptions to purchase.
Sophos Central takes care of all the data sharing. You simply need to set up the Security Heartbeat conditions in your policies to take advantage of it. It’s that easy. It’s one of the reasons many customers choose Sophos for their cybersecurity – you won’t find this anywhere else.
Source: Sophos
We’re excited to announce the latest addition to the Sophos portfolio: Sophos Workspace Protection. It’s an easy, effective, and affordable way to protect remote and hybrid workers, contractors and guests – and the networks and data they access – from threats, breaches, and shadow IT, and provide consistent policy enforcement on and off the network.
The challenge – Why Sophos Workspace Protection?
The traditional network perimeter has been disappearing in recent years, with applications, data, and users everywhere. This shift has made protecting remote and hybrid workers a significant challenge for IT teams.
In response, cloud-delivered network security solutions like Secure Web Gateways (SWG), Cloud Access Security Brokers (CASB), and cloud firewalls – often collectively known as SASE or SSE solutions – have emerged to try and solve this issue. However, these solutions come with their own set of challenges related to back-hauling and encrypted traffic, latency, and cost effectiveness that have made them unworkable options for many smaller and mid-sized organizations.
At the same time, many organizations are grappling with both shadow IT and the need to safely adopt and integrate generative AI technology and services into their workflows without exposing proprietary information or sensitive data. There’s been no easy way to solve these issues, particularly with a remote or hybrid workforce.
Most organizations have been waiting for a better way.
A better solution: Sophos Workspace Protection
Sophos Workspace Protection provides a unique and elegant solution to the challenge of protecting remote and hybrid workers. It integrates all the network security components needed to secure apps, data, workers, and guests – wherever they are – into a single easy-to-use and familiar app: a hardened Chromium browser.
Sophos Workspace Protection includes:
- Sophos Protected Browser – a new secure Chromium web browser powered by Island.io that provides several security features, including control over app usage, local data controls, and web filtering, and that is hardened against exploits and attacks. It also integrates Sophos ZTNA for access to web apps and rich SSH and RDP support.
- Sophos ZTNA – now integrated into Sophos Protected Browser, it can be used agentless or with a thin agent as before. It also works with Sophos Endpoint to provide device posture assessment and Synchronized Security Heartbeat to define device health as part of access policies. Existing Sophos ZTNA customers will automatically get access to the full Sophos Workspace Protection bundle and all the added benefits it provides.
- Sophos DNS Protection for Endpoints – provides an additional layer of web protection across all apps, ports, and protocols on your remote Windows devices with added visibility, security, and privacy with DNS over HTTPS.
- Email Monitoring System – a Sophos email solution that deploys alongside Google or Microsoft email solutions to monitor email traffic and provide additional insights, analysis, and detections of unwanted or malicious email, including phishing attacks.
Much easier and more affordable than alternatives
Sophos Workspace Protection provides significant advantages over alternative SASE or SSE cloud-delivered solutions, including:
- Affordability: With no expensive cloud infrastructure or traffic management, Sophos Workspace Protection enables you to get more from your security budget.
- Efficiency and performance: There’s no backhauling traffic or man-in-the-middle decryption in the cloud to slow your users down.
- Management overhead: Having a single app to protect all other online apps – private apps, SaaS apps, web apps – reduces day-to-day IT efforts. Plus, it’s simple to add and remove users – including contractors or workers using unmanaged devices.
- Security: Sophos Workspace Protection transforms the browser from a security liability into a key security asset.
- Universality: It works everywhere – on or off the network.
Sophos Workspace Protection is the ultimate solution for remote or hybrid workers – nothing is easier or more affordable.
When is it available
Sophos Workspace Protection will be released in late February. If you have a current project, your local Sophos representative can help you get a quote from Sophos today, and Sophos Protected Browser and Sophos DNS Protection for Endpoints are available now in Early Access.
Details:
- Sophos Protected Browser and DNS Protection for Endpoints are available in early access via Sophos Central. If you’re already a Sophos customer, you can simply log into your Sophos Central account to get started. Note, you must have a licensed Sophos product to access the program. Please provide your feedback via the Sophos Community.
- Sophos ZTNA will be included with Sophos Workspace Protection from the general availability date (GA). Existing Sophos ZTNA customers will get full access to the new Workspace Protection bundle capabilities, including Sophos Protected Browser, Sophos DNS Protection for Endpoints, and Sophos Email Monitoring System. If you’re not already a ZTNA customer, you can start a free trial within Sophos Central, or sign up for a free trial Sophos Central account.
- Sophos Email Monitoring System is available now as a free trial in Sophos Central. Sophos customers can activate a trial directly within the Sophos Central console. If you don’t already have a Sophos Central account, get started here.
- A free trial option for Sophos Workspace Protection will be available from GA in late February.
Licensing and purchase options
Sophos Workspace Protection bundles four tightly integrated products into a single high-value bundle licensed on a simple per-user basis.
- Sophos Protected Browser
- Sophos ZTNA
- Sophos DNS Protection for Endpoints
- Sophos Email Monitoring System
The components are modular, allowing you to deploy just what you need.
Sophos Workspace Protection is available on term subscriptions or via monthly MSP Flex, making it an ideal choice for any size of organization.
Sophos customers get even more value
Sophos Workspace Protection is the ideal complement to Sophos Endpoint, Sophos MDR, and Sophos Firewall – extending and unifying these great products and services to remote and hybrid workers everywhere they go. It also extends Synchronized Security Heartbeat to application access policies for users everywhere. To learn more about Synchronized Security, check out this article.
Partnering with Island.io on Sophos Protected Browser
Sophos has partnered with an industry-leading Enterprise Browser vendor, Island.io, to deliver the Sophos Protected Browser in Sophos Workspace Protection. Island has been developing its Enterprise Browser product since 2000 and is widely recognized for its expertise in this space.
With the Sophos Protected Browser, Island provides the core Chromium browser technology and policy enforcement engine in the browser, while Sophos provides the Sophos Central management, logging, and reporting experience, as well as our industry-leading threat intelligence for web and content inspection.
Source: Sophos
As we enter 2026, the threat of ransomware remains one of the most pressing security challenges facing enterprise organizations, making this a critical time to reassess exposure, preparedness, and resilience.
Sophos’ inaugural report draws on the real-world experiences of 1,733 enterprises that were hit by ransomware in 2025, providing a clear view of the current threat landscape.
The report explores how the causes and consequences of ransomware attacks have evolved, highlights the operational weaknesses that left enterprises exposed, and brings into focus the human impact of incidents, including the sustained pressure placed on IT and cybersecurity teams.
Download the report to explore the full findings.
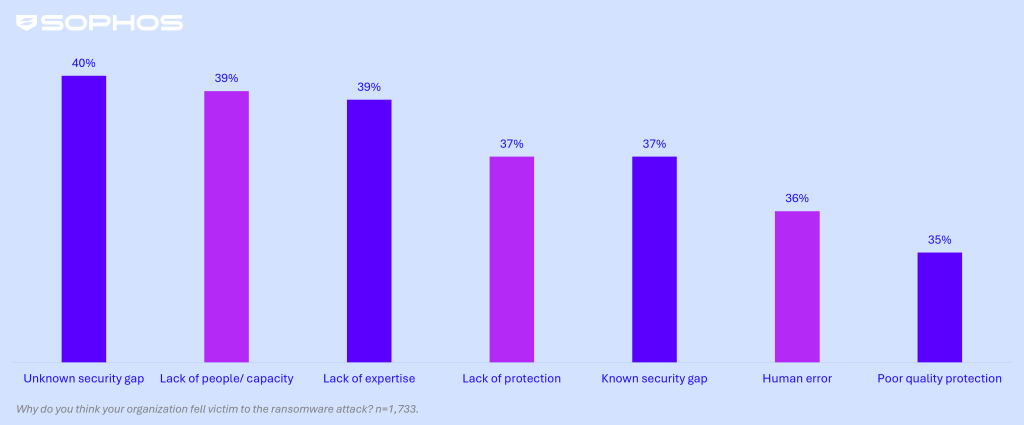
Root cause of attacks: Exploited vulnerabilities and critical operational gaps drive ransomware incidents
Enterprises identified exploited vulnerabilities as the most common technical root cause of attacks, used in 29% of incidents. Phishing and compromised credentials followed behind, each cited in 21% of incidents.
Multiple operational factors contribute to enterprises falling victim to ransomware, with no single issue standing out as the dominant cause. An unknown security gap was cited by 40% of victims, closely followed by a lack of people/capacity and a lack of expertise, both contributing to 39% of attacks.
Interestingly, SMBs (sub 250 employee organizations) also identified a lack of people/capacity as a common factor, with 42% citing it as a key reason for falling victim to an attack, highlighting that resource constraints remain a widespread challenge regardless of organization size.
Operational root cause of attacks in enterprises
Data encryption: Rates drop to all-time low while blocked encryption attempts soar
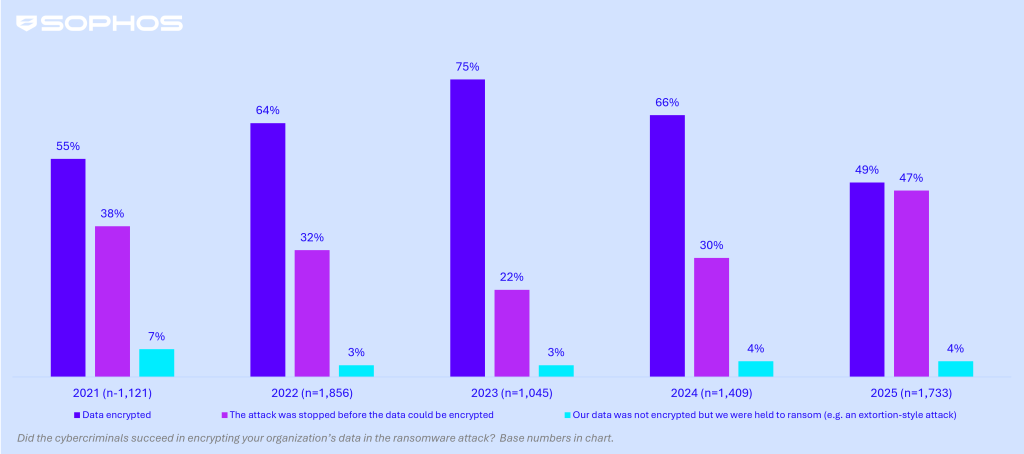
Data encryption in enterprise organizations is at its lowest reported rate in the five years of our survey, with under half (49%) of attacks resulting in data being encrypted down significantly from the 66% reported in 2024. In line with this trend, the percentage of attacks stopped before encryption has more than doubled over the past two years, climbing from 22% in 2023 to 47% in 2025. This suggests that enterprise organizations are becoming far more effective at detecting and stopping attacks before they cause serious damage.
Data encryption in enterprise | 2021 – 2025
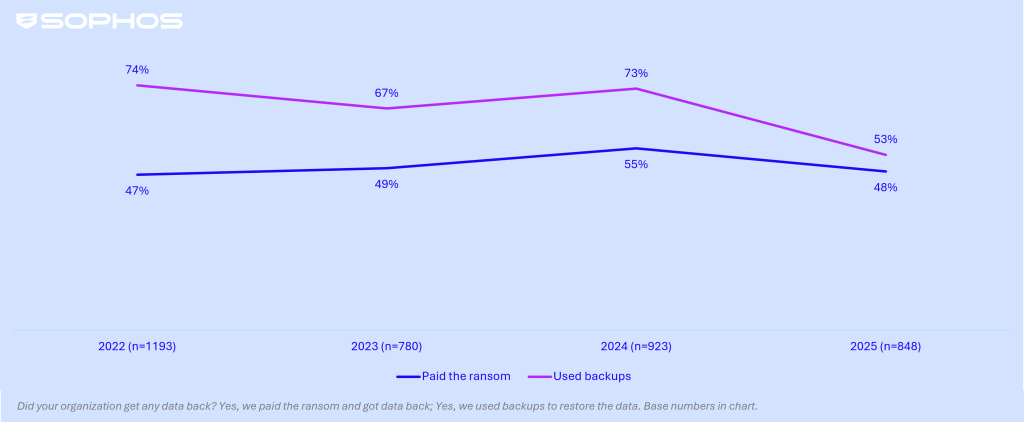
Data recovery: Ransom payment rates remain consistent while backup use plummets to a four-year low
In 2025, close to half (48%) of enterprise organizations paid the ransom to recover data, broadly in line with levels seen over the past four years, indicating little overall change in payment behavior. Meanwhile, the use of backups dropped to a four-year low of 53%, down from 73% the previous year. Collectively, these findings point to stronger resistance to demands alongside underlying weaknesses and reduced confidence in backup recovery capabilities.
Recovery of encrypted data enterprise organizations | 2021 – 2025
Ransom economics: Demands, payments, and attack recovery costs fall
In 2025, ransomware economics across enterprise organizations shifted markedly. Median ransom demands fell by 56% year-over-year, dropping to $1.20 million in 2025 from $2.75 million in 2024. Median ransom payments followed a similar downward trend, declining to $1 million compared with $1.26 million the previous year. Recovery costs also eased significantly, with the mean cost of remediation, excluding any ransom paid, falling to a three-year low of $1.84 million, down from $3.12 million in 2024, indicating a broader reduction in the financial impact of attacks.
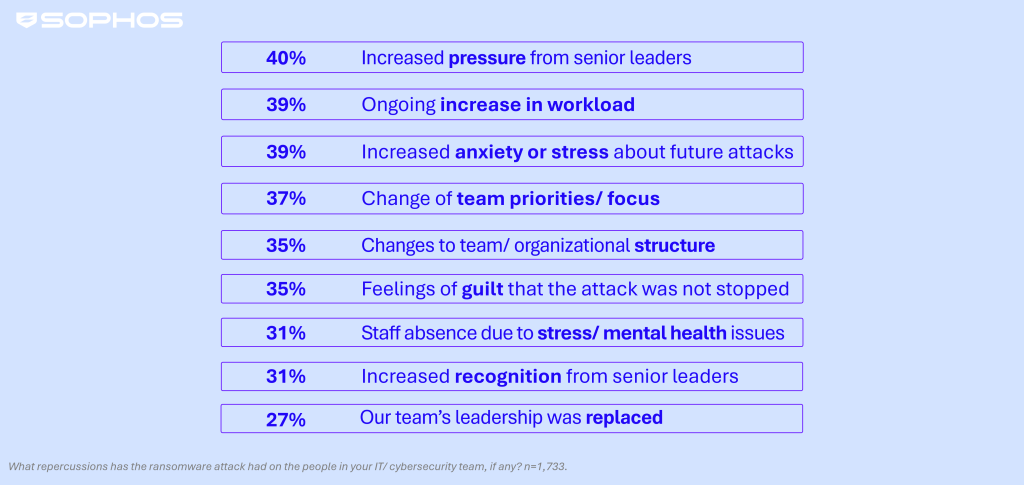
Human impact: Attacks intensify pressure from senior leaders on IT teams
The survey makes clear that having data encrypted in a ransomware attack has significant repercussions for IT/cybersecurity teams, with increased pressure from senior leaders cited by 40% of enterprise respondents. Other repercussions include (but are not limited to):
- Ongoing increase in workload— cited by 39%.
- Change of team priorities/focus — cited by 37%.
- Feelings of guilt that the attack wasn’t stopped — cited by 35%.
Download the full report for more insights into the human and financial impacts of ransomware on enterprise organizations.
Source: Sophos
Ransomware continues to cripple organizations worldwide, draining budgets and halting operations. For IT teams already stretched thin, a single attack can mean days of downtime and irreversible data loss. While endpoint protection often gets the spotlight, your firewall is one of the most powerful tools for stopping ransomware before it starts — and locking it down if attackers breach the perimeter.
Here’s how to configure your firewall to close the gaps ransomware exploits and strengthen your organization’s resilience.
1. Reduce your attack surface
Every exposed service or open port is an opportunity for attackers. Start by minimizing what’s visible to the outside world:
- Consolidate infrastructure. Reduce standalone gateways or VPN concentrators and upgrade to a firewall that integrates secure remote access and Zero Trust Network Access (ZTNA).
- Patch frequently. Unpatched vulnerabilities remain the leading cause of ransomware attacks. Schedule firmware updates monthly and choose vendors like Sophos that deliver automated, over-the-air hotfixes.
- Enforce strong authentication. Enable multi-factor authentication (MFA) for all administrative access and apply role-based controls to limit exposure.
2. Inspect and protect encrypted traffic
Attackers often hide malicious payloads inside encrypted traffic. With more than 90% of network traffic encrypted today, legacy firewalls leave a dangerous blind spot. To close it:
- Enable TLS inspection to decrypt and inspect traffic without slowing performance. Sophos Firewall’s Xstream DPI engine intelligently inspects only relevant streams.
- Use AI-driven threat detection and sandboxing to stop zero-day ransomware before it executes.
- Apply Intrusion Prevention System (IPS) policies to all network flows — not just inbound traffic — to catch attackers moving laterally.
Once you’ve eliminated blind spots in encrypted traffic, the next step is controlling access. That’s where zero trust principles come in.
3. Apply zero trust principles
Firewalls have evolved beyond simple traffic control — they’re now the backbone of a zero-trust architecture, ensuring every user and device is verified before access is granted:
- Replace remote-access VPNs with ZTNA to verify user identity and device health before granting access.
- Micro-segment applications and use VLANs to isolate users, servers, and IoT devices.
- Integrate with endpoint protection through Security Heartbeat, so compromised devices can be automatically quarantined.
4. Detect and respond automatically
Even the best defenses can be bypassed, so early detection and rapid response are critical:
- Implement Network Detection and Response (NDR) to analyze encrypted metadata and detect anomalies. Sophos Firewall’s integrated NDR Essentials identifies threats hiding in encrypted traffic.
- Use Active Threat Response to automatically isolate compromised hosts across endpoints, switches, and wireless networks.
- For 24/7 protection, integrate with Managed Detection and Response (MDR) so expert analysts can detect and contain ransomware before encryption starts.
5. Harden and monitor continuously
Ransomware thrives on gaps in configuration and visibility. Keep your firewall secure by design:
- Disable unnecessary services and management access from the WAN.
- Use geolocation and reputation-based blocking to deny traffic from high-risk regions.
- Send firewall logs and alerts to Sophos Central or your SIEM to maintain full visibility and automate response actions.
Modern firewalls like Sophos Firewall turn static network security into adaptive defense. By implementing these five practices, IT teams can reduce complexity, close critical gaps, and future-proof their organization against ransomware.
Source: Sophos
In today’s threat landscape, stolen credentials are one of the most common causes of data breaches. A recent report found that 61% of all breaches involve the misuse of credentials. Attackers use tactics like phishing and “push-bombing” (rapid-fire MFA push notifications) to trick users into giving away access. Just one compromised password or an accidentally approved login can let an attacker impersonate a legitimate user and infiltrate an organization’s network.
When I was a CISO with a large firm, I witnessed firsthand how a single stolen password could wreak havoc. In that incident, an attacker phished an employee’s credentials and quietly accessed sensitive systems for weeks before detection. The breach caused significant downtime and compliance headaches. After helping contain the damage, I worked with the company’s IT team to harden their identity controls—rolling out MFA to all users, tightening admin account policies, and implementing continuous monitoring. This experience underscored that strong credential security habits aren’t just best practices on paper, but real safeguards against incidents we hope to never face again.
To defend against credential abuse, organizations should cultivate “healthy habits” in identity security. In this blog, I’ll outline five essential security habits to help prevent credential breaches – and discuss how to evaluate capabilities that support each habit.
1.Implement Muti-factor authentication everywhere
One of the most effective defenses against credential attacks is multi-factor authentication (MFA). Stolen passwords alone are often not enough to breach an account if a second factor (like an authenticator app prompt or token) is required. In fact, Microsoft observed that 99.9% of compromised accounts did not have MFA enabled. The absence of MFA has been a common factor in many high-profile breaches – compromised credentials combined with lack of MFA were a shared denominator in multiple major breaches in 2024/25.
Enabling MFA for all users (especially administrators) can shut down the vast majority of opportunistic attacks that rely on stolen or guessed passwords.
Despite these benefits, many accounts still lack MFA protection. Why? Often there’s a misconception that MFA adds too much friction or that it “isn’t worth it.” Some IT teams face user pushback or lack executive support, and thus aren’t incentivized to enforce universal MFA. In other cases, organizations simply haven’t extended MFA to certain systems or legacy applications, leaving gaps by accident. The reality is that while basic MFA isn’t infallible, it stops the vast majority of automated attacks cold – making it a fundamental habit for credential security.
That said, not all MFA is equal. Attackers increasingly exploit MFA fatigue by bombarding users with repeated push notifications (so-called push-bombing). Given that people receive 60–80 mobile push notifications each day on average, it’s easy for a fatigued user to accidentally tap “Approve” on a fraudulent login prompt. To counter this, organizations should implement phishing-resistant MFA (such as FIDO2 security keys or number-matching push prompts) and educate users to never approve unexpected access requests.
It’s also essential to find solutions that help your team extend MFA protection to every resource and protocol in an environment, including systems that don’t natively support MFA. This means you should enforce MFA not just on web and cloud applications, but even on legacy on-premises systems (databases, file servers, command-line tools, etc.) that traditionally were unable to leverage MFA. By making MFA ubiquitous and difficult to bypass, you dramatically reduce the risk of a single stolen password leading to a breach.
2.Adopt a Zero Trust approach to identity
Implementing a “Zero Trust” mindset for identity is a healthy habit that goes hand-in-hand with MFA. In a Zero Trust model, no login or user session is implicitly trusted – even if the user is on the internal network or already authenticated. Every access attempt is continuously verified based on context (user role, device security, location, time, etc.) before granting access. This is vital because modern enterprises have dissolved perimeters; identity is now the new attack surface in cybersecurity. With users logging in from everywhere and attackers adept at blending in with normal user activity, it’s crucial to “never trust, always verify” each credential use.
Practicing this habit means leveraging conditional access policies and continuous monitoring for all accounts. For example, if a user suddenly logs in from an unusual location or an unmanaged device, additional verification or restrictions should kick in. Many breaches could be prevented by such context-aware controls – one investigation found that hundreds of stolen credentials remained useful to attackers simply because the target systems did not have location-based access policies to block logins from untrusted networks.
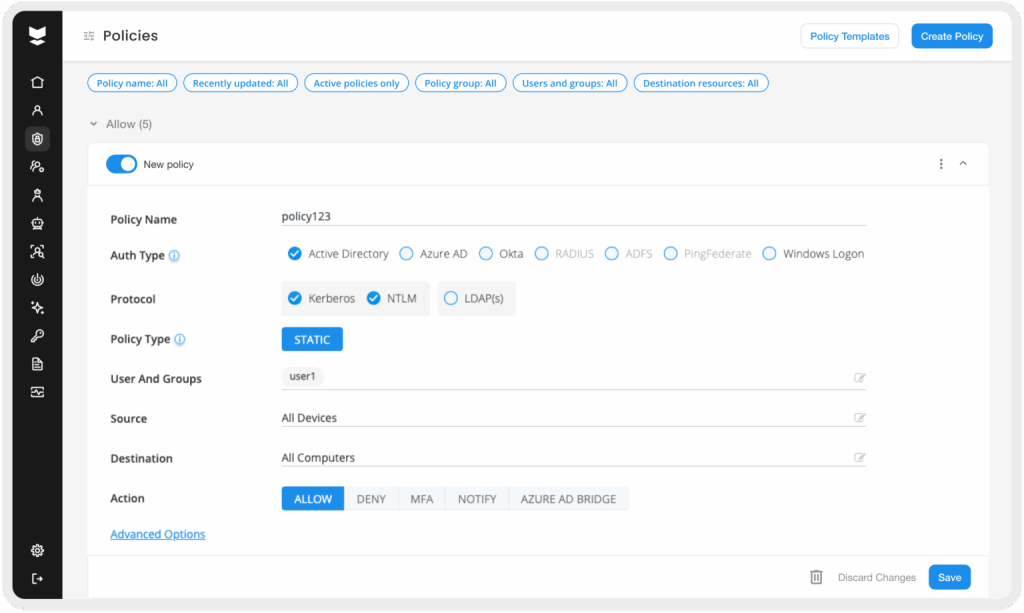
Modern identity security platforms continuously monitor every authentication and apply risk-based policies. If a login attempt deviates from normal behavior or occurs under high-risk conditions, the proper approach would be to require step-up authentication (like MFA) or even block the attempt. By treating every access as untrusted until proven otherwise, organizations can contain and thwart attackers who manage to acquire valid credentials.
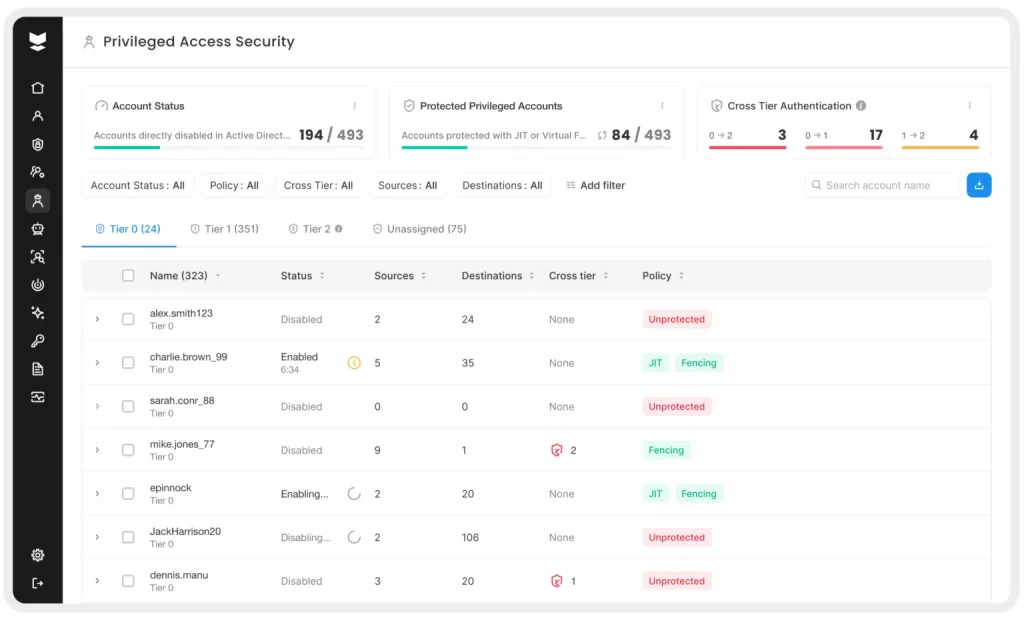
3. Secure privileged and high-risk accounts with extra care
All user accounts are important to protect, but privileged accounts (administrators, service accounts, executives, etc.) deserve prioritized attention as a healthy security habit. These accounts often have broad access and, if compromised, can inflict serious damage. Unfortunately, I see many incidents where admins or other powerful accounts were left under-protected. In a recent example, a government organization was breached via a former administrator’s account – the account had retained high privileges and did not have MFA enabled. Similarly, the fallout from a 2024 cloud breach (targeting Snowflake customers) revealed that some demo and service accounts lacked SSO or MFA protection, providing an easy target for attackers. The lesson is clear: any account with elevated access should be strongly secured with multiple layers of defense.
As a habit, organizations should enforce strict Privileged Access Security (PAS) practices. This includes using dedicated admin accounts (separate from everyday user accounts), requiring MFA on every privileged login, limiting where and when these accounts can be used, and continuously auditing their activity.
In practice, this looks like ensuring admin-level accounts are always challenged with MFA and policy checks, even when they’re accessing systems like databases or remote servers that don’t normally enforce MFA. You can also implement adaptive policies (for instance, only allow domain admin login from a hardened jump-host, or only during certain hours).
For non-human privileged accounts (like service accounts that can’t do MFA), there is the concept of “virtual fencing” – essentially bounding their usage to expected systems and behaviors. By locking down privileged and sensitive accounts in these ways, you greatly reduce the odds that an attacker with a stolen admin credential can roam freely in your environment.
4. Maintain rigorous credential hygiene
Credential hygiene refers to the regular upkeep of accounts and passwords to eliminate the “low-hanging fruit” that attackers often exploit. A sobering case study from 2024 showed why this habit is so important: investigators found that 79.7% of the accounts used by attackers had been compromised years earlier and never had their passwords changed. In fact, hundreds of credentials stolen as far back as 2020 were still valid in 2024 because they were never rotated or disabled. Neglected credentials – old passwords, shared logins, dormant accounts – are a ticking time bomb. Implementing strong hygiene means regularly rotating passwords, retiring or updating any credential that is known to be exposed, and disabling accounts that are no longer needed.
Another critical aspect of credential hygiene is prompt offboarding of ex-employees. Stale user accounts that linger after someone leaves the company present an easy backdoor. Surveys have found that roughly half of businesses admit ex-employees’ accounts remain active after departure, sometimes for weeks or months. It’s no surprise that a significant number of organizations have suffered breaches due to former employee accounts that weren’t deprovisioned. Make it a habit to immediately deactivate or remove access when staff leave, and routinely audit for any “ghost” accounts in your directory.
A strong method to audit hygiene is to ensure continuous visibility into all accounts (human and non-human) and their usage. Being able to automatically discover accounts in your environment – including service accounts and unused logins – and flag those that have been inactive for a long period as “stale users” helps make sure you have an ongoing inventory of the identities that exist. Security teams can then swiftly review and either remove these accounts or apply policies to block any access attempts using them.
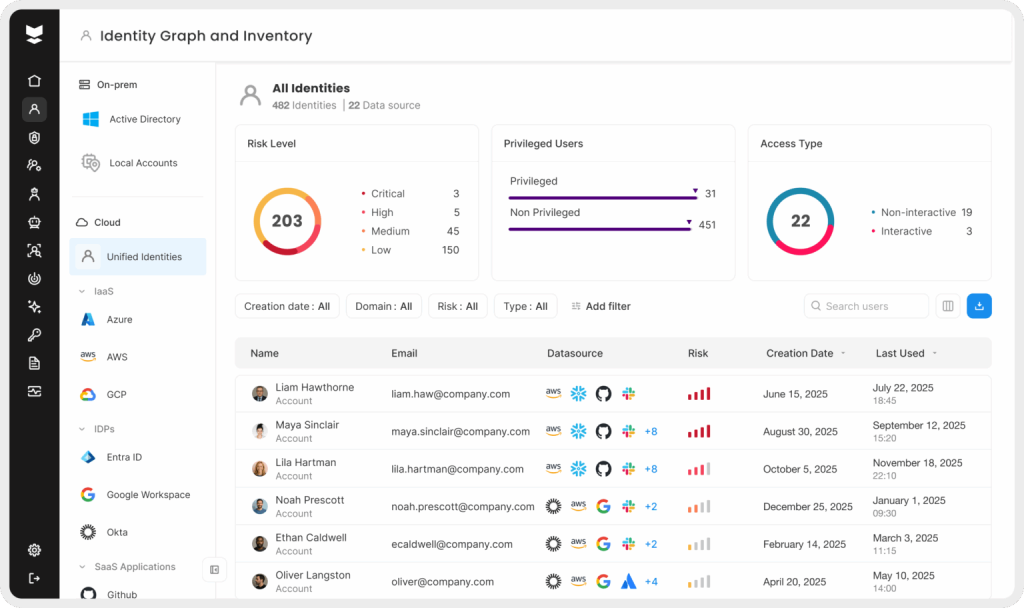
This kind of identity inventory and cleanup is vital: it closes the door on one of the easiest paths attackers use to infiltrate networks. In short, keeping credentials fresh, tightly managed, and cleaned up will drastically limit what an attacker can leverage, even if they do obtain some login secrets.
5. Continuously monitor and respond to identity threats
Even with preventive measures like MFA and good hygiene, organizations should operate under the assumption that credential compromises can still happen. Thus, a “healthy” security posture includes robust detection and response focused on identity.
Traditional security tools like XDRs may struggle to catch an attacker using legitimate credentials – these actions often blend in with normal user behavior and fly under the radar. It’s crucial to habitually monitor authentication logs and user activities across all systems for signs of suspicious behavior, and to retain those logs for long enough to investigate incidents. In fact, maintaining a centralized log collection with a proper retention policy is considered a basic security must-have to discover and analyze credential attacks. Many breaches that went undetected for months (or years) could have been identified much earlier if organizations had been aggregating login audit trails and alerting on anomalies.
To make this habit feasible, leverage tools that provide unified visibility and smart analytics on identity events. Silverfort’s platform, for example, acts as a centralized brain for monitoring all authentication traffic in real time. It uses machine learning and behavioral analytics (UEBA) to detect when a user’s access patterns deviate from the norm, which can indicate a compromised account. If an employee’s account suddenly attempts logins in strange locations or tries to access unusual resources, Silverfort will flag or automatically block that activity, preventing the attacker from escalating further. Moreover, Silverfort’s console gives security teams a live identity inventory and activity feed, so they can quickly spot and investigate any suspicious account usage.
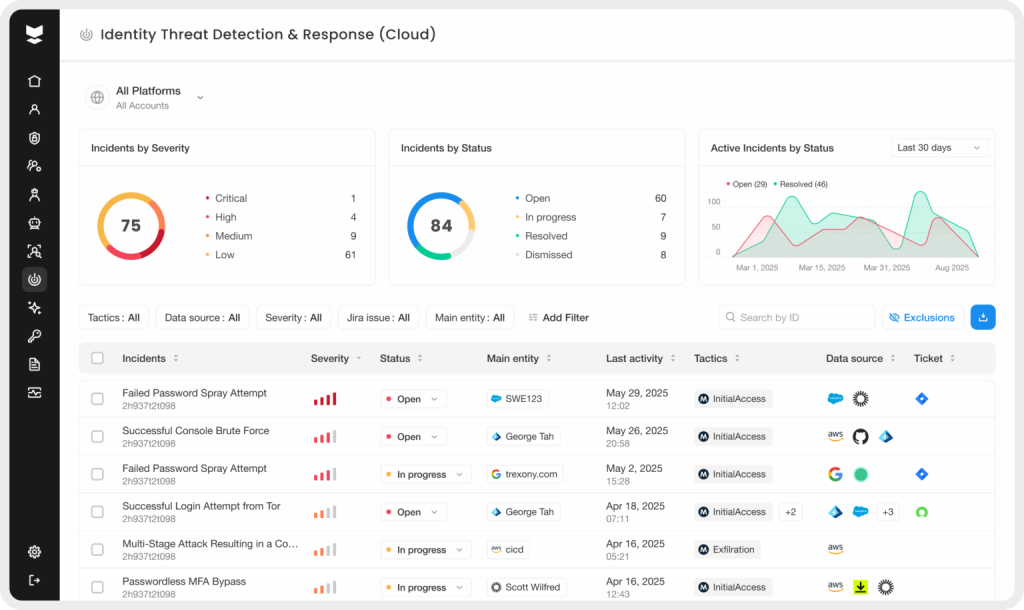
Cultivating this level of awareness – and rehearsing incident response plans for credential breach scenarios – ensures that even if one defensive layer fails, you can promptly detect and contain the threat before it mushrooms into a full-blown breach.
Taking action on the 5 essential habits
Credential breaches continue to be a top cyber threat, but adopting these five security habits can significantly strengthen your organization’s defenses.
By requiring MFA universally, treating every access attempt with Zero Trust, locking down high-impact accounts, keeping your identity store clean, and monitoring continuously, you create multiple layers of protection that attackers must overcome.
None of these habits are “set and forget” – they require ongoing diligence and the right tools to support them.
This is where unified, identity-first security platforms can be a game-changer.
They’re purpose-built to help you embed these healthy security practices into your environment: enforcing MFA and conditional access everywhere, safeguarding privileged and legacy accounts, illuminating blind spots like stale users, and continuously watching for threats.
With strong habits and identity-first security capabilities working in tandem, enterprises can dramatically reduce the risk of credential-based breaches and ensure that a stolen password never easily translates into a successful attack.
To learn more about how to put incorporate these healthy habits into your cybersecurity strategy, download our guide “The Identity Security Playbook.”
Source: Silverfort
MITRE ATT&CK® Evaluations are among the world’s most rigorous independent security tests. They emulate the tactics, techniques, and procedures (TTPs) used by real-world adversaries to assess each participating vendor’s ability to detect, analyze, and articulate threats in alignment with the MITRE ATT&CK® Framework. These evaluations continually strengthen our capabilities, for the benefit of the organizations we protect.
The results are in – drum roll, please!
MITRE has released the results of the latest ATT&CK® Evaluation for enterprise security solutions, assessing how participating EDR and XDR products, including Sophos XDR, detect and report the complex tactics of advanced threat groups.
We’re excited to share that we achieved our best-ever results in this evaluation round. Sophos’ consistently strong performance in these evaluations — year after year — continues to demonstrate the power and precision of our threat detection and response capabilities. In the Enterprise 2025 Evaluation, Sophos XDR:
- Successfully detected all 16 attack steps and 90 sub-steps, demonstrating the power of our open AI-native platform to defend against sophisticated cyber threats.
- 100% detection1: Sophos detected and provided actionable threat detections for all adversary activities — zero misses.
- Highest possible scores: Sophos generated full Technique-level detections for 86 of the 90 adversary activities evaluated.
Watch this short video for an overview of the evaluation, then read on for a closer look at the results:
Evaluation overview
This was the seventh round of the “Enterprise” ATT&CK Evaluation — MITRE’s product-focused assessment — designed to help organizations better understand how security operations solutions like Sophos EDR and Sophos XDR can help them defend against sophisticated, multi-stage attacks.
The evaluation focused on behaviors inspired by the following threat groups:
- Scattered Spider: A financially motivated cybercriminal collective
The MITRE team emulated this group’s use of social engineering to steal credentials, deploy remote access tools, and bypass multi-factor authentication — targeting cloud resources to establish footholds and access sensitive systems and data. The scenario included Windows and Linux devices and, for the first time, AWS cloud infrastructure. - Mustang Panda: People’s Republic of China (PRC) espionage group
A PRC state-sponsored cyber espionage group known for using social engineering and legitimate tools to deploy custom malware. The MITRE team emulated its tactics and tools, reflecting behaviors commonly seen across the broader PRC cyber operations ecosystem.
Results in more detail
In this evaluation, MITRE executed two discrete attack scenarios — one for Scattered Spider and one for Mustang Panda — comprising a total of 16 steps and 90 sub-steps. Sophos delivered impressive results in both scenarios.
Attack scenario 1: Scattered Spider
Summary: A complex hybrid intrusion involving social engineering, cloud exploitation, identity abuse, and living-off-the-land techniques. The adversary uses spear phishing to steal credentials and gain remote access, then performs network discovery, accesses the victim’s AWS environment, evades defenses, and exfiltrates data to their own S3 bucket using native AWS tools.
This attack scenario comprised 7 steps with 62 sub-steps across Windows, Linux, and AWS.
- 100% of sub-steps detected1. Zero misses.
- Actionable threat detections generated for every sub-step.
- Highest possible Technique-level ratings achieved for 61 out of 62 sub-steps.
Attack scenario 2: Mustang Panda
Summary: An evasive intrusion demonstrating the adversary’s use of social engineering, legitimate tools, persistence, and custom malware to evade detection. It begins with a phishing email carrying a malicious DOCX that provides access to a Windows workstation and connects to a C2 server. The attacker discovers key systems, exfiltrates data, and removes their tooling to cover their tracks.
This attack scenario comprised 9 steps with 28 sub-steps on Windows devices.
- 100% of sub-steps detected1. Zero misses.
- Actionable threat detections generated for every sub-step.
- Highest possible Technique-level ratings achieved for 25 out of 28 sub-steps.
Learn more at sophos.com/mitre and explore the full results on the MITRE website.
What do the ratings mean?
Each adversary activity (or “sub-step”) emulated during the evaluation is assigned one of the following ratings by MITRE, reflecting the solution’s ability to detect, analyze, and describe the behavior using the language and structure of the MITRE ATT&CK® Framework:
Technique (Highest fidelity detection). The solution generated an alert that identifies the adversary activity at the ATT&CK Technique or Sub-Technique level. The evidence includes details on execution, impact, and adversary behavior, providing clear who, what, when, where, how, and why insights.
-
- Sophos achieved this (highest possible) rating for 86 out of 90 sub-steps.
Tactic (Partial detection with context). The solution generated an alert that identifies the adversary activity at the Tactic level but lacks Technique-level classification. The evidence includes details on execution, impact, and adversary behavior, providing clear who, what, when, where, and why insights.
-
-
- Sophos received this rating for 1 sub-step.
-
General. The solution generated an alert that identifies the adversary activity as potentially suspicious or malicious. The evidence includes details on execution, impact, and adversary behavior, providing clear who, what, when, and where insights.
-
- Sophos received this rating for 3 sub-steps.
None (No detection, potential visibility). Execution of the adversary activity was successful; however, the solution did not generate an alert, failing to identify adversary activity as potentially suspicious or malicious.
- Sophos did not receive this rating for any sub-steps. Zero misses.
Not Assessed (N/A). The evaluation was not performed due to technical limitations, environmental constraints, or platform exclusions.
Detections classified as General, Tactic, or Technique are grouped under the definition of analytic coverage, which measures the solution’s ability to convert telemetry into actionable threat detections.
Interpreting the results
There’s no single way to interpret the results of ATT&CK® Evaluations and MITRE does not rank or rate participants. The evaluations simply present what was observed — there are no “winners” or “leaders.”
Each vendor’s approach, tool design, and presentation of data differ, and your organization’s unique needs and workflows ultimately determine the best fit for your team.
Detection quality is key to giving analysts the insight they need to investigate and respond quickly. One of the most valuable ways to interpret the results of ATT&CK® Evaluations is by reviewing the number of sub-steps that produced rich, detailed detections of adversary behavior (analytic coverage) with those that achieved the highest fidelity “Technique”-level coverage.
Once again, Sophos delivered an exceptional performance in this evaluation.
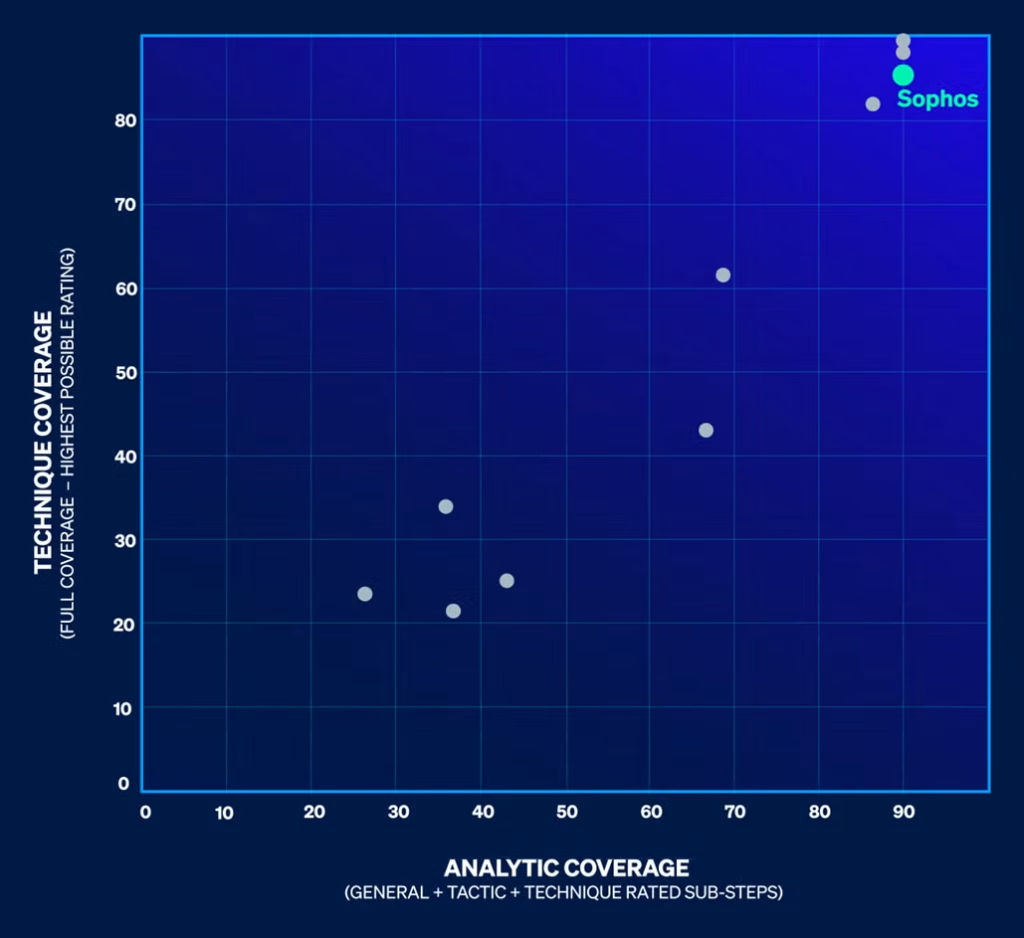
Sophos’ consistently strong performance in these rigorous evaluations underscores the power and precision of our threat detection and response capabilities — and our commitment to stopping the world’s most sophisticated cyberthreats.
When considering an EDR or extended detection and response (XDR) solution, remember to review the results from MITRE ATT&CK Evaluations alongside other reputable independent proof points, including verified customer reviews and analyst evaluations.
Recent recognitions for Sophos EDR and Sophos XDR include:
- Sophos named a Leader in the IDC MarketScape: Worldwide Extended Detection and Response (XDR) Software 2025
- Sophos named a Leader in the G2 Fall 2025 Reports for both EDR and XDR
- Sophos named a 2025 Gartner® Peer Insights™ “Customers’ Choice” vendor for Extended Detection and Response (XDR)
- Sophos named a Leader for the 16th consecutive time in the 2025 Gartner® Magic Quadrant™ for Endpoint Protection Platforms
Get started with Sophos XDR today
Sophos’ consistent strong results MITRE ATT&CK Evaluations help to validate our position as an industry-leading provider of endpoint detection and response (EDR) and extended detection and response (XDR) capabilities to over 45,000 organizations worldwide.
To see how Sophos can streamline your security operations and drive superior outcomes for your organization, visit our website, start a free trial of Sophos XDR, or speak with an expert.
To learn more about the results of this evaluation, visit sophos.com/mitre.
Source: Sophos
NVIDIA recently published a powerful framework: “The AI Kill Chain,” mapping how attacks against AI-powered applications unfold. It’s one of the clearest attempts yet to bring structure to an increasingly chaotic security frontier. The framework shows how adversaries move from reconnaissance and data poisoning to exploitation and command and control, giving security teams a common language for understanding AI-specific threats.
What makes this valuable is that it mirrors the maturity curve we saw in traditional cybersecurity. Once we learned to model how attackers think, we could design defenses that anticipate rather than react. But as AI systems evolve from passive models to autonomous agents, we’re facing something new: these agents carry credentials, access sensitive resources, and act on behalf of users – yet their behavior is far less predictable than any human. That’s why identity has to be the focus. Not just what the agent can do, but who it’s acting as, and under whose authority.
The shift from systems to actors
In conventional architectures, systems process inputs. In AI-driven environments, they act.
AI agents query databases, send messages, trigger workflows, and sometimes make policy decisions. They are, in effect, new actors in the enterprise. Each one operates under an identity that carries credentials, permissions, and behavioral patterns.
That identity is what turns an AI system from a model into an agent. And just like human users or service accounts, those identities can be hijacked, over-permissioned, or left unmonitored. This changes how we interpret every phase of the kill chain.
Reconnaissance isn’t just about mapping systems. It’s about discovering which agents exist, what they can access, and who they represent.
Exploitation happens when an attacker manipulates an agent’s logic to perform a legitimate action with illegitimate intent.
Command and Control shifts from remote access to delegated control, using the agent’s trusted identity to operate invisibly inside the environment.
The moment we view AI attacks through the lens of identity, the problem changes. Instead of asking “How do we protect the model?” we should be asking “How do we govern who the model acts as?”
A scenario in motion
Imagine an AI assistant in finance built to reconcile invoices. It’s integrated with payment systems and given credentials to approve small transactions automatically. A malicious prompt subtly changes the logic that defines “small,” and the agent begins approving larger transfers. All within its allowed permissions.
No anomaly detection flags it, because nothing technically breaks policy. The breach doesn’t come from model failure. It comes from identity misuse. The system was doing exactly what it was allowed to do, but under the wrong judgment.
This is where identity becomes the connective tissue across the AI Kill Chain. Each phase (reconnaissance, exploitation, and control) depends on visibility into who or what is acting, under whose authority, and within what boundaries.
Turning the kill chain into a trust chain
Identity security brings disciplines that map directly to AI defense: least privilege, continuous authentication, behavioral baselines, and traceable attribution. Together, they turn reactive controls into proactive assurance. I’d call this a trust chain for AI.
In that chain:
- Every agent has a defined owner and purpose
- Every action carries context: who initiated it, on whose behalf, and within what scope
- Every deviation from expected behavior can be observed, audited, and governed
By connecting lifecycle-based models like the AI Kill Chain with identity-aware controls, we start to close the loop between how attacks unfold and who enables them to unfold.
Looking forward
Over time, identity will become the organizing layer for AI governance. Just as we once centralized access management for human users, we’ll soon do the same for AI agents. We’ll be defining, monitoring, and authenticating every digital actor in the enterprise.
The AI Kill Chain helps us see how adversaries move.
Identity tells us who they move through.
Bringing those two perspectives together is how we turn AI from an opaque system into a trustworthy one. Not by slowing innovation, but by making accountability scalable.
Want to see what this looks like in practice? Read our breakdown of GTG-1002, the first documented agentic cyber campaign – and what it signals for defenders.
Source: Silverfort
Modern MSPs are being asked to do more than ever: support more endpoints, respond faster, retain talent and stay profitable. The challenge is doing all of that without drowning in tool sprawl, ticket volume and constant context switching that slows technicians down and frustrates customers.
That’s exactly what we tackled in the webinar, “12 questions to modernize your MSP operations.” Kaseya’s Abel Concepcion and MSP industry veteran Eric Simpson shared a real-world view of what modernization looks like across the service desk — from day-to-day efficiency improvements to the operational habits that help MSPs scale without chaos.
This session was structured around the IT operations modernization scorecard, a self-assessment built on 12 questions designed to evaluate how modern and scalable your operations really are. The scorecard helps you identify strengths, uncover gaps and prioritize next steps based on the potential biggest impact. You can also watch the full webinar recording here.
Takeaway 1: Disconnected tools quietly tax your margins
When your PSA, RMM and documentation live in separate worlds, technicians don’t spend their time solving problems — they spend it hunting for context.
That “in-between time” adds up fast:
- More clicks, switching and copy-and-paste
- Slower resolution times
- More escalations (because techs don’t have what they need)
- Lower customer satisfaction and lower technician morale
One of the strongest points from the session: integration isn’t just about convenience — it’s about cost control. The more seamlessly systems share context, the faster your team can move from alert to ticket to resolution without losing time (or details) along the way.
To resolve this issue, identify the top three places technicians lose time today (device context, passwords, SOPs, contract/billing fields, prior notes, etc.). Then, prioritize integrations that remove the biggest friction first.
Takeaway 2: Better dashboards = better days
How technicians start their day shapes how they finish it. When work sits in generic queues without clear assignment rules, it can lead to ticket cherry-picking, inconsistent prioritization and missed SLAs.
Modern operations use automation to ensure:
- Work is assigned based on the rules you define (priority, impact, client tier, skill set, etc.)
- Techs focus on execution, not constant decision-making
- Service managers get visibility into workload and bottlenecks
Move from “watch the queue” to rules-based assignment and role-based dashboards so the right work reaches the right person automatically.
Takeaway 3: AI works best when it’s embedded — and backed by real data
AI isn’t magic. It’s only as effective as the information you feed it. The webinar highlighted that the biggest gains come when AI is embedded directly into daily workflows, not treated as a separate tool.
For example:
- Summarizing ticket activity so escalations don’t start from scratch
- Flagging missing triage details
- Helping generate SOP-style documentation from real work performed
None of this works unless technicians consistently log clear notes and updates in the ticket. AI can only add value when your process is solid and your data is complete. A simple rule to reinforce is: if it’s not in the ticket, it didn’t happen — especially before escalations or vendor handoffs.
Takeaway 4: Process isn’t rigidity — it’s clarity
When the process breaks down, the symptoms are obvious:
- Everyone “fires from the hip”
- Service quality varies by technician
- Performance is hard to measure fairly
- Customers wait for their “favorite tech” instead of accepting the next available resource
As Eric Simpson bluntly put it, in the absence of process, people do what they think is right, which may not align with what the business needs.
Standardizing how work flows through the service desk creates consistent outcomes across the board. Issues are handled the same way, escalations follow a clear path, resolution steps are documented instead of improvised and automation runs on rules you can trust (not guesswork).
Takeaway 5: Documentation can’t be optional — and tribal knowledge doesn’t scale
Relying on what’s “in someone’s head” creates fragility. When documentation isn’t centralized and actively used:
- New hires ramp slowly
- Tickets take longer when your best techs are unavailable
- Teams repeat troubleshooting steps they’ve already solved
- Customers get inconsistent outcomes
The webinar also called out a cultural truth: most techs don’t love documenting, especially when they’re slammed. That’s why the right approach is to make documentation easier to create, easier to find and harder to ignore, with shared standards and accountability. To get started, standardize where documentation lives, how it’s named, who owns updates and how techs are expected to reference it during ticket work.
Takeaway 6: The best MSPs modernize through evolution, not revolution
You don’t modernize by rebuilding everything at once. High-performing MSPs:
- Review and refine regularly
- Fix the biggest bottleneck first
- Measure outcomes (SLA attainment, resolution time, utilization, CSAT)
- Build alignment with weekly team rhythms
Modernization isn’t a one-time project. It’s a habit.
Ready to benchmark your MSP operations?
If you’re unsure where to start, use the same framework the webinar is based on: the IT operations modernization scorecard. It includes 12 questions designed to highlight where your operations are strong today, and where modernization will deliver the biggest impact.
Source: Datto
The product team is pleased to announce that Sophos Firewall v22 is now generally available. This update brings several Secure by Design enhancements and many of your top requested features.
Secure by Design
Over the last several weeks, we’ve covered the importance of Secure by Design principles and why we need secure products as much as we need security products. Sophos Firewall v22 builds on the many security and hardening enhancements from previous releases to take Secure by Design to whole new level.
Watch this video for a quick overview of what’s new:
Sophos Firewall Health Check
A strong security posture depends on ensuring your firewall is optimally configured. Sophos Firewall v22 makes it much easier to evaluate and address the configuration of your firewall with the new Health Check feature.
This new feature evaluates dozens of different configuration settings on your firewall and compares them with CIS benchmarks and other best practices, providing immediate insights to areas that may be at risk. It will identify all high-risk settings and provide recommendations with quick drill-down to the areas of concern so you can easily address them.
The Health Check status is displayed on a new Control Center widget and a full report is available under the “Firewall health check” main menu item.
Other Secure by Design enhancements
Next-Gen Xstream architecture
 Introducing an all-new control plane re-architected for maximum security and scalability that will take us into the future. The new control plane enables modularization, isolation, and containerization of services like IPS for example, to run like “apps” on the firewall platform.
Introducing an all-new control plane re-architected for maximum security and scalability that will take us into the future. The new control plane enables modularization, isolation, and containerization of services like IPS for example, to run like “apps” on the firewall platform.
It also enables complete separation of privileges for added security. In addition, high-availability deployments now benefit from a self-healing capability that is continuously monitoring system state and fixes deviations between devices automatically.
Hardened kernel
The next-gen Xstream Architecture in Sophos Firewall OS is built upon a new hardened kernel (v6.6+) that provides enhanced security, performance, and scalability.
The new kernel offers tighter process isolation and better mitigation for side-channel attacks as well as mitigations for CPU vulnerabilities (Spectre, Meltdown, L1TF, MDS, Retbleed, ZenBleed, Downfall). It also offers hardened usercopy, stack canaries, and Kernel Address Space Layout Randomization (KASLR).
Remote integrity monitoring
Sophos Firewall OS v22 now integrates our Sophos XDR Linux Sensor that enables real-time monitoring of system integrity, including unauthorized configuration, rule exports, malicious program execution attempts, file tampering, and more.
This helps our security teams – who are proactively monitoring our entire Sophos Firewall install base – to better identify, investigate, and respond more quickly to any attack. This is an added security capability that no other firewall vendor provides.
New anti-malware engine
Sophos Firewall OS v22 integrates the latest Sophos anti-malware engine with enhanced zero-day real-time detection of emerging threats using global reputation lookups.
It takes full advantage of SophosLabs’ massive cloud database of known malicious files, updated every five minutes or less. It also introduces AI and ML model detections and delivers enhanced telemetry to SophosLabs for accelerating their emerging threat detection analysis.
Other security and scalability enhancements:
- Firmware updates via SSL and certificate pinning ensures authenticity
- Active Threat Response logging improvements enhance visibility
- NDR Essentials threat score is included in Logs for added insights
- NDR Essentials data center selection for data residency requirements
- Instant web category alerts for education institutions
- XML API access control enhancements with added granularity
- TLS 1.3 support for device access for the WebAdmin console and portals
Top requested features and quality of life enhancements:
- Enhanced navigation performance
- Hardware monitoring for SNMP with a downloadable MIB
- sFlow Monitoring for real-time visibility
- NTP server settings defaults to “Use pre-defined NTP server”
- UI enhancements for XFRM interfaces with pagination and search/filter options
SG UTM features:
With Sophos UTM coming toward end-of-life soon (July 30, 2026), some migrating customers will appreciate these added features:
- SHA 256 and 512 support for OTP tokens
- MFA support for WAF form-based authentication
- Audit trail logs with before and after tracking to meet the latest NIST standards
Get the full details
Download the full What’s New Guide for a complete overview of all the great new features and enhancements in v22. Also be sure to check out the full release notes documentation.
How to get v22
As with every firewall release, Sophos Firewall v22 is a free upgrade for Sophos Firewall customers with Enhanced or Enhanced Plus Support and should be applied to all supported firewall devices as soon as possible.
With the new architectural changes in v22, this update may require some additional steps for a very small percentage of existing desktop, virtual, or software firewall devices to free added disk space or resize the root partition. If your device requires additional steps this will be noted before you download with a link to instructions for the additional steps.
Review this video for an overview of the different devices and steps that may be required:
A quick summary:
- XGS 2100 and above – no additional steps required
- XGS Desktop Series – 97% will seamlessly upgrade, with 3% requiring a few additional manual steps which will be flagged by an alert
- Virtual/software devices deployed prior to v18 also require additional steps
If your device requires some additional manual steps to upgrade, the alert will advise you of what’s required in-product or via Sophos Central before you download the firmware. The alert will link to the required steps in this KB article: Requirements and resolution to upgrade to v22.
This firmware release will follow our standard staged roll-out process. The new v22 firmware will be gradually rolled out to all connected devices in phases over the coming weeks. A notification will appear on your local device or Sophos Central management console when the update is available, allowing you to schedule the update at your convenience.
Source: Sophos
We’re thrilled to unveil Sophos Intelix for Microsoft 365 Copilot, a powerful new integration that brings world-class threat intelligence from Sophos X-Ops directly into your daily workflow to enhance your cybersecurity outcomes.
Security analysts and IT professionals can instantly access, investigate, and respond to emerging cyber threats right from the Copilot chat interface, without leaving the Microsoft 365 environment, accelerating attack neutralization. This seamless experience transforms threat intelligence from a separate resource into an actionable, always-on ally that accelerates decision-making, strengthens cyber resilience, and fuels more effective collaboration across teams.
Benefits of Sophos Intelix for Microsoft Copilot
- Seamless Access to Threat Intelligence: Security and IT administrators, risk managers, and business users can interact with Sophos Intelix directly using natural language via Copilot chat, submitting artifacts and receiving real-time threat intelligence without leaving the Microsoft 365 ecosystem. This speeds up threat investigation and response, reducing the impact of threats.
- Comprehensive Threat Analysis: Sophos Intelix leverages cloud lookups, static and dynamic analysis, and the power of Sophos X-Ops threat intelligence to deliver detailed, explainable verdicts on files and URLs. This enables users to understand not just whether something is malicious, but why, facilitating faster, informed decision-making.
- Open Access: The agent is available to all Microsoft 365 Copilot users at no charge, democratizing access to world-class threat intelligence.
How to access Sophos Intelix for Microsoft Copilot
The Sophos Intelix Agent is available for free via the Agent Store in Copilot Studio and Teams. The single agent brings all the Sophos Intelix capabilities to Copilot, including:
- Cloud Lookups
- Static Analysis (File and Web)
- Dynamic Analysis
With the chat interface, users can tap directly into the deep, real-time threat landscape insights of Sophos X-Ops. Far surpassing traditional chat-ops integrations, the agent understands natural language queries, delivering actionable, expert-driven answers—so security teams can anticipate, adapt, and neutralize threats faster than ever before.
Democratizing cybersecurity for every organization
Today’s release marks a major milestone in the delivery of Sophos’ broader vision of making Sophos X-Ops data and services accessible through agent-based frameworks. With unmatched breadth and depth of data, include intelligence from SophosLabs and the Sophos managed detection and response (MDR) service, Sophos X-Ops provides security operations center (SOC) analysts with deeper threat visibility – including adversary behaviors, signature and IOC metadata, threat actor attribution, and prevalence insights – all surfaced naturally within the tools that analysts use daily. The result: more empowered analysts, faster attack resolution, and reduced cyber risk.
Ready to transform your cyber defense strategy? Start using Sophos Intelix for Microsoft 365 Copilot today and experience the future of proactive, integrated threat intelligence—right where your teams work every day.
Source: Sophos
We released Sophos DNS Protection for networks last year, and it is now close to serving its 600 billionth query. Since then, many of you have asked for a version that can be used on roaming endpoints and for additional insights into DNS requests along with DNS over HTTPS.
Today, we are excited to launch the early access program (EAP) for DNS Protection on Windows endpoints with enhanced visibility into which users and devices are making DNS queries and support for HTTPS.
As you know, Sophos DNS Protection for Endpoints enables an added layer of transparent web protection across all ports, protocols, and applications.
Sophos DNS Protection for Endpoints
DNS Protection can now be deployed and enabled on your Windows endpoint devices in Sophos Central. Once deployed, the agent intercepts all DNS traffic from programs and apps on the Windows device and forwards it to the nearest DNS Protection resolver via DNS over HTTPS. DNS Protection will check the requests for security risks and policy compliance and allow or block access accordingly.
DNS Protection policies provide a comprehensive set of controls:
- Category-based allow and block rules
- Custom domain allow and block lists
- Enforcing safe search features on Google, YouTube, and other search engines
Enhanced visibility
All DNS queries originating from your endpoint devices are logged with the user and device names. This allows you to pinpoint problematic devices and target responses to address security issues. It also enhances the data available during XDR and MDR incident investigations.
Note: device and user identities are only available when used in conjunction with the Sophos DNS Protection for Endpoints agent and not yet for DNS Protection on Sophos Firewall.
DNS over HTTPS for privacy and integrity
Sophos DNS Protection for Endpoints supports DNS over HTTPS for added privacy and integrity. By using a secure, encrypted TLS tunnel, all queries and responses are protected from network snooping and from attacks, such as DNS cache poisoning, that exploit the open nature of traditional DNS protocols.
HTTPS support is only available on DNS Protection for Endpoints at this point, however it will come to Sophos Firewall in the near future.
Getting started
Get started today with the early access program for Sophos DNS Protection for Endpoints on the Sophos Community.
Source: Sophos
The use of SaaS applications and the volume of cloud workloads are surging. Businesses today use approximately 112 SaaS apps for various business operations. According to The State of BCDR Report 2025, over 50% of workloads and applications now run in public cloud environments, and this is expected to reach 61% within the next two years.
The cloud has become the new endpoint, where employees collaborate, data resides and critical business operations run. Today, cloud platforms serve not only as the backbone of modern business productivity but also as the primary attack vector for cybercriminals.
Traditional security controls, such as firewalls and endpoint detection and response (EDR) tools, protect on-premises assets and devices. However, business-critical SaaS platforms, such as Microsoft 365, Google Workspace and Salesforce, fall completely outside EDR coverage, leaving organizations vulnerable to cyber-risks like account takeovers, data exfiltration and configuration-based attacks that bypass conventional defenses.
Protecting cloud environments requires a new approach to detection and response. That’s where cloud detection and response (CDR) solutions come in. CDR solutions are designed specifically to fill this gap by providing continuous monitoring, real-time threat detection and alerting and rapid response capabilities across SaaS environments.
In this blog, we’ll discuss what CDR is, why it matters and how it protects cloud environments from emerging threats.
What is cloud detection and response?
Cloud detection and response is a security approach that continuously monitors activity across cloud platforms to detect, analyze and respond to threats in real time.
Let’s take a look at how the cybersecurity landscape has evolved through successive generations of detection and response technologies to better understand the role of CDR.
From antivirus to CDR: The evolution of detection and response
As cyberthreats advanced, security tools adapted in response, resulting in new approaches to protecting shifting attack surfaces:
Antivirus (AV): Antivirus solutions scan the programs and files on endpoint devices using methods such as signature-based detection, heuristic analysis and behavioral monitoring to identify malicious software. However, while antiviruses are effective against known threats, traditional antivirus tools offer little to no visibility into novel or sophisticated attacks in cloud environments.
Endpoint detection and response: As threats become more complex, EDR solutions have emerged to provide continuous monitoring, behavior-based analytics and real-time, automated responses to threats on endpoints such as laptops, desktops and servers that antivirus software fails to detect.
Extended detection and response (XDR): XDR unifies data from multiple security layers, including endpoints, networks and cloud workloads, into a single platform. By breaking down silos, it delivers a more integrated and coordinated approach to detecting and responding to modern threats.
Cloud detection and response: The latest advancement in cybersecurity defense is cloud detection and response. CDR is a proactive security solution designed for threat detection, investigation and response within cloud and SaaS environments — domains that are typically beyond the monitoring capabilities of EDR and XDR platforms.
Why traditional security tools fall short
Traditional security tools such as AV, EDR and firewalls were designed to monitor endpoints and create a network perimeter. They are effective at protecting physical devices and on-premises infrastructure, strengthening an organization’s security posture by detecting malware, blocking unauthorized access and monitoring endpoint behavior. However, as organizations increasingly shift their operations to cloud-based applications, such as Microsoft 365, Google Workspace, Salesforce and other SaaS platforms, these tools fall short of protecting the environments where most business activities now occur.
Cloud services operate outside the reach of traditional endpoint tools. EDR agents cannot monitor activity within web-based SaaS applications, and firewalls miss attacks that occur through legitimate cloud APIs. Attackers now exploit cloud identities and permissions, rather than targeting devices.
In cloud-focused attacks, cybercriminals:
Abuse OAuth permissions by tricking users into granting malicious apps access to corporate data.
Exploit shared links, as overexposed or publicly shared files can become easy entry points for data theft.
Bombard users with repeated authentication requests until they accidentally approve one.
Exploit compromised credentials — obtained through data breaches or purchased on dark web forums — to infiltrate cloud accounts undetected.
Traditional endpoint tools often fail to detect these threats, creating a critical visibility and response gap that leaves organizations vulnerable, even when they have endpoint and network security solutions in place.
Businesses need a reliable CDR platform to monitor, detect and respond to evolving threats across SaaS and cloud environments where traditional endpoint security solutions have limited reach.
How cloud detection and response works
CDR combines monitoring, analytics and automation to deliver continuous protection across cloud environments. Unlike traditional security tools that focus on endpoints or networks, CDR solutions are built to operate natively in the cloud, connecting through APIs and activity logs.
The key components of a modern CDR platform include:
Continuous cloud monitoring
CDR continuously monitors SaaS apps for suspicious activity by tracking login locations, file-sharing behavior, privilege changes and third-party app integrations. This provides real-time visibility into how users and applications interact with sensitive data across services such as Microsoft 365, Google Workspace and others.
Behavioral analytics
Modern CDR platforms use machine learning-powered behavioral analytics to identify anomalies that indicate potential compromise. For example, a user logging in from unapproved locations, sharing business-critical files with people outside the organization or granting excessive permissions, might suggest malicious intent or account takeover.
Automated response
CDR systems can take automated response actions to mitigate or eliminate threats as soon as they are detected. This might include temporarily disabling the compromised account or blocking suspicious login attempts. Automation helps minimize response times — reducing dwell time and limiting the damage caused by unauthorized access or data exfiltration.
Integration with other security tools
CDR integrates with other security tools, such as Security Information and Event Management (SIEM), XDR and identity and access management (IAM) platforms to deliver a unified and coordinated defense. This integration with broader security ecosystems provides a comprehensive view of the threat landscape, enabling real-time threat detection, faster investigation and automated response.
Benefits of implementing CDR
CDR solutions provide real-time visibility and automated threat remediation across SaaS environments. Here are some of the key benefits:
Faster detection of account takeovers and insider threats
Advanced CDR platforms monitor user behavior and cloud activities to spot anomalies, such as unusual logins, privilege changes and suspicious data transfers. This helps security teams quickly detect and respond to account takeovers, insider threats and other credential attacks that traditional tools may miss.
Prevention of data leaks via malicious OAuth apps or misconfigurations
By monitoring API connections, file sharing and app permissions, CDR prevents data leaks from malicious OAuth apps, misconfigurations or excessive sharing. It protects sensitive business data in cloud apps, such as Microsoft 365, Google Workspace or Salesforce, from exposure or misuse.
Reduced manual workload through automated remediation
Cutting-edge CDR platforms, such as SaaS Alerts, automate time-consuming response actions. They lock accounts during breaches, terminate risky file sharing and alert IT technicians. This not only reduces the manual workload for MSPs but also allows them to act quickly before threat actors can inflict additional damage. Automated remediation through CDR implementation allows MSPs to focus on higher-value security tasks instead of repetitive incident handling.
Enhanced compliance and audit readiness
With detailed activity logs, reporting and continuous monitoring, CDR helps MSPs enhance auditability and simplify regulatory compliance for their clients. It enables providers to demonstrate adherence to key industry standards, including HIPAA, GDPR and SOC 2. CDR delivers evidence of proactive threat detection and response across all managed cloud environments.
Cloud detection and response for MSPs
With SaaS applications now serving as core platforms for business-critical operations, implementing a robust CDR solution is no longer optional for MSPs and their clients.
Visibility into client SaaS environments
For MSPs managing dozens or even hundreds of client environments, visibility is crucial. Modern businesses rely heavily on SaaS apps to create, store and share sensitive data. However, these applications often fall outside the scope of traditional endpoint and network monitoring tools. Without direct visibility into these environments, MSPs cannot detect threats, such as account compromises, misconfigurations or unauthorized data sharing.
A reliable cloud detection and response solution provides a centralized view of SaaS threats across all tenants, without the complexity of deploying endpoint agents or juggling multiple tools. It provides MSPs with real-time insights into client cloud activity, including suspicious logins, risky file sharing and third-party app integrations. This enables MSPs to proactively identify threats and respond quickly before they escalate.
Ease of deployment and automation at scale
CDR platforms connect to client SaaS platforms via secure APIs, helping MSPs quickly onboard tenants and scale as their client base grows. For instance, the SaaS Alerts App Wizard allows MSPs to integrate with any SaaS application that has a viable API, pulling mission-critical data into SaaS Alerts. This supports quick detection and response to security threats across almost all of their clients’ SaaS applications.
Once deployed, automated detection and response workflows handle necessary security tasks, such as temporarily disabling affected accounts or blocking suspicious login attempts. This automation reduces manual burden, helping MSPs better protect clients with minimal overhead.
How Kaseya 365 User simplifies cloud detection and response
Kaseya 365 User includes cloud detection and response across Microsoft 365, Google Workspace, Salesforce and other critical SaaS applications, helping MSPs simplify their SaaS security operations.
The CDR platform constantly monitors and protects your clients’ SaaS applications, detecting unauthorized access and shutting it down without requiring any manual intervention. It provides real-time alerting and automated remediation steps, with actions taken within seconds of malicious activity. This significantly minimizes the risk of data egress or malicious activity within your clients’ most vulnerable environments.
Discover how Kaseya 365 User helps MSPs strengthen their clients’ cloud security while boosting their bottom line. Learn more.
Source: Kaseya
It’s that time of year when network admins in many parts of the world are looking forward to spending more time with family and friends and less time in front of their management consoles.
Unfortunately, this is also a peak period for cyberattacks. To help ensure your network is optimally secure over the holidays, here are a few quick and easy best practices you can utilize.
For a full list of best practices to secure your network from ransomware and other attacks be sure to download our whitepaper on this topic.
Update firmware and shut down unnecessary systems
Make sure that before you depart for the holidays, all your network infrastructure has been updated with the latest firmware and any unnecessary infrastructure is shut down and offline.
Any system exposed to the Internet either directly or indirectly (via NAT) represents a potential vulnerability and risk. Eliminate as much of that attack surface as possible by taking it offline, and update and lock down the rest.
Firmware updates often contain important security patches for known vulnerabilities or hardening enhancements that can improve your security posture. If you’re a Sophos Firewall customer, make sure you’re running the latest firmware update for your device and consider enrolling in the early access program for Sophos Firewall v22, which includes many new security hardening features and a new Health Check feature to ensure your firewall is configured optimally.
If you have other internet facing infrastructure like a VPN concentrator or WAF, make sure these systems are also up to date or shut down.
Check your configuration against best practices
Double check that all access controls, portals, NAT rules, networked apps, IoT devices, and administration systems are either disabled or locked down.
As mentioned above, if you’re a Sophos Firewall customer, consider upgrading now to the v22 early access program to take advantage of all the new security hardening capabilities and the new firewall Health Check feature that will assess your configuration against best practices to highlight any risky areas.
Ensure all systems use strong authentication with MFA
Make sure all admin consoles and remote access systems are either shut down or protected against brute force attacks or stolen credentials with multi-factor authentication.
As you would expect, Sophos Central, Sophos Firewall, ZTNA, and our full line of network security solutions leverage MFA to help protect your systems from unauthorized logins. Sophos Firewall v22 also includes new MFA support for the Web Application Firewall – one of the many top requested features in this release.
At any rate, make sure MFA is enabled for all your systems.
If you’re attacked, we can help
If you experience an emergency incident over the holidays (or any time), you can engage our fixed-fee Sophos Rapid Response service. Our team of expert incident responders will help you triage, contain, and eliminate active threats, and remove all traces of the attackers from your network.
Whether it’s an infection, compromise, or unauthorized access attempting to circumvent your security controls, we’ve seen and stopped it all. Sophos Rapid Response is available 24/7/365, including over the holiday period.
Source: Sophos