
Overpower Threats. Empower IT.
Malwarebytes for Business is now ThreatDown and it’s on a mission to overpower threats and empower IT by removing the complexity of detecting and stopping today’s most advanced threats. ThreatDown pairs technology with services to streamline security and provide robust protection that’s efficient and cost effective. With a channel first mindset across the globe, we empower our partners to help resource-constrained IT organizations.
Award-winning endpoint security solutions that combine layers of protection, threat intelligence, and human expertise to protect organizations from ransomware, malware, viruses and other threats. ThreatDown solutions are built for everyone- not just companies with deep pockets and large security teams. Our solutions combine technology with services to provide robust protection that's efficient and cost-effective.
Videos
-

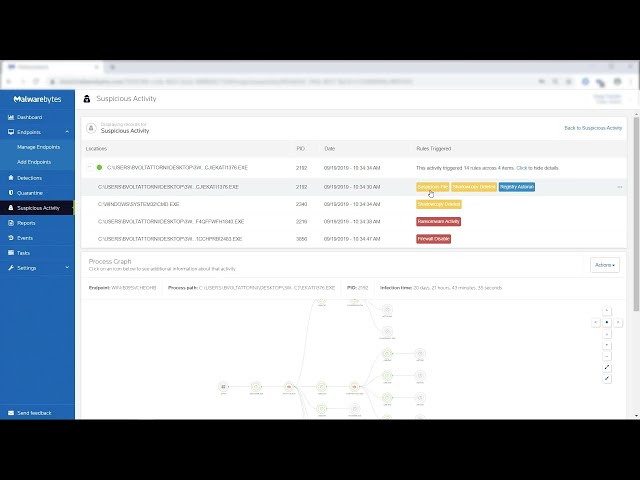
Manage and remediate suspicious activity
-

Cyberprotection for every one
-

What is a digital footprint and how to protect it
-

Configure Endpoint Detection and Response in Malwarebytes OneView
-

How to Install Malwarebytes for Teams - Malwarebytes
-

Malwarebytes Managed Detection and Response (MDR)
-

Install Malwarebytes for Windows
-
Endpoint Detection and Response (EDR) - Malwarebytes
Business cyber security challenges
Escalating threats
Over 68% of firms suffered recent attacks and 80% were unknown “zero-day” threats.
Sources: 2020 EDR Solutions Study, Ponemon Institute
Zero-day detection
Almost 60% of firms need zero-day detection, but high false positives are a key concern.
Complex solutions
More than 61% of firms say complexities and limited staff are significant EDR challenges.
Three critical requirements
Detection and protection against ransomware, malware, trojans, rootkits, backdoors, viruses, brute force attacks, and “zero-day” unknown threats that other tools don’t catch.
Easy
ThreatDown Endpoint Detection and Response for Windows and Mac can easily replace or augment other endpoint security solutions, including Microsoft Defender.
- Non-disruptive, role-based access, deploy within minutes
- Lightweight endpoint agent, robust integrations
- Intuitive cloud-native management console
Effective
ThreatDown EDR uses unique Anomaly Detection machine learning to not only detect known threats, but also find unknown “zero-day” threats.
- Granular isolation for processes, networks and Windows desktops
- Collects detailed threat information for analysis and investigation
- Proprietary Linking Engine removes executables, artifacts, and changes
Efficient
ThreatDown EDR offers remote worker optimization, industry-leading efficiency, high return on investment (ROI), and low total cost of ownership (TCO)
- Guided threat hunting to search for Indicators of Compromise (IOCs)
- 72-hour ransomware rollback for Windows workstations
- No performance impact, uses an order of magnitude fewer resources
ThreatDown next-gen tool
Remote worker protection
Higher Remote Desktop Protocol (RDP) usage resulting from the COVID-19 pandemic have exposed an exploitable vector for ransomware.
ThreatDown Endpoint Detection and Response now includes ThreatDown Brute Force Protection to block malicious login attempts and prevent intrusion attacks targeting RDP on Windows workstations and servers.
Our powerful scan and detection engine provides stronger protection against infections from exploits and packaged and polymorphic malware, making it ideal for remote work environments where users may be easier targets.
Improved threat detection
Sophisticated attacks exploit entry points and security holes, and once attackers are inside, they can set hooks that cause serious damage.
Low false positive alerts
The average enterprise security team spends over 25 percent of their time chasing thousands of false positive alerts each month (Ponemon).
Innovative active threat response keeps endpoints productive
Attack isolation
If an endpoint is attacked, you can easily halt malware from spreading and causing harm.
Network isolation limits device communications, so attackers are locked out and malware can’t “phone home.”
Process isolation restricts which operations can run, halting malware and enabling remote retrieval of suspicious code for investigation while still allowing end users to work away.
Desktop isolation alerts the end user of the threat, temporarily blocks their access, yet keeps the device online for analysis.
With multiple modes of attack isolation, both security teams and end-users maximize their productivity even during attacks.
Automated remediation
Find and reverse all major and subtle changes made by malware.
While traditional approaches focus on removing only the active executable, they ignore residual change that leads to re-infection or pesky PUPs and PUMs. You’re then left to reimage the device, or hope for the best.
Quite the opposite, the proprietary ThreatDown Linking Engine tracks every artifact, change, and process alteration (including memory executables others miss). A true “one and done” solution, it then maps out the correct path to remove all malware permanently, including PUPs and PUMs.
Ransomware rollback
For Windows environments, paying ransomware is no longer a requirement.
It’s possible because we make use of local cache on each endpoint, storing all relevant changes to the device for up to 72 hours. If you’re infected, ThreatDown simply backs out device changes and restores files that were encrypted, deleted, or modified. And data storage space isn’t an issue, as our proprietary dynamic exclusion technology learns “good” behavior of applications and minimizes storage utilized.
The result is peace of mind knowing that ransomware won’t damage your bottom line, reputation, customer experience, or team productivity.
Protect your business in just a few clicks
With a few simple clicks you can protect your business and brand, improve your regulatory compliance posture, and avoid costly downtime. ThreatDown Endpoint Detection and Response for Windows and Mac offers enterprise-class endpoint protection, advanced threat hunting, and reliable isolation, remediation, and response to cybersecurity attacks.





