Latest Free Version of Sophos Mobile Security Delivers Application Protection, Faster Scanning and Web Protection
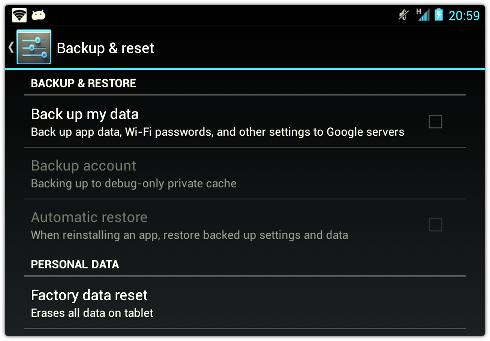
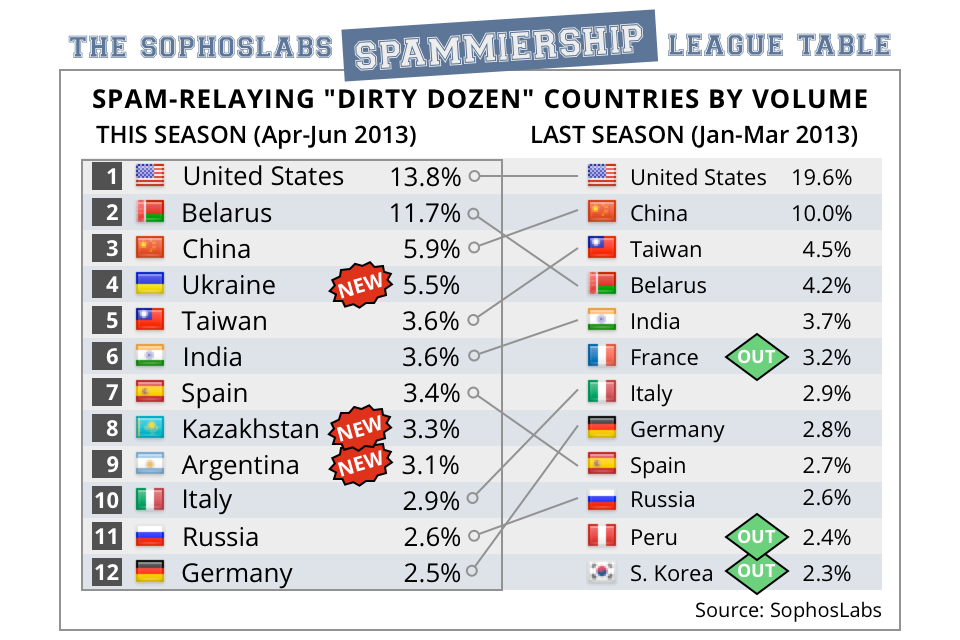
An equally alarming industry statistic, users not running the most recent version of Android (comprising more than 90 percent of active users) are vulnerable to known exploits, resulting in a more than 600 percent increase in Android malware infections.In order to keep up with and prevent these risks, Sophos has introduced the latest version of […]