News
There’s a lot of noise (or confusion) in the market around what “next-gen” endpoint protection actually is. At Sophos, we believe next-gen endpoint protection must deliver an integrated system of prevention, detection and remediation technologies.
The Sophos System Protector does exactly this. It functions as the “brain” of our endpoint protection by automatically applying the best threat protection based on behavior, analytics, heuristics and many other built-in defenses.
Yet all the science and technology in the world is for naught if the protection doesn’t protect. And independent test houses provide the best assessment of how a product will perform in the real world.
Each testing house has a different methodology, and obtaining a balanced view across multiple independent testers is a great way to get an unbiased view of how security products perform in real-world scenarios.
Dennis Technology Labs recently gave Sophos its highest AAA rating, while AV-Test has further verified Sophos leadership. In AV-Test’s most recent round of tests in November-December 2015, Sophos scored a perfect 6 out of 6 for protection – for the fourth time in a row.
We’re delighted to see that both Dennis Technology Labs and AV-Test are rating Sophos so highly.
In contrast, some so-called “next-gen” vendors struggle to keep pace.
In AV-Test’s latest test, Cylance registered a disappointing 29 false positives, compared to an industry average of six, highlighting usability problems in these real-world testing scenarios.
Clearly there’s no replacement for a true “next-gen” endpoint protection solution that delivers in the real world.
You can read the original article here.
Sophos, a global leader in network and endpoint security, today announced the availability of Sophos Mobile Control 6.0, which now includes Sophos Secure Email, a container solution that isolates and secures business data from personal information on devices. Sophos Mobile Control 6.0 also enhances data protection capabilities and allows IT managers to oversee devices used throughout their organization through a simple interface and intuitive workflows.
Within Sophos Mobile Control 6.0 is Sophos Secure Email, a personal information management (PIM) container solution for email, calendar and contacts. Personal and corporate data can be separated, allowing organizations to manage business data security while enhancing user privacy. IT administrators can remotely provision email to employee mobile devices across popular platforms, including iOS, and multiple Android versions.
Also new to version 6.0 is Sophos Secure Workspace which includes Corporate Browser to facilitate safe access to frequently used business productivity sites and applications. Sophos Secure Workspace enables employees to seamlessly access and collaborate on the documents they need, when they need them, in a secure manner. Users also can control levels of access and publishing rights for various cloud storage providers like Dropbox, Google Drive, Microsoft OneDrive and Egnyte. For additional protection, users now can securely move documents and data between mobile devices, cloud storage and corporate endpoints as Sophos SafeGuard file encryption is built in.
With the continued growth in mobile malware, the ability to detect and quarantine infected devices is a growing priority for enterprise mobility management (EMM). In fact, more than 95 percent of attacks today involve harvesting credentials from customer devices and using those stolen credentials to log in to web applications, according to Verizon 2015 Data Breach Investigations Report.
Device security is especially difficult to manage in mid-size enterprises that have widely distributed workforces, yet are resource-stretched. A September 2015 CompTIA study, Managing the Multi-Generational Workforce, showed that nearly half (46 percent) of small and mid-sized businesses have now fully adopted BYOD as a standard practice, as opposed to only 28 percent of large enterprises.
Sophos Mobile Control 6.0 also detects jail-broken or rooted devices, plus malware and potentially unwanted applications (PUAs). The product blocks infected or non-compliant devices from entering the corporate network and automatically blocks malicious or undesirable websites. A recent analysis by third party AV-Test confirmed that Sophos Mobile Control 5.5 detected 100 percent of known Android malware applied during the test period. All of this is done behind the scenes to users so that productivity isn’t sacrificed and critical, confidential data remains private and safe.
Sophos Mobile Control 6.0 is available now from the global network of Sophos certified partners.
You can read the original article, here.
Cyberattacks and data breaches have created a lot negative headlines lately. The good news is that the epidemic of cybercrime has led to a growing emphasis on security in general and encryption in particular.
We wanted to find out just how many organizations are using encryption today to protect sensitive data like customer payment details, company financial records, employee records, and intellectual property.
So we worked with a research company to conduct a survey of IT decision makers at organizations large and small, in various industries, and in six different countries.
What we discovered is that the level of encryption in organizations leaves a lot of room for improvement, although there is hope that many companies are moving in the right direction.
You can see the results of our survey in this infographic, and in our encryption survey report. We’ve also put together some free resources, such as videos and guides, to explain how encryption can help you secure your valuable data. Check them out at sophos.com/encrypt.

You can read the original article, here.
We designed the new Sophos XG Firewall to meet our high standards for security made simple, and with the admin in mind. It should be comfortable and familiar to anyone with experience using a Cyberoam or Sophos UTM.
However, we want to help you get the most out of your XG Firewall, so we’ve created a comprehensive library of “How-To” videos, including a series of Getting Started and Networking videos.
It makes sense to start at the beginning, with a video about XG Firewall registration and setup. So in this post we’re featuring a short and easy-to-follow video that helps you set up your XG Firewall right out of the box.
The video shows you how to:
- Do initial setup of the firewall
- Open and log into the admin console
- Register your device with a MySophos account
- Use the network Setup Wizard
- Configure various interfaces and default policy settings
As an example, here’s one of the videos that covers how to make the most of the new Control Center and Main Menu Navigation
The full list of videos so far includes:
– Registration and Setup Wizard
– DHCP
– Integrated Wireless Access Point
– Site to Site IPsec VPN PreShared Keys
XG Firewall – Learn more
Read these other blog posts to learn about the many innovations in Sophos XG Firewall:
- Sophos XG Firewall: A network security ecosystem with many innovations
- Sophos XG Firewall – Simpler, faster, and more-in-one
- Sophos XG Firewall innovations – Policy management
- Sophos XG Firewall innovations – FastPath packet optimization
- Sophos XG Firewall innovations – User interface
- Sophos Firewall Manager and iView – Centralized management and reporting for all your XG Firewalls
- FAQs for Sophos UTM customers about the new XG Firewall
Sophos is pleased to announce that we received a prestigious Channel Excellence Award this week from IDG’s ChannelPartner magazine. The awards are presented to the top technology and distribution companies in the DACH region.
We were recognized with the 2016 Channel Excellence Award in Security Hardware, besting nine competitors in that category. Additionally, we were selected as a Preferred Vendor in the Security Software category.
The Channel Excellence Awards are based on a thorough and objective study conducted by GfK, the globally-recognized market research company.
Helmut Nohr, Sophos channel sales director, accepted the Channel Excellence Award at a gala held on 20th January in Munich, Germany.
This award complements another major channel win for Sophos in Western Europe – we were named Security Vendor of the Year at the Dutch IT-Channel Awards on 21st January.
The channel community has recognized Sophos with numerous awards, in regions all around the world.
Recently, Sophos was chosen as the CRN Security Vendor of the Year in DACH, and the Best UTM Vendor at the Reseller Middle East Hot 50 Awards 2015; and we garnered the top awards in every security category in the 2015 CRN Annual Report Card – for the second year in a row.
Although Sophos is the recipient of all these awards, it’s our partners who are the real winners, thanks to our channel-first strategy and our industry-leading products.
You can read the original article, here.
At Sophos, we believe you can never have enough encryption. Simply put, encryption is the best way to protect information from loss or theft, the last line of defense against cyberattacks and accidental data exposure.
And yet, we frequently hear about businesses that fail to encrypt their data, often after a devastating breach. Unfortunately, the state of data security today is poor – in 2014, 700 million records were compromised, according to the most recent Verizon Data Breach Investigations Report.
To find out why there are so many data security failures, we conducted a survey of 1,700 IT decision makers, covering six different countries and multiple industries. We asked them what types of data their organizations encrypt, and why they don’t always encrypt everywhere.
The results of our “The State of Encryption Today” survey are instructive, and give us a better understanding of where companies can do better.
Some of the most concerning findings of the survey reveal that, while many companies take the security of their customer data seriously, employees are not protected to the same level.
Private, highly sensitive employee data, including banking details, human resources (HR) files, and personal healthcare records, are frequently not protected by encryption.
For example, 31% of the companies we surveyed that store this type of data admitted that employee bank details are not always encrypted, and 43% don’t always encrypt employee HR records. Also, nearly half (47%) of those that store employee healthcare information fail to always encrypt these records.
While customer data breaches are the ones that get the biggest headlines, companies have an obligation – and may be legally required – to protect sensitive employee data. This is an area of data security that is far too often overlooked.
Company data remains at risk as well. Nearly one-third (30%) of organizations surveyed fail to always encrypt their own corporate financial information, and 41% inconsistently encrypts files containing valuable intellectual property, despite the increasing risks of economic espionage.
Another area of concern is that many organizations don’t recognize that the different types of encryption – full-disk and file encryption – are not and should not be mutually exclusive.
Although full-disk encryption is critical in cases of lost or stolen devices, it doesn’t protect the data once it leaves the device. File-level encryption is often necessary and complementary, so that data is always protected: at rest, in transit, and when stored off-device. Yet only 36% of companies said they use both full-disk and file encryption.
Meanwhile, cloud data security is one area driving increased adoption of encryption. More than eight in ten companies (84%) expressed concern about the safety of data stored in the cloud. Nevertheless, while 80% are using the cloud for storage, only 39% encrypt all files stored in the cloud.
This leads to the next crucial question – why are so many companies failing to protect all types of data, everywhere and at all times?
Companies cite budget, performance concerns and lack of deployment knowledge as the top three barriers to implementing an encryption solution.
Unfortunately, I’m not surprised by these findings because too many people mistakenly believe that encryption is too complicated or too expensive to implement. Despite these concerns, the reality is that modern, next-generation encryption solutions can be easy to deploy and quite cost-effective.
There are some positive results from our survey that give me hope that companies are starting to learn the value of encryption and are beginning to move in the right direction.
A majority of IT professionals we surveyed acknowledged that their companies need to do a better job of encrypting employee, customer and company information. The good news is that 69% of them said they plan to increase their use of encryption within the next two years.
The State of Encryption Today survey confirms that while encryption is widely used and accepted by businesses, there are critical gaps.
Promises to do better “next time” come too late, after the damage has already been done. For the organizations and individuals who are victims of data breaches, a single breach is one too many.
For more information about the challenges and opportunities for data protection in your organization, I recommend reading the full results and analysis of this survey at sophos.com/encryptionsurvey. We’ve also put together several free resources such as videos and guides to help you on your way to better security for all your data at sophos.com/encrypt.
You can read the original article, here.
Sophos has just passed with flying colors two important anti-malware tests conducted by the independent tester Dennis Technology Labs – one for enterprise and another for small and mid-sized business (SMB) endpoint security products – earning the highest rating of “AAA” in both tests.
The tests looked at how the products from Sophos, McAfee, Microsoft, Kaspersky, Symantec and Trend Micro fared in real-world scenarios that replicate what a user would experience when encountering an infected website.
Sophos Endpoint Protection received perfect protection scores in both tests, and was the only product tested with a perfect total accuracy rating in the enterprise test. We also were the only vendor to receive a perfect score in both the enterprise and SMB tests.
In the enterprise test, Sophos Endpoint Protection blocked all threats without any compromises (protection), and it did so without any false positives for legitimate software (legitimacy), for a total accuracy score of 100%, as you can see in the chart below.

Although Kaspersky also received a 100% total accuracy score, when you dig down into the numbers you can see that only Sophos had a perfect total accuracy rating (1024 out of a possible 1024), whereas Kaspersky’s rating (1020 out of 1024) was rounded up to 100%.

Kaspersky lost points in the protection area because it failed to defend against three out of the 100 malware samples used in the test. Rather than blocking the malware from gaining a foothold in the target system, Kaspersky’s product “neutralized” the threats after they had already infected the system, as shown in the “protection details” table below.

Symantec, Trend Micro and Microsoft all suffered in their protection scores because at least one threat compromised the target system, meaning their products allowed the threat to infect the system and did not neutralize the threat after infection.
You’ll notice that, although McAfee successfully defended against all threats in the test, its score in legitimate software ratings was the lowest of all products tested because of false positives.

On the SMB test, Sophos Endpoint Protection once again achieved perfect scores for blocking all threats without blocking any legitimate software.

In this test, Symantec and Kaspersky also received 100% total accuracy scores, but Kaspersky only defended against 97 out of 100 threats – it neutralized three threats after they had infected the target system, as shown below.

Trend Micro and McAfee scored low in protection accuracy because of threats that compromised the target system. Both companies also scored low on the legitimacy portion of the test due to false positives, seen in the table below.

For organizations of any size, a product that defends against all threats but blocks legitimate software is disruptive to the business.
And of course, an anti-malware product that only blocks threats most of the time is not nearly good enough – letting just one threat through is all that an attacker needs to do serious damage to your business’s network, data and reputation.
As Dennis Technology Labs said in its report: “The ideal product would block all threats and allow all legitimate applications.”
As the only product with perfect protection scores and perfect legitimate software scores in both the enterprise and SMB tests, we agree.
These results are also gratifying because Dennis Technology Labs is one of very few testers that truly tests real-world threats in near real time from end to end, giving all layers of protection we have in our product an opportunity to protect the user at every stage of the attack lifecycle.
For more information on test methodology and the complete results, visit the Dennis Technology Labs website to download the full Enterprise Anti-Virus Protection and Small Business Anti-Virus Protection reports.
To see how Sophos Endpoint Protection is simply better than the competition, try it for yourself – sign up today for a free trial.
You can read the original article, here.
I am very pleased to say that we’ve had an overwhelmingly positive response to our announcement that SurfRight is joining the Sophos family, from both SurfRight customers and industry analysts.
I’ve seen a number of great questions raised by SurfRight customers, and I wanted to take a moment to address them here. I can confirm that we are committed to continuing the development and enhancement of the successful HitmanPro product line.
We’re excited about the acquisition of SurfRight because we see a great value in their innovative technology, which we will integrate into our next-generation endpoint solutions for businesses and our standalone tools anyone can use.
We will continue to offer the “free scan” feature of HitmanPro. And Sophos will honor the terms and conditions of all existing SurfRight licenses, including any special promotions or deals. The support forums and services that customers use today will continue. And as we integrate the products into the Sophos Support Community to enhance customer experience, we will do so seamlessly, so no user is left behind.
Developing powerful tools and offering appropriate support for home users is not new to our strategy. We have an established portfolio of free commercial-grade tools for home users, and we continually invest in these products.
We believe that in order to be effective, security must be comprehensive, security must work together as a system, and security products should be simple to use. Effective security technology is important to business users and home users alike, and our portfolio of free tools follows the same development principles.
This month we released a brand new tool, Sophos Home, providing free Internet security for both PCs and Macs via a simple web console. We also offer Sophos Mobile Security for Android, Sophos XG Firewall Home Edition and Sophos Antivirus for Linux.
Sophos will bring the recently acquired SurfRight tools, such as the popular HitmanPro product, into our home user portfolio, and we will continue to develop, expand and improve the powerful HitmanPro technology.
We welcome all SurfRight customers, appreciate your engagement, and thank you for your passionate loyalty to a great product – your security is our priority.
You can read the original article here.
It feels like the perfect time to announce a new free tool that’s designed to bring to our commercial-grade Sophos security to all of your homes. In a bout of creative genius, we decided to call it … Sophos Home. Clever, right?
We decided to do this because we’ve been hearing from employees, customers, partners, and friends that the existing solutions in the market aren’t working for them. We hear complaints about ineffective/cheap consumer technology and products loaded with nagging adware; security companies that sell your data to third parties; and some that still think homes only have a single PC. It seemed to us that no one has done a very good job of building a product designed for the modern family. We thought we could do better so we kicked off the Sophos Home project.
I’m really proud of what our designers and engineers have come up with. It’s a brilliantly simple online management dashboard that sits on top of enterprise-grade, sophisticated Mac and Windows endpoint protection technology to keep all of your computers and family members safe.
It even includes the ability to set restrictions on what kind of websites each computer has access to (my 12 year old is no longer spending his college savings on the Draft Kings fantasy football site).
I could spend a long time telling you about the cool behavioral detection tech that watches apps for malicious actions, or the instant checking we do to make sure the website you’re visiting hasn’t been compromised. The real point is that Sophos Home is industry-leading security tech, but with a new management system designed from the ground up for the home user … and it’s free!
We protect over 100 million employees today and we feel they need the same protection at home, as do their kids, their parents, and their friends. There are far too many threats out there: infected websites that silently drop malware on your computer just by visiting a webpage; ransomware that locks up all your precious files with encryption, and throws away the key unless you pay; and phishing websites set up by hackers to look just like your bank’s website to steal your passwords and drain your accounts.
It’s time for a better solution designed for today’s connected family.
So, give it a try and let us know what you think. Simply go to sophos.com/home and create your free account. Download and install it. That’s all you need to do!
You can read the original article, here.
Sophos, a global leader in network and endpoint security, today announced the acquisition of SurfRight, an innovator in signature-less next-generation endpoint threat detection and response (ETDR) and advanced threat prevention.
Based in Hengelo, the Netherlands, SurfRight has developed a portfolio of technologies that prevent, detect and remediate zero-day and sophisticated attacks by interrupting malware and advanced persistent threat (APT) vectors. SurfRight’s real time anti-exploit technology focuses on detecting and preventing the memory manipulations and abuses that allow malicious code to run in the first place. Generic prevention of exploits at this early stage in the attack chain is a key enhancement to endpoint security mechanisms and can help thwart malicious code in the processor and memory. The portfolio also includes anti-espionage technology and enhanced protection against ransomware attacks such as CryptoLocker.
Sophos is recognized as a leader in endpoint protection today, with a growing set of next-generation technologies such as behavior-based analytics, Malicious Traffic Detection that monitors attempted outbound connections to known bad URLs, and Application Reputation which leverages a crowd-sourced big data warehouse managed by SophosLabs to determine whether a downloaded file is known to be good or bad and prompts the user to take appropriate action. This acquisition will further strengthen Sophos’ leading endpoint protection technology, by adding complementary new defense tactics, delivered either on premise or in the cloud.
Sophos will immediately work to integrate the SurfRight technology into its line of endpoint security solutions. Once the integration work has been completed, Sophos will make the technology acquired from SurfRight available via its global network of more than 15,000 channel partners.
SurfRight’s technology will also further enhance the effectiveness of Sophos’ synchronized security strategy, in which multiple components of security protection, including network security and endpoint security, actively and continuously communicate with each other. This innovative approach leads to faster threat detection and a dramatic reduction in the time and resources required to investigate and address security incidents.
Sophos will continue development and support for SurfRight’s existing product line including its popular HitmanPro malware scanning and removal tools, used by more than 20 million users worldwide. Sophos acquired SurfRight for a cash consideration of $31.8 million and will retain all SurfRight employees and the company’s office in Hengelo. SurfRight CEO Mark Loman will join the Sophos Enduser Security Group, reporting to Dan Schiappa.
You can read the original article, here.
For the third straight time, Sophos has earned 6 out of 6 points for protection in AV-Test’s independent evaluation of endpoint protection products. Our Sophos Endpoint test results show that we detected 100% of zero-day malware attacks in both September and October.
This is now six straight months of 100% detection in “real-world testing.” The “widespread and prevalent malware” test is now reported with an extra decimal place of precision, so instead of our previous 100% (rounded), we’re now at 99.7% in September and 99.9% in October.
We also received a score of six out of six on the usability portion of the test. We recorded zero false positives in that portion of the test. This follows up on our great performance in this category over the last year – we even won AV-Test’s 2014 Best Usability Award.
On the final portion of the test, measuring performance, we scored 5 out of 6 points, indicating that Sophos Endpoint doesn’t significantly slow a computer’s performance while performing tasks such as downloading software, accessing websites, installing programs and copying data. (Other independent tests have found that Sophos has among the lowest performance impacts in the industry).
The independent tests from AV-Test are a benchmark for how we’re doing, and we’re proud of our consistent results. We think it’s validation of our leadership in the industry.
But we’re not going to rest on our laurels.
We’re continuing to innovate and build new protection technologies into our next-gen endpoint solution such as malicious traffic detection and download reputation. Plus, we’re integrating our endpoint and network security together with our industry-first synchronized security technology.
To see how Sophos Endpoint Protection is simply better than the competition, try it for yourself – sign up today for a free trial.
You can read the original article, here.
For decades, the security industry has been treating network security and endpoint security as completely different entities. It’s just like putting one security guard outside the building and another inside the building, but not allowing them to talk to each other.
What if we started over with a fresh and radical approach that delivered better protection by enabling automated and real-time communication between network and endpoint security solutions. One that was synchronized across the entire threat surface, and highly automated, so it could do all this without adding staff or workload.
To accomplish this, we need a system with the following five attributes.
Ecosystem centric: We must prevent, find and stop breaches across the entire IT ecosystem by operating with full awareness of nearby objects and events.
Comprehensive: The solution would need to be comprehensive and cover multiple platforms and devices, to defend against attackers who attack the whole IT system, not just its parts.
Efficient: The solution must lower the team’s workload while improving protection. It cannot add another layer of technology and workload.
Effective: The solution must effectively prevent, detect, investigate and remediate today’s threats across the entire threat surface.
Simple: It must be simple to buy, simple to understand, simple to deploy and simple to use.
This list seems like a tall order indeed. Today’s IT security products are the opposite: threat centric, complex, non-comprehensive, resource intensive, and in total not as coordinated as the attacks they’re supposed to defend against.
Clearly, innovation is needed to succeed.
When the Sophos Next-Gen Firewall detects an advanced threat or an attempt to leak confidential data, it automatically utilizes the Sophos Security Heartbeat to take a series of actions across both the network and endpoint to mitigate risk and stop data loss instantly.
Similarly, if a protected endpoint is discovered to be compromised, synchronized security allows automated and near instantaneous isolation of this endpoint, preventing it from leaking confidential information or sending data to a command-and-control server.
This type of discovery and incident response, which could take weeks or months, has been reduced to seconds with synchronized security.
Synchronized Security – A new approach
Complex, threat centric, headcount dependent, myopic solutions will not meet the needs of resource constrained IT security teams. To reverse the trend of increasing incidents and breaches, we must take a much different approach than in the past. To do this, we must implement new solutions that are simple, yet effective, automated and coordinated – in short, synchronized via technology innovation such as the Sophos Security Heartbeat.
The good news is that this capability is available today from Sophos. To learn more about how synchronized security from Sophos can reduce your risk in the face of today’s cyberthreats, download our free whitepaper, “Synchronized Security: A Revolution in Protection” (no registration required), and visit sophos.com/heartbeat.
Υou can read the original article, here.
The phrase Internet of Things, or IoT for short, turns up all over the place these days. But what is the thing of which the IoT is made?
Is it a specific sort of technology, like a low-powered computer chipset? A special sort of computer, such as one without a screen and keyboard? Is is an online trend, like Snapchat?
The answer, for better or for worse, is all of these, and a lot more besides. Loosely speaking, the IoT refers to a whole class of day-to-day objects – things, if you like – that are now being offered with built-in network connectivity.
This means you can hook them directly to the internet, all on their own, rather than first plugging them into a computer that is connected to the internet.
Very often, these are things that:
- Were not designed or built specifically to be part of the internet.
- Perform functions that do not require the internet.
- Are widely known and commonly-used.
- Have worked just fine for years without being part of the internet.
- But would possibly be more useful, and definitely be much cooler, if only they were online.
Some examples are: TVs, music players and cameras. For many years you’ve been able to connect devices like this to your computer, for example to upload music, download images, or set recording times for your favourite shows.
So it’s not entirely surprising that many of them can now be connected directly to the internet on their own. Trendier items that have recently joined the IoT include: kettles, light bulbs and home thermostats.
You don’t really need your light bulbs online, but it’s kind of cool to be able to set mood lighting in your whole living area using an app on your mobile phone, without having to rig up any special wiring.
And you can probably imagine how remotely controlling individual appliances over Wi-Fi with a single app might end up saving money, improving reliability, being greener, and so on. So we can expect to see more and more IoT devices of this sort, from washing machines and refrigerators to garage door openers.
Lastly, there are numerous specialised devices that are rapidly becoming IoT “things”, such as: drug infusion pumps, electricity meters and even cars.
PROS OF THE IoT
+ Connecting and controlling household devices will become easier and more efficient. If you have ever done any electrical work on an older-model car, you will know just how confusing an automotive wiring loom can be. Much of that complexity comes from the need to run wires hither and thither to connect the battery to each light bulb or device via its own switch or control knob.
+ Assuming suitable networking and connectivity standards, you won’t need a unique, proprietary control unit for each device.
+ Specialised devices such as drug pumps and electricity meters will be easier to update. This means it will be easier to keep up with changes in regulations, best practices, tariffs, and so on.
CONS OF THE IoT
– Experience so far suggests that we can’t rely on the vendors of these devices to make sure they are secure before they invite us to hook them up to the internet. From baby monitor webcams with well-known default passwords to drug pumps with no network passwords at all, computer security often takes second place in the IoT.
– Early adopters run the risk of being blinded by coolness, or oversold on convenience. This may lead to them deploying IoT devices such as webcams and thermostats without thinking what information might leak out about their private lives.
– The IoT’s “things” are frequently just tiny computers that are built down to a price. With this in mind, shortcuts in security are hardly unexpected.
You can read the original article, here.
Attackers are more frequently using previously-unknown malware to evade traditional protection. While conventional anti-malware protection is still absolutely vital as a first line of defense, organizations need additional tools to combat today’s targeted, unknown malware.
Unfortunately, many next-generation solutions designed to deal with unknown threats are too complex and expensive for many businesses to consider. And under-resourced small and mid-sized businesses definitely don’t want yet another point solution to clutter up their network.
This is why we’re launching Sophos Sandstorm, an advanced malware defense solution that complements Sophos security products to quickly and accurately detect, block and respond to evasive threats using powerful, cloud-based sandbox technology.
Sophos Sandstorm is a new breach detection platform across the Sophos portfolio. The first Sandstorm component is a cloud-delivered next-generation sandbox that provides targeted attack protection, visibility and analysis by detecting, blocking and responding to evasive, unknown threats.
Sophos Sandstorm integrates with the Sophos solutions you’re already using:
- Sophos Web Appliance (SWA) 4.2 is the first product to implement Sophos Sandstorm.
- Sandstorm will be integrated with Sophos Email Appliance 4.0, UTM 9.4, Cloud Web Gateway and XG Firewall in 2016.
How Sophos Sandstorm rises above the competition
It’s simple:
- Easy to try – sign up directly from the product interface
- Easy to deploy – simply activate the policy
- Easy to manage – all from within your “three-clicks-to-anywhere” interface
It’s effective:
- Blocks evasive threats – detects threats designed to evade sandboxes that other solutions miss
- Policy control – simple, efficient policy control
- Visible protection – granular, incident-based reports
It’s cloud-delivered:
- Rapid deployment – instant protection with no hardware to deploy or appliance upgrade needed
- Minimal impact on performance – all processing done in the cloud
- Collective intelligence – analysis of threats detected across the broad Sophos customer base
Why should you be interested?
Many organizations recognize the need to take steps protect their business against unknown threats. What they don’t want is yet another point solution to clutter up their network.
If you want an advanced threat solution that’s easy to try and deploy, simple to manage, and uses the best threat intelligence, Sophos Sandstorm checks all these boxes.
Visit sophos.com/sandstorm to learn more about how Sophos Sandstorm works.
You can read the original article, here.
Miercom, a leading, independent test center, recently conducted a comparative test of UTM/Next-Gen Firewall appliances from leading network security vendors including Sophos. Miercom tested our desktop model, the SG 135w, alongside models from Fortinet, Check Point, DELL SonicWALL and WatchGuard.
Miercom also ran a test comparing the performance of the SG 135w desktop model against the competition’s rackmount 1U appliances, a traditionally more powerful form factor.
All models were tested under equal circumstances and using equal packet sizes for a fair comparison. Also, all vendors involved had the chance to demonstrate their performance in a separate test if they didn’t agree with the results. Only WatchGuard made use of that possibility.
So how did the SG 135w, a popular choice as a small business and branch office UTM, stand up against the desktop and rackmount models of our competitors? Below is an overview of the test results, which you can also see in more detail in the full Miercom reports on the desktop and rackmount tests.
Desktop-to-Desktop Comparison
In the primary comparison, Miercom tested the SG 135w* against comparable desktop models in six separate tests measuring throughputs with different features turned on.
Desktop models tested:
- Sophos SG 135w
- Fortinet FortiGate 90D
- Check Point 2200
- DELL SonicWALL TZ600
- WatchGuard XTM 330
The test results show that the SG 135w had superior performance in five out of the six tests. The base firewall throughput of the SG 135w was over four times faster than the models from Dell, Fortinet and WatchGuard, and almost 1.5 times faster than the nearest rival, Check Point.
The SG 135w outperformed the competition in the UTM test with 40% more throughput than the average. Miercom notes that even when all features on the device were turned on for the UTM test:
“Sophos maintains a respectable rate which is considerably higher than its competitors.”
In only one of the six tests did the competition draw even with the SG 135w – in the Firewall + AppCtrl, where Check Point achieved the same throughput performance.
As you can see in the graphic below, the SG 135w has proved itself to be the most powerful desktop model.
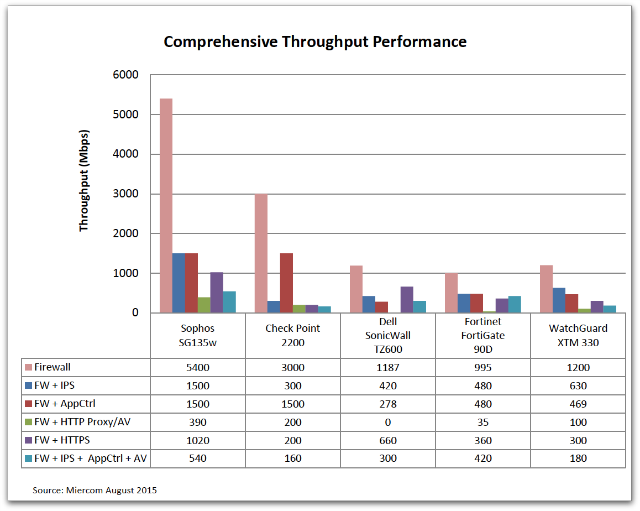
And the strengths of the SG 135w are not limited to performance. Our UTM’s simplicity and ease-of-use was also notable, as Miercom states in its report:
“Overall, the performance of the Sophos SG 135w desktop device was better than most desktop products. Additionally, Sophos has a quick and simple setup. Configuration was straightforward, and the graphical user interface (GUI) was clean and easy to navigate with a minor learning curve.”
Desktop vs. Rackmount
In a separate series of test, Miercom compared the Sophos SG 135w desktop model with the rackmount 1U appliances of the other vendors.
Rackmount models tested:
- Sophos SG 135w (desktop appliance)
- Fortinet FortiGate 100D
- DELL SonicWALL NSA 2600
- WatchGuard XTM 525
Is it really possible to get rackmount performance with a desktop form factor and price?
Well, in the case of the SG 135w, it is possible. The SG 135w’s baseline firewall throughput was 51% higher than the rackmount vendor average. Even in the most difficult test, the SG 135w had fantastic UTM throughput with all features turned on. Our desktop model had almost double the throughput of Dell SonicWALL NSA 2600 and performed only marginally behind the Fortinet FortiGate 100D.
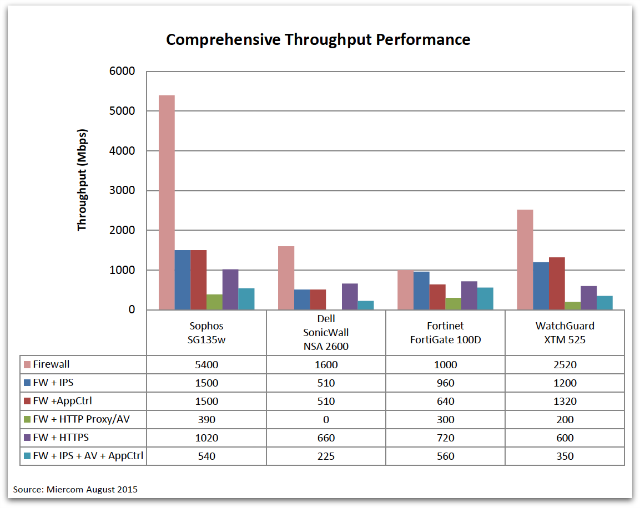
The Bottom Line
What do these tests prove?
The numbers speak for themselves – when measured against the toughest competition in the industry, Sophos SG Series wins with the best performance.
And because the SG 135w desktop model outperforms some of the more costly rackmount models from other vendors, these tests prove that Sophos offers an excellent price-to-performance ratio.
Finally, the tests prove that, with the SG 135w, you can have a UTM appliance that combines ease-of-use and cost effectiveness with performance – without forfeiting features or security.
You can download the full desktop and rackmount comparison reports from Miercom on sophos.com.
* The recently launched XG 135w has an identical hardware specification to SG 135w tested here. In fact all our SG Series and XG Series appliances have identical technical specifications; the XG Series just come preinstalled with different firmware, which is why we’ve given them a new name to differentiate. SG Series = UTM 9, XG Series = XG Firewall. Read more in our blog article about Sophos UTM 9.
Υou can read the original article, here.
People are always looking to save time and money, and hopefully both, with technology. Businesses and consumers love smartphones and computers because they are massively multi-functional, super-fast and efficient. We’ve been doing this for a long time – the spork, that funny looking multi-purpose utensil, dates back to 1874!
More recently, mobile application developers have used cross-platform development tools to increase efficiency in churning out apps that work in all three of the major mobile operating systems – Android, iOS and Windows.
Malware authors are no different. At SophosLabs, we have seen an increase in malicious apps written with cross-platform development tools such as PhoneGap, Titanium, Unity, Xamarin and Cocos2d.
SophosLabs researchers William Lee and Xinran Wu explain in a new research paper – Cross-Platform Mobile Malware: Write Once, Run Everywhere – that security researchers will face greater challenges analyzing and detect these pieces of mobile malware, as cybercriminals increasingly make use of multi-platform tools to hide their malicious code.
Their research demonstrates that malware authors are using cross-platform development tools “to hide their malicious code in HTML files or specific containers loaded by cross-platform frameworks instead of the platform’s native binaries.”
This fascinating research paper (presented earlier this month at the Virus Bulletin International Conference) explores in depth the feasibility of new cross-platform mobile malware and examines the package structures of these malware.
Finally, our researchers suggest a solution for identifying an application’s framework type and writing detection signatures for malware based on those frameworks.
You can check out this paper and other SophosLabs research on our technical papers page.
Υou can read the original article, here.
The release of Sophos XG Firewall with Security Heartbeat has made some headlines this week, and we’re pleased that analysts like John Oltsik of ESG are giving us great reviews. But real success is measured by the responses of our valued partners and customers.
Here’s some of the things we’re hearing from customers and partners about XG Firewall and our synchronized security strategy.
“You hear about large enterprise corporations being breached all the time in the news. What the news doesn’t report is the vast amount of small companies that are being breached and don’t even know it. When I heard that Sophos was planning on having their endpoint talk to their firewalls with the Security Heartbeat, I knew this would revolutionize the security industry and transform the way we help small and medium businesses protect their network. A firewall and an endpoint view threats incredibly differently and now that the two can have a conversation about what they see, security will be elevated to a whole different level. We already know that Sophos is a leader in both endpoint and network security, with proven products deployed worldwide. Synchronized Security and the Security Heartbeat now represent a fundamental shift in managing threats, which will upset not only hackers, but the competition as well.” – Brad Call, Systems Specialist, Internal IT (Sophos partner and customer)
“With the current landscape, threats move at a rapid pace. We’ve seen the security industry continue to come up with new layers of security for IT teams to buy and deploy. It’s refreshing to see that Sophos is taking a different approach to help us simply get more out of what we and our customers already have.” – Roy Busenius, President, Internal IT (Sophos partner and customer)
“What Sophos is doing with synchronized security is impressive. As a company, we are looking forward to how the network will be integrated fully with the endpoint, saving us the amount of time it typically takes to research threats, act on them, and actively manage security for the entire organization.” – Timothy Speakman, System Administrator, Contra Costa Health Services (Sophos customer)
“We are extremely excited about the Sophos product roadmap. The Security Heartbeat is remarkable, particularly when you consider how the firewall will communicate with the endpoint. This new technology is one of the most interesting features on the market and we look forward to where this new technology will take us.” – Kerrigan Addicott-Case, System Administrator, Office Information Systems (Sophos customer)
“There will never be a perfect security solution that stops all the threats. But with Sophos we are getting close to perfect. Sophos’s synchronized security allows everything to talk to one another and is a game changer for the industry.” – Michelle Drolet, CEO, Towerwall (Sophos partner)
Υou can read the original article, here.
By now you have likely heard the big news: Intel Security (formerly known as McAfee) has decided to discontinue selling all of its McAfee SaaS Endpoint offerings, as well as its line of SaaS email protection, SaaS email archiving and SaaS email encryption products (formerly known as MX Logic).
While this is no doubt troubling news for Intel’s partners and customer base, it is much better news for the Sophos partner community. Our partners now have a fantastic opportunity to sell to a broad base of disaffected Intel customers looking for a more stable security vendor.
Whatever Intel’s reasons for discontinuing their SaaS endpoint and email security products, we’re really bullish on the market opportunity for our own cloud-based email protection, archiving and encryption solution – Reflexion.
Email continues to be a major threat vector, allowing malware to get inside the network and sensitive data to get out. We’re investing in the best technology to defend against the latest email threats, and email security is a key product in our growing portfolio of cloud solutions.
Reflexion’s cloud-based email protection is a no-fuss solution to the constant problem of spam and email-borne threats. And we offer cloud-based email encryption as a great solution with minimal performance impact for organizations that need to meet compliance mandates and protect data against accidental loss or theft.
Many organizations in industries with regulations prohibiting the destruction of email communications can also depend on our Reflexion solution for archiving, discovery, and recovery services, with fast search and retrieval capabilities.
Sophos partners can already sell Reflexion products today, and soon all of Reflexion’s cloud email solutions will be integrated into Sophos Cloud.
We continue to believe that integrating Reflexion’s technologies into Sophos Cloud (named Security Product of the Year by PC Pro magazine) is a winning combination – for our customers and Sophos and Reflexion partners.
Sophos Cloud delivers all of your customers’ security needs, in a modular yet comprehensive and integrated fashion. It’s much more than just endpoint protection. Mobile, web, server – and soon, email protection – are available from the same web-based management console, hosted by us or by you as a trusted partner.
We’d like to help our partners take advantage of the enormous opportunity opened up by Intel’s departure from the SaaS endpoint and SaaS email security market, which is why we’re offering free conversions for Intel customers.
Steve Weeks, president of Sophos partner Netcetera, said:
“Migrating to a new solution provider can feel daunting and frustrating. At Netcetera, when one of our vendors was acquired by Google years ago, I initially worried about business disruption and unhappy customers. So it was a big relief when we switched to Sophos’s Reflexion email services. The migration process was smooth and, at the same time, we ended up with a better product and a superior vendor to partner with. I understand how partners working with McAfee must feel right now, but I’ve been telling my peers at other resellers that switching to Sophos is their best bet for a seamless transition. Choosing to work with Sophos has proven to be an excellent decision for Netcetera and our clients.”
We are so confident that you’ll enjoy the benefits of Reflexion that we are offering Sophos partners free migration assistance from Intel’s McAfee SaaS email products, which includes the configuration of customers and users, and the import of the whitelist and blacklist. Additionally, we have waived the ingestion fee of the email archive to Sophos’s RADAR archiving service.
We’ll be reaching out to our partners soon with more information on how you can get the most from this opportunity.
Visit our website to learn more about free migration to Sophos’s Reflexion email services.
You can read the original article, here.
The new SEP sesam 4.4.2. offers a wide range of new, revolutinary backup and restore features, including the support of the latest virtualization platforms, operating systems and applications.
Two highlights of the new release are the industry-leading restore of Microsoft Exchange and SharePoint via Drag and Drop, as well as the block-level based deduplication.
These functions are now also available for Windows-based backup servers and Remote Device Servers (RDS). Furthermore, the bandwidth-sparing replication solution for distributed environments is another great feature which saves time and money.
In SEP sesam 4.4.2 for Windows the software performance has been boosted to complete backups and restores considerably faster. The backup and restore performance is now up to 3 times faster than SEP sesam version 4.4.1 which significantly reduces backup and restore times in windows
environments.
Visit the Release Notes for all new features.
A lot of people are talking about our new Sophos XG Firewall with Security Heartbeat and our vision of synchronized security. Our customers and partners, industry analysts, and the security press are talking about it. There’s a buzz in the air.
And with good reason. You hear phrases like “revolutionary,” “game changing” and “the next thing in next-gen.” Synchronized security is very big deal.
It took all of us at Sophos coming together to execute our strategy of synchronized security. But who better to talk about what synchronized security means for us, and the broader security industry, than those who set the vision and strategy that guide our company? The Sophos senior management team, led by our CEO Kris Hagerman, recently sat down to record their thoughts in a short video.
Kris talks about the challenges the security industry is facing – the increasing attacks, and the growing sophistication and coordination of the attackers. The old security strategies just aren’t enough anymore.
Traditionally the answer has been adding a whole bunch of security products – like security guards protecting a castle – and then adding more when that doesn’t work. Sophos is coordinating those protectors like no one has before.
“What we’re doing at Sophos, really for the first time, is we’re giving those guards radios,” Kris says. “So we’re giving the individual products, the security guards, the chance to communicate with each other.”
“For the first time, we’re taking the next-gen firewall technology and the Sophos endpoint technology, and having them communicate. Putting a heartbeat, putting a pulse between these two formerly isolated islands within security defenses,” says Chief Marketing Officer Matt Fairbanks.
Sophos Chief Technology Officer Joe Levy says the industry has been using the right “ingredients” for security, but not the right “recipe.” Sophos Security Heartbeat allows network and endpoint to exchange contextual information, forming a complete security system.
“Synchronized security is the future of the direction that security is going to have to go. While we as a vendor are the first to deliver this, I consider it inevitable that the rest of the industry follow suit,” Joe says.
Watch the video to hear more from our leadership team about our vision for synchronized security, and what makes it so emblematic of our mission of “security made simple.”
Υou can read the original article, here.






























