News
Apple has made iOS 10 available and will push upgrade notifications out to devices over the next few days. Some early adopters even have iOS 10 already installed!
Good news – Sophos Mobile Control is ready with same-day support of iOS 10. Once iOS 10 is loaded onto your users’ devices, it’ll be supported by all components of Sophos Mobile Control.
For a comprehensive list of iOS 10 features, please visit Apple’s iOS product page. Another good source of information about iOS 10 and the newly-announced Apple gadgets is Digg.com’s live blog from Apple’s recent iPhone 7 keynote.
As long as your users are using the latest versions of Sophos Mobile Control apps, there’s nothing you need to do to fully support iOS 10 across your Sophos Mobile Control estate. We’ve already tested against the various alpha and beta versions of iOS 10 and have modified Sophos Mobile Control to be compatible whenever your users are ready to update their devices.
You can read the original article here.
We’re excited to announce that the new Gartner Magic Quadrant for Unified Threat Management* is out, and Sophos is positioned in the Leaders Quadrant for the fifth year running.
We continue to be one of only three vendors in the Leaders Quadrant. And we think that says a lot about our standing in the eyes of customers, partners and industry analysts.
The Magic Quadrant is based on an assessment of a company’s ability to execute and completeness of vision.
Our strategy for the mid-market and our channel is clearly working very well as we deliver on our promise to make security simple with unique innovations that make our UTM products easy to deploy, manage and use. As a result, more and more partners and customers are turning to Sophos for their next firewall and UTM. In fact, the momentum in our growth is outstanding – more than triple the industry growth rate.
With the launch of our new and innovative XG Firewall and Synchronized Security we are also delivering on our vision for the future of IT Security where security components work better together to improve protection and respond to incidents. And with more and more IT infrastructure moving to the cloud, our leadership in protecting IaaS further reinforces our ability to anticipate important trends impacting your business and ensure your network is secure everywhere.
As the only IT security company to be positioned as a Leader across both Unified Threat Management* and Endpoint Protection Platforms** – we think our complete security offerings uniquely position us to deliver on the next generation of protection – Synchronized Security.
You can access the Magic Quadrant for Unified Threat Management report here (registration required).
You can read the original article here.
The Shadow Brokers are a self-styled hacker group that recently kicked off a tongue-in-cheek media campaign claiming that they’d penetrated the NSA (or someone like that – they’re referring to the victim as the Equation Group).
Shadow Brokers say they’ve made off with a virtual warehouse of tip-top “cyberweapons” that they plan to auction off.
To help you believe they have some good stuff in the auction files, they’ve released a bunch of hacked data for free, including documents, programs, scripts, exploit code and so on.
Interestingly, there’s more free stuff (191MB compressed) than there is data up for auction (134MB compressed):
-rw-rw-r– 1 bloke staff 134289064 25 Jul 10:49 eqgrp-auction-file.tar.xz.gpg
-rw-rw-r– 1 bloke staff 191282372 25 Jul 10:50 eqgrp-free-file.tar.xz.gpg
We can only assume that the “auction” is supposed to be interpreted as a giant lampoon of the buying-and-selling-of-exploits scene, because the terms of the auction are absurd:
- There’s no cutoff time for bidding. The crooks will stop collecting bitcoins and pick a winner if and when they choose, which could be any time (or never).
- You’re not allowed to know what you’re buying. It’s a secret.
- The crooks keep every bid you submit, whether you end up winning or not.
- Once the total of all bids gets to BTC 1M (over $0.5B), everyone in the world gets everything for free.
Actually, for all the tongue-in-cheek here, the Shadow Brokers crew make an excellent point when they explain why they aren’t giving away the list of cybermaterial:
Q. What is in auction files? A: Is secret. Equation Group not know what lost. We want Equation Group to bid so we keep secret. You bid against Equation Group, win and find out or bid pump price up, piss them off, everyone wins.
That’s a common problem after a data breach: not knowing quite how bad it really was, with the result that in your official breach disclosure you have to assume and describe the worst that could have happened.
When a crook breaks into your flat and steals your widescreen TV, you can tell, because there’s a huge area of blank wall where the TV used to be.
But when a crook wanders into your network and steals your data, it’s a different sort of theft: all your data’s still there, as well as being in any number of other places as well.
What we know
What we do know from the Shadow Brokers eqgrp-free-file.tar archive is that something was stolen or leaked by someone, at some unknown earlier time.
Whether it’s only being leaked now by the original thieves, or whether it’s been re-stolen by a new lot of crooks, we don’t know.
But at least one of the exploitable vulnerabilities amongst the free files, found in the Firewall/EXPLOITS/EXBA/ directory, not only works, but also turns out to have been a zero-day bug.
EXBA is short for EXTRABACON, and the EXBA script is documented like this:
#CISCO ASA SNMP exploit script
#Works on most 8.x(y) versions through 8.4(4).
#Do not use against unknown or unsupported versions
The files in the archive are timestamped June 2013, for what that’s worth, and the affected Cisco ASA versions listed date from 2007 to the start of 2012.
ASA is short for Adaptive Security Appliance, one of Cisco’s firewall products.
The bug was obviously news to Cisco, who quickly and creditably responded with a detailed analysis of the flaw.
What to do?
As far as we can see, the exploit and shellcode that Shadow Brokers published for this vulnerability almost certainly won’t work as they stand against any recent version of the Cisco ASA product.
Nevertheless, because the bug was never disclosed, it remained in Cisco’s code.
That means a determined attacker has a huge head start at finding an exploit for recent Cisco ASA products, even if both the EXTRABACON script and its associated attack code needs work.
In other words, check out Cisco’s writeup to check if you’re at risk and, if so, what to do about it.
You can read the original article here.
Being an IT security professional isn’t easy these days; the cyber threat landscape is constantly evolving. Ransomware, Trojans, Malware, and distributed denial of service (DDoS) attacks are some of the most common types of threats. Each has different vectors and flavors, and each brings its own risks and costs. IT pros clearly need multiple layers of security, but which layers are most important? Common solutions range from firewalls to anti-virus software and network intrusion and advanced persistent threat tools.
With all those threats, we understand it must be hard to prioritize which security solutions are the most important to implement. However, DDoS attacks are increasingly common and growing more dangerous and sophisticated, so if you don’t have an anti-DDoS solution in place, consider the risks. Can your network threat defense handle a DDoS attack? It’s proven that intrusion prevention systems and firewalls are no match for DDoS attacks.
If you think your organization is unlikely to be a DDoS target, think again; you don’t have to be a high-profile company or organization to be a victim of DDoS. When most people think of DDoS, they think in terms of the incidents that make headline news, when attacks take a website or application offline. However, DDoS hackers seldom launch attacks to take a website offline. An overwhelming majority (93%) of DDoS attacks are under 1Gbps, and last less than 30 minutes. That may sound harmless, but it’s not. Increasingly hackers use “Dark DDoS” attacks as a smokescreen for more destructive, stealthy cyber-attacks.
Sometimes IT security staff don’t even realize when their website or application is undergoing a DDoS attack. Other times, the attack is noticed, but while the IT security staff are busily investigating why their network performance is dragging, the cyber criminals are equally busy behind that smokescreen, testing for network vulnerabilities, installing malware, stealing intellectual property or exfiltrating sensitive data from your network. By the time IT security staff discover the true source of the problem, the hackers probably did plenty of damage. Even if security staff “swing” the traffic out to a cloud-based scrubbing service, that usually takes 10-30 minutes to enforce.
That’s why investing in automated, inline network threat protection may be your wisest move; it detects and blocks even the smallest DDoS traffic packets. There are many security issues that beg for attention, but DDoS attacks pose a double threat because while they sometimes cripple a website, they more often mask more nefarious and damaging network infiltrations. IT security professionals can cover two bases by having an anti-DDoS appliance in place.
You can read the original article here.
In many parts of the world right now we are right in the middle of back-to-school season. Kids are getting excited to see their friends again and head back to the classroom, and are preparing for the best possible experience in school this year.
But what about at home? With so much of a child’s social life, homework and playtime happening online nowadays, you want to make sure their experience on the internet is as safe and fun as possible.
We have a number of tips that your kids can use to be safer online and on social media. But no matter how careful or internet-savvy your kids might be, criminals are always coming up with new ways to cause problems and find their way into your home computers.
Thankfully, Sophos Home can help. It brings our commercial-grade security straight to your home computers, completely for free. And, it’s just been given a great rating by Tom’s Guide!
Here are 6 ways Sophos Home can protect your kids this school year:
1) Web filtering: Sophos Home offers 28 web filter options, giving you the ability to allow, warn, or block entire categories of websites from your children’s computers. Categories range from blogs and chat sites to gambling and pornography.
2) Web and phishing protection: Even if kids are surfing good sites online, bad things can still happen. We can prevent access to sites that have been unknowingly compromised by malware and prevent kids from being redirected to fake websites posing as the real thing.
3) Potentially Unwanted Application protection: Worried your kids could be downloading apps and programs on their computer that are full of ads, spyware and other issues? Sophos Home can detect and prevent these applications and programs from installing or running.
4) Antivirus/Antimalware: Sophos Home can stop and remove malware that would allow cybercriminals to steal information and spy on your children.
5) Management: Multiple kids in multiple places? Sophos Home can manage and protect up to 10 Macs and PCs on one account, no matter where in the world they are located.
6) Money: Kids cost a lot of money. Sophos Home can protect them all without a penny, shilling, kopek, cent or any other currency you can think of.
We’re a little bit biased, but we think Sophos Home is the ideal way to keep your kids safe online this year, and give you one less thing to worry about.
You can read the original article here.
Sophos officially announced the release of Sophos Email, our brand new secure email gateway solution, as an addition to our Email product range and our Sophos Central management platform.
It’s engineered to provide our leading threat and spam protection to users of Microsoft Exchange Online, Office 365, Google Apps for Work and many other email services. And from what we heard in our recent email security survey, users of cloud-based email services like these are in desperate need of the extra protection it delivers.
We conducted the survey among our Spiceworks community and readers of Naked Security.
We’re just starting to analyze some of the results and they make for interesting reading.
First, they confirmed that businesses are rapidly shifting to cloud-based email with a total of 38% using it today as their primary email platform.

Many are also choosing to use the cloud for security too, with 43% of respondents using a cloud-based service for email security – almost double the percentage of those using the next most popular solution of dedicated email hardware appliances (22%).
18% of our respondents are using email protection as part of their UTM hardware appliance. Virtualized dedicated appliances (12%) were also a popular option, although only 5% were using a virtualized UTM.

When we asked users of the most popular cloud-based email platform – Microsoft Office 365 – about their biggest concerns, system reliability (fear of service downtime or outages) and lack of security came top of the list.

It’s not surprising reliability was a top concern – recent outages are clearly in people’s thoughts.

In terms of security, it’s clear that IT teams are not confident in the security they are getting with Office 365 – 50% of Office 365 users agreed that third party security solutions are essential to extend Office 365 security.

This tallies clearly with Gartner’s prediction that, by 2018, 40% of Office 365 deployments will rely on third party protection – an increase from under 10% in 2015.
Ransomware, malicious attachments, malicious URLs, viruses and phishing were the top five security threats people were worried about, with over half the respondents saying they were very concerned about these threats. Despite this recognition of email-borne threats, over a quarter of respondents admit that they rarely or never review their email security policy to check if it is effective.

We also asked our participants which features are most needed to improve their current solutions. It seems advanced sandboxing solutions, such as Sophos Sandstorm, and data protection features, including encryption and data loss prevention, are the most sought after.
Time-of click protection, which checks URLs in emails as people click them and not just when the email is received, was also a highly requested addition to counter those worries about malicious URLs.
We’ll look more closely into the numbers over the coming weeks. For now, the message is pretty clear – IT teams recognize that email is a primary threat vector, infrastructure and security is moving to the cloud, and businesses are looking for extra protection to make sure they don’t fall foul of the ever-increasing number and sophistication of threats.
So we believe Sophos Email is great for those who are looking to move their email infrastructure and security to the cloud.
And, because Sophos Email is part of Sophos Central, it can be managed right alongside Endpoint, Mobile, Server, Web and Wireless, meaning better security is matched by increased efficiency too.
If you haven’t moved to the cloud just yet, a Sophos Email Appliance or UTM solution may help give you peace of mind.
If you’d like to take a look at Sophos Email or any of our Email products, simply start a free 30-day trial.
You can read the original article here.
We’re honored to announce that Sophos has won three distinguished categories in CRN’s 2016 Annual Report Card (ARC).
Following on from last year’s success, we were named overall winners in both the Network Security category and the Data Security category, as well as receiving the highly regarded Product Innovation award in the Endpoint Security category.
CRN’s study recognizes those technology vendors most highly praised by their solution provider partners, and for over three decades has been a benchmark for quality within the IT channel.
Using the feedback of more than 2,480 solution providers, this year’s honorees were chosen from the results of an extensive, invitation-only survey by The Channel Company’s research team. Participants were asked to evaluate their satisfaction with 80 vendor partners in 24 major product categories.
Kendra Krause, vice president of global channels at Sophos, said she’s delighted with the win:
“We are a next-generation security company with an unparalleled dedication to our channel partners and I am honored that once again our efforts are recognized by those we serve. Winning CRN’s ARC awards validates Sophos as a channel leader that continues to drive the IT security market forward.”
You can read the original article here.
We’ve just updated Sophos Server Protection in Sophos Central, adding next-generation malware prevention and detection techniques for server environments. Solid server security starts with good operational hygiene, which includes restricting who and what can reach the server, and what applications can run.
We’ve now made that easier in Sophos Central Server Protection with the inclusion of:
Malicious Traffic Detection on both Linux and Windows servers: Malware frequently connects to remote servers for further instructions, updates or uploads of data. Malicious Traffic Detection, or MTD, monitors traffic for signs of connectivity to known bad URLs. If malicious traffic is detected, suspect executables are scanned on all servers licensed with Sophos Central Server Protection Advanced and can be blocked on Windows servers.
Peripheral Control: For physical servers, good operational hygiene should include limiting access via peripheral devices, including removable storage, modems and devices such as phones, tablets and cameras. With Sophos Central Server Protection, customers can monitor (Standard license) and block (Advanced license) the use of peripheral devices for their servers with ease.
Application Control: You can now define policies to allow or block certain categories of known applications on servers. This is in addition to our Server Lockdown feature, which doesn’t allow any applications to run other than those explicitly allowed. (Applicable for Windows servers with Advanced licenses).
Download Reputation: We provide a trustworthiness score for each downloadable file, based on SophosLabs research, giving you reassurance that you are downloading only safe files to your server. This is now available with either the Standard or Advanced licenses on Windows servers.
You can get a free trial of Central Server Protection Advanced here. Customers of Central Server Protection Advanced will automatically receive these updates.
You can read the original article here.
Sophos Endpoint Protection has been awarded 2 AAA awards from SE Labs. The top awards come in the latest round of independent tests conducted for Enterprise and SMB companies looking for endpoint protection.
We make every effort to participate in several independent tests, so you don’t have to take the word of us or any other vendor about our products’ efficacy.
SE Labs was created by Simon Edwards, the former technical director of the now-defunct Dennis Technology Labs. Simon is also the former chairman of the Anti-Malware Testing Standards Organization (AMTSO), to which SE Labs and Sophos both belong. In other words, he knows a thing or two about testing security products.
SE Labs’ tests expose products to a variety of malware and simulated exploits. They attempt to use realistic methods to deliver the threats (e.g. email attachments, web downloads, etc.). The lab produces three separate reports: Small Business, Enterprise, and Consumer Endpoint Protection. Sophos Endpoint Protection was included in both the Small Business and Enterprise reports.
Sophos earned a “total accuracy” score of 98% in both the Small Business and Enterprise reports. Total accuracy is a calculated score that accounts for the degree of protection and the rate of false positives.
The SE Labs tests are very relevant to buyers of endpoint protection, as they highlight the need for multiple prevention and detection technologies. The Enterprise report noted that the products which achieved the best results did so “due to a combination of their ability to block malicious URLs, handle exploits and correctly classify legitimate applications and websites.”
Choosing an endpoint protection product that uses multiple techniques to help you prevent, detect and respond to threats is a vital part of your security strategy, and we are delighted that the SE Labs tests have independently verified Sophos’ capabilities on behalf of enterprises and SMBs alike.
You can read the original article here.
It’s official: the highly anticipated public beta for the Sophos XG Firewall v16 is now underway, and we’d love for you to get involved. The product team has been working furiously for the last several months making this one of the most ambitious and exciting product releases ever. It’s loaded with tons of new features and enhancements that we think you’re going to love.
What’s New
- XG Firewall v16 brings over 120 new features and a long list of optimizations and enhancements. The key focus areas for this release:
- Improving the user experience to make it faster and simpler to manage.
- Adding features to provide parity with SG UTM.
- Adding more innovative Synchronized Security features.
The highlights include:
- All new navigation, enhanced control center and improved UI across many areas
- Redesigned Secure Web Gateway style web policy model with inheritance
- Full Email MTA with store and forward capabilities
- Two-factor authentication (one-time-password) support
- New Security Heartbeat and Synchronized Security features
- Microsoft Azure Support
…And so much more!
See what’s new in v16 for complete details on the enhancements and new features.
We want you! We highly encourage you to participate in testing this beta and help make this release the best it can be. Please head on over to our Beta Community Forums to get the latest beta firmware, meet your fellow beta testers and Sophos staff, and share any issues or feedback you have.
XG on Azure
If you’d like to preview XG on Microsoft Azure, send us a request with your Azure subscription ID to azure.marketplace@sophos.com. We’ll whitelist your account for preview access and provide instructions on how to launch XG from the Azure Marketplace.
Learn More about XG Firewall
Learn more about Security Heartbeat and see Sophos XG Firewall in action at sophos.com/xgfirewall. And if you want to get hands on, try it out with our free home edition or sign up for a 30-day trial in your business.
You can read the original article here.
It may be summertime in the Northern Hemisphere, but the first week of August has been marked by a blizzard. A virtual blizzard, that is, of distributed denial of service (DDoS) attacks on some gaming companies. Rockstar Games’ Grand Theft Auto 5, Nintendo Pokémon GO, the PlayStation Network and Blizzard’s Warcraft and battle.net were all affected. The hacker group PoodleCorp claimed responsibility for the DDoS attacks, and says that it plans larger attacks.
It’s not at all surprising that hackers conduct DDoS attacks on gaming companies. When thousands of online gamers are locked out or booted off their games, it gets the attention of the media. Because hackers are often motivated to gain notoriety, the attacks work well for them.
What is surprising, however, is that some gaming companies have not deployed technology to detect and mitigate such attacks. The technology to do so is readily available, and more affordable than ever.
The stakes are high for the gaming companies because when they lose players they lose revenue. In addition, they lose money in terms of spending staff time to troubleshoot DDoS attacks, around the clock, which is expensive. One Corero customer, Jagex, experiences up to 10 attacks per day; fortunately they’re able to detect and mitigate those attacks—without consuming IT security staff time—by using Corero’s family of DDoS Mitigation Hardware.
There is no drought of DDoS attacks now, and analysts forecast that DDoS attacks will only increase in frequency, volume and sophistication. Until gaming companies get smart and defend their network perimeter, they’ll lose the battle against hackers many times in the future.
You can read the original article here.
We’re excited to announce the upcoming launch of Sophos Intercept, ushering in a new era of endpoint protection for modern threats. It’s our new signatureless anti-exploit, anti-ransomware, and anti-hacker technology that includes root-cause analytics and advanced malware cleanup – all managed via the Sophos Central Admin console.
You’ve undoubtedly seen countless headlines about crippling ransomware attacks that cost people hundreds of millions of dollars each year. With Sophos Intercept, we’ve integrated powerful ransomware protection that’s capable of automatically stopping ransomware attacks as soon as they’re detected and rolling back damaged files to a known and safe state.
Ιntercept also includes advanced anti-exploit technology that blocks zero-day threats without the need for traditional file scanning or signature updates. In addition, we’ve added automated forensic reporting that traces attacks back to their origins, pinpoints additional infection points, provides advanced cleanup of malware, and offers prescriptive guidance for strengthening your organization’s security posture. Sophos Intercept also includes comprehensive deep-cleaning technology, which hunts spyware down that other traditional AV misses and rips out deeply embedded, lingering malware to make remediation a snap.
At launch later this year, Sophos Intercept can be installed alongside existing endpoint protection to fend off unknown exploit variants and stealth attacks that traditional cybersecurity software might miss – all with minimal impact to system performance. Intercept will be available as part of our own Sophos Central-managed lineup as Endpoint Ultimate, which combines Endpoint Advanced and Intercept into a dynamic, complete endpoint protection solution.
We’ll be rolling Intercept out later in 2016, but we invite you to take it for a spin today alongside our advanced endpoint protection. If you’re already a Sophos Central customer, simply contact your partner for a beta code; if you’re new to Sophos, please sign up for a free 30-day trial account of Sophos Central to get started. A public beta program is due to open later.
You can read the original article here.
Organizations can be overwhelmed with a constantly evolving cyber threat landscape. There is no shortage of threats, but there is a shortage of trained IT security personnel to guard against them. In particular, the UK, US and Canada are experiencing a shortage of network engineering professionals who have distributed denial of service (DDoS) mitigation skills, according to SC Magazine:
“It is believed that the demand for network engineers with DDoS expertise is growing due to the rise of volumetric attacks on organisations. Whether they build or outsource their DDoS mitigation, organisations require a specialised resource in their IT departments to focus on internal solutions or actively manage vendors”.
Indeed, DDoS is a growing threat, and it’s one that traditional/legacy DDoS mitigation solutions don’t handle as effectively anymore. Legacy solutions, such as centralized scrubbing services, rely too heavily on high thresholds and human intervention (that is, if you can even find network security engineers to fill those positions). Fortunately, a new generation of DDoS protection hardware is available which requires little to no intervention from onsite specialist security engineers.
Automation Reduces Errors
DDoS attacks are increasing in complexity and frequency. They are decreasingly the large, volumetric, attacks that catch the eye of IT security staff (Corero research shows that 93% of attacks are under 1 Gbps). Hackers have become more sophisticated in their techniques by launching specially crafted low-level, multi-vector, attacks that evade traditional scrubbing solutions. Unlike an automated DDoS protection solution, human security agents are seldom able to detect granular, lower-level DDoS attacks that 1) drag down network performance and 2) create smokescreens for attackers to access critical information without being spotted.
Humans make errors, or can’t react fast enough, whereas Corero’s DDoS protection hardware (SmartWall Threat Defense System) is highly automated, catching close to 100% of volumetric DDoS attacks, before they enter your network. For organizations that are short-staffed in their IT security departments, Corero technology offers the following significant benefits:
- Does not require the complex deployment of traditional DDoS protection solutions
- Delivers largely automated protection: it’s an always-on solution with no manual intervention required to detect and mitigate the majority of DDoS attacks
- Can be fully managed by SecureWatch, a Corero service which combines state-of-the-art monitoring and reporting technology, along with highly experienced engineers, to support customers before, during and after an attack.
Stephen Clark, Director of IP Networks at Block Communications Commercial Telecommunications, reported that Corero’s automation feature is something that no other vendor offered:
“We specifically value the automated attack mitigation functionality. Corero’s Security Operations Center monitors conditions for us and responds accordingly. Our team monitors traffic but we don’t have to worry about it. We set it and forget it.”
In general, IT security staff welcome the SmartWall approach because it gives them more time to detect and mitigate other cyber threats.
You can read the original article here.
The iboss Cloud Secure Web Gateway Platform was rigorously tested by the engineers at Meircom Labs and earned their security certification, while showing an unrivaled ability to stop more evasive threats. Here’s a summary of the Meircom findings: The iboss Cloud Secure Web Gateway Platform had substantially higher detection rates than the industry average (97.4% efficacy against Malware samples outperforming the industry average by 14.9%).
Also the iboss solution detected 100% of all malware leveraging the TOR Dark Web to mask communications (iboss achieved 100% efficacy in detecting malware using TOR and other file sharing methods). Miercom said about that amazing ability: “This category of stealth malware requires a high level of discernment by a Secure Web Gateway that many security products are not capable of.”
The iboss Cloud Secure Web Gateway Platform achieved 100% efficacy detecting advanced Mobile Malware, and that is very important, because the increasing role mobile devices play in the modern enterprise and their unique consumerized nature make them an attractive attack surface and exploit target.
The iboss solution achieved 97% efficacy detecting advanced Polymorphic and Zero-Day threats and that is a huge advantage for iboss as compared to other network security products (iboss ability to detect advanced Polymorphic and Zero-Day threats with 100% efficacy).
Furthermore, iboss has real-time detection and Incident based reporting that’s more effective (iboss automatically consolidates and prioritizes events, translating them into actionable incidents; shortening investigative response time and reducing data loss when breaches occur).
You can read the original article here.
Sophos Mobile Control has been given five stars and the “Best Buy” award from SC Magazine, beating AirWatch, IBM and Citrix in the publication’s latest review of mobile device management solutions.
We’re delighted that Sophos Mobile Control came out on top, and received a perfect five out of five stars in all categories in the July 2016 issue.
The review editors at SC Magazine were full of praise for Sophos Mobile Control: “Out of the gate we need to say that this product impressed us.”
“Full of features and relatively easy to deploy and support – excellent documentation.”
“… this is the right way to deploy complicated products or systems.”
“For its strong feature set, value for money, ease of use and deployment, we make this our Best Buy.”
Even the magazine’s customary section about the negative points of each product reads like a ringing endorsement: “Weaknesses: None we can find.”
You can check out the full review on the SC Magazine site, and learn more about Sophos Mobile Control at sophos.com/mobile.
You can read the original article here.
Back in April we announced the release of Sophos Central (previously Sophos Cloud) with its all-new integrated management platform. This marked a major step forward in simplifying security management in an industry that has been increasingly trending toward complicated point products.
We’ve been steadfast in our belief that powerful, feature-filled, and industry-leading security should be integrated and uncomplicated. Today we take another step forward in delivering on that vision, as we add Sophos Wireless to the ever-expanding Sophos Central protection portfolio.
If Maslow was creating his “Hierarchy of Needs” today, wireless access would be right there in the physiological needs alongside food and water. Because of our incessant demand to be connected for personal and business reasons, the cloud-managed Wi-Fi market continues to grow at an exceptional rate, with market analysts suggesting it shows no sign of slowing down anytime soon.
At Sophos we’ve already seen great success with our UTM/Firewall managed wireless and so the next logical step for us was to extend our offering, and bring the simplicity Sophos is famous for to the cloud-managed wireless space. In doing so, we’ll help our partners and customers meet the needs of their wireless-hungry users simply and securely.
Administrators will now be able to configure and manage wireless networks directly from the Sophos Central Admin console. Our new Sophos Wireless service uses our range of Sophos Access Points which, if partners and customer prefer, can be managed via Sophos SG UTM and XG Firewall.
Sophos Central managed Sophos Wireless has all the key features required for essential wireless setup and control, including:
- At-a-glance dashboard with network and client connectivity data
- Traffic usage insights based upon web categorization
- Easy multi-site management and setup
- Visual network planner and Google Maps integration
Our three-week Sophos Central development cycle allows us to rapidly add deeper functionality and pave the way for unique Synchronized Security innovations in the future. As we’ve done with Endpoint and Firewall already, we plan to enable wireless networking to talk with other Sophos Central security services like Endpoint, Mobile, Web and Server security to help elevate levels of protection.
The addition of Wireless to Sophos Central adds to what has been widely recognized as an incredibly powerful and easy-to-use tool for managing endpoint, mobile, web, and server products. Sophos Central lets our Partners, our customers and their end-users get the most out of security:
- Sophos Central Partner helps partners manage and track their business, identify revenue opportunities, and features seamless jump-points to Sophos Central Admin.
- Sophos Central Admin leads the way when it comes to real-time, synchronized security. The identification and remediation of threats becomes a simple one- or two-click affair.
- Sophos Central Self Service makes it easy for end users to work with quarantined email and, in the future, bring-your-own-device provisioning, data encryption, Wi-Fi setup and much, much more.
But we’re not stopping there – we’re going to keep making Sophos Central stronger to ensure it continues to strike a balance between powerful functionality and ease-of-use.
Watch out for more news coming very soon about another new service we’ll be adding later this year. To find out more about Sophos Wireless visit sophos.com/wireless.
You can read the original article here.
Distributed denial of service (DDoS) attacks make headlines when they are 1) large enough to cripple a website and 2) the affected website belongs to a recognizable organization. For example, we’ve seen news stories about attacks on websites with many users (such as PlayStation, a gaming website) or websites that serve a critical function (such as the South African State Broadcasting Corporation). However, most DDoS attacks are not large, volumetric attacks, and DDoS hackers target all kinds of organizations, not only big, household name companies or government agencies. No website or online application is immune to DDoS, and any size DDoS attack is cause for alarm. You see, DDoS is not just a web availability issue; it’s a security issue.
Corero research has shown that the vast majority (93%) of DDoS attacks are under 1 Gbps, and 96% last less than 30 minutes. That’s certainly not enough to cripple a website. So why would hackers launch such attacks, and why should companies care, as long as their network remains up and running?
DDoS Can Mask Security Breaches
Cyber criminals launch low-threshold DDoS attacks— also known as “Dark DDoS”—because they are a cheap and easy way to infiltrate and map a network. Because the attacks are so short – typically less than five minutes in duration – they are usually not detected by security teams or traditional DDoS scrubbing solutions. Because these attacks typically require very little bandwidth to execute, they are nearly impossible to detect without an advanced in-line DDoS protection solution that has granular detection capabilities.
In cases where the IT security staff do notice a DDoS attack in progress, the attack often serves as a decoy to distract security staff while hackers stealthily find pathways and test for vulnerabilities within a network. Hackers may install malware to ex-filtrate sensitive data such as email addresses or credit card numbers or corporate intellectual property. In addition, hackers may “own” or “enslave” the network so it can later be exploited as a bot in a botnet “zombie” army.
DDoS is Often a Precursor to Ransom
Another cause for concern is that DDoS are usually used as a precursor to ransom attacks. Once the hackers find your network’s vulnerabilities, they can either install ransomware, or they can threaten to launch a truly crippling, large volume attack. Either way, the cyber criminals will demand that you cough up some bitcoin to avoid or stop the ransom attack.
Partial-Link Saturation Leads to Performance Degradation
Sub-saturating DDoS attacks cause network congestion and service degradation. This is especially important in a Carrier (Internet Service Provider or Hosting Provider) environment because 1) even small attacks can saturate a customer downstream, and we all know that in an always-on world, network reliability is crucial for subscribers, 2) DDoS traffic is costly to transit across the network, and 3) downtime impacts Service Level Agreements (SLAs). In the highly competitive Carrier arena, SLAs often promise optimum network reliability; the only way to guarantee that is by using an always-on, in-line DDoS mitigation appliance.
Solutions for Effective DDoS Mitigation
The fact is that legacy DDoS mitigation solutions, such as scrubbing, completely overlook the small, low-threshold attacks. Just because a DDoS attack is small doesn’t mean it isn’t a huge problem. It takes hackers only a few minutes to map a network, steal date, install malware, or discover your network vulnerabilities; by the time security staff notice a low-threshold attack in progress and divert traffic to be cleaned at an out-of-band scrubbing center, the damage has likely already been done.
You can read the original article here.
At Sophos, we’re committed to taking a fresh approach to complex problems. In November, we announced synchronized security: no longer does security mean making sense of piecemeal tools and reacting to alerts. With synchronized security, your security solutions communicate with each other both across the network and on endpoints to mitigate risks and stop data loss instantly.
A sophisticated security program shouldn’t just be limited to protection at the firewall and endpoint level of course – your files need to be protected too, wherever they reside, at all times. That’s why Sophos SafeGuard Encryption 8 – launched today – now offers automatic, always-on file-level encryption on endpoints, mobile devices and in cloud storage — across Windows, Mac, iOS and Android.
No longer does file-level encryption mean lengthy set-up by administrators or hand-selecting what files to encrypt. Your users’ files start by default with the highest level of security to keep their sensitive information out of the wrong hands, and from there they can choose to opt-out specific files.
Better yet, it’s all made even more effective and effortless with synchronized security, our coordinated incident response technology.
Three dimensional trust delivers the most secure file-level encryption available
Most encryption technology relies on “user-level trust” which authenticates a user in order to give that person access to the appropriate data. However, if a user’s credentials are compromised then it’s easy for a hacker to gain access to encrypted data.
Sophos Safeguard Encryption 8 takes authentication to a whole new level by verifying trust in 3 dimensions – user, application, and device. So even if a hacker gained access to your credentials, they are still unable to read encrypted data if they are using a foreign device or application.
This level of verification is an industry first and is transparent to the user. The only time your end users will even know their files are protected by encryption is if they’re trying to access something they shouldn’t be.
Encryption works seamlessly with synchronized security
Encryption has always been a core solution for data protection, but we’ve now enabled it as a threat protection technology through integration with our synchronized security capability. For example, if an endpoint detects a compromise, the system health status is changed from a “green” state to “red”, indicating the system is no longer trusted. No matter how they got in, the attacker is stopped dead in their tracks from getting access to sensitive data.
Once the situation is resolved, and the endpoint’s health status is restored to a “green” state, the encryption keys are automatically replaced and the user regains access to all of the encrypted data on the system. This same easy and automatic protection applies to all endpoints and files on your network.
SafeGuard Encryption 8 delivers next-gen data protection across your entire enterprise from mobile phones to tablets, and from endpoints to cloud storage.
This technology is available today from Sophos. You can learn more about Sophos SafeGuard Encryption here, and more about our synchronized security technology at sophos.com/heartbeat.
You can read the original article here.
Corero polled over 100 IT security professionals at Infosecurity Europe 2016 in London last month, and the survey shows that UK businesses are not only worried about distributed denial of service (DDoS) attacks, they want better DDoS protection from Internet Service Providers. Over three quarters (80%) of the IT security professionals polled believe that their organization will be threatened with a DDoS ransom attack. Even more concerning was the finding that almost half (43%) of the security professionals who took part in the survey thought that it was possible that their organization might pay such a ransom demand.
Without doubt, there is a growing threat of cyber extortion attempts targeting UK businesses. Last month (May 2016), the City of London Police warned of a new wave of ransom driven DDoS attacks orchestrated by Lizard Squad, in which UK businesses were told that they would be targeted by a DDoS attack if they refused to pay five bitcoins, equivalent to just over £1,500. Corero’s Security Operations Centre also recorded a sharp increase in hackers targeting their customers with such demands at the end of 2015.
Dave Larson, COO at Corero Network Security, said: “Extortion is one of the oldest tricks in the criminal’s book, and one of the easiest ways for today’s hackers to turn a profit. When your website is taken offline, it can cost businesses over £5,000 a minute in lost revenue, so it’s understandable why some choose to pay the ransom. But this is a dangerous game, because just a few willing participants encourage these threats to spread like wildfire. Rather than trying to negotiate with criminals, the only way to beat these attacks is to have a robust, real-time DDoS mitigation system in place, which can defend against attacks and prevent downtime.
“Like old cousins, ransom demands and DDoS are always being used together in inventive new ways to extract money from victims. For example, low-level, sub-saturating DDoS attacks are usually used as a precursor to ransomware attacks. Because they are so short – typically less than five minutes in duration – they are usually not detected by security teams and allow hackers to find pathways and test for vulnerabilities within a network which can later be exploited through other techniques.”
Other noteworthy statistics from the survey:
- The majority of those surveyed (59%) worry that their ISP does not provide enough protection against DDoS attacks
- Almost a quarter (24%) of respondents believe that their ISP is to blame if a DDoS attack affects their business
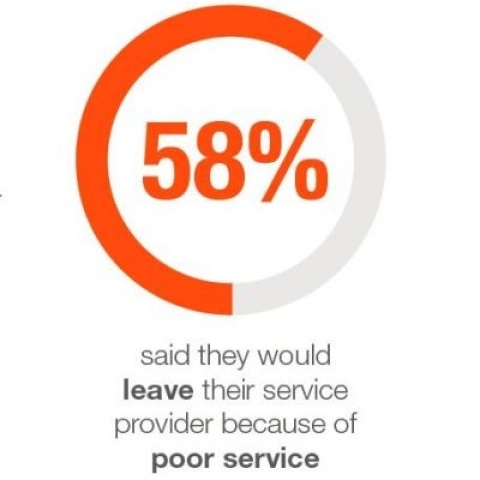
- 58% said that they would leave their service provider because of poor service
- 21% would leave their service provider if it did not offer adequate protection against DDoS attacks
The Role of Internet Service Providers
As DDoS attacks become increasingly sophisticated, many organizations are looking further upstream to their Internet Service Provider to protect against DDoS threats. Over half of those surveyed (53%) believe that ISPs are hiding behind net neutrality laws—the concept of treating all online traffic equally—as a way to dodge their responsibilities in terms of protecting their customers from cyberattacks, such as DDoS.
A telecom company’s role has traditionally been to direct traffic from one destination to another, without passing judgment about the content. Net neutrality, in which carriers treat all data the same, was prized above all else. But the tide of opinion is changing and many customers now want their telecoms to deliver not a decaying mélange of Internet traffic and increasingly sophisticated attack vectors, but a “clean pipe” of good traffic, where the threats have been proactively removed. Providers now have a golden opportunity to offer their customers DDoS protection-as-a-service, and open up valuable new revenue streams in the process – or risk losing their customers.

You can read the original article here.
As a security vendor, we’re often asked, “What about Sophos Antivirus for iPhones and iPads?” We’d love to oblige, but Apple’s iOS development model doesn’t allow the sort of interaction with the operating system that we’d need to build an effective anti-virus program.
In particular, to qualify for the App Store, an app is limited to its own sandbox, where it isn’t supposed to be able to read or interfere with other apps, or to sidestep Apple’s commercial controls.
That makes it impossible for an anti-virus to analyse other apps, or to hook into the operating system itself to scan files after they are downloaded but before they are used. In other words, even trusted vendors can’t publish apps that do what you’d expect from an anti-virus – not unless you jailbreak your phone, which opens up a whole heap of security risks on its own.
The silver lining, however, is that Apple’s strict walled garden approach has made it much harder to sneak malware onto iPhones and iPads, so Apple devices have experienced a minuscule fraction of the malware troubles that have beset the Android ecosystem.
Of course, no walled garden is perfectly secure against attackers, and Apple regularly issues iOS updates to close off software vulnerabilities to help keep the bad guys out.
This means that keeping your device up-to-date with the latest iOS version is an important part of staying secure. Wouldn’t it be great to have a tool that checks and explains why you should upgrade? Especially if it told you what you needed to know without having to wade through pages of technical documentation and security advisories…
The latest addition to our great range of free tools, Sophos Mobile Security for iOS, does just that, and more:
- OS Advisor alerts you when you are behind in your updates. The Advisor provides details about the new OS version and explains the security benefits of upgrading.
- Authenticator manages one-time passwords for two-factor authentication (2FA), also known as two-step verification, so you can login more securely to Google, Facebook, Amazon and many more.
- Secure QR Code Scanner blocks malicious content that may be lurking in QR codes, flagging any issues before you visit the page or content and give away data to the wrong guys.
Why not check out Sophos Mobile Security for iOS yourself? Go to our free tools page to download the app today.
You can read the original article here.