News
AV-Comparatives recently tested 250 Android security apps available on the Google Play Store against 2,000 of the most common Android threats from 2018. The test was designed to simulate real-world conditions and help Android users identify genuine, effective antivirus apps in a space where there’s no shortage of buggy, dubious or ineffective options.
We were delighted to see Sophos Mobile Security pass with flying colors, detecting all of the malware samples with 100% accuracy and no false detections.
One test doesn’t make a perfect product, and neither does two, but we were equally delighted when AV-Test reviewed Sophos Mobile Security and gave it a maximum score too.
Like the AV-Comparatives test, the AV-Test evaluation was designed to simulate real-world conditions. Instead of using the biggest threats from last year though, it challenged Sophos Mobile Security to fend of the very latest Android threats.
The test also recognised the crucial importance of usability on mobile platforms by checking the software’s impact on battery life, traffic and performance, and whether or not it generated false warnings during the installation and use of legitimate apps.
It triumphed in both aspects of the test, scoring 100% for both protection and usability.
Sophos is a strong advocate for thorough independent testing of cybersecurity products. It helps customers choose what’s right for their environment, and it pushes vendors to constantly improve the protection in their technology.
We encourage businesses to evaluate the effectiveness of a product using multiple independent data points and we are delighted that both AV-Comparatives and AV-Test have given Sophos Mobile Security top marks.
Sophos Mobile Security is available for free in unmanaged mode from Google Play and Apple’s App Store. Business customers can license the software for centralized management, deployment, reporting, and more integrations.
To see how Sophos Mobile Security fits into your business, start your 30-day free trial today.
Your mailbox is more valuable than ever to attackers, with 93% of company breaches in security now starting with a phishing email. Whether users are targeted to receive phishing emails, or they have their mailbox compromised to send spam and viruses from your organization’s domain, the risks to your organization are great.
The symptoms of a compromised mailbox
When your domain is used to spread malicious email, it can impact your reputation as an email sender and as a trusted business, leading to blocked messages. There are some common symptoms of this activity, which busy users may struggle to notice, leading to undetected threats:
- The user’s mailbox may be blocked from sending emails
- Missing or deleted emails in their inbox
- Recipients report emails being received, but the user has no corresponding sent item
- The existence of inbox rules that neither the user nor your administrator has created. These rules may forward messages to the Junk folder
- Mail forwarding was recently added to the account without consent.
A connected approach
Thanks to its shared user list, Sophos Central is now able to link mailboxes protected by Sophos Email with the associated computers protected by Sophos Endpoint. Once linked, if Sophos Email detects 5 or more spam or virus emails sent in 10 minutes, the mailbox is automatically blocked while an endpoint scan is carried out. The infection is then removed and alerts are shared via Sophos Central.
Watch our video on Sophos Email Compromised Mailbox Detection:
During this year’s RSA conference (visit us at booth #N6253!), CyberArk announced the release of version 10.8 of the CyberArk Privileged Access Security Solution. Version 10.8 focuses on expanding and improving CyberArk’s ability to continuously discover and protect cloud environments as well as augmenting Just-in-Time capabilities for an easy-to-use privileged access control. We’ve included a demo of Version 10.8’s capabilities at the bottom of the page.
The Cloud
Cloud computing, storage and applications have all become integral to modern organizations and the cloud footprint amongst the world’s organizations continues to grow. One of the main tenets of the cloud is speed; speed of deployment, scaling and integration. However, the increased speed at which cloud computing and storage allows organizations to spin up new virtual machines, instances and storage buckets can lead to headaches for both SOC and IT administrators. As cloud computing and storage has become an increasingly popular way conducting business, a staggering 50% of organizations do not have a privileged access security plan to secure cloud instances.
The newest CyberArk release provides a robust strategy for securing privileged access throughout AWS environments. It enables organizations to detect, alert and respond to potential attacks or misuse in AWS environments relating to Identity and Access Management (IAM) accounts and EC2 instances. To further the integration of these new capabilities, CyberArk customers can now deploy threat detection, alerting and response capabilities as an AMI or CloudFormation template.
It’s no small feat to secure these accounts and instances. A recent CloudInsight Essentials study showed that, among the 31,000 EC2 instances studied, there were 150,000 misconfigurations detected, 30,000 of which were linked to IAM accounts. These IAM accounts provide privileged users sweeping access to create, edit and update AWS Simple Storage Service (S3) buckets. S3 buckets are a public cloud storage resource similar to file folders that can store objects containing descriptive metadata and sensitive information.
With the CyberArk Privileged Access Security Solution, organizations can now continuously discover unmanaged privileged AWS accounts and instances and automatically add these accounts to a list of pending approvals to prevent further misuse. CyberArk customers are also able to initiate automatic Access Key rotation and re-creation if unauthorized or unmanaged access is detected. They can also send alerts to SOC and IT administrators based on detected misuse so that they can take a risk-based approach to their cloud inventories.
Just-in-Time
Just-in-Time solutions are simple to use and that can make life easier. However, it’s important not to lose sight of the rest of the necessary security precautions. Drawbacks to not fully managing and rotating privileged credentials associated with critical servers, databases and cloud-instances include having minimal visibility into activities taking place on those targets and a lack of native workflows. Having a tiered structure in place that implements higher levels of security (automatic session isolation, recording and threat detection and response) on cloud consoles, domain controllers, and other critical systems is a best practice.
Ensuring that the right person has the right access to the right resource at the right time for the right reason is a fundamental component of privileged access security. This is “Just-in-Time access,” a strong option for organizations that are looking to kick-start their privileged access security programs by introducing an easy-to-use solution.
Building on existing Just-in-Time access to Windows servers, which provided users provisional access to a defined subset of Windows servers for a pre-determined amount of time, this release advances those capabilities. Now, administrators have the ability to configure on a minute-by-minute basis the amount of time approved for access to target Windows servers. As part of the CyberArk Privileged Access Security Solution, Just-in-Time access adds another route for organizations to take toward implementing a robust privileged access security program.
In addition to advanced cloud capabilities and Just-in-Time functionality, other features included in this release are:
• A new policy that, if enacted, will require end-users to provide a reason for every privileged connection to a target system. That reason is sent to a reviewer for approval, automatically audited and stored.
• A new authentication method, “Cognito,” for AWS environments that enables application users to sign in directly through a user pool or third-party identity provider and supports the multi-configuration of SAML
Register for our webinar to learn more about CyberArk’s ability to extend privileged threat detection and response to the cloud.
he total number of records exposed in the healthcare sector rose to 11.5 million in 2018, according to the fifth annual Healthcare Breach Report, published by Bitglass.
The number of breaches reached a three-year low at 290 breaches total; however, the number of exposed records nearly doubled from 2017. Also notable in the report was that nearly half (46%) of the 11.5 million individuals who were affected by healthcare breaches in 2018 were so because of hacking and IT incidents.
An analysis of data acquired from a US Department of Health and Human Services (HHS) database that holds information on breaches involving protected health information (PHI) revealed that breaches in the healthcare industry fell into one of four categories.
In addition to those breaches related to malicious hackers and improper IT security, 36% of healthcare data breaches were categorized as caused by unauthorized access or disclosure of protected health information. A smaller number were the result of theft of endpoint devices. According to the report, the number of breaches caused by lost and stolen devices has fallen by nearly 70% since 2014. The final category encompassed those miscellaneous breaches and leaks related to items such as improper disposal of data.
On average, nearly 40,000 people were affected per breach, which is more than double the average number affected in 2017. Given that nearly half of breaches occurred because of hacking or IT issues, the report suggested that bad actors are targeting healthcare IT systems more frequently because they know there are massive amounts of sensitive data stored on those systems.
“Healthcare firms have made progress in bolstering their security and reducing the number of breaches over the last few years,” said Rich Campagna, CMO of Bitglass, in a press release. “However, the growth in hacking and IT incidents does deserve special attention. As such, healthcare organizations must employ the appropriate technologies and cybersecurity best practices if they want to secure the patient data within their IT systems.”
You can read the original article, here.
A report released today by Sophos reveals that IT managers are more likely to catch cybercriminals on their organization’s servers and networks than anywhere else.
The study, 7 Uncomfortable Truths of Endpoint Security, surveyed over 3,100 IT managers in 12 different countries across industry verticals and organization sizes, and was conducted by the independent research specialist Vanson Bourne.
The report reveals that IT managers discovered 37% of their most significant cyberattacks on their organization’s servers and 37% on its networks. Only 17% were discovered on endpoints and 10% were found on mobile devices.
You’ve likely heard the adage: “It’s not a matter of if, but when you’ll be breached”, and the survey data certainly backs that up, with the majority of organizations responding to this survey (68% global average) having already been breached.
That’s why there’s growing momentum to not just focus on the tactics and tools that flat-out prevent attacks, but also to bolster threat response programs to more quickly find intruders already in the network, and to more effectively respond to attacks already underway.
In other words, for organizational security, it’s no longer enough to think about threats stopped at the ‘perimeter’. Companies must also focus on dwell time, which is the time it takes to detect an attack in progress.
Of teams that were able to definitively measure their average attacker dwell time, they responded that they could spot an attacker in as little as 13 hours, with Australia, Brazil, and Canada reporting 10 hours of dwell time on one end of the average, and Japan reporting 17 hours on the other.
If you’re not familiar with industry chatter around dwell time, 13 hours might seem like an eternity for an attacker to be rooting around your organizational assets, but compared to other industry benchmarks — such as the Verizon Data Breach Investigations Report (DBIR), whose respondents on average clock dwell time in weeks or months — 13 hours seems almost impossibly fast.
As the respondent set and the types of threats being assessed in this survey and the Verizon DBIR studies aren’t quite the same, we can’t and shouldn’t make a one-to-one comparison between the two. Instead, this report drills down into why there’s a disparity in results, and why the gulf in detection times from those with dedicated security teams versus those without can hold such variability.
Lack of visibility into attacker behavior and information about attacker paths is still a major barrier to detecting attacks and reducing dwell time. 20% of IT managers who fell victim to one or more cyberattacks last year can’t pinpoint how the attackers gained entry, and 17% don’t know how long the threat was in the environment before it was detected, according to the survey.
To improve this lack of visibility, IT managers need Endpoint Detection and Response (EDR) technology that exposes where threats originate, as well as the digital footprints of attackers moving laterally through a network. 57% of respondents reported that they did not have an EDR solution in place at the moment, but planned to implement one within the next 12 months.
Chester Wisniewski, principal research scientist at Sophos said:
“If IT managers don’t know the origin or movement of an attack, then they can’t minimize risk and interrupt the attack chain to prevent further infiltration.
EDR helps IT managers identify risk and put a process in place for organizations at both ends of the security maturity model. If IT is more focused on detection, EDR can more quickly find, block and remediate; if IT is still building up a security foundation, EDR is an integral piece that provides much needed threat intelligence”.
On average, organizations that investigate one or more potential security incidents each month spend 48 days a year (four days a month) investigating them, according to the survey. It comes as no surprise that IT managers ranked identification of suspicious events (27%), alert management (18%) and prioritization of suspicious events (13%) as the top three features they need from EDR solutions to reduce the time taken to identify and respond to security alerts.
If IT managers have defense-in-depth with EDR, they can investigate an incident more quickly and use the resulting threat intelligence to help find the same infection across an estate. Once cybercriminals know certain types of attacks work, they typically replicate them within organizations. Uncovering and blocking attack patterns would help reduce the number of days IT managers spend investigating potential incidents.
This report drills down into the specifics of the threats detected (what kind and where), as well as the resources spent on incident investigation. By taking a broader look at industries across geographies and organizational size, this report shines a light on the unexpected challenges facing enterprise security as a whole across the globe.
Read the report in full here, or learn about Sophos Intercept X with EDR.
Strong, unique identities are the core of IoT device security. Giving unique identities allows them to be authenticated when they come online and throughout the lifetime. It proves integrity and securely communicates with other devices, services and users. But how do you know what’s the best of the best?
In the true spirit of an “awards season” that just passed, we think it only makes sense to unveil one more: The market’s pick for best in IoT Security – The GlobalSign IoT Identity Platform! In fact, we just took home a 2019 Silver Cybersecurity Excellence Award – recognizing companies, products and individuals demonstrating excellence, innovation and leadership in information security.
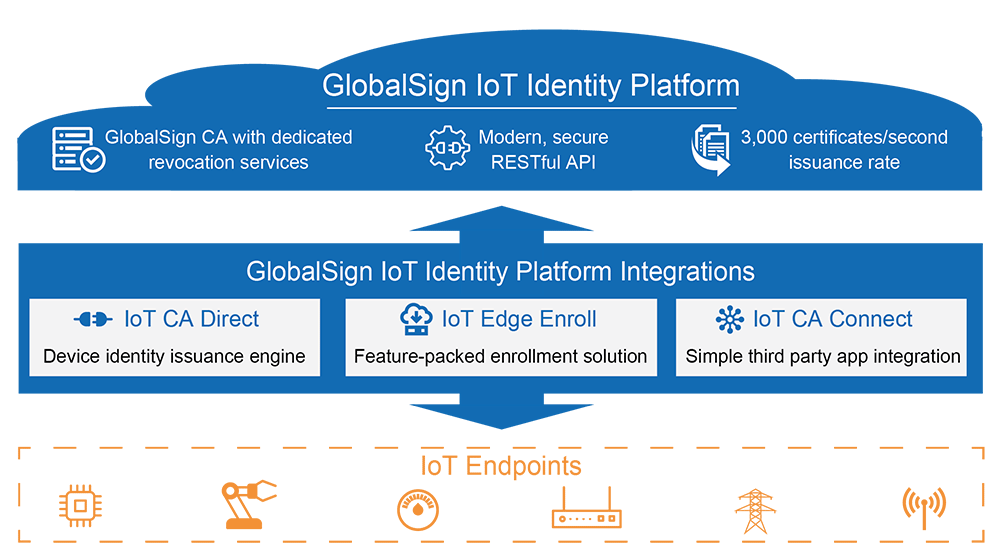
We believe the IoT Identity Platform stands out for an ability to address critical device security requirements. No other product today protects the identity, integrity and privacy of devices and data from chip to cloud through authentication, authorization, and encryption – while staying highly scalable. This is especially true due to the platform being a high volume, high throughput infrastructure, capable of issuing 3,000 certificates per second and enabling customers to validate Proof of Concept with low-volume test certificates – then scale to millions of identities using the same RESTful API.
The IoT Identity Platform can manage all types of digital certificates in any market vertical or IoT Gateway – semiconductor, industrial manufacturing, automotive, smart grid, agriculture, healthcare, construction, logistics and more. The central feature is IoT Edge Enroll, a full-fledged enrollment client used to provision and manage PKI-based identities to IoT devices of all types. The main function is a Registration Authority with an embedded GlobalSign CA Root of Trust, whitelisting, challenge-response, and policy-based management.
Edge Enroll also includes connectors for hardware security modules (HSMs), and can be deployed in a public or private cloud, on-premises, or as a GlobalSign managed service. The offering supports an expanded list of enrollment and communication protocols in response to flexibility required by IoT ecosystems. It backs PKCS #7, #10 and #12, can accommodate batching of certificate/requests, and performs private key generation and key escrow. The solution uses secure TLS communication, IP address whitelisting and integrates with secure elements such as Physical unclonable function (PUF), Trusted Platform Module (TPM), and STSafe (Secure STMicroelectronics microcontroller).
Even better, our solution is also being leveraged across a broad range of industries. Just last April, the platform was integrated with the Arm® Mbed™ Cloud platform – allowing any third-party developer using Mbed Cloud to quickly automate issuance of digital certificates from GlobalSign, along with certificate management services. This also ensures every Mbed supported device can have a unique device certificate from a trusted third party such as GlobalSign.
Last year, we also began working with Longview, a Carnegie Technologies company as it began packaging its newly launched industrial IoT asset management solution. Their development team took an approach that included four key areas: security by design, multiple layers of security, securing the supply chain and partnering for success. Ultimately, Longview IoT packaged the right IoT technologies – including GlobalSign’s IoT Identity Platform — to provide customers with a single, secure, and optimized solution to monitor and manage industrial assets. It delivers end-to-end IoT solutions, pre-configured for various industries and designed to work right out-of-the-box.
The explosion of IoT connected devices is staggering. Although technology has improved manufacturing, enhanced decision-making and improved the safety, comfort and efficiency of our lives – it’s also created the largest attack surface ever. GlobalSign’s IoT Platform rises to this challenge of securing IoT by protecting identity, integrity and privacy of devices and data – from chip to cloud through authentication, authorization and encryption.
So who needs the Oscars? Awards season is over, but our IoT Platform continues to deliver. To learn more, visit https://www.globalsign.com/en/lp/iot-identity-platform/
You can read the original article, here.
Sophos is a strong advocate for thorough independent testing of cybersecurity products to help customers choose what’s right for their environment and for vendors to improve the protection in their technology.
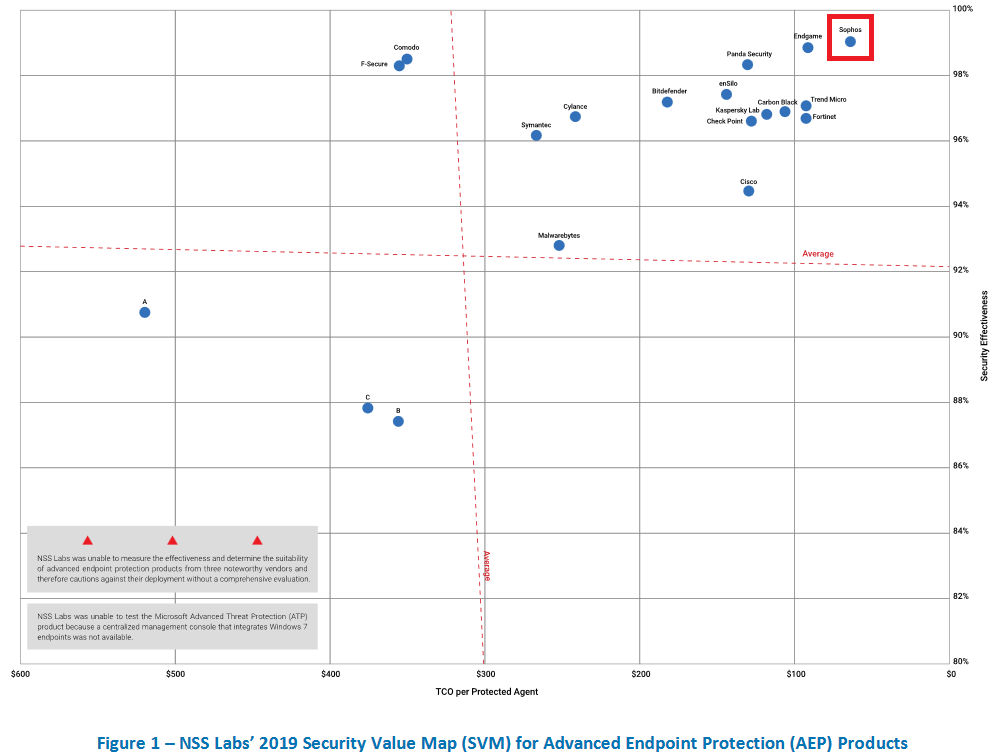
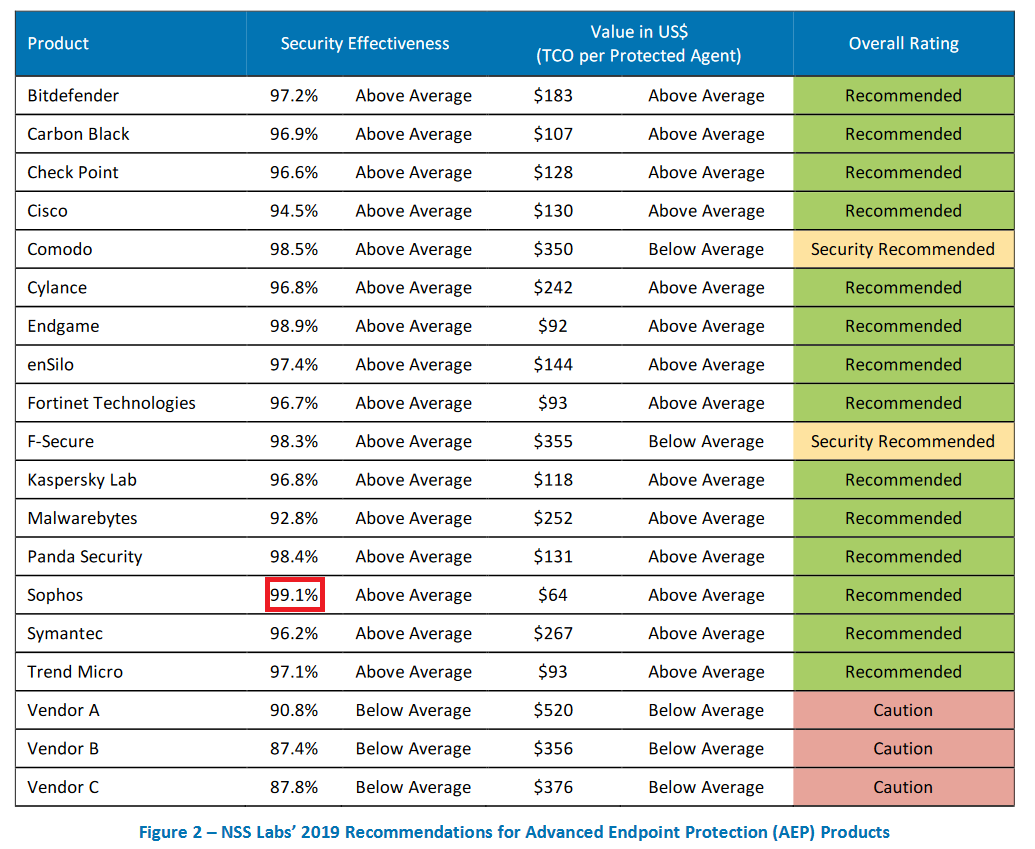
In the 2019 AEP Group Test published by NSS Labs today, our next-gen endpoint solution Intercept X was recognized as having the highest security effectiveness and the most efficient TCO (total cost of ownership) of the 19 endpoint security products tested. In this 2019 AEP Group Test by NSS Labs, we are pleased to see our technology outperform all other products, supporting what our own internal tests and numerous independent reviews have confirmed since the product first launched.
While these results confirm what we already know (it’s great to get high praise) we encourage every business to evaluate the effectiveness of a solution using multiple independent data points and carry out an assessment of its ability to work within their environment. We are confident that we have developed the most effective products but realize every business is unique just like independent testing reports.
Great strides are being made to level the playing fields in cybersecurity testing. Sophos encourages testing to be fair, rigorous, transparent, and collaborative, and it should seek to replicate the threat environment as it exists for customers, not just in lab conditions. Testing labs need to work with vendors to configure environments correctly, vendors should make it easy for their products to be scrutinized, and testing labs should engage end users to specify the features to be reviewed.
As a supporter of the anti-malware testing standards and Board member of AMTSO, Sophos CTO Joe Levy recognizes that while third party cybersecurity tests are not yet perfect, they still have plenty of value.
“Measuring cybersecurity product effectiveness is unimaginably complex. With threats and attack techniques increasing and evolving at an ever-accelerating rate, testing houses need to make extraordinary investments in their laboratories if they are to produce meaningful and rigorous measurements of cybersecurity product effectiveness. But just like all cybersecurity products are not equal, not all testing houses are equal and this remains somewhat opaque to the consumers of their reports, particularly when there is insufficient transparency around methodologies or execution details. Competent independent testing labs provide a great service to vendors and buyers, and are critical to the cybersecurity ecosystem to drive higher standards of protection for all”.
We’re happy to continue to see our products succeed in third party testing and receive awards, and we encourage you to explore the details of the testing reports at www.sophos.com.
If you’re ready to see for yourself, you can download a free trial of Intercept X at www.sophos.com/intercept-x today.
CyberArk aims to make implementing and managing a robust privileged access program as easy as possible for our customers. CyberArk continues to lead the industry with its own investments in innovation to consistently deliver the most value to customers – especially in terms of simplicity, automation and improved operational efficiencies. Over the course of the last calendar year alone, CyberArk introduced dozens of new capabilities to help customers more easily implement and scale their privileged access security controls. Here’s a list of our top seven updates to the Core CyberArk Privileged Access Security solution:
- Privileged Session Management for the Cloud – In March of last year, CyberArk acquired cloud security provider Vaultive and rolled the functionality into the CyberArk Privileged Access Security Solution. This provides organizations with greater visibility and control over privileged business users, social media, SaaS, IaaS and PaaS administrators, and enables customers to manage privileged sessions natively. This introduces yet another method for CyberArk customers to isolate and monitor sessions for web-based applications. These sessions are automatically assigned a risk-score, much like any other privileged session in CyberArk, which helps SOC admins take a risk-based approach to securing their most critical assets. Accounts that revolve around cloud providers (AWS, Azure, Google Cloud Platform) social media (Twitter, Facebook, LinkedIn) and other web applications like Salesforce and OpenShift can now be secured while providing a native login experience to the admins and privileged business users of this critical applications.
- Integrated threat detection and response — Threat detection, alerts, and responses generated by the CyberArk Privileged Access Security Solution are now 100% integrated into the main console and also sent as logs directly to your SIEM tool or other alerting system. CyberArk administrators now have access to in-depth analytics on who or what is utilizing privileged access in the environment and to see this information without having to look up from where they set policies, review sessions or log in to do their other administrative tasks. Not only that, but they are also able to receive prioritized alerts and initiate automated action to take a risk-based approach to privileged access security; tackling the riskiest accounts, credentials and activities first, thus reducing clutter and excessive alerts.
- Automatic Risky Session Termination –CyberArk provides security teams with the tools they need to automatically suspend or terminate risky privileged sessions based on policy from the web based interface or via API. The new tools enables security operations teams to mitigate risk by automatically shutting down or suspending sessions that pose a security risk until verified, rather than waiting for a human to identify the problem and act.
- PowerShell Utility for Un-Suspending Users — When a suspended user needs to be granted re-entry to CyberArk, instead of losing time relying on manual intervention to let the user back in, a member of our Customer Success Team, Randy Brown, came up with clever way to use a PowerShell utility to revive suspended accounts. We’ve made this time-saver available free on GitHub, and this is one of many useful tools made available to our customers on GitHub.
- Automatic Account On-Boarding — Combing through all the privileged accounts that are discovered and onboarding them en masse into the vault can be time consuming. It can also presents a security risk when end users create backdoor access to perform their own tasks. With CyberArk’s recent introduction of automatic account onboarding, neither of these things are an issue anymore. Automatic account onboarding helps administrators scale their privileged controls with reduced human intervention and increased speed to manage privileged accounts that present risk to your organization.
- Privileged Access Security Installer – When CyberArk released version 10.4, it included the Privileged Access Security Installer, which delivers a massive reduction in the steps required to deploy all of the CyberArk Core Privileged Access Security components. This is part of a concerted effort to support smaller deployments that deploy all CyberArk components on a single server.
- CyberArk Marketplace – Since the launch of the CyberArk Marketplace in 2018, CyberArk has deepened the depth and breadth of ready-to-deploy integrations – especially in key areas like IT Management and security software, Industrial Control Systems, Robotic Process Automation and Identity Access Management. Customers who use the CyberArk Marketplace can easily find and deploy integrations from CyberArk’s 100+ certified technical partners to bolster their security posture.
What’s Next?
Right now, cybersecurity professionals are having to do more with less. Having solutions, tools and features in place to help security teams effectively and efficiently use the products in their purview is more essential than ever. We recently hosted a webinar that outlines, and demonstrates new capabilities introduced in version 10 that help customers deploy, integrate and scale with CyberArk. Click here to access the recording and learn more!
This course provides an in-depth study of Sophos Central, designed for experienced technical professionals who will be planning, installing, configuring and supporting deployments in production environments. It consists of presentations and practical lab exercises to reinforce the taught content, and electronic copies of the supporting documents for the course will be provided to each trainee through the online portal. The course is expected to take 3 days to complete, of which approximately 9 hours will be spent on the practical exercises.
Sophos Central Architect Training
3 days Training
Wednesday 20 March 2019 – Friday 22 March 2019
Requirements
Prior to attending this course, trainees should:
- Complete the Sophos Central Endpoint and Server Protection and should have passed the Certified Engineer exam
- Experience with Windows networking and the ability to troubleshoot issues
- A good understanding of IT security
- Experience using the Linux command line for common tasks
- Experience configuring Active Directory Group Policies
- Experience creating and managing virtual servers or desktop
Target audience:
This course is designed for technical professionals who will be planning, installing, configuring and supporting deployments in production environments. And for individuals wishing to obtain the Sophos Central Certified Architect certification.
Objectives:
- On completion of this course, trainees will be able to:
- Design an installation considering all variables
- Undertake a multi-site installation appropriate for a customer environment
- Explain the function of core components, how they work, and how to configure them
- Track the source of infections and cleanup infected devices
- Perform preliminary troubleshooting and basic support of customer environments
Certification:
To become a Sophos Certified Architect, trainees must take and pass an online assessment. The assessment tests their knowledge of both the presented and practical content. The pass mark for the assessment is 80%, and is limited to 3 attempts.
Content
- Module 1: Deployment Scenarios (60 mins)
- Module 2: Client Deployment Methods (65 mins)
- Module 3: Endpoint Protection Policies (80 mins)
- Module 4: Server Protection Policies (30 mins)
- Module 5: Protecting Virtual Servers (60 mins)
- Module 6: Logging and Reporting (45 mins)
- Module 7: Managing Infections (45 mins)
- Module 8: Management (65 mins)
Course content
Module 1: Deployment Scenarios (60 mins)
- Identify some of the common challenges when deploying Central
- Deploy Update Caches – Set up Message Relays
- Configure AD Sync Utility
- Identify where Update Caches and Message Relays should be used
- Labs (45 mins)
- Register and activate a Sophos Central evaluation
- Install Server Protection
- Install and Configure AD Sync Utility
- Deploy an Update Cache and Message Relay
Module 2: Client Deployment Methods (65-75 mins)
- Identify the recommended steps for deploying Sophos Central
- Explain the installation process, and identify the different types of installer
- Automate deployment for Windows, Linux and Mac computers
- Migrate endpoints from Enterprise Console
- Locate installation log files
- Remove third-party products as part of a deployment
- Labs (75-90 mins)
- Enable Server Lockdown
- Deploy using Active Directory Group Policy
- Use the Competitor Removal Tool
- Deploy to a Linux Server using a Script
Module 3: Endpoint Protection Policies (80-90 mins)
- Describe the function and operation of each of the components that make up an Endpoint Protection and Intercept X
- Configure policies to meet a customer’s requirements and follow best practice
- Test and validate Endpoint Protection
- Configure exclusions
- Configure Data Loss Prevention
- Labs (100-120 mins)
- Test Threat Protection Policies
- Configure and Test Exclusions
- Configure Web Control Policies
- Configure Application Control Policies
- Data Control Policies
Module 4: Server Protection Policies (30 mins)
- Configure Server Protection Policies
- Configure and Manage Server Lockdown
- Labs (65-75 mins)
- Configure Sever Groups and Policies
- Manage Server Lockdown
- Test Linux Server Protection
Module 5: Protecting Virtual Servers (60 mins)
- Connect AWS and Azure accounts to Sophos Central – Deploy Server Protection to AWS and Azure
- Deploy and Manage Sophos for Virtual Environments
- Labs (60 mins)
- Download the installer for the Security Virtual Machine
- Install the Security Virtual Machine (SVM) on a Hyper-V Server
- Configure Threat Protection policies to apply to the Security VMs and the Guest VMs they protect
- Perform a manual installation of the Guest VM Agent and view logs
- Test and configure a script to deploy the GVM Agent
- Manage Guest VMs from the Central Console
- Test Guest VM Migration
Module 6: Logging and Reporting (45 mins)
- Explain the types of alert in Sophos Central, and be able to read an RCA
- Use the Sophos Central logs and reports to check the health of your estate
- Export data from Sophos Central into a SIEM application
- Locate client log files on Windows, Mac OS X and Linux
- Labs (55-60 mins)
- Generate and analyze an RCA
- Configure SIEM with Splunk
Module 7: Managing Infections (45-60 mins)
- Identify the types of detection and their properties
- Explain how computers might become infected
- Identify and use the tools available to cleanup malware
- Explain how the quarantine works and manage quarantined items
- Cleanup malware on a Linux Server
- Labs (40 mins)
- Source of Infection Tool
- Release a File from SafeStore
- Disinfect a Linux Server
Module 8: Management (65 mins)
- Use the Controlled Updates policies appropriately
- Enable multi-factor authentication
- Use the Enterprise Dashboard to manage multiple sub-estates
- Identify the benefits of the Partner Dashboard
- Identify common licensing requirements
Labs (25 mins)
- Enable Manually Controlled Updates
- Enable Multi-Factor Authentication
Daily morning headlines from Dark Reading, Krebs on Security, ThreatPost and others remind us that breaches are inevitable – they are not a matter of “if,” but instead, “when.” This is increasingly understood, so one wonders if this reality leads people to make overly rash decisions based on what they read with their morning cuppa joe?
Catch that last question? Let’s talk about recency bias – the tendency to place too much weight on recent events.
While many IT practitioners, especially those in security, believe that we are perfectly astute and calculated bastions of logical decision-making, we are all, indeed, human. And agencies and news publications alike have capitalized on fear mongering, knowing that we cannot avoid consuming and commenting on the latest event driving headlines. Now, while there is little danger in your Kardashian obsession (Mine lately has been Jho Low, the embattled billionaire accused of swindling billions from the Malaysian government), there is potential danger in basing security purchases and strategies purely on the latest security fad.
New tools and technologies constantly enter the security market. Some vendors, often founded by security practitioners, are deploying powerful systems absolutely bursting with functionality, intelligence and potential. Moreover, while the wildly innovative and nascent tools are interesting, security leaders have to provide the most security value they can – increasingly in terms of quantifiable risk reduction — across their entire organization.
What I suggest is, instead of chasing headlines, to adopt technologies that have gained recognition from security thought leaders and influencers for their ability to reduce risk and increase a company’s security posture. One place to look for direction is the Center for Internet Security (CIS), which provides a list of top security controls. This includes what they call “controlled use of administrative privileges” and we call privilege access security. Privileged access exists everywhere in your organization and has existed as long as administrator and superuser accounts have been integral to the operation of applications and infrastructure. Although it seems obvious that protecting privileged access is critical to maintaining security, it was, at a time, viewed as a niche security tool or something organizations could do as an “extra” step to securing the enterprise… a “nice to have,” if you will.
If you look into key regulations, across myriad industries, you will find that protecting privileged access is one of the key tenants to adhere to when the auditors come knocking. PCI-DSS 3.2, Sarbanes Oxley, HIPAA and NERC CIP all require the protection and monitoring of privileged users and sessions. That being said, embarking on a privileged access security program isn’t just about checking the box to fulfill a compliance requirement but a key step in staying one step ahead of the attackers.
Many of us work in high tech because there is constant innovation and cutting edge solutions that push the limits of computing.
Technophiles should not fear as there are privileged access security companies like CyberArk experimenting with bleeding-edge tools, developing brand new technologies and implementing techniques to stay ahead of the attackers. For those interested in innovative techniques and deep privileged access security research, check out the CyberArk Threat Research Blog – and remember, news publications are fighting to be the most sensational and generate the most clicks. Trust your instincts and deploy proven privileged access controls instead.
The corporate network perimeter defensive line no longer exists. With increased attack sophistication and insider threats, organizations can’t guarantee that everything on the inside of their network can be trusted.
This is the principle of Zero Trust architecture. These days, organizations need to build controls immediately around the individual data assets, wherever they reside.
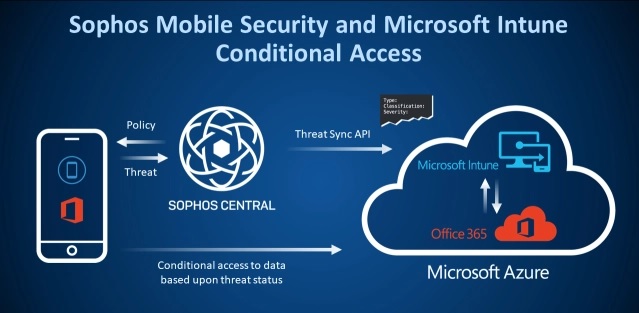
Administrators managing Microsoft Office 365 and Intune have access to the conditional access feature for exactly this purpose. Conditional access provides a set of policies that can be configured to control the circumstances in which users can access resources.
But every policy needs context. Without it, it’s easy to jump to the wrong conclusion. The more context we can provide, the better something can be understood, and the more informed a choice can be made.
Administrators want that extra context. After all, who wouldn’t want to block access to email or sensitive documents from a mobile device found running a malicious application or connected to a Wi-Fi network with a potential man-in-the-middle attack underway?
Sophos Mobile Security is our leading mobile threat defense app. It runs on both Android and iOS devices and can share threat details with Microsoft to provide that extra bit of context. Conditional access policies can now take threat detection results from Sophos into consideration when deciding whether to allow access to request resources.
To learn more about Office 365 and conditional access, visit Microsoft’s conditional access page.
To learn more about Sophos Mobile Security, visit the Sophos website.
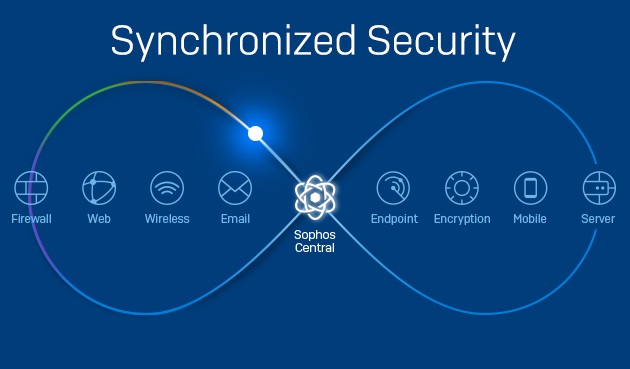
Today we’re excited to announce that XG Firewall, our flagship next-generation firewall, joins Sophos Central, the ultimate cybersecurity management platform in the cloud. Sophos customers can now manage their XG Firewall and Intercept X, alongside their Sophos Server, Mobile and Encryption products – all from a single pane of glass.
This marks the first time that an industry leading firewall product and an industry leading endpoint product are managed together from the same console. And it really couldn’t come at a better time, with dangerous and sophisticated threats like Emotet threatening many organizations with hundreds of new variants every day.
These advanced threats demand a coordinated defense, with multiple layers of security technologies working together to identify, block, and isolate the attack at several points in the chain. This prevents the threat from getting any kind of foothold on the network and spreading laterally.
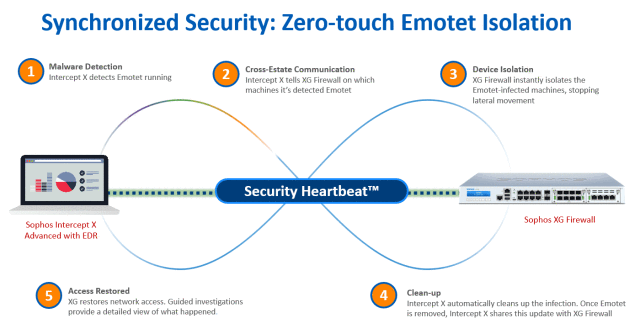
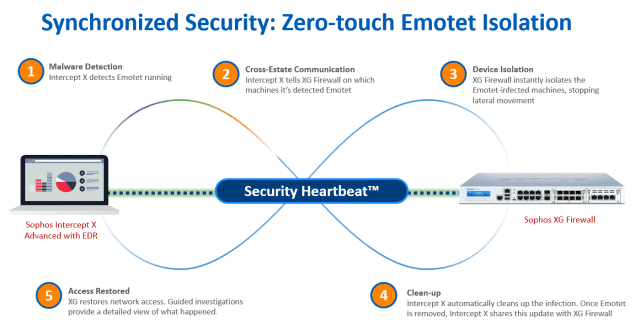
Sophos Synchronized Security and Security Heartbeat provide the ideal solution to identify and respond to threats like Emotet.
Leveraging the latest advanced threat protection technologies and sharing important health, status and telemetry information between XG Firewall and Intercept X, Synchronized Security can see it, stop it, and secure it – before these threats can cause any damage. It’s what I like to refer to as an unfair advantage.
With XG Firewall joining Sophos Central, Synchronized Security just got another unfair advantage when it comes to staying ahead of both the hackers and their latest threats.
Not only do you have a coordinated defense, but you also now have the full benefits of a completely integrated management experience.
XG Firewall joining Sophos Central offers great benefits for everyone
If you’re an existing Sophos Central customer:
If you’re using Sophos Central to manage Intercept X or any other Sophos product, you’ll be familiar with the convenience and ease of managing your IT security through Sophos Central. But now it’s time to synchronize your security.
You can add an XG Series appliance to your network to enable Synchronized Security and unlock the full potential of an integrated security system – easy and risk free. You can manage it in Sophos Central alongside your other Sophos products, and you don’t even need to replace your existing firewall. Check it out.
If you’re an existing XG Firewall customer:
You can now monitor and access all your firewalls securely through Sophos Central – all at no extra charge. Take advantage of the Sophos Central dashboard view for your firewalls, and you’ll get enhanced alerting options as well as direct access to any of your firewalls with a single click. And now you can add Intercept X to your endpoints to enable Synchronized Security, and manage everything from the same console. Check it out.
If you’re new to Sophos:
XG Firewall and Intercept X offer the ultimate protection from today’s advanced threats. Synchronized Security provides a coordinated defense that enables our products to work better together and share information through Security Heartbeat™. And you can now manage everything through a single, easy to use cloud-based console: Sophos Central. Check it out.
You can read the original article, here.
I recently listened to a podcast discussing the expanding legalization of sports betting in the United States.
The guest turned out to be a cybersecurity enthusiast-turned-professional poker player. In one part of the show, he described how, in advance of the Super Bowl, sportsbooks offer hundreds of bets known as propositions, or “props,” on which gamblers can wager their hard-earned dollars.
The props range from the seemingly sensical – How many combined touchdowns will both teams score? – to the more obscure (and slightly absurd) – What color of Gatorade will be dumped on the winning coach?
In gambling, the No. 1 rule is the house always wins. But Super Bowl props provide a potentially advantageous opportunity for the shrewd bettor. Why is this the case?
To explain, the podcast guest drew on his security background and compared the plethora of Super Bowl wagering options to the ever-widening cyberattack surface.
The more choices a smart punter has on which to risk their money, he said, the more likely they will discover opportunities that can be exploited. Thus, their edge of winning is bigger. The same goes for malicious hackers seeking entry into a target organization. Their likelihood of success grows with each available vulnerability.
Which brings us to the point of all of this: Your attack surface is teeming with potential liabilities. Here are the modern-day risks you need to mitigate to help prevent your adversaries from cashing in.
Endpoints
Most advanced threats that evade traditional prevention security measures start on the endpoint, and with the explosive growth of the Internet of Things (IoT), that means you have more ground to cover than ever. Desktops and laptops may be the most common initial infection point, but anything with an internet connection places your organization at risk. That includes non-traditional endpoints, including routers. To overcome limitations, you should combine strong internal policies with testing, detection and response capabilities to help stay protected.
Applications and Databases
Applications act as the digital front door into your organization, and databases are their connected companions. Both necessitate varying forms of protection, each requiring a multi-pronged approach. The threat of vulnerable applications, responsible for a surprisingly large number of the major data breaches in recent years, can be assuaged with web application firewalls, scanning and testing, and stronger development training. Meanwhile, database defense must evolve beyond simple patching to also include vulnerability testing, user rights management and activity monitoring.
End-Users
Phishing is one of those information security problems that even your grandparents know about – yet it remains one of the most successful means of attack, even against businesses that know it’s coming. The reason why is simple: It works. Everybody still uses email, and attackers have invoked clever ways to prey on human emotions and dupe uses into divulging confidential credentials or clicking on links and attachments. To address human frailty and conquer savvy phishers, you should deploy an advanced email security gateway, complemented by a security awareness program that uses creative ways to reach employees.
You can read the original article here.
The financial services industry experiences 35% of all data breaches, earning it the unflattering title of the most-breached sector. It’s easy to understand why. The industry is known for its wide array of interconnected systems and the processing of millions of transactions — factors that render it particularly vulnerable to attack.
As the threat, frequency and impact of these attacks increase, new legal risks emerge, including litigation and steep regulatory fines. In fact, according to a Forbes Insights/K&L Gates survey, the trends that present the most potential for legal risks include dealing with data (69%), cybersecurity (47%), a changing regulatory environment (46%), fraud protection (39%) and digital transformation (39%).
Regulators are reacting quickly. For example, the U.S. Securities and Exchange Commission recently issued new guidance calling for public companies to be more forthcoming when disclosing cybersecurity risks, even before a breach or attack occurs. Financial institutions are also stepping up to increase data security. For instance, 92% of the 200 U.S. financial services executives surveyed by Forbes Insights are currently using encryption technology.
But getting ahead of hackers requires knowing the dangers that lurk outside an organization. Here are the top three threats facing the financial services industry:
1) Web Application Attacks
Financial institutions rely on business-critical web applications to serve customers, promote their services and connect to back-end databases. However, many of these applications are hosted online, making them easily accessible to hackers. Types of web application attacks range from buffer-overflows to SQL injection attacks, in which a hacker injects SQL statements into a data-entry field, tricking the system into revealing confidential data.
2) DDoS Attacks
Distributed denial of service (DDoS) attacks impair the performance of resources, such as servers, causing websites and applications to slow down or crash. The result: angry customers who are unable to access critical financial services when they need them most. For financial services firms, the repercussions can be even worse, including disrupted business flows, stolen data, damaged reputation and lost revenue.
3) Insider Threats
Beyond hackers, employees are among the top cybersecurity threats to financial institutions. Oftentimes, unwitting workers fall victim to phishing scams or accidentally download malware. However, disgruntled employees may collude with hackers by sharing their passwords or intentionally ignoring corporate cybersecurity protocol. Either way, insider threats can take months – sometimes years – to detect.
Safety Practice
Amid increased exposure to these risks, financial institutions need to take measures to ensure greater data security and minimize legal exposure. To do so, consider the following steps:
- Draft internal policies, procedures and contractual provisions regarding the discovery, investigation, remediation and reporting of breaches.
- Obtain the right insurance coverage for various types of cyber risks and consider the adequacy of existing insurance programs.
- Partner with a third-party cybersecurity team that can help manage internet security and prevent cyberattacks and data breaches.
In today’s hyper-connected, technology-driven financial services sector, data security breaches, DDoS attacks and insider threats are on the rise. However, executives in the industry can take action by educating themselves on the dangers ahead and taking the right precautionary measures.
You can read the original article, here.
Your organization likely spends resources in preventing external breaches and taking the necessary measures to ensure that your company’s data is protected. However, did you consider if you’re having coffee with a hacker every morning?
Organizations tend to forget that more than one out of four breaches involve internal actors. According to the 2018 Verizon Data Breach Investigation Report 28% of data breaches were involving internal actors (2018 Verizon Data Breach Investigation Report)
According to the Verizon report, three out of the top-5 action varieties in breaches includes the use of stolen credentials (22%), information acquired through social phishing (17%) and the downright abuse of privileges (11%). Whether the actions of internal actors are intentional or accidental is an interesting question, but nevertheless, the insider threat is considerable, and the result is the same. Data is compromised putting the company at risk.
Handling data while at the same time ensuring the protection of privacy, is a crucial ingredient for success in today’s business environment. Question is how we acknowledge these facts and minimize internal breaches, without increasing distrust and monitoring of our employees’ every move?
1 of 3 employees will sell company information if the price is right
A 2015 survey from Clearswift (Research by Loudhouse for Clearswift, 2015) revealed that 35% of employees were willing to sell company data for the right price. Again: one out of three. To put this information into perspective, the US-based Center for Strategic and International Studies estimates the global annual cost of cybercrime to be upwards of $600 billion (CSIS, Economic Impact of Cybercrime: No slowing down, 2018, p. 6)
Of course, organizations have legal measures to safeguard that employees act ethically, but business processes are most often based on trust of confidentiality, and consequently, without adequate monitoring, internal breaches frequently go undetected.
Internally aided breaches are often caused by employees with easy access to critical company data. Companies usually don’t have sufficient measures implemented to ensure restricted access. In fact, the Verizon Data Breach Investigation Report assess that 26% of the internal actors in breaches are system administrators.
So how can you achieve a balance between providing your employees freedom to operate, while still monitoring and detecting suspicious behavior?
Cybersecurity awareness is key
Even though one of four data breaches involve internal actors, many of those are not a result of greed or any other intentional action, but rather employees’ ignorance of the implications of certain actions. We may all know the famous example of the U.S. Department of Homeland Security, who back in 2011 planted USB sticks with their own company logo in the parking lot outside their office. Shockingly, they found that 90% of the USB sticks were picked up by employees and plugged into computers.
This illustrates the fact that internal data breaches are often not a result of greed, but rather ignorance or unawareness of proper cybersecurity best practices.
How can we make employees think twice before picking up the USB drive and checking the content without hesitation? Opens an e-mail and click on a phony link or reveal logon credentials to someone call from IT support, even though they don’t know the guy? It is important that companies have internal focus on current issues, update operational practices, conduct internal training and implement sufficient data handling and protection policies.
UEBA makes rules based security less critical
By employing a SIEM alongside a UEBA solution and establishing formal measures for operations, companies will be able to setup alarms if e.g. blueprints, strategic roadmaps or new product descriptions are accessed or transferred electronically – thus, providing organizations with the ability to identify and address potential vulnerabilities and anomalies within their IT environment.
It is crucial for companies to start acknowledging the importance of internal breaches and establish measures for responding to the challenge. Often it is small errors leading to increased vulnerability. With LogPoint UEBA, you can easily detect both suspicious user behavior as well as other entities such as cloud, mobile or on-premise applications, endpoints, networks and external threats – out of the box.
By leveraging machine learning and big-data analytics capabilities, built on LogPoint’s unique one taxonomy, our UEBA solution builds baselines for every entity in the network and actions are then evaluated against these baselines. By this, it becomes less critical to define the right rules, saving precious time for your cybersecurity analysts. Our UEBA module will provide unparalleled time-to-value for your business, along with vastly cutting investigation time by your security team.
Needless to say, you didn’t have coffee with a hacker this morning. But you could have had coffee with someone that unintentionally aided external actors to compromise your corporate network.
You can read the original article, here.
The primary reason most organisations look at classifying the data they create and handle is to control access to sensitive information, driven by the need to manage security risk and comply with regulations, such as GDPR. However, this scope is too narrow. By focusing solely on these objectives, they’re missing an opportunity to embrace data categorisation and extract greater business value from all of their data assets.
There are two clear schools of thought around the use of data classification; security and data management:
- Data security: Teams in the security domain consider classification as a means-to-an-end approach that involves security labelling of data according to its sensitivity, to help users and tools identify its value and protect it appropriately.
- Data management: Data teams view classification as the categorising of information in order to improve its quality and utility. Business categorisation of data is based around establishing its context and the content, and then considering who has access to it, and how it is organised, stored, used and deleted across its lifecycle. This domain is primarily concerned with how data can be used to raise business performance and efficiency, streamline processes and improve data governance practices.
At Boldon James we see these two domains as inextricably linked – and for an organisation to get the full benefit from data classification they need to ensure both worlds are connected. To do this, you need to go back to the classification policy, and design an approach that goes beyond simple security labelling to one that harnesses data categorisation.
We’re seeing a growing trend for data classification customers to ask broader questions around their information. They’re taking a wider perspective of the problem, moving from ‘we have all this data – we need to protect it’, to ‘we have all this data – we want it to work harder for us’.
Organisations must shift to a business-centric approach to classification, tagging all information used within the business according to what it is, rather than simply according to the impact of its loss. This enables the data management and security tools that locate, organise, protect and remove data to make truly informed and coordinated decisions.
This more granular labelling can be driven by labelling the data according to its category. Categorising data is readily understood by end users as it deals in the information types they work with every day, and it’s easy for them to assign information to a category. Once you know the category, you can automatically assign all the other related tags that reflect the data management, compliance, retention and security needs of that category – as well as apply policy rules specific to those extra tags.
For example, a document might be categorised and labelled as Staff Travel Request. The data classification tool will then automatically add all the tags that relate to that category – for instance a data management tag of HR/Staff Management/Travel, a retention tag of One Year, a compliance tag of EU-GDPR and a security tag of Confidential/PII. This approach hides the additional granularity, and wraps all the required information up into one easily understood term.
To make the most of the business-enabling value of data, organisations must embrace a more holistic approach to classification that embraces data categorisation and goes beyond simple security labelling.
You can read the original article, here.
The new version of Sophos Home brings business-grade cybersecurity to your home. New features added to Sophos Home which bring powerful, business-grade cybersecurity straight to your home.
Cybercrime is big business, but it doesn’t just target big businesses. Individuals are just as vulnerable to malware and other threats as hospitals, banks, retailers, and other organizations. With Sophos Home, you get the same strong security trusted by thousands of IT professionals, and it’s incredibly simple and easy-to-use.
Artificial Intelligence
From today, Sophos Home Premium for PC has the same artificial intelligence (AI) technology that many people are already using in our enterprise product, Intercept X. This technology allows Sophos Home Premium for PC to detect and block both known and unknown malware before it executes.
In addition to this, new enhanced real-time protection against application and OS exploits stops cybercriminals from controlling trusted apps, using unpatched vulnerabilities to gain access to a system, and stealing credentials.
All versions have new features
In addition to the features that are new for Sophos Home Premium for PC, above, all versions of Sophos Home have had an update.
- Scheduled Scan – Users can now setup and administer scheduled file system scans for customized protection.
- Quarantine – More advanced users can now reconcile true and false positive file detections.
- UI Enhancements – Updates to the user interface make it easier to manage multiple devices’ security from one web browser, wherever the device is.
Take it for a test drive
Sophos Home Premium makes cybersecurity simple… Get a free trial and try it out for yourself.
You can read the original article, here.
Sophos, a global leader in network and endpoint security, today announced that it has acquired endpoint security platform company, DarkBytes. DarkBytes offers a unified platform to deliver security operations center services to organizations of all sizes.
Founded with the mission to deliver enterprise-grade endpoint security through lightweight sensors, asset inventorying, managed threat hunting, and automation technologies, DarkBytes launched their first products in March 2018 and have since been gaining traction in this competitive space. DarkBytes brings to Sophos a highly talented team with rich domain experience in managed detection and response (MDR) and Security Orchestration Automation Response (SOAR).
“Sophos predicts that eventually all IT security products will evolve into adaptive, managed services as more organizations realize that they are unable to scale resources fast enough to respond to today’s threats,” commented Joe Levy, chief technology officer at Sophos. “The strength and architecture of the DarkBytes platform will accelerate Sophos’ plans to introduce global managed security services that will eventually span endpoint, firewall, mobile devices, wireless APs, and more. We welcome the DarkBytes team to Sophos and are excited to introduce these services through our partners over the coming months.”
MDR is a managed cybersecurity service designed to detect and respond to intrusions, malware, and malicious activity that often go undetected, enabling a faster response to eliminate and mitigate those threats. MDR augments security capabilities by providing a continuous monitoring service through a trusted third party, delivered through the combined intelligence of automated response and human expertise.
“The endpoint is the new perimeter of cybersecurity. It’s where the attacks happen and where the data lives,” commented Dennis Griffin, founder and former CEO at DarkBytes. “We built our unified platform to simplify high-end security operations using the combination of endpoint sensors and cloud-delivered analytics as the best way to achieve this. Our vision for using cloud-based, next-gen technology to make enterprise-grade cybersecurity simple to use made Sophos a natural home for the next stage of our development. We look forward to delivering the market’s most comprehensive and flexible endpoint security solutions.”
You can read the original article, here.
Protecting sensitive customer data is a huge priority for today’s organizations, which face intensifying regulatory and compliance pressures and unwavering customer expectations. A single data breach can take a tremendous toll on customer loyalty; 70 percent of consumers report they would cease doing business with an organization in the event it experienced one.
Great strides have been made in ensuring data privacy through a diverse (and still growing) set of techniques, from fortifying networks and servers against external cyberattacks, to using artificial intelligence (AI) to identify and redact and/or encrypt sensitive digital data, to implementing strict policies (even at the office printer!) to ensure only authorized employees can print documents containing private information.
However, a truly rigorous and comprehensive approach to customer data privacy cannot exist unless a major source of breaches – privileged insiders – is addressed. A privileged insider is any individual with valid credentials to access internal resources, and who may use this authorized access to negatively impact the integrity of a system or confidentiality of sensitive customer data.
These individuals may not be motivated by malevolence and greed, nor are they necessarily negligent or lacking ethics. The majority are inadvertent actors – those who are blissfully unaware they’re doing anything wrong and don’t understand the potential consequences. Sixty-four percent of enterprises cite careless employees and contractors as the most common cause of insider threats, according to one recent survey.
Regardless of the root cause of an insider threat, the risks to customer data privacy are significant, and the business repercussions can include lost revenues, remediation expenses, damaged brand reputation, service disruption and more. Five best practices for protecting against insider threats including the following:
Monitor insider activity. Some organizations are reticent to implement monitoring, believing employees will view it as intrusive “big brother” behavior. Clearly this must be handled appropriately, but the benefits of insider monitoring – for both the organization, as well as individual workers – vastly outweigh the drawbacks. According to IBM, an estimated 60 percent of breaches are the result of insiders, and proactive monitoring can be the key to eliminating or reducing these. Organizations should consider education and training that explains clearly to workers how such measures actually benefit them, through greater protection and risk insulation.
Be proactive and constantly analyze. The Ponemon Institute’s latest research shows 191 days – more than six months – as the average length of time it now takes organizations to identify a data breach. In the event of malicious insider involvement, this leaves a substantial window of time to wreak havoc by misusing customer data, before the organization is even aware anything is wrong. It is no longer acceptable to passively monitor network and database activity and block access when something doesn’t look right. Rather, organizations must proactively analyze user behavior and act upon trends they see to stay ahead of potential incidents.
Get granular. One reason breaches are so damaging to customer satisfaction and brand reputation is that, in many cases, more customers are notified than may actually be necessary. When in doubt of exactly whose data was accessed, organizations tend to cast the widest net on all customers that may have possibly been impacted. This is especially true in a post-GDPR world, when organizations are now required to report breaches in 72 hours. Achieving this granularity requires more than simply seeing insiders’ session durations, but rather, understanding exactly how, when and what data was accessed. Perhaps a sensitive database was accessed, but only one section within it, as opposed to the whole thing. In the event an insider breach does happen, such granularity can greatly ease reporting and notification efforts while minimizing unnecessary collateral damage.
Manage credentials. Many organizations fail to manage privileged insider user credentials properly – meaning that if a user’s job function changes and they no longer require access to a sensitive data set, that access is not always terminated. Instead, the user accrues access to increasingly more data as their job function evolves, even though such access may no longer be required. Even worse, Osterman Research recently found that 67 percent of organizations couldn’t be sure whether a former employee is still accessing corporate resources. Mismanaged credentials can create significant exposure risks that become exponentially harder to identify, address and contain once employees walk out the door.
Focus on where the most sensitive data lives. A typical enterprise has many data repositories spread throughout it. Determining which data sources need to be monitored for insider threats is essentially a matter of identifying where the most critical data resides. This is often systems of record like the mainframe. An estimated 80 percent of the world’s corporate data continues to reside or originates on the mainframe, making it a prime target for malicious insiders.
Today’s threats to data privacy are always evolving, but one constant is the human element. Even the most seemingly rigorous data privacy initiative cannot be complete unless it addresses the insider threat. Organizations must be on the offensive, especially since these particular threats, unlike those from the outside, are more preventable.
You can read the original article, here.
The US Department for Homeland Security considers Emotet to be one of the most costly and destructive threats to US business right now. Here’s how Sophos deals with it.
Emotet is truly a threat to be reckoned with. In fact, the US Department for Homeland Security considers Emotet to be among the most costly and destructive threats to US business right now. Not that it limits itself to any one country; its reach is global with infections reported on every continent.
Emotet is a very sophisticated threat that, once in, can quickly infect an entire organization. Like other worms, it spreads without the aid of a user, enabling it to wreak widespread damage.
Once on a computer, Emotet has three main goals:
- Spread onto as many machines as possible.
- Send malicious emails to infect other organizations (damaging your sender reputation in the process).
- Download a malware payload. Traditionally the payloads have mostly been banking Trojans, with Trickbot the most prevalent. Its payload injects code into your browser to automatically debit your bank and PayPal accounts when you next login.
In many cases Emotet also tries to steal data, turning a malware infection into a data breach. Some Emotet variants skim email addresses and names from email client data and archives, likely so they can be sold as part of a wider list and used to spread more malicious spam. Others inspect your web browser, stealing histories and saved usernames and passwords.
To compound the pain, Emotet can also be a smokescreen for targeted ransomware attacks. While organizations are dealing with Emotet infections, ransomware like BitPaymer takes advantage of the distraction to hold the organization’s data hostage.
What makes Emotet so dangerous?
Emotet earns its reputation as one of the most costly and destructive threats for several reasons.
- It only needs one computer that’s not fully protected to infect an entire organization. Once it gets in, it quickly spreads laterally across the network.
- It constantly evolves. The cybercrooks behind this threat work 24/7, publishing multiple new variants and call-home addresses every single day.
- It keeps re-infecting. Emotet constantly tries to spread, often re-infecting machines that have been cleaned up.
Stop Emotet in its tracks with Sophos
Sophos’ advanced technologies can help protect your organization against Emotet.
Intercept X Advanced with EDR uses the power of advanced machine learning to identify and block Emotet files, even new variants that have never been seen before.
Cross-estate threat search enables you to hunt for hidden threats, while guided investigations show you exactly how the threat got in, which machines have been impacted, and how the threat is spreading so you can take remedial action.
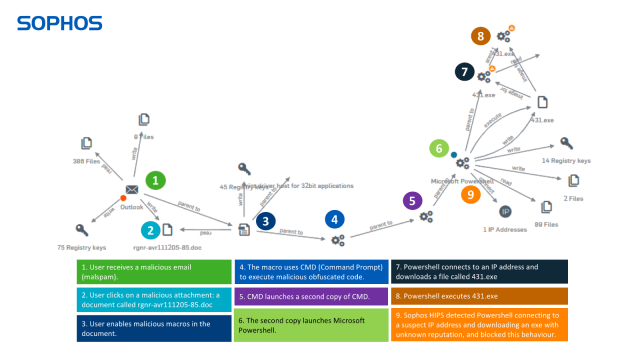
In the example below you can see how Intercept X gives you full visibility of every step in the attack chain. Note: we had to disable multiple layers of protection to allow the attack to get this far – it would normally be blocked much earlier.
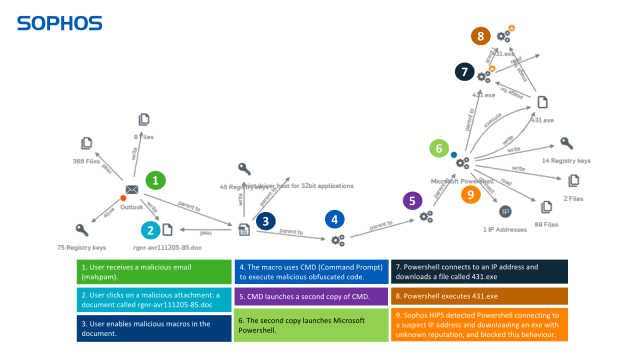
Stopping Emotet with Sophos
The US Department for Homeland Security considers Emotet to be one of the most costly and destructive threats to US business right now. Here’s how Sophos deals with it.

Emotet is truly a threat to be reckoned with. In fact, the US Department for Homeland Security considers Emotet to be among the most costly and destructive threats to US business right now. Not that it limits itself to any one country; its reach is global with infections reported on every continent.
Emotet is a very sophisticated threat that, once in, can quickly infect an entire organization. Like other worms, it spreads without the aid of a user, enabling it to wreak widespread damage.
Once on a computer, Emotet has three main goals:
- Spread onto as many machines as possible.
- Send malicious emails to infect other organizations (damaging your sender reputation in the process).
- Download a malware payload. Traditionally the payloads have mostly been banking Trojans, with Trickbot the most prevalent. Its payload injects code into your browser to automatically debit your bank and PayPal accounts when you next login.
In many cases Emotet also tries to steal data, turning a malware infection into a data breach. Some Emotet variants skim email addresses and names from email client data and archives, likely so they can be sold as part of a wider list and used to spread more malicious spam. Others inspect your web browser, stealing histories and saved usernames and passwords.
To compound the pain, Emotet can also be a smokescreen for targeted ransomware attacks. While organizations are dealing with Emotet infections, ransomware like BitPaymer takes advantage of the distraction to hold the organization’s data hostage.
What makes Emotet so dangerous?
Emotet earns its reputation as one of the most costly and destructive threats for several reasons.
- It only needs one computer that’s not fully protected to infect an entire organization. Once it gets in, it quickly spreads laterally across the network.
- It constantly evolves. The cybercrooks behind this threat work 24/7, publishing multiple new variants and call-home addresses every single day.
- It keeps re-infecting. Emotet constantly tries to spread, often re-infecting machines that have been cleaned up.
Stop Emotet in its tracks with Sophos
Sophos’ advanced technologies can help protect your organization against Emotet.
Intercept X Advanced with EDR uses the power of advanced machine learning to identify and block Emotet files, even new variants that have never been seen before.
Cross-estate threat search enables you to hunt for hidden threats, while guided investigations show you exactly how the threat got in, which machines have been impacted, and how the threat is spreading so you can take remedial action.
In the example below you can see how Intercept X gives you full visibility of every step in the attack chain. Note: we had to disable multiple layers of protection to allow the attack to get this far – it would normally be blocked much earlier.
Sophos XG Firewall’s advanced sandboxing examines the executable files. The HIPS behavioral monitoring detects Emotet, blocking it from entering the organization. XG also blocks all known IP addresses associated with Emotet.
Email protection (both in XG Firewall and Sophos Email) can also scan outbound emails to detect Emotet spam and identify which machines are sending it.
Join forces against Emotet with Synchronized Security
Intercept X and XG Firewall are powerful tools to stop Emotet on their own – and even better together. They share real-time threat information and automatically respond to incidents. When Intercept X detects Emotet running, it notifies XG Firewall which automatically isolates the infected machines, preventing lateral movement. Intercept X then cleans up the infection, telling the firewall once the malware is removed. At this point, XG Firewall restores network access.
Uniquely, by working together, they stop Emotet from moving across your organization. And the best news? All this happens automatically. Zero-touch. In seconds.
You can read more about what Sophos has learned from dealing with Emotet over on our sister site, Naked Security, in our article Fighting Emotet: lessons from the front line. Sophos has also prepared a Knowledge Base article for its customers: Resolving outbreaks of Emotet and TrickBot malware.