News
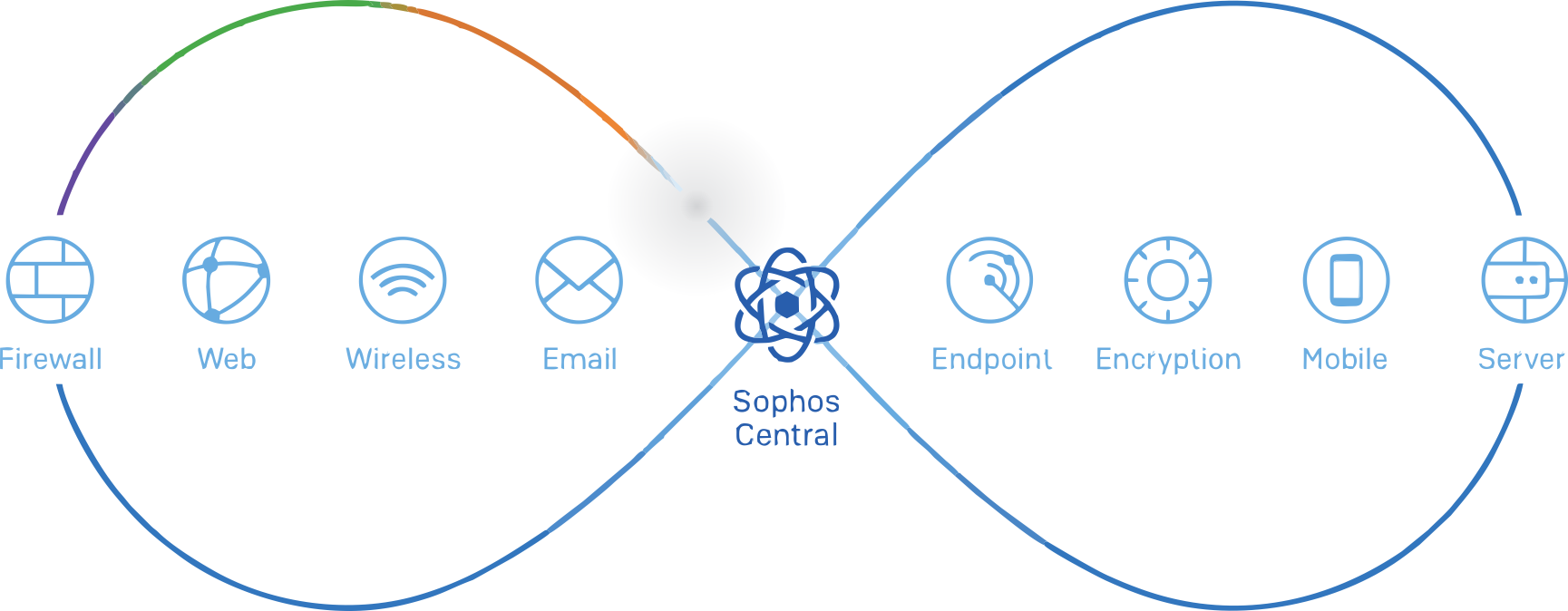
The intuitive management console for all your security solutions.
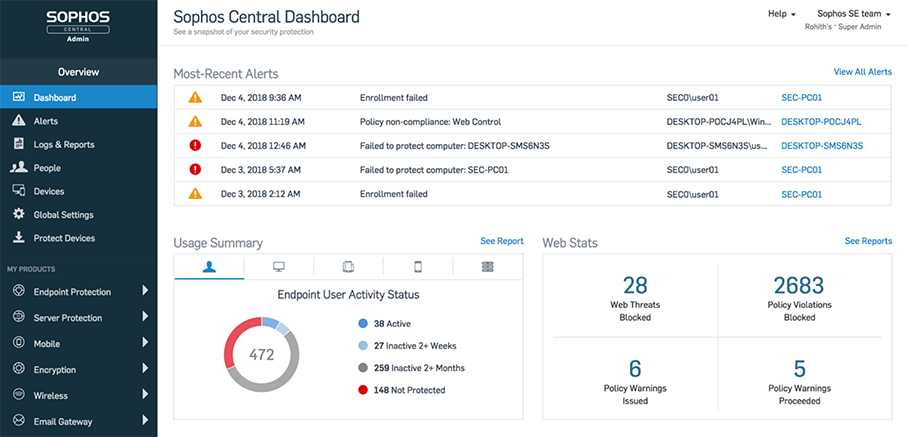
Sophos Central is an award-winning security platform that lets you manage all your products from a single, intuitive interface.
From next-gen endpoint and encryption to mobile and web security, we have you covered. By moving to Sophos Central you’ll enjoy:
- Easier IT management: Control everything through a single, web-based console.
- Superior protection: Get market-leading products engineered to work together.
- Better security ROI: Save time and money by consolidating into a single platform.
Try it for free and see how our Sophos Central can help you to manage your IT security with a single interface, and benefit from the revolutionary Synchronized Security technology. Learn more, here.
This course provides an in-depth study of Sophos Central, designed for experienced technical professionals who will be planning, installing, configuring and supporting deployments in production environments. It consists of presentations and practical lab exercises to reinforce the taught content, and electronic copies of the supporting documents for the course will be provided to each trainee through the online portal. The course is expected to take 3 days to complete, of which approximately 9 hours will be spent on the practical exercises.
Requirement
Prior to attending this course, trainees should:
- Complete the Sophos Central Endpoint and Server Protection and should have passed the Certified Engineer exam
- Experience with Windows networking and the ability to troubleshoot issues
- A good understanding of IT security
- Experience using the Linux command line for common tasks
- Experience configuring Active Directory Group Policies
- Experience creating and managing virtual servers or desktop
Target audience:
This course is designed for technical professionals who will be planning, installing, configuring and supporting deployments in production environments. And for individuals wishing to obtain the Sophos Central Certified Architect certification.
Objectives:
On completion of this course, trainees will be able to:
- Design an installation considering all variables
- Undertake a multi-site installation appropriate for a customer environment
- Explain the function of core components, how they work, and how to configure them
- Track the source of infections and cleanup infected devices
- Perform preliminary troubleshooting and basic support of customer environments
Certification:
To become a Sophos Certified Architect, trainees must take and pass an online assessment. The assessment tests their knowledge of both the presented and practical content. The pass mark for the assessment is 80%, and is limited to 3 attempts.
Duration: 3 days
Content
- Module 1: Deployment Scenarios (60 mins)
- Module 2:Client Deployment Methods (65 mins)
- Module 3:Endpoint Protection Policies (80 mins)
- Module 4:Server Protection Policies (30 mins)
- Module 5:Protecting Virtual Servers (60 mins)
- Module 6:Logging and Reporting (45 mins)
- Module 7: Managing Infections (45 mins)
- Module 8: Endpoint Detection and Response (30mins)
- Module 9:Management (65 mins)
Course content
Module 1: Deployment Scenarios (60 mins)
-
- Identify some of the common challenges when deploying Central
- Deploy Update Caches – Set up Message Relays
- Configure AD Sync Utility
- Identify where Update Caches and Message Relays should be used
- Labs (45 mins)
- Register and activate a Sophos Central evaluation
- Install Server Protection
- Install and Configure AD Sync Utility
- Deploy an Update Cache and Message Relay
Module 2: Client Deployment Methods (65-75 mins)
- Identify the recommended steps for deploying Sophos Central
- Explain the installation process, and identify the different types of installer
- Automate deployment for Windows, Linux and Mac computers
- Migrate endpoints from Enterprise Console
- Locate installation log files
- Remove third-party products as part of a deployment
- Labs (75-90 mins)
- Enable Server Lockdown
- Deploy using Active Directory Group Policy
- Use the Competitor Removal Tool
- Deploy to a Linux Server using a Script
Module 3: Endpoint Protection Policies (80-90 mins)
- Describe the function and operation of each of the components that make up an Endpoint Protection and Intercept X
- Configure policies to meet a customer’s requirements and follow best practice
- Test and validate Endpoint Protection
- Configure exclusions
- Configure Data Loss Prevention
- Labs (100-120 mins)
- Test Threat Protection Policies
- Configure and Test Exclusions
- Configure Web Control Policies
- Configure Application Control Policies
- Data Control Policies
- Configure and test Tamper Protection
Module 4: Server Protection Policies (30 mins)
- Configure Server Protection Policies
- Configure and Manage Server Lockdown
- Labs (65-75 mins)
- Configure Sever Groups and Policies
- Manage Server Lockdown
- Test Linux Server Protection
Module 5: Protecting Virtual Servers (60 mins)
- Connect AWS and Azure accounts to Sophos Central – Deploy Server Protection to AWS and Azure
- Deploy and Manage Sophos for Virtual Environments
- Labs (60 mins)
- Download the installer for the Security Virtual Machine
- Install the Security Virtual Machine (SVM) on a Hyper-V Server
- Configure Threat Protection policies to apply to the Security VMs and the Guest VMs they protect
- Perform a manual installation of the Guest VM Agent and view logs
- Test and configure a script to deploy the GVM Agent
- Manage Guest VMs from the Central Console
- Test Guest VM Migration
Module 6: Logging and Reporting (45 mins)
- Explain the types of alert in Sophos Central, and be able to read an RCA
- Use the Sophos Central logs and reports to check the health of your estate
- Export data from Sophos Central into a SIEM application
- Locate client log files on Windows, Mac OS X and Linux
- Labs (55-60 mins)
- Generate and analyze an RCA
- Configure SIEM with Splunk
Module 7: Managing Infections (45-60 mins)
- Identify the types of detection and their properties
- Explain how computers might become infected
- Identify and use the tools available to cleanup malware
- Explain how the quarantine works and manage quarantined items
- Cleanup malware on a Linux Server
- Labs (40 mins)
- Source of Infection Tool
- Release a File from SafeStore
- Disinfect a Linux Server
Module 8: Endpoint Detection and Response (30 mins)
- Explain what EDR is and how it works
- Demonstrate how to use threat cases and run threat searches
- Explain how to use endpoint isolation for admin initiated and automatic isolation
- Demonstrate how to create a forensic snapshot and interrogate the database
- Labs (30 mins)
-
- Create a forensic snapshot and interrogate the database
- Run a threat search and generate a threat case
Module 9: Management (65 mins)
- Use the Controlled Updates policies appropriately
- Enable multi-factor authentication
- Use the Enterprise Dashboard to manage multiple sub-estates
- Identify the benefits of the Partner Dashboard
- Identify common licensing requirements
- Labs (25 mins)
- Enable Manually Controlled Updates
- Enable Multi-Factor Authentication
Agenda
Trainer: Michael Eleftheroglou
Day 1 Tuesday 11 February 2020
9:30-10:30 Deployment Scenarios
10:30-10:45 Break
10:45-11:30 Labs
11:30-11:45 Break
11:45-13:00 Client Deployment Methods I
13:00-14:00 Break Lunch
14:00-15:30 Labs
15:30-15:45 Break
15:45-17:15 End Point Policies
Day 2 Wednesday 12 February 2020
9:30-11:15 Labs
11:15-11:30 Break
11:30-12:00 Server Protection Policies
12:00-12:15 Break
12:15-13:30 Labs
13:30-14:30 Break- Lunch
14:30-15:30 Protecting Virtual servers
15:30-15:45 Break
15:45-16:45 Labs
16:45-17:30 Logging and Reporting
Day 3 Thursday 13 February 2020
9:30-10:30 Labs
10:30-10:45 Break
10:45- 11:30 Managing Infections
11:30-12:00 Labs
12:00-12:10 Break
12:10-12:40 Endpoint Detection and Response
12:40-13:45 Management
13:45-14:45 Break – Lunch
14:45-17-15 Labs and Exams
To better understand the realities of network security today, Sophos commissioned leading research specialist Vanson Bourne to conduct an independent survey of 3,100 IT managers spanning 12 countries and six continents.
The results shed new light onto the practical reality of today’s network security and the challenges IT teams face. It also reveals the Achilles heel of next-gen firewalls: the struggle to balance performance, privacy and protection.
Expect to find a threat on your network
The first takeaway from the survey is that organizations should expect to be hit by a cyberthreat. Over two-thirds (68%) of respondents fell victim to a cyberattack in the last year.
This propensity to fall victim to a threat is not the result of a lack of protection: 91% of affected organizations were running up-to-date cybersecurity protection at the time of the attack. However, good intentions and good practices are clearly not enough: there are still holes in organizations’ defenses that are enabling threats to get through.
Firewall enhancement wish list
Better threat visibility topped the list of improvements that IT managers want from their firewall, with 36% including it in their top three desired enhancements.
The fact that visibility outranked a desire for better protection illustrates just how significant an issue lack of insight is for IT teams.
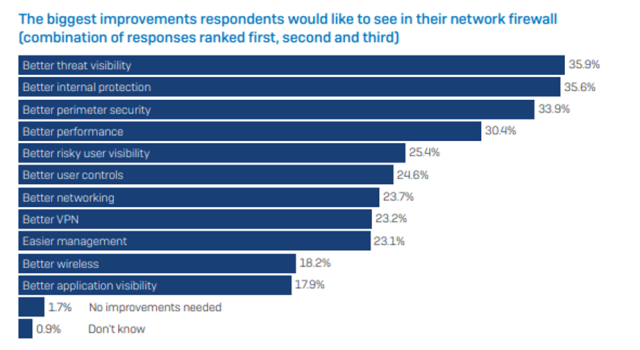
However, firewall security isn’t the only area in need of improvements, three in ten of the IT managers also wanted better performance.
Overall, a clear picture emerged: it’s no longer a question of one or the other, rather, today’s IT teams require both performance and protection from their firewalls.
The understated risk: encrypted traffic
Encryption keeps network traffic private, but it doesn’t mean the contents can be trusted. In fact, encrypted traffic is a huge security risk because it renders firewalls blind to what is flowing through the network and prevents them from identifying and blocking malicious content.
Hackers are actively exploiting encryption to enable their attacks to enter undetected. SophosLabs research has revealed that 32% of malware uses encryption.
The level of encrypted network traffic is rising rapidly. Data from the Google Transparency Report indicates that over 80% of web sessions are now encrypted across all platforms, up from 60% just two years ago. However, the IT managers surveyed believed that on average only 52% of their network traffic is encrypted.
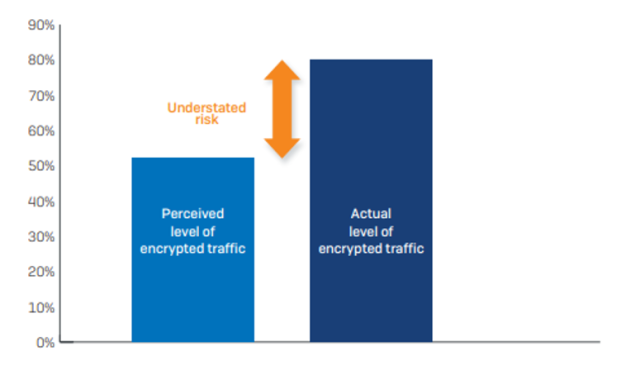
The discrepancy between perceived and actual levels of encryption together with the widespread use of encryption in cyberattacks suggests that encrypted traffic is an underestimated security risk.
The Achilles heel of network security
While 82% of survey respondents agreed that TLS inspection is necessary, only 3.5% of organizations are decrypting their traffic to properly inspect it.
There are a number of reasons behind this: concerns about firewall performance; a lack of proper policy controls; poor user experience; and complexity.
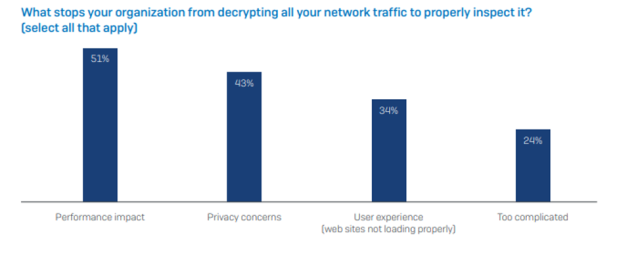
The reality is that most organizations need to carefully balance performance, privacy and security. However, they lack the tools needed to do so effectively and efficiently. As a result, they are choosing to allow encrypted traffic to pass unchecked and putting themselves at risk from hidden network threats.
This inability to balance performance, privacy and protection is the Achilles heel, the hidden weakness, of many next-gen firewall and UTM solutions.
Sophos XG Firewall: Designed for the modern encrypted internet
The Xstream Architecture in XG Firewall v18 offers a ground-up solution to eliminating the network traffic blind spot without impacting performance.
It delivers:
- High performance, a lightweight streaming engine with high connection capacity
- Unmatched visibility into your encrypted traffic flows and any errors
- Top security that supports TLS 1.3 and all modern cipher suites with robust certificate validation
- Inspection of all traffic, being application and port agnostic
- A great user experience with extensive interoperability to avoid breaking the internet
- Powerful policy tools that offer the perfect balance of performance, privacy and protection
The new Xstream SSL Inspection engine will be available to all XG Firewall customers at no extra charge. Try it now as part of the early access program.
To learn more about Sophos XG Firewall and see it in action, visit the web page or start an instant online demo.
Download a PDF copy of the report to get the full survey results.
Nearly every organization today relies on a variety of remote third party vendors to access, maintain and support critical internal systems and resources. These vendors have come to play a critical role in maintaining modern organizations’ complex and distributed enterprise infrastructures.
Given that third party vendor access has been at the heart of recent breaches, CyberArk recently conducted a survey of IT and security decision makers to learn more about common approaches to managing and securing access to critical internal resources. Here are some of the most eye-opening findings:
Third Party Privileged Access is Everywhere.
It’s probably not a shock to most people that 90% of respondents said that they allow third party vendors to access critical internal resources. What was slightly shocking was that more than a quarter (26%) said that they use over 100 third party vendors! That’s a lot of accounts to account for, manage and secure.
For many organizations, securing third party vendor access is incredibly complex – often requiring a cobbled together solution of products like multi-factor authentication, VPN support, corporate shipped laptops, directory services, agents and more. This has not only led to confusion and overload for security practitioners, but also creates difficult and often insecure routes for third parties to access the systems they need to do their jobs.
Which leads to our next finding….
Third Party Access is a Top 10 Organizational Risk.
Nearly three-quarters (72%) of organizations view third party access as one of their top 10 organization-wide security risks, alongside others like cloud abuse, phishing and insider threats. Third party access is quickly rising in the ranks to become a top priority for organizations and for good reason. These attacks and resulting data breaches can be incredibly costly for organizations, both in terms of reputation and financial losses.
Despite this, the same organizations overwhelmingly aren’t satisfied with how they currently approach managing and securing access for these remote vendors. A whopping 89% of respondents felt that they could do better or were completely dissatisfied with their efforts to secure third party vendor access.
Provisioning and Acute Visibility is a Challenge.
So, if third party access is a top 10 risk, why are so many failing to secure it? We found that 50% of organizations state that provisioning and deprovisioning access was their biggest challenge, while 47% highlighted lack of visibility.
Provisioning and deprovisioning access can feel a lot like Goldilocks and the Three Bears. You can’t allow too much access (where vendors have access to things they don’t need or for longer than they’re needed) or too little (where vendors are forced to create unsafe backdoor routes to critical resources). It has to be just right.
However, currently, legacy solutions dominate. For instance, while 86% of organizations rely on VPNs to secure third party access, they were not designed to manage dynamic privileged access requirements like role-based access protection and session recording. On the visibility front, companies aren’t always aware of what third party vendors are doing once they authenticate – and that is a serious problem. A best practice – one often required for audit and compliance – is to record, log and monitor privileged activities.
As organizations depend more and more on third parties to get the work done, the difficulties they face when it comes to security is getting harder and harder to ignore.
Without a dedicated solution specifically for managing third party privileged access, organizations have been forced to use miscast solutions like VPNs . To remedy this problem, we introduced CyberArk Alero, a truly modern, innovative solution.
CyberArk Alero combines Zero Trust access, biometric multi-factor authentication and just-in-time provisioning into one Software-as-a-Service (SaaS)-based solution. Alero ensures that remote vendors only access what they need by integrating with CyberArk Core Privileged Access Security for full audit, recording and remediation capabilities.
Alero is designed to provide fast, easy and secure privileged access for remote vendors who need access to critical internal systems. By not requiring VPNs, agents or passwords Alero removes operational overhead for administrators and improves security.
To learn more about the challenges of securing third party access, read our eBook “Third Party Privileged Access to Critical Systems.” You can also request a demo to find out more about CyberArk Alero.
Intercept X is the one of the world’s best endpoint protections, and our third-party test scores and analyst reports help prove that claim. But to be the best, you must go beyond just protecting Windows machines.
Our goal is to protect your users regardless of which type of endpoint they are using. This includes desktops, laptops, servers, mobile devices and Mac endpoints.
We are proud to announce that Intercept X was the only Mac endpoint protection that achieved a perfect score in every test conducted by AV-Test in 2019. That means we scored six out of six for protection, performance and usability, every time.
The perfect scores for Intercept X meant that we were awarded the badge of “Approved” corporate endpoint protection for MacOS.

Υou can review the test score details at AV-Test:
Business users can learn more about Intercept X and start a free trial today.
Home users can start a free trial of Sophos Home Premium.
While many companies spend a lot of energy protecting their business from external threats, security events initiated by insiders can be just as costly. Malicious insiders not only have intimate knowledge of corporate systems and infrastructure, but they also have something far more powerful: legitimate privileged access.
The challenge of insider threats is pervasive, and recent events indicate it shows no signs of slowing down. Whether watershed examples like Terry Childs, a former network administrator who essentially shut down the city of San Francisco, or cases involving IP theft or fraud, privileged access abuse can take form in a couple of ways. The first is when employees are granted more access than necessary to do their jobs. The second arises when someone with valid access uses privileged accounts to purposefully go against policy and abuses their power.
Regardless of the situation, the insider threat is ultimately a human challenge. Humans are unpredictable and it’s hard to foresee motivation. We want to trust the employees we hire – especially the ones who are given access to our most sensitive information. One key for companies is to understand who has privileged access, and consistently enforce the principle of least privilege – where employees are granted appropriate access to perform their jobs…no more, no less.
In addition, technology can help identify anomalous behavior and send an alert that systems or information were being accessed outside of policy. This adds yet another critical security layer that helps organizations better detect patterns and behaviors that may signal privileged access abuse.
While insider threat stories are certainly cautionary tales on unfettered privileged access for employees – the truth is that once an attacker is in a network it doesn’t matter if they are an attacker thousands of miles away or an employee three feet away – the risks are the same.
To be in the best position to mitigate these threats, organizations need to re-evaluate how they are securing and managing privileged access – not just to protect from the external attacker exploiting weaknesses, but also the malicious insider who might be working right under their noses.
It may have been around for 30 years, but ransomware continues to evolve and bring organizations to their knees. Make sure you’re ready for it.
Thirty years on from the world’s first attack, ransomware is stronger than ever. Cybercriminals continue to evolve their tactics and techniques, taking advantage of changes in technology and society to refine their approach.
The result: highly advanced, highly complex threats that can bring organizations to their knees. When you add together the full costs of remediation, including downtime, people time, device cost, network cost, lost opportunities and ransom paid, the final sums per victim are eye-watering.
What’s next for ransomware?
The one thing we can be sure of is that ransomware is going to keep evolving. Here are three new areas where the tentacles of ransomware are starting to reach.
Public cloud ransomware targets and encrypts data stored in public cloud services like Amazon Web Services (AWS), Microsoft Azure (Azure) and Google Cloud Platform (GCP).
While the public cloud offers lots of advantages, confusion about security responsibilities creates gaps in protection that hackers are quick to exploit.
In addition, weak configuration and open public access to cloud resources (be that storage buckets, databases, user accounts, etc.) make it easier for criminals to breach data storage.
Service provider attacks. As technology and threats become ever more complex, companies are increasingly outsourcing their IT to specialist managed service providers (MSPs).
Cybercriminals have realized that targeting MSPs enables them to hold multiple organizations hostage with a single attack. One attack, many ransoms.
MSPs offer a level of security expertise that is hard to match in many organizations. If you use a MSP, make security one of your selection criteria. A good MSP will be happy to share how it secures both its own and its customers’ organizations.
Encryption-free attacks. The ability to encrypt files was one of the original core capabilities needed to make ransomware a viable cybercrime.
Today cybercriminals no longer need to encrypt your files to hold you hostage. Why? Because they believe you’ll pay up just to stop your data going public.
How to defend against ransomware
Adopt a three-pronged approach to minimize your risk of falling victim to an attack.
1. Threat protection that disrupts the whole attack chain.
As we saw recently with Ryuk, today’s ransomware attacks use multiple techniques and tactics, so focusing your defense on a single technology leaves you very vulnerable.
Instead, deploy a range of technologies to disrupt as many stages in the attack as possible. And integrate the public cloud into your security strategy.
2. Strong security practices.
These include:
- Use multi-factor authentication (MFA)
- Use complex passwords, managed through a password manager
- Limit access rights; give user accounts and admins only the access rights they need
- Make regular backups, and keep them offsite and offline where attackers can’t find them
- Patch early, patch often; ransomware like WannaCry relied on unpatched vulnerabilities to spread
- Lock down your RDP; turn it off if you don’t need it, use rate limiting, 2FA or a VPN if you do
- Ensure tamper protection is enabled – Ryuk and other ransomware strains attempt to disable your endpoint protection, and tamper protection is designed to prevent this from happening
3. Ongoing staff education.
People are invariably the weakest link in cybersecurity, and cybercriminals are experts at exploiting normal human behaviors for nefarious gain. Invest – and keep investing – in staff training.
Learn more
Read our new paper Ransomware: The Cyberthreat that Just Won’t Die for a deeper dive into what’s behind ransomware’s longevity, where it’s going, and how best to defend against it.
How Sophos can help
Sophos offers a range of products and services to help you protect against ransomware:
- Sophos Managed Threat Response (MTR). Many organizations don’t have the expertise, resources, or desire to monitor their network 24/7. The Sophos MTR service is a dedicated, round-the-clock team of threat hunters and response experts who constantly scan for and act on suspicious activity.
- Sophos Intercept X includes advanced protection technologies that stop ransomware on your endpoints and servers at multiple stages of the attack chain, including AI-powered threat protection, exploit protection, credential theft, deep learning and CryptoGuard.
- Sophos XG Firewall is packed with advanced protection to detect and block ransomware attacks, and stop hackers moving laterally around your network to escalate privileges.
- Cloud Optix continuously analyzes public cloud resources to detect, respond and prevent gaps in security across AWS, Azure and GCP public cloud environments that can be exploited in a ransomware attack.
- Synchronized Security. Intercept X and XG Firewall are great on their own, but even better together. If anything triggers a detection, XG Firewall and Intercept X work together to automatically isolate the affected devices – preventing the threat from spreading further.
For the third year in a row Sophos has been recognized as a winner in the CRN Tech Innovators Awards.
In November, CRN, a brand of The Channel Company, named Sophos as the best endpoint security solution, again. This is the third year in a row Sophos has been recognized as a winner for Endpoint Security in the CRN Tech Innovators Awards.
Intercept X Advanced with EDR was chosen from a diverse field of products. It rose above the others thanks to its technological advancements, unique features, and its proven track record of helping customers and partners solve IT and security challenges.
Bob Skelley, CEO of The Channel Company, said of the awards: “CRN’s Tech Innovator Awards honor technology vendors who work tirelessly to craft ground-breaking solutions for end users, matching the speed of the channel’s evolution. The winners in this year’s award categories deserve congratulations for their success in driving IT innovation forward for solution providers and their customers”.
Receiving praise from trusted third parties is nothing new for Intercept X. Recently, it has been ranked #1 by MRG Effitas, SE Labs, AV Comparatives, and NSS Labs. Sophos was named a “Leader” by both Forrester and Gartner for endpoint protection, and Intercept X was named “Editor’s Choice” for best ransomware protection by PC Magazine.
You can read about Intercept X and The Tech Innovator Awards in the December issue of CRN.
As the world rolls into another Cyber Monday, and online shoppers continue their hunt for the best deals, SophosLabs wants to remind you that there’s a metaphorical malware elephant in the room that would like nothing more than to steal financial information, and the use of your computer, for nefarious ends.
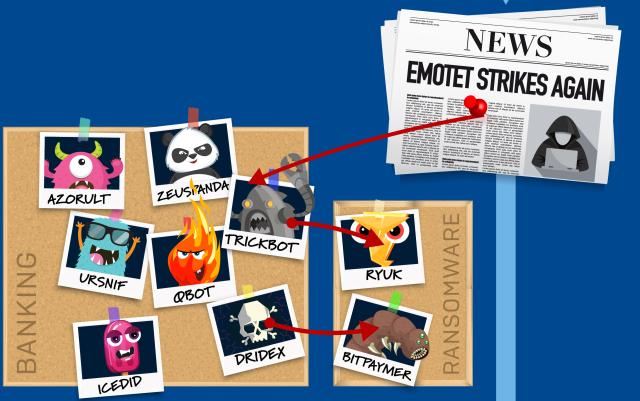
The Emotet Ecosystem infographic, produced by experts within SophosLabs, describes the infection process and subsequent behavior commonly displayed by samples in the Emotet malware family. Emotet is routinely among the most problematic and widely distributed malware family that Sophos researchers encounter daily. If there were such a thing as a Most Wanted list for malware, Emotet would surely top the list.
Emotet serves a purpose both as a standalone malware capable of causing significant harm on its own, and as a distribution network for other malware families, whose operators appear to engage with Emotet’s software distribution capabilities as a matter of routine. Part of the payload package may, in fact, be components that assist Emotet in finding and infecting other victims. In this way, Emotet plays a uniquely central role in a wide variety of malware infection scenarios, just a few of which are illustrated here.
You may download a full-resolution version of the infographic either as a PDF or as a .PNG image.
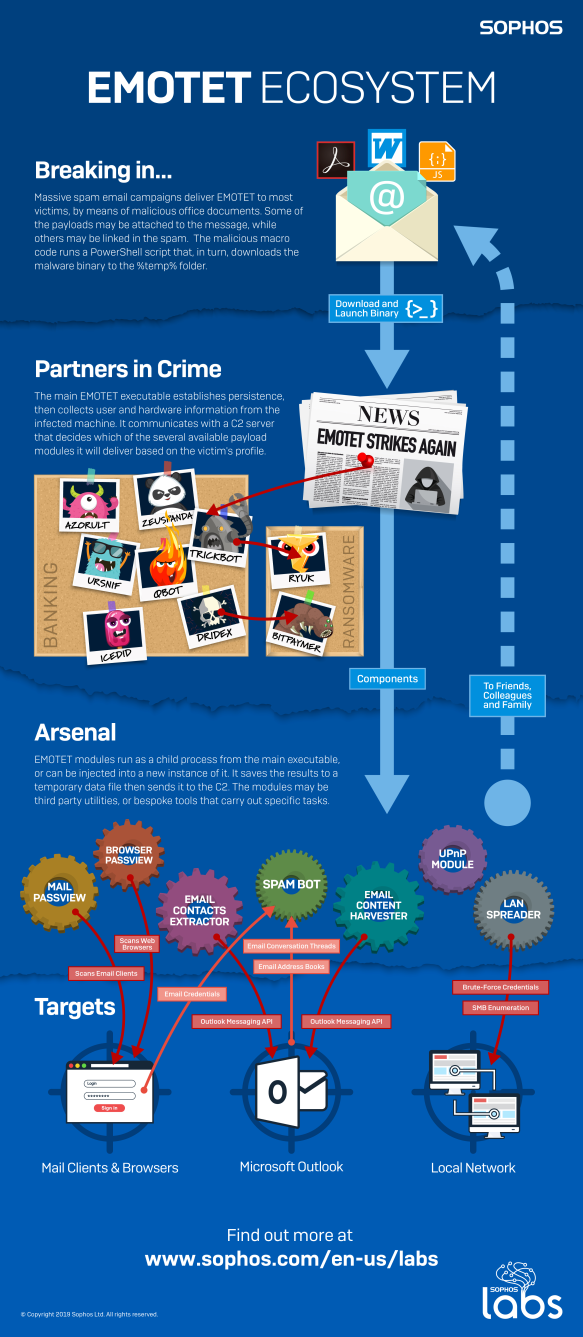
Most Emotet infections begin with a malicious spam email that prompts the recipient to open a malicious Microsoft Office document. The document may be attached to the message, or the message may contain a link to download the document from a website. When someone opens one of these documents, it retrieves the Emotet malware executable and launches it (usually from the %temp% folder) on the victim’s computer.
After establishing persistence (the ability to start itself after a reboot), the malware sends profile information to its operator(s) about the victim and their computer. Knowing about the victim, their computer, and the network on which it is running helps the criminals decide what payloads to deliver. Emotet routinely delivers samples of one or more families of credential-stealing Trojan malware, such as Trickbot, Dridex, Ursnif, or Azorult.
Depending on what the profile information reveals about the target, and the goals or priorities of the attacker, the attacker may leverage the payloads that Emotet distributed to deliver ransomware or other malware payloads. For example, Emotet may deliver Trickbot to the target machine, and then Trickbot may deliver the Ryuk ransomware to that same machine.
The Emotet ecosystem also includes a variety of payloads the malware uses for a variety of ancillary tasks. These payloads may steal and exfiltrate credentials, laterally spread the malware within the network in which the infected machine is located, scrape the target’s hard drive for email addresses, harvest data from the contents of email messages sent to and from the target, or even use the infected machine to send out new spam campaigns to the newly discovered targets.
Some of these additional payloads include legitimate tools for power users that have been publicly available for some time, such as NirSoft’s Mail PassView or Browser PassView. Several of the payloads appear to be specialized for the task, such as the mail scraper/spam bot components. These components extract message text and subject lines from Outlook, which the spam bot component uses to inject a weaponized office document file into the middle of an email thread between the victim and one or more potential targets, using the same subject line as the original message thread.
Such techniques help ensure the Emotet ecosystem continues to grow and flourish, at all of our peril.
Can you see all your network traffic? If not, you’re not alone.
In a vendor-agnostic survey of 3,100 IT managers across 12 countries, commissioned by Sophos, a huge 96% acknowledged that they lack visibility into their network traffic.
Diving deeper into the scale of the issue, it was also revealed that just under half (43%) of all network traffic cannot be identified by the firewall. Instead it falls into a generic bucket such as uncategorized, unknown, unclassified, insufficient data, HTTP, HTTPS, SSL, UDP, TCP, internet, web browsing, etc.
Unsurprisingly, this bandwidth blindness leads to multiple areas of concern, with security topping the list:
| Concern from inability to see all network traffic | % IT managers |
| Security | 58% |
| Productivity | 46% |
| Lack of control/ prioritization | 44% |
| Legal liability / compliance | 41% |
The scale of this issue becomes fully apparent when you learn that better threat visibility is now the single biggest improvement IT managers want from their firewall, knocking ‘better security’ from the top spot.
What’s hiding in your traffic?
Unidentified traffic is an eclectic mix. Some is custom apps that the organization has invested in but whose signatures are not recognized.
Others are potentially unwanted apps (PUAs) that are not required by the organization and which try to fly under the radar. Social messaging apps often fall into this category.
And then there are the malicious apps which bring malware into your organization.
If you can’t see it, you can’t control it. Without visibility into your network traffic you can’t control who and what is using your bandwidth. You can’t prioritize the custom apps, limit the non-essential apps or block the malicious apps.
See everything with Synchronized Security
The solution to bandwidth blindness is to enable your endpoint protection and firewall to work together. Even if the firewall can’t identify the app, the endpoint protection can; by working together they can share and act on this information.
Synchronized Security is Sophos’ award-winning cybersecurity system where XG Firewall and Sophos Intercept X share app, threat, and health data in real time through our revolutionary Security Heartbeat™. Together they enable you to see all apps and processes using your bandwidth.
If XG Firewall can’t identify an app, Intercept X provides the missing information. XG Firewall then automatically classifies the app, applying the necessary traffic rules. We call this Synchronized Application Control.
Watch this short video for a step-by-step guide to setting it up:
Τry Synchronized Application Control for yourself
If you already have XG Firewall and Intercept X, you are all set.
- No need to do anything! Simply follow the instructions in the video to see all your traffic.
If you’re already using XG Firewall
- Activate a free 30-day trial of Intercept X
- Register your XG Firewall in Sophos Central
- Use the XG Firewall reporting to see all apps and processes
If you’re already using Sophos Intercept X
- Activate a free 30-day trial of XG Firewall
- Register your trial license of XG Firewall in Sophos Central
- Set your firewall rules
- Use the XG Firewall reporting to see all apps and processes
If you are new to XG Firewall and Intercept X
- Start a free trial of both products
- Follow the above steps
Speak to your Sophos representative or contact your local Sophos partner to learn more about Synchronized Security, and to discuss how it can help you.
You are a successful business, but what are your aims for data classification? A simple classification solution might tick the boxes, but should your approach really be just a simple tick-box exercise? Our approach sees classification moulded to your business, seamlessly integrating with pre-existing organisational security processes, and crucially, with the way your users work.
You already know that a large percentage of your data is highly sensitive, whether it be HR or Finance specific. So is just one protective label going to be sufficient to protect all that data across the board? Let’s look at some examples where simple document tagging can result in an incorrect classification…
On the surface, a small regional sales report may look very similar to the company’s global sales report. However, the two reports will include different information, produced for different people within the business, and therefore, should not be classified with the same label. Pre-release accounts may look the same as post-release day accounts, and the HR master payroll file could look like an individual annual salary review.
So how do you get real value from a classification solution? Questions such as:
- who can see the document,
- how is it stored, and
- when should it be deleted, must all be considered.
Let’s strip this back…
Firstly, think, why is it you are implementing a data classification solution?
In choosing to do so, you’ve made the first step in accepting that data classification is going to benefit your organisation in one or more ways.
Secondly, work out what labels your organisation is going to need; as just demonstrated, using only one level of sensitivity is not enough for most organisations to effectively protect their data. A further level of labels allows a user to better classify the document, specifying any special content such as PII, or perhaps even PHI data, and ensures that the information is protected and used correctly.
With Boldon James Classifier, labels can be tailored to appropriate job function and level of seniority, effectively controlling distribution. For example, having a “Management” label easily prevents high-level documents being sent to the whole company without approval.
Ultimately, the users’ needs cannot be forgotten. For example, reducing the number of clicks that a user needs to classify a document is important, which is why Boldon James has introduced intelligent suggested classification. Pop-up prompts asking a few simple questions enables the user to make sure the document is labelled with a more accurate classification, as opposed to a generic label based solely on a machine’s interpretation of the document type.
This makes a comprehensive policy easy to understand and use on a daily basis, ensuring that the data is protected to the correct level. Helping users has been taken further by Boldon James with Business-Centric Classification, allowing a user to identify a specific document type such as ‘Jo Blogs Salary Review’ rather than just ‘Payroll’ for instance.
Download the fact sheet to discover more about Boldon James’ data classification offering, and why simple classification is not a sufficient approach for your enterprise business.
Sophos, a global leader in next-generation cloud-enabled cybersecurity solutions, today announced that Sophos Intercept X is once again named the best endpoint security solution by CRN, a brand of The Channel Company. For the third consecutive year, it’s recognized as a winner in the CRN Tech Innovator Awards, which honor innovative hardware, software and services.
“The new SophosLabs Threat Report finds that cyber criminals are raising the stakes with automated, active attacks designed to evade security controls and turn organizations’ trusted management tools against them to make a profit and maximize disruption,” said Erin Malone, vice president, North America channel sales, Sophos. “Sophos is committed to protecting organizations, and we’re continuously innovating to stay ahead of new and evolving threats. This award is validation that we’re arming trusted partners with the industry’s best solutions to thwart complex attacks.”
Hundreds of products were evaluated, and Intercept X outperformed others in technological advancements, uniqueness of features and potential to help solution providers solve common IT challenges. Sophos XG Firewall and Sophos Cloud Optix also make the list as finalists.
Intercept X is the industry’s most sophisticated endpoint prevention solution, offering multiple layers of security to deliver unparalleled protection against advanced attacks. The award-winning solution utilizes behavioral analysis to stop never-before-seen ransomware and boot-record attacks, making it the most advanced anti-ransomware technology available. Powered by deep learning, Intercept X has the industry’s best malware detection engine, as validated by third party testing authorities.
“CRN’s Tech Innovator Awards honor technology vendors who work tirelessly to craft ground-breaking solutions for end users, matching the speed of the channel’s evolution,” said Bob Skelley, CEO of The Channel Company. “The winners in this year’s award categories deserve congratulations for their success in driving IT innovation forward for solution providers and their customers.”
The Tech Innovator Awards will be featured in the December issue of CRN and can be viewed online at http://www.crn.com/techinnovators.
As we embark on a new year, it’s normal to think about what the future will have in store for us. From a cybersecurity perspective, there are a lot of questions about what’s coming. What are the big technology trends and what risks will they pose?
Will attackers be interested in new technologies like AI and biometrics or will they focus on infiltrating conventional systems in new and innovative ways? What will the attack vectors be? Will traditional attack methods continue to reign supreme or will new approaches emerge?
As we head into a new decade, there’s no doubt that attackers will try to use innovation against us, but determining where they will focus is always a challenge. Here are the top security trends we believe will impact both businesses and consumers in 2020:
1. Drones Open up New Pathway for Intelligence Gathering
To date, the security concern around drones has mostly been focused on the physical damage nefarious actors, including nation states, could perpetrate. In 2020, we could start seeing attackers focus more on what drones know and how that information can be exploited for intelligence gathering, corporate espionage and more.
While it’s true that drones have the potential to do physical damage, the longer-term opportunity for attackers is to use drones as another pathway to steal – and manipulate – sensitive information.Goldman Sachs recently predicted that businesses will spend more than $17B in the next five years on drone functionality. With an emphasis on innovation and development, these devices need to be treated the same as any other IoT device with software that gathers and stores sensitive information that needs to be protected.
Organizations need to consider who has the ability to control the drone’s activities, what information the drone is storing, how access to that information is being managed and monitored and, ultimately who owns responsibility for securing it. The creation of a security framework that mitigates emerging security risks and potential regulatory and compliance challenges can help address these questions.
2. The Butterfly Effect of Ransomware
In the first nine months of 2019, reports indicate there were between 600-700 ransomware attacks on government agencies, healthcare providers and schools in the U.S. alone. Cities and public sector organizations around the world have faced a steady barrage of ransomware attacks with momentum continuing to build heading into 2020. With these attacks aimed at disruption and destabilizing systems, cities and towns, in particular, will need to elevate their approach to cyber resiliency.
The constant bombardment will have a butterfly effect that’s impact will reach far beyond what we’ve seen to date. These effects will include:
- Attacker Innovation Shifts to the Cloud: The absence of spectacular ransomware attacks like Petya doesn’t mean attackers have stopped investing in malware. They’re just shifting their focus. In many ways attackers subscribe to the “if it ain’t broke don’t fix it” philosophy. The malware families that have been around for years still work and are effective for many reasons – mostly because many organizations still neglect to adhere to basic patching practices.
That said, attackers keep looking for new ways to monetize their assaults. If they’ve got malware that is steadily performing in Windows environments, what’s the next target? Attackers want access to a greater diversity of systems, including cloud environments and containers. Coming up, we’ll begin to see innovation in ransomware that focuses more on Linux to take broader advantage of digital transformation trends.
- Cyber Insurance Gold Rush Fuels Ransomware Attacks: Despite government warnings not to pay the ransom in ransomware attacks, more organizations are turning to cyber insurance to protect their assets and uptime. We expect to see a significant increase in the number of entities buying cyber insurance, making it one of the fastest growing markets related to cyber security. In fact, cyber insurance is projected to be a $7 billion market in the U.S. alone. However, this investment in “protection” is having a contrary effect – and will drive even greater waves of attacks.
Attackers will target organizations with cyber insurance because those organizations are more likely to pay. Insurance companies weighing the cost benefits of a payout will often choose to pay if the cost of the ransom is less than the cost of the downtime needed to rebuild a network. Ultimately, this gold rush will benefit attackers – tilting the power in their direction, fueling resources and spurring the need for policy changes and disruption across the insurance industry.
3. Election Security: Cyber Attacks as a Disenfranchisement Mechanism
Election security is a hot topic for democracies everywhere. While much of the discussion tends to focus on disinformation campaigns, including the use of deepfake technology to influence opinion, attacks will evolve to disrupt more than just the media.
It’s important to consider the broader effect of disruption and disenfranchisement beyond ballot box tampering. Attackers have repeatedly demonstrated their ability to cause disruption. Their impact on democracies could come in many – even seemingly disconnected – forms.
Stalling major transportation systems – like buses and trains – in major metropolitan areas could keep citizens from safely getting to the polls. A sequence of such attacks targeting core infrastructure – halting transportation, shutting down the electrical grid or launching an attack on voter registration databases – could have a domino effect that negatively impacts the voting system’s ability to operate consistently with trust and reliability.
4. Biometrics Create a False Sense of Security in the Enterprise
With biometric authentication becoming increasingly popular, we’ll begin to see a level of unfounded complacency when it comes to security. While it’s true that biometric authentication is more secure than traditional, key-based authentication methods, attackers typically aren’t after fingerprints, facial data or retinal scans. Today, they want the access that lies behind secure authentication methods.
So, while biometric authentication is a very good way to authenticate a user to a device, organizations must be aware that every time that happens, that biometric data must be encrypted and the assets behind the authentication are kept secure.
Even more importantly, the network authentication token that’s generated must be protected. That token, if compromised by attackers, can allow them to blaze a trail across the network, potentially gaining administrative access and privileged credentials to accomplish their goals – all while masquerading as a legitimate, authenticated employee.
Hot on the heels of the Intercept X for Mobile announcement, we’re delighted to share news of excellent 3rd party test results.
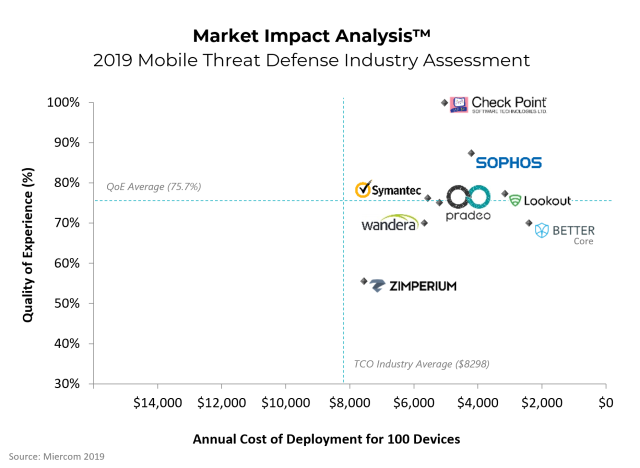
Sophos was rated a top performer in Miercom’s Mobile Threat Defense (MTD) Industry Assessment.
Independent test organization Miercom conducted a study into leading mobile security solutions, measuring protection capabilities and cost of ownership. Sophos aced both categories, demonstrating superb protection against zero-day malware and advanced attacks.
Miercom CEO Robert Smithers said of the product:
“Sophos Mobile proved superior efficacy and a QoE (Quality of Experience) score of 87 percent, 12 percent higher than other products evaluated. This score reflects its ability to detect malware, network threats and device vulnerabilities, while providing appropriate and easy to use interfaces for immediate visibility, control and remediation. Considering it is one of the most affordable solutions for MTD products, Sophos provides an impressive defense that will protect enterprise BYOD networks”.
Mobile devices are sometimes overlooked as an attack surface, but they remain a critical threat vector. Along with the risk of malicious apps, data stored on devices can be compromised through phishing emails or man-in-the-middle network attacks.
Intercept X for Mobile provides powerful device, app and network security. Managed through Sophos Central, you can protect Android and iOS devices right alongside your Windows and macOS clients. Find out more, and sign up for a free trial.
For more details look at Miercom’s full Mobile Threat Defense Industry Assessment.
We’re excited to announce that Sophos Mobile Security will become Sophos Intercept X for Mobile at the end of October. Featuring the industry-leading deep learning technology that already powers Intercept X on desktops and servers, the new Intercept X for Mobile will also sport a brand new interface designed for ease of use and accessibility.
Sophos Intercept X for Mobile will be released together with the upcoming Sophos Mobile 9.5.
How do I get it?
Sophos Intercept X for Mobile is available in the Sophos Mobile Advanced as well as the Central Mobile Security licenses. Existing customers with Sophos Mobile Security do not have to do anything as they will receive the new product as part of their current license.
When will it be available?
Sophos Mobile 9.5 will be available to on-premises customers end of October. The apps installed on mobile devices will also be updated at this time, meaning existing users will see Sophos Mobile Security change to Sophos Intercept X for Mobile. Availability in Sophos Central is planned for early December.

Version 9.5 brings a ton of other great new functionality, such as Chromebook security, management improvements, and advanced reporting. Look out for more information soon!
Intercept X for Mobile (formerly Sophos Mobile Security) – Both updated apps are live!
“Where do I start?” is one of the most common questions we get asked about endpoint detection and response (EDR).
The newly introduced Threat Indicators feature for Sophos EDR answers that question. Threat Indicators makes use of deep learning technology to automatically provide prioritized lists of the most suspicious items across an organization’s endpoints and servers.
Suspicious items are graded from high to low priority. These gradings include details such as file name, SHA 256 hash, the number of devices that have seen the file and if the file has already run, so it’s easy to understand where to begin, even for staff who aren’t cybersecurity specialists.
SophosLabs curated threat intelligence and deep learning analysis gives you the information you need to understand the properties of a suspect file and quickly decide what action to take.
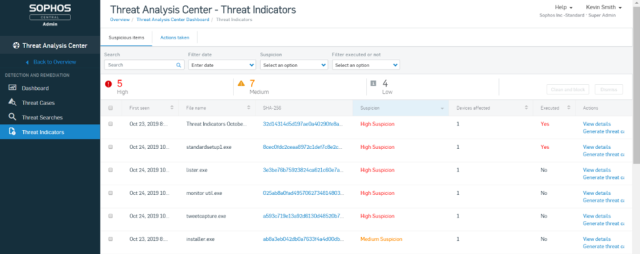
Threat Indicators is available now to all customers that have Intercept X Advanced with EDR or Intercept X Advanced for Server with EDR.
Learn more about EDR and try it out for yourself.
For many organizations implementing privileged access management (PAM) has become high on the priority list – and for good reason. Privileged access is the route to an organization’s most valuable information and assets and protecting them is paramount.
However, many organizations lack visibility into where privileged accounts, credentials and secrets exist. The privilege-related attack surface is often much broader than anticipated. So before you get started with any PAM deployment, there’s one big question you need to answer: How Do You Prioritize Risk?
Here are a few steps that can help:
1. Identify all privileged accounts and credentials. Depending on how many IT assets (systems, databases, applications, SaaS, cloud providers and DevOps tools) you have, there may be tens, hundreds, thousands, or even hundreds of thousands of privileged credentials and secrets across your environment. How can you protect what you don’t even know you have?
The first step to prioritizing risk is to scan and identify all of the privileged accounts and credentials (passwords, SSH keys, passwords hashes, AWS access keys and more) in your environment—on-premises, in the cloud, at the endpoint and across DevOps processes—to understand the scope of potential exposure.
2. Classify types of privileged access by risk. During or after the inventory process, you need to determine a method to evaluate risk. Since you cannot fix everything at once, it’s best to take a risk-based approach, tackling the riskiest areas first and then expanding to new areas over time. Some examples of risk-based prioritization may include identifying:
- Your organization’s most critical systems (using risk classification system or risk-rating mechanisms)
- Systems that contain data that needs to be secured due to regulatory requirements
- Systems with intellectual property or customer data
- Known vulnerable systems (if issues have already been identified from audits, penetration tests or Red Team exercises)
Most organizations start by identifying a small set of accounts that are relatively easy to pinpoint and present high risk and then conduct a Sprint to implement critical privileged access controls in a short period of time (i.e., 30 days). Then, over time, the organization expands coverage to new phases, adding controls to more accounts.
3. Protect the riskiest accounts first to avoid network takeover attacks. In most cases, organizations focus initial efforts on securing tier0 and tier1 critical assets, such as domain administrator accounts and administrator accounts with access to large numbers of machines, particularly servers, as well as application accounts that use domain administrator privileges.
Because cyber attacks that reach the domain controller level can lead to a hostile takeover of network and assets, attackers are starting to apply this approach to new environments, targeting cloud consoles and orchestration tools. Attackers who gain this level of privileged access can control any server, controller, endpoint or piece of data, anywhere on a network.
Regardless of environment, all privileged access to tier0 and tier1 assets should be isolated, all admin credentials should be placed and rotated in a digital vault protected with multi-factor authentication (MFA) and access should be continuously monitored. You should also ensure that there are no hash residuals by design and you are able to detect and block in-progress attacks on domain controllers.
4. Control and secure your infrastructure accounts. Next, many organizations turn their attention to securing and managing the powerful default infrastructure accounts that exist on-premises and in cloud and DevOps environments. Once attackers get their hands on these accounts, they can take ownership of the entire technology stack by compromising a single, unprotected infrastructure account with a default and unchanged password. The same credentials can be used to access similar assets.
Work toward managing 100 percent of these accounts using secure processes and a PAM solution that consistently and securely manages these accounts. All well-known infrastructure accounts should be vaulted and privileged sessions should be isolated and recorded to minimize risk.
5. Limit lateral movement by protecting privilege at the endpoint. Every single workstation in an organization contains privilege by default. Built-in admin accounts allow IT to fix issues locally, but create a massive security gap that attackers target and exploit. Attackers can exploit these risky systems by getting in and then jumping laterally from workstation to workstation until they reach what they are looking for.
It’s important to implement least privilege and just-in-time elevation and access and also remove local administrative rights from workstations. Without strong endpoint security, attackers can easily move laterally into—and around—the network.
6. Protect credentials for third-party applications. For systems to work together, they have to be able to access one another. That’s why the number of machines and applications that require privileged access vastly outnumber people in most organizations today. These non-human entities are difficult to monitor, keep track of or even identify.
Plus commercial off-the-shelf (COTS) apps typically require access to various parts of the network, which attackers can exploit. Remember—you are only as strong as your weakest link.
All privileged accounts used by third-party applications should be centrally stored, managed and rotated in a digital vault. Additionally, all hard-coded credentials should be removed from COTS applications to minimize risk.
7. Manage *NIX SSH Keys. SSH keys are pure gold to a hacker or malicious insider, as they can use unmanaged SSH keys to log in with root access and take over the *NIX (Linux and Unix systems) technology stack. Unix and Linux systems house some of an enterprise’s most sensitive assets and Linux is a commonly deployed operating system in cloud environments. Yet individual privileged accounts and credentials—including SSH keys—used to gain root privileges are often overlooked by security teams.
8. Manage DevOps Secrets in the Cloud and On-Premises. For organizations embracing DevOps technologies, it’s important to dedicate a phase to securing (and then continuously managing) the credentials and secrets used by DevOps tools (i.e., Ansible, Jenkins and Docker) and Platform as a Service (PaaS) solutions (i.e., OpenShift and Pivotal Cloud Foundry).
Make sure these credentials and secrets can be retrieved on the fly and are automatically rotated and managed. This essentially means that your code should be capable of retrieving the necessary privileged credentials from a PAM solution instead of having them hardcoded into an application. Policies for rotating secrets also greatly reduce the risk of secrets becoming compromised.
9. Secure SaaS Admins and Privileged Business Users. Too often, Software as a Service (SaaS) and privileged business users can be forgotten in prioritization efforts. Yet, cyber criminals will steal credentials used by SaaS administrators and privileged business users to get high-level and stealthy access to sensitive systems.
Examples of business critical SaaS applications can be anything from Customer Relationship Management (CRM) software to applications used by the finance, HR and marketing teams. Privileged business users with access to these types of applications can perform very sensitive actions, such as downloading and deleting sensitive data. To prevent this kind of attack, isolate all access to shared IDs and require MFA. Also, monitor and record the sessions of SaaS admins and privileged business users.
While there is no one-size-fits-all approach to security, implementing these steps can help your organization achieve greater risk reduction in less time and satisfy security and regulatory objectives with fewer internal resources.
To learn more, read our eBook, Privileged Access Security for Dummies.
Who’s in charge of security in the public cloud?
It may sound like an odd question, but when working with a cloud provider such as Amazon Web Services (AWS), Microsoft Azure or Google Cloud Platform, it’s important to understand that security is a shared responsibility.
Public cloud providers offer customers a great deal of flexibility in how they build their cloud environments. The consequence of all this flexibility, however, is that providers don’t offer complete protection for virtual networks, virtual machines or data that’s in the cloud.
That shared responsibility model means cloud providers ensure security of the cloud, while the organization (the cloud provider’s customer, i.e. you) is responsible for anything run in the cloud. Now, admins don’t always know what the cloud provider takes care of, and the security controls they themselves must apply. This, as you can imagine, leads to exposed data, file, database and hard drive snapshots.
You might have heard of S3 bucket breaches – of which there have been many! But, this article series aims to break down the other big security-breach risks and how to protect against them, starting with the most common of all…
Public Amazon S3 bucket exposure (with a new twist)
You won’t have to look far to find stories of S3-related data breaches caused by misconfiguration, where S3 security settings were left set to “Public.” AWS has even released an update to help customers from running afoul of this, one of the biggest causes of cloud data breaches.
Reading about the thousands of cases out there, you’d be forgiven for thinking that attackers are only after an organization’s sensitive data in these attacks. Unfortunately, you’d be wrong.
In addition to financial and PII data, one of the main uses of cloud storage accounts like Amazon S3 buckets is to host static website content like HTML files, JavaScript and Style Sheets (CSS). Attacks targeting those resources aren’t targeting exposed data. Instead, they look to modify website files maliciously to steal user financial information.
A fork in the (attackers) road
Both attack chains look the same at the start, with attackers scanning the internet for misconfigured S3 buckets using automated S3 scanners. But this is where our attack paths diverge.
In your typical S3 data breach, attackers now list and sync the valuable contents to local disk and access all the data that was misconfigured in “public” mode.
In the case of our data modification attack: once access is gained, attackers look for JavaScript content and modify it to include malicious code. Now, when a user visits the infected website, the malicious JavaScript code loads, logging all credit and debit card details entered to payment forms. This data is then sent to the criminal’s server.
How to identify and prevent S3 bucket Exposure (both kinds)
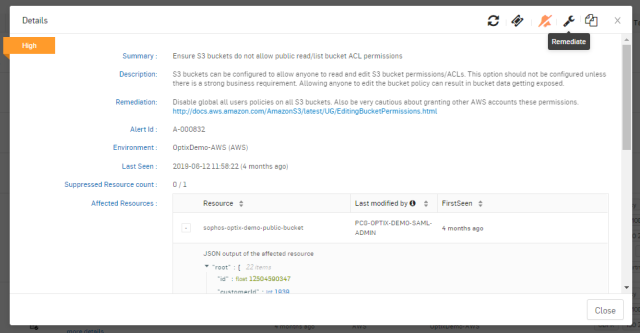
Accidental or malicious changes to the S3 storage configurations that leave organizations exposed are all too common. Cloud Optix makes it simple to quickly identify any publicly accessible data or website files and make them private. It adds an additional level of security to these critical services with Guardrails, ensuring no configuration changes are made without permission.
Cloud Optix alerts you to exposed S3 buckets within minutes, providing contextual alerts that group the affected resources, provide a description of the issue, and remediation steps. These steps include the ability to auto-remediate – updating resource read/write permissions where S3 storage has been left open to the public internet.
Going the extra mile with AI capabilities to detect suspicious user login events, Cloud Optix alerts organizations if the contents of an S3 bucket is modified from an unusual location – suggesting that shared or stolen user credentials are being used remotely.
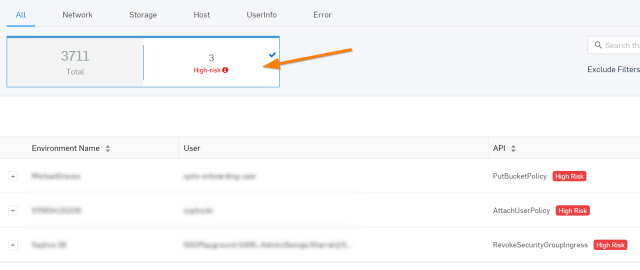
Whatever the end goal of an S3 service breach, these simple steps in Cloud Optix makes it simple to stay one step ahead of attackers.
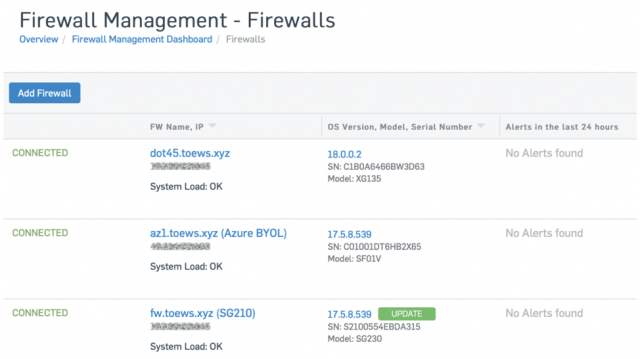
Since XG Firewall joined Sophos Central earlier this year, we’ve been steadily adding features to make day-to-day management of your firewalls even easier. And today, the team is pleased to be kicking off the early access program for Firewall Group Management.
New features in Sophos Central include:
- Management and storage of scheduled backups
- Firmware update management
- Zero-touch deployment of new XG Firewall appliances
- Firewall group management to easily maintain consistency across a group of firewalls
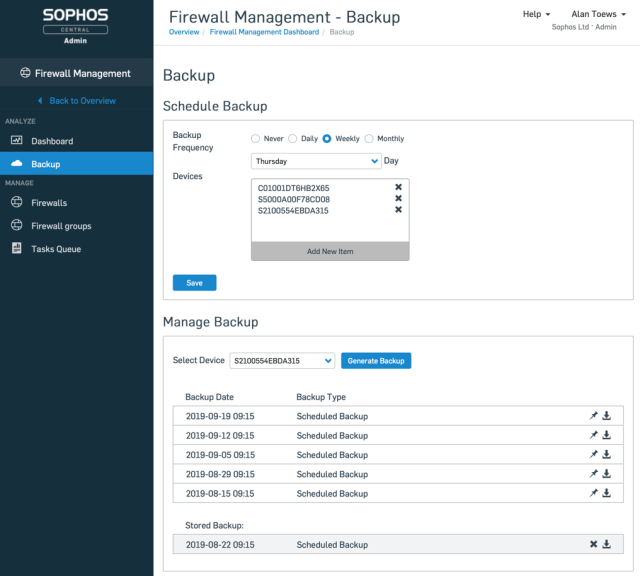
Backup Management
Backups are usually an afterthought, until you really need one.
The Backup Management feature provides peace-of-mind by automating the task of managing scheduled backups. It securely stores them for you in Sophos Central, so when you do need to restore a backup for some reason, it’s super easy.
This feature allows you to:
- Schedule backups daily, weekly or monthly for any or all of your firewalls
- Securely store the last 5 backup files for each firewall
- Permanently store a preferred backup of your choosing
- Download a backup file at any time to restore
Firmware Update Management
To ensure your network is benefitting from the latest features, enhancements, fixes and performance improvements, it’s important to keep your firewalls up to date. But, updating the firmware on several firewalls can take a LOT of time. Well, not anymore!
This feature makes updating your firewall firmware as easy as clicking a button. Once activated, the whole process of downloading the firmware update and rebooting the appliance happens seamlessly, without any further action required on your part.
Zero-Touch Deployment
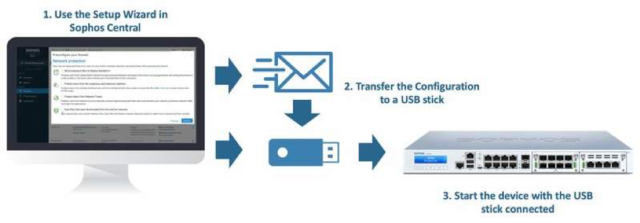
Sometimes you need to setup a firewall at a remote location, and you may not have the expertise on-hand there to fully configure it. This is where the Zero-Touch Deployment feature comes in.
Now you can drop-ship the firewall directly to the remote location and configure it from Sophos Central without having to touch the appliance yourself.
You only need someone there to unbox it, connect it, insert a USB stick with the provisioning configuration file you created, and get it started. You can then fully configure it remotely from Sophos Central.
Zero-touch deployment in three easy steps:
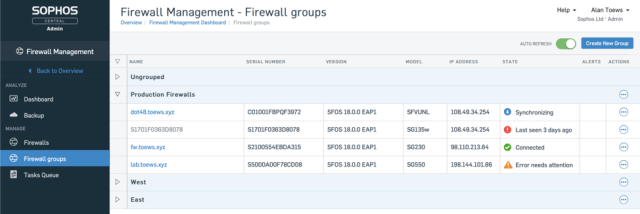
Firewall Group Management
This feature allows you to synchronize policy, objects and other settings across a group of firewalls for consistency. Make a change once, and have it automatically apply to all firewalls in the group.
These new capabilities in Sophos Central are ideal for MSP partners and any customer managing multiple firewalls.
- Simply and easily maintain consistency across a large distributed network
- Save time and effort managing a group of firewalls
- Monitor and access all your firewalls through Sophos Central – at no extra charge.
Getting started with the Early Access Program
You will need to have firewalls running the EAP version of XG Firewall v18 to add them to groups to evaluate the new Firewall Group Management capabilities.
How to join the EAP in 3 easy steps:
- Login to your Sophos Central account
- On the top-right corner, select “Early Access Programs” from the menu under your name
- Look for Firewall Group Membership, and click Join
The new Group Management capabilities will then be under your Firewall Management section of Sophos Central.
Head over to the Community Forums for more information and to provide your valuable feedback.
If you’re planning a migration from Symantec Endpoint Protection (SEP), or at least thinking about it, you’re not alone. More and more organizations are making the switch from Symantec to Sophos for better endpoint protection and easier management.
For those Symantec customers and partners looking to switch we have special offers available.
Sophos continues to invest heavily in Intercept X, our cloud-native next-gen endpoint security that delivers features that can’t be matched by Symantec. Sophos Intercept X consistently gets top marks in third-party tests and analyst reports.
Why Switch? Sophos Intercept X endpoint protection offers better protection and is easier to manage:
- Sophos stops more malware by harnessing the power of deep learning
- Upgrade your ransomware defenses with behavior-based ransomware detection and file roll-back technology
- Block exploit-based and file-less attacks with the industry’s most robust anti-exploit protection
- Manage and protect all your devices in one place with Sophos’ unified, cross-product, cloud-native console
- Synchronize security across products to automate defenses, share intelligence and respond to threats
- Integrate intelligence endpoint detection and response (EDR) with endpoint protection in a single management console and unified agent
- Add expertise with 24/7 threat hunting, detection, and response delivered by an expert team as a fully-managed service
Switching couldn’t be easier. See how simple it is to replace Symantec with Sophos:
Visit Sophos.com/Symantec to learn more about the benefits of switching from Symantec to Sophos.