News
According to data from the “US Bureau of Labor Statistics” some 3 million Americans leave their jobs voluntarily, and according to another study by BambooHR, in a survey of 1000 workers, a third admitted to having spent less than 6 months in a job before changing.
These figures are for the United States, but in Europe the numbers of workers who leave are similar. According to this ADP study, one third of European workers plan to change jobs in the next three years. There is also talk of a war for talent in different sectors such as technology, health services and professional services, in this other Glassdoor report on employment trends for 2020.
Without going into the reasons, advantages or disadvantages of these turnover rates, companies are continually faced with the reality of workers moving to other companies that may or may not be competitors. During the time that workers have been in the company they have had access to private or confidential information to a greater or lesser extent depending on the type of position or company.
Ex-employees often take confidential data and information with them
According to a study conducted by Osterman Reasearch, 69% of the organizations surveyed have suffered a loss of data or knowledge as a result of employee departure: Whether intentional or by mistake, employees may take financial, confidential, customer information, product data, marketing, roadmaps as well as intellectual property to other companies.
There is concern about this type of situation in the management of companies of any size: Employees who go to other companies or to the competition and may carry know-how with them that may lead to loss of competitive advantage. We also find in the press continuously striking cases, but the reality is that it happens every day in different sectors and company sizes.
Sometimes, when a worker leaves the company, they usually see nothing wrong with taking with them data they have been working with during the time they have been in the company. This is true in any sector and any type of job.
For example, a salesperson may see it as normal to take all of the organization’s customer contact data with them, with email, positions, phone numbers, etc. Or if someone works in the engineering field, they may consider it fair to take information about projects, procedures, quality guides, support, designs, etc. that they have been working on. The same applies to software: source code of the applications they have been working on, documentation, projects, etc.
The most common thing is that the person who takes this information does not have any malicious intention. He simply goes to another position in another company, and to do his job well and meet expectations, he considers that at some point he can use this information from the previous position.
How to prevent ex-employees from carrying documents and sensitive information?
The problem is that a good part of companies face this kind of situation when it is already too late. When the employee has left, and it is difficult to know if the sensitive documentation has already been taken, or it is difficult to prove it.
Beyond ethical issues, this is a reality that many companies face on a daily basis. What can be done to prevent this type of situation? We can find different kinds of approaches:
- Notify employees of ownership of information: This is usually done when a person joins the workforce and is given company guidelines or policies or clauses in the contract. The reality is that this is not always read and over time it is forgotten
- Implementing device control tools: Which prevent copying to USBs, etc. These systems have already become obsolete with the boom of the cloud, access to mobile devices, etc. as the information can be anywhere
- With policies to prevent information leaks through DLP systems, CASB, etc: However, many times employees need to work with the information at home, pass it to unmanaged devices, etc. and it is not always possible to prevent sensitive information from being left out of the control of these types of tools.
- Monitoring user behavior (UEBA tools; User Entity Behaviour Analytics) that indicate if a user is having strange behavior patterns regarding the management of sensitive documentation. Perhaps it can be useful if we detect many downloads the week before leaving the company, but many times the information goes out of the control of the company months before, normally, simply because the workers must use it at home, etc.
These methods or systems are limited and often organizations try to use them when it’s too late and the damage has already been done. However, in extreme situations, there is no choice but to use the legal route with the very high costs that this can entail for the organization.
The most effective solution: Data-centric protection
Information can be anywhere, and if it is of value to the company, we must protect it wherever it is. We can protect this type of information through data-centric protection technologies such as SealPath. How so?
- Keep information secure and under control whether it is within the company or if an employee takes it home to work, to other devices etc.
- Limit what others can do with the documents: View only, view and edit only, but not print or copy and paste, etc.
- Have a complete accessibility control: Who accesses it, when, or if someone is trying to open it without permission
- Be able to block access to information in real time even if it is no longer in our hands and is on other computers or networks
[ Know More: DOWNLOAD SEALPATH DATASHEET ]
Protect your sensitive information now, and without waiting for someone to leave and take valuable company data with them. Contact SealPath and we will show you how we can help.
Structure… it is something we humans need in our life to function and survive. We rely on routines and structure to bring an element of predictability to our lives, which in turn makes us feel safe. I think it is fairly safe to say that the situations that have evolved quickly around us in the last few weeks due to the effects of Covid-19 has rocked a lot of the structure in people’s day-to-day lives. For most organisations, these changes in structure have seen the majority of their workforce shifting from office-based working to remote, home working.
For many users, this is a big change, and organisations have been working hard to prepare their users as best they can to provide as much structure as they can amidst these current changes. However, the one thing that organisations cannot afford to risk here is the structure when protecting their data.
Structure is ever more important when dealing with remote users, especially when it has been enforced rather than a choice made by the user. Moving to a home environment means we can lose a lot of the structure provided to us in an office. Away from the common working practices and thought processes of an office environment, remote working factors in more challenges, and it means we may lose sight of the things that are normal to us or are taken for granted in in day-to-day work life. For example, users may face unfamiliar distractions, and be challenged by different focuses and mindsets. Working all these factors in, remote working is a different beast to the safety, and structure, of the office.
Therefore, we may find users are occasionally distracted from performing tasks as they usually would, and security may not be the top of their agenda. Organisations need to make sure they are providing users with the tools to ensure that guards are not being let down simply because of a location and focal change – in essence sticking to the same standards and associated structure that would be provided in the office environment.
Whether working at home or in the office, a structured data protection policy, using solutions such as data classification and DLP, reinforces the need to control how data is managed. Using these tools, employees are reminded and empowered to apply security policy through the hands on classification of all documents and emails as they are created. Documents and data are protected, security policy is embraced and corporate compliance standards are met.
Boldon James Classifier gives your employees structure to data protection. The process begins by setting a classification policy in line with the business requirements, and every new document created must be classified in line with that policy, a structure by which they can follow easily. It takes the pressure off decision making for the user, as they can follow the correct path using customised prompts in order to best classify the document as required. It may seem a trivial step to providing structure for your employees, but these routines allow users to feel safe that they are doing the right thing in protecting sensitive data, giving them one less thing to worry about.
With your users empowered in this way, they are less likely to make mistakes, and organisations know that no matter where their users are, they can continue to ensure sensitive data is being protected in line with regulatory compliance, meaning you can remain safe, compliant and in control.
A new ransomware variant dubbed “ColdLock” has emerged in Taiwan where it’s having a devastating effect on impacted organizations.
Fortunately, Sophos Intercept X gives the cold shoulder to ColdLock, blocking the attack before it can hold you hostage.
Stop ColdLock with Intercept X
ColdLock is a file-less attack. It runs from a PowerShell script where the ransomware code is directly loaded into memory and then executed, all without writing an executable file to the disk.
Intercept X is packed with technologies that protect your organization from ColdLock and other ransomware variants:
- Exploit protection stops the techniques used in file-less, malware-less, and exploit-based attacks.
- CryptoGuard technology stops the unauthorized encryption of files by ransomware, rolling any impacted files back to their original state.
- The deep learning engine uses cutting-edge machine learning to identify and block never-before-seen ransomware before it executes.
- Credential Theft stops privilege escalation, preventing hackers from moving round your system
Plus, the built-in EDR tools give you detailed insight into what happened, so you can see where the threat got in, what it touched, and when it was blocked.
See Intercept X in action
Try out the demo!
Log in to our fully populated demo environment to try Intercept X for yourself. No obligation, no waiting, no set up. Just a ready-to-go demo.
Stories of organizations crippled by ransomware regularly dominate the IT news headlines, and accounts of six- and seven-figure ransom demands are commonplace. But, do the news stories tell the full story?
To understand the reality behind the headlines, Sophos commissioned an independent survey of 5,000 IT managers across 26 countries. The findings provide brand new insight into what actually happens once ransomware hits. Be prepared to be surprised.
The 2020 ransomware reality
The survey provides fresh new insight into the experiences of organizations hit by ransomware, including:
- Almost three quarters of ransomware attacks result in the data being encrypted.
51% of organizations were hit by ransomware in the last year. The criminals succeeded in encrypting the data in 73% of these attacks. - 26% of victims whose data was encrypted got their data back by paying the ransom.
A further 1% paid the ransom but didn’t get their data back. Overall, 95% of organizations that paid the ransom had their data restored. - 94% of organizations whose data was encrypted got it back.
More than twice as many got it back via backups (56%) than by paying the ransom (26%). - Paying the ransom doubles the cost of dealing with a ransomware attack.
The average cost to rectify the impacts of the most recent ransomware attack (considering downtime, people time, device cost, network cost, lost opportunity, ransom paid etc.) is US$732,520 for organizations that don’t pay the ransom, rising to US$1,448,458 for organizations that do pay. - Despite the headlines, the public sector is less affected by ransomware than the private.
45% of public sector organizations were hit by ransomware last year, compared to a global average of 51%, and a high of 60% in the media, leisure, and entertainment industries. - One in five organizations has a major hole in their cybersecurity insurance.
84% of respondents have cybersecurity insurance, but only 64% have insurance that covers ransomware. - Cybersecurity insurance pays the ransom.
For those organizations that have insurance against ransomware, 94% of the time when the ransom is paid to get the data back, it’s the insurance company that pays. - Most successful ransomware attacks include data in the public cloud.
59% of attacks where the data was encrypted involved data in the public cloud. While it’s likely that respondents took a broad interpretation of public cloud, including cloud-based services such as Google Drive and Dropbox and cloud backup such as Veeam, it’s clear that cybercriminals are targeting data wherever it stored.
For the details behind these headlines, read The State of Ransomware 2020 report.
Sophos Intercept X: Protection against ransomware
Ransomware actors combine sophisticated attack techniques with hands-on hacking. Sophos Intercept X endpoint protection gives you the advanced protection technologies you need to disrupt the whole attack chain, including:
- Encryption rollback. CryptoGuard technology blocks the unauthorized encryption of files and rolls them back to their safe state in seconds.
- Exploit protection. Deny attackers by blocking the exploits and techniques used to distribute malware, steal credentials, and escape detection.
- AI-powered threat protection. Artificial intelligence detects both known and unknown malware without relying on signatures
Start an instant online demo to see how Intercept X works in a full environment. You’ll be up and running in less than a minute.
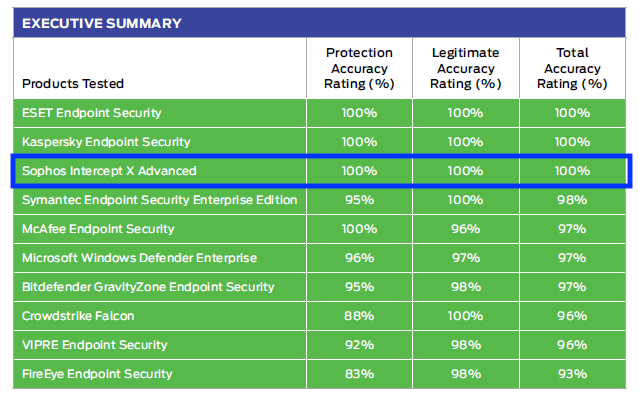
We are thrilled to announce that Intercept X received a 100% total accuracy rating in the enterprise, SMB, and consumer protection tests by SE Labs.
Whether you are protecting your employees at work, or them and their families at home, you will get outstanding protection with Intercept X technology.
The world’s best endpoint protection
Intercept X is the strongest endpoint security on the market, delivering more advanced protection in one solution than anything else out there.
Deep learning AI excels at detecting and neutralizing threats that have never been seen before. Anti-ransomware protection blocks malicious encryption processes and returns affected files to safe, unencrypted states. Advanced defenses against fileless, memory-based attacks keep your organization safe against the latest obfuscated, script-based threats.
Intercept X also includes options for Endpoint Detection and Response (EDR), so you can perform detailed threat hunting and IT security operations hygiene across your endpoints and servers, and a managed service (MTR) that gives you access to a team of Sophos cybersecurity specialists that will hunt threats and take appropriate action on your behalf.
Constant innovation
Our team of cybersecurity experts are constantly enhancing the powerful features in Intercept X. This year alone we’ve incorporated:
- AMSI protection – enhanced protection against fileless attacks, such as obfuscated PowerShell scripts
- Intrusion Prevention System – protects devices against network-based attacks (currently in early access)
- EFSGuard, CTFGuard, and more
Try Intercept X for free
Testing the powerful features in Intercept X couldn’t be more straightforward. Take a free 30 day trial, or if you’d like to learn more head over to Sophos.com.
For a limited time, Sophos customers can add Sophos Home edition at no addition cost.
To view the detailed results from SE Labs: Enterprise | SMB | Consumer
Αυτό το τριήμερο πρόγραμμα εκπαίδευσης σχεδιάστηκε και προορίζεται για έμπειρους τεχνικούς που θέλουν να εγκαθιστούν, αναπτύσσουν, διαμορφώνουν και να υποστηρίζουν το XG Firewall σε παραγωγικά περιβάλλοντα και είναι το αποτέλεσμα βαθιάς μελέτης πάνω στο τείχος προστασίας επόμενης γενιάς της Sophos.
Το πρόγραμμα αποτελείται από παρουσιάσεις και πρακτικές ασκήσεις εργαστηρίων για την ενίσχυση του διδακτικού περιεχομένου. Λόγω της φύσης της παράδοσης και της ποικίλης εμπειρίας των εκπαιδευομένων, ενθαρρύνεται η ανοικτή συζήτηση κατά τη διάρκεια της εκπαίδευσης/ κατάρτισης.
Sophos XG Architect Training (Τρίτη 16 Ιουνίου 2020– Πέμπτη 18 Ιουνίου 2020)
(3 days Training)
Προαπαιτούμενα
XG Firewall _ Certified Engineer course and delta modules up to version 18.0
Συνιστώμενες γνώσεις
- Knowledge of networking to a CompTIA N+ level
- Knowledge of IT security to a CompTIA S+ level
- Experience configuring network security devices
- Be able to troubleshoot and resolve issues in Windows networked environments
- Experience configuring and administering Linux/UNIX systems
Περιεχόμενο της εκπαίδευσης
- Module 1: Deployment
- Module 2: Base Firewall
- Module 3: Network Protection
- Module 4: Synchronized security
- Module 5: Web server Protection
- Module 6: Site to site connections
- Module 7: Authentications
- Module 8: Web Protection
- Module 9: Wireless
- Module 10: Remote Access
- Module 11: High Availability
- Module 12: Public Cloud
Certification
+ exam: Sophos XG Architect
Διάρκεια: 3 ημέρες
Πρόγραμμα
Εκπαιδευτής: Μιχάλης Ελευθέρογλου
Ημέρα 1η 16 Ιουνίου 2020
9:30-10:45 Module 1: Module 1: Deployment and Lab
- Recall important information from Engineer courses
- Deployment modes supported by the XG Firewall
- Understand a range of scenarios where each deployment mode would commonly be used
- Use built-in tools to troubleshoot issues
- Labs
10:45-11:00 Διάλειμμα
11:00-13:00 Module 2: Base Firewall
- Explain how the XG firewal can be accessed
- Understand the types fo interfaces that can be created
- Understand the benefits of Fast Path Technology
- Configure routing per firewall rule
- Understand best practice for ordering firewall rules
- Explain what Local NAT policy is and known how to configure it.
13:00-14:00 Διάλειμμα
14:00-16:00 Labs
- Activate the Sophos XG Firewalls
- Post installation Configuration
- Bridge interfaces
- Create a NAT rule to load balance access to servers
- Create a local NAT policy
- Configure routing using multiple WAN links
- Configure policy-based routing for an MPLS scenario
- Install Sophos Central
16:00-16:15 Διάλειμμα
16:15-17:15 Module 3: Network Protection and Lab
- Explain what IPS is and how traffic can be offloaded to Fastpath
- Demonstrate how to optimize workload y configuring IPS policies
- Examine advanced Intrusion Prevention and optimize policies
- Configure advanced DOS Protection rules
- Demonstrate how the strict policy can be used to protect networks
- Labs- Create Advanced DoS Rules
Ημέρα 2η Τετάρτη 17 Ιουνίου 2020
9:30-11:00: Module 4: Synchronized Security and Labs
- Explain how Security Heartbeat works
- Configure Synchronized Security
- Deploy Synchronized Security in discover and inline modes
- Understand the advantages and disadvantages of deploying
- Synchronizes Security in different scenarios
- Labs
- Configure source-Based Security
- Hearteat firewall rules
- Destination based Security Heartbeat
- Missing Security Heartbeat
- Lateral Movement Protection
11:00-11:15 Διάλειμμα
11:15-13:45 Module 5 Webserver Protection and Labs
- Explain how Websever Protection works
- Describe protection features for a web application
- Configure Web Server authentication
- Publish a web service using the Web Application Firewall
- Use the preconfigured templates to configure Web Server Protection for common purposes
- Configure SlowHTTP protection
- Labs (Web Application Firewall)
- Labs (Load balancing with Web Server Protection)
- Labs (Web Server Authentication and path-specific routing)
13:45-14:45 Διάλειμμα και Γεύμα
14:45-17:45 Module 6: Site to site connections and Labs
- Configure and deploy site to site VPNs in a wide range of environment
- Implement IPsec NATing and failover
- Check and modify route precedence
- Create RED tunnels between XG firewalls
- Understand when to use RED
- Labs ( Create an IPsec site to site VPN
- Labs ( Configure VPN network NATing )
- Labs (Configure VPN failover)
- Labs (Enable RED on the XG firewall)
- Labs (Create a RED tunnel between two XG Firewalls
- Labs (Configure routing for the RED tunnel)
- Labs (Configure route-based VPN)
Ημέρα 3η Πέμπτη 18 Ιουνίου 2020
9:00-10:00 Module 7: Authentications and Labs
- Demonstrate how to configure and use RADIUS accounting
- Deploy STAS in large and complex environment
- Configure SATC and STAS together
- Configure Secure LDAP and identify the different secure connections available
- Labs (configure an Active Directory Authentication server)
- Labs (configure single sing-on using STAS
- Labs (Authenticate users over a site to site VPN)
10:00-11:15 Module 8: Web Protection
- Choose the most appropriate type for web protection in different deployment scenarios
- Enable web filtering using the DPI engine or legacy web proxy
- Configure TLS inspection using the DLP engine or legacy web proxy
- Labs (Install the SSL CA certificate)
- Labs (Configure TLS inspection rules)
- Labs (Create a custom web policy for users)
11:15-11:30 Διάλειμμα
11:30-12:15 Module 9: Wireless
- Explain how Sophos Access Points are deployed and identify some common issues
- Configure RADIUS authentication
- Configure a mesh network
12:15-13:05 Module 10: Remote Access
- Configure Sophos Connect and manage the configuration using Sophos Connect Admin
- Configure an IPsec remote access VPN
- Configure an L2TP remote access VPN for mobile devices
- Labs (Sophos Connect)
13:05-14:25 Module 11: High Availability
- Explain what HA is and how it operates
- Demonstrate how to configure HA and explain the difference between quick and manual configuration
- List the prerequisites for high availability
- Perform troubleshooting steps andc heck the logs to ensure that HA is set up correctly.
- Explain the packet flow in high availability
- Demonstrate how to disable HA
- Labs (Create an Active-Passive cluster)
- Labs (Disable High Availability)
14:25-15:05 Διάλειμμα και Γεύμα
15:05-16-15 Public Cloud and Labs
- Deploy XG firewall in complex network enviroments
- Explain how XG firewall process traffic and use this information to inform the configuration
- Configure advanced networking and protection features
- Deploy XG firewall on public cloud infrastructure
- Labs (Put a service in debug mode to gather logs)
- Labs (Retrieving log files)
- Labs (Troubleshoot an issue from an imported configuration file)
- Labs (Deploy an XG Firewall on Azure (simulation)
16:15 (Εξετάσεις)
This three-day training program was designed and intended for experienced technical professionals who want to install, configure and support the XG Firewall in production environments and is the result of an in-depth study on the next generation firewall of Sophos. The program consists of presentations and practical workshops for the enhancement of teaching content. Due to the nature of the traditions and the varied experience of the trainees, open discussion is encouraged during the training.
Sophos XG Architect Training (Tuesday 16 June 2020– Thursday 18 June 2020)
(3 days Training)
Requirement
XG Firewall _ Certified Engineer course and delta modules up to version 18.0
Recommended Knowledge
- Knowledge of networking to a CompTIA N+ level
- Knowledge of IT security to a CompTIA S+ level
- Experience configuring network security devices
- Be able to troubleshoot and resolve issues in Windows networked environments
- Experience configuring and administering Linux/UNIX systems
Content
- Module 1: Deployment
- Module 2: Base firewall
- Module 3: Network Protection
- Module 4: Synchronized security
- Module 5: Web server Protection
- Module 6: Site to site connections
- Module 7: Authentications
- Module 8: Web Protection
- Module 9: Wireless
- Module 10: Remote Access
- Module 11: High Availability
- Module 12: Pulic Cloud
Certification
+ exam: Sophos XG Architect
Duration 3 days
Agenda
Trainer: Micheal Eleftheroglou
Day 1 Tuesday 16 June 2020
9:30-10:45 Module 1: Deployment and Lab
- Recall important information from Engineer courses
- Deployment modes supported by the XG Firewall
- Understand a range of scenarios where each deployment mode would commonly be used
- Use built-in tools to troubleshoot issues
- Labs
10:45-11:00 break
11:00-13:00 Module 2: Base Firewall
- Explain how the XG firewal can be accessed
- Understand the types fo interfaces that can be created
- Understand the benefits of Fast Path Technology
- Configure routing per firewall rule
- Understand best practice for ordering firewall rules
- Explain what Local NAT policy is and known how to configure it.
13:00-14:00 Lunch
14:00-16:00 Labs
- Activate the Sophos XG Firewalls
- Post installation Configuration
- Bridge interfaces
- Create a NAT rule to load balance access to servers
- Create a local NAT policy
- Configure routing using multiple WAN links
- Configure policy-based routing for an MPLS scenario
- Install Sophos Central
16:00-16:15 Break
16:15-17:15 Module 3:Network Protection and Lab
- Explain what IPS is and how traffic can be offloaded to Fastpath
- Demonstrate how to optimize workload y configuring IPS policies
- Examine advanced Intrusion Prevention and optimize policies
- Configure advanced DOS Protection rules
- Demonstrate how the strict policy can be used to protect networks
- Labs- Create Advanced DoS Rules
Day 2 Wednesday 17 June 2020
9:30-11:00 Module 4: Synchronized Security and Labs
- Explain how Security Heartbeat works
- Configure Synchronized Security
- Deploy Synchronized Security in discover and inline modes
- Understand the advantages and disadvantages of deploying
- Synchronizes Security in different scenarios
- Labs
- Configure source-Based Security
- Hearteat firewall rules
- Destination based Security Heartbeat
- Missing Security Heartbeat
- Lateral Movement Protection
11:00-11:15 Break
11:15-13:45 Module 5 Webserver Protection and Labs
- Explain how Websever Protection works
- Describe protection features for a web application
- Configure Web Server authentication
- Publish a web service using the Web Application Firewall
- Use the preconfigured templates to configure Web Server Protection for common purposes
- Configure SlowHTTP protection
- Labs (Web Application Firewall)
- Labs (Load balancing with Web Server Protection)
- Labs (Web Server Authentication and path-specific routing)
13:45-14:45 Break and Lunch
14:45-17:45 Module 6: Site to site connections and Labs
- Configure and deploy site to site VPNs in a wide range of environment
- Implement IPsec NATing and failover
- Check and modify route precedence
- Create RED tunnels between XG firewalls
- Understand when to use RED
- Labs ( Create an IPsec site to site VPN
- Labs ( Configure VPN network NATing )
- Labs (Configure VPN failover)
- Labs (Enable RED on the XG firewall)
- Labs (Create a RED tunnel between two XG Firewalls
- Labs (Configure routing for the RED tunnel)
- Labs (Configure route-based VPN)
Day 3 Thursday 18 June 2020
9:00-10:00 Module 7: Authentications and Labs
- Demonstrate how to configure and use RADIUS accounting
- Deploy STAS in large and complex environment
- Configure SATC and STAS together
- Configure Secure LDAP and identify the different secure connections available
- Labs (configure an Active Directory Authentication server)
- Labs (configure single sing-on using STAS
- Labs (Authenticate users over a site to site VPN)
10:00-11:15 Module 8: Web Protection
- Choose the most appropriate type for web protection in different deployment scenarios
- Enable web filtering using the DPI engine or legacy web proxy
- Configure TLS inspection using the DLP engine or legacy web proxy
- Labs (Install the SSL CA certificate)
- Labs (Configure TLS inspection rules)
- Labs (Create a custom web policy for users)
11:15-11:30 Break
11:30-12:15 Module 9: Wireless
- Explain how Sophos Access Points are deployed and identify some common issues
- Configure RADIUS authentication
- Configure a mesh network
12:15-13:05 Module 10:Remote Access
- Configure Sophos Connect and manage the configuration using Sophos Connect Admin
- Configure an IPsec remote access VPN
- Configure an L2TP remote access VPN for mobile devices
- Labs (Sophos Connect)
13:05-14:25 Module 11: High Availability
- Explain what HA is and how it operates
- Demonstrate how to configure HA and explain the difference between quick and manual configuration
- List the prerequisites for high availability
- Perform troubleshooting steps andc heck the logs to ensure that HA is set up correctly.
- Explain the packet flow in high availability
- Demonstrate how to disable HA
- Labs (Create an Active-Passive cluster)
- Labs (Disable High Availability)
14:25-15:05 Break – Lunch
15:05-16-15 Public Cloud and Labs
- Deploy XG firewall in complex network enviroments
- Explain how XG firewall process traffic and use this information to inform the configuration
- Configure advanced networking and protection features
- Deploy XG firewall on public cloud infrastructure
- Labs (Put a service in debug mode to gather logs)
- Labs (Retrieving log files)
- Labs (Troubleshoot an issue from an imported configuration file)
- Labs (Deploy an XG Firewall on Azure (simulation)
16:15 (Exams)
What strange times we are currently living in. With workers who are able to work from home (WFH) being told to do so, and essential key workers (emergency services, the military, essential supplies and utility industries) needing to brave the external environment. I have talked to many folks this week about their experience of WFH and hearing many of their woes. VPNs not able to sustain the volume of connections needed, applications which apparently are not set up for remote connections, through to security policies that are not able to determine which sensitive information should be allowed to be accessed from where.
What I have noticed is that WFH shows we are all human. Children in the background who need entertaining, dogs that need attention and cats that need stroking. All of a sudden we gain a more empathetic relationship with our clients and colleagues, and let’s face it most of us go to work because we need to support our family, whatever shape that may take. I am lucky that my daughter has a senior role in in the Emergency Room and that means with her now having to work full time to support Covid-19 patients, my wife and I get to spend more time with our grandson, and he has enlivened a few of my video conferences and help us all realise what is important in these times.
It is very easy for clients that I talk to, to take the option of do nothing, but once we get through the initial, and important, challenge of getting workers to be able to work remotely, they can start to look at how they can improve that experience. All organisations should consider the security of their data and information; more and more people are starting to understand that pure security based labelling is not sufficient. Restricted or sensitive actually mean nothing to a remote worker. If the system gives me access, then I will use it. Personally I have already received in two days, three files which I am sure the originating organisations did not mean to send to me, because their security policies were one dimensional, and not a business taxonomy.
What do I mean by that? Multiple labels that a business user can understand, Sensitive /HR/Salaries or Internal/ Support/Client Data or even Confidential/ Board Only/Project X/Aggressive Takeover.
So until you start to use day-to-day business language in your classification terms, do not be surprised if your staff get it wrong. Helpfully some of those labels can be automatically applied depending upon the departments, and roles they have, so even less user involvement is needed.
However, let me not finish without saying now is a great time to hold proof of concepts, once your immediate tasks of getting remote workers are all up and running. This will then help you to make decisions which can safeguard your organisation’s information and data in a controlled manner.
Governments are telling us not to panic buy, that there will be a plentiful supply of food and essentials. We need to continue the cycle of money for economies to survive, and support businesses within that ecosystem who need the flow of cash to pay staff. I appreciate not all projects can continue, but a blanket excuse of do nothing could halt the economic cycle. If we do that then nobody should be surprised when we come out of the end of the current crisis that their favoured contractors and suppliers are no longer trading. We owe it to ourselves, families and communities to do unto them which we would like them to do to us. Please keep safe and healthy.
Sophos is extremely pleased to announce the availability of XG Firewall on Amazon Web Services (AWS) public cloud infrastructure.
XG Firewall is now available in the AWS marketplace with two flexible licensing options:
- Pay-as-you-go (PAYG) license – ideal for short-term use
- Bring-your-own license (BYOL) – our conventional multi-year term licenses
AWS customers can take full advantage of the many innovations XG Firewall has to offer, like Synchronized Security with Intercept X for Server, the new Xstream Architecture with high-performance TLS 1.3 inspection, and the latest machine learning threat intelligence and sandboxing protection from ransomware and other advanced threats.
Crucially, it enables customers to manage a multi-cloud security strategy from a single cloud console in Sophos Central; including network security with XG Firewall; cloud workload protection with Intercept X for Server; and cloud security posture management with Cloud Optix.
XG Firewall brings full network security and control to AWS integrated into a single solution:
- Xstream Deep Packet Inspection (DPI)
- Intrusion Prevention System (IPS)
- Web filtering, protection and application control
- AV and AI machine-learning threat protection and sandboxing
- TLS inspection with native support for TLS 1.3
- A full-featured Web Application Firewall
In the coming months we will be extending XG Firewall’s integration into AWS with enhancements like auto-scaling, CloudFormation template support, CloudWatch integration and more.
With XG Firewall now available in AWS as well as Microsoft’s Azure public cloud platform, XG Firewall further extends its industry-leading deployment options with support for any combination of cloud, virtual, software, or XG Series hardware appliances. These options make XG Firewall able to fit any network, both now and in the future.
Learn More about XG Firewall protection for your cloud infrastructure.
We are excited to announce that powerful new Endpoint Detection and Response (EDR) features for Intercept X are now available in early access.
This early access program (EAP) brings pre-built, fully customizable SQL queries for both granular threat hunting and IT health checks and management across your organization’s estate. You can join the EAP now.
Live Discover
Live Discover allows you to examine your data for almost any question you can think of by searching across endpoints and servers with SQL queries.
You can choose from a selection of pre-created queries that can be fully customized to pull the exact information that you need.
IT operations and threat hunting sample questions include:
- Why is a machine slow? Is it pending a reboot?
- Are users running unauthorized browser extensions?
- Have any processes had their registry keys or files modified recently?
- Is remote sharing enabled? What about guest accounts?
- What processes are attempting to make network connections on non-standard ports?
Live Response (coming in May to early access)
This feature gives you the ability to respond with precision. Using a cmdline interface, remotely access devices in order to perform further investigation or take action. For example:
- Reboot a device pending updates
- Terminate suspicious processes
- Browse the file system
- Edit configuration files
- Run scripts and programs
How to join the EAP
The EAP is open to everyone that has Intercept X and Intercept X for Server, even if you don’t currently have EDR.
For full instructions on how to join and additional technical information please head over to the Sophos community. We look forward to hearing your feedback!
Sophos is excited to announce that Sandboxie is now an open source tool.
Sandboxie has long been a favorite sandbox-based isolation tool since its original release over fifteen years ago. Now this technology will live on in the hands of its dedicated users.
We are thrilled to give the code to the community. The Sandboxie tool has been built on many years of highly-skilled developer work and is an example of how to integrate with Windows at a very low level.
The Sandboxie user base represents some of the most passionate, forward thinking, and knowledgeable members of the security community, and we hope this announcement will spawn a fresh wave of ideas and use cases.
For more details, and to download the open source release visit https://www.sandboxie.com/.
Ensuring that your endpoint and server protection is correctly configured is one of the most important things you can do for your organization’s security.
This article will give you some quick tips and links to resources so you can get the most out of your Sophos protection.
Getting started
In Sophos Central policies are used to apply protection settings such as specific exploit preventions, application control, and peripheral control. Policies can apply to endpoints, servers, users or groups depending on how you want to set things up. How to create a policy.
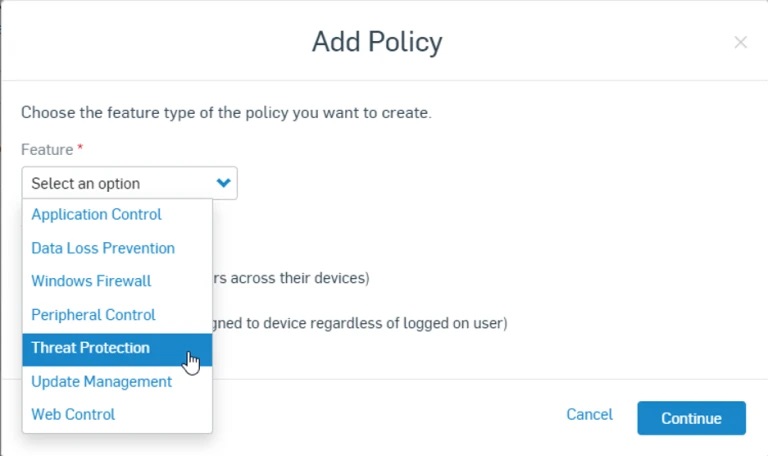
Application Control
Controls which applications should be blocked. For example, uTorrent and Steam games.
Endpoint setup | Server setup
Data Loss Prevention
Stops specific file types or content in a file from being transferred from a device. For example, stop files containing account numbers being sent from a device.
Endpoint setup | Server setup
Windows Firewall
Blocks inbound connections from specific domains or networks. For example, stopping all private networks accessing a device.
Endpoint setup | Server setup
Peripheral Control
Controls what can be plugged into a device. For example, blocking USB sticks and optical drives.
Endpoint setup | Server setup
Threat Protection
Configures protection features. We strongly suggest always using Sophos recommended settings.
Endpoint setup | Server setup
Update Management
Schedules updates to a specific time. For example, setting them after office hours.
Web Control
Stops users downloading risky files or accessing inappropriate websites. For example, block .exe file downloads.
Endpoint setup | Server setup
File Integrity Monitoring (Server only)
Monitors important files and folders for signs of tampering. For example, critical Windows directories or key programs.
How to set one up.
Tamper Protection
Tamper protection stops unauthorized users and types of malware from uninstalling Sophos protection. You should always have it enabled. Learn more.
Do I need to log in and check for alerts?
Users often ask how often they should log in to check for alerts and actions. The good news is that Sophos Central automatically emails admins when there is an event requiring their attention. Here’s how to configure alerts.
Check your security posture with EDR
Endpoint Detection and Response (EDR) is a powerful tool to help you find threats across your network. It’s easy to get started by checking the list of the most suspicious potential threats for investigation in your organization.
We give you curated threat intelligence so you can quickly decide whether a potential threat needs taking care of. Watch the EDR how-to videos.
More information
Intercept X & Central Endpoint Protection support hub
Intercept X for Server and Central Server Protection support hub
|
|
||||||||||||||||||||
Since we began writing last year about the consumer-hostile trend in mobile apps that we’re calling fleeceware, the number of apps we’ve discovered that engage in this practice have only increased. In the first two articles we wrote about fleeceware, we covered various Android apps in the official Play Store charging very high subscriptions for apps of questionable quality or utility.
In this latest round of research, we found more than 30 apps we consider fleeceware in Apple’s official App Store.
Many of these apps charge subscription rates like $30 per month or $9 per week after a 3- or 7-day trial period. If someone kept paying that subscription for a year, it would cost $360 or $468, respectively. For an app.
Like we have seen before, most of these fleeceware apps are image editors, horoscope/fortune telling/palm readers, QR code/barcode scanners, and face filter apps for adding silly tweaks to selfies.
Many of these apps lack any extraordinary features that aren’t already present in many other apps, including truly free apps. It’s debatable that the apps provide “ongoing value to the customer,” as required in Apple’s App Store Review Guidelines for app subscriptions, section 3.1.2(a).
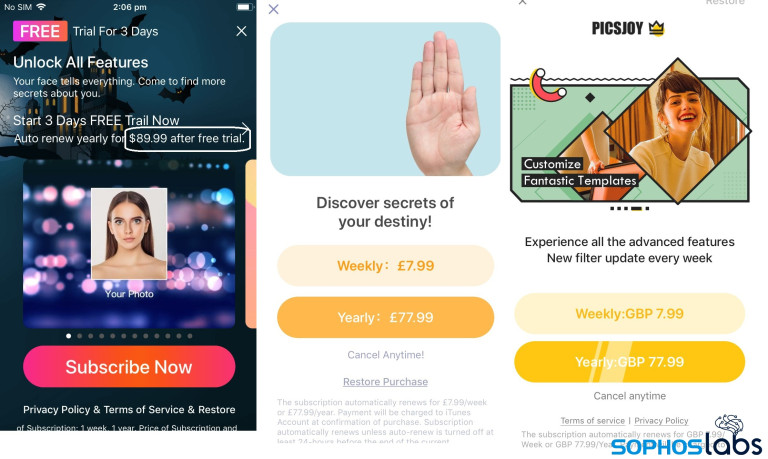

When “free” isn’t really free
Many of the fleeceware apps we see are advertised within the App Store as “free” apps, which puts the apps at odds with section 2.3.2 of the App Store Review Guidelines, which require developers to make sure their “app description, screenshots, and previews clearly indicate whether any featured items, levels, subscriptions, etc. require additional purchases.”
If you think one of these apps is free and install it, the app presents you with a “free trial” notification immediately upon launching the app for the first time. This notification prompts the user to provide payment card details. In some cases, most of the useful features of the app will only be usable if you sign up for the subscription. Some users may sign up to subscribe without reading the fine print, which includes the actual cost of the subscriptions.
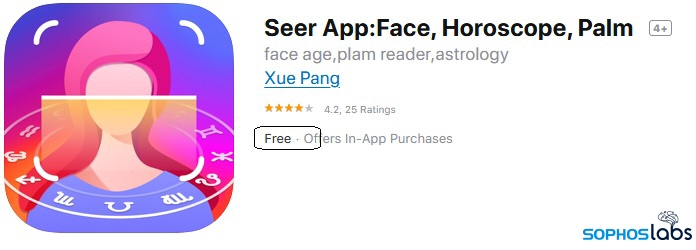
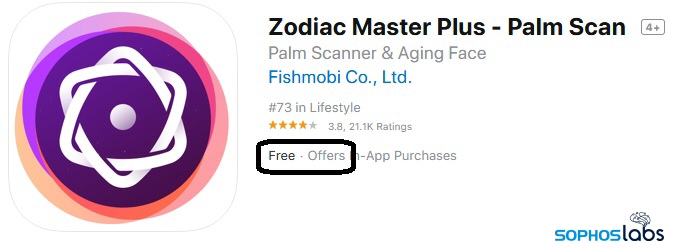
Fleeceware in Top Grossing app charts
While the Apple App Store does not publish the number of downloads for any given app within the app’s listing in the store, the company does keep track of how much money apps make. Many of these fleeceware apps are listed among the top grossing apps, at the time of writing. It’s fair to say these apps are generating plenty of revenue for developers, of which Apple keeps a 30% cut during the first year.
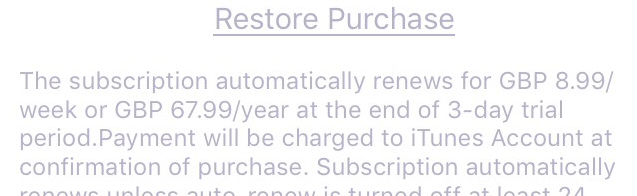 The terms for a Lucky Life subscription displayed in a faint grey text
The terms for a Lucky Life subscription displayed in a faint grey text
Zodiac Master Plus, one of the apps on our list of fleeceware, is listed as the 11th highest revenue-generating app. Another app, named Lucky Life – Future Seer, is earning more revenue than even the extremely popular Britbox, one of the UK’s most popular subscription streaming TV services.

One third party source estimates App Store revenue, which includes all types of purchases, to be $13 billion dollars in 2018, just in the USA.
After one year, Apple gets 15% and the developer’s share increases to 85% of the subscription price.
Advertisements drive more people to fleeceware
If you find yourself wondering why users would even consider installing apps such as these, it’s probably thanks to advertising. These apps are advertised through various popular platforms, including in YouTube videos or on social media platforms like Instagram, TikTok, and even in ads that appear within other apps.
When users visit the app’s page in the App Store app, they’ll find a high number of five-star reviews. While we have no evidence that these are manipulated or artificially inflated reviews, that is another criteria by which the App Store may take action against developers. These advertisements offer a high return on investment, given the high subscription charges.

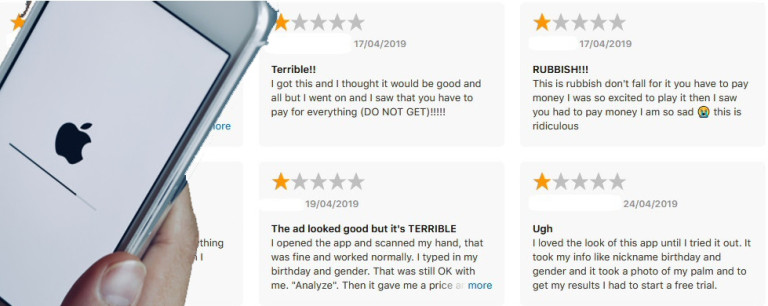
But not all the reviews are upbeat about these products. Here are a few examples of negative user reviews that illustrate how ads attract users to the apps.
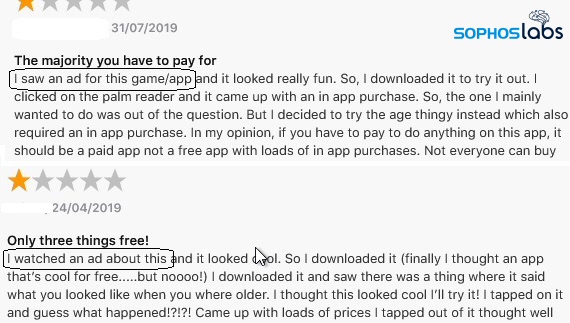 Negative reviews and vulnerable users
Negative reviews and vulnerable users
These apps also have lots of negative, one-star reviews from users complaining about the challenge of canceling subscriptions and getting refunds, with many iPhone and iPad owners wondering aloud why apps that exhibit this type of behavior exist on Apple’s official App Store.
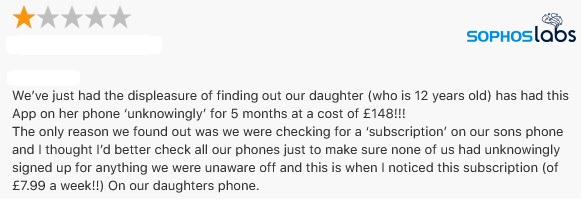
In one instance, one user posted a complaint about being charged £148 (about US$170) over a 5 month period, when his child accidentally subscribed to one of these apps, and he didn’t notice the subscription charges right away.
The negative reviews for some of these products are devastating.
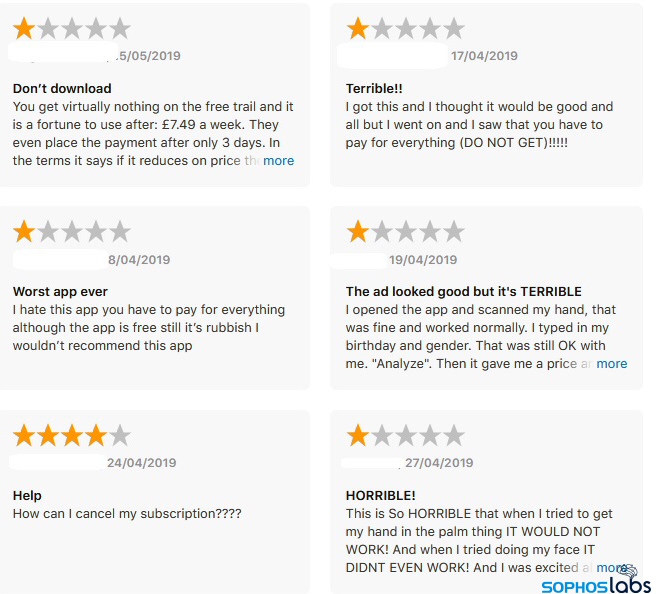
Both iOS and Android face a fleeceware problem
Fleeceware is a problem on both the Android and iOS mobile platforms. The list below is representative of the fleeceware apps we’ve seen at the time of this writing. App publishers also have the ability to introduce new fleeceware apps by releasing new apps with the same subscription policies, or by converting a previously free app into fleeceware by changing the app’s profile in the App Store, though Apple developer policies prohibit this behavior.
Users should remain vigilant and carefully scrutinize the terms for purchasing or “subscribing” to apps promoted through in-app advertisements. If $30 a week seems like a lot to spend on astrology, a barcode reader, or an app that will show you what you’ll look like when you’re 80 years old, find another app.
How to cancel your subscriptions
If you have one of these fleeceware apps and want to change or cancel your subscription, please follow the instructions below
iOS
This is how you can do it on Iphone as described in Apple support page here.
- Open the Settings app.
- Tap your name, then tap Subscriptions.*
- Tap the subscription that you want to manage. Don’t see the subscription that you’re looking for?
- Choose a different subscription option, or tap Cancel Subscription.If you don’t see Cancel Subscription, the subscription is already canceled and won’t renew.
*If you don’t see “Subscriptions” in the Settings app, tap iTunes & App Store instead. Tap your Apple ID (which is usually your email address), then tap View Apple ID. Sign in, scroll down to Subscriptions, then tap Subscriptions.
Android
Instructions for cancelling Android app subscriptions from Google’s Play Store support page:
On your Android phone or tablet, open the Play Store.
- Check if you’re signed in to the correct Google Account.
- Tap the hamburger menu icon
Subscriptions.
- Select the subscription you want to cancel.
- Tap Cancel subscription.
- Follow the instructions.
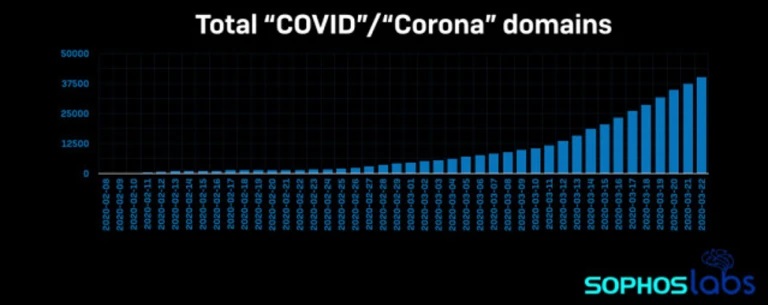
Hackers are busy exploiting coronavirus in their attacks. In recent weeks SophosLabs has seen a surge of COVID- and Corona-related domains registered – while some will be legitimate, it’s a fair bet that the majority are destined for criminal purposes.
Common attack techniques
Phishing attacks using COVID-19 as a lure are the most visible and immediate cybersecurity risk right now. Common tactics include:
Coronavirus news
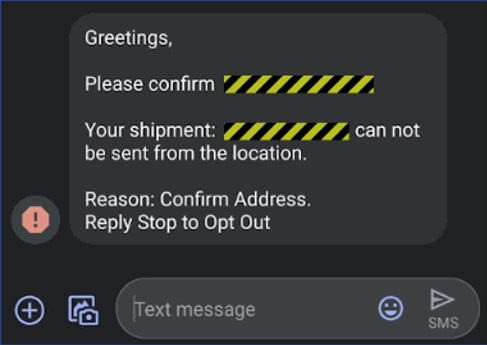
Beware of emails, SMS, and WhatsApp messages from unknown sources with information on coronavirus. Often hackers impersonate legitimate organizations and people to make their messages more believable.
Home delivery scams
With many people waiting on home delivery of essential items, hackers are impersonating delivery services. Their goal: to trick you into clicking malicious links or con you into paying extra ‘delivery’ fees.
 We’re also seeing coronavirus used in other ways, including:
We’re also seeing coronavirus used in other ways, including:
Extortion attempts
Criminals threaten to infect people with coronavirus unless you pay them. Often these threats include a small piece of personal information to make it more believable.

Malicious apps
Purporting to give you useful information on coronavirus, these apps enable the crooks to access all the information on the device – and even hold you to ransom.
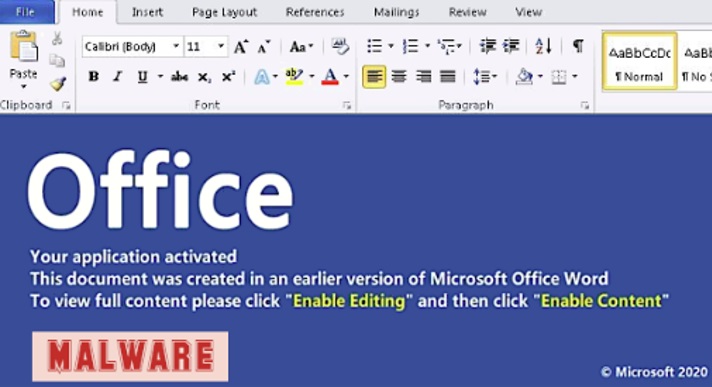
Malicious documents
These documents claim to contain coronavirus-related information. Upon opening them you’re asked to ‘enable editing’ and ‘enable content.’ Doing so installs malicious software onto your computer.
 Practical steps to minimize risk
Practical steps to minimize risk
In the current situation, many people are lowering their guard to phishing attacks and scams. We’re more anxious, more eager for information, and therefore less likely to question something that could be suspect.
With that in mind, here are three practical steps you can take to minimize the risk from coronavirus-related attacks.
Enable Multi-Factor Authentication (MFA)
MFA is a great form of defense against attacks that use a fake login page to trick people into entering their credentials.
Raise awareness of these scams amongst your employees
A simple, but effective, step is to always looks at the actual email address used to send the email, not just the display name. (If you’re on a mobile device click on the display name to reveal the real email address.)
Sophos Phish Threat, our phishing simulation and training tool, is available to everyone for free for 30 days, and now includes a coronavirus phishing template to help train your teams.
Make sure your endpoint and email protection are well-configured
When properly set-up, good protection can catch a phishing attack in multiple ways. You can try our endpoint and email protection for free at any time.
Sophos Cloud Optix has now been certified by the Center for Internet Security (CIS) to accurately assess AWS, Azure and GCP environments based on best practices for secure configuration.
Developed through a unique consensus-based process comprised of cybersecurity professionals and subject matter experts around the world, CIS Benchmarks are recommended as industry-accepted system hardening standards.
The standards are used by organizations in meeting compliance requirements for the Federal Information Security Management Act, PCI, the Health Insurance Portability Accountability Act and other security requirements.
- Amazon Web Services CIS Benchmarks
- Microsoft Azure CIS Benchmarks
- Google Cloud Platform CIS Benchmarks
By certifying Cloud Optix with CIS, Sophos has demonstrated commitment to actively solve the foundational problem of ensuring secure configurations are used throughout AWS, Azure and GCP environments.
Not all certifications are equal
CIS Benchmark Certification is awarded on two profile levels. The aim of the level 1 profile is to lower the attack surface of your organization while keeping machines usable and not hindering business functionality. The level 2 profile is considered “defense in depth” and is intended for environments where security is paramount.
Organizations should investigate whether a vendor offers the level of certification required for their industry, or compliance standard. Sophos has provided evidence that Cloud Optix can accurately report security recommendations in both level 1 and level 2 CIS Benchmark profiles.
This three-day training program was designed and intended for experienced technical professionals who want to install, configure and support the XG Firewall in production environments and is the result of an in-depth study on the next generation firewall of Sophos. The program consists of presentations and practical workshops for the enhancement of teaching content. Due to the nature of the traditions and the varied experience of the trainees, open discussion is encouraged during the training.
Sophos XG Architect Training (Tuesday 28 April 2020– Thursday 30 April 2020)
(3 days Training)
Requirement
XG Firewall _ Certified Engineer course and delta modules up to version 18.0
Recommended Knowledge
- Knowledge of networking to a CompTIA N+ level
- Knowledge of IT security to a CompTIA S+ level
- Experience configuring network security devices
- Be able to troubleshoot and resolve issues in Windows networked environments
- Experience configuring and administering Linux/UNIX systems
Content
- Module 1: Deployment
- Module 2: Base firewall
- Module 3: Network Protection
- Module 4: Synchronized security
- Module 5: Web server Protection
- Module 6: Site to site connections
- Module 7: Authentications
- Module 8: Web Protection
- Module 9: Wireless
- Module 10: Remote Access
- Module 11: High Availability
- Module 12: Pulic Cloud
Certification
+ exam: Sophos XG Architect
Duration 3 days
Agenda
Trainer: Micheal Eleftheroglou
Day 1 Tuesday 28 April 2020
9:30-10:45 Module 1: Deployment and Lab
- Recall important information from Engineer courses
- Deployment modes supported by the XG Firewall
- Understand a range of scenarios where each deployment mode would commonly be used
- Use built-in tools to troubleshoot issues
- Labs
10:45-11:00 break
11:00-13:00 Module 2: Base Firewall
- Explain how the XG firewal can be accessed
- Understand the types fo interfaces that can be created
- Understand the benefits of Fast Path Technology
- Configure routing per firewall rule
- Understand best practice for ordering firewall rules
- Explain what Local NAT policy is and known how to configure it.
13:00-14:00 Lunch
14:00-16:00 Labs
- Activate the Sophos XG Firewalls
- Post installation Configuration
- Bridge interfaces
- Create a NAT rule to load balance access to servers
- Create a local NAT policy
- Configure routing using multiple WAN links
- Configure policy-based routing for an MPLS scenario
- Install Sophos Central
16:00-16:15 Break
16:15-17:15 Module 3:Network Protection and Lab
- Explain what IPS is and how traffic can be offloaded to Fastpath
- Demonstrate how to optimize workload y configuring IPS policies
- Examine advanced Intrusion Prevention and optimize policies
- Configure advanced DOS Protection rules
- Demonstrate how the strict policy can be used to protect networks
- Labs- Create Advanced DoS Rules
Day 2 Wednesday 29 April 2020
9:30-11:00 Module 4: Synchronized Security and Labs
- Explain how Security Heartbeat works
- Configure Synchronized Security
- Deploy Synchronized Security in discover and inline modes
- Understand the advantages and disadvantages of deploying
- Synchronizes Security in different scenarios
- Labs
- Configure source-Based Security
- Hearteat firewall rules
- Destination based Security Heartbeat
- Missing Security Heartbeat
- Lateral Movement Protection
11:00-11:15 Break
11:15-13:45 Module 5 Webserver Protection and Labs
- Explain how Websever Protection works
- Describe protection features for a web application
- Configure Web Server authentication
- Publish a web service using the Web Application Firewall
- Use the preconfigured templates to configure Web Server Protection for common purposes
- Configure SlowHTTP protection
- Labs (Web Application Firewall)
- Labs (Load balancing with Web Server Protection)
- Labs (Web Server Authentication and path-specific routing)
13:45-14:45 Break and Lunch
14:45-17:45 Module 6: Site to site connections and Labs
- Configure and deploy site to site VPNs in a wide range of environment
- Implement IPsec NATing and failover
- Check and modify route precedence
- Create RED tunnels between XG firewalls
- Understand when to use RED
- Labs ( Create an IPsec site to site VPN
- Labs ( Configure VPN network NATing )
- Labs (Configure VPN failover)
- Labs (Enable RED on the XG firewall)
- Labs (Create a RED tunnel between two XG Firewalls
- Labs (Configure routing for the RED tunnel)
- Labs (Configure route-based VPN)
Day 3 Thursday 30 April 2020
9:00-10:00 Module 7: Authentications and Labs
- Demonstrate how to configure and use RADIUS accounting
- Deploy STAS in large and complex environment
- Configure SATC and STAS together
- Configure Secure LDAP and identify the different secure connections available
- Labs (configure an Active Directory Authentication server)
- Labs (configure single sing-on using STAS
- Labs (Authenticate users over a site to site VPN)
10:00-11:15 Module 8: Web Protection
- Choose the most appropriate type for web protection in different deployment scenarios
- Enable web filtering using the DPI engine or legacy web proxy
- Configure TLS inspection using the DLP engine or legacy web proxy
- Labs (Install the SSL CA certificate)
- Labs (Configure TLS inspection rules)
- Labs (Create a custom web policy for users)
11:15-11:30 Break
11:30-12:15 Module 9: Wireless
- Explain how Sophos Access Points are deployed and identify some common issues
- Configure RADIUS authentication
- Configure a mesh network
12:15-13:05 Module 10:Remote Access
- Configure Sophos Connect and manage the configuration using Sophos Connect Admin
- Configure an IPsec remote access VPN
- Configure an L2TP remote access VPN for mobile devices
- Labs (Sophos Connect)
13:05-14:25 Module 11: High Availability
- Explain what HA is and how it operates
- Demonstrate how to configure HA and explain the difference between quick and manual configuration
- List the prerequisites for high availability
- Perform troubleshooting steps andc heck the logs to ensure that HA is set up correctly.
- Explain the packet flow in high availability
- Demonstrate how to disable HA
- Labs (Create an Active-Passive cluster)
- Labs (Disable High Availability)
14:25-15:05 Break – Lunch
15:05-16-15 Public Cloud and Labs
- Deploy XG firewall in complex network enviroments
- Explain how XG firewall process traffic and use this information to inform the configuration
- Configure advanced networking and protection features
- Deploy XG firewall on public cloud infrastructure
- Labs (Put a service in debug mode to gather logs)
- Labs (Retrieving log files)
- Labs (Troubleshoot an issue from an imported configuration file)
- Labs (Deploy an XG Firewall on Azure (simulation)
16:15 (Exams)
The increase in remote working is driving greater use of mobile devices for business purposes. In this article we explore how Sophos Mobile can help you keep your devices and data secure, and how to balance privacy, security and productivity.
Setting up remote employees
Not everyone has the option to use a corporate-owned device and you may need to enable people to start using personal devices for work. Sophos Mobile lets you to secure any combination of personal and corporate-owned devices with minimal effort.
Users can easily set up their personal macOS, Windows 10, or mobile devices via the flexible self-service portal; they can enroll their device, reset passwords, and get help, all without any involvement from IT.
Balancing privacy and security
In Bring Your Own Device (BYOD) scenarios, you need to protect and control business email and data without intruding on your users’ privacy. The container-only management capabilities in Sophos Mobile let you control corporate content in the Sophos Secure Email and Sophos Secure Workspace apps without requiring management of the mobile device itself. This way, your users’ personal information remains private, while company resources are protected.
Protecting against mobile threats
10% of threats are discovered on mobile devices according to our recent survey of 3,100 IT Managers. Sophos Mobile includes Intercept X for Mobile which leverages our Intercept X deep learning engine to protect your users, their devices and corporate data from known and never-before-seen mobile threats. Intercept X for Mobile also gives your users easy-to-use security tools right at their fingertips, such as the Authenticator, Password Safe, Secure QR Code Scanner and Privacy Advisor.
Set up is as simple as downloading the app from the relevant app store and then enrolling your device via the Corporate management tool.
Your users can also use Intercept X for Mobile for free to protect their personal devices – they can simply download and start using today.
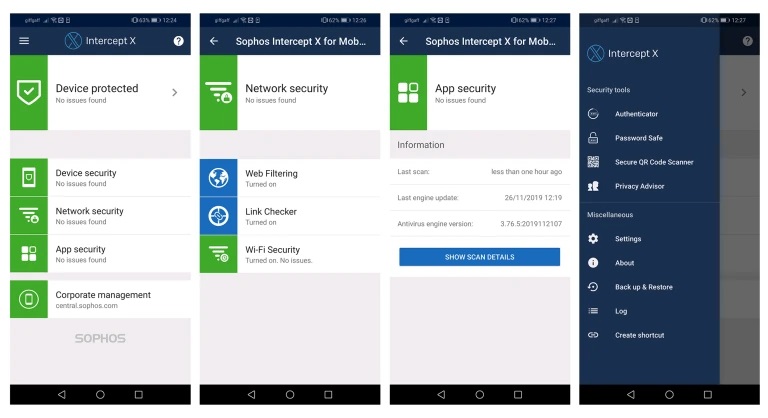
Read our help guide for more information on using Intercept X for Mobile.
Keeping employees safe on the web
Intercept X for Mobile also helps you keep your users safe on the web, stopping risky file types being downloaded, and blocking access to inappropriate websites to maintain productivity and compliance. Read our step-by-step guidelines for creating a Web Filtering policy.
Monitoring and control
Compliance policies in Sophos Mobile help ensure mobile devices are used appropriately – both from a security and business policy perspective. For example, you can:
- Ensure that only reputable apps are downloaded from the relevant app stores
- Block the sideloading of a potentially dangerous app
- Restrict access to business resources
- Allow, forbid or enforce certain features of a device
- Define actions that are executed when a compliance rule is violated
You can create separate compliance policies and assign them to different device groups, allowing you to apply appropriate levels of security and access for your users and devices. See the full list of available compliance rules.
For more information and general configuration steps for both Sophos Mobile and Intercept X for Mobile, take a look at the comprehensive help guide.
|
|||||||||||||||
The widespread nature and severity of coronavirus (COVID-19) continues to raise challenges on a variety of fronts. For many organizations, one of those is the need to enable employees to work from home until it’s safe to return to the office.
Solutions for remote working exist, but they can be costly and complex to implement. And, they may not offer the level of security you need.
If you’re looking for a solution that solves each of these issues, Sophos can help. You can take advantage of our free 90-day XG Virtual Firewall Free Trial to get your employees securely connected from home.
XG Virtual Firewall is available on your favorite virtual platforms including VMware, Hyper-V, Citrix XenApp, and KVM. It provides a bevy of connectivity and security features and it’s easy to set up. Simply visit the free trial page, fill out the form, and you’re off.
Secure connectivity for remote workers
A nice aspect of the virtual free trial is its multi-platform support. You can also select the hardware you want to install it on, which makes the process more convenient.
XG Virtual Firewall includes a base license that offers remote connectivity options for users, including both IPsec through Sophos Connect client, and SSL VPN. Both provide secure methods for connecting from home back to the corporate office and accessing resources such as email, applications, and documents.
Your free trial also includes a FullGuard security bundle that protects your firewall and connected devices from threats such as ransomware, breaches, phishing emails, and more.
You can even add additional services such as Sophos Intercept X to take advantage of our Synchronized Security feature, which shares telemetry data on the health status of each connected device in addition to isolating any endpoint that does become infected so the infection can’t spread laterally to other hosts.
Setting up your XG Virtual Firewall free trial
Keeping your organization running smoothly can be challenging during the best of times. As we switch to a “work from home” model until it’s safe to return to the office, having a solution that meets your remote connectivity and security needs can help make things easier. And, it doesn’t need to be difficult to get up and running quickly.
We’re here to make your XG Virtual Firewall Free Trial simple to deploy and configure so your remote employees can get connected and stay productive. Here are some resources to help you get started.
- Sign up for the XG Virtual Firewall Free Trial
- XG Firewall Virtual and Software Appliance Installation Guide
- XG Firewall: Useful links for configuring VPN remote access
- XG Firewall: How to configure Connect client on XG Firewall
- XG Firewall: How to configure SSL VPN remote access
If you have questions at any point during your free trial please visit our knowledgebase, review our how-to videos, documentation, or contact us.
After 90 days
Should you wish to continue using XG Firewall once the free 90-day trial ends, we can help you transition to a hardware, virtual or cloud instance of XG Firewall. Speak to your Sophos representative to discuss your requirements.