News
It’s easy to pinpoint when the global health crisis forever changed the security landscape. All of a sudden, at exactly the same time, the workforces of entire organizations went remote. And so did the technology teams supporting them.
It’s clear that most organizations won’t be returning to office-based working on the same level as before. And just as users are increasingly dispersed, so are the resources they use: on servers in the office; in cloud-based applications like Office 365 or Salesforce; and in private or public cloud environments on Amazon Web Services (AWS) and Microsoft Azure.
IT teams are being tasked to protect what we’re calling “the Anywhere Organization”: where people can work securely from any location, using any device, and accessing resources wherever they’re held.
3 steps to protect the Anywhere Organization
You wouldn’t bolt your front door but leave your back door unlocked and assume that your home is secure. The same goes for cybersecurity. You need to protect all locations, devices, and resources.
Secure connectivity
Whether employees are logging in from home office setups, at a corporate office, visiting a client, or using a hotel Wi-Fi halfway across the globe, they need to be able to connect securely.
VPN is a tried and trusted approach that has enabled users to connect remotely for years. It was a savior at the beginning of the pandemic, allowing organizations to quickly pivot to secure remote working in just days.
Many organizations are starting to want more than VPN was ever designed to deliver. Zero Trust Network Access (ZTNA) is a great alternative to remote access VPN. It enables users to easily connect to corporate resources from any location while also enhancing your security by constantly verifying the user and validating the health and compliance of the device.
Protect all devices
For today’s Anywhere Organization, protection must work on any device or platform your employees may need to use desktops, laptops, mobile devices, Windows, macOS, Linux, Android, Chromebook, and iOS.
The most devastating cyber threats involve human-led attacks, often exploiting legitimate tools and processes such as PowerShell. Hands-on, live hacking enables attackers to bypass security products and protocols by modifying their tactics, techniques, and procedures (TTPs).
Stopping these human-led attacks requires human-led threat hunting. Either look for an EDR (Endpoint Detection and Response) solution that gives you the tools you need to perform threat hunts from the same console used to manage your endpoint protection, or bring in the experts via a Managed Detection and Response service.
Secure all resources
When it comes to securing the Anywhere Organization, it’s essential to protect the data and workloads your people need to use, while simultaneously securing the networks they’re on.
You may be running servers on-premises, consuming cloud-based applications, or hosting resources in private and public cloud environments on AWS, Azure, or GCP. Most likely, you’re doing all of the above. Whatever your unique situation, you need:
- Next-gen server protection for your cloud, on-premises, or hybrid workload environments.
- Powerful gateway protection with a firewall that secures cloud-based and on-premises environments.
Time to make lemonade
An old adage says, “When life gives you lemons, make lemonade.” And that’s pretty much what the corporate enterprise is doing by adopting the Anywhere Organization trend.
It’s proving out that remote working is a win-win for companies and staff alike in terms of greater productivity and reduced operational costs.
Sophos can help you with all three pillars of secure remote working: secure connectivity, protected devices, and secure resources.
Plus we also make life easier for busy (and often remote) IT teams too: all Sophos protection can be managed through our Sophos Central platform. In fact, customers running a Sophos security system consistently report a 50% reduction in IT workload.

To learn more about how Sophos can help you with secure remote working read our solution brief, Securing the Anywhere Organization.
Source: Sophos
Network security has never been enough to keep bad actors from accessing sensitive data because most breaches occur at the application level. Invicti’s dynamic application security testing (DAST) tools provide the automation, visibility, and scale required to effectively secure web applications.
Invicti is an international web application security software company with a mission to make the internet a safer place, and has brought together Netsparker and Acunetix, two brands that identify web vulnerabilities.
Meet the tools
Acunetix
Acunetix is a vulnerability assessment and management solution, designed to be a part of any enterprise environment by providing multiple integrations as well as options to integrate within custom contexts. Acunetix is renowned for its high-performance engine (written in C++) and the very low rate of false positives. It is available for Microsoft Windows, Linux, and macOS operating systems as well as an online (cloud) solution. The scanner uses a web interface and two unique technologies that help you discover more vulnerabilities: AcuMonitor and AcuSensor (it will help you find the vulnerability in the source code). In addition to an Acunetix scan, you can and you should follow up with further manual tests done using command-line and GUI-based penetration testing tools.

Advantages
- An easy to use, multi-user tool focused on SME/SMB
- Built for efficiency & ease of use Well suited for small security teams
- that do not have dedicated application security resources
- Enables flexible integrations, provides a comprehensive API
- Available on Windows, Linux, macOS and in the cloud
Netsparker
Netsparker finds and reports web application vulnerabilities such as SQL Injection and Cross-site Scripting (XSS) on all types of web applications, regardless of the platform and technology they are built with. Netsparker’s unique and dead accurate Proof-Based Scanning Technology does not just report vulnerabilities, it also produces a Proof of Concept to confirm they are not false positives. Freeing you from having to double check the identified vulnerabilities.
Available as a Windows application (Netsparker Desktop) or as a cloud-based solution (Netsparker Cloud), it is the ultimate, enterprise-class web application security solution.

Advantages
- A Comprehensive multi-team solution geared towards enterprises
- Built to scale
- Ideal for complex and decentralized IT infrastructures
- Can be deployed in the cloud, on-premises, or in any combination
- Helps break down silos between the security and development teams
Focusing on network security leaves vulnerabilities
3 out of 4 security breaches occur at the application level but investments in application security continue to pale compared to network security.

The risks keep growing
The web has gone from 50 million sites in 2005 to over 1.8 billion (and growing) in 2020. Keeping up with this exponential growth and risk is important to protect your organization and customer data.

All applications will be web applications
Businesses worldwide continue moving to the cloud. Analysts predict that by 2025, cloud products will make up more than 50% of the software market. By 2032, this figure may exceed 90%.

What to do? Be safe!
The best of breed DAST solutions help you to:
- Automate mimicked real-world attacks to identify, prioritize, and validate security vulnerabilities in running applications.
- Eliminate the reliance on time-consuming manual penetration testing and the dependency on bug bounty programs.
- Reduce friction between security and development teams and incorporate security into the development process.
Invicti delivers safety
Based in Austin, Texas, Invicti Security specializes in web application security, serving organizations across the world. Invicti was founded in 2018 by bringing together Netsparker and Acunetix, two brands that identify web vulnerabilities to prevent costly data breaches and other security incidents. Netsparker was the first web application security solution to deliver automatic verification of vulnerabilities with its proprietary Proof-Based Scanning™ technology. This best-in-class web application security solution identifies vulnerabilities from the early stages of application development through production. Known for its ease of use, speed and accuracy, Acunetix is a global web security leader and the first-ever automated web application security scanner.
The branch office of one
Prior to the pandemic, there was already a shift in networking underway, with an increasing percentage of the workforce beginning to work from home – at least part-time. This trend has dramatically accelerated over the last year, with the vast majority of organizations either mandating their employees work from home, or strongly encouraging it.
This has transformed many organizations almost overnight into a highly-distributed model with hundreds, if not thousands, of one-person branch offices. The “branch office of one” has become the new normal for many organizations.
This massive shift has created a similarly massive challenge for many IT organizations, who have been scrambling to implement VPN access for their remote workers. As just one example, utilization of our Sophos Connect VPN client with XG Firewall has shot up over 10x to more than 1.4 Million active clients in recent months.
And while VPN technology has been a savior and has served us well, it was never really designed for this new world. VPN can be difficult to deploy and enroll new staff, it can be challenging for end-users to use and creates unnecessary friction, and it does not provide the kind of granular security that most organizations require.
Gartner’s recent report, Solving the Challenges of Modern Remote Access, also highlights the challenges with VPN: licensing, efficiency, relevancy, and suitability for the task.
Protecting your data
If it wasn’t enough that IT organizations are grappling with this massive shift in remote working, the whole industry has come under siege by bad actors and hackers attempting to take advantage of the current situation with increasing attacks on corporate systems and data. The latest Sophos 2021 Threat Report provides an excellent look at how cybercriminals have upped their game.
With a massive collection of branch offices of one and an ever-increasing need for tighter security that is transparent and frictionless, what are the options?
We’re actively working to get Sophos ZTNA, or zero trust network access, into your hands as fast as possible. To help overcome some of the challenges you’re facing with remote workers, it provides a simpler, better, more secure solution to connect your users to important applications and data.
Zero trust network access
ZTNA is founded on the principle of zero trust and is all about verifying the user. It typically leverages multi-factor authentication to prevent stolen credentials from being a source of compromise, then validates the health and compliance of the device to ensure it’s enrolled, up to date, and properly protected. ZTNA then uses that information to make policy-based decisions to determine access and privilege to important networked applications.
![]()
Benefits of ZTNA compared to remote access VPN
While remote access VPN continues to serve us well, ZTNA offers a number of added benefits that make it a much more compelling solution:
- More granular control: ZTNA allows more granular control over who can access certain applications and data, minimizing lateral movement and removing implied trust. VPN is all-or-nothing: once on the network, VPN generally offers access to everything.
- Better security: ZTNA includes device and health status in access policies to further enhance security. VPN does not consider device status, which can put application data at risk to a compromised or non-compliant device.
- Easier to enroll staff: ZTNA is much easier to roll out and is better when it comes to enrolling new employees. VPN involves more challenging and difficult setup and deployment.
- Transparent to users: ZTNA offers “just works” transparency to users with frictionless connection management. VPN can be difficult and prone to initiating support calls.
Overall, ZTNA offers a welcome solution to connecting the branch office of one.
Sophos ZTNA
Sophos ZTNA is a brand new cloud-delivered, cloud-managed product to easily and transparently secure your important business applications with granular controls.
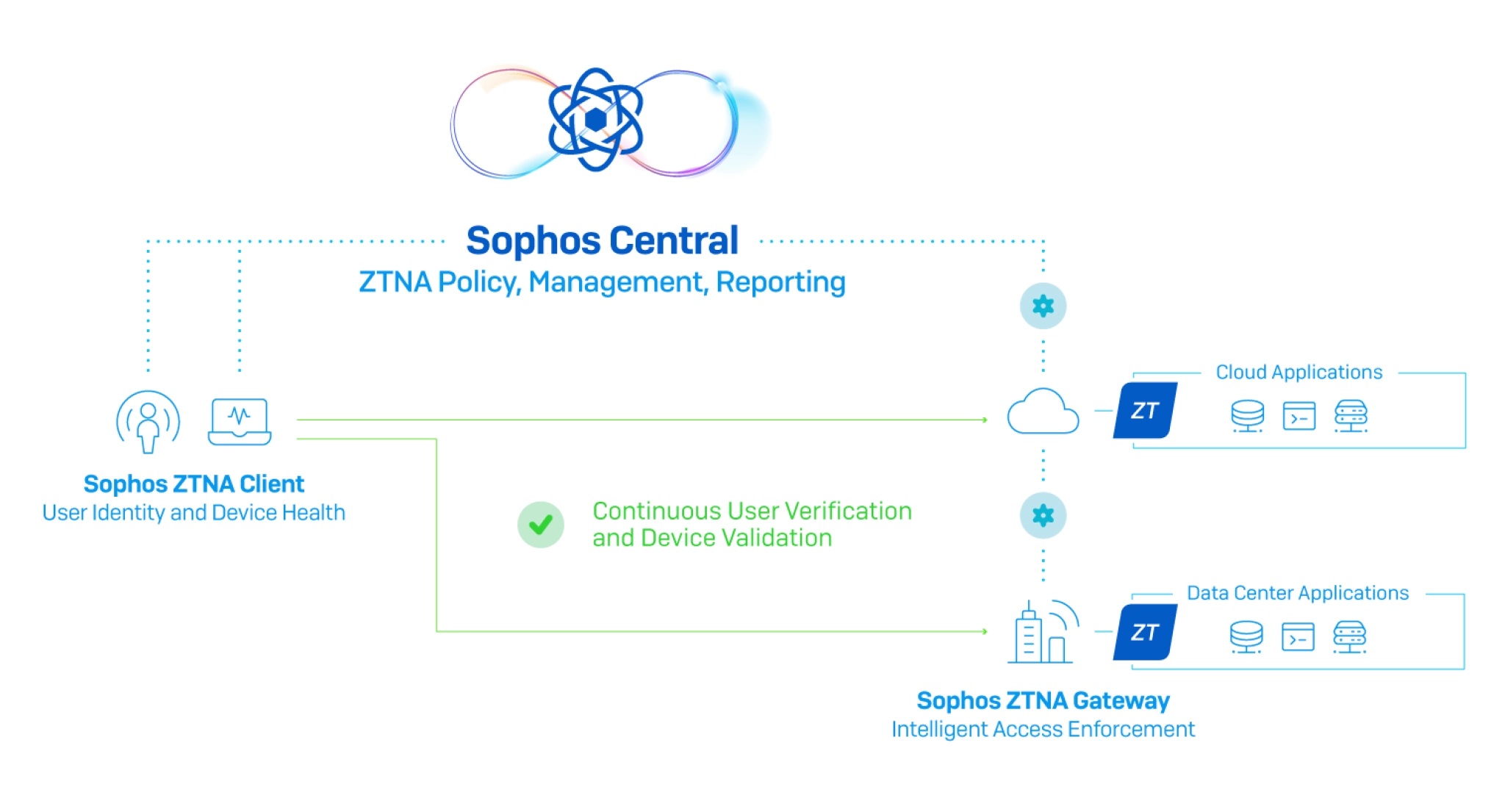
Sophos ZNTA consists of three components:
- Sophos Central provides the ultimate cloud management and reporting solution for all your Sophos products, including Sophos ZTNA. Sophos ZTNA is fully cloud-enabled, with Sophos Central providing easy deployment, granular policy management, and insightful reporting from the cloud.
- Sophos ZTNA Gateway will be available as a virtual appliance for a variety of platforms to secure networked applications on-premise or in the public cloud. AWS and VMware ESXi support will be available initially, closely followed by support for Azure, Hyper-V, Nutanix, and others.
- Sophos ZTNA Client provides transparent and frictionless connectivity to controlled applications for end users based on identity and device health. It is super easy to deploy from Sophos Central, with an option to deploy alongside Intercept X with just one click or instead work standalone with any desktop AV client. It will initially support MacOS and Windows, and later Linux and mobile device platforms as well.
Coming soon
The early access program (EAP) for the initial version of our ZTNA solution will kick off in the next couple of weeks, so stay tuned for additional news. I hope you will all join us in test-driving Sophos ZTNA to make it the best product it can be for launch!
Source: Sophos

Global research and advisory firm 451 Research (part of S&P Global Market Intelligence) has published a comprehensive evaluation of Sophos Rapid Response, our cyber incident emergency response service.
451 Research calls out Sophos Rapid Response as an attractive emergency response service not just for small and midsized businesses, but also larger organizations, and highlights the fixed-fee, 45-day engagement model as “unique in a market that is known for open-ended hourly pricing models, annual retainers and, at times, delayed response.”
Incident response expertise is one of the top cybersecurity-related skillsets missing from IT teams, second only to cloud platform expertise, according to the Voice of the Enterprise (VotE): Information Security, Organizational Dynamics 2020 survey conducted by 451 Research.
Furthermore, the VotE survey found information security staffing levels in enterprises to be inadequate, with IT teams lacking the capacity to deal with the cybersecurity challenges those organizations face.
Sophos’ own research echoes these findings: 81% of IT managers say the ability to find and retain skilled IT security professionals is a major challenge to their ability to deliver IT security*.
This lack of in-house capacity and expertise is pushing many organizations to outsource their cybersecurity. Sophos Rapid Response enables IT teams to plug the gap in cybersecurity skills and resourcing by taking advantage of Sophos’ team of in-house experts.
Read 451 Research’s comprehensive review to get both an in-depth analysis of the incident response services marketplace and impartial overview of the Sophos Rapid Response service.
Every second counts during a cyberattack
Dealing with a cyberattack is a race against time: you need to stop your adversary before they can achieve their objectives. Sophos Rapid Response gets you out of the danger zone fast with our 24/7 team of remote incident responders, threat analysts, and threat hunters.
For more information on the Sophos Rapid Response service, speak to your Sophos representative or visit www.sophos.com/rapidresponse.
Source: Sophos
SonicWall, a cybersecurity vendor serving managed service providers (MSPs) announced on January 22 that they were hacked.
The breach involved “highly sophisticated threat actors exploiting probable zero-day vulnerabilities on certain SonicWall secure remote access products,” according to the company’s statement.
If you’re a SonicWall partner, they’ve outlined some actions you can take to mitigate your risk if you have a product that has been compromised. However, it’s important that MSPs remember the foundations of a secure platform to protect their assets and their clients’.
- Ensure applications are patched and up to date. When applications are not up to date, businesses are more vulnerable. Patch software on a regular basis, or even automatically, to avoid hackers exploiting known vulnerabilities.
- Enable two-factor authentication. This multi-layered security approach is a vital step for MSPs looking for an easy way to better restrict access to their network, applications, and systems.
- Review your remote monitoring policies. Ensure your alerts are set up to keep you in the know of any potential breaches or impacted endpoints.
- Ensure you have a business continuity solution in place. Business continuity and disaster recovery (BCDR) tools are built to restore a device or server in the event of a security breach or disaster. When all else fails, BCDR tools enable businesses to get back up and running when the worst happens, keeping business operations intact.
Source: Datto
This three-day training program was designed and intended for experienced technical professionals who want to install, configure and support the XG Firewall in production environments and is the result of an in-depth study on the next generation firewall of Sophos. The program consists of presentations and practical workshops for the enhancement of teaching content. Due to the nature of the traditions and the varied experience of the trainees, open discussion is encouraged during the training.
Sophos XG Architect Training (3 days Training) Tuesday 16 March 2021 – Thursday 18 March 2021
Requirement
- XG Firewall _ Certified Engineer course and delta modules up to version 18.0
Recommended Knowledge
- Knowledge of networking to a CompTIA N+ level
- Knowledge of IT security to a CompTIA S+ level
- Experience configuring network security devices
- Be able to troubleshoot and resolve issues in Windows networked environments
- Experience configuring and administering Linux/UNIX systems
Content
- Module 1: Deployment
- Module 2: Base firewall
- Module 3: Network Protection
- Module 4: Synchronized security
- Module 5: Web server Protection
- Module 6: Site to site connections
- Module 7: Authentications
- Module 8: Web Protection
- Module 9: Wireless
- Module 10: Remote Access
- Module 11: High Availability
- Module 12: Pulic Cloud
Certification
+ exam: Sophos XG Architect
Duration 3 days
Agenda
Trainer: Micheal Eleftheroglou
Day 1 Tuesday 16 March 2021
9:30-10:45 Module 1: Deployment and Lab
- Recall important information from Engineer courses
- Deployment modes supported by the XG Firewall
- Understand a range of scenarios where each deployment mode would commonly be used
- Use built-in tools to troubleshoot issues
- Labs
10:45-11:00 break
11:00-13:00 Module 2: Base Firewall
- Explain how the XG firewall can be accessed
- Understand the types fo interfaces that can be created
- Understand the benefits of Fast Path Technology
- Configure routing per firewall rule
- Understand best practice for ordering firewall rules
- Explain what Local NAT policy is and known how to configure it.
13:00-14:00 Lunch
14:00-16:00 Labs
- Activate the Sophos XG Firewalls
- Post installation Configuration
- Bridge interfaces
- Create a NAT rule to load balance access to servers
- Create a local NAT policy
- Configure routing using multiple WAN links
- Configure policy-based routing for an MPLS scenario
- Install Sophos Central
16:00-16:15 Break
16:15-17:15 Module 3:Network Protection and Lab
- Explain what IPS is and how traffic can be offloaded to Fastpath
- Demonstrate how to optimize workload y configuring IPS policies
- Examine advanced Intrusion Prevention and optimize policies
- Configure advanced DOS Protection rules
- Demonstrate how the strict policy can be used to protect networks
- Labs- Create Advanced DoS Rules
Day 2 Wednesday 17 March 2021
9:30-11:00 Module 4: Synchronized Security and Labs
- Explain how Security Heartbeat works
- Configure Synchronized Security
- Deploy Synchronized Security in discover and inline modes
- Understand the advantages and disadvantages of deploying
- Synchronizes Security in different scenarios
- Labs
- Configure source-Based Security
- Hearteat firewall rules
- Destination based Security Heartbeat
- Missing Security Heartbeat
- Lateral Movement Protection
11:00-11:15 Break
11:15-13:45 Module 5 Webserver Protection and Labs
- Explain how Websever Protection works
- Describe protection features for a web application
- Configure Web Server authentication
- Publish a web service using the Web Application Firewall
- Use the preconfigured templates to configure Web Server Protection for common purposes
- Configure SlowHTTP protection
- Labs (Web Application Firewall)
- Labs (Load balancing with Web Server Protection)
- Labs (Web Server Authentication and path-specific routing)
13:45-14:45 Break and Lunch
14:45-17:45 Module 6: Site to site connections and Labs
- Configure and deploy site to site VPNs in a wide range of environment
- Implement IPsec NATing and failover
- Check and modify route precedence
- Create RED tunnels between XG firewalls
- Understand when to use RED
- Labs ( Create an IPsec site to site VPN
- Labs ( Configure VPN network NATing )
- Labs (Configure VPN failover)
- Labs (Enable RED on the XG firewall)
- Labs (Create a RED tunnel between two XG Firewalls
- Labs (Configure routing for the RED tunnel)
- Labs (Configure route-based VPN)
Day 3 Thursday 18 March 2021
9:00-10:00 Module 7: Authentications and Labs
- Demonstrate how to configure and use RADIUS accounting
- Deploy STAS in large and complex environment
- Configure SATC and STAS together
- Configure Secure LDAP and identify the different secure connections available
- Labs (configure an Active Directory Authentication server)
- Labs (configure single sing-on using STAS
- Labs (Authenticate users over a site to site VPN)
10:00-11:15 Module 8: Web Protection
- Choose the most appropriate type for web protection in different deployment scenarios
- Enable web filtering using the DPI engine or legacy web proxy
- Configure TLS inspection using the DLP engine or legacy web proxy
- Labs (Install the SSL CA certificate)
- Labs (Configure TLS inspection rules)
- Labs (Create a custom web policy for users)
11:15-11:30 Break
11:30-12:15 Module 9: Wireless
- Explain how Sophos Access Points are deployed and identify some common issues
- Configure RADIUS authentication
- Configure a mesh network
12:15-13:05 Module 10:Remote Access
- Configure Sophos Connect and manage the configuration using Sophos Connect Admin
- Configure an IPsec remote access VPN
- Configure an L2TP remote access VPN for mobile devices
- Labs (Sophos Connect)
13:05-14:25 Module 11: High Availability
- Explain what HA is and how it operates
- Demonstrate how to configure HA and explain the difference between quick and manual configuration
- List the prerequisites for high availability
- Perform troubleshooting steps andc heck the logs to ensure that HA is set up correctly.
- Explain the packet flow in high availability
- Demonstrate how to disable HA
- Labs (Create an Active-Passive cluster)
- Labs (Disable High Availability)
14:25-15:05 Break – Lunch
15:05-16-15 Public Cloud and Labs
- Deploy XG firewall in complex network enviroments
- Explain how XG firewall process traffic and use this information to inform the configuration
- Configure advanced networking and protection features
- Deploy XG firewall on public cloud infrastructure
- Labs (Put a service in debug mode to gather logs)
- Labs (Retrieving log files)
- Labs (Troubleshoot an issue from an imported configuration file)
- Labs (Deploy an XG Firewall on Azure (simulation)
16:15 (Exams)
The Linux Foundation and the Laboratory for Innovation Science at Harvard recently released a Report on the 2020 Free/Open-Source Software Contributor Survey. One of the primary conclusions of this report was the fact that free/open-source software developers often have a very negative approach to security. They spend very little time resolving security issues (an average of 2.27% of their total time spent) and they express no willingness to spend more.
Some of the quotes from the survey were simply disturbing. For example, “I find the enterprise of security a soul-withering chore and a subject best left for the lawyers and process freaks. I am an application developer.” Another example: “I find security an insufferably boring procedural hindrance.”
While the report contains the authors’ strategic recommendations, here are our thoughts about what this situation means for application security and what you can do about it.
How Far and How Wide?
The original report focuses only on free/open-source software (FOSS) but we believe it is important to consider whether this is only a FOSS problem or a problem with all developers.
Based on the survey, most FOSS developers (74.87%) are employed full-time and more than half (51.65%) are specifically paid to develop FOSS. This means that FOSS is often developed by the same people that develop commercial software. We do not believe that the developers change attitude depending on whether the software they work with is free or commercial. Therefore, we believe that this bad attitude towards security extends to all developers.
We also believe that the underlying cause of this attitude is the fact that developers are either taught badly or not taught at all. Most online resources that teach programming completely skip the issue of secure coding practices. Books about programming languages rarely even mention secure coding. Schools also often treat security as an optional subject instead of a core course that should be a prerequisite to all other programming classes.
Therefore, we conclude that the results of this survey may be assumed to apply to all software developers. While in the case of commercial software some security measures may be added by the presence of dedicated security teams, “the root is still rotten”.
Secure Development? Not Likely!
While 86.3% of the respondents of the survey received formal development training, only 39.8% stated that they have formal training in developing secure software. This means that half the developers were taught badly.
Another shock comes from the response to the following question: “When developing software, what are your main sources for security best practices?”. It turns out that only 10.73% learned such best practices from formal classes and courses and 15.51% from corporate training. Nearly half the developers use online articles/blogs (46.54%) and forums (50.66%) as their primary source of information on best practices, which again shows the horrid state of education and the lack of resources about secure coding. And while we at Acunetix pride ourselves on filling the gap and being the teachers (thanks to our articles that explain how vulnerabilities work and how to avoid them), we would much rather have developers learn first from sources that are more reliable than a search engine.
Last but not least, survey results prove that free/open-source software is usually released with no security testing at all. While 36.63% use a SAST tool to scan FOSS source code, only 15.87% use a DAST to test applications. This situation is probably better in the case of commercial software because security teams usually introduce SAST/DAST into the SDLC.
Why the Bad Attitude?
If your application developers have a bad attitude towards security, it is not only due to their education. It may also be because of your business organization, which causes them to feel that they’re not involved in security at all.
Developers don’t feel responsible for security primarily due to the existence of dedicated security teams. If security personnel work in separate organizational units, the developers think that security is not their problem and expect the security researchers to take care of it instead.
Developers also don’t feel responsible because in a traditional organization they rarely are expected to fix their own security-related mistakes. A typical developer writes a piece of code, gets a code review from another developer (probably just as clueless about security), and then forgets about it. Later, a security researcher finds a vulnerability and creates a ticket to fix it. This ticket is assigned to the first available developer – usually not the one who originally introduced the vulnerability.
Such an organization promotes the lack of responsibility for security and fuels negative feelings between developers and security teams. They may view one another as “the ones that cause problems” – and this is what you must aim to change first.
Automation as a Solution
Automating the process of finding and reporting security vulnerabilities as early as possible solves this problem. First of all, errors are reported by a piece of software, not a human – therefore there is no other person to blame. Secondly, the error is reported immediately, usually after the first build attempt, and the build fails, so the developer must fix their own mistake right away. And thirdly, every time the developer is forced to fix their own error, they learn a little more about how to write secure code and how important it is.
The only problem that remains is finding software that can be trusted with this task. Unfortunately, limited capabilities of SAST/DAST software have been the cause of many failures in the past and this is why many developers do not want to use a SAST or a DAST tool.
SAST tools point to potential problems but they report quite a few false positives – the developer spends a lot of time researching something that turns out not to be a vulnerability at all. In the end, developers stop trusting the tool and start hating it. On the other hand, DAST tools report fewer false positives but often don’t provide enough information for the developer to be sure where the vulnerability is and what it can lead to.
Acunetix helps solve such problems. The advantage is that, in the case of the most serious vulnerabilities, Acunetix provides proof of the vulnerability. For example, the developer may receive a report that their code exposed sensitive files from the server – including the content of these sensitive files as evidence.
Conclusions
The most worrying conclusion from this article is that most free/open-source software is inherently insecure and if you want to feel safe using it, you need to do regular security testing yourself.
Another worrying conclusion is that people who should be your first line of defense in IT security are not educated about security and have a bad attitude toward it. This is not something that is going to be easy or quick to change.
Long-term strategic resolutions are needed to solve these major problems and simply implementing an automated solution cannot be perceived as a magic wand. However, if you introduce a reliable automated testing solution such as Acunetix into your DevSecOps SDLC at the earliest stage possible, you will ensure that your software is safe and you will teach your own developers that they need to take responsibility for the security of their code.
Source: Acunetix
This course is designed for technical professionals who will be supporting Sophos Central and provides an overview of how to troubleshoot the product.
Sophos Central Technician Training (2 days Training) – Tuesday 2 March 2021– Wednesday 3 March 2021
The course is expected to take 1 ½ days (10 hours) to complete, of which approximately half will be spent on the practical exercises.
On completion of this course, trainees will be able to:
- Understand the support tools required to investigate common issues
- Identify common issues when reported
- Perform appropriate troubleshooting steps
Prerequisites
Prior to taking this course you should:
- Have completed and passed the Sophos Central Certified Engineer course
- This course uses Windows tools and utilities as part of the troubleshooting process. Students should be comfortable working with following:
- Windows Administrator command prompt
- Control Panel settings
- File and folder permissions
- Windows Services (services.msc)
- Registry Editor (regedit.exe)
- Windows Firewall with Advanced Security
- Active Directory Users and Computers
- Active Directory Group Policies.
Certification
To become a Sophos Certified Technician, trainees must take and pass an online assessment. The assessment tests their knowledge of both the presented and practical content. The pass mark for the assessment is 80% and is limited to 3 attempts.
Lab Environment
Each student will be provided with a pre-configured environment which simulates a company network with two sites, a head office and a branch office and contains Windows Servers, a Windows Desktop and three XG Firewalls
Content
- Module 1: Introduction to Troubleshooting Sophos Central
- Module 2: Client Installation
- Module 3: Active Directory Synchronization
- Module 4: Updating
- Module 5: Policies
- Module 6: Infection and Detection
- Module 7: Threat Response
Certification
+ exam: Sophos Central Technician
Duration 1 1/2 days
Agenda
Trainer: Michael Eleftheroglou
Day 1 Tuesday 2 March 2021
9:30-10:35 Module 1: Introduction to Troubleshooting Sophos Central
- Troubleshooting process
- Alerts and logins in Sophos Central
- Sophos Tools
- Windows Tools
- Client Log Files
- Labs (40 mins)
- Lab Preparation
- Install Server Protection
- Install and Configure AD Sync
- Deploy an Update Cache and Message Relay
10:35-12:40 Module 2: Client Installation
Installation Overview
- Active Directory Group Policy Deployment Failure
- Download Failure
- Competitor Removal Tool
- Package Installation Failure
- Labs (75 mins)
- Troubleshoot CRT Issues
- Uninstall a Deleted Endpoint
- Customize the Competitor Removal Tool
- Troubleshoot Deployment using a Startup Script
- Troubleshoot Failure to Download the Installer
- Troubleshoot Package Installation Failure
12:40-13:20 Lunch
13:20-14:30 Module 3: Active Directory Synchronization
- Active Directory Synchronization Overview
- Windows Password Changed
- Central Password Changed
- Unable to Connect
- Users No Longer Being Synced
- erifying Filters
- Labs (45 mins)
- Troubleshoot Synchronization Failure
- Troubleshoot Connection Errors for Synchronization
- Troubleshoot Groups Not Synchronizing
- Troubleshoot a Missing UserIPsec VPN Could Not Be Established (Scenario 2)
14:30-15:45 Module 4: Updating
Updating (30 mins)
- Updating Overview
- Techniques for Troubleshooting
- Disk Space and Permissions Problems
- Name Resolution
- Sophos Central
- Sophos Certified Technician
- Client Firewall
- Network Firewall
- Labs (45 mins)
- Investigate the Current Configuration
- Simulate Failure of the Update Cache Server
- Modify Proxy Settings
- Modify Firewall Settings
15:45-16:00 Break
16:00-17:05 Module 5:Policies
- Policies Overview
- Management Communication
- Message Relays
- Troubleshooting Connectivity
- Client Deleted from Central
- Labs (45 mins)
- Establish the Current Configuration for Management Communication
- Configure Web Control policies and Global Settings
- Configure Server Groups and Policies
Day 2 Wednesday 3 March 2021
9:30-10:45 Module 6: Infection and Detection
- Cleanup
- Quarantine
- False positives
- Labs (30 mins)
- Release a File from SafeStore
- View File Information in EndPoint Self Help
- Use the Source of Infection Tool
10:45-12:00 Module 7 Threat Response
- Endpoint Detection and Response
- How to read a threat case
- Search for threats
- Detection scenarios
- How to find help from Sophos.
- Labs (30 mins)
- Generate and Analyze Threat Cases
- Create and View a Forensic Snapshot
This course is designed for technical professionals who will be supporting Sophos XG Firewall and provides an overview of how to troubleshoot the product.
Sophos XG Technician Training (2 days Training) – Tuesday 23 February 2021– Wednesday 24 February 2021
The course is expected to take 2 days (16 hours) to complete, of which approximately 4 hours will be spent on the practical exercises.
On completion of this course, trainees will be able to:
- Apply the troubleshooting process to issues
- Use the tools available on the XG Firewall to gather information and investigate issues
- Locate and read log files on the XG Firewall
- Identify and resolve common issues
Prerequisites
Prior to taking this training, you should:
- Have completed and passed the XG Firewall Certified Engineer course and any subsequent delta modules up to version 18.0
- We recommend students have the following knowledge and experience:
- Experience with Windows networking and the ability to troubleshoot issues
- A good understanding of IT security
- Experience configuring network security devices
- Experience configuring and administering Linux/UNIX systems
If you are uncertain whether you meet the necessary prerequisites to take this course, please email us at globaltraining@sophos.com and we will be happy to help.
Certification
To become a Sophos Certified Technician, trainees must take and pass an online assessment. The assessment tests their knowledge of both the presented and practical content. The pass mark for the assessment is 80% and is limited to 3 attempts.
Lab Environment
Each student will be provided with a pre-configured environment that simulates a company network with two sites, a head office and a branch office and contains Windows Servers, a Windows Desktop and three XG Firewalls
Content
- Module 1: Getting Started with Troubleshooting XG Firewall
- Module 2: Troubleshooting Network Protection
- Module 3: Troubleshooting Network Protection II
- Module 4: Troubleshooting Authentication
- Module 5: Troubleshooting Web Protection and Application Control
- Module 6: Troubleshooting Synchronized Security
- Module 7: Troubleshooting Web Server Protection
- Module 8: Troubleshooting Wireless Protection
- Module 9: Troubleshooting Email Protection
- Module 10: Troubleshooting Reporting and How to Get Help
Certification
+ exam: Sophos XG Technician
Duration 2 days
Agenda
Trainer: Michael Eleftheroglou
Day 1, Tuesday 23 February 2021
9:30-11:25 Module 1: Getting Started with Troubleshooting XG Firewall
- Apply the troubleshooting process to issues
- Resolve common device access issues
- Identify the cause of XG Firewall going into failsafe mode
- Troubleshoot and resolve common high availability issues
- Troubleshoot routing issues
- Labs
11:25-11:40 break
11:40-13:40 Module 2: Troubleshooting Network Protection
- Troubleshoot and resolve common configuration issues with firewall rules and NAT rules
- Manage TLS decryption errors
- Determine whether traffic is flowing through the FastPath
- Troubleshooting problems with IPS settings
- Manage ATP alerts
- Labs (40 mins)
- Cannot Access Server in New York from London (Scenario 2)
- DNAT Not Working (Scenario 1)
- DNAT Not Working (Scenario 2)
- Remote Desktop Not Working
13:40-14:15 Lunch
14:15-16:00 Module 3: Troubleshooting Network Protection II
- Troubleshoot and resolve common connection issues for IPsec site-to-site VPNs
- Identify and resolve common SSL VPN issues
- Locate the logs for Sophos Connect and modify the configuration file
- Troubleshoot and resolve common issues for Remote Ethernet Devices (RED)
- Labs (30 mins)
- IPsec VPN Could Not Be Established (Scenario 1)
- IPsec VPN Could Not Be Established (Scenario 2)
- SSL VPN Could Not Be Established
16:00-16:15 Break
16:15-17:45 Module 4: Troubleshooting Authentication
- Troubleshoot issues with the captive portal
- Identify and resolve authentication issues
- Work through the authentication flow to troubleshoot and resolve issues
- Resolve issues with tokens being out of sync
- Labs (20 mins)
- User Cannot Authenticate
- User Not Authenticated with STAS
Day 2, Wednesday 24 February 2021
9:30-11:00 Module 5: Troubleshooting Web Protection and Application Control
- Explain the differences between DPI web scanning and the web proxy, and troubleshoot basic web policy issues
- Enable debug logging for DPI web scanning
- Troubleshoot web proxy performance issues
- Troubleshoot web categorization
- Troubleshoot application control policy issues
- Labs (20 mins)
- Site Incorrectly Blocked for User
- Application Not Working for User
11:00-11:15 Break
11:15-12:45 Module 6 Troubleshooting Synchronized Security
Identify and resolve issues registering XG Firewall with Sophos Central
- Troubleshooting and resolve issues with Security Heartbeat
- Resolve problems with Synchronized User Identity
- Investigate and resolve problems related to lateral movement protection
- Labs (20 mins)
- Cannot Register XG Firewall with Sophos Central
- Endpoint Cannot Establish a Heartbeat with XG Firewall Configure VPN network NATing
12:45-13:30 Break and Lunch
13:30- 14:40 Module 7: Troubleshooting Web Server Protection
- Perform basic web server protection configuration
- Troubleshoot and resolve static URL hardening errors
- Troubleshoot and resolve static form hardening errors
- Troubleshoot and resolve threat filter rule errors
- Identify whether web server authentication issues are caused by the XG Firewall or the web server
- Labs (10 mins)
- Error Using Webmail Server
14:40-15:35 Module 8: Troubleshooting Wireless Protection
- Troubleshoot the access point deployment process
- Resolve common wireless network issues Resolve common wireless network issues
- Identify common causes of performance issues and the configuration that can help resolve them
- List the ports used by wireless protection and how to connect to the access point to gather additional informationLabs (Authenticate users over a site to site VPN)
15:35-15:50 Break
15:50-17:20 Module 9 : Troubleshooting Email Protection
- Identify and resolve basic mail flow problems
- Troubleshoot virus emails that are not detected
- Troubleshoot false positive and false negative spam detections
- Identify the cause of, and resolve, missing quarantine digest issues
- Labs (30 mins)
- Cannot Receive Email
- Cannot Send Email
- Virus Email Delivered
17:20-18:00 Module 10: Troubleshooting Reporting and How to Get Help
- Troubleshoot issues with report generation
- Find help when you are unable to resolve issues yourself
The IT service desk department is tasked with troubleshooting a wide range of technical issues, such as malfunctioning devices, apps that crash, and installations that fail, to name just a few.
Onsite visits, one of the traditional IT troubleshooting methods for devices (offline or online), is no longer an option for many organizations due to the pandemic. Of course, onsite visits had their problems even before the coronavirus—they could be both time-consuming and costly for an organization. The productivity of your IT department is only as good as the resources they have to use each day and the ability to support multiple platforms and devices—on or off your network.
With all that said, BeyondTrust is pleased to announce the availability of version 21.1 of our leading Remote Support solution. This new version introduces functionalities that allow unattended and attended support for additional devices, including for Zebra devices and Raspberry Pi OS, as well as Jump Client-based discovery for Windows devices. These capabilities allow users to maintain, control, and manage their devices using the power of digital technology and computing. The BeyondTrust solution enables service desk teams to gain visibility into the status and performance of these devices with real-time insights about the health of the equipment, and to remotely fix issues as if they had the device in their hands.
In this release customers will also benefit from additional enhancements to our credentials Vault, including the ability to create personal accounts, as well as extending discovery and rotation in the Vault.
Below is a brief round-up of what is new with the release of version 21.1. For more information, you can also check out the release notes.
Jump Client Discovery & Rotation
Jump Clients can now perform discovery and rotation of local credentials (Windows only). This new functionality allows administrators to manage machines individually and set who has access to those machines, without the need to set up a local or shared account on the remote system. This feature complements the use of Jump Points in the network for domain-based rotation, while also allowing for more granular control over smaller groups of machines.
Raspberry Pi OS Support
BeyondTrust’s Secure Remote Access Jump Client Technology has added headless support for the Raspberry Pi OS. Thanks to its low power requirements and high processing capabilities, Raspberry Pi is often leveraged for specialized use cases, such as for equipment or machine monitoring of industrial applications, or even as an edge gateway solution. However, these devices need to be secured, maintained, and optimized, just like any other device.
BeyondTrust Remote Support enables Raspberry Pi secure access. This allowed privileged users to connect to more types of unattended systems, perform administrative actions, and secure who has access to manage these devices.
Zebra Device Support
Zebra devices are constantly on the move, or situated in remote locations, but are critical to empowering employee productivity. The process of supporting these devices—ensuring proper configurations, and effectiveness—has traditionally been time-consuming for help desks, as well as expensive and error-prone. BeyondTrust’s integration with Zebra Technologies gives IT service desk reps the power to access (either attended or unattended), troubleshot, and support Zebra devices to help minimize any potential down time.
BeyondTrust Vault
Included with Remote Support at no additional cost, the BeyondTrust Vault protects privileged credentials with discovery, management, rotation, auditing, and monitoring for any privileged account — from local or domain shared administrator, to a user’s personal admin account, even SSH keys, cloud and social media accounts.
Vault Link in Representative Console
The Desktop and Web Representative Consoles now include a top-level menu item labeled “Vault”, which has a link to the Vault interface in /login. This link enables users in each console to easily access Vault to check in or check out credentials when necessary, either during a session or on the user’s local machine.
Account Groups
Vault administrators can now organize Vault accounts into account groups, providing a better management experience. Admins can now assign account groups to group policies, rather than only individual Vault accounts. Additionally, Vault accounts can be assigned to an account group during the import process.
Personal Accounts
Remote Support users now have the ability to create private generic accounts in Vault. This functionality helps improve the productivity of users by allowing them to manage their own Vault accounts privately for use during remote sessions, or for quick access to other tools. Users can store Generic Credentials that are not managed, rotated, or visible to anyone else but themselves. These credentials are then useable for injection or check out by that user only.
Reporting
Vault reporting now provides more search options and the ability to directly download the report results. The reporting API has been updated to support this new functionality.
Assign Public Portals to Support Teams
BeyondTrust Remote Support allows you to create internal or external-facing web portals, or public-facing web sites. These portals allow your customers or employees to request support. Each portal can be configured with the organization’s branding and support processes. This includes customizing logos and allowing customers to start a BeyondTrust session using click-to-chat.
In this release, admins can now restrict what portals are used by a support team. This new functionality will create more granular control on how a team interacts with the sites.
Extended ADPU Smart Card Support Option
During a support session, a support representative may need to operate with administrative rights to effectively troubleshoot the remote computer. Within environments where security implementations require smart card use for authentication, BeyondTrust enables the support representative to pass administrative credentials to the remote computer from a smart card resident on the rep’s local system.
In this release, we have updated the Virtual Smart Card feature to support Extended APDU.
Taking Your Service Desk to the Next Level with BeyondTrust Remote Support
BeyondTrust Remote Support enables help desk teams to rapidly and securely access and troubleshoot any remote device, across any platform, located anywhere in the world—all via a single solution. The new features in version 20.1 expand what’s already possible with our solution, helping you empower, protect, and scale your service desk.
If you are already a customer, here’s how to get started with version 21.1: https://www.beyondtrust.com/docs/remote-support/getting-started/deployment/web/support-updates.htm
Source: BeyondTrust
Software is never done. Developers—from the biggest to the smallest—release regular updates to increase security, add new features, improve stability, and satisfy compliance mandates. These updates are typically referred to as “patches.”
Many managed service providers (MSPs) recognize patch management as one of the cornerstone capabilities of their service offerings. Maintaining patch management best practices ensures that software bugs or weaknesses are addressed to ensure a secure and optimally efficient computing environment.
As MSPs grow their business, the number of networks they must track grows in step, and the number of client software solutions requiring patch management can expand exponentially. Tracking which platforms each individual client runs, and then manually pushing updates to each one, creates time-intensive levels of extra complexity.
Datto RMM brings order to this critical process with automated patch management. Datto RMM is a fully-featured, secure, cloud-based remote monitoring and management platform which enables MSPs to remotely monitor, manage, and support every endpoint under contract, reducing cost and increasing service delivery efficiency.
With the automated patch management features of Datto RMM, MSPs can schedule updates to unfold at an optimum pace. Setting a timeline is important for security, because patch management isn’t simply a case of installing them the moment that they’re available from a vendor. Updating patches too often is not only time consuming but can lead to system instability. Even worse, the patches themselves can reveal themselves to have flaws—patch management best practices typically call for a grace period before installation in case a new bug is discovered.
Building Cyber Resilience
Cyber resilience, a concept that converges information security, business continuity, and organizational resilience, represents a business’s ability to continuously deliver on its intended outcome, despite adverse cyber events.
“Cyber resilience is the ultimate objective of building an information security program for any business of any size,” says Ryan Weeks, Chief Information Security Officer for Datto. “It’s intended to ensure the availability, integrity, and confidentiality of systems and data through an adverse event.”
According to Weeks, Cyber resilience is built on triple pillars: People, Processes, and Technology. One of the keys to reinforcing the process component of a security program is using technology to automate processes across systems at scale, where it makes sense to do so.
“Technology supports your people and processes to scale once they’re ready,” he explains. “Technology should also support those people and those processes in terms of automation. For a lot of your security processes—especially if you don’t want to hire a huge security team—you’re going to need to rely a lot on automation. Before you go out and start purchasing more technology, you need to look at your existing technology and how you can leverage that to increase your overall effectiveness.”
Activate Automation with Datto RMM
Datto RMM enables MSPs to increase their clients’ Cyber resilience. Using Datto RMM, patch updates can be tightly scheduled, which allows MSPs to track exactly when a patch has been installed. With that heightened level of control, MSPs can ensure that patches are only installed after any of its accompanying bugs have been worked out.
Datto RMM can also be integrated with Datto SIRIS, a reliable, all-in-one business continuity and disaster recovery (BCDR) solution built for MSPs to prevent data loss and minimize downtime for clients. With SIRIS in the mix, system instability that may have accompanied a new patch installation can be fixed quickly by restoring to a previous system version.
MSPs that have automated patch management in their toolkit can win back precious time, a valuable ally in the race to keep pace with a fast-changing landscape. “It doesn’t matter where you are in the Cyber Resilience spectrum—it’s a continuous improvement process,” Weeks concludes. “There will always be more work to do, because things are constantly changing and you need to adapt with that change.”
To learn more about automated patch management and increasing cyber resilience with Datto RMM, schedule a demo.
Source: Datto
As 2020 comes to a close, we look back on another year of increased attacks on managed service providers (MSPs), their small and medium business (SMB) clients, and the ecosystem of tools used within the community. In the face of these events, the MSP community showed the desire to tackle the underlying challenges with increased engagement, new peer forums, and attention in hardening their services. As we look forward to what 2021 might bring, now is a great time to develop or update your plan for managing cyber risk.
Understanding Threats
As a practitioner of risk management at Datto, I look at where we can best spend our time and what areas are the most important to address when it comes to cybersecurity. This is an important concept for MSPs to master in 2021 — it’s a continuous process, and requires adaptability as new threats emerge. While we care about knowing about the possible actors we may face, for example, cybercriminal organizations and loss scenarios such as ransomware within internal systems, it’s how these unfold that is one of the most important pieces to analyze. In this blog, we’ll focus on applying a process to a handful of techniques used by threat actors, surface mitigations, and provide a few tips on prioritization.
Let’s start with three key techniques threat actors have successfully utilized over the last few years as the starting point for our 2021 planning. In stepping through this process you can apply the same thinking to any number of techniques that you uniquely identify.
Phishing
Through the use of various sub-techniques such as malicious attachments and links, these are highly effective for actors in meeting their objectives. The weakness to understand here is the end user and being able to create a situation where they take an action that leads to credential or host compromise.
Stolen Credentials
Often in conjunction with phishing or compromising of a third party, the actor utilizes valid credentials to access websites and services, or to escalate privileges internally. The weakness here is identity and access management.
External Remote Services
MITRE’s ATT&CK framework states, “Remote services such as VPNs, Citrix, and other access mechanisms allow users to connect to internal enterprise network resources from external locations.” There are two potential weaknesses we will focus on for this exercise, user accounts, and vulnerabilities within the exposed services.
Defining Risk Mitigations
Now that we have a better understanding of the techniques used by bad actors and the underlying weaknesses, the next step is to populate a list of mitigations to help reduce the likelihood of these techniques being successful. The list of examples is not exhaustive and in practice should focus on the top ways to reduce risk based on deficiencies in your environment.
Phishing
- Email Security Services – provides additional security capabilities on top of email services above what Exchange and Gmail provide as a part of their base service.
- Security Awareness Training – provided in many forms of content, and phishing simulations.
- Endpoint Controls – if a malicious attachment or link is successful, ensuring the device is patched, services and configuration hardened and has a quality AV/EDR/MDR solution adds layers of security (and resilience!).
Stolen Credentials
- Multi-factor Authentication – ensuring all systems that support it have it enabled, even if you are on network.
- Password Manager – a number of mature solutions exist with the goals of not reusing passwords and having a secure means of generating them for use.
- Notifications – a fairly novel use of the built-in mechanism, and free, alert the user of new logins and device registrations. It’s understood that this is how FireEye detected the most recent breach.
External Remote Services
- Multi-factor Authentication – ensuring all systems that support it have it enabled, worth repeating twice as it is still a major driver of successful attacks on External Remote Services.
- Baseline configurations – expose the bare minimum number of services required, ensure they are vulnerability free, and that they are designed for external connectivity. It’s 2021 and we still have a large number of attacks attributed to Microsoft’s Remote Desktop Protocol being made externally available without a gateway.
- Vulnerability scanning – Whether it is a new vulnerability or a tech mistakenly opening up a vulnerable web service, regular perimeter scans serve as a continuous monitoring source that helps reduce the window that vulnerabilities are exposed to the internet.
Prioritizing the Action Plan
Arguably the hardest part of this exercise is the prioritization of activities in an action plan and finding the time to work through them. As we mentioned in this case study from 2019, don’t tackle the entire list but do put some thought into the activities and their value. While traditional risk management practices take into account financial loss in prioritization, below are a few less structured ways of approaching this problem.
- Attack Frequency – How many times have the techniques on your list been successfully used against your tech stack and user base? The more times something has occurred in the past is a good signal of future likelihood.
- Costs – Is the suggested mitigation a new tool, or is it using what you already have in new ways? Endpoint patching and configuration hardening, and enabling multi-factor authentication are still areas of improvement for MSPs. Even creative use of notifications can lead to more resilient outcomes.
- Business advantage – Determining if the required investment would be a business advantage in marketing and quality of managed services is a useful dimension. (Note: this should almost always be the case, some will just be more visible than others).
As we look at the steps we laid out above, you should walk away with the foundations to build a process that can be used and reused to harden your IT infrastructure. It’s best to set a goal of quarterly assessments at a minimum that review your program’s cyber risk in the face of trending attacks and focus on any new techniques being used.
Business continuity and disaster recovery (BCDR) solutions should serve as a foundational component in every partner’s technology stack. It’s imperative that in 2021, the MSP community’s trend of building in security practices continues. It’s through continuously assessing and improving cyber resiliency that the BCDR solutions will become the last card played rather than the only card.
Source: Datto
Cybersecurity is a fiercely competitive industry. It is unique in the information technology space in that we don’t just face competition from other vendors, we also have human adversaries, and they are the real competition. While our products and services must compete in the market against those from other vendors, it must never happen at the expense of our ability to protect our customers.
Recently, Sophos issued a reminder encouraging the cybersecurity industry to compete foremost on technology, not on threat intelligence. If we in the industry can align ourselves to rapidly share intelligence – ideally approaching real-time – businesses, governments and individuals will be able to defend themselves from adversaries in a more effective and efficient way. It could change the economics of cyber defense, giving defenders an advantage over attackers.
Over the past five years, Sophos has made significant advancements in improving both the usability and the predictiveness of our products, two technology dimensions that I believe vendors should compete in. In particular, we’ve delivered the following:
- An API-first design approach in all our Sophos Central enabled products to facilitate automation and integration with other tools and platforms that our customer and partners use in their operations
- Security operation workflows within our products that are heavily influenced by our Managed Threat Response (MTR) team, and which, as a result, are highly empathetic to practitioners
- Pervasive use throughout our portfolio of high-quality Machine Learning (ML) models that were jointly created by our Sophos AI and SophosLabs teams to help improve detection efficacy and to help focus the attention of security operators
Predictiveness and usability are just two important technology areas where competition among vendors will help raise the bar in the entire industry, but there are, of course, others. If vendors competed on innovative technology improvements like these, and shared threat intelligence, we would collectively make it harder in many ways for adversaries to succeed with their attacks. If we spread our knowledge, everyone could apply defenses to protect against subsequent recurring and/or similar attacks, which means attackers couldn’t use them over and over again – they’d be forced to change infrastructures or tactics, and this would be costly, increasing overall deterrence.
In a recent keynote I was invited to deliver at the Cyber Threat Alliance’s TIPS track at Virus Bulletin 2020, I explored ways we can incentivize enterprises, governments and security vendors to overcome the obstacles that are preventing them from sharing information about cyberthreats. The industry has gotten better, but there are obstacles to overcome. One of these obstacles is privacy, a very real issue that has hindered many for decades now. It’s time we stop hoarding and start looking at advancements in privacy-preserving technologies that can eliminate concerns and help move us forward. This is an important area of research for us as we continue to look for new ways to make operations more expensive and difficult for attackers by reducing the security industry’s obstacles to sharing.
“The closer the security industry gets to sharing and operationalizing threat intelligence in real-time, the more likely we are to meaningfully encumber our adversaries”.
Earlier I mentioned predictiveness as a prime example of a technology that vendors ought to compete on. One of the key methods of improving predictiveness is derived from an exhaustive understanding of the threat landscape, and this is often a function of access to data, whether that is malware samples, phishing campaigns, ransomware characteristics, adversary behaviors, or attack tools.
Sophos has a very large surface area, so we have abundant access to such data. More importantly, SophosLabs and Sophos AI have massive processing pipelines to make sense of all the data we see every day, and our MTR service often gives us very early glimpses into novel threats as they are in their initial (even developmental) stages.
Not all security vendors have uniform access to this kind of data, even if they have access to well-known industry watering holes like VirusTotal. This means that there is not even-footing for vendors or independent researchers to create technology innovations, like more high-quality predictive ML models, because sharing still has barriers. As a measure to help overcome this, I’m excited to announce a joint effort between SophosAI and ReversingLabs, called SOREL-20M, to provide the first production scale malware research dataset with the sole goal of driving industry-wide improvements in security.
Some readers may wonder at the sense of a security company releasing a trove of malware. Rest assured, the samples have been disarmed to prevent accidental execution, and an attacker would have less expensive options available to them than rearming these components. In general, it is essential for defenders to have access to these types of offensive-tools whether in the form of malware samples, or the many tools and frameworks that attackers can use for pre- and post-exploitation. You can read more about this joint venture and the benefits it will bring on our dedicated SophosAI page established, in part, to serve as a platform for these types of data sharing projects like SOREL-20M.
This is just the beginning of more announcements we’re planning about our threat intelligence and tools sharing initiatives, as well as our unfolding philosophy behind the efforts – all in the effort to transform the industry with transparency and openness to better arm defenders and drive the industry forward. Please stay tuned.
Source: Sophos
Across verticals, organizations are experiencing sweeping technological changes.
While many businesses plan proactively for such disruptions and embrace such changes strategically, there will always be times when they get taken by surprise. The sudden and forceful digital transformation (DX) brought about by the COVID-19 pandemic remains a case in point.
In an effort to keep pace with the new normal, several businesses – notably those in healthcare, education, and retail – have embraced remote working and cloud-delivered digital business models, shifting their business workloads into multiple clouds and adopting SaaS applications to emerge more competitive and customer-centric.
As a result, IT leaders and CXOs at several companies are busy virtualizing data centers, corporate offices, and remote sites in order to adopt and grow the distributed enterprise model, which is the first requirement for a successful DX strategy.
However, as organizations implement these fundamental improvements, many find traditional networking architecture to be a major DX challenge. And with the traditional edge network disappearing rapidly – giving way to software-defined Wide Area Networking (SD-WAN) – traditional cybersecurity also warrants a rethink.
By leveraging SD-WAN solutions as part of an interconnected cybersecurity system, your organization can take full advantage of digital transformation and achieve cyber resilience for these changing times.
Here’s how your organization stands to benefit from a secure SD-WAN implementation:
1. Drive performance and improve traffic visibility to reap benefits beyond cost savings
In the early days of SD-WAN, arguments in favor of the technology largely focused on replacing MPLS networks to achieve operating and connectivity cost savings.
In fact, secure SD-WAN delivers a lot more than just a better bottom line. It helps better prioritize mission-critical business applications and maintains session quality for traffic for high-priority solutions such as Office 365 email, CRM, video, and VoIP/unified communications usage.
This is one area where XG Firewall and Sophos Synchronized Security provide an incredible advantage thanks to application visibility, routing, and quality-of-service for key applications.
Synchronized Application Control provides 100% visibility into networked applications, providing a significant advantage in identifying mission-critical applications across distributed networks. Synchronized SD-WAN, a Synchronized Security feature, leverages the added clarity and reliability of application identification that comes with the sharing of Synchronized Application Control information between Sophos-managed endpoints and XG Firewall.
2. Go multi-cloud
With secure SD-WAN, a digital enterprise can adopt a multi-cloud strategy to enhance application availability, performance, and end-user experience.
For example, educational institutions can keep pace with changing educational technologies and roll out rich training and learning resources over multiple clouds. Similarly, a healthcare organization can easily enable the use of new healthcare technologies and applications such as telehealth, cloud-based diagnostic solutions, and telemedicine.
While SD-WAN for a multi-cloud implementation has several industry use-cases, it needs to be noted that any DX initiative requires deploying the right cloud security. According to The State of Cloud Security 2020 survey, 70% of organizations fall victim to public cloud cybersecurity incidents, which includes ransomware, malware attacks, exposed data, compromised accounts, and cryptojacking attempts.
Although SD-WAN networking solutions offer some built-in security, a growing number of organizations are looking to integrate advanced SD-WAN security capabilities. This is where Sophos XG firewall offers a powerful, flexible network connectivity and security solution for every type of network – including public, private, and hybrid clouds for a geographically distributed SD-WAN scenario.
3. Make your network more agile
The biggest motivation driving most of the ongoing DX initiatives is building networks that can scale rapidly to meet the changing needs of an organization, which is why traditional hub-and-spoke model can’t work any longer. Many business no longer see the need for monolithic data centers and larger connectivity pipes to build a single nodal corporate network that enables remote sites and branch offices.
Instead, organizations are increasingly turning to cloud-native applications and deploying to multi-cloud environments such as Amazon AWS, Microsoft Azure, and Google Cloud Platform to make resources easily available to remote workers, branch offices, partners, and customers without having to backhaul the traffic to a centralized data center.
By abstracting software and virtual services from the underlying physical infrastructure, SD-WAN enables greater degrees of flexibility and automation, with reduced complexity to make necessary network changes. Sophos XG Firewall and SD-RED devices enable industries to connect remote offices, devices, and cloud resources easily and securely.
And the Sophos SD-WAN security solution facilitates zero-touch edge and branch connectivity, with secure VPN tunnels and enterprise-grade encryption to securely connect remote sites and branch office locations in a distributed network setup.

Conclusion
A highly flexible and extensible network infrastructure is vital to meet the demands of ongoing DX efforts – and to handle the business and customer needs of tomorrow. As more organizations prepare to take advantage of SD-WAN infrastructure, securing the new network, SaaS applications, and cloud workloads emerge as security priorities. Sophos is committed to enabling SD-WAN led digital transformation for its customers and continues to invest in SD-WAN security, orchestration, and connectivity capabilities.
Visit Sophos.com/SD-WAN to learn more.
Source: Sophos
The new normal. Unprecedented times.
While perhaps the most overused buzzwords in 2020, these terms represent the challenges shared by every organization in facing the difficult realities related to the pandemic.
As a leader in the cybersecurity industry, BeyondTrust is accustomed to a fast pace and regularly adapting to meet new challenges. But 2020 demanded that we evolve in new ways. From the early days of the pandemic, BeyondTrust has remain committed to providing a supportive, flexible, and safe working environment for more than 1,000 employees globally. This has required us to reconsider the ways we connect, collaborate, and support each other while serving our customers.
The BeyondTrust culture is rooted in our Core Values, which existed long before 2020, and they helped us guide the way forward. Enabling remote working was only the start of our pursuit to maintain an exceptional employee experience, despite the challenges.
A Year of New Ideas
The BeyondTrust Culture Committee is a cross-functional, employee-driven group that is tasked with creating positive employee experiences and driving engagement. Just like the cybersecurity industry in which we operate, 2020 demanded that we adapt. During the pandemic, the team has remained focused on providing virtual opportunities for employees to stay connected.
This year, BeyondTrust launched the following initiatives:
- Buddy Program: All new hires are paired with a “buddy” to help them adjust to the new role, as well as provide a familiar face at virtual events and a resource to help foster personal connections.
- Mindfulness & Fitness Programs: These virtual sessions included meditation and yoga, wellness speakers, remote workouts, and applying ‘coffee break’ reminders to promote wellbeing and ward off work-from-home burnout.
- Employee “Lived Experiences” Sharing: Through our Diversity & Inclusion efforts, we found it extremely important and beneficial to give our employees to connect and share their own personal stories related to race, gender, and more.
In a socially distant world, these initiatives have enabled us to not feel remote from each other, despite the physical separation we are experiencing from our colleagues.
Career Development Opportunities
BeyondTrust employees were still seeking opportunities to grow their professional skill set, but with in-person training events and face-to-face meetings off the table, the HR team and the Culture Committee partnered and pivoted to offer virtual alternatives. The following programs were launched 2020:
- Mentorship Program: The July pilot included 12 pairs of employees across all levels and geographic locations, including our CEO, who is presently mentoring one of our US Sales Development Representative Managers. The program will continue formally in January 2021, with over 10% of our employee population interested in becoming mentors and mentees.
- BeyondLearning: An online learning platform available to all employees globally, with access to thousands of courses. From Microsoft Excel to Virtual Work Environments, BeyondLearning provides opportunities for our employees to grow within their role and seek knowledge in other areas of interest.
- Leadership Development Course: Developed in partnership with the Center for Creative Leadership (CCL), the Frontline Leadership Impact course was initially piloted in late 2019 and was due to officially launch in April 2020. Despite the challenges that our employees faced throughout 2020, more than over 160 employees globally participated in the program. Read the Case Study here.
- Leadership Mastermind Program: Utilizing innovative leadership techniques in collaboration with our partner Adaptive Growth, BeyondTrust began embedding appreciative inquiry and design thinking in a leadership training pilot.
Employee Engagement
The first pillar of our Culture Committee is Employee Engagement, where we focus on creating an environment of inclusion and belonging. In 2020, this team:
- Created an organization-wide Microsoft Teams group called “BT Universe,” with a number of affinity channels where employees can informally connect on a variety of topics
- Launched a newsletter, the “Culture Chronicle,” to provide updates on what is happening in the business and where employees can get involved in culture initiatives
- Began a quarterly book club, with the first book and discussions facilitated by our CEO. These meetings provide meaningful opportunities to informally network and share ideas.
BeyondGiving
The Culture Committee also leads the BeyondGiving program, providing volunteer opportunities and other ways to give back. In 2020, BeyondGiving recipients included:
- CALM – Suicide prevention organization in the UK
- Fire Disaster Relief charities in Australia
- Leukemia and Lymphoma Society
- “Movember” in support of Men’s Mental Health
- A variety of food banks in the local communities where we have offices
Diversity & Inclusion (D&I)
The Culture Committee launched our D&I program at the end of 2019, and accelerated efforts after the death of George Floyd and resulting protests across the US and around the world this year. Our D&I efforts and accomplishments included:
- A quarterly speaker series with experts in social and racial justice
- Monthly sharing of lived experiences of our employees
- Recognition as one of the Diversity in Tech Employers of the Year by WomenTech Network
- The development of an Anti-Racism Task Force charged with assessing opportunities for promoting anti-racism and building greater inclusion in our company and in our communities
Expanding on the success of all these initiatives will remain a priority into 2021 and beyond, as the organization continues to seek new ways to elevate our employee experience.
Source: BeyondTrust
In today’s global economy, businesses must be compliant with standards established by various countries so they can service customers around the world.
One such regulation you can’t afford to ignore is the GDPR (General Data Protection Regulation), which is the core of Europe’s digital privacy legislation.
The GDPR applies to any organization that operates within the EU or offers goods or services to customers based in the EU.
These companies need to ensure that personal data is gathered legally and under strict conditions, as well as protected from misuse and exploitation.
Violation of GDPR rules can result in hefty fines, currently set at up to €20 million ($23.3 million), or 4% of a company’s worldwide annual revenue from the preceding financial year, whichever amount is higher.
To ensure that you’re adhering to GDPR guidelines, you need to protect your customers’ information. Here are six technologies that can help you stay compliant:
1. Managed File Transfer (MFT)
Managed file transfer (MFT) solutions use industry-standard network protocols and encryption methods to streamline the management of company data.
These solutions automate data transfer across the organization, network, systems, applications, partners, and cloud environments using a centralized interface.
To use an MFT solution, you’d first securely send a file through an MFT program or email plugin. The software then encrypts the file and delivers it to the intended recipients. Finally, the recipients will decrypt the files so they can read the content.
MFT applications help ensure the secure collection, movement, and usage of personally identifiable data by providing organizations with a holistic view of their data movement processes. Some key security-enhancing capabilities to look for include data encryption, access rights management, and full audit trails.
Related Reading: What is Managed File Transfer (MFT)?
2. Automated data protection processes
You can use these solutions to automate data protection processes and gain better visibility into the movement of sensitive information in and out of your organization. This helps eliminate inefficiencies, errors, and delays caused by manual procedures.
Many of these solutions also offer protection against data loss and data theft while providing enhanced visibility into data breaches.
To make automation work for your business, first define and standardize procedural and technological controls for protecting personal data.
Based on your business model and criteria, you can then select a solution that offers the right features, such as encryption, multi-factor authentication, and pseudonymization to implement the automation.
Related Reading: 5 Benefits of Automation
3. Privacy impact assessments
These technologies help organizations evaluate the potential impact that their business decisions will have on users’ data privacy. Companies can be clued into potential violations early on, so they can avoid issues down the road.
Such assessments are particularly useful in supporting new product launches, geographic expansions, and mergers and acquisition activities.
Organizations can identify high-risk data that’s being collected, assess gaps in their compliance efforts, remediate areas of concern, and create an audit trail to stay compliant.
4. Individual rights compliance
Since the GDPR grants individual users the rights over how businesses use their data, you need the tools that will enable customers to enact the right to access their data, restrict or object to the processing of their data, and data portability.
These solutions allow you to create custom individual rights request forms, provide notifications, and set automated reporting to meet individual rights requirements.
You can identify the storage locations of the data requested by users and fulfill requests within the required 30-day time frame without interfering existing business processes.
Related Reading: What You Need to Know to Prepare for GDPR Compliance
5. Data mapping
Staying GDPR compliant can be particularly challenging for organizations that don’t have an exacting data management practice.
This is because a large part of GDPR focuses on justifying the type and scope of data being collected and demonstrating compliance in a timely manner. Instead of being data processors, organizations need to act as data controllers.
Data mapping solutions help you understand what data your organization is collecting, where the information is being stored, and who has access to it.
With such knowledge, you can determine what additional obligations may apply to the data based on sensitivity, geography, or other factors.
6. Pseudonymization technologies
These technologies allow you to implement a data-masking tactic, which is referenced in the actual text of the regulation.
The technologies work by storing an individual’s information in many separate files and under many different names.
As a result, hackers can’t get their hands on customers’ full information by simply stealing one file or reassembling personally identifiable information from multiple sources.
7. Data classification
The first step to a strong data protection posture is data classification. It provides a firm foundation towards onward compliance, and integrating data classification with necessary data protection tools such as DLP, rights management, encryption and many more will elevate your data protection strategy.
The industry-leading Boldon James Classifier is key to GDPR compliance, as it is designed to reduce data loss incidents and improve DLP solution effectiveness. Visual labelling enhances your workforce’s awareness of the value of the data they are using, whilst metadata labels facilitate more effective application of data security, data management and retention policies.
Related reading: Classification By Design: The Foundation Of Effective Data Protection Compliance
Final thoughts
A data breach will not only cost you a hefty penalty but also tarnish your reputation, erode trust with customers, and impact your long-term profitability.
Investing in the right technologies for GDPR compliance will pay for itself by helping you implement the right measures in risk management and analytics, regulatory compliance, and auditing and reporting so you can stay secure and compliant.
Source: Boldon James
Managed service providers (MSPs) have #giftgoals too, so we’ve put together a “Holiday Wish List” for MSPs with gift ideas to help them maximize efficiencies, deliver great customer service, protect clients from cyber threats and work smarter, not harder, in 2021 and beyond.
- Universal Two-Factor Authentication (2FA) would bring Joy to the World. With threat actors finding ways to bypass preventative measures, 2FA becomes more critical. To be as effective as possible, clients that deploy it on both workstations and server logins gain an extra layer of protection.
- Let us grow, let us grow, let us grow! MSPs become part of a growing community of MSPs when they partner with Datto. Beyond just dependable technology, Datto provides access to the industry’s best resources, education, and marketing tools to grow and scale their business.
- It’s beginning to look a lot like efficiency. Efficiency is the name of the game for any MSP. Gain access to valuable tools and insight with Autotask PSA and Datto RMM, optimizing service delivery, increasing productivity, and finding more time for billable tasks.
- I’m dreaming of no downtime. Businesses have had a tough year, and what better way to improve in 2021 than ensuring they never have to be without their mission-critical systems and data? Give your clients peace of mind with a business continuity solution to get them back up in running in the event of downtime.
- Silver and Gold. Building stronger, trusted relationships with clients is one of the best gifts to receive. MSPs can show clients they deliver exceptional value with quarterly business reviews and detailed performance reporting.
- Clients who *believe* in the power of backup. MSPs know how important backup is when disaster strikes. The best way to protect servers, files, PCs, and SaaS applications all tailored to a client’s needs is with Datto Unified Continuity solutions.
- It’s the most wonderful time of the year for SMBs to migrate to the cloud. Clients that migrate to the cloud see increased efficiencies, more productivity, and cost savings. Plus, bundle in Datto SaaS Protection to back it up, and you’ve just raised your margin on a recurring service.
- All is calm, all is bright. SMBs who invest in data protection and take the security recommendations MSPs make bring their MSPs peace of mind. Datto can help MSPs educate clients about the importance of continuity solutions to strengthen security measures.
- All I want for Christmas is a clear ticket queue. MSPs had a busy year with a near-complete shift to remote working. Give the gift of an empty ticket queue with an intuitive ticket user interface that enables immediate action and resolves issues quickly with Autotask PSA.
- I’ll Be Home for Christmas. Wherever home is, the simple joys of celebrating with loved ones is on everyone’s wish list this year.
Source: Datto
We at Acunetix and Invicti are deeply concerned with the aftermath of the SolarWinds hack and offer our deepest commiserations to all the security personnel who are facing this situation just before Christmas, and to SolarWinds themselves who have been an unwilling agent to the compromise of more than 18,000 organizations.
At the same time, we would like to reassure our customers, partners, and prospects that we are not a customer of SolarWinds and are therefore not in any way affected by this hack. As always, we continue to take the utmost care to ensure that our on-premises and online software and our update download servers are not compromised in any way.
What Happened at SolarWinds?
If you’re not up to date on the news: The SolarWinds Orion network monitoring software, used by more than 18,000 organizations all over the world, was compromised several months ago. An update, downloadable from the SolarWinds update server, was poisoned with a malicious backdoor. This backdoor allowed unknown threat actors to spy on SolarWinds Orion customers and potentially control their systems remotely or escalate into their networks.
The original attack vector remains unknown but there are hints that might give us a clue of what originally happened. Since the first traces of backdoor being used date back to March 2020, it is very probable that SolarWinds was hacked at the beginning of 2020 or in late 2019. This is in line with certain Tweets that suggest that SolarWinds had an open repository on GitHub and used weak passwords. This would not be surprising at all. Openly accessible repositories and exposed databases account for some of the biggest hacks in recent years and common password vulnerabilities are often the underlying cause of major break-ins.
Another potential vector is that the SolarWinds Office 365 account was supposedly compromised, according to information that SolarWinds received from Microsoft. SolarWinds believes that data contained in emails might have allowed the attackers to gain access to other systems (which also suggests poor email culture – you should not use email to send sensitive data). This yet again suggests that it might have been a weak password policy that has been the underlying cause of the breach. Remember, it just takes one user with a weak password for a malicious hacker to enter.
Conclusions from the SolarWinds Hack
While the hack itself is most probably nothing out of the ordinary, what is very much out of the ordinary in this situation is the fact how long it has remained undiscovered. This is what suggests that while the vulnerability might have been trivial, the exploitation itself was not. The attackers, whoever they really are, took a great deal of care to remain undetected in all the infiltrated networks. This is why it is believed that it must have been a major intelligence operation.
This leads to the conclusion that even if you consider a vulnerability or an asset just a minor one, it may be used by the attacker to escalate deeper into your systems – for example, a simple SQL injection on a database that contains no personal data may lead to a complete system compromise. What’s even worse, the attacker may then use your compromised systems to perform an attack on others – an attack that may be even harder to detect, such as in the case of SolarWinds.
Another important conclusion from this hack is that if SolarWinds Orion was a cloud product, the hack would not be possible because there would be no downloadable updates. If the organizations had no internal networks (if they had all their applications in the cloud) and they never needed Orion in the first place, it would not happen either. This may be yet another nudge for organizations to move their assets to the cloud. However, they must not forget that the cloud also has its security concerns. And one of these security concerns is the fact that all cloud apps are web applications.
How Can Acunetix Help?
Since we deal with web application security, Acunetix cannot help organizations with securing their legacy applications and internal networks, such as those that have been infiltrated by the backdoor in SolarWinds Orion. However, Acunetix is an indispensable tool for when you move those applications to the cloud – we also check for exposed databases and weak passwords. To keep all your web assets secure, your best bet is to start with a web vulnerability scanner.
Sophos published its newest threat report. The report encapsulates the work of multiple teams within Sophos, including SophosLabs, Cloud Security, Data Science, and Rapid Response. The daily work of these and other groups in the company help protect Sophos’ customers from an ever-increasing variety and intensity of acts of malfeasance targeting their computer systems and data.
The past year presented the world with challenges that humans haven’t faced in more than a century. While the internet gave us the ability to cope with a global pandemic better than was possible in 1918, we faced new complications in 2020 from ransomware, cryptojackers, and digital theft targeting every conceivable platform – even security appliances.
In our threat report (which you can download here), we’ve attempted to bring a bit of order to the chaos of the past year. We’ve structured the report to discuss the four key domains in which we focused our protection efforts in 2020 and which will guide our planning into 2021:
- The increasingly dire threat of ransomware in all its new forms
- Conventional Windows malware, including tools criminals use to steal data and deliver malicious payloads
- Unconventional malware that targets platforms not traditionally thought of as part of an organization’s attack surface
- How the pandemic impacted attacker behavior as much as how we now work, play, shop, go to school, and socialize – and the challenges involved in protecting those functions.
This was the year that ransomware, for instance, decided that merely encrypting our data and holding it hostage wasn’t quite evil enough. Threat actors discovered that even organizations with the best backups still are willing to pay big money to prevent sensitive data being leaked to the world, turning ransomware attacks into a hybrid hostage-extortion crisis.
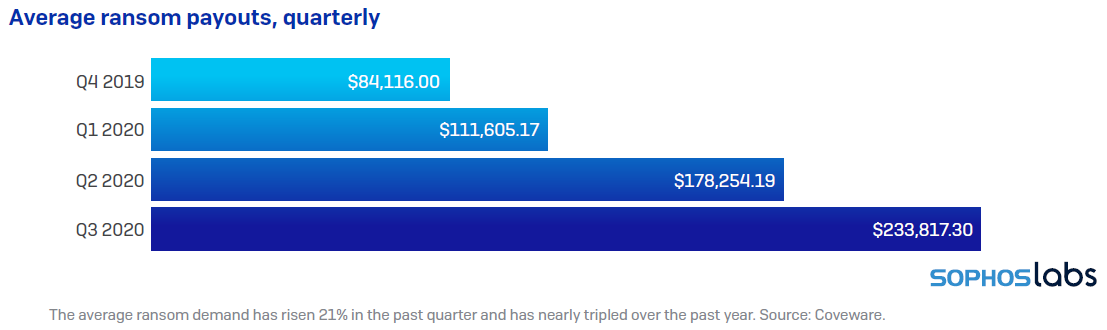
It was also a year when threat actors pushed the ransomware envelope in another way: Initial ransom demands skyrocketed into the millions of dollars per incident, though some criminals made it clear they were willing to bargain with their victims.
As office workers shifted into a work-from-home, lockdown mode, businesses had to devise new ways to provide their employees with secure access into internal computer systems, extending the enterprise perimeter to encapsulate thousands of homes. And as organizations rapidly deployed these remote-access features, attackers devised new ways to use them against us, targeting our VPNs and other internet-facing services and devices for special attention.
For instance, in incidents where we were called in to investigate, we discovered that Windows’s built-in RDP was not only targeted as an initial point of access, but once threat actors gained a foothold inside the perimeter, they began to take advantage of RDP to navigate laterally within an organization.
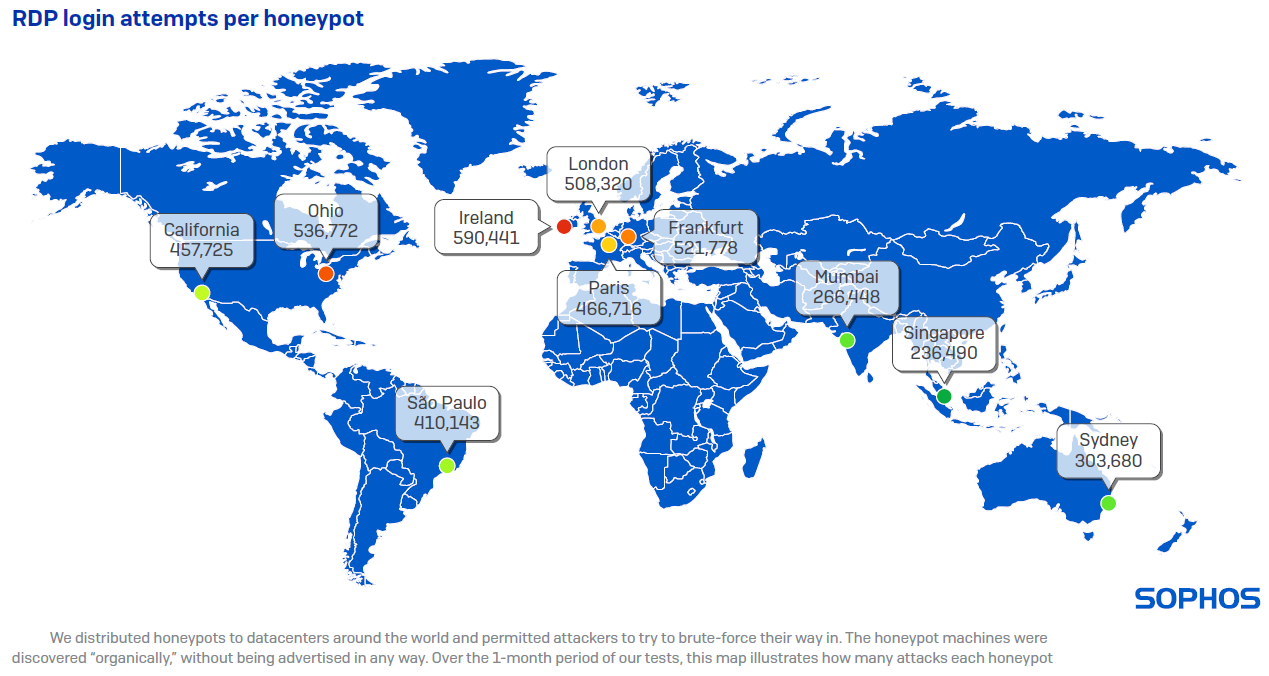
When the Sophos Rapid Response team investigates incidents, they attempt to determine the root cause of attacks. Beyond RDP, the Rapid Response team have also found that attackers increasingly make use of mundane, conventional, common malware to deliver ransomware and other more serious payloads. Any detection, no matter how banal, may be the precursor to a devastating attack.
Attackers also put effort into targeting attacks at technology not traditionally considered part of the attack surface: Networked IoT devices, firewalls, Linux servers, and Macs did not evade the attention of criminals who leveraged vulnerabilities to install cryptominers or other malicious code. And the attackers who did target Windows servers and workstations increasingly employ the tools created by the security industry to probe for or exploit weaknesses, using our analysis tools against us.
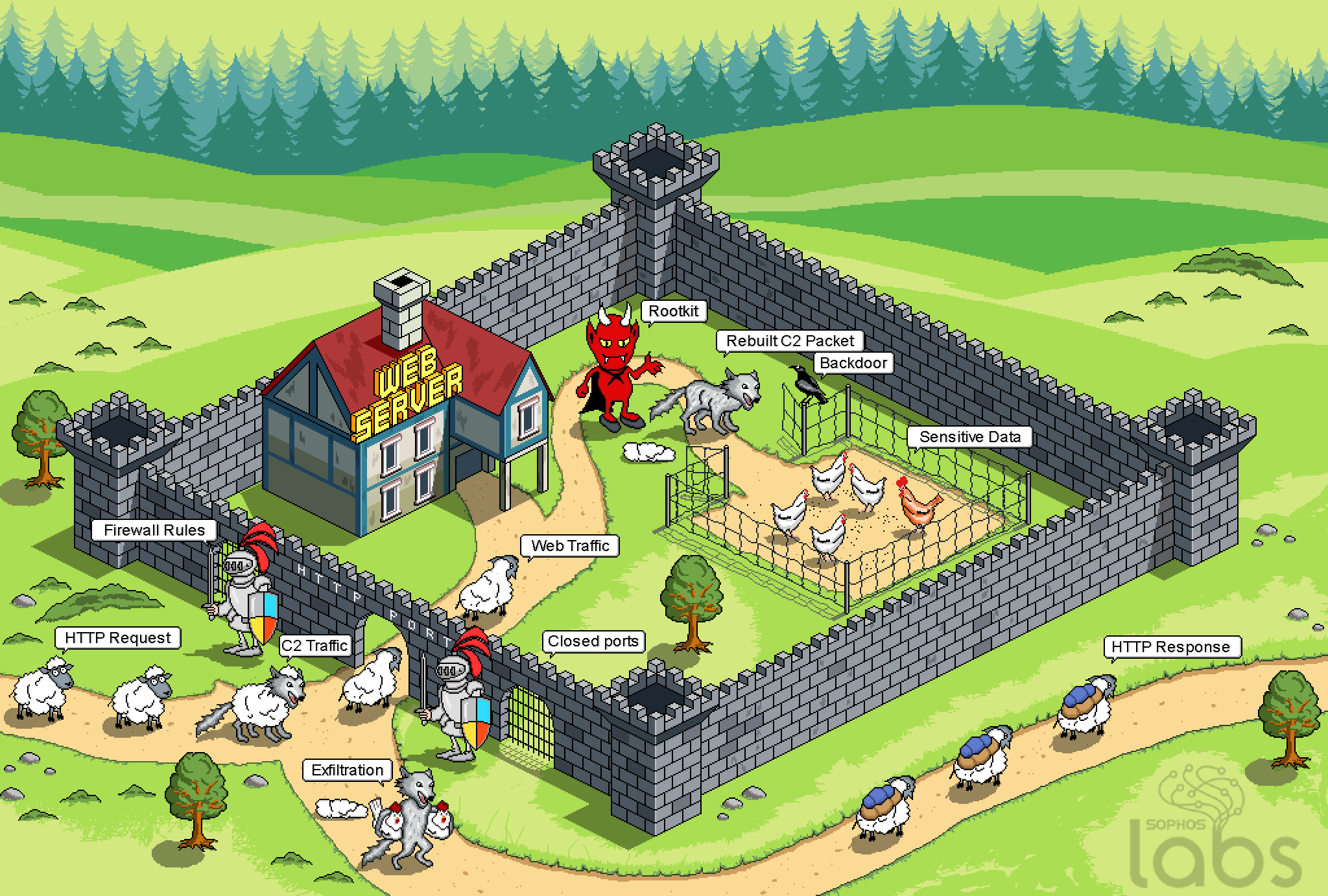
The pandemic factored into everything we did in information security this year, and it sharpened one point: In times of crisis, when systems all around us are under stress, protecting what still works is vitally important to maintaining our ability to survive and thrive. Under attack from all sides, the information security industry and many thousands of practitioners set aside competition and stepped up to work together, as a community, to push back against the darkness.
Source: Sophos
Sophos Home provides the industry’s best protection against ransomware, viruses, malware, exploits, and more. It’s the same enterprise-grade protection available in our business products, which protect millions of computers in the world’s most valuable organizations.
And the newly-launched Sophos Home mobile management app – available now for both iOS and Android – makes remotely monitoring and managing your loved one’s devices easier and more effective than ever before. You’ll enjoy being able to access your Sophos Home dashboard from your mobile device without having to use your computer.
Features include…
- Instant notifications and alerts of new threats
- Remote scanning of computers, regardless of location
- Easy management of device protection settings
- Built-in phone security features such as Face ID, fingerprint scanning, and passcodes
- Optional two-factor authentication for an extra layer of security
- Live chat with customer support to help you tackle more difficult challenges
The Sophos Home mobile management app is available to all Sophos Home Premium customers and anyone trying our free 30-day Sophos Home trial.
Ready to get started? You can download the Sophos Home Mobile Management app at the Apple App Store or Google Play Store.
Don’t already have a Sophos Home Premium account? Head to home.sophos.com to start a 30-day free trial.
Source: Sophos