News
[vc_row][vc_column][vc_column_text]
Over the past two years, organizations worldwide have increased the velocity with which they are moving operations into the cloud and adopting and maturing DevOps, edge computing, edge security, IoT technologies, and a multitude of other digital transformation initiatives.
The long-time mindset of perimeter-focused security is clearly no longer tenable in this environment. Fortunately, the understanding that IT environments must evolve to embrace and embody zero trust principles is now almost universal. With that said, zero trust is not an effective strategy for every use case, or even for every company.
[/vc_column_text][vc_column_text]
Learn more about Zero Trust and Endpoint Privileges
[/vc_column_text][vc_button button_color=”color-210407″ size=”btn-lg” radius=”btn-round” border_width=”0″ link=”url:https%3A%2F%2Fwww.beyondtrust.com%2Fblog%2Fentry%2Fprivilege-escalation-attack-defense-explained%2F%3Futm_source%3DNSS-NewsBlog%26utm_medium%3DArticle%26utm_id%3DNSS||target:%20_blank|”]Privilege Escalation Attack and Defense Explained[/vc_button][vc_button button_color=”color-210407″ size=”btn-lg” radius=”btn-round” border_width=”0″ link=”url:https%3A%2F%2Fwww.beyondtrust.com%2Fresources%2Fwhitepapers%2Fmicrosoft-vulnerability-report%2F%3Futm_source%3DNSS-NewsBlog%26utm_medium%3DArticle%26utm_id%3DNSS||target:%20_blank|”]Microsoft Vulnerabilities Report 2021[/vc_button][vc_button button_color=”color-210407″ size=”btn-lg” radius=”btn-round” border_width=”0″ link=”url:https%3A%2F%2Fwww.beyondtrust.com%2Fresources%2Fwhitepapers%2Fzero-trust-approach-to-windows-mac-endpoint-security%2F%3Futm_source%3DNSS-NewsBlog%26utm_medium%3DArticle%26utm_id%3DNSS||target:%20_blank|”]A Zero Trust Approach to Windows & Mac Endpoint Security[/vc_button][vc_button button_color=”color-210407″ size=”btn-lg” radius=”btn-round” border_width=”0″ link=”url:https%3A%2F%2Fwww.beyondtrust.com%2Fpassword-management%2F%3Futm_source%3DNSS-NewsBlog%26utm_medium%3DArticle%26utm_id%3DNSS||target:%20_blank|”]A Complete Password Management Solution[/vc_button][vc_button button_color=”color-210407″ size=”btn-lg” radius=”btn-round” border_width=”0″ link=”url:https%3A%2F%2Fwww.beyondtrust.com%2Fsecure-remote-access%2F%3Futm_source%3DNSS-NewsBlog%26utm_medium%3DArticle%26utm_id%3DNSS||target:%20_blank|”]Secure Remote Access Solutions[/vc_button][vc_empty_space empty_h=”2″][vc_column_text]
Source: BeyondTrust
[/vc_column_text][/vc_column][/vc_row]
Sophos is thrilled to be awarded Security Vendor of the Year in the European IT & Software Excellence Awards 2021. Now in their 12th year, the awards have been designed to recognise and reward excellence in European software development, IT and Telecoms solutions. Carl Friedmann, Editor at IT Europa, commented:
In what was one of the most crowded award categories, Sophos impressed the judges with the depth and breadth of its offering including a strong managed threat detection and response solution well suited to the needs of the channel.
The awards are voted for by a panel of judges including IT Europa’s editor, Carl Friedmann, and Jessica Figueras, vice chair of the UK Cyber Security Council. Jessica works with start-ups and scale-ups on growth strategy and advises UK Government on technology and policy issues relating to online harms and security.
Jason Ellis, vice president EMEA channel at Sophos shared his delight on this prestigious award win:
Sophos is honoured to win the coveted Security Vendor of the Year 2021 at the European IT and Software Excellence Awards. The extraordinarily high levels of complex ransomware and other cybercrimes has accelerated the need for effective, comprehensive cybersecurity for businesses of all sizes, and this award recognises our dedication to provide the best and most complete set of cybersecurity solutions in the market.
The win follows a year of exceptional innovation. Sophos is leading the industry through integration of AI into its products and services. One of the biggest product evolutions this year is the new Sophos Adaptive Cybersecurity Ecosystem (ACE), an open security architecture that optimises threat prevention, detection and response. Sophos ACE leverages automation and analytics, as well as the collective input of Sophos products, partners, customers, developers, and other security industry vendors, to create protection that continuously improves – a virtuous cycle that is constantly learning and advancing.
In addition, Sophos launched the industry’s only extended detection and response (XDR) solution that synchronizes native endpoint, server, firewall, and email security in 2021.

Source: Sophos
The UK-based PC PRO Excellence Awards are held annually to celebrate the best manufacturers and the best products available.
Whilst the ‘Manufacturer of the Year’ awards are selected by PC PRO readers, the ‘Product of the Year’ awards are selected from the hundreds of products that have been reviewed by the PC PRO team, together with their sister brands, IT Pro and Expert Reviews. We’re told the voting in these categories can involve hot debates within the editorial team, and only the standout products are selected.
The Sophos XG 230 (Rev.2) earned the top spot in the prestigious ‘Business Hardware of the Year’ category, competing with over a hundred other business-focused products.

IT Pro reviewed the XG 230, including the initial setup with Sophos Firewall OS (SFOS), earlier this year, when it was awarded an Editor’s Choice 5-Star rating.
The review highlights the following features:
- Flexible connectivity – built-in and add-on via Flexi Port modules
- Power redundancy option and failover via built-in bypass ports
- Ease of setup using the installation wizard
- Visibility provided by the Control Centre
- Zone-based security policies
- Extensive Web filtering categorization options
- Threat detection using Sophos Sandstorm (now part of Zero-Day Protection)
- Integration in Sophos Central, both for management, and cross-product threat detection and mitigation via the Sophos Security Heartbeat™.
Dave Mitchell, who conducted the review, was a key advocate for the Sophos win, describing our product as follows:
Sophos’ XG 230 Rev.2 impressed us mightily as this no-compromises gateway appliance is a cinch to deploy and offers a remarkable range of security measures for the price. A huge firewall throughput means it can easily keep up with a heavy demand and total integration with the Sophos Central cloud service adds extra levels of versatility.
You can read Dave Mitchell’s full review on the IT Pro website.
This review was conducted prior to the release of our new XGS Series hardware range, which offer all of the above features and many more.
Source: Sophos
[vc_row][vc_column][vc_column_text]
November 1, Athens Greece – NSS, a well established international value-added distributor of leading cutting-edge IT solutions, announced its strategic partnership with HelpSystems, a US based Information Technology and Software Vendor, and a people-first software company focused on helping exceptional organizations build a better IT.
[/vc_column_text][/vc_column][/vc_row][vc_row row_height_percent=”0″ back_color=”color-lxmt” overlay_alpha=”50″ gutter_size=”3″ column_width_percent=”100″ shift_y=”0″ z_index=”0″ shape_dividers=””][vc_column width=”1/1″][vc_column_text]Paolo Cappello, Managing Director of International Development responsible for leading growth in the LATAM, EMEA, and APAC markets stated that “At HelpSystems we’re on a journey to help organizations everywhere Build a Better IT™. Our security and automation software simplifies critical IT processes to give our customers peace of mind. We deliver solutions based on the fundamentals of good technology design: high quality, a top-notch user experience, and the ability to improve performance. In addition, with the recent acquisition of Digital Guardian, one of the DLP leader solution for large and mid-sized organizations, we keep investing hard to create the most powerful data security portfolio in the market to help customers improving further the ability to protect data across a wide set of channels, applications and operating systems. Together with NSS, we will be working in the areas of infrastructure and data protection, systems and network management, business intelligence, security and compliance, with a commitment to focus on offering solutions to improve everyday operations, save time, and cut costs, through reliable software, the expert services, and outstanding support, provided by the NSS team.”[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_column_text]“As pioneers in cutting edge services and technology solutions, we are very excited to welcome HelpSystems to our portfolio and distribute their cutting edge security and automation solutions,” continued George F. Kapaniris, Executive Director, NSS, emphasizing that “We look forward to assisting MSPs to protect their customers business-critical data with automated cybersecurity solutions that help them stay ahead of today’s ever-changing threats.”.
NSS will distribute HelpSystems’ solutions in the markets of SE Europe, including Greece, Cyprus, Malta and Bulgaria and the Adriatic. By offering a comprehensive and unique set of cloud-based solutions, NSS is expanding its portfolio to meet the increasing IT requirements and security needs of businesses during the age of digital transformation.
To find out more please visit: https://www.nss.gr/en/products/security/helpsystems/
About NSS
NSS is an international Value Added Distributor of Affordable Cutting Edge IT solutions, covering technology areas that include information security, network optimization, communications and infrastructure systems. NSS has strategic partnerships with superior vendors offering products & services with leading technologies that place the company ahead of the competition in today’s crowded market. NSS products can be acquired through a selected channel of resellers in Greece, Cyprus, Malta, the Balkan and Adriatic Countries.
[/vc_column_text][/vc_column][/vc_row]
Τα τελευταία χρόνια, η ασφάλεια των Windows έχει σταθερά βελτιωθεί από τη Microsoft, και το ransomware ήταν μία από τις βασικές απειλές που φρόντισε να αντιμετωπίσει μέσω ενσωματωμένων λειτουργιών όπως είναι οι User Account Control (UAC), Windows Defender Application Control και οι κανόνες Attack Surface Reduction (ASR).
Στο συγκεκριμένο άρθρο, εξετάζεται αν η προστασία από το ransomware που είναι ενσωματωμένη στα Windows 10 είναι αρκετή για να σας προστατεύσει.
Η κατάσταση με το ransomware σήμερα
Το ransomware ήταν μεγάλη υπόθεση το 2020. Εταιρείες και οργανισμοί πάσχισαν να οργανώσουν λύσεις απομακρυσμένης πρόσβασης καθώς όλο και περισσότεροι εργαζόμενοι χρειάστηκε να εργαστούν από το σπίτι εξαιτίας της πανδημίας του νέου κορωνοϊού. Οι συμμορίες κυβερνοεγκληματιών παράλληλα όπως προβλεπόταν εκμεταλλεύτηκαν τον πολλαπλασιασμό των απροστάτευτων τερματικών συσκευών και των απροετοίμαστων χρηστών.
Σύμφωνα με ποικίλες εκθέσεις και αναφορές, σε σχέση με το 2019 σημειώθηκε αύξηση 62-150% στις κυβερνοεπιθέσεις το 2020, με ορισμένες αναφορές μάλιστα να κάνουν λόγο για αύξηση στις επιθέσεις ransomware κατά 485%. Και καθώς τα πιο πρόσφατα δεδομένα που έχουμε θέτουν τη μέση πληρωμή λύτρων στα $312.000 σε ορισμένες περιπτώσεις, οι κυβερνοεγκληματικές οργανώσεις κατάφεραν να αποσπάσουν χρηματικά ποσά ύψους εκατομμυρίων δολαρίων. Κατά τη διάρκεια του 2020 επίσης, διαπιστώθηκε αύξηση και στις περιπτώσεις διπλού εκβιασμού, όπου οι κυβερνοεγκληματίες ή χάκερ όχι μόνο απαιτούσαν υπέρογκα ποσά σε λύτρα, αλλά απειλούσαν επίσης και να διαρρεύσουν ή να πουλήσουν εμπιστευτικά δεδομένα στην περίπτωση που δεν πληρώνονταν τα λύτρα.
Το 2021, οι επιθέσεις εξακολουθούν να αυξάνονται. Υπήρξε μάλιστα και μια απότομη άνοδος των επιθέσεων μηδενικής ημέρας, όπου οι χάκερ αξιοποιούν προηγουμένως άγνωστες ευπάθειες στο λογισμικό. Αυξανόμενο είναι επίσης και το ενδιαφέρον των επιτιθέμενων για τις φορητές συσκευές, την ώρα που βεβαίως εξακολουθούν να αξιοποιούν προς όφελος τους τις απροστάτευτες διαδρομές απομακρυσμένης πρόσβασης και τις ανενημέρωτες στον τομέα του λογισμικού τερματικές συσκευές.
Κατεβάστε την έκθεση Malware & Ransomware Threat 2021
3 Προστασίες ασφαλείας των Windows ενάντια στο Ransomware
Ας αξιολογήσουμε τώρα τρεις προστασίες που είναι ενσωματωμένες στα Windows 10 και τις οποίες μπορείτε να χρησιμοποιήσετε για να ενισχύσετε την άμυνα σας έναντι του ransomware και άλλων κακόβουλων προγραμμάτων.
1.Έλεγχος λογαριασμού χρήστη: Το UAC είναι μια συλλογή από λειτουργίες και χαρακτηριστικά των Windows που βοηθούν τους χρήστες να εκτελέσουν προγράμματα και εφαρμογές χωρίς να απαιτούνται δικαιώματα διαχειριστή στο λειτουργικό σύστημα. Οι Προστατευμένοι Λογαριασμοί Διαχειριστή επιτρέπουν στους χρήστες να «τρέχουν» εφαρμογές, προγράμματα ή λειτουργίες με τα τυπικά δικαιώματα χρήστη τις περισσότερες φορές ωστόσο όταν απαιτείται μπορούν να ανέλθουν σε δικαιώματα διαχειριστή.
Το UAC είναι ένας έλεγχος ασφαλείας και όχι όριο ασφαλείας. Ως εκ τούτου, μπορεί να παρακαμφθεί. Η Microsoft συνιστά στους χρήστες να συνδέονται στα Windows όποτε είναι δυνατόν με λογαριασμό τυπικού χρήστη. Οι Προστατευόμενοι Λογαριασμοί Διαχειριστή UAC έχουν σχεδιαστεί για χρήση σε καταναλωτικές συσκευές. Αν και έχουν συμβάλει σε σημαντική βελτίωση της ασφάλειας στα Windows, δεν προορίζονται να παρέχουν ασφάλεια σε εταιρικό ή επιχειρησιακό επίπεδο.
2.Windows Defender Application Control: Αξιοποιώντας μία τεχνολογία που ονομάζεται Continuous Integrity και που είναι δανεισμένη από το λειτουργικό σύστημα Windows Mobile, το Windows Defender Application Control (WDAC) αποτελεί την πιο πρόσφατη τεχνολογία ελέγχου εφαρμογών στα Windows. Έχει σχεδιαστεί για να επιτρέπει στους οργανισμούς να δημιουργούν καταλόγους επιτρεπόμενων εφαρμογών, scripts και άλλων στοιχείων κώδικα στα οποία επιτρέπεται η εκτέλεση. Οτιδήποτε άλλο, συμπεριλαμβανομένου και του ransomware, αποκλείεται.
Το WDAC μπορεί να διαμορφωθεί χρησιμοποιώντας τον Microsoft Endpoint Manager (MEM) ή χρησιμοποιώντας Group Policy. Η πολιτική ομάδας (δυνατότητα των Windows που περιέχει μια ποικιλία προηγμένων ρυθμίσεων, ειδικά για διαχειριστές δικτύου) δεν υποστηρίζει το format πολλαπλών πολιτικών WDAC. Τα αρχεία πολιτικής WDAC δημιουργούνται χρησιμοποιώντας cmdlets PowerShell. Τα cmdlets δημιουργούν ένα ή περισσότερα αρχεία πολιτικής, που περιέχουν λίστες επιτρεπόμενων εφαρμογών και άλλους κανόνες, τους οποίους μπορείτε να εφαρμόσετε σε πελάτες για να αποκλειστεί μη εγκεκριμένος κώδικας. Για υψηλότερο επίπεδο ασφάλειας, τα αρχεία πολιτικής WDAC θα πρέπει να υπογράφονται για να αποτρέψουν τη διαγραφή ή την αλλαγή των κανόνων ελέγχου εφαρμογών από τους διαχειριστές.
3.Κανόνες Μείωσης της Επιφάνειας Επίθεσης: Οι κανόνες Attack Surface Reduction (ASR) αποτελούν μέρος του Windows Defender Exploit Guard. Οι κανόνες μπορούν να χρησιμοποιηθούν για την απενεργοποίηση λειτουργιών που χρησιμοποιούνται συχνά από χάκερ για να αποκτήσουν τον έλεγχο των Windows και να εγκαταστήσουν κακόβουλο λογισμικό. Οι κανόνες ASR ωστόσο μπορούν και να απενεργοποιήσουν λειτουργικότητα που είναι απαραίτητη για τους χρήστες στον οργανισμό σας, και επομένως θα πρέπει πάντα να ρυθμίζονται σε πρώτη φάση σε λειτουργία αξιολόγησης/ ελέγχου, ώστε να μπορείτε να παρακολουθείτε αν μία διαμόρφωση «αποκλεισμού» μπορεί να επηρεάσει τους χρήστες σας.
Οι κανόνες ASR λειτουργούν στα Windows 10 Pro και σε εκδόσεις Enterprise, από την έκδοση 1709 και μετά. Οι κανόνες μπορούν να διαμορφωθούν χρησιμοποιώντας MEM, η οποία είναι και η προτιμώμενη μέθοδος ή χρησιμοποιώντας τα Intune, PowerShell και Group Policy.
Για να έχετε στη διάθεση σας το σύνολο των δυνατοτήτων, συμπεριλαμβανομένης και της προηγμένης παρακολούθησης και ανάλυσης, θα χρειαστείτε μια άδεια Windows 10 Enterprise E5. Διαφορετικά, θα διαπιστώσετε ότι υπάρχουν περιορισμοί στην παρακολούθηση των ακόλουθων συμβάντων στο Αρχείο Καταγραφής Συμβάντων των Windows (Windows Event Log):
- Audit – Windows Event ID 1122 (έλεγχος)
- Block – Windows Event ID 1121 (αποκλεισμός)
- Settings changed – Windows Event ID 5007 (αλλαγές στις ρυθμίσεις)
Οι ενσωματωμένες προστασίες στα Windows είναι μία αρχή, αλλά δεν είναι αρκετές
Αν και τα χαρακτηριστικά Έλεγχος Λογαριασμού Χρήστη (User Account Control) και Έλεγχος Εφαρμογών (Application Control) όπως και οι κανόνες Μείωσης της Επιφάνειας Επίθεσης (ASR) παρέχουν ορισμένες βασικές βελτιώσεις στην προστασία εφόσον έχει γίνει σωστά η διαμόρφωση/ ρύθμιση τους, δεν επαρκούν για την προστασία των χρηστών και των συσκευών από το ransomware. Η πληρέστερη προστασία απέναντι στο ransomware και στο κακόβουλο λογισμικό απαιτεί από τους οργανισμούς να τηρούν τις βέλτιστες πρακτικές, όπως να επιβάλλουν την αρχή του ελάχιστου προνομίου και τη χρήση λογαριασμών τυπικού χρήστη (απλού χρήστη) αντί λογαριασμών διαχειριστή. Ιδανικά, οι συνδυασμένες προστασίες έναντι του ransomware θα μπορούν επίσης να ενορχηστρωθούν μέσα από μία μόλις «οθόνη» (κονσόλα διαχείρισης).
Η διαχείριση της ασφάλειας των Windows μπορεί να είναι περίπλοκη με τα ενσωματωμένα εργαλεία. Αν και οι ενσωματωμένοι έλεγχοι μπορούν να βοηθήσουν, παραμένει απαραίτητο το να διασφαλίσετε ότι οι χρήστες σας δεν συνδέονται σε τερματικές συσκευές με διαπιστευτήρια διαχειριστή τομέα και οι χρήστες δεν διαθέτουν δικαιώματα διαχειριστή στις συσκευές τους. Όταν ένας επιτιθέμενος αποκτήσει προνόμια διαχειριστή, οι περισσότεροι έλεγχοι ασφαλείας των Windows μπορούν να παραμεριστούν.
Για ολοκληρωμένη προστασία ενάντια στο ransomware αναζητήστε μία λύση Διαχείρισης Προνομίων Τερματικών Συσκευών (Endpoint Privilege Management) που περιλαμβάνει τόσο έλεγχο εφαρμογών όσο και δυνατότητες διαχείρισης προνομίου. Η διαχείριση της ασφάλειας επίσης από μία κεντρική κονσόλα, που παρέχει την πλήρη εικόνα της υποδομής σας, δίνει τη δυνατότητα στο τμήμα πληροφορικής σας να σταματήσει το ransomware προτού εισέλθει στο δίκτυο σας ενώ παράλληλα βοηθάει στο να περιορίσετε οποιαδήποτε παραβίαση αναχαιτίζοντας την πλευρική κίνηση (lateral movement).
Πηγή: BeyondTrust
[vc_row][vc_column][vc_column_text]
Microsoft has steadily improved security in Windows in recent years and ransomware has been one of the key threats addressed via built-in features such as User Account Control (UAC), Windows Defender Application Control, and Attack Surface Reduction (ASR) rules.
This blog explores whether the protection against ransomware built-in to Windows 10 is enough to keep you protected.
The State of Ransomware
Ransomware was big business in 2020. Organizations scrambled to extend remote access solutions as more employees than ever needed to work from home because of the global pandemic. Criminal gangs predictably exploited the proliferation of poorly secured endpoints and ill-prepared users.
According to various reports, there was a 62-150% increase in cyberattacks in 2020 compared to 2019, with some reports putting the increase in ransomware as high as 485%. While recent data puts the average ransom payout at $312,000, some cybercrime syndicates have achieved payouts from larger enterprises of well into the millions in U.S. dollars. 2020 also saw an increase in double extortion, where hackers not only demand a financial ransom, but they also threaten to leak or sell confidential data if the ransom is not met.
Attacks continue to increase in 2021. There has been a steep rise in zero-day attacks, where hackers exploit previously unknown vulnerabilities in software. Attackers are also increasing focus on mobile devices, while they continue to exploit poorly secure remote access pathways and unpatched endpoints…
[/vc_column_text][vc_button button_color=”color-150912″ size=”btn-lg” radius=”btn-round” border_width=”0″ link=”url:https%3A%2F%2Fwww.beyondtrust.com%2Fblog%2Fentry%2Fhow-well-do-windows-10-security-features-protect-against-ransomware||target:%20_blank|”]Find out what are the 3 Windows Security Protections against Ransomware[/vc_button][vc_button button_color=”color-210407″ size=”btn-lg” radius=”btn-round” border_width=”0″ link=”url:https%3A%2F%2Fwww.beyondtrust.com%2Fresources%2Fwhitepapers%2Fmalware-threat-report-2021||target:%20_blank|”]Download the 2021 Malware & Ransomware Threat Report[/vc_button][vc_empty_space empty_h=”3″][vc_column_text]Source: BeyondTrust[/vc_column_text][/vc_column][/vc_row]
Autotask PSA is designed to drive efficiency, accountability, and intelligence for managed service providers (MSPs) by unifying people, processes, and data to provide a singular view across their IT managed services business. The latest enhancements with the Autotask PSA 2021.2 release will help close tickets faster and improve the experience for co-managed IT users.
Automation to close tickets faster
The previous release introduced automated ticket tagging. This helped to reduce the time it took to resolve customer issues. Technicians could quickly identify problems, using the “Find a Solution” button. This feature would then search the knowledge base tags for related problems and relevant solutions.
In this latest release of Autotask, the capability of the “Find a Solution” button has been enhanced, activating only if a solution is found from documentation or the knowledgebase. Partners utilizing Datto’s unified PSA-RMM platform will experience further time savings as Datto RMM alerts will automatically tag relevant HelpDesk articles allowing users to resolve issues without spending time searching for solutions.
Client Portal enhancements
Autotask’s Client Portal has also been updated with the ability to authenticate users with their Google or Microsoft authentication and not just Autotask login. This simplifies the experience for clients and allows them to submit tickets, requests, communicate with their MSP, and review status and goals using their organization’s credentials.
Co-Managed IT improvements
For MSPs deploying Autotask PSA in co-managed environments where Autotask is being utilized by clients’ internal IT staff, additional updates have been made to improve co-managed workflows that include:
- Ability to manage visibility and hide tickets as well as internal costs and pricing from co-managed users
- Creation of Co-Managed Primary Resource and Co-Managed Teams per account to drive more efficient communications
- Addition of Co-Managed resource options to workflow rules automating the assigning of work and notifications to resources
- Ticket Transfer option to indicate who is responsible for working on a ticket and easily transfer responsibilities if required
- Email processing updates that associate incoming tickets for the co-managed end user
Autotask LiveMobile App
The Autotask LiveMobile App which enables remote workers to access their Autotask PSA system when they are away from their desks has also been updated. The latest updates to the native iOS and Android bring the Task and Task Accessories (time entry, notes, attachments, etc.) capabilities to the app.
Looking for a PSA platform to help grow your business by unifying Document Management, Service Desk, CRM, Procurement, Billing, and Reporting behind a single pane of glass? Learn more about Autotask PSA today.
Source: Datto
[vc_row][vc_column width=”1/1″][vc_single_image media=”101430″ media_width_percent=”100″ alignment=”center”][vc_empty_space empty_h=”2″][vc_button button_color=”color-150912″ size=”btn-xl” border_animation=”btn-ripple-out” custom_typo=”yes” font_family=”font-762333″ font_weight=”900″ letter_spacing=”fontspace-210350″ border_width=”2″ display=”inline” link=”url:mailto%3Asales%40nss.gr%3Fsubject%3DSophos%20XG%20Architect%20Training%26body%3DI%20would%20like%20to%20participate%20in%20the%20XG%20Architect%20Training%20on%20November%2030th%2C%202021|||” icon=”fa fa-hand-o-right”]Book Your Certification Today![/vc_button][vc_button button_color=”color-283957″ size=”btn-xl” border_animation=”btn-ripple-out” custom_typo=”yes” font_family=”font-377884″ font_weight=”900″ letter_spacing=”fontspace-210350″ border_width=”2″ display=”inline” link=”|||” icon=”fa fa-volume-control-phone”]Call us now for more +30 211 8000 330[/vc_button][vc_separator sep_color=”color-210407″][/vc_column][/vc_row][vc_row row_height_percent=”0″ back_color=”color-lxmt” overlay_alpha=”50″ gutter_size=”3″ column_width_percent=”100″ shift_y=”0″ z_index=”0″ shape_dividers=””][vc_column width=”1/1″][vc_custom_heading heading_semantic=”h1″ text_font=”font-377884″ text_size=”h1″ text_weight=”900″ text_color=”color-210407″]
Sophos XG Architect Training
[/vc_custom_heading][/vc_column][/vc_row][vc_row][vc_column][vc_column_text]
Tuesday 30 November 2021 – Thursday 2 December 2021
(3 days Training)
This three-day training program was designed and intended for experienced technical professionals who want to install, configure and support the XG Firewall in production environments and is the result of an in-depth study on the next generation firewall of Sophos. The program consists of presentations and practical workshops for the enhancement of teaching content. Due to the nature of the traditions and the varied experience of the trainees, open discussion is encouraged during the training.
Requirement
- XG Firewall _ Certified Engineer course and delta modules up to version 18.5
Recommended Knowledge
- Knowledge of networking to a CompTIA N+ level
- Knowledge of IT security to a CompTIA S+ level
- Experience configuring network security devices
- Be able to troubleshoot and resolve issues in Windows networked environments
- Experience configuring and administering Linux/UNIX systems
Content
- Module 1: Deployment
- Module 2: Base firewall
- Module 3: Network Protection
- Module 4: Synchronized security
- Module 5: Web server Protection
- Module 6: Site to site connections
- Module 7: Authentications
- Module 8: Web Protection
- Module 9: Wireless
- Module 10: Remote Access
- Module 11: High Availability
- Module 12: Pulic Cloud
Certification
+ exam: Sophos XG Architect
Duration 3 days
Agenda
Trainer: Micheal Eleftheroglou
Day 1 Tuesday 30 November 2021
9:30-10:45 Module 1: Deployment and Lab
- Recall important information from Engineer courses
- Deployment modes supported by the XG Firewall
- Understand a range of scenarios where each deployment mode would commonly be used
- Use built-in tools to troubleshoot issues
- Labs
10:45-11:00 break
11:00-13:00 Module 2: Base Firewall
- Explain how the XG firewall can be accessed
- Understand the types fo interfaces that can be created
- Understand the benefits of Fast Path Technology
- Configure routing per firewall rule
- Understand best practice for ordering firewall rules
- Explain what Local NAT policy is and known how to configure it.
13:00-14:00 Lunch
14:00-16:00 Labs
- Activate the Sophos XG Firewalls
- Post installation Configuration
- Bridge interfaces
- Create a NAT rule to load balance access to servers
- Create a local NAT policy
- Configure routing using multiple WAN links
- Configure policy-based routing for an MPLS scenario
- Install Sophos Central
16:00-16:15 Break
16:15-17:15 Module 3:Network Protection and Lab
- Explain what IPS is and how traffic can be offloaded to Fastpath
- Demonstrate how to optimize workload y configuring IPS policies
- Examine advanced Intrusion Prevention and optimize policies
- Configure advanced DOS Protection rules
- Demonstrate how the strict policy can be used to protect networks
- Labs- Create Advanced DoS Rules
Day 2 Wednesday 1 December 2021
9:30-11:00 Module 4: Synchronized Security and Labs
- Explain how Security Heartbeat works
- Configure Synchronized Security
- Deploy Synchronized Security in discover and inline modes
- Understand the advantages and disadvantages of deploying
- Synchronizes Security in different scenarios
- Labs
- Configure source-Based Security
- Hearteat firewall rules
- Destination based Security Heartbeat
- Missing Security Heartbeat
- Lateral Movement Protection
11:00-11:15 Break
11:15-13:45 Module 5 Webserver Protection and Labs
- Explain how Websever Protection works
- Describe protection features for a web application
- Configure Web Server authentication
- Publish a web service using the Web Application Firewall
- Use the preconfigured templates to configure Web Server Protection for common purposes
- Configure SlowHTTP protection
- Labs (Web Application Firewall)
- Labs (Load balancing with Web Server Protection)
- Labs (Web Server Authentication and path-specific routing)
13:45-14:45 Break and Lunch
14:45-17:45 Module 6: Site to site connections and Labs
- Configure and deploy site to site VPNs in a wide range of environment
- Implement IPsec NATing and failover
- Check and modify route precedence
- Create RED tunnels between XG firewalls
- Understand when to use RED
- Labs ( Create an IPsec site to site VPN
- Labs ( Configure VPN network NATing )
- Labs (Configure VPN failover)
- Labs (Enable RED on the XG firewall)
- Labs (Create a RED tunnel between two XG Firewalls
- Labs (Configure routing for the RED tunnel)
- Labs (Configure route-based VPN)
Day 3 Thursday 2 December 2021
9:00-10:00 Module 7: Authentications and Labs
- Demonstrate how to configure and use RADIUS accounting
- Deploy STAS in large and complex environment
- Configure SATC and STAS together
- Configure Secure LDAP and identify the different secure connections available
- Labs (configure an Active Directory Authentication server)
- Labs (configure single sing-on using STAS
- Labs (Authenticate users over a site to site VPN)
10:00-11:15 Module 8: Web Protection
- Choose the most appropriate type for web protection in different deployment scenarios
- Enable web filtering using the DPI engine or legacy web proxy
- Configure TLS inspection using the DLP engine or legacy web proxy
- Labs (Install the SSL CA certificate)
- Labs (Configure TLS inspection rules)
- Labs (Create a custom web policy for users)
11:15-11:30 Break
11:30-12:15 Module 9: Wireless
- Explain how Sophos Access Points are deployed and identify some common issues
- Configure RADIUS authentication
- Configure a mesh network
12:15-13:05 Module 10:Remote Access
- Configure Sophos Connect and manage the configuration using Sophos Connect Admin
- Configure an IPsec remote access VPN
- Configure an L2TP remote access VPN for mobile devices
- Labs (Sophos Connect)
13:05-14:25 Module 11: High Availability
- Explain what HA is and how it operates
- Demonstrate how to configure HA and explain the difference between quick and manual configuration
- List the prerequisites for high availability
- Perform troubleshooting steps andc heck the logs to ensure that HA is set up correctly.
- Explain the packet flow in high availability
- Demonstrate how to disable HA
- Labs (Create an Active-Passive cluster)
- Labs (Disable High Availability)
14:25-15:05 Break – Lunch
15:05-16-15 Public Cloud and Labs
- Deploy XG firewall in complex network enviroments
- Explain how XG firewall process traffic and use this information to inform the configuration
- Configure advanced networking and protection features
- Deploy XG firewall on public cloud infrastructure
- Labs (Put a service in debug mode to gather logs)
- Labs (Retrieving log files)
- Labs (Troubleshoot an issue from an imported configuration file)
- Labs (Deploy an XG Firewall on Azure (simulation)
16:15 (Exams)[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_separator sep_color=”color-210407″][vc_empty_space empty_h=”2″][vc_button button_color=”color-150912″ size=”btn-xl” border_animation=”btn-ripple-out” custom_typo=”yes” font_family=”font-377884″ font_weight=”900″ letter_spacing=”fontspace-210350″ border_width=”2″ display=”inline” link=”url:mailto%3Asales%40nss.gr%3Fsubject%3DSophos%20XG%20Architect%20Training%26body%3DI%20would%20like%20to%20participate%20in%20the%20XG%20Architect%20Training%20on%20November%2030th%2C%202021|||” icon=”fa fa-envelope3″]Book Your Certification Today![/vc_button][vc_button button_color=”color-283957″ size=”btn-xl” border_animation=”btn-ripple-out” custom_typo=”yes” font_family=”font-377884″ font_weight=”900″ letter_spacing=”fontspace-210350″ border_width=”2″ display=”inline” link=”|||” icon=”fa fa-volume-control-phone”]Call us now for more +30 211 8000 330[/vc_button][vc_empty_space][vc_single_image media=”101430″ media_width_percent=”100″ alignment=”center”][/vc_column][/vc_row]
Ransomware is a fear-based attack vector. The greater the fear (i.e., loss of revenue, negative brand impact, human cost) the greater the ransom demand.
This is why ransomware groups are often looking to snag high-value targets that are almost too big to fail. It increases the likelihood that the victims will pay.
Hitting the food supply chain would certainly raise the fear factor, which is why it’s no surprise to see a recent ransom attack demanding almost $6 million from Iowa-based food operator New Cooperative. The group behind this attack is none other than BlackMatter.
In early August, we wrote about BlackMatter emerging from the shadows of DarkSide Ransomware-as-a-Service (RaaS). DarkSide is famously associated with the Colonial Pipeline attack; another high-profile, disruptive ransomware event.
This current iteration of Black Matter appears very similar to what we reported previously, including techniques such as the automatic printing of the ransom note.
Sophos Intercept X stops BlackMatter ransomware
Customers running Sophos Intercept X endpoint protection can rest easy knowing they’re protected by multiple layers of defense against ransomware attacks, including BlackMatter.
Sophos’ deep learning malware detection is able to identify BlackMatter ransomware pre-execution. This happens by using artificial intelligence to compare the “DNA” of the executable to the “DNA” of the entire history of malware. If the file appears similar to ransomware, it will be blocked before it’s able to run.
In addition to deep learning, Intercept X includes CryptoGuard anti-ransomware technology. This defense layer detects malicious encryption processes and shuts them down before they can spread. The runtime behavior engine also detects threats running in memory, and any files that happen to get encrypted are rolled back to their previously-safe states.
BlackMatter resources
- BlackMatter ransomware emerges from the shadow of DarkSide
- A defender’s view inside a DarkSide ransomware attack
- What IT security teams can learn from the Colonial Pipeline ransomware attack
Source: Sophos
Malware and ransomware infection rates are increasing, this year alone, malware increased by 358% overall, and ransomware increased by 435% as compared to 2019. To see their partners are fully secure, MSPs are looking towards user laptops and desktops. It is important that MSPs have visibility of user devices and often turn to an RMM solution, especially as the workforce becomes further separated from the corporate network.
Multi-level defense is about adding layers of security to endpoints to ensure they are operating most securely. A typical security stack would look like this:
- Web filtering
- Email filtering
- Antivirus
- Software firewalls
- Operating System patching
- 3rd party software patching
- Ransomware detection
- Encrypted storage
- Standard user account permissions
Datto RMM can be used to monitor and enforce security policies, patch not only the Operating System but also 3rd party applications, ensure antivirus is installed, up to date, and actively scanning and add a second “pair of eyes” using the built-in Datto RMM Ransomware Detection to detect and stop ransomware infections.
MSP’s can use Datto RMM to automatically and silently deploy security tools like Antivirus or web filtering agents such as Cisco Umbrella to endpoints as they are added to sites in RMM to ensure there are no unprotected devices in the environment. Partners often use components to randomize local admin passwords, disable guest accounts and automatically review and limit how many accounts have local admin rights on devices
Dashboards in Datto RMM can be used to see a quick overall view of the security state of the managed devices and is the MSP’s window into the current security status of devices under management.

RMM’s are very good at alerting MSPs to issues, but the goal should not be just to alert but also to attempt the “first fix” so security issues can be automatically resolved quickly.
Datto RMM can run components in response to alerts. In its simplest form, this could be to run a full AV scan if the installed AV cannot automatically quarantine malware right through to automatically isolating machines from the local network if ransomware is detected.
Automated responses are where MSPs can start enforcing security policies, take care of security-related issues, and installing patches to operating systems and 3rd party applications.
The key is not to rely on a single point of defense. Antivirus installed on workstations should not be the only level of protection; it is part of a multi-level security stance.
Source: Datto
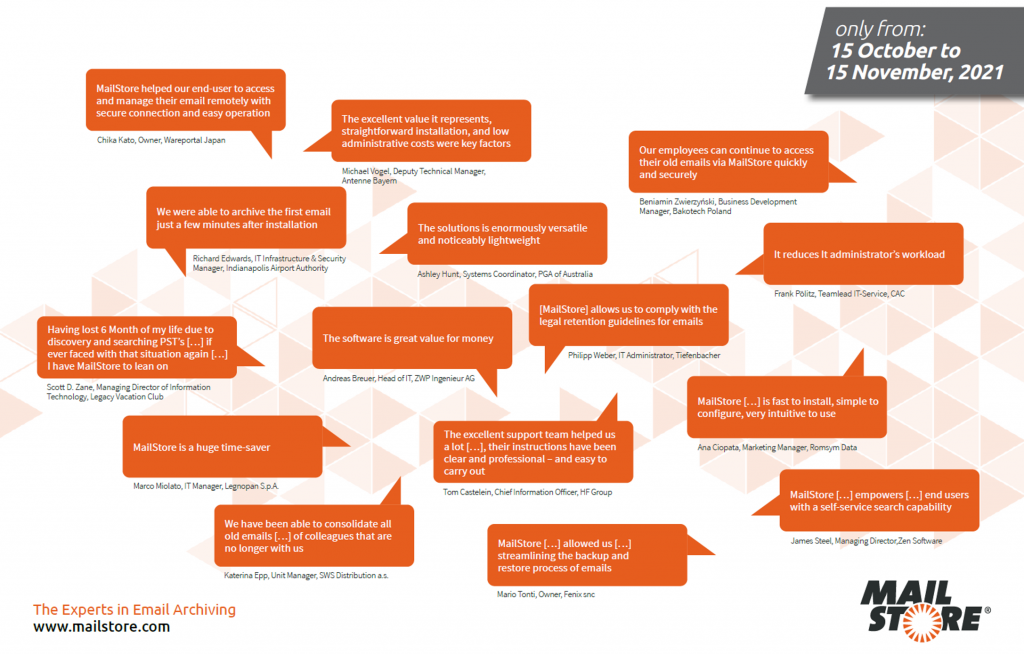
Take advantage of MailStore’s exclusive “15-for-the-price-of-12” anniversary Promotion and become part of the success story.
Exclusively for the 15th anniversary of the email archiving specialist MailStore, you will receive 3 months’ free support in addition to the selected term of your Update & Support Service when you purchase a new MailStore Server license.
Become one of over 80,000 MailStore customers across the globe. Reap the benefits already enjoyed by thousands of MailStore customers and pen your own success story.
15-for-the-price-of-12 Promotion – Terms & Conditions
- Orders must be placed using the promotion code “15 years MailStore”.

- This promotion is valid only when purchasing new MailStore Server licenses with 1, 2 or 3 years of Update & Support Service.
- All eligible orders under this promotion will qualify for 3 extra months of update and support service, i.e.,
- 15 months for the price of 12 months for a 1-year license, 27 months for the price of 24 months with a 2-year license, and 39 months for the price of 36 months with a 3-year license.
- This promotion is valid from 15 October 2021 to 15 November 2021.
- Only registered MailStore channel partners are eligible to participate in this promotion.
- These terms and conditions form a binding legal contract between MailStore Channel Partners and MailStore Software GmbH. By entering the discount code, you agree to be legally bound by the T&Cs.
- MailStore reserves the right to amend, modify, suspend, cancel, or terminate this promotion at any time with immediate effect, and to provide notice of such change via the same or similar means as were used to announce the promotion.
- This offer cannot be sold, transferred, or combined with any other offer or promotion, and is rendered void if altered or reproduced; it has no cash value.
- Each party is liable to the other party in accordance with the applicable statutory provisions in the case of wilful intent, deception and gross negligence, personal injury, or claims asserted under the German Product Liability Act.
- The liability of each party in the case of negligence or breach of a material contractual duty (core duty – “Kardinalpflicht”) is limited to the amount of the foreseeable damage typical under the agreement. A core duty within the meaning of this provision includes the main contractual performance obligations and obligations the fulfillment of which is essential for the due and proper implementation of the contract.
If any provision of these general terms or any specific terms are held to be illegal, invalid, void or otherwise unenforceable, it shall be severed from the remaining provisions which shall continue in full force and effect.
These terms and conditions are governed by the laws of Germany. The mutually agreed place of jurisdiction for all legal disputes is Düsseldorf, Germany.
Five months after the last release, our new MailStore Server Version 13.2 is ready to hit the market! With data security having played the major role in recent versions, Version 13.2 places another aspect of our email archiving solutions, namely performance, under the spotlight. While the new release promises a significant hike in performance in a host of different areas of the software, it has also resulted in a sizable increase in the maximum number of users permitted in a single installation of MailStore Server®, which is targeted at small and mid-sized businesses. Let’s take a look at the details.
What Are the Benefits of Version 13.2?
Enhanced Performance: Faster Than Ever
 This time, the main focus is product performance. Since releasing the last version, we’ve tweaked a few things under the hood, so to speak, and customers and users of all three email archiving solutions MailStore Server, the MailStore Service Provider Edition (SPE), and MailStore Home® can look forward to a major increase in performance.
This time, the main focus is product performance. Since releasing the last version, we’ve tweaked a few things under the hood, so to speak, and customers and users of all three email archiving solutions MailStore Server, the MailStore Service Provider Edition (SPE), and MailStore Home® can look forward to a major increase in performance.
“The boost in performance is perceptible in several areas of the software: for example, the process of rebuilding search indexes is much faster than it was before in all three archiving solutions,” enthuses Heiko Borchardt, Sales Engineer at MailStore Software GmbH. “As a member of the technical support team, I’m in contact with our customers on a daily basis and appreciate that a hike in performance not only delivers technical benefits, but enhances the user experience as well. Our customers are going to be really pleased with this.”
The new release introduces changes such as improved performance when reading recovery records, and performance-optimizing configuration options for archive stores (the latter only applies to MailStore Server and the MailStore SPE). While on the subject of archive stores, you’ll find a blog post with all the details here.
MailStore Server Can Now Be Used by Businesses With up to 2,000 Users
The significant increase in performance of our email archiving solutions comes with another great news: building on other improvements introduced in recent years, MailStore Server can now be used by businesses operating up to 2,000 users (if you have any questions about the system requirements, please contact our support team).
“Depending on the individual IT environment and email volume, our general recommendation was to have no more than 500 users in any single MailStore Server installation,” says Björn Meyn, Product Manager at MailStore Software GmbH. “So we’re really pleased, after extensive testing, to have been able to augment the user limit so significantly in Version 13.2. And our resellers also stand to benefit from this development.”
Other Improvements
In addition to the two highlights of enhanced performance and raising of the user limit, Version 13.2 comes with other improvements. For example, administrators of MailStore SPE can now activate their MailStore SPE installation via a conventional (i.e. non-transparent) proxy and run license reporting through that. Besides that, indexing of PDF attachments is now integrated in all products, thus eliminating the need to install external iFilters. Also, the .NET Core version embedded in MailStore Gateway has been upgraded to guarantee the highest level of security.
GDPR-Certified
As usual, we’ve had our business solutions MailStore Server and the MailStore SPE audited and certified by an independent data protection expert.
 The audit was based on the General Data Protection Regulation (GDPR). This demonstrates that, when used appropriately, MailStore Server and the MailStore SPE meet all relevant requirements governing the processing of personal data set out in the GDPR.
The audit was based on the General Data Protection Regulation (GDPR). This demonstrates that, when used appropriately, MailStore Server and the MailStore SPE meet all relevant requirements governing the processing of personal data set out in the GDPR.
You can request a copy of the official audit certificate from sales@mailstore.com. Registered MailStore partners can download the certificates from our Partner Portal or request it by email from partners@mailstore.com.
Availability
You can download MailStore Server, the MailStore SPE, and MailStore Gateway right now from the company website free of charge. Are you having problems updating to the latest version because your MailStore Server Update & Support Service has expired? If so, please get in touch with us to obtain an upgrade that will allow you to use the latest version of MailStore Server. It makes sense to have an active Update & Support Service for other reasons, too. Click here for a summary of the key arguments.
Interested companies can also download Version 13.2 as part of a free, 30-day trial.
Service providers interested in the MailStore SPE can register here free of charge to obtain all the relevant information, including access to a free trial version.
Home users can download the latest version of MailStore Home free of charge from the Products page of our website.
Source: MailStore
Our new report The State of Ransomware in Manufacturing and Production 2021 reveals that companies in this sector are the least likely to submit to a ransom demand and the most likely to restore encrypted data from backups of all industries surveyed. Just 19% of organizations whose data was encrypted paid attackers to decrypt their files, compared to a global average of 32%.
The report is based on the findings from an independent survey of 5,400 IT decision makers, including 438 in the manufacturing and production sector, conducted at the start of 2021.
Evolving attacker techniques
Overall, 36% of the manufacturing and production organizations surveyed were hit by ransomware last year which is in line with the global average of 37%. Fortunately for this sector, 68% of those whose data was encrypted were able to restore it using backups, a rate considerably above the global average (57%). This high ability to restore data from backups enables many companies to refuse attacker demands, resulting in the low ransom payment rate.
9% of ransomware victims were hit with extortion-based attacks, a pressure technique where attackers don’t encrypt files, but rather threaten to leak stolen information online if a ransom demand isn’t paid. This rate of extortion is higher than the global average of 7%, and may also be linked to the high use of backups which forces adversaries to find other approaches to make money from victims.
Chester Wisniewski, principal research scientist at Sophos, advises that “backups are vital, but they cannot protect against this risk, so manufacturing and production businesses should not rely on them as an anti-extortion defense. Organizations need to extend their anti-ransomware defenses by combining technology with human-led threat hunting to neutralize today’s advanced human-led cyberattacks.”
The cost of ransomware
The overall cost to manufacturing and production organizations to recover from a ransomware attack last year was, on average, $1.52 million. While this is a very considerable sum, it is less than the global average of $1.85 million. Again, the ability to restore data from backups will play a part in keeping recovery costs down.
Fears for the future
While manufacturing and production companies show good resilience in the face of ransomware, the survey revealed that they have the highest expectation of a future attack of all sectors. Of the respondents not hit by ransomware last year, 77% expect to be hit in the future. The sophistication and prevalence of ransomware are the key factors driving this concern.
A sector heavily impacted by the pandemic
IT teams in manufacturing and production were severely affected by the challenges of 2020. This sector was the least likely to experience a decrease in cybersecurity workload over 2020: just 7% said their cyber workload had decreased, vs. a global average of 13%. It also had the fewest respondents who saw improved response time to IT cases (15% vs. a global average of 20%). The silver lining is that cyber skills also increased, with 71% of respondents saying their team’s ability to further develop cybersecurity knowledge and skills increased over 2020.
Learn more
Download the full report to explore the reality of ransomware in manufacturing and production. It also includes recommendations from Sophos experts to minimize the impact of ransomware in future.
Source: Sophos
[vc_row][vc_column][vc_column_text]
Privileged Access & Session Management από την BeyondTrust
Καθώς η πανδημία του 2020 άλλαξε τον παραδοσιακό τρόπο εργασίας, οι εταιρείες αναγκάστηκαν να προσαρμοστούν ξεκινώντας να υποστηρίζουν πλήρως την απομακρυσμένη εργασία. Καθώς συνεχίζεται η διάθεση των εμβολίων, δεν είναι λίγες οι εταιρείες που ξεκίνησαν να καλωσορίζουν τους εργαζόμενους στο γραφείο. Αυτό ωστόσο δεν σημαίνει ότι όλες οι εταιρείες σχεδιάζουν να επιστρέψουν στα ίδια ακριβώς πράγματα με πριν.
Ανεξάρτητα από το που βρίσκεται η εταιρεία σας στο επόμενο κύμα εργασίας, η δημιουργία ενός σχεδίου για την αντιμετώπιση του φυσικού, ψηφιακού ή ανθρώπινου στοιχείου θα διατηρήσει τα δεδομένα ασφαλή και τους ανθρώπους σας υγιείς.[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column][vc_column_text]
“Το 80% των παραβιάσεων είναι αποτέλεσμα
της κατάχρησης ή της κακής χρήσης
προνομιακών διαπιστευτηρίων”
[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column][vc_column_text]
Το PAM εξακολουθεί να αποτελεί υψηλή προτεραιότητα καθώς αρκετές, υψηλού προφίλ παραβιάσεις, συνδέονται με παραβιασμένα/ κλεμμένα διαπιστευτήρια προνομιακών λογαριασμών
Αν προστεθούν και η επιταχυνόμενη μετάβαση στο cloud, η ασάφεια μεταξύ των περιμέτρων ασφάλειας των επιχειρήσεων και η συνολική αύξηση του αριθμού των κυβερνοεπιθέσεων, όλα μαζί, συμβάλλουν στην αύξηση της υιοθέτησης του PAM.
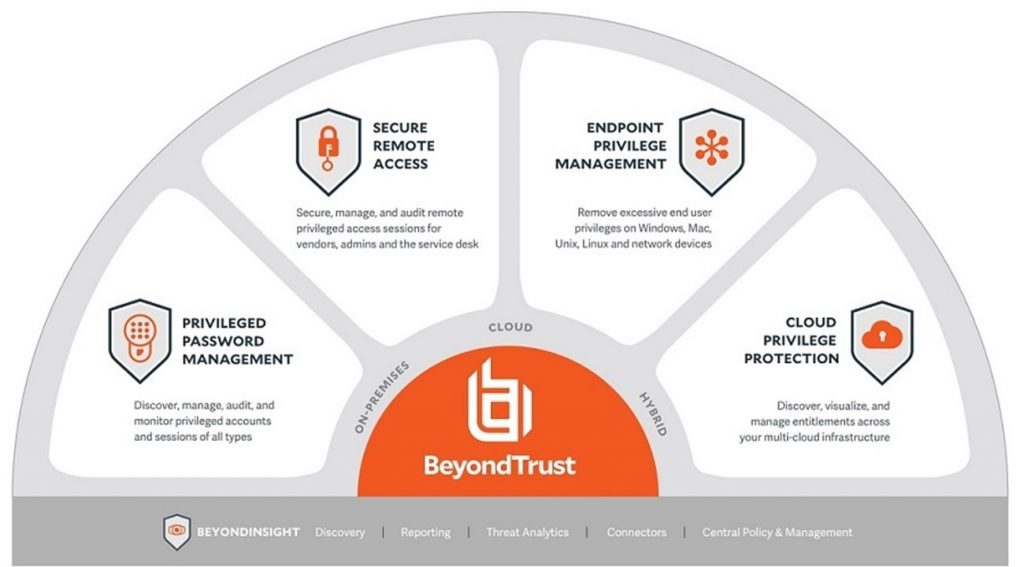 [/vc_column_text][/vc_column][/vc_row][vc_row][vc_column][vc_column_text]Το παραπάνω έρχεται σε συνάρτηση με ότι έχουν δει στη BeyondTrust την τελευταία χρονιά, καθώς οι οργανισμοί συνεχίζουν να υιοθετούν και να εξελίσσουν τις PAM λύσεις τους πέρα από τα απλά/ βασικά προϊόντα PASM, ώστε να περιλαμβάνουν Διαχείριση κλιμάκωσης και εκχώρησης προνομίων (PEDM), Διαχείριση μυστικών και λύσεις Απομακρυσμένης προνομιακής πρόσβασης. Η BeyondTrust προσφέρει το ευρύτερο προϊοντικό χαρτοφυλάκιο PAM στην αγορά έχοντας μάλιστα μεγάλη δύναμη στο PEDM (αναβάθμιση και ανάθεση προνομίων / Privilege Elevation & Delegation) για Windows, Mac, Unix και Linux.
[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column][vc_column_text]Το παραπάνω έρχεται σε συνάρτηση με ότι έχουν δει στη BeyondTrust την τελευταία χρονιά, καθώς οι οργανισμοί συνεχίζουν να υιοθετούν και να εξελίσσουν τις PAM λύσεις τους πέρα από τα απλά/ βασικά προϊόντα PASM, ώστε να περιλαμβάνουν Διαχείριση κλιμάκωσης και εκχώρησης προνομίων (PEDM), Διαχείριση μυστικών και λύσεις Απομακρυσμένης προνομιακής πρόσβασης. Η BeyondTrust προσφέρει το ευρύτερο προϊοντικό χαρτοφυλάκιο PAM στην αγορά έχοντας μάλιστα μεγάλη δύναμη στο PEDM (αναβάθμιση και ανάθεση προνομίων / Privilege Elevation & Delegation) για Windows, Mac, Unix και Linux.
Οι οργανισμοί αναγνωρίζουν ότι η ασφάλεια της απομακρυσμένης πρόσβασης είναι απαραίτητη για τη νέα κανονικότητα της εργασίας από οπουδήποτε (WFA, Work-From-Anywhere), της υβριδικής εργασίας και του επιταχυνόμενου ψηφιακού μετασχηματισμού.
Η BeyondTrust κατέκτησε την αγορά και συνεχίζει να ηγείται
στην αγορά των λύσεων ασφαλούς απομακρυσμένης πρόσβασης
Mε ώριμα προϊόντα απομακρυσμένης προνομιακής πρόσβασης και απομακρυσμένης υποστήριξης, τα οποία είναι χρόνια μπροστά από τα προϊόντα άλλων προμηθευτών PAM όσον αφορά το βάθος και το εύρος των δυνατοτήτων τους.[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column][vc_column_text]
Η ασφάλεια των δικτύων OT (Τεχνολογία Αυτοματισμού, Operational Technology) στο επίκεντρο
Στο Magic Quadrant™ for Privileged Access Management, η Gartner επισημαίνει την αυξανόμενη ανάγκη και ζήτηση για την επέκταση της προνομιακής πρόσβασης σε περιβάλλοντα OT. Αν και το PAM είναι συνήθως μια οριζόντια λύση, με αυξανόμενη ζήτηση από τους τομείς της υγειονομικής περίθαλψης, της βιομηχανίας και των φυσικών πόρων, έκανε την εμφάνιση της μία νέα ανάγκη από «κάθετη» άποψη για συγκεκριμένα χαρακτηριστικά από οργανισμούς που χρησιμοποιούν IoT και OT. Σε αυτούς, περιλαμβάνονται εταιρείες από τον χώρο των υπηρεσιών κοινής ωφέλειας και της ενέργειας καθώς και τα νοσοκομεία. Οι συγκεκριμένοι οργανισμοί χρειάζονται να προστατεύσουν την προνομιακή πρόσβαση στις συσκευές εποπτικού ελέγχου και συλλογής δεδομένων (SCADA) και στις συσκευές OT τους και απαιτούν προ-ρυθμισμένους συνδέσμους σε δημοφιλή συστήματα OT.
Οι λύσεις PAM της BeyondTrust λειτουργούν με «integrated» τρόπο για να ενοποιήσουν τον έλεγχο σε ολόκληρο το σύμπαν των προνομίων σας και να μειώσουν δραστικά την επιφάνεια επίθεσης. Η ικανότητα της να προστατεύει κάθε προνομιούχο χρήστη (άνθρωπο, μηχανή, προμηθευτή, υπάλληλο), κάθε περιουσιακό στοιχείο και κάθε συνεδρία μέσω της πλατφόρμας PAM καθιστά την BeyondTrust τον καλύτερο πάροχο λύσεων PAM για να συνεργαστείτε καθώς οι οργανισμοί καλούνται να λειτουργήσουν στη νέα κανονικότητα και με τα προνόμια σε πολλαπλάσιο βαθμό.[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column][vc_column_text]
Η NSS είναι διεθνής διανομέας Value Added Distributor (VAD) λύσεων πληροφορικής υψηλής τεχνολογίας έχει στρατηγική συνεργασία με την BeyondTrust, παγκόσμιο ηγέτη στη διαχείριση προνομιακής πρόσβασης (Privileged Access Management) και ασφαλούς απομακρυσμένης πρόσβασης (Secure Remote Access), και είναι σε θέση να αξιοποιεί πλήρως το μοντέλο Universal Privilege Management της BeyondTrust, συνδυάζοντας την τεχνογνωσία και τη βαθιά γνώση της αγοράς
[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_button button_color=”color-283957″ size=”btn-xl” radius=”btn-round” border_animation=”btn-ripple-in” border_width=”0″ link=”url:mailto%3Asales%40nss.gr|||” icon=”fa fa-hand-o-right”]Μπορείτε να επικοινωνήσετε μαζί μας στο sales@nss.gr ή στο +30 211 8000 330[/vc_button][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_separator sep_color=”color-150912″][vc_custom_heading text_weight=”200″ text_height=”fontheight-357766″ text_color=”color-283957″]Μάθετε περισσότερα για το PAM της BeyondTrust[/vc_custom_heading][contact-form-7 id=”101372″ title=”Μάθετε περισσότερα…”][vc_separator sep_color=”color-150912″][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][/vc_column][/vc_row]
[vc_row][vc_column][vc_single_image media=”101283″ media_width_percent=”100″ alignment=”center”][vc_button button_color=”color-150912″ size=”btn-xl” border_animation=”btn-ripple-out” custom_typo=”yes” font_family=”font-762333″ font_weight=”900″ letter_spacing=”fontspace-210350″ border_width=”2″ display=”inline” link=”url:mailto%3Asales%40nss.gr%3Fsubject%3DSophos%20XG%20Administration%20Training%26body%3DI%20would%20like%20to%20participate%20in%20the%20XG%20Administration%20Training%20on%20October%2026th%20and%2027th%2C%202021|||” icon=”fa fa-hand-o-right”]Book Your Certification Today![/vc_button][vc_column_text]This course is designed for technical professionals who will be administering Sophos XG Firewall and provides the skills necessary to manage common day-to- day tasks.
On completion of this course, trainees will be able to:
- Explain how XG Firewall help to protect against security threats
- Configure firewall rules,policies and user authentication.
- Demonstrate threat protection and commonly used features
- Perform the initial setup of an XG Firewall and configure the required network settings
- Identify and use troubleshooting tools, reporting and management tasks
Prerequisites
There are no prerequisites for this course; however, it is recommended you should:
- Be knowledge of networking
- Be familiar with security best practices
- Experience configuring network security devices
Certification
To become a Sophos Certified Administrator, trainees must take and pass an online assessment. The assessment tests their knowledge of both the presented and practical content. The pass mark for the assessment is 80%, and is limited to 4 attempts.
Content
- Module 1: XG firewall Overview
- Module 2: Getting started with XG firewall
- Module 3: Network Protection
- Module 4: Webserver protecion
- Module 5: Site to site connections
- Module 6: Authentications
- Module 7: Webprotection and Application control
- Module 8: Application control
- Module 9: Email Protection
- Module 10: wireless protection
- Module 11: Remote Access
- Module 12: Logging, Reporting and Central Management
[/vc_column_text][vc_empty_space empty_h=”3″][vc_button button_color=”color-150912″ size=”btn-xl” border_animation=”btn-ripple-out” custom_typo=”yes” font_family=”font-762333″ font_weight=”900″ letter_spacing=”fontspace-210350″ border_width=”2″ display=”inline” link=”url:mailto%3Asales%40nss.gr%3Fsubject%3DSophos%20XG%20Administration%20Training%26body%3DI%20would%20like%20to%20participate%20in%20the%20XG%20Administration%20Training%20on%20October%2026th%20and%2027th%2C%202021|||” icon=”fa fa-hand-o-right”]Book Your Certification Today![/vc_button][/vc_column][/vc_row][vc_row][vc_column][vc_column_text]
Certification
+ exam: Sophos XG Administrator
Duration
2 days + Labs
Agenda
Trainer: Micheal Eleftheroglou
Day 1 Tuesday 26 October 2021
9:30-10:30 Module 1: XG firewall Overview
10:30-10:45 Break
10:45-12:30 Module 2: Getting started with XG firewall
12:30-13:00 Labs (getting familiar)
13:00-13:30 Lunch
13:30-14:30 Module 3: Network Protection
14:30-15:30 Module 4: Webserver Protection
15:30-15:45 Break
15:45- 17:05 Module 5: Site to Site Connection
Day 2 Wednesday 27 October 2021
9:00-10:20 Module 6: Authentications
10:20-11:20 Module 7: Web Protection and Application Control
11:20-11:30 Break
11:30-12:00 Module 8: Application Control
12:00-12:50 Module 9: Email Protection
12:50-13:30 Lunch
13:30-14:15 Module 10: Wireless Protection
14:15-15:05 Module 11: Remote Access
15:05-15:20 Break
15:20- 16:20 Module 12: Logging, Reporting and Central Management
16:20 Labs discussion[/vc_column_text][vc_empty_space empty_h=”3″][vc_button button_color=”color-150912″ size=”btn-xl” border_animation=”btn-ripple-out” custom_typo=”yes” font_family=”font-762333″ font_weight=”900″ letter_spacing=”fontspace-210350″ border_width=”2″ display=”inline” link=”url:mailto%3Asales%40nss.gr%3Fsubject%3DSophos%20XG%20Administration%20Training%26body%3DI%20would%20like%20to%20participate%20in%20the%20XG%20Administration%20Training%20on%20October%2026th%20and%2027th%2C%202021|||” icon=”fa fa-hand-o-right”]Book Your Certification Today![/vc_button][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_single_image media=”101283″ media_width_percent=”100″ alignment=”center” shape=”img-round” radius=”std”][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][/vc_column][/vc_row]
Ransomware is very much a reality for the finance industry, as revealed in Sophos’ State of Ransomware in Financial Services 2021 report. Based on an independent survey of 550 IT decision makers, it explores the extent and impact of ransomware attacks on mid-sized finance organization worldwide during 2020.
Overall, 34% of the financial services organizations surveyed were hit by ransomware in 2020, and 51% of the organizations impacted said the attackers succeeded in encrypting their data.
Preparation pays off
A quarter (25%) of financial services organizations whose data was encrypted paid the ransom to get their data back. This is lower than the cross-sector average of 32%, and likely a result of the sector’s above average ability to restore data from backups.
It appears that financial services are reaping the benefits of having Business Continuity and Disaster Recovery (BC-DR) plans which prepare them for situations like a ransomware attack. Given that financial services organizations that paid the ransom got back just 63% of their data on average, companies are wise to focus on backups as their primary data recovery method.
Overall, the financial services sector stands out as the only sector where all organizations whose data was encrypted managed to get at least some of it back. Again, it’s likely that financial organizations’ disaster recovery work has prepared them well for a ransomware attack.
Winning the battle, losing the war
When it comes to the actual ransoms paid, financial services come in considerably below average with an average payment of US$69,369 compared to the cross-sector average of US$170,404 (Note: the low number of financial services respondents to this question means the finding is indicative rather than statistically significant.)
The good news stops there, however. The overall ransomware recovery cost for financial services is around a quarter of a million dollars higher than the global average (US$2.10 million vs. US$1.85 million). This is likely due to high spending on remediation measures to keep operations running at all costs, and the high costs of data breach notification, reputational damage, and regulatory fines that all impact this sector. As John Shier, senior security advisor at Sophos, explains:
Strict guidelines in the financial services sector encourage strong defenses. Unfortunately, they also mean that a direct hit with ransomware is likely to be very costly for targeted organizations. If you add up the price of regulatory fines, rebuilding IT systems and stabilizing brand reputation, especially if customer data is lost, you can see why the survey found that recovery costs for mid-sized financial services organizations hit by ransomware in 2020 were in excess of $2 million.
A target for extortion-only attacks
Another worrying data point is the fact that a small, but significant, 8% of financial services organizations hit by ransomware experienced what are known as ‘extortion’ attacks, where data is not encrypted, but stolen and victims are threatened with the online publication of their data unless they pay the ransom. Backups cannot protect against this risk, so financial services organizations should not rely on them as an anti-extortion defense.
Read the full report
To learn more about the impact of ransomware on finance, read the full State of Ransomware in Financial Services 2021 report.
Source: Sophos
To protect your users’ inboxes from phishing, look no further than Sophos Email. Alongside advanced anti-spam and malware protection powered by SophosLabs, Sophos Email includes multiple layers of technology to keep your email phish-free.
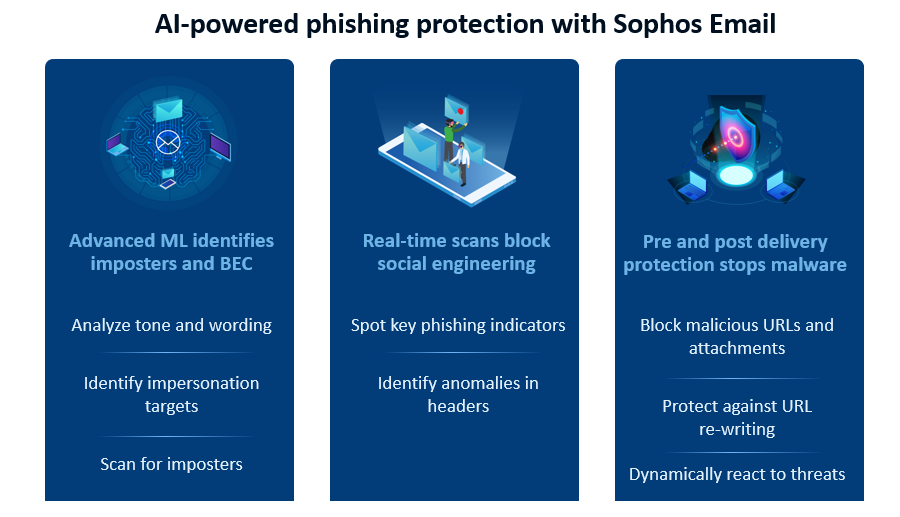
Advanced machine learning identifies phishing imposters and BEC attacks
Criminals often impersonate key individuals in an organization to trick other employees into falling for their scams. Sophos Email uses advanced machine learning to detect targeted impersonation and Business Email Compromise attacks. Utilizing the deep learning neural network created by Sophos AI, Sophos Email analyzes email body content and subject lines for tone and wording to identify suspicious conversations.
For added protection, Sophos Email also includes a setup assistant that integrates with AD Sync to automatically identify the individuals within an organization who are most likely to be impersonated. It scans all inbound mail for display name variations associated with those users, further extending protection against phishing imposters.
Real-time scanning blocks social engineering techniques
Adversaries are experts at using social engineering in their attacks. That’s why Sophos Email scans all inbound messages for key phishing indicators such as brand spoofing and impersonation attempts in real-time using SPF, DKIM, and DMARC authentication techniques and email header anomaly analysis. It spots and blocks phishing emails before they reach your users.
Pre and post delivery protection stops malicious links and malware
The danger with phishing is not the email itself but what it gets people to do. Phishing emails often include malicious links and malware that attackers try to trick you into activating. Sophos Email’s real-time URL scanning and AI-powered cloud sandbox protect against malicious URLs and attachments, ensuring malware never reaches your users’ inboxes.
To avoid detection, attackers sometimes update the link in an email after it has landing in the victims’ inboxes, for example, re-directing safe URLs to malicious ones, or insert malware into a previously-clean web page. Time-of-Click URL rewriting analyzes all URLs at the moment they are clicked, and automatically removes dangerous emails to protect against these post-delivery techniques.
Sophos Email’s Search and Destroy capabilities take this one step further, directly accessing Office 365 mailboxes, to identify and automatically remove emails containing malicious links and malware at the point the threat state changes and before a user ever clicks on them.
Learn more
To find out more head to sophos.com/email. You can start a free trial directly from our website, and if you’re already using Sophos Central you can activate a trial directly within your console in just two clicks.
Source: Sophos
BeyondTrust has just published our Malware Threat Report 2021, produced by the BeyondTrust Labs team, with collaboration from customers and incident response teams using BeyondTrust solutions. The report is based on real-world monitoring and analysis of attacks between Q1 2020 and Q1 2021, and also involves the testing of 150 recent malware strains against the MITRE ATT&CK Framework.
Here are a few key findings published in the report:
- Fileless threats are increasing and being leveraged in the initial attack stages until a strong foothold and persistence mechanism is established and security controls have been disabled.
- Malware-as-as-service (MaaS) is becoming a preferred threat actor model, leading to specialization in the production of malware tools that can be purchased and deployed along various stages of the attack chain.
- The MITRE ATT&CK Framework provides an effective way to distill a wide range of malware strains and cyberattacks into component techniques, which can then be mitigated.
- BeyondTrust’s out-of-the-box policies proactively disrupted all 150 different, common attack chains tested in our analysis.
- Removal of admin rights and implementation of pragmatic application control are two of the most effective security controls for preventing and mitigating the most common malware threats seen today.
Read on for some more highlights on the report, including reoccurring threat themes, and the effectiveness of privilege management at preventing and mitigating cyber threats. You can also download the full report here.
Maturity of the Malware Ecosystem
Cybercrime is a high-growth industry that is constantly evolving with regard to malware ecosystems and their economic models. Parallel to legitimate software companies and the trend towards SaaS, threat actors are shifting to malware-as-service models, with specialists emerging in different areas, including enterprise credential sales, initial access to a target organization, lateral movement capability, or payload delivery.
Today, there are often many different pieces of malware that come together in an attack. A modern ransomware attack could be comprised of multiple threat actors, tools, and platforms. For example:
- Threat actors rent the Necurs botnet and use it to distribute malicious spam.
- Spam contains malicious documents that launches Trickbot.
- Trickbot is used to harvest credentials, access emails, and for lateral movement across the network. The stolen data can be sold or used in later attacks.
- With widespread compromise of the target network, the threat actor sells backdoor access to the network to the highest bidder.
- The buyer then deploys RYUK ransomware via the Trickbot command and control servers.
As threat actors seek to maximize the disruption to organizations and extract the highest ransom payments, the ransomware model is shifting towards human-operated, enterprise-wide attacks.
Rather than create an automated worm that self-propagates across the network, the latest generation of ransomware-as-a-service (RaaS) will tread lightly, establishing a foothold in the network of a large organization. Using common penetration testing tools – such as Cobalt Strike or PowerShell Empire – they then survey the network and spread using privilege escalations to gain control of critical systems and disable security controls, before finally encrypting key systems and exfiltrating data.
PAM – A Powerful, Blended Defense Against Today’s Malware Threats
All too often, malware will not only use multiple techniques to evade detection, but will also exploit excessive privilege granted to end users to disable security controls, which completely undermines your defenses and security investment.
66% of the 58 techniques in the MITRE ATT&CK Framework either recommend using Privileged Account Management, User Account Management, and Application Control as mitigations or list Administrator / SYSTEM accounts as being a prerequisite for the technique to succeed.
Therefore, the control of privileges and application execution prevention is a key defensive measure in mitigating Cobalt Strike and tools/malware with similar capabilities, through a reduction in the attack surface and denying code execution and privileged rights.
Lab-Testing BeyondTrust Trusted Application Protection Against Top Malware Strains
BeyondTrust’s Privilege Management for Windows product is designed to eliminate unnecessary privileges, strictly control privileged access, and provide pragmatic application control to proactively reduce the attack surface. Within this product, is a unique, Trusted Application Protection (TAP) feature, which provides an out-of-the-box policy designed to mitigate common attack techniques—including fileless threats—and prevent high risk applications, such as Web Browsers, PDF viewers, Outlook, and Microsoft Office from being exploited.
Trusted Application Protection uses both privilege management and application control capabilities to prevent these high-risk applications from launching custom malware payloads. It also protects high-risk applications from more sophisticated DLL attack techniques, such as DLL injection, hijacking, and malicious DLL plugins.
To test the effectiveness of Trusted Application Protection, BeyondTrust Labs examined the attack chains of thousands of malware samples from the past year. While malware will constantly change the content of the phishing emails, re-encoding payloads to evade AV, and use new scripting techniques to hide their intent, there is less variability in the attack chains used.
As an example, a threat actor might use a range of document types and create hundreds of variants with unique file signatures. However, every variant will launch CMD, then run a script that pulls down a custom executable payload and launches it. While the document changes, the script, the website hosting the executable, and the payload may all change—the attack chain remains consistent.
For our analysis, we distilled 150 malware samples that represent the attack chains of some of the most prolific malware threats of 2020 – 2021. As you might expect, the most successful malware families tend to vary their attack chains, resulting in a higher number of samples.
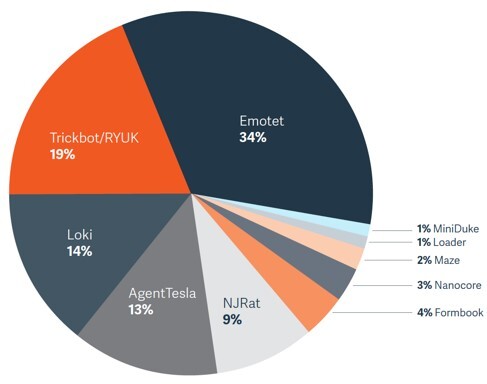
As published in the Malware Threat Report 2021, our analysis clearly demonstrates the remarkable effectiveness of endpoint privilege management, such as BeyondTrust Privilege Management for Windows & Mac and Privilege Management for Unix & Linux products, in proactively stopping these and potential future threats, that leverage similar attack chains.
With that said no one solution can be the sole basis for a strong endpoint security strategy—it takes an ecosystem of solutions working in tandem.
For more findings on how BeyondTrust can help mitigate the most recent malware strains, download the BeyondTrust Labs Malware Threat Report 2021.
Source: BeyondTrust
Phishing is still an effective cyberattack technique because it constantly evolves. To keep up, your phishing defenses need to evolve too.
Our new report, Phishing Insights 2021, reveals the state of phishing and cybersecurity user education based on an independent survey of 5,400 IT professionals. Use it to evaluate your own phishing security posture and identify opportunities to evolve your defenses.
It also provides a real-world case study of a phishing email that led to a multi-million dollar ransomware attack.
Phishing means different things to different people
What is phishing? One of the findings from the survey is that even among IT professionals there is wide variation in what people consider to be a phishing attack. The most common understanding is emails that falsely claim to be from a legitimate organization, usually combined with a threat or request for information. While this was the most popular answer, fewer than six in ten (57%) respondents selected this option, illustrating the breadth of meanings understood by phishing.
46% of respondents consider Business Email Compromise (BEC) attacks to be phishing, while over a third (36%) understand phishing to include threadjacking i.e. when attackers insert themselves into a legitimate email thread as part of an attack.
With this extensive variation in understanding of phishing attacks among IT professionals, it’s reasonable to expect a similar or greater range of interpretations among non-IT employees.
This is a useful reminder to be mindful of the different interpretations of the word ‘phishing’ when providing educational resources and user awareness training. Without the correct context, the training will be less effective.
Phishing has increased since the pandemic
70% of survey respondents reported an increase in phishing attacks on their organization since the start of the pandemic. All sectors were affected, with central government experiencing the highest increase (77%), closely followed by business and professional services (76%) and healthcare (73%).
Fortunately, 98% of organizations had their phishing awareness program in place before COVID-19 hit. Thanks to these programs, employees will have been well placed to withstand the barrage of phishing emails over the last year.
While this is good news, it’s also a reminder to regularly review and update phishing awareness materials and activities to keep them fresh and relevant.
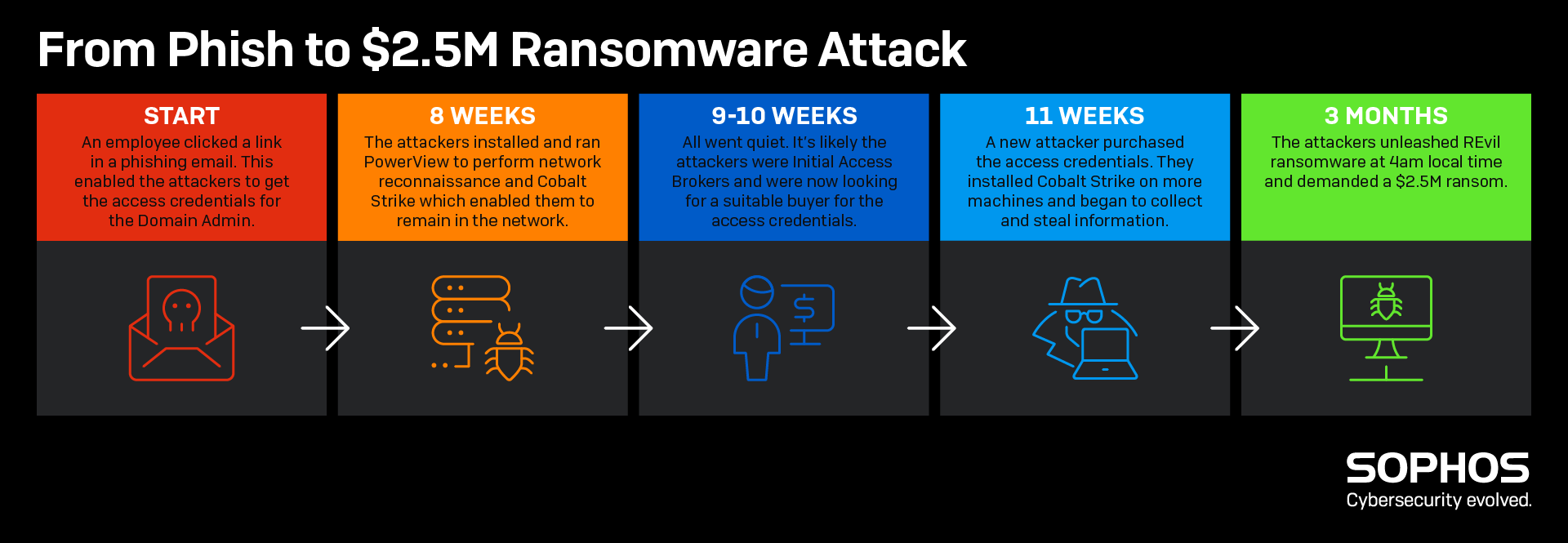
Case study: From phish to multi-million-dollar ransomware attack
Invariably, phishing is just one part of a cyberattack. When a victim falls for a phish, it set off a chain of events that can lead to a devastating attack many weeks or months later.
The Sophos Rapid Response team was recently called in to assist a company experiencing a major ransomware attack that started with a phishing email. As the timeline shows, three months passed between the initial phish and the release of the ransomware payload, with multiple adversaries playing different roles in the attack.
Read the full report
Download the full Phishing Insights 2021 report to dive deeper into the state of phishing and cybersecurity user education, and the timeline of this attack.
Get AI-powered phishing protection with Sophos Email
Sophos Email has multiple layers of technology to protect your users’ inboxes from phishing, and is managed from the same Sophos Central platform as our other next-gen solutions – learn more.
Source: Sophos
Sophos Managed Threat Detection, a new service from the Sophos Managed Threat Response (MTR) team, is available since July 2021.
Sophos Managed Threat Detection provides 24/7 threat monitoring, and it is designed to run in parallel with non-Sophos endpoint protection products, which means you can continue to use your current endpoint protection while enjoying the peace of mind that comes with being monitored by Sophos threat experts.
Managed Threat Detection is tuned to detect suspicious activity that your non-Sophos endpoint may miss or is unable to convict. For example, Ransomware pre-execution and at runtime activity, Active Adversary activities and Persistence. Depending on their severity detections will generate cases. All cases are validated by an analyst before notifying the customer. In this way the service is doing the heavy lifting to ensure customers are provided actionable intelligence and not overloaded with alerts.
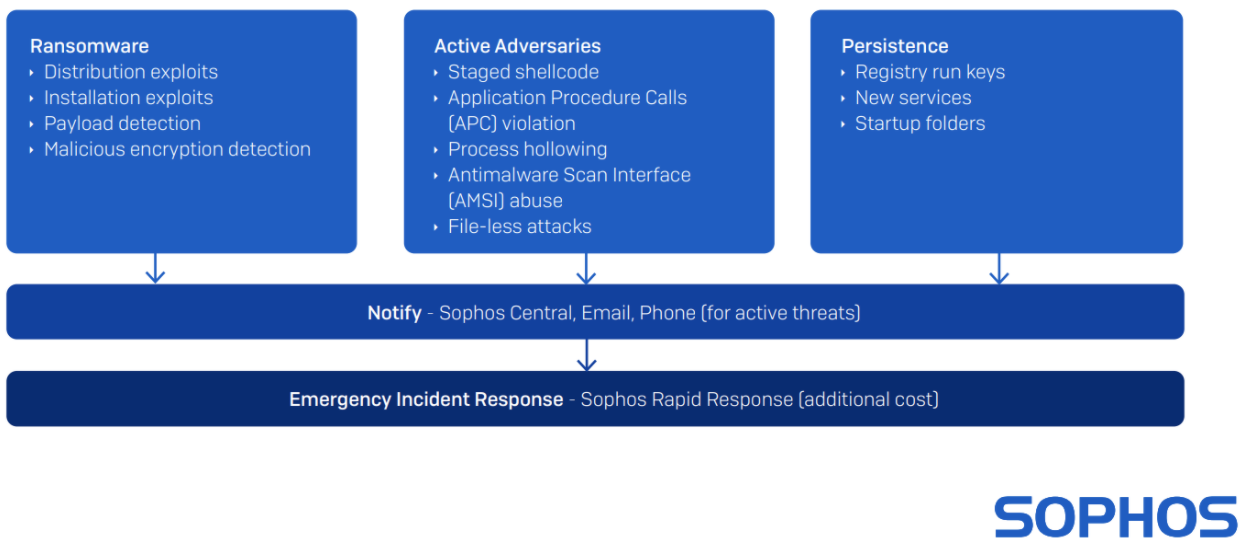
Clear communication is critical when running a security operations program. This is why the Managed Threat Detection service provides a steady stream of information, including weekly and monthly reports, email threat notifications in real time, and a dashboard in Sophos Central.
If incident response help is needed to respond to an active threat the Sophos Rapid Response team is available as an additional service. Sophos Rapid Response provides fast, remote emergency assistance to investigate and neutralize active threats. Sophos customers have a built-in speed advantage since the Rapid Response incident response team will have immediate access to the telemetry and data recorder provided by the Managed Threat Detection agents.
Source: Sophos