News
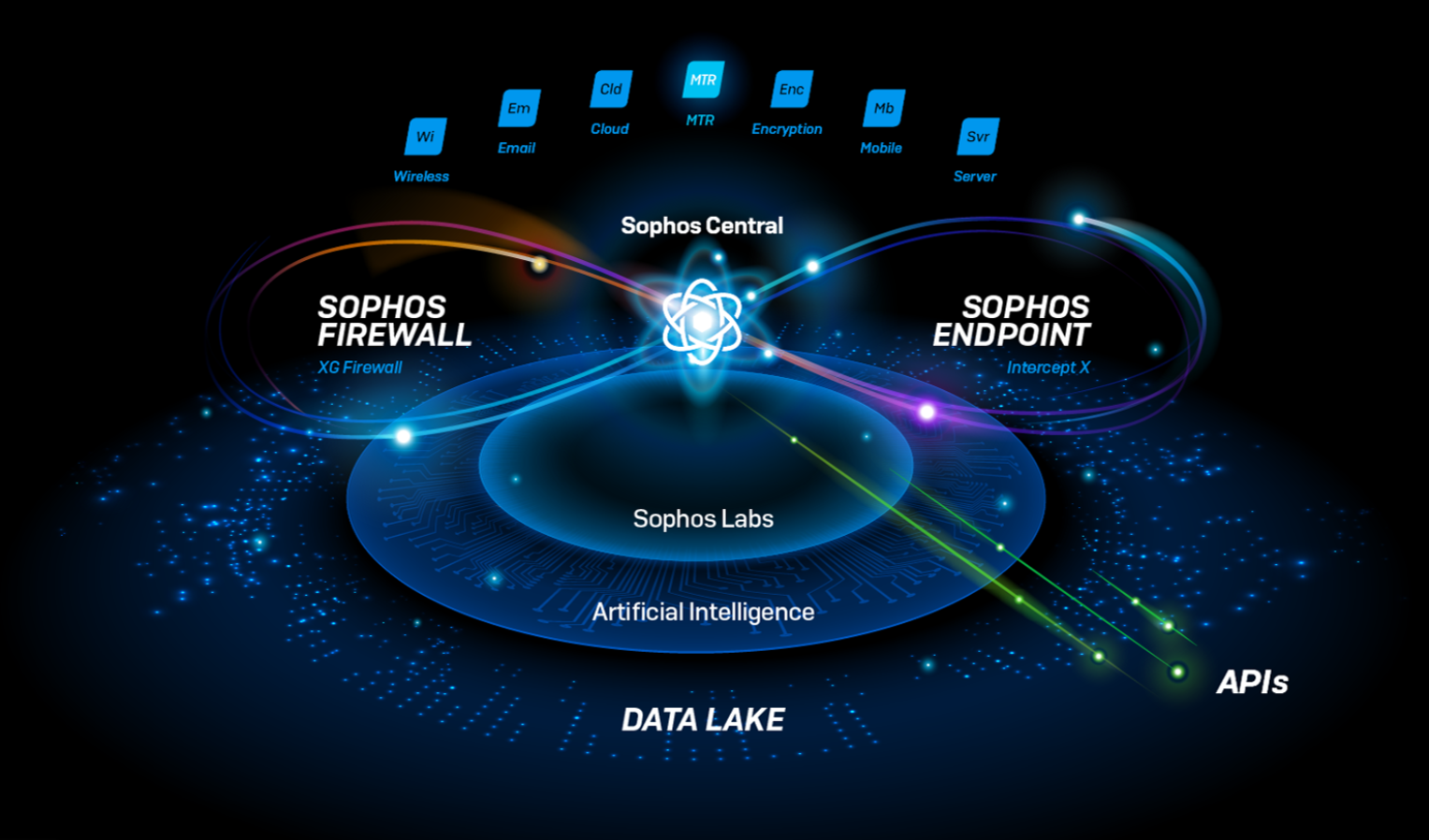
Sophos Central, our cloud-based security platform, has a feature that nobody talks about, but everybody loves.
As an administrator, you create your identity once—and that’s it. Suddenly, on all of your Sophos products, you’re good to go. No need to set up and remember separate user details for your endpoint protection, your email security, and your firewall; it just works.
I doubt anybody ever bought a Sophos product for that reason. But it’s there, and it saves every user a little bit of time and effort right off the bat. They might raise an eyebrow at how easy it was, then they go about their day.
Nobody thinks about how we make it happen.
And that’s fine; in the Sophos Central team, we’ve long understood that the better we do our job, the less you’ll notice. Which is a really good illustration of the power and value of a platform.
Improving your security—and unlocking innovation
First, there’s the obvious part. Having all your cybersecurity solutions working together—and being able to see and control them all through a single pane of glass—saves you a ton of time. Lots of our customers say it cuts their workload by 50% or more.
You can apply global policies, spot issues more easily, and generally keep your organization that much safer. And as important as that is, there’s something even more fundamental happening under the hood.
The reason our user setup process works so smoothly is that we have a whole team of Sophos Central engineers focused solely on the platform. We provide the building blocks (like user identity) to our product teams that they can pick up and use.
In this example, it means your login works across our entire portfolio (you’re welcome). And it’s one less thing for each product team to develop. So instead, they can focus on raising the bar for security and innovation—the reasons you likely chose Sophos products in the first place.
If you think of your specialized cybersecurity solutions as rooms in your home—the kitchen, the living room, the bedroom—it’s easy to see Sophos Central like a thermostat that lets you control the temperature across all of them at once. In fact, it’s also the plumbing, the wiring, and the foundations. It’s all the parts that make a house.
A purpose-built meeting place for your cybersecurity data
And that’s not all. By providing a single platform to underpin all our product development, we create a common point where they can all exchange data and interact.
This is where the magic really happens. You toggle a button, and your solutions start talking to each other. Now an alert on your endpoint protection can trigger a response in your firewall—for example, to isolate a device before ransomware can spread. They share data, so what one solution learns can benefit all the others.
Again, that takes a lot of work behind the scenes. First and foremost, it’s a lot of data to manage, and it increases exponentially with each solution you add. If you’re using Sophos XDR, on a daily basis we likely process 6-20 MB for each endpoint, and another 20-80 MB for each server; in a sizeable organization, that can easily add up to gigabytes per day.
Add your Sophos Firewall logs into the XDR solution and that can be tens of gigabytes a day. Maybe your Sophos Email follows, and potentially you hook in data from your Office 365. Very quickly, you’re into very large volumes of data, daily—with Sophos Central connecting it all, making sense of it for you, and proactively letting you know if anything is out of the ordinary.
And here’s the part we’re really proud of: Sophos Central handles all that data impossibly fast. You can ask for all the endpoints showing a particular hash—the kind of search that’s “go-make-a-coffee” territory on most systems—and Central will have it for you in seconds.
The secret ingredient in our technology stack
Sophos Central can do that because of the smart way we built our data platform. Getting the opportunity to create something this ambitious—and work with such an awesome team—is the whole reason I joined Sophos. I’m so glad I did.
There’s nothing unusual about the stack itself. The platform is built entirely in AWS, with popular technologies like Kafka and Presto, alongside other proven services.
The secret ingredient is the way we put those pieces together.
Specifically, we keep our customers’ objectives in mind when we plan how to ingest, parse, and store their data. For example, we know which reports administrators run most often—so we set up the architecture to find those answers faster. In fact, it means we can go beyond finding your answers quickly; we can have them waiting for you when you log in.
Right from the start of the design process, we spend a lot of time streamlining the things that will make the biggest difference to your day-to-day work. Ironically, if we do our job well, it means they’re the parts you notice least.
So, when you next toggle a button to synchronize a new solution in Sophos Central, and you smile at how instantly it works, spare a thought for all of us behind the scenes. We worked hard to make it that easy.
And if you’re not yet using Sophos Central, maybe it’s time to take it for a test drive. Try for yourself, for free, for 30 days to see how it works for you.
Source: Sophos
In cyberspace, there exists no safe harbor. Every organization with a digital presence is exposed like an island amidst an angry, implacable ocean that seems to send wave after wave of cyberattack.
The year 2021 arguably stands out as the most brutal and shocking in terms of cyberattacks. We have clearly entered an era of “assume breach” and “zero trust”. We need to not only rethink security, but recalibrate it based on the changes to technology happening around us.
 Contact BeyondTrust today to learn how to recalibrate your security with our privileged access management (PAM) solutions to address today’s threats and so you may confidently embrace your digital transformation opportunities.
Contact BeyondTrust today to learn how to recalibrate your security with our privileged access management (PAM) solutions to address today’s threats and so you may confidently embrace your digital transformation opportunities.
Source: BeyondTrust
Sophos Extended Detection and Response (XDR) now goes even further in the public cloud, adding Microsoft Azure (Azure) and Google Cloud Platform (GCP) activity logs alongside Amazon Web Services (AWS) – helping security teams see the bigger picture across public cloud environments.
Integrating data from the Sophos cloud security posture management solution, Cloud Optix, Sophos XDR enables you to detect, assess, and harden cloud workloads and user access against security misconfigurations and vulnerabilities.
New Cloud Optix data sources in Sophos XDR now allow you to easily investigate AWS, Azure, and GCP cloud environment API, CLI, and management console activities. Using fully customizable and pre-written SQL queries, you can uncover initial access attempts on the environment via compromised roles, as well as newly created user roles and resources indicating persistence within the environment, and privilege escalation and exfiltration tactics shown by attackers.

Using Cloud Optix findings as indicators of compromise, we help you pivot by leveraging the Sophos XDR data lake to investigate workload vulnerabilities uncovered by Sophos Intercept X for Server workload protection agents running on those workloads. Examples include the detection of compute workload resources with ports exposed to the internet, such as RDP or SSH. In this scenario, Cloud Optix alerts you to these access vulnerabilities and Sophos XDR allows you to quickly pivot investigations to identify the number of authentication attempts on those instances, and any successful attempts made. You can then act confidently to remove access and prevent a breach, with Cloud Optix providing guided remediation instructions to reduce your mean time to resolve (MTTR) vulnerabilities.
This connected multi-cloud security from one central console helps teams see the bigger picture during investigations, making it easy to quickly identify risk and proactively prevent security incidents.
More Cloud Optix enhancements
This latest update to Sophos Cloud Optix also includes a range of additions to enhance your cloud security monitoring and compliance response:
AWS activity anomalies – New SophosAI models continuously analyze AWS CloudTrail user activity logs. This allows Cloud Optix to build a picture of individual user role activity to identify both accidental changes as well as malicious activity from compromised roles. It brings AWS CloudTrail events to life in a clear and detailed timeline view of user activities, identifying high risk anomalies such as actions performed outside of normal working hours as well as those never performed before.

With this update, you can dramatically shrink alert totals for security teams and help them focus on investigating high-risk patterns of behavior that could lead to security incidents in a fraction of the time that it took them before.
Multiple Jira integration instances – Now add multiple Jira integration instances to a Cloud Optix account. Each cloud environment will be linked to one Jira instance. This could be a separate Jira Instance per environment, or a common Jira instance shared with many environments.
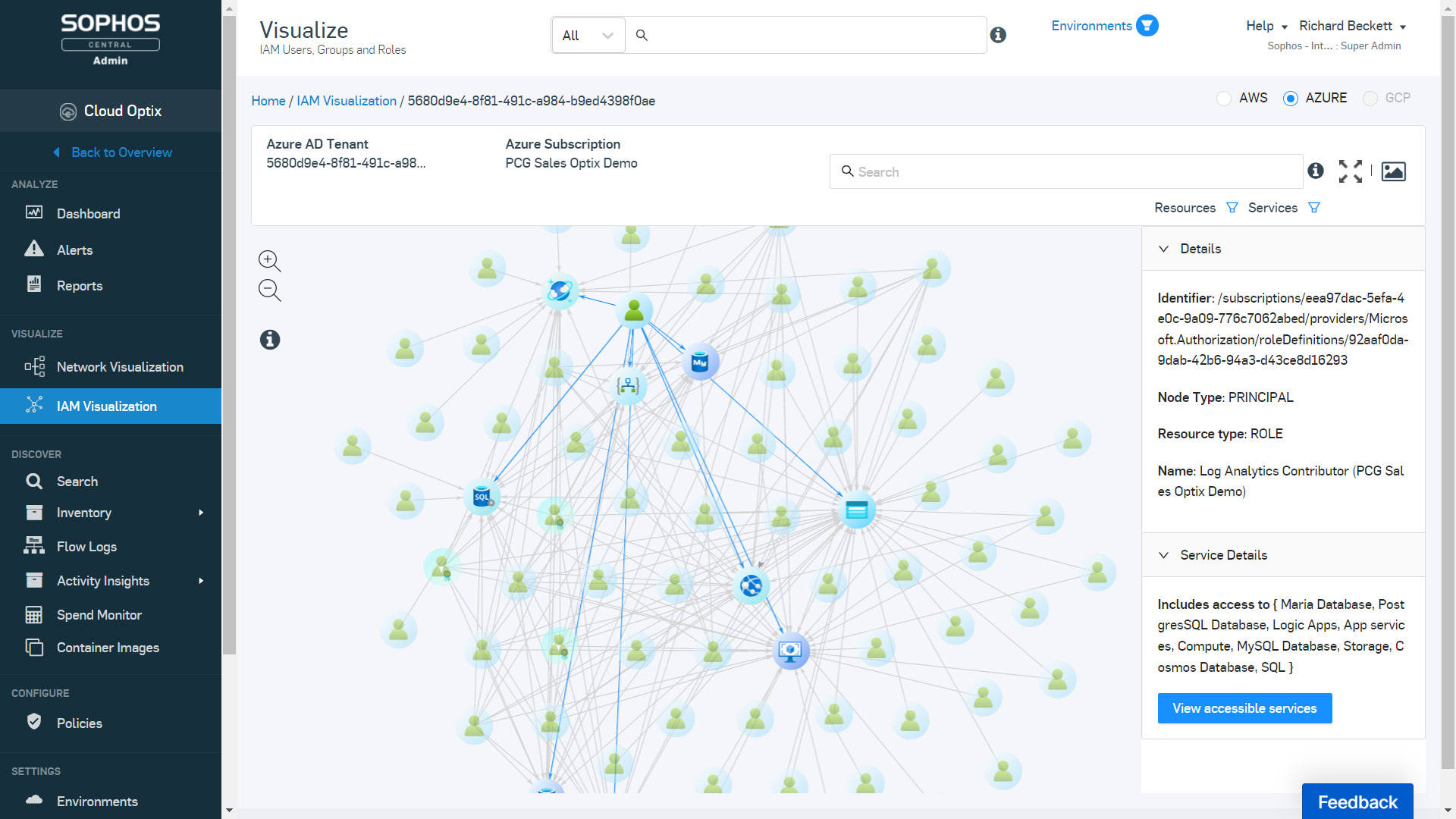
Azure IAM visualization – Visualize the relationships between IAM roles, IAM users, and services in Azure to simplify the management of complex, interwoven IAM roles for multiple Azure subscriptions and Azure AD.
Custom policy alerts – Now create custom alerts based on Cloud Optix advanced search queries. Future security benchmark scans will then raise alerts in Cloud Optix when the criteria of the query is met.
These latest updates and a recap of all Cloud Optix enhancements are available here. To improve your cloud security posture and to try Cloud Optix free for 30 days, visit Sophos.com/Optix today.
Source: Sophos
We’re starting off the new year with a big announcement – a new Sophos product! Sophos ZTNA officially launches today, providing a very innovative solution for securely connecting remote users to applications.
The right product at the right time
If you’re one of the many organizations managing remote workers and you’re concerned about ransomware and threats, this product comes at the perfect time. And Sophos ZTNA solves one of the top complaints of early adopters: multiple agents.
One agent, one console, one vendor
Sophos ZTNA is unique in that it offers a single-agent solution for both Zero Trust Network Access and your next-gen endpoint protection with Intercept X.
While Sophos ZTNA will work with any endpoint solution, it works better together with Sophos Intercept X, providing a single agent, managed from a single console, all from a single vendor.
It also leverages Synchronized Security Heartbeat for device health to enable conditional access and stop threats dead in their tracks. Together, Sophos ZTNA and Intercept X provide the best end-to-end protection for your remote workers and the applications and networks they need to connect to.
You can now order Sophos ZTNA – starting today – and enable your remote work force to securely connect to your hosted applications in an elegant, streamlined, and transparent way.
How to get started
- Talk to your preferred Sophos partner or contact us to request a call back
- Start a 30-day free trial in Sophos Central
Learn more
To learn more about Sophos ZTNA and how it can help you, visit Sophos.com/ZTNA and check out these helpful resources:
Product training and assistance
- Consult the online documentation – also available via the Help section (upper right of the console screen) within Sophos Central
- We have some great product training available as well
- Head over to the community forums for additional content (such as known issues) and to interact with other EAP participants and the Sophos team
A special “Thank you!” to those of you who recently participated in the early access program – your access to Sophos ZTNA will continue through the end of January.
Source: Sophos
Automation used to be a tool that was almost exclusively used in the most technical areas of the business – developers, IT operations, and maybe one or two ambitious business users that could write a macro.
“Now its impact is much further reaching,” says Kevin Vliet, Director of Product Management at HelpSystems. “I would argue that many businesses earn their margins by automating repetitive tasks and reserving their worker’s time for the highest-level operations.”
According to Kevin, to get the most out of automation, your company should embrace an end-to-end automation strategy. “At the end of the day, if you just hand your teams a bunch of miscellaneous automation tools, it’s not necessarily going to create long-lasting assets for your business.” But with end-to-end automation, you can bring together everyone from business to IT to digitally transform your organization.
What is End-to-End Automation?
Simply put, end-to-end automation is the ability to automate processes from the front-end, to the back-end—and everything in between. Front-end automation streamlines tasks focused on interactivity, websites, and attended processes from the user-interface (UI) level. Think of processes like website data extraction, report generation, and data entry. Back-end automation handles the unattended processes and leverages APIs for specifically defined, high-capacity transactions. Think of items like batch processing, database processing, file movement, and PowerShell scripts.
Bringing these approaches together gives your organization a holistic approach. End-to-end automation can give you a complete solution that brings your tech stack together and ultimately helps your business run more efficiently while optimizing resources. This is especially helpful for organizations that are struggling to get a grip on a complex web of IT processes running across a wide variety of applications and platforms.
“The goal is to be efficient and complement the various applications and technologies you bring into your organization to drive your business forward,” Kevin says.
Here are just a few of the most important benefits of end-to-end automation:
- Enforce cross-platform and cross-application dependencies for workflow unification
- Improve consistency and reliability of process execution
- Reduce cost and management effort while improving accessibility within the organization
- Gain a consolidated view of what’s going on across the entire environment
- Automatically identify and respond to issues should they arise
- Provide timely, targeted, and personalized notifications for when manual intervention is required
Solutions for End-to-End Automation
To achieve end-to-end automation, you’ll need to build a strategy using a couple different types of automation solutions that can work together—not in silos. The main components of a solid foundation are workload automation and robotic process automation.
Workload automation (WLA) handles the back-end IT processes that keep your business going. WLA and enterprise job scheduling are designed to schedule, initiate, run, and manage IT tasks related to any business process and transactions. It’s often most used by IT operations teams.
Robotic process automation (RPA) tackles the front-end business processes. By using software bots as digital coworkers alongside your human employees, RPA eliminates the repetitive, manual tasks to boost productivity so your team can keep their focus on more strategic work.
Achieve End-to-End Automation with HelpSystems
HelpSystems is an automation software company that offers leading automation solutions—from the desktop to the server to the network. With the right automation tools, your business can increase productivity, reduce operational costs, improve accuracy, and maximize efficiencies across your IT and business processes.
Stop relying on manual processes or custom scripts. Take back control and embrace a holistic approach to automation—from the back office to the front office. It’s possible with automation solutions from HelpSystems.
Source: HelpSystems
What is the 3-2-1 Backup Rule?
The 3-2-1 backup rule states that you should have 3 copies of your data, 2 different backup formats, and 1 backup stored offsite. This rule was first established by U.S. photographer Peter Krogh in the early 2000’s and has gone on to stand the test of time and is still relevant today.
Backup Vs Business Continuity & Disaster Recovery (BCDR)
However as variations of this rule have developed and businesses try to ensure a more resilient data model, the rule has become just 1 part of an overall protection plan. Most businesses now create and deploy a BCDR or Business Continuity & Disaster Recovery Plan which not only ensures reliable backups of data but also focuses on time of recovery.
Why Use the 3-2-1 Backup Strategy?
The 3-2-1 rule still has value, especially for businesses who aren’t backing up at all. But today, the gold standard is evolving. As businesses develop, most will partner with an MSP or Managed Service Provider to ensure that their IT infrastructure runs smoothly.
One of the key parts of a managed service is to prepare for downtime or a disaster event. The idea of 3-2-1 backup rule is to protect against a single disaster such as a fire or flood in the office, in this situation you would be able to recover from your offsite backup.
However over the years where threats have become more aggressive and reliance on IT grows this rule is no longer enough.
Variations of the 3-2-1 Strategy
Over the years there have been multiple variations of the 3-2-1 rule such as 3-2-1-1-0 and 4-3-2 however these have their own range of issues including costs and time to manage the infrastructure that goes with these strategies.
3-2-1-1-0
3-2-1-1-0 is built on the same foundation as the 3-2-1 rule however it goes a step further by stipulating an additional “Air Gapped” or offline backup and adding a check process to ensure all backups have zero errors.
4-3-2
Suggests that for businesses being managed by MSPs or IT Service Providers you have 4 copies of your data, stored across three locations (Onsite as source, onsite with the MSP and one in the cloud), with two of these being offsite.
Drive efficiency with an automated BCDR Solution – Datto SIRIS
Datto is one of the pioneers of the All-in-one BCDR solution that removes a lot of manual setup, expensive cost and human error in handling different media types across multiple locations.
Datto SIRIS is a flexible BCDR solution that stores a copy of your data locally, and in our cloud that’s built on an immutable storage model, you also have the ability to replicate that data to a secondary datto cloud location for extra resilience.
With our end to end backup encryption, advanced backup verification and mandatory 2FA sign on to access backup data and recover (both locally and from the cloud) you can be confident that your backups are secure and ready for when you need them.
Source: Datto
[vc_row][vc_column][vc_column_text]
Admin, superuser, root – different names for the same concept: an account that has total control over a system. In the Windows world, this account is called Administrator. On Linux and Unix, the account is root. In the Mac world, the account is Admin if you’re working in the UI, and root if you’re in the command line.
No matter what these highly privileged accounts are called, they hold great power over the system and, as they saying goes, “with great power comes great responsibility.” This is why most companies apply the principle of least privilege (PoLP) as part of their security program. PoLP can include, enforcing separation of privileges, such as breaking up administrative responsibilities across different operations accounts; rather than having a single account that can add/delete users, change configurations, and run backups.
Privileged access security: 6 tips for mutlicloud environments
1. Get Your Identity House in Order
2. Focus on Admin
3. Time is on Your Side
4. Modernize Password Management
5. Normalize Cross-Cloud Privilege
6. Optimize and Trace
[/vc_column_text][vc_button button_color=”color-150912″ size=”btn-xl” radius=”btn-round” border_width=”0″ link=”url:https%3A%2F%2Fwww.beyondtrust.com%2Fwebinars%2Fpolp-in-a-multi-cloud-world||target:%20_blank|”]For a deeper dive on this topic: PoLP in a Multicloud World.[/vc_button][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_column_text]Source: BeyondTrust[/vc_column_text][/vc_column][/vc_row]
This is a highly anticipated product release, which couldn’t come at a better time.
If you’re already thinking of replacing a firewall, then it’s very likely that other pieces of network infrastructure are also under discussion. If you’re replacing your Wi-Fi, as soon as you have more than a couple of access points, you need something to power them or the search for available power sockets starts. Or maybe you need to separate IoT devices from other business devices on the network in one of your many remote offices. The answer is almost always a switch. And if everything comes from a single vendor, you can generally improve your network visibility, reduce your management overhead, and potentially also optimize the price.
While switches may not be the first products you think of when considering cybersecurity, access layer switches are generally the gatekeepers for device access to the rest of the network, and as if that weren’t enough, they’re the masters of segmentation. I’m sure we’ve all learned in our networking 101 best practices book, network segmentation is key when it comes to minimizing the exposure of a network in case of a breach, as it prevents lateral movement. Of course, many other solutions also have their role to play in that scenario, but you should never underestimate the role a switch can play.
And so, by popular demand, we’re now introducing switches.
The Sophos Switch Series
We will initially offer eight models, with two more expected towards mid-2022. Here’s a snapshot of the key specifications.

All switches can be managed in Sophos Central alongside your other Sophos products, however, the full feature set and configuration will only be available via the local web user interface from the first release. Management is also supported using the Command Line Interface (CLI) or Simple Networking Management Protocol (SNMP).
Sophos Central will be the key to some unique features in the future and yes, we do eventually plan to offer synchronized security, however, there is no final date for the introduction of that functionality that we can communicate at this time.
If you’re one of the many businesses struggling with ever-more devices to connect and power and are looking for a way to take back control of your network, Sophos Switch may just be the perfect solution. Our switches are ideal for small and medium-sized business, branch offices, retail, services, even remote and home offices will benefit from a more business-oriented setup, now that many of those have gone from being temporary to permanent.
While launching a hardware product in the current climate takes a bit of coordination, we will have first limited quantities available from December 16 and volumes will ramp up from January 2022 onwards. We plan to do the official market announcement for these products on January 11.
Further information is available on our website under sophos.com/switch.
Source: Sophos
Understandably, the terms data security and data privacy are frequently muddled together and sometimes used interchangeably. While they are naturally connected, they are also unique and separate concepts.
To help ensure the data your customers and employees entrust to your organization is both handled appropriately and secured throughout its lifecycle, review these concepts, along with their associated policies, procedures, and technologies, to help prevent malicious or unintentional misuse or loss of data.
What is Data Privacy?
Data privacy focuses on how personal data is collected, used, and shared – in other words, its governance. Regulations and laws addressing data privacy can vary by state and country in terms of how stringent they are and how they are enforced.
Worldwide, countries are coming to the realization that the strict guidelines designed to protect personal data privacy are in the best interest of both an organization and individuals. The European Union’s General Data Protection Regulation (GDPR) is the strictest regulation to date, with other countries modeling regulations after the privacy mandates of the GDPR. Some of note: the California Consumer Privacy Act (CCPA), Brazil’s Lei Geral de Protecao de Dados (LGPD) and Canada’s proposed Digital Charter Implementation Act, to name a few.
While these enacted and proposed regulations are a huge step in ensuring data privacy, without a solid data security foundation and technological solutions in place, data privacy simply cannot happen.
What is Data Security?
Data security, as opposed to data privacy, focuses on how data is protected from the many external and internal threats that exist. Data security policies and procedures can mitigate cyberthreats and inadvertent misuse; however, just putting these measures in place does not typically fully address data privacy concerns and regulations.
Data security encompasses the actual solutions an organization puts in place to protect digital data at all points – from endpoints to networks to the perimeter.
A comprehensive data security policy should form the blueprint for your data security measures and cover three key areas: people, processes, and technological solutions to help enforce any policies set to surround and protect sensitive and private data.
What’s the Difference Between Data Privacy and Data Security?
First, data privacy is NOT the same as data security. Data security is all the measures, policies, and technologies taken to protect data from external and internal threats. However, applying data security measures alone does not necessarily satisfy data privacy requirements. Data privacy still requires adherence to regulations surrounding how the data organizations secure is collected, shared, and used.
Data security protects data from malicious threats; data privacy addresses responsible governance or use of that data.
When developing data security policies, the focus of protection measures is on preventing unauthorized access to data. Tools such as encryption, user authentication, and tokenization can all amp up an organization’s security stance.
When tackling data privacy concerns, the focus is on data being procured, processed, stored and sent in compliance and with consent of the data subject. If an organization is gathering data, individuals need to know what type of data will be collected, why it is needed and who will share this data for transparency. In addition, the data subject needs to agree to these terms.
Using data with respect to an individual’s privacy is the key to data privacy. Data security measures can help ensure that personal identification in collected data is protected.
Protect Data Privacy and Security with Layers of Security Solutions
Is there a singular solution to offer protection? No. However, establishing policies and procedures to address sensitive data protection, as well as layering security solutions, can provide outstanding protection to data throughout its lifecycle.
Layering solutions can address both privacy and security concerns. When choosing technology to support your organizational privacy and security policies, check to ensure that the solutions can easily integrate to address these three key tactics:
- Identify and classify files that may contain sensitive data
- Encrypt data to render sensitive data unreadable unless authorized
- Detect and prevent leaks of sensitive information outside your organization
- Secure and protect sensitive data that is shared inside and outside your organization
- Manage rights to digital data to encrypt and control access to data no matter where it travels
HelpSystems offers a suite of data security solutions, including data loss protection, identification and classification, secure managed file transfer, and more.
Source: HelpSystems
Customers have spoken–naming Sophos an October 2021 Gartner Peer Insights Customers’ Choice for Endpoint Protection Platforms (EPP). What’s more, Sophos is the highest rated and most reviewed vendor, and the only vendor to be named a Customers’ Choice in all four global deployment regions: North America, EMEA, Latin America, and Asia Pacific. Across 505 independent reviews, customers overwhelmingly recommend Sophos, with an average rating of 4.8 out of 5 as of 31st August 2021.
Based solely on independent customer reviews that have been rigorously evaluated by Gartner, we believe this nomination is testament to the unparalleled real-world protection, detection, and response that Sophos delivers every day to enterprise customers around the globe.
Double recognition is a double honor
This distinction follows hot on the heels of Sophos being named a Leader in the 2021 Gartner® Magic Quadrant™ for Endpoint Protection Platforms (EPP) in May 2021. To be recognized by both our customers and Gartner analysts this year is a double honor in our view and we could not be more proud.
The voice of the customer
Gartner Peer Insights shares the independent voice of verified enterprise customers. Recent feedback on Sophos’s endpoint protection includes:
“Detection & protection that truly keeps up with the ever-growing threat landscape”
Manufacturing, $50M–$250M, North America
“The deep learning and artificial intelligence give an excellent detection response which has led to a significant decrease in ransomware attacks”
Retail, $10B–$30B, Asia Pacific
“Zero-day detections are excellent. We’re notified of threats by Sophos often before our SOC knows what may be going on”
Manufacturing, $500M – $1B, North America/Latin America/Asia Pacific
These are just three of over 750 Sophos endpoint protection customer reviews available on the Gartner Peer Insights site. I would like to take this opportunity to thank our customers who have shared their feedback; we truly appreciate your time and your trust.
Optimize prevention. Minimize time to detect and respond
Sophos Endpoint gives you world-leading prevention, detection and response capabilities designed for real-world environments. Whether you choose to manage your security yourself or have our team do it for you, you are backed by unparalleled human and technical expertise.
Optimize prevention
No one is more focused on preventing attacks than Sophos and over the past year independent 3rd party testing shows we stop, on average, 99.98% of all threats. We achieve this via a two-pronged strategy:
Reduce the attack surface, removing opportunities for attackers to penetrate your organization. This includes:
- Blocking potentially unwanted applications and malicious or suspect websites based on content or URL rating
- Controlling what applications and devices are allowed to run
- Locking down server configurations in a single click
Prevent attacks from running, using layered protection technologies to stop both the threats and the tactics attackers use:
- AI-based behavior prevention blocks the unknown based on techniques, behaviors, and anomalies
- Behavior-based anti-ransomware technology prevents attackers from encrypting your files
- Exploit prevention stops the techniques attackers use, protecting against attacks that leverage previously unknown vulnerabilities
By stopping attackers from gaining a foothold, Sophos reduces the signal-to-noise ratio, enabling defenders to focus on fewer, more accurate detections.
Minimize time to detect and respond
Our robust tools and human expertise quickly identify, defuse, and eject attackers before they can take control.
- We provide 24/7/365 threat hunting and neutralization delivered as a fully-managed service by Sophos experts
- Our team becomes your team, and our threat hunting expertise helps augment and extend your team
- The open Sophos XDR platform integrates with your existing security operations (and we’re proud to be named a Representative Vendor in the new Gartner Market Guide for XDR)
Ultimately this approach delivers superior security outcomes for our customers: better protection, reduced risk, and lower total cost of ownership (TCO).
Learn more
To dive deeper into these independent reviews of Sophos’ endpoint protection, I encourage you to:
- Review the October 2021 Gartner Peer Insights Customers’ Choice for endpoint protection platforms (EPP)
- Read the 750 verified customer reviews on Gartner Peer Insights site
- Check out the 2021 Gartner Magic Quadrant for Endpoint Protection Platforms
If you’d like to discuss your endpoint security requirements and how Sophos can help, please reach out to your Sophos representative or speak with our in-house team who would be delighted to help.
Source: Sophos
BeyondTrust announced the release of BeyondTrust Cloud Privilege Broker, a new solution built from the ground up to help customers regain control over critical cloud infrastructure and better communicate and mitigate risks associated with multicloud entitlements. Cloud Privilege Broker empowers customers with a centralized, efficient, and granular way to manage thousands of permissions and entitlements across their cloud footprint.
Cloud Privilege Broker is BeyondTrust’s first product in the Cloud Infrastructure Entitlements Management (CIEM) space. With this solution, we are leveraging our experience and know-how in managing privileged access and applying the principle of least privilege (PoLP), and extending it to cloud infrastructure. Cloud Privilege Broker helps organizations defend against data breaches, malicious attacks, and other risks posed by excessive cloud permissions.
As organizations accelerate their digital transformation projects and migrate more and more resources to the cloud, the proliferation and complexity of cloud services has led to a skyrocketing of over-permissioned identities. Organizations increasingly struggle with identifying who has access to what data and resources across which cloud platforms. This gap in visibility creates a risky environment, putting pressure on IT and security teams already taxed with limited tools and resources. To mitigate this risk, organizations must implement effective cloud infrastructure security controls to avoid leaving their cloud environments open to attack.
Cloud service providers (CSPs), such as Amazon Web Services and Microsoft Azure, have their own identity and access management tools, with unique language and security responsibility models; but these tools are designed only for their own environments, which means managing permissions across multiple clouds requires a ‘swivel chair’ approach from console to console. This siloed approach is inefficient, it increases the risk of a breach, and amplifies the costs for non-compliance.
BeyondTrust Cloud Privilege Broker gives IT and Security teams immediate visibility of permissions and entitlements with the discovery of users, roles, and policies across multiple platforms—via a single console. As a cloud-hosted SaaS offering, the solution can be deployed quickly with immediate classification of risk. Cloud Privilege Broker prioritizes a list of critical items and provides guided remediation, across different platforms, dramatically improving your cloud security posture.
We are excited about the fast time-to-value we can offer our customers, with a deployment that can be done within an hour. We have leveraged our deep expertise in managing privileges to naturally extend to helping our customers secure their infrastructure across multiple clouds, significantly reducing risk and improving overall visibility and security.
Multicloud Security, Made Simple
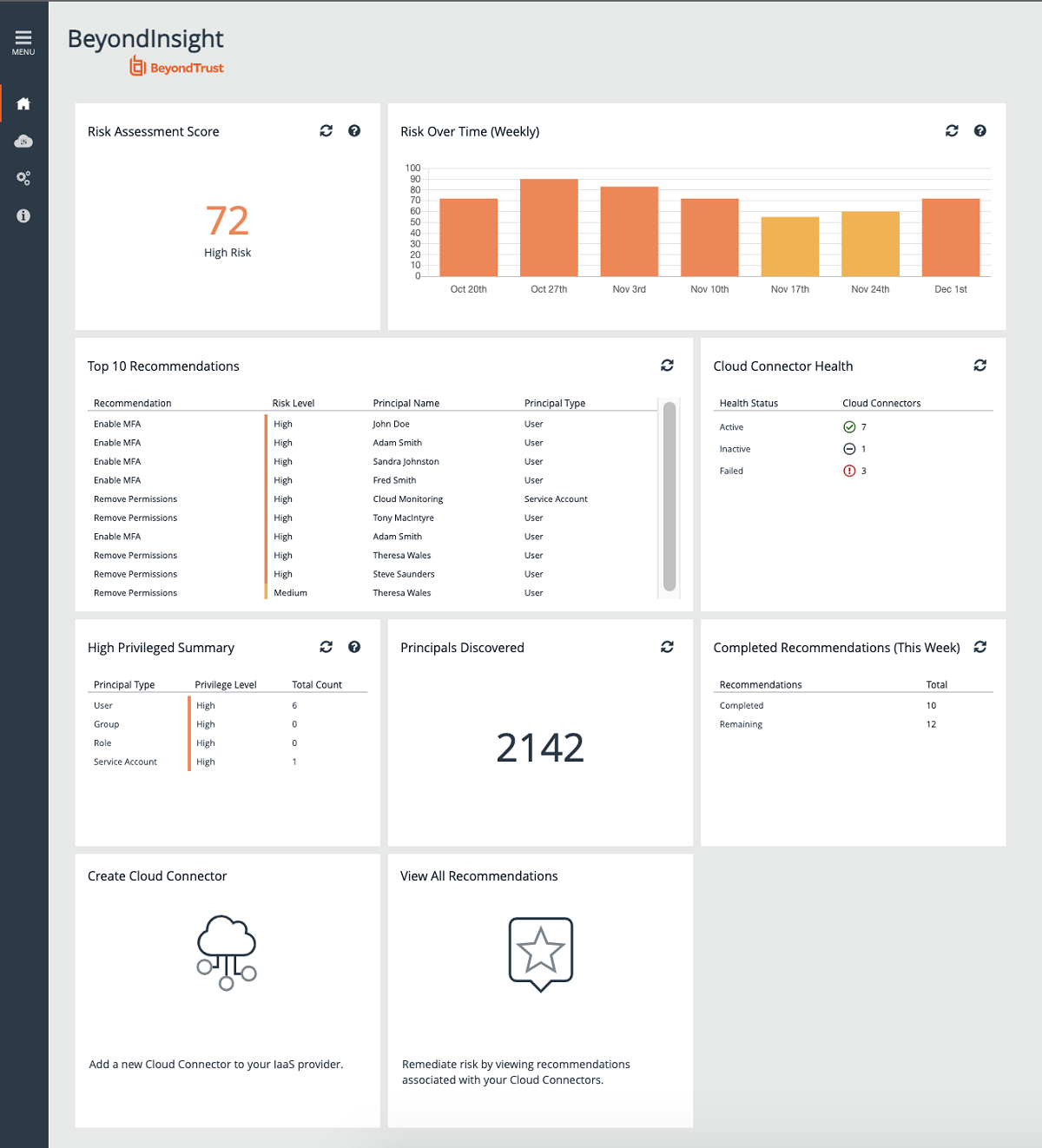
BeyondTrust customers have impressed upon us the importance of understanding and communicating the risk associated with cloud permissions and entitlements. For this reason, we have created a simple, user-friendly, but effective, dashboard that provides an overall risk score and risk-over-time.
We believe that the best way to mitigate cloud risk and work towards a zero trust model is through the implementation of least privilege policies. We help our customers accomplish this with granular recommendations and guided remediation. This approach removes uncertainty and ensures that the mitigation efforts are as effective as possible by tackling highly privileged items first.
Cloud Privilege Broker is deployed on our BeyondInsight platform, providing a familiar user interface and experience for BeyondTrust customers. The solution enables organizations to:
- Gain immediate visibility over permissions and entitlements across multicloud infrastructure
- Rapidly identify high-privileged users
- Simplify management of entitlements by providing granular recommendations for implementing policies across cloud platforms, from a single interface
- Mitigate privilege creep by continually exposing and right-sizing excessive permissions
- Understand the risk associated with entitlements, with a single risk score
- Track mitigation efforts with a view of risk over time
- Help security and audit teams meet and prove compliance with a view of completed recommendations and an audit trail.
With Cloud Privilege Broker, you have centralized, efficient, and granular management of thousands of cloud permissions and entitlements that puts teams back in control of their critical infrastructure, significantly reducing the risk of a data breach. Cloud Privilege Broker is built on a modern cloud technology platform that leverages a microservices architecture, enabling built-in scalability and resilience.
Cloud Privilege Broker is now available. Learn more.
Source: BeyondTrust
We are pleased to announce that Sophos Intercept X has received ‘Top Product’ certification in AV-TEST’s October 2021 testing for Windows devices. This follows a perfect score for protection, usability and performance in the June 2021 testing for macOS devices and ‘Approved’ certification in the July 2021 test for Android devices.
These AV-TEST awards are among a number of recent highlights for Sophos Intercept X:
SE Labs
SE Labs named Intercept X as the ‘Best Enterprise Endpoint Solution’ in their 2021 Annual Report. This fantastic achievement follows Intercept X receiving Best Small Business Endpoint Solution for two years running in the SE Labs 2019-2020 Annual Reports.
Gartner®
Gartner recently published its first-ever Market Guide for Extended Detection and Response (XDR) which provides guidance for security and risk management leaders considering investments in XDR. Sophos is named among a shortlist of 12 Representative Vendors offering an XDR solution.
Earlier this year, Sophos was named a “Leader” in the 2021 Gartner Magic Quadrant for Endpoint Protection Platforms (EPP) for the 12th consecutive report. While other vendors come and go, Sophos continues to lead.
Sophos Intercept X endpoint protection is rated 4.8/5 on Gartner Peer Insights as of November 26, 2021, based on 577 verified reviews over the previous 12 months.
CRN
Sophos MTR won the award for ‘Best Managed Detection and Response’ at the CRN 2021 Tech Innovator Awards. With Sophos MTR, organizations benefit from 24/7/365 threat hunting, detection and response, delivered as a fully-managed service by our expert operators.
Try Sophos Intercept X today
Activate a free trial today and take Sophos Intercept X for a test drive. It combines industry-leading prevention capabilities that block ransomware, exploits and never seen before malware with powerful XDR for advanced threat hunting and IT operations.
Source: Sophos
Branch networks are present in several industries, but they often share common needs. Here are five present trends when it comes to branch networking.
Centralized and Remote Management
Despite the challenges brought, COVID-19 couldn’t stop all businesses from growing. It might even have made them stronger! Enterprises that know how to make use of a quality branch network system are the ones who thrive in these difficult times. With employees working from home and the business environment being uncertain, you should be able to manage all branches without a hitch from one location, be it the headquarters, a data center, or simply your home office.
Enhanced Security
Moving everything from the data center to the cloud is, in no doubt, more efficient and convenient, but is it safe? Gartner introduced the concept of SASE (Secure Access Service Edge) in 2019. However, enterprises are still concerned about the cybersecurity of their branch networks in 2021. When cyberattacks only get more aggressive over time, it is time to review your current branch network infrastructure to make sure all your data and top business secrets are in good hands.
Ready for 5G
More and more enterprises will be using 5G technology as it becomes more prominent and it enables rapid development of new branches. When it comes to connectivity, speed is not everything though. Other than using 5G, you also need to ensure that the network you are using is reliable anytime anywhere.
Automation and AI Support
You may not need a robotic arm at your store to impress customers, but automating your services and using artificial intelligence will definitely add value to your business. By incorporating IoT-friendly devices into your network infrastructure, you will not only increase the efficiency and cut the cost of your branches in the long term, but also enhance the customer experience and upgrade your brand image.
MPLS Replacement
We all know about the benefits of implementing SD-WAN solutions and the importance of replacing the expensive MPLS (Multiprotocol Label Switching). While fancy new technologies might seem like the perfect solution for your branch networking, it is easy for us to omit the fact that the hard part is the integration. Thus, other than looking for cool and cutting-edge devices, you may also consider the flexibility and versatility of the new solution.
Source: Peplink
Dec
Τα δίκτυα υποκαταστημάτων βρίσκονται σε πολλούς διαφορετικούς κλάδους, ωστόσο πολύ συχνά μοιράζονται τις ίδιες ανάγκες. Παρακάτω, ακολουθούν πέντε τρέχουσες τάσεις όσον αφορά τη δικτύωση υποκαταστημάτων.
Κεντρική και Απομακρυσμένη Διαχείριση
Παρά τις προκλήσεις που έφερε, πανδημία του νέου κορωνοϊού και η ασθένεια COVID-19, δεν κατάφερε να εμποδίσει την ανάπτυξη όλων των επιχειρήσεων. Ενδεχομένως μάλιστα να τις έκανε και πιο δυνατές!
Οι επιχειρήσεις που γνωρίζουν πως να κάνουν χρήση ενός ποιοτικού συστήματος δικτύωσης υποκαταστημάτων είναι εκείνες που ευδοκιμούν σε αυτούς τους δύσκολους καιρούς. Με τους υπαλλήλους -σε πολλές περιπτώσεις- να εξακολουθούν να εργάζονται από το σπίτι και το επιχειρηματικό περιβάλλον να παραμένει αβέβαιο, οφείλετε να είστε σε θέση να διαχειρίζεστε όλα τα υποκαταστήματα σας απροβλημάτιστα από μία τοποθεσία, είτε πρόκειται για τα κεντρικά σας γραφεία, είτε πρόκειται για κάποιο κέντρο δεδομένων είτε απλώς από το οικιακό γραφείο σας.
Ενισχυμένη ασφάλεια
Η μετάβαση -όλων των επιχειρηματικών σας δραστηριοτήτων- από το κέντρο δεδομένων στο cloud ενισχύει αναμφισβήτητα την αποτελεσματικότητα και την ευκολία, ωστόσο είναι παράλληλα και ασφαλής; Μπορεί η γνωστή εταιρεία Gartner να εισήγαγε την έννοια του SASE (Secure Access Service Edge) το 2019, οι επιχειρήσεις ωστόσο δύο χρόνια μετά εξακολουθούν να ανησυχούν για την κυβερνοασφάλεια των δικτύων υποκαταστημάτων τους το 2021. Όταν οι κυβερνοεπιθέσεις με την πάροδο του χρόνου γίνονται όλο και σφοδρότερες, είναι καιρός να αναθεωρήσετε την τρέχουσα υποδομή του δικτύου υποκαταστημάτων σας για να διασφαλίσετε ότι όλα τα δεδομένα και τα κρίσιμης σημασίας επιχειρηματικά μυστικά σας βρίσκονται σε καλά χέρια.
Έτοιμοι για το 5G
Όλο και περισσότερες επιχειρήσεις θα ξεκινήσουν να χρησιμοποιούν την τεχνολογία 5G καθώς γίνεται όλο και πιο απαραίτητη επιτρέποντας παράλληλα την ταχεία ανάπτυξη νέων υποκαταστημάτων. Πάντως, πρέπει να έχετε στο νου σας, ότι όταν πρόκειται για συνδεσιμότητα, η ταχύτητα δεν είναι αυτοσκοπός και σίγουρα δεν είναι το παν. Εκτός από τη χρήση της τεχνολογίας 5G, θα πρέπει επίσης να διασφαλίσετε ότι το δίκτυο που χρησιμοποιείτε είναι αξιόπιστο οπουδήποτε και ανά πάσα στιγμή.
Αυτοματισμοί και Τεχνητή Νοημοσύνη
Μπορεί να μην απαιτείται η ύπαρξη ενός ρομποτικού βραχίονα στο υποκατάστημα σας για να εντυπωσιάσετε τους πελάτες σας, ωστόσο η αυτοματοποίηση των υπηρεσιών σας και η χρήση Τεχνητής Νοημοσύνης αποτελούν προστιθέμενη αξία για την επιχείρηση σας. Με την ενσωμάτωση φιλικών προς το IoT συσκευών στην δικτυακή υποδομή σας, όχι μόνο θα αυξήσετε την αποτελεσματικότητα και θα μειώσετε το κόστος των υποκαταστημάτων σας μακροπρόθεσμα, αλλά θα βελτιώσετε την εμπειρία των πελατών σας και θα αναβαθμίσετε την εικόνα της επιχείρησης σας και του brand σας.
Αντικατάσταση MPLS
Όλοι γνωρίζουμε τα οφέλη της εφαρμογής λύσεων SD-WAN και τη σημασία της αντικατάστασης των ακριβότερων MPLS (Multiprotocol Label Switching). Αν και οι «φανταχτερές» νέες τεχνολογίες μοιάζουν πολλές φορές ως η τέλεια λύση για τη δικτύωση των υποκαταστημάτων σας, είναι απαραίτητο να επισημάνουμε ότι το δύσκολο κομμάτι είναι η ενσωμάτωση. Επομένως, εκτός από την αναζήτηση μοντέρνων και πρωτοποριακών συσκευών, μπορείτε επίσης να λάβετε υπόψη την ευελιξία και την προσαρμοστικότητα της νέας λύσης σας.
Πηγή: Peplink
We are thrilled to announce that Sophos Intercept X has been named as the Best Enterprise Endpoint Solution in the SE Labs 2021 Annual Report.
This fantastic achievement follows Intercept X receiving Best Small Business Endpoint Solution for two years running in SE Labs 2019-2020 Annual Reports. We believe this recognition is due to our combination of prevention, detection and response that blocks threats before they impact your environment.

Get industry leading protection
Sophos Intercept X gives your organization powerful protection against the very latest threats.
Stop threats early
Neutralizing an attack before it impacts your environment is key, not relying solely on manual investigation and response.
- Reduce the attack surface. Control apps and devices, block risky websites and PUAs and neutralize malware even when it hasn’t been seen before
- Stop ransomware. Block malicious encryption processes and rollback affected files to a safe state
- Lock down exploit techniques. Stop exploits frequently used by attackers such as privilege escalation and credential dumping
Minimize time to detect
When investigating suspicious activity or IT operations issues, breadth of data and context are vital for making quick, informed decisions.
- Eliminate noise. A strong layer of automated defenses means there is less to investigate, saving you time
- Prioritize effectively. Utilize a prioritized list of suspicious items for investigation with guided actions for faster response
- See your entire environment. Native integration of endpoint, server, firewall, email, and cloud data sources means you see everything that happens in your organization
Minimize time to respond
Speed is of the essence when dealing with an active threat, making automated responses crucial.
- Respond automatically. Detected threats are automatically cleaned up and a threat case generated
- Get products that collaborate. Cross-product integrations will automatically isolate compromised devices, show all active applications, lock out WiFi connections and more
- Rest easy with managed security. Choose a fully managed 24/7 security service run by Sophos cybersecurity experts
Take a free trial or learn more about Intercept X.
Source: Sophos
In typical computing environments, an identity represents a one-to-one relationship between a carbon-based life and their digital presence. Their digital presence, however, can have multiple accounts, multiple credentials, and an infinite number of entitlements in electronic format.
With that short intro aside, let’s now consider the top 6 problems a CISO may experience.
1. Employees with the Same (or Similar) Names
2. Floating Employees
3. Over-Provisioning
4. Mergers and Acquisitions
5. Non-Human Identities
6. Vendor / Third-Party Identities
One thing is certain, if you build a new environment from scratch, you certainly should consider these problems at the outset so they do not escalate as your organization grows.
Read more on BeyondTrust
[vc_row][vc_column][vc_column_text]
SophosLabs, the Sophos Managed Threat Response team, and the SophosAI data science group releases our 2022 Threat Report this morning. This report represents the collective wisdom of our malware analysts, the machine and network forensics specialists, and machine learning experts that make up these core teams within Sophos, and offers some analysis of the events that transpired in 2021, and how we believe they will help shape the threat landscape in 2022 and beyond.
While you can download and read the report in its entirety, we wanted to share some of the insights covered in the report to give you a taste.
The report is organized into five parts, in which we cover the ransomware epidemic and its aftermath, trends in conventional malware that targets Windows computers, malware on mobile platforms, security threats to infrastructure, and a section that covers the field of artificial intelligence, and how it applies to the practice of information security.
The fight against ransomware
Our ransomware coverage in 2021 was led by a hybrid team of analysts, some of whom reverse-engineer and study malware behavior, and others who step in to intervene in ransomware attacks targeting customers. The latter group, known as Sophos Rapid Response, had a busy year dealing with a variety of ransomware families, and the threat actor groups whose work is to break in to organizations and deliver that ransomware into their networks.
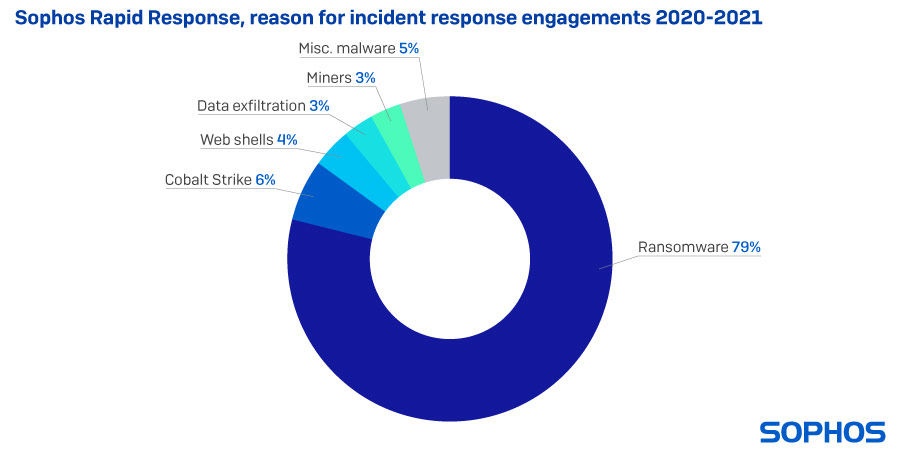
The vast majority of these customer engagements involved ransomware in 2021, but we were also asked to step in to help customers with cases involving Cobalt Strike, a commercially-marketed tool used legitimately by professional penetration testers and ‘red teams’ whose source code was leaked online in 2020. Criminals now routinely abuse these tools by delivering them as malware payloads. As a result of several high-profile vulnerabilities in Microsoft Exchange, we were called upon to deal with many more web shells than normal in 2020.
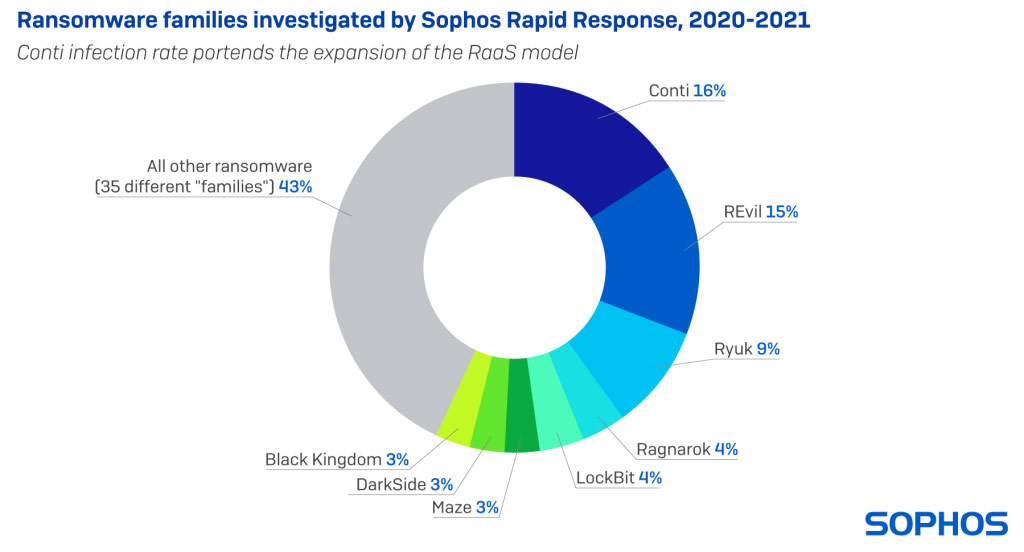
But the vast majority of cases involved ransomware, and among those, the Conti and REvil families were most frequently involved. Both Conti and REvil pioneered and developed the ransomware-as-a-service business model, where a small core team of developers built the ransomware itself, and a larger group of affiliates acted as the delivery mechanism, actively breaking in to networks by any means available: Brute-force attacks against internet-facing services; exploits of vulnerable software; and occasionally, by obtaining legitimate credentials from ‘initial access brokers,’ a type of criminal service provider.
Countering attackers at every turn
The SophosLabs team were called upon to improve our behavioral detection capabilities in 2021, and in so doing, we found that dual-use attack tools like Cobalt Strike were most frequently a component of the kinds of hands-on-keyboards attacks preferred by ransomware groups. But we also started to see other threat actors take advantage of a wide variety of commercial software and utilities designed for IT administrators or security professionals.
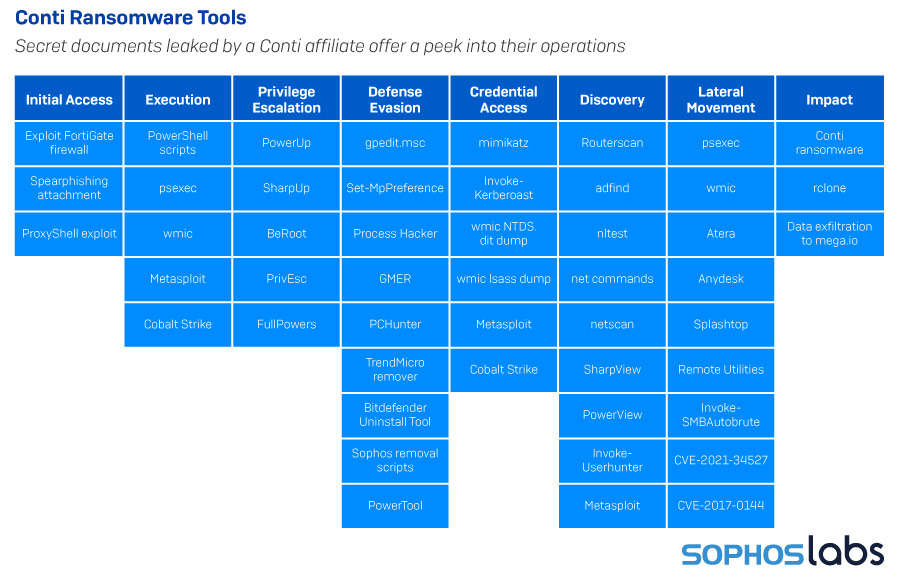
When an affiliate customer of the Conti ransomware leaked a playbook designed to help affiliates break in and steal information, we not only gained insight into the tools, tactics, and procedures of the Conti affiliates — it answered an important question about why, when we knew so many different groups had been active as Conti affiliates, their TTPs remains strikingly similar.
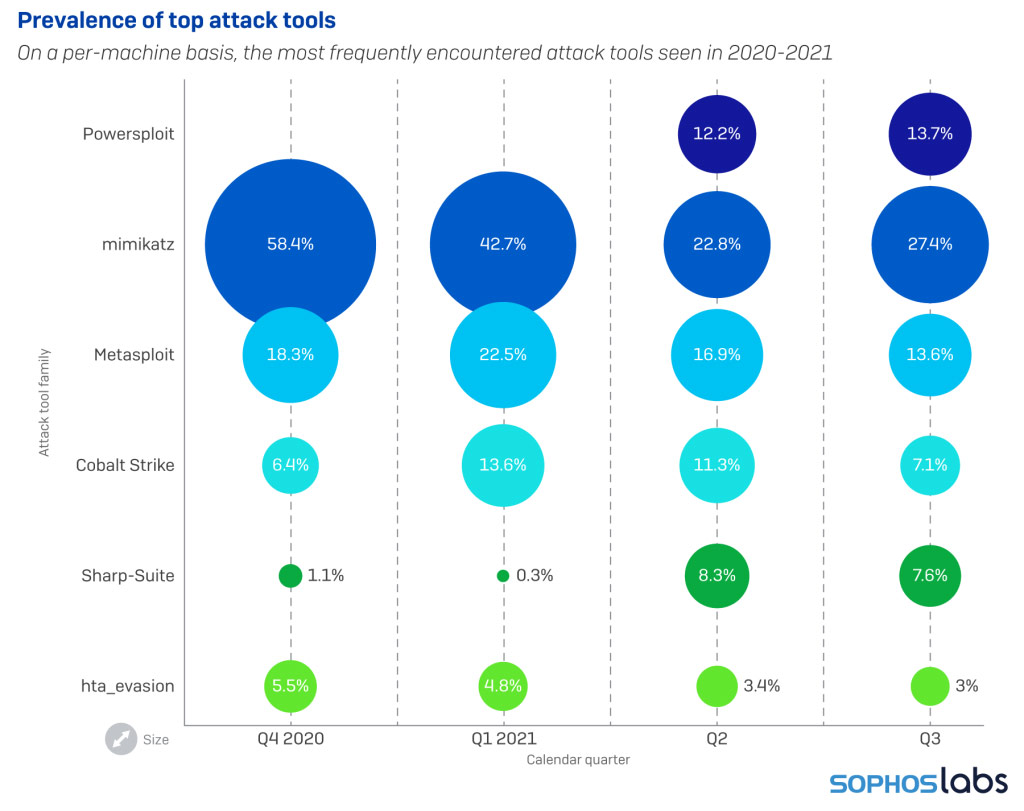
Among the attacker tools most commonly seen by our scanners, the mimikatz password sniffing and cracking tool was the one we most frequently discovered. Both the Metasploit framework and components of Cobalt Strike also came into play quite often, usually alongside a wide variety of other tools. Sophos currently tracks detections of more than 180 different software packages that fall into this grey area between explicitly malicious and completely benign software.
Android and iOS still under threat
Mobile platforms are increasingly under threat as we impart more of our daily computing tasks to these pocket computers. Scams and fraud account for a large part of the attacks we see on both Apple’s and Alphabet’s mobile platforms. Some of these are delivered by the platforms’ own app stores, but we’ve also seen a rise in malware that originates with a text message over SMS or a mobile chat platform like Telegram. Users on mobile devices often cannot tell where shortened links sent via these platforms will take them, and may lead the recipients into trouble.
For more on these stories, and other analysis of the threat landscape, check out the Sophos 2022 Threat Report.
Source: Sophos
[/vc_column_text][/vc_column][/vc_row]
For several years now, we’ve been hearing that MSPs will become obsolete, rendered unnecessary as businesses take advantage of more plug-and-play, cloud-based platforms, and tools. “Why use an MSP,” they say, “when in the very near future, I’ll just be able to buy all my services and monitoring in the cloud?”
But at Iconic IT, we’ve found just the opposite to be true. The more cloud-based tools we offer to small and medium-sized businesses, the more they seem to need our services. In a way, the move to the cloud has freed us, taking us away from wires and server rooms and into the boardroom. And Iconic has provided that leadership to our clients, in no small part because of our partnership with Datto.
There’s an abundance of cloud backup and monitoring systems out there, but we’ve found that Datto products have allowed us to do more and provide better for our clients. To put it simply, Datto tools have allowed us to be more:
1. Strategic
Cloud-based tools have taken away a lot of the grunt work, installations, and comms bottlenecks we used to know. And with Datto, we have visibility into our client’s entire network. And because it’s in the cloud, we don’t have to worry about our own hardware to maintain. We can manage all our client’s endpoints, and come back to them with focused, clear security advice. We can focus on the true issues because Datto filters out the noise. And when we make big cybersecurity saves, our clients can relax knowing we have their back.
That’s no small thing. When they know their basic security needs are covered, they have space to talk about their future needs. We can ask them questions like: how can we help you solve the issues you’ll be facing soon? And how can we build your tech infrastructure now, so you’ll have the right foundation to build on?
This kind of discussion led us to land a small bank system in the Denver area as a customer. We were able to consolidate all their backups and monitoring into one unified system—while helping them meet all their data regulatory requirements. They got better service, at a better price, and reduced their business headaches considerably.
2. Responsive
What will happen to my business if there’s a disaster? A power outage? Flooding? A massive ransomware attack? How quickly can you get my business up and running again?
This is the central question clients ask us, and we’d better have the right answer. We feel comfortable selling our Datto backup systems because we use them ourselves. And we’ve seen first-hand how well it works. Just last winter, for instance, we had a power outage at our headquarters in Rochester, New York that lasted for two days. When we had that snowstorm, our servers went down too. But we were able to run everything on Datto’s servers, and it worked just like our own on-site server rooms were operating. Our employees never knew the difference, and neither did our customers, who are relying on us to be able to keep their networks going.
3. Affordable
This may raise some eyebrows, but we’ve found the investment is worth it. Why? Because Datto was one of the first to market with their backup and monitoring technologies, and their systems are the most mature. Their systems work seamlessly with ours. The labor costs that save us are enormous, because it works every time, with very few hiccups.
Datto’s products also scale well, based on the size of our clients and their user base. As more providers like Datto provide this kind of price package, the more we can drive enterprise-grade security and backup to even the smallest of clients.
4. Ahead of the security curve
Cybersecurity has been topic number one for MSPs for a while now, as ransomware and hacking attempts have risen to near unimaginable levels. But it’s our job to imagine just how bad it can get, and keep encouraging our clients to invest.
Datto products help us get there because they’ve created a true partnership with MSPs. When monitoring tickets get to us, we know they’re actionable and worth our time. We never have to worry about whether our backups are going to work. We know they will.
Luckily, market forces seem to be pushing even smaller clients to invest in sophisticated cybersecurity tools. It doesn’t hurt that the Biden White House has taken on the cybersecurity of businesses as a national security issue. They will be issuing guidelines that will likely help us sell through complex security products like RMM.
With the right partnerships, the future looks bright
We firmly believe that MSPs will only continue to rise, as we combine our “friendly local IT guys” with the monitoring power and backup capacity of companies like Datto. Small businesses have always been the country’s great innovation engine. And as their tech partners, it’s up to MSPs like us to see that they keep pace. We’re looking forward to everything the future can bring us, and we hope you are, too.
Source: Datto
Whether you have no archiving or are simply using what’s built into Microsoft Exchange Server (on-premises), your archiving choice may be hurting the organization more than it’s helping.
The archiving of email from within Microsoft Exchange Server is a multi-faceted thing; many see the archive as a backup (which it can sort of act as one, but that’s not its’ purpose) for older email, while others see it as a means to offload unnecessary email to lower the storage load on Microsoft Exchange over time.
The reality is the archive is much more. The archive serves as a historical record of all email correspondence. It has a role in lawsuits, proving adherence to regulations, aiding in locating prior correspondence, or just helping a user find a forgotten email address of someone they previously communicated with.
The archive has the potential to become involved in many parts of operations, so it’s important to be sure the archiving methodology you have today is the correct one. But you may think whatever is in place now is just fine, but there are three reasons why you should consider your email archiving options.
Reason 1 – You May Not Be Meeting the Business Needs
Many times, IT folks start with the technology first and work their way back to business requirements. With email archiving having financial, legal, and technical implications, it’s imperative that you first understand what the business needs from archiving… and then go find the best way to implement it. For example, legal may want the email sent and received by specific roles within the organization to be held for, say, seven years, while finance wants to keep storage costs down and minimize any retention whatsoever, all while HR needs emails between two specific individuals held for 2 years in case of a lawsuit.
See? Everyone has their own needs – and it is possible to meet everyone’s requirement; you just need to start with the business needs and then determine first if your current archiving method meets those needs and if not, what solution will.
Reason 2 – Not all Archiving is the Same
There is no magic “archive this mailbox” checkbox and suddenly all the right emails are archived. The closest thing to this is Journaling within Exchange, where a copy of every email is stored. While comprehensive in scope, it may be overkill from both a storage and search perspective, making even this option less than viable. In addition to the “what” is archived, there’s also concerns around who can access the archive, is the data a read-only archive, is it secure, will it be available if Exchange is down, and more.
It’s important to list out the important criteria and expectations your organization have for an archiving solution, and to determine how each of your archiving choices meet the need.
Reason 3 – You May Be Missing the Compliance Mark
We’ve left compliance for last, as the growing list of compliance regulations continually makes archiving that much more complex.  Where one regulation mandates keeping specific email content for 5 years, another wants to keep a completely separate set of emails for 7 years. Sure, that Journaling option previously mentioned can do the trick if you keep everything for the longest duration required, but that method comes with a hefty storage and productivity price tag. It’s important to implement email archiving in a way that meets the specific needs of each regulation; with the newer laws spelling out hefty fines, the organization has to get the archiving right.
Where one regulation mandates keeping specific email content for 5 years, another wants to keep a completely separate set of emails for 7 years. Sure, that Journaling option previously mentioned can do the trick if you keep everything for the longest duration required, but that method comes with a hefty storage and productivity price tag. It’s important to implement email archiving in a way that meets the specific needs of each regulation; with the newer laws spelling out hefty fines, the organization has to get the archiving right.
Ready to Consider Your Options?
An email archive is a critical part of your messaging environment and not just a copy of old emails. Upon realizing its importance, you recognize the need to truly look into whether native options meet the need or not. Your next steps are to determine what business factors will influence your archiving needs and evaluate your archiving options – whether they rest within Exchange itself or are third-party.
Source: MailStore
This month marks the two-year anniversary of the launch of Sophos Managed Threat Response (MTR), our 24/7 human-led threat hunting, detection, and response service.
As we celebrate, we are excited to announce another milestone: Sophos MTR now protects more than one million devices!
This impressive achievement follows substantial growth in the number of organizations that rely on Sophos MTR to keep them safe from cyber threats. We’ve seen more than 500% growth since August 2020, when we announced that Sophos MTR had eclipsed the 1,000-customer mark. Now, we protect more than 6,000 customers.
This exceptional growth rate is a testament to the threat hunting and remediation expertise of our global, 24/7 team.
What is driving so many organizations to choose Sophos Managed Threat Response?
- Industry-best expertise: Finding and retaining skilled staff is a huge challenge for organizations of all sizes. In fact, according to a 2020 survey of 5,000 global IT managers, 81% of organizations said their ability to find and retain skilled IT security professionals is a major challenge to their ability to deliver IT security – with more than a quarter saying it’s their “single biggest challenge.” Sophos MTR provides peace of mind that you’re backed by an industry-best team of security experts who are working 24/7 to protect your organization. They’ve seen and stopped it all, and they’ve got you protected – all at a lower total cost compared to building similar functionality in-house.
- Ransomware: It’s no surprise that the single biggest threat driving interest in Sophos MTR is ransomware. The statistics behind ransomware are shocking. In the past year, 37% of organizations were hit with ransomware, and criminals were able to successfully succeed in encrypting victims’ data more than half the time. Unfortunately, even for organizations who pay the ransom, on average only 65% of the encrypted data is restored, which is why it’s increasingly important to neutralize attacks before the adversaries achieve their goals. With an average recovery bill for a ransomware attack of $1.85M (considering downtime, people time, device cost, network cost, lost opportunity, and ransom paid), the business decision to go with a managed detection and response (MDR) provider like Sophos MTR is very clear.
- Hands-on-keyboard response: Many MDR providers simply notify customers of attacks or suspicious events, which means it’s then up to the customers to manage things on their own. Sophos MTR stands apart from other services by providing targeted hands-on-keyboard response for all customers to stop attacks before damage can occur. It’s the “R” in “MDR” – and it’s available at no additional cost.
- We’re part of your team: Sophos MTR customers love to tell us that they feel like we’re part of their in-house team. Continual communication and openness strengthens a real partnership, helping each customer improve their broader security posture. For example, if one of our customers is concerned about a particular threat – perhaps because a peer in another organization was impacted – they can reach out to the MTR team and we’ll start a threat hunt to ensure they’re safe.
The best news is that we’re just getting started! We continue to expand our global team and further develop our world-leading detection and response capabilities in partnership with the experts in SophosLabs and SophosAI.
To discuss how Sophos MTR can support your organization, speak to your Sophos representative.
Source: Sophos