News
We’re thrilled to unveil Sophos Intelix for Microsoft 365 Copilot, a powerful new integration that brings world-class threat intelligence from Sophos X-Ops directly into your daily workflow to enhance your cybersecurity outcomes.
Security analysts and IT professionals can instantly access, investigate, and respond to emerging cyber threats right from the Copilot chat interface, without leaving the Microsoft 365 environment, accelerating attack neutralization. This seamless experience transforms threat intelligence from a separate resource into an actionable, always-on ally that accelerates decision-making, strengthens cyber resilience, and fuels more effective collaboration across teams.
Benefits of Sophos Intelix for Microsoft Copilot
- Seamless Access to Threat Intelligence: Security and IT administrators, risk managers, and business users can interact with Sophos Intelix directly using natural language via Copilot chat, submitting artifacts and receiving real-time threat intelligence without leaving the Microsoft 365 ecosystem. This speeds up threat investigation and response, reducing the impact of threats.
- Comprehensive Threat Analysis: Sophos Intelix leverages cloud lookups, static and dynamic analysis, and the power of Sophos X-Ops threat intelligence to deliver detailed, explainable verdicts on files and URLs. This enables users to understand not just whether something is malicious, but why, facilitating faster, informed decision-making.
- Open Access: The agent is available to all Microsoft 365 Copilot users at no charge, democratizing access to world-class threat intelligence.
How to access Sophos Intelix for Microsoft Copilot
The Sophos Intelix Agent is available for free via the Agent Store in Copilot Studio and Teams. The single agent brings all the Sophos Intelix capabilities to Copilot, including:
- Cloud Lookups
- Static Analysis (File and Web)
- Dynamic Analysis
With the chat interface, users can tap directly into the deep, real-time threat landscape insights of Sophos X-Ops. Far surpassing traditional chat-ops integrations, the agent understands natural language queries, delivering actionable, expert-driven answers—so security teams can anticipate, adapt, and neutralize threats faster than ever before.
Democratizing cybersecurity for every organization
Today’s release marks a major milestone in the delivery of Sophos’ broader vision of making Sophos X-Ops data and services accessible through agent-based frameworks. With unmatched breadth and depth of data, include intelligence from SophosLabs and the Sophos managed detection and response (MDR) service, Sophos X-Ops provides security operations center (SOC) analysts with deeper threat visibility – including adversary behaviors, signature and IOC metadata, threat actor attribution, and prevalence insights – all surfaced naturally within the tools that analysts use daily. The result: more empowered analysts, faster attack resolution, and reduced cyber risk.
Ready to transform your cyber defense strategy? Start using Sophos Intelix for Microsoft 365 Copilot today and experience the future of proactive, integrated threat intelligence—right where your teams work every day.
Source: Sophos
We released Sophos DNS Protection for networks last year, and it is now close to serving its 600 billionth query. Since then, many of you have asked for a version that can be used on roaming endpoints and for additional insights into DNS requests along with DNS over HTTPS.
Today, we are excited to launch the early access program (EAP) for DNS Protection on Windows endpoints with enhanced visibility into which users and devices are making DNS queries and support for HTTPS.
As you know, Sophos DNS Protection for Endpoints enables an added layer of transparent web protection across all ports, protocols, and applications.
Sophos DNS Protection for Endpoints
DNS Protection can now be deployed and enabled on your Windows endpoint devices in Sophos Central. Once deployed, the agent intercepts all DNS traffic from programs and apps on the Windows device and forwards it to the nearest DNS Protection resolver via DNS over HTTPS. DNS Protection will check the requests for security risks and policy compliance and allow or block access accordingly.
DNS Protection policies provide a comprehensive set of controls:
- Category-based allow and block rules
- Custom domain allow and block lists
- Enforcing safe search features on Google, YouTube, and other search engines
Enhanced visibility
All DNS queries originating from your endpoint devices are logged with the user and device names. This allows you to pinpoint problematic devices and target responses to address security issues. It also enhances the data available during XDR and MDR incident investigations.
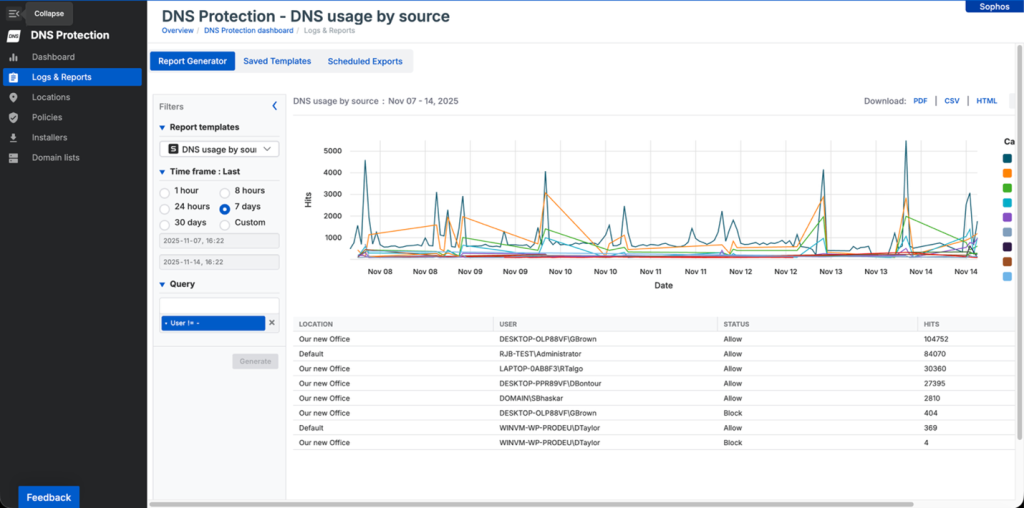
Note: device and user identities are only available when used in conjunction with the Sophos DNS Protection for Endpoints agent and not yet for DNS Protection on Sophos Firewall.
DNS over HTTPS for privacy and integrity
Sophos DNS Protection for Endpoints supports DNS over HTTPS for added privacy and integrity. By using a secure, encrypted TLS tunnel, all queries and responses are protected from network snooping and from attacks, such as DNS cache poisoning, that exploit the open nature of traditional DNS protocols.
HTTPS support is only available on DNS Protection for Endpoints at this point, however it will come to Sophos Firewall in the near future.
Getting started
Get started today with the early access program for Sophos DNS Protection for Endpoints on the Sophos Community.
Source: Sophos
The use of SaaS applications and the volume of cloud workloads are surging. Businesses today use approximately 112 SaaS apps for various business operations. According to The State of BCDR Report 2025, over 50% of workloads and applications now run in public cloud environments, and this is expected to reach 61% within the next two years.
The cloud has become the new endpoint, where employees collaborate, data resides and critical business operations run. Today, cloud platforms serve not only as the backbone of modern business productivity but also as the primary attack vector for cybercriminals.
Traditional security controls, such as firewalls and endpoint detection and response (EDR) tools, protect on-premises assets and devices. However, business-critical SaaS platforms, such as Microsoft 365, Google Workspace and Salesforce, fall completely outside EDR coverage, leaving organizations vulnerable to cyber-risks like account takeovers, data exfiltration and configuration-based attacks that bypass conventional defenses.
Protecting cloud environments requires a new approach to detection and response. That’s where cloud detection and response (CDR) solutions come in. CDR solutions are designed specifically to fill this gap by providing continuous monitoring, real-time threat detection and alerting and rapid response capabilities across SaaS environments.
In this blog, we’ll discuss what CDR is, why it matters and how it protects cloud environments from emerging threats.
What is cloud detection and response?
Cloud detection and response is a security approach that continuously monitors activity across cloud platforms to detect, analyze and respond to threats in real time.
Let’s take a look at how the cybersecurity landscape has evolved through successive generations of detection and response technologies to better understand the role of CDR.
From antivirus to CDR: The evolution of detection and response
As cyberthreats advanced, security tools adapted in response, resulting in new approaches to protecting shifting attack surfaces:
Antivirus (AV): Antivirus solutions scan the programs and files on endpoint devices using methods such as signature-based detection, heuristic analysis and behavioral monitoring to identify malicious software. However, while antiviruses are effective against known threats, traditional antivirus tools offer little to no visibility into novel or sophisticated attacks in cloud environments.
Endpoint detection and response: As threats become more complex, EDR solutions have emerged to provide continuous monitoring, behavior-based analytics and real-time, automated responses to threats on endpoints such as laptops, desktops and servers that antivirus software fails to detect.
Extended detection and response (XDR): XDR unifies data from multiple security layers, including endpoints, networks and cloud workloads, into a single platform. By breaking down silos, it delivers a more integrated and coordinated approach to detecting and responding to modern threats.
Cloud detection and response: The latest advancement in cybersecurity defense is cloud detection and response. CDR is a proactive security solution designed for threat detection, investigation and response within cloud and SaaS environments — domains that are typically beyond the monitoring capabilities of EDR and XDR platforms.
Why traditional security tools fall short
Traditional security tools such as AV, EDR and firewalls were designed to monitor endpoints and create a network perimeter. They are effective at protecting physical devices and on-premises infrastructure, strengthening an organization’s security posture by detecting malware, blocking unauthorized access and monitoring endpoint behavior. However, as organizations increasingly shift their operations to cloud-based applications, such as Microsoft 365, Google Workspace, Salesforce and other SaaS platforms, these tools fall short of protecting the environments where most business activities now occur.
Cloud services operate outside the reach of traditional endpoint tools. EDR agents cannot monitor activity within web-based SaaS applications, and firewalls miss attacks that occur through legitimate cloud APIs. Attackers now exploit cloud identities and permissions, rather than targeting devices.
In cloud-focused attacks, cybercriminals:
Abuse OAuth permissions by tricking users into granting malicious apps access to corporate data.
Exploit shared links, as overexposed or publicly shared files can become easy entry points for data theft.
Bombard users with repeated authentication requests until they accidentally approve one.
Exploit compromised credentials — obtained through data breaches or purchased on dark web forums — to infiltrate cloud accounts undetected.
Traditional endpoint tools often fail to detect these threats, creating a critical visibility and response gap that leaves organizations vulnerable, even when they have endpoint and network security solutions in place.
Businesses need a reliable CDR platform to monitor, detect and respond to evolving threats across SaaS and cloud environments where traditional endpoint security solutions have limited reach.
How cloud detection and response works
CDR combines monitoring, analytics and automation to deliver continuous protection across cloud environments. Unlike traditional security tools that focus on endpoints or networks, CDR solutions are built to operate natively in the cloud, connecting through APIs and activity logs.
The key components of a modern CDR platform include:
Continuous cloud monitoring
CDR continuously monitors SaaS apps for suspicious activity by tracking login locations, file-sharing behavior, privilege changes and third-party app integrations. This provides real-time visibility into how users and applications interact with sensitive data across services such as Microsoft 365, Google Workspace and others.
Behavioral analytics
Modern CDR platforms use machine learning-powered behavioral analytics to identify anomalies that indicate potential compromise. For example, a user logging in from unapproved locations, sharing business-critical files with people outside the organization or granting excessive permissions, might suggest malicious intent or account takeover.
Automated response
CDR systems can take automated response actions to mitigate or eliminate threats as soon as they are detected. This might include temporarily disabling the compromised account or blocking suspicious login attempts. Automation helps minimize response times — reducing dwell time and limiting the damage caused by unauthorized access or data exfiltration.
Integration with other security tools
CDR integrates with other security tools, such as Security Information and Event Management (SIEM), XDR and identity and access management (IAM) platforms to deliver a unified and coordinated defense. This integration with broader security ecosystems provides a comprehensive view of the threat landscape, enabling real-time threat detection, faster investigation and automated response.
Benefits of implementing CDR
CDR solutions provide real-time visibility and automated threat remediation across SaaS environments. Here are some of the key benefits:
Faster detection of account takeovers and insider threats
Advanced CDR platforms monitor user behavior and cloud activities to spot anomalies, such as unusual logins, privilege changes and suspicious data transfers. This helps security teams quickly detect and respond to account takeovers, insider threats and other credential attacks that traditional tools may miss.
Prevention of data leaks via malicious OAuth apps or misconfigurations
By monitoring API connections, file sharing and app permissions, CDR prevents data leaks from malicious OAuth apps, misconfigurations or excessive sharing. It protects sensitive business data in cloud apps, such as Microsoft 365, Google Workspace or Salesforce, from exposure or misuse.
Reduced manual workload through automated remediation
Cutting-edge CDR platforms, such as SaaS Alerts, automate time-consuming response actions. They lock accounts during breaches, terminate risky file sharing and alert IT technicians. This not only reduces the manual workload for MSPs but also allows them to act quickly before threat actors can inflict additional damage. Automated remediation through CDR implementation allows MSPs to focus on higher-value security tasks instead of repetitive incident handling.
Enhanced compliance and audit readiness
With detailed activity logs, reporting and continuous monitoring, CDR helps MSPs enhance auditability and simplify regulatory compliance for their clients. It enables providers to demonstrate adherence to key industry standards, including HIPAA, GDPR and SOC 2. CDR delivers evidence of proactive threat detection and response across all managed cloud environments.
Cloud detection and response for MSPs
With SaaS applications now serving as core platforms for business-critical operations, implementing a robust CDR solution is no longer optional for MSPs and their clients.
Visibility into client SaaS environments
For MSPs managing dozens or even hundreds of client environments, visibility is crucial. Modern businesses rely heavily on SaaS apps to create, store and share sensitive data. However, these applications often fall outside the scope of traditional endpoint and network monitoring tools. Without direct visibility into these environments, MSPs cannot detect threats, such as account compromises, misconfigurations or unauthorized data sharing.
A reliable cloud detection and response solution provides a centralized view of SaaS threats across all tenants, without the complexity of deploying endpoint agents or juggling multiple tools. It provides MSPs with real-time insights into client cloud activity, including suspicious logins, risky file sharing and third-party app integrations. This enables MSPs to proactively identify threats and respond quickly before they escalate.
Ease of deployment and automation at scale
CDR platforms connect to client SaaS platforms via secure APIs, helping MSPs quickly onboard tenants and scale as their client base grows. For instance, the SaaS Alerts App Wizard allows MSPs to integrate with any SaaS application that has a viable API, pulling mission-critical data into SaaS Alerts. This supports quick detection and response to security threats across almost all of their clients’ SaaS applications.
Once deployed, automated detection and response workflows handle necessary security tasks, such as temporarily disabling affected accounts or blocking suspicious login attempts. This automation reduces manual burden, helping MSPs better protect clients with minimal overhead.
How Kaseya 365 User simplifies cloud detection and response
Kaseya 365 User includes cloud detection and response across Microsoft 365, Google Workspace, Salesforce and other critical SaaS applications, helping MSPs simplify their SaaS security operations.
The CDR platform constantly monitors and protects your clients’ SaaS applications, detecting unauthorized access and shutting it down without requiring any manual intervention. It provides real-time alerting and automated remediation steps, with actions taken within seconds of malicious activity. This significantly minimizes the risk of data egress or malicious activity within your clients’ most vulnerable environments.
Discover how Kaseya 365 User helps MSPs strengthen their clients’ cloud security while boosting their bottom line. Learn more.
Source: Kaseya
It’s that time of year when network admins in many parts of the world are looking forward to spending more time with family and friends and less time in front of their management consoles.
Unfortunately, this is also a peak period for cyberattacks. To help ensure your network is optimally secure over the holidays, here are a few quick and easy best practices you can utilize.
For a full list of best practices to secure your network from ransomware and other attacks be sure to download our whitepaper on this topic.
Update firmware and shut down unnecessary systems
Make sure that before you depart for the holidays, all your network infrastructure has been updated with the latest firmware and any unnecessary infrastructure is shut down and offline.
Any system exposed to the Internet either directly or indirectly (via NAT) represents a potential vulnerability and risk. Eliminate as much of that attack surface as possible by taking it offline, and update and lock down the rest.
Firmware updates often contain important security patches for known vulnerabilities or hardening enhancements that can improve your security posture. If you’re a Sophos Firewall customer, make sure you’re running the latest firmware update for your device and consider enrolling in the early access program for Sophos Firewall v22, which includes many new security hardening features and a new Health Check feature to ensure your firewall is configured optimally.
If you have other internet facing infrastructure like a VPN concentrator or WAF, make sure these systems are also up to date or shut down.
Check your configuration against best practices
Double check that all access controls, portals, NAT rules, networked apps, IoT devices, and administration systems are either disabled or locked down.
As mentioned above, if you’re a Sophos Firewall customer, consider upgrading now to the v22 early access program to take advantage of all the new security hardening capabilities and the new firewall Health Check feature that will assess your configuration against best practices to highlight any risky areas.
Ensure all systems use strong authentication with MFA
Make sure all admin consoles and remote access systems are either shut down or protected against brute force attacks or stolen credentials with multi-factor authentication.
As you would expect, Sophos Central, Sophos Firewall, ZTNA, and our full line of network security solutions leverage MFA to help protect your systems from unauthorized logins. Sophos Firewall v22 also includes new MFA support for the Web Application Firewall – one of the many top requested features in this release.
At any rate, make sure MFA is enabled for all your systems.
If you’re attacked, we can help
If you experience an emergency incident over the holidays (or any time), you can engage our fixed-fee Sophos Rapid Response service. Our team of expert incident responders will help you triage, contain, and eliminate active threats, and remove all traces of the attackers from your network.
Whether it’s an infection, compromise, or unauthorized access attempting to circumvent your security controls, we’ve seen and stopped it all. Sophos Rapid Response is available 24/7/365, including over the holiday period.
Source: Sophos
In the rapidly evolving landscape of cyber threats, artificial intelligence is no longer a luxury: it’s a necessity. At Sophos, we recognized this reality early: we’ve been integrating sophisticated AI capabilities across our product portfolio since 2017.
This deep, practical expertise has allowed us to build the industry’s largest AI-native security platform, combining both predictive machine learning (ML) and revolutionary generative AI (GenAI) to deliver faster detection and smarter, more automated responses.
However, power requires principle. Our long-standing commitment to leveraging AI for defense is governed by a framework designed to ensure that our technologies are not only effective but are also developed and deployed with the highest standards of safety, ethics, and trust.
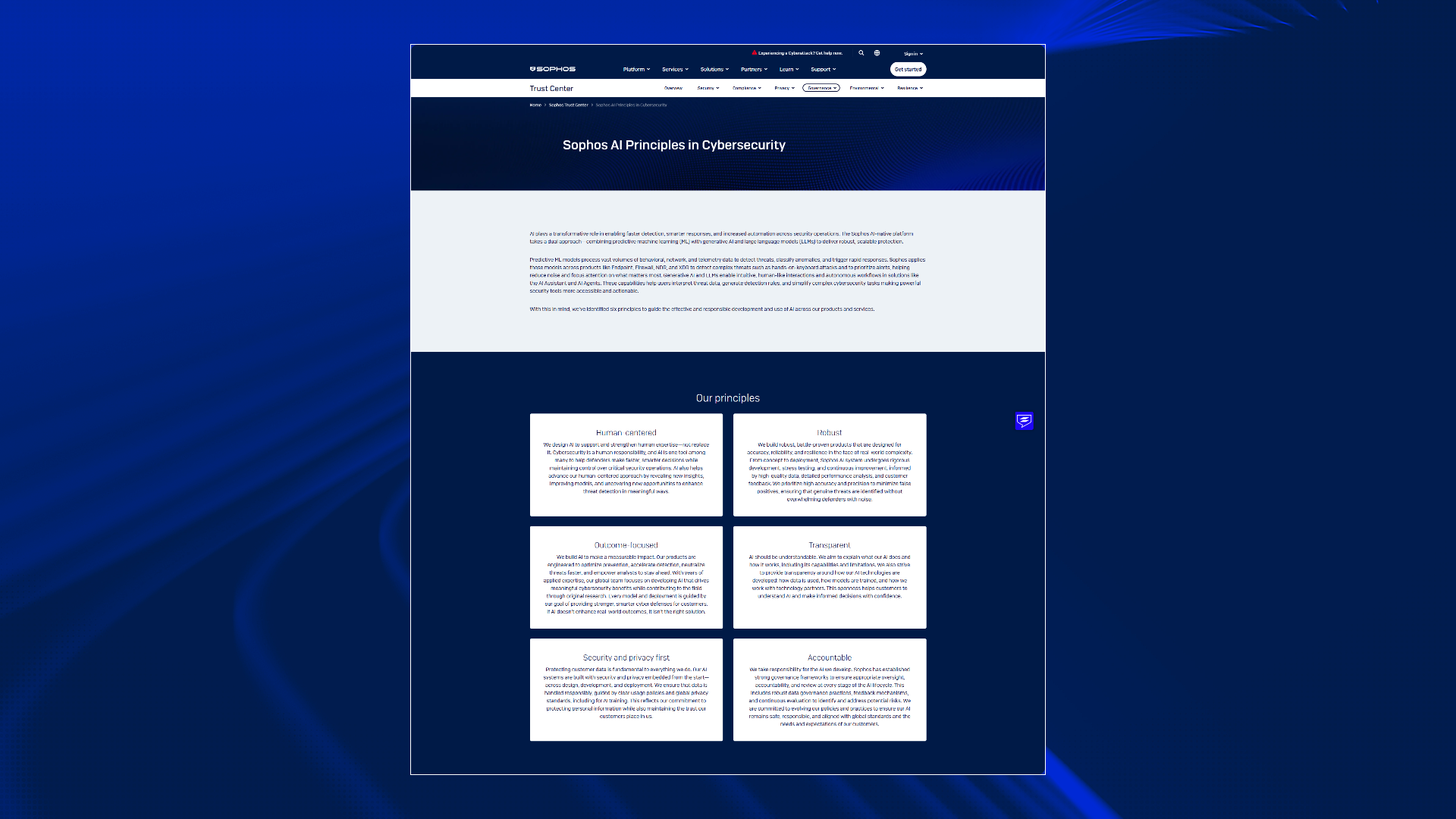
The six pillars of our responsible AI framework
Our approach to responsible AI in cybersecurity is built on six core principles, which guide every phase of development, deployment, and monitoring:
- Human-centered: We design AI to enhance human expertise, not replace it. Our tools are built to support security analysts, allowing them to make faster, smarter decisions while maintaining full control over critical security operations.
- Robust: Our models undergo rigorous development, stress testing, and continuous improvement, ensuring high accuracy and precision to minimize false positives and maintain resilience against real-world complexity and adversarial attacks.
- Outcome-focused: We measure success by real-world impact. Our AI is engineered to optimize prevention, accelerate detection, and neutralize threats faster, focusing on measurable cybersecurity benefits for our customers.
- Security and privacy first: Protecting customer data is paramount. Our systems are built with security and privacy embedded from the start, guided by clear usage policies and global standards. Crucially, we do not share customer data to train third-party large language models (LLMs).
- Accountable: We have established strong governance frameworks with clear roles and oversight to manage risk and review our AI systems at every stage, ensuring we take full responsibility for the technology we develop.
- Transparent: Effective security partnership requires understanding the tools you rely on. We strive to explain what our AI does and how it works, including its capabilities and, importantly, its limitations. We provide clarity around how our AI technologies are developed, including how data is utilized for training our proprietary models, and how we work with technology partners.
Sophos continues to leverage the transformative power of AI to defeat cyberattacks. By anchoring our innovation in a steadfast commitment to human oversight, robust engineering, and complete transparency, we ensure our technologies remain a trustworthy and powerful asset in the global fight against cybercrime.
This openness, through product documentation and governance practices, empowers our customers to make informed decisions and assess the suitability of our AI solutions for their unique needs.
In that spirit, we invite you to further review our AI Principles in Cybersecurity and Responsible AI FAQs web pages, both located in the Sophos Trust Center.
Source: Sophos
Ransomware attacks are evolving faster than ever. For already stretched IT and security teams, staying ahead can feel impossible, but it doesn’t have to be.
The right combination of firewall and endpoint security can stop ransomware before it spreads and restore confidence at the edge of your network.
To help organizations navigate this shifting threat landscape, Chris McCormack, Sophos Network Security Specialist, presented how integrated defenses built on Sophos Firewall and Sophos Endpoint can reduce risk and rebuild trust. Here are five key takeaways from our recent webinar, “Rebuilding Trust at the Edge: A Smarter Approach to Firewall Security.”
Reduce your attack surface
Every exposed system is a potential entry point. Consolidating and securing infrastructure limits opportunities for attackers — and makes your defenses simpler and more effective.
“The best practices to prevent being attacked or targeted in the first place are perhaps most important,” McCormack said during the webinar. “These reduce your surface area of attack or risk of being attacked, which is largely focused on things like minimizing exposed infrastructure and ensuring that what you do have that’s exposed is hardened so it’s not an attractive target — or at least not as attractive as the next vendor.”
Start by identifying everything that is exposed to the internet and removing what’s unnecessary, and hardening what must remain. The fewer targets you present, the harder it is for attackers to get in, and the easier it is for your team to defend.
Design systems to be secure from the start
Security shouldn’t be bolted on — it should be built in. Systems exposed to the internet must be configured correctly, continuously updated, and hardened against attacks.
“Make sure you look for a vendor that can provide automatic over-the-air updates or critical patches that don’t require you to lift a finger,” McCormack said. “You shouldn’t have to schedule a firmware upgrade or reboot your network every time there’s a new vulnerability discovered.”
Sophos Firewall’s automated patching, strong default policies, and cloud-managed configuration through Sophos Central simplify security operations for even small IT teams. Enforcing strong passwords, enabling multi-factor authentication, and applying zero-trust principles are baseline controls that keep intruders out.
Adopt Zero Trust Network Access (ZTNA)
Traditional VPNs assume trust once a connection is made. ZTNA flips that model — no user or device is trusted by default.
Sophos ZTNA verifies identity and device health before granting access, dramatically reducing the risk of lateral movement if an attacker gets ahold of credentials.
“I can’t stress enough the importance of utilizing [ZTNA], which is all about trusting nothing and verifying everything,” McCormack said. “Credential theft [is] a key root cause of ransomware attacks. That’s because many firewalls, many organizations, and network security are trusting that if you have those credentials, we trust you. ZTNA solves this problem.”
Integrated through the Sophos Central platform, Sophos Zero Trust Network Access (ZTNA) offers unified visibility and control over users, devices, and applications — from a single pane of glass. It is a smarter, more secure way to connect remote users and ensure every interaction with your network is legitimate.
Don’t let encrypted traffic hide threats
With most internet traffic now encrypted, attackers use it to mask their movements.
Sophos Firewall uses intelligent TLS inspection and AI-powered analysts to reveal hidden threats — without compromising performance.
“There are technologies out there now that you can use that leverage AI to discover encrypted threat communications and network traffic without you actually having to do the heavy lifting of decrypting that traffic,” he said.
By combining deep packet inspection with insight from Sophos X-ops threat intelligence, Sophos Firewall detects and blocks malware, command and control traffic, and exploits within encrypted sessions — ensuring attackers cannot hide in plain sight.
Detect and respond to active threats — Fast
Even with strong defenses, incidents can still happen — and speed is everything.
Segment your network to contain threats, monitor east-west traffic with Sophos Network Detection and Response (NDR), and unify response through Sophos Extended Detection and Response (XDR).
“Technologies like NDR are typically something you would only find in large enterprise networks, but we’re making it available to everyone and for free,” McCormack said. “So, if a threat is detected by any of our products or an analyst, that information is shared immediately with all other software, and the response kicks off automatically.”
Sophos XDR and NDR work together to give complete visibility across endpoints, firewalls, and email by correlating data to spot suspicious behavior, isolating compromised devices, and stopping attackers in their tracks. This synchronized defense, powered by real-time intelligence, gives security teams enterprise-grade speed and confidence.
Source: Sophos
SealPath, a leading provider of data-focused security and digital rights management, announces the launch of its new product “SealPath Data Classification powered by Getvisibility”.
By utilizing the latest in Artificial Intelligence and Machine Learning technology, it provides its customers with advanced data visibility, protection, control, and dynamic understanding solutions as they are created.
This innovative tool, enhanced with AI for data classification and automatic protection of labeled information, provides the technology that corporate clients need to classify data securely and accurately throughout its lifecycle. This way, organizations from any sector gain the ability to prevent data leaks and comply with the strictest data protection regulations.
With SealPath’s classification, the user receives suggestions on the classification level when creating and editing a document. The software learns and adapts to different types of documents, continuously improving its accuracy through AI, and allows organizations to classify unstructured information with unprecedented confidence.
SealPath information protection is 100% integrated with the new intelligent data classification system, so those files labeled with a specific classification level or subject to specific regulation can be protected automatically and without user intervention.
“SealPath Data Classification powered by GetVisibility was born in response to the obsolete technologies that many companies are currently using to classify and manage their data. The solution’s machine learning models have been previously trained for years through data containing a wide range of document types, from personal, medical, and financial information, and different market verticals. These meticulously trained models, combined with robust software specialized in data classification, minimize human error, costs, and time in labeling corporate information. We hope that this new solution completely transforms the way organizations classify and protect their information,” says Luis Ángel del Valle, CEO of SealPath.
SealPath Data Classification employs a flexible approach, considering different dimensions like data sensitivity, associated regulations (PCI, GDPR, CMMC, etc.), data types, and distribution scope. In this way, the system can adapt the classification to the organization based on the aforementioned dimensions.
SealPath’s protection, along with the AI and Machine Learning classification system, streamlines an organization’s efforts to prevent data classification errors quickly and cost-effectively.
Learn more about SealPath Data Classification here.
Source: Sealpath
We’re excited to share that Silverfort is named as an Example Vendor in the 2025 Gartner A Well-Run Active Directory Requires Strong Identity Controls, authored by Paul Rabinovich, May 2025.
Silverfort is proud to be recognized as an Example Vendor in three key areas of the report:
- Implement MFA to Resources Integrated with AD
- Implement Identity Posture Management and Identity Threat Detection and Response (ITDR)
- MFA Integration Options for AD-Bound Legacy Applications (Authentication Forwarding Solutions)
As organizations race toward the future of the cloud, Active Directory remains one of the most challenging assets to protect. It’s deeply embedded in enterprise infrastructure, and while companies modernize, securing AD and other legacy systems can’t be an afterthought. They still hold the keys to critical access and remain prime targets for attackers.
Silverfort helps organizations secure every identity—human, machine and AI—from legacy to cloud, including the systems that traditional tools can’t cover.
Active Directory security demands strong identity controls
AD has long been the backbone of enterprise identity—and a prime target for attackers.
While AD remains critical, too many organizations are leaving it exposed to credential compromise, lateral movement and privilege escalation.
How Silverfort puts Gartner’s framework into action
Silverfort helps organizations put these best practices into action. Our identity security platform extends modern identity security to AD authentication paths, including systems and protocols traditional identity and access management (IAM) tools can’t reach.
Silverfort delivers MFA protection to every resource and access path, including homegrown applications, command-line tools, legacy systems, and OT environments, while continuously analyzing every authentication across AD and Entra ID for risky behavior.
With Silverfort’s Non-Human Identity (NHI) Security, organizations can discover all NHIs across AD and cloud, map their behavior and risk, and enforce real-time protection for AD service accounts through virtual fencing policies. By combining adaptive MFA, identity security posture management (ISPM), and real-time identity threat detection and response (ITDR), Silverfort helps secure the heart of enterprise identity from the attacks that target it most—all without any infrastructure changes.
Leading the next era of Identity Security
Identity is the new security perimeter, and AD remains central. As environments become more hybrid and threats more sophisticated, organizations need visibility into every authentication, real-time threat detection, and inline, risk-based enforcement for both human and non-human identities.
That’s the evolution Silverfort leads. By integrating seamlessly with both AD and cloud identity providers, Silverfort delivers the most compete security across all types of identities (including human, machine, and AI agents), systems, and applications.
With Silverfort, identity and security teams can work together to enforce MFA protection, continuous risk assessments, ISPM, and ITDR from a unified platform, securing every authentication without disrupting users or infrastructure. This approach embodies the same principles Gartner outlines in its framework: building strong, layered identity controls that protect AD today while preparing for the future of hybrid identity.
Source: Silverfort
In the last few articles on the topic of our latest Sophos Firewall release, we’ve discussed the importance of Secure by Design and covered one of the highlights of this release: the new Health Check feature. There are also a number of other important enhancements to Secure by Design in Sophos Firewall v22. Let’s take a look.
Next-Gen Xstream Architecture
 Sophos Firewall introduced the Xstream Architecture as a key component of v18, enabling XGS Series appliances to take full advantage of the added processing power and capabilities it provided. Since then, Sophos Firewall’s Xstream Architecture has been constantly scaling and adapting to bring additional performance to customer networks.
Sophos Firewall introduced the Xstream Architecture as a key component of v18, enabling XGS Series appliances to take full advantage of the added processing power and capabilities it provided. Since then, Sophos Firewall’s Xstream Architecture has been constantly scaling and adapting to bring additional performance to customer networks.
This is all thanks to the programmable nature of Sophos Firewall’s Xstream Architecture that is NOT dependent on custom silicon ASICs – and in fact works equally well on general-purpose CPUs, virtual CPUs, and our XGS Series models that have dedicated flow processors.
Sophos Firewall v22 introduces our next-generation Xstream Architecture, which has an all-new control plane re-architected for maximum security and scalability to take us into the future. The new control plane enables modularization, isolation, and containerization of services like IPS for example, to run like “apps” on the firewall platform. It also enables complete separation of privileges for added security.
The net result is an ultra-secure, scalable, and streamlined architecture built for the future. This next-gen Xstream Architecture lays a foundation for highly secure, scalable, and modular containerized services, n-node clustering, and full RESTful APIs for high-performance remote management and automation.
High-availability self-healing
In addition, this Next-Gen Xstream Architecture adds a new self-healing capability to high-availability deployments that is continuously monitoring system state and fixes deviations between devices automatically.
Hardened kernel
 The next-gen Xstream Architecture in Sophos Firewall OS is built upon a new hardened kernel (v6.6+) that provides enhanced security, performance, and scalability to maximize current and future hardware. The new kernel offers tighter process isolation and better mitigation for side-channel attacks as well as mitigations for CPU vulnerabilities (Spectre, Meltdown, L1TF, MDS, Retbleed, ZenBleed, Downfall). It also offers hardened usercopy, stack canaries, and Kernel Address Space Layout Randomization (KASLR).
The next-gen Xstream Architecture in Sophos Firewall OS is built upon a new hardened kernel (v6.6+) that provides enhanced security, performance, and scalability to maximize current and future hardware. The new kernel offers tighter process isolation and better mitigation for side-channel attacks as well as mitigations for CPU vulnerabilities (Spectre, Meltdown, L1TF, MDS, Retbleed, ZenBleed, Downfall). It also offers hardened usercopy, stack canaries, and Kernel Address Space Layout Randomization (KASLR).
Remote integrity monitoring
Sophos Firewall OS v22 now integrates our Sophos XDR Linux Sensor that enables real-time monitoring of system integrity, including unauthorized configuration, rule exports, malicious program execution attempts, file tampering, and more.
This helps our security teams who are constantly monitoring our entire Sophos Firewall customer base to better identify, investigate, and respond more quickly to any attack. This is an added security capability that no other firewall vendor provides.
New anti-malware engine
Sophos Firewall OS v22 integrates the latest Sophos anti-malware engine with enhanced zero-day, real-time detection of emerging threats using global reputation lookups. This is possible thanks to a massive cloud database of known malicious files, which is updated every 5 mins or less.
It also introduces AI and ML model detections and delivers enhanced telemetry to SophosLabs for accelerating their emerging threat detection analysis.
Get started today
Be sure to get involved in the Sophos Firewall v22 Early Access Program to better secure your and your customers’ networks and help make this release the best it can be. Also be sure to review the What’s New Guide for a full list of all the new capabilities in Sophos Firewall v22.
Source: Sophos
Keeper Security, the leading cybersecurity provider of zero-trust and zero-knowledge Privileged Access Management (PAM) software protecting passwords, passkeys, privileged accounts, secrets and remote connections, today announces Keeper Forcefield™, the first-of-its kind protection against memory-based attacks on Windows devices. Forcefield is a groundbreaking kernel-level endpoint security product that proactively defends against memory-based attacks, including credential theft from infostealers and runtime memory-scraping malware. Keeper® is the first cybersecurity software company to deliver real-time memory protection at both the user and kernel levels, raising the standard for endpoint security in enterprise environments.
Attackers are increasingly bypassing traditional cybersecurity defenses by targeting unprotected memory rather than exploiting vulnerabilities. Malicious software delivered through phishing attacks or other methods can access application memory to extract passwords, session tokens and other sensitive data – circumventing traditional encryption methods. Keeper Forcefield closes this dangerous gap by locking down memory access at the kernel level. Unlike conventional antivirus or Endpoint Detection and Response (EDR) tools, it enforces real-time memory protection capable of blocking non-privileged, fileless and zero-day attacks without degrading system performance.
“Forcefield closes one of the most dangerous blind spots in endpoint security,” said Craig Lurey, CTO and Co-founder of Keeper Security. “Malware can extract sensitive information directly from a device’s memory, even at the user level where administrative privilege isn’t required. Forcefield prevents this type of exploit entirely without disrupting trusted applications or everyday workflows.”
Forcefield provides peace of mind by actively safeguarding sensitive data from unauthorized access while operating silently in the background. It installs a lightweight, kernel-level driver that shields protected application memory from unauthorized access. Users can easily toggle Forcefield on or off within the Keeper Desktop application or deploy it via Group Policy. The solution continuously differentiates between trusted and untrusted processes in real-time, ensuring legitimate activity continues uninterrupted while malicious or unknown processes are blocked from scraping sensitive data.
How Keeper Forcefield works:
- Kernel-level protection – Actively monitors and restricts memory access to protected applications.
- Selective memory restriction – Blocks unauthorized processes from reading protected application memory.
- Smart process validation – Differentiates between trusted and untrusted processes in real time.
- Uninterrupted system performance – Runs quietly without impacting system or application performance.
Windows applications protected by Forcefield include:
- Web browsers – Chrome, Firefox, Edge, Brave, Opera and Vivaldi
- Keeper software – Desktop App, Web Vault, Browser Extensions, Gateway, Bridge, Commander and KeeperChat
- Operating systems – Windows 11 x64 and ARM64
Forcefield is available for both individual users and enterprise environments. Organizations can deploy protection across fleets of Windows devices in minutes using existing management tools, ensuring scalable and consistent endpoint defense without added friction.
For more information or to download Keeper Forcefield, visit www.keepersecurity.com/forcefield-endpoint-protection.
Source: Keeper Security and PR Newswire
Keeper Security, the leading cybersecurity provider of zero-trust and zero-knowledge Privileged Access Management (PAM) software, today announces that it has been recognized among leading vendors in the 2025 Gartner® Magic Quadrant™ for Privileged Access Management report.
The Gartner Magic Quadrant is widely considered one of the most influential evaluations in enterprise technology, providing security leaders with insights in selecting trusted solutions in today’s rapidly evolving technological landscape. KeeperPAM delivers a modern, cloud-native solution that unifies password and passkey management, secrets and connection management with zero-trust network access, remote browser isolation, privileged session management and endpoint privilege management in a single, easy-to-deploy platform. Designed for today’s hybrid IT environments, KeeperPAM leverages agentic AI and native integrations to provide organizations with complete visibility, control and compliance across every user, device and system.
Keeper differentiates itself in the PAM market with comprehensive enterprise-wide coverage and seamless integration with your technology stack. The next-gen PAM platform centralizes access to systems and data with zero-trust security, enforcing role-based policies and MFA across all assets.
- Password management: Protect and securely share passwords, passkeys and confidential data in a zero-knowledge vault with role-based access control, auditing and reporting.
- Secrets management: Integrate CI/CD pipelines, DevOps tools, custom software and multi-cloud environments into a fully-managed, zero-knowledge platform to secure infrastructure secrets and reduce secrets sprawl.
- Session management: Provide secure, credential-free access to sensitive systems while maintaining full visibility and control over privileged sessions.
- Remote browser isolation: Secure internal web-based applications, cloud apps and BYOD devices from malware, prevent data exfiltration and control browsing sessions with full auditing, session recording and password autofill.
- Endpoint privilege management: An advanced Privileged Elevation and Delegation Management (PEDM) solution that provides secure, Just-in-Time (JIT) privileged access across all Windows, Linux and macOS endpoints, with optional approval workflows and MFA enforcement.
- Admin console and control plane: Streamline deployment, user provisioning and policy enforcement through a centralized admin interface that seamlessly integrates with your existing identity stack.
- AI-powered session analysis that replaces manual log reviews with automated insights, giving organizations the speed and accuracy needed to stay ahead of modern cyber threats.
“KeeperPAM was engineered from the ground up to meet the realities of modern IT environments – cloud-first and hybrid, distributed and highly dynamic,” said Craig Lurey, CTO and Co-founder of Keeper Security. “Our platform eliminates the complexity of legacy PAM tools by delivering a unified, zero-knowledge solution that deploys in minutes and scales effortlessly. By integrating credential and privileged access management with advanced capabilities like AI-powered session analysis and remote browser isolation, we’re empowering security and DevOps teams with tools that are both powerful and intuitive. We believe this recognition from Gartner affirms our commitment to redefining PAM through innovation, simplicity and uncompromising security.”
In 2025, Enterprise Management Associates (EMA) identified Keeper as a Value Leader in the PAM Radar Report, while GigaOm ranked Keeper the Overall Leader in its Password Management Report for the fourth consecutive year. Newsweek also highlighted Keeper among America’s Best Online Platforms, where it achieved the highest ranking of any cybersecurity vendor in the Business Solutions category.
Keeper’s innovation leadership has been further validated with multiple award wins in 2025, including being recognized as the Most Innovative Cybersecurity Company and earning top honors in both Privileged Access Management and Zero-Trust Security in the Cybersecurity Excellence Awards. The Globee Awards selected Keeper as the Cybersecurity Company of the Year, and the Global Infosec Awards honored the company in nine categories, including wins for privileged access management and zero trust.
“We believe Keeper’s recognition in the Gartner Magic Quadrant underscores the momentum we’ve built by challenging legacy approaches to privileged access management,” said Darren Guccione, CEO and Co-founder of Keeper Security. “KeeperPAM reimagines PAM for the modern enterprise, making it simple and scalable, while preserving the foundation of zero-trust and zero-knowledge security. Our vision is to empower organizations everywhere with a platform that is more secure, more intuitive and more accessible, enabling them to stay ahead of today’s rapidly evolving cyber threats.”
With FedRAMP and GovRAMP Authorization; SOC 2 Type II attestation; ISO 27001, 27017 and 27018 certifications and FIPS 140-3 validation; KeeperPAM meets the highest standards of compliance. These achievements provide customers with assurance that Keeper’s platform not only strengthens security but also simplifies audit and regulatory requirements.
Access the full Gartner Magic Quadrant Report for Privileged Access Management to learn more. To learn more about Keeper’s enterprise, business and government solutions, visit KeeperSecurity.com.
Source: Keeper Security and PR newswire
Sophos Firewall v22 is now in early access and the participation has been outstanding.
One of the highlights of this release is the new Health Check feature. This is just one of the many Secure by Design elements in this release, but it’s an important one.
A critical part of keeping your network secure is ensuring your firewall is optimally configured to prevent attackers from exploiting any openings or weak points in your security posture. Sophos Firewall v22 makes your job of optimally securing your firewall much easier with the new Health Check feature.
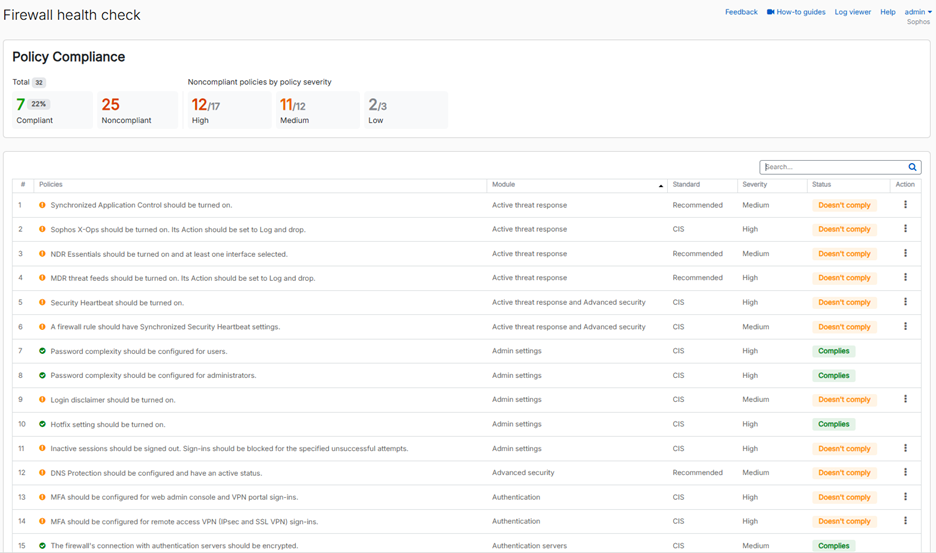
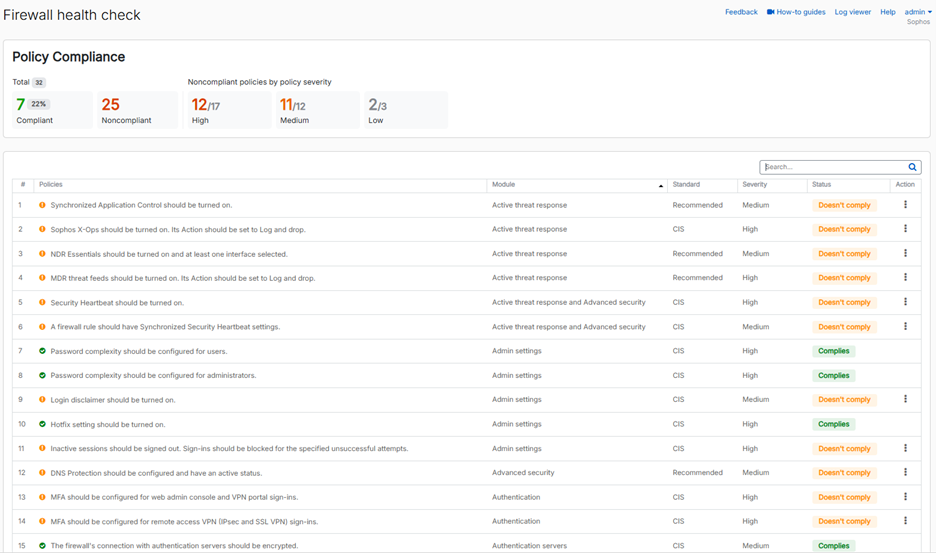
This new feature evaluates dozens of different configuration settings on your firewall and compares them with CIS (Center for Internet Security) benchmarks and our own recommended best practices, providing immediate insights into areas that may be at risk. It will identify all high-risk settings and provide recommendations with easy drill-down to the areas of concern so you can easily address them.
Watch this short video to see how to take advantage of this new feature:
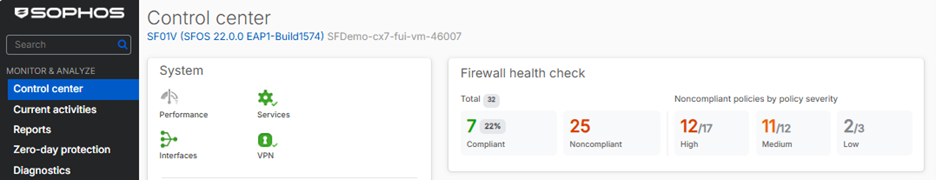
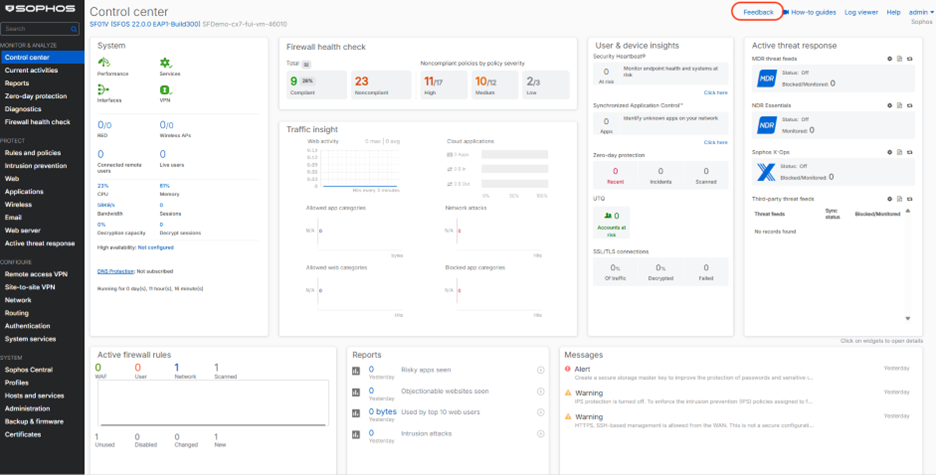
As shown in the video, there’s a new Control Center dashboard widget with click-through drill-down to the new feature:
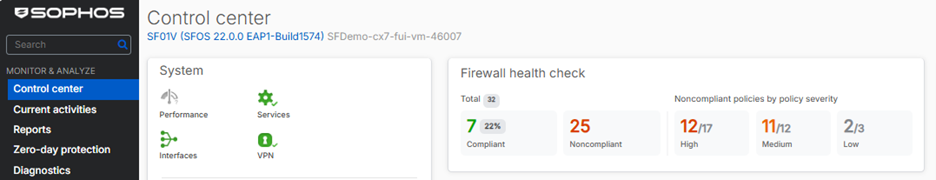
The new Health Check feature has a dedicated main menu item on the left side to access the full detailed report on the compliance of your device:
You might be wondering about CIS. The Center for Internet Security (CIS) is a nonprofit community of IT professionals dedicated to evolving standards and best practices for securing IT systems and data.
 You can get more insights into our partnership by visiting the Sophos page on the CIS Benchmarks website. You can also download the benchmark PDF from their website for deeper insights into why these configuration changes are considered a best practice.
You can get more insights into our partnership by visiting the Sophos page on the CIS Benchmarks website. You can also download the benchmark PDF from their website for deeper insights into why these configuration changes are considered a best practice.
The current version on the website was developed based on SFOS v21, but of course also applies just as well to v22. We will be updating the document in partnership with CIS going forward.
Be sure to get involved in the Sophos Firewall v22 Early Access Program to better secure your network and help make this release the best it can be. Also be sure to review the What’s New Guide for a full list of all the new capabilities in Sophos Firewall v22.
Source: Sophos
Recent events with F5 and SonicWall underline a continuing issue: network infrastructure is constantly under attack, and the cybersecurity industry continues to grapple with deep product security challenges.
Our adversaries are targeting the very tools designed to defend us. These are not opportunistic attacks: they’re a long-term strategy requiring years of research and are increasingly involving direct breaches of vendors’ own engineering and product environments.
As disclosed in our Pacific Rim research from last year, Sophos has direct experience with this. We discovered an internal breach of our firewall division in 2018, followed by attacks against customer devices that demonstrated an uncanny knowledge of our product architecture. A handful of other vendors have disclosed similar internal intrusions but this likely only scratches the surface of a wider issue.
What can we do? As Ollie Whitehouse at the National Cyber Security Centre has pointed out, this is ultimately a market incentives problem. Buyers need to demand better. Not by punishing vendors who disclose breaches, but by rewarding vendors who embrace transparency and demonstrate a real commitment to Secure by Design principles.
Over the last several releases, we have continued to invest in implementing Secure by Design principles into all our products, including Sophos Firewall. Sophos Firewall has had numerous updates in the last few years to aggressively harden the product, make it easier to patch vulnerabilities, and to identify when a customer is under attack.
As you probably know, Sophos Firewall is unique in offering zero-touch over-the-air hotfixes that can be used to patch new vulnerabilities without scheduling downtime. Sophos is also the only vendor that is actively monitoring our install base to help identify signs of an attack early.
Sophos Firewall v22 takes Secure by Design to a new level with several important enhancements:
Improved workload isolation – With our next-gen Xstream Architecture, SFOS v22 introduces an all-new control plane re-architected for increased defense-in-depth and scalability. The new control plane enables deeper modularization, isolation, and containerization of services.
Hardened kernel – The next-gen Xstream Architecture in Sophos Firewall OS is built upon a new hardened kernel (v6.6+) that provides enhanced security, performance, and scalability to maximize current and future hardware. This new kernel offers tighter process isolation and better mitigation for side-channel attacks as well as mitigations for CPU vulnerabilities. It also offers hardened usercopy, stack canaries, and Kernel Address Space Layout Randomization (KASLR).
Remote integrity monitoring – Sophos Firewall OS v22 now integrates our Sophos XDR Linux Sensor that enables real-time monitoring of system integrity, including unauthorized configuration, rule exports, malicious program execution attempts, file tampering, and more. This helps our security teams – who are proactively monitoring our entire Sophos Firewall install base – to better identify, investigate, and respond more quickly to any attack. This is an added security capability that no other firewall vendor provides.
Sophos Firewall Health Check – A strong security posture depends on ensuring your firewall and other network infrastructure is optimally configured. Sophos Firewall v22 makes it much easier to evaluate and address the configuration of your firewall with the new Health Check feature, which checks dozens of different configuration settings on your firewall and compares them with CIS benchmarks and other best practices, providing immediate insights into areas that may be at risk.
Be sure to get involved in the Sophos Firewall v22 Early Access Program to better secure your network and help make this release the best it can be.
If you’re a researcher, we welcome security research on our products so please do participate in our bug bounty program. You can receive up to $50K for findings on our firewall platform.
Source: Sophos
Ransomware remains one of today’s most disruptive cyber threats, but it is far from the only one.
Attackers are also exploiting unpatched systems, launching AI-driven phishing campaigns, and using stolen credentials to infiltrate systems and steal sensitive data. These tactics are evolving fast, and IT and security teams are feeling the pressure.
According to Sophos’ 2025 State of Ransomware report:
- 32% of attacks began with unpatched vulnerabilities.
- 28% of victims experienced both encryption and data theft.
- 49% paid the ransom to recover their data.
- 41% of IT teams reported increased anxiety or stress post-attack.
These numbers make one thing clear: organizations need to shift from reacting to preventing.
“Security isn’t just about stopping attacks — it’s about taking back control,” says Joe Levy, Sophos CEO. “That starts with prevention. The earlier you act, the more control you have over your outcomes.”
Inside the toolkit
The Sophos free Cybersecurity Best Practices Toolkit brings together practical, prevention-first resources for organizations of every size. Each one is designed to help you prepare, protect, and practice your response before attackers strike.
Plan Your Response: Incident Response Planning Guide
Build a clear incident response playbook. Learn how to document actions, communicate with stakeholders, and capture lessons from post-incident reviews – get legal documentation tips, communication templates, and guidance on forensic analysis.
Protect your network: Network security best practices for preventing ransomware
Apply proven best practices to harden your network against ransomware and other threats. Learn how to reduce your attack surface, inspect encrypted traffic, and implement zero-trust network access (ZTNA) to block lateral movement.
Practice Readiness: Tabletop Exercise Guide
This guide walks you through how to run realistic tabletop exercises that simulate attacks like insider threats, ransomware, and supply chain compromises, helping to find gaps before attackers do and improve cross-functional communication.
As the guide notes, “Walking through responses in a simulated incident enables participants to develop fluency with the actions needed in a real attack, accelerating execution.”
Why prevention must come first
Every hour saved in detection or response reduces cost, risk, and stress for your team. Prevention isn’t a philosophy — it’s a measurable advantage.
The toolkit outlines how to:
- Run tabletop exercises regularly to test readiness.
- Patch vulnerabilities quickly — addressing the top cause of ransomware in 2025.
- Segment networks to limit attacker movement.
- Replace VPNs with ZTNA to eliminate implicit trust.
- Inspect encrypted traffic to reveal hidden threats
Take control of your defenses today.
Whether you’re a small business, a school district, or a global enterprise, the Sophos Cybersecurity Toolkit gives you a clear path to stronger defenses and greater control, before attackers make their move.
Explore the Cybersecurity toolkit and start building your prevention-first strategy today.
Source: Sophos
Adversaries exploit compromised identities, infrastructure weaknesses, and misconfigurations to gain unauthorized access to sensitive data and systems, putting user-based access and controls at the frontline of modern IT and cybersecurity.
However, with identities no longer confined to the network perimeter, and the widespread shift to cloud and remote work, monitoring and securing identity systems has become increasingly complex. Indicating the scale of the issue, Sophos Incident Response analysis shows that 95% of Microsoft Entra ID environments are misconfigured, creating an open door for threat actors to escalate privileges and launch identity-based attacks.
Protect against identity-based attacks
Introducing Sophos Identity Threat Detection and Response (ITDR) — a powerful new solution that prevents identity-based attacks by continuously monitoring your environment for identity risks and misconfigurations and providing dark web intelligence on compromised credentials.
Built on the proven Secureworks Taegis IDR product, Sophos ITDR is fully integrated into Sophos’ open, AI-native platform, Sophos Central, enabling new and existing customers to deploy with speed and confidence.
Sophos ITDR automatically runs more than 80 advanced identity posture checks, going far beyond basic hygiene to uncover risks in minutes. The solution includes full coverage of MITRE ATT&CK Credential Access techniques, alerts you when credentials are exposed in data breaches, and flags anomalous user activity.
Sophos ITDR helps you:
- Reduce your identity attack surface: Sophos ITDR continuously scans your Microsoft Entra ID environment to uncover misconfigurations, identify security gaps, and provides clear, actionable recommendations.
- Monitor for leaked or stolen credentials: In the past year, the number of stolen credentials offered for sale on one of the dark web’s largest marketplaces has more than doubled*. Sophos ITDR protects user accounts from unauthorized access by monitoring the dark web and breach databases and alerting you when credentials have been exposed.
- Identify risky user behavior: Sophos ITDR detects abnormal activity associated with stolen credentials or insider threats, such as unusual login patterns.
- Protect against identity-based threats: Sophos ITDR enables analysts to respond quickly and effectively with built-in actions such as forcing password resets and locking down suspicious accounts.
A critical part of a complete security solution
Identity is a vital component of any modern security strategy. Sophos provides unmatched cyber defenses through an open, AI-native platform spanning identity, endpoints, network, firewall, cloud, email, and productivity tools. Sophos ITDR strengthens your defenses and is available as an add-on for Sophos Extended Detection and Response (XDR) and Sophos Managed Detection and Response (MDR):
- Sophos XDR + Sophos ITDR: Equip your in-house security teams with advanced tools to detect and stop active adversaries and identity-based threats.
- Sophos MDR + Sophos ITDR: Offload investigations and response activities for identity-based threats to our expert analysts, freeing your IT and security staff to focus on core business priorities.
Learn how Sophos ITDR can elevate your identity security — speak to an expert or visit Sophos.com/ITDR to start a free, no-obligation trial today.
Source: Sophos
We’re pleased to announce that the early access program (EAP) is now underway for the latest Sophos Firewall release. This update brings several Secure by Design enhancements and many of your top requested features.
Secure By Design
Internet facing infrastructure has recently come under increasing attacks to exploit vulnerabilities and other weaknesses to gain a foothold on networks.
As you know, at Sophos, we take security very seriously and over the last several releases we have invested in implementing many Secure By Design principles to harden the product and make it a much more difficult target. This release takes Secure by Design to a whole new level.
Sophos Firewall Health Check
A strong security posture depends on keeping your firmware up to date and ensuring your firewall is optimally configured. Sophos Firewall v22 makes it much easier to evaluate and address the configuration of your firewall with the new Health Check feature.
This new feature evaluates dozens of different configuration settings on your firewall and compares them with CIS benchmarks and other best practices, providing immediate insights to areas that may be at risk. It will identify all high-risk settings and provide recommendations with quick drill-down to the areas of concern so you can easily address them.
The health check status is displayed on a new Control Center widget and a full report is available under the “Firewall health check” main menu item.
Other Secure By Design enhancements:
- Next-gen Xstream Architecture – introduces an all-new control plane re-architected for maximum security and scalability to take us into the future. The new control plane enables modularization, isolation, and containerization of services like IPS for example, to run like “apps” on the firewall platform. It also enables complete separation of privileges for added security. In addition, high-availability deployments now benefit from a self-healing capability that is continuously monitoring system state and fixes deviations between devices automatically.
- Hardened kernel – The next-gen Xstream Architecture in Sophos Firewall OS is built upon a new hardened kernel (v6.6+) that provides enhanced security, performance, and scalability to maximize current and future hardware. This new kernel offers tighter process isolation and better mitigation for side-channel attacks as well as mitigations for CPU vulnerabilities (Spectre, Meltdown, L1TF, MDS, Retbleed, ZenBleed, Downfall). It also offers hardened usercopy, stack canaries, and Kernel Address Space Layout Randomization (KASLR).
- Remote integrity monitoring – Sophos Firewall OS v22 now integrates our Sophos XDR Linux Sensor that enables real-time monitoring of system integrity, including unauthorized configuration, rule exports, malicious program execution attempts, file tampering, and more. This helps our security teams, who are proactively monitoring our entire Sophos Firewall install base to better identify, investigate, and respond more quickly to any attack. This is an added security capability that no other firewall vendor provides.
- New anti-malware engine – Sophos Firewall OS v22 integrates the latest Sophos anti-malware engine with enhanced zero-day real-time detection of emerging threats using global reputation lookups. It takes full advantage of SophosLabs’ massive cloud database of known malicious files, updated every five minutes or less. It also introduces AI and ML model detections and delivers enhanced telemetry to SophosLabs for accelerating their emerging threat detection analysis.
Other security and scalability enhancements:
- Firmware updates via SSL and certificate pinning ensures authenticity
- Active Threat Response logging improvements enhanced visibility
- NDR Essentials threat score is included in Logs for added insights
- NDR Essentials data center selection for data residency requirements
- Instant web category alerts for education institutions
- XML API access control enhancements with added granularity
- TLS 1.3 support for device access for the WebAdmin console and portals
Streamlined management and quality of life enhancements:
- Enhanced navigation performance
- Hardware monitoring for SNMP with a downloadable MIB
- sFlow Monitoring for real-time visibility
- NTP server settings defaults to “Use pre-defined NTP server”
- UI enhancements for XFRM interfaces with pagination and search/filter options
SG UTM features:
With Sophos UTM heading toward end-of-life soon (July 30, 2026), some migrating customers will appreciate these added features:
- SHA 256 and 512 support for OTP tokens
- MFA support for WAF form-based authentication
- Audit trail logs with before and after tracking to meet the latest NIST standards
Get the full details
Download the full What’s New Guide for a complete overview of all the great new features and enhancements in v22.
Get started today
You can download the upgrade package or installer for v22 from the Sophos Firewall v22 EAP Registration Page. Simply submit your details and the download links will be emailed to you straight away.
All support during the EAP will be through our forums on the Sophos Firewall Community.
Please provide feedback using the option at the top of every screen in your Sophos Firewall as highlighted below in red or via the Community Forums.
Source: Sophos
Just under a year ago, we announced the acquisition of the cloud-forward identity security company, Rezonate. A very exciting milestone for our company. As the product leader, I was excited by the challenge: integrating an entire company, with its own products and capabilities, into our platform.
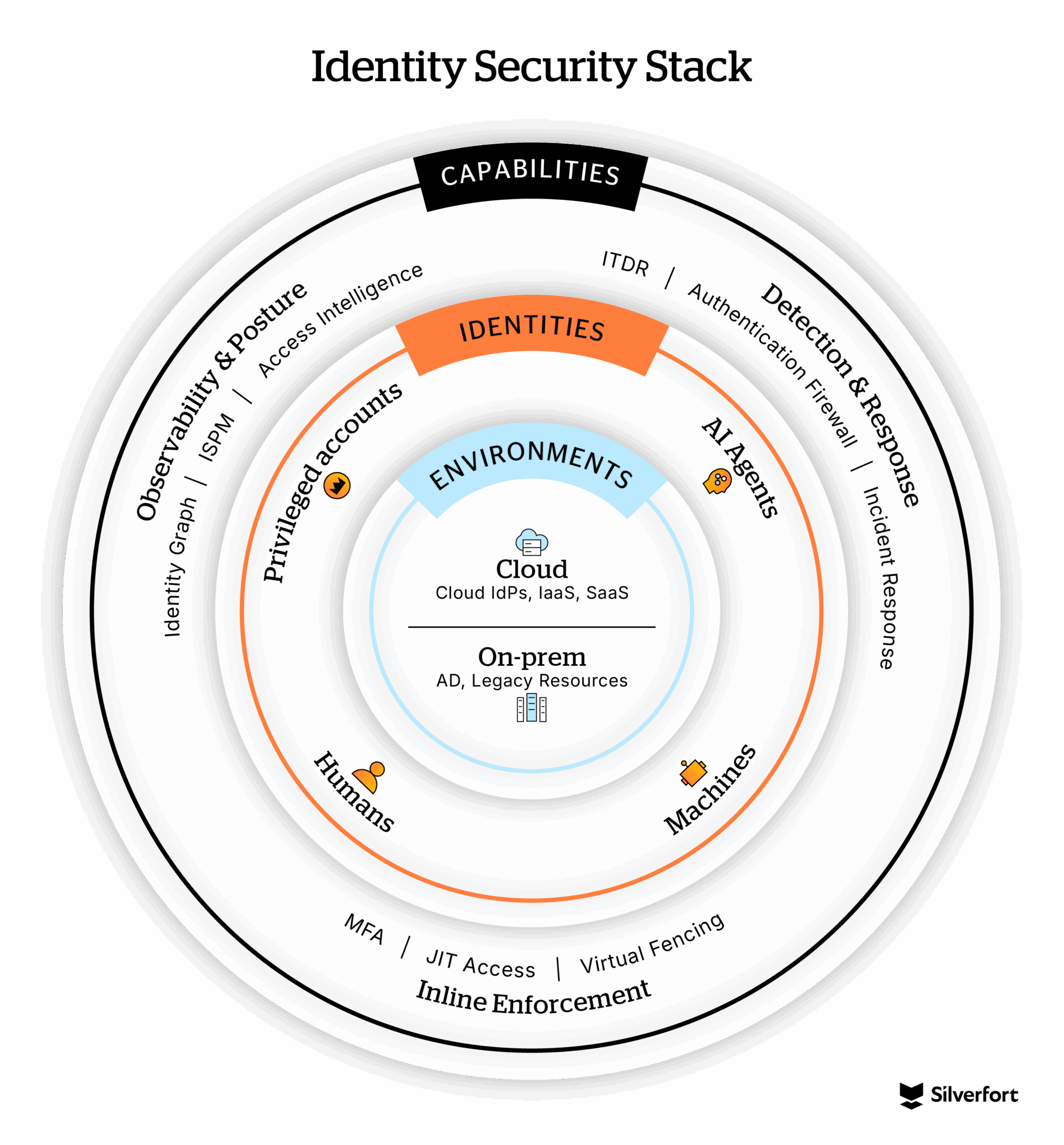
Speed mattered, but this milestone wasn’t just about how fast we could move; it was about redefining what identity security could actually be. Our vision has always been to deliver the most complete identity security platform: protecting every environment and every type of identity with the broadest set of capabilities. And today, I can say we’re continuing to deliver that vision with the latest expansion of the Silverfort Identity Security Platform.
Enterprises are drowning in identity complexity that spans hybrid environments—legacy Active Directory setups, cloud IAMs, SaaS sprawl, machine identities, and AI agents. Everyone’s asking the same questions: Who has access to what? How’s that access being used? And how can I control access?
Until now, the answer has usually been, “We can’t.” Point solutions offer partial visibility leading to gaps and blind spots regularly abused by attackers. The problem only grows as enterprises run parts of their business in the cloud.
We knew we had to meet our customers where they are.
Earlier this year, we announced our expansion to secure cloud-based non-human identities (NHIs). Today, I’m excited to announce the complete expansion of all our products to the cloud and unveil two new capabilities: Identity Graph & Inventory and Access Intelligence. These two innovations deliver the unified visibility and context customers need to take action and secure identities everywhere. They also solidify our leadership in the emerging Identity Visibility and Intelligence Platform (IVIP) space—giving enterprises both observability and insights to stay ahead of identity threats while driving operational efficiency.
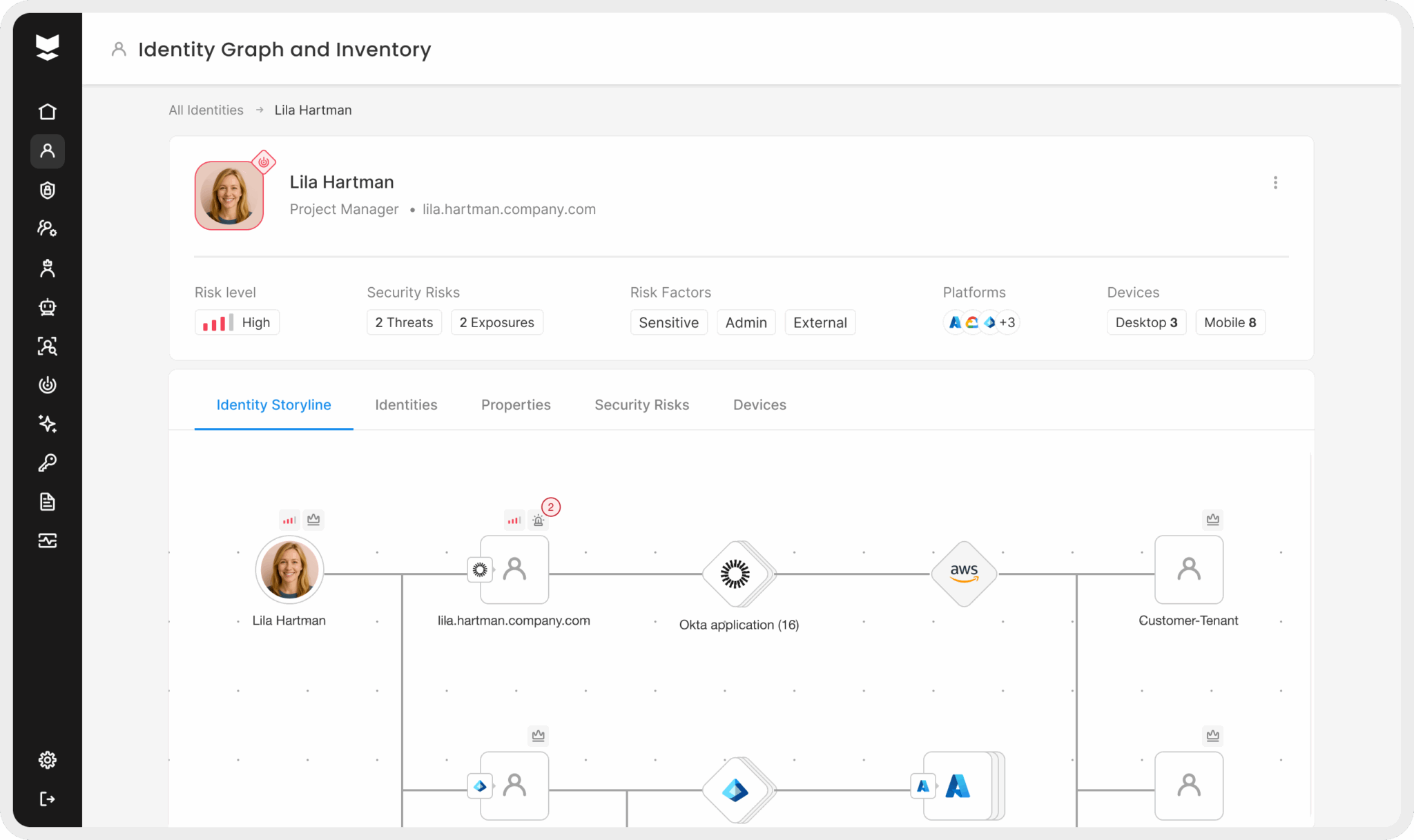
Identity Graph & Inventory: See Everything, Miss Nothing
With Identity Graph & Inventory, we’ve made every identity across your entire identity fabric visible—every user, machine, entitlement, and relationship mapped dynamically across cloud and on-prem systems. It’s a single source of truth that helps teams surfaces hidden access paths and over-privileged accounts, investigate faster, simplify audits, and eliminate blind spots. Instead of static spreadsheets or fragmented reports, you get living intelligence that reflects your real environment.
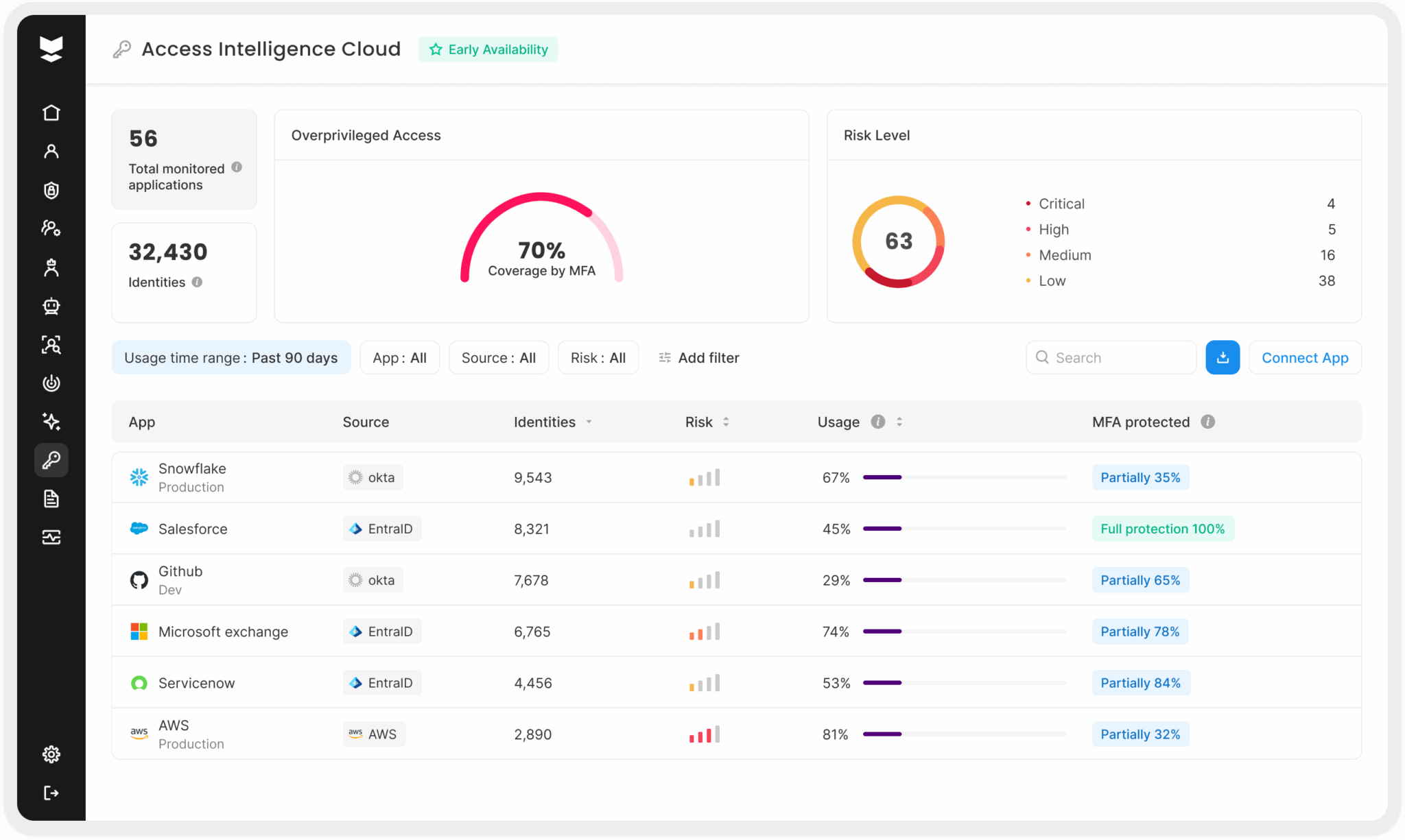
Access Intelligence: See what’s really happening and get to Least Privilege faster
Silverfort Access Intelligence gives teams something they’ve never had before—a clear, resource-centric view of how access is actually being used. It goes beyond permissions to show which users are really connecting to which resources, and how often. This visibility helps organizations enforce least privilege, uncover unused accounts and licenses, and stop threats before they spread.
Identity security done right
Silverfort is known for its unmatched protection for legacy environments. Customers use our platform to extend MFA to critical systems like VPNs, servers, file systems, databases, homegrown apps that were once beyond reach. With unique inline enforcement across every authentication in Active Directory, teams get context and control to protect service accounts, human users, and privileged access—in a single control plane. Teams can strengthen protection and uncover operational efficiencies.
With our latest release, we’re extending the core principles of identity security to the cloud. Customers now have complete visibility across their hybrid IAM stack and can take security-first approach to identity. They are up and running, avoiding the painful “security versus productivity” tradeoffs, and maturing their identity security programs faster than ever.
Now, our platform secures every type of identity—human, machine, and AI—across every environment. It gives organizations the complete picture and the ability to act on it, in real time.
If you’d like to see what’s new, take a moment to check out a demo of Identity Graph & Inventory and Access Intelligence. We think you’ll like what you see.
Source: Silverfort
As cyber threats evolve, organizations must constantly adapt their identity security strategies to stay protected. One of the most significant elements of modern security strategies is network segmentation, which involves the division of a network into smaller, isolated segments to limit unauthorized access to sensitive resources.
As network segmentation is well-known and implemented by most organizations, the rise of identity threats presents a more modern approach to segmentation from the identity control plane.
A further extension of this concept is identity segmentation, which focuses on the identity and attributes of the users, devices, and applications. This approach enables organizations to apply granular access controls to specific identities, improving their overall security posture and protection against unauthorized access.
In this blog, we will explore the difference between network segmentation and identity segmentation. We will also explore how identity segmentation is the key to implementing a true Zero Trust strategy.
The Evolution of Network Segmentation
Network segmentation is a security approach that isolates segments in the enterprise network to reduce the attack surface. Network segmentation works best in the “castle and moat” enterprise environment, securing all exposure points in the environment. This approach has been heavily implemented since the early 2000s by security and IT teams.
While this approach has proven effective in most network security strategies, the evolving nature of cyber threats highlights gaps in network segmentation.
Network segmentation access policies are typically defined by firewall rules or VLANs, which tend to be static and dependent on network traffic. These static policies are dependent on the device and not the user’s access requirements, often granting broad access to users based on their location within the network. Attackers increasingly target user identities, exploiting compromised credentials to gain unauthorized access.
The approach does not adapt to the dynamic nature of modern work environments, where users access resources from a variety of devices and locations. Network segmentation fails to provide the granular control required to secure identities effectively.
Identity Segmentation Boosts Identity Security Posture
Identity segmentation is the approach to security that involves managing and controlling access based on user identities, roles, and attributes. Instead of relying on rigid network boundaries such as IP access lists and firewall rules, identity segmentation divides the network not just from a physical or geographical standpoint, but also from the perspective of the identity control plane.
This is done by segmenting an environment based on the identity and attributes of users, devices, and applications. By doing so, organizations can implement granular access controls, ensuring users only have access to the resources necessary for their roles.
Network Segmentation vs Identity Segmentation
Network segmentation involves dividing a network into different segments to enhance security and control. Traditional network segmentation relies on factors like IP addresses, VLANs, and physical separation to create these segments. While effective at limiting the impact of a breach within the network, network segmentation often falls short in addressing the dynamic and evolving nature of user identities.
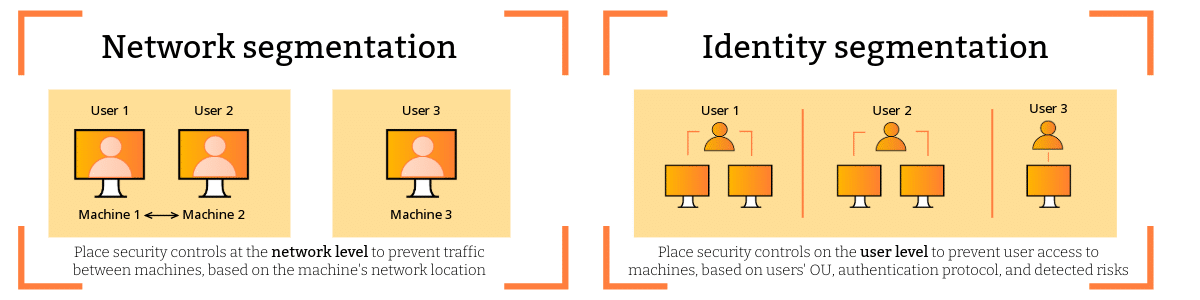
On the other hand, identity segmentation shifts the focus to user identities. This approach aligns with modern security threats where users are the primary targets and threats often exploit compromised credentials. Identity segmentation involves creating access controls based on user attributes, roles, and behavior, so users can only access the resources necessary for their roles, irrespective of their network location.
The primary difference lies in their focus: network segmentation emphasizes securing pathways and infrastructure, while identity segmentation centers on safeguarding individual user identities. Network segmentation tends to rely on static policies based on network structure, whereas identity segmentation involves dynamic and context-aware access controls based on user attributes. Identity segmentation is particularly effective in countering identity-based threats, which have become increasingly prevalent in the cybersecurity landscape.
Adapting to the Zero Trust Architecture
To implement a Zero Trust architecture, all organizations must protect their identities, devices, networks, applications, and workloads, as well as data. It is important to note that while many organizations have successfully implemented a few principles of the Zero Trust model, most still need to strengthen their identity security posture management.
Strong identity management and protection enables organizations to respond more rapidly and precisely when a potential threat arises. IT teams can better track and alert on any identity threats that come up, prompting proactive measures to stop potential unauthorized access attempts.
To construct a complete Zero Trust architecture across your environments, identity management and identity protection must be the core components. This will enable you to manage and protect all aspects of identity effectively, which is essential for safeguarding all types of assets, including those that are on-prem.
Source: Silverfort
You face no shortage of challenges in securing your organization from cyberattacks. The threat landscape continues to evolve, attack surfaces are expanding with the advent of new technologies, new adversary tactics and techniques keep emerging, and there’s more scrutiny than ever about what you’re doing to safeguard your environment.
Accurately assessing where you’re vulnerable to threats isn’t easy. Testing your defenses is an effective, proactive way to measure the strength of your security and set a course for lowering your risk before a threat actor strikes.
Put your defenses to the test and determine your risk
Introducing Sophos Advisory Services – proactive security testing services that provide expert, independent assessment of your cyber defenses and recommendations for improvement. These services support a more strategic approach to cybersecurity by identifying weak spots in your environment, allowing you to fortify your resiliency against potential attacks.
We’re delighted to announce general availability of four security testing services: External Penetration Testing, Internal Penetration Testing, Wireless Network Penetration Testing, and Web Application Security Assessment.
These services…
- Discover weak spots in your defenses. Uncover vulnerabilities in your environment that adversaries could exploit, based on the powerful combination of our experience from performing thousands of engagements and the latest threat intelligence from Sophos X-Ops.
- Assess your risk of being breached. Understand your real-world risk of being impacted by a cyber incident before an attack hits your business.
- Demonstrate your sound security practices to business partners. Show your organization’s commitment to cybersecurity to your customers, partners, stakeholders, regulators, and cyber insurance provider.
- Fortify your cyber resiliency. Make your security programs more resilient against threats. Testing is infused with current and relevant threat information from our research and testing teams.
Available today!
Sophos now offers the following security testing and assessment services:
- External Penetration Testing: Assesses your defenses against an adversary trying to exploit your environment from outside the perimeter.
- Internal Penetration Testing: Evaluates controls inside your perimeter to gauge interior defenses and guard against insider threats.
- Wireless Network Penetration Testing: Assesses your wireless network security networks and how attackers may attempt to gain access.
- Web Application Security Assessment: Tests your web applications for known vulnerabilities.
Sophos Advisory Services are delivered by our world-class team of cross-discipline security testers, backed by hundreds of security analysts and threat research experts.
Our services aren’t check-the-box, generic pass/fail tests. Our security experts meet with you before testing begins to understand your challenges and objectives. When testing concludes, we provide you with a detailed report for technical and non-technical audiences, featuring all steps taken during the engagement, our findings, and actionable recommendations you can use to elevate your organization’s security posture.
Learn more about how Sophos Advisory Services can uncover weak spots in your defenses and fortify your cyber resiliency. Speak to an expert today or visit Sophos.com/Advisory-Services.
Source: Sophos
In today’s fast-paced digital world, the relentless nature of cyber threats is taking a significant toll on the very people charged with defending our businesses: cybersecurity professionals.
 Our latest report, “The Human Cost of Vigilance: Addressing Cybersecurity Burnout in 2025,” sheds light on this growing crisis.
Our latest report, “The Human Cost of Vigilance: Addressing Cybersecurity Burnout in 2025,” sheds light on this growing crisis.
The report examines the direct human impact of these pressures, drawing on new research data to reveal the prevalence, key drivers, and consequences of burnout, ultimately underscoring how strategic solutions can mitigate this critical issue.
In the first quarter of 2025, data was collected via a vendor-agnostic survey of 5,000 IT and cybersecurity professionals across 17 countries, with the survey asking respondents about their experiences with burnout during 2024.
Pervasive strain and extensive repercussions
When asked about personal experiences of cyber fatigue or burnout, 76% of respondents reported experiencing it either constantly, frequently, or occasionally themselves over the last year.
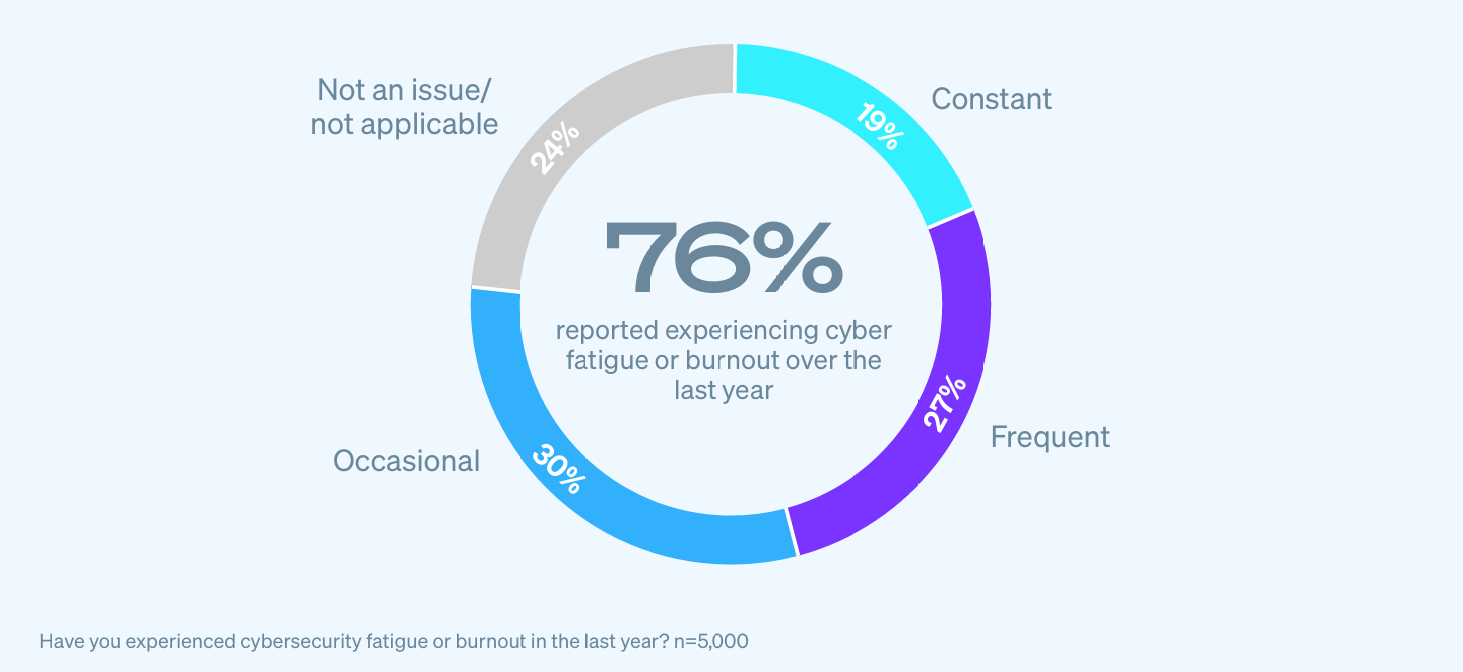
What’s more: the problem is getting worse, with 69% of respondents reporting that cybersecurity fatigue and burnout increased from 2023 to 2024.
The consequences of burnout
Unsurprisingly, burnout has significant negative impacts on the individuals that experience it, with almost half (46%) reporting heightened anxiety about cyberattacks or breaches, 39% admitting to reduced productivity at work, and a third saying they have had a reduced level of engagement at work.
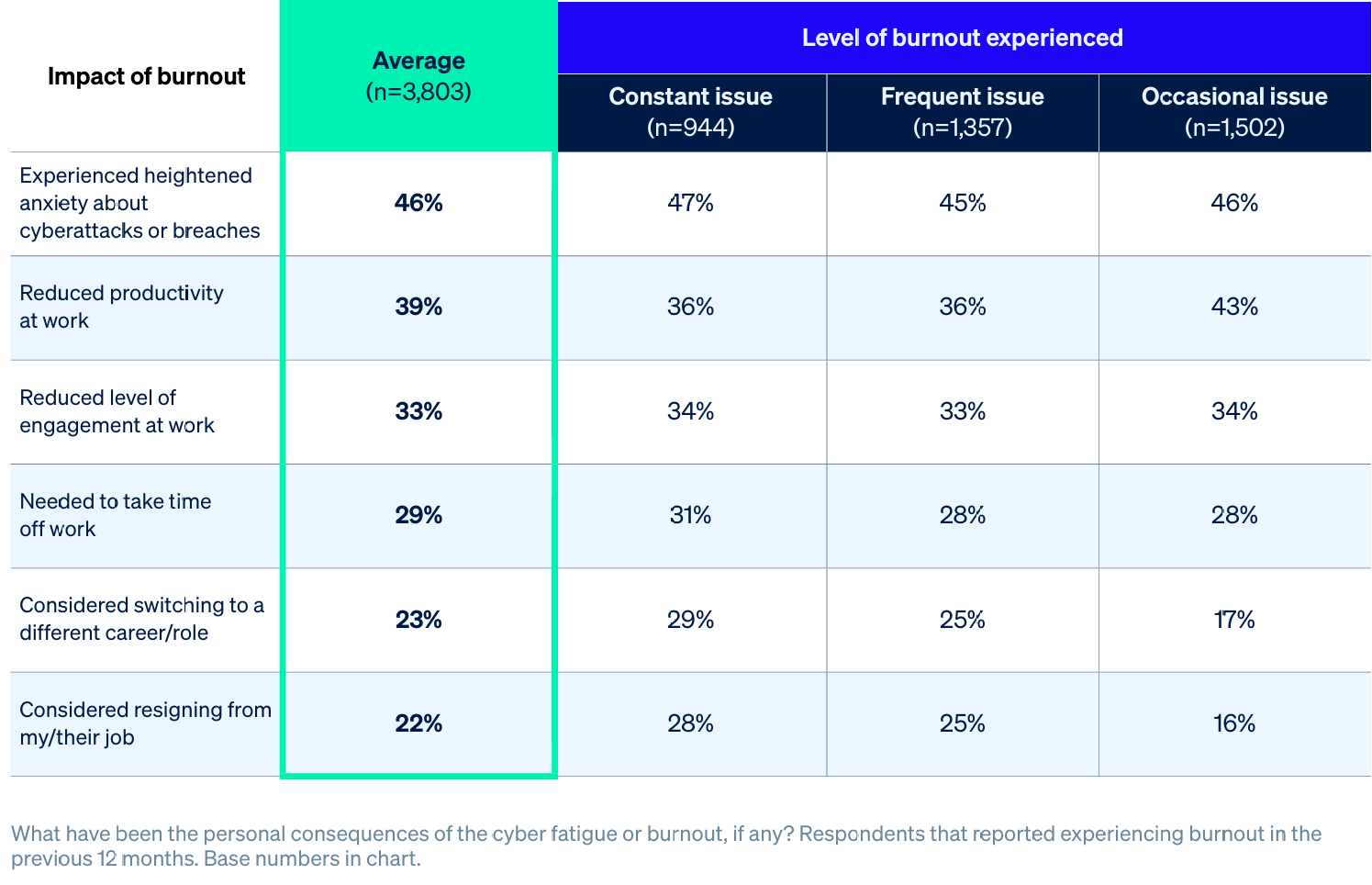
These figures highlight a pervasive challenge that directly undermines the effectiveness and sustainability of cybersecurity defenses.
Core causes of strain
The results reveal that cybersecurity stress is not just a technical issue: it’s a business one as well.
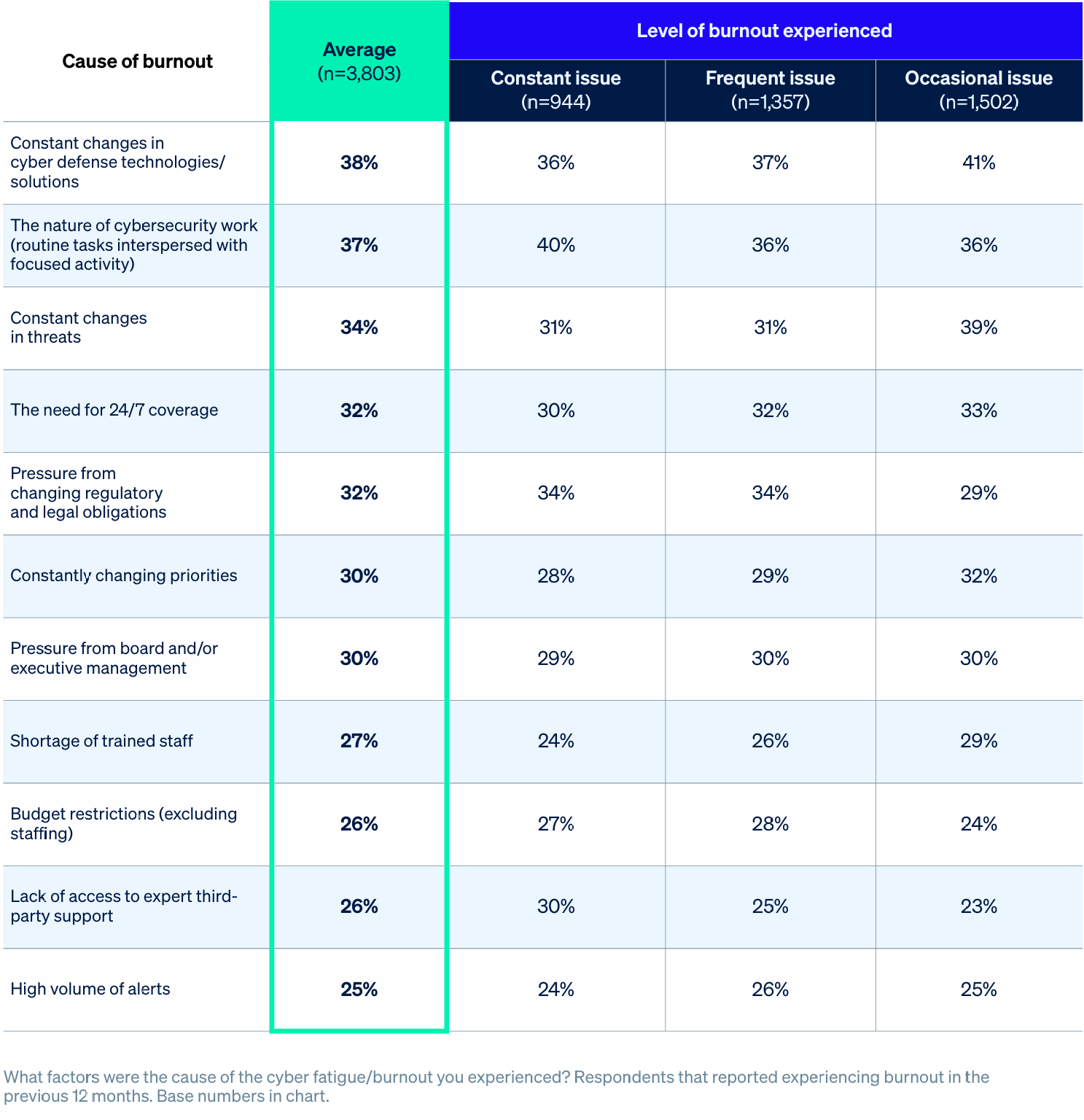
On average, respondents cited three separate factors that contributed to them experiencing burnout, highlighting the multiple pressures that IT teams face.
Learn more
It’s not all bad news, fortunately. For more details on these findings and to learn about potential solutions, we invite you to download the full report.
Source: Sophos