News
For your organization and others alike, its bottom-line growth is understandably priority number one. But as you’re likely well aware, the growing cyber threat landscape means more risks to organizations’ bottom lines are emerging every day. And while creating a sound cybersecurity strategy can seem overwhelming to teams low on resources, time, or talent, bad data management can be far more detrimental in the long run for an organization looking to grow. The following six risks pose the biggest threat to your organization’s continued growth and deserve your security team’s attention moving forward. And the good news is – many of these risks can be addressed methodically, with the help of trusted partners, to bolster your cybersecurity where you need it most and strengthen it over time.
1. Cyberattacks
Every day, cyberattacks are becoming more frequent, sophisticated, and damaging. Whether hackers choose to invade an organization’s network by taking advantage of an unpatched zero-day vulnerability, deliver a dangerous payload to halt their operations, or intercept network traffic to steal data, if that organization isn’t prepared for such an attack, its bottom line can take a serious hit.
Cybercriminals’ use of malware, and specifically ransomware, has seen a dramatic uptick since the beginning of the pandemic. According to SonicWall’s 2022 Cyber Threat Report, 623.3 million ransomware attacks were recorded in 2021, marking more than a 100% increase from the year before and more than a 300% increase from 2019. Furthermore, evidence suggests that both ransom demands and ransom payments are trending in the same direction. According to an update of Palo Alto Network’s 2021 Unit 42 Ransomware Threat Report, the average ransom demand has skyrocketed to $5.3 million, and the average cost of a ransom payment has risen to a staggering $570,000. The payment of a large ransom, the cost of halting business operations, and any harm the malware may have inflicted on an organization’s systems can all dramatically affect that organization’s bottom line, and if any sensitive data was compromised, the bill can soar even higher.
2. Unprotected Data
While a cyberattack in and of itself can be incredibly detrimental and costly, as we alluded to, when an organization’s sensitive data is stolen or otherwise compromised as a result, their bottom line can take an even larger hit. According to IBM’s 2021 Cost of a Data Breach Report, the average cost of a breach rose by 10% compared to 2020, now sitting at $4.24 million per breach.
Leaving your organization susceptible to a breach can exacerbate the fallout of an already costly cyberattack. For example, while a ransom payment may only cost an organization $570, 000, that figure does not account for costs associated with the suspension of business operations, the reinstatement of systems, investigation costs, and perhaps most importantly, compliance fines. In reality, the total average cost of a ransomware attack comes out to a whopping $4.62 million. While cyber insurance can help to cover some of these damages, ultimately, taking steps to protect your organization’s data before a breach ever happens is the most important factor in avoiding a breach’s unanticipated costs.
3. Human Error
When organizations take steps to protect their data against breaches, more often than not, they mistakenly prioritize protecting against outsider threats first. And while breaches are certainly prone to occurring because of an outsider with malicious intentions, insider threats and accidents can sometimes be overlooked. Egress’ 2021 Insider Data Breach Survey found that an overwhelming 94% of organizations experienced an insider data breach in the previous 12 months and 84% of organizations experienced a security incident because of an employee mistake.
Considering the average breach now costs organizations $4.24 million, it should go without saying that protecting against insider threats like human error is just as if not far more important than protecting against purposeful external attacks. Organizations can begin to combat human error by securing the way their employees share its data. Ensuring your organization’s sensitive data is encrypted in transit and can only be opened, read, modified, and forwarded by those with specific permissions is key to avoiding an accidental, yet just as costly data breach.
4. A Flat Network
Because human error is now such a prominent source of data breaches, granting employees too much access to your organization’s network can be incredibly dangerous. According to Verizon’s 2021 Data Breach Investigations Report, the use of stolen employee credentials was present in a quarter of all breaches in the previous 12 months. When an employee whose credentials have been stolen has full or close-to-full network access, a hacker will have the same level of access while posing as that employee.
A way for organizations to begin combatting this risk is to properly segment their network. Rather than the organization’s various network components all depending on a singular perimeter defense system, segmenting the network into several smaller sub-networks will only allow employees (or any bad actor posing as an employee) to have the least amount of access necessary. Although the goal of addressing security risks is to prevent a breach before one ever occurs, if and when one does occur, organizations can take advantage of a segmented network to limit the impact of the breach and quickly contain the threat.
5. Undertrained Employees
A lack of employee training is consistently one of the biggest contributors to breaches that occur as a result of human error, and a lack of training can show itself in several ways. Most pertinently, employees have shown themselves to be susceptible to social engineering attacks, and a bit more specifically, phishing attacks. A 2021 report by atlasVPN indicated that social engineering attacks were responsible for the most organizational data breaches (14%) in 2020. Furthermore, PhishLabs’ most recent Quarterly Threat Trends & Intelligence Report found phishing site volume increased by 28% in 2021, among other concerning statistics.
A lack of comprehensive, consistent, and engaging training can also lead to bad password hygiene, password theft, or even accidental data breaches like those discussed earlier. Proper employee training, on the other hand, can help to mitigate phishing and other social engineering attacks when implemented according to best practices. Unfortunately, organizations often neglect security training, and will sometimes even fail to create and enforce data security policies and procedures for employees to follow in the first place.
6. A False Sense of Security
For the most part, all of the data security risks discussed up to this point are fixable by implementing concrete changes within your organization. Unprotected data and external threats like hackers can be accounted for by implementing data security solutions that integrate with your software and workflows. Undertrained employees and human error within an organization often go hand-in-hand and can be addressed by creating a thorough set of corporate data security policies and taking a more frequent and engaging approach to employee training. Even an outdated network security model can be updated to fall in line with best practices.
Having a false sense of security, though, is perhaps an even more dangerous risk to organizations’ security because fixing it requires a change in philosophy from the top down. If an organization’s c-level executives maintain an “it will never happen to us” mindset— “it” referring to a major security incident—other security risks may not appear to be risks at all. Evidence suggests that nearly 8 in 10 consumers decide which organizations to do business with based on their reputation for information security, and because it only takes a single data breach to leave an organization’s reputation and bottom line severely damaged, changing your organization’s security mindset for the better is well worth the time and effort even if it isn’t an easy fix.
Source: HelpSystems
Organizations everywhere are rapidly shifting their technology stacks to include cloud services, remote work, IoT, and much more. This “digital transformation” is well underway in 2022, and it will only continue to grow. In this blog, we’ll look at the impact digital transformation is having on cybersecurity practices and controls, and the benefits identity and access security can offer.
Why is Digital Transformation Increasing the Attack Surface?
The embrace of DevOps has led to a convergence of coding and infrastructure management because, well…infrastructure is now software, too. With these shifts comes the realization that cybersecurity practices and controls need updates, too, from both a governance standpoint and a technical one. This is especially true in the realm of identity and access management (IAM)—particularly privileged identity and access security.
In truth, with all facets of IT becoming software-driven, most assets and elements of our infrastructure (both on-premise and in the cloud) are software-based in nature. This means everything has an identity of varying types. The explosion in access brings new risks and challenges that organizations have to plan for and navigate to take advantage of new technologies. Security teams now have a vastly larger identity attack surface due to digital transformation, including the following:
- Traditional on-premises directory services, mainframes, ERP systems, and other sources of record for user identities
- Application and service accounts, internally
- DevOps users and accounts for development and pipeline deployments
- Cloud service accounts for SaaS and PaaS/IaaS service orientation
- Federation services that provide single sign-on (SSO), and other cloud security and identity brokering services and tools
- IoT and SCADA platforms, systems, and services that are now exposed to APIs and internet access
The list goes on, far beyond these examples.
Everything is software; cloud is the “new normal” for infrastructure and application deployment; most workers are at least somewhat remote; and we’re trying to hold it all together from a security and compliance point-of-view.
Fortunately, the concept of digital transformation is also extending to the realm of identity and access management, and to information security and risk management, in general.
The Top Benefits of Identity and Access Security
First, we have vastly better synchronization, federation, and SSO capabilities than we have had in the past. This can help to centralize and coordinate identities of all sorts across platforms and between environments. Funneling as many identity interactions through a central platform can help enormously in managing and monitoring accounts and activity.
Next, we have privileged user controls capable of integrating with both on-premises and cloud-based service environments. This moves us away from traditional passwords and towards token-based authorization based in robust policy.
Finally, we are getting better at controlling remote access both to and from cloud resources, as well as traditional end-user access to internal environments. This is also beginning to extend to services, like IoT devices.
Where Do We Go from Here?
In my on-demand webinar, Digital Transformation, All Roads Lead to Identity, I highlight some of the most innovative and exciting trends, with an emphasis on cloud service implementation and DevOps. The discussion will delve into the types of identity attack vectors that can surface when implementing new technologies and IT practices, and how we can plan to tackle them head-on with planning, control and process definition, and leading cybersecurity technologies.
Source: BeyondTrust
The financial services cybersecurity environment is extremely complex, with a dizzying number of often-overlapping regulations, ongoing threats, and understaffed teams trying to manage it all. Despite paying significant attention to security, many organizations continue to be the targets of advanced persistent threats, fraud, sophisticated phishing campaigns, and other bold efforts to access the personally identifiable information (PII) and other sensitive IP they maintain.
Cyber-Attacks Are at a Record High – and Won’t Lessen Any Time Soon
Threat actors are emboldened in times of chaos. Their tenacious tactics—and frequent successes—rise in concert with geopolitical, social, and environmental upheaval.
2021 was a particularly devastating year in terms of cyber-attacks, and the financial services industry was hit hard. The rapid information digitization in the industry and ability of threat groups to avoid discovery and penalty have enabled seemingly unchecked advances. State-sponsored hacking campaigns have increased globally, making it difficult for many governments to curtail phishing attacks and ransomware sanctioned at the highest levels by rogue nations.
The scourge isn’t expected to abate in the coming months. FS-ISAC, the Financial Services Information Sharing and Analysis Center, recently announced in its Navigating Cyber 2022 Report that the top threats this year are expected to be third-party attacks, zero-day vulnerability exploits, and ransomware. Organizations need to further efforts to harden security now to protect their businesses and their customers.
Business Email Compromise (BEC) Fraud and Ransomware Attacks Delivered Through Phishing
PhishLabs research found 33.8% of all phishing attacks in Q1 of 2021 targeted financial institutions, and that figure rose to 61.3% of all phishing sites in Q4. These types of attacks have become highly sophisticated in recent years with well-designed emails and realistic messaging. This makes it difficult for employees to differentiate malicious endeavors from harmless communications. In fact, highly targeted business email compromise (BEC) schemes continue to trick employees into thinking one of their executives is asking them to take a particular action regarding sensitive financial information, such as transferring funds into a new account. You can learn more about handling BEC in this recent article.
Phishing emails can also deliver ransomware that encrypts or locks down systems until a threat actor’s demands are met. These attacks quickly take hold of networks after an employee clicks a link or opens a malicious attachment. Ransomware can be particularly devastating for financial services firms as they can’t afford downtime or the loss of direct access to funds.
Maintaining Compliance with Strict Regulations
GDPR, CCPA, SOX, GLBA, FINRA, PCI DSS—the financial services industry is no stranger to the alphabet soup of regulatory requirements governing all aspects of how sensitive data is stored, shared, processed, and destroyed. These details must be understood and addressed to comply with restrictions for data residency, sovereignty, and localization.
Compliance can present a significant burden to understaffed IT and InfoSec teams as they walk a fine tightrope to balance acceptable risk and business convenience. As the global workforce gap is around 2.72 million security professionals, it’s often a significant effort not only to maintain compliant practices, but also to monitor and document ongoing adherence. Additionally, staying up on the changes to the fine print of regulations can also pose a challenge. Of note, the PCI Security Standards Council (PCI SSC) recently published PCI Data Security Standard v4.0 to address emerging threats to the high-value account information PCI DSS safeguards.
Cloud and Online Services Add Fuel to the Cyber-Attack Fire
Like many companies, financial services organizations have embraced the trend of digital transformation and looked to the cloud and/or managed service providers (MSPs) to augment their capabilities. Mission-critical workloads and data now reside in the cloud to support geographically dispersed workforces and customers as well as access to this information via smartphone apps and mobile devices.
As such, the traditional on-premises security perimeter has disappeared. While the fast provisioning, 24/7 IT resources, and impressive uptime of the cloud offer notable benefits for financial services enterprises, reliance on hybrid or full cloud infrastructure can inject another layer of complexity when it comes to security. Teams need to fully understand their contract with cloud providers and MSPs to scope out responsibilities and security practices—and avoid surprises.
Resilience Is Needed Throughout the Supply Chain
Not all financial services organizations thoroughly understand how their partners handle security. This is a dangerous oversight, as an attack on a third-party provider can have a ripple effect throughout the industry, particularly for shared services. Ensure your supply chain partners have taken the right security steps to protect themselves as well as your business in a way that meets applicable compliance mandates and can ensure business continuity. Many well-known organizations have made the news for their association with smaller partners that didn’t effectively protect data or left vulnerabilities unchecked.
How Financial Services Organizations Can Prioritize and Manage Cybersecurity Risk
Given the complexity of this high stakes environment, the next logical question for CISOs and their teams is “How can we manage our risk?”. HelpSystems works with leading financial services organizations to assess the efficacy of existing efforts and identify vulnerabilities and areas of improvement. There are three key solution spheres to consider when working to enhance your level of visibility, control, and protection.
- Identify and manage the vulnerabilities
Modernizing your approach to vulnerability detection and management hinges on maximizing automation and achieving efficiency in the tools you use. Performing host discovery and vulnerability scans of external (internet facing) and internal IP-based systems and networks is an excellent start. Monitoring security risk scores is another valuable tactic. Learn more about HelpSystems vulnerability management. - Discover and secure valuable data
You know you have sensitive data stored on computers, cloud and on-premises servers, mobile devices, and more. But it must be classified before it can be protected properly. To do this, you’ll have to determine where data is stored, how it’s used, and where it flows. This includes identifying both structured and unstructured data. Learn more about HelpSystems data protection. - Collaborate securely and compliantly
Working with internal employees and external stakeholders including customers, partners, and third-party business associates requires strict attention to how data and files are shared. Safeguarding financial file transfers using secure managed file transfer (MFT) gives you full control and audit capabilities over how sensitive PII moves and who can access it. Learn more about HelpSystems secure managed file transfer.
Staying Positive in an Uncertain Landscape
Cyber-attacks have become weapons, scare tactics that erode trust and peace of mind, and weary financial service security teams are becoming desensitized to the ongoing state of high alert. At HelpSystems, we’re here to help. Our teams are dedicated to developing new ways to detect and thwart global threat actors and the chaos they cause. Our software keeps your valuable sensitive data protected.
The concept of least privilege roughly states that all users, applications, and processes should only be granted access to the minimum data and resources they need to perform their job, and for the least time necessary. In many cases, this equates to standard user access.
However, many basic OS, management, application, and software functions (e.g. configuration utilities) for Unix and Linux platforms require more than just standard privileged access. Traditionally, this required end users to possess elevated privileges in the form of root or administrative usernames and passwords. To overcome this inherent security and compliance risk, organizations must remove the need to distribute and maintain root and administrative credentials. That’s where third-party commercial Unix/Linux privilege management solutions come in. Enterprise-class solutions offer multiple benefits over native Unix/Linux capabilities and open-source tools like sudo.
But where do you start with Unix/Linux privilege management?
How do you know what to tackle first? BeyondTrust’s 30+ years in pioneering the Unix/Linux least privilege market tells us you can reduce Unix/Linux attack surfaces and improve compliance by doing five basic things really well. I’ve mapped some key capabilities in our Privilege Management for Unix & Linux product to these use cases.
1) Remove the need to log in as root
Many system and application users of Unix and Linux use the phrase, “I need root,” declaring they can only perform their daily job functions if they can log on as “root”, the most powerful user on the system. Root is often referred to as the “God” user as there is little the root user cannot do.
Allowing usage of the root account complicates the ability to audit an individual’s actions (promoting account sharing) and inhibits the use of a strong, changeable password for the root account due to the need for multiple identities to use the account at any given time. These characteristics dramatically increase risk. The organization faces a heightened danger from insider threats via malicious and accidental behaviors, as well as additional exposure from external threats due to weak and non-changing passwords. There is zero accountability when using root to perform administrative functions.
Privilege Management for Unix & Linux implements a true least privilege delegation model. The product enables users to run any command at a higher privilege level, so long as it is allowed by a policy defined in the centralized policy server. Removing the need for users to logon as root enables much tighter security controls around the root user account. Integrating a privileged password management system, such as BeyondTrust Password Safe, layers on further security and productivity benefits by proactively vaulting and managing these credentials.
Privilege Management for Unix & Linux does not rely on open-source privilege escalation tools like sudo, thereby further reducing the risk of critical vulnerabilities.
2) Consolidate logs and make the data accessible quickly and efficiently
It’s well-established that the command line nature of Unix and Linux systems doesn’t lend itself to easily-consumed searching capabilities. This drawback becomes especially apparent in very large enterprise systems with multiple log servers concurrently running. With that said, consolidating vast amounts of data, and finding what you are looking for, is key in identifying mistakes and mitigating risk.
BeyondTrust solves this problem via a powerful integration between Privilege Management for Unix and Linux and ElasticSearch/Logstash. This integration empowers customers to zero in on what they seek, quickly and efficiently. Privilege Management for Unix & Linux sends log data to ElasticSearch, where it is indexed in near real-time. The indexed data is searchable from within our dedicated management platform.
The unified search interface allows customers to search PMUL log data in an easy-to-use, “Google like” search interface. While the search syntax can be simple, it also provides advanced search capabilities. Advanced search features include Logical operators (and/or) Precedence, Wildcard searching, Field-specific searching, and/or Exact match searching using double quotes, and more. IT stakeholders benefit from having real-time visibility into the state of privilege-related Unix and Linux risks at their fingertips.
Privilege Management for Unix & Linux and AD Bridge (BeyondTrust’s solution for centralizing authentication for Unix/Linux environments by extension of AD’s Kerberos authentication and single sign-on capabilities) display the unified search results in bespoke grids. Titles will highlight the number of results for each product, and all search results will be highlighted in the grid and the details card. All results can be downloaded in either json or CSV format.
You can read more about this feature here.
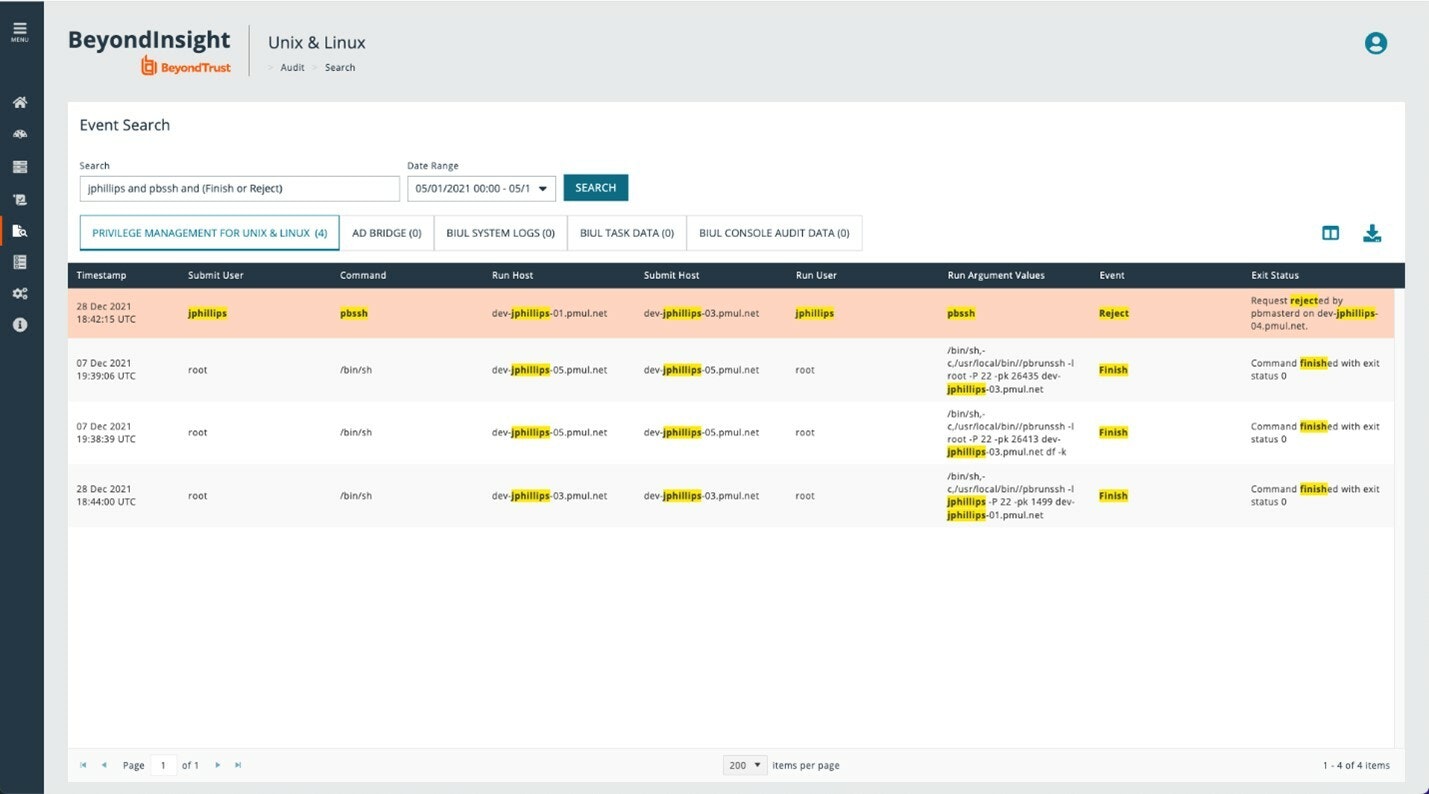
3) Achieve compliance for the root account – indelible audit trail, unimpeachable logs
From time to time, the most senior admins will have a legitimate need to leverage root capabilities. These sensitive use cases may include certain types of system-level changes, or just reflect the ad-hoc nature of the commands the user may need to issue. One challenge is that compliance teams need to monitor ALL activity and ensure accountability for actions, especially considering the privilege level being used during these sessions. Compliance teams need to cleanly identify:
- who was using the root account
- when they were using the root account
- what activities were performed/commands typed by the root account.
It is also imperative to protect log files from any sort of tampering. Searching the log files is critical for enabling the compliance team to find what they are looking for quickly and efficiently.
Privilege Management for Unix & Linux allows standard-named user accounts to elevate their rights to root level, with full session logging and session replays, providing a centralized, indelible audit trail and ultimate accountability for each individual system administrator. A dedicated management platform delivers a powerful, unified search experience where all log files are consolidated and can be searched via its ElasticSearch integration.
4) Faster forensics, when time is of the essence
Logging all Unix/Linux user activity can quickly become untenable. When a forensic investigation needs to be performed, organizations can waste time and manpower performing investigations as the sheer amount of data that is generated can be overwhelming.
With Privilege Management for Unix & Linux, event logs can be dynamically named, centrally located, and access controlled in the central management console. Our product utilizes Elastic to index all recorded sessions, with all information accessible via command line or REST API. Data is indexed in near real-time so customers can build pro-active analytics using the built-in Kibana dashboard.
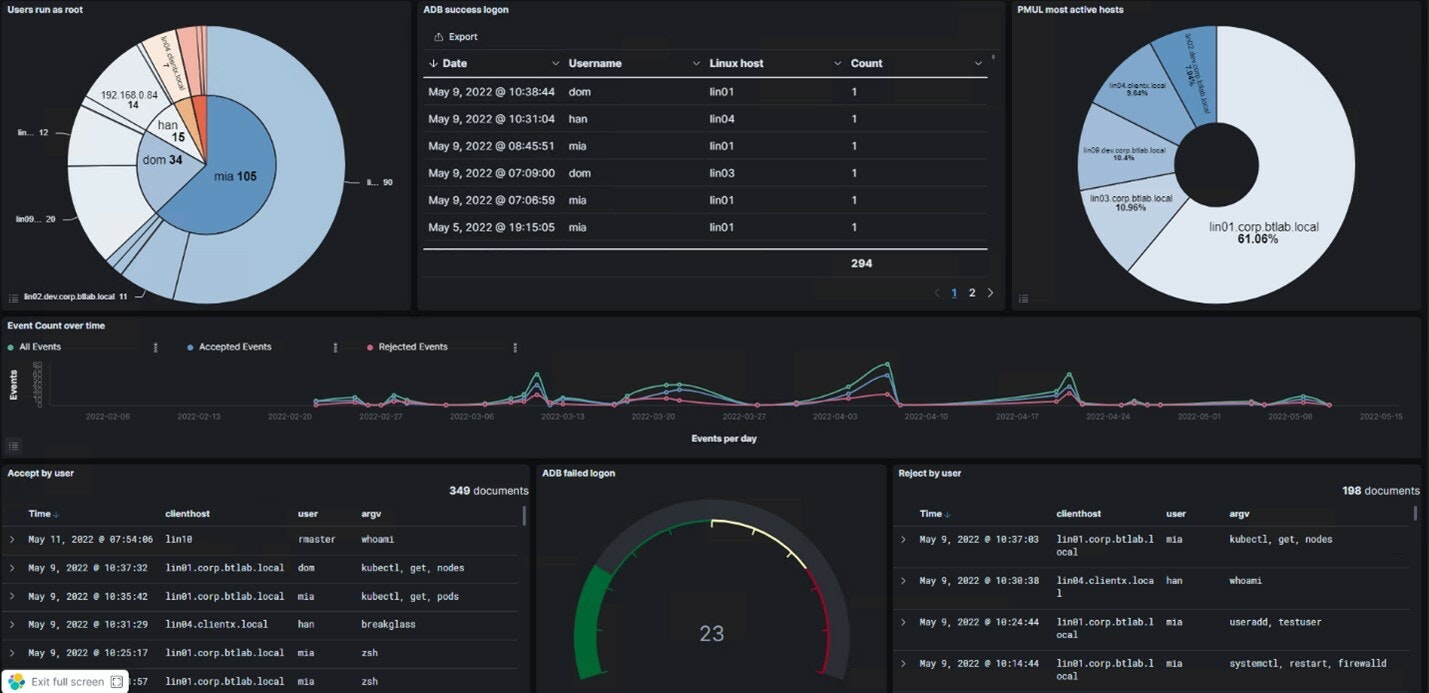
5) Record all Unix/Linux sessions – everything typed, everything seen
Least privilege is an ideal for most security groups, but sometimes, you just need to turn over a privileged shell, such as a root level shell. Strict auditing is a good way to keep honest people honest. So, for trusted admins, a full root shell is often no issue, as long as their activity is recorded in a tamperproof way to meet compliance needs.
One simple line in Privilege Management for Unix & Linux policy turns on full session recording, which is then dynamically named and automatically indexed using ElasticSearch. This capability enables organizations to view the session in many different ways:
- interactive playback
- video style playback
- session transcript
- command history
- searchable index (this capability provides flexibility to quickly turn on and search user activity, reducing risk).
How well are you performing each of these five activities now? What is standing in your way?
Time to retire (or supplement) sudo?
Sudo has been around for a long time. As the number of systems and users has grown, management of sudo has become very time-consuming, and completely untenable in even moderately complex environments. Coupled with limitations of the controls available in sudo, systems now seem overly exposed to an increasing number of internal and external security threats.
Privilege Management for Unix & Linux provides a far more flexible policy language, allowing for creation of infinitely more granular policies at both the command and system level. Privilege Management for Unix & Linux increases security in several ways, including moving the policy and log data off the users’ workstation or server, and utilizing the latest encryption technology for data both in transit and at rest.
The compliance and security benefits of using a commercial least privilege solution versus native sudo capabilities is significant. And for those organizations on a zero trust journey, the BeyondTrust solution provides must-have security controls around Unix/Linux systems and administration.
As you consider how to improve the maturity of your Unix/Linux server security and compliance, consider the five use cases I discussed in this blog.
Source: BeyondTrust
Security leaders have never faced such pressure to protect their organization’s data and reputation from the dangers that surround them. The COVID-19 pandemic permanently changed cybersecurity, from cloud migration to remote work to security at the edge. At the same time, threats have increased. No one is immune to the potential of social engineering attacks, zero-day exploits, and other attempts to steal data and peace of mind.
With this backdrop, HelpSystems commissioned a survey in partnership with ISMG in the fall of 2021 to better understand COVID’s impact on data security, how leaders feel about their progress, and the practices and priorities that define their strategies. The newly released results provide a snapshot of how enterprises are evolving their data security strategies in order to help others enhance their own journeys.
Key Findings:
From surveying over 180 cybersecurity leaders worldwide, we found that companies seem to be returning to a state of normalcy as they shift their attention from COVID mitigation to strategic planning. Implementing controls to secure IP as they support the new reality of hybrid workforces is top of mind for these leaders.
And yet, there are gaps in data security. Amid the focus on digital transformation, targeted social engineering attacks and ransomware continue to make inroads.
Some Highlights:
- 89% of survey respondents say their enterprises are more—or at least as—cybersecure as they were one year ago.
- 52% say cyberthreats have become fiercer in that time period.
- 19% say COVID-19 disrupted their data security initiatives.
- 63% say data visibility is the biggest challenge facing organizations today.
- 64% say a breach that exposes sensitive customer data is their top fear.
- 97% expect level or increased funding for cybersecurity in 2023, and key areas of investment will be enterprise data loss prevention (DLP), data classification, and encryption.
Key Takeaways:
- What got you here won’t secure you tomorrow. With mass cloud migration, new software vulnerabilities, and an adversarial focus on supply chain disruption, security strategies that protect your enterprise today won’t be the ones to rely on tomorrow, and cloud security strategies are going to continue to be imperative.
- Everything starts with data security. Fears are high about sensitive customer data being exposed, and rightly so. If there’s no line of sight to where sensitive data and IP reside and who can access it, it can’t be protected. Gaining visibility to that data is critical, which is reflected in the 2023 spending priorities noted in this survey as data classification, encryption, and DLP.
- New ventures require new partners. With the great resignation and shortage of cybersecurity skills and staff, vendors who can offer technology and skills to address data security challenges are key to success in every industry. A partner like HelpSystems can help you meet your objectives and close the security gaps you can’t address with personnel.
- The perimeter-less enterprise has broadened the attack surface. Aggressive, sophisticated cybercriminals including nation-state actors have taken full advantage of security environments being in flux as companies worked to support remote and hybrid workplaces. Enterprises need to harness the power of vulnerability scanning and implement robust email security measures to guard against phishing, business email compromise, and ransomware.
- Employees are often the first line of defense. Cybercriminals often seek to infiltrate a company through its employees, often trying various types of phishing campaigns. Although 86% of survey respondents said employees have participated in security awareness training over the past 12 months, only 32% considered it very effective (60% said it was somewhat effective). This indicates there’s room for improvement in this area.
Silver Linings and the Ongoing Digital Transformation
Although the threat landscape has changed remarkably over the past two years, IT security teams are beginning to settle into the new environment. Eighty-nine percent of respondents said they had a defined security policy, and more than 80% had updated it over the past two years. This is encouraging.
Awareness of potential risks is higher than it was pre-pandemic, and enterprises are working hard to assess their growing infrastructures and secure them like never before.
There is certainly work to be done to understand how the best practices required today will support cybersecurity in 2022 and beyond. The first step for many is to take a holistic approach to data security to understand the types of data that exist, where it resides, who can access it, and what level of protection it requires.
READ THE REPORT
Source: HelpSystems
Remote access VPN has long served us well, but the recent increase in remote working has cast a spotlight on the limitations of this aging technology.
Remote access VPN has been a staple of most networks for decades, providing a secure method to remotely access systems and resources on the network. However, VPN was developed to mimic the experience of being in the office. Once you’re in, you’ve got broad access to everything.
Zero trust network access (ZTNA), on the other hand, can be summed up in four words: trust nothing, verify everything. It’s based on the principle that any connection to your network should be treated as hostile until it’s been authenticated, authorized, and granted access to resources.
Simply put: with virtual private networking (VPN), you’re providing broad network access. With ZTNA, you’re providing specific application access.
Traditional remote access VPN vs. ZTNA
There are several differences between traditional remote access VPN and ZTNA. Here are some important ones, covering trust, device health, administration, and more.
Trust
With remote access VPN, users are implicitly trusted with broad access to resources, which can create serious security risks.
ZTNA treats each user and device individually so that only the resources that user and device are allowed to access are made available. Instead of granting users complete freedom of movement on the network, individual tunnels are established between the user and the specific gateway for the application they’re authorized to access – and nothing more.
Device health
Remote access VPN has no awareness of the health state of a connecting device. If a compromised device connects via VPN, it could affect the rest of the network.
ZTNA integrates device compliance and health into access policies, giving you the option to exclude non-compliant, infected, or compromised systems from accessing corporate applications and data. This greatly reduces the risk of data theft or leakage.
Remote connections
Remote access VPN provides a single point-of-presence on the network, which means a potentially inefficient backhauling of traffic from multiple locations, datacenters, or applications through the remote access VPN tunnel. 
ZTNA functions equally well and securely from any connection point, be it home, hotel, coffee shop, or office. Connection management is secure and transparent regardless of where the user and device are located, making it a seamless experience no matter where the user is working.
ZTNA is also a great way to ensure greater security controls during Remote Desktop Protocol (RDP) sessions. Known challenges with RDP include exposed default ports, no support for multi-factor authentication (MFA), broad network access, and of course security vulnerabilities. RDP server vulnerabilities and mistakenly-open RDP connections can be directly exploited by attackers, who leverage such exploits to identify themselves as trusted RDP users. With ZTNA, such users would be treated as hostile by ZTNA authentication features.
Visibility
Remote access VPN is unaware of the traffic and usage patterns it is facilitating, making visibility into user activity and application usage more challenging.
Since ZTNA access is micro-segmented, it can offer increased visibility into application activity. This makes monitoring application status, capacity planning, and licensing management and auditing much easier.
User experience
 Remote access VPN clients are notorious for offering a poor user experience, adding latency or negatively impacting performance, suffering from connectivity issues, and generally being a burden on the helpdesk.
Remote access VPN clients are notorious for offering a poor user experience, adding latency or negatively impacting performance, suffering from connectivity issues, and generally being a burden on the helpdesk.
ZTNA provides a frictionless, seamless end-user experience by automatically establishing secure connections on demand. This is all done behind the scenes, so most users won’t even be aware of the ZTNA solution that’s helping protect their data.
Administration
 Remote access VPN clients are difficult to set up, deploy, enroll new users, and decommission departing users. VPN is also challenging to administer on the firewall or gateway side, especially with multiple nodes, firewall access rules, IP management, traffic flows, and routing. It quickly becomes a full-time job.
Remote access VPN clients are difficult to set up, deploy, enroll new users, and decommission departing users. VPN is also challenging to administer on the firewall or gateway side, especially with multiple nodes, firewall access rules, IP management, traffic flows, and routing. It quickly becomes a full-time job.
ZTNA solutions are often much leaner, cleaner, and easier to deploy and manage. They’re also more agile in quickly changing environments with users, apps, and devices coming and going – making day-to-day administration quick and painless.
What to look for in a ZTNA solution
Be sure to consider these important capabilities when comparing ZTNA solutions from different vendors:
Cloud-delivered, cloud-managed
Cloud management offers tremendous benefits: being able to get up and running quickly, reduced management infrastructure, easy deployment and enrollment, and instant, secure access from anywhere on any device.
Integration with your other cybersecurity solutions
While most ZTNA solutions can work perfectly fine as standalone products, there are significant benefits from having a solution that is tightly integrated with your other cybersecurity products, such as your firewalls and endpoints. A common, integrated cloud management console can be a force multiplier for reducing training time and day-to-day management overhead.
It can also provide unique insights across your various IT security products, especially if they share telemetry. This can dramatically bolster security and offer real-time response when a compromised device or threat gets on the network.
User and management experience
Make sure the solution you’re considering offers both an excellent end-user experience as well as easy administration and management. With more users working remotely, enrollment and efficient device setup is critical when it comes to getting new users productive as quickly as possible.
Be sure to pay attention to how the ZTNA agent is deployed and how easy it is to add new users to policies. Also ensure the solution you’re investing in offers a smooth, frictionless experience for end users. It should also provide visibility into application activity to help you be proactive in identifying peak load, capacity, license usage, and even application issues.
Sophos ZTNA
Sophos ZTNA has been designed from the start to make zero trust network access easy, integrated, and secure.
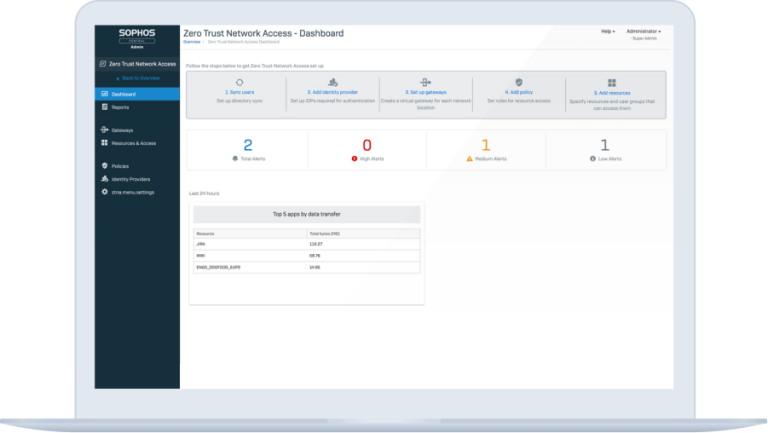
It’s cloud-delivered, cloud-managed, and integrated into Sophos Central, the world’s most trusted cybersecurity platform. From Sophos Central, you can not only manage ZTNA, but also your Sophos firewalls, endpoints, server protection, mobile devices, cloud security, email protection, much more.
Sophos ZTNA is also unique in that it integrates tightly with both Sophos Firewall and Sophos Intercept X-protected endpoints to share real-time device health between the firewall, device, ZTNA, and Sophos Central to automatically respond to threats or non-compliant devices. It acts like a round-the-clock administrator, automatically limiting access and isolating compromised systems until they’re cleaned up.
Sophos customers agree that the time saving benefits of a fully integrated Sophos cybersecurity solution are enormous. They say that using the Sophos suite of products together for automatic threat identification and response is like doubling the size of their IT team. Of course, Sophos ZTNA will work with any other vendor’s security products, but it’s unique in working better together with the rest of the Sophos ecosystem to provide tangible real-world benefits to visibility, protection, and response.
Visit Sophos.com/ZTNA to learn more or try it for yourself.
Source: Sophos
Datto, the leading global provider of security and cloud-based software solutions purpose-built for Managed Service Providers (MSPs), launched two continuity solutions, including its next generation SIRIS 5 product featuring up to 4X the performance and Cloud Continuity for PCs, improved for today’s dynamic, hybrid workforce. Both all-in-one backup and recovery solutions empower MSPs with best-in-class continuity for their small and medium business (SMB) clients. In the event of a physical loss, ransomware, hardware failure, or other disasters, Datto provides multiple recovery and restore options whether onsite or remote.
Last year in Q4, over 80% of ransomware attacks targeted SMBs, with an average business interruption of 20 days following successful attacks, which can be crippling for a smaller organization.¹ To survive attacks, SMBs must have access to business continuity solutions that can quickly restore their data and operations to prevent significant downtime and business interruptions. Business Continuity and Disaster Recovery (BCDR) is an established backbone of any ransomware recovery strategy.
Datto’s all-in-one complete BCDR solution with immutable backups and the secure Datto Cloud makes SIRIS 5 one of the best last lines of defense against cyberattacks, restoring business operations for SMBs within minutes. With SIRIS 5, partners can expect:
- Performance: Up to 4X more performance and an upgraded RAM and CPU that provides faster disaster recovery performance than ever before
- Reliability: Industry-standard server hardware, redundant power supplies, reliable enterprise SAS HDDs, HDD RAID, and advanced diagnostics for improved reliability
- Simplicity: Streamlined appliance options consolidate the best features to optimize performance, plus create an easier selection and upgrade process for partners
The SIRIS 5 appliance will run on purpose-built certified hardware powered by Dell. Dell’s world-class server hardware provides the industry-standard in reliability, serviceability, global reach, and supply chain resilience. Each SIRIS 5 device will undergo stepped-up comprehensive quality testing at a Datto facility and is backed by Datto’s 5-year warranty. Coupled with Datto’s renowned 24/7/365 support, Datto partners will have access to the most robust and reliable business continuity solution Datto has ever offered.
“An MSP’s best defense against evolving ransomware threats is a high-performing and reliable BCDR solution一and SIRIS 5 is Datto’s most powerful and flexible solution yet,” said Bob Petrocelli, Chief Technology Officer at Datto. “With its cloud-first architecture and integrated security, the SIRIS platform was created for MSPs, delivering an essential all-in-one solution for backup and recovery. We’re proud to release our flagship SIRIS 5 product which will deliver next-level reliability and performance when it matters most.”
“The number one concern for our clients is what a cyberattack would mean for their business. We need strong backup and recovery solutions in place if all else fails to ensure they’re up and running with minimal disruption,” said Razwan Ahmad, CEO of N.O.C. Systems LLC, a Datto MSP partner located in Connecticut. “With SIRIS 5 we know we’re covered. Datto’s world-class technology and support enables us to protect our clients’ data and livelihoods with the strongest solution.”
SIRIS 5 is allready available across the globe.
Source: Datto
As breaches continue to rise, cybersecurity and development professionals are feeling the pressure to maintain their organizations’ security postures.
Invicti Security™ today released research in its State of the DevSecOps Professional: At Work and off the Clock report unveiling how developers and security professionals are overworked and understaffed, yet prideful of their roles within their organizations.
Conducted in partnership with Wakefield Research, the report is based on a survey of 500 cybersecurity professionals and software developers with at least a Director title within their organization. Surveyed individuals came from U.S. companies with 2,000 or more employees.
The survey reveals that the Great Resignation and impending cyberattacks have created added stress on their jobs:
- DevSecOps professionals spend more than 4 hours each workday addressing security issues that never should have happened in the first place, with 41% of cybersecurity professionals spending 5+ hours addressing security issues compared to 32% of their developer counterparts.
- After the last vulnerability is discovered, 81% of professionals are likely to already feel anxious about the next.
- It’s affecting personal lives too. Half of cybersecurity and development pros (50%) have had to log in over the weekend or on their own time, and 1 in 3 blew off a date or night out with friends. In fact, 41% of developers blew off a night out compared to 34% of their cybersecurity counterparts.
Despite this, the majority of professionals are proud of their careers, and they see their overall work making a positive impact. The findings show:
- Because of their work, 65% of cybersecurity and development professionals believe they’ve saved their companies $1M+ this year by preventing breaches.
- 94% agree that digital transformation and the move to a remote work model in recent years have made their role more valuable and rewarding.
- They believe they’ve chosen an attractive career path. Eighty-eight percent said they would be proud to put “cybersecurity expert” in an online dating profile.
- Working relationships are improving between security and development. 49% of respondents say they are “besties” with their counterparts, while 28% say they are “frenemies.” That’s up 14% from the Fall Edition of the Invicti AppSec Indicator.
“Moving to the cloud and the pressure to secure everything without slowing down business priorities has made cybersecurity and development professionals the unsung heroes of their organization,” said Sonali Shah, Chief Product Officer at Invicti. “But with strapped teams, organizations are struggling to retain talent. That’s why it’s critical to prioritize technology that protects the organization while also enabling collaboration, automating manual tasks, and in turn, promoting overall well-being.”
Source: Invicti
Customers have spoken, naming Sophos a Gartner® Peer Insights™ Customers’ Choice for Network Firewalls.
Across 359 verified customer reviews, customers overwhelmingly recommend Sophos, with an average rating of 4.7/5 across 359 as of February 28, 2022. Overall, Sophos is the highest rated among all named vendors with at least 150 reviews.
CLICK HERE TO DOWNLOAD THE REPORT
In addition, Sophos is the only Network Firewall Customers’ Choice vendor for public Sector, Government, and Education customers, and is also named a Customers’ Choice for Midsize Enterprise, Manufacturing, Services, Asia/Pacific, and EMEA.
Based solely on independent customer reviews that have been rigorously evaluated by Gartner, we believe this nomination is a testament to the unparalleled protection, superior visibility, easier management, and excellent value that Sophos Firewall delivers every day to customers around the globe.
Unique double recognition
Sophos is the only vendor to be named Customers’ Choice for BOTH the 2021 Voice of the Customer: Endpoint Protection Platforms and the 2022 Voice of the Customer: Network Firewalls.
Via our Adaptive Cybersecurity Ecosystem, customers benefit from some of the most powerful endpoint, workload, network, cloud, and email security solutions available. And it’s all managed through a unified cloud-based platform and underpinned by the collective threat intelligence of our security operations, Sophos Labs, and Sophos AI experts.
Hear from over 500 Sophos Firewall customers
Gartner Peer Insights shares the independent voice of verified enterprise customers. Recent feedback includes:
These are just a few of over 500 Sophos network firewall customer reviews available on the Gartner Peer Insights site. I would like to take this opportunity to thank our customers who have shared their feedback; we truly appreciate your time and your trust.
Sophos Firewall optimizes your network protection
Sophos Firewall delivers powerful protection and performance for even the most demanding network environments with benefits you just can’t get with any other firewall:
Expose hidden risks – Sophos Firewall does a far better job of exposing hidden risks than other solutions through a visual dashboard, rich on-box and cloud reporting, and unique risk insights.
Block unknown threats – Sophos Firewall makes blocking unknown threats faster, easier, and more effective than other firewalls with advanced high-performance TLS inspection and a full suite of advanced protection capabilities that are very easy to set up and manage.
Automatically respond to incidents – Sophos Firewall with Synchronized Security automatically responds to incidents on the network thanks to Sophos Security Heartbeat, which shares real-time intelligence between your Sophos Endpoint protection and your Sophos Firewall.
Speak with your Sophos representative to discuss how Sophos Firewall can help you achieve your network security goals.
Sophos Firewall is even better with SFOS v19
Sophos Firewall continues to get stronger with our latest release, which delivers Xstream SD-WAN, high-performance VPN, and powerful new search capabilities to help optimize your network protection and performance even further. If you’re already using Sophos Firewall, be sure to check out the latest release information and upgrade today!
Source: Sophos
Cybersecurity is not an industry that is synonymous with fashion. We have never had an iPhone moment before; that point when a smart, sparkly new technology appears that is so useful and usable that it goes from nowhere to becoming the de rigueur standard in the space of just a few years.
Most of what hits the press about cybersecurity is the – Who just got their brand annihilated by a very public mega-breach? Or, What snarky new trend are the cybercriminals leveraging?
It’s nice to have some good news for a change.
The good news here is: Passwords are dying out.
No, really they are.
Yes, there will still be some passwords around BUT due to the relatively recent development of certain new security standards and protocols – organizations are now able to move to a passwordless model. And as it turns out – this passwordless model has quite a few substantial security benefits – if you put the pieces together correctly.
In my on-demand webinar Zero Trust = Zero Passwords?, we explore exactly what passwordless really means – and for good reason – because any organization retaining an ongoing reliance on passwords is rapidly marking itself out as a highly vulnerable target for cybercriminals. In other words, no organization wants to get caught out not knowing what passwordless is and what security benefits it can bring.
Perhaps it is because I started out as an auditor – but there is nothing more concerning to me (right now) than any supplier who still needs each user to authenticate with a username and password – and to do it on every session – and on top of that – has no secondary authentication either. They literally might as well paint a large bullseye over the door of their corporate headquarters – and place a brush matt in the entrance emblazoned with the words “Hackers welcome”.
In addition to the transition away from passwords, another emergent trend is towards the buzz of Zero Trust. Just what is zero trust? Does the definition depend on who you talk to? Is zero trust easy to deploy? And – does it fit with the exciting trend of going passwordless?
I have taken my experiences (good and bad) and research into zero trust and passwordless security to put together a concise explanation of these topics and how they relate to each other. I have also included some top tips – and an outline of the potential pitfalls to be aware of during deployment.
Zero Trust has become the buzzword of the moment in cybersecurity sector at the moment – but what is it really? After all – a lot of the principles (apply least privilege, trust nothing by default, …) really do not sound any different from the core security principles we are supposed to have been applying for a long time.
Join the on-demand webinar session for a fun and insightful journey into the world of zero trust and passwordless authentication. Does zero trust mean zero passwords? Check out the session to find out!
Source: BeyondTrust
Sophos recently released the State of Ransomware 2022, its annual study of the real-world ransomware experiences of IT professionals working at the frontline around the globe.
The study has revealed an ever more challenging attack environment together with the growing financial and operational burden ransomware places on its victims. It also shines new light on the relationship between ransomware and cyber insurance, and the role insurance is playing in driving changes to cyber defenses.
This year, 5,600 IT professional from 31 countries participated in the research, with 965 sharing details of ransom payments made.
Key findings include:
- Ransom attacks are more frequent – 66% of organizations surveyed were hit with ransomware in 2021, up from 37% in 2020
- Ransom payments are higher – In 2021, 11% of organizations said they paid ransoms of $1 million or more, up from 4% in 2020, while the percentage of organizations paying less than $10,000 dropped to 21% from 34% in 2020. Overall, the average ransom paid by organizations that had data encrypted in their most significant ransomware attack, increased nearly fivefold to reach $812,360
- More victims are paying the ransom – In 2021, 46% of organizations that had data encrypted in a ransomware attack paid the ransom. Twenty-six percent of organizations that were able to restore encrypted data using backups in 2021 also paid the ransom
- The impact of a ransomware attack can be immense – The average cost to recover from the most recent ransomware attack in 2021 was $1.4 million. It took on average one month to recover from the damage and disruption. 90% of organizations said the attack had impacted their ability to operate, and 86% of private sector victims said they had lost business and/or revenue because of the attack
- Many organizations rely on cyber insurance to help them recover from a ransomware attack – 83% of mid-sized organizations had cyber insurance that covers them in the event of a ransomware attack
- Cyber insurance almost always pays out – In 98% of incidents where the victim had cyber insurance that covered ransomware, the insurer paid some or all the costs incurred (with 40% overall covering the ransom payment)
- 94% of those with cyber insurance said that their experience of getting it has changed over the last 12 months, with higher demands for cybersecurity measures, more complex or expensive policies and fewer organizations offering insurance protection
“The findings suggest we may have reached a peak in the evolutionary journey of ransomware, where attackers’ greed for ever higher ransom payments is colliding head on with a hardening of the cyber insurance market as insurers increasingly seek to reduce their ransomware risk and exposure,” said Chester Wisniewski, principal research scientist at Sophos.
“In recent years, it has become increasingly easy for cybercriminals to deploy ransomware, with almost everything available as-a-service. Second, many cyber insurance providers have covered a wide range of ransomware recovery costs, including the ransom, likely contributing to ever higher ransom demands. However, the results indicate that cyber insurance is getting tougher and in the future ransomware victims may become less willing or less able to pay sky high ransoms. Sadly, this is unlikely to reduce the overall risk of a ransomware attack. Ransomware attacks are not as resource intensive as some other, more hand-crafted cyberattacks, so any return is a return worth grabbing and cybercriminals will continue to go after the low hanging fruit.”
To learn more, read the State of Ransomware 2022.
About the study
Sophos commissioned research agency Vanson Bourne to conduct an independent, vendor-agnostic survey of 5,600 IT professionals in mid-sized organizations (100-5,000 employees) across 31 countries. The survey was conducted during January and February 2022, and respondents were asked to respond based on their experiences over the previous year. Respondents were from Australia, Austria, Belgium, Brazil, Canada, chile, Colombia, Czech Republic, France, Germany, Hungary, India, Israel, Italy, Japan, Malaysia, Mexico, Netherlands, Nigeria, Philippines, Poland, Saudi Arabia, Singapore, South Africa, Spain, Sweden, Switzerland, Turkey, UAE, UK, and US.
Source: Sophos
Backing up servers, workstations, and other devices is a best practice and business imperative, but backups alone are no guarantee of business continuity and data protection. While creating a backup, be it a disk images or copies of files, is the start of a disaster recovery plan, it is no guarantee that a company can recover if the backup is damaged. However, an even greater concern could be the theft of an organization’s confidential data if a backup itself is stolen or otherwise compromised by an attacker.
Today’s cyber criminals are far more devious and effective than those of generations past. In the early 2000s, a cyberattack often consisted of damage to data or the theft of files. Today, attackers can steal data without the victims even knowing the theft occurred.
Phantom cloud accounts
With so much data today stored in the cloud, sophisticated attackers now can redirect backups or traditional data storage from the victim’s own cloud-based accounts to those of the attackers. Essentially, today we have organizations saving their data to their attackers’ web accounts, even though it would appear to the victim that their data was housed safely in their own cloud environment.
For organizations that are saving their backups to the cloud, their security professionals need to ensure periodically that they are indeed saving the backups to their own accounts, not a redirected account. Using compromised systems administrator credentials and by by-passing second-factor authentication in a manner similar to that of Russian state actors described in the Sophos Naked Security article CISO warning: “Russian actions bypassed 2FA” – what happened and how to avoid it, cyber criminals can highjack one or more accounts on a cloud server and access corporate files, including backups.
Protect your backups
Backups that are not encrypted could be compromised, allowing attackers with the ability to both read the data in the backup and/or inject malware into the backup so that if the organization’s servers are later compromised, the backup would re-infect the servers when the backup is restored.
Having encrypted backups is not only a best practice for cybersecurity but one of the 12 keystone security controls the cyber insurance firm Marsh McLennan Agency lists as a top five security control required to qualify for obtaining cyber insurance. Encrypted backups rank right up at the top of the list of essential controls along with multifactor authentication, endpoint detection and response, privileged access management, and email filtering and web security.
Backup products that monitor for anomalies in access and data patterns can be used to identify potential malware on the system, including ransomware attacks. Integrating the server backups with existing security information and event management (SIEM) software or security orchestration, automation and response (SOAR) applications could help the IT security team identify system aberrations that could alert the team to a potential system compromise.
Plan for an attack
Creating a backup strategy that anticipates an attack can provide the organization backing up their data with an edge. Let us assume that the servers being backed up are running a version of Windows, be it for workstations (Windows 10 or 11, for example) or a Windows Server version. If the organization is primarily a Windows-centric enterprise, then an appropriate backup system would be running Linux and storing the resultant backup on a Linux system not connected to the corporate network.
While this approach is not foolproof, it will eliminate a sizeable percentage of attacks designed for Windows-based networks.
Selecting the right off-site storage environment can have a significant impact on the restore rime required for a backup. If you choose to have a hot site as a backup — a site that exactly mirrors the existing network so if the primary network fails, there is a duplicate ready to take its place — consider putting some distance between the two sites.
After a major hurricane hit Florida in the early 2000s, one company was forced offline for several weeks because its hot site was located just a few miles away. Flooding not only damaged the company’s primary data center but also the backup. Similar occurrences were reported after the felling of the two World Trade Center towers. A major data center was located below one of the towers. Companies in the towers that used the data center as their hot backup not only lost everything in their offices, but also all their backups when the data center was buried under tons of debris.
A better option is to select a location perhaps a hundred or more miles away. While there will be lag time between writing data to a local disk and writing that same data to the hot backup, the physical separation eliminates any potential carry-over effect from a disaster, natural such as flooding from a hurricane or fire damage from a massive forest fire. Rarely does a natural disaster impact facilities a hundred or more miles apart, although that could happen if the facilities are long natural disaster lines, such as common paths for hurricanes on the east coast.
Protecting backups from being compromised, intercepted, or damaged is an essential task of an organization’s cybersecurity team. With World Backup Day right around the corner, security teams should re-double their efforts to ensure every backup is safe, secure, encrypted and stored in multiple locations, including at least one location far from the source servers.
Source: Sophos
We’re excited to share that Sophos has acquired SOC.OS, an innovative company based in the UK that solves the problem of alert fatigue and limited visibility so prevalent in IT security environments. Finding the key signals amongst the noise, SOC.OS consolidates and prioritizes high volumes of security alerts from dozens of IT products and platforms across an organization’s estate, allowing security operations teams to quickly understand and respond to the most urgent ones.
With SOC.OS, Sophos plans to advance its Managed Threat Response (MTR) and Extended Detection and Response (XDR) solutions for organizations of all sizes by including additional telemetry and context from alerts and events across dozens of third-party endpoint, server, firewall, Identity and Access Management (IAM), cloud workload, email, and mobile security products.
According to the Gartner® Market Guide for Extended Detection and Response, Nov. 8, 2021, “To make XDR a long-term investment, (organizations need to) evaluate breadth and depth of ecosystem integration. The easier the XDR can integrate into your existing environment, the better an investment it will be.”
Sophos MTR is one of the fastest-growing new offerings in the company’s history. We now stand as one of the largest Managed Detection and Response (MDR) operations in the world, delivering superior security outcomes through an MTR service with more than 8,000 customers. The top enhancement request from these customers is ‘better integrations with existing security environments,’ and with the innovative technology from SOC.OS, we will be able to do just that – seamlessly integrate Sophos’ MTR and XDR solutions with an organization’s current set of security and IT solutions, optimized their return on investment. SOC.OS will also provide our Adaptive Cybersecurity Ecosystem with a broader set of third-party telemetry, so security analysts have better visibility into important events and alerts. SOC.OS has an impressive list of integrations that will benefit Sophos customers as we continue to expand and develop industry-leading XDR and MDR capabilities.
“Alert fatigue and lack of visibility still plague security teams worldwide. Considering this, against the backdrop of constantly changing cyberthreats and a challenging talent landscape, defenders need new and innovative products and services that can help them solve more complex incidents in less time. For many defenders, however, the complexity and cost of traditional security solutions act as barriers to adoption. By joining forces with Sophos, we can address these challenges together, head on. The sum is greater than our parts, and by combining our capabilities, we’re positioned to offer truly unique, cost effective and highly accessible products and services to those who need it most, on a global scale.”
Dave Mareels, CEO and co-founder, SOC.OS
We’re very excited to bring the team and technology from SOC.OS onboard. In the meantime, on behalf of Sophos, Joe Levy, Chief Technology Officer (CTO), would like to extend a very warm welcome to SOC.OS employees and customers.
For more information, please see the press release.
Source: Sophos
We’re thrilled to announce that Intercept X scored 100% Total Accuracy ratings for enterprise and small business, and Sophos Home scored a 100% Total Accuracy rating for consumer protection in the SE Labs Jan – Mar 2022 Endpoint Security Tests.
100% for enterprise protection
Intercept X reinforced why it was named the SE Labs Best Enterprise Endpoint Protection 2021 with a clean sweep, scoring 100% for protection accuracy, legitimate accuracy, and total accuracy with zero false positives. View the full results here.
100% for small business protection
Scoring 100% for protection accuracy, legitimate accuracy, and total accuracy with zero false positives, Intercept X is the perfect choice for securing small businesses. View the full results here.
100% for home protection
Home users are exposed to the same malware and attacks as large enterprises. Sophos Home uses the same powerful technology that keeps those organizations safe. It scored 100% for protection accuracy, legitimate accuracy, and total accuracy with zero false positives. View the full results here.
Try Intercept X today
Intercept X reduces the attack surface and prevents attacks from running. It combines anti-exploit, anti-ransomware, deep learning AI, and control technology to stop attacks before they impact your systems. It integrates powerful extended detection and response (XDR) with automated detections and investigations, so you can minimize the time to detect and respond to threats. Learn more and start your free trial.
Looking for protection for your home devices? Start a free trial of Sophos Home.
Source: Sophos
When searching for security solutions for your organization, it may be easy to assume your solutions need to be unique to your data, your employees, and your industry; and you wouldn’t be wrong in your assessment. Choosing the right security solutions that are financially sustainable, integrate with your current solution(s), and streamline rather than obstruct workflows can mean opting for vastly different ones compared to your closest competitors. What nearly every modern organization has in common today, though, is that they create and share more data than they ever have before.
Organizations’ desire to make collaboration and the transfer of data in general as seamless and efficient as possible has only increased in recent years, and the rapid transition to remote work due to the COVID-19 pandemic has only intensified that desire. But just because collaboration is becoming easier and more automated does not necessarily mean your data is becoming more secure. While data classification solutions can help identify and give context to your data and secure managed file transfer solutions can encrypt that data and streamline transfer processes, organizations often find their data and its protection are out of their control once it leaves their network or the bounds of their MFT tool.
This is where the concept of secure data sharing comes into the equation for many of these organizations. Like with other types of security solutions, however, data tracking can serve different purposes depending on the types of data your organization handles and the situation in which the data tracking is employed. Organizations can help to solve these three commonly faced security challenges by tracking their data.
Secure Data Sharing Gives Organizations Better Visibility Over Employee Activity
One of the most fundamental components of secure data sharing is data tracking, and a common issue organizations frequently face when they don’t track their data is a general lack of visibility. Data tracking allows organizations to keep their sensitive data protected by knowing where it’s located, how it’s being handled, who can access it, and who those people are sharing it with.
Without proper data visibility, it can become quite difficult to monitor how well (or how poorly) your organization’s employees are following the company’s corporate data security policies, thus making those policies more difficult to consistently enforce. If one or several of your employees are actively practicing bad security hygiene, without data tracking, your organization’s security team may fail to identify those bad practices until a data breach occurs. In this way, data tracking can be seen as a preventative measure with its objective being to prevent a breach before one ever occurs.
Secure Data Sharing Allows Better Data Policy Oversight Across Organizations
While it’s one thing to ensure proper visibility over your own employees, ensuring the same level of visibility once sensitive data leaves your organization is a challenge of its own. Oftentimes, IT and security executives will find that they’re able to maintain healthy data security practices within the bounds of their organization, but when their data leaves the organization, proper control over its access and handling is lost.
Organizations are sharing more information than ever before and, as time goes on, it’s safe to assume more organizations will aim to establish more collaborative data ecosystems. According to TechRadar, such organizations that choose to embrace these ecosystems have the potential to save up to 9% of their annual revenue over the next several years. More collaborative environments make organizations more productive, create savings, and add revenue.
With more data sharing, however, comes more security risk. Thankfully, some of that risk can be alleviated by practicing secure data sharing. While corporate data security policy compliance can sometimes be encouraged, monitored, and enforced within your organization with methods besides data tracking like continued education and training, once the data leaves the organization, it becomes far more difficult to know whether or not it is being handled according to your corporate standards. No matter who may hold your data in their hands, employing solutions that make use of secure data sharing practices like data tracking, access privilege control, multi-factor authentication, and end-to-end encryption will give you and your organization more power over your data anywhere and anytime.
Secure Data Sharing Can Prevent a Breach Before One Ever Occurs
Even after employing a solution that tracks your organization’s data to ensure your employees and partners are handling it with care, accidents can still happen. The reality of collaboration is that, beginning the moment your sensitive data leaves the organization, it becomes more susceptible to a breach.
While data tracking on its own may not be enough to stop a breach from happening, organizations can take advantage of it to better understand where, why, and how a breach occurred. Gaining such information can be instrumental in preventing more breaches from occurring in the future, particularly if the original breach was caused by human error.
Gaining information from a breach can help you to know where your data security strategy may have gone wrong, but the goal of expanding on data tracking by implementing more comprehensive data sharing solutions should be to prevent a costly data breach before one ever occurs. At HelpSystems, we firmly believe our secure data sharing solutions can do just that.
Secure Your Data Wherever It’s Shared with HelpSystems Data Security Solutions
Take your data sharing capabilities to the next level with by pairing our GoAnywhere managed file transfer (MFT) solution with the power of Vera’s Digital Rights Management (DRM) to ensure your organization’s sensitive data remains secure wherever it goes. By pairing these solutions together, you can feel safe in the knowledge that your data’s security is not bound by the confines of your organization and, no matter where it is, you will have the highest level of visibility, security, and control at all times. For more information on this integration, read our datasheet.
Source: HelpSystems
[vc_row][vc_column][vc_custom_heading heading_semantic=”h1″ text_size=”h1″ text_weight=”300″ text_color=”color-210407″]Datto. What Is SaaS Protection (Software as a Service)? (Part 2)[/vc_custom_heading][vc_column_text]
Why the SaaS business model is a good fit for managed service providers
Leveraging SaaS services for your clients is a great way to scale your service offerings. Software as a Service solutions are normally delivered by a license subscription model which fits perfectly with the MSP service model. The overall objective is to be able to quote your clients on a per user/per month basis.
SaaS tools present different risks to your clients’ data than traditional software. As a result, you can enhance your service offering further with rsecurity add-ons.
How to ensure SaaS security with a multi-layered security approach
As an MSP you can deliver security as a service as an add-on for SaaS products to ensure that your users are protected.
Shared data responsibility & SaaS backup
Most SaaS providers design their SaaS infrastructure with built-in redundancy and other high availability measures to ensure that they won’t lose your cloud data.
However, if you have deleted data or fallen victim to a cyberattack, the responsibility to restore that data may fall on your shoulders. Microsoft calls this the Shared Responsibility Model. As an MSP your credibility is on the line to be sure that you’re protecting your clients’ data no matter who is responsible for a data loss. In your clients’ eyes you are solely responsible for protecting their data.
This is why Datto developed SaaS Protection, so you can take full control of protecting data stored within Microsoft 365 and Google Workspace.
Learn more about how Datto SaaS protection is your first line of defense against cloud data loss.
Login controls/authentication
One of the major benefits of SaaS apps is that your data is available anywhere. However, this can also make your data vulnerable to social engineering attacks which attempt to gain your login credentials.
There are a few ways to mitigate this threat. One method is to train end users and your own employees about what to look for in social engineering attacks, such as phishing emails. Another is to activate 2FA, or Two Factor Authentication, login on all SaaS applications — more and more businesses are making this login authentication a requirement for access as attack vectors grow and risks to data increase.
Be cautious of SaaS integrations
On the surface, data integration and streamlining the flow of data across business applications seem like obvious steps. However, as you improve data flow you may also be easing access for hackers or increasing possible vulnerabilities from cyberattacks.
It’s essential to always test and verify every application that you integrate to ensure that you’re not increasing exposure to threats.
Advanced Threat Protection for SaaS platforms
Another great way to protect users is with an advanced threat protection (ATP) solution such as Datto SaaS Defense. ATP solutions are designed to stop attacks/malicious emails before users even have a chance to interact with them.
Protecting SaaS data with Datto SaaS Protection and SaaS Defense
With Datto SaaS Defense, MSPs can proactively defend against malware, business email compromise (BEC), and phishing attacks that target Microsoft Exchange, OneDrive, SharePoint, and Teams. With Datto SaaS Protection working alongside SaaS Defense, you are able to backup, protect and recover SaaS data whenever necessary.
Source: Datto[/vc_column_text][/vc_column][/vc_row]
Times are changing—employees are working from home, using more devices, and moving more data around than ever before. Organizations are recognizing that helping their employees to work and collaborate faster and more efficiently is key to surviving in an ever-changing and increasingly competitive market. While for some organizations, this may simply mean adding a new application to their ecosystem to streamline workflows, for others, it means undergoing a complete digital transformation. But what does this mean and how can organizations begin their digital transformation today?
What is Digital Transformation?
According to Gartner, digital transformation—or more specifically digital business transformation—is the process of exploiting digital technologies and supporting capabilities to create a robust, new digital business model. The common objectives of digital transformation are to accommodate a growing and/or changing workforce, improve scalability to increase the speed and efficiency of employees’ work and collaborative efforts, streamline workflows, meet ever-growing customer and market demands, and ultimately, to grow profits.
For small and large organizations alike, digital transformation is increasingly becoming much less of an “if” question and much more of a “when” question. They’re finding that by shifting to modern business models via new technologies and capabilities, their employees, customers, and future business outlooks all benefit in a big way. Consequently, organizations are often motivated to initiate and follow through with a digital transformation as quickly as possible. The ongoing COVID-19 pandemic, which has undeniably shifted how (and where) businesses and their employees operate, has only intensified this motivation.
Unfortunately for many organizations, though, they’ve quickly found there is no one-size-fits-all solution for digital transformation; and, oftentimes, digital transformation can look far different for your organization compared to that of your closest competitors. In a 2020 study that surveyed 895 companies that had undergone digital transformation, Boston Consulting Group found that a staggering 70% of organizations did not reach their target with their efforts, including 26% of total respondents that failed to deliver outright and produced “no sustainable change.” In contrast, only 30% of surveyed organizations achieved or exceeded their digital transformation goals, resulting in sustainable change.
This begs the question: “why does digital transformation fail so frequently, and how can I prevent this within my organization?” To answer this question, however, one must first understand how organizations are now commonly accelerating their digital transformation through cloud technologies.
Why Are Organizations Turning to the Cloud for Their Digital Transformation?
More and more, organizations are integrating cloud solutions into their daily operations and future business plans. The cloud infrastructure market is growing so quickly, in fact, that it made approximately $49 billion more in 2021 compared to the year before, according to Synergy Research Group. By adopting a cloud ecosystem, these organizations are making workplace collaboration faster and more efficient, streamlining workflows, and eliminating the need to purchase hardware and software. Furthermore, the cloud is flexible and scalable enough to evolve with your organization while simultaneously cutting maintenance costs for your IT department, giving them more financial space to work on innovation instead.
Particularly in the wake of the COVID-19 pandemic, and the resulting spike in remote work, the benefits of implementing cloud technologies within your organization are only becoming more apparent. Whether your organization plans to use public cloud services, a private cloud, or a hybrid cloud to consolidate the advantages of both, the flexibility and growth potential a cloud ecosystem can provide for your organization should make its implementation a relatively easy decision. With that in mind, though, rushing to make your organization’s cloud open and collaborative too quickly can lead to more problems than solutions.
Establishing Cloud Security Will Help Your Digital Transformation Succeed
While switching to cloud computing can undoubtedly be a big step in the right direction in your organization’s digital transformation efforts, one thing should be understood: cloud adoption is not always successful, and inadequate security is often the culprit behind its failure. The 2021 Thales Global Cloud Security Study found that approximately 40% of organizations experienced a cloud-based data breach this past year and a whopping 83% of organizations failed to encrypt at least half of their data being stored in the cloud.
Cloud adoption can certainly also cut costs for organizations when used safely and appropriately, but data breaches can become a big contributor to some of the hidden costs of cloud computing. Not only can these breaches lead to the loss of customers and revenue, but they can also lead to hefty fines as a result of data compliance violations, and potentially even larger settlement costs that will go toward those affected by the breaches.
What often fools organizations into thinking about cloud security as an afterthought is that many of the main public cloud providers, like AWS, Microsoft Azure, Google Cloud, and Elasticsearch, already have pre-existing security embedded in their cloud’s infrastructure. Because every organization uses its cloud resources differently, though, misconfigurations by the customer rather than the provider are often the cause of data breaches. Depending on which cloud model a given organization uses, a single breach can cost them an average of anywhere from $3.61 million to $4.8 million, according to the 2021 IBM Cost of a Data Breach Report.
Thankfully for these organizations, just as cloud services can be outsourced, the same can be said for cloud security. They can begin to simplify and feel more confident in their cloud security by using automated tools to keep security settings in check and take human error out of the equation. Having adequate visibility into your organization’s cloud ecosystem from the ground up is just as important. Establishing a comprehensive corporate data security policy and then implementing layered data security solutions that follow those policies can serve to heighten your visibility while reducing the burden on your internal security teams.
Take Your Cloud Security to the Next Level with HelpSystems Data Security Solutions
Regardless of whether your organization plans to implement a public, private, on-premise, or hybrid cloud model to advance its digital transformation, HelpSystems has several solutions available to help address your most critical cloud security concerns. Read our Data Security Use Cases Guide to see how we solve common problems, and when you’re ready, talk with one of our experts to begin building your cloud security strategy.
Source: HelpSystems
[vc_row][vc_column][vc_custom_heading heading_semantic=”h1″ text_size=”h1″ text_weight=”300″ text_color=”color-210407″]Datto. What Is SaaS Defense (Software as a Service)? (Part 1)[/vc_custom_heading][vc_column_text]SaaS stands for “Software as a Service” and is a cloud-based IT service. It is an on-demand software that can be accessed by the user via an internet connection. Saas is one of the most popular ways to provide business software to consumers thanks to its many benefits, including scalability, low cost, and ease-of-use.
As businesses have shifted from office-based to remote work, leveraging SaaS platforms has been key to keeping businesses running. However, with this increase in remote workers comes an increase in security risks due to the lack of secure infrastructure of a corporate office. To help managed service providers (MSPs) protect remote workers from potential cloud data loss, we have compiled this useful guide.
Read on for a deep dive into SaaS and how you can protect yourself from potential security threats.
SaaS vs traditional software
SaaS is a software distribution model where the software and its data are centrally hosted. This model offers benefits to customers by providing a more stable environment and making it easier for them to maintain their software.
Traditional software is typically installed on a customer’s own computers and managed by that customer. It provides more control over the environment, but it also means that the customer has to install updates, manage backups, and install new hardware if necessary.
Common examples of SaaS companies
There are thousands of SaaS software vendors to choose from, but the more popular ones include:
- Google Workspace
- Microsoft 365
- Salesforce
- Dropbox
- Slack
- Hubspot
These companies are leading examples within the SaaS industry and have come to define the framework of successful Software as a Service companies. However, it’s always worth investigating who has liability for what when it comes to choosing a SaaS Vendor. We put together a few top tips from Managed Service Providers on what to look for.
Types of SaaS solutions
- Accounting Software
- Billing and Invoicing Software
- Collaboration
- Customer Relationship Management (CRM) Software
- Email Marketing Software
- Enterprise Resource Planning (ERP) Software
- HR
- Marketing Automation
- Project Management Software
- And more
SaaS tools are primarily involved in key business functions and often contain sensitive data. As a result, they are also prime targets for cyber attacks and hackers.
Discover how to protect your business data with Datto SaaS Protection.
What to look for in a business SaaS solution
When it comes to looking for the right SaaS technology to protect your clients’ data it’s essential to make sure it fits your purpose. Here are five key elements to look out for:
1. Liability
Know who is liable for what SaaS providers ensure they won’t lose your customers’ cloud data with built-in redundancy and other high availability measures. However, they do not take responsibility for restoring data if your customers were to lose it. Microsoft calls this the Shared Responsibility Model for data protection.
2. Comprehensive protection
Some SaaS backup solutions only protect email, files, and folders. However, there are solutions available today that offer more comprehensive coverage. When selecting a backup product, look for solutions that offer protection for things like contacts, shared drives, collaboration and chat tools, and calendars. SaaS protection solutions that offer this type of coverage are far more effective at maintaining business continuity than less robust offerings.
Learn more about comprehensive SaaS Protection
3. RPO/RTO
Recovery point objective (RPO) and recovery time objective (RTO) are also critical considerations. These metrics refer to the point in time you can restore to and how fast you can perform a restore, respectively. When it comes to backup these are largely dictated by the frequency of backups and what specifically is being protected.
Solutions that offer frequent backups address RPO since they enable you to restore to a recent point in time, minimizing data loss. As noted above, these make restores faster and easier by reducing the amount of manual effort to perform restores. Plus, they enable users to access data in the event of an outage.
4. Security/Compliance
Many MSPs serve clients in verticals with significant security and compliance requirements. So, choosing a SaaS protection solution that can address these needs is essential. Look for products that back up data in compliance with Service Organization Control (SOC 1/ SSAE 16 and SOC 2 Type II) reporting standards that can meet clients’ HIPAA and GDPR compliance needs.
Solutions that enable automated retention management to meet compliance standards can reduce the need for manual intervention. This streamlines management and ensures that client data is stored for the right length of time.
5. MSP business growth
No discussion of product evaluation for MSPs is complete without considering profitability. Look for products that have the features and functionality you need at a price point that allows you to build margins on your services. Consider products that offer pricing benefits for MSPs such as sales-based discounting and flexible “pay for what you use” licensing.
As noted above, products that increase efficiency can also grow margin and increase revenue, since they require less manual intervention. You may also want to bundle SaaS protection on top of SaaS services that you already deliver — this has proven effective for some MSPs. This isn’t necessarily part of the product evaluation process, but it’s worth noting when discussing business growth.
To get more top tips on what to look for in a business SaaS protection solution, download our ebook.
https://www.youtube.com/watch?v=ZR1PJiSbzCg[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][/vc_column][/vc_row]
There is a maxim in the business continuity market that says that a backup on its own is worthless, but restoring a backup successfully is priceless. Too many organizations have suffered from backups that either failed to restore—or restore correctly—or that were already compromised. Failed backups are of no value from a business continuity perspective.
However, backups that restore correctly, are clean of all malware, and were encrypted so that the IT security teams knows that they were not compromised after the backup was created, are considered the best scenario for IT managers.
According to Sophos’ The State of Ransomware 2021 report, 37% of respondents said they were hit by ransomware and on average. While 96% said they got back their data after paying the ransom, only 65% of the encrypted data that was affected was restored. These statistics underscore how essential it is to not only have secure backups, but also protected backups stored in more than one physical location that are directly connected to the network.
Types of backups
There are five types of backups:
- Full File-based backup: A full backup is the simplest form of backup, which contains all the folders and files that you selected to be backed up. This is called a file-based backup because it only backs up visible files, not hidden or system files that are often hidden.
- Incremental Backup: This backup only includes files that were not backed up the last time. When restoring backups made from incremental backups, you must restore each incremental backup in order that it was created, starting with the full backup.
- Differential Backup: Differential backups only include data that was added or changed since the most recent full backup. When restoring using this method, you need only restore the initial full backup and the most recent incremental backup.
- Image Backups: An image backup includes everything on the disk, including any hidden or system files. You can use incremental or differential images to supplement your full image backup.
- Copy Jobs: This includes individual files or folders copied from one location to another.
Recommendations on effective backup restores
Since restoring the backup really is the ultimate goal, it is important to focus on what makes for successful backup-and-restore policies and procedures. Here are some recommendations that you might find helpful.
- Scan and validate: Scanning a drive for malware and other potential compromises prior to backing it up helps to reduce the possibility of restoring a problem should the drive in question become compromised. Once a backup is created, that backup immediately should be rescanned to validate the backup was successful and can be restored. This significantly reduces the future potential of having an invalid or corrupted backup. This should be done with master backups (full file backup or image backup) and any incremental or differential backups.
- Multiple copies: It is a best practice to have multiple copies of each backup — one easily accessible and one off-site in the cloud. For highly sensitive data or mission-critical intellectual property, you might consider a physical copy stored in a vault. Multiple copies provide additional security should your primary backup site become damaged or compromised. If you store physical copies offsite, make sure each physical disk is clearly identified with a date of creation and description of what is on the disk.
- Encrypted backups: A best practice is to encrypt all backups.
- Write-protected backups: Some security professionals use an application that not only encrypts the data, but also locks the backup so it cannot be decrypted, mounted and then modified. While some IT security pros prefer to be able to rescan a backup periodically or install security patches into a backup, others prefer to keep backups pristine and apply patches only if the backup needs to be restored.
- Test your backups: Even if you are not required to restore a backup due to a failure, it is a good practice to periodically restore a backup to a test machine. This practice enables the security team to test restoration policies and procedures periodically. Should software change or new staffers added, such tabletop exercises help ensure expertise of the staff.
Best backup schedules
One of the more popular backup strategies is called the Grandfather Father Son Backup. This consists of a “grandfather” backup that is done once a month, the “father” component being a full backup once a week, and the “son” backup being a daily incremental. There are variations of this approach with the father backup being a weekly differential backup. It also could include a variety of backups during the day, such as an hourly catch-up or a backup at any time after specific criteria is met, such as prior to a software installation or a reconfiguration of the network, or after a malware scan.
As part of this backup strategy, the security staff might choose to do one backup at one time for a local site or cloud instance and a second time for the opposite local or cloud instance. The overhead will depend on various factors, including the backup software you select, whether you are backing up to the cloud or locally, the amount of data being backed up, and metrics that might be unique to your situation.
Learn more
Sophos offers two products that help protect your backups. Sophos Workload Protection secures backups in the cloud and on the premises. Sophos Cloud Optix monitors Amazon Web Services (AWS), Microsoft Azure and Google Cloud Platform (GCP) accounts for cloud storage services without backup schedules enabled and provides guided remediation.
Source: Sophos
3 Data Centric Security Strategies for 2022
Despite massive growth in data security spending, the number of data breaches is increasing. With constant changes in how and where work is done—thanks in part to growth in both cloud computing and mobile device usage—the threats are changing, too. And so are the strategies taken to mitigate those threats.
It’s time to consider whether the safeguards and plans your organization has in place are enough.
Today’s Cybersecurity Threats and Responses
Today’s biggest threats rely on gaps in your data security and knowledge. For example, phishing, an established threat that’s only been growing, hinges on the hope that people don’t know how to successfully identify a fraudulent email. On the other hand, ransomware lays in wait for access to sensitive systems and data that aren’t adequately protected.
To stay ahead of these attacks, organizations must stay committed to engaging and educating employees on the growing ingenuity of hackers, as well as identifying security gaps in their systems and processes and discovering new safeguards they can implement.
“2022 is the year that the C suite recognizes that they are getting further and further behind on their security projects.” – Tom Huntington, Executive Vice President of Technical Solutions at HelpSystems
For your organization, responding to today’s hazards could be as easy as implementing multi-factor authentication for your internal systems, or as involved as a total top-down rebuilding of your data security strategy. Whichever the case, take a step back, identify your vulnerabilities, and start making plans to update your data security strategy for the upcoming year.
What is a Defense in Depth Strategy?
Defense in depth (DiD) is a security approach that employs multiple safeguards to protect against cybersecurity threats and breaches. While the defense in depth strategy is based on similar military strategies that rely on multiple layers of security to slow down an attack, it strengthens the approach by attempting to thwart the attack entirely. “The motto, ‘prevent first, detect always,’ must be adopted as a core preset for secure security operations programs. Remember, the goal of security is not to stop a hack. The goal is to prevent, detect, and respond to a threat actor before they successfully achieve their goal,” says Joe Vest, Tech Director for Cobalt Strike by HelpSystems.
“The motto, ‘prevent first, detect always,’ must be adopted as a core preset for secure security operations programs.”– Joe Vest, Tech Director — Cobalt Strike by HelpSystemsIt’s important to be both on the offensive and the defensive, which can be achieved via methods to test for cracks, prevent access, and, in the worst-case scenario, detect it. IBM notes that “organizations struggle with slow detection and response times, while threat actors are rapidly gaining speed and moving to the cloud.” This is where a defense in depth strategy can help: with multiple stopgaps in place, it’s easier to impede an attack and identify it before any data is lost.
A defense in depth strategy can be broken down into three distinct areas:
- Physical: Think of your favorite heist film: what physical barriers is between your data and the outside world? These can include walls, retina scanners, locks, security cameras, or—if it’s Hollywood—laser beams would-be robbers can limbo through.
- Technical: Any hardware or software that’s in place to prevent and monitor access to your data centers or data itself. Returning to the Hollywood example, if you can imagine a hacker pressing random keys to break into a system, that’s the technical barrier.
- Administrative: The procedure side of the defense strategy. This is the security policy that your CISO spent months planning out, onboarding and offboarding access rules, data handling and sharing policies, and anything else that may inform what physical and technical barriers you need to put in place.
The redundancies within the defense in depth strategy provide a more robust barricade to potential hackers and, thanks to multiple layers addressing the same weaknesses, covers gaps that might otherwise be missed.
What is a Data Centric Security Strategy?
A data centric security strategy is a plan to focus on protecting an organization’s data. This includes any technology, processes, and policies that govern how data is collected, used, and stored throughout the data’s lifecycle. Rather than the traditional infrastructure-focused approach, which leans more heavily on protecting on-premise and cloud-based hardware and software from everything from cyber threats to physical breaches to natural disasters, a data centric approach takes a closer interest in the data contained in those environments.
Alongside the many data compliance requirements rolled out in recent years, consumer opinion has also been changing. Today, 63 percent of consumers rank an organization’s data collection and storage practice as the most important element to consider when sharing sensitive information.
Industry research and best practices indicate that there are four key gaps in data security architecture that puts your data at risk. These are:
- Behavior: Will people follow processes properly, or will they take shortcuts that could put your data at risk?
- Visibility: Do you understand the data that you are sending and storing, and are only the appropriate people accessing it? Can you see who accesses it?
- Control: Can you limit who accesses data, or what data is shared and sent?
- Response Time: Does your organization as a whole—from your employees, to your procedures, to your infrastructure—have the flexibility to implement and understand changes in technology or processes?
Data centric security solutions offer businesses the ability to guarantee file-level security—to secure, track, and share any kind of data, no matter where it’s stored or located, or how it travels with robust policy enforcement, strong encryption, and strict access controls.
What is a Data and Risk Management Strategy?
One of the broader security strategies, data and risk management covers a wide range of steps organizations follow to protect data. You can start moving towards a data risk management strategy by doing the following:
- Assess your risk factors: What gaps do you currently have? What would a breach mean for you?
- Plan for attack: What will you do if an attack occurs? Do you have a mitigation and response plan in place?
- Educate your employees: Can your employees, especially the C-Suite, who tend to be the most targeted, identify a phishing attempt? Do they know the best practices for file sharing or network access?
- Understand your data: What data do you have on hand, who has access, and when do you get rid of it?
- Use a data security solution: Do you have software solutions in place, and do they give you the visibility you need to be proactive?
Among the barriers to successfully safeguarding data is discovering where sensitive data resides within an organization, according to The 2021 Global Encryption Trends Study, a survey conducted by the Ponemon Institute. Understanding what data you have on hand and where it’s stored is an essential step in any data-focused security strategy—you don’t want to have inconsequential information under lock and key, but sensitive, business-critical data out in the open.
More organizations are starting to use data classification systems to properly classify data’s sensitivity and create access controls. And, to keep that data internal, data loss prevention and content inspection solutions are often layered for added security.
How MFT Fits into Your Data Security Strategy
Managed file transfer (MFT) is a key player for protecting your data. MFT software solutions are centralized secure file transfer tools that solve key data transfer issues. These include human error during manual transfers, improved security with industry-standard encryption, and auditing, tracking, and auto-resume for failed transfers, so you know where your data is, who has access to it, and whether or not it’s arrived as expected.
Source: HelpSystems