News
It’s not news that cybercrime is a constant battle—large enterprises and small businesses everywhere are susceptible to a myriad of advanced email threats and socially engineered attacks, such as executive or brand impersonation. According to IC3’s Internet Crime Report, over $44 million in losses in 2021 were a direct result of malicious phishing and advanced email scams.
Despite billions having been invested into perimeter and endpoint security since the onset of the pandemic and the birth of remote or hybrid work environments, phishing and business email compromise (BEC) scams have become primary attack vectors into organizations, often giving threat actors the toehold they need to wreak havoc on companies and their customers. Additionally, there are infinite savvy social engineering ploys that easily evade most of the email defenses in use today.
How Do Phishing Schemes Happen?
Interestingly, these incredibly complex scams can be deployed with fairly simple methods. Threat actors have become highly skilled at impersonating brands or domains or spoofing individual emails to steal account holder credentials. How does this occur? Unfortunately, both employees and customers are often too trusting of emails that make it to their inboxes. These scams often impersonate people of authority and target employees who have access to financial information and present a time-sensitive scenario, such as needing an “urgent wire transfer” to pay an invoice for a supposed vendor. The bank account for that vendor is, of course, one controlled by the cybercriminals. With this method, BEC actors trick unsuspecting employees out of millions of dollars each year.
To compound the problem, bad actors have evolved their strategies and discovered that targeting anyone along the org chart—even interns—can result in a breach when they ask for (or offer) something as simple as a free iTunes gift card. These same threat actors realized that they could compromise employee inboxes, providing an avenue to sift through emails to identify additional opportunities for fraud. In tandem, threat actors can set up and send multiple phish from the central attack infrastructure—whether they are fake sending domains or IPs.
Prevention & Mitigation through Customer Phishing Protection
Being able to detect a phishing scheme early in its lifecycle is the first step in reducing risk. This is why HelpSystems provides a comprehensive customer phishing protection offering from Agari and PhishLabs: to prevent, detect, and disrupt phishing attacks. As phishing campaigns and infrastructure multiply, many organizations find themselves in need of more proactive and robust protection that can deliver the email authentication, risk protection, threat intelligence, and mitigation capabilities necessary to successfully fend off attacks.
Agari analyzes two trillion emails per year claiming to be from domains across the world’s largest cloud email providers. By combining Agari’s tools with third-party sender knowledge, your organization’s legitimate email can be authenticated, and unauthorized messages blocked from reaching customers. This is accomplished through Agari Brand Protection, which stops phishing by automating the process of DMARC email authentication and enforcement to protect customers from cyberattacks.
How? During a phishing scam, DMARC failures identify a threat or suspicious message once it launches and the intel included in that specific failure report is automatically fed by Agari to PhishLabs without the need for intervention from a SOC team member. And once a threat is identified, mitigation is immediately pursued without requiring any client intervention, reducing the amount of time needed to address threats and shut them down.
This direct integration between Agari and PhishLabs expedites the phishing detection process exponentially. It can also disrupt more phish by taking down the campaign attack-sending infrastructure. In some instances, Agari reports will provide additional intelligence on the sending infrastructure, and PhishLabs will pick this up and identify the infrastructure details, gather malicious evidence, and then pursue takedown. And once the central infrastructure is down, it substantially disrupts a threat actor’s ability to stage additional phishing campaigns.
Detection through Digital Risk Protection
PhishLabs’ Digital Risk Protection automatically integrates the intelligence collected from Agari Brand Protection into an extensive collection apparatus that consumes a broad range of sources, including:
- Spam feeds
- Domain registrations
- SSL transparency logs
- Passive DNS monitoring
- Active DNS queries
- DMARC failure reports
PhishLabs continuously mines this intelligence to proactively detect phishing campaigns early in the attack cycle. By integrating Agari’s collected intelligence, PhishLabs can identify threats and take immediate action to disrupt them using automated kill switches and preferred escalation integrations. PhishLabs also uses Agari’s artificial intelligence capabilities to pursue the mitigation of underlying campaign infrastructure to further disrupt phishing attempts, leading to the deterrence of future attacks.
By combining best-of-breed services, HelpSystems’ Customer Phishing Protection bundle from Agari and PhishLabs significantly reduces the complexities associated with stopping phishing campaigns and helps enterprises achieve end-to-end phishing protection through a trusted partnership and seamless integration.
For a personalized demo of HelpSystems’ Customer Phishing Protection bundle, click here.
Source: HelpSystems
Once upon a time, it was often necessary to define the term “ransomware” as it was frequently met with questioning looks and the need for clarification. Nowadays, you can hardly go a day without hearing about some sort of attack. What has made ransomware such a pervasive threat, and how can organizations learn to better protect themselves? In this blog, we’ll discuss why so many are worried about ransomware and how Core Impact’s latest ransomware simulation feature makes this pen testing tool more effective than ever at reducing your risk.
The Concern Over Ransomware
According to the 2022 Penetration Testing Report, ransomware is one of the top concerns for cybersecurity professionals. Unfortunately, the ever-constant anxiety over ransomware is well justified. A report by PhishLabs shows there is a consistently rapid increase in ransomware, with a growth rate of well over 100% year over year. The cost of ransomware attacks is also on the rise and has even put some organizations out of business. The average ransom demand alone was $220,298 in 2021. The recovery cost is much steeper, and averages at $1.8 million.
Ransomware has perhaps become so prevalent due to ease of use. Not only can you purchase ransomware kits off the dark web, you can also hire the work out, using Ransomware-as-a-Service (RAAS) providers. Additionally, the most popular ransomware vectors are built into every organization and impossible to close—according to the 2021 Malware Report, 70% of ransomware breaches had entered the surveyed organizations using phishing emails.
However, despite these challenges, organizations are not helpless against ransomware threats. Just like so many things in life, the key to improving your defenses comes down to regular practice.
Ransomware Simulation with Core Impact
Users of Core Impact can now efficiently simulate a ransomware attack using an automated Rapid Pen Test (RPT). Given ransomware’s close association with phishing campaigns, the simulator can easily be paired with a phishing campaign RPT for deployment. From there, security teams are then able to mimic the behavior of multiple ransomware families, encrypting user-specified files using a fully reversible symmetric key. They can also exfiltrate files to establish which mission critical data is most at risk after the initial breach is complete.
Additionally, if enabled, the ransomware simulator offers an automatic rollback after a set amount of time, leaving the environment as it was before the attack. If files remain encrypted, this gives defensive utilities a chance for detection and subsequent triggering of corrective actions.
Finally, Core Impact’s ransomware simulator enables the definitive move of most ransomware strains: the ransom note. Security teams can create and leave an explanatory README file once the exercise has been completed. This file will inform a user that they have experienced a ransomware scenario and can prompt them to contact the security team or provide other next steps, such as further training on ransomware and how it can get into your system.
You can see Core Impact’s ransomware simulation in action in the overview video below:
Source: Core Security
Congratulations! You’ve just completed a penetration test. So what now?
A pen test shouldn’t represent the pinnacle of your security efforts. Rather, the test validates what your organization is doing right and highlights areas for improvement.
Even if the test showed that it was possible to gain administrative access and move laterally through your network, this doesn’t mean you have “failed.” Rather, the purpose of a pen test is to find vulnerabilities so your organization can fix them before they are exploited and to advance the security of the network.
Take these four steps to maximize the effectiveness of pen testing:
- Review and discuss the results
- Develop a remediation plan
- Validate implementation
- Focus on continuous improvement
Review and Discuss the Results
The retrospective process after a pen test varies depending on several factors: the company’s needs, who completed the pen test, and the quality of the report.
A report should include these elements:
Summary of successful scenarios: An executive summary will list the steps that were performed, which ones were successful from an attacker point of view, and which ones failed.
List of information gathered: A comprehensive report will include any information that could be a security weakness, including hosts, applications, identities, email addresses, credentials, and misconfigurations.
List and description of vulnerabilities: Also look for a prioritized list of the found vulnerabilities with the common vulnerabilities and exposures (CVE) score and exploit potential. Ranking vulnerabilities by potential severity will help with the development of a remediation roadmap. By pairing with a vulnerability management solution, you can refine prioritization even further with additional analysis and relevant risk context.
Detailed description of procedures: A description and audit trail of all performed activities and their results will allow your security staff to retest for specific vulnerabilities after a patch has been applied or remediation performed.
Additionally, it’s critical that the C-suite knows what IT is doing to protect network infrastructure. An executive report outlining the high-level findings and remediation steps provides useful education and can help make the business case for necessary resources to move forward.
Develop a Remediation Plan
Although it may seem counterintuitive, resist the urge to start making changes immediately. Developing a remediation plan is an essential first step, as it allows you time to prioritize planned fixes and research any mitigation strategies you may not fully understand. Many pen test reports include a rating on how severe the finding is based on potential impact and likelihood of exploitation, which will help you establish priorities.
Every finding should have a plan with a priority and, if possible, be assigned to someone to remediate — with a due date. Those plans should be loaded into your security ticketing system so that you can track progress and completion of each task.
You want to avoid having the same critical vulnerabilities on multiple tests. If you aren’t keeping up with pen test findings and remediating them as soon as practical, you’re compromising your company’s cybersecurity posture.
Validate the Implementation
Once the findings from the pen test have been remediated, it’s time to validate that the changes actually solved the issue. You can rerun the scenario that uncovered the vulnerability to ensure the fix is sufficient. Additionally, performing regular penetration tests can provide updated information on your security posture, particularly after changes have been made to your infrastructure. If you are using a vulnerability management solution that provides risk-based scoring, you can rerun your scans to assess whether your scores have improved.
Before running subsequent pen tests, however, it’s helpful to review the scope and findings of previous pen tests. The scope of each pen test can vary widely, with some looking more broadly at the IT infrastructure and others focusing on particular problem areas. By taking into account whether additional or different tests should be completed, you can ensure that you’re getting the most valuable insights possible.
Focus on Continuous Improvement
Cybersecurity is a journey — not a destination. Your next pen test will likely uncover new vulnerabilities that require different types of remediation. If your pen testers return no findings, you should question the competence the efficacy of the test.
You also must recognize that some vulnerabilities will require larger-scale changes. If a vulnerability requires multi-factor authentication (MFA), for example, that’s a large project that will require capital spend and time to implement. Likewise, if your company is prone to phishing attacks, it will take time to implement a phishing solution to reduce your business risk.
While a passing grade on a pen test may help prove compliance to external auditors, pen tests provide even more value as agnostic assessments of your organization’s security posture.
A security team’s work is never done, so the focus should be on continuous improvement as you prepare for the next penetration test.
Source: Core Security by HelpSystems
Protect all your servers, from on-prem to multi-cloud, Windows to Linux, all fully integrated within Sophos Central.
As customers transition server workloads from on-prem to cloud hosts, containers, or serverless environments, they need their environments to be tough, hard to compromise, and quick to recover.
To achieve that, they need a single integrated security platform that unifies their cloud security and provides visibility of their complete estate.
With the shared security model (AWS, Azure), customers are responsible for securing their instances, applications, and data.
Sophos helps customers achieve this by providing a unified cloud security platform based on four key pillars:
- Secure access – Protect credentials and securely access services
- Protect workloads – Detect, query, and secure hybrid cloud workloads
- Secure the network – Cloud network security and automated threat response
- Integrate with DevOps – Enable customers to embed security into development processes
Introducing Sophos Cloud Native Security
Sophos Cloud Native Security addresses the requirements of protecting workloads, providing comprehensive security coverage across environments, workloads, and identities. It gives customers comprehensive, centralized visibility, prioritized detections, and faster incident response time.
The Sophos Cloud Native Security bundle is a single SKU that includes Sophos Intercept X Advanced for Server with XDR and Sophos Cloud Optix Advanced to provide:
- Visibility, governance, entitlements management, and compliance across single and multi-cloud environments, including Amazon Web Services, Microsoft Azure, and Google Cloud Platform, as well as traditional on-prem monitoring.
- Protection and detection for infrastructure and data today and as it evolves in the future, with flexible host and container workload security for Windows and Linux
- Increased agility and collaboration across the organization, with cloud environment security posture alerts integrated with popular SIEM, collaboration, workflow, and DevOps tools.
A customer’s security team can manage Cloud Native Security, or they can have it managed by the Sophos Managed Threat Response service to fast-track their cyber resilience in order to best meet the security incidents of today.
Cloud Native Security and the new Cloud Native Firewall solution, which will be in preview (EAP) soon, are integrated with the Sophos XDR platform. The Cloud Native Firewall will support IPS, WAF rules, micro-segmentation, and Admission Control and be deployable from native Kubernetes, AWS EKS, and Azure AKS.
Cloud Native Security is available today. Learn more at Sophos.com/Cloud.
Source: Sophos
Trust is a dangerous word in IT, especially when that trust is granted without much consideration: when it’s implied, or when it’s never questioned.
Creating a sealed-off perimeter where everything and everyone within the network is fully trusted has proven to be a flawed design. Yet, that’s how many networks are still implemented today.
Anyone with access to the network, either physically or via VPN, has broad access to everything on that network regardless of who they are, or what state their device is in.
There’s got to be a better way, right? Well, there is. It’s called zero trust… or trust nothing, verify everything… continuously.
With zero trust, nothing is implicitly trusted. Trust has to be earned – constantly. Zero trust is a very simple and elegant way of micro-segmenting the network so that only users who prove their identity and have compliant devices can access only very specific resources – and NOT the whole network. This has tremendous benefits for security.
Watch this short 3-minute video to learn more about why zero trust is so important:
Sophos ZTNA
Sophos ZTNA utilizes the principles of zero trust to provide workers with secure access to the networked applications, data, and systems they need to do their jobs… no matter where they’re located.
It’s just a better way of providing network access for remote workers, with greatly enhanced security, easier management, and a much more transparent end-user experience compared to old-school VPN.
And it’s the only ZTNA solution that’s tightly integrated with next-gen endpoint protection for a single-agent, single-console, single-vendor solution for all your remote workers’ protection and connectivity needs.
Check it out at Sophos.com/ZTNA
Source: Sophos
Sophos ZTNA has received Frost & Sullivan’s prestigious Global New Product Innovation Award in the zero trust network access industry. Frost & Sullivan applies a rigorous analytical process to evaluate multiple vendors for each award category before determining the final award recipient.
We are very honored that Sophos ZTNA was awarded this distinction based on alignment with needs, value, and customer experience.

Frost & Sullivan praised our focus on listening to market needs, keeping what is often considered an intimidating new technology simple to understand and easy to adopt. They also praised us for addressing the top complaints about existing solutions on the market.
They noted that we are uniquely positioned to provide a compelling integrated ZTNA and next-gen endpoint solution, something other vendors are unable to offer.
They acknowledged the significant benefits this type of integrated solution enables, such as Synchronized Security to share device health, a single agent deployment, and a single management console, along with a very elegant and simple licensing scheme.
Frost & Sullivan concluded that Sophos ZTNA matches customer needs for simplification in every aspect, ranging from design to purchase and service experience by integrating our ZTNA solution into our broader ecosystem of cybersecurity products, all managed from a single cloud console – Sophos Central.
“Sophos has designed an innovative ZTNA solution… With its strong overall performance, Sophos earns Frost & Sullivan’s 2022 Global New Product Innovation Award in the zero trust network access industry”
Download the full Frost & Sullivan Award Report and check Sophos.com/ZTNA for more information.
Source: Sophos
Sophos Firewall OS v19 MR1 brings a number of additional enhancements and fixes to what is already one of our best firewall updates ever.
Sophos Firewall OS v19 was released just a few months ago, and has already been adopted by a huge number of partners and customers.
They’ve upgraded to take advantage of the many Xstream SD-WAN and VPN enhancements. This latest update, v19 MR1, brings a number of additional enhancements and fixes to what is already one of our best firewall updates ever.
VPN and SD-WAN enhancements
- SSLVPN remote access – static IP lease support to enable mapping of remote users with static IP addresses to improve user traceability, monitoring and visibility. This also includes static IP leases with an external Radius server.
- IPsec VPN enhancements – includes adding default IPsec site-to-site IKEv2 policies for improved head office to branch office tunnels, eliminating manual fine tuning for re-key interval, dead peer detection (DPD) action, and key negotiation. Defaults were also updated to prevent flapping of UDP connections (VoIP, Skype, RDP, Zoom, etc.). Also disabled “vpn conn-remove-tunnel-up” and enabled “vpn conn-remove-on-failover” for new configuration (but does not impact existing deployments).
- SD-RED – now supports multiple DHCP servers for RED interfaces
- SD-WAN Profiles – The Rule-ID and index column are added on the SD-WAN profile management page for easier troubleshooting
Other enhancements
- Anti-malware engine – anti-malware engines and associated components were upgraded to full 64-bit operation to provide optimal performance and future support. Note that the secondary malware scan engine, Avira, will no longer provide detection updates for the 32-bit version after December 31, 2022. Anyone using Avira will need to upgrade to v19 MR1 or v18.5 MR5 (to be released soon) before the end of the year or switch to just using the Sophos engine.
- Synchronized Security – improved Sophos Central Firewall Management resilience in environments with thousands of endpoint certificates being used for Synchronized Security Heartbeat.
- Email – added an option to report a spam email as a false positive from the quarantine release screen
- Sophos Assistant – added an option to opt-out of the Sophos Assistant
- Additional fixes – over 50+ additional performance, stability, and security fixes and enhancements are also included
See the release notes for full details.
Important licensing change for future firmware updates
As covered in this recent community blog post, SFOS v19 MR1 introduces a support requirement for firmware upgrades which will come into effect for customers without a valid support subscription after they’ve used an initial free upgrade allocation.
To summarize:
- No change for customers with a valid support subscription (about 80% of customers)
- Future action will be required by the remaining 20% who do not have a support subscription, but also no immediate change
How to get it
This release will follow our regular Firewall firmware release process and timeline.
Source: Sophos
Can you believe it? Cobalt Strike is 10 years old! Think back to the summer of 2012. The Olympics were taking place in London. CERN announced the discovery of a new particle. The Mars Rover, Curiosity, successfully landed on the red planet. And despite the numerous eschatological claims of the world ending by December, Raphael Mudge diligently worked to create and debut a solution unique to the cybersecurity market.
Raphael designed Cobalt Strike as a big brother to Armitage, his original project that served as a graphical cyber-attack management tool for Metasploit. Cobalt Strike quickly took off as an advanced adversary emulation tool ideal for post-exploitation exercises by Red Teams.
Flash forward to 2022 and not only is the world still turning, Cobalt Strike continues to mature, having become a favorite tool of top cybersecurity experts. The Cobalt Strike team has also grown accordingly, with more members than ever working on research activities to further add features, enhance security, and fulfill customer requests. With version 4.7 nearly ready, we’re eager to show you what we’ve been working on.
However, we’d be remiss not to take a moment to pause and thank the Cobalt Strike user community for all you’ve done to contribute over the years to help this solution evolve. But how could we best show our appreciation? A glitter unicorn card talking about “celebrating the journey”? A flash mob dance to Hall & Oates’ “You Make My Dreams Come True”? Hire a plane to write “With users like you, we’ve Cobalt Struck gold!” It turns out that that it is very difficult to express gratitude in a non-cheesy way, but we’ve tried our best with the following video:
Source: HelpSystems
TLS is a popular Internet security protocol designed to establish secure communications that provides both privacy and data security. TLS was first developed by the Internet Engineering Task Force (IETF) with the first version being published in 1999.
TLS was created from another encryption protocol called Secure Sockets Layer, or SSL. Since both protocols are so closely related, you may hear others use SSL and TLS interchangeably to describe secure communications over the Internet.
Ports 587, 2525, and 465 are commonly used to establish secure connections, but which you use varies based on whether you’re using IMAP or POP3 to access emails from your server. Your system administrator can also set specific ports for encryption on mail servers and other applications.
What is STARTTLS?
STARTTLS is a protocol command used to prompt an email server that the client wishes to upgrade the connection from an insecure connection to a secure one. STARTTLS can take an insecure connection and make it secure via TLS protocol. Having this option enabled on your mail server allows a secure connection to be established before any emails are sent.
How does TLS protect email communications?
TLS plays a role in protecting email communications by establishing a secure and encrypted connection between two points. TLS utilizes asymmetric encryption to keep email communications private and untampered with while in transit. In other words, using encryption for emails ensures that the contents of the message cannot be read or modified while being sent and provides a mechanism for authentication between the sender and recipient.
Emails that use SMTP risk having their messages compromised by man-in-the-middle attacks or wiretaps if they are operating without encryption. These attacks can silently copy your emails and read their contents or even change the contents of the message while it’s in transit. This not only compromises the integrity of the email, but can provide valuable information to attackers who are capable of launching even more sophisticated attacks against your domain, such as spear phishing or whaling campaigns.
Secure connections are established using a series of steps known as a “TLS handshake”. This handshake requires two parties in order to create a secure connection. When a message is sent using TLS, the handshake process gets into motion as follows:
- During the first phase, the client and server will specify which version of TLS they will use for the session.
- Then the client and server will pick which cipher suit they will use.
- The identity of the server will then be authenticated using the server’s TLS certificate.
- Finally, session keys will be generated and used to encrypt the email messages once the handshake is completed.
How to check if an email is using TLS
Today, close to 90% of emails both sent and received are encrypted. But how can you check for yourself?
Server administrators should be able to verify their email server is using some form of encryption by checking their certificate store and validating that their certificate is both installed correctly and up to date.
If you’re simply checking an email, you can verify if the message was sent using encryption by checking the headers of the message. In Gmail, this can be done by opening the email in question and clicking on the small arrow next to your name underneath the sender’s address.
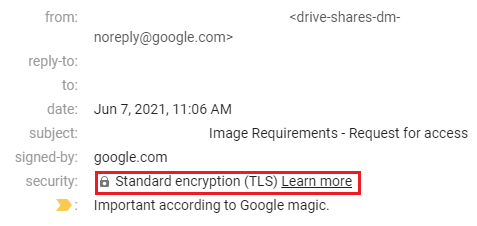
This can be done in Microsoft Outlook as well by opening the email you wish to check, and then navigating to File > Properties. This will open up the email header information which will contain any TLS information if available.
Is TLS the only protection I need?
TLS plays a vital role in email security, but it can’t protect against all email-based threats. Emails using encryption are protected against:
- Man-in-the-middle attacks
- Messages read or eavesdropped on by attackers while in transit
- Messages being forwarded to attackers
However, TLS cannot protect emails against:
- Phishing attempts using lookalike domains
- Malicious attachments that contain viruses
- Links inside of emails that redirect to phishing sites
- Emails that use social engineering to trick recipients into sharing sensitive information
- Servers sending spoof emails from domains that they do not control or defend
The Agari Advantage
Agari’s Email Security solutions utilize TLS and DMARC to ensure that emails are encrypted, as well as protected against phishing attacks from domain spoofing. Phishing attacks that use lookalike domains trick unsuspecting recipients into clicking links or sending sensitive information by pretending to be a trusted sender. These attacks can occur directly over a secure connection since they don’t have to abuse a lack of encryption to succeed.
By combining TLS encryption, organizations can deploy a security strategy that stops email-based attacks at all levels. For email protection beyond TLS, watch Agari’s Phishing Defense simulated product tour to see it in action for yourself!
Source: HelpSystems
Organizations are rapidly switching to Sophos’ managed detection and response service to enjoy better cybersecurity outcome.
We are thrilled to share that Sophos Managed Threat Response (MTR), our 24/7 human-led threat hunting, detection, and response service, now supports over 10,000 organizations around the world.
As cyber threats grow in both volume and complexity, organizations of all sizes and industries are increasingly turning to Sophos to enhance their cyber defenses. Testament to the quality of service and threat protection we provide, in independent reviews on Gartner Peer Insights customers rate us 4.7/5 as of July 2022.
Along with our customer base, we’re also expanding our our MDR services to support customers on their security journeys. For example, following our recent acquisition of SOC.OS we plan to include additional telemetry and context from alerts and events across dozens of third-party endpoint, server, firewall, identity and access management (IAM), cloud workload, email, and mobile security products. This will enable security operations teams to quickly understand and respond to the most urgent alerts across their entire estate.
Your security. Our responsibility.
We recognize and value the trust that customers place in us when they choose Sophos MTR. From the frontline threat hunters and response specialists in the MTR team to the malware, AI and engineering experts working behind the scenes, we are all fully focused on improving your cybersecurity outcomes.
Of course, each organization is different. That’s why we offer flexible service options that enable you to choose the level of support that best meet your needs.
- Managed by Sophos. Full 24/7/365 threat hunting and neutralization delivered by Sophos security operations specialists
- Managed together. Our experts work alongside your experts, enhancing your security operations and extending your protection, including evening, weekend and vacation cover
- Managed by you. Sophos XDR enables and empowers your team to conduct your threat hunting in-house using the latest next-gen technologies and threat intel insights
Our experts use the same Sophos next-gen technology as your experts, making it easy to switch support levels when your requirements change.
Sophos MTR in action: Neutralizing Cuba ransomware
Let me share with you a recent example of how Sophos MTR identified and neutralized a ransomware attack on a manufacturing organization, preventing data exfiltration, data encryption, business interruption, lost revenue, and remediation costs.
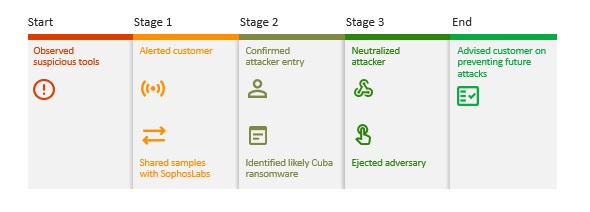
- Our operators detected suspicious indicators in the environment of a 200-seat customer working in the manufacturing sector. They noticed tools associated with ransomware groups along with Cobalt Strike, an adversary simulation tool that is commonly abused by threat actors
- Sophos MTR instantly alerted the customer and started an investigation, sharing samples with SophosLabs for detailed analysis
- Within 30 minutes SophosLabs confirmed a threat actor had gained access to the customers’ environment, and the adversary’s tactics, techniques, and procedures (TTP) matched the early stages of a Cuba ransomware attack
- Our team rapidly neutralized and evicted the adversary, preventing both data exfiltration and data encryption, and saving the customer hundreds of thousands of dollars of remediation cost, not to mention business interruption and lost earnings
- We were also able to guide the customer on how to harden their defenses to reduce the likelihood of future incidents
Improving cybersecurity outcomes at London South Bank University
Sophos MTR has enabled London South Bank University in the UK to strengthen cybersecurity for their 20,000 students and 2,500 staff while also freeing up the IT team to deliver initiatives that have increased student satisfaction. Hear their story in their word:
Πως μπορεί να σας βοηθήσει η Sophos
H Sophos μπορεί να προστατεύσει και να ενδυναμώσει τον οργανισμό σας, όπως ακριβώς έκανε στην περίπτωση του London South Bank University και χιλιάδες άλλους οργανισμούς σε όλο τον κόσμο.
Μιλήστε με τους ειδικούς συμβούλους της εταιρείας για να μάθετε περισσότερα για την υπηρεσία Sophos MTR και να συζητήσετε μαζί τους για το πως μπορούν να σας βοηθήσουν να επιτύχετε καλύτερα αποτελέσματα όσον αφορά την κυβερνοασφάλεια.
Source: Sophos
How companies can layer security solutions to ensure their data is fully protected no matter where it resides, how it travels or is shared.
Data is Everywhere
Enterprise data security is all about protecting sensitive data and ensuring that protected information is not compromised. Data can be anywhere and everywhere, so securing it has gotten increasingly complex from inside and outside the organization. Further complicating data security is the shifting from centralized storage in a data center to distributed and portable datasets located on user devices, remote locations, connected endpoints, and multiple clouds. Data is no longer a static thing secured behind a firewall. Instead, data often move across numerous environments and different locations, devices, and geographies.
Modern data security must start at the business level. Effective data security is about visibility, classification, and automation. Visibility focuses on understanding which data is important to protect; classification is about creating scenarios, rules, and categories for safeguarding sensitive information. Automation helps enforce and ensure the controls, policies, and data handling rules are in place.
HelpSystems has several offerings that address the roadmap for effective data security and automation. At its core, enterprise data security has multiple pillars, including data classification, data loss prevention (DLP), email security, domain-based message authentication reporting & conformance (DMARC), and secure managed file transfer (MFT) solutions. Below is a short overview of how HelpSystems supports organizations with enterprise data management (we will go further in-depth in subsequent articles.)
Data Classification
From the moment data is created, it becomes a liability. This is especially true if the data has no context. How can an organization protect its valuable, sensitive data if they don’t know what data they have? Identifying and classifying different data types, such as personally identifiable information (PII), is the basis of any good security plan. Classifying data provides important clarity for users and downstream security tools.
HelpSystems has 35 years of data classification experience and offers tailored solutions depending on different customer requirements.
Enterprise DLP
One of the main challenges with DLP is understanding trafficked data throughout the enterprise. Many traditional methods for monitoring and managing inbound and outbound traffic fall short as anyone with access to sensitive data can download and share corporate information.
In 2021, HelpSystems acquired DLP provider Digital Guardian to augment their SaaS and managed service endpoint, network, and cloud DLP capabilities.
Email Security
When data travels in and out of a network by email, the policies and security controls in the email solution protect the organization from outbound data leakage and inbound threats. Data labelling ensures that sensitive data is handled correctly, data is protected against viruses and malware, and if messages contain unauthorized information, it is automatically removed.
The Clearswift Email Security solution works seamlessly with other HelpSystems data security tools to provide continuous protection as data moves via email.
Securing Enterprise Email with DMARC
Bad actors use obfuscation methods to send phishing emails, social engineering, spam, ransomware, and malware emails disguised as legitimate sources to trick unwitting victims. These attacks inflict significant damage to an enterprise’s reputation and brand and, in most cases, cause consequential financial loss.
HelpSystem’s DMARC solution, Agari, helps its customers to monitor, detect, and respond to all related email streams under their name to prevent the malicious ones from affecting their customers’ and employees’ inboxes.
Managed File Transfer & Rights Management
Organizations increasingly rely on exchanging sensitive data between their constituents, including customers, business partners, employees, and suppliers. These file transfers include reports, contracts, employee and customer information, and project information – any manipulation or loss of data results in compliance and overall security issues. The efficient movement of data between an organization and its third-party partners must be secure, auditable, and accountable for data privacy and integrity.
HelpSystems’ Secure Managed File Transfer solutions, GoAnywhere and Globalscape address the security, encryption, and data protection needed when transferring sensitive information across the enterprise and its trusted third parties. Adding Digital Rights Management (DRM) adds further encryption to ensure files remain protected after the file transfer.
Securing Data and Email Across the Enterprise
HelpSystems data protection, email security, and secure file transfer solutions are viable options for organizations of all sizes that require enhanced data and communications protection. The technologies cover the “full-circle of life” from monitoring traffic, sanitizing sensitive data, blocking malicious behavior, deleting uncompliant information, and encrypting the data when it’s in motion or at rest.
We believe a solid business strategy that focuses on “buy what you can, build what you have to, and integrate for competitive advantage” will assist HelpSystems in differentiating itself in a hyper-competitive data security marketplace.
Source: HelpSystems
Malware and ransomware infection rates are increasing year-over-year, with ransomware attacks doubling in 2021 according to the Verizon Data Breach Investigations Report and 50% to 75% of ransomware victims being small businesses. It is more important than ever for MSPs to take a multi-layer security strategy to protect their customers.
Multi-layer defense is about adding layers of security to the environment to ensure you are operating as securely as possible. A typical SMB security stack would look like this:
-
Email security and advanced threat protection
-
Endpoint security
-
Patch management
-
Ransomware detection
-
Network security – firewall
-
Multi-factor authentication
-
Web-content filtering
-
Standard user account permissions
-
Backup and recovery
A key step when MSPs want to ensure their partners are fully secure is to focus on securing endpoints — mainly desktops and laptops. In this blog post, we will cover the key components of securing endpoints in an effective manner.
Email security and advanced threat protection
Because email is still a key attack vector, it is important to have advanced threat protection (ATP) in addition to the basic email security provided by the email provider. Effective pre-delivery email security prevents malware from entering the environment in the first place.
Datto SaaS Defense is designed to stop attacks before they reach the end user, allowing MSPs to proactively defend against a variety of malware that targets not only the Microsoft Exchange inbox, but the collaboration tools inside Microsoft 365 such as Microsoft OneDrive, Microsoft SharePoint and Microsoft Teams.
Endpoint security
Antivirus (AV)
Antivirus software runs automatically in the background on the endpoints in your environment and scans your system for known malware based on established virus definitions. When your AV detects malware, it removes it from the endpoint to protect your organization. While in the past having an AV on each endpoint was enough, this is now considered as just the first step in endpoint security.
Datto RMM ensures antivirus is installed and up-to-date. It is vital for MSPs to have accurate information about the status of antivirus solutions on all endpoints. Datto RMM’s universal antivirus detection not only detects the presence of antivirus solutions on endpoints, but also reports the status of these solutions.
Endpoint detection and response (EDR)
EDR alerts you to suspicious activity that may indicate a malware attack. Real-time alerts aim to reduce the time-to-detection of threats, which can have a significant impact on the chances to recover from incidents such as ransomware. Once an EDR tool has alerted you to suspicious activity, a security analyst will typically analyze the information and choose next steps. More broadly, these tools collect and monitor data pertaining to potential cybersecurity threats to the network. Your team can analyze this data to determine the root cause of security issues and use it to support incident response and management strategies. Recently CISA designated EDR as a critical component for cybersecurity, yet many firms still do not have this capability.
Patch management
Patches are updates to operating systems, software applications and networking devices, built to fix security vulnerabilities. They are crucial to designing an effective cybersecurity strategy because they often close security gaps that could allow bad actors entry into endpoint devices and IT networks. Unpatched vulnerabilities are one of the leading causes of security breaches. To ensure timely deployment of patches MSPs typically use patch management tools that provide them with detailed insights into apps and devices that are potentially at risk.
By using automated patch management tools MSPs can patch multiple endpoint devices simultaneously, enabling them to maintain a consistent security posture across all managed endpoints. Policy-based patching automation also helps MSPs be more efficient by reducing cumbersome manual updates and enhances the service delivery experience by minimizing end-user interruptions. Datto RMM’s built-in patch management engine makes patch management effortless and scalable for MSPs via flexible policies and automation.
Ransomware detection
Datto RMM’s unique Ransomware Detection functionality monitors endpoints for ransomware infection using proprietary behavioral analysis of files and alerts you when a device is infected. Once ransomware is detected, Datto RMM can isolate the device and attempt to stop suspected ransomware processes to prevent the ransomware from spreading. It enables MSPs to monitor endpoints for ransomware at scale, take steps to prevent the spread of ransomware and reduce time to remediation.
Backup and recovery
Your clients may have different needs when it comes to their endpoint security strategy. However, one essential component should be endpoint backup. When other endpoint security measures fail, an updated backup of the device will ensure that you still have access to all necessary information no matter what happens.
In other words, security starts with recovery. It is crucial to backup endpoints in order to allow recovery in case of a cyber incident. Datto Cloud Continuity for PCs enhances endpoint security and acts as a last line of defense by protecting data in case of a hardware failure, accidental deletion, ransomware attack, or another disaster. Cloud Continuity ensures endpoints can be restored to their pre-disaster state quickly and easily.
By backing up your clients’ data to the cloud, you can ensure their important files are safe and accessible even if their computer is damaged or destroyed. In addition, cloud backup can help your clients comply with data loss prevention (DLP) regulations and keep their business running in the event of a systems outage. If you’re looking for a reliable and secure way to back up your clients’ data, consider adding cloud backup services to your multi-layered security strategy to enhance your existing endpoint monitoring services.
Download the Security Best Practices Checklist to start today with some simple actions to protect your customers from ransomware.
Source: Datto
Your professional services automation (PSA) solution is at the heart of your MSP practice. The Datto Autotask PSA team has been hard at work on the latest quarterly release, adding several new updates to make it even more secure, efficient and responsive to your needs.
Autotask PSA is a powerful, intuitive cloud-based PSA platform that provides a singular view of the entire business. By centralizing MSP business operations, Autotask PSA enables you to make data-driven decisions to improve service, productivity and profitability.
The 2022.1 Autotask PSA release is now available, with significant improvements to inventory, security and sales tax functionality. Here are the latest additions:
Inventory restructure
The ability to better track and manage your inventory reduces sales friction, enabling proactive management and optimization of inventory stock. Autotask PSA’s Inventory feature tracks the items that you have in stock to resell to your customers. The 2022.1 release provides enhanced tracking and reporting capabilities to better manage and evaluate your inventory.
Now you can:
-
Introduce stocked items for better tracking of your inventory products
-
Enable tracking of multiple vendor purchase orders
- Benefit from improved reporting and analytics capabilities
Client Portal two-factor authentication (2FA)
A security-first approach is fundamental to all Datto solutions. 2FA is an additional security layer that addresses the vulnerabilities of a standard password approach. With the newly added 2FA on Autotask PSA, you can:
-
Enable multi-factor authentication for client portal admins if you choose not to mandate from the MSP side
-
Easily view who has this feature configured
- Conveniently reset authentication if needed
TaxJar integration
Sales tax automation is a must for multi-jurisdiction regions (for US and Canada only) due to the time savings for MSPs (no calculations required) and compliance to regional tax laws. Autotask PSA is now integrated with TaxJar, a cloud-based sales tax compliance platform. Use TaxJar to:
-
Enable tax compliance for those dealing with multiple jurisdictions
-
Simplify tax calculations
-
Save valuable time
In addition, Autotask PSA has been updated with 20+ enhancements inspired by you, our MSP user community. We are constantly soliciting your feedback to make Autotask PSA even better, and we’ve acted on your insights with new improvements that include:
-
Expanded Microsoft Teams scheduling capabilities
-
Ability to import invoice preferences versus updating one by one
-
Refactored contract wizards
-
Ability to import additional data fields related to your tasks
Looking for a PSA platform to help grow your business by unifying Document Management, Service Desk, CRM, Procurement, Billing, and Reporting behind a single pane of glass? Learn more about Autotask PSA today.
Source: Datto
Ransomware attacks can be mitigated with some security measures and techniques, but in terms of publishing of sensitive data, only data encryption protection can help you. Find out in this article how to protect your sensitive data with encryption, steps for an effective encryption strategy and what to encrypt.
Taking back control of your data through Encryption
It is established that encryption is important to secure your data, but that is not the only solution. It is not only important for modern security but is also core to modern computing if you want to excel in an internet driven environment. In fact, it is more important that you have an effective information policy where big tech companies and third-party providers allow you to cloud compute, and store and share vast amounts of information online; it is only essential that you encrypt all that data before using these services if you manage sensitive data.
It is not only important to fully evaluate and prioritize which data needs to be enabled to be accessed and stored, it is also crucial that you fully encrypt all of the documents and communication files before putting them online. This way you can greatly reduce the vulnerability of your organization and/or company’s potential of a data breach by big cybersecurity thieves.
Who is at Risk?
Despite the incidences of frequent cyber attacks, data breaches and identity thefts, IDC reports that only 3% of those information leaks and data breaches was encrypted and protected. This means that 97% of that data was not encrypted and highly exposed, with only 3% unusable to the cyber thieves due to being encrypted and inaccessible despite being stolen.
One of the greatest responsible motivator of wide spread of ransomware is to make money or gain profit through ransom. As far today’s scenario is concerned, the objective of ransomware is damage, destruction, harming victim at any state and yield as much money as possible either by hooks or crooks.
Some people are more at danger than others:
- Corporate or Business Sector are most favorable target for ransomware initiators due to the presence of huge amount of confidential data regarding its consumer, sales, purchase, ledgers, journals, quotations, taxes etc. Loss of such documents can cause the whole business to shut down or bear major losses. Thus, corporate sectors opted to willfully pay ransom instead of suffering setback. The proceedings of World Congress on Engineering and Computer Sciences estimated that out of all victims, around 46% of corporations are targeted, out of these 88% were not using encryption.
- Public or Government Sector. This mostly comprises of educational institutions, power corporations, telecommunications, law enforcement wings, hospitals, banks, transportation and all those establishments that have direct impact on public. The risk of not being encrypted comes from hackers affecting such institutions, increases the probability of getting ransom because upkeep and maintenance of the offline digital copies of huge pile of data is difficult and denial to pay ransom will lead to setbacks in terms of minimum 3 to 6 months, i.e., another big deal of nearly a fresh start. Similarly, infecting government sector fulfil two major objectives of crooks, one to ensure the payment of ransom and if not, then steal the data regarding defense, citizens, budgets, policies etc. and sell it for money over dark net. Hence, encryption of all these data can not only save the organizations and public departments from paying huge amounts of ransom, but also prevent the theft of piles of data that could otherwise set back public or organizational affairs by upto 3 to 6 months or even more!
- Home Users or Individuals are softest targets of ransomware due to their least fluency with technical aspects of computers. Although a home user generally does not have huge amount of data compared to corporate sector and not related to public concerns but still have extreme significance to its holder that includes reports, projects, pictures, game files, emails, credit card information, online shopping behaviors, etc. Extortion and pressure of ransom payment further increased by eradication of any backup files and disabling of system restore just before commencement of encryption of files by ransomware.
Steps for an effective encryption or data protection management plan
It is important to formulate an encryption or protection plan by following through the three critical questions to allow yourself control over which data to encrypt and protect:
- Analyze which data needs to be encrypted: Since it’s your data and your company, it is important that you carefully analyze, evaluate, and prioritize which date needs to be encrypted the most. For instance, this could include personally identifiable information (PII) and any trade secrets that would be harmful if leaked.
- Having a document protection plan: Having encryption is the first step and having an encryption is the last and second most crucial step in your data protection. It is important that you decide what happens with your data while it is in transit and while at rest. These require different levels of protection and you can fully control what happens when. For instance, you can choose to destroy a file if it is shared beyond what you initially provided access for. But, for this to work, you need to have that type of encryption embedded in your file beforehand.
- Establish solid and easy-to-manage protection policies: It is a busy world and you may often get too caught up in day-to-day affairs of your company to bother with data breaches of previous documents. However, you can choose types of protection policies management plans to automatically keep up with your data while it is at rest and whenever, wherever it is accessed or shared online. This way you can assess your encryption performance regularly to get clear of any serious data breaches.

If you want to learn more about a more detailed approach and deploy to protect your corporate data through a data-centric security approach, read this article.
Knowing what to Encrypt and How much to Encrypt?
Organizations or public sector departments and businesses must be told what information should be safeguarded when encrypting files or folders on file servers or cloud repositories. It’s also critical to use automation to make file protection easier, especially when encrypting folders or safeguarding data in information repositories. In order to avoid spill of privacy, disclosure of confidentiality and enhance a secure transmission of message between two parties the encryption tools are designed to provide safety and ensuring security goals during communication. Take for instance, the Zero Trust Security Model, which focuses on the ‘layer’ protection, on the premise that since every data is so mobile online, it is important to assume that no one or nothing can be trusted.
IRM (Information Rights Management); beyond encryption
IRM systems deal with the challenge on what happens with data once it is in transit or has left the perimeters. Also known as E-DRM (Enterprise Digital Rights Management) or EIP&C (Enterprise Information Protection & Control, it uses a highly sophisticated and effective form of cryptographic protection that applies to files that are travelling and provides protection wherever they transit. The IRM’s system approach is to apply a layered protection to the data that can be controlled even if it is no longer in the network, whether it is in a cloud, on a mobile device, etc.
If the data reaches someone it shouldn’t of whom you consider shouldn’t have access to it, you can revoke the access remotely. You can set expiry dates for documents. Give users more or fewer permissions in real time (Edit when before they could only Read, or restrict the permission to read-only if we don’t want them to edit or print). The ease with which this type of solution may be implemented means you can start using it right away and encrypt and regulate important data that your firm controls internally or with third parties.
One of the most critical aspects of this technology is its ability to be made simple to use so that non-technical people can manage protected data as if it were unprotected data. One part of encryption is allowing end users to be at ease in assessing and using, sharing, editing, transferring their own data without having technical difficulties and know-how of cryptography. It is done by making it compatible with the apps that users use on a daily basis, such as Office, Adobe, and AutoCAD, as well as the information repositories that companies often use, such as File Servers, One Drive, G-Suite, Microsoft Office 365 Cloud applications, SharePoint, Drop Box, and so on.
Hence, depending on the vulnerability of the data, the extent of damage the leakage or theft of which document can have on an organization, you can choose to apply different levels of protection. For instance, if you are sharing confidential information about a new tender with your business partner, you may allow it to be shared with only specific parties, departments with only view-only permissions – beyond which if accessed, the files could not be assessed and if tried to decrypt, would be of no use to potential competitors.
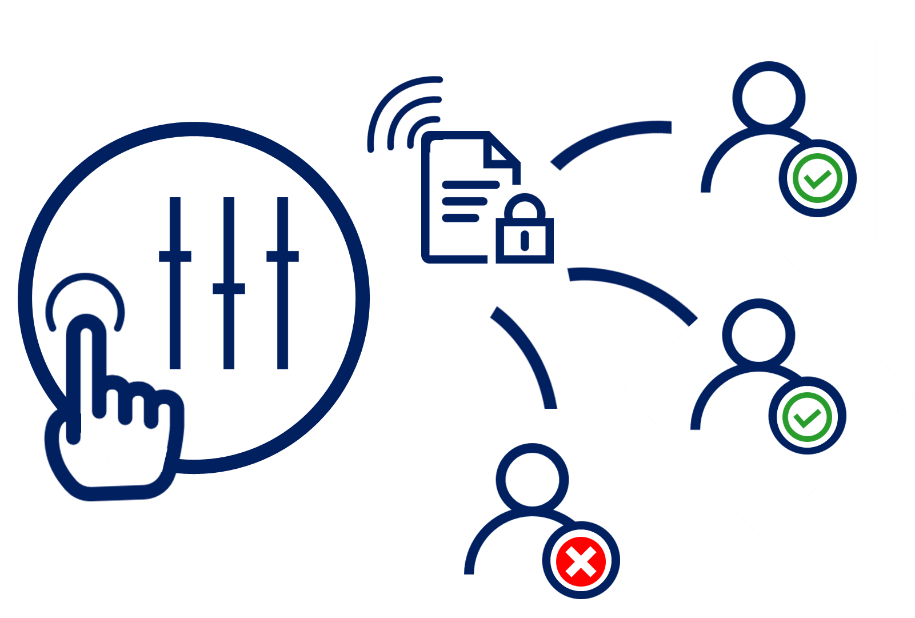
On the other hand, you might want to limit access to your company’s data that may harm your company, employees, customer base and business partners, if stolen. You can put a minimal protection but with certain levels of access permission. You can choose exactly what happens with which type of data, develop a ‘protection in use’ policy of the encryption and not just a protection in rest or transit. Also, although many organizations and public departments may have pinpoint documents labeled as ‘public’, ‘private’, ‘confidential’, ‘internal use only’, etc, it is more evident on paper than online. Being able to encrypt them according to the levels of classification on paper would be the real win for these organizations. IRM integrated with data classification tools allow you to automatically protect classified or labelled data with a specific IRM protection policy.
Takeaways of Protecting Your Documents Through a Data-Centric Security Approach
It is established that encryption involves a data-centric security management strategy to protect the collective interests of an individual or organization, employees, customers, partners and more. Some of the advantages of having a multi-layer encryption-based protection based in a data-centric security approach for your online data may include:
- Protection of sensitive documents without relying on user actions.
- Ensuring protection of data whether information is travelling outside network perimeter, being accessed by an outsider or while it is in transit, at rest and in use.
- Control what users can do with your documents (View only, copy & paste, edit, print, etc.).
- Monitor, allow or disallow access regardless of where your data is.
- Revoke access to sensitive information even if you provided access permission before.
- Protecting your intellectual property rights by having full control of your data, hence making it almost impossible to be stolen by competitors and imprinters.
SealPath allows you to develop an effective management system for all your sensitive data you want to protect with effective protection, monitoring, and automation systems. You can ensure efficient protection using an integrated IRM (or E-DRM) model to ensure protection of your data in use, at rest and in transit, without having to worry about theft or paying ransoms due to theft.
Source: Sealpath
Secure access service edge (SASE) is set to make cybersecurity simpler and more robust. At Sophos, we’re already well on the way.
Increasingly, secure access service edge (SASE) looks like the future of cybersecurity. As point solutions start to converge and share their data, applying security policies in a smart, unified way can save time, simplify workloads, and shore up configuration gaps.
Here at Sophos, this has been clear to us for some time. We’ve been working behind the scenes for a number of years to align our products around a common vision and approach.
As a result, our SASE capabilities will be seamless when they arrive. They’ll be unique from anything else you might see in the market, and you’ll be able to leverage them using the Sophos technologies you already know and love.
What is SASE?
According to Gartner, SASE combines network security functions with wide area networking (WAN) capabilities so organizations can deliver access dynamically, in a secure way.
It’s “a new package of technologies… with the ability to identify sensitive data or malware and the ability to decrypt content at line speed, with continuous monitoring of sessions for risk and trust levels.”
Because SASE integrates network functions like software defined wide area networking (SD-WAN) with both on-premises and cloud-based security into a single system, you can seamlessly implement policies across your entire estate. That saves you time and money on setup and management while delivering a consistent, secure experience.
Importantly, SASE is intelligent about how and where it applies your policies. It will assess whether your devices and applications need private access, or whether to enforce zero trust network access (ZTNA) in the cloud. This gives you the security you need, where and when you need it—increasing performance and reducing bandwidth costs and latency.
What SASE looks like today
Here’s the clever part. The functions that will become the core of Sophos’s SASE capability are largely already built into the tools you use today.
In Sophos Central, we have a central management point that acts as a unified data plane, ensuring consistency and compatibility, with shared building blocks. We don’t need to make our products work together; they’re already made that way.
And we use containerization to build our products, so extra features and upgrades, such as SASE capabilities, can be configured in an extra module and slotted in seamlessly, without downtime.
That may seem like a small thing. But when you are ready to move to SASE, it’ll make all the difference. You won’t need to learn another new technology; just connect the tools you know. And—as you’ve come to expect from Sophos—it’ll just work.
The Sophos difference
When you use Sophos SASE, you’ll feel the difference in three important ways:
Products built with convergence in mind
With Sophos, everything is designed within the same platform, from the same building blocks, delivering a unified, consistent experience across your whole security ecosystem.
We’re not trying to take a bunch of disconnected security solutions and bolt them together—so each part of the system works slightly differently, and every update risks a problem elsewhere.
Instead, every aspect will feel the same, making the experience easy, consistent, and intuitive everywhere—for your IT team and your users—which is the point of SASE in the first place.
Centralized data lake for effective threat response
Our SASE solution will draw on our existing expertise in storing and analyzing firewall log data in a centralized data lake. That’s a powerful resource for SecOps professionals—whether yours or ours.
New threats emerge every day, so by keeping your log data for 30 days, you can backtrack to see if any newly discovered forms of attack have affected your organization.
Again, this is already built into our tools. The number of Sophos Firewalls connected to our data lake has more than doubled in the last 12 months, while our Central Firewall Reporting gives almost limitless processing potential.
And because Sophos offers 24/7 threat hunting and remediation services, you know there’s always a team of full-time security experts just a call away, looking at exactly the same data you are.
Smooth, painless activation
We build our network protection solutions using containerized microservices—so they’re easy to adapt and upgrade. When we change one aspect or policy, it’s applied seamlessly across your whole ecosystem.
In the short term, that means you don’t need to replace your solutions to take advantage of SASE. And in the future, you can scale quickly in the cloud, and easily tune your system to match your organization’s evolving needs.
Whether you’re ready to make the move soon or need more time, you can be safe in the knowledge that our products are adaptable—and ready when you are.
Sophos is your partner for the future
Security solutions are converging, and fast. But, as with all new technology, it can take time to feel comfortable making the switch. So it’s good to know the Sophos solutions you use today don’t have a limited shelf life. They are future-proof and ready for SASE when you are.
Learn more about our SASE strategy and suite of products, available today and coming soon. If you’re eager to get going, watch for our upcoming early access programs, coming soon for new products like our Cloud Native Firewall, ZTNA-as-a-Service, and Cloud Web Gateway.
Source: Sophos
Ransomware attacks can be mitigated with some security measures and techniques, but in terms of publishing of sensitive data, only data encryption protection can help you. Find out in this article how to protect your sensitive data with encryption, steps for an effective encryption strategy and what to encrypt.
With the advancement of technology, a handful of cybercriminals have become more adept at hiding their malware code to avoid the most difficult-to-evade security measures. Because it is freely available on the dark web, ransomware does not need very difficult skills.
Cyber criminals are so successful with their ransomware because they constantly incorporate new technological advancements into their attacks and employ them faster than others. For example, consider the well-known phenomenon of adware creeping itself using readme.txt files in your computer, or data breachers occurring through word and pdf files, stealing huge amounts of sensitive data. Cherry on top is this data is then sold off to willing parties for thousands of dollars, comprising passwords, identities, confidential information, project data, company secrets and what not.
Why encrypt data against ransomware attacks?
Encryption can assist tackle the growing privacy and security challenges that both consumers and organizations face, as well as deter hackers who wish to steal our information. IBM reports that ransomware attacks cost organizations upto $4.62 million per breach, not including the ransom demand by cyber thieves for decryption keys in exchange! With the presence of a huge black market for stolen data, it is wise to have protection policy than regrets, lost time and money and huge losses in turnover due to your company’s name labeled as a company compromised in data security protection measures.
In this article you will find out a detailed post about: “the importance of Encryption“.
How having an Encryption Policy is the best strategy for modern computing?
According to a research, only 30% of companies have an active encryption policy despite frequent data breaches in the 21st century. Encryption is the core for today’s computing driven commercial environment. With huge amounts of incoming and outgoing data with a set of data breachers working to steal your information, encryption is the utmost security protection organizations, businesses and individuals can put to protect from theft. Encryption can assist tackle the growing privacy and security challenges that both consumers and organizations face, as well as deter hackers who wish to steal your information, be it login credentials, confidential information about your new project or company secrets that your competitors can leverage from.
Using Encryption to protect your Organization Data from Breaches and Ransomware
You might have the popular maxim, ‘if you use a free service, you are the product’. This also holds true for companies and other organizations that rely upon big third party service providers. Whether you are an individual or organization, the technology services that your company uses are reliant upon your data — data about your employees, your customers and your business — to generate their revenues and profits. Of course, if you share your word/pdf files with huge amounts of information with a third-party for whatever reasons, you are exposing yourself and your company to data breaches without encryption. An un-encrypted file can be accessed, shared, edited by any third-party and god forbid even deleted or sold off to competitors and data buyers by a potential cyber criminal. Encryption is the key to taking back some data control from technology processes that gain access to individual and corporate information just because they can. Huge companies like Facebook, Whatsapp and Apple rely on promising data security through end-to-end encryption policy as positive selling points. Similarly, encryption of your documents can keep your documents away from prying eyes for both competitor tech companies and cyber criminals alike, even if they somehow get access to it!
Industrial Spy Stolen Data
Cybercriminals now operate with modern computing to carry out high profile and sometimes state sponsored cyber hacking and data breach activities to gain an edge over potential foes and competitors. Failure at protecting your data through encryption could have grave implications for your organization in terms of ransom, data breaches, damage to company’s name and major losses in revenue. In November 2021, the FBI and Interpol uncovered a major data theft by Nigerian cybercriminals, found to have stolen data from 50,000 organizations! Similarly, in May 2021 a massive data breach occurred when Air India reported approximately 4.5 million records stolen from its seemingly secure database. So where does all the stolen data go?

Cyber criminals have launched a new cyberspace called Industrial Spy that sells all the compromised data from such breached companies, sometimes even offering it for free to its members. Unlike traditional cyber marketplaces for stolen data, Industrial Spy doesn’t work to merely extort enterprises and impose GDPR fines. Industrial Spy allows organizations to purchase data of their competitors or breached data to large scale cybercriminals such as trade classified information, accounting reports, manufacturing diagrams and client databases.
The marketplace has different levels of data offerings, from $2 for individual files up to “premium” stolen data related which represents all data stolen from an organization and that could be proposed for million of dollars. For instance, Industrial Spy is currently selling an Indian company’s data in their premium category for $1.4 million, paid in Bitcoin. On the other hand, much of their data is being sold as individual files, where threat actors can purchase the specific files they want for $2 each. The marketplace also offers free stolen data packs, likely to entice other threat actors to use the site. However, it would not be surprising if the new marketplace is used to extort victims into purchasing their information in order to prevent it from being sold to other cybercriminals.
According to BleepingComputer, the malware executables that create README.txt files to promote Industrial Spy website on Telegram and Twitter was discovered by MalwareHunterTeam security specialists. When these malware files are executed, they generate text files in every folder on the machine, including a description of the service as well as a link to the Tor website. This readme.txt file shows such messages to potential buyers: “There you can buy or download for free private and compromising data of your competitors. We publish schemes, drawings, technologies, political and military secrets, accounting reports and clients databases. All these things were gathered from the largest worldwide companies, conglomerates, and concerns with every activity. We gather data using a vulnerability in their IT infrastructure.” An investigation conducted by BleepingComputer shows that these executables are being distributed via other malware downloaders that are frequently camouflaged as cracks and adware. While the site isn’t very popular yet, businesses and security professionals are recommended to keep an eye on it and the information it claims to sell. You might never know when your company is the next target!
MailStore announced the new version 22.1. New MailStore V22.1 brings optimized usability, security and compliance. Almost six weeks later, MailStore announced V22.1.1 for error-free archiving with public folders on Microsoft 365 and recently, the company announced the release of V22.2 offering support for the operating systems Windows 11 and Windows Server 2022 (Essentials, Standard και Datacenter).
However, before we talk about the new features brought by version 22.2 of MailStore, we will refer to those brought by the V22.1, after of course the significant change in the nomenclature and the numbering scheme of MailStore products.
MailStore V22.1
Administrators of MailStore Server and the MailStore Service Provider Edition (SPE) will benefit from a better user experience with optimized usability and stability, while business owners will be pleased with the enhanced security and a new compliance feature. This is especially the case for businesses that are using our add-on tool MailStore Gateway. MailStore Home users aren’t going away empty-handed either, as we’ve improved the user friendliness.
If you’re wondering why Version 13.2 is being succeeded by Version 22.1, don’t worry: you haven’t missed eight main versions, nor have we got our maths wrong. With the latest version, we’ve changed our numbering scheme for MailStore product versions. The new numbering system reflects the time of the release, so, Version 22.1 stands for the first quarter of 2022. You’ll find more information, together with a series of FAQs, in our blog post New Version Numbering System for MailStore Products.
The version number will be given the format YY.Q, where YY stands for the year and Q for the quarter of the release (e.g. 22.1 for the first quarter of 2022). The full version number will appear thus: <YY.Q.N.BBBBB>, where YY is the 2-digit year, Q is the quarter, N is the release number in the respective quarter, beginning with 0, and BBBBB is the build number of the release. For example: 22.1.0.12345 would be the first release in the first quarter of 2022 with build number 12345.
New Features for MailStore Server and the MailStore Service Provider Edition
With Version 22.1 of MailStore Server and the MailStore Service Provider Edition, administrators will benefit from a better user experience, while business owners will be delighted with a new compliance feature. Moreover, the updated GDPR certification means that customers can rest assured that Version 22.1 helps meet the requirements of the EU’s GDPR.
A Better User Experience
By popular request, admins can now determine much quicker whether they need to take action in the archive. The subject lines of the status reports in MailStore Server and the MailStore SPE now alert administrators of the need to take direct action, if necessary. So, without having to examine every status report in detail, administrators can tell immediately whether, let’s say, an error has occurred in the archive and action is required. This can save precious time in everyday work, especially on mobile devices.
Version 22.1 of MailStore Server also lets admins install a new license without having to reboot the MailStore Client. So, it’s now possible to renew your Update & Support Service or switch from a trial version to a productive system without interruption, even if you have not yet activated the automatic license updating function.
Another improvement is the new input validation feature, which immediately notifies MailStore Server and MailStore SPE administrators if they have used invalid characters in the text fields of a file and folder path, e.g. when specifying which PST file is to be archived. Input validation has also been introduced when configuring the automatic creation of archive storage, too. Early detection of invalid characters avoids subsequent errors; so, rather than spending time searching for invalid entries later, the administrator can correct them straight away.
Compliance
In the new version of MailStore Server and the MailStore SPE, the audit log now records how specific archiving and export profiles have been configured in the past. The resulting “full configuration history” can be used to track how certain settings have been modified over time and how this was done. This can be useful during audits and also helps with compliance. The logged information can also be used to resolve issues with archiving and export profiles, should technical problems occur.
Updated GDPR Certification
It goes without saying that Version 22.1 of our business solutions, MailStore Server and the MailStore SPE, has again been certified by independent data protection experts.
The certification takes into account all relevant aspects of the European General Data Protection Regulation (GDPR) and shows that, when used appropriately, both MailStore Server and the MailStore SPE meet all the requirements governing the processing of personal data set out in the GDPR.
New Features for MailStore Gateway
MailStore Gateway is a free add-on tool to support the simple archiving of cloud services such as Microsoft 365 and Google Workspace, and can be used as a supplement to MailStore Server and the MailStore SPE. With Version 22.1, users of MailStore Gateway profit from several new security features.
Enhanced Security
By popular request, administrators can now use Let’s Encrypt™ certificates in MailStore Gateway. This gives our customers a convenient way to use Let’s Encrypt’s free and trusted certificates to safely encrypt all incoming communications running through MailStore Gateway. The certificates can be configured during installation and at any time in MailStore Gateway’s configuration tool, and are renewed automatically every 60 days. Additional information on using Let’s Encrypt certificates with MailStore Gateway can be found in our Help section.
Moreover, the new version of MailStore Gateway uses .NET 6, i.e. the latest .NET LTS release. Also, as we are no longer bundling .NET runtime with the MailStore Gateway installer, you can update your installed .NET runtimes at operating system level (e.g. via Windows Update). This means that you’ll be able to update the .NET framework without having to update MailStore Gateway. During the installation process, the MailStore Gateway installer checks whether the .NET 6 framework exists on your system. If not, the latest version of the framework is downloaded.
Another improvement concerns the handling of TLS/SSL connections by .NET; this has now been updated in line with Microsoft’s current best practices.
New Features for MailStore Home
Although the new release focuses on our business solutions, home users of our archiving solution MailStore Home are not leaving empty-handed either. MailStore Home users, too, will benefit from the new input validation feature, which immediately notifies them if invalid characters are used in the text fields of a file and folder path. Invalid characters are detected early, which means that subsequent errors are avoided and users can correct their inputs straight away.
MailStore Version 22.2
The MailStore email archiving solutions are well known for always supporting the latest operating systems. Following this tradition, MailStore 22.2 now supports Windows 11 and Windows Server 2022, enabling our customers to use their MailStore installation with Microsoft’s most recent operating systems. This provides customers with maximum flexibility and independence when choosing the OS platform for their MailStore installation. In addition, our support of the latest operating systems emphasizes MailStore’s commitment to always protect our customers’ long-term investment in MailStore email archiving solutions. The new version also enables MailStore customers to use TLS 1.3 encryption where available, i.e., currently on Windows Server 2022 or Windows 11 only. This increases security for customers when using MailStore software remotely, even on public networks (e.g. at locations like airports), by being able to use the latest encryption standard. Besides the changes mentioned above, the new version offers various under-the-hood improvements for increased stability, security & performance and as a basis for future enhancements. For example, the underlying framework was updated to .NET Framework 4.8. Also, there is an update of third-party library, which fixes several minor issues in archiving, displaying and exporting of emails. Updated is also the internal database engine for improving stability, security and performance.
For MailStore Server
Supported Operating Systems (32-bit and 64-bit Versions where applicable)
- Microsoft Windows 11
- Microsoft Windows 10
- Microsoft Windows 8.1
- Microsoft Windows 7 SP11
- Microsoft Windows Server 2022 (Essentials, Standard, Datacenter)
- Microsoft Windows Server 2019 (Essentials, Standard, Datacenter)
- Microsoft Windows Server 2016 (Essentials, Standard, Datacenter)
- Microsoft Windows Server 2012 and 2012 R2 (Foundation, Essentials, Standard, Datacenter)
- Microsoft Windows Small Business Server 2011 SP11
- Microsoft Windows Server 2008 R2 SP11 (Foundation, Standard, Enterprise, Datacenter)
For MailStore Service Provider Edition
Supported operating systems
- Windows Server 2008 R2 SP11 Standard, Enterprise or Datacenter (Server Core Installation)
- Windows Server 2008 R2 SP11 Standard, Enterprise or Datacenter (Server with a GUI)
- Windows Server 2012 Standard or Datacenter (Server Core Installation)
- Windows Server 2012 Standard or Datacenter (Server with a GUI)
- Windows Server 2012 R2 Standard or Datacenter (Server Core Installation)
- Windows Server 2012 R2 Standard or Datacenter (Server with a GUI)
- Windows Server 2016 Standard or Datacenter (Server Core Installation)
- Windows Server 2016 Standard or Datacenter (Server with a GUI)
- Windows Server 2019 Standard or Datacenter (Server Core Installation)
- Windows Server 2019 Standard or Datacenter (Server with a GUI)
- Windows Server 2022 Standard or Datacenter (Server Core Installation)
- Windows Server 2022 Standard or Datacenter (Server with a GUI)
Additional Requirements
- .NET Framework 4.8
Get the latest insights into ransomware attacks, ransom payments, and the fast-changing cyber insurance healthcare market over the last year.
Sophos has just launched the State of Ransomware in Healthcare 2022, an insightful report carved out of its annual study of the real-world ransomware experiences of healthcare IT professionals. This year, 5,600 IT professionals, including 381 in healthcare, from 31 countries participated in the research.
The study reveals a growing ransomware attack rate on healthcare, resulting in an increasingly tough, broader threat environment for this sector. The study also focuses on the rapidly evolving relationship between ransomware and cyber insurance in healthcare, highlighting how often and how much ransom was paid out by insurance providers against claims by healthcare.
 Here are some key findings from the report:
Here are some key findings from the report:
- Ransomware attacks on healthcare almost doubled – 66% of healthcare organizations surveyed were hit by ransomware in 2021, up from 34% in 2020
- A more challenging healthcare threat environment– this sector saw the highest increase in volume (69%) and perceived complexity (67%) of cyber attacks and the second-highest increase in the impact (59%) of such attacks
- Healthcare is most likely to pay the ransom, ranking first with 61% of organizations paying the ransom to get encrypted data back, compared with the global average of 46%; this is almost double than 34% who paid the ransom in 2020
- But, healthcare pays the least ransom amount – US$197K was the ransom amount paid by healthcare in 2021 compared with the global average of US$812K
- Less data is recovered after paying the ransom – healthcare organizations that paid the ransom got back only 65% of their data in 2021, down from 69% in 2020; furthermore, only 2% of those that paid the ransom in 2021 got ALL their data back, down from 8% in 2020
- High cost to recover from ransomware incidents – healthcare ranked second highest at US$1.85M in terms of the average cost to rectify ransomware attacks compared with the global average of US$1.40M
- Long recovery time from ransomware attacks – 44% of healthcare organizations that suffered an attack in the last year took up to a week to recover from the most significant attack, whereas 25% of them took up to one month
- Low cyber insurance coverage in healthcare – only 78% of healthcare organizations have cyber insurance coverage compared with the global average of 83%
- Cyber insurance driving better cyber defenses – 97% of healthcare organizations with cyber insurance have upgraded their cyber defenses to improve their cyber insurance position
- Cyber insurance almost always pays out – in 97% of incidents where the healthcare organization had cyber insurance that covered ransomware, the insurer paid some or all the costs incurred (with 47% overall covering the ransom payment)
The growing rate of ransomware attacks in healthcare reflects the success of the ransomware-as-a-service model, which significantly extends the reach of ransomware by reducing the skill level required to deploy an attack. Most healthcare organizations are choosing to reduce the financial risk associated with such attacks by taking cyber insurance.
However, it is getting harder for healthcare to get coverage, likely because of the high rate of ransomware incidents in this sector. The subsequent insurance coverage gap is leaving many healthcare organizations exposed to the full cost of an attack, increasing the overall ransomware remediation costs. As the coverage becomes more challenging to get, healthcare is bolstering its cyber defenses to improve its cyber insurance position.
Read more about the State of Ransomware in Healthcare 2022.
Source: Sophos
We’re proud to have been named Cybersecurity Company of the Year by Cyber Defense Magazine. It is an Editor’s Choice winner in the publication’s 10th annual Global InfoSec Awards.
“Cybercriminals are constantly changing their tactics, techniques and procedures to evade detection, and Sophos forensic evidence shows a 36% increase in attacker dwell time in 2021.
The fact that attackers are lingering in victim environments for weeks on end – and far longer for smaller organizations – should serve as a wakeup call to businesses worldwide,” said Raja Patel, senior vice president of products at Sophos. “Sophos is helping organizations detect intruders and neutralize threats throughout the attack chain before they cause damage, and we’re honored to accept this award.”
Sophos’ comprehensive and integrated portfolio of solutions and managed services protects against ransomware and other advanced cyberthreats. Pillar offerings – including Sophos Intercept X, Sophos XDR, Sophos Firewall, Sophos ZTNA, and Sophos Cloud Security – are easily managed in the cloud-native Sophos Central platform.
Customers can also choose to have them managed by Sophos MTR, a threat hunting, detection, investigation, and response service that provides a dedicated 24/7 security team to rapidly identify and neutralize sophisticated and complex threats.
Offerings are part of the Sophos Adaptive Cybersecurity Ecosystem, where they share real-time threat intelligence for faster and more contextual and synchronized detection, protection and response. Working together, the solutions can better identify and quickly respond to active threats.
“Sophos embodies three major features we judges look for: understanding tomorrow’s threats, today; providing cost-effective solutions; and innovating in unexpected ways that can help mitigate cyber risk and get one step ahead of the next breach,” said Gary Miliefsky, publisher of Cyber Defense Magazine.
Cyber Defense Magazine announced the winners at RSA Conference 2022. A full list of winners is available online at http://www.cyberdefenseawards.com/.
Source: Sophos
Sophos Firewall OS v18.5 MR4 is a fully supported upgrade from v17.5 MR14 and later, v18 MR3 and later, and all previous versions of v18.5.
While many organizations have already upgraded to SFOS v19 to take advantage of all the great new SD-WAN, VPN, and quality-of-life improvements, we know many of you are possibly waiting for the first maintenance release for v19 before jumping in. The team is hard at work on the first MR for v19, but in the meantime, they’ve released a nice update for v18.5 with MR4.
What’s new in SFOS v18.5 MR4
- Static multicast enhancements
- CLI support for “multicast-decrement-ttl enable/disable” to control the TTL value in static multicast route forwarding use cases. This can prevent multicast traffic from getting dropped due to expiring TTL values at the time of forwarding.
- Increased the default multicast group limit to 250 to support an increased number of OSPF neighbors. This can be changed via CLI “multicast-group-limit”
- Improved log file handling and CSC logging for enhanced troubleshooting
- Zero-day protection – An additional data center location for cloud-based machine learning file analysis is now available in Asia Pacific: Sydney, Australia.
- Added QMI driver support for Cellular WAN
- Several important security, performance, and reliability enhancements
- Fixes 85+ field-reported issues
Check out the v18.5 MR4 release notes for full details.
Of course, these new enhancements will also be included in v19 MR1 when it becomes available.
How to get it
The release of v18.5 MR4 follows our regular firmware release process so you can download it now from MySophos or wait until it appears in your console over the next few weeks.
Sophos Firewall OS v18.5 MR4 is a fully supported upgrade from v17.5 MR14 and later, v18 MR3 and later, and all previous versions of v18.5. Please refer to the Upgrade information tab in the release notes for more details.
The importance of updating and upgrading
It is critically important for your network security that you keep all your firewall devices up to date, either on v18.5 MR4 or v19, as every release of SFOS includes important security fixes. We know many customers have devices running old, end-of-life, and unsupported firmware releases that are putting their networks at risk – make sure you check all your Sophos Firewall devices and either update them, upgrade them, or decommission and disconnect them.
If you have XG 85(w) or XG 105(w) devices, they must be upgraded to XGS Series very soon as they are end-of-life and no longer supported as of August 17th, 2022.
Source: Sophos