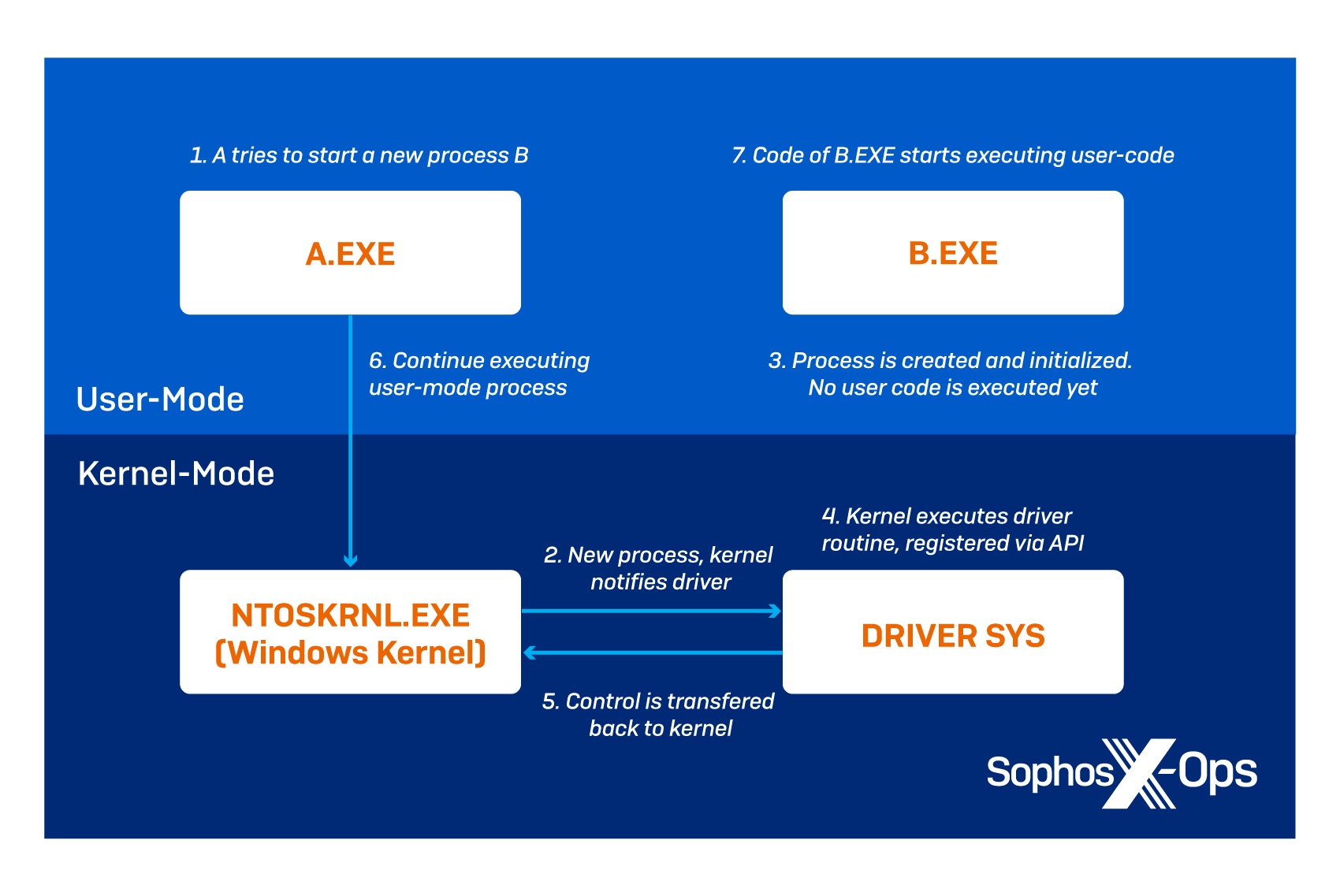
News
IT-SA EXPO&CONGRESS IS EUROPE’S LARGEST TRADE FAIR FOR IT SECURITY…
…and one of the most important dialogue platforms for IT security solutions.
The trade fair covers the entire range of products and services in the field of cybersecurity: hardware, software, training and consulting services as well as Security as a Service. Important topics at it-sa are cloud and mobile security, data and network security, the protection of critical infrastructures, and industrial Security.
Since 2009, it-sa Expo&Congress in Nuremberg has been the meeting place for decision-makers, experts and IT security officers from all sectors of the economy. Whether they represent industry, the service sector or public administration, the exhibitors at it-sa offer customized and individual solutions.

On the exhibitor side, it-sa addresses the entire IT security market, including physical IT security. The event thus offers trade visitors a showcase of the IT security industry from Germany and abroad that is unique in Europe. Outstanding innovations by young companies in the field of cyber security will be honored with the ATHENE Startup Award UP@it-sa.
The freely accessible lecture program and product-neutral contributions and discussion panels from the it-sa insights series provide trade fair visitors to it-sa with the latest expertise in the industry. In addition, the congress program Congress@it-sa, organized in cooperation with renowned associations and organizations, offers an intensive dialogue on current topics in IT security.
NSS’s Executive Director, George F. Kapaniris, visited Europe’s largest cyber security exhibition/conference and had meetings with partners and prominent executives from the cyber security field, including SOPHOS, BeyondTrust, Fortra (HelpSystems), Cherry Solutions and others.
NSS is an international Value Added Distributor of leading edge IT solutions, covering technology areas including information security, networking, unified communications, data storage, virtualization, and data centre infrastructure systems. Through high technology and deep knowledge of the marketplace, NSS executes the due diligence to select leading edge strategic partnerships with superior vendors and leading technologies that give our channel an opportunity to differentiate from the competition in a crowded market through first class proven solutions.



NSS offers its resellers a portfolio of products that integrate to each other ideally for creating innovative solutions. NSS together with the channel partners can develop opportunities and convert them to sales. NSS having developed a circle of trust with the vendors use trade-in options to encourage new business together with the channel. Last but not least, NSS is applying waste management practices in order to dispose of used equipment securely and responsibly, sometimes even helping in acquiring the new equipment offered. NSS Professional services include extensive presales, implementation, configuration and training. NSS has an impressive pool of skilled engineers and consultants to support the VARs.
HelpSystems announced today that it has become Fortra™ a name synchronous with security and defense. This evolution reflects the company’s enhanced commitment to helping customers simplify the complexity of cybersecurity in a business environment increasingly under siege. With a stronger line of defense from a single provider, organizations of all kinds can look to Fortra to increase security maturity while reducing the burdens to everyday productivity.
“The cybersecurity industry is always changing, and we’re evolving along with it,” said Kate Bolseth, CEO, Fortra. “This is a pivotal, exciting moment for us as we’re defining a new, bold path forward that will bring positive change to the industry and our customers. Everyone at Fortra is rallying behind this movement to tackle seemingly unmanageable security challenges and alleviate the constant worry many of our customers face. As Fortra, we want our customers to think of us as their cybersecurity ally, with them every step of the way.”
 In recent years, Fortra has grown to more than 3,000 employees with offices in 18 countries and over 30,000 global customers. As part of this evolution, the company shifted its focus to cybersecurity and automation, building a best-in-class portfolio with key capabilities in data security, infrastructure protection, and managed security services. These acquisitions have included Alert Logic, Digital Guardian, Cobalt Strike, Tripwire, Digital Defense, Terranova Security, Agari, PhishLabs, Core Security, GoAnywhere, Titus, and other well-known software and services providers.
In recent years, Fortra has grown to more than 3,000 employees with offices in 18 countries and over 30,000 global customers. As part of this evolution, the company shifted its focus to cybersecurity and automation, building a best-in-class portfolio with key capabilities in data security, infrastructure protection, and managed security services. These acquisitions have included Alert Logic, Digital Guardian, Cobalt Strike, Tripwire, Digital Defense, Terranova Security, Agari, PhishLabs, Core Security, GoAnywhere, Titus, and other well-known software and services providers.
Such a rich collection of proven solutions has built the organization’s roster of industry experts and enabled innovative integrations to help customers solve challenges in new, streamlined ways. These integrations incorporate emerging threat intelligence for more effective protection against rapidly evolving cyberthreats. In fact, Fortra’s 350-person threat research and intelligence team stays abreast of emerging threats not only to guide customers in their defense efforts, but also to infuse its software and services with critical insights.
“We’re proud of our role as a trusted leader in the industry and will continue to give our customers the same people-first support and best-in-class solution portfolio they’ve come to expect, making cybersecurity stronger and simpler than ever before,” Bolseth said.
HelpSystems Is Now Fortra
The realm of cybersecurity and automation is always changing, and we’re evolving right alongside it. Say hello to Fortra, the new face of HelpSystems. We’re bringing you the same people-first support you’ve come to expect from HelpSystems, only now we’ve been Fortra-fied with the purpose of providing you with exceptional protection and peace of mind along every step of your journey.
Our team of expert problem solvers is ready to find answers to your organization’s toughest problems, and our best-in-class portfolio ensures that we’ll land on an integrated, scalable solution that’s right for you.
We’re tenacious in our pursuit of a stronger, simpler future for cybersecurity.
Who’s with us?

The Fortra Story
Problem solver. Proactive protector. Relentless ally.
These three pillars represent who Fortra is as a positive changemaker for cybersecurity. Our approach is different, and we’re proud of that. We transformed the industry by bringing the leading solutions into one best-in-class portfolio, creating a stronger line of defense from a single provider.
But we know cybersecurity is always changing, and we should never get too comfortable. It’s why our team of experts is dedicated to building leading solutions and adapting to stay ahead of the ever-evolving threat landscape.
We also understand that we’re more powerful together, so we prioritize collaboration with customers. We take the time to listen to each organization’s concerns, and provide the right solutions to help put worries to rest. Because ultimately, we know that the road to creating a stronger, simpler future for cybersecurity begins with the daily commitment of finding better ways to reduce risk while supporting productivity.
We’re Stronger When We’re All Stronger
 At Fortra we’re on a journey to help organizations everywhere realize their full potential. Our Diversity, Equity, and Inclusion (DEI) Council is effecting meaningful change in our organization – change that will make us stronger and enable us to build more equitable communities.
At Fortra we’re on a journey to help organizations everywhere realize their full potential. Our Diversity, Equity, and Inclusion (DEI) Council is effecting meaningful change in our organization – change that will make us stronger and enable us to build more equitable communities.
The right way to do that is to channel the passion, talent, and perspectives of a diverse team. We strive for equity for all and recognize we’re better when we involve everyone, inclusive of age, sex, race, nationality, gender identity, sexual orientation, religious affiliation, parental status, marital status, military service, disability status, neurodiversity, and all other qualities that create unique individuals.
Learn more at Fortra.com
Hackers have a deep playbook for penetrating networks. Even when managed service providers (MSPs) provide their clients with a robust defense, malicious actors can still infiltrate systems to launch ransomware or other attacks.
Small and medium-sized businesses (SMBs) look to MSPs for help because they can’t protect themselves in the face of mounting threats. For example, a recent study showed that ransomware attacks have nearly doubled since 2020, just one of many attack vectors that can severely impact company operations.
While MSPs are increasingly well-versed in cybersecurity measures, they can become overwhelmed. Software tools such as antivirus (AV) and endpoint detection and response (EDR) help them to detect when security issues arise. However, many MSPs do not have the necessary capabilities to carry out threat hunting and incident response for digital forensics investigations and analyzing malware.
Highly trained cybersecurity professionals with the skills to provide advanced threat protection (ATP) are expensive to hire and in high demand. The vast majority of MSPs are not in the position to build up a massive ATP infrastructure and team, but they do have a quality option: managed detection and response (MDR).
Also known as a managed security operations center (SOC), or MDR, managed SOC provides the highest level of threat protection to MSPs and their clients. It combines technology solutions with expert human teams for advanced threat hunting, monitoring and incident response. Armed with MDR, MSPs can identify threats and quickly limit their impact without having to add costly additional staff.
What is MDR? A cybersecurity necessity
The role of managed SOC, or MDR, solutions has evolved significantly in an MSP’s practice. For an increasingly large proportion of SMB clients, MDR has gone from a nice-to-have to a necessity.
This shift is reflected in the core tenets of the NIST cybersecurity framework, a set of interconnected steps for managing risk to critical infrastructure. They are:
- Identify
- Protect
- Detect
- Respond
- Recover
Most organizations today – MSPs, small businesses, IT departments – spend 85% of their budget on “protect”, leaving only a small portion to spend on the other four phases. However, there is a growing awareness that a change in cybersecurity investment is now needed. The leading research firm Gartner recently observed:
“IT risk and security leaders must move from trying to prevent every threat and acknowledge that perfect protection is not achievable. Organizations need to detect and respond to malicious behaviors and incidents, because even the best preventative controls will not prevent all incidents.”
Adding MDR and managed SOC are how MSPs address this reality. For example, protection measures such as AV and firewall may detect malicious files, but additional security must now go far beyond that.
That’s because hackers are increasingly using techniques to infiltrate networks that do not appear malicious on the surface, allowing them to evade defenses. Once a hacker has entered an SMB’s network with this technique, they can dwell unseen in the system, gathering critical information before they strike.
For instance, bad actors know that they can use a normal tool like the Windows PowerShell command-line interface (CLI) for abnormal activities. Working from PowerShell, a hacker can then pull the Mimikatz open-source application to watch for and harvest authentication credentials as packets move through the system. AV software won’t register something like that as a malicious act, but it’s certainly a suspicious one, especially if the commands are originating from a hostile nation.
MDR helps MSPs to spot bad behaviors that get past AV and other traditional protective measures. With a solution like Datto Managed SOC in place, MSPs are alerted of these hidden compromises so they can find, contain and neutralize such an attack before it becomes a major problem.
Better economics
From a security standpoint, MDR makes sense, especially as ransomware gangs and other bad actors become increasingly sophisticated.
Outsourcing MDR to a managed SOC is also the right budgetary choice for an MSP – and often the only feasible option. That’s because building a SOC from the ground up in-house is prohibitively expensive. Without even accounting for the technology infrastructure, the staffing costs can be staggering. In order to run 24/7 a SOC needs at least three expert security analysts, but it reasonably requires several more than that.
However, skilled MDR professionals are in high demand now and are commanding equally high salaries. That leads to a Catch-22 for MSPs who are considering homegrown MDR services: Do you invest heavily in setting up your in-house SOC first and then try and get the clients? Or do you sell clients on it and then try to build up the staff and services to keep your promises? It’s an expensive risk on the one hand, a reputational risk on the other.
The more sensible path for MSPs is to white label their MDR by outsourcing a managed SOC service. That’s how MSPs are responding to this growing need in the market, in a way that they couldn’t do otherwise.
The role of remediation
With MDR in place via a managed SOC, MSPs can go on the offensive by detecting and containing security threats before they spread. This threat hunting is key to cybersecurity remediation, which is the process of identifying and fixing IT security problems. Remediation also involves resolving any issues that might have arisen after a breach.
 Threat hunting is a more mature security activity requiring deep experience in forensics and incident response – initiatives that most MSPs lack the people, training and tools to undertake. The operations of more and more SMBs are transitioning to digital infrastructure, however, meaning that anyone can become a target. That’s because any kind of customer information today has value, so it can be stolen and resold on the dark web.
Threat hunting is a more mature security activity requiring deep experience in forensics and incident response – initiatives that most MSPs lack the people, training and tools to undertake. The operations of more and more SMBs are transitioning to digital infrastructure, however, meaning that anyone can become a target. That’s because any kind of customer information today has value, so it can be stolen and resold on the dark web.
When an MSP offers MDR, cybersecurity becomes proactive. Managed SOC experts are trained to root out bad actors that have infiltrated SMB endpoints and networks and contain those threats. As discussed above, that goes beyond negating the likes of malware, ransomware, distributed denial of service (DDOS) attacks, and phishing: MDR professionals recognize seemingly normal activities that can devastate a business if left unchecked.
Managed SOC is MDR: How to find the right provider
The right MDR ensures that MSPs can instantly extend their team to include world-class personnel who are experts in 24×7 threat monitoring.
MSPs should look for a managed SOC that protects clients across their entire infrastructure including endpoints, networks and the cloud. Efficient log monitoring, threat intelligence and hunting, breach detection, intrusion monitoring, advanced malware prevention, and PSA ticketing should all be included. These features are essential for comprehensive protection and effective remediation that won’t tax MSP personnel.
Improve your security offerings and experience the confidence that comes with continuous protection against attackers. Schedule a demo of Datto Managed SOC.
Source: Datto
I am thrilled to announce the launch of new third-party security technology compatibilities with Sophos Managed Detection and Response (MDR), our industry-leading service that currently secures more than 12,000 customers worldwide.
By integrating data and telemetry from third-party endpoint, cloud, identity, email, firewall, and other security technologies as part of the Sophos Adaptive Cybersecurity Ecosystem, Sophos MDR can better detect and remediate attacks with speed and precision across diverse customer and operating environments.
Compatibility with your complete cybersecurity environment
Recognizing their commitment to Sophos, all Sophos MTR customers will automatically be upgraded–at no additional charge–to Sophos MDR Complete, our top-tier subscription, later this year. We’re grateful to them for their enthusiastic support over these past three years, and we want to continue to exceed their expectations, so we designed Sophos MDR to make the transition completely effortless and transparent.
We’ve also learned a lot from them: The number one request has always been support for third-party products and platforms, including other endpoint solutions. With these new integrations, security data and telemetry from vendors such as Microsoft, CrowdStrike, Palo Alto Networks, Fortinet, Check Point, Amazon Web Services (AWS), Okta, Google, and many others can be automatically consolidated, correlated, and prioritized with insights from the Sophos Adaptive Cybersecurity Ecosystem and our Sophos X-Ops threat intelligence unit.
MDR that meets you where you are
Every organization has some investment in cyber-risk mitigation technology, but no matter the strength of that defense, a determined attacker will eventually defeat technology alone. It’s helpful to use a shield metaphor when thinking about this: shields buy you time when under attack, but you must use that time to react, or your shield will eventually fail. Missed signals or reaction delays due to complex multi-vendor environments can mean the difference between defense success and failure.
Leveraging a comprehensive cross-product set of telemetry, our teams of experts can quickly and accurately detect and remediate threats across the broad range of a customer’s existing environment, including complex, multi-security vendor scenarios, before they turn into something more damaging, like ransomware or a wide scale data breach.
“The approach that many cybersecurity technology providers have taken with their Extended Detection and Response, and their resulting MDR offerings, is to focus on integrating only their own proprietary hardware and software products, resulting in a closed and limited ecosystem offering. The challenge of this approach is that attributes of existing IT architectures may not be negotiable, given the realities of commercial contracts, technical debt, or IT complexity. By expanding its MDR offering to include compatibility with third-party cybersecurity products, Sophos is delivering a more technology-agnostic managed service that truly meets customers where they are and the realities they are forced to embrace.”
Frank Dickson, group vice president, IDC’s Security and Trust research practice
Openness and compatibility have become absolute essentials for effective cyber defenses, and Sophos MDR delivers superior outcomes in the face of today’s challenges.
24/7 threat hunting designed around your business
The need for always-on security operations has become an imperative. However, the complexity of modern operating environments and the velocity of cyberthreats make it increasingly difficult for most organizations to successfully manage detection and response on their own. Sophos MDR is customizable with different service tiers and threat response options. Customers choose the level of response according to their needs:
- Sophos MDR operations team executes full-scale incident response for you
- We co-manage threat response in collaboration with your team
- Your security operations group gets detailed alert notifications and remediation guidance to help them manage threat response
“Unlike many MDR services in the market today, you don’t have to make any compromises with Sophos – you can keep the cybersecurity tools you already have in place, choose what level of support you need, and what outcomes you want to achieve. Sophos is setting a new standard for how MDR should be delivered, and I won’t be surprised when other providers follow in its footsteps.”
Jeremy Weiss, executive technology strategist, CDW
Availability
Integrations with select third-party security technologies will be generally available at no charge by year end. Customers can also purchase additional integration packs for other compatibility, with pricing based on the number of seats.
Get started with Sophos MDR today
To learn more about Sophos MDR and to discuss how we can you stop advanced cyberthreats, speak with a security adviser and get a custom quote today.
Source: Sophos
Sophos received the highest possible rating in the Product Vision, Execution Roadmap, Supporting Products and Services, Efficacy, Threat Intelligence, Zero Trust environments, and IP Sec and VPN criteri.
Sophos is proud to announce our recognition as a Strong Performer in The Forrester Wave™: Enterprise Firewalls, Q4 2022. We were among a select group of companies that were invited to participate in this report, and we believe it is due to the size, strength, and growth of our Sophos Firewall customer base.
Forrester identified the 10 top vendors in the market, conducted a thorough evaluation against 25 criteria, and Sophos tied for the 2nd highest score in the Strategy category.
Sophos received the highest possible rating in the Product Vision, Execution Roadmap, and Supporting Products and Services criteria, all of which were within the Strategy category. We believe this is a testimony to the aggressive execution of our strategy and roadmap that has delivered several ground-breaking releases. These releases include our Xstream Architecture, powerful XGS Series product line with Xstream Flow Processors, and recent addition of Xstream SD-WAN capabilities, providing our customers and channel partners with differentiated industry-leading protection and performance.
According to the Forrester report: “Sophos has a bold near-term vision for hybrid network security…[and has] added both cloud and on-prem ZTNA, building toward a Zero Trust edge architecture.”
Sophos Firewall also received the highest possible marks in the Efficacy and Threat Intelligence criteria. We are continually enhancing the security technology in Sophos Firewall backed by our world-class Sophos X-Ops team which leverages the predictive, real-time, and real-world threat intelligence from SophosLabs, SophosAI, and our Sophos SecOps teams. Together, this collaboration and integration delivers stronger, more innovative protection, detection and response capabilities. Sophos Firewall is also uniquely integrated with our next-gen endpoint, XDR, and MDR platforms to deliver unmatched visibility and response to active threats.
According to the Forrester report: “Sophos excels at efficacy and quarantine… enthusiastic customer references cited the vendor’s integration with its endpoint software that can autoquarantine infected (and missed-heartbeat) hosts.”
In summary, the Forrester report concluded: “Sophos is an excellent fit for small and medium-size businesses with on-premises users or many distributed locations.”
Sophos Firewall and the XGS Series appliances
Sophos Firewall and the XGS Series appliances with dedicated Xstream Flow Processors provide the ultimate in next-gen firewall visibility, protection, and response with SD-WAN application acceleration, high-performance TLS inspection, and powerful machine learning-based threat protection.
Speak to our network security experts to learn more and get a custom quote, or explore the online demo today.
Source: Sophos
We’ve expanded our Managed Detection and Response service (originally called Sophos MTR) and given it a new name: Sophos MDR. Recognizing their commitment to Sophos, Sophos MTR customers will be upgraded–at no additional charge–to Sophos MDR Complete, our top-tier of service, later this year. Customers will enjoy the same great level of service, plus a host of new capabilities including extended data retention and a new monthly threat landscape webcast.
Delivering the No. 1 customer request: compatibility with non-Sophos tools
With Sophos MDR Complete, analysts can detect and respond to threats across the cybersecurity ecosystem by leveraging security data from both Sophos and non-Sophos security tools. Customers can take advantage of:
- Free integrations with Sophos next-gen technologies, including our endpoint, firewall, cloud, and email protection solutions as well as the new Sophos Network Detection and Response (NDR) solution.
- Compatibility to run alongside 3rd party endpoint protection solutions
- Free integration with the Microsoft portfolio through Graph Security
- 3rd party integrations, available for purchase with add-on licenses for virtually any other security tool that generates threat detection data, including Palo Alto Networks, Fortinet, Check Point, Rapid7, Amazon Web Services (AWS), Google, Okta, Darktrace, and many others
The more we can see, the more we can detect and the faster we can respond. With each additional data source, our analysts gain deeper visibility as they begin to see around corners and into the actions taking place beyond the endpoint. By automatically correlating data from Sophos and non-Sophos tools, we can see higher fidelity detections and reduce manual investigation times. And customers get more out of the tools they already have.
There are so many benefits to expanding your detection and response ecosystem to include your existing security solutions. For example:
- Firewall and network telemetry can identify rogue assets and unprotected devices, as well as insider threats and novel attacks
- Email alerts can pinpoint initial entry into the network and attempts to steal account names and passwords
- Identity data can point to unauthorized network entry and attempts to move through higher levels of permissions
- Cloud alerts can indicate unauthorized network access, efforts to steal account names and passwords, and access to proprietary data
Plus much more!
To learn more about our third-party integrations and discuss extending your security defences with full-environment threat detection and response, reach out to your Sophos account team or Sophos partner.
Extended data storage and monthly webcast
For all Sophos MDR service tiers, including Sophos MDR Complete, we are increasing standard data storage to 90 days at no additional cost. With the median dwell time for intrusions not involving ransomware coming in at 34 days*, this extended data storage will better enable analysts to determine the root cause of incidents and, in turn, better advise on how to harden defenses to prevent further attacks. Customers who require a longer data retention period, for example to meet compliance or regulatory requirements, can take advantage of an add-on license for a full year of data storage.
It can be challenging to keep up with the fast pace of security threats. We are excited to introduce an exclusive monthly webcast for MDR Complete customers, the Sophos MDR ThreatCast, where we’ll share observations on recent threat activity across our 12,000+ customer base. Attendees will get to know the team of threat analysts and researchers working behind the scenes to protect their organizations and deepen their understanding of the threat landscape.
Scale incident response
Like Sophos MTR Advanced, with MDR Complete, once suspicious activity is detected, the MDR operations team contains and eradicates the threat. Their systematic approach enables them to identify the root cause and then use these insights to elevate protection across the entire customer base.
We’ll take care of the upgrade for you
All Sophos MTR customers will be automatically upgraded to Sophos MDR Complete later this year. We’ll take care of everything for you – no need to do anything.
Not yet using Sophos MDR?
Sophos MDR meets you where you are. Our expert analysts detect and respond in minutes to threats across your entire environment, 24/7/365, whether you need full-scale incident response or assistance making more accurate decisions. To learn more, visit www.sophos.com/mdr or speak with an adviser today.
Source: Sophos
How to prevent data leakage from insider attacks
Insider threats involve stealing information and conducting malicious activity. A sophisticated insider threat actor may use tools traditionally associated with an external threat. For instance, an insider engaging in malicious behavior could install data-capturing software, exploit a system missing security patches, and access resources using backdoors to conduct data-gathering activity.
Ultimately, we need to recognize insider threats are able to succeed due to at least one of the following:
A. Excessive/inadequately managed privileges (covered in steps 1 – 5 below)
B. Poor security hygiene (vulnerability, configuration management, and audit/log management, covered in steps 5 – 10 below)
With the above (A+ B) in mind, all organizations should implement these security best practices to mitigate insider threat risks:
1. Enforce least privilege and separation of privilege: No one should ever use an administrative account for day-to-day usage (i.e. email, web searches, etc.). This also applies to administrators as the potential risk is much higher should their account be compromised, such as by clicking on a malicious phishing link. All users should be restricted to standard user permissions and only have the ability gain momentary privileged access via controlled and monitored workflows. Privileged Access Management (PAM) solutions are specifically designed to manage this use case.
2. Restrict data access: Only administrators or role-specific employees (not executives) should have access to data en masse. This prevents an insider from dumping large quantities of information, or an executive’s account being hacked and leveraged against the organization to exfiltrate data.
3. Mature identity and access management (IAM) policies: All access to sensitive data should only be for valid employees. Former employees, contractors, and even auditors, should not have routine access. Accounts should be removed or deleted per your organization’s policy. Implement a just-in-time-access model to eliminate standing privileges and ensure all privileged access is finite.
4. Use Enterprise Password Managers: Employees come and go. If the passwords are the same as people leave and new hires are onboarded, the risk to sensitive data increases since former employees technically still have known passwords to the company’s sensitive information. Passwords should be random and unpredictable. Use password management solutions to automate password security best practices via a centralized vault.
5. Implement robust monitoring: Monitoring user behavior and network activity is critical to detecting anomalous, or otherwise dangerous, activity and acting early enough before it causes damage. Privileged activity is especially important to monitor as it poses the most risk for damage and can mean an attack is on its way to quickly escalating. Monitor logs, sessions, keystrokes, and applications and also implement screen recording. If an insider accesses a sensitive system to steal information, session monitoring can document their access and identify how and when they extracted the information. Data loss prevention (DLP) solutions may also help here, but only if the point of egress is considered a risk, or there are regulatory compliance ramifications.
6. Ensure anti-virus or endpoint protection solutions are installed, operating, and stay up-to-date to identify any malware being used by an insider threat.
7. Allow Windows and third-party applications to auto-update, or deploy a patch management solution to apply relevant security patches in a timely manner to remediate the risks of a vulnerability being exploited.
8. Utilize a vulnerability assessment or management solution to determine where risks exist in the environment and correct them in a timely manner so an insider cannot exploit a security weakness.
9. Implement an Application Control solution with Trusted Application Protection (TAP) to ensure only authorized applications execute with the proper privileges to mitigate the risk of rogue, surveillance, or data collection utilities. Ideally, the solution also has fileless threat protection capabilities that can apply context to activities and requests from trusted applications, including blocking child process.
10. Where possible, segment users from systems and resources to reduce “line-of-site” risks. That is, make sure your network is segmented–not flat—to avoid over-reaching access.
Most businesses fail at adequately implementing these basic security controls. However, following the above 10 practices can significantly help protect against insider threats as well as other attack vectors.
Implementing insider threat protection
Insider threats are not going away. The goal is to stop the data leakage and be aware an insider has multiple attack vectors to achieve their goals.
As security professionals, we need to mitigate the insider risks at the source. A briefcase of paper represents an insider threat, but is probably not as relevant as a USB stick with your entire database of client information.
In the end, an insider typically still needs privileges to steal all this information. Removing excessive privileges, such as by implementing privileged access management (PAM) controls and closing open security holes via vulnerability management will help minimize your attack surface from insider exploits, as well as many other types of attacks. In addition to security controls over access, organizations need to layer strong monitoring capabilities for insider threat detection. Finally, training security analysts and other IT staff on insider threat indicators, and how to respond to them, is important in nullifying any active risk.
Source: BeyondTrust
What is an insider threat?
An insider threat is an internal persona acting as a trusted asset (employee, contractor, vendor, partner, etc.) behaving as a threat actor. Typically, the insider exhibits malicious behavior with intent, but sometimes, they are unaware of their actions are directed by an external threat actor. Regardless, the insider misuses their access and privileges for illicit purposes intentionally, or as directed by an external force.
Today, we need to be realistic about what an insider threat is and acknowledge that they have occurred, in various forms, for ages. Years of threat data shows us that insider threats are typically the hardest to detect, while also posing the most potential for damage. By recognizing insider threat indicators, organizations can detect insider attacks faster and prevent, or mitigate, the damage.
The risks of insider threats
By now, most security professionals are well-versed regarding the risks from insider threats. Years ago, these attacks regularly captured news headlines, but today they are the silent threat few organizations want to disclose or publicly admit.
Regardless of the malicious techniques an insider threat actor employs, they are not behaving in the best interest of the company. The insider is potentially breaking the law, and likely exfiltrating information they do not have permission to possess, or performing other damaging actions.
A longstanding example of an insider threat is the stealing of clients lists by a salesperson, executive, etc., who is planning to leave the organization. Perhaps they have photocopied or printed the client lists and purchase orders so they have a competitive edge when starting at their next role with a new employer.
Today, with electronic media, and the Internet, an insider can egresse substantive volumes of data without anyone noticing. And, as a reminder, that file cabinet of sensitive information can fit on a USB thumb drive in a person’s pocket or be posted to a personal cloud-based file share, making the contents even more susceptible to additional threats.
While insider threats are perpetrated with ever-more ease thanks to modern modern technology, it’s a subject most organizations find difficult to discuss.
Human beings will do unusual things in the most dire of situations, but if they are not permitted to, many insider threat risks can be mitigated.
A shortlist representing some of the more interesting and well-documented insider threats include:
- Edward Snowden – NSA insider threat and self-proclaimed whistle blower. (Government)
- Elliot Greenleaf Law Firm – Multiple attorneys extracted and deleted sensitive information (Legal)
- South Georgia Medical Center – A former employee downloaded personal information (Healthcare)
How to assess your vulnerability to insider threats
As we evaluate how to identify and mitigate the risks associated with insider threats, consider these facts regarding your organization:
- How many people have access to sensitive information en masse?
- Who can export large quantities of information from a query or third-party system?
- Are all the active accounts valid?
- Are all accounts related to people that are still employed at the organization or via third parties?
- How do you identify rogue or shadow IT accounts?
- How often do you change the passwords for sensitive accounts?
- Do you monitor privileged access to sensitive systems and data?
In fairness, honestly answering those questions could be opening Pandora’s box. You may not like the answers, or not even know where to begin to get the answers. Nonetheless, you should answer them all if you care about addressing insider threat risk. First, you need to understand your baseline risk and where you should prioritize your next mitigation actions.
Common insider threat indicators & how to detect them
The best way to detect insider threats is to look for indicators of compromise (IoCs) that can be attributed to inappropriate behavior. Sometimes, these can be difficult to detect compared to normal operations, but there is almost always a symptom that will allude to malicious intent.
To that end, consider the following insider threat indicators along with the detection methods:
- Unusual copying, downloading, or movement of sensitive information: This becomes especially concerning when the data or information is moved to an atypical or unauthorized destination. Simply interacting with sensitive data can be an indicator of compromise for unauthorized individuals. This is relatively easy to detect based on identities and access logs. However, if the insider normally and frequently interacts with the data, then it’s the unusual destination that may indicate illicit activity. Destinations can include unauthorized, removable media such as USB drives, cloud-based file storage solutions, and even email.
- Anomalous network search activity: A common assumption is that an insider threat actor knows what data they are looking for and where to find it. That is not always true. Insider threats can be as opportunistic as the next attacker. Malicious Insiders may actively search networks, intranets, ports, applications, etc. for sensitive information that they can extract and leverage. Therefore, monitor for applications and identities performing broad searches and network scans to locate files, buckets, and applications that can give up information as a part of the attack chain.
- Unusual access and login anomalies: If the insider lacks access to data or systems as a part of the business role, but suddenly starts making attempts at access, it could indicate an insider attack is underway. Monitoring authentication and authorization activity is critical to detect for indicators of compromise. If you consider all enterprise assets, consolidation of logs to a SIEM is crucial to gain this perspective. One-off activity will help identify potential anomalies, especially when such access is new. This requires more than just pattern matching in a SIEM and the advanced capability to look for one-time behaviors.
- Misuse of native, or other already installed, tools: Insider threat actors often use tools to help extract information from key systems to satisfy their nefarious missions. Detection of foreign tools can flag an indicator of compromise. However, if the insider is savvy, they may execute a living-off the land (LotL) attack. This entails leveraging native toolsets and other trusted enterprise tools to progress their attack. In that case, behavior becomes the key indicator of compromise. Behaviors to monitor for include access outside of normal business hours, access without proper change control, and network access from unusual or foreign locations. Advanced application control that also protects against fileless threats, such as misuse of trusted applications, is a an important tool for identifying and protecting against these insider threat activities.
Source: BeyondTrust
Sophos, a global leader in next-generation cybersecurity, today announced that BlackByte, one of the newer, “heavy-hitter” ransomware gangs, has added a sophisticated “Bring Your Own Driver” technique to bypass more than 1,000 drivers used by industry Endpoint Detection and Response (EDR) products. Sophos details the attack tactics, techniques and procedures (TTPs) in the report, “Remove all the Callbacks – BlackByte Ransomware Disables EDR via RTCore64.sys Abuse.”
BlackByte, featured in a Secret Service and FBI special advisory earlier this year as a threat to critical infrastructure, reemerged in May from a brief hiatus with a new leak site and new extortion tactics. Now, it appears that the group has added new attack methods, as well. Specifically, they’ve been abusing a vulnerability in RTCorec6.sys, a graphics utility driver for Windows systems. This particular vulnerability allows them to communicate directly with the targeted system’s kernel, commanding it to disable callback routines used by EDR providers, as well as the ETW (Event Tracing for Windows) Microsoft-Windows-Threat-Intelligence-Provider. EDR vendors frequently use this feature to monitor the use of commonly maliciously abused API calls; if this feature is disabled, the EDR vendors that rely on this feature are also rendered ineffective.
“If you think of computers as a fortress, for many EDR providers, ETW is the guard at the front gate. If the guard goes down, then that leaves the rest of the system extremely vulnerable. And, because ETW is used by so many different providers, BlackByte’s pool of potential targets for deploying this EDR bypass is enormous,” commented Christopher Budd, senior manager, threat research, Sophos.
BlackByte is not the only ransomware gang taking advantage of the “Bring Your Own Driver” to bypass security products. AvosLocker abused a vulnerability in a different driver to disable antivirus solutions in May.
“Anecdotally, from what we’re seeing in the field, it does appear that EDR bypass is becoming a more popular technique for ransomware threat groups. This is not surprising. Threat actors often leverage tools and techniques developed by the ‘offensive security’ industry to launch attacks faster and with minimal effort. In fact, it appears that BlackByte pulled at least part of its EDR bypass implementation from the open-source tool EDRSandblast,” said Budd. “With criminals adopting work done by the offensive security industry, it’s critical for defenders to monitor new evasion and exploitation techniques and implement mitigations before these techniques become widely available on the cybercrime scene.”
To learn more about BlackByte’s latest TTPs and how to keep systems safe, download the full report from Sophos.com.
Source: Sophos
This quarter too, we’re happy to present a new version of our software for email archiving. Version 22.3 of MailStore Server and the MailStore Service Provider Edition (SPE) is available right now. The new version officially supports Microsoft Outlook 2021. Once again, we’ve made some tweaks in terms of the security of our software. And, as ever, we’ve done our utmost to improve the overall user experience. It goes without saying that Version 22.3 of MailStore Server and the MailStore Service Provider Edition will also be GDPR-certified.
 New Features for MailStore Server and the MailStore Service Provider Edition
New Features for MailStore Server and the MailStore Service Provider Edition
Find out more about the improvements you can expect in Version 22.3 of MailStore Server and the MailStore SPE.
Support for Microsoft Outlook 2021
Our email archiving solutions have a reputation for supporting the latest mail servers and clients. Following this tradition, MailStore 22.3 now officially supports Microsoft Outlook 2021, which means you can use your MailStore Outlook Add-in with Microsoft’s latest email client. This gives you maximum flexibility and autonomy when it comes to choosing an email client. Email archiving is a long-term solution that aims to safely retain your emails and attachments over many years. So, it’s important for us to know that your long-term investment in MailStore is protected and that our software will remain compatible with all your systems in the future.
More Security
Long-time MailStore customers and partners know that every new version of our product comes with added security. And it’s no different this time. The new version prevents brute-force attacks during the login routine. Failed login attempts, i.e. using incorrect credentials, causes the login process to slow down: fraudsters are unable to deploy brute-force methods and your email archive remains protected.
Even Better Usability
In addition, MailStore 22.3 enhances the experience for MSPs using the MailStore SPE. Admins are now able to modify the automatic execution of profiles on the server via the API. MSPs can adapt and save on system resources. We’ve also improved the login routine of the MailStore Outlook Add-in.
Updated Certification: Meeting Data Privacy Requirements
As usual, the latest version of our software, Version 22.3 of MailStore Server and the MailStore SPE, will be certified by an independent data privacy expert.
The certification will take into account all relevant aspects of the European General Data Protection Regulation (GDPR) and will affirm that, when used appropriately, both MailStore Server and the MailStore SPE meet all the requirements governing the processing of personal data set out in the GDPR.
You can request a copy of the official GDPR audit certificate from sales@mailstore.com shortly. Registered MailStore partners can download the certificates from our Partner Portal or request it by email from partners@mailstore.com soon.
Availability
You can download the new version of MailStore Server and the MailStore Service Provider Edition free of charge from our website.
If your MailStore Server Update & Support Service has expired, please contact us to purchase an upgrade that will allow you to use the latest version of MailStore Server. Read here to find out about other good reasons for having an active Update & Support Service agreement in place.
Interested companies can also download MailStore Server Version 22.3 as part of a free, 30-day trial. If you are an MSP and are interested in offering email archiving as a service based on the MailStore SPE, please contact our sales team at partners@mailstore.com. Alternatively, you can sign up as an authorized MailStore Partner with us right now for free.
Source: MailStore
The reality is that technology solutions alone cannot prevent every cyberattack. Stopping the most advanced attacks requires human-led threat hunting, investigation, and response. Which is where MDR, or managed detection and response, services come in.
MDR is a fully managed, 24/7 service delivered by experts who specialize in detecting and responding to cyberattacks that technology solutions alone cannot prevent.
While threat hunting can be performed in house using EDR (endpoint detection and response) and XDR (extended detection and response) tools, there are extensive benefits to using an MDR service either alongside your in-house team or as a fully outsourced service.
How to work with MDR services
All types of organizations across all sectors use MDR services, from small companies with limited IT resources to large enterprises with an in-house SOC group. There are three main MDR response models:
- MDR team completely manages threat response on behalf of the customer
- MDR team works with the in-house team, co-managing threat response
- MDR team alerts the in-house team and provides remediation guidance
At Sophos we support all three approaches, adapting to individual customer requirements as needed.
Reason #1: Elevate your cyber defenses
One of the major advantages of using an MDR provider over in-house only security operations programs is elevated protection against ransomware and other advanced cyber threats.
An MDR vendor will experience a far greater volume and variety of attacks than any individual organization, giving them a level of expertise that is almost impossible to replicate in house. MDR service providers also have much greater fluency in using threat hunting tools, enabling them to respond more quickly and accurately.
Working as part of a large team also enables analysts to share their knowledge and insights, further accelerating response and developing ‘community immunity’ i.e. where learnings from one organization are applied to others with a similar profile.

Reason #2: Free-up IT capacity
Anecdotally, the biggest benefit reported by IT teams on adopting Sophos MDR is that it frees them up to support business-focused initiatives.
Threat hunting is time-consuming, and unpredictable work that often prevents IT teams from focusing on more strategic projects. Organizations using Sophos MDR report considerable IT efficiency gains from using our service, which in turn enables them to better support their organization’s goals.
Reason #3: Get 24/7 peace of mind
With malicious actors located around the globe, an attack can come at any time. By providing 24/7 coverage, MDR services provide considerable reassurance and peace of mind.
For IT teams this means — literally — being able to sleep better at night. They can relax knowing that the buck stops with the MDR provider. For senior leaders and customers, 24/7 expert coverage and a high level of cyber readiness at all times provides powerful reassurance that their data and the organization itself are well protected.

Reason #4: Add expertise, not headcount
Threat hunting is a highly complex operation. Individuals in this space need to possess a specific and niche set of skills, which makes recruiting threat hunting expertise an uphill task for many organizations. MDR services provide the expertise for you. At Sophos, we have hundreds of expert analysts that provide continuous MDR services to customers across the globe.

Reason #5: Improve your cybersecurity ROI
Maintaining a 24/7 threat hunting team is expensive, requiring at least five or six full-time staff. MDR services provide a cost-effective way to secure your organization and stretch your cybersecurity budget further. Plus, by elevating your protection, MDR services also greatly reduce the risk of experiencing a costly data breach and avoid the financial pain of dealing with a major incident.
If you use an MDR vendor that also offers endpoint – and other – cybersecurity offerings you can enjoy considerable TCO advantages from consolidating with a single provider as well as streamlining your vendor management efforts. Furthermore, by choosing a vendor that enables you to leverage your existing investments you can increase the ROI on existing spend.

Learn more
To learn more about the top benefits reported by organizations that use MDR services, download our whitepaper here.
Sophos MDR is the world’s most trusted MDR service, securing over 11,000 organizations against the most advanced threats, including ransomware. With the highest rating on Gartner Peer Insights and the Top Vendor recognition in the 2022 G2 Grid® for MDR services serving the midmarket³, with Sophos MDR your cyber defenses are in good hands.
For more information and to discuss how it can help you, speak with one of our advisors or visit www.sophos.com/mdr today.
Sophos: Sophos
We’ve just released the State of Ransomware in State and Local Government 2022 report, which offers fresh insights into ransomware attack rates, costs and recovery, and ransom payouts in state and local government organizations over the last year.
The report is based on our annual study of the real-world ransomware experiences of IT professionals, of which 199 respondents belonged to the state and local government sector, working in mid-sized companies (100-5,000 employees) across 31 countries.
The study reveals an increasingly challenging threat environment with state and local government reporting an above-average increase in the perceived volume of attacks and the impact of attacks. It also sheds light onto the relationship between ransomware and cyber insurance, including the role cyber insurance is playing in driving changes to cyber defenses.
Here are the key findings from the report:
- 58% of state and local government organizations were hit by ransomware in 2021, up from 34% in 2020 – an increase of 70% over the course of a year
- At the same time, the sector reported one of the lowest ransomware attack rates, at 58% compared to the cross-sector average of 66%
- State and local government reported one of the highest data encryption rates following ransomware attacks: 72% in state and local government vs 65% across sectors
- Only 20% said they were able to stop an attack before the data could be encrypted, considerably below the cross-sector average of 31%
- Just 63% of state and local government organizations whose data was encrypted used backups to restore data compared to the cross-sector average of 73%
- 32% of state and local government organizations paid the ransom to restore encrypted data – the lowest reported ransom payment rate across all sectors and considerably below the global average of 46%
- The average ransom payment by state and local government organizations was less than one-third of the cross-sector average: $213,801 in state and local government vs $812,360 across sectors
- On average, only 58% of encrypted data was recovered by state and local government, lower than the cross-sector average recovery rate of 61%
- State and local government organizations reported the lowest recovery cost of all sectors at $0.66M. This represents a drop of almost $1 million from the average cost of $1.64M reported by the sector the year prior. In comparison, the cross-sector average cost was US$1.4M.
- 80% of state and local government organizations reported having cyber insurance coverage against ransomware, lower than the cross-sector average of 83%
- Cyber insurance is driving state and local government organizations to improve cyber defenses: 96% have upgraded their cyber defenses to secure coverage
- State and local government organizations reported the lowest clean-up payout rate of 44%, considerably lower than the cross-sector average of 77%. The sector reported an above-average rate of ransom payout by insurance providers, with insurers paying out in almost half (49%) of incidents compared to the cross-sector average of 40%
The increasing rate of ransomware attacks in state and local government demonstrates that adversaries have become considerably more capable of executing attacks at scale by successfully deploying the ransomware-as-a-service model.
Most state and local government organizations are choosing to reduce the financial risk associated with such attacks by taking out cyber insurance. For them, it is reassuring to know that insurers pay some costs in almost all claims.
However, it is getting harder for organizations – especially in the state and local government sector – to secure coverage. This has driven almost all state and local government organizations to make changes to their cyber defenses to improve their cyber insurance positions.
Read the full report: The State of Ransomware in State and Local Government 2022
Sophos: Sophos
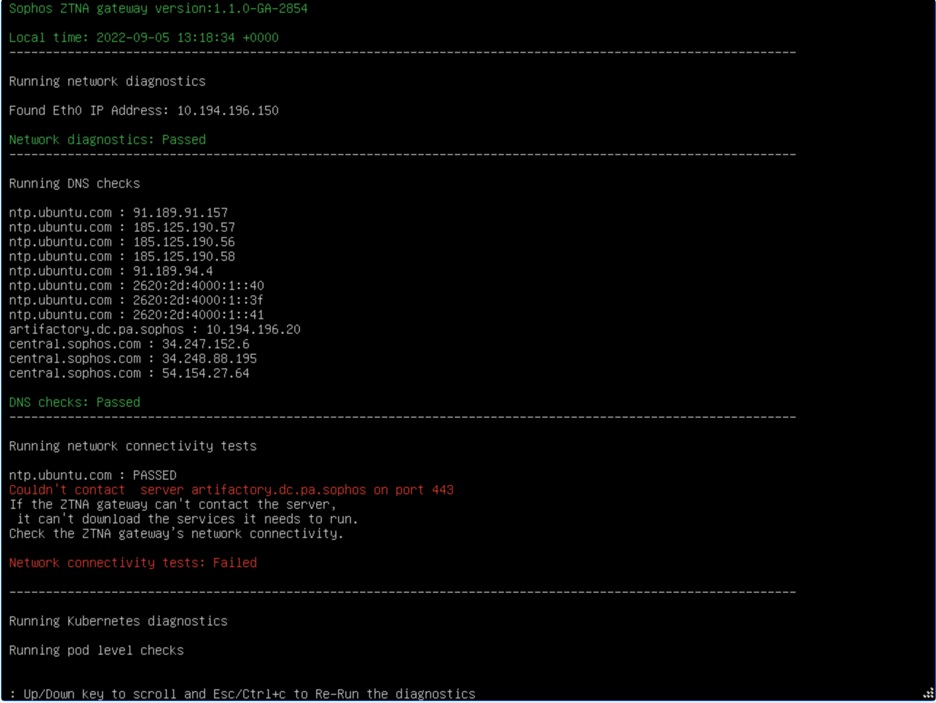
Sophos Zero Trust Network Access is now available with gateway support for the Microsoft Hyper-V 2016 platform and above. This release also introduces troubleshooting and scalability enhancements with an increase in tunnel capacity from 1,000 to 10,000 clients per node, representing a ten-fold increase.
New to this release:
- Hyper-V support
- Troubleshooting via console diagnostics
- Capacity enhancements
- SaaS application access with Synchronized Security
Hyper-V 2016+ support
Hyper-V support expands the ZTNA gateway deployment options considerably by including Microsoft’s very popular hypervisor platform. Download the new ZTNA gateway image for Hyper-V from the ZTNA Gateways area in Sophos Central. Click “Download gateway V”’ at the top of the screen.
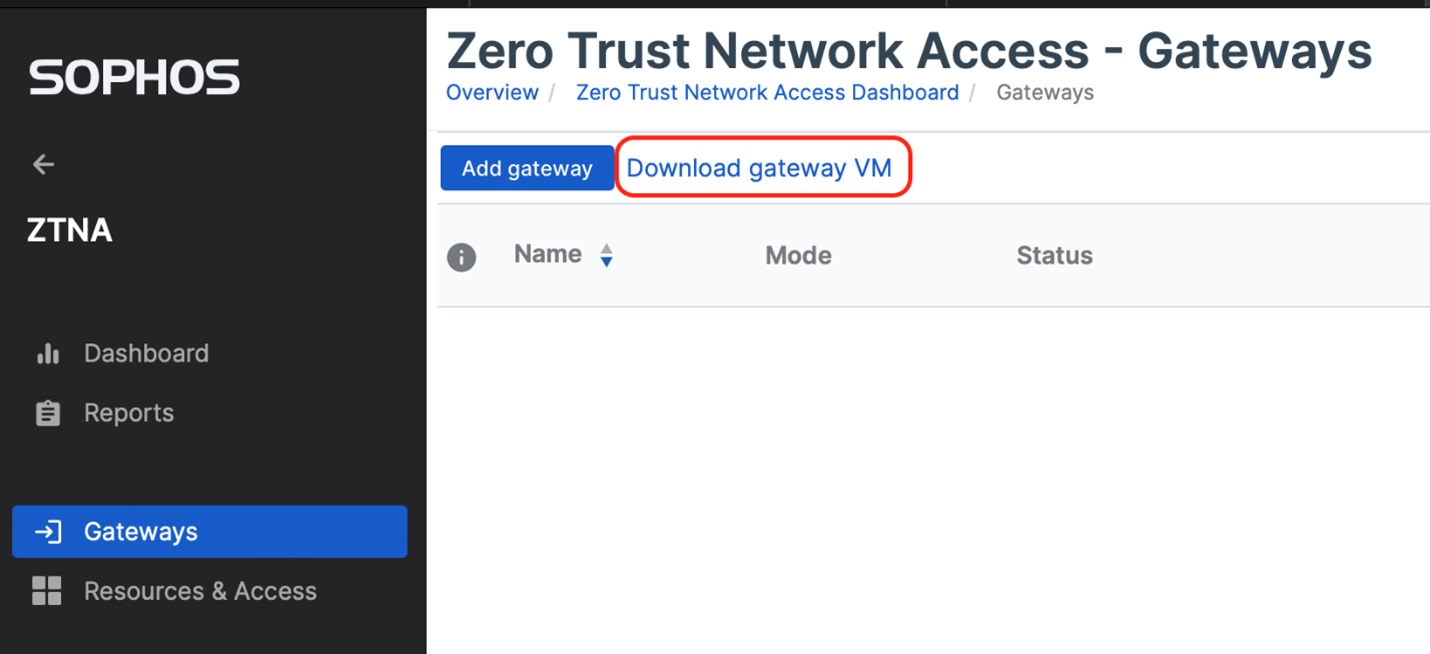
The virtual gateway is also accessible from the “Protect Devices” menu in Sophos Central.
Troubleshooting via console diagnostics
One of the most frequently requested enhancements, which comes with this release, is support for troubleshooting via console diagnostics on the ZTNA gateway.
Users can access the console and run pre-defined diagnostics tests to troubleshoot connectivity or other issues preventing a gateway from being managed via Sophos Central. A brief explanation will be displayed on the console itself. Check out the ZTNA troubleshooting guide for further information.
Node capacity and scaling enhancements
Client capacity has been significantly enhanced in this release. Sophos ZTNA gateways with a single VM node (using 2 cores and 4 GB of RAM) now support up to 10,000 clients, and the maximum cluster of 9 nodes supports up to 90,000 clients. This represents a ten-fold increase over the previous version.
Existing deployments should update their gateway firmware to take advantage of this enhanced capacity.
Zero trust access to SaaS applications
ZTNA takes advantage of the simplicity of SaaS-based IP access enforcement and provides a new method for controlling access to SaaS applications.
ZTNA routes SaaS application traffic via the ZTNA gateway and provides several security benefits.
- Visibility into SaaS access: visibility and reporting from application access to SaaS and private applications.
- Enforcement: control what users and access methods are allowed to SaaS apps with a zero-trust approach.
- Dynamic access with Synchronized Security: automatically isolate and gate access from infected endpoints to stop threats from spreading and impacting data in SaaS applications and private applications.
To take advantage of this feature, your SaaS applications must support IP access controls. Whether your users are working remotely or in the office, ZTNA ensures that only verified users and healthy devices can access your important SaaS applications. While this is not a replacement for a full-featured CASB solution, it does provide additional controls and security enhancements for your SaaS applications and data.
Find out more in the ZTNA user documentation.
New to Sophos ZTNA?
If you’re new to Sophos ZTNA and want to learn more, head over to Sophos.com/ZTNA to learn why ZTNA is the ideal remote-access solution to securely connect users to your networked applications.
- Download our latest whitepaper on the Top Six Advantages of ZTNA
- Watch a video on Remote Access VPN vs ZTNA
- Get the latest ZTNA datasheet
Source: Sophos
The retail sector is no exception when it comes to the growing ransomware challenge that other industries face today. Retail saw the second highest rate of ransomware attacks across sectors, with two in three organizations reporting data encryption following a ransomware attack.
We’ve just released the State of Ransomware in Retail 2022 report, which offers fresh insights into ransomware attack rates, costs and recovery, and ransom payouts by retail organizations over the last year.
The report is based on our annual study of the real-world ransomware experiences of IT professionals, of which 422 respondents belonged to the retail sector, working in mid-sized companies (100-5,000 employees) across 31 countries.
The study reveals an increasingly challenging attack environment, with retail https://vimeo.com/744259875reporting an above-average financial and operational impact of ransomware attacks. It also sheds light onto the relationship between ransomware and cyber insurance, including the role cyber insurance is playing in driving changes to cyber defenses.
Here are the key findings from the report:
- Retail reported a 75% increase in the rate of ransomware attacks over the last year: 77% of organizations were hit in 2021, up from 44% in 2020
- The increased attack rate is part of a cross-sector, global trend. The retail sector reported the second-highest rate of ransomware attacks across all sectors
- Retail experienced an above-average rate of data encryption at 68%; for comparison, the global average was 65%
- Only 28% of retail respondents said they were able to stop an attack before data could be encrypted – below the global average of 31%
- 49% of retail organizations paid the ransom to restore data – higher than the global average of 46%
- The amount of data restored by retail after paying the ransom dropped from 67% in 2020 to 62% in 2021. Following the same trend, the percentage of retail organizations that got ALL their encrypted data back went down from 9% in 2020 to 5% in 2021. For comparison, the global average in 2021 was 4%.
- The average ransom payment by retail was less than one-third of the cross-sector average: $226,044 in retail vs $812,360 across sectors
- The overall cost to remediate a ransomware attack for retail organizations dropped over the last year, down from US$1.97M in 2020 to US$1.27 in 2021. The cross-sector average was US$1.4M, for comparison.
- 88% of retail organizations reported having cyber insurance coverage against ransomware – the second highest rate across all sectors, compared with the cross-sector average of 83%
- Cyber insurance is driving retail organizations to improve cyber defenses – 97% in retail have upgraded their cyber defenses to secure coverage
- Retail reported a below-average rate of ransom payout by insurance providers at 35% compared to the cross-sector average of 40%
The increasing rate of ransomware attacks in retail demonstrates that adversaries have become considerably more capable of executing attacks at scale by successfully deploying the ransomware-as-a-service model.
Most retail organizations are choosing to reduce the financial risks associated with such attacks by taking cyber insurance. For them, it is reassuring to know that insurers pay some costs in almost all claims. However, the sector has one of the lowest ransom payout rates by cyber insurers.
It is getting harder for organizations, especially in the retail sector, to secure coverage. This has driven almost all retail organizations to make changes to their cyber defenses to improve their cyber insurance positions.
Read the full report: The State of Ransomware in Retail 2022
Source: Sophos
Kaseya, the leading global provider of unified IT management and security software for managed service providers (MSPs) and mid-market enterprises (MMEs), opened DattoCon in person following a three-year pandemic-induced hiatus.

The conference attracted over 2.700 from 29 countries and was held September 11-13th at the Walter E. Washington Convention Center in Washington, D.C. Kaseya CEO Fred Voccola joined by leaders from Datto, articulated the strategic direction of Datto and unveiled a host of innovations, including the latest additions to the security portfolio available for Datto Partners to offer to their customers.
“We are super excited about this year’s DattoCon and sharing with our partners, how much stronger we are as a result of Kaseya and Datto coming together,” said Voccola. “We’re also happy to have everyone back together for the first in person DattoCon since the pandemic – this will be a tremendous opportunity for networking, learning and some fun!”

Fred Voccola shared the vision behind combining Datto and Kaseya and highlighted exciting new developments, including new product innovations and enhanced pricing options for Datto partners during his CEO keynote address. A big message during Monday’s start of DattoCon 2022 was helping MSPs make the most of the massive market opportunity with SMBs by reducing their pain points.
Kaseya is going to make Datto more affordable and help MSPs and address challenges like “vendor fatigue.” That’s according to Fred Voccola, Kaseya’s CEO. He addressed MSPs during the start of this week’s DattoCon 2022 in Washington, D.C. More than 2,700 attendees are at the conference.

Voccola said Datto‘s Autotask is the best professional services platform (PSA), and its remote monitoring and management (RMM) “rocks.” He also said MSPs will see an average 15% reduction in the cost of Datto solutions. “Is Kaseya going to force a change in commercial terms?” Voccola said. “Absolutely not, we’re not changing any terms of existing licensing deals. We will continue the existing business models and offer enhanced savings for longer-term commitments.” MSPs are suffering from vendor fatigue in that the average MSP is working with 17 vendors, he said. That’s “too much overhead and a pain in the butt.” Kaseya and Datto coming together can potentially reduce that from 17 to one, “greatly reducing complexity in managing vendors,” Voccola said. “We address this with workflow integrations,” he said. “Because we own the platform and control the road map, we’re able to deliver hundreds of deep integrations, adding about 25 per month, on top of lightweight integrations we have.”

It’s now been 10 weeks since Kaseya completed its $6.2 billion acquisition of Datto. The deal has generated controversy from MSPs concerned Datto will change for the worse as a result. Voccola (pictured on stage above) said Datto plus Kaseya is “100% focused” on partner-centricity. “Our company exists to serve the MSP community,” he said. “This company only succeeds when you succeed. We recognize everything we do is built around that fact.”
With the Datto acquisition, the combined company is making a $14 billion investment in the MSP community.
Voccola said Kaseya and Datto coming together is “transformational” for the industry. “But us as a company, we’re going to make mistakes, but we’re going to do more things right than wrong,” he said. “And our strategy is invest a ton of resources in … what we believe is needed to make MSPs successful.”
Kaseya didn’t buy Datto to create value by cutting costs and maximizing earnings, Voccola said. “Our investment thesis is one of growth, and growth requires investment,” he said. Kaseya already has added 65 people in R&D and plans to add an additional 100 in the months ahead, Voccola said. Also, January 1 of this year, there were 826 bodies in software development. Today, there’s 891. By the end of the year, we are hoping to have a little over 1,000 people, he said.
“We are giving the ammunition, the resources to the people who design really awesome products so they can do more,” he said. “This isn’t something that’s going to backtrack if the global economy slows down.” Kaseya has worked to commercially integrate new products from the Datto acquisition. And Kaseya will integrate all of Datto by January, Voccola said. “There are already six workflow integrations completed, and we’ll be adding 30 in the coming weeks, all done within IT Complete,” he said.

Datto’s global partner program is expanding, offering more partners the ability to participate in the MSP growth-oriented program. This includes doubling market development funds (MDF) and tripling global partner program personnel. Attendees also got a preview of multiple innovations the company is planning, including Datto Managed SOC, powered by RocketCyber; Datto EDR; and Datto Secure Edge, a SASE offering. These solutions allow users to securely connect from anywhere and access sensitive data in the cloud, the company said.
Source: Datto, Channel Futures, Channel Futures and CRN
Did you know that human mistakes are to blame for 95% of all cybersecurity breaches?
Cyberattacks can affect any firm, regardless of size. To launch these attacks and access an organization’s computer systems, hackers are employing increasingly complex methods. Depending on your location, you may be required to follow specific cybersecurity regulations to demonstrate that your essential assets are protected.
If you don’t, you could face high fines and legal difficulties if your data is exposed as a result of a system breach. As a result, there’s a lot of pressure to comply with these stringent cybersecurity laws and regulations.
Read on to find out more.
What does cybersecurity regulatory compliance mean?
Cybersecurity regulatory compliance entails adhering to several measures to safeguard data confidentiality, integrity, and accessibility.
Cybersecurity standards vary depending on the industry and sector, but they often require the use of a variety of organizational processes and technology to protect data.
The CIS, the NIST Cybersecurity Framework, and ISO 27001 are just a few security frameworks and sources of controls.
Major government cybersecurity regulations
For smooth operations, your business needs to be compliant with the law. Some major government and banking cybersecurity compliance regulations include:
HIPAA
HIPAA is an acronym for the Health Insurance Portability and Accountability Act. Approved in 1996, this legislation contains restrictions to ensure the privacy, integrity, and accessibility of Personal Health Information (PHI).
HIPAA involves healthcare cybersecurity regulations that apply to healthcare providers, health plans, and others who manage PHI. If you’re not sure if HIPAA applies to you, we recommend speaking with an attorney with regulatory compliance experience.
GDPR
The General Data Protection Regulation (GDPR) is a set of data privacy policies that the European Union introduced in 2018 to coordinate data privacy laws across Europe.
All EU member states, the European Economic Area (EEA), and personal data transfers beyond the EU and EEA are covered by the GDPR. This means that GDPR obligations apply to any firm that collects data or targets individuals in the EU, regardless of its location.
The GDPR’s principal goal is to give individuals more control over their data while simultaneously unifying EU legislation to make the regulatory environment easier for transnational businesses. The GDPR specifies guidelines for personal data protection, data minimization, and security.
FERPA
The Family Educational Rights and Privacy Act, or FERPA, is a federal statute that protects the confidentiality of student educational data. All institutions that receive financing from the US Department of Education are subject to this law.
FERPA provides parents, students over the age of 18, and students attending colleges, universities, or trade schools with specific rights and safeguards regarding their educational records.
CCPA
The California Consumer Privacy Act (CCPA) is a state statute enacted to strengthen the privacy rights and consumer protections of California residents. Taking effect in 2020, this was the first law in the United States to provide comprehensive data privacy laws, similar to the GDPR in the European Union.
The CCPA applies to any California-based corporation that generates at least $25 million in annual revenue, makes more than 50% of its revenue from user data collection, or collects data on more than 50,000 users. This includes any corporation that collects or sells personal information from California users, regardless of the location.
Although these four above are some of the most well-known regulations there are lots more out there so it’s always important to check your local regulations with a legal professional.
4 tips for cybersecurity regulatory compliance
Cybersecurity compliance is a core part of any business. To keep up with relevant cybersecurity rules and regulations so you can be compliant, here are some basic steps.
1. Identify what requirements may apply
To start working toward cybersecurity regulatory compliance, you must first determine which regulations or laws you must follow. To begin with, data breach notification regulations exist in every state in the United States, requiring you to tell customers if their personal information is compromised.
For example, regardless of which state your firm is in, if your business deals with the financial information of a New York resident, you would be subject to the NYDFS Cybersecurity Regulation’s set of standards.
Furthermore, the California Consumer Privacy Act and the New York Department of Financial Services Cybersecurity Regulation impose restrictions that may apply to your firm based in any state if you deal with data covered by these laws.
2. Implement policies, procedures, and process controls
It’s not only about technology when it comes to cybersecurity regulatory compliance. It’s also critical to have risk-mitigation policies and processes in place for both compliance and safety.
There is no technical precaution in the world that can prohibit a committed employee from downloading malware onto company systems or visiting unsafe websites.
3. Conduct risk and vulnerability assessments
Almost every significant cybersecurity compliance obligation necessitates a thorough risk and vulnerability analysis. These are crucial in determining the most serious security issues in your organization, as well as the controls you already have in place.
When doing vulnerability assessments, it’s also important to think about your risk of ransomware attacks.
4. Review and test
Examine any applicable government cybersecurity rules that must be followed, and make sure to test your controls regularly. It’s easy to lose track of cybersecurity laws and regulations as firms grow and develop, but regular testing can help you stay on track.
It’s a good idea to keep an eye on compliance as new standards emerge and existing ones change, and to test both technological and process controls regularly. If you are unsure whether you are meeting a compliance requirement, we recommend consulting with a cybersecurity compliance attorney.
How Datto can help
The sort of data you manage, your industry, your regulatory body, and the geographic boundaries in which you operate all influence your regulatory responsibilities.
However, you should speak with a compliance consultant or an attorney to determine the specific cybersecurity regulations that apply to your company.
Contact us if you or your business requires assistance in dealing with cybersecurity compliance obligations. We will be pleased to address any questions you may have about our services.
Source: Datto
With perimeter boundaries quickly blurring thanks to remote care and telehealth, the implicit trust placed in perimeter-centric security makes healthcare dangerously vulnerable.
The Sophos State of Ransomware in Healthcare 2022 report revealed a 94% increase in ransomware attacks on healthcare year over year, with 66% of healthcare organizations getting hit by ransomware in 2021.
Furthermore, 61% of these attacks resulted in data encryption, making healthcare data unavailable until the victims paid ransom or restored their systems. Such attacks can prove deadly as they disrupt patient care and safety.
So, healthcare today is as much about securing patient data as it is about providing effective patient care.
It’s a challenge for caregivers, remote healthcare workers, and outsourced staff who need access to such data to provide uninterrupted and remote patient care.
Not only do they need to contend with multiple industry regulations that regulate the use of protected health information (PHI), including the Health Insurance Portability and Accountability Act (HIPAA), but there’s also a labyrinth of access and authentication complexities as well.
The industry is moving to cloud-based apps and services while also witnessing a proliferation of IoMT devices, telehealth, remote patient monitoring, portable medical devices, augmented reality, and robotics – all of which use existing IT infrastructure and legacy security technologies, resulting in a broader attack surface.
Most attacks on healthcare organizations exploit the inherent trust and unrestricted access given to the users and devices that are protected by traditional perimeter-based security.
With perimeter boundaries quickly blurring thanks to remote care and telehealth, the implicit trust that organizations place in their perimeter-centric security makes them dangerously vulnerable.
ZTNA – or zero trust network access – makes healthcare IT more effortless and secure by verifying user identity, device health, and access policy before seamlessly granting access to network resources. It only connects users to very specific applications or systems, not the entire network.
ZTNA eliminates vulnerable VPN clients and can prevent compromised devices from connecting to applications and data, effectively preventing lateral movement and attacks like ransomware from getting a foothold on the network.
With Sophos ZTNA, you get the added benefit of a single-agent, single-console, single vendor solution for both ZTNA and your next-gen endpoint protection.
Sophos ZTNA uniquely integrates with Sophos Intercept X endpoint protection to constantly share status and health information and can automatically isolate compromised systems and prevent threats from moving or stealing data.
Sophos ZTNA removes implicit trust in your healthcare organization’s applications, users, and devices and provides segmented access to your systems and resources only to those who need it.
Learn more at Sophos.com/ZTNA.
Source: Sophos
[vc_row][vc_column width=”1/1″][vc_single_image media=”103038″ media_width_percent=”100″][vc_empty_space empty_h=”2″][vc_button button_color=”color-150912″ size=”btn-xl” border_animation=”btn-ripple-out” custom_typo=”yes” font_family=”font-762333″ font_weight=”900″ letter_spacing=”fontspace-210350″ border_width=”2″ display=”inline” link=”url:mailto%3Asales%40nss.gr%3Fsubject%3DSophos%20XGS%20Architect%20Training%26body%3DI%20would%20like%20to%20participate%20in%20the%20XGS%20Architect%20Training%20on%20the%2021st%20and%2022nd%20of%20September%202022||target:%20_blank|” icon=”fa fa-hand-o-right”]Book Your Training Today![/vc_button][vc_button button_color=”color-283957″ size=”btn-xl” border_animation=”btn-ripple-out” custom_typo=”yes” font_family=”font-377884″ font_weight=”900″ letter_spacing=”fontspace-210350″ border_width=”2″ display=”inline” link=”|||” icon=”fa fa-volume-control-phone”]Call us now for more +30 211 8000 330[/vc_button][vc_separator sep_color=”color-210407″][/vc_column][/vc_row][vc_row row_height_percent=”0″ back_color=”color-210407″ overlay_alpha=”50″ gutter_size=”3″ column_width_percent=”100″ shift_y=”0″ z_index=”0″][vc_column width=”1/1″][vc_custom_heading heading_semantic=”h1″ text_font=”font-377884″ text_size=”h1″ text_weight=”200″ text_color=”color-xsdn”]Sophos XGS Architect Training [/vc_custom_heading][/vc_column][/vc_row][vc_row][vc_column][vc_column_text]
Wednesday, September 21 & Thursday, September 22
(2 days crash Training / NSS Training Center – on premises)
A two-days crash training program which is designed and intended for experienced technical professionals who want to install, configure and support the XGS Firewall in production environments and is the result of an in-depth study on the next generation firewall of Sophos.
Trainer: Micheal Eleftheroglou
Training room: NSS ATC training room 3rd floor
Requirement
- XGS Firewall _ Certified Engineer course and delta modules up to version 18.5
Recommended Knowledge
- Knowledge of networking to a CompTIA N+ level
- Knowledge of IT security to a CompTIA S+ level
- Experience configuring network security devices
- Be able to troubleshoot and resolve issues in Windows networked environments
- Experience configuring and administering Linux/UNIX systems
Content
- Module 1: Deployment
- Module 2: Base firewall
- Module 3: Network Protection
- Module 4: Synchronized security
- Module 5: Web server Protection
- Module 6: Site to site connections
- Module 7: Authentications
- Module 8: Web Protection
- Module 9: Wireless
- Module 10: Remote Access
- Module 11: High Availability
- Module 12: Pulic Cloud
Certification
+ exam: Sophos XGS Architect
Duration 2 days
Language: Greek & English
[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column width=”1/1″][vc_separator sep_color=”color-210407″][vc_empty_space empty_h=”2″][vc_button button_color=”color-150912″ size=”btn-xl” border_animation=”btn-ripple-out” custom_typo=”yes” font_family=”font-762333″ font_weight=”900″ letter_spacing=”fontspace-210350″ border_width=”2″ display=”inline” link=”url:mailto%3Asales%40nss.gr%3Fsubject%3DSophos%20XGS%20Architect%20Training%26body%3DI%20would%20like%20to%20participate%20in%20the%20XGS%20Architect%20Training%20on%20the%2021st%20and%2022nd%20of%20September%202022||target:%20_blank|” icon=”fa fa-hand-o-right”]Book Your Training Today![/vc_button][vc_button button_color=”color-283957″ size=”btn-xl” border_animation=”btn-ripple-out” custom_typo=”yes” font_family=”font-377884″ font_weight=”900″ letter_spacing=”fontspace-210350″ border_width=”2″ display=”inline” link=”|||” icon=”fa fa-volume-control-phone”]Call us now for more +30 211 8000 330[/vc_button][vc_single_image media=”103038″ media_width_percent=”100″ alignment=”center”][/vc_column][/vc_row]
Before trying to better understand what enterprise data security is, it’s best to know the meaning of data security in a broader sense. In essence, data security is everything that surrounds the protection of digital data from destructive forces or unwanted actions of unauthorized users, such as from a cyberattack or data breach. Data security should be a priority for just about any business or organization from mom-and-pop shops to mid-market companies; cyberattacks and data breaches do not discriminate.
The same can be said for large enterprises with several thousand employees, though, and oftentimes, the consequences of a security incident can be even more damaging due to the nature of the data those organizations handle. Enterprises like hospitals, financial institutions, and manufacturers create, transfer, and store particularly sensitive information that, in the eyes of cybercriminals, can be far more lucrative. In this way, because enterprises require specific solutions that can handle the sheer volume and sensitivity of the data they manage, enterprise data security is often considered a highly calculated and sophisticated form of data security.
Why Does Enterprise Data Security Matter?
What often separates a security incident experienced by an enterprise from a security incident experienced by a small- or mid-size organization is the scale of the impact. For example, if a small retail business is hit with a ransomware attack, there’s no doubt that the business would need to find a means of restoring operations, whether that means paying the ransom or finding another means of stopping the attack, but the attack wouldn’t necessarily have immediate, negative repercussions for the business’ customers. On the other side of that coin, however, if an enterprise like a hospital were to be hit with that same ransomware attack, highly sensitive information like health records, financial information, social security numbers, and more could be put at risk, but more importantly, the health of patients could be put in immediate jeopardy.
In short, enterprises and their daily operations are often considered essential to the point that any disruption, breach, or attack could cause immediate, severe complications for many. That reality, in combination with the sharp rise in hybrid work environments and remote collaboration, means data is less static than ever before, there are higher chances of an accidental data breach occurring, and more attack vectors are available for criminals to exploit. As a result, enterprise data security solutions should protect data throughout its entire life cycle and must be as comprehensive and far-reaching as possible to ideally prevent security incidents from ever occurring.
Common Pain Points in Enterprise Data Security
Choosing the Right Solutions
Choosing the right data security solution(s) can be a daunting task in and of itself, particularly for enterprises that are only just beginning to ramp up their security efforts. Are there any already-known weak points in your data’s life cycle, and could any of that data cause your enterprise harm if compromised? Does your enterprise already have other security solutions in place? These are all questions worth exploring before attempting to find more solutions to add to your security plan. Otherwise, you may find that your newly implemented solutions cause more headache than protection.
Data Visibility
Data visibility remains one of the most common pain points in enterprise data security, with a whopping 63% of respondents from our 2022 CISO Perspectives: Data Security Survey reporting that it is their organization’s biggest security challenge. Particularly for large enterprises, whose thousands of employees handle sensitive data daily, being able to locate where that data moves can be a tricky task without the proper solutions in place. If those enterprises don’t know where their sensitive data lies, adequately protecting it from getting into the wrong hands becomes far more difficult, if not nearly impossible. Data protection solutions like data classification, data loss prevention (DLP), and digital rights management (DRM) can help to identify sensitive data, track it wherever it goes, and even revoke access in real-time in case of a breach.
Ease of Use
For security solutions to be effective in practice, they should be easy for employees to implement in their workflows, work with your enterprise’s existing security framework, and integrate with one another if several solutions are being used together. Unfortunately, security solutions aren’t always easy to use , so it’s always best to explore all your options, take advantage of solutions that automate complicated processes when possible, and ensure that implementing a given solution won’t place significantly more work on your employees’ shoulders.
Threats Outpacing Security Initiatives
Circling back to our 2022 CISO Perspectives: Data Security Survey, 52% of respondents claim that cyber threats have become fiercer in the past year. Creating and implementing a data security strategy within a large enterprise can be a lengthy process, and because the threat landscape is ever-growing, “catching up” to those threats before an attack actually occurs can feel like an impossible task. Even so, rushing to create and implement a data security plan without taking time to weigh all your options could turn out to be just as dangerous. The time to begin taking data security seriously is now but doing so with time and care will ensure that your data security strategy is ultimately successful.
How to Tackle Enterprise Data Security
Generally speaking, depending on which security solutions are most compatible with your enterprise’s existing infrastructure, workflows, and data, the best solutions for your enterprise could look vastly different than those of your closest competitors. But even so, the most successful enterprise data security strategies still have some common ground.
Create a Layered Security Plan
While individual security solutions can adequately keep your enterprise’s data secure during part of its life cycle, there is no silver bullet solution that will keep it protected at all times. The best way to ensure that your sensitive data is protected at creation, in transit, and at rest is to layer several solutions together for comprehensive, integrated coverage. Work not only to ensure that your data is properly labeled, wrapped in encryption, and has granular access controls attached to it, but also that your employees are trained to spot phishing emails, that your corporate network is properly segmented, and that all devices used by employees are updated and secured.
Find Solutions That Cause the Least Resistance
Data security solutions should work with your enterprise and its employees, not against them. If you find that your implemented solutions have slowed workflows or are creating more work for your employees, it may be time to consider other options. Start by taking advantage of solution integrations with automated processes, like how HelpSystems secure file transfer solutions can automatically apply digital rights management as soon as a file is securely transferred.
Find Solutions That Are Flexible and Scalable
Although your enterprise may already be well-established and employ thousands of people, changes can happen quickly, and your security solutions need to be able to adapt. While finding solutions that will meet your enterprise’s security needs now is paramount, finding solutions that are flexible and scalable enough to evolve with your organization in the future can save the time and effort that would otherwise be spent shopping for new solutions.
Source: HelpSystems
When a large-scale data loss recently occurred at a backup provider, it shined a new spotlight on data safety. Managed service providers (MSPs) that were directly affected, as well as those that weren’t, had to re-evaluate their approach to client data protection.
When you place top priority on dependable backup, you position yourself to maintain long-term customer trust. This safeguards your own reputation and MSP business in the process.
At Datto, reliability of data safety eclipses all other considerations in the design of our business continuity and disaster recovery (BCDR) solutions including SIRIS, ALTO and Datto Continuity for Microsoft Azure. This approach is also central to our backup and restore solutions Cloud Continuity for PCs and SaaS Protection +.
The resilience of a purpose-built cloud
The Datto Cloud, purpose-built for backup and recovery, is immutable cloud storage made for MSPs like you. This means it provides the highest level of data protection, minimizing downtime for both MSP business and your clients.
We currently operate the Datto Cloud with more than 1.5 Exabyte (1500 petabytes) of data stored. As that number continues to increase, Datto has no plans to move our data backup and recovery storage to a third-party cloud. In fact, with the exponential growth of our partner MSPs’ businesses, Datto has performed eight data center migrations since 2018 to keep pace, and we have never lost a single byte of customer data, HDD, or server in the process.
MSPs that choose the predictable Datto Cloud are safeguarding more than your clients’ data — your services, MSP practices and reputation all have maximum protection. There are revenue benefits too, as the scalable Datto Cloud allows MSPs to keep growing your business. Datto invests heavily into scaling the cloud, to exceed the requirements of the fastest-growing MSPs and eliminate those unwelcome “no space” surprises.
Redundant and reliable
What makes the Datto Cloud highly reliable? Industry-best multi-tier resiliency and redundancy are present on every level, from HDDs to servers to data centers. If any major component of the Datto Cloud malfunctions, the data remains safe so you can keep providing predictable services to your clients.
Best practices have been applied at each stage to strengthen the Datto Cloud. In the Americas and EU, all data is replicated geographically from one data center to another that is in a distant location. Our abundance of caution extends to the server racks, where everything is redundant including:
-
Power sources
-
Power distribution units (PDU)
-
Power supply units (PSU)
-
Network interface cards (NIC)
-
HDDs are in RAID configurations
-
and more
As a result, the Datto Cloud is well equipped to minimize outages and the risk of data loss. When you choose Datto you can be sure that you will fully recover client systems after any disaster, so you can win the trust of your customers and accelerate business growth.
Do not deduplicate in the cloud
There’s another key factor that contributes to data safety: the file storage techniques used once files or workloads are backed up to the data center. A cornerstone of Datto’s commitment to MSP success is minimizing risk, a mindset that informs our strategic technology decisions.
One example of this is our design of the Datto Cloud. To increase the resilience of backups and diminish the risk of data loss, we intentionally decided not to use deduplication in the cloud. Deduplication is a storage method used by backup providers to reduce their storage resource consumption and associated costs. Its tradeoff is an increased risk of sprawling data loss that can have a disastrous impact on MSPs and their customers.
Deduplication works by storing identical blocks of data just once and then leveraging metadata to point to the actual data block content. For example, imagine one 20 MB PDF is stored in five folders for five different salespeople — the result is 100 MB of disk space maintaining one 20 MB file. With deduplication, only one complete copy is stored, and others are simply references pointing to that one saved copy. Users still see their files in place, but only 1/5th of the necessary storage is being consumed. Sounds great? Not necessarily.
The downside of deduplication emerges if the metadata or the stored block become corrupted or lost. That’s when multiple backups, customers, and MSPs can be affected. In our example, if the stored data is corrupt, all five files would be gone forever. With lost or corrupt metadata, it would be even worse — it would be nearly impossible to know which backups or salespeople have lost the file. Without the metadata, it becomes extremely difficult to determine which backups, customers or MSPs are affected.
Datto eliminates this hazard by using Inverse Chain Technology instead of deduplication. This is an elegant solution for issues associated with traditional backup chains, as while it transfers and stores only the differences between backups, each backup is seen as full and independent of other backup points,whether they come from the same machine, different machines, different users, or different MSPs.
Not only is there no deduplication metadata involved in the Datto Cloud, our Inverse Chain Technology eliminates the need for rehydration (the reconstruction of previously deduplicated data) or incremental backup chain reconstruction, which can be a very slow process. As a result, MSPs can easily tune and adjust backup parameters, and instantly restore to any point in time. This strategic design decision is one more reason why Datto assures confidence in the safety of your backups, as well as your ability to recover your clients’ systems quickly after a disaster.
As you evaluate your options for backup, being certain about data safety must take top priority. With the purpose-built and secure Datto Cloud at the core, the reliability of Datto solutions provide protection built for the MSP.
Source: Datto