News
We are thrilled to announce that Sophos has, once again, been named a Leader in the 2022 Gartner® Magic Quadrant™ for Endpoint Protection Platforms (EPP). This marks our 13th consecutive recognition as a Leader.
A Leader, again
We believe a key factor contributing to our continued Leader position is our relentless focus on innovation. While threats and operating environments have evolved over the last 13 reports, Sophos has continued to keep customers ahead of even the most advanced attacks.
Sophos’ services and products are powered by Sophos X-Ops, our cross-domain threat intelligence unit that brings together deep expertise across the attack environment. Armed with this deep understanding, we are able to build powerful, effective defenses against even the most advanced threats. Unparalleled ransomware protection, deep learning artificial intelligence, exploit prevention, and active adversary mitigations in our endpoint protection stop attacks cold.
Further advancing our cybersecurity leadership with the recent launch of the newly enhanced Sophos MDR service, Sophos is the first endpoint security vendor to deliver MDR across both its own product portfolio as well as customers’ existing security deployments. Sophos MDR now integrates telemetry from third-party endpoint, firewall, cloud, identity, email, and other security technologies as part of the Sophos Adaptive Cybersecurity Ecosystem, further accelerating threat detection and response.
Most trusted MDR service
Sophos MDR is the world’s most trusted MDR service, protecting more than 15,000 organizations against advanced threats that technology alone cannot stop. It addresses the growing need for flexible managed services and threat response options, meeting customers – ranging from small businesses to large corporations – where they are.
Learn more about our service and speak with our security advisers to discuss how Sophos MDR can help you.
Double recognition is a double honor
Our Gartner Magic Quadrant for EPP recognition follows Sophos being named a 2021 Gartner® Peer Insights™ Customers’ Choice for Endpoint Protection Platforms.
To us, being recognized in the Gartner Magic Quadrant for EPP and named a Gartner Peer Insights Customers’ Choice for EPP is a tremendous honor and, we believe, testament to the quality of our protection and service we provide.
Read the full report at https://www.sophos.com/en-us/report/magic-quadrant-endpoint-protection-platforms
Source: Sophos
Trust is one of the most important aspects of business, especially when it comes to the collection and use of people’s personal data. As consumers advocate for organisations to take more precautions in handling their personal data, legislative bodies are listening, and more data privacy regulations are being passed globally each year. Being proactive in complying with, or better yet, staying ahead of regulatory requirements, can be used to your organisation’s advantage to drive consumer trust and business opportunities.
This blog will explore consumer concerns regarding personal data, how leveraging data privacy regulations benefits organisations and consumers, and what steps your organisation can take to both build data privacy practice and maintain consumer trust.
Consumer distrust is a growing problem
Consumers are becoming more aware and concerned about how their personal data is being used and handled. The following statistics demonstrate the concern and distrust that is developing among consumers:
- 87% of executives think customers highly trust their companies when only about 30% actually do
- 86% of consumers say data privacy is a growing concern
- 75% of executives say that since the pandemic began, they have had a harder time building and maintaining trust with their customers
- 71% of consumers say they’re unlikely to buy if a company loses their trust
- 40% of consumers don’t trust organisations to use their data ethically
- 30% of consumers aren’t willing to share their personal data for any reason
Furthering and validating these concerns in a recent Salesforce study, nearly half of consumers surveyed said they lost trust in brands due to misuse of personal information. Once trust has been broken, more than half (55%) of consumers say they will NEVER give the brand their business again.
Use a proactive approach to complying with privacy regulations
This misuse of personal data has driven consumers to advocate for more precautions to be taken with their personal data, driving the emergence of various privacy regulations globally such as GDPR and CCPA. Cisco’s Consumer Privacy Survey highlights “Consumers want transparency and control with respect to business data practices – an increasing number will act to protect their data”. In order to meet consumer desires regarding the handling of personal data, one of the best things your organisation can do is to start protecting consumer’s data right now. This approach shows consumers that you understand their concerns and are taking proactive steps to protecting their data. Rather than simply waiting for a privacy regulation to go into effect, or scrambling to protect personal data only because it is the law, taking early action sends customers a clear message about your organisation’s priorities and values.
How to improve your data privacy practice and build consumer trust
Now that we’ve identified how getting a head start on protecting consumer data can be beneficial, let’s explore how to go about implementing this strategy into your organisation. An article by Entrepreneur’s Organization for Inc. outlines three ways how you can both improve your privacy practices and build customer trust at the same time regarding personal data:
1.Map your data
Mapping your data, also known as creating a data inventory, involves following a data record through your system from the point of collection to deletion. Data mapping can help your company understand:
- What types of information are actively collected
- What data is actually being used
- Who the information is shared with and who has access to it
- Where and how long data is being stored
- Where your processes deviate from stated policies
Many companies think they know this information already, but most businesses collect more information than they need, store it too long, and have poor access controls that leave data vulnerable to exposure.
A data map gives you the empirical information you need to recognise and address these issues.
Data classification can assist with data mapping by identifying and categorising data into set schema, giving you greater visibility of what data you have and where it resides. Alongside the labeling capabilities of data classification, monitoring and reporting modules give your organisation further insight into who has access to what data and what they are doing with it.
2.Set your privacy strategy and policy
A data privacy strategy and policy is crucial to keeping your consumer’s personal data secure. Once you know where the weak points in your processes are, you can start building a new privacy strategy that’s legally compliant and future-proofed against changes to either privacy laws or best practices.
Foundational principles that should be part of any privacy program include:
- Seeking cross-functional input from all your teams
- Maximising data value while minimising the amount collected by focusing on first-party data (data collected directly from consumers, as opposed to an outside source such as a paid list)
- Establishing a culture of privacy through continuous employee training
It’s much easier to craft a privacy policy once you’re armed with an accurate data map and a strong privacy strategy.
A good privacy policy accurately describes how your company collects and processes consumer information, is short and easy to understand (no legal jargon) and is clearly visible on your website.
Data classification solutions enable users to assign visual labels to the data they create, collect, and store, so that informed decisions can be taken about how it is managed, protected and shared, both within and outside of your organisation. Involving your users in data privacy strategies aids in establishing a culture of privacy, teaching them the value of the data they are handling, and ensuring set privacy strategies and policies are followed.
3.Brag about it
Almost 76 percent of companies that invest in a robust privacy program see increased loyalty and trust from their customers. But even the best privacy program in the world won’t help you if your customers don’t know about it.
Marketing your business’s commitment to privacy is just as essential to building digital trust as building your privacy program in the first place. Instead of treating privacy as a cost center, weave your commitment into all your messaging until it becomes a key part of your brand’s reputation.
With consumer trust dropping, and the emergence of global data privacy regulations on the rise, it is more important than ever for organisations know what data they have, where it is located, and how it is being used.
Gartner predicts that by the end of 2023, modern privacy laws will cover the personal information of 75% of the world’s population, so why not embrace this trend of privacy regulations to benefit both your organisation and your consumers?
Learn more about how our data classification solutions can help your organisation build trust with your consumers by scheduling a free demo today.
Source: Boldon James
Check out the latest enhancements in our market-leading Sophos Intercept X Endpoint solution that protects Windows, macOS, and Linux systems against never-before seen ransomware, malware, phishing, web threats, and attacker-led behaviors.
Year in, year out, Sophos Intercept X Endpoint delivers superior cybersecurity outcomes to over a quarter of a million organizations worldwide thanks to our relentless focus on innovation and our commitment to delivering the strongest protection.
Testament to the quality of our defenses, Sophos ranked as industry best in SE Labs’ protection tests in the fourth quarter of 2022, earning AAA ratings across the board. In both the Enterprise and SMB categories, we achieved:
• 100% rating for Protection Accuracy
• 100% rating for Legitimate Accuracy
• 100% rating for Total Accuracy
Customers also give Sophos top scores. As of February 20th, 2023, Sophos Intercept X Endpoint has a 4.8/5 rating across 374 independent reviews on Gartner Peer Insights, with 95% of customers saying they would recommend Sophos.
While we’re proud of all these results, we are passionate about protecting our users, so I want to share with you some recent enhancements that help our customers stay ahead of today’s well-funded, constantly innovating adversaries and streamline day-to-day endpoint security management.
Adaptive Active Adversary Protection
We’re constantly developing new protection techniques to guard our customers against the latest attacks. One of the latest additions to Sophos Endpoint security is Adaptive Active Adversary Protection. This new capability from SophosLabs is automatically activated whenever we detect signs that a device has been compromised and there is a hands-on-keyboard attack in progress.
Adaptive Active Adversary Protection temporarily puts the impacted device into a more aggressive security mode that disrupts and delays the attacker by automatically blocking a wide range of activities that are commonly performed in human-led attacks. Just a few examples of the malicious behaviors that we prevent include:
- Attempts to run remote admin tools
- Attempts to run untrusted executables
- Attempts to boot the machine in Safe Mode
Plus many, many more…
By stopping a malicious actor from performing these activities, Adaptive Active Adversary Protection slows the attack and buys time for security teams to respond to the threat before the adversary can achieve their goal. Once there are no further signs of adversary activity on the device, Adaptive Active Adversary Protection is turned off automatically. No manual enablement or tuning required!
Account Health Check
Sophos Endpoint is packed with technologies that protect organizations against advanced threats. The Account Health Check lets you quickly ensure those capabilities are correctly configured and deployed, optimizing your protection. Available to all customers via the Sophos Central platform, the Account Health Check performs several key assessments:
- Software assignment – do devices have all the Sophos Endpoint software components assigned to them?
- Threat policy – are policies using Sophos’ recommended settings?
- Exclusions – are any exclusions creating attack surface exposure?
- Tamper protection – has tamper protection been disabled on any workstations and servers?
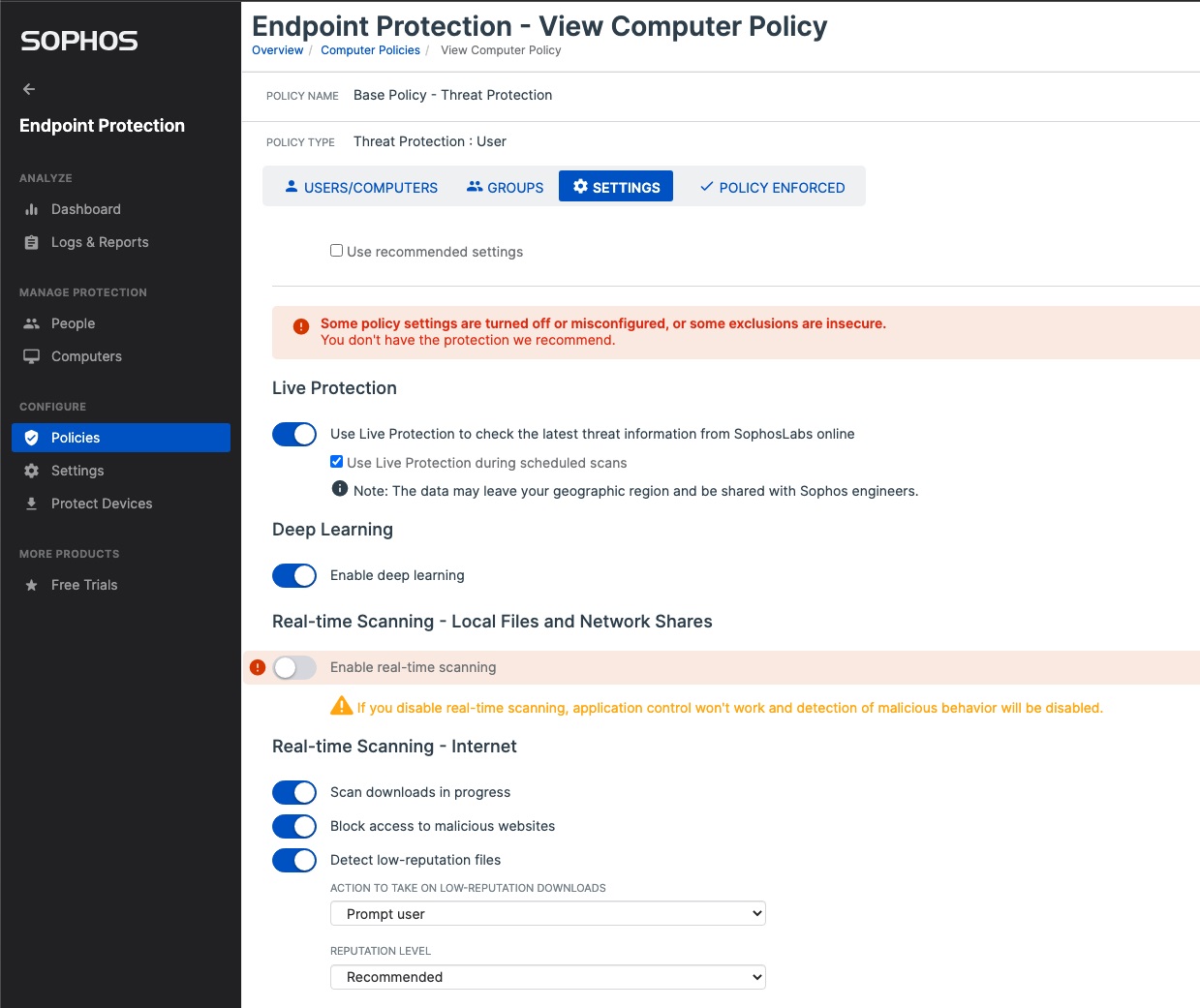
Should the Account Health Check detect any issues, a simple ‘fix automatically’ option lets you update your protection instantly to the recommended settings. Customers have used this easy remediation option over 11,000 times in the three months since we introduced this feature, optimizing their security posture in a single click.
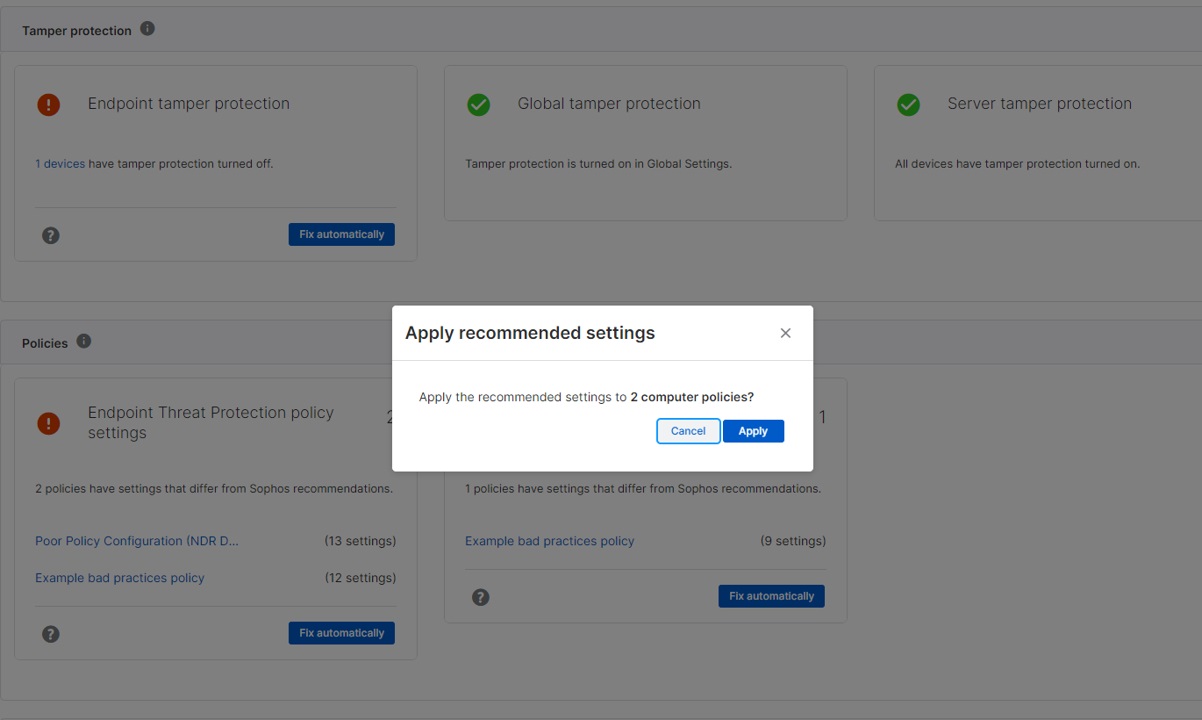
While recommended settings are automatically applied with all new Sophos deployments, over time issues can develop as devices are added and removed, team members change, and different software subscriptions are purchased. We recommend reviewing the Account Health Check at least every three months – and ideally monthly – to maintain a healthy environment.
Enhanced Software Management Options
Although all organizations need the same high levels of protection, larger companies often require more granular management capabilities. We recently released Fixed Term Support packages and special ‘Maintenance Release’ (MR) packages for Windows computers and servers, with macOS and Linux coverage coming later this year.
Fixed Term Support packages enable customers to precisely control which versions of Sophos Endpoint software they deploy on specific devices/groups of Windows devices. This allows you to control when devices are upgraded instead of being on the Sophos update schedule.
Special ‘Maintenance Release’ (MR) packages are where Sophos Support makes packages available to specific customers that contain fixes before the next full software rollout. Customers can apply these packages immediately to targeted devices, rapidly accelerating an organization’s ability to address an issue.
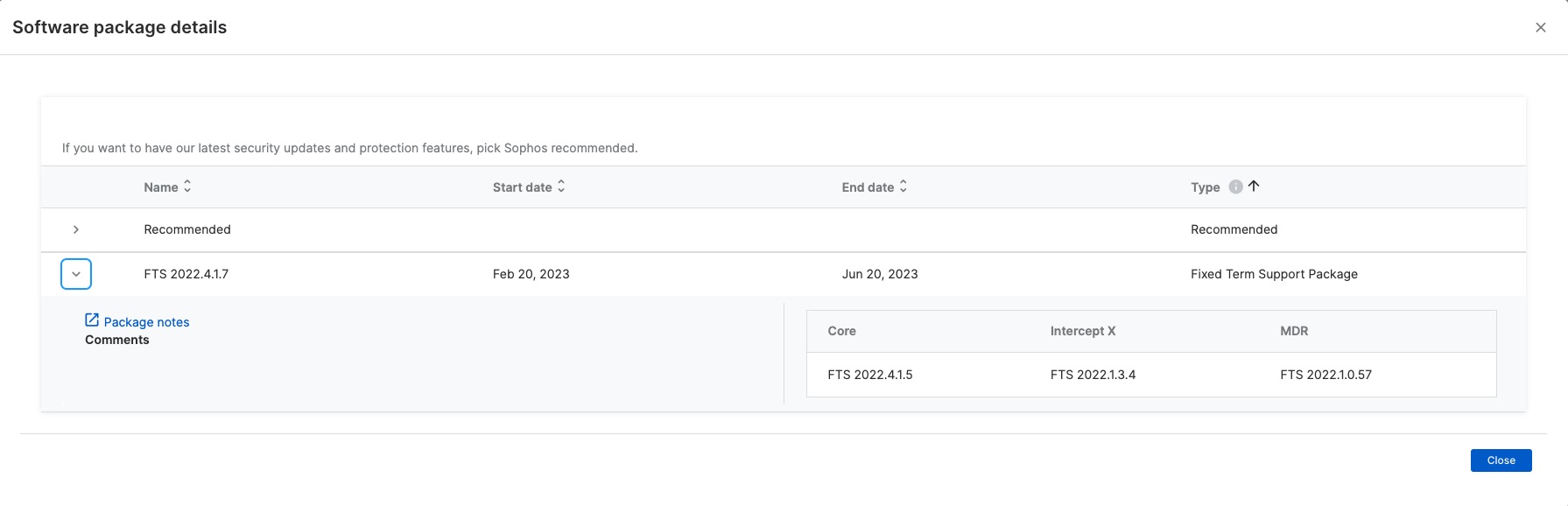
Read more about these features on the Sophos Community.
Malware Protection Enhancements for Linux
Customers asked us for on-access malware scanning and quarantine for Linux machines – and we’ve delivered. These features are now live, complementing our existing Linux protection functionality, including runtime detections, live detection, and live response.
As a reminder, the legacy Sophos Antivirus for Linux product will be retired in July 2023, so if you’re still using Sophos Antivirus for Linux, switch to the new Sophos Protection for Linux agent today.
Faster, Lightweight Agent
Sophos Endpoint delivers superior protection without compromise. We’ve expanded our protection capabilities while also reducing the Windows agent’s memory footprint by 40% and reducing the number of processes by over 30%. Plus, we’ve introduced a new XDR-sensor deployment option that is ~80% lighter than the older full agent. The result: accelerated performance of applications, workloads, and devices.
Built-in ZTNA Agent – on Windows and macOS Devices
Zero-Trust Network Access (ZTNA) is fast becoming the remote access technology of choice for organizations of all sizes. It enhances security, is easier to manage, and works reliably everywhere without getting in the way.
Sophos Intercept X Endpoint is the only endpoint protection solution with a built-in ZTNA agent, future-proofing customers’ defenses. Following our recent addition of macOS support, organizations can extend their protection to include Sophos ZTNA across their entire estate at any time, without the need to deploy an additional agent*. Both solutions are managed through the Sophos Central platform for elevated ease of use.
* Requires Sophos ZTNA subscription purchase
More Coming Soon!
We have an exciting and aggressive roadmap that continues our delivery of innovative, market-leading protection for our customers. In the coming months, we look forward to introducing a Long-Term Support (LTS) version for Windows that allows customers to stay on a static version for up to 18 months. This is particularly useful for critical infrastructure where version control is strictly controlled.
We’ll also be adding a new software version report in the Central UI. With the ability to define which version/packages are deployed to every device, this new report will enable customers to quickly review and identify versions/packages running on their devices.
Following the very warm customer response to the Account Health Check, we will soon be launching additional features including a new ‘snooze’ option to defer checks to a later time, proactive alerts that notify you whenever a configuration change is made that affects cyber health, and scoring that enables you to track improvements in security posture over time.
We’re further enhancing the Sophos Linux Sensor (SLS), adding the ability to ingest detection data into the Sophos Data Lake and Threat Analysis Center, and we’ll also enable security teams to create and manage runtime detections in Sophos Central.
Plus, for macOS, admin-led device isolation will be available imminently, and we’re planning to open our Early Access Program (EAP) for HTTPS decryption for web protection next quarter. I look forward to sharing more details about these and other enhancements shortly.
Explore Sophos Endpoint Security Today
To find out more about Sophos Endpoint and how it can help your organization better defend against today’s advanced attacks, speak with a Sophos adviser or your partner today.
Source: Sophos
Sophos Firewall v19.5 was released in November and has been our fastest-adopted release, with over 50,000 firewalls already having upgraded. It’s also been our best quality release ever: it’s packed with great features that boost performance, resiliency, and management ease.
If you haven’t already upgraded your Sophos Firewall to v19.5, here are the top five reasons you should upgrade today:
- Added performance: Sophos Firewall OS v19.5 includes Xstream FastPath acceleration of TLS encrypted traffic and improvements in IPSec tunnel capacity and performance, leveraging the programmable Xstream Flow Processors in every XGS Series firewall appliance.
- Robust SD-WAN: SFOS v19.5 includes a new SD-WAN load balancing capability that can use multiple SD-WAN links for added performance and redundancy, as well as OSPFv3 (IPv6) dynamic routing support.
- High availability: Several enhancements improve managing high-availability deployments in active-active or active-passive setups, including new status and visibility improvements along with redundant link support.
- Azure AD integration: Makes it easier for firewall admins in an Azure AD environment to log in and manage Sophos firewalls using the same credentials.
- Host and services search: This feature makes it easy to find the network object you’re looking for and reduce the duplication of assets.
Here’s a quick overview of everything that’s new in Sophos Firewall v19.5:
And, as usual, every Sophos Firewall release includes important security, performance, and reliability enhancements. See the full release notes for details. Also check the latest training materials available for Sophos Customers and Sophos Partners.
Upgrading couldn’t be easier
If you manage your firewalls in Sophos Central, simply click the download arrow for the firewall you want to upgrade and choose “Schedule Upgrades”…

You can also log in and upgrade the firewall locally. Upon logging in, you should see this pop-up appear – simply choose “Upgrade now”…
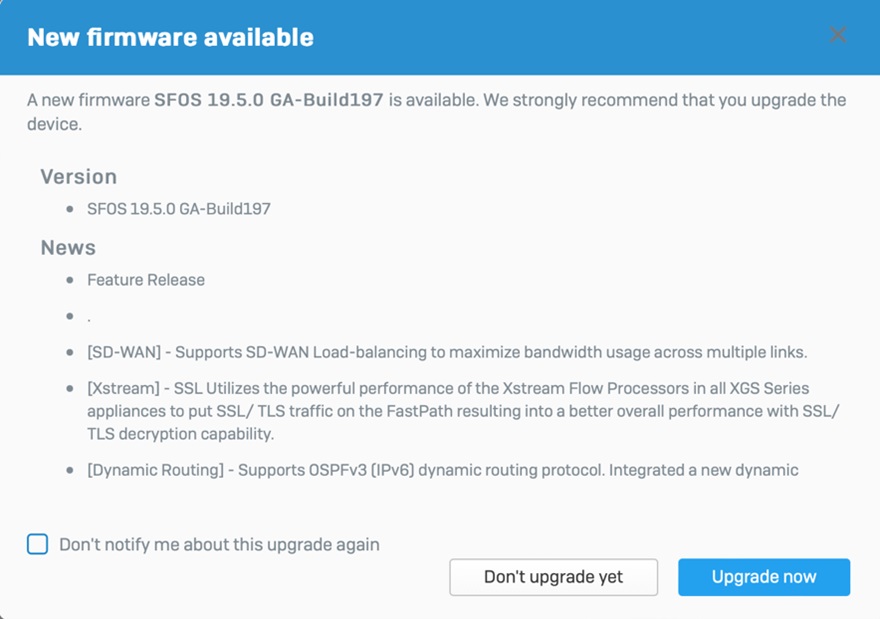
If you don’t see the above window when you log into your firewall, navigate to Backup & Firmware > Firmware and check for new firmware to download the latest release:
Get started upgrading today!
Source: Sophos
Data loss is a constant threat to businesses, and the risk it comes with is not just a monetary one from breaching regulatory requirements, but perhaps far more costly in the long run is the potential reputational damage. When it comes to your organisation’s security ecosystem, Data Loss Prevention (DLP) solutions are a key priority for anyone handling sensitive data. There are two main types of DLP – Network DLP and Endpoint DLP – each providing a different function to protecting and securing sensitive data. Let’s explore what Network DLP (NDLP) and Endpoint DLP (EDLP) are, the differences between them, and how data classification integrates to bolster DLP decision making.
Network DLP (NDLP)
Network DLP (NDLP), also referred to as data-in-motion protection, mitigates the risk of data loss by monitoring, controlling, and reporting the flow of sensitive data via the network, email, or web. It sees data as it moves through the network and enforces policies at that time. For example, if a user attempts to send an email with sensitive data, NDLP inspects that traffic and can automatically take actions based on the organisation’s predefined policies such as block, audit, forward, notify, encrypt, and quarantine. NDLP also has visibility into web traffic such as social media sites for added protection.
A major benefit to NDLP is that it can be deployed with very little overhead and does not require much upkeep. However, as NDLP uses a box or virtual machine on the corporate network that data traffic passes through, devices must be connected to your network in order to protect data. If the device is off the network and not on a corporate VPN, NDLP does not have visibility into what is happening with data and cannot protect it. Even with a VPN, NDLP does not directly prevent data from being saved on external devices such as USB drives.
Endpoint DLP (EDLP)
Endpoint DLP (EDLP) monitors all endpoints such as laptops, desktops, phones, and any other device on which data is used, moved, or stored. With EDLP, an agent lives on the endpoint (the system) and gives you visibility into the data as it is created or updated and is then tagged to alert the user if it contains sensitive data. The agent can also see actions such as copy/paste, screenshots, and printing, and can restrict those processes, and prevents data from being saved on a USB drive, CD, or DVD. EDLP can protect data either on or off the corporate network, so data is protected even if users are working remotely and not connected to the corporate network via VPN.
Having data protected at its source is an enormous benefit, however EDLP requires the deployment and ongoing maintenance of agent software on every protected device. Volume of upkeep will depend on the number of laptops, desktops, severs, etc. in your organisation. This can be a lot to deploy and manage if the organisation has a multitude of devices to keep up with.
How they differ
While NDLP and EDLP work to the same end goal, preventing sensitive data loss, they are very different when it comes to what levels of control they offer and how they are deployed. The main difference between NDLP and EDLP is that NDLP secures communications on the organisation’s network, while EDLP safeguards intellectual property and ensures compliance with company policies. As discussed previously, NDLP protects data only in your company’s network, so a VPN must be used to make it conducive to a remote environment. However, NDLP is easy to deploy and does not require a dedicated resource once deployed. Meanwhile, EDLP protects data at the source offering deeper insight, but requires ongoing deployment and maintenance of the agent software on every device, which can be challenging to manage depending on the number of devices being used.
Questions to consider when choosing between NDLP and EDLP:
Deciding which option is best for your organisation depends on a few key factors:
- How much control over the endpoint do you have?
If you have devices that you are unable to modify for whatever reason (geographical location, personal device, etc.) and are allowing access to the corporate network and corporate data, then NDLP is the best option for the short term. Changes to endpoint policy are typically long-term plans in most organisations, and you do not want to wait to start protecting your data.
- How do you prioritise the thoroughness of data inspection vs. time, effort, and monetary investment in the inspection process?
NDLP is much faster to deploy and easier to maintain while EDLP provides deeper and more thorough insight and protection. Ultimately, you will need to make a realistic assessment of your organisations needs vs. capabilities.
Using data classification to enhance DLP
Both NDLP and EDLP provide a comprehensive set of control points at which to police the distribution of information – within the network and at the endpoint devices. However, unless the significance of the data is accurately determined, then even a pervasive set of control points will not prevent data leakage. A data classification solution assists users in applying consistent classification metadata to information, supplying DLP solutions with reliable insight into the meaning and value of data, which complements the detection methods based on keywords and regular expressions alone. With the business context captured in the metadata, DLP can then apply decisions in a consistent manner in order to control the distribution of information or apply further security measures.
Another benefit to data classification is that it helps mitigate one of the most prevalent hindrances to DLP – “false positives”. Organisations looking to deploy data loss prevention solutions are commonly faced with the dilemma of how to maximise the value of automated content scanning whilst avoiding the negative impact of “false positive” results. In order to avoid an adverse effect on business processes, DLP solutions can end-up being detuned to the point where only simple, highly predictable checks can be performed, for example, checking for credit card numbers, employee numbers, material codes, etc. As a result, the solution is left unable to identify the true business value of most information and to apply relevant controls. By engaging knowledge workers in the process of classifying the unstructured data that they routinely handle, it becomes possible to supply the DLP solution with predictable, meaningful metadata that greatly improves the reliability of DLP decision making. With improved accuracy of DLP decision making, the incidence of “false positives”, that are so frustrating to users and damaging to business processes, can be significantly reduced without compromising effectiveness.
With data being one of a businesses’ most valuable assets, implementing either NDLP or EDLP alongside a best-of-breed data classification solution, can help organisations maintain visibility and control of their data, keeping it safe, secure, and compliant. No matter which DLP route you choose, when paired with a classification solution, both NDLP and EDLP are some of the most effective tools for preventing data loss.
Source: Fortra
The Datto SMB Cybersecurity Survey for MSPs Report has been released, and it is packed with crucial information for MSPs to help them grow their sales and learn more about their clients’ pain points. The survey was created from a subset of data collected in a survey of 2,913 IT decision-makers conducted in July and August 2022. Respondents were required to be an IT decision-maker at an SMB with 10–300 employees. The markets chosen for analysis were North America (U.S. and Canada), the U.K., Germany, Australia and New Zealand, the Netherlands and Singapore. These seven key takeaways give MSPs a look into the minds of SMB cybersecurity decision-makers.
5 Key Takeaways from the Datto SMB Cybersecurity for SMBs Report
Businesses are getting the message that cybersecurity is critical to their success loud and clear, and they’re acting accordingly, creating a world of opportunity for MSPs. These are seven of the most notable data points in our report for MSPs.
1. IT decision-makers are in a buying mood.
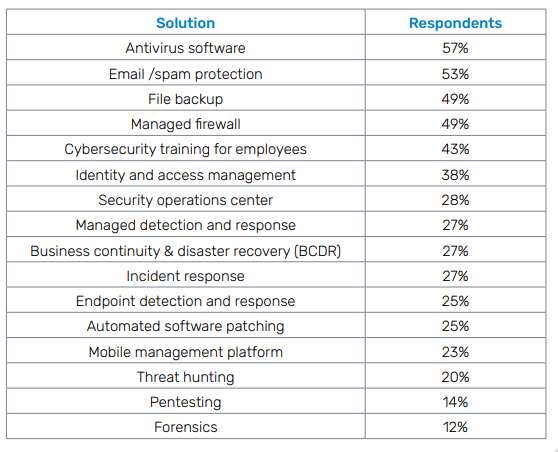
Businesses are very concerned about security and ready to make investments to keep their organizations safe. SMBs continue to experience significant security challenges and they recognize that they need to spend to solve them, with about half of our survey respondents planning to spend on email security, backup and antivirus protection.
What security solutions are SMBs planning to invest in in the next 12 months?
2. Security is front and center on most SMB priority lists.
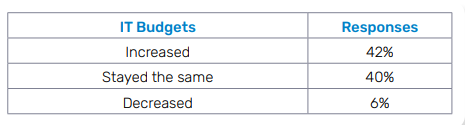
High-profile cyberattacks and strict data privacy laws have increased the importance of security for businesses. Few SMBs are cutting back on security spending, instead, they’re investing in security. Four in 10 of our survey respondents said that their organization is increasing their cybersecurity spending, and most expect that to continue – excellent news for MSPs in today’s challenging economy.
Are SMBs increasing or decreasing security spending?
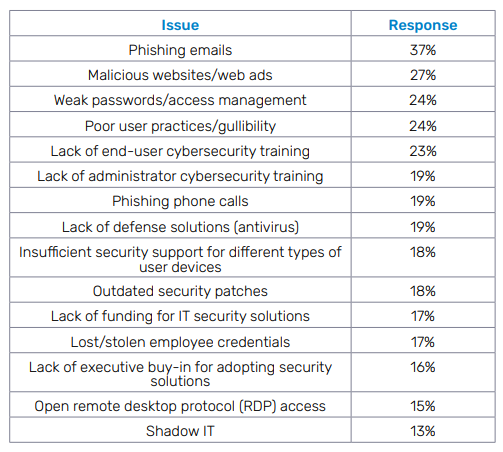
3. Phishing is the biggest security woe that SMBs face.
Business IT leaders are worried about phishing and the danger it brings in its wake. Malicious advertisements are also troubling businesses. It’s also interesting to note the prominence of poor security practices and lack of training on this list. Security awareness training is a powerful and affordable tool for any business to use to mitigate security risk, yet far too many businesses aren’t getting the full benefit by running haphazard or infrequent training. This list does contain a spot of good news for MSPs: there are revenue growth possibilities for MSPs around email security and security training with phishing simulations.
What do SMBs see as their biggest security challenges?
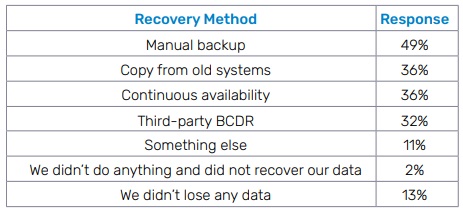
4. Downtime is costly, but many businesses don’t have the right tools in place to minimize it.
MSPs have a golden opportunity to expand revenue and help their customers reduce expensive downtime with solutions like BCDR, managed SOC and incident response planning. Just under half of survey respondents (49%) said that their organizations relied on manual backup to recover data in their last cybersecurity incident. That means that half of the businesses we surveyed need to update to cloud backup and learn the benefits of BCDR — a big opportunity score for MSPs.
What are the most common methods used to recover data in the event of an incident?
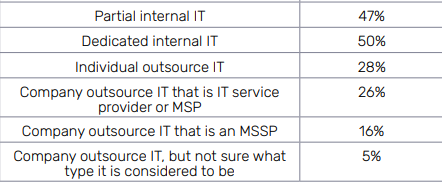
5. Many SMBs need outside help to handle security.
More than half of our survey respondents admitted that a successful phishing attack or even worse, a ransomware attack, would seriously wound their organization with some saying that it could be a fatal blow. Many SMBs have that expectation because they’re not prepared to handle the fallout from a cyberattack. The cybersecurity skills shortage is only compounding their problems. That’s a big reason why a significant number of SMBs tend to rely on outsourced IT security. Businesses will continue to require expert help to maintain and enhance their security, and almost half of the IT professionals that we surveyed said that their organization relies on an MSP or MSSP to get the job done.
How do SMBs manage their security?
Learn more about the mindset, motivation and challenges of SMB security decision-makers by reading the Datto SMB Cybersecurity for SMBs Report, available now.
Source: Datto
We recently launched Sophos Network Detection and Response (NDR) and it’s already providing real-world value for organizations looking to elevate their defenses against sophisticated attackers and zero-day threats.
Sophos NDR continuously monitors network traffic to detect suspicious activities that may be indicative of attacker activity, leveraging a combination of machine learning, advanced analytics, and rule-based matching techniques.
It detects a wide range of security risks, including rogue devices (unauthorized, potentially malicious devices that are communicating across the network), unprotected devices (legitimate devices that could be used as an entry point), insider threats, zero-day attacks, and threats involving IoT and OT devices.
Plus, when combined with other security telemetry, Sophos NDR enables threat analysts to paint a more complete, accurate picture of the entire attack path and progression, enabling a faster, more comprehensive response.
Sophos NDR is an add-on integration for Sophos MDR, our market-leading managed detection and response service that today serves over 14,000 organizations worldwide. Later this year, we’ll also be making Sophos NDR available with Sophos Extended Detection and Response (XDR) for those organizations that prefer to conduct their own threat hunting activities – more on this in a future post.
The importance of network detection and response
NDR is an essential part of an effective defense-in-depth strategy. Why? Because the network is the one place a stealthy, committed adversary cannot hide.
Attackers go to great lengths to avoid being detected and Defense Evasion is well known MITRE ATT&CK Tactic at the system level. Exploits can hide out of sight of EDR solutions, and adversaries can disable and delete system logs. But they still have to traverse the network.
As adversaries continue to evolve their tactics, techniques, and procedures (TTPs) to bypass security controls, NDR is fast becoming a security imperative.
Sophos NDR: unparalleled network threat detection
Sophos NDR is powered by five real-time threat detection engines that use patented multi-layered technologies to detect even the stealthiest of attacks.
The Data Detection Engine is an extensible query engine that uses a deep learning prediction model to analyze 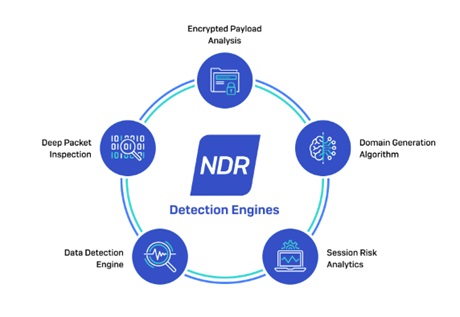 encrypted traffic and identify patterns across unrelated network flows.
encrypted traffic and identify patterns across unrelated network flows.
Deep Packet Inspection uses known indicators of compromise to identify threat actors and malicious tactics, techniques, and procedures across encrypted and unencrypted network traffic.
Encrypted Payload Analytics detects zero-day C2 servers and new variants of malware families based on patterns found in the session size, direction, and interarrival times.
Domain Generation Algorithm identifies dynamic domain generation technology used by malware to avoid detection.
Session Risk Analytics is a powerful logic engine that utilizes rules that send alerts based on session-based risk factors.
These five engines monitor east-west (internal) traffic and north-south (outgoing/incoming) traffic to detect and flag anomalies indicative of threat activity. Alerts generated by Sophos NDR include:
- Network scanning activity
- Unexpected SSH sessions to never-before accessed systems
- Suspected beaconing activity
- Suspected C2 connections
- Communication on non-standard ports
- Malware present in encrypted traffic
- Encoded PowerShell execution
- Abnormal volumes of data sent
Leveraging Sophos NDR telemetry to stop advanced threats
Network security telemetry is a powerful threat hunting resource on its own, and especially useful when combined with signals from across the full security ecosystem.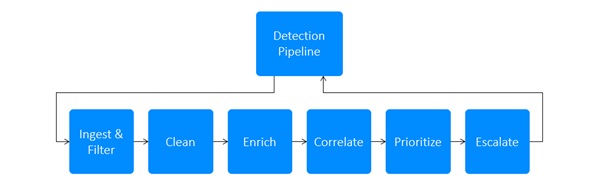
Sophos MDR leverages alerts from Sophos and third-party network, endpoint, firewall, email, identity, and cloud solutions to accelerate threat detection and response.
Alerts are processed through the Sophos MDR Detection Pipeline where they are transformed into normalized schema, mapped to the MITRE ATT&CK® framework, and enriched with third-party intelligence. Related alerts are grouped in clusters which are then prioritized and escalated to detection specialists for investigation and response.
Let me walk you through a couple of example scenarios where Sophos MDR leverages telemetry from Sophos NDR in conjunction with insights from other technologies.
Scenario 1
- Email solution detects a message containing a malicious attachment
- Endpoint protection detects a suspicious file download
- Endpoint protection detects that an unknown process launched an interactive shell
- Sophos NDR detects a suspected Command and Control (C2) connection
- Endpoint protection detects suspected credential harvesting
- Sophos NDR detects suspected lateral movement using SSH
By correlating the email, endpoint, and NDR alerts, Sophos MDR can quickly ascertain that there has likely been a successful phishing attack that has resulted in credential theft and lateral movement. Armed with this insight, we can step in to swiftly contain, neutralize, and remediate the attack, minimizing impact.
Scenario 2
- Sophos NDR detects a device communicating on the internal network
- Endpoint protection has no known device under management
Combining data points from these two separate technologies enables us to identify that there is an unmanaged device communicating on the network. At this point, we investigate further to determine whether it’s the result of an internal user policy violation or an adversary-managed system, and then take appropriate action.
Already using an alternative NDR solution? No problem.
We understand that organizations already have security solutions in place. The challenge for many companies is how to manage, interpret, and respond to the information they provide. All too often, we speak with IT teams that are drowning in alerts or unable to digest the complex telemetry.
With the Sophos MDR add-on integration packs, our analysts can leverage telemetry from the third-party security tools you’re already using (including NDR solutions from Darktrace and Thinkst Canary) to detect and respond to advanced, human-led attacks. With our experts managing your security operations, you can elevate your defenses and increase return on your existing investments.
Learn more
To learn more about Sophos NDR and Sophos MDR and the superior cybersecurity outcomes our customers enjoy, arrange a call with one of our security experts today. Be sure to check out our NDR community channel as well.
If you’d like to hear what our customers have to say about Sophos MDR, take a look at the independent reviews on Gartner Peer Insights and check out why we’re the #1 rated MDR service by G2 Peer Reviews.
Source: Sophos
Ransomware and phishing are usually put in two separate categories when cyberattack methodologies are discussed. However, ransomware operators are increasingly leveraging phishing tactics to deploy their malicious payloads, and the potential for compromise is exponentiating as a result.
Ransomware and Phishing – a match made in heaven
Phishing is the number one delivery vehicle for ransomware, states risk management firm Deloitte. Industry sources agree, and phishing was identified as the primary vehicle for ransomware in Coveware’s Q4 2020 Quarterly Ransomware Report. It beat out RDP (Remote Desktop Protocol) as the top initial attack vector, once the remote work avalanche of 2020 died down, and has since moved up as the fastest way to get malicious code in front of an organization.
In a recent survey, it was revealed that a staggering 78% of organizations experienced one or more ransomware attacks in 2021, 68% of which stated that the attack originated from a direct email payload, second-stage malware delivery, or similar cause. And, IBM’s Cyber Resilient Organization Study noted the top three causes of ransomware that year as social media (19%), malicious websites (22%), and phishing (45%).
The logic? Phishing emails are easy to send and lure the unsuspecting victim in with minimal awareness of an attack. The carefully crafted device of a social engineering scheme, the emails are customized to specific targets and appear to be from legitimate, even familiar, senders. Faced with unmanageable email volumes, even many once-careful users fail to scrutinize incoming mail and note small changes that would otherwise be suspicious red flags. Once the victim opens an email from their “bank” or “internet service provider” and confirms a few account details – or even just clicks into the malicious fake site – the payload detonates and the work of stealing and/or encrypting sensitive data begins. Once this work is completed, users are locked out and a ransom note appears.
Phishing on Social Media
While popularly exploited on email servers, phishing attacks are not confined to inboxes. One of the rising vectors, as noted by the IBM study, is social media. Collaboration tools like Teams and Slack are prime grooming places for establishing trust and exploiting “coworkers”. Online spaces like LinkedIn are particularly vulnerable to facilitating attacks; as platforms built for connecting with strangers, they encourage direct messages which often contain links to shared professional interests. Many of those links are credible – some are not. Unfortunately, with ransomware one click is all it takes.
Ransomware operators also glean the personal information shared on social networking sites to craft a more custom-built attack. The authenticity and believability of many of the messages – “Hey Don, it was great talking to you at DEF CON. Here’s that link I was telling you about” – can fool even the most savvy. And, as Deloitte states, “many users are simply not sufficiently skeptical when it comes to receiving requests to do things like transfer funds, open attachments, or provide sensitive information.”
Unfortunately, users don’t even have to engage to be at risk. A ransomware tool discovered in 2016 scraped the social media accounts of its victims to create personalized campaigns, ironically threatening to see its users in court if the ransom was not paid. Security researchers similarly noted Facebook-centered ransomware activity, allowing attackers to embed malicious code into uploaded image files which a misconfiguration then forced users to download.
AI-Powered Ransomware
The one saving grace is that customizing ransomware phishing attacks is time-consuming work. It requires human effort and insight and is difficult to scale. However, Artificial Intelligence could close the gap that makes even that automatable before long. “We have already seen [ransomware groups] hire pen testers to break into networks to figure out how to deploy ransomware. The next step will be that they will start hiring ML and AI experts to automate their malware campaigns,” said cybersecurity expert Mikko Hyppönen. Mark Driver, a research vice president at Gartner, says this could mean an even greater acceleration of attacks. “It’s not worth their effort if it takes them hours and hours to do it manually,” he explains. “But if they can automate it, absolutely.” The bottom line? “It’s terrifying.”
The danger is not only AI-powered ransomware models, but AI-driven deepfakes that can impersonate legitimate sources and make phishing attempts that much more convincing. Reported cases of face- and voice- altering AI technology increased by 13% last year, and 66% of surveyed cybersecurity professionals reported seeing one in the past twelve months. Deepfakes in cyberattacks aren’t coming, they’re already here.
Prevent Phishing Attacks and Ransomware
One industry report noted that the number of ransomware attacks doubled year-over-year in 2021, and we are reminded that nearly 80% of organizations experienced at least one attack. This makes for very dire predictions. However, the best defense is a good offense and several offensive strategies exist for mitigating ransomware attacks.
Criminals aren’t the only ones who can hire pen testers. Probing your environment for weak spots is one of the best ways to stress test your environment before attackers can take advantage of vulnerabilities. Given the fact that 82% of breaches are attributable to the “human element” – a healthy portion of error included – it’s next to inevitable that despite an organization’s best efforts, a phishing attempt will succeed sometime. When it does, malware will infiltrate the network looking for systems to exploit and data to exfiltrate. Red teaming, attack simulation, and black box fuzzing allow your team to see what’s possible to attackers before they do.
Email security and anti-phishing measures need to be combined with an offensive security strategy for the best defense-in-depth approach. Together, they focus on preventing ransomware payloads from detonating and harming your network.
Source: Fortra
Reports of cyberattacks continue to plague the news, from attacks on airport computer systems, to increased phishing scams around the holidays, to new ransomware groups entering the landscape at greater attack volumes. The increase of attacks, both in volume and severity, means your company needs the utmost protection – a single program or system simply won’t cut it anymore.
A layered approach to your cybersecurity can help you stop threats before they can become attacks.
Reason 1: Identify, Exploit, and Predict Security Weaknesses and Their Impact
By layering different cybersecurity products, you are getting a robust program while taking an offensive cybersecurity approach, rather than a reactive approach. By putting defenses and security operations to the test with a full attack simulation, you see the whole picture at one time. You’ll see where vulnerabilities lie, prioritize remediation, undercover potential post-attack scenarios and costs, test your employees to see who is susceptible to falling victim to a threat, and more. Then, you can fix areas of weakness before threat actors can find them and potentially cost your company hundreds of thousands of dollars.
Reason 2: Allows You to Focus on Real Threats
With the information from your simulations and tests in hand, you can use the Common Vulnerabilities and Exposures database to discern which vulnerabilities pose a real threat and should be remediated first so damage from exploitation is minimized. If you’re not sure how to address the vulnerability, that’s ok! That’s what the database is for – you can coordinate efforts with IT and cybersecurity professionals to ensure vulnerabilities are addressed properly.
Cut through the clutter and allocate resources efficiently and effectively. This is immensely important for companies with a small or limited IT team – don’t waste time nd money on low-risk threats when your resources could be better utilized on high-risk gaps.
Reason 3: Streamline and Centralize Your Vendors and Processes
The last thing you need to be doing is managing multiple vendors and processes. Why have one program for network scanning, one for penetration testing, and one for threat emulation when you could have them all together?
Consolidate your vendors by finding one who offers multiple solutions under their umbrella so you get a layered, offensive cybersecurity solution and seamlessly transition between products and features to get a full view of what’s going on in your network. Consolidation also allows you to reduce console fatigue by having everything in one place with solutions that are integrated and operating properly, helps ensure regulatory compliance and creates reports for security auditors.
Look for a vendor who will act as an extension of your team, with a dedicated account representative who empowers you and listens to you. You want a partner who continually innovates, introducing new features, benefits, updates and products as part of their commitment to delivering the best in cybersecurity protection.
Your Answer to a Layered, Offensive Cybersecurity Solution
At Digital Defense, we offer our Frontline VM, Core Impact, and Cobalt Strike products in one bundle. With the “Elite Bundle”, networks are scanned, vulnerabilities are prioritized, areas of potential exploitation are identified, and defense and security operations are tested with a full-attack simulation so you can stay one step ahead of threat actors.
Don’t risk your network becoming inaccessible due to an attacker’s overtake. Don’t risk your company’s trustworthiness and reputation being reduced thanks to an attacker spoofing your domain or brand name. Contact us to learn more or get started with your layered approach to offensive cybersecurity.
Source: Fortra
Financial institutions sit on a goldmine of sensitive data: corporate financial data, customer data, credit card data, and more. Digital innovations, complex IT processes, accelerated cloud adoption, remote workforces, and a growing reliance on third-party vendors contribute to a challenging risk landscape in banking and financial services. This has resulted in widened attack surfaces and vulnerable networks that are prone to security breaches.
In fact, a 2022 Sophos survey of 444 IT professionals working in the financial services sector revealed that 55% of organizations were hit by ransomware in 2021 – a 62% increase over the previous year.
And it’s not just ransomware. The overall IT environment in financial services has become even more challenging: 55% of organizations reported an increase in attack volume over the last year, 64% reported an increase in attack complexity, and 55% reported an increase in the impact of attacks.
A lot is at stake if the network security or data held by banking and financial services organizations is compromised. Oftentimes, an entire country’s economy can be impacted when a large bank or financial system is involved. Therefore, it becomes critical that access to financial resources is heavily guarded and access privileges are provided to users only as needed to carry out their roles and responsibilities.
A typical enterprise cybersecurity model relies on perimeter-based security. Once authenticated, a user can move laterally and access a broad range of resources within the network, regardless of their role and need for access. This can become a serious vulnerability if the user account is compromised: attackers get free access to financial data repositories and system apps. However, continual authentication and assessment of user identity, device health, and access policies can ensure more effective protection against security breaches in financial institutions.
ZTNA – or zero trust network access – is a game-changer for the financial services sector. It secures remote and hybrid workers, sensitive financial data, and networks and applications by constantly verifying user identity, device health, and access policies before granting access to network resources.
ZTNA eliminates vulnerable VPN clients, integrates device health, and allows granular access to resources defined by policies to give remote workers secure and seamless access to specific applications and data. Remote and external users and their devices are no longer implicitly trusted: they and their devices must earn trust constantly.
ZTNA policy can prevent a compromised device from connecting to applications and data, effectively preventing lateral movement and attacks like ransomware from getting a foothold on banking and financial services networks.
With Sophos ZTNA, you get the added benefit of a single-agent, single-console, single-vendor solution for both ZTNA and your next-gen endpoint protection. Sophos ZTNA uniquely integrates with Sophos Intercept X to constantly share status and health information with each other to automatically isolate compromised systems and prevent threats from moving or stealing data.
Sophos ZTNA removes implicit trust in your financial institution’s applications, users, and devices and allows segmented access to your systems and resources to just those who need it. Learn more at Sophos.com/ZTNA.
Source: Sophos
Datto, a Kaseya company, and a leading global provider of security and cloud-based software solutions purpose-built for managed service providers (MSPs), today released its 2023 State of Ransomware report, which surveyed nearly 3,000 IT professionals in small to medium-sized businesses across eight countries (the United States, Canada, the United Kingdom, Germany, the Netherlands, Australia, New Zealand, and Singapore). The report shows that SMBs are aware of increasing cyber threats and allocating resources and investing in areas such as network and cloud security.
Key takeaways from this year’s survey include:
- About a fifth of IT budget is dedicated to security and many are seeing increases in budgets. 47% of SMBs plan to invest in network security in the next year.
- Over 50% of SMBs have implemented AV and email/spam protection, with network and cloud security as the top areas planned for investment in the next year.
- 37% of respondents run IT security vulnerability assessments three or more times a year, with 62% running them at least twice a year.
- 69% of SMBs currently have cyber insurance and 34% of those without cyber insurance are highly likely to get it in the next year.
- 42% of SMBs with cyber insurance think it’s extremely likely that a ransomware attack will happen in the next year, while only 16% of SMBs without cyber insurance think the same.
“We’re seeing many businesses take more steps to protect themselves against threat actors,” said Chris McKie, VP of Product Marketing for Security and Networking Solutions. “Whether they’re investing in new security products or utilizing multiple security frameworks, most SMBs realize the very real threat that ransomware poses for their business, and they’re doing what they can to keep themselves safe.”
Only 3 in 10 of SMBs have a best-in-class recovery plan in place, with 52% of them claiming they have a standard recovery plan in place. MSPs can help their clients improve their disaster recovery plan by building out their security and backup offerings or requiring clients to have cyber insurance. Cyber insurance can offset the risks of potential breaches, something which became increasingly more important when many SMBs accelerated their digital transformation efforts during the COVID-19 pandemic.
Additional insightful findings:
- Rather be phishing. Compared to ransomware, respondents think phishing is more likely to occur in the next year. Many think this is the better alternative, as they believe its impact is lower than the impact of ransomware.
- Getting insured. Organizations with cyber insurance are more actively engaged in their cybersecurity. They have more IT support, more cybersecurity frameworks (CSFs), and more security solutions. They’re also more likely to have experienced a cyber security incident in the past.
- The right frame of mind. CIS framework is the most used cybersecurity framework, with 34% of respondents utilizing it. This is followed by CMMC (30%), COBIT (27%), and NIST (22%).
For the past seven years, Datto has surveyed IT professionals worldwide to gain insight into industry trends so that knowledge can then be shared with the IT community to better understand and service customers.
Click here to download the full report 2023 State of Ransomware report.
Source: Datto
We are excited to share that Sophos Intercept X Advanced with XDR has been named the top-ranked and sole leader in the Omdia Universe report for comprehensive extended detection and response (XDR) solutions.
The global research company ranked Sophos the highest in nearly all capabilities categories – excelling above competitive offerings with industry-best threat response, deployment, management, pricing, and licensing – with Sophos Intercept X Advanced with XDR delivering “a dominant showing in Threat Response and Resolution, an area in which other solutions were underwhelming.”
According to Omdia’s analysis in the report, Sophos should appear on organizations’ shortlist if they are in search of:
- An enterprise-grade solution with intuitive usability across the board
- Superior threat remediation with automated response actions for common scenarios
- Straightforward pricing and licensing, plus support from Sophos and its partners
Eric Parizo, Managing Principal Analyst, Omdia, commented “Omdia believes that the best Comprehensive XDR solutions deliver a fundamentally different approach to threat detection, investigation and response (TDIR) – one that’s faster, easier, more automated, and ultimately more effective. With this criteria in mind, it should be no surprise that Sophos Intercept X Advanced with XDR is the overall top ranked solution in the 2022-23 Comprehensive XDR Omdia Universe.”
Read the full report here.
Faster, more accurate detection and response
Sophos Intercept X with XDR combines powerful protection capabilities, including anti-ransomware technology, deep learning artificial intelligence, exploit prevention, and active adversary mitigations to stop attacks, with our best-in-class XDR tool for faster, more accurate detection and response.
Reduce time to detect and investigate
Sophos XDR lets you instantly get the information that matters via an extensive library of pre-written, customizable templates covering many different threat hunting and IT operations scenarios – or write your own. You have access to live device data, up to 90 days of on-disk data, 30 days of data stored in the Sophos Data Lake cloud repository, and an automatically generated list of suspicious items so you know exactly where to start.
Accelerate response
With AI-prioritized risk scores for each detection that leverage threat intelligence from Sophos X-Ops, Sophos XDR make it easy to identify the issues that need immediate attention. Detections include crucial information such as time and description of detection, process name, and hash, and you can easily enrich data by looking up a hash on VirusTotal, the reputation of an IP address on SANS, or by creating your own enrichments with any web service.
Armed with the information you need, Sophos XDR enables you respond quickly, even if the impacted device isn’t physically present. You can remotely access devices to perform further investigation, install and uninstall software, or remediate any additional issues via the cloud-based Sophos Central platform.
Coming soon: vendor agnostic telemetry integration
We recently added the ability to integrate vendor agnostic telemetry from third-party security technologies into Sophos Managed Detection and Response (MDR), providing unprecedented visibility and detection across diverse operating environments. The same vendor agnostic telemetry integrations will be available in Sophos XDR in 2023, further enhancing detection and response and enabling customers to increase return on their existing security investments.
Get started with Sophos XDR
To take Sophos XDR for a test drive, simply activate a free trial today. Organizations already using the Sophos Central platform can switch on Sophos XDR in just a couple of clicks directly from the Free Trials section of their management console. If you’re new to Sophos, start a free trial of Sophos Intercept X with XDR to explore both our protection and XDR capabilities.
24/7 managed detection and response using Sophos XDR
Sophos XDR underpins Sophos MDR, the world’s most popular MDR solution. If you’re looking for all the benefit of XDR combined with a 24/7 human-led threat detection, investigation, and response service delivered over 500 expert analysts, take a look at Sophos MDR. To learn more and discuss the best option for your organization, speak with our security advisers today.
Source: Sophos
In 2022, geopolitical unrest and an expanding online attack surface contributed to the emergence of several themes across the cyber landscape. Infrastructures associated with opposing ideologies were highly targeted, with government agencies, supply chains, and IOT devices falling victim to high-profile campaigns. Cybercriminals launched increasingly advanced attacks on vulnerable entities, with DDoS, ransomware, and hacking for a cause all consistently making headlines. And governments around the world began responding with laws and regulations to combat the escalating threats associated with cyberattacks on organizations big and small.
Looking ahead to 2023, Fortra’s security experts anticipate new cyber challenges will emerge, and in return, organizations and authorities will work together to better strengthen their security posture and response to threats. Below is a look at what our cybersecurity experts predict for 2023.
Hacktivism and Geopolitics
The conflict in Ukraine and impending recession are two examples of factors that drove an uptick in emotionally-driven cybercrime and recruitment in 2022. Experts believe that scams associated with current events, such as political instability and war, will continue to trigger emotional responses from bad actors, with government agencies and businesses as prime targets.
The economic downturn will cause negative impacts to the cybercommunity, as history dictates an increase in cybercrime during recessions. Security teams should be on the lookout for scams masquerading as government assistance programs and job recruitment as attackers look to take advantage of job seekers or those otherwise dealing with difficult circumstances. The consequences of online attacks during the recession could be exacerbated if cybersecurity operations experience cuts in an effort to curb costs.
These spending shifts may make it easier for threat actors to recruit insiders as a point of access to company networks. This method of compromising systems will increase as actors opt to pay disgruntled employees for credentials rather than penetrate a network on their own. Additionally, as data is shared more broadly across applications, the implications around who can access that data will become more and more a question of security at organizational and geopolitical levels.
Expanded operational information sharing between private and public entities will become more commonplace as security teams acknowledge the need for broader visibility into situations across the globe and how they may affect their organizations. Attack responses will mature as a result.
Expanded Attack Targets
In 2023, the attack surface will continue to expand for both public and private companies, and daily probings will represent the norm as criminals use tools to scan the internet for vulnerabilities in operational systems and IoT devices. Implementing only one layer of security controls to combat compromise will fail to be sufficient.
Security teams should expect to see phishing emails increase in volume and variety in 2023. Ransomware and malware will remain a consistent threat, and response-based campaigns that fail to flag indicator-based security controls such as BEC and spear phishing will increasingly make it into user inboxes. These attacks prove difficult to detect as they lack links and attachments, instead relying on correspondence-based calls-to-action to make it into user inboxes.
Identity deception will become a significant threat in the new year. Attackers are targeting businesses on external channels such as social media, SMS, and search engines, with criminals leaning heavily on impersonation as a tactic. Threat actors will also embrace Artificial Intelligence to enhance campaigns and determine targets. On a positive note, these unconventional attack methods will encourage the formation of cyber allies across entities to share critical information and tools that will aid in the detection of attacks.
Multi-factor authentication (MFA) will also be the target of increased exploits. Attackers will work to compromise integrity through techniques like verification-grabbing malware and SIM swapping. Organizations should consider implementing passwordless authentication to complement MFA.
Improved Attack Responses
In 2023, attack responses will be improved upon through better controls and progress toward zero trust. Organizations will move past basic controls implemented during the COVID-driven rush to digital transformation and invest time in securing data assets that need the most protection.
Sharing avenues will continue to open between organizations, and knowledge and controls over who has access to data will be prioritized through MFA, monitoring, zero trust, and encryption.
Ongoing training that is engaging and relevant will be critical to helping users identify attacks based on real world incidents and that comply with an organization’s policies.
Threat actors will continue to go after the lowest hanging fruit and target vulnerable entities within the supply chain, investing in mid-sized organizations less equipped from a security standpoint, including credit unions, insurance, and healthcare organizations. As a result, evaluations and audits of supply chains will increase. There will also be a magnifying glass on the vendor base and what is being done with the data provided to them. The expectations placed on vendors will only grow, as they will be expected to solve for multiple use cases.
Laws and Regulations
In 2023, we can expect more cross-government and cross-nation collaborations as cybersecurity is seen as a priority. At a non-federal level, the first round of grants for the $1 billion in FEMA and CISA BIL funding will be available for state, local, and territorial governments to help understand and mitigate infrastructure risks.
More laws and guidance are expected from a federal level, spanning topics from data privacy to ransomware payments, as CISA and the DOD engage in long-term strategic planning. The FTC just announced a new rule addressing the impersonation of government and businesses, which will help with the reporting and removal of offending websites, domains, advertisements, and more in the new year. In Europe, lawmakers will continue to iron out kinks in the General Data Protection Regulation (GDPR) to support smooth data transfer out of the EU.
According to Gartner, three quarters of the world’s population will be under privacy regulations in 2023. From a business perspective, increased presence in the digital space will likely lead to more violations as organizations struggle to navigate compliance and privacy regulations.
Cyber Insurance
Cyber insurance will become a priority for businesses in 2023, as a growing number of customers expect organizations to be policyholders. That being said, market correction due to increased premiums and justification of spend will likely take place, with organizations requiring more from providers.
The increased likelihood of a cyber attack on businesses in 2023 will also contribute to complicated pre-audits and renewal processes, as well as more disputes and reduced payouts. Insurers will continue to implement a growing number of controls on the companies before providing coverage, to make sure customers comply with standards set.
The tactics, techniques, and procedures of cybercriminals will become more differentiated in 2023, as attackers lean toward the end goal of either profit or outcome of a specific cause. These elements will require security teams to continuously examine world events through a broad lens and prepare for how activity might affect their company. As these threats persist, organizations should prioritize cyber security initiatives that will promote better standards and increased awareness of threats. Security teams should also establish more proactive means of securing systems through early detection of vulnerabilities, visibility across relevant channels, and broad controls.
Source: Fortra
More organizations trust Sophos for managed detection and response (MDR) than any other vendor, and we’re also the highest user-rated MDR solution.

G2, a leading customer review site for cybersecurity solutions, has named Sophos the top overall MDR solution in their Winter 2023 Report, rating us above 10 other leading vendors.
Specifically, Sophos MDR is the #1 rated solution in the following categories:
- Overall MDR Grid
- Mid-Market Grid
- Momentum Index
- Usability Index
- Implementation Index
Hear what a few Sophos MDR customers have to say about our service:
- “We get an extended team that not only monitors the security logs but also proactively does threat hunting and helps us protect our network against vulnerabilities.”
- “In general, the cyber-security suite performs well against continuous threats to our organization and offers us a centralized overview of this data in a highly efficient manner.”
- “Sophos MDR takes over the first level of threat hunting and response responsibility so our team can focus on our work”
Good cyber defense isn’t just about technology. The skills gap in cybersecurity continues to grow at an alarming rate, and many organizations are simply unable to stay ahead of well-organized, innovative, and increasingly industrialized adversaries.
With Sophos MDR, customers benefit from a 24/7 fully managed security operations service delivered by experts who specialize in detecting and responding to cyberattacks that technology alone can’t stop. Sophos is the first and only endpoint security provider to integrate both native and vendor-agnostic telemetry from third-party tools, accelerating threat detection, investigation, and response and enabling customers to increase return on their existing security investments.
In addition to our G2 recognition, we’ve been honored recently with further industry recognition for our innovation and delivery of superior cybersecurity outcomes. Sophos MDR successfully reported malicious activity across all 10 MITRE ATT&CK® steps in the inaugural MITRE Engenuity ATT&CK® Evaluation for security service providers. Plus, Sophos MDR was recognized as providing the Best Cyber Managed Threat Response for U.S. government organizations by American Security. To be recognized both by customers and analysts is tremendous validation of the superior cybersecurity outcomes we deliver to our customers around the globe.
We owe a huge thank you to our customers for their trust and commitment in selecting Sophos as their cybersecurity services partner. We don’t take this praise lightly and will continue to innovate relentlessly to adapt to any new threats the New Year brings.
Get started today
Sophos MDR is taking the market by storm. More than 13,000 organizations already rely on Sophos for 24/7 threat detection, investigation, and response, making it the world’s most trusted MDR service. Visit our website to learn more about both our service and third-party integrations and arrange a call with a Sophos security advisor.
Source: Sophos
While the shift from paper copies to digital storage has enabled organizations to increase efficiency in countless ways, bad actors have also launched countless attacks to steal private information. In order to protect this valuable data, many industries now have cybersecurity regulations. HIPAA has been expanded for healthcare and NERC applies to the utilities and energy sector, and higher education institutions must adhere to HEOA, to name a few. With so many new or expanded regulations—from SOX to the GDPR to the CMMC, cybersecurity teams have the added task of maintaining compliance, often with no new headcount to help with additional work.
For instance, many of these regulations either imply or specifically require pen testing as a way to evaluate an organization’s security posture and adherence. Requirement 11.3 of the Payment Card Industry Data Security Standard (PCI DSS), for example, states that a comprehensive pen testing program must be implemented.
It’s no surprise that, according to the 2020 Pen Testing Report, 67% of the cybersecurity professionals surveyed reported that compliance was the primary reason that they performed pen tests. Why is pen testing a key component of compliance initiatives, and what is the best strategy for meeting this requirement?
Why is Pen Testing So Crucial for Compliance?
By exploiting an organization’s infrastructure, pen testing can demonstrate exactly how an attacker could gain access to sensitive data. As attack strategies grow and evolve, periodic mandated testing makes certain that organizations can stay one step ahead by uncovering and fixing security weaknesses before they can be exploited. Additionally, for auditors, these tests can also verify that other mandated security measures are in place or working properly.
Meeting Basic Compliance Needs with Pen Testing Tools
Many falsely assume that in order to meet compliance needs, third-party testing is required. However, this typically is not the case. In fact, PCI DSS, which has some of the most explicit requirements for pen testing, doesn’t state that a third-party test is necessary.
Some organizations find that many aspects of compliance testing are straightforward and even repetitive. A pen testing tool like Core Impact provides an easy to follow and established automated framework that can support these types of tests as it doesn’t require extensive pen testing experience.
For example, one of the external tests listed in PCI DSS Requirement 11.3 are web application layer pen tests, which are needed to identify weaknesses like SQL injection or cross-site scripting (XSS). Core Impact’s automated One-Step WebApps Vulnerability Test identifies these weaknesses, as well as others like broken authentication, broken access control, and security misconfigurations. Additionally, Core Impact’s intuitive wizards and automation capabilities help testers gather information, execute attacks, escalate privileges, and more.
Some organizations find third-party services ideal for determining compliance needs and obtaining strategic support with initial tests. They then use pen testing tools to maintain compliance. For example, PCI DSS states that any vulnerabilities identified during testing must be fixed, and that a follow-up test is required to verify that they have been resolved. A third-party may conduct the initial testing, and then a security team member could deploy an automated test to validate these remediation efforts.
Finding the Right Third Party for Complex Testing
By using an automated tool for basic compliance tests, a third-party service can be utilized for more complex needs. For instance, PCI DSS and most other regulations require testing to take place after a major change to the operation environment. This may involve a test with multiple attack chains or other sophisticated tests to ensure that such changes didn’t cause new security weaknesses.
However, this requires an organization to be more discerning of the third-party they choose. Many firms focus on running simple tests with a wide scope—all of which can be handled by a security team using a tool like Core Impact. It’s important to find a service with experts that tailor their tests for your needs and goals so you can get the most value out of a third-party service.
The Future of Pen Testing and Compliance
As time goes on, it is likely that more regulations will be put into place—the GDPR, CCPA, and the CMMC have all been enacted in the last three years. With so many requirements to meet, it’s easy to start to see compliance as boxes to be checked. But by using your resources wisely—streamlining the routine with automation, and using expert services for more unique, complex issues—you can use compliance initiatives as an opportunity to advance your security posture to the next level.
See what Core Impact can do
Assess and testisecurity vulnerabilities throughout your organization with the most comprehensive penetration testing software.
GET A DEMO
GET THE GUIDE
Facebook. Twitter. Instagram. LinkedIn. YouTube. Pinterest. Mastodon. The list goes on. Whether you love or loathe social media, these platforms have become integral to how we communicate as individuals and businesses. Cybercriminals have also taken note, embracing these communication channels wholeheartedly to reach vast audiences quickly, anonymously, and cheaply, successfully defrauding targets of all stripes.
The stats aren’t pretty: According to the August 2022 Quarterly Threat Trends & Intelligence Report from Fortra’s PhishLabs and Agari, attacks per target increased 102% from Q2 2021 to Q2 2022. No industry is immune, but those in financial services continue to suffer the most extensive abuse with more than 68% of the attacks in Q2 2022 alone.
Social Media Platforms Are Hotbeds for Fraud
Threat actors range from amateur script kiddies flexing their skills to state-sponsored cybercrime outfits that constantly test and evolve their latest scams, optimizing techniques to achieve bigger cash-outs and evade takedown. Scammers excel at using social media to defraud victims with crafty and aggressive campaigns that can be difficult to spot, much less counteract and prosecute.
Social media and email account creation is simple and anonymous, and most people innately trust posts they believe to be coming from household names and institutions. Security leaders in all sectors are wise to educate themselves and their organization’s employees on how to detect these threats and what to do if they’re a victim of attack.
Common Social Media Threats
Companies that fall prey to scammers risk financial and data loss, reputational harm, erosion of employee and customer trust, and general business disruption. Below are three threat types to be aware of:
Impersonation
Threat actors work hard to spoof company brands and their employees. Executives in particular are popular targets as organizations increasingly encourage their leaders to establish a regular presence on platforms such as LinkedIn and Twitter. Scammers can easily access high-quality logos, imagery, and messaging online to emulate well-known companies and industry execs in a way that looks legitimate and encourages interaction.
Counterfeit Campaigns
With this type of brand abuse, threat actors create believable posts designed to lure victims to sham websites they control. Counterfeit campaign ads may entice shoppers to purchase discounted goods that will never arrive or get people to enter login credentials that criminals then capture on the back end. Oftentimes, when the social media platform or other authority investigates reported abuse, they find the ads have been modified to look generic.
Steganography
Photos and images are critical to the success of many social media campaigns and posts. Unfortunately, many can be harmful when clicked as they’re actually crawling with malicious code. Steganography is the practice of embedding messages, images, or files inside other messages, images, or files, and it’s prevalent on social media. Photos can be altered, deep faked, or configured to deliver malware onto the computer of someone who clicks the post.
How to Spot and React to Social Media Scams
It can be difficult to recognize social media scams, and even harder to take down threat actors. This means security awareness training and related prevention tactics are key to your defense strategy.
1. Build Relationships With Popular Platforms
Establish relationships with the social media providers you leverage so you have a direct point of contact. This will greatly improve your chances of removing malicious content should you find it. Part of this effort is also making sure you have evidence of fraud to submit. Make sure you capture all relevant examples, as the social media platform will require solid proof in the form of links, screengrabs, and more.
2. Implement Employee Security Awareness Training
Knowledge truly is power when it comes to recognizing potentially dangerous social media attacks as employees are your first line of defense. It’s important to train team members to have a healthy level of suspicion and encourage them to tap into their intuition when something doesn’t seem quite right or look legitimate online.
As threats are constantly changing, look to solutions that keep up with the latest scams and give employees hands-on practice with identifying threats. Security awareness training from Fortra’s Terranova Security delivers inclusive interactive content that focuses on building a security mindset among employees so they know how to handle social media, phishing, and other everyday risks.
3. Protect Against Harmful Images
Part of your employee education program should include the potential dangers of images generated both inside and outside the organization. Incorporating document sanitization capabilities with Fortra’s Clearswift Secure Email Gateway(SEG) and Clearswift Secure Web Gateway (SWG) will enable you to cleanse images and reduce the risk of steganography in a way that doesn’t disrupt productivity.
Go in-depth on the social media threat landscape with this digital risk protection playbook, which gives tips on how to identify and mitigate the top risks to your organization.
Get the guide.
Source: Fortra
“Sophos stopped everything in our tests,” says SE Labs.
We’re delighted to share that Sophos Endpoint ranked as industry best in SE Labs’ protection tests in the fourth quarter of 2022, earning AAA ratings across the board.
In both the Enterprise and SMB categories, we achieved…
- 100% rating for Protection Accuracy
- 100% rating for Legitimate Accuracy
- 100% rating for Total Accuracy
Here are the links to the latest reports: Endpoint Security: Enterprise | Endpoint Security: Small Business
These results are a testament to the market-leading protection technologies in Sophos Endpoint that deliver superior cybersecurity outcomes for over 250,000 organizations around the world.
Commenting on the results, Simon Edwards, CEO of SE Labs, said:
“With its 100% accuracy, Sophos validated that its endpoint security works. Sophos stopped everything in our tests.”
SE Labs is one of the few security testers in the industry that simulates modern-day attack tools and the tactics, techniques, and procedures (TTPs) that cybercriminals and penetration testers are currently using in the real world.
These include malware, targeted threats, and later-stage defense capabilities like behavioral, memory, and anti-malware scan interface (AMSI) detections and protections against “impact on objectives” behavior, such as ransomware file encryption. Sophos consistently defeated all attacks with 100% accuracy.
Following the results, Simon Reed, Senior Vice President of SophosLabs, said:
“These SE Labs’ AAA awards solidify our leadership position as an endpoint provider and showcase our ability to stop complex attacks that use a variety of techniques, tools, and objectives.”
The need to simulate modern-day attacks
Reputable third-party testing is an important tool to help organizations make informed decisions about their technology stacks and security investments. However, as attacks increase in volume and complexity, meaningful results can only be achieved when the tests reflect the real-world realities organizations face today.
As Edwards explains:
“It is essential for organizations to be able to rely on credible, full attack chain tests that duplicate real-world scenarios. It is not only about throwing a wider range of attacks at the products, but each step of the attack must be realistic, too. You can’t just make up what you think attackers are doing and hope you’re right. This is why SE Labs tracks cybercriminal behaviors and builds tests based on how attackers try to compromise victims.”
Sophos Endpoint: world-leading protection against advanced threats
With decades of cyberthreat intelligence, Sophos designs endpoint protection for real-time defense against modern-day advanced attacks. With a focus on preventing attacks as early as possible, Sophos’ cybersecurity strategy is to deliver multiple layers of protection to defend the entire attack chain against the many different threat vectors that attackers use to escalate and carry out attacks.
These technologies lead to superior cybersecurity outcomes for our customers, as proven by third-party testing from world-class firms like SE Labs.
Test drive Sophos Endpoint for yourself
Sophos Endpoint secures more than a quarter of a million organizations worldwide from active adversaries, ransomware, phishing, malware, and more. Speak to our security advisers to discuss how we can help you, and take a test drive today.
Source: Sophos
Gartner forecast a $600 billion global market in 2022 for technology that powers hyperautomation. Without a doubt, hyperautomation has quickly moved from an industry buzzword to the way companies of all sizes approach automation.
Surveys from the technology research and consulting firm show that a majority of CEOs and two-thirds of boards of directors are demanding operational excellence and growth that hyperautomation strategies can help bring. Gartner estimates that 56% of companies have four-plus simultaneous hyperautomation initiatives, while leading companies have more than 10 concurrent projects running.
Like any emerging technology term, hyperautomation can have widely divergent meanings, depending on who’s using, buying, or selling hyperautomation products and services. This article will wade into the concept of hyperautomation, how it compares to other automation tools, and how it can transform business processes.
What is Hyperautomation?
One definition of hyperautomation is the disciplined use of automation tools to automate anything and everything that can possibly be automated. By automating manual, time-consuming, and complex processes, hyperautomation increases employee efficiency and productivity. Companies also benefit through the ability to scale and flex as automation needs grow and evolve.
Another definition combines robotic process automation with other automation tools to increase the range and sophistication of projects. For example, adding workload automation, intelligent document processing, processing mining, or other automation tools to RPA would equal hyperautomation.
Finally, hyperautomation can also mean a continual integration of automation in a discover/automate cycle or loop that repeats as a company works through its processes.
Hyperautomation vs RPA: How Do They Differ?
Consider RPA the foundation to automation, streamlining manual processes by performing rules-based, repetitive tasks quicker and more efficiently than humans can. RPA bots can communicate with other business applications much like a human, pulling or pushing structured data to other systems and applications as appropriate to help with automated report generation, web browser automation, and much more. RPA tools are used throughout organizations to boost productivity, reduce errors, create efficiencies, and more.
But to achieve hyperautomation, you’ll need more than just RPA in your toolkit. Those tools can include workload automation, artificial intelligence, secure file transfer, and many more. While RPA has countless uses throughout organizations, the addition of complementary tools can greatly extend the range of possible automation projects. Combining RPA with other products allows companies to automate even more processes and take on more complex projects.
Intelligent Automation vs Hyperautomation
While intelligent automation is a component of hyperautomation, not all hyperautomation configurations include intelligent tools. Intelligent automation allows you to tackle more sophisticated automation scenarios where judgment and decision-making are needed. An example of this is intelligent document processing, which leverages machine learning and artificial intelligence to capture and transform unstructured data, making it more useable across your organization. RPA can then use that data to populate forms, make calculations, interact with other systems, and perform other automation tasks.
In contrast, combining RPA with workload automation, for example, can be considered hyperautomation but does not have an intelligent aspect. Intelligent automation includes tools used in hyperautomation, while hyperautomation is a concept that uses multiple tools to automate as many processes as possible.
The Fortra Approach to Hyperautomation
Many automation vendors create a closed ecosystem, forcing customers to often use less-than-ideal tools that can add limitations and expense to automation efforts. Despite claims to the contrary, no single tool can provide a comprehensive, end-to-end hyperautomation experience.
Buyers have many options for automating work which gives them the ability to take a best-of-breed approach to hyperautomation—looking for the best tool, no matter the vendor. At Fortra, we make it easier for users to achieve hyperautomation with a portfolio of automation products that integrate seamlessly with other systems and applications to fit a multi-vendor tech stack.
You get the benefits of working with one vendor for many products, while maintaining the ability to use the best-of-breed approach if you find a better fit or already have an existing solution in place. Fortra’s automation solutions include Automate for robotic process automation, Automate Intelligent Capture for intelligent document processing, JAMS for workload automation, GoAnywhere for secure file transfer, and Webdocs Forms Management for secure forms.
No automation solution can handle every task and every scenario. That’s why companies should look beyond a one-size-fits-all approach and examine flexible, scalable solutions that let companies automate in a way that best suits their unique needs and meets digital transformation goals.
Explore the Value of Holistic, End-to-End Automation
Automation solutions from Fortra can help your business gain efficiencies and scale the number and complexity of automation products. Learn more about our holistic approach to enterprise IT automation.
Source: Fortra
It’s that time of year when people in many parts of the world are look forward to spending time with family, friends, and taking a bit of a break. However, it’s also when bad actors, and adversaries switch into high gear, looking to take advantage of the fact that many networks are less utilized and less scrutinized over the holiday period. Ransomware attacks, to give just one example, typically increase at this time of year.
With that in mind, here are some quick and easy best practices to better protect your network while you take some well-deserved time out.
1. Shut down unneeded systems
This is especially important for any systems that offer RDP access as it is often used by adversaries as an entry point or tool to move laterally within a network. The same advice applies to IoT devices. If they aren’t needed, shut them down for the holidays. If you really need to have some systems with RDP access enabled, double-check and then triple-check the security.
If you haven’t already, consider ZTNA to secure access to your RDP systems and other applications. In fact, the holidays maybe the ideal time to start a Sophos ZTNA free trial for you and your team. At the very least, make sure any RDP solutions are protected with multi-factor authentication to prevent brute-forced or stolen credentials from being a point of compromise.
2. Update firewall and network infrastructure firmware
If you have a Sophos Firewall, we recently released v19.5 which includes a number of security enhancements, performance improvements, and new features such as:
- Xstream FastPath TLS encrypted traffic inspection
- SD-WAN load balancing
- VPN performance improvements
- High Availability enhancements
- New Azure AD integration for secure login
- And much more!
Regardless of your preferred vendor, make sure your firewall and other network infrastructure such as VPN concentrators, switches, and other devices are all running the latest release as they often contain important fixes for known vulnerabilities.
3. Call on Sophos Rapid Response if you experience an attack
If you experience an emergency incident over the holidays (or anytime), you can engage our fixed fee Sophos Rapid Response service. Our team of expert incident responders will help you triage, contain, and eliminate active threats, and remove all traces of the attackers from your network. Whether it is an infection, compromise, or unauthorized access attempting to circumvent your security controls, we have seen and stopped it all. Sophos Rapid Response is available 24/7/365, including over the holiday period.
Download the network security best practices whitepaper
For our full list of network security best practices to protect your network from ransomware, download our new whitepaper. In the meantime, I wish you a happy – and secure – holiday season!
Source: Sophos
We are excited to share that Sophos has been named the best managed detection and response (MDR), endpoint, network, and anti-malware security provider for U.S. government organizations by American Security Today.
Sophos is a platinum winner in the 2022 ‘ASTORS’ Homeland Security Awards, which honor market leading solutions used by government agencies and entities, as well as businesses of all sizes across the United States.
The cybersecurity of our nation is at a critical inflection point amidst an escalation of ever-changing, complex cyberattacks, as evidenced in the Sophos 2023 Threat Report. Sophos is committed to helping federal agencies advance their cybersecurity defenses with both innovative solutions and human-led threat detection and response, and these latest recognitions are validation that Sophos is arming frontline teams in the U.S. with industry-best protection.
As explained by Tammy Waitt, editorial director at American Security Today, “‘ASTORS’ nominations are evaluated on their technical innovation, interoperability, specific impact within the category, overall impact to the industry, relatability to other industry technologies, and application feasibility outside of the industry. Winners are selected by our American Security Today expert panel of judges, and the ‘ASTORS’ Homeland Security Awards are presented at the Platinum, Gold, Silver, and Bronze levels.”
Sophos reigns as providing the Best Cyber Managed Threat Response with Sophos MDR, an industry-leading service used by more than 13,000 organizations for 24/7 threat hunting, detection and response. Our recently expanded service now integrates telemetry from third-party security technologies, providing unprecedented visibility and detection across diverse operating environments.
Sophos further leads as the Best Endpoint Threat Solution and Best Anti-Malware Solution with Sophos Intercept X with XDR, and the Best Network Security Solution with Sophos Firewall. These offerings are part of the Sophos Adaptive Cybersecurity Ecosystem where they share real-time threat intelligence with Sophos’ broad portfolio of solutions and services for faster and more contextual response to attacks. Sophos’ security solutions are further powered by predictive, real-time and deeply researched threat intelligence from Sophos X-Ops, and are easily managed in the cloud-native Sophos Central platform or by Sophos MDR.
A list of winners is available online.
Source: Sophos