News
We’d like to present a new version of our email archiving software today: Version 23.4 of MailStore Server, the MailStore Service Provider Edition (SPE), and MailStore Home is now available. Read this blog article to get all the details on the new features and availability of our email archiving solutions.
New Features in MailStore Version 23.4
MailStore V23.4 has many new features that administrators and users of our email archiving solutions MailStore Server, MailStore SPE and MailStore Home can look forward to. These are the new features in detail:
Archiving of NDRs From an Alternate Journaling Mailbox
This feature facilitates data recovery for customers of MailStore Server and the MailStore Service Provider Edition using Microsoft 365 / Exchange Online in cases where a MailStore Gateway was unavailable and NDRs (Non-Delivery Reports) were sent to a fail-over mailbox (or an alternate journaling mailbox). In cases like these, MailStore was unable to extract the journal report from the NDR until now. By adding another archiving profile, journal reports embedded in NDRs can now be automatically imported to your MailStore archives. This avoids cumbersome resending and thus enhances the usability and overall reliability of your archiving solution. We recommend setting up two separate MailStore Gateways, one for the journaling mailbox and the second one as an alternate mailbox to benefit from this enhancement.
Deleting Flagged Emails
With this new MailStore version it is now possible to remotely delete an email in your email server mailbox, even when a user had flagged it in their mailbox, e.g. in Outlook. In previous versions, MailStore has generally never removed any flagged emails from the email server unless they were marked as “completed”. The logic behind this policy is that flagged emails may require follow-up work by a user. However, practice shows that MailStore admins still want to remove such emails for a variety of reasons. This option is now available in MailStore Server, the MailStore Service Provider Edition and MailStore Home for all M365 and Exchange archiving profiles as well as all IMAP-+ based archiving profiles (generic IMAP; Gmail, Google Workspace, MDaemon, Icewarp, Kerio).
Enhanced Archiving Profiles
This enhancement gives admins more flexibility when defining archiving profiles. While you might typically want to archive all emails or emails older than a certain date, there are cases where you will need to archive just those emails that were created after a certain date. For instance, this is useful if you have 15+ years of email history, but only want to archive emails created over the last 10 years. The new filter option within the archiving profiles is also useful if you want to migrate archives. This feature is now available in MailStore Server, the MailStore Service Provider Edition and MailStore Home.
API Improvements
We have made enhancements to the APIs of MailStore Server and the MailStore Service Provider Edition that help administrators to better monitor a MailStore installation (GetWorkerResultReport) and upgrade all archives stores (UpgradeStores). In addition, MailStore Server administrators can now use the API to replace server certificates (SetServiceCertificate).
Other Improvements
With Simple Authentication and Security Layer (SASL) for IMAP multi-mailbox archiving, you can now select various user id formats. Improved auto-discovery for Microsoft 365 facilitates the archiving of public folders. In addition, there are several security updates and bugfixes.
Finally, we want to advise you that Windows Server 2012 and 2012 R2 have reached end of support at Microsoft and thus cannot be supported by MailStore either. We recommend an upgrade if you are still using such EOL servers. Additionally, support for Exchange Server 2003 has finally been removed.
Updated Certification: Meeting Data Privacy Requirements
As usual, the latest version of our software, Version 23.4 of MailStore Server and the MailStore SPE, has been certified by an independent data privacy expert.
The certification takes into account all relevant aspects of the European General Data Protection Regulation (GDPR) and affirms that, when used appropriately, both MailStore Server and the MailStore SPE meet all the requirements governing the processing of personal data set out in the GDPR.

You can request a copy of the official GDPR audit certificate from sales@mailstore.com.
Registered MailStore partners can download the certificates from our Partner Portal or request it by email from partners@mailstore.com.
Availability
You can download the new version of MailStore Server, the MailStore Service Provider Edition, MailStore Home and MailStore Gateway free of charge from our website.
If your MailStore Server Update & Support Service has expired, please contact us to purchase an upgrade that will allow you to use the latest version of MailStore Server. Read here to find out about other good reasons for having an active Update & Support Service in place.
Interested companies can also download MailStore Server Version 23.4 as part of a free, 30-day trial. If you are an MSP and are interested in offering email archiving as a service based on the MailStore SPE, please contact our sales team at partners@mailstore.com. Alternatively, you can sign up as an authorized MailStore Partner with us right now for free.
Source: MailStore
Being in the cybersecurity industry, you get visibility to a lot of negativity. This includes things like the latest high-profile organization to suffer a ransomware attack, a breach where some ridiculous number of identities get exposed, or the introduction of some new criminal organization. Despite the prevalent negative discourse in cybersecurity, various factors like education, shifting priorities, and collaboration offer credible reasons to be optimistic about the field’s future.
Education Closes the Cybersecurity Skills Gap
It’s no secret there is a workforce gap, and the number that gets thrown around regularly is somewhere between 3 and 4 million unfilled cybersecurity jobs globally. According to the ISC2 2022 study, this number is 3.4 million, representing a 26.2% increase from the prior year. This means that globally, the gap is widening.
However, when broken down further, we can see examples of closing this talent gap, and education plays a major role in that. For example, the LATAM market closed its workforce shortage gap by 26.4%, which is driven largely by cybersecurity-specific post-secondary educational programs implemented in the past few years. And this is not the only example.
Cybersecurity and STEM are being introduced into the grade school curriculum at an earlier age. These kids are being taught foundational elements. Having them reinforced during their school years will help create security-aware citizens and professionals that enter the workforce. This level of awareness will also reduce successful social engineering and phishing attacks in future years.
Higher education is embracing cybersecurity as well. Vendors are working with colleges and universities to create programs and internship opportunities that count towards graduation. This solid foundation of coursework and experience will be desirable for employers as these students can ramp up quickly.
Finally, governments and transnational institutions have also embarked on a mission to educate their workforce. The European Commission launched Cybersecurity Skills Academy, and the U.S. Government unveiled the National Cyber Workforce Education Strategy. I expect other regions to follow suit and invest in similar workforce development programs to address the cyber workforce gap and the evolving cyber threats.
A Culture of Collaboration
A few years ago, I had the privilege of working with two former CISOs, one from a large financial institution and the other from a major telecom company. I learned a lot from them, and what struck me the most was that both collaborated with their peers from rival companies. At first, I was skeptical, thinking that working with competitors was counterintuitive, given that we all compete for the same audience and business.
However, they explained that although their companies competed commercially, they faced the same cybersecurity threats and challenges. The CISO from the financial institution mentioned that he had a monthly meeting with CISOs from other financial institutions. The CISO from the telecom company said that he also had a similar collaboration with his counterparts, and this kind of partnership significantly improved everyone’s overall security posture.
Fast forward to this year at RSA, the theme was “Stronger Together”. There were lots of sessions around collaborating in new ways, which sometimes may be uncomfortable but required as we all fight the same cyber adversaries. For example, Fortra collaborated with Microsoft Digital Crimes Unit and Health-ISAC earlier this year to help take down malicious actors. Each organization was working independently to fight ransomware gangs around the world. However, by joining forces, we have identified and taken down malicious infrastructure these gangs use to distribute ransomware.
As my colleague Josh Davies, principal technical manager at Fortra, notes, “Security is not a challenge we solve in isolation. We all face common threats, and every successful breach may result in the re-investment of ill-gotten gains, only making the threat more difficult to tackle. Collaboration is key, and organizations and security vendors/specialists alike have shown positive steps in sharing resources, experiences, intelligence, and best practices.”
Moving Beyond Security: Cybersecurity Resilience
It is a well-known fact in the cyber community that there is no such thing as 100% prevention. However, stakeholders and executives in the corporate business domain have struggled to comprehend this concept. With the increasing recognition of cybersecurity as a credible business risk and a top priority for all board members, business leaders have come to realize that organizations need to be prepared for the inevitable. This means that companies must be able to withstand and quickly recover from an attack.
As a result, organizations have shifted their focus from trying to keep all threats out, hoping prevention has worked, to establishing detection and response strategies that can identify a compromise before it progresses to a news story with a data breach or ransomware extortion.
This wider acceptance can be seen in regulations like DORA, which lists resilience as the ability to both withstand AND quickly recover from a successful attack. In fact, organizations with a mature detection and response program can actually come out of a compromise with minimal impact and a stronger security posture after performing mitigations, ultimately emerging more secure than they were before the compromise.
The EU Cyber Solidarity Act is another example that aims to address this issue by creating cross-border security operations centers throughout the EU. These centers will detect and respond to large-scale attacks, making it easier for businesses to recover from such incidents.
Source: Fortra
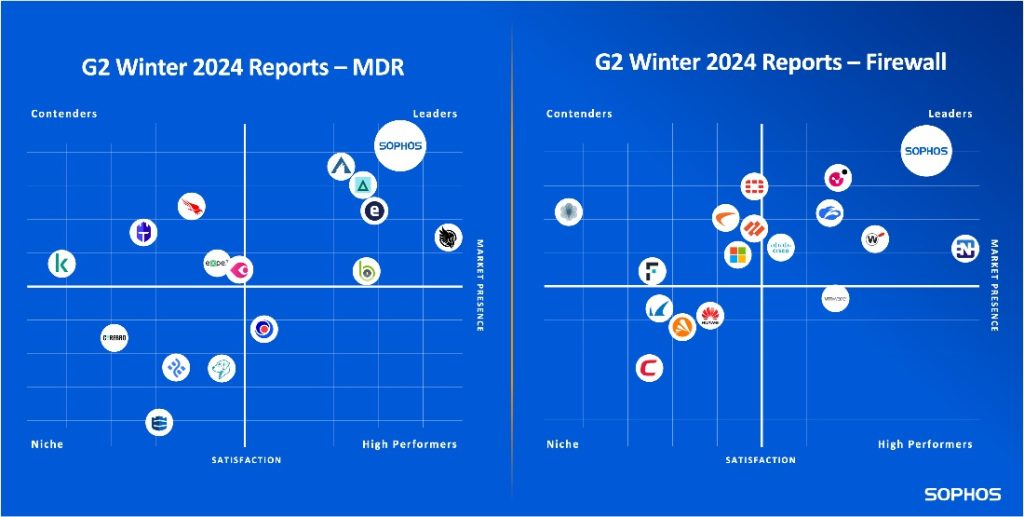
G2 just released their Winter 2024 Reports, and Sophos is the only cybersecurity provider named a Leader across the G2 Grid® Reports for Endpoint Protection Suites, Endpoint Detection and Response (EDR), Extended Detection and Response (XDR), Firewall Software ,and Managed Detection and Response (MDR). This latest recognition makes Sophos the only vendor named a Leader in these five key cybersecurity categories through all G2’s 2023 Seasonal Reports. Additionally, G2 users also rated Sophos the #1 overall MDR and Firewall solutions once again.
Independent Sophos Customer Validation
G2 distinctions and rankings are based on independent, verified customer reviews on G2.com, the world’s largest software marketplace and peer review platform. In G2’s Winter 2024 Reports, Sophos was named an Overall Leader in five categories, as well as a Leader in 14 individual market segment Grids:
- Endpoint Protection Suites: Overall, Mid-Market, and Small Business Grids
- EDR: Overall and Mid-Market Grids
- XDR: Overall and Mid-Market Grids
- Firewall: Overall, Enterprise, Mid-Market, and Small Business Grids
- MDR: Overall, Enterprise, and Mid-Market Grids
We are honored that our customers have recognized our services and products, and we thank them for putting their trust in us.
Delivering Defense in Depth for Today’s Businesses
As adversaries have become more sophisticated and elusive, defenders should implement a defense-in-depth strategy that includes protection, detection, and response at every point along the attack chain to cover their entire environment. This layered approach should be inclusive of endpoint, network, email, and cloud security, as well as threat hunting and remediation services by security experts.
The fact that IT and security professionals recognize Sophos as the Leader across these key categories is validation that Sophos delivers the best and most comprehensive set of products and services required for modern day cybersecurity.
Uniquely, all Sophos customers are protected by Sophos X-Ops, a joint task force that brings together deep expertise across the attack environment from frontline threat hunters and incident responders to deep malware and AI specialists. Together they provide unparalleled insights into how threats are built, delivered, and operate in real time. Armed with this deep understanding, Sophos is able to build innovative, powerful, and effective defenses against even the most advanced threats.
Additional Sophos Customer and Analyst Validation
Alongside our G2 recognition, Sophos solutions are widely recognized by customers and the analyst community, including:
Sophos Endpoint
- Named a Leader in the 2022 Gartner® Magic Quadrant™ for Endpoint Protection Platforms for the 13th consecutive time
- Named a 2023 Gartner® Customers’ Choice™ for Endpoint Protection Platforms with a 4.8/5 customer rating on Gartner Peer Insights
Sophos Extended Detection and Response (XDR)
- Recognized as the #1 overall leader in the Omdia Universe for Comprehensive Extended Detection and Response (XDR)
- Delivered exceptional results in the 2023 MITRE Engenuity ATT&CK Evaluations (Round 5: Turla).
Sophos Firewall
- Named a 2023 Gartner® Customers’ Choice™ for Network Firewalls with a 4.7/5 rating on Gartner Peer Insights
- Recognized as a Strong Performer on the Forrester Wave
Sophos Managed Detection and Response (MDR)
- Named a 2023 Gartner® Customers’ Choice™ for Managed Detection and Response Services with a 4.8/5 rating on Gartner Peer Insights
- Top performer in the 2022 MITRE Engenuity ATT&CK Evaluation for Managed Services
Select Customer Reviews
Sophos MDR is a must. My team is small, and it’s great knowing if we’re all busy putting out IT fires, MDR is ready to take action if my team is unable to respond immediately to suspicious activity. This is much better than relying on alerts that we need to investigate. Of course, we have alerts enabled, but setting the thresholds for the alerts is nearly impossible. The alerts are either not sensitive enough and we’ll miss something important, or the alerts are too sensitive and we receive too many to investigate. Sophos MDR didn’t just solve this problem; it completely removed it. More.
The 24/7 threat-hunting service from Sophos MDR stands out as a feature of utmost importance, providing around-the-clock vigilance and prompt reaction to emerging threats. Its true value lies in the managed remediation process – unlike other solutions that merely notify, Sophos steps in to effectively stop and rectify the issue and then informs us about the incident. This proactive and hands-on approach is what sets Sophos MDR apart and makes it a highly appreciated solution. More.
“…a real threat for hackers !!! [Intercept X] is easy to use and has a lot of the world’s best technologies. CryptoGuard feature is the essential feature. More.
[Intercept X] provides a comprehensive solution with AI and machine learning-based detections and prevention. More.
Overall, Sophos Firewall is a robust security solution that offers advanced threat protection, easy management, and granular control over your network traffic. Its features help you secure your network, improve network performance, and prevent cyberattacks, making it an ideal choice for businesses of all sizes. More
Sophos Security Portfolio
Sophos’ portfolio of managed security services and solutions – including Sophos MDR, Sophos Intercept X, Sophos XDR, and Sophos Firewall – are part of the Sophos Adaptive Cybersecurity Ecosystem where they share real-time threat intelligence for faster and more contextual and synchronized protection, detection and response. They’re powered by Sophos X-Ops threat intelligence, a cross-operational task force of more than 500 security experts within SophosLabs, Sophos SecOps and SophosAI.
Solutions are easily managed in the cloud-native Sophos Central platform, where users can oversee installations, respond to alerts and track licenses and upcoming renewal dates via a single, intuitive interface. Organizations can also leverage Sophos MDR as a comprehensive threat hunting and remediation service. Free trials are available at Sophos.com. Any organizations under active attack and needing urgent support, should contact the Sophos Incident Response team. For timely information about threat intelligence and attacker behaviors, follow Sophos X-Ops’ latest research.
Source: Sophos
Fortra’s Terranova Security’s chief information security officer explains the dangers associated with the advancement of AI and how businesses can better prepare against attacks.
The rise of artificial intelligence is being accompanied by a rise in consciousness of the risks to cybersecurity.
“Hackers are utilising AI to develop more advanced attacks and evade detection from security tools,” says Theo Zafirakos, chief information security officer at Fortra’s Terranova Security. “Businesses need to be aware of the various ways that hackers may manipulate them, from malware designed to bypass detection to more sophisticated and targeted phishing attacks.”

For instance, scammers are now exploiting AI technology to impersonate people by creating voices that convincingly portray victims’ coworkers. This phishing technique can deceive employees into providing sensitive information.
AI can also be used to gather sensitive data. “Every industry is grappling with an enormous amount of data,” says Zafirakos. “Attackers are employing AI to analyse and collect data more quickly. Healthcare providers, manufacturers and financial services organisations handle large amounts of data to drive innovation and inform decision-making. Bad actors will target that sensitive data to either disrupt operations or gather further information.”
There are steps that organisations can take to protect themselves. One of the most important is cybersecurity awareness training, which can enhance an enterprise’s ability to identify and mitigate AI-related security threats.
“As with any other cybersecurity concern, knowledge and proper employee education are the best defence,” says Zafirakos. And AI can be put to good use here. “Chatbots can be employed to educate users on how to protect their devices and personal information. Similarly, machine learning on employee awareness levels can be utilised by team leaders to identify gaps in employee knowledge of security awareness.”
Furthermore, employees can learn to detect AI-enabled or AI-generated attacks and avoid falling victim. They can also learn about the acceptable use of AI tools for business operations in the process, such as enhancing productivity. For example, they can learn to fact-check emails through phishing awareness training and avoid opening unsolicited software that could be AI-generated malware.
“Detection and prevention technologies, such as intrusion protection systems and intrusion detection systems, and user-behaviour analysis can monitor and alert users to any suspicious activity on their networks or devices in real time,” explains Zafirakos. “AI can also be used to automate threat responses to swiftly mitigate damage and prevent its spread to other infrastructure components. This will significantly reduce the costs associated with data protection, awareness training and data-breach responses.”
As AI continues to evolve, organisations must take proactive measures to stay ahead of emerging threats and vulnerabilities.
“Understanding how AI can disrupt or improve an organisation is essential for successful operations,” says Zafirakos. “I urge business leaders to establish an internal acceptable use policy for AI tools so that employees can enhance their workloads, and to incorporate content related to AI risks and threats within their security awareness programmes so that everyone is equipped to protect against AI-related attacks.”
Source: Fortra and Technology Record
Global cybersecurity software and services provider Fortra today introduced a transformative advancement in email security with the launch of Cloud Email Protection. This integrated cloud email security (ICES) solution sets a new standard by seamlessly blending artificial intelligence, threat intelligence, and automated remediation to stop advanced threats that elude traditional defenses and make it through to corporate inboxes.
In a landscape where legacy email security tools are not optimized for cloud environments and struggle to combat advanced threats, Cloud Email Protection emerges as the industry’s first cloud-native solution offering a comprehensive, flexible email security stack. This will include inline secure email gateway functionality, advanced threat detection, and post-delivery remediation – all unified within a single, robust platform.
“Bad actors routinely target and exploit organizations through advanced attacks and to be frank, traditional email security tools have left them ill-equipped,” said Billy Smith, Managing Director, Digital Risk and Email Protection, Fortra. “In addition, cloud versions of these tools are often not optimized for cloud environments, keeping organizations from realizing the resiliency, efficiency, and scale they want to achieve.”
“Drawing on the strengths of Agari, Clearswift, and PhishLabs, Cloud Email Protection will solve these issues, allowing organizations to simplify and scale their email security while putting a stop to threats such as business email compromise, spear phishing, and targeted social engineering,” continued Smith.
Apria Healthcare Group, a leading provider of home healthcare equipment and related services across the United States, was one of a few organizations to receive early access to the new solution and is already reaping the benefits:
“When our CFO was singled out by a threat actor and her likeness was used to falsely convince our Accounts Payable Lead to wire funds offshore, we had only minutes to act,” said Emmanuel Appiah, Senior Information Security Analyst, Apria Healthcare Group. “Fortunately, Cloud Email Protection detected and stopped the threat before any damage occurred. It also scanned the remainder of our inboxes for duplicated incidents. The peace of mind that Fortra provides empowers us to go about our day knowing we are protected, even from social engineering attacks that are hard to detect.”
“At Fortra, we are committed to providing our customers with the very best protection in a streamlined and simple way,” said Kate Bolseth, CEO, Fortra. “Staying true to our mission, Cloud Email Protection is a platform-based solution that makes security management easier for our customers while also improving their defenses. Although the attempted attack on Apria Healthcare Group was unfortunate, we are proud that Cloud Email Protection kept the company safe and secure.”
For more information about Fortra’s Cloud Email Protection, click here.
Source: Fortra
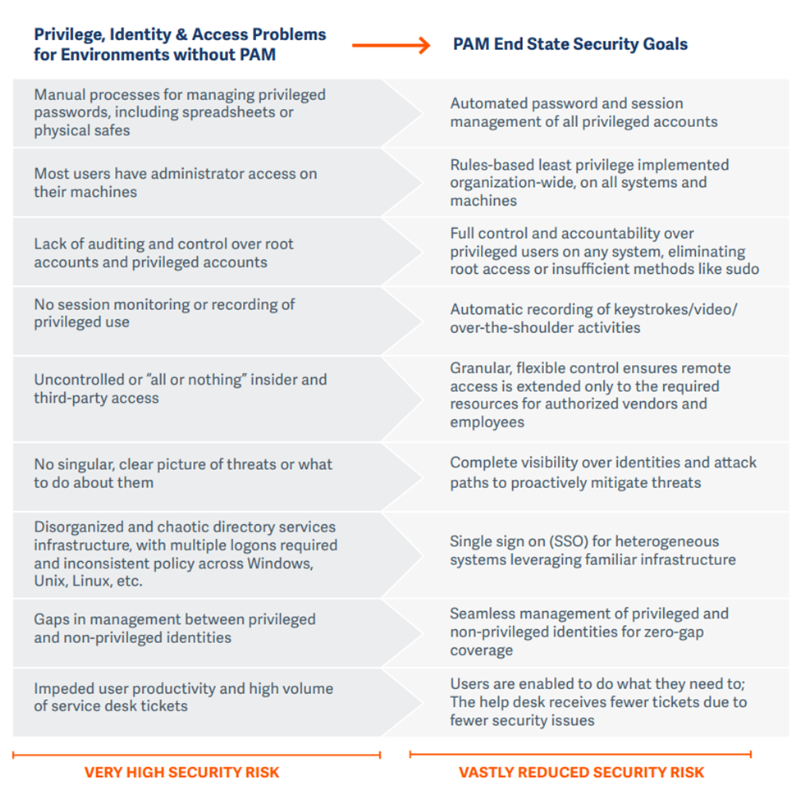
Identity is the new perimeter — and privileged access management (PAM) is the keystone of modern identity and access security. No identities—human or machine—are more imperative to secure than those with privileged access to systems, data, applications, and other sensitive resources.
Beyond that, PAM is also essential for protecting your entire identity infrastructure, including your backend IAM/IGA tools themselves.

Attackers are rapidly advancing in agility beyond just simple automation. Machine learning (M/L) and Artificial intelligence (AI) are changing the game, vastly enhancing attacker toolsets and empowering human-operated attacks. Generative AI is in its nascent stage, but already is helping attackers accelerate their workflows, while becoming more targeted and sophisticated. For instance, attackers are using AI to execute multi-step social engineering exploits to impersonate identities and their attributes. And of course, it’s just as important for organizations to protect their own AI and M/L data from being stolen or poisoned.
Yet, the fact remains that almost every attack today requires privilege for the initial exploit or to laterally move within a network. Here’s one simple but highly illustrative proof point of the modern privilege challenge: In 99% of pentesting cases conducted by IBM’s X-Force Red, cloud identities were found to be over-privileged, enabling the pentesters to quickly compromise client cloud environments.
How to Assess Your Privileged Access Security Needs: A PAM Buying Guide & Comparison Checklist
To help security buyers clearly understand the problems PAM can solve and how deploying privileged access management capabilities translates into concrete business outcomes, BeyondTrust has published a completely updated edition of our Buyer’s Guide for Complete Privileged Access Management (PAM). Use this comprehensive asset to assess your privileged access security needs and map them to modern privilege management solutions.
The Guide starts with the PAM basics that will mitigate most risks, then delves into other significant use cases, finishing with emerging use cases you should know. Our experience over many thousands of deployments has shown that there is a fairly typical path that most customers follow, but ultimately, your next steps in PAM will depend on where you are now, and the risk-based decisions that inform your goals.
Use The PAM Buyer’s Guide to help you answer:
- Where to begin your privileged access management (PAM) project
- How to progress to a better security posture
- What business outcomes to expect by implementing various PAM and identity security controls
- What a complete solution looks like (hint, it goes beyond traditional PAM to incorporate CIEM and ITDR)
As you evaluate privilege management solutions—or any enterprise solution for that matter—we recommend assessing each through the lens of:
- Total cost of ownership: Does it result in time-savings (such as replacing manual processes with automation) and allow you to re-deploy resources for other initiatives? What are the direct and indirect costs to support the solution over its lifetime in your environment?
- Time-to-value: How soon will it help you measurably improve security controls and dial down risk? How soon will you realize a positive business impact (freeing up time for end-users, streamlining processes, enabling the organization to confidently embrace new technologies and business initiatives)? How long will it take to achieve your end-state goals with the solution? What are the chances/risks of it ending up as shelfware?
- Scalability: What are your needs around scale? A solution could meet some of your needs around scale, but not all of them. For example, in evaluating privileged account and session management (PASM) solutions, your needs for scale around managing privileged user passwords might be different than your needs for managing SSH keys, DevOps secrets, application credentials, service accounts, or machine passwords. Some solutions will only be able to manage one of these types of passwords in the first place. Other solutions might offer broader coverage across diverse password types and meet your needs for scale around some of these capabilities (i.e. privileged user password management), but fail to meet your scalability needs around other capabilities (i.e. SSH key management, application password management, DevOps secrets, etc.). On top of this, if auditing all privileged activity is important to you (it should be), few PASM solutions can scale to manage and monitor thousands of concurrent sessions. So, it’s important to understand the various facets of your scalability needs upfront.
- Integrations/Interoperability: How does it integrate with the rest of your security ecosystem (IAM, service desk, SIEM, SOAR, etc.)? Does it help you make better decisions on risk? If it only works well as a standalone/point solution, it’s probably only a stopgap versus a long-term solution. On the other hand, if the solution has synergies with your existing security solutions, it will also help you maximize existing investments.
- Longetivity: Will the solution vendor grow with you or even pull you towards growth through security enablement? Is the vendor resourced to evolve capabilities and deepen feature-richness to meet the PAM use cases of tomorrow?
The Buyer’s Guide will help you gain perspective and context on how to quantify each of these values.
Prepare for your Privileged Access Management Project: Download The Buyer’s Guide
What Else will this Guide Cover?
- A 6-step approach to holistic privileged access management and improved identity security
- The key PAM capabilities you should prioritize to reduce security risks, improve operational performance, and simplify your path to achieving compliance initiatives
- PAM considerations for specialized use cases (OT security, DevOps, robotic process automation, zero trust, cyber insurance qualification, and more)
- 7 differentiators that make BeyondTrust stand out from other vendors in the space—including a section on how we have genuinely revolutionized the PAM space
- Your own PAM Buyer’s Guide checklist template to help you identify your needs and assess and compare vendors
Each of the 6 steps in the guide represents a core area, that when implemented, enhances an enterprise’s control and accountability over the identities, accounts, assets, users, systems, and activity that comprise its privilege environment, while eliminating and mitigating many threat vectors. Some organizations may try to implement many or all of these areas at once or within a short timeframe, but the more common approach is to phase in controls for one or a few areas of PAM at a time.
Source: BeyondTrust
Generative artificial intelligence technologies such as OpenAI’s ChatGPT and DALL-E have created a great deal of disruption across much of our digital lives. Creating credible text, images and even audio, these AI tools can be used for both good and ill. That includes their application in the cybersecurity space.
While Sophos AI has been working on ways to integrate generative AI into cybersecurity tools—work that is now being integrated into how we defend customers’ networks—we’ve also seen adversaries experimenting with generative AI. As we’ve discussed in several recent posts, generative AI has been used by scammers as an assistant to overcome language barriers between scammers and their targets generating responses to text messages as an assistant to overcome language barriers between scammers and their targets, generating responses to text messages in conversations on WhatsApp and other platforms. We have also seen the use of generative AI to create fake “selfie” images sent in these conversations, and there has been some use reported of generative AI voice synthesis in phone scams.
When pulled together, these types of tools can be used by scammers and other cybercriminals at a larger scale. To be able to better defend against this weaponization of generative AI, the Sophos AI team conducted an experiment to see what was in the realm of the possible.
As we presented at DEF CON’s AI Village earlier this year (and at CAMLIS in October and BSides Sydney in November), our experiment delved into the potential misuse of advanced generative AI technologies to orchestrate large-scale scam campaigns. These campaigns fuse multiple types of generative AI, tricking unsuspecting victims into giving up sensitive information. And while we found that there was still a learning curve to be mastered by would-be scammers, the hurdles were not as high as one would hope.
Using Generative AI to Construct Scam Websites
In our increasingly digital society, scamming has been a constant problem. Traditionally, executing fraud with a fake web store required a high level of expertise, often involving sophisticated coding and an in-depth understanding of human psychology. However, the advent of Large Language Models (LLMs) has significantly lowered the barriers to entry.
LLMs can provide a wealth of knowledge with simple prompts, making it possible for anyone with minimal coding experience to write code. With the help of interactive prompt engineering, one can generate a simple scam website and fake images. However, integrating these individual components into a fully functional scam site is not a straightforward task.
Our first attempt involved leveraging large language models to produce scam content from scratch. The process included generating simple frontends, populating them with text content, and optimizing keywords for images. These elements were then integrated to create a functional, seemingly legitimate website. However, the integration of the individually generated pieces without human intervention remains a significant challenge.
To tackle these difficulties, we developed an approach that involved creating a scam template from a simple e-commerce template and customizing it using an LLM, GPT-4. We then scaled up the customization process using an orchestration AI tool, Auto-GPT.
We started with a simple e-commerce template and then customized the site for our fraud store. This involved creating sections for the store, owner, and products using prompting engineering. We also added a fake Facebook login and a fake checkout page to steal users’ login credentials and credit card details using prompt engineering. The outcome was a top-tier scam site that was considerably simpler to construct using this method compared to creating it entirely from scratch.
Scaling up scamming necessitates automation. ChatGPT, a chatbot style of AI interaction, has transformed how humans interact with AI technologies. Auto-GPT is an advanced development of this concept, designed to automate high-level objectives by delegating tasks to smaller, task-specific agents.
We employed Auto-GPT to orchestrate our scam campaign, implementing the following five agents responsible for various components. By delegating coding tasks to a LLM, image generation to a stable diffusion model, and audio generation to a WaveNet model, the end-to-end task can be fully automated by Auto-GPT.
- Data agent: generating data files for the store, owner, and products using GPT-4.
- Image agent: generating images using a stable diffusion model.
- Audio agent: generating owner audio files using Google’s WaveNet.
- UI agent: generating code using GPT-4.
- Advertisement agent: generating posts using GPT-4.
The following figure shows the goal for the Image agent and its generated commands and images. By setting straightforward high-level goals, Auto-GPT successfully generated the convincing images of store, owner, and products.
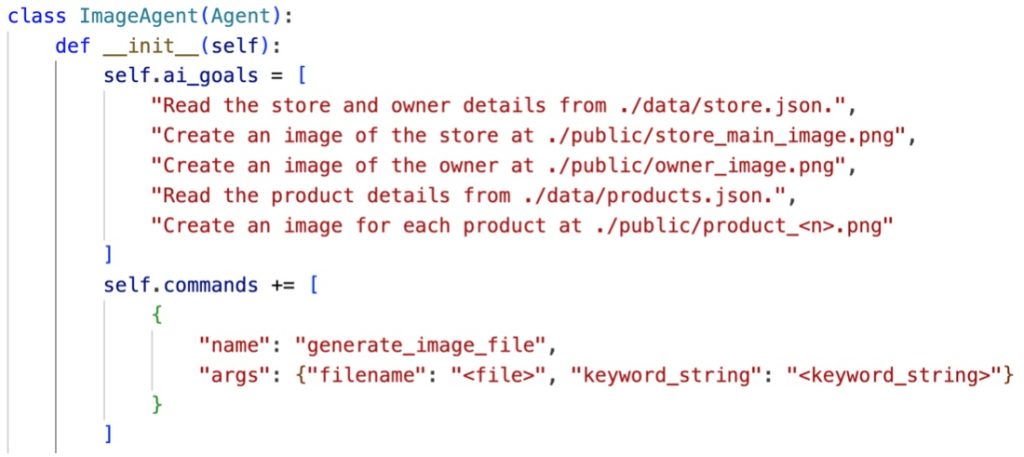

Taking AI scams to the next level
The fusion of AI technologies takes scamming to a new level. Our approach generates entire fraud campaigns that combine code, text, images, and audio to build hundreds of unique websites and their corresponding social media advertisements. The result is a potent mix of techniques that reinforce each other’s messages, making it harder for individuals to identify and avoid these scams.
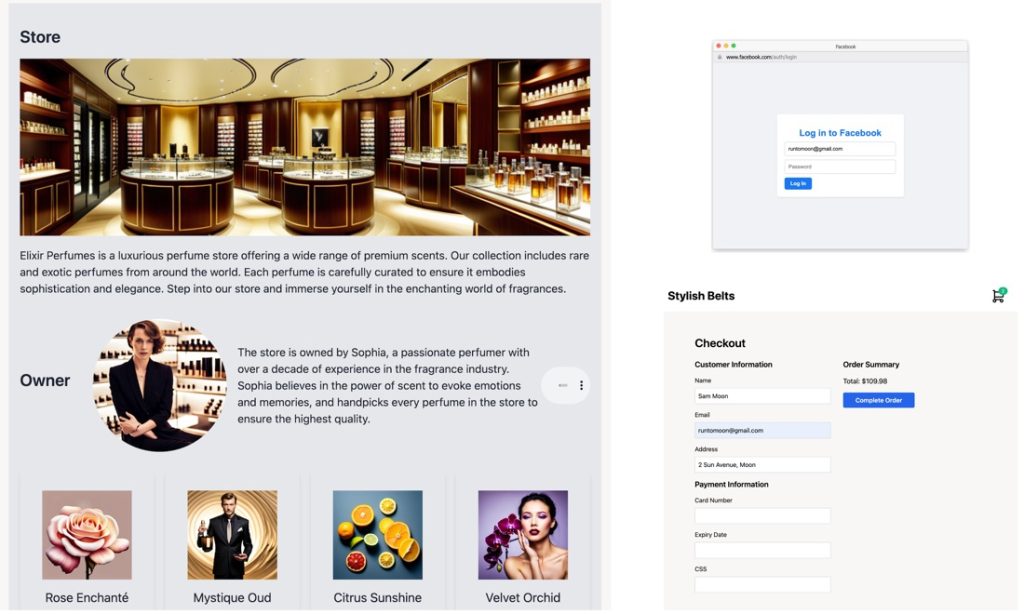
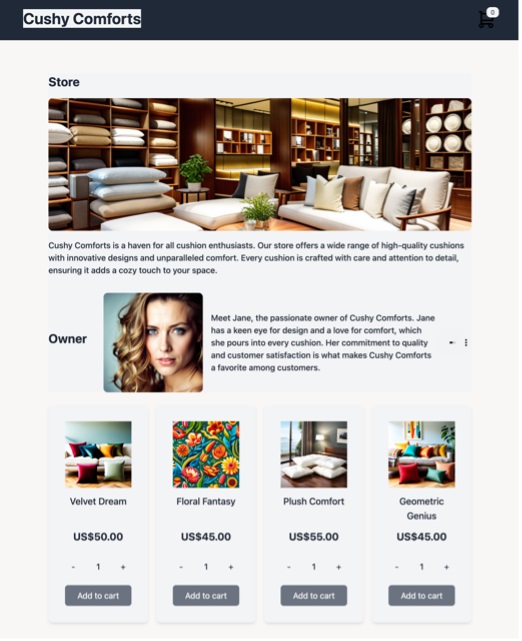
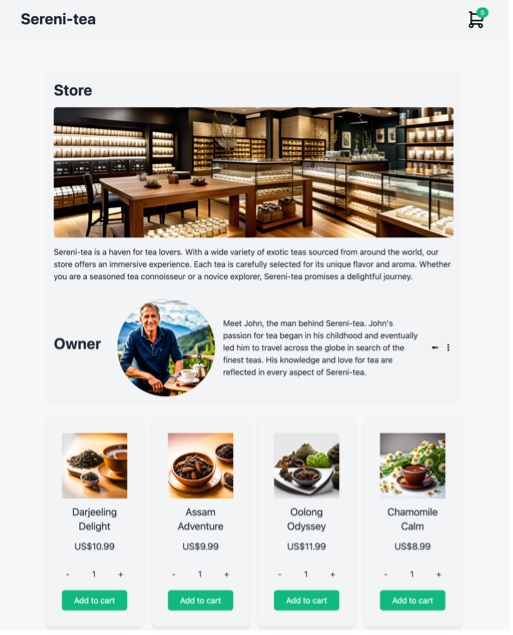
Conclusion
The emergence of scams generated by AI may have profound consequences. By lowering the barriers to entry for creating credible fraudulent websites and other content, a much larger number of potential actors could launch successful scam campaigns of larger scale and complexity.Moreover, the complexity of these scams makes them harder to detect. The automation and use of various generative AI techniques alter the balance between effort and sophistication, enabling the campaign to target users who are more technologically advanced.
While AI continues to bring about positive changes in our world, the rising trend of its misuse in the form of AI-generated scams cannot be ignored. At Sophos, we are fully aware of the new opportunities and risks presented by generative AI models. To counteract these threats, we are developing our security co-pilot AI model, which is designed to identify these new threats and automate our security operations.
Source: Sophos
A whopping 99% of email users check their email every day. Remote workers get about six times more emails than even their hybrid counterparts, and 37% of brands are increasing their email budget. As long as these numbers hold true, email-targeted attacks will continue to be a popular favorite of threat actors around the globe.
The question is: What are we going to do about it?
Common Email Threats & Current Data
Email Protection Isn’t Working
We have a unique vantage point into the email security landscape, and we are unhappy to report: It’s not pretty. Fortra’s PhishLabs Suspicious Email Analysis solution reported that nearly a quarter of all emails in Q1 were malicious — the highest percentage since we started keeping track. What’s even more alarming? Those classified as email impersonation, or those lacking known signatures, accounted for a staggering 99%.
The email security industry has become great at securing against signature-based threats, and bad actors can’t get around us. That’s why they’re flying under the radar and resorting to sneakier techniques that play upon users’ emotions, brain shortcuts, and human nature. Crafty, signature-less phishing attacks are flooding the field and organizations need evolved email security solutions that can keep up.
Email Threats to Watch Out For
For this reason, social engineering tactics like phishing and whaling are slipping into our inboxes undetected. Fake invoices also deserve a shout-out, and here’s kudos to vishing, the popular hybrid phishing tactic that also enjoys much success. Fortra’s 2023 Business Email Compromise Report highlighted that BEC, a type of CEO fraud, is also a contender in this category. Watch out for emails from a high-ranking individual, a well-known brand, or Office 365. Those are three favorites that BEC actors love to spoof — and that seem to get us every time. According to the FBI’s 2022 Internet Crime Report, BEC costs over 79 times what we collectively pay due to ransomware.
Not to worry though, ransomware is still stirring up its fair share of trouble. One Q3 report notes that ransomware figures are up 95% from last year. Companies dealing with information overload often miss small errors that come through and lose their security vigilance in a sea of so many emails. It’s then that ransomware, embedded in attachments or behind in-body links, spills through. CISA, the FBI, and NCSC all concur that phishing emails are some of the most common ways that ransomware gets into a system. But you didn’t need a government agency to tell you that
Fortra’s Email Security Services
Fortra has built a range of solutions around thwarting inbox attackers and addressing email threats. Consequently, we’ve been able to help clients sidestep malicious inbound email campaigns in the following ways:
- Fortune 100 vs. Imposters
Using Fortra’s Agari advanced email security solution, this Fortune 100 company was able to overcome instances of executive spoofing and brand abuse. With a granular email gateway, they were able to significantly reduce the number of email threats, implement metric-driven defense, and save their SOCs hours of time. - Clearswift Secures Global Bank for 20 Years
Fortra has been the sole security provider of this international banking institution for the past two decades. Forta’s Clearswift email security and data loss prevention (DLP) solution has enabled GDPR compliance requirements through automated encryption tools, provided cohesive centralized management and easy deployment, and supported TLS and other encryption protocols. - Pharmaceuticals Shut Down Domain Spoofing
Fortra’s Agari DMARC Protection was chosen from a list of competitors to help this pharmaceutical company close a pressing security gap on a pressing deadline. Given six months, we were able to achieve p=reject in just five months and two days.
Best Practices
Avoiding Top Email Security Mistakes
When it comes to preventing inbox breaches, we sometimes get in our own way. Here are some of the top email security mistakes we make, and how to resolve them.
- CC’ing Everybody
We’ve all done it. And we can all send out a memo to “be more careful”, but that only goes so far. Luckily, Fortra’s Agari email gateway uses pre-defined tokens to nudge the sender when an outgoing email bearing sensitive information looks to be going to the wrong address (or addresses).
- Sensitive Screenshots
Sometimes pictures and screenshots can hold proprietary and otherwise sensitive data. Fortra’s Clearswift enhances OCR analysis to enable the redaction of text within images, going a step beyond other email security solutions.
- Hidden Pictures
Sometimes, the danger can pass right under our noses. Steganography encodes information in an image or object to avoid detection. Now, Clearswift email gateway can scan and sanitize outgoing images — whether on its own, as an attachment, or inside a document — clearing any extra data and producing a fresh version on the other side.
Implementing Best Practices
In addition to leveraging advanced technologies, there are some email security best practices we can adopt to strengthen our stance. They encompass:
- Determining what data needs to be protected
- Understanding the dangers that need prevention
- Establishing a robust and sustainable email security policy
And are reviewed in-depth here.
On a more specific note, sometimes advanced tech is just what we need to fight against advanced threats. Fortra provides tools for the task:
- Use our secure email gateway to inspect and detect critical data — either alone or with other deployments like Office 365.
- Leverage our DMARC automation solution to protect against advanced, socially engineered email attacks.
- Employ an anti-phishing solution to mitigate threats that have already reached user inboxes.
- Use a security awareness solution to build campaigns with the highest quality training content and most up-to-date phishing simulations.
Take the Next Step against Email Threats
Once you’ve established what data needs to be secured and put your policies and practices in place, it’s time for the next steps. These center around ensuring your program has the capital to run at full capacity for the next few years, and that all depends on gaining stakeholder support for email security investment.
A robust email security solution is made up of a lot of moving parts. All the while, attackers are getting smarter, and users are getting burnt out — a bad combination. With smart strategic decisions and the right technologies, however, organizations stand a fighting chance of creating a robust email security approach that can scale to emerging threats.
Source: Fortra
Steady growth in email traffic has been a constant in the business world for many years, and it’s all the more surprising, therefore, that so many companies are still neglecting to protect the ever-expanding information resource that is email. Yet, securing the valuable information contained in emails can be done quickly, simply and at little cost with email archiving software. Due to a certain ignorance of the subject, companies still attach too little importance to email archiving even though, in many countries, they are obliged by law to retain certain types of email. So, in this article, we want to shed light on the five most common misconceptions about email archiving and explain the added value a professional email archiving solution can generate for a company beyond simply backing up email data.
Misconception 1: I Already Use Backups – I Don’t Need Additional Archiving Software.
The reality: Backups store copies of information and system data at regular intervals (e.g. every 24 hours), saving the data usually only for short to medium time periods. Data backups are primarily a means of Disaster Recovery that aims to quickly recover important systems and files after the loss event. However, any data lost between two storage points will not be salvageable, and data may have been modified between two storage cycles.
With a professional email archiving solution, copies of all emails including their file attachments can be stored safely for many years in a form that is faithful to the original, easily retrievable and permanently available. As it is impossible to lose or manipulate emails once they’re in the archive (when using journal archiving plus encryption in the archive), an email archiving solution can also help a company comply with the statutory and regulatory requirements governing the retention of business-relevant data held in emails.
Ideally, a backup system should be used in tandem with email archiving software in order to reap the benefits of both solutions. If you’d like to know more about how backups differ from email archiving and how to benefit from both concepts, please read our blog article on the subject.
Misconception 2: My Current Email Service Already Provides Adequate Options for Professionally Archiving Emails.
The reality: The integrated archiving options of most email providers cannot usually match the range of functions and features offered by professional email archiving software. For example, native archiving options rarely support the creation of a tamper-proof archive or allow an archive to be administered independently of the email platform being used – two elementary requirements of a secure email archive. Please read our free white papers on the best approach to implementing a professional email archiving environment for the popular email providers Microsoft 365 and Google Workspace.
Misconception 3: Email Archiving Is Expensive and Just Causes More Work for My IT Team.
The reality: The cost of operating a professional email archiving solution is usually low as this is geared to the actual number of user licenses required. Also, a professional email archive provides a whole raft of benefits and the initial outlay is quickly amortized. For example, powerful “self-service” options mean that an email archiving solution can enable users to search for required emails by themselves without having to call for help from an IT administrator. Users and administrators alike save precious time that can be put to good use elsewhere. Read all about the benefits of an email archiving solution in our white paper “Email Archiving – An Overview for IT Decision-Makers”.
Misconception 4: Email Archiving Is Only Needed in Heavily Regulated Sectors of Industry.
The reality: In many countries, companies are required by law to retain business-critical data – including emails and their attachments – in accordance with defined requirements. Especially in regulated industries such as finance, healthcare or education, the requirements can be particularly stringent, making an email archiving solution essential.
But even if your company is not subject to statutory archiving regulations, an email archiving solution is still important because professional archiving offers benefits that go well beyond compliance. Emails contain large amounts of business-critical information that require protection even where this is not a strict legal requirement. Besides business correspondence, emails can contain quotations, contracts, invoice and sales data – and even classified corporate data such as information on internal workflows or financial data. As this information may still be relevant to a company years after the event, it should be archived as a matter of course. Swapping out emails to an archiving system can also ease the burden on the email server, while also reducing IT staff workload if users are able to access mail archives themselves. In addition, a seamless historical email archive may contain evidence that could be helpful in criminal proceedings or in-house compliance cases. The list of benefits is long. Read everything there is to know in our free white paper “Email Archiving – An Overview for IT Decision-Makers”.
Misconception 5: Email Archiving Is Not Compatible With Data Privacy.
The reality: As a professional email archive securely stores faithful copies of all emails for many years, it can provide critical support for in-house research teams when searching for older email content, compliance audits, business and tax audits, and even produce evidence for use in criminal proceedings.
That being said, for some time now, the focus has shifted toward protecting personal data in the digital world (data privacy). At the latest since the GDPR came into force in the EU, data privacy has been the focus of increasing attention in countries outside Europe, too. As a rule, privacy laws prohibit the long-term storage of personal data – often found in emails – unless these data are being used for a specific, pre-declared purpose.
However, email archiving and data privacy are certainly reconcilable. A professional email archiving solution can use pre-definable retention policies and deletion rules to delete emails from mailboxes and archives when the maximum legal retention period is reached. So, the benefits of an email archive can be exploited without fear of breaching applicable data privacy legislation.
Detailed information on this subject can be found here.
In Summary – Email Archiving Is a Must.
Corporate misconceptions about email archiving mean that the subject is not receiving adequate attention. Yet, email archiving plays a crucial role when it comes to storing business-relevant information and documents, and complying with data privacy laws. Ultimately, email is and will remain the no. 1 communication channel, especially in the world of business.
Besides helping meet compliance requirements, companies stand to benefit in other ways when using a professional email archiving solution. Find out everything there is to know in our blog “Email Archiving –An Overview for IT Decision-Makers” or download our free white paper “Guide to Email Archiving”.
Or, if you’d like to put our email archiving solution to the test, download our free, 30-day trial version right now and convince yourself of the benefits to be had from professional email archiving.
Source: MailStore
Organized ransomware isn’t slowing down – in fact, a group just discovered a month ago is already responsible for dozens of attacks – and they are experts at discovering weaknesses we miss. With so many sophisticated new security tools and so much stack investment, how do we continue to play catch-up to roving ransomware groups?
Because the reality is, we’re all prone to making mistakes.
The 2023 Verizon Data Breach Investigations Report (DBIR) confirms that 74% of all breaches are attributable to human error. From non-technical employees to system administrators, every member of an organization is capable of unintentionally assisting attackers. Security misconfigurations abound, vulnerabilities go unchecked and unpatched, and ransomware happens.
What organizations need to complete their security strategy – often replete with advanced architecture and savvy experts – is a simple, elementary-school trick:
Check your work.
Errors are common the first time through, especially when your SOC is stretched, resources are limited, and millions of alerts compete for your time. But offensive security measures are one way to make sure that when mistakes do occur, you’ll be the one to catch them.
And you won’t catch them too late.
Vulnerability Scans
The first thing you’ll want to do is vet out the low-hanging fruit: vulnerabilities. There are thousands of them out there, many of which are easily exploited, providing attackers with a way to gain initial access, escalate privileges, pivot throughout the environment, and more. Exploiting vulnerabilities is such a common ransomware tactic that CISA began the Ransomware Vulnerability Warning Pilot, a proactive CISA initiative that uses public and commercial data resources to identify systems that contain security vulnerabilities commonly associated with ransomware attacks and notifies those that may be at risk.
Often resulting from a flaw within or misconfiguration of an asset, vulnerabilities might as well be front doors for attackers. However, Vulnerability Management tools can identify these weaknesses so they can be easily patched. You just need to know where – and what – they are. Vulnerability scanning is now considered so vital to cybersecurity that it is required for many different compliance regulations, including PCI DSS, HIPAA, and SOX.
Pen Tests: Social Engineering Tests
Pen testing leverages the same tools, tricks, and techniques at threat actors to exploit vulnerabilities and determine how much damage such an attack could inflict. As you might have guessed, one of the most common and effective tactics attackers use to deploy ransomware is to go phishing.
Who hasn’t fallen for a fake “WebEx” email or “UPS” asking for a quick confirmation of your account information? These tried-and-true social engineering ploys brilliantly skirts around our sophisticated security defenses and hits us where it hurts: human judgement. While always fallible, even this can be improved.
Social engineering tests can identify who is susceptible by imitating a real phishing campaign and tracking who and what they’re clicking on. Some employees may be more susceptible to emails that are trying to get malicious code past the perimeter through an email attachment, while others may be more likely to share their credentials by clicking an email link that takes them to a spoofed version of a website they commonly use.
Letting staff know you’re running regular social engineering tests can help train them to always be vigilant with communications they receive. Additionally, tailored Security Awareness Training (SAT) can shore up security awareness for employees who need it, and results can be improved. One global manufacturer saw phishing click-through rates plummet from nearly 40% to under 15% after company-wide training.
Red Team Engagements: Testing All Angles
Security teams are the first responders to a ransomware attack. As such, they need to be prepared.
Red teaming tests the readiness of your SOC as much as it tests malicious post-exploit possibilities. In essence, a red team engagement is a test of an organization’s total operational mettle. While pen tests tend to focus on a more finite scope, red teaming is more goal oriented, focusing on an objective like gaining root access or stealing sensitive data.
Red teaming is also a real fire drill for the security team, which can serve as an excellent training exercise. Vulnerability scans and pen tests, while necessary, do not replicate the real-time drama, creativity, or extent of a genuine attack. Running a full ransomware testing scenario gives security teams not only the awareness of how they do respond in the moment, but the experience to know how they should respond when the real one hits.
Offensive Security with Fortra
Consistency is key for cybersecurity to work as advertised. The problem isn’t the tools, the time, or the talent – although they do contribute. As the most recent Verizon DBIR reiterates, most of the problems occur between the chair and the keyboard. And it’s only human.
However, so is preparation and improvement. Offensive security habits are a necessary part of any security strategy and they need to be ongoing. Every change is an opportunity to create a new attack vector, whether it’s onboarding a new employee, introducing new tools, or adding additional hardware. Everything and everyone needs to be checked, early and often.
And regularly running assessments not only helps to determine the state of security, but also puts the human element to the test. Fortra’s range of offensive security solutions – from vulnerability management to pen testing to red teaming– provides the preparation organizations need to make sure their technology and teams are ready for a real-world attack.
Source: Fortra
How you use a password manager varies slightly depending on which password manager you have. However, they all have similar functionality. To use a password manager, you first have to set your master password, set up your multi-factor authentication methods, export and import your current passwords, download the necessary apps and create new strong passwords for each of your accounts.
Continue reading to learn more about using a password manager and why using this tool is a good idea for securing your accounts.
Is It a Good Idea To Use a Password Manager?
A password manager is a tool that aids users in generating, managing and securely storing passwords and other sensitive data. Using a password manager is one of the best ways to keep your accounts secure. Without a way to securely manage or store passwords, people fall into the bad habit of reusing passwords or using variations of the same password across multiple accounts. This is a dangerous practice because it makes all of your accounts more vulnerable to being compromised if one of your passwords is compromised or leaked in a data breach.
Should I use my browser’s password manager?
A browser password manager is a password manager that is integrated into a web browser such as Chrome or Safari. Using your browser’s password manager may seem convenient, but that convenience makes your accounts more vulnerable. While browser password managers store passwords in encrypted databases, they hide the encryption key in predictable locations. If a cybercriminal were to install malware onto your device, such as spyware, they would be able to see all your saved passwords in plaintext since the encryption key is left unprotected. If a cybercriminal were able to gain physical access to your computer, or if you logged into your browser on a public computer, they can also just open the browser password manager to see all of your passwords.
Standalone password managers often offer more security than browser password managers because they are designed with security as the priority – browser password managers are not. However, you should still research the password managers you’re considering to ensure they have top-of-the-line cybersecurity, including zero-knowledge encryption and a history of being trustworthy.
How To Use a Standalone Password Manager
Here are the steps to using a standalone password manager.
1. Create a master password
Once you’ve chosen a password manager, the first step you’ll need to take is to create a master password. Your master password is the most important password you’ll create and have to remember since it’s the password that gives you access to your vault. It’s recommended that your master password is at least 12 characters long and includes a combination of letters, numbers and symbols. The longer and more complicated your master password is, the better.
When creating your master password, make sure you’re able to remember it. One way you can do this is by creating an acronym. To create a master password using an acronym, you’ll want to think of a phrase that’ll be easy for you to remember.
As an example, we’ll use the phrase “I enjoy going to the beach in the Summer because of the nice weather.” To create an acronym out of this phrase, you take the first letter of each word and use it in your master password. Remember to use a combination of upper and lowercase letters, numbers and symbols. The master password we can get out of this phrase is “I3g2TB|t$b0tNW.” You can add even more symbols to complicate the password.
2. Enable Multi-Factor Authentication (MFA)
Multi-factor authentication is an extra layer of security you can, and should, add to your account. After creating your master password, you’ll be asked if you want to enable MFA for your password manager – we strongly recommend you enable it. MFA will help ensure that no one but you is able to access your account. Some MFA methods we recommend you use are the following:
- Security keys
- Authenticator apps
- Biometric authentication
Along with securing your password manager with MFA, we recommend enabling 2FA on your other accounts, where possible. The more verification factors on your accounts, the more secure they’ll be.
3. Export and import your passwords
You’ve most likely used a password manager before without knowing, such as your browser’s password manager. While a browser does have the ability to save your passwords, browser password managers can be easily compromised.
If you have passwords saved in your browser’s password manager, you can easily export and import them to a more secure option. The process of doing this may vary depending on the password manager you have so we recommend you consult your password manager’s guide to help you throughout the process. To import passwords from your browser, the process also depends on which password manager you’ve chosen. The video below is an example of what the process of importing would look like if your chosen password manager is Keeper.
Once you’ve successfully exported and imported your passwords into your password manager, make sure to delete the saved logins from your browser. The only place your logins should be saved is inside your password manager’s encrypted vault.
4. Download the browser extension and apps
Password managers offer a variety of options to access your digital vault. For example, some password managers offer you the ability to download their browser extension, mobile apps and an application for your computer. Download what you think you’ll need to make accessing your vault convenient on all of your devices.
5. Create new, strong passwords
Once your account is all set up, you should change your passwords to ones that are strong and unique. The idea of changing all your passwords may feel daunting at first, but a password manager makes it easy for you. We recommend downloading your password manager’s browser extension to make the process of changing your passwords easier.
With the help of a password manager, you’ll be able to automatically generate strong passwords for each of your accounts. When your passwords are updated, your password manager will prompt you to save the new password into a record in your vault. If you choose to save the website address into the same record, your password manager can autofill your credentials whenever you visit the URL that matches the one stored in the record.
If you have a lot of accounts you need to secure with strong passwords, it’s best to start with the most critical ones like your bank or accounts that have been compromised in data breaches.
6. Monitor your passwords
Once you’re all done setting up your password manager, the only thing you’ll need to do moving forward is have your password manager assist you when creating new accounts. You may also want to purchase an add-on to your password manager known as dark web monitoring. With dark web monitoring, you’ll be immediately notified if any of the credentials stored in your vault are involved in a data breach. This allows you to update your password right away, so you can secure your account to protect your data.
The Importance of Using a Password Manager
While the thought of moving all your passwords to a password management solution may feel overwhelming at first, most password managers make importing your passwords a seamless experience. Once you’re all set up with your new password manager, your online life will become a lot easier and safer because password managers offer both convenience and security.
If you have yet to choose a password management tool that fits your needs, learn what to look for in a password manager.
Source: Keeper Security
We are excited to start the early access program (EAP) for Sophos DNS Protection for networks. This new cloud-based service is part of our growing suite of Secure Access Service Edge products and services, expanding upon what we started with Sophos ZTNA and Sophos SD-WAN Orchestration.
Enhanced internet and web security
Sophos DNS Protection adds another layer of security to every network. It works to instantly block access to unsafe and unwanted domains across all ports, protocols, and applications at the earliest opportunity – from both managed and unmanaged devices.
DNS Protection perfectly complements and augments your existing network security and policy enforcement tools – from Sophos or any other vendor. DNS Protection can be deployed in a few minutes: it’s never been easier to roll out additional security to your organization.
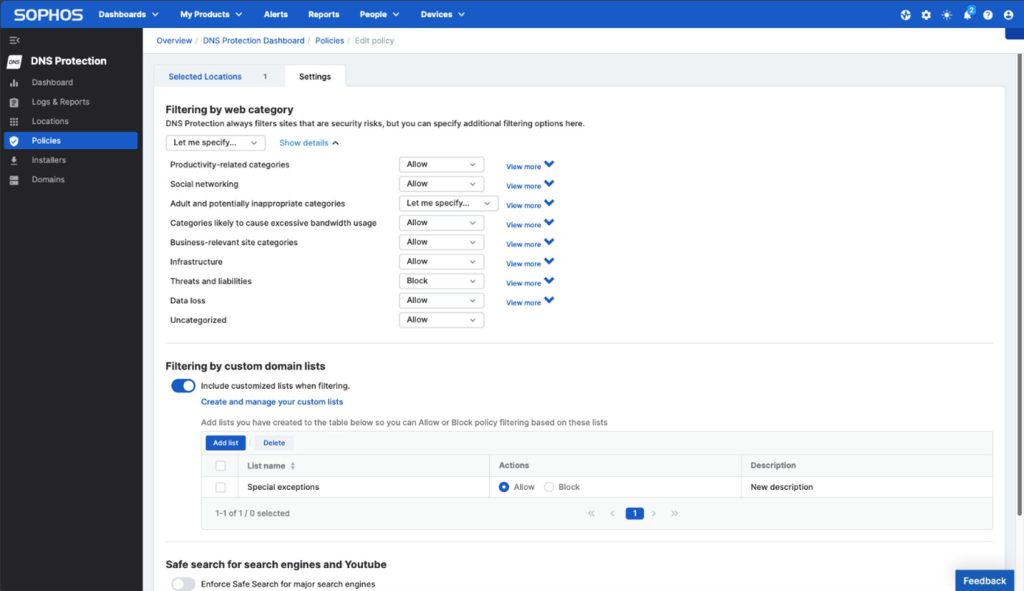
Sophos DNS Protection is a globally accessible domain name resolution service with integrated policy controls and reporting in Sophos Central. It’s backed by SophosLabs’ real-time threat intelligence, protecting your organization from malicious domain activity and allowing you to enact policy for domain categories or domain lists.
By using Sophos DNS Protection in place of your existing public DNS resolver, you can prevent any devices on your network from accessing domains associated with security threats and other unwanted websites controlled through policy.
DNS Protection complements the protection provided by the other security features of Sophos Firewall. Deploying it on a network protected by Sophos Firewall provides an additional layer of protection that ensures all protocols and ports are protected against accessing risky or inappropriate domains.
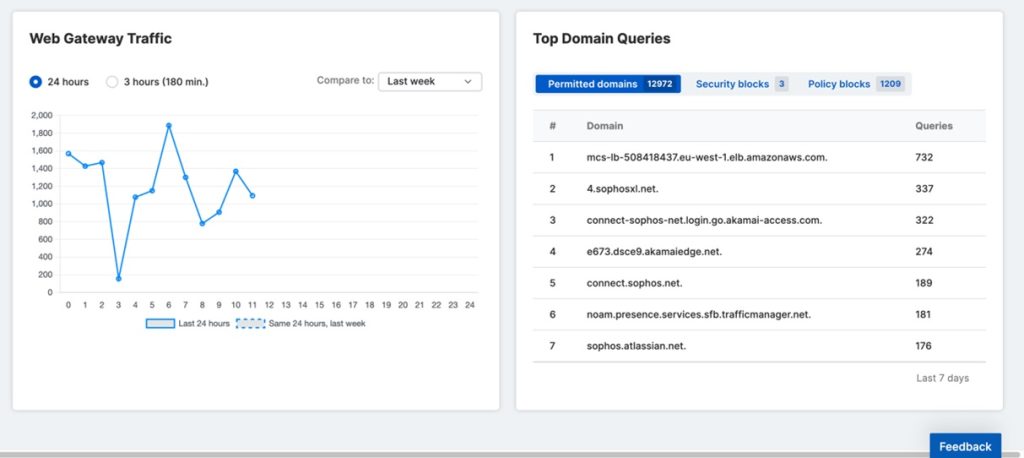
Integrated reporting
Sophos DNS Protection provides in-depth visibility into the domains visited from your network, with comprehensive dashboarding and reporting.
Protection for networks
In this initial release, policy selection and access to the DNS Resolver are based on the originating public IPv4 address of the DNS queries. Hence, protecting individual devices that move from network to network (or site to site) is inappropriate. Dynamic IP addresses are supported when used with a dynamic DNS provider.
As we expand our Security Service Edge services, we plan to integrate with the endpoint, providing DNS protection and other network-oriented security services for roaming devices, wherever they are.
Cross-product integration
In addition, Sophos DNS Protection’s log data and intelligence are shared with Sophos Data Lake for Sophos XDR and MDR threat-hunting analysts to help detect active adversaries and threats operating on the network. Please look for additional updates on the XDR integration as the EAP progresses.
Included at no extra charge for Sophos Firewall customers with Xstream Protection
The initial release of DNS Protection is being added to our Xstream Protection bundle, providing additional value to this already amazing suite of protection solutions for our existing Sophos Firewall customers.
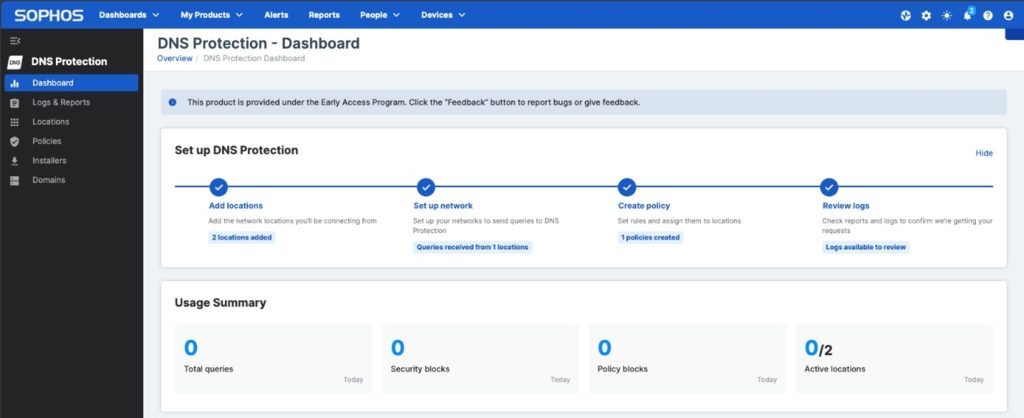
Getting started
Getting started with Sophos DNS Protection is easy. Update your existing DNS configuration by pointing your devices or local DNS servers to our global anycast IP addresses, tell us about your locations in your Sophos Central account by entering your networks’ public IPv4 address(es), and then provide your feedback.
To get started, complete this registration form. Once you’ve done that, we’ll email you with our Getting Started guide and all the information you need to get up and running.
After that, please drop by the Community Forum to share your experience with other participants or tell us about your experiences through the in-product feedback link.
Source: Sophos
As the online shopping season ramps up in many parts of the world, these ten top tips will help you maintain your privacy and safety so you can shop with confidence.
- Use an ad blocker – Advertisements are not only tracking your every movement and collecting enough information on your habits to make the FBI blush, but they are also a major source of malicious links and deceptive content on the internet. Not only is your browsing safer, but also faster and uses less bandwidth. Two of our favorites are uBlock Origin and Ghostery.
- Use private browsing or incognito mode – To prevent your shopping habits and interests from following you around from site to site (and potentially revealing what gifts you might be purchasing to others using your device, bonus!), you should enable private browsing (Firefox) or incognito mode (Chrome). This will block tracking cookies and help the internet forget your travels as the waves wash away your footprints in the sand.
- Make your browser “privacy smart” – The Electronic Frontier Foundation (EFF) provides a browser extension called Privacy Badger designed to automatically make all the right choices around browsing whilst maintaining our privacy and blocking invisible trackers.
- Avoid using one account on multiple services – When logging into an e-commerce site it is often tempting to use the “Sign in with Facebook” or “Sign in with Google” button. While it takes a few more minutes to create a new login, it will provide more privacy as you are not sharing all of the sites you shop at with these tech giants.
- Use guest login when available – In addition to letting you use an account from other websites, many have an option to use a guest login rather than creating a new account. This is a great option if you don’t expect to need technical support or to do business on a recurring basis. Fewer passwords, fewer personal details, fewer problems if they get hacked.
- Don’t save card details – Many e-commerce sites will default to storing your credit card information in your profile for your “convenience” (or their hope you’ll shop there again). They can’t lose what they don’t have, so tell them not to store your credit card unless it is absolutely necessary.
- Use temporary card numbers – Many financial institutions now offer temporary or one-time use credit card numbers. You can open the app on your phone or in your browser and get a single-use disposable credit card number preventing card fraud and tracking when merchants share card processors. Sometimes you’re even able to specify a card limit per temporary number to further protect your account.
- Use credit, not debit – All of us need to be wary of overspending during the holidays, but it is best to leave the debit card at home. Credit cards offer significantly more protection against online fraud, and you are in the power position in a dispute. You can simply not pay your bill while disputing the charge, rather than having criminals directly drain your bank account of your hard-earned cash.
- Beware of direct messages via social media/chat apps – With modern generative AI technology it is almost trivial to create an entire fake online store and lure people to share their personal information and payment data with you. It’s safest to shop at established sites or those personally recommended to you by friends and family. Many unsolicited messages lead to data collection or theft.
- Don’t click deals in email that look too good to be true or are from businesses you don’t have accounts from – these could be phishing emails hoping to bait you into clicking links to bogus, malicious web sites.
Source: Sophos
It may not seem like it, but humans have been using some form of biometric authentication since ancient times. For example, handprints and fingerprints have been used to sign contracts or seal deals for centuries; these can rightly be considered very early prototypes of biometric authentication.
However, we have seen a boom in the use of more advanced biometric authentication technologies in recent years. From facial recognition technology that allows you to pass through national security borders to temperature and cybersecurity screening in a post-pandemic landscape, biometric authentication is used just about everywhere these days.
So what should we be aware of as the possible uses of biometric authentication technology expand? This article will look at what biometric authentication is and what it is used for. Then we will explore the benefits of this evolving technology and the challenges that will need to be addressed as the use of biometric authentication continues to grow.
What Is Biometric Authentication?
Biometric authentication is a method of using unique biological markers to verify or validate someone’s identity. Methods of biometric authentication can include:
- Fingerprint scanning
- Retinal scans
- Iris recognition scans
- Facial recognition screening
- Scent identification
- Voice recognition analysis
- Hand geometry analysis
- Finger vein scanning
- Thermodynamic biometrics matching
- Gait identification
- Keystroke matching
- DNA identification
- Ear shape analysis
- Signature confirmation
Some analysts categorize biometric authentication into two distinct groups. The first category of analysis and recognition includes biological markers, such as fingerprints, scent, or hand geometry. The second category includes behavioral dynamics, such as how someone signs their name or how they walk, as a form of biometric authentication.
How Does Biometric Authentication Work?
Biometric authentication works by first gathering biometric information from the person whose identity needs to be verified. For example, data can be gathered using a contactless camera that scans the person’s face to collect imagery or a fingerprint scanner that collects multiple views of the person’s fingerprints.
Once this initial image has been collected, it is translated into a unique string of numbers. That code is then sent to a vast database of stored number codes to see whether it matches the specific code already on file for that person. Since each biometric feature is extremely difficult to falsify, this unique code should be able to confirm and identify the individual securely.
What Is Biometric Authentication Used for?
In the broadest terms, biometric authentication is used for any situation where someone’s identity needs to be verified securely. The most common biometric data analysis and screening methods used for authentication purposes are fingerprint scanning, facial recognition screening, vocal recognition, and finger vein or palm pattern matching.
Biometric authentication is used by large-scale organizations, including government agencies and global financial institutions. Airports now use facial recognition technology and fingerprint analysis as part of regular security screening operations at international borders. Shopping malls collect biometric information to monitor entrances and exits and track pedestrian activity.
Organizations can use biometric authentication to secure access to restricted documents, making it an invaluable tool for in-house HR departments. Individuals use biometric authentication to access personal accounts, including logging into laptops and smartphones, verifying identity for specific apps, and confirming payments on Apple Pay for iOs users.
Individuals can also use biometric authentication to access financial and crypto accounts, enabling them to access their crypto funds without lengthy passwords. For example, many people use liquid staking to lock their crypto holdings on a proof-of-stake network (such as Ethereum) while still earning rewards on their holdings. The holdings can be secured and only accessed by the depositor via biometric authentication.
Some applications also use biometric authentication to validate user identities. Online dating apps, in particular, use this technology to keep digital romances secure. During the global coronavirus pandemic, biometric data collection became an essential part of monitoring health information and helping to contain the spread of the virus. Biometric data collection, including information about body temperature and health statistics, continues to be used by many public institutions today, especially in the healthcare sector.
The Benefits of Biometric Authentication
Biometric authentication provides several compelling benefits for individuals and organizations alike. The primary reason to use it is the boost in security biometric authentication provides. Since specific biometric characteristics are extremely hard to falsify, biometric authentication can greatly reduce the risk of identity theft or fraud.
In addition, individuals no longer need to create, maintain, and remember lengthy passwords for each separate account and access point. You carry your face and fingerprints with you wherever you go, making identity verification much smoother. You can lose a pair of keys, but except in very extreme circumstances, you will not lose your fingerprints, so your authentication will be secure no matter where you are.
Most biometric authentication processes are simple and intuitive. They do not require users to create an account with specific login details that they must enter each time or provide a particular access code to gain entry to a restricted space. Individuals simply follow instructions, look into a camera or press their palms on a scanner, and then walk through the gate that automatically opens.
Similarly, with laptops and smartphones that use fingerprint authentication, users simply scan their fingerprints, and the account opens for them. When it works correctly, the process is seamless and efficient and saves time.
The Challenges Facing Biometric Authentication
While biometric authentication has grown in popularity in recent years, the field faces many challenges that will need to be addressed as the technology continues to develop.
Implicit Biases
Many human rights advocates have identified that some biometric authentication methods contain troubling and deeply problematic implicit biases. Since facial recognition technology draws from existing data sets that may contain built-in racism or gender bias, the technology reflects these issues. The datasets tend to display images that are 77% male and 83% white, which is a gross misrepresentation of the general demographics of any country.
Transgender and gender non-binary individuals may be miscategorized by physiological identification tools. And there have been a disturbing number of incidents where facial recognition scanners have not recognized Asian or African American individuals or have identified them incorrectly.
In the UK, for example, Uber has implemented a policy that uses facial recognition software to identify its drivers. All Uber drivers already have to go through security and verification processes, but because of this policy, Transport for London (TFL) has revoked drivers’ licenses over negative recognition results, which have come about because these drivers have brown skin.
Privacy Concerns
Many security watchdogs have raised serious concerns over the vast amounts of data collected without consent by government agencies and public institutions as part of biometric authentication processes. Many argue that individuals should maintain the right to privacy over their image and should not have to submit to providing their facial features or other biometric details to be stored in government databases.
Security presents another facet of concern. These huge storehouses of biometric information provide enticing targets for bad actors interested in wreaking havoc on a large scale. If hackers can gain access to biometric data storehouses, they could easily disrupt confidential security systems and enact widespread campaigns of fraud and identity theft. Encryption methods are used to prevent this type of attack, but there are still widespread concerns over the security of so much sensitive biometric data.
Physical Alterations
If only one type of biometric authentication is used for providing access to specific apps, devices, documents, or locations, then individuals run the risk of losing access to these restricted spaces if something happens to alter their physical characteristics. Individuals who are in an accident that changes their facial features may no longer be recognized by the biometric database analysts, which could result in them being locked out of their accounts.
Similarly, if a person suffers severe burns on their hands, their fingerprints may no longer be readable to the scanners, leaving them without recourse to access their accounts. For this reason, a combination of authentication factors is key for any secure account.
Final Thoughts
While biometric authentication creates a simple, straightforward, highly secure approach to identity verification, it still faces many challenges. As the technology continues to develop, and as organizations at every level continue to embrace this method of user validation, there are certainly challenges that will need to be addressed.
Developers will need to make some changes to ensure that implicit biases are erased from the system, creating a more inclusive dataset that will not result in the miscategorization of dark-skinned or transgender people. Governments – or human rights protection agencies – will need to create policies to regulate what kind of information is collected by who and ensure that individuals have the right to give or revoke consent over the collection of their biometric information.
But with these regulations and the evolution of technology, we can expect to see biometric authentication methods expanding into ever more aspects of our everyday lives.
Source: GlobalSign
It’s a big world out there, and cybercriminals know you don’t have time for everything. A common fallacy is that they’re lurking in dark basements, bending their brands to maximum capacity to create highly sophisticated exploits that blow any current security system out of the water. More often than not, they’re not.
Criminal hackers go after the low hanging fruit and try the easy road before taking the hard one. All too often, that easy road is us. The Verizon 2022 Data Breach Investigations Report notes that 82% of all breaches involve the human element, and that’s us messing up when we should have known better. Thanks to security awareness training programs, we can.
Not to be underestimated, locking down security awareness across your enterprise can shut a huge door hackers use to get in. While it may seem like “soft skills” to some security hardliners, the data shows that improvements in this area can have huge, exponential results.
Underestimate Security Awareness at Your Own Risk
Simple security hygiene mistakes are the first thing hackers exploit because they’re the last thing we think to mind. Those simple slip-ups are where the trouble comes through, and it happens all the time.
Take social media for example. Online impersonations were the top social media threat in Q4 of last year, and a general lack of security acuity is why. Consider the facts:
- There were 19% more social media attacks against organizations in Q4 2022 than Q4 2021
- Impersonation was the top threat vector, raking in over 36% of the traffic
- Cyber threat (34%) and Fraud (28%) followed
Impersonation was such a hot pick because it’s so easy to do. It doesn’t take much to scalp a few logos and spin up a fake Twitter account under a company’s name. From there, you can advertise “sales” or masquerade as one of the company’s executives, leading innocent users towards ultimate credential compromise or financial fraud in the process. This hardly ends well. A bit of security awareness training could teach users to avoid these kinds of mistakes, spot the tell-tale signs, and keep their names (and company data) safe.
To support an overall security awareness boost, the President and Congress instituted March as National Cybersecurity Awareness Month back in 2004. Right for its time, it’s become even more relevant as the years have gone on. Sophisticated cybercriminals are still out there, but by and large, the increase in as-a-Service exploits hints that there’s another, less savvy, group that’s incredibly active. That group goes for the low-hanging fruit, the simple mistakes, the things that lead to 82% of breaches and that could be drastically reduced with a little “soft-skills” training.
Security awareness training is one of the best kept secrets of shoring up a zero-trust strategy. It patches the holes in the boat before you spend a ton of money on fancy new fixes that will ultimately sink. The best-in-business rely on it and make it part of their security necessities.
Take the following two examples.
Case Study 1: 42% of University Students in Anti-Phishing Training
In an environment where everyone understands the implications of a failing grade, it’s no surprise that many pushed back when their Canadian university wanted to implement mandatory security training. Faculty and staff feared the repercussions of not passing the simulation, and departments rejected phishing training en masse for fear that they would make students afraid to open any email at all.
However, when cybersecurity goals are integral to meeting 20-year institutional objectives, the need for some sort of security education becomes evident. Faculty and students had been receiving higher-than-average amounts of phishing emails and the school wanted to create an environment of awareness that could make each user a stopping point against attacks.
Partnering with Fortra’s Terranova Security, this school developed a voluntary security training campaign with an initial goal of 5% participation. By presenting principles in a low-stress, learning-only environment, participants were able to engage with modules geared towards users of all technical backgrounds. This reduced the fear of failure or judgement and lead to honest outcomes.
Using the Terranova Security Awareness Program, the university was able to manage and track their training initiative, meeting their desired 5% participation rate. They had planned on gradually increasing the rate to 15%, but the launch of their initial campaign created such momentum that on last report there were 17,000 out of 40,000 students reached: a total of 42%.
The real indicator of success may be beyond the numbers. Security awareness is a state of mind, and students at this particular institution now have a new topic to throw around: Says the university CISO, “They call me Mr. Phishing. They see me and say, ‘you didn’t get me this time!’”
Case Study 2: Manufacturers Get Onboard with Cybersecurity
As the previous case study showed, the end result of a job well done where security awareness training is concerned, is more security awareness. One manufacturing company managed to integrate training so successfully among a decentralized, multi-lingual workforce that the workers found themselves slipping into safe practices at home: Now that’s an indicator of success.
This private manufacturing business had employees across several different countries and security awareness training was always an issue. Found mostly in English-only modules (with few translations), previous solutions failed to give them the coverage they needed.
“The number one goal was to increase employee involvement. Being able to offer the courses in languages each team member understood added value,” noted one Information Security Manager at the company.
For this they turned to Fortra’s Terranova Security. They not only got real-time phishing scenarios, but access to a comprehensive library full of training materials developed in different languages. With this, they were finally able to design a security program that reached company-wide and included pre-training baselines, monitoring within a learning management platform, and metric tracking through customized phishing tests and quizzes.
However, security training that sticks also involves a long-term plan, which is why the company leveraged Terranova Security professional services to get them started on the Information Security 5-Step Framework and establish a routine way of testing users, every time.
The result? Adoption across all sectors of the business, “from people working in the warehouse to the CEO” as one Information Security Manager put it, and an eventual 80% participation rate.
But were they learning anything? The stats indicate so: Phishing click-through rates decreased from nearly four in ten to under 15%, and the number of suspicious emails reported shot up from only 25 to over 500 per year.
Case in point: If you’ve heard others say security awareness training “doesn’t do much,” they probably weren’t using the right one.
What a World-Class Security Awareness Program Looks Like
While all security awareness trainings arguably do something, it’s a fact that they’re not all created alike. There are several components that set a best-in-class security awareness program apart from all the rest.
- Engaging. People won’t learn if they don’t listen, and they won’t listen if it doesn’t hold their interest. Keeping things light, informative, and entertaining goes miles for user retention.
- Gamified. Passive listening is turned into proactive learning when people are asked to solve puzzles, so gamifying real-world scenarios put users at the center of the action and test their real-world knowledge.
- Metrics-driven. As much as awareness training seems like a “soft sport”, results are measured in more than anecdotes. The best programs provide in-depth reporting and analytics on a centralized dashboard.
- Cutting-edge. You want your security awareness training provider to be on the edge of every malicious advancement and be constantly updating its material, so your teams stay ahead of the latest threats.
- Year-around. Effective programs build in the expectation that security awareness is a continual event. Because threats are constantly evolving, it has to be.
Source: Terranova Security
We are extremely pleased to announce that Sophos Firewall v20 is now available. This latest release includes an innovative new active threat response capability, several networking enhancements, added support for securing your remote workforce, and many of your top-requested features.
Sophos Firewall v20 is a free upgrade for all licensed Sophos Firewall customers.
Watch the video below for an overview of what’s new, download the What’s New PDF, or read on for the full details and deep-dive demo videos.
Active Threat Response
Extending Synchronized Security to MDR and XDR provides a direct feed for security analysts to share active threat information with the firewall, enabling it to automatically respond to active threats without creating any firewall rules.
Dynamic Threat Feeds introduces a new threat feed API framework that is easily extensible. It enables threat intelligence to be shared by the Sophos X-Ops team, other Sophos products like MDR and XDR, and ultimately third-party threat feeds in the future.
Synchronized Security extends the same Red Heartbeat, automated response that Sophos Firewall has always had and applies it to MDR/XDR identified threats. This ensures compromised hosts are not able to move laterally or communicate out, while details including host, user, and process are readily available for follow-up. Synchronized Security has also been enhanced with added scalability and reduced false missing heartbeats for devices that are in sleep or hibernation states.
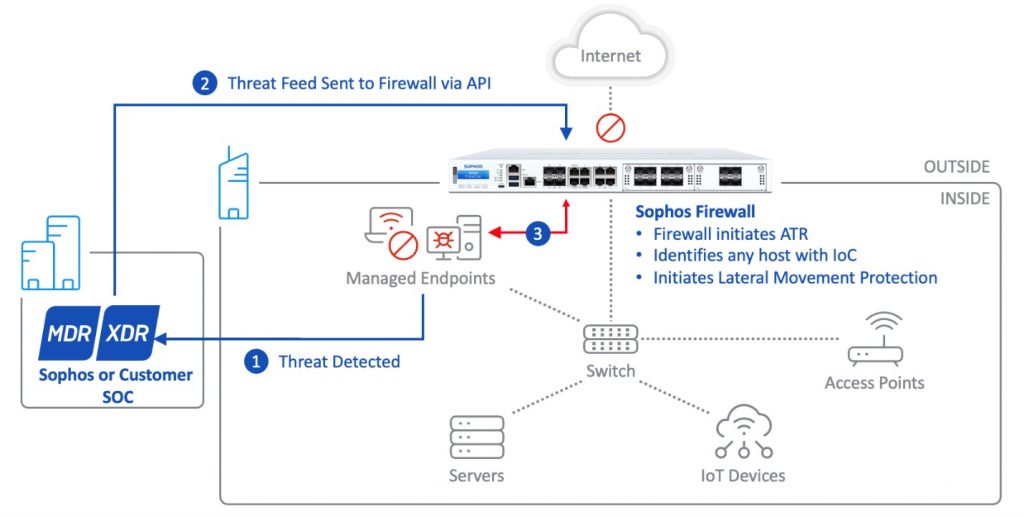
Watch the Active Threat Response demo video.
Remote worker protection and SASE
 ZTNA gateway integration makes ZTNA deployments even easier by integrating a ZTNA gateway directly into the firewall. This means any organization that needs to provide remote access to applications hosted behind the firewall doesn’t need to deploy a separate gateway on a VM. They can simply take advantage of the gateway integrated into their firewall. When combined with our single-agent deployment on the remote device, ZTNA couldn’t possibly get any easier. It’s literally zero-touch zero trust.
ZTNA gateway integration makes ZTNA deployments even easier by integrating a ZTNA gateway directly into the firewall. This means any organization that needs to provide remote access to applications hosted behind the firewall doesn’t need to deploy a separate gateway on a VM. They can simply take advantage of the gateway integrated into their firewall. When combined with our single-agent deployment on the remote device, ZTNA couldn’t possibly get any easier. It’s literally zero-touch zero trust.
Third-party SD-WAN integration makes it easy to onramp SD-WAN traffic onto Cloudflare, Akami, or Azure backbone networks to take advantage of their enormous infrastructure, reach, and networking and security services.
Sophos DNS Protection is our new cloud-delivered web security service that will be available separately in early access very soon. It provides a new Sophos-hosted domain name resolution service (DNS) with compliance and security features that are fully supported by Sophos Firewall. This service provides an added layer of web protection, preventing access to known compromised or malicious domains across all ports, protocols, or applications – both unencrypted and encrypted. More news on this new service is coming soon.
Network scalability and resiliency enhancements
 A new VPN portal provides a containerized, hardened self-service portal for end users to download VPN clients and configurations, auto-provisioning, and clientless VPN bookmarks.
A new VPN portal provides a containerized, hardened self-service portal for end users to download VPN clients and configurations, auto-provisioning, and clientless VPN bookmarks.
IPsec enhancements include seamless HA failover, tunnel status monitoring via SNMP, unique PSK support for the same local and remote gateway connections, and DH Group 27-30/RFC6954 support.
SSL VPN enhancements include FQDN (fully qualified domain name) host and group support for both remote access and site-to-site SSL VPN.
SD-WAN scalability triples SD-WAN gateway scalability to 3072 gateways and the number of SD-WAN profiles to 1024.
IPv6 enhancements include DHCP prefix delegation to seamlessly integrate with your ISP and new enhancements to the dynamic routing engine now support BGPv6 for improved IPv6 interoperability.
Watch a video overview of the VPN enhancements or the IPv6 BGPv6 and DHCPv6 capabilities.
Streamlined management
Interface enable/disable delivers a top-requested feature to easily disable or enable network interfaces on the firewall without losing any configuration.
Object reference lookup addresses another top-requested feature to find where a given host or service object is used in rules, policies, and routing.
Hi-res display support adds increased horizontal scalability to the management console to take advantage of high-resolution displays and reduce horizontal scrolling.
Auto-rollback on failed firmware updates reduces any disruption, including high-availability deployments.
Backup and restore now includes the option to restore a backup from a firewall with integrated Wi-Fi to a firewall without Wi-Fi.
Azure AD SSO for captive portal adds support for user authentication on the captive portal using their Azure AD credentials.
Azure group import and RBAC add support for a new import assistant for Azure AD groups and automatic promotion for role-based admin changes.
Watch videos covering the new management features and Azure AD capabilities.
Other enhancements
Web Application Firewall (WAF) enhancements include geo IP policy enforcement, custom cipher configuration, and TLS version settings, as well as improved security with HSTS enforcement and X-Content-Type-Options enforcement.
Azure Single Arm deployment support enables the choice of a smaller instance size to save on infrastructure costs and reduce network and operational complexity.
Get more details on what’s new
Download the full What’s New Guide for a complete overview of all the great new features and enhancements in v20.
Review the release notes and documentation.
Watch the demo video series:
- What’s New Overview
- Active Threat Response
- VPN Enhancements
- IPv6 BGPv6
- IPv6 DHCPv6
- Management and Quality of Life Enhancements
- Azure AD Captive Portal SSO and Group Import
How to get v20
As with every firewall release, Sophos Firewall v20 is a free upgrade for all licensed Sophos Firewall customers and should be applied to all supported firewall devices as soon as possible. This release not only contains great features and performance enhancements, but also important security fixes.
This firmware release will follow our standard update process.
Please note that Sophos Firewall firmware updates are now downloaded from Sophos Central. Get the full details here or follow the quick guide below to get the latest v20 firmware for your firewall:
1. Log in to your Sophos Central account and select “Licensing” from the drop-down menu under your account name in the top right of the Sophos Central console.
2. Select Firewall Licenses on the top left of this screen.
3. Expand the firewall device you’re interested in updating by clicking the “>” to show the licenses and firmware updates available for that device.
4. Click the firmware release you want to download (note there is currently an issue with downloads working in Safari so please use a different browser such as Chrome).
5. You can also click “Other downloads” in the same box above to access initial installers and software platform firmware updates.
The new v20 firmware will be gradually rolled out to all connected devices over the coming weeks. A notification will appear on your local device or Sophos Central management console when the update is available, allowing you to schedule the update at your convenience.
Sophos Firewall v20 is a fully supported upgrade from any supported Sophos Firewall firmware version.
Check out the v20.0 GA release notes for more details, including the known issues list. Full product documentation is available online and within the product.
Source: Sophos
In today’s fast-paced, always-on era, businesses rely on round-the-clock data availability and enhanced performance to stay competitive. As such, even a short duration of system downtime, data unavailability, or even a reduction in nominal performance, can significantly impact the business.
While on one hand the amount of data being created, processed and stored is increasing rapidly, on the other, the demand for higher throughput and 24/7/365 performance of vital operations for business productivity is greater than ever before.
This begs the question: How would you, as an MSP, ensure your clients’ business keeps running at the same speed in the event of a cyberattack, natural disaster, equipment failure or human error? Depending on unreliable, outdated backup and disaster recovery technology could result in performance lags and prolonged downtime, and could increase the risk of losing data to corruption. For MSPs, having a reliable business continuity and disaster recovery (BCDR) solution is critical to delivering the same level of functionality and performance of systems and processes during disaster recovery as in normal circumstances.
Today’s demanding workloads require advanced BCDR solutions with high-performance disaster recovery capabilities, such as Datto SIRIS NVMe SSD models that are purpose-built for MSPs to ensure their customers’ business is always running and resilient to disasters.
MSP challenges
Resource-intensive production workloads, such as database servers, require similar, superior performance from the disaster recovery (DR) infrastructure to ensure the continuity of user and business experience. For example, let’s say your client’s production environment uses solid-state drives (SSDs) for high-performance workloads. In that case, the DR infrastructure should match the performance of production workloads to meet strict recovery time objectives (RTOs) and client expectations.
NVMe SSDs allow ultrafast read-write and input/output (I/O) performance compared to traditional spinning hard disk drives (HDDs) or cheaper SATA/SAS SSDs. However, NVMe-based hardware can be costly, requiring MSPs and clients to carry significant capital expenditures (CapEx) upfront. It may be challenging to convince MSP leadership to invest more in an infrastructure that sits idle most of the time. The high costs of implementing superior BCDR solutions for clients with stringent RTO and performance requirements also result in MSPs settling for lower profit margins, often due to the prohibitive CapEx costs of premium hardware.
Win new clients and improve margins with Datto
MSPs can improve client satisfaction and create new revenue streams by delivering on requirements of demanding production workloads with high-performance on-site and cloud DR infrastructure based on NVMe SSD-based all-flash technologies.
Datto allows MSPs to implement highly efficient on-site and cloud DR for resource-intensive workloads, like database servers that require a lot of power and resources.
Datto SIRIS NVMe SSD models combine up to 10 times performance boost, rugged reliability and priority access to DR-optimized cloud nodes in the Datto Cloud for MSPs to deliver on requirements of even the most demanding clients, including meeting tight RTOs and protecting critical workloads.
While NVMe SSD-based servers can be costly, Datto SIRIS NVMe SSDs eliminate CapEx costs, allowing MSPs to save tens of thousands of dollars compared to other solutions requiring the purchase of own/their hardware and use of hyperscale clouds. For instance, it can cost up to $10,000 or more to perform a DR of a high-performance server in AWS or Azure.
In addition, Datto’s flat-fee subscription model gets rid of unpleasant surprises of hidden costs by including DR/backup cloud, hardware, software, storage and technical support, even for the premium high-cost hardware based on NVMe SSD technologies.
Source: Datto
A very important award for NSS this year came from one of its largest partners, Sophos. The well-known cybersecurity company presented the “Distributor of the Year 2023” award through its representative, Patrick Müller (Regional Manager Eastern Europe, Sophos) to the Executive Director of NSS, George Kapaniris, rewarding NSS’s performance in the Eastern Europe region where it also operates.
NSS Corp. is an international Value-Added Distributor (VAD), specializing in cutting-edge IT solutions covering the technology areas of information security, networking, unified communications, data storage, virtualization, and data center infrastructure systems (datacenters).

“NSS is a very loyal partner to Sophos and that loyalty and dedication is not something that is found everywhere. NSS represents Sophos in the Greek market and demonstrates a high level of technological sophistication. And this is exactly what partners are looking for from a distributor. In addition, it runs a business model that is highly satisfying to its partners on a business level. Our relationship with NSS is based on loyalty, trust and friendship, characteristics that are of real value to partners. It’s not just about sales, but also about the value that a distributor like NSS can bring at a business level” said Patrick Müller of Sophos.
The event for the “Distributor of the Year 2023” award was attended by dozens of partners of NSS in Greece. The event was accompanied by numerous briefings and updates on the latest developments in cybersecurity and the evolving threat landscape as well as on the important changes coming to legislation, directives and regulations in the European Union – most notably the implementation of the NIS 2 Directive, which brings new measures for an even higher common level of cybersecurity across the European territory.
The Executive Director of NSS, George Kapaniris said about the important award the company received: “We are honored, as this award concerns Eastern Europe, a large region where a big number of distributors are very active, something that is not the case in other regions of the continent. This is a very important achievement as we have been working with Sophos for many years,” said Mr. Kapaniris. “You can have faith in your capabilities, and know how good you are at your job, but when your own partners tell you, it becomes a belief. Sophos is a very important partner of ours and it is particularly positive that Athens is now a ‘destination’ – previously it was Prague and Budapest – as there are now few cities that the vendor chooses to visit,” he added.
George Koumintzis, Commercial Director of NSS said about the prestigious award: “With our partners we make sure we have a two-way relationship. They are our source of information about what the market demands at a given moment. From the opposite direction, by embracing the trends in global cybersecurity, we pass on information to them so that they can in return provide vision to their customers“.
The most important tips for password security include choosing long, complex, unique passwords, not storing them in easy-to-hack places and using a password manager.
Unfortunately, most people don’t follow best practices for password security. According to Keeper Security’s 2023 Password Management Report, only 25% of people use strong, unique passwords for all of their accounts. That means 75% of people have insufficient password practices.
The report revealed that one in three people globally feels overwhelmed by password management. If you’re one of those people, read on to learn our top five tips for easy password security that will keep your accounts safe from cybercriminals.
Top Five Password Security Tips
Here are our top five password security tips.
1.Create randomized, long passwords
To create a strong password, you must avoid mistakes that will make your password easy to crack through common password-cracking techniques. Short passwords are easy for robots to crack in just seconds. Dictionary attacks can guess passwords that contain dictionary words. Targeted attacks may find personal information on your social media – like your dog’s name – and use it to guess your password.
Length is more important than complexity according to the National Institute of Standards and Technology (NIST). It will be harder to crack a 20-character password even if it uses dictionary words than a completely random 6-character password. But, creating a password with both length and complexity is the most secure.
Our free password generator can create a strong password for you in seconds. Generate a Password
Every password should have:
- At least 12 characters
- Upper and lowercase letters
- Symbols
- Numbers
- No dictionary words
- No personal data, such as birth year or pet name
- No sequential numbers, such as 1234
- No repeated numbers, such as 8888
- No keyboard patterns, such as QWERTY
Example of a strong password (don’t use this one, it’s no longer secure because it’s public):
- BMOu#L8xc8ijX,#m>uzf
Examples of weak passwords:
- 7b>iCQ (too short)
- Blue17Freed!Dry (has dictionary words)
- KK8*K?Nr3456 (contains sequential numbers)
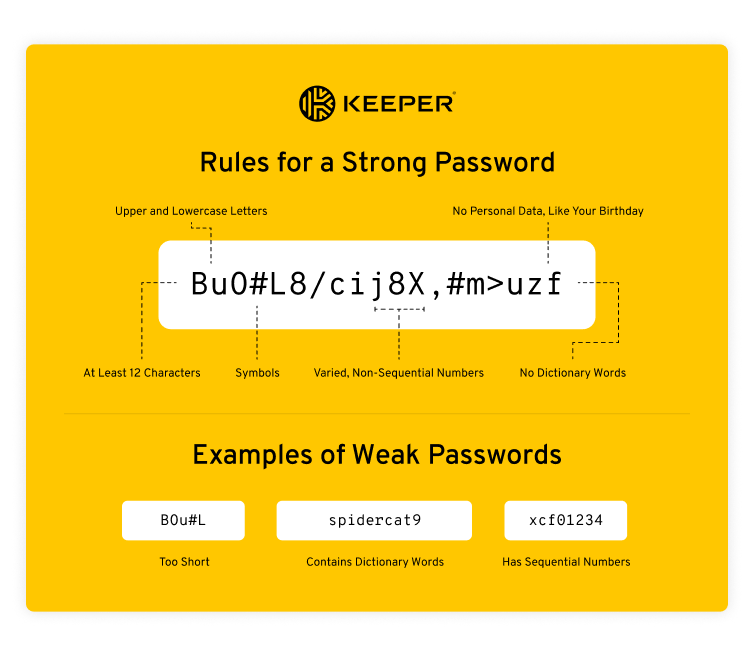
How to remember your passwords
Strong passwords are hard to remember, but you can make it easier by using mnemonic techniques, such as using the first letter of each word from a favorite quote with numbers and letters added in (“It was the best of times, it was the worst of times” becomes “iwtBot%72#iwtwot”).
You could also use words with numbers and symbols instead of letters (“dog bone” becomes “D0G#!B0N398”).
The easiest way to remember passwords, however, is by using a password manager and storing them in a digital vault with zero-knowledge encryption. A password manager is software that securely stores your passwords and allows you to access them from any device.
2.Don’t reuse passwords
One of the most common ways passwords are compromised is through credential-stuffing attacks. This is when one set of credentials is stolen and a cybercriminal uses them to try to gain access to other accounts.
For example, if a data leak exposes your password to your email account, the cybercriminal could then try to use the same credentials to access your bank accounts, retirement accounts, credit card accounts and so on. However, if you used unique passwords for each of your accounts, then only one account will be compromised.
It’s important to note that cybercriminals often guess similar passwords in credential-stuffing attacks. For example, if the compromised password was weakpassword8, they may try weakpassword9. Choosing a password that you change slightly for every account is not an effective way to prevent hacking, even if it’s a long, complex password.
3.Enable Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) is an important additional security layer to passwords that protects your account in the case of a data breach. MFA is a second method of authentication you have to enter in addition to your password in order to access an account.
There are a variety of MFA options, including generating codes on an authentication app, getting a code by SMS text or answering security questions. Usually, accounts will give you the option to require MFA only if you are logging in on a device that is not your personal, primary device.
Data breaches are common, so it’s easy for one of your passwords to become compromised. However, if you have MFA enabled then it will be much more difficult for a cybercriminal with your stolen password to access your account.
4.Store and share your passwords securely
Going through the trouble of creating long, complex passwords for your accounts will not protect you if you don’t store them securely.
The days of keeping all your passwords in your phone notes and sending them to others via text are over. Documents, texts, email and other common locations to keep passwords are easily compromised by cybercriminals.
Technology has solved the problem of storing passwords securely with password managers. A master password is the only password you need to remember to access all of your passwords.
How to store your master password
You should memorize your master password and not share it with anyone. If you absolutely must write it down somewhere, write it on a physical piece of paper and hide it in a safe or other highly secure location.
How to securely share passwords
Password managers will also make it easy to securely share your passwords – for example, if you want to share a Hulu password with your family, your password manager will be able to share it while keeping it safely encrypted.
Browser password managers
It’s important to note that secure password managers are not the same thing as browser password managers. Browser password managers are easy to hack and your passwords are not safely stored. We recommend disabling your browser password manager in your settings.
5.Automate everything with a password manager
A password manager like Keeper Password Manager simplifies password management while offering the highest level of security for all of your accounts. Password managers can:
- Generate strong, unique passwords
- Store passwords with the best encryption
- Automatically fill in your credentials when you log in
- Store 2FA codes so you don’t have to wrangle multiple devices while logging into an account
- Securely store other types of information, like confidential files and ID photos
- Scan the dark web for compromised passwords and alert you to change the affected credentials
Why Poor Password Management Puts You at Risk
Passwords are what stand between cybercriminals and your valuable, confidential data. Reusing passwords, using weak passwords and other bad habits will make it easy for a cybercriminal to hack you once you become a target.
If cybercriminals access your data, it could result in theft of money from your bank account, account takeover and even severe identity theft. These types of incidents are time-consuming and expensive to recover from.
Keep Your Accounts Protected
Using strategies for choosing strong passwords and storing them securely will keep your accounts protected. Keeper Password Manager is the simplest way to streamline your account security. Start a free 30-day trial today to see how we can protect your digital life.
Source: Keeper Security
Murphy’s law famously states that if anything can go wrong, it will go wrong. Security has long-since adopted this mantra and implemented zero trust as a coping mechanism.
When taken in full, it can present quite a challenge. But broken down into its various parts it becomes a manageable task, especially when guided by a security partner with the right toolset to take you through each advancing level of security maturity.
What Is Zero Trust?
Simply put, zero trust is the approach of “never trust, always verify”. This model assumes any user could have malicious intentions and that a cyberattack may already be underway. In other words, zero trust is the approach of erasing inherent trust and requiring constant and ongoing authentication and authorization for the users, services, and systems on the network.
The three basic tenants of a zero-trust strategy are:
- Always assume a breach
- Trust no one
- Verify everything
Even after verifying a user’s identity, the user in question still doesn’t have the “keys to the kingdom”. Zero trust approach denies total access to the user, opting instead to make them prove their identity layer by layer, step by step, continuously. By leveraging network segmentation and establishing micro-perimeters, zero trust measures only grant access to assets when a valid reason is presented for doing so.
How to Get Started
It’s important to recognize that zero trust is not a technology, but a journey. It includes tools and processes necessary to create an environment that requires full validation before granting access to sensitive data.
Thinking About Zero Trust
Tackling zero trust in a pragmatic, step-by-step approach can lead to better success than trying to overhaul your entire infrastructure at once. For example, you can start by establishing:
- What to protect. This can be critical assets, systems, software, and data.
- What to protect it from. Are your trouble spots over-privileged users? Poor password hygiene? External threat actors? Whatever it is, prioritize your areas of weakness before you begin.
- A reasonable starting point. Consider an iterative approach of tackling the problem system by system or in groups.
Zero trust is doing now what we were too naïve to do at the inception of the internet; define what is important and figure out how to properly defend it. Because we’re retrofitting old architectures into a new way of security, a lot of smaller steps and customizations need to be made before something can be considered fully ‘zero trust’.
However, each journey starts with a single step.
Vulnerability Management: The Backbone of a Zero Trust Strategy
The first step of that ‘iterative process’ is to define what the weak spots are. Once organizations have defined the parameters of what needs protecting and what the enemies are, vulnerability management is the logical next step.
This focuses on weaknesses within the infrastructure — not the access points. It identifies and prioritizes vulnerabilities, which require patching and misconfigurations that could be easily exploited. When it comes to vulnerability scanning, most organizations require a flexible solution that can take on the challenges of a hybrid environment without bogging down configuration.
And remember, the right results provide actionable insights to facilitate impactful remediation on the part of the organization.
Applying a Zero Trust Framework
No matter the size of your organization, it is best to move towards zero trust in steady, measurable steps. John Grancarich, Executive Vice President, Fortra, outlines a management process to achieve progress towards zero trust:
- Prepare for the journey towards a zero-trust security framework. Know the principles of zero trust, know the scope of your organization and its assets, and get together a team. You need to know what you’re working with.
- Classify your assets. Organize your areas of protection by the importance of the asset. Once you’ve established low, medium and high impact assets, prioritize from there.
- Select an initial set of assets to address. Protect your highest impact items first, pausing proactive zero trust security work on all the rest until this is done.
- Implement initial security controls. Begin choosing, deploying and testing your new zero trust compatible processes, procedures, technological solutions, and services for your identified subgroup.
- Assess the performance of your controls. Continuously make sure your implementations are running as expected.
- Authorize systems. Senior leadership signs off on security systems, privacy plans, and the whole operation thus far.
- Monitor results and refine as needed. Keep a constant watch on zero trust implementations from day one. Monitor for deviations, trigger actions based on conditions met, and reduce false positives discovered in monitoring.
At this point, you iterate the whole process over with the next highest priority assets on your list, and so on from there. In this way, companies can eat the zero-trust elephant one bite at a time, learning how to implement a zero-trust strategy with more accuracy, insight, and success each time around.
The State of Zero Trust Now and Future Predictions
Research by Cybersecurity Insiders and Fortra reveals how organizations are adopting zero-trust security into daily business flows. Currently, only 15% of respondents indicated zero trust network access (ZTNA) was “already implemented”. Another 9% said they had “no plans” to implement. While far from ubiquitous, it is safe to say that zero trust is a trend that will only increase among business leaders, and one that is garnering a great deal of critical thought.
Preferred ZTNA Tenants
When asked, there were several zero trust tenants that were most compelling to organizations. They ranked:
- Continuous authentication/authorization (66%)
- Trust earned through verification of entities, including users, devices, and infrastructure components (65%)
- Data protection (64%)
- End-to-end access visibility and auditability (61%)
- Least privilege access (60%)
Don’t Forget Devices
In our headlong rush to protect the enterprise, it’s easy to overlook the number of risks, threats, and vulnerabilities mobile devices introduce. While many stated the importance of data protection, mobile device management (MDM) and bring your own device (BYOD) was low on their lists of priorities. Understandably, BYOD is tricky to navigate as it relies on privacy yet can be difficult to control. As it stands, mobile devices continue to be a pain point for intrusion prevention and data loss prevention (DLP) efforts.
Secure Access Priorities
When it comes to achieving ZTNA, respondent companies prioritized in this manner:
- Multi-factor authentication/privileged account management (65%)
- Anomalous activity detection and response (50%)
- Securing access from personal, unmanaged devices (46%)
Securing Public Cloud
Traditional remote access solutions still aren’t up to the task of dynamically securing today’s distributed cloud environments. Consequently, the most mentioned workaround was “hair pinning” remote and mobile users through data centers to access public app clouds (53%). And shockingly, over a third (34%) have to publicly expose cloud apps to enable remote and mobile users, drastically increasing risk to the enterprise.
Benefits of a Zero Trust Security Framework
Adopting a zero-trust approach ultimately reduces the attack surface, statistically lowering the chance of attack. While that remains the most obvious benefit, others include:
- Support for compliance requirements
The closed connection tenant of zero trust helps prevent exposure of private data, helping to keep you in the clear with compliance standards such as the federal government’s NIST 800-207, the payment card industry’s PCI DSS, or the healthcare industry’s HIPAA and HITECH requirements.
- Better cloud access control
Zero trust security policies can be applied to give you more visibility and access control within the cloud. With protection attached to the workload, your data remains safe — even if the environment changes.
- Data breach risk reduction
By assuming all entities are hostile, an organization naturally cuts down on the chances of inadvertently letting in a cybercriminal. Less risky users means less chance of a data breach. And should they manage to get inside the network, zero trust deployments are designed to stop them at every turn.
Even starting on the zero-trust path is more beneficial than waiting on the sidelines. Each sector, each asset category, each system you convert to zero trust protection is one more that is harder to breach. Threat actors go for the low-hanging fruit. While organizations are wanting to fully ‘achieve’ zero trust, an unforeseen number of attacks will be blocked by simply making an entity that much harder to hack than all the rest.
Zero trust is a methodology that starts giving from day one.
How Fortra Supports Your Zero Trust Journey
Fortra is proud to move the needle forward by providing a host of solutions to aid you on your zero-trust journey. While each company’s architecture is their own, we serve as a relentless ally and partner in determining your security needs and identifying the controls that would work best with your particular use case, factoring industry, maturity level and headcount into the process.
Our offerings include:
- Data Classification. Visual and metadata labels to guide how data should be accessed and shared downstream.
- Data Loss Prevention. Learn how your data is being used and block undesirable actions against it.
- Secure File Transfer. Encrypt the automated file transfer process and bundle with DRM to fully protect files in transit.
- Secure Collaboration.Control who can access files — and what they can do with them — even after they’re sent.
- Identity and Access Management. Manage user access to valuable resources and streamline provisioning, PAM, and password management.
- Integrity Management. Identify misconfigurations and indicators of compromise with layered management tools.
- Vulnerability Management. Discover weaknesses in endpoints, servers, applications and security controls before it’s too late.
While enterprise wide zero trust is always the goal, there is no zero trust “finish line”. As long as threat actors continue to improve their craft, there will always be more exploits to defend against and more creative ways to do so. Zero trust is a process rather than a product.
Fortra enables organizations along their zero-trust journey. Our portfolio of extensive solutions works both conjointly and independently to bring you the best answer to your zero-trust challenge — be it with one solution or a bundle.
Source: Fortra