Looking into current Security Information and Event Management (SIEM) systems, one can notice that all of them attempt to meet certain criteria, such as the native support provided for different log sources and the design of modern features in order to perform data examination and analysis on the sheer volume of the generated log data.
Among these criteria, the compliance management initiatives and the availability of computer forensics capabilities lay at the heart of the discussion. In the present post, the issue under scrutiny is what is computer forensics and how can it be used in today’s world.
A Historic Perspective
Forensics has been around since the dawn of justice. The well-known examples of studying fingerprints or blood groupings and DNA have been used for a long time in order to determine the nature of a crime and locate the perpetrator. Around 1910, Albert Osborn became the first person to develop the essential features of documenting evidence during the examination process. Later, in 1984 the Computer Analysis and Response Team (CART) was established to provide support to FBI’s field offices searching for computer evidence.
Computer forensics, -also called Digital Forensics- has emerged due to the vast increase of cyber activity among the general public. This growth led to greater awareness of the importance of Computer Security and the protection against computer-facilitated crimes. However, the two terms are entirely different despite that they are often closely associated.
- Computer security focuses on techniques and technologies in order to prevent the unauthorized access on computer systems and mainly protect against violation of confidentiality, integrity and availability of data managed by the systems.
- Computer forensics is primarily concerned with the acquisition, preservation and analysis of data gathered by a compromised system after an unauthorized access has taken place.
Cyber Crime Calls for Forensics
Our dependency on computer systems has given way to novel cyber criminal activities. Theft of intellectual property, damage of company service networks, financial fraud, system penetration and data exfiltration are just few of the computer-facilitated crimes that are being committed even as we speak. They differentiate in terms of how the attack takes place, either as external or insider attacks, where a breach of trust from employees within an organization is involved.
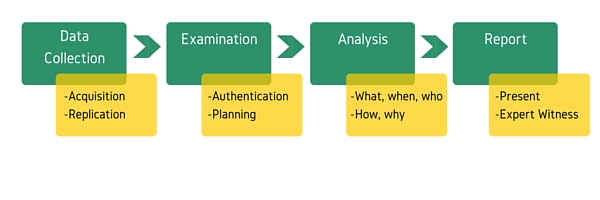
Forensics investigation always comes after the attack has been launched and detected, and it follows certain stages and procedures in order to guarantee that the collected digital evidence can be used by law enforcement to track and prosecute cyber criminals.
Why is Computer Forensics Needed?
Picture a hypothetical scenario where your organization’s premises have been breached by criminals who broke into and stole valuable assets like money, equipment or confidential reports. The first thing that any responsible executive would do is to evaluate the situation and call law enforcement investigators in order to examine the area and gather any useful evidence.
Now, let’s suppose that the crime had been committed electronically, by breaching the organization’s network, acquiring important data and getting access to undisclosed information. Keep also in mind, that the intruder could be an employee of the company using the organization’s computers. As with the case of a physical crime, the person in charge should evaluate the situation, which in the computer security case means to correctly evaluate the alerts coming from host and network intrusion detection and prevention systems (IDPS) and then use the correct tools in order to collect and analyze any data that could be useful digital evidence.
Computer forensics is the next step of the procedure, where you apply contemporary techniques to gather and preserve evidence from the computing devices of interest in a way that is suitable for admission in a court of law. Imagine how flexible the procedure can become if the appropriate tools for evaluating the situation have been preconfigured for dealing effectively with such cases. Finally, consider that cyber crimes occur much more frequently than physical ones, especially when referring to organizations as victims.
Strategic Planning for Business
Despite Dr. Wolfe’s definition, computer forensics as a science can also be used as application in cases that do not or do not want to involve a court of law. Especially in the case of an insider attack, forensics tools can be used to gather evidence that the executive can then use against the employee in order to prove his involvement in the attack. In general, if the organization is concerned about resolving any problems caused by computer security breaches, it would be reasonable to look into the advanced search capabilities of a SIEM platform and emphasize on the reporting and data visualization features of the SIEM solution. It will save valuable time and resources of an organization if its SIEM is set up in a simple and easy to use way for storing and locating data and instantaneously generating the appropriate reports or other graphic formats.
However, performance is less valuable without context in the forensics case. Much of the current debate in the computer security space tends to accentuate the ability of convergence between computer forensics and SIEM in the area of real-time security analytics rather than differentiate the two areas. The underlying issue is what features do the current SIEM solutions provide that can assist in data examination and analysis and which features should be included in a SIEM platform in order to satisfy some of the computer forensics requirements.
You can read the original article here.






