Have you ever thought how many accounts in your environment operate outside of your visibility and control? One of the biggest identity security blind spots, often ignored by organizations but frequently used by attackers – is Local Accounts.
Unlike domain-based accounts that security teams can easily detect and monitor, local accounts are left in the dark with limited to no visibility into their activity and privileges. This gap has become such a critical issue that the FBI recently issued a warning, urging organizations to disable local administrator accounts to reduce the risk of cyberattacks.
In this blog, we’ll explore the different security risks posed by local accounts, and how Silverfort’s new local authentications visibility feature helps organizations to close the blind spot.
Understanding local accounts: what they are and how they work
Local accounts exist in 2 main types: local user accounts and local administrator accounts. Let’s describe each type in more detail:
- Local user accounts
These are standard accounts with limited access permissions, typically used for basic access to an endpoint. Local users can log in and operate a system but lack administrative privileges to make any system-wide changes.
- Local administrator accounts
These accounts have full control over an endpoint, allowing users to install software, modify system settings and create new accounts. Built-in local admin accounts (for instance, default Microsoft Windows “Administrator” account) are often under high risk as they can be exploited by attackers for compromise and privilege escalation.
While domain accounts are centrally managed through Active Directory (AD) or an Identity Provider (IdP), local accounts exist only on individual endpoint. From an identity management perspective, the key difference between local and domain accounts is who manages them:
- Local accounts exist and are controlled on the individual endpoint. The user has full control on the system, including privilege access to critical settings, with no visibility from the security teams.
- Domain accounts, on the other hand, are managed centrally by domain administrators within Active Directory (AD) or an Identity Provider (IdP). Security teams have more visibility into domain accounts and the ability to enforce security controls on each user, with specific policies and restrictions configuration.
Local accounts are often used for administrative tasks or legacy systems to provide access to a specific computer or device, but lack of monitoring and advanced security controls offered by domain-based accounts.
The hidden risks of local accounts
From a security perspective, local accounts by themselves won’t cause major security risks. But not managing them properly can have serious impact on the organization. Main of these risks are lack of visibility, limited centralized management, and weaker security controls. These challenges make local accounts a prime target for attackers looking to move laterally and escalate privileges undetected.
Let’s focus on the identity security risks of local accounts in more detail:
1.Lack of visibility: a blind spot in authentication monitoring
One of the biggest risks of local accounts is that security teams can’t see what they can’t track. Unlike domain-based authentications, which are centrally logged and stored, local accounts’ activities are isolated into individual endpoints and do not have any records in AD or IdP logs. This means that any malicious activity, including failed logins, unusual access patterns or compromised credentials, makes it nearly impossible to detect it before it’s too late.
2.Limited centralized management: a security and operational nightmare
Local accounts are stored outside of the directory-based identity management scope. And security teams struggle not only on enforcing policies but even on tracking who has access to what. Many organizations rely on default passwords or static credentials for local accounts without proper credential rotation, which increases the risk of unauthorized access. Without any central authentications management, organizations have fragmented security controls that attackers can easily exploit for compromise.
3.Weaker security controls: an open door for attackers
Local accounts are rarely secured with strong security controls, like Multi-Factor Authentication (MFA) or other security controls, resulting in an easy target for attackers. Once a local account is compromised, it can be used to escalate privileges or move laterally across the environment without triggering any security alerts. This makes local accounts a critical blind spot in organization’s identity security posture.
How Silverfort enables local accounts visibility
With Silverfort you can now enhance your visibility into local accounts authentications, starting from Silverfort for Windows Logon version 2.1.3.
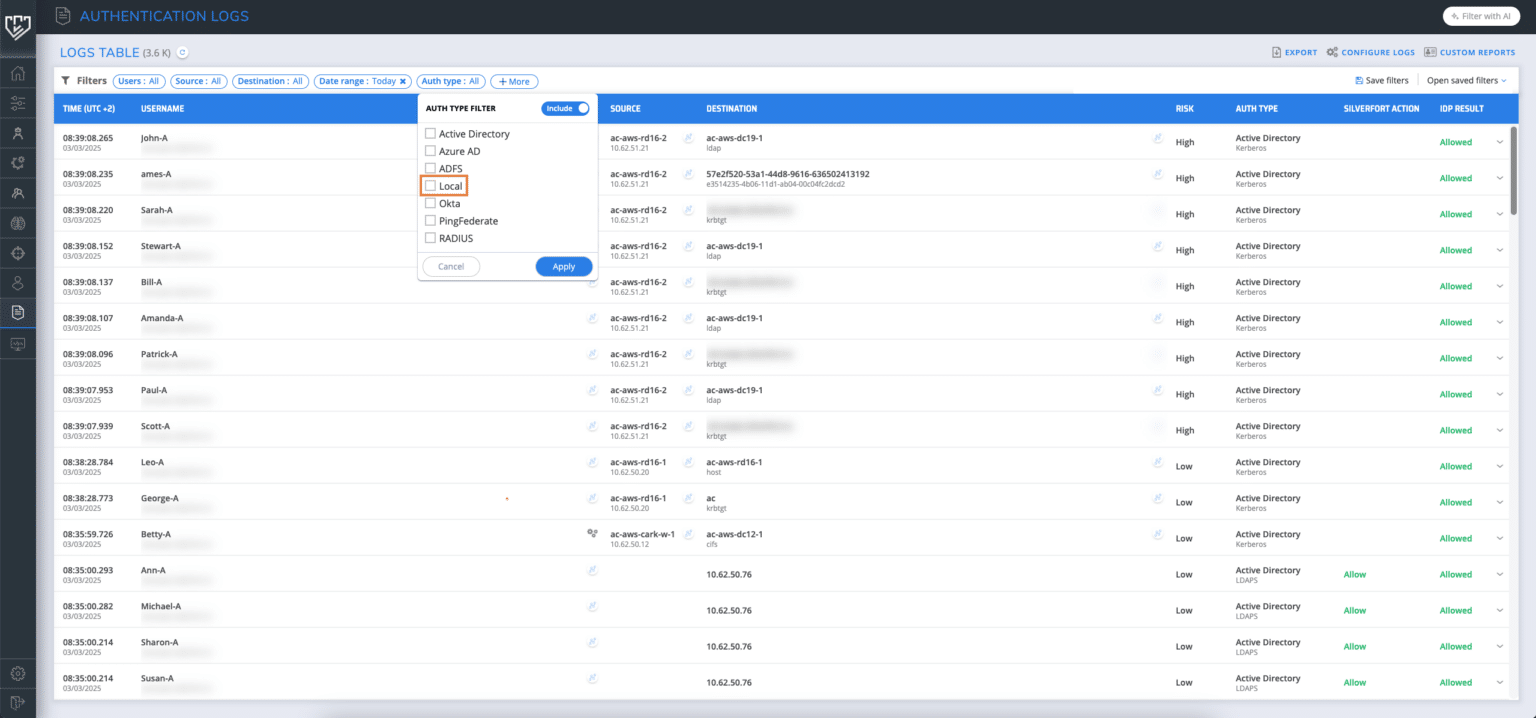
When a local user accesses a Windows machine with Silverfort for Windows logon installed, the authentication will be recorded with the auth type “Local”, and you will gain complete visibility into these access attempts from Silverfort Logs screen by filtering by Auth type = “Local”.
Video: Example of how to filter local user authentications in Silverfort’s logs screen
This new product capability allows you to track local logons for Windows. By filtering local account access attempts, you can quickly identify any malicious activities, including potential credential misuse.
Shining a light on local accounts: the first step to protection
Local accounts have always been seen as a security blind spot which attackers can utilize to create an easy entry to compromise an environment and stay unnoticed. Without visibility into the accounts’ authentication activities, you could not detect or respond to any of these malicious activities before they escalate.
With Silverfort’s real-time visibility into local accounts’ authentications, you can finally unlock new hidden layer of identity security from being completely unseen to monitor, track and investigate these identities. This is a solid ground to start towards complete security and protection of local accounts.
Ready to explore hidden local accounts in your environment? If you are an existing customer, please reach out to your customer success manager or schedule a call with one of our experts.
Source: Silverfort





